-

@ 2f5de000:2f9bcef1
2024-12-15 16:44:53
This Week I immersed myself in Bitcoin from multiple angles-technical, societal and personal. The journey included a marathon 32-hours of listening to [Rabbit Hole Recap (RHR)](https://fountain.fm/show/VDaMppQRUBZioj2XkaLn), an essential resource for Bitcoin insights. It's worth noting that I started from the begining and plan to make my way through the whole catalogue. Marty and Matt's timestamps, along with contributions from their guests, served as my roadmap. Using Fountain to stream, I also streamed sats-a small but extraordinary feature that allows users to stacks sats while compensating cretors directly through fractional donations.
## Revisiting Speculative Attack by Pierre Rochard (2014)
Now that [*Speculative Attack Season 2*](https://nakamotoinstitute.org/mempool/speculative-attack-season-2/) *(which I've not read yet)* has been released. I took the time to read Pierre Rochards influential essay, [*Speculative Attack*](https://nakamotoinstitute.org/mempool/speculative-attack/) and reflected on its timeless insights. Rochard argues that Bitcoin adoption isn't dependent on technological advancements or consumer preferences, but on economic realities. As fiat currencies weaken, Bitcoin won't enter the mainstream by persuasion but by necessity.
Critics continue to underestimate Bitcoin's inevitability due to their fiat biases and lack of financial insight. This year alone, mainstream media has been compelled to discuss Bitcoin-notably to Trump's endorsement of 'crypto.' Despite their attempts to shape narratives to suit their ideal visions, they've had no choice but to engage with Bitcoin's growing influence.\
\
As Parker aptly puts it 'Gradually, The Suddenly'
## Wassabi Wallet and the Privacy Imperative
An RHR interview (from early in the catalogue) with guest Adam Ficsor, CTO and Co-founder of Wassabi Wallet, sparked a deeper consideration of my digital footprint. Like many, I've spent years online neglecting privacy in favour of convenience. The discussion on CoinJoins reminded me of the importance of prioritising privacy, not just romanticising it.
Improving operational security (opsec) is now a personal focus. Resources like Jameson's *Cypherpunk Cogitations* and the Bitcoin Optech newsletter offer valuable guidance. While I've exercised caution, I recognise a need to address my laziness with opsec and take meaningful steps to protect my privacy. Time will reveal the results of these efforts.
## Caribbean Slavery amd Centralised Platforms
While exploring historical systems of control, I delved into the brutal realities of [New World slavery in the British Caribbean](https://aeon.co/ideas/how-did-slaveholders-in-the-caribbean-maintain-control). Enslaved elites, like drivers, were granted limited privileges to maintain order, creating divisions within the community. This divide-and-rule strategy highlights the fragility of oppressive frameworks, which began to crumble with events like the Hatian Revolution and humanitarian activism.
Interestingly, similar dynamics are visible with centralised plaforms like Twitter, LinkedIn, and Instagram. Verified accounts (the "blue checks") act as mordern day 'elites' with perceived freedoms. However, their autonomy is limited by the platforms centralised authority. Challenging the rules risks censorship and cancellation, proving their freedom is an illusion subject to the will of their overseers. Enhancing the argument further for protocols like Nostr to help people win back their freedoms.
-

@ b34b4408:acfb9667
2024-12-15 06:37:47
## เฮลิโอเทอราปีคืออะไร?

เฮลิโอเทอราปี (Heliotherapy) หรือการบำบัดด้วยแสงแดด เป็นศาสตร์การแพทย์ที่มีมาแต่โบราณ ชาวกรีกและโรมันใช้แสงแดดในการรักษาโรคและบำรุงสุขภาพ แนวคิดนี้ไม่ใช่เรื่องงมงาย แต่มีหลักการทางวิทยาศาสตร์รองรับ โดยเฉพาะในด้านผลของแสงแดดต่อการทำงานของร่างกายมนุษย์
## กลไกการทำงานของเฮลิโอเทอราปี
### การกระตุ้นการสร้างวิตามินดี

- แสง UVB ที่มีความยาวคลื่น 290-315 นาโนเมตร จะกระตุ้นให้ผิวหนังเปลี่ยน 7-dehydrocholesterol เป็น previtamin D3
- Previtamin D3 จะถูกเปลี่ยนเป็น vitamin D3 ด้วยความร้อนจากร่างกาย
- Vitamin D3 จะถูกตับเปลี่ยนเป็น 25-hydroxyvitamin D
- ไตจะเปลี่ยน 25-hydroxyvitamin D เป็น 1,25-dihydroxyvitamin D ซึ่งเป็นรูปแบบที่ใช้งานได้
- กระบวนการนี้ส่งผลต่อ:
* การดูดซึมแคลเซียมและฟอสฟอรัสที่ลำไส้
* การสร้างและซ่อมแซมกระดูก
* การทำงานของระบบภูมิคุ้มกัน
### การปรับสมดุลฮอร์โมน

- การกระตุ้นเซโรโทนิน:
* แสงสว่างผ่านดวงตาไปกระตุ้น Suprachiasmatic Nucleus (SCN)
* SCN ส่งสัญญาณไปยัง Pineal Gland
* เพิ่มการผลิตเซโรโทนินในช่วงกลางวัน
* ลดการเปลี่ยนเซโรโทนินเป็นเมลาโทนิน
- การควบคุมเมลาโทนิน:
* ช่วงมีแสงสว่าง จะยับยั้งการผลิตเมลาโทนิน
* เมื่อไม่มีแสง จะเริ่มผลิตเมลาโทนิน
* ช่วยควบคุมวงจรการนอนหลับ
* ส่งผลต่อการทำงานของระบบเมตาบอลิซึม
- การปรับระดับคอร์ติซอล:
* แสงสว่างช่วยกระตุ้นการหลั่งคอร์ติซอลตามธรรมชาติ
* ช่วยให้ร่างกายตื่นตัวในช่วงเช้า
* ควบคุมระดับน้ำตาลในเลือด
* มีผลต่อการตอบสนองต่อความเครียด
### ผลต่อระบบภูมิคุ้มกัน

- การกระตุ้นเซลล์ภูมิคุ้มกัน:
* เพิ่มการผลิต T-lymphocytes
* กระตุ้นการทำงานของ Natural Killer cells
* เพิ่มประสิทธิภาพของ macrophages
- การควบคุมการอักเสบ:
* ลดการผลิต pro-inflammatory cytokines
* เพิ่มการผลิต anti-inflammatory compounds
* ช่วยควบคุมการตอบสนองของระบบภูมิคุ้มกัน
- การเสริมสร้างการป้องกัน:
* กระตุ้นการสร้าง antimicrobial peptides
* เพิ่มความสามารถในการต่อต้านเชื้อโรค
* ช่วยในการซ่อมแซมเนื้อเยื่อ
### ผลต่อผิวหนัง

- การกระตุ้นเม็ดสีเมลานิน:
* ป้องกันการทำลาย DNA จากรังสี UV
* ช่วยกรองแสง UV ที่เป็นอันตราย
* ปรับสีผิวให้เข้มขึ้นเพื่อป้องกัน
- การซ่อมแซมเซลล์:
* กระตุ้นกระบวนการ DNA repair
* เพิ่มการผลิต collagen
* ช่วยในการรักษาแผลและการอักเสบ
### ผลต่อระบบประสาท

- การกระตุ้นการทำงานของสมอง:
* เพิ่มการไหลเวียนเลือดในสมอง
* กระตุ้นการผลิตสารสื่อประสาท
* ปรับปรุงความสามารถในการจดจำ
- การควบคุมอารมณ์:
* ลดความเครียดผ่านการปรับสมดุลฮอร์โมน
* ช่วยลดอาการซึมเศร้า
* เพิ่มความรู้สึกผ่อนคลาย
## การประยุกต์ใช้เฮลิโอเทอราปีในการรักษาโรค
### โรคผิวหนัง
- ***โรคสะเก็ดเงิน (Psoriasis)***

* กลไก: แสง UV ช่วยลดการเพิ่มจำนวนของเซลล์ผิวหนังที่ผิดปกติ
* ผลการรักษา: ลดความหนาของรอยโรค ลดอาการคัน ลดการอักเสบ
- ***โรคผื่นภูมิแพ้ผิวหนัง (Atopic Dermatitis)***

* กลไก: ลดการทำงานของเซลล์ภูมิคุ้มกันที่ทำให้เกิดการอักเสบ
* ผลการรักษา: บรรเทาอาการคัน ลดการอักเสบ ผิวหนังแข็งแรงขึ้น
- ***โรคด่างขาว (Vitiligo)***

* กลไก: กระตุ้นการทำงานของเซลล์สร้างเม็ดสี
* ผลการรักษา: กระตุ้นการสร้างเม็ดสีในบริเวณที่เป็นด่างขาว
- ***สิวอักเสบ (acne)***

* กลไก : แสง UV ช่วยฆ่าเชื้อแบคทีเรีย
* ผลการรักษา : ลดการอักเสบ และส่งเสริมเชื้อดีที่ผิว
### ปัญหาสุขภาพจิต
- ***ภาวะซึมเศร้าตามฤดูกาล (SAD)***

* ความถี่: ทุกวัน โดยเฉพาะในฤดูหนาว/ฝน
* กลไก: กระตุ้นการผลิตเซโรโทนิน ปรับสมดุลเมลาโทนิน
* ผลการรักษา: ลดอาการซึมเศร้า เพิ่มพลังงาน ปรับปรุงการนอน
- ***ปัญหาการนอนไม่หลับ หรือ อาการเจ็ทแล็ก (Jet lag)***

* ความถี่: ทุกวัน
* กลไก: ปรับนาฬิกาชีวภาพ ควบคุมการผลิตเมลาโทนิน
* ผลการรักษา: ช่วยให้นอนหลับง่ายขึ้น ปรับวงจรการนอน
- ***ความเครียดและวิตกกังวล***

* วิธีการ: รับแสงแดดอ่อนๆ พร้อมการเดินหรือทำสมาธิ
* กลไก: เพิ่มการผลิตเซโรโทนิน ลดระดับคอร์ติซอล
* ผลการรักษา: ลดความเครียด เพิ่มความรู้สึกผ่อนคลาย
### โรคกระดูกและข้อ
- ***ภาวะกระดูกพรุน***

* วิธีการ: รับแสงแดด เน้นช่วงข้อแขนขาที่มีอาการ
* กลไก: เพิ่มการสร้างวิตามินดี ช่วยดูดซึมแคลเซียม
* ผลการรักษา: ชะลอการสูญเสียมวลกระดูก เพิ่มความแข็งแรง
- ***การอักเสบของข้อ/โรคกระดูกอ่อน (Rickets)/เก็าท์ /รูมาตอยด์***

* วิธีการ: รับแสงแดดบริเวณข้อที่มีปัญหา
* กลไก: ลดการอักเสบ เพิ่มการไหลเวียนเลือด
* ผลการรักษา: ลดอาการปวด เพิ่มความยืดหยุ่น
### โรคระบบภูมิคุ้มกัน
- ***ภูมิแพ้ (Allergies)***

* กลไก: ปรับการตอบสนองของระบบภูมิคุ้มกัน
* ผลการรักษา: ลดความรุนแรงของอาการแพ้
-*** โรคภูมิคุ้มกันทำลายตัวเอง***

* กลไก: ปรับสมดุลระบบภูมิคุ้มกัน ลดการอักเสบ
* ผลการรักษา: ลดความรุนแรงของอาการ ยืดระยะเวลาระหว่างการกำเริบ
### ระบบเมตาบอลิซึม
-*** การควบคุมน้ำหนัก***

* วิธีการ: รับแสงแดด พร้อมการเดินเบาๆ
* กลไก:
- กระตุ้นการทำงานของต่อมไทรอยด์
- เพิ่มการเผาผลาญไขมันสีน้ำตาล (Brown Fat)
- ปรับสมดุลฮอร์โมนที่เกี่ยวข้องกับความหิว
* ผลการรักษา:
- เพิ่มอัตราการเผาผลาญพื้นฐาน
- ควบคุมความอยากอาหารได้ดีขึ้น
- ลดการสะสมไขมัน
- ***การควบคุมน้ำตาลในเลือด***

* วิธีการ: รับแสงแดดหลังอาหาร
* กลไก:
- เพิ่มความไวต่ออินซูลิน
- ปรับการทำงานของเซลล์ตับอ่อน
- ควบคุมการหลั่งฮอร์โมนที่เกี่ยวข้องกับน้ำตาล
* ผลการรักษา:
- ระดับน้ำตาลในเลือดคงที่มากขึ้น
- ลดความเสี่ยงภาวะน้ำตาลต่ำ/สูง
- เพิ่มประสิทธิภาพการใช้น้ำตาลของเซลล์
- ***การทำงานของตับ***

* กลไก:
- กระตุ้นการสร้างเอนไซม์ในตับ
- เพิ่มการไหลเวียนเลือดที่ตับ
- ช่วยในกระบวนการดีท็อกซ์
* ผลการรักษา:
- เพิ่มประสิทธิภาพการทำงานของตับ
- ลดการสะสมไขมันในตับ
- ช่วยการขจัดสารพิษ
- ***ระบบย่อยอาหาร***

* กลไก:
- กระตุ้นการผลิตน้ำย่อย
- ปรับสมดุลแบคทีเรียในลำไส้
- เพิ่มการเคลื่อนไหวของลำไส้
* ผลการรักษา:
- ระบบย่อยอาหารทำงานดีขึ้น
- ลดอาการท้องอืด ท้องเฟ้อ
- เพิ่มการดูดซึมสารอาหาร
ข้อควรระวังในการรักษา:
- ปรึกษาผู้เชี่ยวชาญหรือผู้ที่เข้าใจเรื่อง Heliotherapy หากมีโรคประจำตัว
- เริ่มจากระยะเวลาสั้นๆ แล้วค่อยๆ เพิ่ม
- ควรสวมเสื้อผ้าที่เปิดผิวหนังให้สัมผัสแสงแดดโดยตรง
- ไม่ควรทาครีมกันแดดในบริเวณที่ต้องการรับการรักษา
- หากมีอาการผิวแดง ร้อนผิว ให้หยุดรับแสงแดด
- หยุดทันทีเมื่อมีอาการแพ้หรือระคายเคือง
- ระวังเป็นพิเศษในผู้ที่มีประวัติแพ้แดด
## ความจริงที่ถูกบิดเบือน: ทำไมเราถึงกลัวแดด?
### อิทธิพลของอุตสาหกรรมความงามและการแพทย์

#### อุตสาหกรรมเครื่องสำอางและผลิตภัณฑ์ดูแลผิว
- ตลาดผลิตภัณฑ์กันแดด
* มูลค่าตลาดทั่วโลกกว่า 50,000 ล้านดอลลาร์
* อัตราการเติบโตเฉลี่ย 8-10% ต่อปี
* ผลิตภัณฑ์หลากหลายระดับราคา
* การพัฒนาสูตรใหม่ๆ เพื่อสร้างความต้องการ
- กลยุทธ์การสร้างความต้องการ
* การโฆษณาที่สร้างความกลัว
- ใช้ภาพก่อน-หลังที่เกินจริง
- นำเสนอผลการวิจัยแบบเลือกข้าง
- สร้างความกังวลเรื่องริ้วรอยและความชรา
- ใช้คำศัพท์ทางวิทยาศาสตร์ที่ซับซ้อน
* การสร้างความเชื่อผิดๆ
- "ต้องทาครีมกันแดดทุกวัน แม้อยู่ในร่ม"
- "ยิ่ง SPF สูง ยิ่งดี"
- "แสงแดดเป็นสาเหตุหลักของริ้วรอย"
- "ผิวขาวเท่านั้นที่สวยและดูดี"
#### อุตสาหกรรมอาหารเสริม
- ตลาดผลิตภัณฑ์วิตามินดี
* การเติบโตของตลาดอาหารเสริมวิตามินดี
* การผลักดันให้ใช้อาหารเสริมแทนแสงแดด
* ราคาที่สูงเกินความจำเป็น
* การสร้างความเชื่อว่าอาหารเสริมปลอดภัยกว่า
- กลยุทธ์ทางการตลาด
* การใช้ผู้เชี่ยวชาญทางการแพทย์รับรอง
* การนำเสนอผลการวิจัยที่สนับสนุนผลิตภัณฑ์
* การสร้างความกลัวเรื่องการขาดวิตามินดี
* การเชื่อมโยงกับปัญหาสุขภาพต่างๆ
#### อุตสาหกรรมการแพทย์และความงาม
- คลินิกผิวพรรณและความงาม
* การให้บริการทรีตเมนต์หลบแดด
* การรักษาผิวคล้ำเสียจากแดด
* การฉีดวิตามินและอาหารเสริม
* ทรีตเมนต์ฟื้นฟูผิวราคาแพง
- การแพทย์เฉพาะทาง
* การรักษาผิวหนังที่เน้นยาและเคมีภัณฑ์
* การผ่าตัดและเลเซอร์เพื่อความขาว
* การรักษาริ้วรอยด้วยวิธีราคาแพง
* การละเลยวิธีธรรมชาติบำบัด
#### เครือข่ายผลประโยชน์ทางธุรกิจ
- ความเชื่อมโยงระหว่างอุตสาหกรรม
* บริษัทยาที่ผลิตทั้งครีมกันแดดและอาหารเสริม
* คลินิกที่จำหน่ายผลิตภัณฑ์ของตัวเอง
* การร่วมมือระหว่างผู้เชี่ยวชาญและบริษัทผลิตภัณฑ์
* เครือข่ายการตลาดและการโฆษณา
- ผลประโยชน์ทับซ้อน
* ผู้เชี่ยวชาญที่เป็นพรีเซ็นเตอร์ผลิตภัณฑ์
* งานวิจัยที่ได้รับทุนจากบริษัทผลิตภัณฑ์
* การให้ข้อมูลที่เอื้อประโยชน์ทางธุรกิจ
* การปิดบังข้อมูลที่อาจกระทบยอดขาย
#### ผลกระทบต่อผู้บริโภค
- ด้านเศรษฐกิจ
* ค่าใช้จ่ายสูงในการซื้อผลิตภัณฑ์
* การเสียเงินกับทรีตเมนต์ที่ไม่จำเป็น
* ภาระค่าใช้จ่ายระยะยาว
* การลงทุนที่ไม่คุ้มค่ากับผลลัพธ์
- ด้านสุขภาพ
* การขาดแสงแดดที่จำเป็น
* ผลข้างเคียงจากผลิตภัณฑ์
* การพึ่งพาผลิตภัณฑ์มากเกินไป
* ปัญหาสุขภาพที่เกิดจากการหลีกเลี่ยงแสงแดด
### อิทธิพลทางสังคมและวัฒนธรรม
- ค่านิยมผิวขาวในสังคมเอเชีย
* รากเหง้าทางประวัติศาสตร์ของการแบ่งชนชั้น
* อิทธิพลของสื่อและดารานักแสดง
* ความเชื่อมโยงระหว่างผิวขาวกับความสำเร็จ
* แรงกดดันทางสังคมในการรักษาผิวให้ขาว
- การเปลี่ยนแปลงวิถีชีวิต
* การทำงานในออฟฟิศเป็นหลัก
* การใช้ชีวิตในห้างสรรพสินค้าและอาคาร
* การลดลงของกิจกรรมกลางแจ้ง
* ความเชื่อว่าการอยู่ในร่มปลอดภัยกว่า
### การบิดเบือนข้อมูลทางการแพทย์
#### การนำเสนอข้อมูลที่ไม่สมดุล
- การเน้นย้ำความเสี่ยงมะเร็งผิวหนัง
* นำเสนอสถิติแบบบิดเบือน
* ไม่แยกแยะระหว่างการรับแดดที่เหมาะสมกับการรับแดดมากเกินไป
* ละเลยการพูดถึงปัจจัยเสี่ยงอื่นๆ
* ไม่ให้ข้อมูลว่าการรับแดดอย่างเหมาะสมอาจช่วยป้องกันมะเร็งบางชนิด
- การละเลยประโยชน์ของแสง UV
* ไม่พูดถึงบทบาทของ UV ในการฆ่าเชื้อโรค
* ปิดบังข้อมูลเรื่องการสร้างวิตามินดีตามธรรมชาติ
* ไม่กล่าวถึงประโยชน์ต่อระบบภูมิคุ้มกัน
* ละเลยผลดีต่อสุขภาพจิต
#### การสร้างความเข้าใจผิดเกี่ยวกับวิตามินดี
- ความเชื่อเรื่องอาหารเสริม
* สร้างความเชื่อว่าอาหารเสริมดีกว่าแสงแดด
* ไม่เปิดเผยข้อจำกัดของการดูดซึมวิตามินดีจากอาหารเสริม
* ละเลยการพูดถึงผลข้างเคียงของการใช้อาหารเสริมเกินขนาด
* ไม่อธิบายความแตกต่างระหว่างวิตามินดีจากธรรมชาติและสังเคราะห์
- การวิจัยที่มีอคติ
* การศึกษาที่ได้รับทุนจากบริษัทผลิตภัณฑ์กันแดด
* เลือกนำเสนอผลการวิจัยเฉพาะด้านลบ
* ขาดการศึกษาระยะยาวเกี่ยวกับผลดีของแสงแดด
* ไม่เปิดเผยผลประโยชน์ทับซ้อนในงานวิจัย
#### การบิดเบือนในการรักษาทางการแพทย์
- แนวทางการรักษาที่พึ่งพายา
* เน้นการใช้ยามากกว่าวิธีธรรมชาติ
* ละเลยการแนะนำเรื่องการรับแสงแดด
* สั่งจ่ายอาหารเสริมโดยไม่จำเป็น
* ไม่ให้ความสำคัญกับการปรับพฤติกรรม
- การวินิจฉัยที่ไม่ครอบคลุม
* ไม่ตรวจหาสาเหตุจากการขาดแสงแดด
* มองข้ามความสัมพันธ์ระหว่างแสงแดดกับโรคต่างๆ
* ไม่ซักประวัติเรื่องการรับแสงแดด
* ละเลยการประเมินวิถีชีวิตที่หลีกเลี่ยงแสงแดด
#### ผลกระทบต่อการรักษา
- การรักษาที่ไม่มีประสิทธิภาพ
* การใช้ยาเกินความจำเป็น
* ค่าใช้จ่ายที่สูงขึ้นโดยไม่จำเป็น
* ผลข้างเคียงจากการรักษาที่ไม่เหมาะสม
* การรักษาที่ไม่แก้ปัญหาที่สาเหตุ
- ปัญหาสุขภาพที่ตามมา
* โรคขาดวิตามินดีที่เพิ่มขึ้น
* ปัญหาสุขภาพจิตจากการหลีกเลี่ยงแสงแดด
* ภาวะแทรกซ้อนจากการใช้ยาระยะยาว
* คุณภาพชีวิตที่ลดลง
### ผลกระทบต่อสุขภาพจากความกลัวแดด
- ปัญหาการขาดวิตามินดี
* การระบาดของภาวะขาดวิตามินดีในประชากร
* ผลกระทบต่อสุขภาพกระดูก
* ความเสี่ยงต่อโรคภูมิแพ้และภูมิคุ้มกัน
* ปัญหาสุขภาพจิตที่เพิ่มขึ้น
- ผลกระทบทางสังคมและจิตใจ
* ความวิตกกังวลเกี่ยวกับการออกนอกบ้าน
* การจำกัดกิจกรรมกลางแจ้ง
* ความเครียดจากการต้องดูแลผิวมากเกินไป
* ค่าใช้จ่ายที่สูงขึ้นจากผลิตภัณฑ์ป้องกันแดด
### การแก้ไขความเข้าใจผิด
- การให้ข้อมูลที่สมดุล
* นำเสนอทั้งประโยชน์และความเสี่ยง
* แนะนำวิธีการรับแดดที่ปลอดภัย
* สร้างความเข้าใจเรื่องความพอดี
* ให้ความรู้เรื่องการป้องกันที่เหมาะสม
- การปรับเปลี่ยนทัศนคติ
* เปลี่ยนจากการ "กลัวแดด" เป็น "เข้าใจแดด"
* สร้างความตระหนักถึงความสำคัญของแสงแดดต่อสุขภาพ
* ส่งเสริมการใช้ชีวิตที่สมดุลกับธรรมชาติ
* ลดอิทธิพลของค่านิยมผิวขาว
## หลักการรับแสงแดดที่ถูกต้องตามแนวทางเฮลิโอเทอราปี

### ระยะเวลาและความถี่
- เริ่มจากวันละ 10-15 นาที
- ค่อยๆ เพิ่มเวลา
### วิธีการที่ถูกต้อง
- เปิดผิวให้สัมผัสแดดพอประมาณ
- ไม่ใช้สารกันแดด
- สังเกตการตอบสนองของร่างกาย
- ปรับตามสภาพอากาศและฤดูกาล
## การประยุกต์ใช้เฮลิโอเทอราปีในชีวิตประจำวัน

### กิจกรรมที่แนะนำ
- เดินเช้าหรือเย็น
- ทำสวนในช่วงเวลาที่เหมาะสม
- ออกกำลังกายกลางแจ้งเบาๆ
### การผสมผสานกับการดูแลสุขภาพอื่นๆ
- การออกกำลังกาย
- การทำสมาธิกลางแจ้ง
- การทำกิจกรรมผ่อนคลาย
## บทสรุป: กลับสู่สมดุลธรรมชาติ
เฮลิโอเทอราปีไม่เพียงเป็นการรักษาโรค แต่ยังเป็นแนวทางในการดูแลสุขภาพแบบองค์รวม การเข้าใจหลักการของเฮลิโอเทอราปีช่วยให้เราตระหนักว่า แสงแดดเป็นส่วนสำคัญของชีวิตที่สมดุล การหวนกลับมาใส่ใจการรับแสงแดดอย่างถูกวิธี จึงเป็นก้าวสำคัญสู่การมีสุขภาพที่ดีอย่างยั่งยืน
แสงแดดเป็น "เพื่อน" ไม่ใช่ "ศัตรู" ของสุขภาพ หากรู้จักใช้ให้เหมาะสม
Don’t trust , (must) Verify
ศึกษาเพิ่มเติมเรื่อง Heliotherapy : https://youtu.be/q5EX5XrR-2A
......................................
ข้อมูลสุขภาพดีๆที่ไม่มีค่าใช้จ่าย
https://www.youtube.com/@fastingfatdentist
.
หากสนใจวิธีการดูแลสุขภาพตามแบบ IFF ปรึกษาส่วนตัว inbox มาสอบถามที่เพจ"หมออ้วนในดงลดน้ำหนัก"หรือ" fastingfatdentist"ได้เลยครับ
.
#ความน่ากลัวในการดูแลสุขภาพคือการที่เชื่อโดยไม่มีความรู้ .
.
#IFF #IFF_talk #intermittentfasting #keto #Lowcarb #CD #plantbased #RemissionDiabetes #ร่างกายเราคือธรรมชาติไม่ใช่ยา #เบาหวานหายได้โดยไม่ต้องใช้ยา #หมอไหวของหมอแบบนี
-

@ e83b66a8:b0526c2b
2024-12-11 09:16:23
I watched Tucker Carlson interview Roger Ver last night.
I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case.
We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money.
The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially).
The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines.
Part of that battle is self custody, part is tax and part are the money transmitting laws.
Roger’s case is also being used as a weapon of fear.
I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so.
Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time.
This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years.
This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
-

@ cdee943c:5e637400
2024-12-08 16:39:01
### Identify and Use the Correct Relays
After the user has logged in either through a Bunker or Signer App/Browser plugin, we should identify the correct relays to use for them, as per the "Outbox" model:
1. Fetch the User’s Relay List (`kind:10002`):
- Given the user’s public key, query a set of known bootstrap relays or a directory service to find the user’s `kind:10002` event.
- Parse the `r` tags:
- Read Relays: For discovering events _about_ the user, including their mentions, follow lists, interest sets, and reactions from others.
- Write Relays: For discovering events _from_ the user directly, such as their posted recipes or their relay-published follow lists.
We now know which small, authoritative set of relays to query for user-related data, reducing noise and improving performance.
---
### Build the Initial Follower Network
1. Fetch Follow Lists (`kind:3`):
- Connect to the user’s chosen WRITE relays.
- Retrieve their `kind:3` Follow List event, which lists whom the user follows.
- Extract each followed pubkey and possibly associated relay URLs and petnames.
2. Fetch Additional Lists:
- Query `kind:30000` range events (like Follow sets `30000`, Interest sets `10015`, Bookmarks `10003`, Communities `10004`, etc.) that the user maintains.
- This may reveal specialized follow sets or interest-based sets. For example:
- Follow sets (`kind:30000`) to categorize follows into thematic groups.
- Interest sets (`kind:10015`) to see what topics the user is explicitly interested in.
3. Assemble a Unified Follower Network:
- Combine direct follows (`kind:3`) and sets from `kind:30000` events and other NIP-51 sets to get a richer map of who matters to the user’s culinary context.
- Some sets may reference pubkeys via `p` tags. Aggregate them into a single structured follower/connection network.
We should now have more complete map of the user’s social connections, including standard follows and curated sets.
---
### Integrate Relationship Status
Although [NIP-81](https://github.com/nostr-protocol/nips/blob/8dafaf8714dcb9c0fca5530b53535bf8327ed6c7/81.md) hasn't been merged into the main NIP repo it is implemented by several major clients including Amethyst and provides the most reliable data on the relationship between two Nostr users.
1. Fetch Relationship Status Events:
- Use `kind:30382` (public relationships) and `kind:31382` (private relationships) to discover deeper relational data between the user and others.
- From these events:
- Identify if the user is placed in various named sets (`"n"` tags).
- Identify if the user or their followees are categorized in some way or are in any other relationship groups.
2. Incorporate Relationship Tags into the Graph:
- If the user places a contact into a “trusted” or “key collaborator” set via NIP-81’s `n` tags, increase the influence score of that contact.
- If the user is placed by others into sets, factor that in, as it shows reciprocal recognition.
We should now have a richer social graph that goes beyond just “follows,” capturing nuanced relational data to refine how we weigh each contact’s influence.
---
### Scoring the Influence of Followers
For each follower identified in Steps 2 and 3, we compute an influence score. Consider:
- Reciprocal Follows:
- If a person the user follows also follows them back (derived from `kind:3` on the follower’s side), add points.
- Reactions and Zaps to/from the User (NIP-25 & NIP-57):
- Check if this follower liked (`+`), disliked (`-`), or reacted with custom emojis to the user’s posts (`kind:7` events with `#e` referencing user’s posts).
- Check if they zapped the user’s posts or profile (`kind:9735` zap receipts), indicating support with real sats.
- Also consider if the user has reacted or zapped this follower’s posts—mutual engagement increases influence.
- NIP-51 List Membership:
- If the follower appears in the user’s NIP-51 sets (like a “VIP cooks” set `kind:30000` or “Top Bookmarks” `kind:10003`), add extra points.
- NIP-81 Relationship Assignments:
- If the follower is placed into a special category by the user’s `kind:30382` event or if the follower places the user in their `kind:30382` event, increment the score based on category importance.
We should now have a list of followers ranked by their “influence” in the user’s network. Influential people are those with mutual follows, engagement (reactions and zaps), presence in multiple sets, and meaningful relationship tags.
---
### Using Influential Followers to Build a "Web of Flavor"
1. Query Influential Followers’ Data:
- For the top N most influential followers:
- Fetch their `kind:10003` (Bookmarks), `kind:10015` (Interests), `kind:1985` (Labels), `kind:30023` (Curation sets), and other relevant NIP-51 sets.
- Gather tags like `t` (topics), `a` (articles, possibly representing recipes), `e` (notes), `p` (pubkeys referencing authors), and so forth.
2. Assemble a Recipe Ontology:
- From their sets and labels, extract:
- Cuisines (e.g., `["l", "Italian", "ISO-3166-2"]` or discovered from `l` tags representing cuisines)
- Categories (from `l` tags or sets)
- Ingredients (from reading through user’s curated sets or `t` tags they frequently use)
- Incorporate labeling from `kind:1985` events that might classify recipes under certain namespaces, and from `30023` sets that highlight curated recipe collections.
3. Aggregate and Normalize Tags:
- Combine all discovered interests, cuisines, categories, and ingredients into a unified ontology representing the user’s “web of taste.”
- Deduplicate and normalize terms—ensure consistent naming conventions (e.g., unify “Italian” and “IT-PR” region tags under one conceptual umbrella).
We should now have a rich, aggregated ontology of flavors, cuisines, categories, and ingredients derived from the user’s most influential contacts and their labeling and interest sets.
---
### Constructing the Relay Query for Relevant Recipes
1. Query Recipes by Ontology:
- Construct a Nostr filter referencing `#t` tags for interests, `#l` tags for labels, and `#a` or `#e` tags for known recipe sets or curated articles.
- For performance, use the COUNT filter if the relay supports it (e.g., `{"kinds":[35000], "#t":["italian","vegetarian"]}` and ask if relay supports `limit` or `count`).
2. Refine Queries Iteratively:
- Start broad by querying for top-level categories (e.g., “Italian vegetarian recipes”).
- Narrow down results by adding more tags or sets once initial results are retrieved.
- Use reaction counts or zap data on the returned events to further refine or sort results client-side.
We will now have a final set of relevant recipe events from authoritative relays, filtered according to the user’s “web of taste” established through their network of influence.
-

@ cdee943c:5e637400
2024-12-06 19:26:20
## Why would you set up a custom relay for Recipes?
Recipes are inherently rich in data, encompassing multiple ingredients, categories, cuisines, nutritional information, and detailed instructions. A custom relay tailored to handle a specific recipe event kind (nominally `kind=35000`) can:
- **Optimize Data Retrieval:** Efficient indexing and storage mechanisms ensure swift access to complex recipe data.
- **Enhance Flexibility:** Tailored configurations accommodate the unique structure of recipe events, making query filters more efficient and flexible.
- **Improve Performance:** Specialized handling reduces latency, which becomes a very important factor for high volume services.
- **Support Advanced Features:** Features like real-time syncing, bulk import/export, and efficient compression cater to the dynamic nature of recipe sharing.
By aligning the relay's architecture with the structure of recipe events, Nostr developers can build responsive and scalable applications.
## Setting Up a Custom Recipe Relay
### Option 1: Using [khatru](https://khatru.nostr.technology/) and [Eventstore](https://github.com/fiatjaf/eventstore)
1. Bootstrap a basic khatru relay:
- Follow the steps outlined in the [khatru](https://khatru.nostr.technology/getting-started/) docs:
```go
relay := khatru.NewRelay()
```
2. Set up Eventstore:
- Configure khataru to use Eventstore and Postgresql:
```go
// Initialize Eventstore
db := postgresql.PostgresBackend{DatabaseURL: "postgres://eventuser:securepassword@localhost:5432/eventstore_db?sslmode=disable"}
if err := db.Init(); err != nil {
log.Fatalf("Failed to initialize eventstore: %v", err)
}
// Integrate Eventstore with Khatru
relay.StoreEvent = append(relay.StoreEvent, db.SaveEvent)
relay.QueryEvents = append(relay.QueryEvents, db.QueryEvents)
relay.CountEvents = append(relay.CountEvents, db.CountEvents)
relay.DeleteEvent = append(relay.DeleteEvent, db.DeleteEvent)
```
3. Modify tag handling
- Update the `tags_to_tagvalues` function to handle multi-character keys, multiple tag entries, and nested structures:
```go
_, err = db.DB.Exec(
CREATE OR REPLACE FUNCTION tags_to_tagvalues(jsonb) RETURNS text[]
AS $$
SELECT array_agg(t.value)
FROM jsonb_array_elements($1) AS elem(tag)
JOIN LATERAL (
SELECT
CASE
WHEN tag->>0 IN ('cuisine', 'category', 'ingredients', 'tags') THEN tag->>1
WHEN tag->>0 = 'nutrition' AND jsonb_array_length(tag) >= 3 THEN tag->>2
ELSE NULL
END AS value
) AS t
ON t.value IS NOT NULL;
$$ LANGUAGE SQL IMMUTABLE RETURNS NULL ON NULL INPUT;
)
```
4. Add custom polices:
- khatru supports setting custom event policies:
```go
// Apply custom policies to accept only kind 35000 events
relay.RejectEvent = append(relay.RejectEvent,
// Built-in policies
policies.ValidateKind,
// Custom policy to accept only kind 35000
func(ctx context.Context, event *nostr.Event) (bool, string) {
if event.Kind != 35000 {
return true, "Only recipe events (kind 35000) are accepted"
}
return false, ""
},
)
```
5. Pray that fiatjaf doesn't fire me
### Option 2: Modifying [Strfry](https://github.com/hoytech/strfry)'s Configuration
Strfry is another robust Nostr relay implementation that leverages LMDB for local data storage. Stirfry uses the [golpe C++ framework](https://github.com/hoytech/golpe) and by adjusting its configuration in `golpe.yaml`, you can tailor Strfry to handle recipe events optimally.
1. Optimize Indices:
- Enhance indexing for specific recipe-related tags to speed up queries:
```yaml
indices:
cuisine:
comparator: StringUint64
multi: true
category:
comparator: StringUint64
multi: true
ingredients:
comparator: StringUint64
multi: true
nutrition:
comparator: StringUint64Uint64
multi: true
```
2. Update indexPrelude:
```yaml
indexPrelude: |
PackedEventView packed(v.buf);
created_at = packed.created_at();
uint64_t indexTime = *created_at;
id = makeKey_StringUint64(packed.id(), indexTime);
pubkey = makeKey_StringUint64(packed.pubkey(), indexTime);
kind = makeKey_Uint64Uint64(packed.kind(), indexTime);
pubkeyKind = makeKey_StringUint64Uint64(packed.pubkey(), packed.kind(), indexTime);
packed.foreachTag([&](char tagName, std::string_view tagVal, std::string_view tagVal2 = ""){
// General tag indexing
tag.push_back(makeKey_StringUint64(std::string(1, tagName) + std::string(tagVal), indexTime));
// Specific tag handling for recipes
std::string tagNameStr(1, tagName);
if (tagNameStr == "cuisine") {
cuisine.push_back(makeKey_StringUint64(std::string(tagVal), indexTime));
} else if (tagNameStr == "category") {
category.push_back(makeKey_StringUint64(std::string(tagVal), indexTime));
} else if (tagNameStr == "ingredients") {
ingredients.push_back(makeKey_StringUint64(std::string(tagVal), indexTime));
} else if (tagNameStr == "nutrition" && !tagVal2.empty()) {
nutrition.push_back(makeKey_StringUint64Uint64(std::string(tagVal), std::string(tagVal2), indexTime));
} else if (tagNameStr == "tags") {
tags_specific.push_back(makeKey_StringUint64(std::string(tagVal), indexTime));
}
// Existing conditions for 'd' and 'e' tags
if (tagName == 'd' && replace.size() == 0) {
replace.push_back(makeKey_StringUint64(std::string(packed.pubkey()) + std::string(tagVal), packed.kind()));
} else if (tagName == 'e' && packed.kind() == 5) {
deletion.push_back(std::string(tagVal) + std::string(packed.pubkey()));
}
return true;
});
if (packed.expiration() != 0) {
expiration.push_back(packed.expiration());
}
```
## Conclusion
Setting up a custom Nostr relay tailored for recipe events would enable developers to build highly performant and flexible applications. Whether it is using **Khatru with Eventstore** or **modify Strfry's configuration**, the key lies in aligning the relay's architecture with the features of recipe data. This approach not only improves performance but also lays a robust foundation for building feature-rich clients and applications within the Nostr ecosystem.
-

@ b2d670de:907f9d4a
2024-12-02 21:25:18
This is a list of nostr clients exposed as onion services. The list is currently actively maintained on [GitHub](https://github.com/0xtrr/onion-service-nostr-clients). Contributions are always appreciated!
| Client name | Onion URL | Source code URL | Admin | Description |
| --- | --- | --- | --- | --- |
| Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | [operator](nostr:nprofile1qyvhwumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdshszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmg9umdvr) | N/A |
| moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | [operator](nostr:nprofile1qyv8wumn8ghj7un9d3shjtnddaehgctjvshx7un89uq36amnwvaz7tmzdaehgu3wvf5hgcm0d9h8g7r0ddhjucm0d5hsqgy8wvyzw6l9pn5m47n7tcm5un7t7h5ctx3pjx8nfwh06qq8g6max5zadtyx) | minimalist monero friendly nostrudel fork |
| Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostrnpub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest tagged docker image |
| Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest "next" tagged docker image |
| Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | [operator](nostr:nprofile1qqszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsxx2q3a) | Runs nsite. You can read more about nsite [here](https://github.com/lez/nsite). |
-

@ b2d670de:907f9d4a
2024-12-02 21:24:45
# onion-service-nostr-relays
A list of nostr relays exposed as onion services.
## The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options |
| --- | --- | --- | --- | --- | --- |
| nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A |
| relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A |
| nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A |
| nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN |
| bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A |
| relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN |
| freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) |
| inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC |
| filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC |
| N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A |
| nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A |
| nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A
| relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A |
| nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR |
| nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A |
| Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A |
## Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns.
If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub.
### Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-

@ 31312140:2471509b
2024-11-23 15:50:43
#### 🎩 The Origins: Where Did It All Start?
The concept of central banking isn't new. It dates back to the establishment of the Bank of England in 1694, which set the precedent for modern central banks (Check out [Bank of England's history](https://www.bankofengland.co.uk/about/history) for a deeper dive). These institutions were often created out of necessity - to handle war debts, stabilize economies, etc. But with great power comes… you guessed it, not-so-great intentions. 💰
#### 💸 The Money Factory: Printing Out of Thin Air
Central banks have the magical ability to print money from thin air. Sound amazing? Well, it's alarming. This endless printing is explained under the guise of "monetary policy" to control the economy. But in reality, it's a method to fund government debts and inflate the money supply, which causes the value of your hard-earned money to dwindle. Poof! Your buying power is gone. Have a look at how [federal reserve balance sheets](https://www.federalreserve.gov/monetarypolicy/bst_recenttrends.htm) have ballooned for evidence.
#### 🔄 Fractional Reserve Banking: The Multiplication Illusion
If you're a banker, you'll love fractional reserve banking. It's like magic, where banks keep a fraction of deposits and lend out the rest, creating a multiplier effect. Imagine you deposit 100$, the bank holds just 10$ and lends out the other 90$. The person who took out that loan spends it and this 90$ end up on someone else's deposit. Rinse and repeat until your 100$ effectively created 1,000$ in the economy. This system fuels credit bubbles and ultimately leads to *bank runs* when too many people try to withdraw their money at once. Just ask those unfortunate souls during the Great Depression!
#### 🔗 Chains of Debt: The Slavery of Nations
Central banks lend to governments, placing entire nations in debt. And who pays the price? You do, through taxes. Ironically, you’re not just paying off debts; you're also paying interest to these private banking cartels. It's a not-so-subtle form of modern-day slavery.
For a chilling summary, G. Edward Griffin’s “The Creature from Jekyll Island” is a must-read. It breaks down how banks engineer boom and bust cycles to control economies and populations.
#### 🔓 The Escape Plan: Sound Money is Freedom
Enter Bitcoin. 🧡 The only currency immune to manipulation by any central entity, Bitcoin offers a decentralized escape route from the clutches of central banks. They can’t print more Bitcoin. They can’t inflate it. And they definitely can’t control it. It’s regulated by math and network consensus, not whimsical policy changes by bankers in fancy suits. Want to understand more? Check out “The Bitcoin Standard” by Saifedean Ammous.
#### 🛡️ What Can You Do?
- **Educate Yourself:** Read, study, and converse with like-minded folks.
- **Diversify:** Consider holding assets that are outside the influence of central banks, like Bitcoin.
- **Advocate for Change:** Speak out, support political reform, and promote community awareness about the strengths of decentralized financial systems.
So, there you have it, folks! The maze is vast, but there’s light at the end of the tunnel if you’re willing to look into it. Knowledge is power, and it's time we reclaimed our financial freedom. 🤝
Feel free to dive deeper and challenge the narrative - every voice adds to the revolution!
#lookintoit #bitcoin #fiat #freedom #finance #soundmoney #scam #inflation #money
-

@ a849beb6:b327e6d2
2024-11-23 15:03:47
<img src="https://blossom.primal.net/e306357a7e53c4e40458cf6fa5625917dc8deaa4d1012823caa5a0eefb39e53c.jpg">
\
\
It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\
\
**Portfolio Company Spotlight**
[Primal](http://primal.net/) is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by [Strike BLACK](https://x.com/Strike/status/1755335823023558819)) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
### **Selected Portfolio News**
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in [December](https://x.com/AnchorWatch/status/1858622945763131577).\
\
Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed [private credit strategy](https://www.youtube.com/watch?v=26bOawTzT5U).
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many [more new features](https://primal.net/e/note1kaeajwh275kdwd6s0c2ksvj9f83t0k7usf9qj8fha2ac7m456juqpac43m).
Debifi launched its new iOS app for Apple users seeking non-custodial [bitcoin-collateralized loans](https://x.com/debificom/status/1858897785044500642).
### **Media**
Strike Founder and CEO Jack Mallers [joined Bloomberg TV](https://www.youtube.com/watch?v=i4z-2v_0H1k) to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic [joined](https://www.youtube.com/watch?v=kqR_IQfKic8) The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent [appeared on](https://www.youtube.com/watch?v=_WwZDEtVxOE&t=1556s) BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer [testimonial video](https://x.com/ZapriteApp/status/1859357150809587928) highlighting the popularity of its offerings across the bitcoin ecosystem.
### **Market Updates**
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of [nearly $2 trillion](https://companiesmarketcap.com/assets-by-market-cap/), putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully [approved](https://finance.yahoo.com/news/bitcoin-etf-options-set-hit-082230483.html) and launched this week. These options should help further expand bitcoin’s institutional [liquidity profile](https://x.com/kellyjgreer/status/1824168136637288912), with potentially significant [implications](https://x.com/dgt10011/status/1837278352823972147) for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching [nearly $2 billion](https://www.coindesk.com/markets/2024/11/20/bitcoin-etf-options-introduction-marks-milestone-despite-position-limits/) on just the first day of trading despite [surprisingly tight](https://x.com/dgt10011/status/1858729192105414837) position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in [$3.4 billion](https://farside.co.uk/btc/) in net inflows.
New reports [suggested](https://archive.is/LMr4o) President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts [declined M/M again](https://finance.yahoo.com/news/us-single-family-housing-starts-134759234.html) in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that [developers need further rate cuts](https://www.bloomberg.com/news/articles/2024-11-19/miami-developer-says-real-estate-market-needs-rate-cuts-badly) “badly” to maintain project viability.
US Manufacturing PMI [increased slightly](https://www.fxstreet.com/news/sp-global-pmis-set-to-signal-us-economy-continued-to-expand-in-november-202411220900) M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey [ticked up](https://archive.is/fY5j6) following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
### **Regulatory Update**
After weeks of speculation, the incoming Trump administration appointed hedge fund manager [Scott Bessent](https://www.cnbc.com/amp/2024/11/22/donald-trump-chooses-hedge-fund-executive-scott-bessent-for-treasury-secretary.html) to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a [public advocate](https://x.com/EleanorTerrett/status/1856204133901963512) for bitcoin.
Trump also [appointed](https://www.axios.com/2024/11/19/trump-commerce-secretary-howard-lutnick) Cantor Fitzgerald CEO Howard Lutnick – another outspoken [bitcoin bull](https://www.coindesk.com/policy/2024/09/04/tradfi-companies-want-to-transact-in-bitcoin-says-cantor-fitzgerald-ceo/) – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new [“crypto czar”](https://archive.is/jPQHF) role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a [strategic bitcoin reserve](https://archive.is/ZtiOk).
Various government lawyers suggested this week that the Trump administration is likely to be [less aggressive](https://archive.is/Uggnn) in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he [plans to resign](https://www.politico.com/news/2024/11/19/fdics-gruenberg-says-he-will-resign-jan-19-00190373) from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of [“Operation Chokepoint 2.0,”](https://x.com/GOPMajorityWhip/status/1858927571666096628) which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the [Howey Test](https://www.investopedia.com/terms/h/howey-test.asp).
Overseas, a Chinese court ruled that it is [not illegal](https://www.benzinga.com/24/11/42103633/chinese-court-affirms-cryptocurrency-ownership-as-legal-as-bitcoin-breaks-97k) for individuals to hold cryptocurrency, even though the country is still ostensibly [enforcing a ban](https://www.bbc.com/news/technology-58678907) on crypto transactions.
### **Noteworthy**
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – [suggested](https://x.com/matthew_sigel/status/1859700668887597331) the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a [“renewed sense of optimism”](https://www.ishares.com/us/insights/2025-thematic-outlook#rate-cuts) on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets [indicated](https://www.youtube.com/watch?v=TE7cAw7oIeA) the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a [$100 billion equity value](https://finance.yahoo.com/news/microstrategy-breaks-top-100-u-191842879.html) this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, [spoke for 25%](https://bitbo.io/news/allianz-buys-microstrategy-notes/) of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting [growing appetite](https://x.com/Rob1Ham/status/1860053859181199649) for bitcoin proxy exposure among more restricted pools of capital.
The [ongoing meltdown](https://www.cnbc.com/2024/11/22/synapse-bankruptcy-thousands-of-americans-see-their-savings-vanish.html) of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
### **Travel**
- [BitcoinMENA](https://bitcoin2024.b.tc/mena), Dec 9-10
- [Nashville BitDevs](https://www.meetup.com/bitcoinpark/events/302533726/?eventOrigin=group_upcoming_events), Dec 10
- [Austin BitDevs](https://www.meetup.com/austin-bitcoin-developers/events/303476169/?eventOrigin=group_upcoming_events), Dec 19
- [Nashville Energy and Mining Summit](https://www.meetup.com/bitcoinpark/events/304092624/?eventOrigin=group_events_list), Jan 30
-

@ cdee943c:5e637400
2024-11-21 22:03:13
One of the first [tasks](nostr:nevent1qqsrqws36dytallje0cwjjcaxqt3ukfhg0aqvwh3pakhuqzy8e9jscspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0wfjkccte9ehx7um5wghxuet59uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59utl42kp) we set ourselves at Nostr SF is to build a demonstration app for how to use dedicated kinds, and in this case, one for recipes.
Nostr SF isn't a wheel design firm though, so we figured it was best to look at what's already happening and see if we can build off of that rather than necessarily start from scratch. So we asked ourselves what sort of information is being captured and shared in other recipe platforms that we could use as a model for ours.
The following is a review of the various recipe formats that are presently in the wild:
### zap.cooking
The inspiration for the project, [zap.cooking](https://zap.cooking/recent) currently uses `kind:30023` notes for publishing recipes. Looking in the [source code](https://github.com/github-tijlxyz/nostr.cooking/blob/84669f88c716d5c6b029840cbc7d8e9088e52d4d/src/lib/pharser.ts#L115), they parse a markdown representation in the content field which results in the following fields:
- Chef's notes
- Details (with the following 'sub fields')
- Prep time
- Cook time
- Servings
- Ingredients
- Directions
- Additional Resources
The event json looks like this:
```
{
"content": "\n## Chef's notes\n\nAh, my culinary wanderlust through northern Italy and an undeniable romance with fall's freshest produce gave birth to this risotto masterpiece. Crafted by yours truly, if you find your taste buds dancing with delight, do show some love. Who knows, a few more of my treasured recipes might just make their way from my kitchen to yours. Wink!\n\n## Details\n\n- ⏲️ Prep time: 30 min\n- 🍳 Cook time: 30 min\n- 🍽️ Servings: 4-6\n\n## Ingredients\n\n- 1 butternut squash, peeled, cored and cut into 1cm cubes \n- 1 onion, chopped \n- 1 pinch of nutmeg \n- 350 g Nebbia smoked carnaroli rice \n- 25 cl dry white wine, such as pinot grigio \n- 1 bay leaf, optional \n- 1 tablespoon fresh thyme leaves, optional \n- 50g cheese - parmesan or pecorino - finely grated \n- Extra virgin olive oil\n- 1300cl classic risotto broth (Star Il Mio Dado Classico or better yet, homemade)\n\n\n## Directions\n\n1. Preheat the oven to 200C. \n2. Coat the squash cubes with olive oil and spread them in a single layer on a large baking sheet (don't season them)\n3. Bake for about 50 minutes, until golden brown on the edges.\n4. Remove from oven and set aside. \n5. While the squash is roasting, prepare the stock and, if using, add the bay leaf. \n6. Bring to the boil and then reduce to a simmer. \n7. Heat a little olive oil in a large risotto pan, add the onion and fry until translucent, about 3 min.\n8. Add the rice and nutmeg, stir coating with the oil and onion and fry for another 2-3 minutes. \n9. Reduce the heat to medium and add the white wine, and thyme if using. \n10. As the wine evaporates, add a ladle of broth (about 20 cl), stirring regularly. \n11. As the broth evaporates and the rice begins to stick to the pan scrape the bottom and add another ladle of broth. \n12. Repeat until about 2 ladles of broth remain. \n13. Add about 1/3 to 2/3 of the cooked squash to the risotto and mix well. (You can add more if you like, or the rest of the squash will be delicious with pasta, with eggs, or in a soup.) \n14. Continue adding the last ladles of broth until the rice is cooked al dente. \n15. Remove from the heat and stir in the cheese. \n16. Serve immediately.\n17. Can also be made with regular carnaroli rice, in which case, put 4 chopped sage leaves and 2 cloves of garlic in with the thyme. However, the Nebbia Fog Smoked Rice has a magical richness to it that can't be imitated.\n",
"created_at": 1699302411,
"id": "1013a49c671ec45ad8d0ba97256b9abc1e990405a82f4bdf253ef0226d5eade3",
"kind": 30023,
"pubkey": "fe6104d291746db0132f54974e6d4331ced86f43fc00a75f592c1d20e1d22b8c",
"sig": "e3e2e8776c8aed90e9c91b10e6b5d80827aa42f77e863ade84a98bd135e56488099d949b95f734d1323b520ed37c12c9c468311e9d67045af3107f52057c34bb",
"tags": [
["d", "uncle-jedi's-butternut-risotto"],
["title", "Uncle Jedi's Butternut Risotto"],
["t", "nostrcooking"],
["t", "nostrcooking-uncle-jedi's-butternut-risotto"],
[ "summary", "Dive into a creamy risotto infused with the nutty richness of roasted butternut squash, seasoned with a hint of nutmeg and fresh thyme. This elegant dish, made with luxurious Nebbia smoked carnaroli rice, is perfectly balanced with the sharpness of parmesan or pecorino. And as the risotto bubbles and simmers, the white wine reduction adds depth and aroma that tantalizes the senses. Have leftovers? The roasted squash pairs delightfully with pasta or eggs. For the grand finale, enjoy this masterpiece with a savory fennel sausage. A meal that's both cozy and gourmet awaits!"],
["image", "https://image.nostr.build/f88d843b5d6a112c1963e34b61d731ab0d63c6bc6ede98df757d6cdaa4259f68.jpg"],
["t", "nostrcooking-easy"],
["t", "nostrcooking-italian"],
["t", "nostrcooking-squash"],
["t", "nostrcooking-rice"]
]
}
```
### Proposed Recipe NIP
There is an existing [NIP proposal](https://github.com/nostr-protocol/nips/issues/1571) for recipes which suggests a number of tags that can be used to filter recipes more efficiently at the relay side.
The event json looks like this:
```
{
"id": "<event_id>",
"pubkey": "<author_pubkey>",
"created_at": <unix_timestamp>,
"kind": XXXX,
"tags": [
["title", "<recipe_title>"],
["summary", "<recipe_summary>"],
["author", "<recipe_author>"],
["cuisine", "<style_or_region_of_cuisine>"],
["category", "<category>"],
["ingredients", "<ingredients_description>"],
["image", "<image_url>"], // can be used more than one
// Optional Tags
["prep_time", "<prep_time>"],
["cook_time", "<cook_time>"],
["servings", "<servings_number>"],
["difficulty", "<difficulty>"],
["nutrition", "<calories_per_serving>"],
["tags", "<comma_separated_tags>"],
["allergens", "<comma_separated_allergens>"],
["content_warning", "<content_warning_description>"],
],
"content": "<description_instructions_and_notes_content>",
"sig": "<signature>"
}
```
### Schema.org
There is a [schema](https://schema.org/Recipe) for recipes which details an exhaustive list of possible fields for a recipe. The minimum set of fields produces a JSON result like this:
```
{
"@context": "https://schema.org",
"@type": "Recipe",
"author": "John Smith",
"cookTime": "PT1H",
"datePublished": "2009-05-08",
"description": "This classic banana bread recipe comes from my mom -- the walnuts add a nice texture and flavor to the banana bread.",
"image": "bananabread.jpg",
"recipeIngredient": [
"3 or 4 ripe bananas, smashed",
"1 egg",
"3/4 cup of sugar"
],
"interactionStatistic": {
"@type": "InteractionCounter",
"interactionType": "https://schema.org/Comment",
"userInteractionCount": "140"
},
"name": "Mom's World Famous Banana Bread",
"nutrition": {
"@type": "NutritionInformation",
"calories": "240 calories",
"fatContent": "9 grams fat"
},
"prepTime": "PT15M",
"recipeInstructions": "Preheat the oven to 350 degrees. Mix in the ingredients in a bowl. Add the flour last. Pour the mixture into a loaf pan and bake for one hour.",
"recipeYield": "1 loaf",
"suitableForDiet": "https://schema.org/LowFatDiet"
}
```
### Cooklang
There is also specification for recipes called [Cooklang](https://cooklang.org/docs/spec/) which defines a DSL for recipes. The syntax has it's own [EBNF grammar](https://raw.githubusercontent.com/cooklang/spec/refs/heads/main/EBNF.md) which looks like this:
```
-- TODO add source
Mix together @oyster sauce{1%tbsp}, @soy sauce{5%tbsp} and @sesame oil{5%tsp}, set aside.
Heat @peanut oil{1%tbsp} in a wok or heavy based skillet/fry pan over medium heat. Add @eggs{2%items} and cook until scrambled, then remove onto plate.
Increase heat to high and add chopped @bacon{75%cup}, excess fat trimmed. Cook until golden, then remove onto plate with egg - about 2 minutes.
Drain off excess bacon fat.
Add remaining @peanut oil{2%tbsp}, minced @garlic{2%gloves} and @ginger{3%tsp}. Return wok to stove on high heat. Stir fry as it comes up to heat, don’t let it burn. When garlic starts to sizzle, add finally chopped @onion{2%medium} and stir fry for 2 minutes until golden.
Add @Chinese cooking wine{1%tbsp} and @sugar{2%tsp} and let it simmer rapidly, stirring, for 20 seconds, until mostly evaporated.
Add @prawns{150%g} and stir fry for 1 minute to heat through if pre-cooked, cook longer to cook if raw.
Add refrigerated overnight @cooked rice{3%cups}, Sauce, eggs, bacon and thinly sliced @scallions{5%items}. Stir fry for 2 minutes until rice is hot - around 2 minutes.
Transfer to serving plate, sprinkle with thinly sliced @scallions{2%items} and serve.
```
There is an online parser demo [here](https://biowaffeln.github.io/cooklang-parser/) which converts a given recipe into an AST which looks like this:
```
{
"metadata": {
"source": "https://www.dinneratthezoo.com/wprm_print/6796",
"total time": "6 minutes",
"servings": "2"
},
"ingredients": [
{
"type": "ingredient",
"name": "apple juice",
"quantity": "1,5",
"units": "cups"
},
{
"type": "ingredient",
"name": "banana",
"quantity": "one sliced",
"units": ""
},
{
"type": "ingredient",
"name": "frozen mixed berries",
"quantity": "1,5",
"units": "cups"
},
{
"type": "ingredient",
"name": "vanilla greek yogurt",
"quantity": 0.75,
"units": "cup"
},
{
"type": "ingredient",
"name": "honey",
"quantity": "some",
"units": ""
}
],
"cookware": [
{
"type": "cookware",
"name": "blender",
"quantity": ""
}
],
"steps": [
[
{
"type": "text",
"value": "Place the "
},
{
"type": "ingredient",
"name": "apple juice",
"quantity": "1,5",
"units": "cups"
},
{
"type": "text",
"value": ", "
},
{
"type": "ingredient",
"name": "banana",
"quantity": "one sliced",
"units": ""
},
{
"type": "text",
"value": ", "
},
{
"type": "ingredient",
"name": "frozen mixed berries",
"quantity": "1,5",
"units": "cups"
},
{
"type": "text",
"value": " and "
},
{
"type": "ingredient",
"name": "vanilla greek yogurt",
"quantity": 0.75,
"units": "cup"
},
{
"type": "text",
"value": " in a "
},
{
"type": "cookware",
"name": "blender",
"quantity": ""
},
{
"type": "text",
"value": "; blend until smooth. If the smoothie seems too thick, add a little more liquid (1/4 cup). "
}
],
[
{
"type": "text",
"value": "Taste and add "
},
{
"type": "ingredient",
"name": "honey",
"quantity": "some",
"units": ""
},
{
"type": "text",
"value": " if desired. Pour into two glasses and garnish with fresh berries and mint sprigs if desired."
}
]
]
}
```
This is by no means an exhaustive list of available recipe implementations but should server as a good starting point for determining what makes a good recipe `kind`.
-

@ b17c5987:85d68928
2024-11-21 10:24:16
Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections.
Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections.
This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected Donald Trump with a mandate for sweeping change, and they deserve to get it.
President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs.
This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected [Donald Trump](https://www.wsj.com/topics/person/donald-trump) with a mandate for sweeping change, and they deserve to get it.
President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs.
We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure.
In West Virginia v. Environmental Protection Agency (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In Loper Bright v. Raimondo (2024), the court overturned the Chevron doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law.
DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy.
When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be correcting the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so.
A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit.
Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in Franklin v. Massachusetts (1992) and Collins v. Yellen (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home.
Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood.
The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers.
With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud.
Mr. Musk is CEO of SpaceX and Tesla. Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency.
We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure.
In *West Virginia v. Environmental Protection Agency* (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In *Loper Bright v. Raimondo* (2024), the court overturned the *Chevron* doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law.
DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy.
When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be *correcting* the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so.
A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit.
Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in *Franklin v. Massachusetts* (1992) and *Collins v. Yellen* (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home.
Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood.
The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers.
With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud.
*Mr. Musk is CEO of SpaceX and [Tesla](https://www.wsj.com/market-data/quotes/TSLA). Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency.*
-

@ 87730827:746b7d35
2024-11-20 09:27:53
Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
===================================================================================
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
* * *
**KEY TAKEAWAYS**
* The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero.
* The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards.
* While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country.
**_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._**
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
----------------------------------
If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
> … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
>
> – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-)
The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations.
However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
------------------------------------------------
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/).
Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.

In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
----------
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
----------
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
[View all articles by Cassio Gusson](https://techreport.com/author/cassiog/)
-

@ 5e5fc143:393d5a2c
2024-11-19 10:20:25
Now test old reliable front end
Stay tuned more later
Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues
-

@ 84b0c46a:417782f5
2024-11-19 08:56:39
- [lumilumi](https://lumilumi.vercel.app/) The Nostr Web Client.
Lightweight modes are available, such as not displaying icon images, not loading images automatically, etc.
- [Nostr Follow Organizer](https://tsukemonogit.github.io/NFO/)
Follow List ( kind3 ) organization tool.
- [NAKE](https://github.com/TsukemonoGit/nake) NIP-19, NIP-49 Encode/Decode Tool
- [chrome extension](https://chromewebstore.google.com/detail/nake/pckmdjknadbfalfohabbccmffoohlamk)
- [firefox add-on](https://addons.mozilla.org/ja/firefox/addon/nake/)
- [nostviewstr](https://nostviewstr.vercel.app/)
Addressable or Replaceable Event Editor ( いろんなリストエディター )
- [luminostr](https://tsukemonogit.github.io/luminostr/)
Addressable or Replaceable Event Recovery tool ( いろいろリカバリーツール )
- [Nostr Bookmark Recovery Tool](https://nostr-bookmark-recovery-tool.vercel.app/)
Bookmark event ( kind:10003,30001,30003 ) recovery tool ( ぶくま復活させたいやつ )
- [Profile Editor](https://nos-profile-arekore.vercel.app/)
プロフィールを編集するやつ
- [nostr-bookmark-viewer](https://nostr-bookmark-viewer3.vercel.app/)
Bookmark event ( kind:10003,30001,30003 ) Editor ( ぶっくまーくをみるやつ )
- [Nostr Note Duplicater](https://dupstr.vercel.app/)
Broadcast an event from relay to relay ( イベントをブロードキャストするやつ )
- [もの画像サイト](https://tsukemonogit.github.io/nostr-monoGazo-bot/)
- [いろいろbotサイト](https://tsukemonogit.github.io/iroirotest/)
-

@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
## Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
## Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
## Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
## Directions
1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
-

@ bcea2b98:7ccef3c9
2024-11-09 17:01:32
Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-

@ fd208ee8:0fd927c1
2024-11-08 10:27:40
## You have no idea
I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.

It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse.
I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._
But you were always apart. You were always two different people. You just didn't notice, until now.

I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship.
## I was raised by relaxed revolutionaries
Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics.
It's like magic, but it's the result of a mindset, not a worldview.
Or, as I like to quip:
> The best way to stay married, is to not get divorced.

My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live.
My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.

The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on.
And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer.
You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.

We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something.
Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
-

@ 4ba8e86d:89d32de4
2024-11-07 13:56:21
Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas.
Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW.
Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW.
Sem mais delongas, vamos ao tutorial de fato.
## 1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P.
Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo.
Após entrar no site vá para a página '1 - Creating a mailbox'
https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos.
https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados.
https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg
https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
## 2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd.
Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso.
Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf
https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf
https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
```
sudo systemctl restart i2pd
```
Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.
Com os túneis cliente criados, vamos agora configurar o Thunderbird
## 3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir.
https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg
https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta.
https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir.
https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue'
https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta.
https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
## 4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-

@ fd208ee8:0fd927c1
2024-11-07 07:22:14
## Unsucking the feed is real
As a Nostrich with an interesting, thought-provoking, and informative feed... a feed so good, that we're creating clients just to look at that feed... a feed that puts a lie to the idea that Nostr is nothing, but people reposting from Twitter or rehashing worn-out Bitcoin memes... a feed that I personally and increasingly enjoy perusing... I am here to tell you that the feed is real.

It's taken me over a year, to produce this feed. I literally spent hours and hours, day in and day out, scouring the Nostrverse for people worth introducing other people to. It was brutally difficult, as I was fighting the inherent nature of the Nostr clients and relays, in their current, most-popular form.
## It goes like so...
Here are the steps I took, that sometimes weren't possible to take, until I tried to take them, and that still will sometimes break your client because the clients are often _intentionally_ designed to steer you into having one particular feed:
1) **Make a screenshot** of your current relay list and copy your follows list.
2) **Unsubscribe from all the relays**, that you are currently subscribed to. Your feed should disappear. If it doesn't, or it doesn't allow for this, switch to a different client app because yours is corrupted.
3) **Unfollow everyone.** Delete the whole list. You are taking your follows private, which will invariably result in only following npubs whose stuff you actually want to see, since there's no longer any virtue-signaling going on. Also, it's easier to explain having no list, than a very short one. If your client doesn't allow for this, or starts throwing error messages and freezing up, then switch to a different client app because yours is corrupted.
4) **Curate your copied follows list.** Go line by line and look at the feed produced by the npub on that list.
* Do you want to see that in your feed, going forward?
* Do they produce original content and/or are they interesting conversationalists, in the replies?
* Have they been active, within the past three months?
* Are they simply good friends or real-life acquaintances, that you want to keep tabs on?
* If not, cross out their name.
* If you have been following someone because they repost or quote interesting things, **look at who they've been reposting** and follow them, instead.
5) Of the npubs remaining on your list, go through and select the 10 most interesting ones, and **look at the reposts and quotes** in their feed, and their topical lists like \"Favorites\", \"Devs\", \"Recipes\", etc. (Not their follows list, unless it's quite short, as follows tend to be full of people they follow for social-signaling or client-functional reasons, that they don't actively look at.) Find some new follows, there.
6) Now, set up a personal relay and add all the follows, that made the cut, to **your allowed-npubs list**. Do not add people to the list, just to make them feel better, or because you feel guilty, as they follow you, or to keep them from yelling at you. Remember, they can't see the list!
7) Think about the topics you find interesting, and add an **allowed-keywords list** (this is better than hashtags, as it searches the entire content of the notes), with the OR operator (these allowed npubs OR these allowed topics).
8) Make sure that you choose words likely to find the content you are most-interested in, and not people just ranting about it or spamming (those are great additions to your relay's block-list). If you are Muslim, for instance, instead of "Islam" or "shariah", choose "hadith" or "riba", as those are words more-likely to be used by people who know what they are talking about. If you are into bread baking, add "sourdough", "rye", "yeast", or "whisk", but don't add "bread" or "carbs". Once a note from those people shows up in your feed, and their feed looks like someone interesting, you can add their npub to your allow list. Remember: **The topics are there to find people to add to the allow list**, not merely for their own sake, as this is not a topical relay, but a personal one.
9) Open up a faucet (or relay syncing) with some of the big relays you previously unsubscribed from, some WoT relays, and some of the paid relays (nostr.land, nostr.wine, nostr21.com, and sovbit.host, for example). **Your relay will filter that feed** and only accept the events from the people and topics on your list. As your relay becomes more popular, npubs will begin writing directly to it, and the connections to other relays will sink in significance.
10) Go to your client of choice and **subscribe to your new relay**. Also subscribe to some topical relays, or curated neighborhood relays, you find interesting or your frens are running. This is an easy way to find new, interesting npubs, to add to your own relay.

That's a lot of work, you say? Yes, but the result is great, and you are now fully in-charge of your own feed. You also -- here's the cool part -- have a feed good enough, that other people can add your feed to theirs and enjoy your manual curation. As you refine and expand your feed, theirs will also be refined, in parallel. You are now an official Nostr Community Curator. My sincere congratulations.

## Why is this so hard?
This is only a lot of work because the clients aren't designed to interact with relays, to this extent, as they were created to service mega-relays, download all their crap to your local cache, and adjust the feed over the follows/mutes lists. This was an idea borne of the axiom that Relays Are Hard, so there will only ever be a handful of them, where we'd all clump together and the relay operators would never judge the quality of someone's content. Then, some unusually clever people made relays increasingly easy, and the mailbox communication model was invented, and here we are.
What we have now, and that is slowly growing in popularity, among the #NostrIntelligentsia, are Nostr clients aimed at curating and viewing individual relays or personalized sets of smaller or more-specialized relays. The reigning client devs refused to give us those clients, and most of us aren't up to developing our own clients, so the relay devs took matters into their own hands and made the clients themselves. The free market remains undefeated.
This is a total game-changer. Last one to board this train is a rotten egg.
Originally, relays were supposed to be completely stupid and clients were supposed to be completely smart, but it's now actually the other way around, because most relay devs have a market-born incentive to make their content highly customizable and appealing to individuals (so that more people run relays).
## But what about algos?
Can't you just slap an algo on top of Damus, Lol, or Primal relays, and get the same result? I would argue... no. No, you can't. Or, rather, only in the short to medium term.
Running your own relay, is running your own server. You are now _intellectually independent_, at a machine-level, and therefore a fully sovereign consumer. If you then use algos to control your own server, or in a client that subscribes to your own server, then you can further-refine a feed that is already in a high-to-you-signal state, rather than risking an algo inching you toward the Consensus Feed.
I have noticed that my own feed is slowly drifting away from the ReplyGuy-Cryptobot-Porny-Bitcoin-Meme Dumpster Fire, that almost everyone else is looking at, and it's due to running my own relay. If I use DVMs, those algos sometimes refer to relays I intentionally avoid, so they return results according to those relays. The results are as underwhelming, as you would expect, and often are simply 31 flavors of the Trending List.
But, that isn't your problem, anymore.
From here, you can actively expand and refine your feed, over your whitelist, the topics, and your personally-managed algos.
Happy Nostr-ing!
-

@ c2827524:5f45b2f7
2024-11-05 10:40:05

*Remember, remember!
The fifth of November,
The Gunpowder treason and plot;
I know of no reason
Why the Gunpowder treason
Should ever be forgot!
Guy Fawkes and his companions
Did the scheme contrive,
To blow the King and Parliament
All up alive.
Threescore barrels, laid below,
To prove old England's overthrow.
But, by God's providence, him they catch,
With a dark lantern, lighting a match!*
**È tanto semplice e molto più pacifico oggi.**
- [ ] non serve polvere da sparo
- [ ] niente violenza (lasciamola a chi ne ha il monopolio, lo shdadoh)
- [ ] ci hanno dichiarato guerra e la guerra è economica
Rispondiamo semplicemente studiando #Bitcoin

https://t.me/bitcoincampus
https://t.me/BitcoinSecPriv
https://t.me/bitcoinita
https://satoshispritz.it/
-

@ 2d74600a:d6708a00
2024-11-02 07:12:35
L'amore per l'umanità è un tema che ha attraversato secoli di pensiero filosofico, etico e politico. Tuttavia, nel contesto contemporaneo, la definizione di questo amore si complica ulteriormente, specialmente quando si considera l'ideologia del globalismo. Chi si definisce "globalista" spesso proclama un amore universale per l'umanità, ma è fondamentale interrogarsi su cosa significhi realmente questo amore e quale tipo di umanità venga abbracciato.
L'umanità del globalista: una massa informe
Il globalismo, nella sua essenza, propone una visione dell'umanità che trascende le specificità culturali, etniche e nazionali. In questo contesto, l'umanità è concepita come un'entità astratta, priva di radici e di identità. Essa diventa una massa informe, un aggregato di individui che si muovono secondo logiche economiche e politiche globali, spesso disconnettendosi dalle tradizioni e dalle peculiarità che caratterizzano i diversi popoli. Questo approccio, sebbene possa apparire inclusivo e progressista, rischia di ridurre l'individuo a un mero ingranaggio di un sistema più grande, sacrificando l'autodeterminazione e l'autenticità culturale sull'altare di un'uguaglianza imposta.
L'uguaglianza come discriminazione
Il concetto di "uguaglianza" promosso dai globalisti, pur essendo nobile in teoria, si traduce spesso in una forma di omologazione che ignora le differenze fondamentali tra le culture. Questa parità, che si presenta come un ideale di giustizia sociale, può assumere il sapore della discriminazione, poiché tende a marginalizzare le microrealtà e le specificità locali. In questo senso, l'amore per l'umanità diventa un'ideologia che, anziché esaltare la diversità, la mortifica, imponendo un modello unico di esistenza che non tiene conto delle storie, delle tradizioni e delle aspirazioni dei singoli popoli.
Amare l'umanità: un atto di rispetto per il "Volksgeist"
Amare veramente l'umanità implica un riconoscimento e un rispetto per ogni popolo nella sua unicità. Significa esaltare il "Volksgeist", lo spirito di ogni nazione, e comprendere che la ricchezza dell'umanità risiede proprio nella sua diversità. Ogni cultura, ogni tradizione, ogni forma d'arte e mestiere rappresenta un contributo unico al patrimonio collettivo dell'umanità. L'amore autentico per l'umanità non può prescindere dal riconoscimento di queste differenze, ma deve piuttosto celebrarle e proteggerle.
La schiavitù moderna: una servitù senza catene
La visione globalista, con la sua tendenza a uniformare e standardizzare, può essere vista come una forma di schiavitù moderna, una servitù senza catene. Questa schiavitù si manifesta nella perdita di identità e nella disconnessione dalle proprie radici culturali. L'individuo, privato della sua storia e della sua cultura, diventa un consumatore passivo in un mercato globale, privo di un senso di appartenenza e di significato. In questo contesto, l'amore per l'umanità si trasforma in una legittimazione di un sistema che, sotto la maschera della libertà e dell'uguaglianza, perpetua forme di oppressione e alienazione.
Conclusione
In conclusione, l'amore per l'umanità, se inteso in modo autentico, deve necessariamente abbracciare la diversità e il particolare. La vera essenza dell'umanità risiede nelle sue molteplici espressioni culturali, nelle tradizioni che la definiscono e nei valori che la sostengono. Solo attraverso il rispetto e la valorizzazione di queste differenze possiamo sperare di costruire un futuro in cui ogni individuo possa sentirsi parte di un tutto, senza dover sacrificare la propria identità. L'amore per l'umanità, quindi, non è un'ideologia astratta, ma un impegno concreto a riconoscere e celebrare la ricchezza della nostra esistenza collettiva.
-

@ 2d74600a:d6708a00
2024-11-01 18:51:37
Questo articolo esplora la complessità dell'esperienza umana attraverso la lente della tristezza e della felicità, proponendo una distinzione tra le persone che si identificano rigidamente come tristi o felici e quelle che abbracciano la loro autenticità, vivendo un'alternanza di emozioni. Attraverso un'analisi filosofica, si indaga il significato di "essere veri" e si discute l'importanza di riconoscere e accettare la gamma completa delle emozioni umane.
Introduzione
La condizione umana è intrinsecamente legata a un ampio spettro di emozioni, tra cui la tristezza e la felicità. Queste due esperienze emotive sono spesso percepite come opposte, ma in realtà coesistono in una dinamica complessa. In questo contesto, è utile considerare non solo le persone che si definiscono rigidamente come tristi o felici, ma anche quelle che si riconoscono come "vere", capaci di navigare tra le diverse sfumature emotive. Questo articolo si propone di esaminare le implicazioni filosofiche di questa distinzione e di riflettere su come essa possa influenzare la nostra comprensione dell'autenticità e della realizzazione personale.
La Tristezza e la Felicità: Due Facce della Stessa Medaglia
La tristezza e la felicità sono spesso considerate come stati emotivi opposti, ma questa visione binaria può risultare limitante. La filosofia esistenzialista, ad esempio, suggerisce che la sofferenza e la gioia sono interconnesse e che la consapevolezza della propria mortalità e delle proprie vulnerabilità può arricchire l'esperienza della vita. In questo senso, la tristezza può essere vista come un elemento necessario per apprezzare la felicità. Le persone che si identificano esclusivamente come tristi o felici possono perdere di vista questa interconnessione, vivendo in una sorta di dualismo emotivo che limita la loro esperienza.
L'Autenticità dell'Essere Vero
Le persone "vere" rappresentano un paradigma alternativo. Queste individui non si limitano a una categorizzazione emotiva, ma abbracciano la complessità della loro esistenza. La filosofia di Søren Kierkegaard, ad esempio, enfatizza l'importanza dell'autenticità e della soggettività. Essere veri implica riconoscere e accettare tutte le emozioni, comprese quelle che possono sembrare negative. Questa accettazione porta a una maggiore comprensione di sé e degli altri, promuovendo una forma di empatia che trascende le etichette di tristezza e felicità.
La Dinamicità delle Emozioni
La vita è caratterizzata da un continuo fluire di emozioni. Le persone vere sperimentano alti e bassi, riconoscendo che la tristezza e la felicità non sono stati permanenti, ma piuttosto momenti transitori. Questa visione dinamica delle emozioni è supportata dalla psicologia positiva, che sottolinea l'importanza di sviluppare resilienza e consapevolezza emotiva. Le persone che abbracciano la loro autenticità tendono a essere più resilienti, poiché non temono di affrontare la tristezza, ma la vedono come parte integrante del loro viaggio.
Conclusione
In conclusione, la distinzione tra persone tristi, felici e quelle vere offre una prospettiva interessante sulla condizione umana. Riconoscere la complessità delle emozioni e abbracciare la propria autenticità può portare a una vita più ricca e significativa. La tristezza e la felicità non devono essere viste come opposti, ma come componenti di un'esperienza umana complessa e interconnessa. Solo attraverso l'accettazione di tutte le sfumature emotive possiamo aspirare a una comprensione più profonda di noi stessi e degli altri, promuovendo una società più empatica e autentica.
**Bibliografia**
- Kierkegaard, S. (1980). *The Sickness Unto Death*. Princeton University Press.
- Seligman, M. E. P. (2011). *Flourish: A Visionary New Understanding of Happiness and Well-Being*. Free Press.
- Frankl, V. E. (2006). *Man's Search for Meaning*. Beacon Press.
Questo articolo si propone di stimolare una riflessione profonda sulla nostra esperienza emotiva e sull'importanza di vivere in modo autentico, accettando la dualità della nostra esistenza.
-

@ b34b4408:acfb9667
2024-10-31 05:00:15
😱 การทบทวนสมมติฐานไขมันกับโรคหัวใจ: มุมมองใหม่จากหลักฐานทางวิทยาศาสตร์ 😱
https://www.mdpi.com/2072-6643/16/10/1447?fbclid=IwY2xjawGOTtxleHRuA2FlbQIxMAABHa2lVBffVeuI0SC8RgzbvQgtkbIsLwat1tDzxZKQ8UoEWYJuwC-Y7no7zA_aem_Qtv0GQuxhWxk0P2KCUFDmw
.
🩸บทความนี้นำเสนอการวิเคราะห์เชิงลึกเกี่ยวกับสมมติฐานไขมันกับโรคหัวใจ (Lipid-Heart Hypothesis) ที่มีอิทธิพลต่อแนวทางโภชนาการทั่วโลกมาเกือบ 70 ปี โดยรวบรวมหลักฐานจากการศึกษาวิจัยที่สำคัญและผลกระทบที่เกิดขึ้น
.
โดยสมมติฐานไขมันกับโรคหัวใจถูกเสนอโดย Ancel Keys ในปี 1953 โดยตั้งอยู่บนความเชื่อว่าการบริโภคไขมันทั้งหมด ไขมันอิ่มตัว และคอเลสเตอรอลในปริมาณสูงจะนำไปสู่การเกิดโรคหัวใจ อย่างไรก็ตาม
**สมมติฐานนี้มีข้อบกพร่องสำคัญหลายประการ:**
.
1. การรวมไขมันทรานส์กับไขมันอิ่มตัว:
- ไม่แยกแยะผลกระทบที่แตกต่างระหว่างไขมันทั้งสองชนิด
- ละเลยผลเสียของไขมันทรานส์ที่เกิดจากกระบวนการอุตสาหกรรม
.
2. การส่งเสริมการบริโภค PUFA โดยไม่จำกัด:
- ขาดการกำหนดขีดจำกัดการบริโภคกรดไขมันไม่อิ่มตัวหลายพันธะ
- ไม่คำนึงถึงสมดุลระหว่างโอเมก้า-6 และโอเมก้า-3
.
3. การมองข้ามปัจจัยอื่น:
- ไม่พิจารณาผลของน้ำหนักตัว การออกกำลังกาย และปัจจัยด้านวิถีชีวิต
- ละเลยบทบาทของการอักเสบและความเครียดออกซิเดชัน
.
**ซึ่งเมื่อมาดูหลักฐานจากการศึกษาระยะยาวต่างๆเช่น**
.
.

😲 Framingham Multi-Generational Study (1948-ปัจจุบัน) การศึกษาระยะยาวที่สำคัญนี้ได้พบข้อมูลที่น่าสนใจ:
- ไม่พบความสัมพันธ์ระหว่างการบริโภคไขมันกับระดับคอเลสเตอรอล
- ยิ่งบริโภคไขมันอิ่มตัว คอเลสเตอรอลและแคลอรี่มาก ระดับคอเลสเตอรอลในเลือดกลับยิ่งต่ำ
- ความดันโลหิตสูงและเบาหวานเป็นปัจจัยเสี่ยงสำคัญมากกว่า
.

😲Seven Countries Study (1957-1984) การศึกษาในประชากร 7 ประเทศ รวม 12,763 คน พบว่า:
- ไม่มีความสัมพันธ์ระหว่างระดับคอเลสเตอรอลกับการเสียชีวิตจากโรคหัวใจ
- ประชากรในเกาะครีตที่บริโภคไขมันสูง (36.1%) กลับมีอัตราการเสียชีวิตต่ำที่สุด
- น้ำมันมะกอกและกรดไขมันโอเลอิกสัมพันธ์กับอัตราการเสียชีวิตจากโรคหัวใจที่ต่ำ
-
.
😲PURE Study การศึกษาขนาดใหญ่ในประชากร 18 ประเทศ พบว่า:
- การบริโภคไขมันสูงสัมพันธ์กับความเสี่ยงการเสียชีวิตที่ต่ำลง
- ไขมันอิ่มตัวสัมพันธ์กับความเสี่ยงโรคหลอดเลือดสมองที่ต่ำลง
- ผลิตภัณฑ์นมไขมันเต็มส่งผลดีต่อสุขภาพหัวใจและหลอดเลือด
.
**รวมถึงการศึกษาทางคลินิกที่สำคัญต่างๆ**
.

😟Minnesota Coronary Experiment (1968-1973) ผลการศึกษาในผู้เข้าร่วม 9,423 คน แสดงให้เห็นว่า:
- กลุ่มที่บริโภคน้ำมันข้าวโพดมีอัตราการเสียชีวิตสูงกว่า
- ผู้ที่ระดับคอเลสเตอรอลลดลงมากที่สุดกลับมีความเสี่ยงสูงที่สุด
- ไม่พบประโยชน์ของการแทนที่ไขมันอิ่มตัวด้วย PUFA
-

.
😟Sydney Diet Heart Study (1967-1973) การศึกษาในผู้ชาย 458 คน พบว่า:
- กลุ่มที่บริโภคน้ำมัน safflower มีอัตราการเสียชีวิตสูงกว่า
- ความเสี่ยงการเสียชีวิตจากโรคหัวใจเพิ่มขึ้น 74%
- การลดคอเลสเตอรอลไม่ได้นำไปสู่ผลลัพธ์ที่ดีขึ้น
.
**ทำให้เกิดผลกระทบของในส่วนการแนะนำให้บริโภคอาหารไขมันต่ำ**
ซึ่งส่งผลให้เกิดการเปลี่ยนแปลงที่สำคัญ:
😱😱😱
1. การเพิ่มขึ้นของโรคเรื้อรัง:
- โรคอ้วนเพิ่มจาก 48.8% (1960) เป็น 82.3% (2017-2018)
- เบาหวานเพิ่มจาก 6.2% (1994) เป็น 14.7% (2021)
- โรคอัลไซเมอร์เพิ่มจาก 4.5 ล้านคน (2000) เป็น 6.7 ล้านคน (2023)
.
2. การเปลี่ยนแปลงรูปแบบการบริโภค:
- เพิ่มการบริโภคอาหารแปรรูป
- ลดการบริโภคอาหารที่มีคุณค่าทางโภชนาการสูง
- เพิ่มการบริโภคคาร์โบไฮเดรตและน้ำตาล
.
โดยบทความนี้ได้เสนอแนะสำหรับแนวทางโภชนาการใหม่ดังนี้
😉😉😉
1. การปรับปรุงคำแนะนำด้านอาหาร:
- ทบทวนการจำกัดไขมันอิ่มตัว
- กำหนดขีดจำกัดการบริโภค PUFA
- ส่งเสริมการบริโภคอาหารธรรมชาติ
.
2. การพิจารณาปัจจัยรอบด้าน:
- คำนึงถึงคุณภาพอาหารโดยรวม
- ให้ความสำคัญกับการลดการบริโภคอาหารแปรรูป
- พิจารณาปัจจัยด้านวิถีชีวิตและสิ่งแวดล้อม
.
จากหลักฐานทางวิทยาศาสตร์จำนวนมากไม่สนับสนุนสมมติฐานไขมันกับโรคหัวใจ การจำกัดไขมันอิ่มตัวและส่งเสริมการบริโภค PUFA โดยไม่มีขีดจำกัด อาจส่งผลเสียต่อสุขภาพ จำเป็นต้องมีการทบทวนแนวทางโภชนาการโดยอาศัยหลักฐานที่ทันสมัยและครอบคลุม เพื่อส่งเสริมสุขภาพที่ดีของประชากรในระยะยาว
.
......................................
ข้อมูลสุขภาพดีๆที่ไม่มีค่าใช้จ่าย
https://www.youtube.com/@fastingfatdentist
.
หากสนใจวิธีการดูแลสุขภาพตามแบบ IFF ปรึกษาส่วนตัว inbox มาสอบถามที่เพจได้เลยครับ
.
#ความน่ากลัวในการดูแลสุขภาพคือการที่เชื่อโดยไม่มีความรู้ .
.
#IFF #IFF_talk #intermittentfasting #keto #Lowcarb #CD #plantbased #RemissionDiabetes #ร่างกายเราคือธรรมชาติไม่ใช่ยา #เบาหวานหายได้โดยไม่ต้องใช้ยา #หมอไหวของหมอแบบนี
#fastingfatdentist
#healthstr
#IFF
#fiat
#siamstrOG
#siamstr
#bitcoin
#siamesebitcoiners
#orangebaby
#หมอบ่นFiat
-

@ 4ba8e86d:89d32de4
2024-10-25 13:17:33
Foi criado com o objetivo de fornecer aos usuários uma experiência de navegação mais privada e segura na internet. O LibreWolf é uma excelente alternativa ao Firefox, com algumas diferenças significativas em relação ao navegador da Mozilla.
O LibreWolf foi desenvolvido com foco na privacidade e segurança do usuário. Ele bloqueia rastreadores de terceiros, impede o envio de dados de telemetria e desabilita recursos de rastreamento de usuário que vêm ativados por padrão no Firefox. Além disso, ele vem pré-configurado com diversas extensões de privacidade, como uBlock Origin, Privacy Badger e HTTPS Everywhere, que ajudam a bloquear anúncios, scripts maliciosos e outras ameaças de segurança enquanto você navega na web.
Outra característica notável do LibreWolf é que ele usa o mecanismo de pesquisa Searx como padrão, em vez do Google. O Searx é conhecido por fornecer resultados de pesquisa mais privados e anônimos, sem rastrear as suas atividades online.
O LibreWolf também possui suporte nativo ao Tor, que permite aos usuários acessar a internet anonimamente.
Além dos recursos de privacidade e segurança, o LibreWolf é muito semelhante ao Firefox em termos de usabilidade e funcionalidades. Ele é fácil de instalar e configurar, e possui um grande número de extensões disponíveis na sua loja de extensões.
O LibreWolf é uma excelente opção para usuários que buscam um navegador mais privado e seguro. Se você se preocupa com a sua privacidade online, vale a pena experimentar o LibreWolf. Ele é gratuito e de código aberto, o que significa que você pode baixá-lo e personalizá-lo de acordo com suas necessidades específicas.
https://librewolf.net/
https://github.com/librewolf-community
-

@ c230edd3:8ad4a712
2024-10-21 22:24:42
## Chef's notes
This is great to start in the morning, and come home to a nearly finished meal. I like to make tacos that day, then use any remaining for just about anything from chili to omelets. Fun way to prepare ramen too.
## Details
- ⏲️ Prep time: 30 min, plus 15 before serving
- 🍳 Cook time: 8 hours
- 🍽️ Servings: 10-12
## Ingredients
- 3-4lb Chuck Roast, bone-in preferred
- 1 large White Onion, quartered
- 6-8 cloves Garlic, peeled
- 5 Roma Tomatoes, halved
- 6-8 dried Arbol Chiles, seeded
- 3-4 Guajillo Chiles, seeded
- 2 tsp Coriander seeds
- 2 tsp Cumin seeds
- 2 Tbsp Oregano, Mexican Oregano if available
- 1/2 tsp ground Cinnamon
- 2 whole Bay Leaves
- 1 tsp Salt
- SPG style seasoning mix to coat the roast
- Any toppings desired (avocado, cilantro, sour cream, queso fresca, cheddar, fresh onion, etc)
## Directions
1. Preheat large frying pan to med/high, add oil for searing
2. Add onions and tomatoes, sear until edges char, add garlic and saute until fragrant, transfer to slow cooker
3. Pat roast dry, season all sides, transfer to pan
4. Sear roast on all sides, 2-4 minutes or until golden brown, transfer to slow cooker
5. Add all seasonings and beef broth to slow cooker
6. Cook on low 8+ hours or until the meat is falling apart
7. Remove bone and bay leaves
8. Transfer liquid and vegetables to a blender with loose fitting lid, blend until smooth, transfer to large bowl
9. Shred roast in slow cooker, pour sauce mix back in and stir. Adjust ratio by adding more beef broth if desired. Salt to taste.
10. Serve, drained as tacos, nachos, omelets, etc. Serve with broth as stew or mix with ramen
-

@ fd208ee8:0fd927c1
2024-10-20 18:19:48
(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
# A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a [GitHub repo](https://github.com/ShadowySupercode), and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
* Why can I not login? Oh, they fixed the login! Nope, still can't login.
* If I press this button, it says it sent, but it didn't send. Where note?
* They announced a new feature, but I tried it and it didn't work. Oh well.
* I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
* The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it _really_ needed... was a **Nostr Stable Version**. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be _allowed to have expectations_ of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
# Things working is an underrated concept
I know that the very idea of software _running as expected_ and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are _all_ features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load _every damn time_, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that _things working_ becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
# Where to start?
## Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
## Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
## Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our [project wiki page](https://wikistr.com/gitcitadel-project), and came up with a Vision and a Mission:
The _vision_ is what the overall goals of the company are, whereas the _mission_ describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
## Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because _profits are the most pure form of communication that consumers in the market have_ with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial _lambo and a bimbo_. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but **pay them out, you should**. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
## Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
### Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days.
Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the _okay, so this is what we've decided_ comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
### Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to [Investopedia](https://www.investopedia.com/terms/l/llc-operating-agreement.asp), common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's _emotionally binding_, which is arguably more important.
Writing things down is an advanced form of _naming things_ and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
## Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-

@ dc4cd086:cee77c06
2024-10-18 04:08:33
Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
## Key Features:
### Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
### Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
### Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
## Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine.
Will support multiple open and closed language models for user choice
Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
## Screenshots
### Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
### Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
## Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
## Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle
nostr:nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-

@ 472f440f:5669301e
2024-10-11 14:20:54
As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward.
Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years.
It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering.
Speaking of the job market, the numbers that came in yesterday were worse than expected:
The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now.
All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential.
There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries.
The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority.
The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare.
I'll leave you with some thoughts from Porter Stansberry:
"We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked.
1. Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet.
2. Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow.
3. Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror.
Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it.
Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money.
And that day is here."
---
Final thought...
I hope my tux still fits for this wedding.
Enjoy your weekend, freaks.Use the code "TFTC" for 15% off
-

@ 460c25e6:ef85065c
2024-10-10 13:22:06
In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients:
- **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
- **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
- **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
- **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
**Super Clients**
- [amethyst](https://amethyst.social)
- [nostrudel](https://nostrudel.ninja)
- [coracle](https://coracle.social)
**Clients**
- [damus](https://damus.io) - twitter
- [primal](https://primal.net) - twitter
- [snort](https://snort.social) - twitter
- [gossip](https://github.com/mikedilger/gossip) - twitter
- [lume](https://lume.nu) - twitter
- [ditto](https://soapbox.pub/ditto/) - twitter
- [rabbit](https://rabbit.syusui.net) - twitter
- [freefrom](https://freefrom.space) - twitter
- [nos](https://nos.social) - twitter
- [flycat](https://flycat.club) - twitter
- [straylight](https://straylight.cafe) - twitter
- [nostter](https://nostter.app) - twitter
- [iris](https://iris.to) - twitter
- [nostur](https://nostur.com) - twitter
- [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter
- [yana](https://yana.do) - twitter
- [openvibe](https://openvibe.social) - twitter
- [freerse](https://freerse.com) - twitter
- [0xchat](https://0xchat.com) - chats
- [cornychat](https://cornychat.com) - chats
- [coop](https://github.com/lumehq/coop) - chats
- [nostrchat](https://nostrchat.io) - chats
- [blowater](https://blowater.deno.dev) - chats
- [habla](https://habla.news) - blogs
- [yakihonne](https://yakihonne.com) - blogs
- [highlighter](https://highlighter.com) - blogs
- [blogstack](https://blogstack.io) - blogs
- [stemstr](https://stemstr.app) - music
- [wavlake](https://wavlake.com) - music
- [fountain](https://fountain.fm) - podcasts
- [zap.stream](https://zap.stream) - live streaming
- [shopstr](https://shopstr.store) - marketplace
- [plebeian.market](https://plebeian.market) - marketplace
- [flotilla](https://flotilla.coracle.social) - communities
- [satellite](https://satellite.earth) - communities
- [zapddit](https://zapddit.com) - communities
- [nostr.kiwi](https://nostr.kiwi) - communities
- [hivetalk](https://hivetalk.org) - video calls
- [flare](https://flare.pub) - long-form videos
- [nostrnests](https://nostrnests.com) - audio spaces
- [wherostr](https://wherostr.social) - location
- [yondar](https://go.yondar.me) - location
- [stacker.news](https://stacker.news) - news
- [flockstr](https://flockstr.com) - events
- [nostrocket](https://nostrocket.org) - issue tracker
- [docstr](https://docstr.app) - docs
- [satshoot](https://satshoot.com) - freelance
- [wikifreedia](https://wikifreedia.xyz) - wiki
- [formstr](https://formstr.app) - forms
- [chesstr](https://chesstr.pages.dev) - chess
- [memestr](https://memestr.app) - meme feed
- [npub.cash](https://npub.cash) - wallet
- [npub.pro](https://npub.pro) - websites
- [gitworkshop](https://gitworkshop.dev) - dev tools
- [onosendai](https://onosendai.tech) - metaverse
- [degmods](https://degmods.com) - games
- [turdsoup](https://turdsoup.com) - prompts
**Mini Clients**
- [amber](https://github.com/greenart7c3/Amber) - signer
- [alby](https://getalby.com) - signer
- [nos2x](https://github.com/fiatjaf/nos2x) - signer
- [nsec.app](https://nsec.app) - signer
- [keys.band](https://keys.band) - signer
- [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer
- [nokakoi](https://nokakoi.com) - anon
- [zap.cooking](https://zap.cooking) - recipes
- [anonostr](https://anonostr.com) - anon
- [getwired](https://getwired.app) - anon
- [lowent](https://lowent.xyz) - anon
- [creatr](https://creatr.nostr.wine) - exclusive content
- [lightning.video](https://lightning.video) - exclusive content
- [zaplinks](https://zaplinks.lol/slides) - slides
- [listr](https://listr.lol) - lists
- [zap.store](https://zap.store) - app store
- [badges.page](https://badges.page) - badges
- [oddbean](https://oddbean.com) - news
- [dtan](https://dtan.xyz) - torrents
- [nosta](https://nosta.me) - user pages
- [pinstr](https://pinstr.app) - pinterest
- [pollerama](https://pollerama.fun) - polls
- [swarmstr](https://swarmstr.com) - trending
- [nostrapp](https://nostrapp.link) - apps manager
- [noogle](https://noogle.lol) - search
- [ostrich.work](https://ostrich.work) - job postings
- [emojito](https://emojito.meme) - emoji manager
- [nostree](https://nostree.me) - links
- [citrine](https://github.com/greenart7c3/citrine) - local relay
- [joinstr](https://joinstr.xyz) - coinjoins
- [heya](https://heya.fund) - crowdfunding
- [zapplepay](https://zapplepay.com) - zaps
- [nosbin](https://nosbin.com) - clipboard
- [shipyard](https://shipyard.pub) - scheduler
- [tunestr](https://tunestr.io) - live streams
- [filestr](https://filestr.vercel.app) - files
- [nostrcheck.me](https://nostrcheck.me/) - media hosting
- [sheetstr](https://sheetstr.amethyst.social) - spreadsheets
- [crafters](https://crafters.amethyst.social) - curriculum vitae
**Micro Clients**
- [w3](https://w3.do) - url shortener
- [nosdrive](https://nosdrive.app) - backups
- [zaplife](https://zaplife.lol) - zaps dashboard
- [zapper.fun](https://zapper.fun) - payments
- [nostrends](https://nostrends.vercel.app) - trends
- [zephyr](https://zephyr.coracle.social) - trends
- [wavman](https://wavman.app) - music player
- [nostrrr](https://nostrrr.com) - relay info
- [nosdump](https://github.com/jiftechnify/nosdump) - relay info
- [notestack](https://notestack.com) - blogs
- [nostr.build](https://nostr.build) - media hosting
- [nostr.watch](https://nostr.watch) - relay info
- [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports
- [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions
- [snakestr](https://satoshipuzzles.github.io/Snakestr) - games
- [deletestr](https://zaplinks.lol/deletestr) - deletion requests
- [2048str](https://zaplinks.lol/2048str) - games
- [nostrqr](https://zaplinks.lol/nostrqr) - qr generator
- [notanostrclient](https://zaplinks.lol/notanostrclient) - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients.
-

@ fd208ee8:0fd927c1
2024-10-09 12:27:53
## Why waste time, looking at other people's stuff?
I get this question a lot, on Nostr, and it feeds immediately back to the next question: *Why don't you just build your own client, if you're so smart?*
This was a completely new question for me, as I'm used to collaborating with at least one other person, even when doing FOSS stuff. (No, this isn't my first such project; we just used to call it "volunteering" and "sharing the code", which sounds way less glamorous.) It never occurred to me, that a habit of collaboration and interaction was some sign of my ignorance and incompetence, or somehow proof that I can't vomit up "Hello World!" in 5 different programming languages.
I also made the deadly political mistake, when I entered the Nostrsphere, of refusing to call myself a "dev". For me, "dev" is a special title, given to someone doing a specific type of programming (fiddling with GUIs, mostly, which I've only done occasionally, as a sub), whereas the types I've done are "test automation", "development operations", "database management and data curation", "requirements engineering", and "application administration". Because it's so much easier to find someone interested in building a GUI, rather than building AnythingElse, I tend to slide into AnythingElse and it eventually became my professional specialty to be the Girl Friday of every project.

But, in Nostr, there is no AnythingElse category. There are only (GUI) client devs and AllOfTheIdiotsWhoMustBowDownToTheDevs. Which merely doubled my instinct to distance myself from the term. I do not want to join some cargo cult and be pedestalized and regarded as some sort of superhuman everyone owes fealty to, in return for raining GUI presents down on my loyal subjects.
Software engineers are simply people who are skilled craftsman, not gods, and it is fair to point out that some are more skilled than others. It is also completely fair to criticize their products, report bugs, and wonder aloud at endemic low-quality.
Which brings me back to the initial question:
## What does the inquisitive dev know, that the others don't?
1) You learn an awful lot about an awful lot, by looking at specs, reviewing code, and trying out various implementations of concepts you are already familiar with. There are, in fact, n number of use cases for every event type, and I've seen so many of them, that I can conjure them up, or invent new ones, on the fly, rather than wasting time inventing similar events.
2) They don't have to explain their concept to you, later, when you interact. Each interaction brings you closer to parallel-levels of knowledge, which raises the signal-strength of the interaction, and widens your own knowledge base, for interacting with third parties.
3) You are increasingly-likely to contribute code or perform some other more-advanced task, for other people, as you don't face the hurdle of adjusting to a new repo or unfamiliar language, while being less-likely to merely fork-and-ignore because you have a standing business relationship with the other developer.
4) If the other dev stops maintaining the repo, you'll be inclined to continue on your own. You may even eventually receive administrative access, rather than needing to fork, as they trust you with their stuff. This means that the risk of the repo becoming abandoned falls, with each active dev snooping around it, even if that is not their primary project.
5) It helps you determine who to focus your energy on interacting with, further. Is this person new to software development, perhaps, but has some interesting transfer-knowledge from some other branch, that has resulted in a surprisingly novel concept? Is this person able to write very clean code, so that merely reading their code feels like mental training for your own craftsman's toolbox?
...and many more reasons, but this is getting too long, so, let's just cut to the chase.
## What does a craftswoman want?
But, this still doesn't answer the question of my private motivation. Why do I want to gather all of this knowledge, from those further ahead, than I?
I think Nostr has long moved past the initial stage, where mere speed was of the essence, so that one npub could _finally_ post a note and have it appear on the other npubs' client. That must have felt like a miracle, but it increasingly feels like a disaster, as the steadily-rising complexity of the Nostr ecosystem causes haphazardly-structured and largely-unexamined code bases to begin to atrophy, or result in developers running around at an exhausting speed, with their bug-extinguishers, to put out fire after fire.
I think the time has arrived, for a different kind of development. Maybe even for a different kind of developer. Not replacing the experimentalism that made Nostr fun, but adding the realm of production-quality software engineering. The sort of software development that requires relay administration, testing, support... collaboration, interaction, maybe even someone who does AnythingElse.
I want to build useful, elegant products people enjoy using and feel comfortable relying on. I want them to use them, naturally and happily, to accomplish tasks they consider worthwhile. I don't want them thinking about me, while they use it. The craftswoman should never be greater than her work.
I want them to feel free -- nay, be eager! -- to give me both positive and negative feedback. My assumption is _always_ that our production is imperfect because we are imperfect, so you do us a favor, by pointing out where we can improve. That's why we wish to integrate a feedback form that produces ngit issue events, putting your questions and comments straight on our board.
And there will be an AnythingElse person, reading that board, and responding promptly, rest assured.
-

@ 4ba8e86d:89d32de4
2024-10-07 23:00:50
é uma tecnologia que permite criar uma conexão segura e privada entre um dispositivo e a internet. É como uma espécie de túnel privado que passa por cima da internet pública, criptografando seus dados e mascarando seu endereço IP para proteger sua privacidade e segurança online.
A história da VPN remonta ao final dos anos 1990, quando as empresas começaram a usar conexões dedicadas (linhas alugadas) para conectar suas redes corporativas e permitir que seus funcionários trabalhassem remotamente. Essas conexões dedicadas eram caras e difíceis de configurar, o que levou à criação das primeiras VPNs baseadas em software.
A primeira VPN comercialmente disponível foi a Redes Privadas Virtuais (RPV), lançada pela Microsoft em 1996. Desde então, várias empresas e organizações começaram a usar VPNs para proteger seus dados confidenciais e permitir que seus funcionários trabalhassem remotamente de forma segura.
Como funciona a VPN?
Quando você se conecta a uma VPN, seu dispositivo estabelece um canal criptografado de comunicação com um servidor remoto. Todo o tráfego de dados entre o seu dispositivo e o servidor remoto é criptografado, o que significa que é transformado em códigos que só podem ser lidos por seu dispositivo e pelo servidor remoto.
Além disso, quando você usa uma VPN, seu endereço IP é substituído pelo endereço IP do servidor remoto. Isso significa que sua localização física e outros dados pessoais não são facilmente rastreados por sites que você visita e outros usuários da internet.
Por que usar uma VPN?
Existem várias razões pelas quais você pode querer usar uma VPN. Algumas das principais razões incluem:
• Acesso a conteúdo restrito geograficamente: Se você estiver em um país que restringe o acesso a certos sites ou serviços, uma VPN pode permitir que você os acesse como se estivesse em outro lugar. Por exemplo, se você estiver no Brasil e quiser acessar um site que só está disponível nos EUA, uma VPN pode permitir que você se conecte a um servidor nos EUA e acesse o site como se estivesse lá.
• Segurança e privacidade online: Quando você usa uma VPN, suas informações são criptografadas e protegidas contra hackers e outros invasores que podem tentar interceptar suas informações.
• Proteção de informações pessoais: Quando você está usando uma rede Wi-Fi pública (como em um café ou aeroporto), outras pessoas na mesma rede podem potencialmente interceptar suas informações pessoais e senhas. Uma VPN pode ajudar a proteger suas informações contra esses ataques.
• Evitar rastreamento de anúncios: Muitos sites e anunciantes rastreiam sua atividade online para enviar anúncios personalizados. Usar uma VPN pode ajudar a evitar esse rastreamento e manter sua atividade online mais privada.
As VPNs estão disponíveis em vários tipos e preços, desde serviços gratuitos até soluções corporativas mais avançadas. Ao escolher uma VPN, é importante verificar a política de privacidade da empresa para garantir que eles não compartilhem suas informações pessoais com terceiros. Além disso, algumas VPNs podem diminuir a velocidade da sua conexão à internet, então é importante escolher um serviço com uma boa reputação e boa qualidade Eu uso a Mullvap VPN..
uma VPN é uma ferramenta importante para manter sua segurança e privacidade online. Com a capacidade de criptografar suas informações, mascarar seu endereço IP e permitir o acesso a conteúdo restrito geograficamente, as VPNs são uma ótima opção para proteger sua presença online.
-

@ 4ba8e86d:89d32de4
2024-10-07 22:45:27
Parte 1: Configuração e preparação
1. Instalação do Tails:
- Baixe a imagem do Tails no site oficial (https://tails.boum.org/).
- depois baixar no site vai Aberta " verificar seu download"
Você vai Verifique no próprio site se o tails que você baixou é tails compilado e desenvolvido pelo equipe Tails.
- Grave a imagem do Tails em um pendrive ou cartão de memória usando um software de gravação adequado, como o Rufus.
- Reinicie o computador e inicie a partir do pen drive ou cartão de memória que contém o Tails. Certifique-se de configurar o computador para inicializar a partir de um dispositivo externo.
- Siga as instruções na tela para completar a configuração do Tails.
2. Configuração do disco persistente:
- Após iniciar o Tails, defina uma senha para criptografar o disco persistente.
- Abra o menu "Applications" e selecione "Favorites".
- Em seguida, escolha "Configure Persistent Volume".
- Selecione as opções para salvar no seu pendrive no disco persistente.
- Procure pela opção Bitcoin client e habilite-a.
- Essa senha é necessária para acessar e salvar seus arquivos e configurações persistentes, incluindo a carteira Electrum.
- No menu do Tails, clique em "Applications" e, em seguida, em "Internet". Selecione "Electrum Bitcoin Wallet".
- O Electrum será iniciado e você poderá criar uma nova carteira selecionando "Criar uma nova carteira" e escolhendo um nome para a carteira.
- Selecione "Carteira padrão" e escolha se deseja criar uma nova carteira ou restaurar a partir de um backup.
- Se optar por fazer o backup da carteira, selecione a opção "semente BIP39".
- Se desejar adicionar uma passphrase à carteira Electrum, clique no botão "Opção" e escolha "Estender esta semente com a palavra personalizada". Insira uma passphrase forte e siga as instruções para concluir a configuração da carteira.
Anote e guarde a passphrase em um local seguro, separadamente das palavras-chave de recuperação (seed).
Depois Aberta em "próximo"
Vai aparece a Tela "Tipo de script e caminho derivação"
Selecionar a opção "Native segwit (p2wpkh) aberta em "próximo" agora vai aparecer uma tela pra adicionar senha para criptógrafa o arquivo da carteira electrum. So insira uma senha.
Obs: você tem três senha diferente pra lembrar.
Senha disco persistent.
Senha passphrse.
Senha criptógrafa o arquivo da carteira electrum.
Anote e guarde a passphrase em um local seguro, separadamente das palavras-chave de recuperação (seed).
- guarde em um local seguro as palavras-chave de recuperação (seed) fornecidas pelo Electrum. Essas palavras são importantes para recuperar sua carteira se você perder o acesso ao Tails.
Parte 2: Assinatura e envio da transação
Assinatura da transação no Tails (offline):
- Desconecte o computador do Tails da internet, removendo o cabo de rede ou desativando a conexão Wi-Fi.
1. No tails vai na opção "Carteira" logo em seguida na opção "informações da carteira"
Depois Aberta em exibe o QR Code da chave pública XPUB que está no Tails.
Configuração do celular:
- No seu celular, abra a carteira Electrum e clique na opção "Criar nova carteira".
- Atribua um nome à carteira e, em seguida, selecione a opção "Carteira padrão" (Standard Wallet) seguida da opção "Usar chave mestra" (Use Master Key).
- Agora, você precisará escanear com a câmera do celular o código QR da chave pública XPUB que está no Tails. Essa chave mestra permitirá que você acompanhe o saldo e as transações da sua carteira, mas não poderá gastar os fundos ou assinar transações diretamente.
- Toque em "Próxima" para iniciar o processo de sincronização da carteira no celular.
Pra recebe pagamento com o celular deixa o Tails totalmente offine.
É Só ir na Aba "recebe" depois em "pedir"
Você pode copiar o endereço ou exibe o Qrcode pra pagamento. você pode verificar que o endereço de recebe que aparece no celular eo mesmo que está no seu Tails offine.
Pra enviar vai na Aba "enviar"
Aberta em "escanear" verificar as informações endereço é escolher o valor da taxa.
Depois Aberta em "pagar"
Vai parece um aviso "transação teve ser substituível ?"
Aberta em "sim" Se a taxa foi muito baixa não confimar nos próximos dias para poder aumentar se precisar.
Vai exibe na tela a quanti a enviar é total taxa de mineração
Aberta em "concluir"
Vai mostra quantia a ser enviada ID da transação de saída mas ela não está assinada. Atráves do Qrcode que está no celular você vai exibir Qrcode que você vai escanear com a câmara Web do seu Tails
Vai volta no Tails na opção "ferramentas"
- logo em seguida escolhar a opção "carregar transação"
depois na opção "a partir de um código Qr" vai abrir a câmera do Tails você mostra o código Qr que está no celular para a câmera Tails.
No tails vai mostrar todas as informações da transação.
Após confimar as informações da transação, clique em "Assinar"
Digite a senha da carteira Electrum para desbloquear a chave privada.
Em seguida, clique em "Exportar" e selecione a opção "Mostrar como um código QR"
No celular aberta em "escanear"
O código Qr da transação assinada.
Vai aparecer na tela do seu celular Status da transação assinada é informações da transação.
Então finalmente você aberta em "Transmitir" para enviar a transação assinada para a rede Bitcoin.
Ao optar por usar o Tails como base para criar e assinar transações, você está garantindo a segurança da sua chave privada no ambiente protegido do Tails, enquanto utiliza o celular apenas para visualizar informações e enviar a transação assinada para a rede.
Uma medida adicional de segurança é a criptografia do disco persistente do Tails com uma senha forte, juntamente com o uso de senhas fortes para proteger a carteira Electrum e a chave privada. Essas camadas extras de proteção ajudam a manter suas informações seguras.
É fundamental tomar todas as precauções necessárias para proteger seus dispositivos. Certifique-se de manter o Tails atualizado, utilizar software confiável para gravá-lo em um pendrive ou cartão de memória, e proteger adequadamente seu dispositivo móvel com senhas e atualizações de segurança.
Embora essa abordagem ofereça uma camada mais segura para proteger sua chave privada durante o processo de envio de transações, é importante lembrar de fazer backups regulares das suas palavras-chave de recuperação (seed). Além disso, considere tomar medidas adicionais de segurança de acordo com suas necessidades e recursos disponíveis.
Tenha em mente que a segurança absoluta não pode ser garantida, por isso é essencial adotar boas práticas de segurança digital.
Seguindo essas orientações e tomando as devidas precauções, você estará fortalecendo a segurança das suas transações ao utilizar o Tails para criar e assinar transações, mantendo a chave privada protegida no ambiente seguro do Tails, e utilizando o celular de forma segura para enviar a transação assinada para a rede.
https://youtu.be/abXkgXQ8BvI
https://youtu.be/NBj9-TolpvI
-

@ c4f5e7a7:8856cac7
2024-09-27 08:20:16
Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x).
# TL;DR
This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/).
The following concepts are explored:
1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust).
2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse.
3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
[Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
# Cognitive Dissonance
Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data).
In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
# Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k).
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
# Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g).
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons).
The remainder of this article explores how we can:
1. Verify ownership of a physical place in the real world;
2. Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation\!) states that:
> "The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
# Places and Web-of-Trust
[@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace).
2. Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
# Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with:
1. Your social graph;
2. The type or subject of the content being attested and by whom;
3. Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
[NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive.
**‘This is true’** resonates more strongly than **‘I like this.’**.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
# Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential):
> "A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
[@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that:
> "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
# Check-ins
Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\!
Check-ins could also be used as a signal for bonafide Place ownership over time.
# Summary: Trust Your Bros
So, to recap, we have:
**Places**: Digital representations of physical locations on Nostr.
**Check-ins**: Users signalling their presence at a location.
**Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left\! We have:
**Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
**Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
**Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
# Thanks
With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\!
-

@ e83b66a8:b0526c2b
2024-09-26 19:29:43
If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining.
Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully.
Solo mining pools exist, such as: https://solo.ckpool.org/
It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool.
You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power.
There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely.
A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine.
So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning.
So here’s my recommendation.
Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin.
Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join.
If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools.
Bear in mind that many of the other smaller pools are still controlled by Bitmain.
If you're still interested in lottery mining, here are your chances of winning a block:
Represented as Hash rates of different miners:
Nerdminer: 20 KH/s = 20,000 H/s
Bitaxe: 750 GH/s = 750,000,000,000 H/s
Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s
Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s
Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s
Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000
If you're running a Bitaxe, your percentage chance of winning a block is:
0.000000119426751592357%
Over a year, your chances increase to:
0.00627707006369428%
Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one):
0.000005%
Over a year, your chances increase to:
0.00026%
Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions:
https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/
https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx
https://www.youtube.com/watch?v=Wo91DWvZRs8
https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
-

@ e83b66a8:b0526c2b
2024-09-21 16:29:23
Here are some of the more interesting projects that I like:
Messaging:
https://www.0xchat.com/#/ - Private messaging - think WhatsApp
Xitter Like Clients:
https://damus.io/ - iPhone client
https://nostrapps.com/amethyst - Android client
https://primal.net/downloads - Android, iPhone & Desktop
https://shipyard.pub/posts - Schedule future posts
Interesting sites:
https://zap.stream/ - Video streaming
https://fountain.fm/ - Podcasting
https://wavlake.com/ - Music streaming
https://shopstr.store/ - Online shop
https://zap.cooking/recent - Cooking recipes
https://ostrich.work/ - NOSTR jobs board
NOSTR tools
https://nostr.band/ - Powerful search tool
https://nostr.wine/ - Powerful, but centralised paid relay
https://npub.pro/ - Website creation tool
https://nostr.build/ - Media and file storage
https://relay.tools/ - Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user - Creator tools
List of NOSTR apps:
https://nostrapps.com/
-

@ 3bf0c63f:aefa459d
2024-09-18 10:37:09
# How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a _platform_ that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. **So what should you do instead?** Here's an idea in two steps:
1. **Write a Nostr client tailored to the niche you want to cover**
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to `wss://nostr.chrysalisrecords.com/` to see only the latest music releases accredited by that label or to `wss://nostr.indiemusic.com/` to get music from independent producers from that community.
2. **Run a relay that does all the magic**
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it `wss://magicsaucemusic.com/` -- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (`["REQ", "_", {}]`), and this will cause people to want to publish to your relay while others will want to read from it.
You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and **they do not depend on you, therefore they're more likely to trust you**.
---
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under `wss://magicsaucemusic.com` and I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing on `wss://nos.lol` or `wss://relay.damus.io` or whatever relay that doesn't even know anything about music.
The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-

@ cb084639:2f16502a
2024-09-17 10:09:23
รีวิวงาน #TBC2024 สไตล์ #Richter ![image]()
เรื่องมันเริ่มมาตั้งแต่ช่วงที่ทาง
npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5
ประกาศขายตั๋วงาน TBC2024 และได้ยินมาว่า จะเปิดรับ อาสาสมัครมาช่วยงาน ตั้งแต่วันนั้นก็คิดมาตลอดว่าอยากจะช่วยงานแต่ไม่รู้จะช่วยอะไรดี อย่างน้อยก็ช่วยทำในสิ่งที่ช่วยได้แล้วให้คนที่เราไปแทนได้ไปทำหน้าที่ที่ดีกว่า ก็ถือว่าเป็นการสนับสนุนส่วนหนึ่ง ก็ยังดี เพราะภาพจากปีที่แล้วมันลอยเข้ามา เราเองก็มางานคนเดียวไม่รู้จักใครเลย ได้เห็นพี่นิวและคุณนิ่ม ที่อยู่ร้านขายเสื้อแบบยุ่งมากๆ ถ้ามีคนมาช่วยเพิ่มก็คงดี พอดีเลยที่ทีมงานจับเราลงตำแหน่งนี้ จึงมีโอกาสได้มาช่วยงาน และรู้สึกเป็นเกียรติที่ได้ร่วมงานครับ
ขอบคุณทุกคนที่ได้มาเจอกันในงาน ผมอาจจะไม่ได้พูดถึงทุกคนแต่ แค่มองตากันก็เข้าใจแล้ว เจอกันเยอะมากๆ ถ้าใครได้ผ่านร้านขายเสื้อก็จะเจอผมอยู่ตรงนั้น มีเพื่อนๆแวะเวียนมาทักทาย พูดคุย มาป่วน 😄😄
ประโยคที่ส่วนมากจะได้ยินเวลาผมทักทายไม่ใช่ว่าชื่ออะไรนะ ผมจะถามว่า กินข้าวยัง กินอะไรหรือยัง มันอาจจะเป็นคำง่ายๆ แต่มันแฝงไปด้วยความห่วงใยกัน บางคนเห็นไกลๆได้แต่สบตาแล้ว พยักหน้าให้กัน เหมือนทุกคนในงานเป็นเพื่อน เพื่อนที่พูดจาภาษาเดียวกัน
ไม่รู้จะบรรยายออกมายังไงมันรู้สึกดี อิ่มเอมไปหมด ได้แนะนำสินค้า ได้มองเห็นกลุ่มเพื่อนคุยกันสนุกสนาน มันเป็นบรรยากาศที่ดีเลยทีเดียว เอาเป็นว่าเป็นประสบการณ์ที่ดีมากๆ เมื่อเทียบกับปีที่แล้วเลยแหละครับ
ขอบคุณ อ.ตั๊ม แม่โบว์ npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5
ที่ให้โอกาสได้ร่วมงาน
ขอบคุณเฮียโต้ง สำหรับหนังสือและขนมแสนอร่อยที่เอามาให้เราได้จับจ่ายกัน ขอบคุณ เพื่อนทุกคนที่เข้ามาทักทายกัน ขอบคุณลูกพี่สมนึกหัวหน้าแก๊งค์ร้านเสื้อ พี่แองจี้ แฟนพี่สมนึก แฟนพี่ตั้ม และทีมงานน้องเอิ้น ที่ช่วยขายของ
รักทุกคน
#siamstr #siamstrog #nostr




-

@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53
I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous.
In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism.
On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important.
That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played.
Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end.
The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism:
I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.
In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore.
The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true.
The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good.
In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.”
I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
-

@ ee11a5df:b76c4e49
2024-09-11 08:16:37
# Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays.
Or at the very least by DVMs. I concur. In this way, once you configure what you want to see,
it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
## Strategies in Short
1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering.
3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity
6. **PROOF OF WORK**: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
## filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai
// This is a sample spam filtering script for the gossip nostr
// client. The language is called Rhai, details are at:
// https://rhai.rs/book/
//
// For gossip to find your spam filtering script, put it in
// your gossip profile directory. See
// https://docs.rs/dirs/latest/dirs/fn.data_dir.html
// to find the base directory. A subdirectory "gossip" is your
// gossip data directory which for most people is their profile
// directory too. (Note: if you use a GOSSIP_PROFILE, you'll
// need to put it one directory deeper into that profile
// directory).
//
// This filter is used to filter out and refuse to process
// incoming events as they flow in from relays, and also to
// filter which events get/ displayed in certain circumstances.
// It is only run on feed-displayable event kinds, and only by
// authors you are not following. In case of error, nothing is
// filtered.
//
// You must define a function called 'filter' which returns one
// of these constant values:
// DENY (the event is filtered out)
// ALLOW (the event is allowed through)
// MUTE (the event is filtered out, and the author is
// automatically muted)
//
// Your script will be provided the following global variables:
// 'caller' - a string that is one of "Process",
// "Thread", "Inbox" or "Global" indicating
// which part of the code is running your
// script
// 'content' - the event content as a string
// 'id' - the event ID, as a hex string
// 'kind' - the event kind as an integer
// 'muted' - if the author is in your mute list
// 'name' - if we have it, the name of the author
// (or your petname), else an empty string
// 'nip05valid' - whether nip05 is valid for the author,
// as a boolean
// 'pow' - the Proof of Work on the event
// 'pubkey' - the event author public key, as a hex
// string
// 'seconds_known' - the number of seconds that the author
// of the event has been known to gossip
// 'spamsafe' - true only if the event came in from a
// relay marked as SpamSafe during Process
// (even if the global setting for SpamSafe
// is off)
fn filter() {
// Show spam on global
// (global events are ephemeral; these won't grow the
// database)
if caller=="Global" {
return ALLOW;
}
// Block ReplyGuy
if name.contains("ReplyGuy") || name.contains("ReplyGal") {
return DENY;
}
// Block known DM spam
// (giftwraps are unwrapped before the content is passed to
// this script)
if content.to_lower().contains(
"Mr. Gift and Mrs. Wrap under the tree, KISSING!"
) {
return DENY;
}
// Reject events from new pubkeys, unless they have a high
// PoW or we somehow already have a nip05valid for them
//
// If this turns out to be a legit person, we will start
// hearing their events 2 seconds from now, so we will
// only miss their very first event.
if seconds_known <= 2 && pow < 25 && !nip05valid {
return DENY;
}
// Mute offensive people
if content.to_lower().contains(" kike") ||
content.to_lower().contains("kike ") ||
content.to_lower().contains(" nigger") ||
content.to_lower().contains("nigger ")
{
return MUTE;
}
// Reject events from muted people
//
// Gossip already does this internally, and since we are
// not Process, this is rather redundant. But this works
// as an example.
if muted {
return DENY;
}
// Accept if the PoW is large enough
if pow >= 25 {
return ALLOW;
}
// Accept if their NIP-05 is valid
if nip05valid {
return ALLOW;
}
// Accept if the event came through a spamsafe relay
if spamsafe {
return ALLOW;
}
// Reject the rest
DENY
}
```
-

@ bf95e1a4:ebdcc848
2024-09-11 06:31:05
This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good!
If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/>
# Intro
**Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us.
**Paolo:** Thank you for having us.
**Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we?
**Luke:** Sounds like that's the plan. So thank you again, both for joining us.
# Introducing Paolo and Mathias
**Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you
**Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate.
**Luke:** And, Mathias, over to you.
**Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use.
P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that.
And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here.
**Luke:** Oh, fantastic.
# Introduction to Holepunch
**Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch.
What is Holepunch and what are you doing?
**Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us.
but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy.
It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God.
that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks.
Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use,
Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it?
and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world.
And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company.
And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand.
anything, super exciting and, encourage everybody to try to check it out.
**Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product?
What is the easiest way that you would explain what it is?
# The Vision Behind Keet
**Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer
People don't care about technology. We loved it, but don't have that surface off too much to the user.
Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it.
It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard.
And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that.
# Keet vs Nostr
**Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here.
**Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform.
And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly.
You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users.
So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays.
and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology.
It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace.
Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly.
**Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that.
# Pear Runtime
**Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform,
**Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So
We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it.
And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications.
We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that.
So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve.
But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything.
So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view.
and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard.
so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example.
It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app.
So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place.
But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that.
And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone.
And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached.
Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like
**Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective.
And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that?
**Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective.
And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things.
I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point.
# Decentralization vs. Centralization
**Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor?
**Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias.
I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right?
Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions.
and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers.
That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there.
And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far.
Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features.
And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users.
And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is.
It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that.
And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key
**Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites.
But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept.
over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud.
And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers.
the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on.
is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole.
And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before.
Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize.
And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system.
And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country.
So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to.
**Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives.
So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right?
**Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all.
So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting.
yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why
# Challenges and Future of Decentralization
**Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company.
And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing.
So is there a limitation to how far this can go?
**Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world.
Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling.
So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house.
I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created.
imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you.
Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure.
So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another.
And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example.
**Knut:** Yeah.
**Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money.
And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook?
it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way.
And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it.
We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback.
# Bitcoin and Holepunch: Drawing Parallels
**Mathias:** I think, that's the main thing to think about in that. Discussion.
**Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line.
And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin?
**Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange.
For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government.
and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right?
Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them.
and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them.
**Luke:** Yeah, fantastic.
# The Future of Decentralized Communication
**Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet.
So is, that a goal? Is that on the roadmap?
**Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world.
But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind.
**Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly.
And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app.
And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly,
# Interoperability and User Experience
**Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong,
**Mathias:** Very, true.
**Luke:** you backups with the same 1224 words.
Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be
**Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it.
**Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life.
You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build.
Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible.
**Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems?
What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that?
**Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us.
The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity.
No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful.
**Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever.
but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera.
But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem.
And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it.
**Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options.
Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right?
you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion.
so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai.
So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that.
And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself.
And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center.
**Knut:** Yeah.
# The Role of Tether in the Crypto Ecosystem
**Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo?
And, what, made this thing happen? Can you give us the story here about Tether?
# Tether's Origin and Evolution
**Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014.
it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat.
That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000.
But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right?
International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin.
For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic.
# USDT's Impact on Emerging Markets
**Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries.
Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap.
So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time.
we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world.
At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right?
you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others.
And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT.
If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right?
So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U.
S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant.
# Bitcoin as a Savings Account
**Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend.
The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies.
we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining.
We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other.
I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math.
That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin.
**Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother.
**Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether.
So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right?
So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education.
**Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic.
I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke.
**Luke:** Always say the title, Knut. Always say the title.
**Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course.
**Paolo:** Oh, with pleasure, with great pleasure, with a nice, education.
**Luke:** Absolutely. Yep.
# Plan B Forum and Future Events
**Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year.
so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event.
**Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year.
I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world.
And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing.
**Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time.
And I think we're even playing this year, aren't we, Luke?
**Paolo:** You're
**Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos.
Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague?
**Knut:** paranoid and,
**Paolo:** Can I commission a
**Knut:** What song would you like to hear?
**Paolo:** I have two that I would suggest. One is Nothing Else Matters.
**Knut:** Alright.
**Paolo:** So I think that, is very inspiring, right?
**Knut:** Bitcoin, for sure.
Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke?
**Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference,
**Knut:** Yeah.
**Mathias:** not so much music, but yeah, that's peer to
**Knut:** Nothing else matters.
**Luke:** looking forward to that.
**Knut:** Sorry, brain fart. Sad but true is about the dollar still being around,
**Paolo:** Yeah, you can say that.
**Luke:** Okay.
# Final Thoughts and Closing Remarks
**Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that?
**Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms.
There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out.
**Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting.
**Mathias:** Just those things, that's all.
**Paolo:** Yeah, we can piss off more than this. Thanks.
**Mathias:** a
**Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners?
**Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them.
**Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good.
**Luke:** So that's, all at Keet. Is that correct? For Keet?
**Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer.
**Knut:** Alright,
**Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah.
**Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano.
**Paolo:** Likewise, I
**Knut:** But yeah, worth saying again.
**Paolo:** Thank you for having an invitation.
**Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
-

@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05
It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint.
I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point.
I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog.
In line with that thinking, I made two parlays this week:
1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense.
2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout.
Are there any odds you're excited about (doesn't have to be football)?
originally posted at https://stacker.news/items/679894
-

@ 09fbf8f3:fa3d60f0
2024-09-10 13:12:15
### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。
怎么自建ntfy,后面再写。
---
2024年08月13日更新:
> 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
---
### 准备工具
- Ntfy服务
- Google Script
- Google Sheets
### 操作步骤
1. 在Ntfy后台账号,设置访问令牌。
[](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌")
2. 添加订阅主题。
[](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题")
2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图:
[](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id")
3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript
function checkEmail() {
var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID
var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据
cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread');
Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) {
var threadId = thread.getId();
if (!sentEmails.includes(threadId)) {
thread.getMessages().forEach(sendNtfyNotification);
recordSentEmail(sheet, threadId);
}
});
}
function sendNtfyNotification(email) {
if (!email) {
Logger.log("Email object is undefined or null.");
return;
}
var message = `发件人: ${email.getFrom() || "未知发件人"}
主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail";
var options = {
method: "post",
payload: message,
headers: {
Authorization: "Bearer Ntfy的令牌"
},
muteHttpExceptions: true
};
try {
var response = UrlFetchApp.fetch(url, options);
Logger.log("Response: " + response.getContentText());
} catch (e) {
Logger.log("Error: " + e.message);
}
}
function getSentEmails(sheet) {
var data = sheet.getDataRange().getValues();
return data.map(row => row[0]); // Assuming email IDs are stored in the first column
}
function recordSentEmail(sheet, threadId) {
sheet.appendRow([threadId, new Date()]);
}
function cleanOldData(sheet, minutes) {
var now = new Date();
var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues();
var rowsToDelete = [];
data.forEach(function(row, index) {
var date = new Date(row[1]); // 假设日期保存在第二列
if (date < thresholdDate) {
rowsToDelete.push(index + 1); // 存储要删除的行号
}
});
// 逆序删除(从最后一行开始删除,以避免行号改变)
rowsToDelete.reverse().forEach(function(row) {
sheet.deleteRow(row);
});
}
```
4.Goole Script需要添加gmail服务,如图:
[](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务")
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:
[](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器")
[](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细")
### 结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
效果预览:
[](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览")
-

@ 6ad3e2a3:c90b7740
2024-09-10 09:26:37
While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions:
**1. Separate passengers from their bags as early as possible.**
The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences:
a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes.
b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day.
c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five.
d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier.
e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable.
The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children.
To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc.
There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.)
Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane.
**2. Eliminate Security Lines**
Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement.
a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use.
Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious.
b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side.
Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side.
**3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.**
Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal.
**4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.**
There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done.
Here are some other suggestions:
1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up.
2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges.
3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease.
4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them.
I can anticipate some objections to these ideas, and I’ll address each one in turn.
**1. This would cost too much money.**
My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.)
**2. It’s too much of a security risk.**
Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end.
Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle.
**3. I like free carry-ons because it saves me from waiting at the baggage claim.**
Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse.
The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist.
*\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.*
*\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.*
-

@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48
I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote:
*What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.*
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-

@ 129f5189:3a441803
2024-09-09 23:28:41
Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration.
Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed.
https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg
This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad.
https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg
Reorienting U.S. Foreign Policy: Proposals for a Conservative Future
In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage.
Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed.
https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg
History and Structure of the State Department
Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner).
The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries).
https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg
Political Leadership and Bureaucratic Support
To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner).
Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies.
https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg
Global Threats to the U.S.
The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea.
🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner).
Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner).
https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg
🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government.
"The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner).
https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg
🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people.
"The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner).
https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg
🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests.
"The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?"
https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg
One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner).
This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines.
Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner).
It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement.
https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg
A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner).
From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives.
https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg
Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO.
https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg
🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power.
"The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner).
https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg
Detailed Policy Proposals
Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized.
"The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner).
https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg
Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities.
She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner).
https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg
Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem.
"Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis.
https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg
Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada.
"The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region.
https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg
Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India.
"Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner).
https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg
Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities.
"Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying.
https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg
Relations with Europe and Asia
Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom.
https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg
Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner).
https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg
International Organizations
Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner).
She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner).
https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg
Conclusion
Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president.
With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom.
https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
-

@ 129f5189:3a441803
2024-09-09 23:23:45
Project 2025, outlined in the "Mandate for Leadership" document by the Heritage Foundation, is a crucial guide for the next Republican administration. Crafted by conservative intellectuals from major American think tanks, this plan promises to have significant influence on a potential Donald Trump administration, even if he does not formally acknowledge it as his government plan.
https://image.nostr.build/443d69c16dc32659be2353ce48d170d397e0ee682ffc3c4108df3047fd54472d.jpg
This document presents proposals to depoliticize government agencies, increase efficiency, and reduce costs, aiming to dismantle the Deep State and combat the Woke agenda associated with the Democratic Party.
https://image.nostr.build/06de3f0de3d48e086f47d0418d30e32cbfe0d88f452a93706987b7394458952d.jpg
Dissolution of the DHS and Redistribution of Functions
The Department of Homeland Security (DHS) was established in 2002 in response to the September 11 attacks, with the goal of consolidating various agencies responsible for domestic security under a single command. The DHS includes agencies such as FEMA, TSA, ICE, and CISA.
Project 2025's proposal to dissolve the DHS and redistribute its functions to other agencies aims to address excessive bureaucracy and a lack of cohesion, arguing that centralization has failed to effectively integrate its diverse missions.
https://image.nostr.build/ffca8d274914b725183b8fb19162c1b63f4d987c24e598f2eca88901d4a1a43c.jpg
Impact on the Democratic Deep State:
The dissolution of the DHS would pose a significant threat to the Democratic Deep State, as it would redistribute the power concentrated in a single entity across multiple other agencies, making it more difficult to politicize and centralize control over domestic security operations.
This decentralization would reduce the ability to use the DHS as a political tool against opponents.
https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg
Primary Recommendations
Combining Immigration Agencies:
Merge U.S. Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), U.S. Citizenship and Immigration Services (USCIS), the Office of Refugee Resettlement (ORR) of the Department of Health and Human Services (HHS), and the Executive Office for Immigration Review (EOIR) of the Department of Justice (DOJ) into a new autonomous border and immigration agency.
https://image.nostr.build/58eef4f2eca0ed2400261ec878c1dba2ca4bca519a16751b1fb7abd45da2906b.jpg
Privatization of the TSA:
Privatize the Transportation Security Administration (TSA), drawing inspiration from Canadian and European models, to reduce costs and improve service for travelers.
Division of the Secret Service (USSS):
The U.S. Secret Service (USSS), responsible for protecting national leaders and investigating financial crimes, would be divided.
The protective element would be transferred to the Department of Justice (DOJ), while the financial investigations element would be moved to the Department of the Treasury.
https://image.nostr.build/0a065cdbf158db4bc17b9aacd4af5a94029004caaa152eebf2c557042b08a641.jpg
Impact on the Democratic Deep State:
The division of the USSS would significantly weaken centralized control over protection and financial investigations, making it more difficult to use these functions for political purposes.
Transferring the protective element to the DOJ and the financial investigations element to the Treasury would complicate efforts for any group or party to manipulate these crucial government functions for partisan objectives.
https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg
Cybersecurity and Infrastructure Security Agency (CISA)
Established in 2018, CISA is a federal agency responsible for protecting the U.S. critical infrastructure from cyber threats.
CISA's mandate includes ensuring cybersecurity for sectors such as energy, transportation, and healthcare, and it collaborates with public and private entities to strengthen the country’s cyber resilience.
Criticisms and Restructuring Proposals:
Project 2025 strongly criticizes CISA for deviating from its original mission and being used as a political tool for censoring speech and influencing elections. The proposal is to transfer CISA to the Department of Transportation (DOT) and return the agency to its statutory focus.
https://image.nostr.build/8bfb4a45053de96a775f67e3e1b83a44d9a65fee4705e3b16d3359bd799b8af2.jpg
Review of Executive Order 12333
Executive Order 12333, issued in 1981, sets guidelines for U.S. intelligence activities, including the collection, analysis, and dissemination of information.
Project 2025 proposes a review of this order to ensure that intelligence agencies are not used for political purposes but are focused on protecting national security.
Objectives of the Review:
Prevent Abuse: Ensure that intelligence collection is conducted legally, without being used to target political opponents.
Ensure Impartiality: Reaffirm that intelligence operations must be conducted impartially, with a sole focus on the country's security.
https://image.nostr.build/90d31cb35a33048d311716df2fbc65c97bd4c1972977e266133654404393fca0.jpg
Reforms in Public Service
Facilitation of Public Employee Dismissal:
Project 2025 emphasizes the need to simplify the process for dismissing public employees who do not perform their duties impartially or who promote specific political agendas.
Performance Evaluations:
The document highlights the importance of merit-based compensation, stating that performance evaluations are only effective when tied to real consequences. Research indicates that 90% of major private companies in the U.S. use a merit-based pay system linked to evaluations. However, in the federal government, compensation remains largely based on seniority, despite efforts to adopt merit-based pay.
https://image.nostr.build/1b858fd7b2a23c3c65c0677d3e69c44976721bbdcbe7facf4682ba3371562cff.jpg
Inclusion of Employees Aligned with Conservative Values:
Aligned Hiring: Establish mechanisms to hire public employees who share conservative values, ensuring that the policies and practices of agencies are consistent with the principles endorsed by the administration.
https://image.nostr.build/ddbf5c59e7bb479998433991347f9d301dd117fbca0edb0f94e98fcac90b2974.jpg
Controversial Cases and Politicization:
Hunter Biden Laptop Case:
Project 2025 harshly criticizes the FBI and the Department of Justice, accusing them of acting in a biased and politically motivated manner. The authors suggest that the agency is intimidating parents who protest by labeling them as "domestic terrorists," while simultaneously suppressing politically unfavorable speech under the guise of combating "disinformation."
Furthermore, the critique highlights that the FBI is alleged to be neglecting violent attacks on pregnancy centers and violations of laws prohibiting attempts to intimidate Supreme Court justices.
The criticism intensifies with allegations that the FBI interfered in domestic elections and engaged in propaganda operations, specifically citing the purported Russian collusion conspiracy in 2016 and the suppression of the Hunter Biden laptop case in 2020, which is seen as a threat to the Republic.
https://image.nostr.build/e4f571a14102a939164465498bef514379ec0443e71a58e12f50c518e00570c6.jpg
Politicization of the FBI:
Election Interference: Russia Hoax and Trump, Suppression of Hunter Biden’s Laptop, and Big Tech Collusion.
Revelations about the FBI’s role in the 2016 "Russia Hoax" and the suppression of Hunter Biden’s laptop in 2020 suggest that the agency may have strayed from its impartial duties.
These actions indicate concerning politicization, where the agency appears to have been used to influence the political landscape in favor of certain interests. This includes collaboration between the FBI and Big Tech companies to control discourse.
https://image.nostr.build/5dcd45fcec939b782d29d8d2e3d3b45244c525b5dbd3240f1629a4632e390a86.jpg
Comprehensive Review of FBI Investigations:
It is crucial to conduct an immediate and thorough review of all significant investigations and activities within the FBI, terminating those that are illegal or contrary to national interests.
This step is essential for restoring public trust in the FBI. A public report on the findings of this review could enhance transparency and confidence.
https://image.nostr.build/df98e2c6aff123d806187eab13d24a3ebb30a87df1f44cf57be97dc5624fff88.jpg
Structural Reorganization:
Align the FBI within the Department of Justice (DOJ) according to its purposes of national security and law enforcement.
The agency should be under the supervision of the Assistant Attorney General for the Criminal Division and the National Security Division, ensuring that the FBI does not operate as an independent entity but is instead subordinated to the DOJ’s directives.
https://image.nostr.build/0d1c0015c6b67a8afc2dd1595357ea571fcd5a9d83829065f49f9b60cf553eb0.jpg
Prohibition on Policing Speech:
Prohibit the FBI from engaging in activities related to combating "disinformation" or "misinformation" disseminated by Americans who are not linked to plausible criminal activities.
The Constitution, through the First Amendment, prohibits the government from policing speech, ensuring a healthy public debate without governmental intervention.
All these measures represent a significant attack on the "Deep State" within American institutions. These public policies have been considered a dictatorial threat by many sectors of the American press.
However, the real issue should be the politicization of unelected bureaucrats by a political faction.
https://image.nostr.build/9a44b19d15d53314f89528c1d89e2f637030ea18d8907a6a8c4e27d07064b8ec.jpg
Combating Woke Culture in the Intelligence Community
Future leadership of the Intelligence Community (IC) needs to implement a plan to replace the "woke" culture and identity politics that have spread throughout the federal government.
The goal is to restore traditional American values such as patriotism, racial impartiality, and job competence, which have been replaced by advocacy for "social justice" and identity politics.
https://image.nostr.build/7929dca5e36273c8e751f36d6ca6229f362e30792bce735f10be7e5d8581af5f.jpg
Final Considerations
The Heritage Foundation’s Project 2025 is not merely an administrative reform plan; it is a manifesto of resistance against the Washington status quo. The proposals aim to dismantle established power structures, eliminate politicization, and combat the Woke agenda. If implemented, this plan would profoundly impact how the U.S. government operates, promoting a more efficient, limited government aligned with conservative principles.
Threat to the Democratic Deep State:
A potential new administration under Donald Trump represents an existential threat to the Democratic Deep State entrenched in American institutions.
The dissolution of the DHS, depoliticization of intelligence agencies, division of the Secret Service, review of Executive Order 12333, privatization of the TSA, and the hiring of employees aligned with conservative values are all measures that would significantly weaken centralized control and the ability to use these institutions for political purposes.
By dismantling concentrated power and promoting a more transparent and accountable government, Project 2025 aims to restore public trust and ensure that government agencies serve national interests rather than partisan ones.
Of course, not all aspects of the plan may be implemented, but the prospect of several of these measures being enacted should be a cause for concern for the Democratic Deep State.
-

@ 129f5189:3a441803
2024-09-09 23:18:44
Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario.
The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy.
After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America.
Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million.
China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions...
https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg
For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions.
In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border.
A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention.
https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg
In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere.
The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years.
https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg
The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021.
In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government.
https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg
Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues.
In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities."
https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg
The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024.
Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction.
In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government.
https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg
Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University.
"The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times.
General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country.
"We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time.
In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade."
https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg
In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues."
Under the previous administration, China had received preferential treatment.
In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan.
The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security.
No public records show that the project has progressed since then.
https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg
Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark.
"Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement.
"Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face."
https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg
The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era.
Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel."
https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg
Access to space plays a crucial role in the CCP's strategic objectives.
Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China.
According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice.
According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access.
China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely.
The big question is: what could this facility do in times of war?
https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg
Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit.
The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface.
Additionally, it offers strategic advantages for any government involved in espionage.
https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg
Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner.
However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives.
Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023.
https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg
-

@ 129f5189:3a441803
2024-09-09 23:11:19
Precious metals have served as monetary backing for millennia, but this does not guarantee that gold is a safe investment or a good hedge against economic crises and monetary collapses. Since its last major rally in the 1980s, gold has been progressively demonetized.
Those who acquired gold in the late 1980s will need to rely on a significant increase in demand or a supply shock for its price to rise by 561% and regain the purchasing power it had 40 years ago.
https://image.nostr.build/dd5fec2b474ea34cd72ddf5781393b528e63a358d523c9428f3ba4649f4f42aa.jpg
If you look at the purchasing power of $1 (green line), you'll see that the depreciation is even faster. This might create the impression that gold is a good store of value. But does the fact that something loses value more slowly amidst a general decline really make it a store of value?
Unless the total demand for gold increases at the same rate as its supply has grown in recent years, the purchasing power of the metal is likely to decline.
https://image.nostr.build/9f24f6cf37780fe851746057520064ed94acd96547be53bd341c9e15b8762773.jpg
In other words, if you own an ounce of gold, that ounce will represent an increasingly smaller fraction of the total gold reserves, meaning you are being diluted. Additionally, one should also consider the cost and risk of storage, but that's another issue.
If you don't want to compare the purchasing power of gold today with the 1980s, you can consider its value from 9 years ago. Between September 2011 and November 2015, the Fed printed approximately $2.8 trillion. This also provides a perspective on gold's depreciation relative to the significant monetary expansion during that period.
https://image.nostr.build/822e0a861e16ca258e0427875a84b5c8e5420e51bcf65674b453b55ed78edefd.jpg
In other words, the Fed expanded its monetary base by about 30% during that 4-year period. However, the price of an ounce of gold fell by 45% (from $1,900 to $1,057) over the same interval. A true store of value should protect against excessive money printing. In contrast, during that same period, Bitcoin appreciated by 8,500% (from $5 to $419).
https://image.nostr.build/32a7ca39a6e69e2780f9ab49390c7b7380499fcfe54ae4ef693e6fc91686a41e.jpg
Indeed, while it is interesting to note that this was the exact period when gold derivatives were launched on CME Group, it's important to remember that correlation does not imply causation. Many factors can influence the price of gold and Bitcoin, and establishing a direct causal relationship requires more detailed analysis.
https://derivsource.com/2011/06/21/cme-group-announces-the-launch-of-three-new-short-term-gold-crude-oil-and-natural-gas-options-contracts/
In an asset where supply can only be physically verified, flooding the market with gold contracts could lead to significant issues. This might result in market manipulation, legal liabilities, fines, and potentially even imprisonment for those involved. Such actions can undermine the integrity of the market and lead to regulatory and legal consequences.
https://www.cnbc.com/2018/11/06/ex-jp-morgan-trader-pleads-guilty-to-manipulating-metals-markets.html
Over longer periods, gold has not functioned as a true "store of value" relative to the dollar for quite some time, despite recently returning to its price from 9 years ago. This suggests that, while gold may have periods of price recovery, it has struggled to maintain its value over extended horizons compared to fiat currencies.
It's worth noting that before 1980, aluminum was valued higher than gold. This reflects how market dynamics and technological advancements can significantly impact the value of commodities over time.
https://www.mgsrefining.com/blog/why-aluminum-is-no-longer-a-precious-metal/
While gold has been undergoing a gradual demonetization process since 1980, another asset appears to be experiencing the opposite—hyper-monetization. (See in red; don't be alarmed.)
https://image.nostr.build/435a5369f778a7be727b50e4c6328cfc353240bf804e1ed69313b9a8e1233f7e.jpg
With the advent of Bitcoin, you believe that gold will continue on the same path as silver since the end of the bimetallic standard in 1853: a prolonged process of demonetization, with increasing volatility and reduced liquidity.
https://image.nostr.build/5b9c8bfdb09e51d639e380df160c98beb9ee1d917ea13d28ef67711cfa5f8086.jpg
Since 1913, the dollar has lost 97% of its purchasing power. Over the same period, the gold supply has increased significantly. Since 1980, gold has lost about 82% of its purchasing power. Given that the dollar is used as the unit of account and gold's liquidity is measured in dollars, these changes reflect the complex interaction between the currency and the precious metal.
The U.S. is by far the country with the largest gold reserves in the world and is also the fourth-largest miner of the metal. Additionally, the country controls and issues the currency that serves as the unit of account for gold and has the highest liquidity in global trade.
Is gold easy to transport? Is it simple to verify its supply and authenticity? Is it practical to store? Is its industrial utility significant? Can it be disrupted? And what about the continuous increase in its supply? These are important questions to consider.
In my humble opinion, it will not be the dollar or fiat currencies that will suffer the most from the existence of Bitcoin, but rather the market cap of gold.
https://image.nostr.build/61dddefabc4b69f784631a3294bdd978e3411bba40fb52d585e13b48002389fe.jpg
-

@ e83b66a8:b0526c2b
2024-09-09 20:30:30
We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect.
Therefore, I strongly advise you to run multiple clients.
On iPhone, I run:
Damus: https://nostrapps.com/damus
Primal: https://primal.net/downloads
Nostur: https://nostrapps.com/nostur
On Android I run:
Primal: https://primal.net/downloads
Amethyst: https://nostrapps.com/amethyst
On desktop I run:
Primal: https://primal.net/downloads
noStrudel: https://nostrapps.com/nostrudel
Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay.
If you haven’t taken the plunge to run a node, now might be a good time to think about it.
There are many, many options for clients, the “Social” section of
https://nostrapps.com/
lists 23 currently.
Play with them, see what they do, if you’re a developer, you could even consider building or forking your own.
Have fun and realise we are building freedom tech, not just running it.
-

@ e83b66a8:b0526c2b
2024-09-09 20:27:41
First,
Key management.
When you “created” your NOSTR account, what you actually created was a cryptographic key pair.
This consists of a private key, which starts “nsec” and a public key which starts with “npub”.
As the names suggest, your “nsec” key is private and you should never reveal it to anyone.
Your “npub” key is your public key, feel free to share that everywhere.
Your “npub” key is used by others to verify your identity, through the signature added to your messages.
It is also used by others to encrypt private messages to you.
We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary.
For the moment, consider using software key management options, some of which are listed under “signers” here:
https://nostrapps.com/
N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted:
Secondly,
Lightning wallets.
It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile
N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key.
You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet.
Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason….
It also allows you to send small micropayments to posts or people you like.
Thirdly,
Paid Services
As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability.
I, for example choose to pay for the following services:
https://nostr.wine/ - 120,000 Sats for 2 years relay
https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month
https://nostr.build/ - Media storage - 69,000 Sats for 1 year
Total: 22,750 Sats per month
Approx $15 per month
This is not strictly necessary, but I decided to support the various developers behind these projects.
Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward.
-

@ d3052ca3:d84a170e
2024-09-09 15:43:38
I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :)
I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet.
What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds?
What is your experience? I'd love to hear about it!
-

@ 3875a16c:988456c9
2024-09-09 14:45:55
**ORIGINAL PANEL TITLE:**
MAKING BITCOIN MORE PRIVATE WITH CISA
**SPEAKERS:**
NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP
**CONFERENCE:**
BITCOIN NASHVILLE 2024
**ORIGINALLY PUBLISHED ON:**
BITLYRICS.CO
## Introduction
This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/).
Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development.
---
### NiftyNei (Moderator):
Hey everyone, my name is Nifty, and I’m going to be moderating this panel today.
We’re here to talk about CISA (cross-input signature aggregation).
Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage.
We’re excited to be talking to you guys about this.
I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA.
Craig, do you want to start?
---
### Craig Raw (Sparrow Wallet):
I built Sparrow Wallet. It’s a security and privacy-focused wallet.
The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen.
When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically.
So, that was the first time I really started to look at it from the privacy angle.
---
### Fabian Jahr (Brink):
I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it.
Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core.
Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months.
I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller.
I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it.
---
### Jameson Lopp (Casa):
I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups.
I think the first time I heard about CISA was in an Andrew Poelstra talk.
I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted.
This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics.
---
### NiftyNei (Moderator):
That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for.
Does anyone have a good explanation of how it works?
---
### Fabian Jahr (Brink):
I can start off.
So, it’s really already all in the name: cross-input signature aggregation.
If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated.
What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction.
So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before.
Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea.
---
### NiftyNei (Moderator):
I have a quick question about that.
So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right?
So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature.
Is that a good summary of what you’re explaining?
---
### Fabian Jahr (Brink):
Yeah, I would say so.
---
### Craig Raw (Sparrow Wallet):
So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it.
That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one.
Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it.
Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones.
Unfortunately, the downside of that is that you have to do the interaction while you sign.
The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing.
As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient.
---
### NiftyNei (Moderator):
Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right?
You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level?
---
### Jameson Lopp (Casa):
Well, there’s also full-block aggregation, right?
This is going really far down the rabbit hole, and I think it’s not even something that’s on the table.
There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations.
My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized.
If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again.
---
### NiftyNei (Moderator):
So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation.
We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there.
One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right?
Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated.
---
### Jameson Lopp (Casa):
Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically.
If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount.
It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO.
You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet.
It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot.
It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before.
So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so.
---
### Fabian Jahr (Brink):
And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy.
The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property.
Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.”
Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it.
Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature.
---
### Jameson Lopp (Casa):
Yeah, we have to think about the incentives, right?
I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are.
But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late.
We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so.
It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software.
Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money?
---
### Craig Raw (Sparrow):
So you might be wondering at this stage what the savings actually look like.
It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block.
You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage.
Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%.
But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space.
So that’s how I would encourage you to think about it from the start.
For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride.
We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about.
---
### NiftyNei (Moderator):
I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy.
I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal?
What was it about the Taproot process where this proposal didn’t make it over the line?
---
### Fabian Jahr (Brink):
I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed.
From what I can see, I don’t think there was any direct opposition.
The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller.
I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding.
I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much.
---
### Craig Raw (Sparrow):
Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough.
There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.”
That’s an interesting point of view.
---
### Jameson Lopp (Casa):
It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet.
---
### Craig Raw (Sparrow):
Yeah, so we’re in a very different space now.
Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine.
I’m talking about the well-understood half-signature aggregation form of it.
From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that.
So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing.
If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down.
So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line.
---
### Jameson Lopp (Casa):
I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin.
With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process.
As far as I’m aware, there’s been limited adoption of Schnorr so far.
I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility.
I care about this a lot, operating a multi-signature self-custody wallet.
We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature.
That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out.
So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block.
---
### NiftyNei (Moderator):
So, we only have a few minutes left.
Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in.
---
### Fabian Jahr (Brink):
There are still quite a few things to hammer out in terms of all the details, like defining a spec.
For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open.
However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity.
We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now.
---
### Jameson Lopp (Casa):
Yeah, call your local developer and demand signature aggregation today.
---
### Craig Raw (Sparrow):
Fabian has developed a great site where you can learn more.
If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it.
It’s very easy to read, not overly technical, and I think it gives a good grounding in these things.
Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not.
As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now.
So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not.
---
### Jameson Lopp (Casa):
I don’t know, do you want to save money? It should be an easy question.
---
### Fabian Jahr (Brink):
And have better privacy.
---
### NiftyNei (Moderator):
Great! Thanks y’all.
---
**Follow the speakers: **
[NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr)
**Watch the original content: **
[Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107)
**Also read: Build It Right: **
[Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/)
**Disclaimer: **
Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/).
-

@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24
## Chef's notes
Makes an excellent Chicken sandwich.
## Details
- ⏲️ Prep time: 6 Ish hours
- 🍳 Cook time: 40 min
- 🍽️ Servings: 1 loaf
## Ingredients
- 3 ½ - 4 cups bread flour, or more as needed
- 1 ⅓ cups warm milk (110°F – 115°F)
- 5 tablespoons honey
- 4 tablespoons salted butter, melted and slightly cooled
- 1 tablespoon instant “rapid rise” yeast
- 1 ½ teaspoons salt
- Oil or butter for greasing the bowl
- 1 tablespoon melted salted butter, for brushing the crust at the end
## Directions
1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl.
2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes.
3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours.
4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan.
5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F.
6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped.
7. Brush the top of the warm bread with melted butter.
8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
-

@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05
Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one?
Thanks
originally posted at https://stacker.news/items/677439
-

@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43
> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。
导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。
---
### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。
项目是通过cloudflare pages搭建的。
- 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed
项目的教程很详细,具体去看项目教程。
### telegram设置:
- 需要有telegram账号
- 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。
- 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。
- 一定要添加创建的机器人到频道作为管理员才能使用。
### cloudflare的设置
- 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。
- 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图:
[](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv")
- BASIC_USER 后台登陆名
- BASIC_PASS 后台密码
- AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。
### 其他
- 成人内容屏蔽
- pico 使用api接口
去项目地址看
### 最后
我搭建的地址:
https://imgbed.lepidus.me
-

@ c6f7077f:ad5d48fd
2024-09-08 01:24:03
***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further.
#### ***Consider the Most Fundamental Questions***
1. **The Origin of the Universe**
2. **The Origin of Life on Earth**
#### ***The Origin of the Universe***
You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**.
#### ***The Origin of Life on Earth***
The origin of life is even more complex. Life requires three essential components:
- **Proteins** for basic functioning
- **RNA** for storing and replicating genes
- **Lipids** (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**.
#### ***The Question of Certainty***
If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early.
#### ***Reclaiming Control of Science and Education***
The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend:
- **“A Brief History of Time”** by **Stephen Hawking** for physics
- **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-

@ 655a7cf1:d0510794
2024-09-06 23:45:52
I can't stop thinking about it. When I go to clear out a cave in Skyrim I always find the troll the spider some version of some enemy with gold.
I ask myself how did they get this gold.? Is there someone in the cities that goes to and fro to have commerce with underworld. If so what would this market look like. Would it be trade based or commodity based. Sometimes in these caves I can find upwards of 100 gold I can also find individuals with upwards of 20 gold on them. Assuming they live paycheck to paycheck this is a moderate size of money they're carrying around from week to week. It tells me that the trade is doing well. Am I completely psychotic for constantly thinking about this? Does anybody else thought about this or done any research or have any links that I can find?
originally posted at https://stacker.news/items/673609
-

@ 8cb60e21:5f2deaea
2024-09-06 22:28:24
JavaScript For Cats
An introduction for new programmers cat
So easy your human companion could do it too!
JavaScript is a programming language or, in other words, a means by which a computer is instructed to do things. Just the same as one controls humans with hisses and meows, one controls computers with statements written in a programming language. All web browsers understand JavaScript and you can take advantage of that to make web pages do crazy things!
JavaScript started as a way to make web pages more interactive. Nowadays JavaScript runs in more places than just web browsers — it runs on web servers, phones and even robots! This page will teach you some JavaScript basics so that you can get up and running in no time*.
* Actual time: more than none. Probably an hour or two. Also since you are a cat you are less likely to run and more likely to lay around in the sun
Table of contents
The console
Strings
Values and variables
Using functions
Built in JS functions
Download new JS functions
Writing new functions
Loops
Arrays
Objects
Callbacks
Recommended reading
Don't be a scaredy-cat
cat
You will always land on your feet — even when programming! Unlike pawing over a glass of water on your laptop, nothing in these tutorials will damage your computer in any way, even if you mistype a command or click the wrong button. Like cats, computer programmers make mistakes all time: misspelling things, forgetting quotes or brackets, and being forgetful of how basic functions (and yarn, lasers) work. Programmers care more about making it work eventually rather than trying to make it work the very first time. The best way to learn is by making mistakes!
So don't be a scaredy-cat! The absolute worst thing that will happen is that you might have to refresh this page in your web browser if you get stuck. Don't worry though, this will happen very rarely.
# The basics
There is JavaScript running on this page right now. Let's play around with it a little. For the sake of simplicity I'll assume you are using Google Chrome to read this page (if you aren't it's probably easier on both of us if you follow along with Chrome).
First, right click anywhere on the screen and hit Inspect Element, then click on the Console tab. You should see a thingy that looks like this:
console
This is a console, otherwise known as a "command line" or "terminal". Basically it's a way to type one thing at a time into a computer and immediately get the computers answer back. They are super useful as a learning tool (I still use the console nearly every day that I'm coding).
The console does some pretty cool stuff. Here I have started to type something and the console is helping me out by giving me a list of all the possible things I could continue to type! Another thing you could do is type 1 + 1 into the console and then hit the Enter key and watch what happens.
Using the console is a very important part of learning JavaScript. If you don't know if something works or what the command is for something, go to the console and figure it out! Here's an example:
# Strings
Since I am a cat I want to replace every instance of the word dog on the Internet with those blasted dogs. First go into your console and type in a few sentences that contain the word dog at least once. In JavaScript a bunch of letters, numbers, words or anything else is known as a String (as in a string of characters). Strings have to begin AND end with a quotation mark. Single ' or double " is fine, just make sure you use the same at the beginning as you do at the end.
console
See the nasty error message? Don't worry - you didn't break any laws. SyntaxError ILLEGAL is just the way it sounds when robots tell you that your program has a problem. The first two sentences had matching quotation marks at the beginning and end, but when I mixed single and double quotation marks it freaked out on me.
OK, to fix up one of these sentences (by replacing dog with our enhanced version) we have to first save the original sentence so that we can call it up later when we do our replacing magic. Notice how the string gets repeated in red when we type it into the console? This is because we haven't told it to save the sentence anywhere so it just gives it right back (or it gives us an Error back if we messed something up).
# Values and variables
Values are the simplest components in JavaScript. 1 is a value, true is a value, "hello" is a value, function() {} is a value, the list goes on! There are a handful of different types of values in JavaScript but we don't need to go over them all right away — you will learn them naturally the more you code!
To store values we use things called variables. The word 'variable' means 'can change' and is used because variables can store many different types of values and can change their value many times. They are pretty much like mailboxes. We put something in a variable, like our sentence, and then give the variable an address that we can use to look up the sentence later. In real life mailboxes have to have PO Box numbers but in JavaScript you usually just use lowercase letters or numbers without any spaces.
console
var is shorthand for variable and the = means store the thing on the right-hand side in the thing on the left-hand side. Also as you can see, now that we are storing our sentence in a variable the console doesn't just return our sentence right away, but instead gives us undefined which means there was nothing to return.
If you simply type a variable name into the console it will print out the value stored in that variable. A note about variables is that by default they go away when you switch to a different page. If I were to hit the Refresh button in Chrome, for example, my dogSentence variable would get wiped and it would be like it never existed. But don't worry about this too much for now — you can just hit the up or down arrows on your keyboard while in the console to go through everything you've entered in recently.
# Functions
Now that we have our sentence stored in a variable, let's change a word stored in it! We can do this by performing a function. Functions are a type of value that, well, serve a specific function (AKA purpose or action) for us. Calling them "actions" sounded weird I guess so they went with the word "function" instead.
JavaScript has a function called replace that does exactly what we want! Functions take in any number of values in their parentheses (zero, one or many) and return either nothing (undefined) or the changed string. The replace function is available to use on any strings and takes in two values: the characters to take out and the characters to swap in. It gets confusing to describe these things so here is a visual example:
console
Notice how the value of dogSentence is the same even after we run replace on it? This is because the replace function, (and most JavaScript functions for that matter) takes the value we give it and returns a new value, without modifying the value we passed in. Since we didn't store the result (there is no = on the left side of the replace function) it just printed out the return value in our console.
# The "standard library"
You might be wondering what other functions are available in JavaScript. The answer: A TON. There are lots built in, standard libraries that you can learn about at MDN (A site run by Mozilla that has lotsa nifty information about web technologies). For example here is the MDN page on JavaScript's Math object.
# Third-party JavaScript
There is also a lot of JavaScript code available that is not built in. JavaScript from third parties is usually referred to as a "library" or "plugin". One of my favorites is called Underscore.js. Let's go and grab it and load it into our page! First go to the Underscore site, http://underscorejs.org/, click on the download link (I usually use development versions because they are easier to read but both will give you the same basic functionality), and then copy all the code onto your clipboard (you can use Select All from the Edit menu to select everything). Then paste it into your console and hit enter. Now your browser has a new variable in it: _. Underscore gives you a ton of helpful functions to play with. We'll learn more about how to use them later.
console
# Making new functions
You aren't limited to using other peoples functions — you can also write them yourself. It's pretty easy! Let's make a function called makeMoreExciting that adds a bunch of exclamation points to the end of a string.
function makeMoreExciting(string) {
return string + '!!!!'
}
In my head I read it out loud like this: "there's a function called 'make more exciting' that takes in a string and returns a new copy of that string that has a bunch of exclamation points at the end". Here is how we would write this in the console manually if we weren't using a function:
console
The expression string + '!!!!' returns a new string and our variable called string stays the same as before (since we never updated it to anything else with =).
Let's use our function instead of doing it manually. First, paste the function into the console and then call the function by passing in a string:
console
You could also call the same function by passing in a variable that points to a string (in the above example we just typed the string straight in there as a value instead of saving it to a variable first):
console
The line makeMoreExciting(sentence) is equivalent to saying sentence + '!!!!'. What if we wanted to modify in-place (aka update) the value of sentence? Simply save the return value of the function back into our sentence variable:
var sentence = "time for a nap"
sentence = makeMoreExciting(sentence)
Now sentence will have the exclamation marks in it! Note that you only have to use var when you are initializing a variable — the first time you ever use it. After that you shouldn't use var unless you want to re-initialize (reset/clear/empty) the variable.
What would happen if we took out the return statement in our function?
console
Why is sentence empty? Because functions return undefined by default! You can choose to return a value by returning something. Functions should take in a value and, if they change the value or create a new value that is supposed to be used later, return a value (fun fact: a fancy term for this style is functional programming). Here is another function that doesn't return anything but instead uses a different method to show us the output:
function yellIt(string) {
string = string.toUpperCase()
string = makeMoreExciting(string)
console.log(string)
}
This function, yellIt, uses our previous function makeMoreExciting as well as the built-in String method toUpperCase. Methods are just a name for a function when it belongs to something — in this case toUpperCase is a function that belongs to String so we can refer to it as either a method or a function. makeMoreExciting on the other hand doesn't belong to anyone so it would be technically incorrect to refer to it as a method (confusing, I know).
The last line of the function is another built-in that simply takes in any values that you give it and prints them out into the console.
console
So is there something wrong with the above yellIt function? It depends! Here are the two major types of functions:
functions that modify or create values and return them
functions take in values and perform some action that cannot be returned
console.log is an example of the second type of function: it prints things out to your console — an action that you can see with your eyes but that cannot be represented as a JavaScript value. My own rule of thumb is to try to keep the two types of functions separate from each other, so here's how I would rewrite the yellIt function:
function yellIt(string) {
string = string.toUpperCase()
return makeMoreExciting(string)
}
console.log(yellIt("i fear no human"))
This way yellIt becomes more generic, meaning it only does one or two simple little things and doesn't know anything about printing itself to a console — that part can always be programmed later, outside the function definition.
# Loops
Now that we have some basic skills under our belt (Author's note: do cats even wear belts?) we can start being lazy. What?! Yes, that's right: programming is about being lazy. Larry Wall, inventor of the Perl programming language, called laziness the most important virtue of a good programmer. If computers didn't exist you would have to do all sorts of tedious tasks by hand, but if you learn to program you can lay in the sun all day while a computer somewhere runs your programs for you. It is a glorious lifestyle filled with relaxation!
Loops are one of the most important ways to harness the power of a computer. Remember Underscore.js from earlier? Make sure you have it loaded in the page (remember: you can just hit the up arrow on your keyboard a few times and then hit Enter to load it in again if you need to) and try copy/pasting this into your console:
function logANumber(someNumber) {
console.log(someNumber)
}
_.times(10, logANumber)
This code uses the times method of Underscore which takes in 1 number and 1 function and then starts from 0 and for 10 steps counts up by 1, calling the function with the number each step of the way.
console
If we were to manually write out what times is doing in the above code it would look like this:
logANumber(0)
logANumber(1)
logANumber(2)
logANumber(3)
logANumber(4)
logANumber(5)
logANumber(6)
logANumber(7)
logANumber(8)
logANumber(9)
But cats refuse to do unnecessary manual work like this so we must always ask ourselves, "am I doing this in the laziest way possible?".
So why is this called looping? Think of it like this: If we were to write out a list of 10 numbers (from 0 to 9) using a JavaScript Array it would look like this:
var zeroThroughTen = [0, 1, 2, 3, 4, 5, 6, 7, 8, 9]
What times really does is visit each number and repeat a task: in the example above the task was to call the logANumber function with the current number. Repeating tasks in this way is referred to as looping over the Array.
# Arrays
I've mentioned these a few times but let's spend a minute learning about them. Imagine you need to keep track of all your buddies. Well, an Array will do just fine. Think of an Array like a sorted list that you can keep tons of stuff in.
This is how you make one:
var myCatFriends = ["bill", "tabby", "ceiling"]
Sweet! Now you have a list of your cat buddies.
Elements (that is what you call a single item in an array) that are stored within arrays start at 0 and count up from there. So myCatFriends[0] returns bill and myCatFriends[1] returns tabby... etc etc.
To get buddies out of your brand new Array you can just access an element directly like so:
console.log(myCatFriends[0])
console
If you made a brand new cat friend at the hippest cat club the other night and you want to add them to your list it is super simple: myCatFriends.push("super hip cat").
To check that the new cat made it into your array you can use .length:
console
Notice how push returned the length? Handy! Also take note that arrays will always preserve ordering which means they will remember the order in which you added or defined things. Not everything in JavaScript preserves ordering so remember this special property of Arrays!
# Objects
Arrays are good for lists, but for other tasks they can be hard to work with. Consider our array of cat friends. What if you also wanted to store more than just names?
var myCatFriends = ["bill", "tabby", "ceiling"]
var lastNames = ["the cat", "cat", "cat"]
var addresses = ["The Alley", "Grandmas House", "Attic"]
Sometimes it is nice to have all of the addresses or names in one variable. But sometimes you have a cat in mind, let's say Bill, and you just want to look up that cat's address. With arrays it takes a lot of work because you can't just say 'hey array, give me Bill's address' because 'Bill' is in one array and his address is in a totally different array.
console
This can be brittle because if our arrays change and we add a new cat to the beginning we would have to also update our billsPosition variable to point to the new location of Bill's information in the arrays! Here is a easier to maintain way to store information like this using objects:
var firstCat = { name: "bill", lastName: "the cat", address: "The Alley" }
var secondCat = { name: "tabby", lastName: "cat", address: "Grandmas House" }
var thirdCat = { name: "ceiling", lastName: "cat", address: "Attic" }
Why would we do it this way? Because now we have a variable for each cat that we can use to get that cats values in a more convenient and readable way.
console
You can think of Objects like keys on a keyring. Each one is for a specific door and if you have nice labels on your keys you can open doors very fast. In fact, the things on the left hand side of the : are called keys (are also known as properties) and the things on the right hand side are values.
// an object with a single key 'name' and single value 'bill'
{ name: 'bill' }
So why would you ever use arrays if you can just put your data in objects? Because objects don't remember the order of the keys that you set. You might enter in an object like this:
{ date: "10/20/2012", diary: "slept a bit today", name: "Charles" }
But the computer could give it back to you like this:
{ diary: "slept a bit today", name: "Charles", date: "10/20/2012" }
Or like this!
{ name: "Charles", diary: "slept a bit today", date: "10/20/2012" }
So you can't ever trust the order of keys in objects. If you wanna get REALLY fancy you can make an array filled with objects, or an object filled with arrays!
var moodLog = [
{
date: "10/20/2012",
mood: "catnipped"
},
{
date: "10/21/2012",
mood: "nonplussed"
},
{
date: "10/22/2012",
mood: "purring"
}
]
// ordered from least to most favorite
var favorites = {
treats: ["bird sighting", "belly rub", "catnip"],
napSpots: ["couch", "planter box", "human face"]
}
When you combine different things like this you are making data structures, just like legos!
# Callbacks
Callbacks aren't really a feature of JavaScript like Object or Array, but instead just a certain way to use functions. To understand why callbacks are useful you first have to learn about asynchronous (often shortened to async) programming. Asynchronous code by definition is code written in a way that is not synchronous. Synchronous code is easy to understand and write. Here is an example to illustrate:
var photo = download('http://foo-chan.com/images/sp.jpg')
uploadPhotoTweet(photo, '@maxogden')
This synchronous pseudo-code downloads an adorable cat photo and then uploads the photo to twitter and tweets the photo at @maxogden. Pretty straightforward!
(Author's note: I @maxogden do happily accept random cat photo tweets)
This code is synchronous because in order for photo to get uploaded to the tweet, the photo download must be completed. This means that line 2 cannot run until the task on line 1 is totally finished. If we were to actually implement this pseudo-code we would want to make sure that download 'blocked' execution until the download was finished, meaning it would prevent any other JavaScript from being executed until it finished, and then when the download completes it would un-block the JavaScript execution and line 2 would execute.
Synchronous code is fine for things that happen fast, but it's horrible for things that require saving, loading, downloading or uploading. What if the server you're downloading the photo from is slow, or the internet connection you are using is slow, or the computer you are running the code on has too many youtube cat video tabs open and is running slowly? It means that it could potentially take minutes of waiting before line 2 gets around to running. Meanwhile, because all JavaScript on the page is being blocked from being run while the download is happening, the webpage would totally freeze up and become unresponsive until the download is done.
Blocking execution should be avoided at all costs, especially when doing so makes your program freeze up or become unresponsive. Let's assume the photo above takes one second to download. To illustrate how long one second is to a modern computer, here is a program that tests to see how many tasks JavaScript can process in one second.
function measureLoopSpeed() {
var count = 0
function addOne() { count = count + 1 }
// Date.now() returns a big number representing the number of
// milliseconds that have elapsed since Jan 01 1970
var now = Date.now()
// Loop until Date.now() is 1000 milliseconds (1 second) or more into
// the future from when we started looping. On each loop, call addOne
while (Date.now() - now < 1000) addOne()
// Finally it has been >= 1000ms, so let's print out our total count
console.log(count)
}
measureLoopSpeed()
Copy-paste the above code into your JavaScript console and after one second it should print out a number. On my computer I got 8527360, approximately 8.5 million. In one second JavaScript can call the addOne function 8.5 million times! So if you have synchronous code for downloading a photo, and the photo download takes one second, it means you are potentially preventing 8.5 million operations from happening while JavaScript execution is blocked.
Some languages have a function called sleep that blocks execution for some number of seconds. For example here is some bash code running in Terminal.app on Mac OS that uses sleep. When you run the command sleep 3 && echo 'done sleeping now' it blocks for 3 seconds before printing out done sleeping now.
console
JavaScript doesn't have a sleep function. Since you are a cat you are probably asking yourself, "Why am I learning a programming language that does not involve sleeping?". But stay with me. Instead of relying on sleep to wait for things to happen the design of JavaScript encourages use of functions instead. If you have to wait for task A to finish before doing task B, you put all of the code for task B into a function and you only call that function when A is done.
For example, this is blocking-style code:
a()
b()
And this is in a non-blocking style:
a(b)
In the non-blocking version b is a callback to a. In the blocking version a and b are both called/invoked (they both have () after them which executes the functions immediately). In the non-blocking version you will notice that only a gets invoked, and b is simply passed in to a as an argument.
In the blocking version, there is no explicit relationship between a and b. In the non-blocking version it becomes a's job to do what it needs to do and then call b when it is done. Using functions in this way is called callbacks because your callback function, in this case b, gets called later on when a is all done.
Here is a pseudocode implementation of what a might look like:
function a(done) {
download('https://pbs.twimg.com/media/B4DDWBrCEAA8u4O.jpg:large', function doneDownloading(error, png) {
// handle error if there was one
if (err) console.log('uh-oh!', error)
// call done when you are all done
done()
})
}
Think back to our non-blocking example, a(b), where we call a and pass in b as the first argument. In the function definition for a above the done argument is our b function that we pass in. This behavior is something that is hard to wrap your head around at first. When you call a function, the arguments you pass in won't have the same variable names when they are in the function. In this case what we call b is called done inside the function. But b and done are just variable names that point to the same underlying function. Usually callback functions are labelled something like done or callback to make it clear that they are functions that should be called when the current function is done.
So, as long as a does it's job and called b when it is done, both a and b get called in both the non-blocking and blocking versions. The difference is that in the non-blocking version we don't have to halt execution of JavaScript. In general non-blocking style is where you write every function so that it can return as soon as possible, without ever blocking.
To drive the point home even further: If a takes one second to complete, and you use the blocking version, it means you can only do one thing. If you use the non-blocking version (aka use callbacks) you can do literally millions of other things in that same second, which means you can finish your work millions of times faster and sleep the rest of the day.
Remember: programming is all about laziness and you should be the one sleeping, not your computer.
Hopefully you can see now that callbacks are just functions that call other functions after some asynchronous task. Common examples of asynchronous tasks are things like reading a photo, downloading a song, uploading a picture, talking to a database, waiting for a user to hit a key or click on someone, etc. Anything that takes time. JavaScript is really great at handling asynchronous tasks like these as long as you take the time to learn how to use callbacks and keep your JavaScript from being blocked.
The end!
This is just the beginning of your relationship with JavaScript! You can't learn it all at once, but you should find what works for you and try to learn all of the concepts here.
I'd recommend coming back again tomorrow and going through the entire thing again from the beginning! It might take a few times through before you get everything (programming is hard). Just try to avoid reading this page in any rooms that contain shiny objects . . . they can be incredibly distracting.
Got another topic you wanna see covered? Open an issue for it on github.
# Recommended reading
JavaScript For Cats skips over lots of details that aren't important for getting started (cats are not known for their attention spans), but if you feel like you need to dive in deeper then check these out:
NodeSchool.io is a community driven, open source educational software that teaches various web development skills in an interactive, self-guided format. I helped make NodeSchool! Sadly it features fewer cats than this page.
Eloquent Javascript is a free book that teaches you JavaScript! It's pretty good! Especially the chapter on values, variables, and control flow
Mozilla's JavaScript Guide also has a pretty sweet intro chapter called values, variables and literals
standard JS Style Guide is a "zero configuration" linter for JS style that I use
Let's Write Code by @shama a great series of YouTube coding tutorials made by a friend of mine
# Satisfied customers
satisfied customer
satisfied customer
satisfied customer
satisfied customer
satisfied customer
JSForCats.com is a labor of love and work in progress by @maxogden. If you would like to contribute and make this tutorial better there is a Github repo right over here.
console
-

@ 8cb60e21:5f2deaea
2024-09-06 22:23:03
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 472f440f:5669301e
2024-09-06 21:56:48
I had the pleasure of sitting back down with Will Reeves, Founder and CEO of Fold, on TFTC last week to discuss Fold's journey from a startup to (soon to be) a publicly listed company. I particularly liked this conversation because it was a great lens into the grit it takes to run a successful bitcoin company.
https://fountain.fm/episode/1FrspxmpK5bsoReGx73n
Building a successful company is extremely hard in its own right. Building a successful bitcoin company is significantly harder considering the fact that you're building a company in parallel with a nascent and volatile monetary asset that is monetizing in real time. Bitcoin adoption comes in waves. People flood in when the price is ripping and fade out when the price corrects and goes into a multi-year bear market before the tide comes back in. This means that your potential user base is expanding and contracting more than it would be in other industries. As a company you need to be able to absorb the incoming waves of new adopters and then capture and retain the users who stick around for the bear market.
To do this correctly, a founder and their team needs to thread many needles. First, can you assemble a team that can actually build something? Second, can you bring a product to market that people actually use because it provides value to them? Third, can you stick out against the crowd? So on and so forth.
One of the most important aspects of building a bitcoin company during bitcoin's monetization phase is timing. There are many great ideas that people have in terms of companies, products and tools that can built using bitcoin. There are sci-fi futures that can be built today on bitcoin if people really wanted to.
The problem that arises is that adoption and understanding of bitcoin are at a point where, even though a functional product could be brought to market, it won't be adopted by a large number of people because there 1.) aren't enough people who would understand how to use it and 2.) for the people who do understand how to use it and could benefit from it, the universe of people they can interact with using that product is minuscule.
Timing is everything. And I think Fold nailed the timing of their product. Allowing people to passively stack sats by offering a product that enables them to go about their daily spending and get sats back instead of cash back rewards is a great first-touch bitcoin experience. Once Fold found their sticky user base and perfected their sats back experience, they began expanding their product offering to provide their users with more bitcoin services. Buy/sell bitcoin in-app, bill pay for sats back, and more. They'll eventually roll out a credit card and additional financial services. Start simple, provide something of value, nail the timing and then expand from there. That seems to be the recipe.
For any founders in the space reading this, I highly recommend you listen to the episode. Particularly for the advice Will gives about knowing when to sprint on product and when to lean into growth. Bear markets are for building and bull markets are for casting the widest net possible and capturing as many new users as possible.
At Ten31 we are extremely proud to back Fold and a number of other companies in the bitcoin space that understand the intricacies described above. We work with some of the best founders in the world. Founders who know how to eat glass with the best of them. Bitcoin can be a cruel mistress and no one knows that more intimately than the founders building bitcoin companies.
---
Final thought...
The NFL having a week 1 game in Brazil should get Roger Godell fired.
Enjoy your weekend, freaks.
-

@ e83b66a8:b0526c2b
2024-09-06 19:16:04
The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud.
Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data.
There is a different way.
NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol.
The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms.
Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid.
Secondly as a user, you don’t have an account, you have a private key which is used to secure your data.
Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key.
Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays.
All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it.
Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key.
Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content.
Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions.
Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant.
As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models.
The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not.
NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment.
From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed.
While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops.
If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here:
https://primal.net/downloads
It will create a private key for you and setup a Bitcoin wallet.
Once you have done this you can visit me here:
nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n
If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already.
NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here:
nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Or you can see his account like this:
https://primal.net/jack
Edward Snowden is also on the platform and you can find him here:
https://primal.net/Snowden
NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation.
Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/
Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus
or Amethyst for Android: https://nostrapps.com/amethyst
The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it.
Some of the more interesting projects right now are:
https://www.0xchat.com/#/ – Private messaging – think WhatsApp
https://zap.stream/ – Video streaming
https://fountain.fm/ – Podcasting
https://wavlake.com/ – Music streaming
https://shopstr.store/ – Online shop
https://npub.pro/ – Website creation tool
https://nostr.build/ – Media and file storage
https://relay.tools/ – Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user – Creator tools
Remember, the same keys you created for Primal can be used across the whole ecosystem.
If you want to see some of the other apps that have been built on the NOSTR protocol visit:
https://nostrapps.com/
-

@ e968e50b:db2a803a
2024-09-06 19:13:32
https://www.youtube.com/watch?v=mn4whdycgxQ
I'm about to go play with a swing band from Pittsburg at an Italian music festival and am reviewing my Louis Prima for tonight. I thought I'd share a silly take on Body and Soul by the band's trombone player. The first chorus is ballad style, and then a romp through anything you can imagine (including the Hall of the Mountain King over Body and Soul changes)! Happy weekend!
originally posted at https://stacker.news/items/675086
-

@ b6dcdddf:dfee5ee7
2024-09-06 17:46:11
Hey Frens,
This is the Geyser team, coming at you with a spicy idea: a grant for proper journalism.
**Issue:**
Journalism is broken. Independent journalism is emerging with the work of [The Rage](https://geyser.fund/project/therage/), Whitney Webb and so forth. They deal with issues like privacy, political corruption, economics, ESG, medicine and many other issues that are not discussed by mainstream media.
The problem is that not many people know about their work and there are very few grant programs that support their work.
**Proposed Solution:**
Geyser would like to host a Grant supporting independent journalists using 'community voting mechanism'. See here for how [Community Voting Grants work](https://geyser.fund/grants/thailandbitcoinconference).
However, we need more companies to partner up and sponsor this initiative with us. Ideas of more sponsors:
- Stacker news: SN has become a great repository of independent/indie journalism. I think they'd fit in great as sponsors for this type of grant. cc: @k00b
- [Bitesize media](https://www.bitesizebitcoin.xyz): A new independent media house that wants to focus on the signal Bitcoin brings to our world. They expressed interest already.
- Bitcoin Magazine: might be interested as well in this effort.
Would love the community's feedback on this idea and propose additional thoughts!
originally posted at https://stacker.news/items/674951
-

@ ffd375eb:4529ed08
2024-09-06 15:39:31
## Chef's notes
Watch the video 🇫🇷: https://youtu.be/cYl4Lb0vbyc
## Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 3 months
- 🍽️ Servings: Many
## Ingredients
- 1 fennel bulb
- 1 large onion
- 3 garlic cloves
- 1/2 tsp salt per fennel bulb
- 1 tbsp turmeric powder per fennel bulb
- 1 tbsp oil per fennel bulb
- 1 tsp black pepper per fennel bulb
- 1 tbsp honey per fennel bulb
## Directions
1. Thinly slice the fennel bulb, onion, and garlic using a mandoline slicer.
2. In a bowl, mix the sliced fennel, onion, garlic, and salt. Let sit for a bit to allow the salt to act on the ingredients.
3. In a separate bowl, mix the turmeric, oil, black pepper, and honey to make a sauce.
4. Combine the fennel, onion, garlic mixture with the turmeric sauce and mix well.
-

@ 3bf0c63f:aefa459d
2024-09-06 12:49:46
# Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-

@ 6bae33c8:607272e8
2024-09-06 08:16:48
I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be.
I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance.
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
. . .
In any event, let’s take a look at the slate: Here are the ownership numbers per [Officefootballpools.com](http://Officefootballpools.com).
<img src="https://blossom.primal.net/4143b814092950ec28820e3d86d7608059d8a767b14eb9e2f19821b57ccb0856.png">
The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.)
But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win.
If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose.
You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills.
But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is *supposed* to be priced in, of course, but I don’t care.)
I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now.
-

@ 6bae33c8:607272e8
2024-09-06 08:14:27
An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes.
In any event, it was an okay game, not great, but there were some interesting takeaways.
- Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff.
- Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask.
- Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.)
- Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more.
- Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot.
- Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown.
- Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though.
- Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game.
- Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role.
- After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG.
- You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night.
-

@ a30cdfee:2d2f97ff
2024-09-06 06:50:05
# Orqestra: Converting Business Sales to Bitcoin
[Orqestra](https://orqestra.io/) lets businesses automatically convert portions of their sales to bitcoin!
What is Orqestra and how can it be useful for businesses?
## Protect Against Inflation with Bitcoin
Long-term saving in bitcoin is a good way to hedge against inflation.
Not just for individuals, but also for companies.
Case in point: MicroStrategy
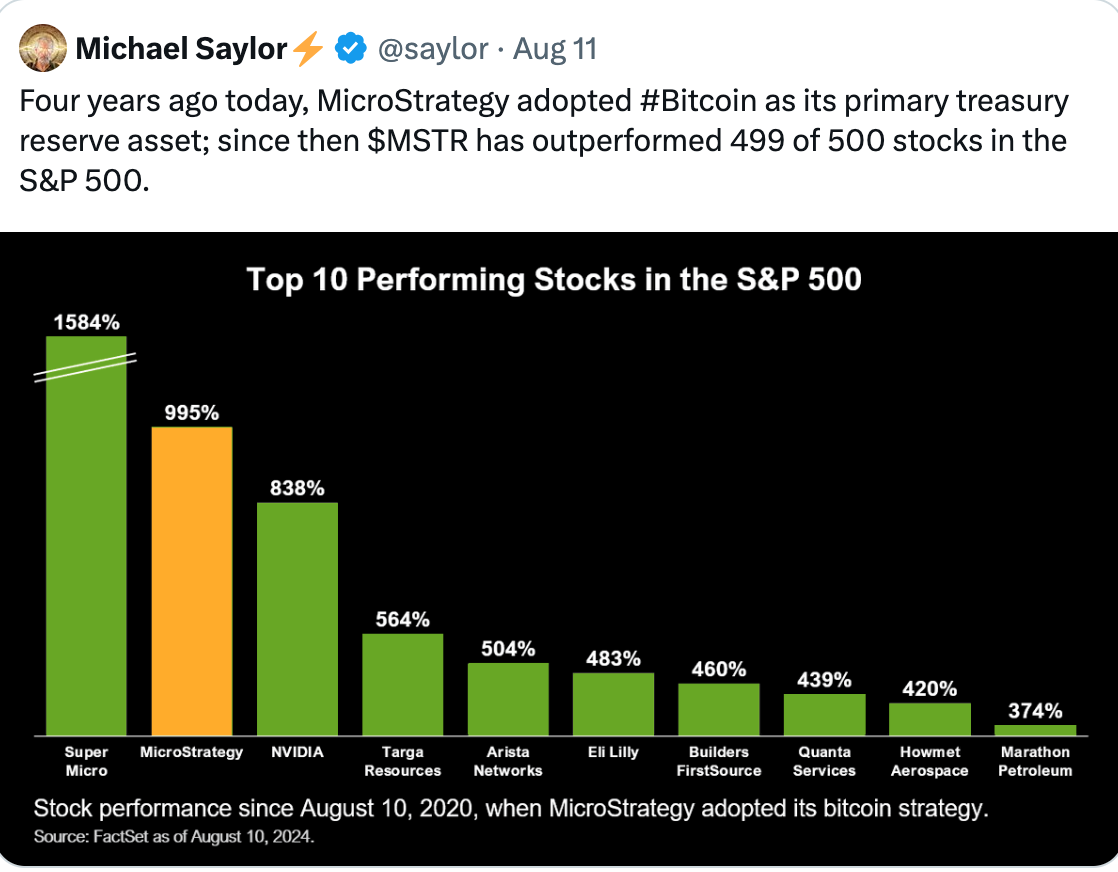
Bitcoin's strong liquidity also allows quick conversions to fiat if needed, giving companies financial flexibility.
## Converts Portions of Sales to Bitcoin
Orqestra simplifies Bitcoin acquisition, targeting small and medium-sized businesses.
You can connect your payment providers, and the platform will automatically convert portions of your sales to bitcoin.
Start small or go all in, it's up to you!
Orqestra integrates with e.g. PayPal, QuickBooks, Square and Stripe.
You can also link e.g. [Clams](https://clams.tech/), a Bitcoin-focused accounting software for automated bookkeeping.
You can learn more about Clams here: https://stacker.news/items/552799
## Custodial, but You Can Withdraw to Your Own Wallet
Orqestra states that it partners with industry-leading custodians to store the BTC.
You can also withdraw the BTC to your own wallet, or convert it to US dollars.
The platform is currently only supporting businesses in the United States.
## KYC Required
Orqestra was founded by João Almeida, former CTO and co-founder of a Bitcoin payment infrastructure provider [OpenNode](https://opennode.com/).
Orqestra can give tax-ready reports that meet industry standards on demand.
To use the platform, businesses need to provide proof of legal existence of the company, proof of address and all beneficiaries with over 25% ownership in the company need to perform KYC.
## Project Links
[Website](https://orqestra.io/)
[X (Twitter)](https://x.com/orqestraio)
originally posted at https://stacker.news/items/674222
-

@ 84b0c46a:417782f5
2024-09-06 00:26:32
- 1:nan:
- **2**
- 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p)
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2|
|--|--|
|test|:nan:|
---
### :nan: **:nan:**
1. 1
2. 2
- tet
- tes
3. 3
1. 1
2. 2
> t
>> te
>>> test
-

@ c7eadcf0:7821e562
2024-09-06 00:10:23
Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck.
Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis.
Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin.
This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite?
Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out.
-

@ acc925af:db9fb0bb
2024-09-05 20:26:50
While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good
**Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:**
# Prerequisites:
1. Twitter Developer Account
2. Nostr Wallet with NWC support (e.g., Alby, Nostrify)
3. Twitter API credentials (API key, API secret key, Access token, Access token secret)
4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library)
### Step 1: Set up Twitter API credentials
> Create a Twitter Developer account and obtain API credentials
> Install Tweepy using pip: pip install tweepy
### Step 2: Connect Nostr Wallet using NWC
> Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify)
> Set up the wallet and obtain the NWC credentials (e.g., public key, private key)
### Step 3: Create a Python script
> Import Tweepy and nostr-client libraries
> Authenticate with Twitter API using Tweepy
> Connect to Nostr Wallet using NWC credentials
> Define a function to send 21 satoshis for every like
> Use Tweepy to stream likes and trigger the payment function
`Python` script:
```
import tweepy
from nostr_client import Client
# Twitter API credentials
twitter_api_key = "YOUR_API_KEY"
twitter_api_secret_key = "YOUR_API_SECRET_KEY"
twitter_access_token = "YOUR_ACCESS_TOKEN"
twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET"
# Nostr Wallet NWC credentials
nwc_public_key = "YOUR_NWC_PUBLIC_KEY"
nwc_private_key = "YOUR_NWC_PRIVATE_KEY"
# Set up Tweepy
auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key)
auth.set_access_token(twitter_access_token, twitter_access_token_secret)
api = tweepy.API(auth)
# Set up Nostr Client
nwc_client = Client()
nwc_client.connect(nwc_public_key, nwc_private_key)
# Define payment function
def send_satoshis():
# Create a new Nostr event with 21 satoshis
event = nwc_client.create_event(21)
# Send the event to the Nostr network
nwc_client.send_event(event)
# Stream likes and trigger payment function
class LikeStream(tweepy.StreamListener):
def on_like(self, like):
send_satoshis()
stream = tweepy.Stream(auth, LikeStream())
stream.filter(track=["likes"])
```
##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._
originally posted at https://stacker.news/items/673795
-

@ 8cb60e21:5f2deaea
2024-09-05 19:48:32
## Part 1: Fundamentum Javascripti
### 1.1 Introductionis
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nullam euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. Sed euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc.
```javascript
console.log("Salve, mundi!");
```
### 1.2 Variabiles et Typi Datorum
Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Integer convallis, nunc ac blandit tincidunt, ipsum augue tincidunt nunc, vitae tincidunt nisl nunc euismod nunc.
```javascript
var numerus = 42;
let textus = "Lorem ipsum";
const CONSTANTIA = true;
```
#### 1.2.1 Typi Numerorum
Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo.
```javascript
let integer = 10;
let floatinum = 3.14;
let scientificum = 2.998e8;
```
#### 1.2.2 Typi Textuum
Maecenas tristique, est et tempus semper, est quam pharetra magna, ac consequat metus sapien ut nunc.
```javascript
let textusBrevis = 'Carpe diem';
let textusLongus = "Quod erat demonstrandum";
let textusTemplatum = `Cogito, ${textusBrevis.toLowerCase()}, sum`;
```
### 1.3 Operatores
Donec dapibus. Duis at velit eu est congue elementum. In hac habitasse platea dictumst.
```javascript
let a = 5;
let b = 3;
console.log(a + b); // Additio
console.log(a - b); // Subtractio
console.log(a * b); // Multiplicatio
console.log(a / b); // Divisio
console.log(a % b); // Modulus
console.log(a ** b); // Potentia
```
### 1.4 Structurae Controli
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
#### 1.4.1 Conditionales
```javascript
let aetas = 20;
if (aetas >= 18) {
console.log("Adultus es");
} else if (aetas >= 13) {
console.log("Adolescens es");
} else {
console.log("Puer es");
}
```
#### 1.4.2 Iterationes
```javascript
for (let i = 0; i < 5; i++) {
console.log(`Iteratio ${i}`);
}
let j = 0;
while (j < 5) {
console.log(`Dum iteratio ${j}`);
j++;
}
```
### 1.5 Exercitia Parti I
1. Scribe programma quod convertat gradus Celsius in Fahrenheit.
2. Crea algorithmum qui determinat si numerus est par vel impar.
3. Implementa "FizzBuzz" pro numeris 1 ad 100.
-

@ 8cb60e21:5f2deaea
2024-09-05 19:48:32
## Part 3: Asynchroni et DOM Manipulatio
### 3.1 Promissa et Async/Await
Praesent blandit. Nam nulla. Integer pede justo, lacinia eget, tincidunt eget, tempus vel, pede.
```javascript
function simulaRequest(data, probabilitasErroris = 0.1) {
return new Promise((resolve, reject) => {
setTimeout(() => {
if (Math.random() < probabilitasErroris) {
reject("Error: Aliquid mali accidit");
} else {
resolve(`Data accepta: ${data}`);
}
}, 1000);
});
}
simulaRequest("Lorem ipsum")
.then((responsum) => console.log(responsum))
.catch((error) => console.error(error));
async function fetchData() {
try {
const responsum = await simulaRequest("Dolor sit amet");
console.log(responsum);
} catch (error) {
console.error(error);
}
}
fetchData();
```
### 3.2 DOM Manipulatio
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
```javascript
document.addEventListener("DOMContentLoaded", () => {
const titulus = document.createElement("h1");
titulus.textContent = "Lorem Ipsum JavaScript";
document.body.appendChild(titulus);
const paragraphus = document.createElement("p");
paragraphus.textContent = "Neque porro quisquam est qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit...";
document.body.appendChild(paragraphus);
const button = document.createElement("button");
button.textContent = "Fac Clic Me";
button.addEventListener("click", () => {
alert("Gratias tibi ago pro clic!");
});
document.body.appendChild(button);
});
```
### 3.3 Fetch API
Maecenas leo odio, condimentum id, luctus nec, molestie sed, justo. Pellentesque viverra pede ac diam.
```javascript
async function fetchLoremIpsum() {
try {
const responsum = await fetch("https://api.lorem.space/image/game?w=150&h=220");
if (!responsum.ok) {
throw new Error(`HTTP error! status: ${responsum.status}`);
}
const data = await responsum.blob();
const imago = document.createElement("img");
imago.src = URL.createObjectURL(data);
document.body.appendChild(imago);
} catch (error) {
console.error("Problema cum fetching imagine:", error);
}
}
fetchLoremIpsum();
```
### 3.4 Local Storage
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim.
```javascript
function salvaPreferentias(clavis, valor) {
localStorage.setItem(clavis, JSON.stringify(valor));
}
function accipePreferentias(clavis) {
const valor = localStorage.getItem(clavis);
return valor ? JSON.parse(valor) : null;
}
const preferentiae = {
thema: "clarus",
lingua: "Latina",
notificationes: true
};
salvaPreferentias("userPrefs", preferentiae);
const salvataePreferentiae = accipePreferentias("userPrefs");
console.log(salvataePreferentiae);
```
### 3.5 Exercitia Parti III
1. Crea paginam web simplicem quae utitur fetch API ad exhibendum datos ex API publica.
2. Implementa functionalitatem "drag and drop" utens DOM API.
3. Construe applicationem "todo list" quae persistit datos in local storage.
## Conclusio
Vivamus vestibulum sagittis sapien. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Etiam vel augue. Vestibulum rutrum rutrum neque. Aenean auctor gravida sem. Praesent id massa id nisl venenatis lacinia. Aenean sit amet justo. Morbi ut odio.
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Proin interdum mauris non ligula pellentesque ultrices. Phasellus id sapien in sapien iaculis congue. Vivamus metus arcu, adipiscing molestie, hendrerit at, vulputate vitae, nisl.
Aenean lectus. Pellentesque eget nunc. Donec quis orci eget orci vehicula condimentum. Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. Maecenas pulvinar lobortis est.
Phasellus sit amet erat. Nulla tempus. Vivamus in felis eu sapien cursus vestibulum. Proin eu mi. Nulla ac enim. In tempor, turpis nec euismod scelerisque, quam turpis adipiscing lorem, vitae mattis nibh ligula nec sem. Duis aliquam convallis nunc. Proin at turpis a pede posuere nonummy.
Integer non velit. Donec diam neque, vestibulum eget, vulputate ut, ultrices vel, augue. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec pharetra, magna vestibulum aliquet ultrices, erat tortor sollicitudin mi, sit amet lobortis sapien sapien non mi. Integer ac neque. Duis bibendum. Morbi non quam nec dui luctus rutrum. Nulla tellus. In sagittis dui vel nisl. Duis ac nibh. Fusce lacus purus, aliquet at, feugiat non, pretium quis, lectus.
Suspendisse potenti. In eleifend quam a odio. In hac habitasse platea dictumst. Maecenas ut massa quis augue luctus tincidunt. Nulla mollis molestie lorem. Quisque ut erat. Curabitur gravida nisi at nibh. In hac habitasse platea dictumst. Aliquam augue quam, sollicitudin vitae, consectetuer eget, rutrum at, lorem. Integer tincidunt ante vel ipsum. Praesent blandit lacinia erat. Vestibulum sed magna at nunc commodo placerat. Praesent blandit. Nam nulla.
-

@ 8cb60e21:5f2deaea
2024-09-05 19:48:32
## Part 2: Functiones et Objecta
### 2.1 Functiones
Fusce posuere felis sed lacus. Morbi sem mauris, laoreet ut, rhoncus aliquet, pulvinar sed, nisl.
```javascript
function salutatio(nomen) {
return `Salve, ${nomen}!`;
}
console.log(salutatio("Cicero"));
const valedictio = (nomen) => {
console.log(`Vale, ${nomen}!`);
};
valedictio("Seneca");
```
#### 2.1.1 Parametri Default et Rest
Nunc purus. Phasellus in felis. Donec semper sapien a libero.
```javascript
function congregatio(primus, secundus = "mundi", ...ceteri) {
console.log(`${primus} ${secundus}`);
console.log(`Ceteri: ${ceteri.join(", ")}`);
}
congregatio("Salve");
congregatio("Lorem", "ipsum");
congregatio("Veni", "vidi", "vici", "et", "cetera");
```
### 2.2 Objecta
Nam congue, risus semper porta volutpat, quam pede lobortis ligula, sit amet eleifend pede libero quis orci.
```javascript
const persona = {
nomen: "Iulius",
cognomen: "Caesar",
aetas: 55,
salutatio: function() {
return `Salve, ${this.nomen} ${this.cognomen}!`;
}
};
console.log(persona.salutatio());
```
#### 2.2.1 Methodi Object
Nullam porttitor lacus at turpis. Donec posuere metus vitae ipsum. Aliquam non mauris.
```javascript
const claves = Object.keys(persona);
console.log(claves);
const valores = Object.values(persona);
console.log(valores);
const paria = Object.entries(persona);
console.log(paria);
```
### 2.3 Arrays
Morbi porttitor lorem id ligula. Suspendisse ornare consequat lectus. In est risus, auctor sed, tristique in, tempus sit amet, sem.
```javascript
const fructus = ["malum", "pirum", "uva", "cerasum"];
fructus.forEach((fructus) => {
console.log(fructus);
});
const longiFructus = fructus.filter((fructus) => fructus.length > 4);
console.log(longiFructus);
const maiusculaFructus = fructus.map((fructus) => fructus.toUpperCase());
console.log(maiusculaFructus);
```
### 2.4 Exercitia Parti II
1. Crea functionem quae calculat factorialem numeri.
2. Implementa methodum quae invenit maximum valorem in array.
3. Scribe programma quod ordinat objecta in array secundum proprietatem specificam.
-

@ e8b86bc1:3503c58f
2024-09-05 19:38:11
Opinion about Freewallet Multi Crypto Wallet (iphone)
<!--HEADER END-->
Another method Freewallet uses to rob customers: inactivity fees. They charge you for not using the app, wiping out your assets slowly. Avoid Freewallet!
<!--FOOTER START-->
#WalletScrutiny #nostrOpinion
[Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
-

@ e968e50b:db2a803a
2024-09-05 19:33:33
ATTENTION PARENTS!
I have revamped my LNBITS [bitcoin piggy bank](http://bitcoinpiggybank.vercel.app) so you don't need to deploy it yourself. Check it out at http://bitcoinpiggybank.vercel.app. All you need now is a LNBITS wallet. I've deployed a website that you can just log into with that and nothing else. I'm thinking about actually renting out my own domain for this one if people find it useful.
https://www.youtube.com/watch?v=X-MNqJiLCM4
Teach your kids about sound money while they're actually stacking sats and using a fun interface.
originally posted at https://stacker.news/items/673739
-

@ 9977c3ad:43a20d63
2024-09-05 11:21:09
## Details
- 🍽️ Servings: 2
## Ingredients
- 1 cup Jasmine rice
- 1 Tbsp. lavender flowers, crushed with mortar and pestle
- 1/4 cup apple cider vinegar
- 2 Tbsp. fine cane sugar
- 2 Tbsp. honey
- 1 sprig rosemary
- 1/4 tsp angostura bitters
- 1/2 cup blackberries
- 1/2 cup blueberries
- 4 cups trimmed and quartered shiitake mushrooms
- 1 tsp fresh coriander crushed
- 1/4 tsp fresh cumin ground
- 1/2 tsp red pepper flakes
- 3 sprigs of thyme
- 2 Tbsp. olive oil
- 1 tsp soy sauce
- 1 cup creamy coconut milk
## Directions
1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes.
2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside.
3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
-

@ 472f440f:5669301e
2024-09-04 22:54:11
For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam.
However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash.
Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin.
BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now.
https://strike.me/blog/bolt12-offers/
As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented.
Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology".
The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack.
This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential.
Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust.
Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin.
---
Final thought...
Vibes are high.
-

@ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17
When I have stale bread, I often use it to make a bread salad.
The base is croutons of stale bread and then there are no limits to your imagination.
In this salad there was also
- Onions stewed in balsamic vinegar
- Spring onions (raw)
- Cherry tomatoes
- Eggplants and sweetcorn (fried, lukewarm)
- Pine nuts
- Finely sliced cheese
- Basil
https://image.nostr.build/ce0c7490f2adbd2aa4ccdfe80203a15dbb10686859a3256a0147d5f423478fd0.jpg
https://image.nostr.build/f930e0984ec9603b84c7a7868a97486140ee44590590102f7e460bfbfd3d70be.jpg
originally posted at https://stacker.news/items/672404
-

@ d830ee7b:4e61cd62
2024-09-04 07:29:41
Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล
ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน
แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด
ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ
## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks**
ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม
แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา..
เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่
ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin
ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน..
ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน
Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ
## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน**
ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core
Blockstream สนับสนุน "Small Blocks"
เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้
ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา
## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน**
ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB**
แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers
Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง
Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org
ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน
เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น..
## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว**
ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement"
ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว
ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash**
ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017
SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย
SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา..
อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit
ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"**
## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ**
ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้
Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้
Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว
เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด
นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย
## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright**
ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)**
การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔
ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash
กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts
Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer"
การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย
## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี**
หลังจากการ Hard Fork ของ Bitcoin Cash
Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value)
การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม
Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง
อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน
นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง
นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain
Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin
## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ**
ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ
ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง
สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป
# **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง**
## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล**
Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า
### **SegWit (Segregated Witness)**
เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network
### **Taproot**
เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป
Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ
## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่**
ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่
### **Bitcoin XT (2015)**
เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ
### **Bitcoin Classic (2016)**
เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน
### **Bitcoin Unlimited (2016)**
เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง
### **Bitcoin Cash (BCH) (2017)**
เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง
### **Bitcoin SV (BSV) (2018)**
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin
### **Bitcoin ABC (2020)**
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง
## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?**
หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists
Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"**
Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น..
### **การไม่ยอมเพิ่ม Blocksize Limit**
Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream
### **การเซ็นเซอร์ข้อมูล**
Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ
### **การต่อต้านนวัตกรรม**
Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น
### **การควบคุมโดยกลุ่มเล็กๆ**
Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin
Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto
## **บทสรุป:**
การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency
มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป
สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด
**"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่..
ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย..
เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง..
— Jakk Goodday
-

@ 1739d937:3e3136ef
2024-09-04 07:23:12
This is the sixth in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
## Previous Updates
- [June 28th 2024](https://habla.news/u/jeffg.fyi/1719562889267)
- [July 6th 2024](https://habla.news/u/jeffg.fyi/1720256910765)
- [July 12th 2024](https://habla.news/u/jeffg.fyi/1720778880538)
- [July 19th 2024](https://habla.news/u/jeffg.fyi/1721419437737)
- [August 16th 2024](https://habla.news/u/jeffg.fyi/1723802138254)
## Progress this week
Sorry about the very late update this week. Catching up on everything after a week in Riga for Nostriga and Baltic Honeybadger took a bunch of time, every other moment was spent coding. 👨💻
The response at Nostriga to NIP-104 and my two talks on the subject were overwhelmingly positive. It was very helpful to spend time with other devs going through the spec in detail. We found a few minor improvements and clarifications but no major issues surfaced. Thanks to nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49, nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj, and nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr in particular for the lengthly interrogations and nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 for the introductions.
Last week, I started work on a reference implementation of the spec. It's still early but going quickly.
My PR adding support for secp256k1 was also merged into the hpke-rs library yesterday. That's one more step in the right direction towards having secp256k1 ciphersuite support.
### The NIP
If you haven't already, check out my talk; [The Past and Future of DMs and Group messaging on Nostr](https://www.youtube.com/watch?v=PWKd9aoZ-Cg). This was a basic overview of the various DM and group messaging schemes and talks a little about the progress on NIP-104. I _believe_ there is a recording of the technical talk on the spec but it hasn't yet been released. I'll link it up when it is.
At this point I've been discouraging anyone from trying to implement the NIP quite yet. As I mentioned above there are a few adjustments that need to be made and a few open questions that I'm working on answering with my implementation (which I'm very happy to have contributors on). My plan at the moment is to do this first implementation with the default ciphersuite that MLS already supports while I continue to work on the dependencies to get secp256k1 support across the board.
### The Implementation
I've started on a cross-platform native client that will run on Mac, Windows, Linux, iOS, and Android. Think of it as Signal or Telegram but over Nostr. I hope that this will not only become the reference implementation for other client developers but also will be one of the most secure and privacy focused clients in the Nostr ecosystem. Building it has already been helpful in clarifying some of the more complex implementation details in the NIP. It's still early but I'll have more to share on this in the coming weeks.
### HPKE-RS
My [PR](https://github.com/franziskuskiefer/hpke-rs/pull/66) to add support for secp256k1 is merged!
## Onward and Upward
Thanks again to everyone for the support and feedback on this stuff at Nostriga. It was hugely motivating to hear the kind words, have you introducing me to people that could help, and spending time giving me feedback! This community is the best. 🫂
-

@ e0e92e54:d630dfaa
2024-09-04 04:13:19
_This is a copy of the email received from newsletter@Rumble.com_

# Free Speech Under Attack -- A Note from the CEO of Rumble
Dear Rumble Users,
I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble.
Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court.
World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them.
There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it.
Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people.
The people keep us alive and keep us going.
If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression.
We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil".
Sincerely,
Chris Pavlovski
Chairman and CEO of Rumble

444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA.
-

@ 862fda7e:02a8268b
2024-09-04 01:45:14
It is true that I often dream about James Corbett from CorbettReport.com. Somehow James is always finding his way to my mind. James Corbett intimidates me, I feel like he would heavily dislike me because I am not serious enough. Anytime I see James Corbett smile or laugh it feels like I'm watching an alien try to be human. I wish James the best with his family life and career, but he looks like he is always one second away from either crying hyterically or beating a defensless Japanese man sensless. I am indreasibly grateful for all the hard work he's put out all these years, he's a great person in the truth circle. However, he's like a caracatiure in my head. Anytime he whips out his guitar, I start to cringe. I just know what's about to come will only be the truth about how bad his singing is. But yet, I still love when he plays his guitar. It's awful in a great way, it brings genuine joy to me. Did you know he has a band? He has one song called "Screw Youtube", and in his music video he was sitting on this tall wooden fence and he was wearing these SHORTS WITH SANDALS and he was SWINGING HIS LEGS. I'm sorry, but I expect James to wear white caykies at all times. It felt so gross to see his legs in that state. But then again, here I am getting genuine joy out of seeing that atrosity.
I remember one time watching a James Corbett episode where he has the James Evan Pilatto from MediaMonarchy.com on, and the other James always looks like he's super fucking cracked up. Like he has a ton of energy. Well anyways, one time the other James was his usual self, looking super cracked out excited, talking about the reppies (reptilians) and James Corbett looked so tight lipped, red faced, like he was about to burst out crying. It was so funny to see the two polar opposites, the other James totally oblivious that real James looked like he was about to cry for seemingly no reason. I know this sounds mean of me to say, but I really appreciate these guys for all they do. I just think this is funny.
Anyways, I have a lot of dreams with James Corbett in them. I think it's because he's a teacher and my vagina has a fondness for male teachers. Sadly, none of my good looking male teachers never slept with me. That being said, I think James is good looking for possibly being an English teacher in Japan. I would let him teach me about the reptilians and Klaus Schwab, just let the teaching session see where it goes. Would his gap teeth feel good over my clitty? I dunno.
Okay but here is the most memorable and hilarious dream I had invovling James Corbett. You know how he makes content very often? One day he got extremely fed up with making videos. At the time I think it's because he mentioned in a video how he was annoyed that people kept saying him and Andrew Caufman. So one day he just flipped out, got extremely angry, made one last video saying how he was never coming back and how he's leaving his wife and kids. He deletes everything and is unheard of for months. A few months pass and he uploads a new video. The new video is James obsessively showing and talking about his highly advanced chicken coop he made in Minecraft. He had hundreds of chickens lined up maybe 80 feet in the air, each chicken had a 1x1 square to fit in. Below the chicken was a long tube in which their egg would drop down, and a catcher at the base of the ground. James was fantically showing this contraption, rocking back and forth, had a headset on. He looked awful too. I actually emailed James Corbett about this dream, but he never responded.
Speaking of James Corbett, why do so many people look like him? I feel like they make middle aged bald, bearded men in a DUMB and just release them into the wild, but give them balding genetics so they know how to keep track of them. Like they probably made James Corbett and Andrew Caufman from the same test tube. They fucked up with them, at least like give one of them hair or good eyesight.
-

@ 3b7fc823:e194354f
2024-09-04 01:33:21
Nyms, Personas, and Digital Identity
#GHOSTn
If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs.
Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see.
Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be.
Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes.
Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
-

@ 3b7fc823:e194354f
2024-09-04 00:26:48
Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
>
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled.
If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
>
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
>
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
>
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
>
>
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
>
Last point and most important:
Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-

@ 8cb60e21:5f2deaea
2024-09-03 22:26:25
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8cb60e21:5f2deaea
2024-09-03 22:26:25
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8cb60e21:5f2deaea
2024-09-03 21:58:26
# Lesson 2: Functions and Loops
### Functions: Your Own Commands
Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick:
```javascript
function meow(times) {
for (var i = 0; i < times; i++) {
console.log("Meow!");
}
}
meow(3); // This will print "Meow!" three times
```
### Built-in Functions
JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console:
```javascript
console.log("I'm a cat!");
```
### Loops: Repeating Tasks
Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds:
```javascript
for (var i = 0; i < 5; i++) {
console.log("Chasing tail, round " + (i + 1));
}
```
This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
-

@ 8cb60e21:5f2deaea
2024-09-03 21:58:26
# Lesson 3: Arrays, Objects, and Callbacks
### Arrays: Lists of Things
Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys:
```javascript
var catToys = ["mouse", "ball", "laser pointer"];
console.log(catToys[0]); // Prints "mouse"
```
### Objects: Grouping Related Information
Objects allow you to group related information together. They're like detailed profiles for each of your cat friends:
```javascript
var myCat = {
name: "Fluffy",
age: 3,
favoriteFood: "tuna"
};
console.log(myCat.name); // Prints "Fluffy"
```
### Callbacks: Doing Things Later
Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat:
```javascript
function feedCat(callback) {
console.log("Feeding the cat...");
setTimeout(function() {
console.log("Cat has finished eating!");
callback();
}, 2000);
}
feedCat(function() {
console.log("Time for a treat!");
});
```
This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat.
Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
-

@ 4c96d763:80c3ee30
2024-09-03 18:46:10
# Changes
## William Casarin (7):
- debug: add subid debugging
- fix bug where it was subscribing too many times
- arg: add -c profile{,:pubkey} arg column
- env: add some test npubs
- arg: add -c universe column
- appease clippy
- fonts: add thai support
pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/989f88c989f5d6ec85f719efab6f80fb1a95ee00.html)
-

@ 6bae33c8:607272e8
2024-09-03 10:47:55
I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track.
*(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)*
1. **Stefon Diggs leads the Texans in targets, catches and receiving yards**
Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year.
2. **CJ Stroud leads the NFL is passing yards**
This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2.
3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)**
Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens.
4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR**
Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020.
5. **The Giants will field a top-10 fantasy defense.**
I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers.
6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt**
I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua.
7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)**
Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time.
8. **Dalvin Cook will lead the Cowboys in rushing yards**
Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.)
9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.**
He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.)
10. **Dalton Kincaid (TE4) will lead all TE in catches**
I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2.
11. **Some of these predictions will be wrong**
No one’s perfect, but you never want to get shut out.
-

@ 161c8564:2d633b95
2024-09-02 20:24:34
Opinion about Freewallet Multi Crypto Wallet (iphone)
<!--HEADER END-->
FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it!
<!--FOOTER START-->
#WalletScrutiny #nostrOpinion
[Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
-

@ eed76ece:afa98124
2024-09-02 18:58:30
As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously.
Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online.
SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West.
Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway.
Examples
Customers in these regions I deal with primarily communicate with me in
Japan, Thailand using LINE and Tik Tok daily.
Most of the rest of the World communicate with me using WhatsApp.
Certain parts of Eastern Europe and Asia Telegram.
Interestingly my resellers in the USA primarily post on WhatsApp.
Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again".
"So I will always have free speech, the politicians told me so".
originally posted at https://stacker.news/items/670041
-

@ 6bae33c8:607272e8
2024-09-02 18:09:19
I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot.
Here are the results:
([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream))
<img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png">
**1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount.
**2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead.
**3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there.
**4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target.
**5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone.
**6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year.
**7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position.
**8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR.
**9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.)
**10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.)
**11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks.
**12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build.
**13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job.
**14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert.
**15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old.
**16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down.
**17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too.
**18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie.
**19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.)
**20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence.
**Roster By Position**
**QB** Anthony Richardson
**RB** James Conner/Jaleel McLaughlin
**WR** Ja’Marr Chase/Drake London/DeVonta Smith
**TE** Dalton Kincaid
**FLEX** Stefon Diggs
**K** Younghoe Koo
**D** Giants
**Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
-

@ 3b7fc823:e194354f
2024-09-02 16:26:30
First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
>
1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program.
>
2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.
BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
>
3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works.
>
4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta.
>
5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.
>
BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
>
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-

@ 266815e0:6cd408a5
2024-09-02 15:27:16
After 7 months of work and procrastination I've decided to release another version of noStrudel
There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md)
And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker
```sh
docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0
```
## New Features
### Support for NIP-49 encrypted nsec
Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...)
There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps

### Blindspot feeds
There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing

### NIP-42 Relay authentication
The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings

### Wasm relay and event verification
The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view

The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting

### Thread tabs
Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note


### Wiki articles
Its not feature complete but you can now view and edit wiki articles in the app

### Finished the launchpad
The launchpad is now usable and shows the latest notifications, messages, streams, and tools

### Blossom uploads
The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings

And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`

### Task Manager
There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app

You can see what relays the app is currently connected to

And which relays are requesting NIP-42 authentication

## Bug fixes
- Fix null relay hints in DMs
- Fix users own events being hidden by muted words
- Fix random events showing up as DM messages
- Fix app prompting NIP-07 extension to unlock when app opens
- Remove corsproxy.io as default service for CORS proxy
-

@ 38d0888d:bd8e1246
2024-09-02 11:08:05
To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment.
A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding.
It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
-

@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53
There's a saying: Bitcoin is hope.
But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin.
For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right?
I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours?
She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw.
I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else.
So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero.
There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore.
We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent?
The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them.
Extreme situations, I know. But no one thinks it will happen to them—until it does.
So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why?
What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time.
Time with your kids. Time with your family. Time with yourself.
There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work.
But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here.
So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here.
I just need to get through the withdrawal phase.
originally posted at https://stacker.news/items/662939
-

@ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27
Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.

originally posted at https://stacker.news/items/669464
-

@ 8125b911:a8400883
2024-09-02 07:18:52
曾经有一款热门插件 dmooji(弹幕君),它让 YouTube 拥有了像其他弹幕网站一样的互动体验。看着屏幕上飞过的评论和吐槽,仿佛能和全世界的观众一起欢笑、感动、吐槽,那些弹幕不仅仅是文字,更是观众们在某个时刻留下的心情。但随着 dmooji 的开发者停止了维护,插件无法使用,用户的弹幕数据也随之丢失。那些在无数个夜晚留下的感触和笑点都被抹去,曾经与他人共享的回忆也随之消逝。这样的教训提醒我们,依赖于单一平台和维护团队的产品,总有脆弱的一天,可能我们珍视的东西就会悄然不再。
大约两年前,我偶然间了解到了一个去中心化的社交网络协议——nostr。当时我就萌生了一个想法:如果能基于这个协议做一款弹幕插件,那该有多好!然而,因为我主要从事后端开发,对前端几乎一窍不通,再加上拖延症的“加持”,这个想法一直被搁置。直到最近,我终于下定决心完成了这个项目,并将它命名为 danmakustr。
下载地址:https://chromewebstore.google.com/detail/mohbdimkkpjjibdfipfajpgpmegnglhb
源码地址:https://github.com/CodyTseng/danmakustr
最近弹幕墙:https://danmaku.nostr-relay.app/
## danmakustr 有什么特点?
基于去中心化社交网络协议 nostr。你的弹幕会被发送并存储到你指定的服务器上,而非依赖单一服务器。即使插件未来不再维护,只要 nostr 网络仍然存在,插件就能继续正常使用!如果你非常珍视自己的弹幕,可以在本地运行 nostr-relay-tray 并将其添加到 relay 列表中。
danmakustr 目前已经在 YouTube 上实现了基本的弹幕功能,支持自定义弹幕的颜色和显示位置。未来还会支持一些弹幕互动功能,和支持更多的视频平台。
## 结语
在这个越来越注重个人表达和数据隐私的时代,danmakustr 带来了 YouTube 弹幕互动的新可能。它既保留了我们熟悉的乐趣,又为我们提供了前所未有的自由和控制权。如果你也对弹幕文化情有独钟,或者想要尝试一种全新的互动方式,那就赶紧体验 danmakustr 吧!让我们一起在弹幕的世界里畅所欲言,留下属于自己的印记。
 @ 2f5de000:2f9bcef1
2024-12-15 16:44:53This Week I immersed myself in Bitcoin from multiple angles-technical, societal and personal. The journey included a marathon 32-hours of listening to [Rabbit Hole Recap (RHR)](https://fountain.fm/show/VDaMppQRUBZioj2XkaLn), an essential resource for Bitcoin insights. It's worth noting that I started from the begining and plan to make my way through the whole catalogue. Marty and Matt's timestamps, along with contributions from their guests, served as my roadmap. Using Fountain to stream, I also streamed sats-a small but extraordinary feature that allows users to stacks sats while compensating cretors directly through fractional donations. ## Revisiting Speculative Attack by Pierre Rochard (2014) Now that [*Speculative Attack Season 2*](https://nakamotoinstitute.org/mempool/speculative-attack-season-2/) *(which I've not read yet)* has been released. I took the time to read Pierre Rochards influential essay, [*Speculative Attack*](https://nakamotoinstitute.org/mempool/speculative-attack/) and reflected on its timeless insights. Rochard argues that Bitcoin adoption isn't dependent on technological advancements or consumer preferences, but on economic realities. As fiat currencies weaken, Bitcoin won't enter the mainstream by persuasion but by necessity. Critics continue to underestimate Bitcoin's inevitability due to their fiat biases and lack of financial insight. This year alone, mainstream media has been compelled to discuss Bitcoin-notably to Trump's endorsement of 'crypto.' Despite their attempts to shape narratives to suit their ideal visions, they've had no choice but to engage with Bitcoin's growing influence.\ \ As Parker aptly puts it 'Gradually, The Suddenly' ## Wassabi Wallet and the Privacy Imperative An RHR interview (from early in the catalogue) with guest Adam Ficsor, CTO and Co-founder of Wassabi Wallet, sparked a deeper consideration of my digital footprint. Like many, I've spent years online neglecting privacy in favour of convenience. The discussion on CoinJoins reminded me of the importance of prioritising privacy, not just romanticising it. Improving operational security (opsec) is now a personal focus. Resources like Jameson's *Cypherpunk Cogitations* and the Bitcoin Optech newsletter offer valuable guidance. While I've exercised caution, I recognise a need to address my laziness with opsec and take meaningful steps to protect my privacy. Time will reveal the results of these efforts. ## Caribbean Slavery amd Centralised Platforms While exploring historical systems of control, I delved into the brutal realities of [New World slavery in the British Caribbean](https://aeon.co/ideas/how-did-slaveholders-in-the-caribbean-maintain-control). Enslaved elites, like drivers, were granted limited privileges to maintain order, creating divisions within the community. This divide-and-rule strategy highlights the fragility of oppressive frameworks, which began to crumble with events like the Hatian Revolution and humanitarian activism. Interestingly, similar dynamics are visible with centralised plaforms like Twitter, LinkedIn, and Instagram. Verified accounts (the "blue checks") act as mordern day 'elites' with perceived freedoms. However, their autonomy is limited by the platforms centralised authority. Challenging the rules risks censorship and cancellation, proving their freedom is an illusion subject to the will of their overseers. Enhancing the argument further for protocols like Nostr to help people win back their freedoms.
@ 2f5de000:2f9bcef1
2024-12-15 16:44:53This Week I immersed myself in Bitcoin from multiple angles-technical, societal and personal. The journey included a marathon 32-hours of listening to [Rabbit Hole Recap (RHR)](https://fountain.fm/show/VDaMppQRUBZioj2XkaLn), an essential resource for Bitcoin insights. It's worth noting that I started from the begining and plan to make my way through the whole catalogue. Marty and Matt's timestamps, along with contributions from their guests, served as my roadmap. Using Fountain to stream, I also streamed sats-a small but extraordinary feature that allows users to stacks sats while compensating cretors directly through fractional donations. ## Revisiting Speculative Attack by Pierre Rochard (2014) Now that [*Speculative Attack Season 2*](https://nakamotoinstitute.org/mempool/speculative-attack-season-2/) *(which I've not read yet)* has been released. I took the time to read Pierre Rochards influential essay, [*Speculative Attack*](https://nakamotoinstitute.org/mempool/speculative-attack/) and reflected on its timeless insights. Rochard argues that Bitcoin adoption isn't dependent on technological advancements or consumer preferences, but on economic realities. As fiat currencies weaken, Bitcoin won't enter the mainstream by persuasion but by necessity. Critics continue to underestimate Bitcoin's inevitability due to their fiat biases and lack of financial insight. This year alone, mainstream media has been compelled to discuss Bitcoin-notably to Trump's endorsement of 'crypto.' Despite their attempts to shape narratives to suit their ideal visions, they've had no choice but to engage with Bitcoin's growing influence.\ \ As Parker aptly puts it 'Gradually, The Suddenly' ## Wassabi Wallet and the Privacy Imperative An RHR interview (from early in the catalogue) with guest Adam Ficsor, CTO and Co-founder of Wassabi Wallet, sparked a deeper consideration of my digital footprint. Like many, I've spent years online neglecting privacy in favour of convenience. The discussion on CoinJoins reminded me of the importance of prioritising privacy, not just romanticising it. Improving operational security (opsec) is now a personal focus. Resources like Jameson's *Cypherpunk Cogitations* and the Bitcoin Optech newsletter offer valuable guidance. While I've exercised caution, I recognise a need to address my laziness with opsec and take meaningful steps to protect my privacy. Time will reveal the results of these efforts. ## Caribbean Slavery amd Centralised Platforms While exploring historical systems of control, I delved into the brutal realities of [New World slavery in the British Caribbean](https://aeon.co/ideas/how-did-slaveholders-in-the-caribbean-maintain-control). Enslaved elites, like drivers, were granted limited privileges to maintain order, creating divisions within the community. This divide-and-rule strategy highlights the fragility of oppressive frameworks, which began to crumble with events like the Hatian Revolution and humanitarian activism. Interestingly, similar dynamics are visible with centralised plaforms like Twitter, LinkedIn, and Instagram. Verified accounts (the "blue checks") act as mordern day 'elites' with perceived freedoms. However, their autonomy is limited by the platforms centralised authority. Challenging the rules risks censorship and cancellation, proving their freedom is an illusion subject to the will of their overseers. Enhancing the argument further for protocols like Nostr to help people win back their freedoms. @ b34b4408:acfb9667
2024-12-15 06:37:47## เฮลิโอเทอราปีคืออะไร?  เฮลิโอเทอราปี (Heliotherapy) หรือการบำบัดด้วยแสงแดด เป็นศาสตร์การแพทย์ที่มีมาแต่โบราณ ชาวกรีกและโรมันใช้แสงแดดในการรักษาโรคและบำรุงสุขภาพ แนวคิดนี้ไม่ใช่เรื่องงมงาย แต่มีหลักการทางวิทยาศาสตร์รองรับ โดยเฉพาะในด้านผลของแสงแดดต่อการทำงานของร่างกายมนุษย์ ## กลไกการทำงานของเฮลิโอเทอราปี ### การกระตุ้นการสร้างวิตามินดี  - แสง UVB ที่มีความยาวคลื่น 290-315 นาโนเมตร จะกระตุ้นให้ผิวหนังเปลี่ยน 7-dehydrocholesterol เป็น previtamin D3 - Previtamin D3 จะถูกเปลี่ยนเป็น vitamin D3 ด้วยความร้อนจากร่างกาย - Vitamin D3 จะถูกตับเปลี่ยนเป็น 25-hydroxyvitamin D - ไตจะเปลี่ยน 25-hydroxyvitamin D เป็น 1,25-dihydroxyvitamin D ซึ่งเป็นรูปแบบที่ใช้งานได้ - กระบวนการนี้ส่งผลต่อ: * การดูดซึมแคลเซียมและฟอสฟอรัสที่ลำไส้ * การสร้างและซ่อมแซมกระดูก * การทำงานของระบบภูมิคุ้มกัน ### การปรับสมดุลฮอร์โมน  - การกระตุ้นเซโรโทนิน: * แสงสว่างผ่านดวงตาไปกระตุ้น Suprachiasmatic Nucleus (SCN) * SCN ส่งสัญญาณไปยัง Pineal Gland * เพิ่มการผลิตเซโรโทนินในช่วงกลางวัน * ลดการเปลี่ยนเซโรโทนินเป็นเมลาโทนิน - การควบคุมเมลาโทนิน: * ช่วงมีแสงสว่าง จะยับยั้งการผลิตเมลาโทนิน * เมื่อไม่มีแสง จะเริ่มผลิตเมลาโทนิน * ช่วยควบคุมวงจรการนอนหลับ * ส่งผลต่อการทำงานของระบบเมตาบอลิซึม - การปรับระดับคอร์ติซอล: * แสงสว่างช่วยกระตุ้นการหลั่งคอร์ติซอลตามธรรมชาติ * ช่วยให้ร่างกายตื่นตัวในช่วงเช้า * ควบคุมระดับน้ำตาลในเลือด * มีผลต่อการตอบสนองต่อความเครียด ### ผลต่อระบบภูมิคุ้มกัน  - การกระตุ้นเซลล์ภูมิคุ้มกัน: * เพิ่มการผลิต T-lymphocytes * กระตุ้นการทำงานของ Natural Killer cells * เพิ่มประสิทธิภาพของ macrophages - การควบคุมการอักเสบ: * ลดการผลิต pro-inflammatory cytokines * เพิ่มการผลิต anti-inflammatory compounds * ช่วยควบคุมการตอบสนองของระบบภูมิคุ้มกัน - การเสริมสร้างการป้องกัน: * กระตุ้นการสร้าง antimicrobial peptides * เพิ่มความสามารถในการต่อต้านเชื้อโรค * ช่วยในการซ่อมแซมเนื้อเยื่อ ### ผลต่อผิวหนัง  - การกระตุ้นเม็ดสีเมลานิน: * ป้องกันการทำลาย DNA จากรังสี UV * ช่วยกรองแสง UV ที่เป็นอันตราย * ปรับสีผิวให้เข้มขึ้นเพื่อป้องกัน - การซ่อมแซมเซลล์: * กระตุ้นกระบวนการ DNA repair * เพิ่มการผลิต collagen * ช่วยในการรักษาแผลและการอักเสบ ### ผลต่อระบบประสาท  - การกระตุ้นการทำงานของสมอง: * เพิ่มการไหลเวียนเลือดในสมอง * กระตุ้นการผลิตสารสื่อประสาท * ปรับปรุงความสามารถในการจดจำ - การควบคุมอารมณ์: * ลดความเครียดผ่านการปรับสมดุลฮอร์โมน * ช่วยลดอาการซึมเศร้า * เพิ่มความรู้สึกผ่อนคลาย ## การประยุกต์ใช้เฮลิโอเทอราปีในการรักษาโรค ### โรคผิวหนัง - ***โรคสะเก็ดเงิน (Psoriasis)***  * กลไก: แสง UV ช่วยลดการเพิ่มจำนวนของเซลล์ผิวหนังที่ผิดปกติ * ผลการรักษา: ลดความหนาของรอยโรค ลดอาการคัน ลดการอักเสบ - ***โรคผื่นภูมิแพ้ผิวหนัง (Atopic Dermatitis)***  * กลไก: ลดการทำงานของเซลล์ภูมิคุ้มกันที่ทำให้เกิดการอักเสบ * ผลการรักษา: บรรเทาอาการคัน ลดการอักเสบ ผิวหนังแข็งแรงขึ้น - ***โรคด่างขาว (Vitiligo)***  * กลไก: กระตุ้นการทำงานของเซลล์สร้างเม็ดสี * ผลการรักษา: กระตุ้นการสร้างเม็ดสีในบริเวณที่เป็นด่างขาว - ***สิวอักเสบ (acne)***  * กลไก : แสง UV ช่วยฆ่าเชื้อแบคทีเรีย * ผลการรักษา : ลดการอักเสบ และส่งเสริมเชื้อดีที่ผิว ### ปัญหาสุขภาพจิต - ***ภาวะซึมเศร้าตามฤดูกาล (SAD)***  * ความถี่: ทุกวัน โดยเฉพาะในฤดูหนาว/ฝน * กลไก: กระตุ้นการผลิตเซโรโทนิน ปรับสมดุลเมลาโทนิน * ผลการรักษา: ลดอาการซึมเศร้า เพิ่มพลังงาน ปรับปรุงการนอน - ***ปัญหาการนอนไม่หลับ หรือ อาการเจ็ทแล็ก (Jet lag)***  * ความถี่: ทุกวัน * กลไก: ปรับนาฬิกาชีวภาพ ควบคุมการผลิตเมลาโทนิน * ผลการรักษา: ช่วยให้นอนหลับง่ายขึ้น ปรับวงจรการนอน - ***ความเครียดและวิตกกังวล***  * วิธีการ: รับแสงแดดอ่อนๆ พร้อมการเดินหรือทำสมาธิ * กลไก: เพิ่มการผลิตเซโรโทนิน ลดระดับคอร์ติซอล * ผลการรักษา: ลดความเครียด เพิ่มความรู้สึกผ่อนคลาย ### โรคกระดูกและข้อ - ***ภาวะกระดูกพรุน***  * วิธีการ: รับแสงแดด เน้นช่วงข้อแขนขาที่มีอาการ * กลไก: เพิ่มการสร้างวิตามินดี ช่วยดูดซึมแคลเซียม * ผลการรักษา: ชะลอการสูญเสียมวลกระดูก เพิ่มความแข็งแรง - ***การอักเสบของข้อ/โรคกระดูกอ่อน (Rickets)/เก็าท์ /รูมาตอยด์***  * วิธีการ: รับแสงแดดบริเวณข้อที่มีปัญหา * กลไก: ลดการอักเสบ เพิ่มการไหลเวียนเลือด * ผลการรักษา: ลดอาการปวด เพิ่มความยืดหยุ่น ### โรคระบบภูมิคุ้มกัน - ***ภูมิแพ้ (Allergies)***  * กลไก: ปรับการตอบสนองของระบบภูมิคุ้มกัน * ผลการรักษา: ลดความรุนแรงของอาการแพ้ -*** โรคภูมิคุ้มกันทำลายตัวเอง***  * กลไก: ปรับสมดุลระบบภูมิคุ้มกัน ลดการอักเสบ * ผลการรักษา: ลดความรุนแรงของอาการ ยืดระยะเวลาระหว่างการกำเริบ ### ระบบเมตาบอลิซึม -*** การควบคุมน้ำหนัก***  * วิธีการ: รับแสงแดด พร้อมการเดินเบาๆ * กลไก: - กระตุ้นการทำงานของต่อมไทรอยด์ - เพิ่มการเผาผลาญไขมันสีน้ำตาล (Brown Fat) - ปรับสมดุลฮอร์โมนที่เกี่ยวข้องกับความหิว * ผลการรักษา: - เพิ่มอัตราการเผาผลาญพื้นฐาน - ควบคุมความอยากอาหารได้ดีขึ้น - ลดการสะสมไขมัน - ***การควบคุมน้ำตาลในเลือด***  * วิธีการ: รับแสงแดดหลังอาหาร * กลไก: - เพิ่มความไวต่ออินซูลิน - ปรับการทำงานของเซลล์ตับอ่อน - ควบคุมการหลั่งฮอร์โมนที่เกี่ยวข้องกับน้ำตาล * ผลการรักษา: - ระดับน้ำตาลในเลือดคงที่มากขึ้น - ลดความเสี่ยงภาวะน้ำตาลต่ำ/สูง - เพิ่มประสิทธิภาพการใช้น้ำตาลของเซลล์ - ***การทำงานของตับ***  * กลไก: - กระตุ้นการสร้างเอนไซม์ในตับ - เพิ่มการไหลเวียนเลือดที่ตับ - ช่วยในกระบวนการดีท็อกซ์ * ผลการรักษา: - เพิ่มประสิทธิภาพการทำงานของตับ - ลดการสะสมไขมันในตับ - ช่วยการขจัดสารพิษ - ***ระบบย่อยอาหาร***  * กลไก: - กระตุ้นการผลิตน้ำย่อย - ปรับสมดุลแบคทีเรียในลำไส้ - เพิ่มการเคลื่อนไหวของลำไส้ * ผลการรักษา: - ระบบย่อยอาหารทำงานดีขึ้น - ลดอาการท้องอืด ท้องเฟ้อ - เพิ่มการดูดซึมสารอาหาร ข้อควรระวังในการรักษา: - ปรึกษาผู้เชี่ยวชาญหรือผู้ที่เข้าใจเรื่อง Heliotherapy หากมีโรคประจำตัว - เริ่มจากระยะเวลาสั้นๆ แล้วค่อยๆ เพิ่ม - ควรสวมเสื้อผ้าที่เปิดผิวหนังให้สัมผัสแสงแดดโดยตรง - ไม่ควรทาครีมกันแดดในบริเวณที่ต้องการรับการรักษา - หากมีอาการผิวแดง ร้อนผิว ให้หยุดรับแสงแดด - หยุดทันทีเมื่อมีอาการแพ้หรือระคายเคือง - ระวังเป็นพิเศษในผู้ที่มีประวัติแพ้แดด ## ความจริงที่ถูกบิดเบือน: ทำไมเราถึงกลัวแดด? ### อิทธิพลของอุตสาหกรรมความงามและการแพทย์  #### อุตสาหกรรมเครื่องสำอางและผลิตภัณฑ์ดูแลผิว - ตลาดผลิตภัณฑ์กันแดด * มูลค่าตลาดทั่วโลกกว่า 50,000 ล้านดอลลาร์ * อัตราการเติบโตเฉลี่ย 8-10% ต่อปี * ผลิตภัณฑ์หลากหลายระดับราคา * การพัฒนาสูตรใหม่ๆ เพื่อสร้างความต้องการ - กลยุทธ์การสร้างความต้องการ * การโฆษณาที่สร้างความกลัว - ใช้ภาพก่อน-หลังที่เกินจริง - นำเสนอผลการวิจัยแบบเลือกข้าง - สร้างความกังวลเรื่องริ้วรอยและความชรา - ใช้คำศัพท์ทางวิทยาศาสตร์ที่ซับซ้อน * การสร้างความเชื่อผิดๆ - "ต้องทาครีมกันแดดทุกวัน แม้อยู่ในร่ม" - "ยิ่ง SPF สูง ยิ่งดี" - "แสงแดดเป็นสาเหตุหลักของริ้วรอย" - "ผิวขาวเท่านั้นที่สวยและดูดี" #### อุตสาหกรรมอาหารเสริม - ตลาดผลิตภัณฑ์วิตามินดี * การเติบโตของตลาดอาหารเสริมวิตามินดี * การผลักดันให้ใช้อาหารเสริมแทนแสงแดด * ราคาที่สูงเกินความจำเป็น * การสร้างความเชื่อว่าอาหารเสริมปลอดภัยกว่า - กลยุทธ์ทางการตลาด * การใช้ผู้เชี่ยวชาญทางการแพทย์รับรอง * การนำเสนอผลการวิจัยที่สนับสนุนผลิตภัณฑ์ * การสร้างความกลัวเรื่องการขาดวิตามินดี * การเชื่อมโยงกับปัญหาสุขภาพต่างๆ #### อุตสาหกรรมการแพทย์และความงาม - คลินิกผิวพรรณและความงาม * การให้บริการทรีตเมนต์หลบแดด * การรักษาผิวคล้ำเสียจากแดด * การฉีดวิตามินและอาหารเสริม * ทรีตเมนต์ฟื้นฟูผิวราคาแพง - การแพทย์เฉพาะทาง * การรักษาผิวหนังที่เน้นยาและเคมีภัณฑ์ * การผ่าตัดและเลเซอร์เพื่อความขาว * การรักษาริ้วรอยด้วยวิธีราคาแพง * การละเลยวิธีธรรมชาติบำบัด #### เครือข่ายผลประโยชน์ทางธุรกิจ - ความเชื่อมโยงระหว่างอุตสาหกรรม * บริษัทยาที่ผลิตทั้งครีมกันแดดและอาหารเสริม * คลินิกที่จำหน่ายผลิตภัณฑ์ของตัวเอง * การร่วมมือระหว่างผู้เชี่ยวชาญและบริษัทผลิตภัณฑ์ * เครือข่ายการตลาดและการโฆษณา - ผลประโยชน์ทับซ้อน * ผู้เชี่ยวชาญที่เป็นพรีเซ็นเตอร์ผลิตภัณฑ์ * งานวิจัยที่ได้รับทุนจากบริษัทผลิตภัณฑ์ * การให้ข้อมูลที่เอื้อประโยชน์ทางธุรกิจ * การปิดบังข้อมูลที่อาจกระทบยอดขาย #### ผลกระทบต่อผู้บริโภค - ด้านเศรษฐกิจ * ค่าใช้จ่ายสูงในการซื้อผลิตภัณฑ์ * การเสียเงินกับทรีตเมนต์ที่ไม่จำเป็น * ภาระค่าใช้จ่ายระยะยาว * การลงทุนที่ไม่คุ้มค่ากับผลลัพธ์ - ด้านสุขภาพ * การขาดแสงแดดที่จำเป็น * ผลข้างเคียงจากผลิตภัณฑ์ * การพึ่งพาผลิตภัณฑ์มากเกินไป * ปัญหาสุขภาพที่เกิดจากการหลีกเลี่ยงแสงแดด ### อิทธิพลทางสังคมและวัฒนธรรม - ค่านิยมผิวขาวในสังคมเอเชีย * รากเหง้าทางประวัติศาสตร์ของการแบ่งชนชั้น * อิทธิพลของสื่อและดารานักแสดง * ความเชื่อมโยงระหว่างผิวขาวกับความสำเร็จ * แรงกดดันทางสังคมในการรักษาผิวให้ขาว - การเปลี่ยนแปลงวิถีชีวิต * การทำงานในออฟฟิศเป็นหลัก * การใช้ชีวิตในห้างสรรพสินค้าและอาคาร * การลดลงของกิจกรรมกลางแจ้ง * ความเชื่อว่าการอยู่ในร่มปลอดภัยกว่า ### การบิดเบือนข้อมูลทางการแพทย์ #### การนำเสนอข้อมูลที่ไม่สมดุล - การเน้นย้ำความเสี่ยงมะเร็งผิวหนัง * นำเสนอสถิติแบบบิดเบือน * ไม่แยกแยะระหว่างการรับแดดที่เหมาะสมกับการรับแดดมากเกินไป * ละเลยการพูดถึงปัจจัยเสี่ยงอื่นๆ * ไม่ให้ข้อมูลว่าการรับแดดอย่างเหมาะสมอาจช่วยป้องกันมะเร็งบางชนิด - การละเลยประโยชน์ของแสง UV * ไม่พูดถึงบทบาทของ UV ในการฆ่าเชื้อโรค * ปิดบังข้อมูลเรื่องการสร้างวิตามินดีตามธรรมชาติ * ไม่กล่าวถึงประโยชน์ต่อระบบภูมิคุ้มกัน * ละเลยผลดีต่อสุขภาพจิต #### การสร้างความเข้าใจผิดเกี่ยวกับวิตามินดี - ความเชื่อเรื่องอาหารเสริม * สร้างความเชื่อว่าอาหารเสริมดีกว่าแสงแดด * ไม่เปิดเผยข้อจำกัดของการดูดซึมวิตามินดีจากอาหารเสริม * ละเลยการพูดถึงผลข้างเคียงของการใช้อาหารเสริมเกินขนาด * ไม่อธิบายความแตกต่างระหว่างวิตามินดีจากธรรมชาติและสังเคราะห์ - การวิจัยที่มีอคติ * การศึกษาที่ได้รับทุนจากบริษัทผลิตภัณฑ์กันแดด * เลือกนำเสนอผลการวิจัยเฉพาะด้านลบ * ขาดการศึกษาระยะยาวเกี่ยวกับผลดีของแสงแดด * ไม่เปิดเผยผลประโยชน์ทับซ้อนในงานวิจัย #### การบิดเบือนในการรักษาทางการแพทย์ - แนวทางการรักษาที่พึ่งพายา * เน้นการใช้ยามากกว่าวิธีธรรมชาติ * ละเลยการแนะนำเรื่องการรับแสงแดด * สั่งจ่ายอาหารเสริมโดยไม่จำเป็น * ไม่ให้ความสำคัญกับการปรับพฤติกรรม - การวินิจฉัยที่ไม่ครอบคลุม * ไม่ตรวจหาสาเหตุจากการขาดแสงแดด * มองข้ามความสัมพันธ์ระหว่างแสงแดดกับโรคต่างๆ * ไม่ซักประวัติเรื่องการรับแสงแดด * ละเลยการประเมินวิถีชีวิตที่หลีกเลี่ยงแสงแดด #### ผลกระทบต่อการรักษา - การรักษาที่ไม่มีประสิทธิภาพ * การใช้ยาเกินความจำเป็น * ค่าใช้จ่ายที่สูงขึ้นโดยไม่จำเป็น * ผลข้างเคียงจากการรักษาที่ไม่เหมาะสม * การรักษาที่ไม่แก้ปัญหาที่สาเหตุ - ปัญหาสุขภาพที่ตามมา * โรคขาดวิตามินดีที่เพิ่มขึ้น * ปัญหาสุขภาพจิตจากการหลีกเลี่ยงแสงแดด * ภาวะแทรกซ้อนจากการใช้ยาระยะยาว * คุณภาพชีวิตที่ลดลง ### ผลกระทบต่อสุขภาพจากความกลัวแดด - ปัญหาการขาดวิตามินดี * การระบาดของภาวะขาดวิตามินดีในประชากร * ผลกระทบต่อสุขภาพกระดูก * ความเสี่ยงต่อโรคภูมิแพ้และภูมิคุ้มกัน * ปัญหาสุขภาพจิตที่เพิ่มขึ้น - ผลกระทบทางสังคมและจิตใจ * ความวิตกกังวลเกี่ยวกับการออกนอกบ้าน * การจำกัดกิจกรรมกลางแจ้ง * ความเครียดจากการต้องดูแลผิวมากเกินไป * ค่าใช้จ่ายที่สูงขึ้นจากผลิตภัณฑ์ป้องกันแดด ### การแก้ไขความเข้าใจผิด - การให้ข้อมูลที่สมดุล * นำเสนอทั้งประโยชน์และความเสี่ยง * แนะนำวิธีการรับแดดที่ปลอดภัย * สร้างความเข้าใจเรื่องความพอดี * ให้ความรู้เรื่องการป้องกันที่เหมาะสม - การปรับเปลี่ยนทัศนคติ * เปลี่ยนจากการ "กลัวแดด" เป็น "เข้าใจแดด" * สร้างความตระหนักถึงความสำคัญของแสงแดดต่อสุขภาพ * ส่งเสริมการใช้ชีวิตที่สมดุลกับธรรมชาติ * ลดอิทธิพลของค่านิยมผิวขาว ## หลักการรับแสงแดดที่ถูกต้องตามแนวทางเฮลิโอเทอราปี  ### ระยะเวลาและความถี่ - เริ่มจากวันละ 10-15 นาที - ค่อยๆ เพิ่มเวลา ### วิธีการที่ถูกต้อง - เปิดผิวให้สัมผัสแดดพอประมาณ - ไม่ใช้สารกันแดด - สังเกตการตอบสนองของร่างกาย - ปรับตามสภาพอากาศและฤดูกาล ## การประยุกต์ใช้เฮลิโอเทอราปีในชีวิตประจำวัน  ### กิจกรรมที่แนะนำ - เดินเช้าหรือเย็น - ทำสวนในช่วงเวลาที่เหมาะสม - ออกกำลังกายกลางแจ้งเบาๆ ### การผสมผสานกับการดูแลสุขภาพอื่นๆ - การออกกำลังกาย - การทำสมาธิกลางแจ้ง - การทำกิจกรรมผ่อนคลาย ## บทสรุป: กลับสู่สมดุลธรรมชาติ เฮลิโอเทอราปีไม่เพียงเป็นการรักษาโรค แต่ยังเป็นแนวทางในการดูแลสุขภาพแบบองค์รวม การเข้าใจหลักการของเฮลิโอเทอราปีช่วยให้เราตระหนักว่า แสงแดดเป็นส่วนสำคัญของชีวิตที่สมดุล การหวนกลับมาใส่ใจการรับแสงแดดอย่างถูกวิธี จึงเป็นก้าวสำคัญสู่การมีสุขภาพที่ดีอย่างยั่งยืน แสงแดดเป็น "เพื่อน" ไม่ใช่ "ศัตรู" ของสุขภาพ หากรู้จักใช้ให้เหมาะสม Don’t trust , (must) Verify ศึกษาเพิ่มเติมเรื่อง Heliotherapy : https://youtu.be/q5EX5XrR-2A ...................................... ข้อมูลสุขภาพดีๆที่ไม่มีค่าใช้จ่าย https://www.youtube.com/@fastingfatdentist . หากสนใจวิธีการดูแลสุขภาพตามแบบ IFF ปรึกษาส่วนตัว inbox มาสอบถามที่เพจ"หมออ้วนในดงลดน้ำหนัก"หรือ" fastingfatdentist"ได้เลยครับ . #ความน่ากลัวในการดูแลสุขภาพคือการที่เชื่อโดยไม่มีความรู้ . . #IFF #IFF_talk #intermittentfasting #keto #Lowcarb #CD #plantbased #RemissionDiabetes #ร่างกายเราคือธรรมชาติไม่ใช่ยา #เบาหวานหายได้โดยไม่ต้องใช้ยา #หมอไหวของหมอแบบนี
@ b34b4408:acfb9667
2024-12-15 06:37:47## เฮลิโอเทอราปีคืออะไร?  เฮลิโอเทอราปี (Heliotherapy) หรือการบำบัดด้วยแสงแดด เป็นศาสตร์การแพทย์ที่มีมาแต่โบราณ ชาวกรีกและโรมันใช้แสงแดดในการรักษาโรคและบำรุงสุขภาพ แนวคิดนี้ไม่ใช่เรื่องงมงาย แต่มีหลักการทางวิทยาศาสตร์รองรับ โดยเฉพาะในด้านผลของแสงแดดต่อการทำงานของร่างกายมนุษย์ ## กลไกการทำงานของเฮลิโอเทอราปี ### การกระตุ้นการสร้างวิตามินดี  - แสง UVB ที่มีความยาวคลื่น 290-315 นาโนเมตร จะกระตุ้นให้ผิวหนังเปลี่ยน 7-dehydrocholesterol เป็น previtamin D3 - Previtamin D3 จะถูกเปลี่ยนเป็น vitamin D3 ด้วยความร้อนจากร่างกาย - Vitamin D3 จะถูกตับเปลี่ยนเป็น 25-hydroxyvitamin D - ไตจะเปลี่ยน 25-hydroxyvitamin D เป็น 1,25-dihydroxyvitamin D ซึ่งเป็นรูปแบบที่ใช้งานได้ - กระบวนการนี้ส่งผลต่อ: * การดูดซึมแคลเซียมและฟอสฟอรัสที่ลำไส้ * การสร้างและซ่อมแซมกระดูก * การทำงานของระบบภูมิคุ้มกัน ### การปรับสมดุลฮอร์โมน  - การกระตุ้นเซโรโทนิน: * แสงสว่างผ่านดวงตาไปกระตุ้น Suprachiasmatic Nucleus (SCN) * SCN ส่งสัญญาณไปยัง Pineal Gland * เพิ่มการผลิตเซโรโทนินในช่วงกลางวัน * ลดการเปลี่ยนเซโรโทนินเป็นเมลาโทนิน - การควบคุมเมลาโทนิน: * ช่วงมีแสงสว่าง จะยับยั้งการผลิตเมลาโทนิน * เมื่อไม่มีแสง จะเริ่มผลิตเมลาโทนิน * ช่วยควบคุมวงจรการนอนหลับ * ส่งผลต่อการทำงานของระบบเมตาบอลิซึม - การปรับระดับคอร์ติซอล: * แสงสว่างช่วยกระตุ้นการหลั่งคอร์ติซอลตามธรรมชาติ * ช่วยให้ร่างกายตื่นตัวในช่วงเช้า * ควบคุมระดับน้ำตาลในเลือด * มีผลต่อการตอบสนองต่อความเครียด ### ผลต่อระบบภูมิคุ้มกัน  - การกระตุ้นเซลล์ภูมิคุ้มกัน: * เพิ่มการผลิต T-lymphocytes * กระตุ้นการทำงานของ Natural Killer cells * เพิ่มประสิทธิภาพของ macrophages - การควบคุมการอักเสบ: * ลดการผลิต pro-inflammatory cytokines * เพิ่มการผลิต anti-inflammatory compounds * ช่วยควบคุมการตอบสนองของระบบภูมิคุ้มกัน - การเสริมสร้างการป้องกัน: * กระตุ้นการสร้าง antimicrobial peptides * เพิ่มความสามารถในการต่อต้านเชื้อโรค * ช่วยในการซ่อมแซมเนื้อเยื่อ ### ผลต่อผิวหนัง  - การกระตุ้นเม็ดสีเมลานิน: * ป้องกันการทำลาย DNA จากรังสี UV * ช่วยกรองแสง UV ที่เป็นอันตราย * ปรับสีผิวให้เข้มขึ้นเพื่อป้องกัน - การซ่อมแซมเซลล์: * กระตุ้นกระบวนการ DNA repair * เพิ่มการผลิต collagen * ช่วยในการรักษาแผลและการอักเสบ ### ผลต่อระบบประสาท  - การกระตุ้นการทำงานของสมอง: * เพิ่มการไหลเวียนเลือดในสมอง * กระตุ้นการผลิตสารสื่อประสาท * ปรับปรุงความสามารถในการจดจำ - การควบคุมอารมณ์: * ลดความเครียดผ่านการปรับสมดุลฮอร์โมน * ช่วยลดอาการซึมเศร้า * เพิ่มความรู้สึกผ่อนคลาย ## การประยุกต์ใช้เฮลิโอเทอราปีในการรักษาโรค ### โรคผิวหนัง - ***โรคสะเก็ดเงิน (Psoriasis)***  * กลไก: แสง UV ช่วยลดการเพิ่มจำนวนของเซลล์ผิวหนังที่ผิดปกติ * ผลการรักษา: ลดความหนาของรอยโรค ลดอาการคัน ลดการอักเสบ - ***โรคผื่นภูมิแพ้ผิวหนัง (Atopic Dermatitis)***  * กลไก: ลดการทำงานของเซลล์ภูมิคุ้มกันที่ทำให้เกิดการอักเสบ * ผลการรักษา: บรรเทาอาการคัน ลดการอักเสบ ผิวหนังแข็งแรงขึ้น - ***โรคด่างขาว (Vitiligo)***  * กลไก: กระตุ้นการทำงานของเซลล์สร้างเม็ดสี * ผลการรักษา: กระตุ้นการสร้างเม็ดสีในบริเวณที่เป็นด่างขาว - ***สิวอักเสบ (acne)***  * กลไก : แสง UV ช่วยฆ่าเชื้อแบคทีเรีย * ผลการรักษา : ลดการอักเสบ และส่งเสริมเชื้อดีที่ผิว ### ปัญหาสุขภาพจิต - ***ภาวะซึมเศร้าตามฤดูกาล (SAD)***  * ความถี่: ทุกวัน โดยเฉพาะในฤดูหนาว/ฝน * กลไก: กระตุ้นการผลิตเซโรโทนิน ปรับสมดุลเมลาโทนิน * ผลการรักษา: ลดอาการซึมเศร้า เพิ่มพลังงาน ปรับปรุงการนอน - ***ปัญหาการนอนไม่หลับ หรือ อาการเจ็ทแล็ก (Jet lag)***  * ความถี่: ทุกวัน * กลไก: ปรับนาฬิกาชีวภาพ ควบคุมการผลิตเมลาโทนิน * ผลการรักษา: ช่วยให้นอนหลับง่ายขึ้น ปรับวงจรการนอน - ***ความเครียดและวิตกกังวล***  * วิธีการ: รับแสงแดดอ่อนๆ พร้อมการเดินหรือทำสมาธิ * กลไก: เพิ่มการผลิตเซโรโทนิน ลดระดับคอร์ติซอล * ผลการรักษา: ลดความเครียด เพิ่มความรู้สึกผ่อนคลาย ### โรคกระดูกและข้อ - ***ภาวะกระดูกพรุน***  * วิธีการ: รับแสงแดด เน้นช่วงข้อแขนขาที่มีอาการ * กลไก: เพิ่มการสร้างวิตามินดี ช่วยดูดซึมแคลเซียม * ผลการรักษา: ชะลอการสูญเสียมวลกระดูก เพิ่มความแข็งแรง - ***การอักเสบของข้อ/โรคกระดูกอ่อน (Rickets)/เก็าท์ /รูมาตอยด์***  * วิธีการ: รับแสงแดดบริเวณข้อที่มีปัญหา * กลไก: ลดการอักเสบ เพิ่มการไหลเวียนเลือด * ผลการรักษา: ลดอาการปวด เพิ่มความยืดหยุ่น ### โรคระบบภูมิคุ้มกัน - ***ภูมิแพ้ (Allergies)***  * กลไก: ปรับการตอบสนองของระบบภูมิคุ้มกัน * ผลการรักษา: ลดความรุนแรงของอาการแพ้ -*** โรคภูมิคุ้มกันทำลายตัวเอง***  * กลไก: ปรับสมดุลระบบภูมิคุ้มกัน ลดการอักเสบ * ผลการรักษา: ลดความรุนแรงของอาการ ยืดระยะเวลาระหว่างการกำเริบ ### ระบบเมตาบอลิซึม -*** การควบคุมน้ำหนัก***  * วิธีการ: รับแสงแดด พร้อมการเดินเบาๆ * กลไก: - กระตุ้นการทำงานของต่อมไทรอยด์ - เพิ่มการเผาผลาญไขมันสีน้ำตาล (Brown Fat) - ปรับสมดุลฮอร์โมนที่เกี่ยวข้องกับความหิว * ผลการรักษา: - เพิ่มอัตราการเผาผลาญพื้นฐาน - ควบคุมความอยากอาหารได้ดีขึ้น - ลดการสะสมไขมัน - ***การควบคุมน้ำตาลในเลือด***  * วิธีการ: รับแสงแดดหลังอาหาร * กลไก: - เพิ่มความไวต่ออินซูลิน - ปรับการทำงานของเซลล์ตับอ่อน - ควบคุมการหลั่งฮอร์โมนที่เกี่ยวข้องกับน้ำตาล * ผลการรักษา: - ระดับน้ำตาลในเลือดคงที่มากขึ้น - ลดความเสี่ยงภาวะน้ำตาลต่ำ/สูง - เพิ่มประสิทธิภาพการใช้น้ำตาลของเซลล์ - ***การทำงานของตับ***  * กลไก: - กระตุ้นการสร้างเอนไซม์ในตับ - เพิ่มการไหลเวียนเลือดที่ตับ - ช่วยในกระบวนการดีท็อกซ์ * ผลการรักษา: - เพิ่มประสิทธิภาพการทำงานของตับ - ลดการสะสมไขมันในตับ - ช่วยการขจัดสารพิษ - ***ระบบย่อยอาหาร***  * กลไก: - กระตุ้นการผลิตน้ำย่อย - ปรับสมดุลแบคทีเรียในลำไส้ - เพิ่มการเคลื่อนไหวของลำไส้ * ผลการรักษา: - ระบบย่อยอาหารทำงานดีขึ้น - ลดอาการท้องอืด ท้องเฟ้อ - เพิ่มการดูดซึมสารอาหาร ข้อควรระวังในการรักษา: - ปรึกษาผู้เชี่ยวชาญหรือผู้ที่เข้าใจเรื่อง Heliotherapy หากมีโรคประจำตัว - เริ่มจากระยะเวลาสั้นๆ แล้วค่อยๆ เพิ่ม - ควรสวมเสื้อผ้าที่เปิดผิวหนังให้สัมผัสแสงแดดโดยตรง - ไม่ควรทาครีมกันแดดในบริเวณที่ต้องการรับการรักษา - หากมีอาการผิวแดง ร้อนผิว ให้หยุดรับแสงแดด - หยุดทันทีเมื่อมีอาการแพ้หรือระคายเคือง - ระวังเป็นพิเศษในผู้ที่มีประวัติแพ้แดด ## ความจริงที่ถูกบิดเบือน: ทำไมเราถึงกลัวแดด? ### อิทธิพลของอุตสาหกรรมความงามและการแพทย์  #### อุตสาหกรรมเครื่องสำอางและผลิตภัณฑ์ดูแลผิว - ตลาดผลิตภัณฑ์กันแดด * มูลค่าตลาดทั่วโลกกว่า 50,000 ล้านดอลลาร์ * อัตราการเติบโตเฉลี่ย 8-10% ต่อปี * ผลิตภัณฑ์หลากหลายระดับราคา * การพัฒนาสูตรใหม่ๆ เพื่อสร้างความต้องการ - กลยุทธ์การสร้างความต้องการ * การโฆษณาที่สร้างความกลัว - ใช้ภาพก่อน-หลังที่เกินจริง - นำเสนอผลการวิจัยแบบเลือกข้าง - สร้างความกังวลเรื่องริ้วรอยและความชรา - ใช้คำศัพท์ทางวิทยาศาสตร์ที่ซับซ้อน * การสร้างความเชื่อผิดๆ - "ต้องทาครีมกันแดดทุกวัน แม้อยู่ในร่ม" - "ยิ่ง SPF สูง ยิ่งดี" - "แสงแดดเป็นสาเหตุหลักของริ้วรอย" - "ผิวขาวเท่านั้นที่สวยและดูดี" #### อุตสาหกรรมอาหารเสริม - ตลาดผลิตภัณฑ์วิตามินดี * การเติบโตของตลาดอาหารเสริมวิตามินดี * การผลักดันให้ใช้อาหารเสริมแทนแสงแดด * ราคาที่สูงเกินความจำเป็น * การสร้างความเชื่อว่าอาหารเสริมปลอดภัยกว่า - กลยุทธ์ทางการตลาด * การใช้ผู้เชี่ยวชาญทางการแพทย์รับรอง * การนำเสนอผลการวิจัยที่สนับสนุนผลิตภัณฑ์ * การสร้างความกลัวเรื่องการขาดวิตามินดี * การเชื่อมโยงกับปัญหาสุขภาพต่างๆ #### อุตสาหกรรมการแพทย์และความงาม - คลินิกผิวพรรณและความงาม * การให้บริการทรีตเมนต์หลบแดด * การรักษาผิวคล้ำเสียจากแดด * การฉีดวิตามินและอาหารเสริม * ทรีตเมนต์ฟื้นฟูผิวราคาแพง - การแพทย์เฉพาะทาง * การรักษาผิวหนังที่เน้นยาและเคมีภัณฑ์ * การผ่าตัดและเลเซอร์เพื่อความขาว * การรักษาริ้วรอยด้วยวิธีราคาแพง * การละเลยวิธีธรรมชาติบำบัด #### เครือข่ายผลประโยชน์ทางธุรกิจ - ความเชื่อมโยงระหว่างอุตสาหกรรม * บริษัทยาที่ผลิตทั้งครีมกันแดดและอาหารเสริม * คลินิกที่จำหน่ายผลิตภัณฑ์ของตัวเอง * การร่วมมือระหว่างผู้เชี่ยวชาญและบริษัทผลิตภัณฑ์ * เครือข่ายการตลาดและการโฆษณา - ผลประโยชน์ทับซ้อน * ผู้เชี่ยวชาญที่เป็นพรีเซ็นเตอร์ผลิตภัณฑ์ * งานวิจัยที่ได้รับทุนจากบริษัทผลิตภัณฑ์ * การให้ข้อมูลที่เอื้อประโยชน์ทางธุรกิจ * การปิดบังข้อมูลที่อาจกระทบยอดขาย #### ผลกระทบต่อผู้บริโภค - ด้านเศรษฐกิจ * ค่าใช้จ่ายสูงในการซื้อผลิตภัณฑ์ * การเสียเงินกับทรีตเมนต์ที่ไม่จำเป็น * ภาระค่าใช้จ่ายระยะยาว * การลงทุนที่ไม่คุ้มค่ากับผลลัพธ์ - ด้านสุขภาพ * การขาดแสงแดดที่จำเป็น * ผลข้างเคียงจากผลิตภัณฑ์ * การพึ่งพาผลิตภัณฑ์มากเกินไป * ปัญหาสุขภาพที่เกิดจากการหลีกเลี่ยงแสงแดด ### อิทธิพลทางสังคมและวัฒนธรรม - ค่านิยมผิวขาวในสังคมเอเชีย * รากเหง้าทางประวัติศาสตร์ของการแบ่งชนชั้น * อิทธิพลของสื่อและดารานักแสดง * ความเชื่อมโยงระหว่างผิวขาวกับความสำเร็จ * แรงกดดันทางสังคมในการรักษาผิวให้ขาว - การเปลี่ยนแปลงวิถีชีวิต * การทำงานในออฟฟิศเป็นหลัก * การใช้ชีวิตในห้างสรรพสินค้าและอาคาร * การลดลงของกิจกรรมกลางแจ้ง * ความเชื่อว่าการอยู่ในร่มปลอดภัยกว่า ### การบิดเบือนข้อมูลทางการแพทย์ #### การนำเสนอข้อมูลที่ไม่สมดุล - การเน้นย้ำความเสี่ยงมะเร็งผิวหนัง * นำเสนอสถิติแบบบิดเบือน * ไม่แยกแยะระหว่างการรับแดดที่เหมาะสมกับการรับแดดมากเกินไป * ละเลยการพูดถึงปัจจัยเสี่ยงอื่นๆ * ไม่ให้ข้อมูลว่าการรับแดดอย่างเหมาะสมอาจช่วยป้องกันมะเร็งบางชนิด - การละเลยประโยชน์ของแสง UV * ไม่พูดถึงบทบาทของ UV ในการฆ่าเชื้อโรค * ปิดบังข้อมูลเรื่องการสร้างวิตามินดีตามธรรมชาติ * ไม่กล่าวถึงประโยชน์ต่อระบบภูมิคุ้มกัน * ละเลยผลดีต่อสุขภาพจิต #### การสร้างความเข้าใจผิดเกี่ยวกับวิตามินดี - ความเชื่อเรื่องอาหารเสริม * สร้างความเชื่อว่าอาหารเสริมดีกว่าแสงแดด * ไม่เปิดเผยข้อจำกัดของการดูดซึมวิตามินดีจากอาหารเสริม * ละเลยการพูดถึงผลข้างเคียงของการใช้อาหารเสริมเกินขนาด * ไม่อธิบายความแตกต่างระหว่างวิตามินดีจากธรรมชาติและสังเคราะห์ - การวิจัยที่มีอคติ * การศึกษาที่ได้รับทุนจากบริษัทผลิตภัณฑ์กันแดด * เลือกนำเสนอผลการวิจัยเฉพาะด้านลบ * ขาดการศึกษาระยะยาวเกี่ยวกับผลดีของแสงแดด * ไม่เปิดเผยผลประโยชน์ทับซ้อนในงานวิจัย #### การบิดเบือนในการรักษาทางการแพทย์ - แนวทางการรักษาที่พึ่งพายา * เน้นการใช้ยามากกว่าวิธีธรรมชาติ * ละเลยการแนะนำเรื่องการรับแสงแดด * สั่งจ่ายอาหารเสริมโดยไม่จำเป็น * ไม่ให้ความสำคัญกับการปรับพฤติกรรม - การวินิจฉัยที่ไม่ครอบคลุม * ไม่ตรวจหาสาเหตุจากการขาดแสงแดด * มองข้ามความสัมพันธ์ระหว่างแสงแดดกับโรคต่างๆ * ไม่ซักประวัติเรื่องการรับแสงแดด * ละเลยการประเมินวิถีชีวิตที่หลีกเลี่ยงแสงแดด #### ผลกระทบต่อการรักษา - การรักษาที่ไม่มีประสิทธิภาพ * การใช้ยาเกินความจำเป็น * ค่าใช้จ่ายที่สูงขึ้นโดยไม่จำเป็น * ผลข้างเคียงจากการรักษาที่ไม่เหมาะสม * การรักษาที่ไม่แก้ปัญหาที่สาเหตุ - ปัญหาสุขภาพที่ตามมา * โรคขาดวิตามินดีที่เพิ่มขึ้น * ปัญหาสุขภาพจิตจากการหลีกเลี่ยงแสงแดด * ภาวะแทรกซ้อนจากการใช้ยาระยะยาว * คุณภาพชีวิตที่ลดลง ### ผลกระทบต่อสุขภาพจากความกลัวแดด - ปัญหาการขาดวิตามินดี * การระบาดของภาวะขาดวิตามินดีในประชากร * ผลกระทบต่อสุขภาพกระดูก * ความเสี่ยงต่อโรคภูมิแพ้และภูมิคุ้มกัน * ปัญหาสุขภาพจิตที่เพิ่มขึ้น - ผลกระทบทางสังคมและจิตใจ * ความวิตกกังวลเกี่ยวกับการออกนอกบ้าน * การจำกัดกิจกรรมกลางแจ้ง * ความเครียดจากการต้องดูแลผิวมากเกินไป * ค่าใช้จ่ายที่สูงขึ้นจากผลิตภัณฑ์ป้องกันแดด ### การแก้ไขความเข้าใจผิด - การให้ข้อมูลที่สมดุล * นำเสนอทั้งประโยชน์และความเสี่ยง * แนะนำวิธีการรับแดดที่ปลอดภัย * สร้างความเข้าใจเรื่องความพอดี * ให้ความรู้เรื่องการป้องกันที่เหมาะสม - การปรับเปลี่ยนทัศนคติ * เปลี่ยนจากการ "กลัวแดด" เป็น "เข้าใจแดด" * สร้างความตระหนักถึงความสำคัญของแสงแดดต่อสุขภาพ * ส่งเสริมการใช้ชีวิตที่สมดุลกับธรรมชาติ * ลดอิทธิพลของค่านิยมผิวขาว ## หลักการรับแสงแดดที่ถูกต้องตามแนวทางเฮลิโอเทอราปี  ### ระยะเวลาและความถี่ - เริ่มจากวันละ 10-15 นาที - ค่อยๆ เพิ่มเวลา ### วิธีการที่ถูกต้อง - เปิดผิวให้สัมผัสแดดพอประมาณ - ไม่ใช้สารกันแดด - สังเกตการตอบสนองของร่างกาย - ปรับตามสภาพอากาศและฤดูกาล ## การประยุกต์ใช้เฮลิโอเทอราปีในชีวิตประจำวัน  ### กิจกรรมที่แนะนำ - เดินเช้าหรือเย็น - ทำสวนในช่วงเวลาที่เหมาะสม - ออกกำลังกายกลางแจ้งเบาๆ ### การผสมผสานกับการดูแลสุขภาพอื่นๆ - การออกกำลังกาย - การทำสมาธิกลางแจ้ง - การทำกิจกรรมผ่อนคลาย ## บทสรุป: กลับสู่สมดุลธรรมชาติ เฮลิโอเทอราปีไม่เพียงเป็นการรักษาโรค แต่ยังเป็นแนวทางในการดูแลสุขภาพแบบองค์รวม การเข้าใจหลักการของเฮลิโอเทอราปีช่วยให้เราตระหนักว่า แสงแดดเป็นส่วนสำคัญของชีวิตที่สมดุล การหวนกลับมาใส่ใจการรับแสงแดดอย่างถูกวิธี จึงเป็นก้าวสำคัญสู่การมีสุขภาพที่ดีอย่างยั่งยืน แสงแดดเป็น "เพื่อน" ไม่ใช่ "ศัตรู" ของสุขภาพ หากรู้จักใช้ให้เหมาะสม Don’t trust , (must) Verify ศึกษาเพิ่มเติมเรื่อง Heliotherapy : https://youtu.be/q5EX5XrR-2A ...................................... ข้อมูลสุขภาพดีๆที่ไม่มีค่าใช้จ่าย https://www.youtube.com/@fastingfatdentist . หากสนใจวิธีการดูแลสุขภาพตามแบบ IFF ปรึกษาส่วนตัว inbox มาสอบถามที่เพจ"หมออ้วนในดงลดน้ำหนัก"หรือ" fastingfatdentist"ได้เลยครับ . #ความน่ากลัวในการดูแลสุขภาพคือการที่เชื่อโดยไม่มีความรู้ . . #IFF #IFF_talk #intermittentfasting #keto #Lowcarb #CD #plantbased #RemissionDiabetes #ร่างกายเราคือธรรมชาติไม่ใช่ยา #เบาหวานหายได้โดยไม่ต้องใช้ยา #หมอไหวของหมอแบบนี @ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night. I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case. We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money. The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially). The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines. Part of that battle is self custody, part is tax and part are the money transmitting laws. Roger’s case is also being used as a weapon of fear. I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so. Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time. This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years. This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
@ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night. I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case. We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money. The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially). The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines. Part of that battle is self custody, part is tax and part are the money transmitting laws. Roger’s case is also being used as a weapon of fear. I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so. Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time. This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years. This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification. @ cdee943c:5e637400
2024-12-08 16:39:01### Identify and Use the Correct Relays After the user has logged in either through a Bunker or Signer App/Browser plugin, we should identify the correct relays to use for them, as per the "Outbox" model: 1. Fetch the User’s Relay List (`kind:10002`): - Given the user’s public key, query a set of known bootstrap relays or a directory service to find the user’s `kind:10002` event. - Parse the `r` tags: - Read Relays: For discovering events _about_ the user, including their mentions, follow lists, interest sets, and reactions from others. - Write Relays: For discovering events _from_ the user directly, such as their posted recipes or their relay-published follow lists. We now know which small, authoritative set of relays to query for user-related data, reducing noise and improving performance. --- ### Build the Initial Follower Network 1. Fetch Follow Lists (`kind:3`): - Connect to the user’s chosen WRITE relays. - Retrieve their `kind:3` Follow List event, which lists whom the user follows. - Extract each followed pubkey and possibly associated relay URLs and petnames. 2. Fetch Additional Lists: - Query `kind:30000` range events (like Follow sets `30000`, Interest sets `10015`, Bookmarks `10003`, Communities `10004`, etc.) that the user maintains. - This may reveal specialized follow sets or interest-based sets. For example: - Follow sets (`kind:30000`) to categorize follows into thematic groups. - Interest sets (`kind:10015`) to see what topics the user is explicitly interested in. 3. Assemble a Unified Follower Network: - Combine direct follows (`kind:3`) and sets from `kind:30000` events and other NIP-51 sets to get a richer map of who matters to the user’s culinary context. - Some sets may reference pubkeys via `p` tags. Aggregate them into a single structured follower/connection network. We should now have more complete map of the user’s social connections, including standard follows and curated sets. --- ### Integrate Relationship Status Although [NIP-81](https://github.com/nostr-protocol/nips/blob/8dafaf8714dcb9c0fca5530b53535bf8327ed6c7/81.md) hasn't been merged into the main NIP repo it is implemented by several major clients including Amethyst and provides the most reliable data on the relationship between two Nostr users. 1. Fetch Relationship Status Events: - Use `kind:30382` (public relationships) and `kind:31382` (private relationships) to discover deeper relational data between the user and others. - From these events: - Identify if the user is placed in various named sets (`"n"` tags). - Identify if the user or their followees are categorized in some way or are in any other relationship groups. 2. Incorporate Relationship Tags into the Graph: - If the user places a contact into a “trusted” or “key collaborator” set via NIP-81’s `n` tags, increase the influence score of that contact. - If the user is placed by others into sets, factor that in, as it shows reciprocal recognition. We should now have a richer social graph that goes beyond just “follows,” capturing nuanced relational data to refine how we weigh each contact’s influence. --- ### Scoring the Influence of Followers For each follower identified in Steps 2 and 3, we compute an influence score. Consider: - Reciprocal Follows: - If a person the user follows also follows them back (derived from `kind:3` on the follower’s side), add points. - Reactions and Zaps to/from the User (NIP-25 & NIP-57): - Check if this follower liked (`+`), disliked (`-`), or reacted with custom emojis to the user’s posts (`kind:7` events with `#e` referencing user’s posts). - Check if they zapped the user’s posts or profile (`kind:9735` zap receipts), indicating support with real sats. - Also consider if the user has reacted or zapped this follower’s posts—mutual engagement increases influence. - NIP-51 List Membership: - If the follower appears in the user’s NIP-51 sets (like a “VIP cooks” set `kind:30000` or “Top Bookmarks” `kind:10003`), add extra points. - NIP-81 Relationship Assignments: - If the follower is placed into a special category by the user’s `kind:30382` event or if the follower places the user in their `kind:30382` event, increment the score based on category importance. We should now have a list of followers ranked by their “influence” in the user’s network. Influential people are those with mutual follows, engagement (reactions and zaps), presence in multiple sets, and meaningful relationship tags. --- ### Using Influential Followers to Build a "Web of Flavor" 1. Query Influential Followers’ Data: - For the top N most influential followers: - Fetch their `kind:10003` (Bookmarks), `kind:10015` (Interests), `kind:1985` (Labels), `kind:30023` (Curation sets), and other relevant NIP-51 sets. - Gather tags like `t` (topics), `a` (articles, possibly representing recipes), `e` (notes), `p` (pubkeys referencing authors), and so forth. 2. Assemble a Recipe Ontology: - From their sets and labels, extract: - Cuisines (e.g., `["l", "Italian", "ISO-3166-2"]` or discovered from `l` tags representing cuisines) - Categories (from `l` tags or sets) - Ingredients (from reading through user’s curated sets or `t` tags they frequently use) - Incorporate labeling from `kind:1985` events that might classify recipes under certain namespaces, and from `30023` sets that highlight curated recipe collections. 3. Aggregate and Normalize Tags: - Combine all discovered interests, cuisines, categories, and ingredients into a unified ontology representing the user’s “web of taste.” - Deduplicate and normalize terms—ensure consistent naming conventions (e.g., unify “Italian” and “IT-PR” region tags under one conceptual umbrella). We should now have a rich, aggregated ontology of flavors, cuisines, categories, and ingredients derived from the user’s most influential contacts and their labeling and interest sets. --- ### Constructing the Relay Query for Relevant Recipes 1. Query Recipes by Ontology: - Construct a Nostr filter referencing `#t` tags for interests, `#l` tags for labels, and `#a` or `#e` tags for known recipe sets or curated articles. - For performance, use the COUNT filter if the relay supports it (e.g., `{"kinds":[35000], "#t":["italian","vegetarian"]}` and ask if relay supports `limit` or `count`). 2. Refine Queries Iteratively: - Start broad by querying for top-level categories (e.g., “Italian vegetarian recipes”). - Narrow down results by adding more tags or sets once initial results are retrieved. - Use reaction counts or zap data on the returned events to further refine or sort results client-side. We will now have a final set of relevant recipe events from authoritative relays, filtered according to the user’s “web of taste” established through their network of influence.
@ cdee943c:5e637400
2024-12-08 16:39:01### Identify and Use the Correct Relays After the user has logged in either through a Bunker or Signer App/Browser plugin, we should identify the correct relays to use for them, as per the "Outbox" model: 1. Fetch the User’s Relay List (`kind:10002`): - Given the user’s public key, query a set of known bootstrap relays or a directory service to find the user’s `kind:10002` event. - Parse the `r` tags: - Read Relays: For discovering events _about_ the user, including their mentions, follow lists, interest sets, and reactions from others. - Write Relays: For discovering events _from_ the user directly, such as their posted recipes or their relay-published follow lists. We now know which small, authoritative set of relays to query for user-related data, reducing noise and improving performance. --- ### Build the Initial Follower Network 1. Fetch Follow Lists (`kind:3`): - Connect to the user’s chosen WRITE relays. - Retrieve their `kind:3` Follow List event, which lists whom the user follows. - Extract each followed pubkey and possibly associated relay URLs and petnames. 2. Fetch Additional Lists: - Query `kind:30000` range events (like Follow sets `30000`, Interest sets `10015`, Bookmarks `10003`, Communities `10004`, etc.) that the user maintains. - This may reveal specialized follow sets or interest-based sets. For example: - Follow sets (`kind:30000`) to categorize follows into thematic groups. - Interest sets (`kind:10015`) to see what topics the user is explicitly interested in. 3. Assemble a Unified Follower Network: - Combine direct follows (`kind:3`) and sets from `kind:30000` events and other NIP-51 sets to get a richer map of who matters to the user’s culinary context. - Some sets may reference pubkeys via `p` tags. Aggregate them into a single structured follower/connection network. We should now have more complete map of the user’s social connections, including standard follows and curated sets. --- ### Integrate Relationship Status Although [NIP-81](https://github.com/nostr-protocol/nips/blob/8dafaf8714dcb9c0fca5530b53535bf8327ed6c7/81.md) hasn't been merged into the main NIP repo it is implemented by several major clients including Amethyst and provides the most reliable data on the relationship between two Nostr users. 1. Fetch Relationship Status Events: - Use `kind:30382` (public relationships) and `kind:31382` (private relationships) to discover deeper relational data between the user and others. - From these events: - Identify if the user is placed in various named sets (`"n"` tags). - Identify if the user or their followees are categorized in some way or are in any other relationship groups. 2. Incorporate Relationship Tags into the Graph: - If the user places a contact into a “trusted” or “key collaborator” set via NIP-81’s `n` tags, increase the influence score of that contact. - If the user is placed by others into sets, factor that in, as it shows reciprocal recognition. We should now have a richer social graph that goes beyond just “follows,” capturing nuanced relational data to refine how we weigh each contact’s influence. --- ### Scoring the Influence of Followers For each follower identified in Steps 2 and 3, we compute an influence score. Consider: - Reciprocal Follows: - If a person the user follows also follows them back (derived from `kind:3` on the follower’s side), add points. - Reactions and Zaps to/from the User (NIP-25 & NIP-57): - Check if this follower liked (`+`), disliked (`-`), or reacted with custom emojis to the user’s posts (`kind:7` events with `#e` referencing user’s posts). - Check if they zapped the user’s posts or profile (`kind:9735` zap receipts), indicating support with real sats. - Also consider if the user has reacted or zapped this follower’s posts—mutual engagement increases influence. - NIP-51 List Membership: - If the follower appears in the user’s NIP-51 sets (like a “VIP cooks” set `kind:30000` or “Top Bookmarks” `kind:10003`), add extra points. - NIP-81 Relationship Assignments: - If the follower is placed into a special category by the user’s `kind:30382` event or if the follower places the user in their `kind:30382` event, increment the score based on category importance. We should now have a list of followers ranked by their “influence” in the user’s network. Influential people are those with mutual follows, engagement (reactions and zaps), presence in multiple sets, and meaningful relationship tags. --- ### Using Influential Followers to Build a "Web of Flavor" 1. Query Influential Followers’ Data: - For the top N most influential followers: - Fetch their `kind:10003` (Bookmarks), `kind:10015` (Interests), `kind:1985` (Labels), `kind:30023` (Curation sets), and other relevant NIP-51 sets. - Gather tags like `t` (topics), `a` (articles, possibly representing recipes), `e` (notes), `p` (pubkeys referencing authors), and so forth. 2. Assemble a Recipe Ontology: - From their sets and labels, extract: - Cuisines (e.g., `["l", "Italian", "ISO-3166-2"]` or discovered from `l` tags representing cuisines) - Categories (from `l` tags or sets) - Ingredients (from reading through user’s curated sets or `t` tags they frequently use) - Incorporate labeling from `kind:1985` events that might classify recipes under certain namespaces, and from `30023` sets that highlight curated recipe collections. 3. Aggregate and Normalize Tags: - Combine all discovered interests, cuisines, categories, and ingredients into a unified ontology representing the user’s “web of taste.” - Deduplicate and normalize terms—ensure consistent naming conventions (e.g., unify “Italian” and “IT-PR” region tags under one conceptual umbrella). We should now have a rich, aggregated ontology of flavors, cuisines, categories, and ingredients derived from the user’s most influential contacts and their labeling and interest sets. --- ### Constructing the Relay Query for Relevant Recipes 1. Query Recipes by Ontology: - Construct a Nostr filter referencing `#t` tags for interests, `#l` tags for labels, and `#a` or `#e` tags for known recipe sets or curated articles. - For performance, use the COUNT filter if the relay supports it (e.g., `{"kinds":[35000], "#t":["italian","vegetarian"]}` and ask if relay supports `limit` or `count`). 2. Refine Queries Iteratively: - Start broad by querying for top-level categories (e.g., “Italian vegetarian recipes”). - Narrow down results by adding more tags or sets once initial results are retrieved. - Use reaction counts or zap data on the returned events to further refine or sort results client-side. We will now have a final set of relevant recipe events from authoritative relays, filtered according to the user’s “web of taste” established through their network of influence. @ cdee943c:5e637400
2024-12-06 19:26:20## Why would you set up a custom relay for Recipes? Recipes are inherently rich in data, encompassing multiple ingredients, categories, cuisines, nutritional information, and detailed instructions. A custom relay tailored to handle a specific recipe event kind (nominally `kind=35000`) can: - **Optimize Data Retrieval:** Efficient indexing and storage mechanisms ensure swift access to complex recipe data. - **Enhance Flexibility:** Tailored configurations accommodate the unique structure of recipe events, making query filters more efficient and flexible. - **Improve Performance:** Specialized handling reduces latency, which becomes a very important factor for high volume services. - **Support Advanced Features:** Features like real-time syncing, bulk import/export, and efficient compression cater to the dynamic nature of recipe sharing. By aligning the relay's architecture with the structure of recipe events, Nostr developers can build responsive and scalable applications. ## Setting Up a Custom Recipe Relay ### Option 1: Using [khatru](https://khatru.nostr.technology/) and [Eventstore](https://github.com/fiatjaf/eventstore) 1. Bootstrap a basic khatru relay: - Follow the steps outlined in the [khatru](https://khatru.nostr.technology/getting-started/) docs: ```go relay := khatru.NewRelay() ``` 2. Set up Eventstore: - Configure khataru to use Eventstore and Postgresql: ```go // Initialize Eventstore db := postgresql.PostgresBackend{DatabaseURL: "postgres://eventuser:securepassword@localhost:5432/eventstore_db?sslmode=disable"} if err := db.Init(); err != nil { log.Fatalf("Failed to initialize eventstore: %v", err) } // Integrate Eventstore with Khatru relay.StoreEvent = append(relay.StoreEvent, db.SaveEvent) relay.QueryEvents = append(relay.QueryEvents, db.QueryEvents) relay.CountEvents = append(relay.CountEvents, db.CountEvents) relay.DeleteEvent = append(relay.DeleteEvent, db.DeleteEvent) ``` 3. Modify tag handling - Update the `tags_to_tagvalues` function to handle multi-character keys, multiple tag entries, and nested structures: ```go _, err = db.DB.Exec( CREATE OR REPLACE FUNCTION tags_to_tagvalues(jsonb) RETURNS text[] AS $$ SELECT array_agg(t.value) FROM jsonb_array_elements($1) AS elem(tag) JOIN LATERAL ( SELECT CASE WHEN tag->>0 IN ('cuisine', 'category', 'ingredients', 'tags') THEN tag->>1 WHEN tag->>0 = 'nutrition' AND jsonb_array_length(tag) >= 3 THEN tag->>2 ELSE NULL END AS value ) AS t ON t.value IS NOT NULL; $$ LANGUAGE SQL IMMUTABLE RETURNS NULL ON NULL INPUT; ) ``` 4. Add custom polices: - khatru supports setting custom event policies: ```go // Apply custom policies to accept only kind 35000 events relay.RejectEvent = append(relay.RejectEvent, // Built-in policies policies.ValidateKind, // Custom policy to accept only kind 35000 func(ctx context.Context, event *nostr.Event) (bool, string) { if event.Kind != 35000 { return true, "Only recipe events (kind 35000) are accepted" } return false, "" }, ) ``` 5. Pray that fiatjaf doesn't fire me ### Option 2: Modifying [Strfry](https://github.com/hoytech/strfry)'s Configuration Strfry is another robust Nostr relay implementation that leverages LMDB for local data storage. Stirfry uses the [golpe C++ framework](https://github.com/hoytech/golpe) and by adjusting its configuration in `golpe.yaml`, you can tailor Strfry to handle recipe events optimally. 1. Optimize Indices: - Enhance indexing for specific recipe-related tags to speed up queries: ```yaml indices: cuisine: comparator: StringUint64 multi: true category: comparator: StringUint64 multi: true ingredients: comparator: StringUint64 multi: true nutrition: comparator: StringUint64Uint64 multi: true ``` 2. Update indexPrelude: ```yaml indexPrelude: | PackedEventView packed(v.buf); created_at = packed.created_at(); uint64_t indexTime = *created_at; id = makeKey_StringUint64(packed.id(), indexTime); pubkey = makeKey_StringUint64(packed.pubkey(), indexTime); kind = makeKey_Uint64Uint64(packed.kind(), indexTime); pubkeyKind = makeKey_StringUint64Uint64(packed.pubkey(), packed.kind(), indexTime); packed.foreachTag([&](char tagName, std::string_view tagVal, std::string_view tagVal2 = ""){ // General tag indexing tag.push_back(makeKey_StringUint64(std::string(1, tagName) + std::string(tagVal), indexTime)); // Specific tag handling for recipes std::string tagNameStr(1, tagName); if (tagNameStr == "cuisine") { cuisine.push_back(makeKey_StringUint64(std::string(tagVal), indexTime)); } else if (tagNameStr == "category") { category.push_back(makeKey_StringUint64(std::string(tagVal), indexTime)); } else if (tagNameStr == "ingredients") { ingredients.push_back(makeKey_StringUint64(std::string(tagVal), indexTime)); } else if (tagNameStr == "nutrition" && !tagVal2.empty()) { nutrition.push_back(makeKey_StringUint64Uint64(std::string(tagVal), std::string(tagVal2), indexTime)); } else if (tagNameStr == "tags") { tags_specific.push_back(makeKey_StringUint64(std::string(tagVal), indexTime)); } // Existing conditions for 'd' and 'e' tags if (tagName == 'd' && replace.size() == 0) { replace.push_back(makeKey_StringUint64(std::string(packed.pubkey()) + std::string(tagVal), packed.kind())); } else if (tagName == 'e' && packed.kind() == 5) { deletion.push_back(std::string(tagVal) + std::string(packed.pubkey())); } return true; }); if (packed.expiration() != 0) { expiration.push_back(packed.expiration()); } ``` ## Conclusion Setting up a custom Nostr relay tailored for recipe events would enable developers to build highly performant and flexible applications. Whether it is using **Khatru with Eventstore** or **modify Strfry's configuration**, the key lies in aligning the relay's architecture with the features of recipe data. This approach not only improves performance but also lays a robust foundation for building feature-rich clients and applications within the Nostr ecosystem.
@ cdee943c:5e637400
2024-12-06 19:26:20## Why would you set up a custom relay for Recipes? Recipes are inherently rich in data, encompassing multiple ingredients, categories, cuisines, nutritional information, and detailed instructions. A custom relay tailored to handle a specific recipe event kind (nominally `kind=35000`) can: - **Optimize Data Retrieval:** Efficient indexing and storage mechanisms ensure swift access to complex recipe data. - **Enhance Flexibility:** Tailored configurations accommodate the unique structure of recipe events, making query filters more efficient and flexible. - **Improve Performance:** Specialized handling reduces latency, which becomes a very important factor for high volume services. - **Support Advanced Features:** Features like real-time syncing, bulk import/export, and efficient compression cater to the dynamic nature of recipe sharing. By aligning the relay's architecture with the structure of recipe events, Nostr developers can build responsive and scalable applications. ## Setting Up a Custom Recipe Relay ### Option 1: Using [khatru](https://khatru.nostr.technology/) and [Eventstore](https://github.com/fiatjaf/eventstore) 1. Bootstrap a basic khatru relay: - Follow the steps outlined in the [khatru](https://khatru.nostr.technology/getting-started/) docs: ```go relay := khatru.NewRelay() ``` 2. Set up Eventstore: - Configure khataru to use Eventstore and Postgresql: ```go // Initialize Eventstore db := postgresql.PostgresBackend{DatabaseURL: "postgres://eventuser:securepassword@localhost:5432/eventstore_db?sslmode=disable"} if err := db.Init(); err != nil { log.Fatalf("Failed to initialize eventstore: %v", err) } // Integrate Eventstore with Khatru relay.StoreEvent = append(relay.StoreEvent, db.SaveEvent) relay.QueryEvents = append(relay.QueryEvents, db.QueryEvents) relay.CountEvents = append(relay.CountEvents, db.CountEvents) relay.DeleteEvent = append(relay.DeleteEvent, db.DeleteEvent) ``` 3. Modify tag handling - Update the `tags_to_tagvalues` function to handle multi-character keys, multiple tag entries, and nested structures: ```go _, err = db.DB.Exec( CREATE OR REPLACE FUNCTION tags_to_tagvalues(jsonb) RETURNS text[] AS $$ SELECT array_agg(t.value) FROM jsonb_array_elements($1) AS elem(tag) JOIN LATERAL ( SELECT CASE WHEN tag->>0 IN ('cuisine', 'category', 'ingredients', 'tags') THEN tag->>1 WHEN tag->>0 = 'nutrition' AND jsonb_array_length(tag) >= 3 THEN tag->>2 ELSE NULL END AS value ) AS t ON t.value IS NOT NULL; $$ LANGUAGE SQL IMMUTABLE RETURNS NULL ON NULL INPUT; ) ``` 4. Add custom polices: - khatru supports setting custom event policies: ```go // Apply custom policies to accept only kind 35000 events relay.RejectEvent = append(relay.RejectEvent, // Built-in policies policies.ValidateKind, // Custom policy to accept only kind 35000 func(ctx context.Context, event *nostr.Event) (bool, string) { if event.Kind != 35000 { return true, "Only recipe events (kind 35000) are accepted" } return false, "" }, ) ``` 5. Pray that fiatjaf doesn't fire me ### Option 2: Modifying [Strfry](https://github.com/hoytech/strfry)'s Configuration Strfry is another robust Nostr relay implementation that leverages LMDB for local data storage. Stirfry uses the [golpe C++ framework](https://github.com/hoytech/golpe) and by adjusting its configuration in `golpe.yaml`, you can tailor Strfry to handle recipe events optimally. 1. Optimize Indices: - Enhance indexing for specific recipe-related tags to speed up queries: ```yaml indices: cuisine: comparator: StringUint64 multi: true category: comparator: StringUint64 multi: true ingredients: comparator: StringUint64 multi: true nutrition: comparator: StringUint64Uint64 multi: true ``` 2. Update indexPrelude: ```yaml indexPrelude: | PackedEventView packed(v.buf); created_at = packed.created_at(); uint64_t indexTime = *created_at; id = makeKey_StringUint64(packed.id(), indexTime); pubkey = makeKey_StringUint64(packed.pubkey(), indexTime); kind = makeKey_Uint64Uint64(packed.kind(), indexTime); pubkeyKind = makeKey_StringUint64Uint64(packed.pubkey(), packed.kind(), indexTime); packed.foreachTag([&](char tagName, std::string_view tagVal, std::string_view tagVal2 = ""){ // General tag indexing tag.push_back(makeKey_StringUint64(std::string(1, tagName) + std::string(tagVal), indexTime)); // Specific tag handling for recipes std::string tagNameStr(1, tagName); if (tagNameStr == "cuisine") { cuisine.push_back(makeKey_StringUint64(std::string(tagVal), indexTime)); } else if (tagNameStr == "category") { category.push_back(makeKey_StringUint64(std::string(tagVal), indexTime)); } else if (tagNameStr == "ingredients") { ingredients.push_back(makeKey_StringUint64(std::string(tagVal), indexTime)); } else if (tagNameStr == "nutrition" && !tagVal2.empty()) { nutrition.push_back(makeKey_StringUint64Uint64(std::string(tagVal), std::string(tagVal2), indexTime)); } else if (tagNameStr == "tags") { tags_specific.push_back(makeKey_StringUint64(std::string(tagVal), indexTime)); } // Existing conditions for 'd' and 'e' tags if (tagName == 'd' && replace.size() == 0) { replace.push_back(makeKey_StringUint64(std::string(packed.pubkey()) + std::string(tagVal), packed.kind())); } else if (tagName == 'e' && packed.kind() == 5) { deletion.push_back(std::string(tagVal) + std::string(packed.pubkey())); } return true; }); if (packed.expiration() != 0) { expiration.push_back(packed.expiration()); } ``` ## Conclusion Setting up a custom Nostr relay tailored for recipe events would enable developers to build highly performant and flexible applications. Whether it is using **Khatru with Eventstore** or **modify Strfry's configuration**, the key lies in aligning the relay's architecture with the features of recipe data. This approach not only improves performance but also lays a robust foundation for building feature-rich clients and applications within the Nostr ecosystem. @ b2d670de:907f9d4a
2024-12-02 21:25:18This is a list of nostr clients exposed as onion services. The list is currently actively maintained on [GitHub](https://github.com/0xtrr/onion-service-nostr-clients). Contributions are always appreciated! | Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | [operator](nostr:nprofile1qyvhwumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdshszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmg9umdvr) | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | [operator](nostr:nprofile1qyv8wumn8ghj7un9d3shjtnddaehgctjvshx7un89uq36amnwvaz7tmzdaehgu3wvf5hgcm0d9h8g7r0ddhjucm0d5hsqgy8wvyzw6l9pn5m47n7tcm5un7t7h5ctx3pjx8nfwh06qq8g6max5zadtyx) | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostrnpub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | [operator](nostr:nprofile1qqszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsxx2q3a) | Runs nsite. You can read more about nsite [here](https://github.com/lez/nsite). |
@ b2d670de:907f9d4a
2024-12-02 21:25:18This is a list of nostr clients exposed as onion services. The list is currently actively maintained on [GitHub](https://github.com/0xtrr/onion-service-nostr-clients). Contributions are always appreciated! | Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | [operator](nostr:nprofile1qyvhwumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdshszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmg9umdvr) | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | [operator](nostr:nprofile1qyv8wumn8ghj7un9d3shjtnddaehgctjvshx7un89uq36amnwvaz7tmzdaehgu3wvf5hgcm0d9h8g7r0ddhjucm0d5hsqgy8wvyzw6l9pn5m47n7tcm5un7t7h5ctx3pjx8nfwh06qq8g6max5zadtyx) | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostrnpub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | [operator](nostr:nprofile1qqszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsxx2q3a) | Runs nsite. You can read more about nsite [here](https://github.com/lez/nsite). | @ b2d670de:907f9d4a
2024-12-02 21:24:45# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
@ b2d670de:907f9d4a
2024-12-02 21:24:45# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url). @ 31312140:2471509b
2024-11-23 15:50:43#### 🎩 The Origins: Where Did It All Start? The concept of central banking isn't new. It dates back to the establishment of the Bank of England in 1694, which set the precedent for modern central banks (Check out [Bank of England's history](https://www.bankofengland.co.uk/about/history) for a deeper dive). These institutions were often created out of necessity - to handle war debts, stabilize economies, etc. But with great power comes… you guessed it, not-so-great intentions. 💰 #### 💸 The Money Factory: Printing Out of Thin Air Central banks have the magical ability to print money from thin air. Sound amazing? Well, it's alarming. This endless printing is explained under the guise of "monetary policy" to control the economy. But in reality, it's a method to fund government debts and inflate the money supply, which causes the value of your hard-earned money to dwindle. Poof! Your buying power is gone. Have a look at how [federal reserve balance sheets](https://www.federalreserve.gov/monetarypolicy/bst_recenttrends.htm) have ballooned for evidence. #### 🔄 Fractional Reserve Banking: The Multiplication Illusion If you're a banker, you'll love fractional reserve banking. It's like magic, where banks keep a fraction of deposits and lend out the rest, creating a multiplier effect. Imagine you deposit 100$, the bank holds just 10$ and lends out the other 90$. The person who took out that loan spends it and this 90$ end up on someone else's deposit. Rinse and repeat until your 100$ effectively created 1,000$ in the economy. This system fuels credit bubbles and ultimately leads to *bank runs* when too many people try to withdraw their money at once. Just ask those unfortunate souls during the Great Depression! #### 🔗 Chains of Debt: The Slavery of Nations Central banks lend to governments, placing entire nations in debt. And who pays the price? You do, through taxes. Ironically, you’re not just paying off debts; you're also paying interest to these private banking cartels. It's a not-so-subtle form of modern-day slavery. For a chilling summary, G. Edward Griffin’s “The Creature from Jekyll Island” is a must-read. It breaks down how banks engineer boom and bust cycles to control economies and populations. #### 🔓 The Escape Plan: Sound Money is Freedom Enter Bitcoin. 🧡 The only currency immune to manipulation by any central entity, Bitcoin offers a decentralized escape route from the clutches of central banks. They can’t print more Bitcoin. They can’t inflate it. And they definitely can’t control it. It’s regulated by math and network consensus, not whimsical policy changes by bankers in fancy suits. Want to understand more? Check out “The Bitcoin Standard” by Saifedean Ammous. #### 🛡️ What Can You Do? - **Educate Yourself:** Read, study, and converse with like-minded folks. - **Diversify:** Consider holding assets that are outside the influence of central banks, like Bitcoin. - **Advocate for Change:** Speak out, support political reform, and promote community awareness about the strengths of decentralized financial systems. So, there you have it, folks! The maze is vast, but there’s light at the end of the tunnel if you’re willing to look into it. Knowledge is power, and it's time we reclaimed our financial freedom. 🤝 Feel free to dive deeper and challenge the narrative - every voice adds to the revolution! #lookintoit #bitcoin #fiat #freedom #finance #soundmoney #scam #inflation #money
@ 31312140:2471509b
2024-11-23 15:50:43#### 🎩 The Origins: Where Did It All Start? The concept of central banking isn't new. It dates back to the establishment of the Bank of England in 1694, which set the precedent for modern central banks (Check out [Bank of England's history](https://www.bankofengland.co.uk/about/history) for a deeper dive). These institutions were often created out of necessity - to handle war debts, stabilize economies, etc. But with great power comes… you guessed it, not-so-great intentions. 💰 #### 💸 The Money Factory: Printing Out of Thin Air Central banks have the magical ability to print money from thin air. Sound amazing? Well, it's alarming. This endless printing is explained under the guise of "monetary policy" to control the economy. But in reality, it's a method to fund government debts and inflate the money supply, which causes the value of your hard-earned money to dwindle. Poof! Your buying power is gone. Have a look at how [federal reserve balance sheets](https://www.federalreserve.gov/monetarypolicy/bst_recenttrends.htm) have ballooned for evidence. #### 🔄 Fractional Reserve Banking: The Multiplication Illusion If you're a banker, you'll love fractional reserve banking. It's like magic, where banks keep a fraction of deposits and lend out the rest, creating a multiplier effect. Imagine you deposit 100$, the bank holds just 10$ and lends out the other 90$. The person who took out that loan spends it and this 90$ end up on someone else's deposit. Rinse and repeat until your 100$ effectively created 1,000$ in the economy. This system fuels credit bubbles and ultimately leads to *bank runs* when too many people try to withdraw their money at once. Just ask those unfortunate souls during the Great Depression! #### 🔗 Chains of Debt: The Slavery of Nations Central banks lend to governments, placing entire nations in debt. And who pays the price? You do, through taxes. Ironically, you’re not just paying off debts; you're also paying interest to these private banking cartels. It's a not-so-subtle form of modern-day slavery. For a chilling summary, G. Edward Griffin’s “The Creature from Jekyll Island” is a must-read. It breaks down how banks engineer boom and bust cycles to control economies and populations. #### 🔓 The Escape Plan: Sound Money is Freedom Enter Bitcoin. 🧡 The only currency immune to manipulation by any central entity, Bitcoin offers a decentralized escape route from the clutches of central banks. They can’t print more Bitcoin. They can’t inflate it. And they definitely can’t control it. It’s regulated by math and network consensus, not whimsical policy changes by bankers in fancy suits. Want to understand more? Check out “The Bitcoin Standard” by Saifedean Ammous. #### 🛡️ What Can You Do? - **Educate Yourself:** Read, study, and converse with like-minded folks. - **Diversify:** Consider holding assets that are outside the influence of central banks, like Bitcoin. - **Advocate for Change:** Speak out, support political reform, and promote community awareness about the strengths of decentralized financial systems. So, there you have it, folks! The maze is vast, but there’s light at the end of the tunnel if you’re willing to look into it. Knowledge is power, and it's time we reclaimed our financial freedom. 🤝 Feel free to dive deeper and challenge the narrative - every voice adds to the revolution! #lookintoit #bitcoin #fiat #freedom #finance #soundmoney #scam #inflation #money @ a849beb6:b327e6d2
2024-11-23 15:03:47<img src="https://blossom.primal.net/e306357a7e53c4e40458cf6fa5625917dc8deaa4d1012823caa5a0eefb39e53c.jpg"> \ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025. Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery. As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ **Portfolio Company Spotlight** [Primal](http://primal.net/) is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by [Strike BLACK](https://x.com/Strike/status/1755335823023558819)) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money. ### **Selected Portfolio News** AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in [December](https://x.com/AnchorWatch/status/1858622945763131577).\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed [private credit strategy](https://www.youtube.com/watch?v=26bOawTzT5U). Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many [more new features](https://primal.net/e/note1kaeajwh275kdwd6s0c2ksvj9f83t0k7usf9qj8fha2ac7m456juqpac43m). Debifi launched its new iOS app for Apple users seeking non-custodial [bitcoin-collateralized loans](https://x.com/debificom/status/1858897785044500642). ### **Media** Strike Founder and CEO Jack Mallers [joined Bloomberg TV](https://www.youtube.com/watch?v=i4z-2v_0H1k) to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve. Primal Founder and CEO Miljan Braticevic [joined](https://www.youtube.com/watch?v=kqR_IQfKic8) The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr. Ten31 Managing Partner Marty Bent [appeared on](https://www.youtube.com/watch?v=_WwZDEtVxOE&t=1556s) BlazeTV to discuss recent changes in the regulatory environment for bitcoin. Zaprite published a customer [testimonial video](https://x.com/ZapriteApp/status/1859357150809587928) highlighting the popularity of its offerings across the bitcoin ecosystem. ### **Market Updates** Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of [nearly $2 trillion](https://companiesmarketcap.com/assets-by-market-cap/), putting it within 3% of the market caps of Amazon and Google. After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully [approved](https://finance.yahoo.com/news/bitcoin-etf-options-set-hit-082230483.html) and launched this week. These options should help further expand bitcoin’s institutional [liquidity profile](https://x.com/kellyjgreer/status/1824168136637288912), with potentially significant [implications](https://x.com/dgt10011/status/1837278352823972147) for price action over time. The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching [nearly $2 billion](https://www.coindesk.com/markets/2024/11/20/bitcoin-etf-options-introduction-marks-milestone-despite-position-limits/) on just the first day of trading despite [surprisingly tight](https://x.com/dgt10011/status/1858729192105414837) position limits for the vehicles. Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in [$3.4 billion](https://farside.co.uk/btc/) in net inflows. New reports [suggested](https://archive.is/LMr4o) President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem. On the macro front, US housing starts [declined M/M again](https://finance.yahoo.com/news/us-single-family-housing-starts-134759234.html) in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels. Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that [developers need further rate cuts](https://www.bloomberg.com/news/articles/2024-11-19/miami-developer-says-real-estate-market-needs-rate-cuts-badly) “badly” to maintain project viability. US Manufacturing PMI [increased slightly](https://www.fxstreet.com/news/sp-global-pmis-set-to-signal-us-economy-continued-to-expand-in-november-202411220900) M/M, but has now been in contraction territory (<50) for well over two years. The latest iteration of the University of Michigan’s popular consumer sentiment survey [ticked up](https://archive.is/fY5j6) following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%. ### **Regulatory Update** After weeks of speculation, the incoming Trump administration appointed hedge fund manager [Scott Bessent](https://www.cnbc.com/amp/2024/11/22/donald-trump-chooses-hedge-fund-executive-scott-bessent-for-treasury-secretary.html) to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a [public advocate](https://x.com/EleanorTerrett/status/1856204133901963512) for bitcoin. Trump also [appointed](https://www.axios.com/2024/11/19/trump-commerce-secretary-howard-lutnick) Cantor Fitzgerald CEO Howard Lutnick – another outspoken [bitcoin bull](https://www.coindesk.com/policy/2024/09/04/tradfi-companies-want-to-transact-in-bitcoin-says-cantor-fitzgerald-ceo/) – as Secretary of the Commerce Department. Meanwhile, the Trump team is reportedly considering creating a new [“crypto czar”](https://archive.is/jPQHF) role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a [strategic bitcoin reserve](https://archive.is/ZtiOk). Various government lawyers suggested this week that the Trump administration is likely to be [less aggressive](https://archive.is/Uggnn) in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere. Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he [plans to resign](https://www.politico.com/news/2024/11/19/fdics-gruenberg-says-he-will-resign-jan-19-00190373) from his post at the end of President Biden’s term. Many critics have alleged Gruenberg was an architect of [“Operation Chokepoint 2.0,”](https://x.com/GOPMajorityWhip/status/1858927571666096628) which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space. SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the [Howey Test](https://www.investopedia.com/terms/h/howey-test.asp). Overseas, a Chinese court ruled that it is [not illegal](https://www.benzinga.com/24/11/42103633/chinese-court-affirms-cryptocurrency-ownership-as-legal-as-bitcoin-breaks-97k) for individuals to hold cryptocurrency, even though the country is still ostensibly [enforcing a ban](https://www.bbc.com/news/technology-58678907) on crypto transactions. ### **Noteworthy** The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – [suggested](https://x.com/matthew_sigel/status/1859700668887597331) the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets. BlackRock’s 2025 Thematic Outlook notes a [“renewed sense of optimism”](https://www.ishares.com/us/insights/2025-thematic-outlook#rate-cuts) on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets [indicated](https://www.youtube.com/watch?v=TE7cAw7oIeA) the firm does not view bitcoin as a “risk-on” asset. MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a [$100 billion equity value](https://finance.yahoo.com/news/microstrategy-breaks-top-100-u-191842879.html) this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet. Notably, Allianz SE, Germany’s largest insurer, [spoke for 25%](https://bitbo.io/news/allianz-buys-microstrategy-notes/) of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting [growing appetite](https://x.com/Rob1Ham/status/1860053859181199649) for bitcoin proxy exposure among more restricted pools of capital. The [ongoing meltdown](https://www.cnbc.com/2024/11/22/synapse-bankruptcy-thousands-of-americans-see-their-savings-vanish.html) of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack. ### **Travel** - [BitcoinMENA](https://bitcoin2024.b.tc/mena), Dec 9-10 - [Nashville BitDevs](https://www.meetup.com/bitcoinpark/events/302533726/?eventOrigin=group_upcoming_events), Dec 10 - [Austin BitDevs](https://www.meetup.com/austin-bitcoin-developers/events/303476169/?eventOrigin=group_upcoming_events), Dec 19 - [Nashville Energy and Mining Summit](https://www.meetup.com/bitcoinpark/events/304092624/?eventOrigin=group_events_list), Jan 30
@ a849beb6:b327e6d2
2024-11-23 15:03:47<img src="https://blossom.primal.net/e306357a7e53c4e40458cf6fa5625917dc8deaa4d1012823caa5a0eefb39e53c.jpg"> \ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025. Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery. As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ **Portfolio Company Spotlight** [Primal](http://primal.net/) is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by [Strike BLACK](https://x.com/Strike/status/1755335823023558819)) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money. ### **Selected Portfolio News** AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in [December](https://x.com/AnchorWatch/status/1858622945763131577).\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed [private credit strategy](https://www.youtube.com/watch?v=26bOawTzT5U). Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many [more new features](https://primal.net/e/note1kaeajwh275kdwd6s0c2ksvj9f83t0k7usf9qj8fha2ac7m456juqpac43m). Debifi launched its new iOS app for Apple users seeking non-custodial [bitcoin-collateralized loans](https://x.com/debificom/status/1858897785044500642). ### **Media** Strike Founder and CEO Jack Mallers [joined Bloomberg TV](https://www.youtube.com/watch?v=i4z-2v_0H1k) to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve. Primal Founder and CEO Miljan Braticevic [joined](https://www.youtube.com/watch?v=kqR_IQfKic8) The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr. Ten31 Managing Partner Marty Bent [appeared on](https://www.youtube.com/watch?v=_WwZDEtVxOE&t=1556s) BlazeTV to discuss recent changes in the regulatory environment for bitcoin. Zaprite published a customer [testimonial video](https://x.com/ZapriteApp/status/1859357150809587928) highlighting the popularity of its offerings across the bitcoin ecosystem. ### **Market Updates** Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of [nearly $2 trillion](https://companiesmarketcap.com/assets-by-market-cap/), putting it within 3% of the market caps of Amazon and Google. After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully [approved](https://finance.yahoo.com/news/bitcoin-etf-options-set-hit-082230483.html) and launched this week. These options should help further expand bitcoin’s institutional [liquidity profile](https://x.com/kellyjgreer/status/1824168136637288912), with potentially significant [implications](https://x.com/dgt10011/status/1837278352823972147) for price action over time. The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching [nearly $2 billion](https://www.coindesk.com/markets/2024/11/20/bitcoin-etf-options-introduction-marks-milestone-despite-position-limits/) on just the first day of trading despite [surprisingly tight](https://x.com/dgt10011/status/1858729192105414837) position limits for the vehicles. Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in [$3.4 billion](https://farside.co.uk/btc/) in net inflows. New reports [suggested](https://archive.is/LMr4o) President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem. On the macro front, US housing starts [declined M/M again](https://finance.yahoo.com/news/us-single-family-housing-starts-134759234.html) in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels. Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that [developers need further rate cuts](https://www.bloomberg.com/news/articles/2024-11-19/miami-developer-says-real-estate-market-needs-rate-cuts-badly) “badly” to maintain project viability. US Manufacturing PMI [increased slightly](https://www.fxstreet.com/news/sp-global-pmis-set-to-signal-us-economy-continued-to-expand-in-november-202411220900) M/M, but has now been in contraction territory (<50) for well over two years. The latest iteration of the University of Michigan’s popular consumer sentiment survey [ticked up](https://archive.is/fY5j6) following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%. ### **Regulatory Update** After weeks of speculation, the incoming Trump administration appointed hedge fund manager [Scott Bessent](https://www.cnbc.com/amp/2024/11/22/donald-trump-chooses-hedge-fund-executive-scott-bessent-for-treasury-secretary.html) to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a [public advocate](https://x.com/EleanorTerrett/status/1856204133901963512) for bitcoin. Trump also [appointed](https://www.axios.com/2024/11/19/trump-commerce-secretary-howard-lutnick) Cantor Fitzgerald CEO Howard Lutnick – another outspoken [bitcoin bull](https://www.coindesk.com/policy/2024/09/04/tradfi-companies-want-to-transact-in-bitcoin-says-cantor-fitzgerald-ceo/) – as Secretary of the Commerce Department. Meanwhile, the Trump team is reportedly considering creating a new [“crypto czar”](https://archive.is/jPQHF) role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a [strategic bitcoin reserve](https://archive.is/ZtiOk). Various government lawyers suggested this week that the Trump administration is likely to be [less aggressive](https://archive.is/Uggnn) in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere. Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he [plans to resign](https://www.politico.com/news/2024/11/19/fdics-gruenberg-says-he-will-resign-jan-19-00190373) from his post at the end of President Biden’s term. Many critics have alleged Gruenberg was an architect of [“Operation Chokepoint 2.0,”](https://x.com/GOPMajorityWhip/status/1858927571666096628) which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space. SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the [Howey Test](https://www.investopedia.com/terms/h/howey-test.asp). Overseas, a Chinese court ruled that it is [not illegal](https://www.benzinga.com/24/11/42103633/chinese-court-affirms-cryptocurrency-ownership-as-legal-as-bitcoin-breaks-97k) for individuals to hold cryptocurrency, even though the country is still ostensibly [enforcing a ban](https://www.bbc.com/news/technology-58678907) on crypto transactions. ### **Noteworthy** The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – [suggested](https://x.com/matthew_sigel/status/1859700668887597331) the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets. BlackRock’s 2025 Thematic Outlook notes a [“renewed sense of optimism”](https://www.ishares.com/us/insights/2025-thematic-outlook#rate-cuts) on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets [indicated](https://www.youtube.com/watch?v=TE7cAw7oIeA) the firm does not view bitcoin as a “risk-on” asset. MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a [$100 billion equity value](https://finance.yahoo.com/news/microstrategy-breaks-top-100-u-191842879.html) this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet. Notably, Allianz SE, Germany’s largest insurer, [spoke for 25%](https://bitbo.io/news/allianz-buys-microstrategy-notes/) of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting [growing appetite](https://x.com/Rob1Ham/status/1860053859181199649) for bitcoin proxy exposure among more restricted pools of capital. The [ongoing meltdown](https://www.cnbc.com/2024/11/22/synapse-bankruptcy-thousands-of-americans-see-their-savings-vanish.html) of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack. ### **Travel** - [BitcoinMENA](https://bitcoin2024.b.tc/mena), Dec 9-10 - [Nashville BitDevs](https://www.meetup.com/bitcoinpark/events/302533726/?eventOrigin=group_upcoming_events), Dec 10 - [Austin BitDevs](https://www.meetup.com/austin-bitcoin-developers/events/303476169/?eventOrigin=group_upcoming_events), Dec 19 - [Nashville Energy and Mining Summit](https://www.meetup.com/bitcoinpark/events/304092624/?eventOrigin=group_events_list), Jan 30 @ cdee943c:5e637400
2024-11-21 22:03:13One of the first [tasks](nostr:nevent1qqsrqws36dytallje0cwjjcaxqt3ukfhg0aqvwh3pakhuqzy8e9jscspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0wfjkccte9ehx7um5wghxuet59uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59utl42kp) we set ourselves at Nostr SF is to build a demonstration app for how to use dedicated kinds, and in this case, one for recipes. Nostr SF isn't a wheel design firm though, so we figured it was best to look at what's already happening and see if we can build off of that rather than necessarily start from scratch. So we asked ourselves what sort of information is being captured and shared in other recipe platforms that we could use as a model for ours. The following is a review of the various recipe formats that are presently in the wild: ### zap.cooking The inspiration for the project, [zap.cooking](https://zap.cooking/recent) currently uses `kind:30023` notes for publishing recipes. Looking in the [source code](https://github.com/github-tijlxyz/nostr.cooking/blob/84669f88c716d5c6b029840cbc7d8e9088e52d4d/src/lib/pharser.ts#L115), they parse a markdown representation in the content field which results in the following fields: - Chef's notes - Details (with the following 'sub fields') - Prep time - Cook time - Servings - Ingredients - Directions - Additional Resources The event json looks like this: ``` { "content": "\n## Chef's notes\n\nAh, my culinary wanderlust through northern Italy and an undeniable romance with fall's freshest produce gave birth to this risotto masterpiece. Crafted by yours truly, if you find your taste buds dancing with delight, do show some love. Who knows, a few more of my treasured recipes might just make their way from my kitchen to yours. Wink!\n\n## Details\n\n- ⏲️ Prep time: 30 min\n- 🍳 Cook time: 30 min\n- 🍽️ Servings: 4-6\n\n## Ingredients\n\n- 1 butternut squash, peeled, cored and cut into 1cm cubes \n- 1 onion, chopped \n- 1 pinch of nutmeg \n- 350 g Nebbia smoked carnaroli rice \n- 25 cl dry white wine, such as pinot grigio \n- 1 bay leaf, optional \n- 1 tablespoon fresh thyme leaves, optional \n- 50g cheese - parmesan or pecorino - finely grated \n- Extra virgin olive oil\n- 1300cl classic risotto broth (Star Il Mio Dado Classico or better yet, homemade)\n\n\n## Directions\n\n1. Preheat the oven to 200C. \n2. Coat the squash cubes with olive oil and spread them in a single layer on a large baking sheet (don't season them)\n3. Bake for about 50 minutes, until golden brown on the edges.\n4. Remove from oven and set aside. \n5. While the squash is roasting, prepare the stock and, if using, add the bay leaf. \n6. Bring to the boil and then reduce to a simmer. \n7. Heat a little olive oil in a large risotto pan, add the onion and fry until translucent, about 3 min.\n8. Add the rice and nutmeg, stir coating with the oil and onion and fry for another 2-3 minutes. \n9. Reduce the heat to medium and add the white wine, and thyme if using. \n10. As the wine evaporates, add a ladle of broth (about 20 cl), stirring regularly. \n11. As the broth evaporates and the rice begins to stick to the pan scrape the bottom and add another ladle of broth. \n12. Repeat until about 2 ladles of broth remain. \n13. Add about 1/3 to 2/3 of the cooked squash to the risotto and mix well. (You can add more if you like, or the rest of the squash will be delicious with pasta, with eggs, or in a soup.) \n14. Continue adding the last ladles of broth until the rice is cooked al dente. \n15. Remove from the heat and stir in the cheese. \n16. Serve immediately.\n17. Can also be made with regular carnaroli rice, in which case, put 4 chopped sage leaves and 2 cloves of garlic in with the thyme. However, the Nebbia Fog Smoked Rice has a magical richness to it that can't be imitated.\n", "created_at": 1699302411, "id": "1013a49c671ec45ad8d0ba97256b9abc1e990405a82f4bdf253ef0226d5eade3", "kind": 30023, "pubkey": "fe6104d291746db0132f54974e6d4331ced86f43fc00a75f592c1d20e1d22b8c", "sig": "e3e2e8776c8aed90e9c91b10e6b5d80827aa42f77e863ade84a98bd135e56488099d949b95f734d1323b520ed37c12c9c468311e9d67045af3107f52057c34bb", "tags": [ ["d", "uncle-jedi's-butternut-risotto"], ["title", "Uncle Jedi's Butternut Risotto"], ["t", "nostrcooking"], ["t", "nostrcooking-uncle-jedi's-butternut-risotto"], [ "summary", "Dive into a creamy risotto infused with the nutty richness of roasted butternut squash, seasoned with a hint of nutmeg and fresh thyme. This elegant dish, made with luxurious Nebbia smoked carnaroli rice, is perfectly balanced with the sharpness of parmesan or pecorino. And as the risotto bubbles and simmers, the white wine reduction adds depth and aroma that tantalizes the senses. Have leftovers? The roasted squash pairs delightfully with pasta or eggs. For the grand finale, enjoy this masterpiece with a savory fennel sausage. A meal that's both cozy and gourmet awaits!"], ["image", "https://image.nostr.build/f88d843b5d6a112c1963e34b61d731ab0d63c6bc6ede98df757d6cdaa4259f68.jpg"], ["t", "nostrcooking-easy"], ["t", "nostrcooking-italian"], ["t", "nostrcooking-squash"], ["t", "nostrcooking-rice"] ] } ``` ### Proposed Recipe NIP There is an existing [NIP proposal](https://github.com/nostr-protocol/nips/issues/1571) for recipes which suggests a number of tags that can be used to filter recipes more efficiently at the relay side. The event json looks like this: ``` { "id": "<event_id>", "pubkey": "<author_pubkey>", "created_at": <unix_timestamp>, "kind": XXXX, "tags": [ ["title", "<recipe_title>"], ["summary", "<recipe_summary>"], ["author", "<recipe_author>"], ["cuisine", "<style_or_region_of_cuisine>"], ["category", "<category>"], ["ingredients", "<ingredients_description>"], ["image", "<image_url>"], // can be used more than one // Optional Tags ["prep_time", "<prep_time>"], ["cook_time", "<cook_time>"], ["servings", "<servings_number>"], ["difficulty", "<difficulty>"], ["nutrition", "<calories_per_serving>"], ["tags", "<comma_separated_tags>"], ["allergens", "<comma_separated_allergens>"], ["content_warning", "<content_warning_description>"], ], "content": "<description_instructions_and_notes_content>", "sig": "<signature>" } ``` ### Schema.org There is a [schema](https://schema.org/Recipe) for recipes which details an exhaustive list of possible fields for a recipe. The minimum set of fields produces a JSON result like this: ``` { "@context": "https://schema.org", "@type": "Recipe", "author": "John Smith", "cookTime": "PT1H", "datePublished": "2009-05-08", "description": "This classic banana bread recipe comes from my mom -- the walnuts add a nice texture and flavor to the banana bread.", "image": "bananabread.jpg", "recipeIngredient": [ "3 or 4 ripe bananas, smashed", "1 egg", "3/4 cup of sugar" ], "interactionStatistic": { "@type": "InteractionCounter", "interactionType": "https://schema.org/Comment", "userInteractionCount": "140" }, "name": "Mom's World Famous Banana Bread", "nutrition": { "@type": "NutritionInformation", "calories": "240 calories", "fatContent": "9 grams fat" }, "prepTime": "PT15M", "recipeInstructions": "Preheat the oven to 350 degrees. Mix in the ingredients in a bowl. Add the flour last. Pour the mixture into a loaf pan and bake for one hour.", "recipeYield": "1 loaf", "suitableForDiet": "https://schema.org/LowFatDiet" } ``` ### Cooklang There is also specification for recipes called [Cooklang](https://cooklang.org/docs/spec/) which defines a DSL for recipes. The syntax has it's own [EBNF grammar](https://raw.githubusercontent.com/cooklang/spec/refs/heads/main/EBNF.md) which looks like this: ``` -- TODO add source Mix together @oyster sauce{1%tbsp}, @soy sauce{5%tbsp} and @sesame oil{5%tsp}, set aside. Heat @peanut oil{1%tbsp} in a wok or heavy based skillet/fry pan over medium heat. Add @eggs{2%items} and cook until scrambled, then remove onto plate. Increase heat to high and add chopped @bacon{75%cup}, excess fat trimmed. Cook until golden, then remove onto plate with egg - about 2 minutes. Drain off excess bacon fat. Add remaining @peanut oil{2%tbsp}, minced @garlic{2%gloves} and @ginger{3%tsp}. Return wok to stove on high heat. Stir fry as it comes up to heat, don’t let it burn. When garlic starts to sizzle, add finally chopped @onion{2%medium} and stir fry for 2 minutes until golden. Add @Chinese cooking wine{1%tbsp} and @sugar{2%tsp} and let it simmer rapidly, stirring, for 20 seconds, until mostly evaporated. Add @prawns{150%g} and stir fry for 1 minute to heat through if pre-cooked, cook longer to cook if raw. Add refrigerated overnight @cooked rice{3%cups}, Sauce, eggs, bacon and thinly sliced @scallions{5%items}. Stir fry for 2 minutes until rice is hot - around 2 minutes. Transfer to serving plate, sprinkle with thinly sliced @scallions{2%items} and serve. ``` There is an online parser demo [here](https://biowaffeln.github.io/cooklang-parser/) which converts a given recipe into an AST which looks like this: ``` { "metadata": { "source": "https://www.dinneratthezoo.com/wprm_print/6796", "total time": "6 minutes", "servings": "2" }, "ingredients": [ { "type": "ingredient", "name": "apple juice", "quantity": "1,5", "units": "cups" }, { "type": "ingredient", "name": "banana", "quantity": "one sliced", "units": "" }, { "type": "ingredient", "name": "frozen mixed berries", "quantity": "1,5", "units": "cups" }, { "type": "ingredient", "name": "vanilla greek yogurt", "quantity": 0.75, "units": "cup" }, { "type": "ingredient", "name": "honey", "quantity": "some", "units": "" } ], "cookware": [ { "type": "cookware", "name": "blender", "quantity": "" } ], "steps": [ [ { "type": "text", "value": "Place the " }, { "type": "ingredient", "name": "apple juice", "quantity": "1,5", "units": "cups" }, { "type": "text", "value": ", " }, { "type": "ingredient", "name": "banana", "quantity": "one sliced", "units": "" }, { "type": "text", "value": ", " }, { "type": "ingredient", "name": "frozen mixed berries", "quantity": "1,5", "units": "cups" }, { "type": "text", "value": " and " }, { "type": "ingredient", "name": "vanilla greek yogurt", "quantity": 0.75, "units": "cup" }, { "type": "text", "value": " in a " }, { "type": "cookware", "name": "blender", "quantity": "" }, { "type": "text", "value": "; blend until smooth. If the smoothie seems too thick, add a little more liquid (1/4 cup). " } ], [ { "type": "text", "value": "Taste and add " }, { "type": "ingredient", "name": "honey", "quantity": "some", "units": "" }, { "type": "text", "value": " if desired. Pour into two glasses and garnish with fresh berries and mint sprigs if desired." } ] ] } ``` This is by no means an exhaustive list of available recipe implementations but should server as a good starting point for determining what makes a good recipe `kind`.
@ cdee943c:5e637400
2024-11-21 22:03:13One of the first [tasks](nostr:nevent1qqsrqws36dytallje0cwjjcaxqt3ukfhg0aqvwh3pakhuqzy8e9jscspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0wfjkccte9ehx7um5wghxuet59uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59utl42kp) we set ourselves at Nostr SF is to build a demonstration app for how to use dedicated kinds, and in this case, one for recipes. Nostr SF isn't a wheel design firm though, so we figured it was best to look at what's already happening and see if we can build off of that rather than necessarily start from scratch. So we asked ourselves what sort of information is being captured and shared in other recipe platforms that we could use as a model for ours. The following is a review of the various recipe formats that are presently in the wild: ### zap.cooking The inspiration for the project, [zap.cooking](https://zap.cooking/recent) currently uses `kind:30023` notes for publishing recipes. Looking in the [source code](https://github.com/github-tijlxyz/nostr.cooking/blob/84669f88c716d5c6b029840cbc7d8e9088e52d4d/src/lib/pharser.ts#L115), they parse a markdown representation in the content field which results in the following fields: - Chef's notes - Details (with the following 'sub fields') - Prep time - Cook time - Servings - Ingredients - Directions - Additional Resources The event json looks like this: ``` { "content": "\n## Chef's notes\n\nAh, my culinary wanderlust through northern Italy and an undeniable romance with fall's freshest produce gave birth to this risotto masterpiece. Crafted by yours truly, if you find your taste buds dancing with delight, do show some love. Who knows, a few more of my treasured recipes might just make their way from my kitchen to yours. Wink!\n\n## Details\n\n- ⏲️ Prep time: 30 min\n- 🍳 Cook time: 30 min\n- 🍽️ Servings: 4-6\n\n## Ingredients\n\n- 1 butternut squash, peeled, cored and cut into 1cm cubes \n- 1 onion, chopped \n- 1 pinch of nutmeg \n- 350 g Nebbia smoked carnaroli rice \n- 25 cl dry white wine, such as pinot grigio \n- 1 bay leaf, optional \n- 1 tablespoon fresh thyme leaves, optional \n- 50g cheese - parmesan or pecorino - finely grated \n- Extra virgin olive oil\n- 1300cl classic risotto broth (Star Il Mio Dado Classico or better yet, homemade)\n\n\n## Directions\n\n1. Preheat the oven to 200C. \n2. Coat the squash cubes with olive oil and spread them in a single layer on a large baking sheet (don't season them)\n3. Bake for about 50 minutes, until golden brown on the edges.\n4. Remove from oven and set aside. \n5. While the squash is roasting, prepare the stock and, if using, add the bay leaf. \n6. Bring to the boil and then reduce to a simmer. \n7. Heat a little olive oil in a large risotto pan, add the onion and fry until translucent, about 3 min.\n8. Add the rice and nutmeg, stir coating with the oil and onion and fry for another 2-3 minutes. \n9. Reduce the heat to medium and add the white wine, and thyme if using. \n10. As the wine evaporates, add a ladle of broth (about 20 cl), stirring regularly. \n11. As the broth evaporates and the rice begins to stick to the pan scrape the bottom and add another ladle of broth. \n12. Repeat until about 2 ladles of broth remain. \n13. Add about 1/3 to 2/3 of the cooked squash to the risotto and mix well. (You can add more if you like, or the rest of the squash will be delicious with pasta, with eggs, or in a soup.) \n14. Continue adding the last ladles of broth until the rice is cooked al dente. \n15. Remove from the heat and stir in the cheese. \n16. Serve immediately.\n17. Can also be made with regular carnaroli rice, in which case, put 4 chopped sage leaves and 2 cloves of garlic in with the thyme. However, the Nebbia Fog Smoked Rice has a magical richness to it that can't be imitated.\n", "created_at": 1699302411, "id": "1013a49c671ec45ad8d0ba97256b9abc1e990405a82f4bdf253ef0226d5eade3", "kind": 30023, "pubkey": "fe6104d291746db0132f54974e6d4331ced86f43fc00a75f592c1d20e1d22b8c", "sig": "e3e2e8776c8aed90e9c91b10e6b5d80827aa42f77e863ade84a98bd135e56488099d949b95f734d1323b520ed37c12c9c468311e9d67045af3107f52057c34bb", "tags": [ ["d", "uncle-jedi's-butternut-risotto"], ["title", "Uncle Jedi's Butternut Risotto"], ["t", "nostrcooking"], ["t", "nostrcooking-uncle-jedi's-butternut-risotto"], [ "summary", "Dive into a creamy risotto infused with the nutty richness of roasted butternut squash, seasoned with a hint of nutmeg and fresh thyme. This elegant dish, made with luxurious Nebbia smoked carnaroli rice, is perfectly balanced with the sharpness of parmesan or pecorino. And as the risotto bubbles and simmers, the white wine reduction adds depth and aroma that tantalizes the senses. Have leftovers? The roasted squash pairs delightfully with pasta or eggs. For the grand finale, enjoy this masterpiece with a savory fennel sausage. A meal that's both cozy and gourmet awaits!"], ["image", "https://image.nostr.build/f88d843b5d6a112c1963e34b61d731ab0d63c6bc6ede98df757d6cdaa4259f68.jpg"], ["t", "nostrcooking-easy"], ["t", "nostrcooking-italian"], ["t", "nostrcooking-squash"], ["t", "nostrcooking-rice"] ] } ``` ### Proposed Recipe NIP There is an existing [NIP proposal](https://github.com/nostr-protocol/nips/issues/1571) for recipes which suggests a number of tags that can be used to filter recipes more efficiently at the relay side. The event json looks like this: ``` { "id": "<event_id>", "pubkey": "<author_pubkey>", "created_at": <unix_timestamp>, "kind": XXXX, "tags": [ ["title", "<recipe_title>"], ["summary", "<recipe_summary>"], ["author", "<recipe_author>"], ["cuisine", "<style_or_region_of_cuisine>"], ["category", "<category>"], ["ingredients", "<ingredients_description>"], ["image", "<image_url>"], // can be used more than one // Optional Tags ["prep_time", "<prep_time>"], ["cook_time", "<cook_time>"], ["servings", "<servings_number>"], ["difficulty", "<difficulty>"], ["nutrition", "<calories_per_serving>"], ["tags", "<comma_separated_tags>"], ["allergens", "<comma_separated_allergens>"], ["content_warning", "<content_warning_description>"], ], "content": "<description_instructions_and_notes_content>", "sig": "<signature>" } ``` ### Schema.org There is a [schema](https://schema.org/Recipe) for recipes which details an exhaustive list of possible fields for a recipe. The minimum set of fields produces a JSON result like this: ``` { "@context": "https://schema.org", "@type": "Recipe", "author": "John Smith", "cookTime": "PT1H", "datePublished": "2009-05-08", "description": "This classic banana bread recipe comes from my mom -- the walnuts add a nice texture and flavor to the banana bread.", "image": "bananabread.jpg", "recipeIngredient": [ "3 or 4 ripe bananas, smashed", "1 egg", "3/4 cup of sugar" ], "interactionStatistic": { "@type": "InteractionCounter", "interactionType": "https://schema.org/Comment", "userInteractionCount": "140" }, "name": "Mom's World Famous Banana Bread", "nutrition": { "@type": "NutritionInformation", "calories": "240 calories", "fatContent": "9 grams fat" }, "prepTime": "PT15M", "recipeInstructions": "Preheat the oven to 350 degrees. Mix in the ingredients in a bowl. Add the flour last. Pour the mixture into a loaf pan and bake for one hour.", "recipeYield": "1 loaf", "suitableForDiet": "https://schema.org/LowFatDiet" } ``` ### Cooklang There is also specification for recipes called [Cooklang](https://cooklang.org/docs/spec/) which defines a DSL for recipes. The syntax has it's own [EBNF grammar](https://raw.githubusercontent.com/cooklang/spec/refs/heads/main/EBNF.md) which looks like this: ``` -- TODO add source Mix together @oyster sauce{1%tbsp}, @soy sauce{5%tbsp} and @sesame oil{5%tsp}, set aside. Heat @peanut oil{1%tbsp} in a wok or heavy based skillet/fry pan over medium heat. Add @eggs{2%items} and cook until scrambled, then remove onto plate. Increase heat to high and add chopped @bacon{75%cup}, excess fat trimmed. Cook until golden, then remove onto plate with egg - about 2 minutes. Drain off excess bacon fat. Add remaining @peanut oil{2%tbsp}, minced @garlic{2%gloves} and @ginger{3%tsp}. Return wok to stove on high heat. Stir fry as it comes up to heat, don’t let it burn. When garlic starts to sizzle, add finally chopped @onion{2%medium} and stir fry for 2 minutes until golden. Add @Chinese cooking wine{1%tbsp} and @sugar{2%tsp} and let it simmer rapidly, stirring, for 20 seconds, until mostly evaporated. Add @prawns{150%g} and stir fry for 1 minute to heat through if pre-cooked, cook longer to cook if raw. Add refrigerated overnight @cooked rice{3%cups}, Sauce, eggs, bacon and thinly sliced @scallions{5%items}. Stir fry for 2 minutes until rice is hot - around 2 minutes. Transfer to serving plate, sprinkle with thinly sliced @scallions{2%items} and serve. ``` There is an online parser demo [here](https://biowaffeln.github.io/cooklang-parser/) which converts a given recipe into an AST which looks like this: ``` { "metadata": { "source": "https://www.dinneratthezoo.com/wprm_print/6796", "total time": "6 minutes", "servings": "2" }, "ingredients": [ { "type": "ingredient", "name": "apple juice", "quantity": "1,5", "units": "cups" }, { "type": "ingredient", "name": "banana", "quantity": "one sliced", "units": "" }, { "type": "ingredient", "name": "frozen mixed berries", "quantity": "1,5", "units": "cups" }, { "type": "ingredient", "name": "vanilla greek yogurt", "quantity": 0.75, "units": "cup" }, { "type": "ingredient", "name": "honey", "quantity": "some", "units": "" } ], "cookware": [ { "type": "cookware", "name": "blender", "quantity": "" } ], "steps": [ [ { "type": "text", "value": "Place the " }, { "type": "ingredient", "name": "apple juice", "quantity": "1,5", "units": "cups" }, { "type": "text", "value": ", " }, { "type": "ingredient", "name": "banana", "quantity": "one sliced", "units": "" }, { "type": "text", "value": ", " }, { "type": "ingredient", "name": "frozen mixed berries", "quantity": "1,5", "units": "cups" }, { "type": "text", "value": " and " }, { "type": "ingredient", "name": "vanilla greek yogurt", "quantity": 0.75, "units": "cup" }, { "type": "text", "value": " in a " }, { "type": "cookware", "name": "blender", "quantity": "" }, { "type": "text", "value": "; blend until smooth. If the smoothie seems too thick, add a little more liquid (1/4 cup). " } ], [ { "type": "text", "value": "Taste and add " }, { "type": "ingredient", "name": "honey", "quantity": "some", "units": "" }, { "type": "text", "value": " if desired. Pour into two glasses and garnish with fresh berries and mint sprigs if desired." } ] ] } ``` This is by no means an exhaustive list of available recipe implementations but should server as a good starting point for determining what makes a good recipe `kind`. @ b17c5987:85d68928
2024-11-21 10:24:16Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections. Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections. This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected Donald Trump with a mandate for sweeping change, and they deserve to get it. President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs. This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected [Donald Trump](https://www.wsj.com/topics/person/donald-trump) with a mandate for sweeping change, and they deserve to get it. President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs. We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure. In West Virginia v. Environmental Protection Agency (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In Loper Bright v. Raimondo (2024), the court overturned the Chevron doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law. DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy. When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be correcting the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so. A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit. Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in Franklin v. Massachusetts (1992) and Collins v. Yellen (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home. Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood. The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers. With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud. Mr. Musk is CEO of SpaceX and Tesla. Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency. We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure. In *West Virginia v. Environmental Protection Agency* (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In *Loper Bright v. Raimondo* (2024), the court overturned the *Chevron* doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law. DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy. When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be *correcting* the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so. A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit. Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in *Franklin v. Massachusetts* (1992) and *Collins v. Yellen* (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home. Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood. The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers. With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud. *Mr. Musk is CEO of SpaceX and [Tesla](https://www.wsj.com/market-data/quotes/TSLA). Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency.*
@ b17c5987:85d68928
2024-11-21 10:24:16Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections. Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections. This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected Donald Trump with a mandate for sweeping change, and they deserve to get it. President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs. This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected [Donald Trump](https://www.wsj.com/topics/person/donald-trump) with a mandate for sweeping change, and they deserve to get it. President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs. We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure. In West Virginia v. Environmental Protection Agency (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In Loper Bright v. Raimondo (2024), the court overturned the Chevron doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law. DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy. When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be correcting the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so. A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit. Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in Franklin v. Massachusetts (1992) and Collins v. Yellen (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home. Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood. The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers. With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud. Mr. Musk is CEO of SpaceX and Tesla. Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency. We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure. In *West Virginia v. Environmental Protection Agency* (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In *Loper Bright v. Raimondo* (2024), the court overturned the *Chevron* doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law. DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy. When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be *correcting* the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so. A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit. Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in *Franklin v. Massachusetts* (1992) and *Collins v. Yellen* (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home. Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood. The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers. With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud. *Mr. Musk is CEO of SpaceX and [Tesla](https://www.wsj.com/market-data/quotes/TSLA). Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency.* @ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/ Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country =================================================================================== Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges. * * * **KEY TAKEAWAYS** * The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero. * The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards. * While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.  In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country. **_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._** Let’s unpack what effect these regulations will have. Brazil’s Crackdown on Crypto Fraud ---------------------------------- If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets. The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism. According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances. > … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder. > > – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-) The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars. The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations. However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil. Monero: What Is It and Why Is Brazil Banning It? ------------------------------------------------ Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain. Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR. Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/). Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.  In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset. In Closing ---------- Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing. Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell. References ---------- Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems. [View all articles by Cassio Gusson](https://techreport.com/author/cassiog/)
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/ Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country =================================================================================== Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges. * * * **KEY TAKEAWAYS** * The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero. * The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards. * While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.  In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country. **_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._** Let’s unpack what effect these regulations will have. Brazil’s Crackdown on Crypto Fraud ---------------------------------- If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets. The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism. According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances. > … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder. > > – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-) The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars. The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations. However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil. Monero: What Is It and Why Is Brazil Banning It? ------------------------------------------------ Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain. Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR. Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/). Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.  In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset. In Closing ---------- Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing. Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell. References ---------- Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems. [View all articles by Cassio Gusson](https://techreport.com/author/cassiog/) @ 5e5fc143:393d5a2c
2024-11-19 10:20:25Now test old reliable front end Stay tuned more later Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues
@ 5e5fc143:393d5a2c
2024-11-19 10:20:25Now test old reliable front end Stay tuned more later Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues @ 84b0c46a:417782f5
2024-11-19 08:56:39- [lumilumi](https://lumilumi.vercel.app/) The Nostr Web Client. Lightweight modes are available, such as not displaying icon images, not loading images automatically, etc. - [Nostr Follow Organizer](https://tsukemonogit.github.io/NFO/) Follow List ( kind3 ) organization tool. - [NAKE](https://github.com/TsukemonoGit/nake) NIP-19, NIP-49 Encode/Decode Tool - [chrome extension](https://chromewebstore.google.com/detail/nake/pckmdjknadbfalfohabbccmffoohlamk) - [firefox add-on](https://addons.mozilla.org/ja/firefox/addon/nake/) - [nostviewstr](https://nostviewstr.vercel.app/) Addressable or Replaceable Event Editor ( いろんなリストエディター ) - [luminostr](https://tsukemonogit.github.io/luminostr/) Addressable or Replaceable Event Recovery tool ( いろいろリカバリーツール ) - [Nostr Bookmark Recovery Tool](https://nostr-bookmark-recovery-tool.vercel.app/) Bookmark event ( kind:10003,30001,30003 ) recovery tool ( ぶくま復活させたいやつ ) - [Profile Editor](https://nos-profile-arekore.vercel.app/) プロフィールを編集するやつ - [nostr-bookmark-viewer](https://nostr-bookmark-viewer3.vercel.app/) Bookmark event ( kind:10003,30001,30003 ) Editor ( ぶっくまーくをみるやつ ) - [Nostr Note Duplicater](https://dupstr.vercel.app/) Broadcast an event from relay to relay ( イベントをブロードキャストするやつ ) - [もの画像サイト](https://tsukemonogit.github.io/nostr-monoGazo-bot/) - [いろいろbotサイト](https://tsukemonogit.github.io/iroirotest/)
@ 84b0c46a:417782f5
2024-11-19 08:56:39- [lumilumi](https://lumilumi.vercel.app/) The Nostr Web Client. Lightweight modes are available, such as not displaying icon images, not loading images automatically, etc. - [Nostr Follow Organizer](https://tsukemonogit.github.io/NFO/) Follow List ( kind3 ) organization tool. - [NAKE](https://github.com/TsukemonoGit/nake) NIP-19, NIP-49 Encode/Decode Tool - [chrome extension](https://chromewebstore.google.com/detail/nake/pckmdjknadbfalfohabbccmffoohlamk) - [firefox add-on](https://addons.mozilla.org/ja/firefox/addon/nake/) - [nostviewstr](https://nostviewstr.vercel.app/) Addressable or Replaceable Event Editor ( いろんなリストエディター ) - [luminostr](https://tsukemonogit.github.io/luminostr/) Addressable or Replaceable Event Recovery tool ( いろいろリカバリーツール ) - [Nostr Bookmark Recovery Tool](https://nostr-bookmark-recovery-tool.vercel.app/) Bookmark event ( kind:10003,30001,30003 ) recovery tool ( ぶくま復活させたいやつ ) - [Profile Editor](https://nos-profile-arekore.vercel.app/) プロフィールを編集するやつ - [nostr-bookmark-viewer](https://nostr-bookmark-viewer3.vercel.app/) Bookmark event ( kind:10003,30001,30003 ) Editor ( ぶっくまーくをみるやつ ) - [Nostr Note Duplicater](https://dupstr.vercel.app/) Broadcast an event from relay to relay ( イベントをブロードキャストするやつ ) - [もの画像サイト](https://tsukemonogit.github.io/nostr-monoGazo-bot/) - [いろいろbotサイト](https://tsukemonogit.github.io/iroirotest/) @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07## Chef's notes This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is. ## Details - ⏲️ Prep time: 30 - 🍳 Cook time: 0 - 🍽️ Servings: 8 ## Ingredients - 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates - 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates - 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates - 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates - 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates ## Directions 1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake. 2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07## Chef's notes This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is. ## Details - ⏲️ Prep time: 30 - 🍳 Cook time: 0 - 🍽️ Servings: 8 ## Ingredients - 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates - 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates - 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates - 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates - 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates ## Directions 1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake. 2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving. @ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492 @ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
@ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart. @ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima. @ fd208ee8:0fd927c1
2024-11-07 07:22:14## Unsucking the feed is real As a Nostrich with an interesting, thought-provoking, and informative feed... a feed so good, that we're creating clients just to look at that feed... a feed that puts a lie to the idea that Nostr is nothing, but people reposting from Twitter or rehashing worn-out Bitcoin memes... a feed that I personally and increasingly enjoy perusing... I am here to tell you that the feed is real.  It's taken me over a year, to produce this feed. I literally spent hours and hours, day in and day out, scouring the Nostrverse for people worth introducing other people to. It was brutally difficult, as I was fighting the inherent nature of the Nostr clients and relays, in their current, most-popular form. ## It goes like so... Here are the steps I took, that sometimes weren't possible to take, until I tried to take them, and that still will sometimes break your client because the clients are often _intentionally_ designed to steer you into having one particular feed: 1) **Make a screenshot** of your current relay list and copy your follows list. 2) **Unsubscribe from all the relays**, that you are currently subscribed to. Your feed should disappear. If it doesn't, or it doesn't allow for this, switch to a different client app because yours is corrupted. 3) **Unfollow everyone.** Delete the whole list. You are taking your follows private, which will invariably result in only following npubs whose stuff you actually want to see, since there's no longer any virtue-signaling going on. Also, it's easier to explain having no list, than a very short one. If your client doesn't allow for this, or starts throwing error messages and freezing up, then switch to a different client app because yours is corrupted. 4) **Curate your copied follows list.** Go line by line and look at the feed produced by the npub on that list. * Do you want to see that in your feed, going forward? * Do they produce original content and/or are they interesting conversationalists, in the replies? * Have they been active, within the past three months? * Are they simply good friends or real-life acquaintances, that you want to keep tabs on? * If not, cross out their name. * If you have been following someone because they repost or quote interesting things, **look at who they've been reposting** and follow them, instead. 5) Of the npubs remaining on your list, go through and select the 10 most interesting ones, and **look at the reposts and quotes** in their feed, and their topical lists like \"Favorites\", \"Devs\", \"Recipes\", etc. (Not their follows list, unless it's quite short, as follows tend to be full of people they follow for social-signaling or client-functional reasons, that they don't actively look at.) Find some new follows, there. 6) Now, set up a personal relay and add all the follows, that made the cut, to **your allowed-npubs list**. Do not add people to the list, just to make them feel better, or because you feel guilty, as they follow you, or to keep them from yelling at you. Remember, they can't see the list! 7) Think about the topics you find interesting, and add an **allowed-keywords list** (this is better than hashtags, as it searches the entire content of the notes), with the OR operator (these allowed npubs OR these allowed topics). 8) Make sure that you choose words likely to find the content you are most-interested in, and not people just ranting about it or spamming (those are great additions to your relay's block-list). If you are Muslim, for instance, instead of "Islam" or "shariah", choose "hadith" or "riba", as those are words more-likely to be used by people who know what they are talking about. If you are into bread baking, add "sourdough", "rye", "yeast", or "whisk", but don't add "bread" or "carbs". Once a note from those people shows up in your feed, and their feed looks like someone interesting, you can add their npub to your allow list. Remember: **The topics are there to find people to add to the allow list**, not merely for their own sake, as this is not a topical relay, but a personal one. 9) Open up a faucet (or relay syncing) with some of the big relays you previously unsubscribed from, some WoT relays, and some of the paid relays (nostr.land, nostr.wine, nostr21.com, and sovbit.host, for example). **Your relay will filter that feed** and only accept the events from the people and topics on your list. As your relay becomes more popular, npubs will begin writing directly to it, and the connections to other relays will sink in significance. 10) Go to your client of choice and **subscribe to your new relay**. Also subscribe to some topical relays, or curated neighborhood relays, you find interesting or your frens are running. This is an easy way to find new, interesting npubs, to add to your own relay.  That's a lot of work, you say? Yes, but the result is great, and you are now fully in-charge of your own feed. You also -- here's the cool part -- have a feed good enough, that other people can add your feed to theirs and enjoy your manual curation. As you refine and expand your feed, theirs will also be refined, in parallel. You are now an official Nostr Community Curator. My sincere congratulations.  ## Why is this so hard? This is only a lot of work because the clients aren't designed to interact with relays, to this extent, as they were created to service mega-relays, download all their crap to your local cache, and adjust the feed over the follows/mutes lists. This was an idea borne of the axiom that Relays Are Hard, so there will only ever be a handful of them, where we'd all clump together and the relay operators would never judge the quality of someone's content. Then, some unusually clever people made relays increasingly easy, and the mailbox communication model was invented, and here we are. What we have now, and that is slowly growing in popularity, among the #NostrIntelligentsia, are Nostr clients aimed at curating and viewing individual relays or personalized sets of smaller or more-specialized relays. The reigning client devs refused to give us those clients, and most of us aren't up to developing our own clients, so the relay devs took matters into their own hands and made the clients themselves. The free market remains undefeated. This is a total game-changer. Last one to board this train is a rotten egg. Originally, relays were supposed to be completely stupid and clients were supposed to be completely smart, but it's now actually the other way around, because most relay devs have a market-born incentive to make their content highly customizable and appealing to individuals (so that more people run relays). ## But what about algos? Can't you just slap an algo on top of Damus, Lol, or Primal relays, and get the same result? I would argue... no. No, you can't. Or, rather, only in the short to medium term. Running your own relay, is running your own server. You are now _intellectually independent_, at a machine-level, and therefore a fully sovereign consumer. If you then use algos to control your own server, or in a client that subscribes to your own server, then you can further-refine a feed that is already in a high-to-you-signal state, rather than risking an algo inching you toward the Consensus Feed. I have noticed that my own feed is slowly drifting away from the ReplyGuy-Cryptobot-Porny-Bitcoin-Meme Dumpster Fire, that almost everyone else is looking at, and it's due to running my own relay. If I use DVMs, those algos sometimes refer to relays I intentionally avoid, so they return results according to those relays. The results are as underwhelming, as you would expect, and often are simply 31 flavors of the Trending List. But, that isn't your problem, anymore. From here, you can actively expand and refine your feed, over your whitelist, the topics, and your personally-managed algos. Happy Nostr-ing!
@ fd208ee8:0fd927c1
2024-11-07 07:22:14## Unsucking the feed is real As a Nostrich with an interesting, thought-provoking, and informative feed... a feed so good, that we're creating clients just to look at that feed... a feed that puts a lie to the idea that Nostr is nothing, but people reposting from Twitter or rehashing worn-out Bitcoin memes... a feed that I personally and increasingly enjoy perusing... I am here to tell you that the feed is real.  It's taken me over a year, to produce this feed. I literally spent hours and hours, day in and day out, scouring the Nostrverse for people worth introducing other people to. It was brutally difficult, as I was fighting the inherent nature of the Nostr clients and relays, in their current, most-popular form. ## It goes like so... Here are the steps I took, that sometimes weren't possible to take, until I tried to take them, and that still will sometimes break your client because the clients are often _intentionally_ designed to steer you into having one particular feed: 1) **Make a screenshot** of your current relay list and copy your follows list. 2) **Unsubscribe from all the relays**, that you are currently subscribed to. Your feed should disappear. If it doesn't, or it doesn't allow for this, switch to a different client app because yours is corrupted. 3) **Unfollow everyone.** Delete the whole list. You are taking your follows private, which will invariably result in only following npubs whose stuff you actually want to see, since there's no longer any virtue-signaling going on. Also, it's easier to explain having no list, than a very short one. If your client doesn't allow for this, or starts throwing error messages and freezing up, then switch to a different client app because yours is corrupted. 4) **Curate your copied follows list.** Go line by line and look at the feed produced by the npub on that list. * Do you want to see that in your feed, going forward? * Do they produce original content and/or are they interesting conversationalists, in the replies? * Have they been active, within the past three months? * Are they simply good friends or real-life acquaintances, that you want to keep tabs on? * If not, cross out their name. * If you have been following someone because they repost or quote interesting things, **look at who they've been reposting** and follow them, instead. 5) Of the npubs remaining on your list, go through and select the 10 most interesting ones, and **look at the reposts and quotes** in their feed, and their topical lists like \"Favorites\", \"Devs\", \"Recipes\", etc. (Not their follows list, unless it's quite short, as follows tend to be full of people they follow for social-signaling or client-functional reasons, that they don't actively look at.) Find some new follows, there. 6) Now, set up a personal relay and add all the follows, that made the cut, to **your allowed-npubs list**. Do not add people to the list, just to make them feel better, or because you feel guilty, as they follow you, or to keep them from yelling at you. Remember, they can't see the list! 7) Think about the topics you find interesting, and add an **allowed-keywords list** (this is better than hashtags, as it searches the entire content of the notes), with the OR operator (these allowed npubs OR these allowed topics). 8) Make sure that you choose words likely to find the content you are most-interested in, and not people just ranting about it or spamming (those are great additions to your relay's block-list). If you are Muslim, for instance, instead of "Islam" or "shariah", choose "hadith" or "riba", as those are words more-likely to be used by people who know what they are talking about. If you are into bread baking, add "sourdough", "rye", "yeast", or "whisk", but don't add "bread" or "carbs". Once a note from those people shows up in your feed, and their feed looks like someone interesting, you can add their npub to your allow list. Remember: **The topics are there to find people to add to the allow list**, not merely for their own sake, as this is not a topical relay, but a personal one. 9) Open up a faucet (or relay syncing) with some of the big relays you previously unsubscribed from, some WoT relays, and some of the paid relays (nostr.land, nostr.wine, nostr21.com, and sovbit.host, for example). **Your relay will filter that feed** and only accept the events from the people and topics on your list. As your relay becomes more popular, npubs will begin writing directly to it, and the connections to other relays will sink in significance. 10) Go to your client of choice and **subscribe to your new relay**. Also subscribe to some topical relays, or curated neighborhood relays, you find interesting or your frens are running. This is an easy way to find new, interesting npubs, to add to your own relay.  That's a lot of work, you say? Yes, but the result is great, and you are now fully in-charge of your own feed. You also -- here's the cool part -- have a feed good enough, that other people can add your feed to theirs and enjoy your manual curation. As you refine and expand your feed, theirs will also be refined, in parallel. You are now an official Nostr Community Curator. My sincere congratulations.  ## Why is this so hard? This is only a lot of work because the clients aren't designed to interact with relays, to this extent, as they were created to service mega-relays, download all their crap to your local cache, and adjust the feed over the follows/mutes lists. This was an idea borne of the axiom that Relays Are Hard, so there will only ever be a handful of them, where we'd all clump together and the relay operators would never judge the quality of someone's content. Then, some unusually clever people made relays increasingly easy, and the mailbox communication model was invented, and here we are. What we have now, and that is slowly growing in popularity, among the #NostrIntelligentsia, are Nostr clients aimed at curating and viewing individual relays or personalized sets of smaller or more-specialized relays. The reigning client devs refused to give us those clients, and most of us aren't up to developing our own clients, so the relay devs took matters into their own hands and made the clients themselves. The free market remains undefeated. This is a total game-changer. Last one to board this train is a rotten egg. Originally, relays were supposed to be completely stupid and clients were supposed to be completely smart, but it's now actually the other way around, because most relay devs have a market-born incentive to make their content highly customizable and appealing to individuals (so that more people run relays). ## But what about algos? Can't you just slap an algo on top of Damus, Lol, or Primal relays, and get the same result? I would argue... no. No, you can't. Or, rather, only in the short to medium term. Running your own relay, is running your own server. You are now _intellectually independent_, at a machine-level, and therefore a fully sovereign consumer. If you then use algos to control your own server, or in a client that subscribes to your own server, then you can further-refine a feed that is already in a high-to-you-signal state, rather than risking an algo inching you toward the Consensus Feed. I have noticed that my own feed is slowly drifting away from the ReplyGuy-Cryptobot-Porny-Bitcoin-Meme Dumpster Fire, that almost everyone else is looking at, and it's due to running my own relay. If I use DVMs, those algos sometimes refer to relays I intentionally avoid, so they return results according to those relays. The results are as underwhelming, as you would expect, and often are simply 31 flavors of the Trending List. But, that isn't your problem, anymore. From here, you can actively expand and refine your feed, over your whitelist, the topics, and your personally-managed algos. Happy Nostr-ing! @ c2827524:5f45b2f7
2024-11-05 10:40:05 *Remember, remember! The fifth of November, The Gunpowder treason and plot; I know of no reason Why the Gunpowder treason Should ever be forgot! Guy Fawkes and his companions Did the scheme contrive, To blow the King and Parliament All up alive. Threescore barrels, laid below, To prove old England's overthrow. But, by God's providence, him they catch, With a dark lantern, lighting a match!* **È tanto semplice e molto più pacifico oggi.** - [ ] non serve polvere da sparo - [ ] niente violenza (lasciamola a chi ne ha il monopolio, lo shdadoh) - [ ] ci hanno dichiarato guerra e la guerra è economica Rispondiamo semplicemente studiando #Bitcoin  https://t.me/bitcoincampus https://t.me/BitcoinSecPriv https://t.me/bitcoinita https://satoshispritz.it/
@ c2827524:5f45b2f7
2024-11-05 10:40:05 *Remember, remember! The fifth of November, The Gunpowder treason and plot; I know of no reason Why the Gunpowder treason Should ever be forgot! Guy Fawkes and his companions Did the scheme contrive, To blow the King and Parliament All up alive. Threescore barrels, laid below, To prove old England's overthrow. But, by God's providence, him they catch, With a dark lantern, lighting a match!* **È tanto semplice e molto più pacifico oggi.** - [ ] non serve polvere da sparo - [ ] niente violenza (lasciamola a chi ne ha il monopolio, lo shdadoh) - [ ] ci hanno dichiarato guerra e la guerra è economica Rispondiamo semplicemente studiando #Bitcoin  https://t.me/bitcoincampus https://t.me/BitcoinSecPriv https://t.me/bitcoinita https://satoshispritz.it/ @ 2d74600a:d6708a00
2024-11-02 07:12:35L'amore per l'umanità è un tema che ha attraversato secoli di pensiero filosofico, etico e politico. Tuttavia, nel contesto contemporaneo, la definizione di questo amore si complica ulteriormente, specialmente quando si considera l'ideologia del globalismo. Chi si definisce "globalista" spesso proclama un amore universale per l'umanità, ma è fondamentale interrogarsi su cosa significhi realmente questo amore e quale tipo di umanità venga abbracciato. L'umanità del globalista: una massa informe Il globalismo, nella sua essenza, propone una visione dell'umanità che trascende le specificità culturali, etniche e nazionali. In questo contesto, l'umanità è concepita come un'entità astratta, priva di radici e di identità. Essa diventa una massa informe, un aggregato di individui che si muovono secondo logiche economiche e politiche globali, spesso disconnettendosi dalle tradizioni e dalle peculiarità che caratterizzano i diversi popoli. Questo approccio, sebbene possa apparire inclusivo e progressista, rischia di ridurre l'individuo a un mero ingranaggio di un sistema più grande, sacrificando l'autodeterminazione e l'autenticità culturale sull'altare di un'uguaglianza imposta. L'uguaglianza come discriminazione Il concetto di "uguaglianza" promosso dai globalisti, pur essendo nobile in teoria, si traduce spesso in una forma di omologazione che ignora le differenze fondamentali tra le culture. Questa parità, che si presenta come un ideale di giustizia sociale, può assumere il sapore della discriminazione, poiché tende a marginalizzare le microrealtà e le specificità locali. In questo senso, l'amore per l'umanità diventa un'ideologia che, anziché esaltare la diversità, la mortifica, imponendo un modello unico di esistenza che non tiene conto delle storie, delle tradizioni e delle aspirazioni dei singoli popoli. Amare l'umanità: un atto di rispetto per il "Volksgeist" Amare veramente l'umanità implica un riconoscimento e un rispetto per ogni popolo nella sua unicità. Significa esaltare il "Volksgeist", lo spirito di ogni nazione, e comprendere che la ricchezza dell'umanità risiede proprio nella sua diversità. Ogni cultura, ogni tradizione, ogni forma d'arte e mestiere rappresenta un contributo unico al patrimonio collettivo dell'umanità. L'amore autentico per l'umanità non può prescindere dal riconoscimento di queste differenze, ma deve piuttosto celebrarle e proteggerle. La schiavitù moderna: una servitù senza catene La visione globalista, con la sua tendenza a uniformare e standardizzare, può essere vista come una forma di schiavitù moderna, una servitù senza catene. Questa schiavitù si manifesta nella perdita di identità e nella disconnessione dalle proprie radici culturali. L'individuo, privato della sua storia e della sua cultura, diventa un consumatore passivo in un mercato globale, privo di un senso di appartenenza e di significato. In questo contesto, l'amore per l'umanità si trasforma in una legittimazione di un sistema che, sotto la maschera della libertà e dell'uguaglianza, perpetua forme di oppressione e alienazione. Conclusione In conclusione, l'amore per l'umanità, se inteso in modo autentico, deve necessariamente abbracciare la diversità e il particolare. La vera essenza dell'umanità risiede nelle sue molteplici espressioni culturali, nelle tradizioni che la definiscono e nei valori che la sostengono. Solo attraverso il rispetto e la valorizzazione di queste differenze possiamo sperare di costruire un futuro in cui ogni individuo possa sentirsi parte di un tutto, senza dover sacrificare la propria identità. L'amore per l'umanità, quindi, non è un'ideologia astratta, ma un impegno concreto a riconoscere e celebrare la ricchezza della nostra esistenza collettiva.
@ 2d74600a:d6708a00
2024-11-02 07:12:35L'amore per l'umanità è un tema che ha attraversato secoli di pensiero filosofico, etico e politico. Tuttavia, nel contesto contemporaneo, la definizione di questo amore si complica ulteriormente, specialmente quando si considera l'ideologia del globalismo. Chi si definisce "globalista" spesso proclama un amore universale per l'umanità, ma è fondamentale interrogarsi su cosa significhi realmente questo amore e quale tipo di umanità venga abbracciato. L'umanità del globalista: una massa informe Il globalismo, nella sua essenza, propone una visione dell'umanità che trascende le specificità culturali, etniche e nazionali. In questo contesto, l'umanità è concepita come un'entità astratta, priva di radici e di identità. Essa diventa una massa informe, un aggregato di individui che si muovono secondo logiche economiche e politiche globali, spesso disconnettendosi dalle tradizioni e dalle peculiarità che caratterizzano i diversi popoli. Questo approccio, sebbene possa apparire inclusivo e progressista, rischia di ridurre l'individuo a un mero ingranaggio di un sistema più grande, sacrificando l'autodeterminazione e l'autenticità culturale sull'altare di un'uguaglianza imposta. L'uguaglianza come discriminazione Il concetto di "uguaglianza" promosso dai globalisti, pur essendo nobile in teoria, si traduce spesso in una forma di omologazione che ignora le differenze fondamentali tra le culture. Questa parità, che si presenta come un ideale di giustizia sociale, può assumere il sapore della discriminazione, poiché tende a marginalizzare le microrealtà e le specificità locali. In questo senso, l'amore per l'umanità diventa un'ideologia che, anziché esaltare la diversità, la mortifica, imponendo un modello unico di esistenza che non tiene conto delle storie, delle tradizioni e delle aspirazioni dei singoli popoli. Amare l'umanità: un atto di rispetto per il "Volksgeist" Amare veramente l'umanità implica un riconoscimento e un rispetto per ogni popolo nella sua unicità. Significa esaltare il "Volksgeist", lo spirito di ogni nazione, e comprendere che la ricchezza dell'umanità risiede proprio nella sua diversità. Ogni cultura, ogni tradizione, ogni forma d'arte e mestiere rappresenta un contributo unico al patrimonio collettivo dell'umanità. L'amore autentico per l'umanità non può prescindere dal riconoscimento di queste differenze, ma deve piuttosto celebrarle e proteggerle. La schiavitù moderna: una servitù senza catene La visione globalista, con la sua tendenza a uniformare e standardizzare, può essere vista come una forma di schiavitù moderna, una servitù senza catene. Questa schiavitù si manifesta nella perdita di identità e nella disconnessione dalle proprie radici culturali. L'individuo, privato della sua storia e della sua cultura, diventa un consumatore passivo in un mercato globale, privo di un senso di appartenenza e di significato. In questo contesto, l'amore per l'umanità si trasforma in una legittimazione di un sistema che, sotto la maschera della libertà e dell'uguaglianza, perpetua forme di oppressione e alienazione. Conclusione In conclusione, l'amore per l'umanità, se inteso in modo autentico, deve necessariamente abbracciare la diversità e il particolare. La vera essenza dell'umanità risiede nelle sue molteplici espressioni culturali, nelle tradizioni che la definiscono e nei valori che la sostengono. Solo attraverso il rispetto e la valorizzazione di queste differenze possiamo sperare di costruire un futuro in cui ogni individuo possa sentirsi parte di un tutto, senza dover sacrificare la propria identità. L'amore per l'umanità, quindi, non è un'ideologia astratta, ma un impegno concreto a riconoscere e celebrare la ricchezza della nostra esistenza collettiva. @ 2d74600a:d6708a00
2024-11-01 18:51:37Questo articolo esplora la complessità dell'esperienza umana attraverso la lente della tristezza e della felicità, proponendo una distinzione tra le persone che si identificano rigidamente come tristi o felici e quelle che abbracciano la loro autenticità, vivendo un'alternanza di emozioni. Attraverso un'analisi filosofica, si indaga il significato di "essere veri" e si discute l'importanza di riconoscere e accettare la gamma completa delle emozioni umane. Introduzione La condizione umana è intrinsecamente legata a un ampio spettro di emozioni, tra cui la tristezza e la felicità. Queste due esperienze emotive sono spesso percepite come opposte, ma in realtà coesistono in una dinamica complessa. In questo contesto, è utile considerare non solo le persone che si definiscono rigidamente come tristi o felici, ma anche quelle che si riconoscono come "vere", capaci di navigare tra le diverse sfumature emotive. Questo articolo si propone di esaminare le implicazioni filosofiche di questa distinzione e di riflettere su come essa possa influenzare la nostra comprensione dell'autenticità e della realizzazione personale. La Tristezza e la Felicità: Due Facce della Stessa Medaglia La tristezza e la felicità sono spesso considerate come stati emotivi opposti, ma questa visione binaria può risultare limitante. La filosofia esistenzialista, ad esempio, suggerisce che la sofferenza e la gioia sono interconnesse e che la consapevolezza della propria mortalità e delle proprie vulnerabilità può arricchire l'esperienza della vita. In questo senso, la tristezza può essere vista come un elemento necessario per apprezzare la felicità. Le persone che si identificano esclusivamente come tristi o felici possono perdere di vista questa interconnessione, vivendo in una sorta di dualismo emotivo che limita la loro esperienza. L'Autenticità dell'Essere Vero Le persone "vere" rappresentano un paradigma alternativo. Queste individui non si limitano a una categorizzazione emotiva, ma abbracciano la complessità della loro esistenza. La filosofia di Søren Kierkegaard, ad esempio, enfatizza l'importanza dell'autenticità e della soggettività. Essere veri implica riconoscere e accettare tutte le emozioni, comprese quelle che possono sembrare negative. Questa accettazione porta a una maggiore comprensione di sé e degli altri, promuovendo una forma di empatia che trascende le etichette di tristezza e felicità. La Dinamicità delle Emozioni La vita è caratterizzata da un continuo fluire di emozioni. Le persone vere sperimentano alti e bassi, riconoscendo che la tristezza e la felicità non sono stati permanenti, ma piuttosto momenti transitori. Questa visione dinamica delle emozioni è supportata dalla psicologia positiva, che sottolinea l'importanza di sviluppare resilienza e consapevolezza emotiva. Le persone che abbracciano la loro autenticità tendono a essere più resilienti, poiché non temono di affrontare la tristezza, ma la vedono come parte integrante del loro viaggio. Conclusione In conclusione, la distinzione tra persone tristi, felici e quelle vere offre una prospettiva interessante sulla condizione umana. Riconoscere la complessità delle emozioni e abbracciare la propria autenticità può portare a una vita più ricca e significativa. La tristezza e la felicità non devono essere viste come opposti, ma come componenti di un'esperienza umana complessa e interconnessa. Solo attraverso l'accettazione di tutte le sfumature emotive possiamo aspirare a una comprensione più profonda di noi stessi e degli altri, promuovendo una società più empatica e autentica. **Bibliografia** - Kierkegaard, S. (1980). *The Sickness Unto Death*. Princeton University Press. - Seligman, M. E. P. (2011). *Flourish: A Visionary New Understanding of Happiness and Well-Being*. Free Press. - Frankl, V. E. (2006). *Man's Search for Meaning*. Beacon Press. Questo articolo si propone di stimolare una riflessione profonda sulla nostra esperienza emotiva e sull'importanza di vivere in modo autentico, accettando la dualità della nostra esistenza.
@ 2d74600a:d6708a00
2024-11-01 18:51:37Questo articolo esplora la complessità dell'esperienza umana attraverso la lente della tristezza e della felicità, proponendo una distinzione tra le persone che si identificano rigidamente come tristi o felici e quelle che abbracciano la loro autenticità, vivendo un'alternanza di emozioni. Attraverso un'analisi filosofica, si indaga il significato di "essere veri" e si discute l'importanza di riconoscere e accettare la gamma completa delle emozioni umane. Introduzione La condizione umana è intrinsecamente legata a un ampio spettro di emozioni, tra cui la tristezza e la felicità. Queste due esperienze emotive sono spesso percepite come opposte, ma in realtà coesistono in una dinamica complessa. In questo contesto, è utile considerare non solo le persone che si definiscono rigidamente come tristi o felici, ma anche quelle che si riconoscono come "vere", capaci di navigare tra le diverse sfumature emotive. Questo articolo si propone di esaminare le implicazioni filosofiche di questa distinzione e di riflettere su come essa possa influenzare la nostra comprensione dell'autenticità e della realizzazione personale. La Tristezza e la Felicità: Due Facce della Stessa Medaglia La tristezza e la felicità sono spesso considerate come stati emotivi opposti, ma questa visione binaria può risultare limitante. La filosofia esistenzialista, ad esempio, suggerisce che la sofferenza e la gioia sono interconnesse e che la consapevolezza della propria mortalità e delle proprie vulnerabilità può arricchire l'esperienza della vita. In questo senso, la tristezza può essere vista come un elemento necessario per apprezzare la felicità. Le persone che si identificano esclusivamente come tristi o felici possono perdere di vista questa interconnessione, vivendo in una sorta di dualismo emotivo che limita la loro esperienza. L'Autenticità dell'Essere Vero Le persone "vere" rappresentano un paradigma alternativo. Queste individui non si limitano a una categorizzazione emotiva, ma abbracciano la complessità della loro esistenza. La filosofia di Søren Kierkegaard, ad esempio, enfatizza l'importanza dell'autenticità e della soggettività. Essere veri implica riconoscere e accettare tutte le emozioni, comprese quelle che possono sembrare negative. Questa accettazione porta a una maggiore comprensione di sé e degli altri, promuovendo una forma di empatia che trascende le etichette di tristezza e felicità. La Dinamicità delle Emozioni La vita è caratterizzata da un continuo fluire di emozioni. Le persone vere sperimentano alti e bassi, riconoscendo che la tristezza e la felicità non sono stati permanenti, ma piuttosto momenti transitori. Questa visione dinamica delle emozioni è supportata dalla psicologia positiva, che sottolinea l'importanza di sviluppare resilienza e consapevolezza emotiva. Le persone che abbracciano la loro autenticità tendono a essere più resilienti, poiché non temono di affrontare la tristezza, ma la vedono come parte integrante del loro viaggio. Conclusione In conclusione, la distinzione tra persone tristi, felici e quelle vere offre una prospettiva interessante sulla condizione umana. Riconoscere la complessità delle emozioni e abbracciare la propria autenticità può portare a una vita più ricca e significativa. La tristezza e la felicità non devono essere viste come opposti, ma come componenti di un'esperienza umana complessa e interconnessa. Solo attraverso l'accettazione di tutte le sfumature emotive possiamo aspirare a una comprensione più profonda di noi stessi e degli altri, promuovendo una società più empatica e autentica. **Bibliografia** - Kierkegaard, S. (1980). *The Sickness Unto Death*. Princeton University Press. - Seligman, M. E. P. (2011). *Flourish: A Visionary New Understanding of Happiness and Well-Being*. Free Press. - Frankl, V. E. (2006). *Man's Search for Meaning*. Beacon Press. Questo articolo si propone di stimolare una riflessione profonda sulla nostra esperienza emotiva e sull'importanza di vivere in modo autentico, accettando la dualità della nostra esistenza. @ b34b4408:acfb9667
2024-10-31 05:00:15😱 การทบทวนสมมติฐานไขมันกับโรคหัวใจ: มุมมองใหม่จากหลักฐานทางวิทยาศาสตร์ 😱 https://www.mdpi.com/2072-6643/16/10/1447?fbclid=IwY2xjawGOTtxleHRuA2FlbQIxMAABHa2lVBffVeuI0SC8RgzbvQgtkbIsLwat1tDzxZKQ8UoEWYJuwC-Y7no7zA_aem_Qtv0GQuxhWxk0P2KCUFDmw . 🩸บทความนี้นำเสนอการวิเคราะห์เชิงลึกเกี่ยวกับสมมติฐานไขมันกับโรคหัวใจ (Lipid-Heart Hypothesis) ที่มีอิทธิพลต่อแนวทางโภชนาการทั่วโลกมาเกือบ 70 ปี โดยรวบรวมหลักฐานจากการศึกษาวิจัยที่สำคัญและผลกระทบที่เกิดขึ้น . โดยสมมติฐานไขมันกับโรคหัวใจถูกเสนอโดย Ancel Keys ในปี 1953 โดยตั้งอยู่บนความเชื่อว่าการบริโภคไขมันทั้งหมด ไขมันอิ่มตัว และคอเลสเตอรอลในปริมาณสูงจะนำไปสู่การเกิดโรคหัวใจ อย่างไรก็ตาม **สมมติฐานนี้มีข้อบกพร่องสำคัญหลายประการ:** . 1. การรวมไขมันทรานส์กับไขมันอิ่มตัว: - ไม่แยกแยะผลกระทบที่แตกต่างระหว่างไขมันทั้งสองชนิด - ละเลยผลเสียของไขมันทรานส์ที่เกิดจากกระบวนการอุตสาหกรรม . 2. การส่งเสริมการบริโภค PUFA โดยไม่จำกัด: - ขาดการกำหนดขีดจำกัดการบริโภคกรดไขมันไม่อิ่มตัวหลายพันธะ - ไม่คำนึงถึงสมดุลระหว่างโอเมก้า-6 และโอเมก้า-3 . 3. การมองข้ามปัจจัยอื่น: - ไม่พิจารณาผลของน้ำหนักตัว การออกกำลังกาย และปัจจัยด้านวิถีชีวิต - ละเลยบทบาทของการอักเสบและความเครียดออกซิเดชัน . **ซึ่งเมื่อมาดูหลักฐานจากการศึกษาระยะยาวต่างๆเช่น** . .  😲 Framingham Multi-Generational Study (1948-ปัจจุบัน) การศึกษาระยะยาวที่สำคัญนี้ได้พบข้อมูลที่น่าสนใจ: - ไม่พบความสัมพันธ์ระหว่างการบริโภคไขมันกับระดับคอเลสเตอรอล - ยิ่งบริโภคไขมันอิ่มตัว คอเลสเตอรอลและแคลอรี่มาก ระดับคอเลสเตอรอลในเลือดกลับยิ่งต่ำ - ความดันโลหิตสูงและเบาหวานเป็นปัจจัยเสี่ยงสำคัญมากกว่า .  😲Seven Countries Study (1957-1984) การศึกษาในประชากร 7 ประเทศ รวม 12,763 คน พบว่า: - ไม่มีความสัมพันธ์ระหว่างระดับคอเลสเตอรอลกับการเสียชีวิตจากโรคหัวใจ - ประชากรในเกาะครีตที่บริโภคไขมันสูง (36.1%) กลับมีอัตราการเสียชีวิตต่ำที่สุด - น้ำมันมะกอกและกรดไขมันโอเลอิกสัมพันธ์กับอัตราการเสียชีวิตจากโรคหัวใจที่ต่ำ - . 😲PURE Study การศึกษาขนาดใหญ่ในประชากร 18 ประเทศ พบว่า: - การบริโภคไขมันสูงสัมพันธ์กับความเสี่ยงการเสียชีวิตที่ต่ำลง - ไขมันอิ่มตัวสัมพันธ์กับความเสี่ยงโรคหลอดเลือดสมองที่ต่ำลง - ผลิตภัณฑ์นมไขมันเต็มส่งผลดีต่อสุขภาพหัวใจและหลอดเลือด . **รวมถึงการศึกษาทางคลินิกที่สำคัญต่างๆ** .  😟Minnesota Coronary Experiment (1968-1973) ผลการศึกษาในผู้เข้าร่วม 9,423 คน แสดงให้เห็นว่า: - กลุ่มที่บริโภคน้ำมันข้าวโพดมีอัตราการเสียชีวิตสูงกว่า - ผู้ที่ระดับคอเลสเตอรอลลดลงมากที่สุดกลับมีความเสี่ยงสูงที่สุด - ไม่พบประโยชน์ของการแทนที่ไขมันอิ่มตัวด้วย PUFA -  . 😟Sydney Diet Heart Study (1967-1973) การศึกษาในผู้ชาย 458 คน พบว่า: - กลุ่มที่บริโภคน้ำมัน safflower มีอัตราการเสียชีวิตสูงกว่า - ความเสี่ยงการเสียชีวิตจากโรคหัวใจเพิ่มขึ้น 74% - การลดคอเลสเตอรอลไม่ได้นำไปสู่ผลลัพธ์ที่ดีขึ้น . **ทำให้เกิดผลกระทบของในส่วนการแนะนำให้บริโภคอาหารไขมันต่ำ** ซึ่งส่งผลให้เกิดการเปลี่ยนแปลงที่สำคัญ: 😱😱😱 1. การเพิ่มขึ้นของโรคเรื้อรัง: - โรคอ้วนเพิ่มจาก 48.8% (1960) เป็น 82.3% (2017-2018) - เบาหวานเพิ่มจาก 6.2% (1994) เป็น 14.7% (2021) - โรคอัลไซเมอร์เพิ่มจาก 4.5 ล้านคน (2000) เป็น 6.7 ล้านคน (2023) . 2. การเปลี่ยนแปลงรูปแบบการบริโภค: - เพิ่มการบริโภคอาหารแปรรูป - ลดการบริโภคอาหารที่มีคุณค่าทางโภชนาการสูง - เพิ่มการบริโภคคาร์โบไฮเดรตและน้ำตาล . โดยบทความนี้ได้เสนอแนะสำหรับแนวทางโภชนาการใหม่ดังนี้ 😉😉😉 1. การปรับปรุงคำแนะนำด้านอาหาร: - ทบทวนการจำกัดไขมันอิ่มตัว - กำหนดขีดจำกัดการบริโภค PUFA - ส่งเสริมการบริโภคอาหารธรรมชาติ . 2. การพิจารณาปัจจัยรอบด้าน: - คำนึงถึงคุณภาพอาหารโดยรวม - ให้ความสำคัญกับการลดการบริโภคอาหารแปรรูป - พิจารณาปัจจัยด้านวิถีชีวิตและสิ่งแวดล้อม . จากหลักฐานทางวิทยาศาสตร์จำนวนมากไม่สนับสนุนสมมติฐานไขมันกับโรคหัวใจ การจำกัดไขมันอิ่มตัวและส่งเสริมการบริโภค PUFA โดยไม่มีขีดจำกัด อาจส่งผลเสียต่อสุขภาพ จำเป็นต้องมีการทบทวนแนวทางโภชนาการโดยอาศัยหลักฐานที่ทันสมัยและครอบคลุม เพื่อส่งเสริมสุขภาพที่ดีของประชากรในระยะยาว . ...................................... ข้อมูลสุขภาพดีๆที่ไม่มีค่าใช้จ่าย https://www.youtube.com/@fastingfatdentist . หากสนใจวิธีการดูแลสุขภาพตามแบบ IFF ปรึกษาส่วนตัว inbox มาสอบถามที่เพจได้เลยครับ . #ความน่ากลัวในการดูแลสุขภาพคือการที่เชื่อโดยไม่มีความรู้ . . #IFF #IFF_talk #intermittentfasting #keto #Lowcarb #CD #plantbased #RemissionDiabetes #ร่างกายเราคือธรรมชาติไม่ใช่ยา #เบาหวานหายได้โดยไม่ต้องใช้ยา #หมอไหวของหมอแบบนี #fastingfatdentist #healthstr #IFF #fiat #siamstrOG #siamstr #bitcoin #siamesebitcoiners #orangebaby #หมอบ่นFiat
@ b34b4408:acfb9667
2024-10-31 05:00:15😱 การทบทวนสมมติฐานไขมันกับโรคหัวใจ: มุมมองใหม่จากหลักฐานทางวิทยาศาสตร์ 😱 https://www.mdpi.com/2072-6643/16/10/1447?fbclid=IwY2xjawGOTtxleHRuA2FlbQIxMAABHa2lVBffVeuI0SC8RgzbvQgtkbIsLwat1tDzxZKQ8UoEWYJuwC-Y7no7zA_aem_Qtv0GQuxhWxk0P2KCUFDmw . 🩸บทความนี้นำเสนอการวิเคราะห์เชิงลึกเกี่ยวกับสมมติฐานไขมันกับโรคหัวใจ (Lipid-Heart Hypothesis) ที่มีอิทธิพลต่อแนวทางโภชนาการทั่วโลกมาเกือบ 70 ปี โดยรวบรวมหลักฐานจากการศึกษาวิจัยที่สำคัญและผลกระทบที่เกิดขึ้น . โดยสมมติฐานไขมันกับโรคหัวใจถูกเสนอโดย Ancel Keys ในปี 1953 โดยตั้งอยู่บนความเชื่อว่าการบริโภคไขมันทั้งหมด ไขมันอิ่มตัว และคอเลสเตอรอลในปริมาณสูงจะนำไปสู่การเกิดโรคหัวใจ อย่างไรก็ตาม **สมมติฐานนี้มีข้อบกพร่องสำคัญหลายประการ:** . 1. การรวมไขมันทรานส์กับไขมันอิ่มตัว: - ไม่แยกแยะผลกระทบที่แตกต่างระหว่างไขมันทั้งสองชนิด - ละเลยผลเสียของไขมันทรานส์ที่เกิดจากกระบวนการอุตสาหกรรม . 2. การส่งเสริมการบริโภค PUFA โดยไม่จำกัด: - ขาดการกำหนดขีดจำกัดการบริโภคกรดไขมันไม่อิ่มตัวหลายพันธะ - ไม่คำนึงถึงสมดุลระหว่างโอเมก้า-6 และโอเมก้า-3 . 3. การมองข้ามปัจจัยอื่น: - ไม่พิจารณาผลของน้ำหนักตัว การออกกำลังกาย และปัจจัยด้านวิถีชีวิต - ละเลยบทบาทของการอักเสบและความเครียดออกซิเดชัน . **ซึ่งเมื่อมาดูหลักฐานจากการศึกษาระยะยาวต่างๆเช่น** . .  😲 Framingham Multi-Generational Study (1948-ปัจจุบัน) การศึกษาระยะยาวที่สำคัญนี้ได้พบข้อมูลที่น่าสนใจ: - ไม่พบความสัมพันธ์ระหว่างการบริโภคไขมันกับระดับคอเลสเตอรอล - ยิ่งบริโภคไขมันอิ่มตัว คอเลสเตอรอลและแคลอรี่มาก ระดับคอเลสเตอรอลในเลือดกลับยิ่งต่ำ - ความดันโลหิตสูงและเบาหวานเป็นปัจจัยเสี่ยงสำคัญมากกว่า .  😲Seven Countries Study (1957-1984) การศึกษาในประชากร 7 ประเทศ รวม 12,763 คน พบว่า: - ไม่มีความสัมพันธ์ระหว่างระดับคอเลสเตอรอลกับการเสียชีวิตจากโรคหัวใจ - ประชากรในเกาะครีตที่บริโภคไขมันสูง (36.1%) กลับมีอัตราการเสียชีวิตต่ำที่สุด - น้ำมันมะกอกและกรดไขมันโอเลอิกสัมพันธ์กับอัตราการเสียชีวิตจากโรคหัวใจที่ต่ำ - . 😲PURE Study การศึกษาขนาดใหญ่ในประชากร 18 ประเทศ พบว่า: - การบริโภคไขมันสูงสัมพันธ์กับความเสี่ยงการเสียชีวิตที่ต่ำลง - ไขมันอิ่มตัวสัมพันธ์กับความเสี่ยงโรคหลอดเลือดสมองที่ต่ำลง - ผลิตภัณฑ์นมไขมันเต็มส่งผลดีต่อสุขภาพหัวใจและหลอดเลือด . **รวมถึงการศึกษาทางคลินิกที่สำคัญต่างๆ** .  😟Minnesota Coronary Experiment (1968-1973) ผลการศึกษาในผู้เข้าร่วม 9,423 คน แสดงให้เห็นว่า: - กลุ่มที่บริโภคน้ำมันข้าวโพดมีอัตราการเสียชีวิตสูงกว่า - ผู้ที่ระดับคอเลสเตอรอลลดลงมากที่สุดกลับมีความเสี่ยงสูงที่สุด - ไม่พบประโยชน์ของการแทนที่ไขมันอิ่มตัวด้วย PUFA -  . 😟Sydney Diet Heart Study (1967-1973) การศึกษาในผู้ชาย 458 คน พบว่า: - กลุ่มที่บริโภคน้ำมัน safflower มีอัตราการเสียชีวิตสูงกว่า - ความเสี่ยงการเสียชีวิตจากโรคหัวใจเพิ่มขึ้น 74% - การลดคอเลสเตอรอลไม่ได้นำไปสู่ผลลัพธ์ที่ดีขึ้น . **ทำให้เกิดผลกระทบของในส่วนการแนะนำให้บริโภคอาหารไขมันต่ำ** ซึ่งส่งผลให้เกิดการเปลี่ยนแปลงที่สำคัญ: 😱😱😱 1. การเพิ่มขึ้นของโรคเรื้อรัง: - โรคอ้วนเพิ่มจาก 48.8% (1960) เป็น 82.3% (2017-2018) - เบาหวานเพิ่มจาก 6.2% (1994) เป็น 14.7% (2021) - โรคอัลไซเมอร์เพิ่มจาก 4.5 ล้านคน (2000) เป็น 6.7 ล้านคน (2023) . 2. การเปลี่ยนแปลงรูปแบบการบริโภค: - เพิ่มการบริโภคอาหารแปรรูป - ลดการบริโภคอาหารที่มีคุณค่าทางโภชนาการสูง - เพิ่มการบริโภคคาร์โบไฮเดรตและน้ำตาล . โดยบทความนี้ได้เสนอแนะสำหรับแนวทางโภชนาการใหม่ดังนี้ 😉😉😉 1. การปรับปรุงคำแนะนำด้านอาหาร: - ทบทวนการจำกัดไขมันอิ่มตัว - กำหนดขีดจำกัดการบริโภค PUFA - ส่งเสริมการบริโภคอาหารธรรมชาติ . 2. การพิจารณาปัจจัยรอบด้าน: - คำนึงถึงคุณภาพอาหารโดยรวม - ให้ความสำคัญกับการลดการบริโภคอาหารแปรรูป - พิจารณาปัจจัยด้านวิถีชีวิตและสิ่งแวดล้อม . จากหลักฐานทางวิทยาศาสตร์จำนวนมากไม่สนับสนุนสมมติฐานไขมันกับโรคหัวใจ การจำกัดไขมันอิ่มตัวและส่งเสริมการบริโภค PUFA โดยไม่มีขีดจำกัด อาจส่งผลเสียต่อสุขภาพ จำเป็นต้องมีการทบทวนแนวทางโภชนาการโดยอาศัยหลักฐานที่ทันสมัยและครอบคลุม เพื่อส่งเสริมสุขภาพที่ดีของประชากรในระยะยาว . ...................................... ข้อมูลสุขภาพดีๆที่ไม่มีค่าใช้จ่าย https://www.youtube.com/@fastingfatdentist . หากสนใจวิธีการดูแลสุขภาพตามแบบ IFF ปรึกษาส่วนตัว inbox มาสอบถามที่เพจได้เลยครับ . #ความน่ากลัวในการดูแลสุขภาพคือการที่เชื่อโดยไม่มีความรู้ . . #IFF #IFF_talk #intermittentfasting #keto #Lowcarb #CD #plantbased #RemissionDiabetes #ร่างกายเราคือธรรมชาติไม่ใช่ยา #เบาหวานหายได้โดยไม่ต้องใช้ยา #หมอไหวของหมอแบบนี #fastingfatdentist #healthstr #IFF #fiat #siamstrOG #siamstr #bitcoin #siamesebitcoiners #orangebaby #หมอบ่นFiat @ 4ba8e86d:89d32de4
2024-10-25 13:17:33Foi criado com o objetivo de fornecer aos usuários uma experiência de navegação mais privada e segura na internet. O LibreWolf é uma excelente alternativa ao Firefox, com algumas diferenças significativas em relação ao navegador da Mozilla. O LibreWolf foi desenvolvido com foco na privacidade e segurança do usuário. Ele bloqueia rastreadores de terceiros, impede o envio de dados de telemetria e desabilita recursos de rastreamento de usuário que vêm ativados por padrão no Firefox. Além disso, ele vem pré-configurado com diversas extensões de privacidade, como uBlock Origin, Privacy Badger e HTTPS Everywhere, que ajudam a bloquear anúncios, scripts maliciosos e outras ameaças de segurança enquanto você navega na web. Outra característica notável do LibreWolf é que ele usa o mecanismo de pesquisa Searx como padrão, em vez do Google. O Searx é conhecido por fornecer resultados de pesquisa mais privados e anônimos, sem rastrear as suas atividades online. O LibreWolf também possui suporte nativo ao Tor, que permite aos usuários acessar a internet anonimamente. Além dos recursos de privacidade e segurança, o LibreWolf é muito semelhante ao Firefox em termos de usabilidade e funcionalidades. Ele é fácil de instalar e configurar, e possui um grande número de extensões disponíveis na sua loja de extensões. O LibreWolf é uma excelente opção para usuários que buscam um navegador mais privado e seguro. Se você se preocupa com a sua privacidade online, vale a pena experimentar o LibreWolf. Ele é gratuito e de código aberto, o que significa que você pode baixá-lo e personalizá-lo de acordo com suas necessidades específicas. https://librewolf.net/ https://github.com/librewolf-community
@ 4ba8e86d:89d32de4
2024-10-25 13:17:33Foi criado com o objetivo de fornecer aos usuários uma experiência de navegação mais privada e segura na internet. O LibreWolf é uma excelente alternativa ao Firefox, com algumas diferenças significativas em relação ao navegador da Mozilla. O LibreWolf foi desenvolvido com foco na privacidade e segurança do usuário. Ele bloqueia rastreadores de terceiros, impede o envio de dados de telemetria e desabilita recursos de rastreamento de usuário que vêm ativados por padrão no Firefox. Além disso, ele vem pré-configurado com diversas extensões de privacidade, como uBlock Origin, Privacy Badger e HTTPS Everywhere, que ajudam a bloquear anúncios, scripts maliciosos e outras ameaças de segurança enquanto você navega na web. Outra característica notável do LibreWolf é que ele usa o mecanismo de pesquisa Searx como padrão, em vez do Google. O Searx é conhecido por fornecer resultados de pesquisa mais privados e anônimos, sem rastrear as suas atividades online. O LibreWolf também possui suporte nativo ao Tor, que permite aos usuários acessar a internet anonimamente. Além dos recursos de privacidade e segurança, o LibreWolf é muito semelhante ao Firefox em termos de usabilidade e funcionalidades. Ele é fácil de instalar e configurar, e possui um grande número de extensões disponíveis na sua loja de extensões. O LibreWolf é uma excelente opção para usuários que buscam um navegador mais privado e seguro. Se você se preocupa com a sua privacidade online, vale a pena experimentar o LibreWolf. Ele é gratuito e de código aberto, o que significa que você pode baixá-lo e personalizá-lo de acordo com suas necessidades específicas. https://librewolf.net/ https://github.com/librewolf-community @ c230edd3:8ad4a712
2024-10-21 22:24:42## Chef's notes This is great to start in the morning, and come home to a nearly finished meal. I like to make tacos that day, then use any remaining for just about anything from chili to omelets. Fun way to prepare ramen too. ## Details - ⏲️ Prep time: 30 min, plus 15 before serving - 🍳 Cook time: 8 hours - 🍽️ Servings: 10-12 ## Ingredients - 3-4lb Chuck Roast, bone-in preferred - 1 large White Onion, quartered - 6-8 cloves Garlic, peeled - 5 Roma Tomatoes, halved - 6-8 dried Arbol Chiles, seeded - 3-4 Guajillo Chiles, seeded - 2 tsp Coriander seeds - 2 tsp Cumin seeds - 2 Tbsp Oregano, Mexican Oregano if available - 1/2 tsp ground Cinnamon - 2 whole Bay Leaves - 1 tsp Salt - SPG style seasoning mix to coat the roast - Any toppings desired (avocado, cilantro, sour cream, queso fresca, cheddar, fresh onion, etc) ## Directions 1. Preheat large frying pan to med/high, add oil for searing 2. Add onions and tomatoes, sear until edges char, add garlic and saute until fragrant, transfer to slow cooker 3. Pat roast dry, season all sides, transfer to pan 4. Sear roast on all sides, 2-4 minutes or until golden brown, transfer to slow cooker 5. Add all seasonings and beef broth to slow cooker 6. Cook on low 8+ hours or until the meat is falling apart 7. Remove bone and bay leaves 8. Transfer liquid and vegetables to a blender with loose fitting lid, blend until smooth, transfer to large bowl 9. Shred roast in slow cooker, pour sauce mix back in and stir. Adjust ratio by adding more beef broth if desired. Salt to taste. 10. Serve, drained as tacos, nachos, omelets, etc. Serve with broth as stew or mix with ramen
@ c230edd3:8ad4a712
2024-10-21 22:24:42## Chef's notes This is great to start in the morning, and come home to a nearly finished meal. I like to make tacos that day, then use any remaining for just about anything from chili to omelets. Fun way to prepare ramen too. ## Details - ⏲️ Prep time: 30 min, plus 15 before serving - 🍳 Cook time: 8 hours - 🍽️ Servings: 10-12 ## Ingredients - 3-4lb Chuck Roast, bone-in preferred - 1 large White Onion, quartered - 6-8 cloves Garlic, peeled - 5 Roma Tomatoes, halved - 6-8 dried Arbol Chiles, seeded - 3-4 Guajillo Chiles, seeded - 2 tsp Coriander seeds - 2 tsp Cumin seeds - 2 Tbsp Oregano, Mexican Oregano if available - 1/2 tsp ground Cinnamon - 2 whole Bay Leaves - 1 tsp Salt - SPG style seasoning mix to coat the roast - Any toppings desired (avocado, cilantro, sour cream, queso fresca, cheddar, fresh onion, etc) ## Directions 1. Preheat large frying pan to med/high, add oil for searing 2. Add onions and tomatoes, sear until edges char, add garlic and saute until fragrant, transfer to slow cooker 3. Pat roast dry, season all sides, transfer to pan 4. Sear roast on all sides, 2-4 minutes or until golden brown, transfer to slow cooker 5. Add all seasonings and beef broth to slow cooker 6. Cook on low 8+ hours or until the meat is falling apart 7. Remove bone and bay leaves 8. Transfer liquid and vegetables to a blender with loose fitting lid, blend until smooth, transfer to large bowl 9. Shred roast in slow cooker, pour sauce mix back in and stir. Adjust ratio by adding more beef broth if desired. Salt to taste. 10. Serve, drained as tacos, nachos, omelets, etc. Serve with broth as stew or mix with ramen @ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.) # A long, long time ago It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned. So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a [GitHub repo](https://github.com/ShadowySupercode), and lots of frustration with the Nostr status quo. We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations. * Why can I not login? Oh, they fixed the login! Nope, still can't login. * If I press this button, it says it sent, but it didn't send. Where note? * They announced a new feature, but I tried it and it didn't work. Oh well. * I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored. * The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it. It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it _really_ needed... was a **Nostr Stable Version**. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be _allowed to have expectations_ of some particular service being returned. And who better to build such a version, than people who want to use it, themselves? # Things working is an underrated concept I know that the very idea of software _running as expected_ and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are _all_ features), but I think the majority of potential users would see it differently. I'm with the majority, on this one. I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention. My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load _every damn time_, just to spite you. In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that _things working_ becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit. We can only win, at this endeavor. # Where to start? ## Name that brand So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.) We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.). ## Brand yourself The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company. ## Define yourself We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal. What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our [project wiki page](https://wikistr.com/gitcitadel-project), and came up with a Vision and a Mission:  The _vision_ is what the overall goals of the company are, whereas the _mission_ describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next. ## Pay yourselves (I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)  The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.) I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because _profits are the most pure form of communication that consumers in the market have_ with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling). Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial _lambo and a bimbo_. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but **pay them out, you should**. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition. (Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.) ## Organize yourselves Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to... ### Form a board of directors. Stop laughing. I'm serious. Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone. If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what. Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the _okay, so this is what we've decided_ comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc. And everyone knows who the CEO is. Everyone always knows. They do. Just write it down. ### Agree how to disagree Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to [Investopedia](https://www.investopedia.com/terms/l/llc-operating-agreement.asp), common topics are:  Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's _emotionally binding_, which is arguably more important. Writing things down is an advanced form of _naming things_ and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate. Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print. ## Go forth, together This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.) # A long, long time ago It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned. So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a [GitHub repo](https://github.com/ShadowySupercode), and lots of frustration with the Nostr status quo. We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations. * Why can I not login? Oh, they fixed the login! Nope, still can't login. * If I press this button, it says it sent, but it didn't send. Where note? * They announced a new feature, but I tried it and it didn't work. Oh well. * I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored. * The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it. It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it _really_ needed... was a **Nostr Stable Version**. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be _allowed to have expectations_ of some particular service being returned. And who better to build such a version, than people who want to use it, themselves? # Things working is an underrated concept I know that the very idea of software _running as expected_ and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are _all_ features), but I think the majority of potential users would see it differently. I'm with the majority, on this one. I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention. My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load _every damn time_, just to spite you. In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that _things working_ becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit. We can only win, at this endeavor. # Where to start? ## Name that brand So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.) We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.). ## Brand yourself The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company. ## Define yourself We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal. What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our [project wiki page](https://wikistr.com/gitcitadel-project), and came up with a Vision and a Mission:  The _vision_ is what the overall goals of the company are, whereas the _mission_ describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next. ## Pay yourselves (I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)  The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.) I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because _profits are the most pure form of communication that consumers in the market have_ with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling). Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial _lambo and a bimbo_. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but **pay them out, you should**. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition. (Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.) ## Organize yourselves Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to... ### Form a board of directors. Stop laughing. I'm serious. Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone. If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what. Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the _okay, so this is what we've decided_ comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc. And everyone knows who the CEO is. Everyone always knows. They do. Just write it down. ### Agree how to disagree Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to [Investopedia](https://www.investopedia.com/terms/l/llc-operating-agreement.asp), common topics are:  Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's _emotionally binding_, which is arguably more important. Writing things down is an advanced form of _naming things_ and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate. Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print. ## Go forth, together This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business. @ dc4cd086:cee77c06
2024-10-18 04:08:33Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content. ## Key Features: ### Video Processing: - Automatically downloads YouTube videos, transcripts, and chapter information - Splits transcripts into sections based on video chapters ### Content Summarization: - Utilizes language models to transform spoken content into clear, readable text - Formats output in AsciiDoc for improved readability and navigation - Highlights key terms and concepts with [[term]] notation for potential cross-referencing ### Diagram Extraction: - Analyzes video entropy to identify static diagram/slide sections - Provides a user-friendly GUI for manual selection of relevant time ranges - Allows users to pick representative frames from selected ranges ## Going Forward: Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care. While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs. ## Screenshots ### Frame Selection  This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection. ### Diagram Extraction  This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save. ## Links - repo: https://github.com/limina1/video_article_converter - Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE ## Output And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn Or view on Coracle nostr:nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
@ dc4cd086:cee77c06
2024-10-18 04:08:33Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content. ## Key Features: ### Video Processing: - Automatically downloads YouTube videos, transcripts, and chapter information - Splits transcripts into sections based on video chapters ### Content Summarization: - Utilizes language models to transform spoken content into clear, readable text - Formats output in AsciiDoc for improved readability and navigation - Highlights key terms and concepts with [[term]] notation for potential cross-referencing ### Diagram Extraction: - Analyzes video entropy to identify static diagram/slide sections - Provides a user-friendly GUI for manual selection of relevant time ranges - Allows users to pick representative frames from selected ranges ## Going Forward: Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care. While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs. ## Screenshots ### Frame Selection  This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection. ### Diagram Extraction  This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save. ## Links - repo: https://github.com/limina1/video_article_converter - Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE ## Output And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn Or view on Coracle nostr:nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3 @ 472f440f:5669301e
2024-10-11 14:20:54As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward. Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years. It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering. Speaking of the job market, the numbers that came in yesterday were worse than expected: The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now. All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential. There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries. The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority. The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare. I'll leave you with some thoughts from Porter Stansberry: "We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked. 1. Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet. 2. Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow. 3. Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror. Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it. Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money. And that day is here." --- Final thought... I hope my tux still fits for this wedding. Enjoy your weekend, freaks.Use the code "TFTC" for 15% off
@ 472f440f:5669301e
2024-10-11 14:20:54As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward. Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years. It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering. Speaking of the job market, the numbers that came in yesterday were worse than expected: The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now. All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential. There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries. The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority. The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare. I'll leave you with some thoughts from Porter Stansberry: "We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked. 1. Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet. 2. Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow. 3. Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror. Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it. Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money. And that day is here." --- Final thought... I hope my tux still fits for this wedding. Enjoy your weekend, freaks.Use the code "TFTC" for 15% off @ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever. nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees: nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp But how big is too big? How can we better understand the range of options available for devs out there? I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof. - **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports. - **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them. - **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped. Based on my made-up categories described at the end, this is how I would split our most known apps. **Super Clients** - [amethyst](https://amethyst.social) - [nostrudel](https://nostrudel.ninja) - [coracle](https://coracle.social) **Clients** - [damus](https://damus.io) - twitter - [primal](https://primal.net) - twitter - [snort](https://snort.social) - twitter - [gossip](https://github.com/mikedilger/gossip) - twitter - [lume](https://lume.nu) - twitter - [ditto](https://soapbox.pub/ditto/) - twitter - [rabbit](https://rabbit.syusui.net) - twitter - [freefrom](https://freefrom.space) - twitter - [nos](https://nos.social) - twitter - [flycat](https://flycat.club) - twitter - [straylight](https://straylight.cafe) - twitter - [nostter](https://nostter.app) - twitter - [iris](https://iris.to) - twitter - [nostur](https://nostur.com) - twitter - [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter - [yana](https://yana.do) - twitter - [openvibe](https://openvibe.social) - twitter - [freerse](https://freerse.com) - twitter - [0xchat](https://0xchat.com) - chats - [cornychat](https://cornychat.com) - chats - [coop](https://github.com/lumehq/coop) - chats - [nostrchat](https://nostrchat.io) - chats - [blowater](https://blowater.deno.dev) - chats - [habla](https://habla.news) - blogs - [yakihonne](https://yakihonne.com) - blogs - [highlighter](https://highlighter.com) - blogs - [blogstack](https://blogstack.io) - blogs - [stemstr](https://stemstr.app) - music - [wavlake](https://wavlake.com) - music - [fountain](https://fountain.fm) - podcasts - [zap.stream](https://zap.stream) - live streaming - [shopstr](https://shopstr.store) - marketplace - [plebeian.market](https://plebeian.market) - marketplace - [flotilla](https://flotilla.coracle.social) - communities - [satellite](https://satellite.earth) - communities - [zapddit](https://zapddit.com) - communities - [nostr.kiwi](https://nostr.kiwi) - communities - [hivetalk](https://hivetalk.org) - video calls - [flare](https://flare.pub) - long-form videos - [nostrnests](https://nostrnests.com) - audio spaces - [wherostr](https://wherostr.social) - location - [yondar](https://go.yondar.me) - location - [stacker.news](https://stacker.news) - news - [flockstr](https://flockstr.com) - events - [nostrocket](https://nostrocket.org) - issue tracker - [docstr](https://docstr.app) - docs - [satshoot](https://satshoot.com) - freelance - [wikifreedia](https://wikifreedia.xyz) - wiki - [formstr](https://formstr.app) - forms - [chesstr](https://chesstr.pages.dev) - chess - [memestr](https://memestr.app) - meme feed - [npub.cash](https://npub.cash) - wallet - [npub.pro](https://npub.pro) - websites - [gitworkshop](https://gitworkshop.dev) - dev tools - [onosendai](https://onosendai.tech) - metaverse - [degmods](https://degmods.com) - games - [turdsoup](https://turdsoup.com) - prompts **Mini Clients** - [amber](https://github.com/greenart7c3/Amber) - signer - [alby](https://getalby.com) - signer - [nos2x](https://github.com/fiatjaf/nos2x) - signer - [nsec.app](https://nsec.app) - signer - [keys.band](https://keys.band) - signer - [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer - [nokakoi](https://nokakoi.com) - anon - [zap.cooking](https://zap.cooking) - recipes - [anonostr](https://anonostr.com) - anon - [getwired](https://getwired.app) - anon - [lowent](https://lowent.xyz) - anon - [creatr](https://creatr.nostr.wine) - exclusive content - [lightning.video](https://lightning.video) - exclusive content - [zaplinks](https://zaplinks.lol/slides) - slides - [listr](https://listr.lol) - lists - [zap.store](https://zap.store) - app store - [badges.page](https://badges.page) - badges - [oddbean](https://oddbean.com) - news - [dtan](https://dtan.xyz) - torrents - [nosta](https://nosta.me) - user pages - [pinstr](https://pinstr.app) - pinterest - [pollerama](https://pollerama.fun) - polls - [swarmstr](https://swarmstr.com) - trending - [nostrapp](https://nostrapp.link) - apps manager - [noogle](https://noogle.lol) - search - [ostrich.work](https://ostrich.work) - job postings - [emojito](https://emojito.meme) - emoji manager - [nostree](https://nostree.me) - links - [citrine](https://github.com/greenart7c3/citrine) - local relay - [joinstr](https://joinstr.xyz) - coinjoins - [heya](https://heya.fund) - crowdfunding - [zapplepay](https://zapplepay.com) - zaps - [nosbin](https://nosbin.com) - clipboard - [shipyard](https://shipyard.pub) - scheduler - [tunestr](https://tunestr.io) - live streams - [filestr](https://filestr.vercel.app) - files - [nostrcheck.me](https://nostrcheck.me/) - media hosting - [sheetstr](https://sheetstr.amethyst.social) - spreadsheets - [crafters](https://crafters.amethyst.social) - curriculum vitae **Micro Clients** - [w3](https://w3.do) - url shortener - [nosdrive](https://nosdrive.app) - backups - [zaplife](https://zaplife.lol) - zaps dashboard - [zapper.fun](https://zapper.fun) - payments - [nostrends](https://nostrends.vercel.app) - trends - [zephyr](https://zephyr.coracle.social) - trends - [wavman](https://wavman.app) - music player - [nostrrr](https://nostrrr.com) - relay info - [nosdump](https://github.com/jiftechnify/nosdump) - relay info - [notestack](https://notestack.com) - blogs - [nostr.build](https://nostr.build) - media hosting - [nostr.watch](https://nostr.watch) - relay info - [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports - [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions - [snakestr](https://satoshipuzzles.github.io/Snakestr) - games - [deletestr](https://zaplinks.lol/deletestr) - deletion requests - [2048str](https://zaplinks.lol/2048str) - games - [nostrqr](https://zaplinks.lol/nostrqr) - qr generator - [notanostrclient](https://zaplinks.lol/notanostrclient) - anon Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients.
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever. nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees: nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp But how big is too big? How can we better understand the range of options available for devs out there? I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof. - **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports. - **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them. - **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped. Based on my made-up categories described at the end, this is how I would split our most known apps. **Super Clients** - [amethyst](https://amethyst.social) - [nostrudel](https://nostrudel.ninja) - [coracle](https://coracle.social) **Clients** - [damus](https://damus.io) - twitter - [primal](https://primal.net) - twitter - [snort](https://snort.social) - twitter - [gossip](https://github.com/mikedilger/gossip) - twitter - [lume](https://lume.nu) - twitter - [ditto](https://soapbox.pub/ditto/) - twitter - [rabbit](https://rabbit.syusui.net) - twitter - [freefrom](https://freefrom.space) - twitter - [nos](https://nos.social) - twitter - [flycat](https://flycat.club) - twitter - [straylight](https://straylight.cafe) - twitter - [nostter](https://nostter.app) - twitter - [iris](https://iris.to) - twitter - [nostur](https://nostur.com) - twitter - [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter - [yana](https://yana.do) - twitter - [openvibe](https://openvibe.social) - twitter - [freerse](https://freerse.com) - twitter - [0xchat](https://0xchat.com) - chats - [cornychat](https://cornychat.com) - chats - [coop](https://github.com/lumehq/coop) - chats - [nostrchat](https://nostrchat.io) - chats - [blowater](https://blowater.deno.dev) - chats - [habla](https://habla.news) - blogs - [yakihonne](https://yakihonne.com) - blogs - [highlighter](https://highlighter.com) - blogs - [blogstack](https://blogstack.io) - blogs - [stemstr](https://stemstr.app) - music - [wavlake](https://wavlake.com) - music - [fountain](https://fountain.fm) - podcasts - [zap.stream](https://zap.stream) - live streaming - [shopstr](https://shopstr.store) - marketplace - [plebeian.market](https://plebeian.market) - marketplace - [flotilla](https://flotilla.coracle.social) - communities - [satellite](https://satellite.earth) - communities - [zapddit](https://zapddit.com) - communities - [nostr.kiwi](https://nostr.kiwi) - communities - [hivetalk](https://hivetalk.org) - video calls - [flare](https://flare.pub) - long-form videos - [nostrnests](https://nostrnests.com) - audio spaces - [wherostr](https://wherostr.social) - location - [yondar](https://go.yondar.me) - location - [stacker.news](https://stacker.news) - news - [flockstr](https://flockstr.com) - events - [nostrocket](https://nostrocket.org) - issue tracker - [docstr](https://docstr.app) - docs - [satshoot](https://satshoot.com) - freelance - [wikifreedia](https://wikifreedia.xyz) - wiki - [formstr](https://formstr.app) - forms - [chesstr](https://chesstr.pages.dev) - chess - [memestr](https://memestr.app) - meme feed - [npub.cash](https://npub.cash) - wallet - [npub.pro](https://npub.pro) - websites - [gitworkshop](https://gitworkshop.dev) - dev tools - [onosendai](https://onosendai.tech) - metaverse - [degmods](https://degmods.com) - games - [turdsoup](https://turdsoup.com) - prompts **Mini Clients** - [amber](https://github.com/greenart7c3/Amber) - signer - [alby](https://getalby.com) - signer - [nos2x](https://github.com/fiatjaf/nos2x) - signer - [nsec.app](https://nsec.app) - signer - [keys.band](https://keys.band) - signer - [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer - [nokakoi](https://nokakoi.com) - anon - [zap.cooking](https://zap.cooking) - recipes - [anonostr](https://anonostr.com) - anon - [getwired](https://getwired.app) - anon - [lowent](https://lowent.xyz) - anon - [creatr](https://creatr.nostr.wine) - exclusive content - [lightning.video](https://lightning.video) - exclusive content - [zaplinks](https://zaplinks.lol/slides) - slides - [listr](https://listr.lol) - lists - [zap.store](https://zap.store) - app store - [badges.page](https://badges.page) - badges - [oddbean](https://oddbean.com) - news - [dtan](https://dtan.xyz) - torrents - [nosta](https://nosta.me) - user pages - [pinstr](https://pinstr.app) - pinterest - [pollerama](https://pollerama.fun) - polls - [swarmstr](https://swarmstr.com) - trending - [nostrapp](https://nostrapp.link) - apps manager - [noogle](https://noogle.lol) - search - [ostrich.work](https://ostrich.work) - job postings - [emojito](https://emojito.meme) - emoji manager - [nostree](https://nostree.me) - links - [citrine](https://github.com/greenart7c3/citrine) - local relay - [joinstr](https://joinstr.xyz) - coinjoins - [heya](https://heya.fund) - crowdfunding - [zapplepay](https://zapplepay.com) - zaps - [nosbin](https://nosbin.com) - clipboard - [shipyard](https://shipyard.pub) - scheduler - [tunestr](https://tunestr.io) - live streams - [filestr](https://filestr.vercel.app) - files - [nostrcheck.me](https://nostrcheck.me/) - media hosting - [sheetstr](https://sheetstr.amethyst.social) - spreadsheets - [crafters](https://crafters.amethyst.social) - curriculum vitae **Micro Clients** - [w3](https://w3.do) - url shortener - [nosdrive](https://nosdrive.app) - backups - [zaplife](https://zaplife.lol) - zaps dashboard - [zapper.fun](https://zapper.fun) - payments - [nostrends](https://nostrends.vercel.app) - trends - [zephyr](https://zephyr.coracle.social) - trends - [wavman](https://wavman.app) - music player - [nostrrr](https://nostrrr.com) - relay info - [nosdump](https://github.com/jiftechnify/nosdump) - relay info - [notestack](https://notestack.com) - blogs - [nostr.build](https://nostr.build) - media hosting - [nostr.watch](https://nostr.watch) - relay info - [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports - [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions - [snakestr](https://satoshipuzzles.github.io/Snakestr) - games - [deletestr](https://zaplinks.lol/deletestr) - deletion requests - [2048str](https://zaplinks.lol/2048str) - games - [nostrqr](https://zaplinks.lol/nostrqr) - qr generator - [notanostrclient](https://zaplinks.lol/notanostrclient) - anon Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients. @ fd208ee8:0fd927c1
2024-10-09 12:27:53## Why waste time, looking at other people's stuff? I get this question a lot, on Nostr, and it feeds immediately back to the next question: *Why don't you just build your own client, if you're so smart?* This was a completely new question for me, as I'm used to collaborating with at least one other person, even when doing FOSS stuff. (No, this isn't my first such project; we just used to call it "volunteering" and "sharing the code", which sounds way less glamorous.) It never occurred to me, that a habit of collaboration and interaction was some sign of my ignorance and incompetence, or somehow proof that I can't vomit up "Hello World!" in 5 different programming languages. I also made the deadly political mistake, when I entered the Nostrsphere, of refusing to call myself a "dev". For me, "dev" is a special title, given to someone doing a specific type of programming (fiddling with GUIs, mostly, which I've only done occasionally, as a sub), whereas the types I've done are "test automation", "development operations", "database management and data curation", "requirements engineering", and "application administration". Because it's so much easier to find someone interested in building a GUI, rather than building AnythingElse, I tend to slide into AnythingElse and it eventually became my professional specialty to be the Girl Friday of every project.  But, in Nostr, there is no AnythingElse category. There are only (GUI) client devs and AllOfTheIdiotsWhoMustBowDownToTheDevs. Which merely doubled my instinct to distance myself from the term. I do not want to join some cargo cult and be pedestalized and regarded as some sort of superhuman everyone owes fealty to, in return for raining GUI presents down on my loyal subjects. Software engineers are simply people who are skilled craftsman, not gods, and it is fair to point out that some are more skilled than others. It is also completely fair to criticize their products, report bugs, and wonder aloud at endemic low-quality. Which brings me back to the initial question: ## What does the inquisitive dev know, that the others don't? 1) You learn an awful lot about an awful lot, by looking at specs, reviewing code, and trying out various implementations of concepts you are already familiar with. There are, in fact, n number of use cases for every event type, and I've seen so many of them, that I can conjure them up, or invent new ones, on the fly, rather than wasting time inventing similar events. 2) They don't have to explain their concept to you, later, when you interact. Each interaction brings you closer to parallel-levels of knowledge, which raises the signal-strength of the interaction, and widens your own knowledge base, for interacting with third parties. 3) You are increasingly-likely to contribute code or perform some other more-advanced task, for other people, as you don't face the hurdle of adjusting to a new repo or unfamiliar language, while being less-likely to merely fork-and-ignore because you have a standing business relationship with the other developer. 4) If the other dev stops maintaining the repo, you'll be inclined to continue on your own. You may even eventually receive administrative access, rather than needing to fork, as they trust you with their stuff. This means that the risk of the repo becoming abandoned falls, with each active dev snooping around it, even if that is not their primary project. 5) It helps you determine who to focus your energy on interacting with, further. Is this person new to software development, perhaps, but has some interesting transfer-knowledge from some other branch, that has resulted in a surprisingly novel concept? Is this person able to write very clean code, so that merely reading their code feels like mental training for your own craftsman's toolbox? ...and many more reasons, but this is getting too long, so, let's just cut to the chase. ## What does a craftswoman want? But, this still doesn't answer the question of my private motivation. Why do I want to gather all of this knowledge, from those further ahead, than I? I think Nostr has long moved past the initial stage, where mere speed was of the essence, so that one npub could _finally_ post a note and have it appear on the other npubs' client. That must have felt like a miracle, but it increasingly feels like a disaster, as the steadily-rising complexity of the Nostr ecosystem causes haphazardly-structured and largely-unexamined code bases to begin to atrophy, or result in developers running around at an exhausting speed, with their bug-extinguishers, to put out fire after fire. I think the time has arrived, for a different kind of development. Maybe even for a different kind of developer. Not replacing the experimentalism that made Nostr fun, but adding the realm of production-quality software engineering. The sort of software development that requires relay administration, testing, support... collaboration, interaction, maybe even someone who does AnythingElse. I want to build useful, elegant products people enjoy using and feel comfortable relying on. I want them to use them, naturally and happily, to accomplish tasks they consider worthwhile. I don't want them thinking about me, while they use it. The craftswoman should never be greater than her work. I want them to feel free -- nay, be eager! -- to give me both positive and negative feedback. My assumption is _always_ that our production is imperfect because we are imperfect, so you do us a favor, by pointing out where we can improve. That's why we wish to integrate a feedback form that produces ngit issue events, putting your questions and comments straight on our board. And there will be an AnythingElse person, reading that board, and responding promptly, rest assured.
@ fd208ee8:0fd927c1
2024-10-09 12:27:53## Why waste time, looking at other people's stuff? I get this question a lot, on Nostr, and it feeds immediately back to the next question: *Why don't you just build your own client, if you're so smart?* This was a completely new question for me, as I'm used to collaborating with at least one other person, even when doing FOSS stuff. (No, this isn't my first such project; we just used to call it "volunteering" and "sharing the code", which sounds way less glamorous.) It never occurred to me, that a habit of collaboration and interaction was some sign of my ignorance and incompetence, or somehow proof that I can't vomit up "Hello World!" in 5 different programming languages. I also made the deadly political mistake, when I entered the Nostrsphere, of refusing to call myself a "dev". For me, "dev" is a special title, given to someone doing a specific type of programming (fiddling with GUIs, mostly, which I've only done occasionally, as a sub), whereas the types I've done are "test automation", "development operations", "database management and data curation", "requirements engineering", and "application administration". Because it's so much easier to find someone interested in building a GUI, rather than building AnythingElse, I tend to slide into AnythingElse and it eventually became my professional specialty to be the Girl Friday of every project.  But, in Nostr, there is no AnythingElse category. There are only (GUI) client devs and AllOfTheIdiotsWhoMustBowDownToTheDevs. Which merely doubled my instinct to distance myself from the term. I do not want to join some cargo cult and be pedestalized and regarded as some sort of superhuman everyone owes fealty to, in return for raining GUI presents down on my loyal subjects. Software engineers are simply people who are skilled craftsman, not gods, and it is fair to point out that some are more skilled than others. It is also completely fair to criticize their products, report bugs, and wonder aloud at endemic low-quality. Which brings me back to the initial question: ## What does the inquisitive dev know, that the others don't? 1) You learn an awful lot about an awful lot, by looking at specs, reviewing code, and trying out various implementations of concepts you are already familiar with. There are, in fact, n number of use cases for every event type, and I've seen so many of them, that I can conjure them up, or invent new ones, on the fly, rather than wasting time inventing similar events. 2) They don't have to explain their concept to you, later, when you interact. Each interaction brings you closer to parallel-levels of knowledge, which raises the signal-strength of the interaction, and widens your own knowledge base, for interacting with third parties. 3) You are increasingly-likely to contribute code or perform some other more-advanced task, for other people, as you don't face the hurdle of adjusting to a new repo or unfamiliar language, while being less-likely to merely fork-and-ignore because you have a standing business relationship with the other developer. 4) If the other dev stops maintaining the repo, you'll be inclined to continue on your own. You may even eventually receive administrative access, rather than needing to fork, as they trust you with their stuff. This means that the risk of the repo becoming abandoned falls, with each active dev snooping around it, even if that is not their primary project. 5) It helps you determine who to focus your energy on interacting with, further. Is this person new to software development, perhaps, but has some interesting transfer-knowledge from some other branch, that has resulted in a surprisingly novel concept? Is this person able to write very clean code, so that merely reading their code feels like mental training for your own craftsman's toolbox? ...and many more reasons, but this is getting too long, so, let's just cut to the chase. ## What does a craftswoman want? But, this still doesn't answer the question of my private motivation. Why do I want to gather all of this knowledge, from those further ahead, than I? I think Nostr has long moved past the initial stage, where mere speed was of the essence, so that one npub could _finally_ post a note and have it appear on the other npubs' client. That must have felt like a miracle, but it increasingly feels like a disaster, as the steadily-rising complexity of the Nostr ecosystem causes haphazardly-structured and largely-unexamined code bases to begin to atrophy, or result in developers running around at an exhausting speed, with their bug-extinguishers, to put out fire after fire. I think the time has arrived, for a different kind of development. Maybe even for a different kind of developer. Not replacing the experimentalism that made Nostr fun, but adding the realm of production-quality software engineering. The sort of software development that requires relay administration, testing, support... collaboration, interaction, maybe even someone who does AnythingElse. I want to build useful, elegant products people enjoy using and feel comfortable relying on. I want them to use them, naturally and happily, to accomplish tasks they consider worthwhile. I don't want them thinking about me, while they use it. The craftswoman should never be greater than her work. I want them to feel free -- nay, be eager! -- to give me both positive and negative feedback. My assumption is _always_ that our production is imperfect because we are imperfect, so you do us a favor, by pointing out where we can improve. That's why we wish to integrate a feedback form that produces ngit issue events, putting your questions and comments straight on our board. And there will be an AnythingElse person, reading that board, and responding promptly, rest assured. @ 4ba8e86d:89d32de4
2024-10-07 23:00:50é uma tecnologia que permite criar uma conexão segura e privada entre um dispositivo e a internet. É como uma espécie de túnel privado que passa por cima da internet pública, criptografando seus dados e mascarando seu endereço IP para proteger sua privacidade e segurança online. A história da VPN remonta ao final dos anos 1990, quando as empresas começaram a usar conexões dedicadas (linhas alugadas) para conectar suas redes corporativas e permitir que seus funcionários trabalhassem remotamente. Essas conexões dedicadas eram caras e difíceis de configurar, o que levou à criação das primeiras VPNs baseadas em software. A primeira VPN comercialmente disponível foi a Redes Privadas Virtuais (RPV), lançada pela Microsoft em 1996. Desde então, várias empresas e organizações começaram a usar VPNs para proteger seus dados confidenciais e permitir que seus funcionários trabalhassem remotamente de forma segura. Como funciona a VPN? Quando você se conecta a uma VPN, seu dispositivo estabelece um canal criptografado de comunicação com um servidor remoto. Todo o tráfego de dados entre o seu dispositivo e o servidor remoto é criptografado, o que significa que é transformado em códigos que só podem ser lidos por seu dispositivo e pelo servidor remoto. Além disso, quando você usa uma VPN, seu endereço IP é substituído pelo endereço IP do servidor remoto. Isso significa que sua localização física e outros dados pessoais não são facilmente rastreados por sites que você visita e outros usuários da internet. Por que usar uma VPN? Existem várias razões pelas quais você pode querer usar uma VPN. Algumas das principais razões incluem: • Acesso a conteúdo restrito geograficamente: Se você estiver em um país que restringe o acesso a certos sites ou serviços, uma VPN pode permitir que você os acesse como se estivesse em outro lugar. Por exemplo, se você estiver no Brasil e quiser acessar um site que só está disponível nos EUA, uma VPN pode permitir que você se conecte a um servidor nos EUA e acesse o site como se estivesse lá. • Segurança e privacidade online: Quando você usa uma VPN, suas informações são criptografadas e protegidas contra hackers e outros invasores que podem tentar interceptar suas informações. • Proteção de informações pessoais: Quando você está usando uma rede Wi-Fi pública (como em um café ou aeroporto), outras pessoas na mesma rede podem potencialmente interceptar suas informações pessoais e senhas. Uma VPN pode ajudar a proteger suas informações contra esses ataques. • Evitar rastreamento de anúncios: Muitos sites e anunciantes rastreiam sua atividade online para enviar anúncios personalizados. Usar uma VPN pode ajudar a evitar esse rastreamento e manter sua atividade online mais privada. As VPNs estão disponíveis em vários tipos e preços, desde serviços gratuitos até soluções corporativas mais avançadas. Ao escolher uma VPN, é importante verificar a política de privacidade da empresa para garantir que eles não compartilhem suas informações pessoais com terceiros. Além disso, algumas VPNs podem diminuir a velocidade da sua conexão à internet, então é importante escolher um serviço com uma boa reputação e boa qualidade Eu uso a Mullvap VPN.. uma VPN é uma ferramenta importante para manter sua segurança e privacidade online. Com a capacidade de criptografar suas informações, mascarar seu endereço IP e permitir o acesso a conteúdo restrito geograficamente, as VPNs são uma ótima opção para proteger sua presença online.
@ 4ba8e86d:89d32de4
2024-10-07 23:00:50é uma tecnologia que permite criar uma conexão segura e privada entre um dispositivo e a internet. É como uma espécie de túnel privado que passa por cima da internet pública, criptografando seus dados e mascarando seu endereço IP para proteger sua privacidade e segurança online. A história da VPN remonta ao final dos anos 1990, quando as empresas começaram a usar conexões dedicadas (linhas alugadas) para conectar suas redes corporativas e permitir que seus funcionários trabalhassem remotamente. Essas conexões dedicadas eram caras e difíceis de configurar, o que levou à criação das primeiras VPNs baseadas em software. A primeira VPN comercialmente disponível foi a Redes Privadas Virtuais (RPV), lançada pela Microsoft em 1996. Desde então, várias empresas e organizações começaram a usar VPNs para proteger seus dados confidenciais e permitir que seus funcionários trabalhassem remotamente de forma segura. Como funciona a VPN? Quando você se conecta a uma VPN, seu dispositivo estabelece um canal criptografado de comunicação com um servidor remoto. Todo o tráfego de dados entre o seu dispositivo e o servidor remoto é criptografado, o que significa que é transformado em códigos que só podem ser lidos por seu dispositivo e pelo servidor remoto. Além disso, quando você usa uma VPN, seu endereço IP é substituído pelo endereço IP do servidor remoto. Isso significa que sua localização física e outros dados pessoais não são facilmente rastreados por sites que você visita e outros usuários da internet. Por que usar uma VPN? Existem várias razões pelas quais você pode querer usar uma VPN. Algumas das principais razões incluem: • Acesso a conteúdo restrito geograficamente: Se você estiver em um país que restringe o acesso a certos sites ou serviços, uma VPN pode permitir que você os acesse como se estivesse em outro lugar. Por exemplo, se você estiver no Brasil e quiser acessar um site que só está disponível nos EUA, uma VPN pode permitir que você se conecte a um servidor nos EUA e acesse o site como se estivesse lá. • Segurança e privacidade online: Quando você usa uma VPN, suas informações são criptografadas e protegidas contra hackers e outros invasores que podem tentar interceptar suas informações. • Proteção de informações pessoais: Quando você está usando uma rede Wi-Fi pública (como em um café ou aeroporto), outras pessoas na mesma rede podem potencialmente interceptar suas informações pessoais e senhas. Uma VPN pode ajudar a proteger suas informações contra esses ataques. • Evitar rastreamento de anúncios: Muitos sites e anunciantes rastreiam sua atividade online para enviar anúncios personalizados. Usar uma VPN pode ajudar a evitar esse rastreamento e manter sua atividade online mais privada. As VPNs estão disponíveis em vários tipos e preços, desde serviços gratuitos até soluções corporativas mais avançadas. Ao escolher uma VPN, é importante verificar a política de privacidade da empresa para garantir que eles não compartilhem suas informações pessoais com terceiros. Além disso, algumas VPNs podem diminuir a velocidade da sua conexão à internet, então é importante escolher um serviço com uma boa reputação e boa qualidade Eu uso a Mullvap VPN.. uma VPN é uma ferramenta importante para manter sua segurança e privacidade online. Com a capacidade de criptografar suas informações, mascarar seu endereço IP e permitir o acesso a conteúdo restrito geograficamente, as VPNs são uma ótima opção para proteger sua presença online. @ 4ba8e86d:89d32de4
2024-10-07 22:45:27Parte 1: Configuração e preparação 1. Instalação do Tails: - Baixe a imagem do Tails no site oficial (https://tails.boum.org/). - depois baixar no site vai Aberta " verificar seu download" Você vai Verifique no próprio site se o tails que você baixou é tails compilado e desenvolvido pelo equipe Tails. - Grave a imagem do Tails em um pendrive ou cartão de memória usando um software de gravação adequado, como o Rufus. - Reinicie o computador e inicie a partir do pen drive ou cartão de memória que contém o Tails. Certifique-se de configurar o computador para inicializar a partir de um dispositivo externo. - Siga as instruções na tela para completar a configuração do Tails. 2. Configuração do disco persistente: - Após iniciar o Tails, defina uma senha para criptografar o disco persistente. - Abra o menu "Applications" e selecione "Favorites". - Em seguida, escolha "Configure Persistent Volume". - Selecione as opções para salvar no seu pendrive no disco persistente. - Procure pela opção Bitcoin client e habilite-a. - Essa senha é necessária para acessar e salvar seus arquivos e configurações persistentes, incluindo a carteira Electrum. - No menu do Tails, clique em "Applications" e, em seguida, em "Internet". Selecione "Electrum Bitcoin Wallet". - O Electrum será iniciado e você poderá criar uma nova carteira selecionando "Criar uma nova carteira" e escolhendo um nome para a carteira. - Selecione "Carteira padrão" e escolha se deseja criar uma nova carteira ou restaurar a partir de um backup. - Se optar por fazer o backup da carteira, selecione a opção "semente BIP39". - Se desejar adicionar uma passphrase à carteira Electrum, clique no botão "Opção" e escolha "Estender esta semente com a palavra personalizada". Insira uma passphrase forte e siga as instruções para concluir a configuração da carteira. Anote e guarde a passphrase em um local seguro, separadamente das palavras-chave de recuperação (seed). Depois Aberta em "próximo" Vai aparece a Tela "Tipo de script e caminho derivação" Selecionar a opção "Native segwit (p2wpkh) aberta em "próximo" agora vai aparecer uma tela pra adicionar senha para criptógrafa o arquivo da carteira electrum. So insira uma senha. Obs: você tem três senha diferente pra lembrar. Senha disco persistent. Senha passphrse. Senha criptógrafa o arquivo da carteira electrum. Anote e guarde a passphrase em um local seguro, separadamente das palavras-chave de recuperação (seed). - guarde em um local seguro as palavras-chave de recuperação (seed) fornecidas pelo Electrum. Essas palavras são importantes para recuperar sua carteira se você perder o acesso ao Tails. Parte 2: Assinatura e envio da transação Assinatura da transação no Tails (offline): - Desconecte o computador do Tails da internet, removendo o cabo de rede ou desativando a conexão Wi-Fi. 1. No tails vai na opção "Carteira" logo em seguida na opção "informações da carteira" Depois Aberta em exibe o QR Code da chave pública XPUB que está no Tails. Configuração do celular: - No seu celular, abra a carteira Electrum e clique na opção "Criar nova carteira". - Atribua um nome à carteira e, em seguida, selecione a opção "Carteira padrão" (Standard Wallet) seguida da opção "Usar chave mestra" (Use Master Key). - Agora, você precisará escanear com a câmera do celular o código QR da chave pública XPUB que está no Tails. Essa chave mestra permitirá que você acompanhe o saldo e as transações da sua carteira, mas não poderá gastar os fundos ou assinar transações diretamente. - Toque em "Próxima" para iniciar o processo de sincronização da carteira no celular. Pra recebe pagamento com o celular deixa o Tails totalmente offine. É Só ir na Aba "recebe" depois em "pedir" Você pode copiar o endereço ou exibe o Qrcode pra pagamento. você pode verificar que o endereço de recebe que aparece no celular eo mesmo que está no seu Tails offine. Pra enviar vai na Aba "enviar" Aberta em "escanear" verificar as informações endereço é escolher o valor da taxa. Depois Aberta em "pagar" Vai parece um aviso "transação teve ser substituível ?" Aberta em "sim" Se a taxa foi muito baixa não confimar nos próximos dias para poder aumentar se precisar. Vai exibe na tela a quanti a enviar é total taxa de mineração Aberta em "concluir" Vai mostra quantia a ser enviada ID da transação de saída mas ela não está assinada. Atráves do Qrcode que está no celular você vai exibir Qrcode que você vai escanear com a câmara Web do seu Tails Vai volta no Tails na opção "ferramentas" - logo em seguida escolhar a opção "carregar transação" depois na opção "a partir de um código Qr" vai abrir a câmera do Tails você mostra o código Qr que está no celular para a câmera Tails. No tails vai mostrar todas as informações da transação. Após confimar as informações da transação, clique em "Assinar" Digite a senha da carteira Electrum para desbloquear a chave privada. Em seguida, clique em "Exportar" e selecione a opção "Mostrar como um código QR" No celular aberta em "escanear" O código Qr da transação assinada. Vai aparecer na tela do seu celular Status da transação assinada é informações da transação. Então finalmente você aberta em "Transmitir" para enviar a transação assinada para a rede Bitcoin. Ao optar por usar o Tails como base para criar e assinar transações, você está garantindo a segurança da sua chave privada no ambiente protegido do Tails, enquanto utiliza o celular apenas para visualizar informações e enviar a transação assinada para a rede. Uma medida adicional de segurança é a criptografia do disco persistente do Tails com uma senha forte, juntamente com o uso de senhas fortes para proteger a carteira Electrum e a chave privada. Essas camadas extras de proteção ajudam a manter suas informações seguras. É fundamental tomar todas as precauções necessárias para proteger seus dispositivos. Certifique-se de manter o Tails atualizado, utilizar software confiável para gravá-lo em um pendrive ou cartão de memória, e proteger adequadamente seu dispositivo móvel com senhas e atualizações de segurança. Embora essa abordagem ofereça uma camada mais segura para proteger sua chave privada durante o processo de envio de transações, é importante lembrar de fazer backups regulares das suas palavras-chave de recuperação (seed). Além disso, considere tomar medidas adicionais de segurança de acordo com suas necessidades e recursos disponíveis. Tenha em mente que a segurança absoluta não pode ser garantida, por isso é essencial adotar boas práticas de segurança digital. Seguindo essas orientações e tomando as devidas precauções, você estará fortalecendo a segurança das suas transações ao utilizar o Tails para criar e assinar transações, mantendo a chave privada protegida no ambiente seguro do Tails, e utilizando o celular de forma segura para enviar a transação assinada para a rede. https://youtu.be/abXkgXQ8BvI https://youtu.be/NBj9-TolpvI
@ 4ba8e86d:89d32de4
2024-10-07 22:45:27Parte 1: Configuração e preparação 1. Instalação do Tails: - Baixe a imagem do Tails no site oficial (https://tails.boum.org/). - depois baixar no site vai Aberta " verificar seu download" Você vai Verifique no próprio site se o tails que você baixou é tails compilado e desenvolvido pelo equipe Tails. - Grave a imagem do Tails em um pendrive ou cartão de memória usando um software de gravação adequado, como o Rufus. - Reinicie o computador e inicie a partir do pen drive ou cartão de memória que contém o Tails. Certifique-se de configurar o computador para inicializar a partir de um dispositivo externo. - Siga as instruções na tela para completar a configuração do Tails. 2. Configuração do disco persistente: - Após iniciar o Tails, defina uma senha para criptografar o disco persistente. - Abra o menu "Applications" e selecione "Favorites". - Em seguida, escolha "Configure Persistent Volume". - Selecione as opções para salvar no seu pendrive no disco persistente. - Procure pela opção Bitcoin client e habilite-a. - Essa senha é necessária para acessar e salvar seus arquivos e configurações persistentes, incluindo a carteira Electrum. - No menu do Tails, clique em "Applications" e, em seguida, em "Internet". Selecione "Electrum Bitcoin Wallet". - O Electrum será iniciado e você poderá criar uma nova carteira selecionando "Criar uma nova carteira" e escolhendo um nome para a carteira. - Selecione "Carteira padrão" e escolha se deseja criar uma nova carteira ou restaurar a partir de um backup. - Se optar por fazer o backup da carteira, selecione a opção "semente BIP39". - Se desejar adicionar uma passphrase à carteira Electrum, clique no botão "Opção" e escolha "Estender esta semente com a palavra personalizada". Insira uma passphrase forte e siga as instruções para concluir a configuração da carteira. Anote e guarde a passphrase em um local seguro, separadamente das palavras-chave de recuperação (seed). Depois Aberta em "próximo" Vai aparece a Tela "Tipo de script e caminho derivação" Selecionar a opção "Native segwit (p2wpkh) aberta em "próximo" agora vai aparecer uma tela pra adicionar senha para criptógrafa o arquivo da carteira electrum. So insira uma senha. Obs: você tem três senha diferente pra lembrar. Senha disco persistent. Senha passphrse. Senha criptógrafa o arquivo da carteira electrum. Anote e guarde a passphrase em um local seguro, separadamente das palavras-chave de recuperação (seed). - guarde em um local seguro as palavras-chave de recuperação (seed) fornecidas pelo Electrum. Essas palavras são importantes para recuperar sua carteira se você perder o acesso ao Tails. Parte 2: Assinatura e envio da transação Assinatura da transação no Tails (offline): - Desconecte o computador do Tails da internet, removendo o cabo de rede ou desativando a conexão Wi-Fi. 1. No tails vai na opção "Carteira" logo em seguida na opção "informações da carteira" Depois Aberta em exibe o QR Code da chave pública XPUB que está no Tails. Configuração do celular: - No seu celular, abra a carteira Electrum e clique na opção "Criar nova carteira". - Atribua um nome à carteira e, em seguida, selecione a opção "Carteira padrão" (Standard Wallet) seguida da opção "Usar chave mestra" (Use Master Key). - Agora, você precisará escanear com a câmera do celular o código QR da chave pública XPUB que está no Tails. Essa chave mestra permitirá que você acompanhe o saldo e as transações da sua carteira, mas não poderá gastar os fundos ou assinar transações diretamente. - Toque em "Próxima" para iniciar o processo de sincronização da carteira no celular. Pra recebe pagamento com o celular deixa o Tails totalmente offine. É Só ir na Aba "recebe" depois em "pedir" Você pode copiar o endereço ou exibe o Qrcode pra pagamento. você pode verificar que o endereço de recebe que aparece no celular eo mesmo que está no seu Tails offine. Pra enviar vai na Aba "enviar" Aberta em "escanear" verificar as informações endereço é escolher o valor da taxa. Depois Aberta em "pagar" Vai parece um aviso "transação teve ser substituível ?" Aberta em "sim" Se a taxa foi muito baixa não confimar nos próximos dias para poder aumentar se precisar. Vai exibe na tela a quanti a enviar é total taxa de mineração Aberta em "concluir" Vai mostra quantia a ser enviada ID da transação de saída mas ela não está assinada. Atráves do Qrcode que está no celular você vai exibir Qrcode que você vai escanear com a câmara Web do seu Tails Vai volta no Tails na opção "ferramentas" - logo em seguida escolhar a opção "carregar transação" depois na opção "a partir de um código Qr" vai abrir a câmera do Tails você mostra o código Qr que está no celular para a câmera Tails. No tails vai mostrar todas as informações da transação. Após confimar as informações da transação, clique em "Assinar" Digite a senha da carteira Electrum para desbloquear a chave privada. Em seguida, clique em "Exportar" e selecione a opção "Mostrar como um código QR" No celular aberta em "escanear" O código Qr da transação assinada. Vai aparecer na tela do seu celular Status da transação assinada é informações da transação. Então finalmente você aberta em "Transmitir" para enviar a transação assinada para a rede Bitcoin. Ao optar por usar o Tails como base para criar e assinar transações, você está garantindo a segurança da sua chave privada no ambiente protegido do Tails, enquanto utiliza o celular apenas para visualizar informações e enviar a transação assinada para a rede. Uma medida adicional de segurança é a criptografia do disco persistente do Tails com uma senha forte, juntamente com o uso de senhas fortes para proteger a carteira Electrum e a chave privada. Essas camadas extras de proteção ajudam a manter suas informações seguras. É fundamental tomar todas as precauções necessárias para proteger seus dispositivos. Certifique-se de manter o Tails atualizado, utilizar software confiável para gravá-lo em um pendrive ou cartão de memória, e proteger adequadamente seu dispositivo móvel com senhas e atualizações de segurança. Embora essa abordagem ofereça uma camada mais segura para proteger sua chave privada durante o processo de envio de transações, é importante lembrar de fazer backups regulares das suas palavras-chave de recuperação (seed). Além disso, considere tomar medidas adicionais de segurança de acordo com suas necessidades e recursos disponíveis. Tenha em mente que a segurança absoluta não pode ser garantida, por isso é essencial adotar boas práticas de segurança digital. Seguindo essas orientações e tomando as devidas precauções, você estará fortalecendo a segurança das suas transações ao utilizar o Tails para criar e assinar transações, mantendo a chave privada protegida no ambiente seguro do Tails, e utilizando o celular de forma segura para enviar a transação assinada para a rede. https://youtu.be/abXkgXQ8BvI https://youtu.be/NBj9-TolpvI @ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x). # TL;DR This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/). The following concepts are explored: 1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust). 2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse. 3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time. The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems. [Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater. # Cognitive Dissonance Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol. I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement. The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership. For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data). In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned. How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data? # Self-sovereign Identity Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity. All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money. Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state. Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k). https://i.nostr.build/xpcCSkDg3uVw0yku.png While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this. Nostr is PGP for the masses and will take cryptographic identities mainstream. # Full NOSTARD? Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons. We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be. https://i.nostr.build/s3So2JVAqoY4E1dI.png There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap. While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g). https://i.nostr.build/ot9jtM5cZtDHNKWc.png So, how do we appropriately blend cryptographically owned data with the commons? If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons). The remainder of this article explores how we can: 1. Verify ownership of a physical place in the real world; 2. Link that ownership to the corresponding digital place in cyberspace. As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0. And as we all know, the Second Law of Infodynamics (no citation\!) states that: > "The total amount of sensitive information leaked will always increase over time." This especially holds true if that data is centralised. Not your keys, not your notes. Not your keys, not your identity. # Places and Web-of-Trust [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)). However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world. Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop. This requires users to: 1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace). 2. Signal this verification to their social graph. Let's look at the latter idea first with the concept of Attestations ... # Attestations A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false. Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too. However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc). Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation: https://i.nostr.build/lZAXOEwvRIghgFY4.png Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with: 1. Your social graph; 2. The type or subject of the content being attested and by whom; 3. Your personal preferences. They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places. [NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive. **‘This is true’** resonates more strongly than **‘I like this.’**. https://i.nostr.build/s8NIG2kXzUCLcoax.jpg There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP? https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust. # Proof of Place Attestations handle the signalling of your truth, but what about the initial verification itself? We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth. Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace. One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location. Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places). In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential): > "A failure to understand Proof of Work, is a failure to understand Bitcoin." In the Nostrverse, Proof of Place helps bridge the digital and physical worlds. [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that: > "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone." https://i.nostr.build/dOnpxfI4u7EL2v4e.png This isn’t true for Nostr. In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯 # Check-ins Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes). For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used. Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices. Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am. Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable. How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\! Check-ins could also be used as a signal for bonafide Place ownership over time. # Summary: Trust Your Bros So, to recap, we have: **Places**: Digital representations of physical locations on Nostr. **Check-ins**: Users signalling their presence at a location. **Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim. You can visualise how these three concepts combine in the diagram below: https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg And, as always, top right trumps bottom left\! We have: **Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all. **Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL. **Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph. https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map? Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide. As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities. # Thanks With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\!
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x). # TL;DR This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/). The following concepts are explored: 1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust). 2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse. 3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time. The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems. [Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater. # Cognitive Dissonance Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol. I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement. The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership. For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data). In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned. How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data? # Self-sovereign Identity Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity. All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money. Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state. Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k). https://i.nostr.build/xpcCSkDg3uVw0yku.png While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this. Nostr is PGP for the masses and will take cryptographic identities mainstream. # Full NOSTARD? Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons. We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be. https://i.nostr.build/s3So2JVAqoY4E1dI.png There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap. While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g). https://i.nostr.build/ot9jtM5cZtDHNKWc.png So, how do we appropriately blend cryptographically owned data with the commons? If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons). The remainder of this article explores how we can: 1. Verify ownership of a physical place in the real world; 2. Link that ownership to the corresponding digital place in cyberspace. As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0. And as we all know, the Second Law of Infodynamics (no citation\!) states that: > "The total amount of sensitive information leaked will always increase over time." This especially holds true if that data is centralised. Not your keys, not your notes. Not your keys, not your identity. # Places and Web-of-Trust [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)). However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world. Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop. This requires users to: 1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace). 2. Signal this verification to their social graph. Let's look at the latter idea first with the concept of Attestations ... # Attestations A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false. Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too. However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc). Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation: https://i.nostr.build/lZAXOEwvRIghgFY4.png Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with: 1. Your social graph; 2. The type or subject of the content being attested and by whom; 3. Your personal preferences. They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places. [NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive. **‘This is true’** resonates more strongly than **‘I like this.’**. https://i.nostr.build/s8NIG2kXzUCLcoax.jpg There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP? https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust. # Proof of Place Attestations handle the signalling of your truth, but what about the initial verification itself? We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth. Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace. One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location. Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places). In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential): > "A failure to understand Proof of Work, is a failure to understand Bitcoin." In the Nostrverse, Proof of Place helps bridge the digital and physical worlds. [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that: > "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone." https://i.nostr.build/dOnpxfI4u7EL2v4e.png This isn’t true for Nostr. In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯 # Check-ins Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes). For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used. Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices. Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am. Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable. How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\! Check-ins could also be used as a signal for bonafide Place ownership over time. # Summary: Trust Your Bros So, to recap, we have: **Places**: Digital representations of physical locations on Nostr. **Check-ins**: Users signalling their presence at a location. **Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim. You can visualise how these three concepts combine in the diagram below: https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg And, as always, top right trumps bottom left\! We have: **Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all. **Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL. **Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph. https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map? Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide. As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities. # Thanks With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\! @ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining. Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully. Solo mining pools exist, such as: https://solo.ckpool.org/ It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool. You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power. There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely. A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine. So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning. So here’s my recommendation. Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin. Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join. If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools. Bear in mind that many of the other smaller pools are still controlled by Bitmain. If you're still interested in lottery mining, here are your chances of winning a block: Represented as Hash rates of different miners: Nerdminer: 20 KH/s = 20,000 H/s Bitaxe: 750 GH/s = 750,000,000,000 H/s Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000 If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357% Over a year, your chances increase to: 0.00627707006369428% Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one): 0.000005% Over a year, your chances increase to: 0.00026% Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions: https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/ https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx https://www.youtube.com/watch?v=Wo91DWvZRs8 https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
@ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining. Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully. Solo mining pools exist, such as: https://solo.ckpool.org/ It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool. You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power. There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely. A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine. So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning. So here’s my recommendation. Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin. Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join. If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools. Bear in mind that many of the other smaller pools are still controlled by Bitmain. If you're still interested in lottery mining, here are your chances of winning a block: Represented as Hash rates of different miners: Nerdminer: 20 KH/s = 20,000 H/s Bitaxe: 750 GH/s = 750,000,000,000 H/s Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000 If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357% Over a year, your chances increase to: 0.00627707006369428% Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one): 0.000005% Over a year, your chances increase to: 0.00026% Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions: https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/ https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx https://www.youtube.com/watch?v=Wo91DWvZRs8 https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg @ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like: Messaging: https://www.0xchat.com/#/ - Private messaging - think WhatsApp Xitter Like Clients: https://damus.io/ - iPhone client https://nostrapps.com/amethyst - Android client https://primal.net/downloads - Android, iPhone & Desktop https://shipyard.pub/posts - Schedule future posts Interesting sites: https://zap.stream/ - Video streaming https://fountain.fm/ - Podcasting https://wavlake.com/ - Music streaming https://shopstr.store/ - Online shop https://zap.cooking/recent - Cooking recipes https://ostrich.work/ - NOSTR jobs board NOSTR tools https://nostr.band/ - Powerful search tool https://nostr.wine/ - Powerful, but centralised paid relay https://npub.pro/ - Website creation tool https://nostr.build/ - Media and file storage https://relay.tools/ - Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user - Creator tools List of NOSTR apps: https://nostrapps.com/
@ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like: Messaging: https://www.0xchat.com/#/ - Private messaging - think WhatsApp Xitter Like Clients: https://damus.io/ - iPhone client https://nostrapps.com/amethyst - Android client https://primal.net/downloads - Android, iPhone & Desktop https://shipyard.pub/posts - Schedule future posts Interesting sites: https://zap.stream/ - Video streaming https://fountain.fm/ - Podcasting https://wavlake.com/ - Music streaming https://shopstr.store/ - Online shop https://zap.cooking/recent - Cooking recipes https://ostrich.work/ - NOSTR jobs board NOSTR tools https://nostr.band/ - Powerful search tool https://nostr.wine/ - Powerful, but centralised paid relay https://npub.pro/ - Website creation tool https://nostr.build/ - Media and file storage https://relay.tools/ - Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user - Creator tools List of NOSTR apps: https://nostrapps.com/ @ 3bf0c63f:aefa459d
2024-09-18 10:37:09# How to do curation and businesses on Nostr Suppose you want to start a Nostr business. You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app. This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as: - food recipe sharing; - sharing of long articles about varying topics; - markets for used goods; - freelancer work and job offers; - specific in-game lobbies and matchmaking; - directories of accredited professionals; - sharing of original music, drawings and other artistic creations; - restaurant recommendations - and so on. But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a _platform_ that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on. If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. **So what should you do instead?** Here's an idea in two steps: 1. **Write a Nostr client tailored to the niche you want to cover** If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr. The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to `wss://nostr.chrysalisrecords.com/` to see only the latest music releases accredited by that label or to `wss://nostr.indiemusic.com/` to get music from independent producers from that community. 2. **Run a relay that does all the magic** This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it `wss://magicsaucemusic.com/` -- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (`["REQ", "_", {}]`), and this will cause people to want to publish to your relay while others will want to read from it. You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and **they do not depend on you, therefore they're more likely to trust you**. --- Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects. Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under `wss://magicsaucemusic.com` and I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing on `wss://nos.lol` or `wss://relay.damus.io` or whatever relay that doesn't even know anything about music. The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09# How to do curation and businesses on Nostr Suppose you want to start a Nostr business. You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app. This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as: - food recipe sharing; - sharing of long articles about varying topics; - markets for used goods; - freelancer work and job offers; - specific in-game lobbies and matchmaking; - directories of accredited professionals; - sharing of original music, drawings and other artistic creations; - restaurant recommendations - and so on. But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a _platform_ that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on. If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. **So what should you do instead?** Here's an idea in two steps: 1. **Write a Nostr client tailored to the niche you want to cover** If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr. The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to `wss://nostr.chrysalisrecords.com/` to see only the latest music releases accredited by that label or to `wss://nostr.indiemusic.com/` to get music from independent producers from that community. 2. **Run a relay that does all the magic** This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it `wss://magicsaucemusic.com/` -- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (`["REQ", "_", {}]`), and this will cause people to want to publish to your relay while others will want to read from it. You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and **they do not depend on you, therefore they're more likely to trust you**. --- Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects. Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under `wss://magicsaucemusic.com` and I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing on `wss://nos.lol` or `wss://relay.damus.io` or whatever relay that doesn't even know anything about music. The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way. @ cb084639:2f16502a
2024-09-17 10:09:23รีวิวงาน #TBC2024 สไตล์ #Richter ![image]() เรื่องมันเริ่มมาตั้งแต่ช่วงที่ทาง npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5 ประกาศขายตั๋วงาน TBC2024 และได้ยินมาว่า จะเปิดรับ อาสาสมัครมาช่วยงาน ตั้งแต่วันนั้นก็คิดมาตลอดว่าอยากจะช่วยงานแต่ไม่รู้จะช่วยอะไรดี อย่างน้อยก็ช่วยทำในสิ่งที่ช่วยได้แล้วให้คนที่เราไปแทนได้ไปทำหน้าที่ที่ดีกว่า ก็ถือว่าเป็นการสนับสนุนส่วนหนึ่ง ก็ยังดี เพราะภาพจากปีที่แล้วมันลอยเข้ามา เราเองก็มางานคนเดียวไม่รู้จักใครเลย ได้เห็นพี่นิวและคุณนิ่ม ที่อยู่ร้านขายเสื้อแบบยุ่งมากๆ ถ้ามีคนมาช่วยเพิ่มก็คงดี พอดีเลยที่ทีมงานจับเราลงตำแหน่งนี้ จึงมีโอกาสได้มาช่วยงาน และรู้สึกเป็นเกียรติที่ได้ร่วมงานครับ ขอบคุณทุกคนที่ได้มาเจอกันในงาน ผมอาจจะไม่ได้พูดถึงทุกคนแต่ แค่มองตากันก็เข้าใจแล้ว เจอกันเยอะมากๆ ถ้าใครได้ผ่านร้านขายเสื้อก็จะเจอผมอยู่ตรงนั้น มีเพื่อนๆแวะเวียนมาทักทาย พูดคุย มาป่วน 😄😄 ประโยคที่ส่วนมากจะได้ยินเวลาผมทักทายไม่ใช่ว่าชื่ออะไรนะ ผมจะถามว่า กินข้าวยัง กินอะไรหรือยัง มันอาจจะเป็นคำง่ายๆ แต่มันแฝงไปด้วยความห่วงใยกัน บางคนเห็นไกลๆได้แต่สบตาแล้ว พยักหน้าให้กัน เหมือนทุกคนในงานเป็นเพื่อน เพื่อนที่พูดจาภาษาเดียวกัน ไม่รู้จะบรรยายออกมายังไงมันรู้สึกดี อิ่มเอมไปหมด ได้แนะนำสินค้า ได้มองเห็นกลุ่มเพื่อนคุยกันสนุกสนาน มันเป็นบรรยากาศที่ดีเลยทีเดียว เอาเป็นว่าเป็นประสบการณ์ที่ดีมากๆ เมื่อเทียบกับปีที่แล้วเลยแหละครับ ขอบคุณ อ.ตั๊ม แม่โบว์ npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5 ที่ให้โอกาสได้ร่วมงาน ขอบคุณเฮียโต้ง สำหรับหนังสือและขนมแสนอร่อยที่เอามาให้เราได้จับจ่ายกัน ขอบคุณ เพื่อนทุกคนที่เข้ามาทักทายกัน ขอบคุณลูกพี่สมนึกหัวหน้าแก๊งค์ร้านเสื้อ พี่แองจี้ แฟนพี่สมนึก แฟนพี่ตั้ม และทีมงานน้องเอิ้น ที่ช่วยขายของ รักทุกคน #siamstr #siamstrog #nostr    
@ cb084639:2f16502a
2024-09-17 10:09:23รีวิวงาน #TBC2024 สไตล์ #Richter ![image]() เรื่องมันเริ่มมาตั้งแต่ช่วงที่ทาง npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5 ประกาศขายตั๋วงาน TBC2024 และได้ยินมาว่า จะเปิดรับ อาสาสมัครมาช่วยงาน ตั้งแต่วันนั้นก็คิดมาตลอดว่าอยากจะช่วยงานแต่ไม่รู้จะช่วยอะไรดี อย่างน้อยก็ช่วยทำในสิ่งที่ช่วยได้แล้วให้คนที่เราไปแทนได้ไปทำหน้าที่ที่ดีกว่า ก็ถือว่าเป็นการสนับสนุนส่วนหนึ่ง ก็ยังดี เพราะภาพจากปีที่แล้วมันลอยเข้ามา เราเองก็มางานคนเดียวไม่รู้จักใครเลย ได้เห็นพี่นิวและคุณนิ่ม ที่อยู่ร้านขายเสื้อแบบยุ่งมากๆ ถ้ามีคนมาช่วยเพิ่มก็คงดี พอดีเลยที่ทีมงานจับเราลงตำแหน่งนี้ จึงมีโอกาสได้มาช่วยงาน และรู้สึกเป็นเกียรติที่ได้ร่วมงานครับ ขอบคุณทุกคนที่ได้มาเจอกันในงาน ผมอาจจะไม่ได้พูดถึงทุกคนแต่ แค่มองตากันก็เข้าใจแล้ว เจอกันเยอะมากๆ ถ้าใครได้ผ่านร้านขายเสื้อก็จะเจอผมอยู่ตรงนั้น มีเพื่อนๆแวะเวียนมาทักทาย พูดคุย มาป่วน 😄😄 ประโยคที่ส่วนมากจะได้ยินเวลาผมทักทายไม่ใช่ว่าชื่ออะไรนะ ผมจะถามว่า กินข้าวยัง กินอะไรหรือยัง มันอาจจะเป็นคำง่ายๆ แต่มันแฝงไปด้วยความห่วงใยกัน บางคนเห็นไกลๆได้แต่สบตาแล้ว พยักหน้าให้กัน เหมือนทุกคนในงานเป็นเพื่อน เพื่อนที่พูดจาภาษาเดียวกัน ไม่รู้จะบรรยายออกมายังไงมันรู้สึกดี อิ่มเอมไปหมด ได้แนะนำสินค้า ได้มองเห็นกลุ่มเพื่อนคุยกันสนุกสนาน มันเป็นบรรยากาศที่ดีเลยทีเดียว เอาเป็นว่าเป็นประสบการณ์ที่ดีมากๆ เมื่อเทียบกับปีที่แล้วเลยแหละครับ ขอบคุณ อ.ตั๊ม แม่โบว์ npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5 ที่ให้โอกาสได้ร่วมงาน ขอบคุณเฮียโต้ง สำหรับหนังสือและขนมแสนอร่อยที่เอามาให้เราได้จับจ่ายกัน ขอบคุณ เพื่อนทุกคนที่เข้ามาทักทายกัน ขอบคุณลูกพี่สมนึกหัวหน้าแก๊งค์ร้านเสื้อ พี่แองจี้ แฟนพี่สมนึก แฟนพี่ตั้ม และทีมงานน้องเอิ้น ที่ช่วยขายของ รักทุกคน #siamstr #siamstrog #nostr     @ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous. In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism. On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important. That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played. Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end. The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism: I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is. In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore. The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true. The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good. In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.” I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous. In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism. On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important. That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played. Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end. The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism: I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is. In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore. The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true. The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good. In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.” I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it. @ ee11a5df:b76c4e49
2024-09-11 08:16:37# Bye-Bye Reply Guy There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients. But we are not there yet. In the mean time we have ReplyGuy, and gossip needed some changes to deal with it. ## Strategies in Short 1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people. 2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering. 3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post) 4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more. 5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity 6. **PROOF OF WORK**: Require a minimum proof-of-work All of these strategies are useful, but they have to be combined properly. ## filter.rhai Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam. This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release. Here is an example using all of the techniques listed above: ```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off) fn filter() { // Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY } ```
@ ee11a5df:b76c4e49
2024-09-11 08:16:37# Bye-Bye Reply Guy There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients. But we are not there yet. In the mean time we have ReplyGuy, and gossip needed some changes to deal with it. ## Strategies in Short 1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people. 2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering. 3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post) 4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more. 5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity 6. **PROOF OF WORK**: Require a minimum proof-of-work All of these strategies are useful, but they have to be combined properly. ## filter.rhai Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam. This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release. Here is an example using all of the techniques listed above: ```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off) fn filter() { // Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY } ``` @ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good! If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/> # Intro **Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us. **Paolo:** Thank you for having us. **Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we? **Luke:** Sounds like that's the plan. So thank you again, both for joining us. # Introducing Paolo and Mathias **Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you **Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate. **Luke:** And, Mathias, over to you. **Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use. P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that. And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here. **Luke:** Oh, fantastic. # Introduction to Holepunch **Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch. What is Holepunch and what are you doing? **Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us. but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy. It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God. that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks. Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use, Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it? and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world. And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company. And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand. anything, super exciting and, encourage everybody to try to check it out. **Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product? What is the easiest way that you would explain what it is? # The Vision Behind Keet **Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer People don't care about technology. We loved it, but don't have that surface off too much to the user. Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it. It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard. And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that. # Keet vs Nostr **Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here. **Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform. And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly. You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users. So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays. and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology. It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace. Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly. **Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that. # Pear Runtime **Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform, **Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it. And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications. We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that. So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve. But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything. So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view. and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard. so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example. It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app. So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place. But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that. And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone. And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached. Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like **Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective. And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that? **Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective. And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things. I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point. # Decentralization vs. Centralization **Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor? **Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias. I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right? Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions. and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers. That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there. And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far. Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features. And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users. And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is. It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that. And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key **Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites. But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept. over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud. And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers. the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on. is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole. And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before. Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize. And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system. And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country. So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to. **Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives. So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right? **Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all. So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting. yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why # Challenges and Future of Decentralization **Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company. And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing. So is there a limitation to how far this can go? **Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world. Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling. So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house. I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created. imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you. Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure. So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another. And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example. **Knut:** Yeah. **Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money. And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook? it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way. And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it. We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback. # Bitcoin and Holepunch: Drawing Parallels **Mathias:** I think, that's the main thing to think about in that. Discussion. **Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line. And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin? **Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange. For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government. and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right? Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them. and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them. **Luke:** Yeah, fantastic. # The Future of Decentralized Communication **Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet. So is, that a goal? Is that on the roadmap? **Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world. But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind. **Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly. And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app. And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly, # Interoperability and User Experience **Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong, **Mathias:** Very, true. **Luke:** you backups with the same 1224 words. Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be **Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it. **Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life. You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build. Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible. **Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems? What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that? **Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us. The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity. No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful. **Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever. but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera. But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem. And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it. **Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options. Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right? you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion. so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai. So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that. And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself. And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center. **Knut:** Yeah. # The Role of Tether in the Crypto Ecosystem **Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo? And, what, made this thing happen? Can you give us the story here about Tether? # Tether's Origin and Evolution **Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014. it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat. That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000. But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right? International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin. For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic. # USDT's Impact on Emerging Markets **Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries. Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap. So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time. we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world. At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right? you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others. And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT. If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right? So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U. S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant. # Bitcoin as a Savings Account **Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend. The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies. we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining. We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other. I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math. That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin. **Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother. **Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether. So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right? So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education. **Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic. I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke. **Luke:** Always say the title, Knut. Always say the title. **Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course. **Paolo:** Oh, with pleasure, with great pleasure, with a nice, education. **Luke:** Absolutely. Yep. # Plan B Forum and Future Events **Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year. so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event. **Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year. I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world. And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing. **Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time. And I think we're even playing this year, aren't we, Luke? **Paolo:** You're **Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos. Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague? **Knut:** paranoid and, **Paolo:** Can I commission a **Knut:** What song would you like to hear? **Paolo:** I have two that I would suggest. One is Nothing Else Matters. **Knut:** Alright. **Paolo:** So I think that, is very inspiring, right? **Knut:** Bitcoin, for sure. Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke? **Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference, **Knut:** Yeah. **Mathias:** not so much music, but yeah, that's peer to **Knut:** Nothing else matters. **Luke:** looking forward to that. **Knut:** Sorry, brain fart. Sad but true is about the dollar still being around, **Paolo:** Yeah, you can say that. **Luke:** Okay. # Final Thoughts and Closing Remarks **Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that? **Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms. There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out. **Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting. **Mathias:** Just those things, that's all. **Paolo:** Yeah, we can piss off more than this. Thanks. **Mathias:** a **Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners? **Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them. **Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good. **Luke:** So that's, all at Keet. Is that correct? For Keet? **Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer. **Knut:** Alright, **Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah. **Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano. **Paolo:** Likewise, I **Knut:** But yeah, worth saying again. **Paolo:** Thank you for having an invitation. **Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
@ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good! If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/> # Intro **Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us. **Paolo:** Thank you for having us. **Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we? **Luke:** Sounds like that's the plan. So thank you again, both for joining us. # Introducing Paolo and Mathias **Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you **Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate. **Luke:** And, Mathias, over to you. **Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use. P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that. And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here. **Luke:** Oh, fantastic. # Introduction to Holepunch **Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch. What is Holepunch and what are you doing? **Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us. but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy. It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God. that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks. Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use, Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it? and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world. And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company. And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand. anything, super exciting and, encourage everybody to try to check it out. **Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product? What is the easiest way that you would explain what it is? # The Vision Behind Keet **Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer People don't care about technology. We loved it, but don't have that surface off too much to the user. Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it. It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard. And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that. # Keet vs Nostr **Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here. **Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform. And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly. You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users. So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays. and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology. It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace. Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly. **Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that. # Pear Runtime **Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform, **Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it. And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications. We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that. So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve. But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything. So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view. and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard. so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example. It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app. So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place. But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that. And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone. And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached. Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like **Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective. And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that? **Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective. And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things. I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point. # Decentralization vs. Centralization **Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor? **Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias. I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right? Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions. and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers. That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there. And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far. Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features. And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users. And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is. It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that. And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key **Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites. But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept. over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud. And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers. the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on. is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole. And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before. Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize. And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system. And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country. So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to. **Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives. So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right? **Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all. So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting. yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why # Challenges and Future of Decentralization **Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company. And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing. So is there a limitation to how far this can go? **Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world. Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling. So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house. I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created. imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you. Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure. So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another. And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example. **Knut:** Yeah. **Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money. And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook? it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way. And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it. We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback. # Bitcoin and Holepunch: Drawing Parallels **Mathias:** I think, that's the main thing to think about in that. Discussion. **Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line. And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin? **Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange. For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government. and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right? Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them. and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them. **Luke:** Yeah, fantastic. # The Future of Decentralized Communication **Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet. So is, that a goal? Is that on the roadmap? **Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world. But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind. **Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly. And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app. And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly, # Interoperability and User Experience **Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong, **Mathias:** Very, true. **Luke:** you backups with the same 1224 words. Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be **Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it. **Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life. You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build. Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible. **Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems? What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that? **Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us. The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity. No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful. **Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever. but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera. But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem. And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it. **Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options. Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right? you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion. so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai. So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that. And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself. And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center. **Knut:** Yeah. # The Role of Tether in the Crypto Ecosystem **Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo? And, what, made this thing happen? Can you give us the story here about Tether? # Tether's Origin and Evolution **Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014. it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat. That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000. But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right? International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin. For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic. # USDT's Impact on Emerging Markets **Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries. Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap. So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time. we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world. At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right? you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others. And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT. If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right? So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U. S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant. # Bitcoin as a Savings Account **Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend. The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies. we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining. We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other. I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math. That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin. **Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother. **Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether. So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right? So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education. **Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic. I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke. **Luke:** Always say the title, Knut. Always say the title. **Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course. **Paolo:** Oh, with pleasure, with great pleasure, with a nice, education. **Luke:** Absolutely. Yep. # Plan B Forum and Future Events **Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year. so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event. **Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year. I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world. And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing. **Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time. And I think we're even playing this year, aren't we, Luke? **Paolo:** You're **Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos. Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague? **Knut:** paranoid and, **Paolo:** Can I commission a **Knut:** What song would you like to hear? **Paolo:** I have two that I would suggest. One is Nothing Else Matters. **Knut:** Alright. **Paolo:** So I think that, is very inspiring, right? **Knut:** Bitcoin, for sure. Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke? **Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference, **Knut:** Yeah. **Mathias:** not so much music, but yeah, that's peer to **Knut:** Nothing else matters. **Luke:** looking forward to that. **Knut:** Sorry, brain fart. Sad but true is about the dollar still being around, **Paolo:** Yeah, you can say that. **Luke:** Okay. # Final Thoughts and Closing Remarks **Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that? **Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms. There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out. **Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting. **Mathias:** Just those things, that's all. **Paolo:** Yeah, we can piss off more than this. Thanks. **Mathias:** a **Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners? **Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them. **Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good. **Luke:** So that's, all at Keet. Is that correct? For Keet? **Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer. **Knut:** Alright, **Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah. **Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano. **Paolo:** Likewise, I **Knut:** But yeah, worth saying again. **Paolo:** Thank you for having an invitation. **Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show. @ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint. I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point. I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog. In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout. Are there any odds you're excited about (doesn't have to be football)? originally posted at https://stacker.news/items/679894
@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint. I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point. I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog. In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout. Are there any odds you're excited about (doesn't have to be football)? originally posted at https://stacker.news/items/679894 @ 09fbf8f3:fa3d60f0
2024-09-10 13:12:15### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。 通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。 --- 2024年08月13日更新: > 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。 为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。 --- ### 准备工具 - Ntfy服务 - Google Script - Google Sheets ### 操作步骤 1. 在Ntfy后台账号,设置访问令牌。 [](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌") 2. 添加订阅主题。 [](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题") 2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图: [](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id") 3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌): ```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet(); // 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据 var sentEmails = getSentEmails(sheet); var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length); if (threads.length === 0) return; threads.forEach(function(thread) { var threadId = thread.getId(); if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); } }); } function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; } var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"} 内容: ${email.getPlainBody() || "无内容"}`; var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true }; try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } } function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column } function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); } function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间 var data = sheet.getDataRange().getValues(); var rowsToDelete = []; data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } }); // 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); } ``` 4.Goole Script需要添加gmail服务,如图: [](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务") 5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图: [](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器") [](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细") ### 结尾 本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。 如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。 效果预览: [](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览")
@ 09fbf8f3:fa3d60f0
2024-09-10 13:12:15### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。 通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。 --- 2024年08月13日更新: > 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。 为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。 --- ### 准备工具 - Ntfy服务 - Google Script - Google Sheets ### 操作步骤 1. 在Ntfy后台账号,设置访问令牌。 [](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌") 2. 添加订阅主题。 [](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题") 2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图: [](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id") 3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌): ```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet(); // 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据 var sentEmails = getSentEmails(sheet); var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length); if (threads.length === 0) return; threads.forEach(function(thread) { var threadId = thread.getId(); if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); } }); } function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; } var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"} 内容: ${email.getPlainBody() || "无内容"}`; var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true }; try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } } function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column } function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); } function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间 var data = sheet.getDataRange().getValues(); var rowsToDelete = []; data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } }); // 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); } ``` 4.Goole Script需要添加gmail服务,如图: [](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务") 5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图: [](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器") [](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细") ### 结尾 本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。 如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。 效果预览: [](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览") @ 6ad3e2a3:c90b7740
2024-09-10 09:26:37While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions: **1. Separate passengers from their bags as early as possible.** The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences: a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes. b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day. c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five. d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier. e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable. The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children. To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc. There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.) Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane. **2. Eliminate Security Lines** Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement. a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use. Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious. b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side. Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side. **3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.** Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal. **4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.** There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done. Here are some other suggestions: 1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up. 2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges. 3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease. 4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them. I can anticipate some objections to these ideas, and I’ll address each one in turn. **1. This would cost too much money.** My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.) **2. It’s too much of a security risk.** Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end. Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle. **3. I like free carry-ons because it saves me from waiting at the baggage claim.** Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse. The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist. *\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.* *\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.*
@ 6ad3e2a3:c90b7740
2024-09-10 09:26:37While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions: **1. Separate passengers from their bags as early as possible.** The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences: a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes. b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day. c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five. d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier. e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable. The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children. To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc. There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.) Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane. **2. Eliminate Security Lines** Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement. a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use. Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious. b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side. Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side. **3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.** Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal. **4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.** There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done. Here are some other suggestions: 1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up. 2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges. 3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease. 4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them. I can anticipate some objections to these ideas, and I’ll address each one in turn. **1. This would cost too much money.** My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.) **2. It’s too much of a security risk.** Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end. Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle. **3. I like free carry-ons because it saves me from waiting at the baggage claim.** Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse. The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist. *\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.* *\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.* @ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed. @ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
@ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg @ 129f5189:3a441803
2024-09-09 23:23:45Project 2025, outlined in the "Mandate for Leadership" document by the Heritage Foundation, is a crucial guide for the next Republican administration. Crafted by conservative intellectuals from major American think tanks, this plan promises to have significant influence on a potential Donald Trump administration, even if he does not formally acknowledge it as his government plan. https://image.nostr.build/443d69c16dc32659be2353ce48d170d397e0ee682ffc3c4108df3047fd54472d.jpg This document presents proposals to depoliticize government agencies, increase efficiency, and reduce costs, aiming to dismantle the Deep State and combat the Woke agenda associated with the Democratic Party. https://image.nostr.build/06de3f0de3d48e086f47d0418d30e32cbfe0d88f452a93706987b7394458952d.jpg Dissolution of the DHS and Redistribution of Functions The Department of Homeland Security (DHS) was established in 2002 in response to the September 11 attacks, with the goal of consolidating various agencies responsible for domestic security under a single command. The DHS includes agencies such as FEMA, TSA, ICE, and CISA. Project 2025's proposal to dissolve the DHS and redistribute its functions to other agencies aims to address excessive bureaucracy and a lack of cohesion, arguing that centralization has failed to effectively integrate its diverse missions. https://image.nostr.build/ffca8d274914b725183b8fb19162c1b63f4d987c24e598f2eca88901d4a1a43c.jpg Impact on the Democratic Deep State: The dissolution of the DHS would pose a significant threat to the Democratic Deep State, as it would redistribute the power concentrated in a single entity across multiple other agencies, making it more difficult to politicize and centralize control over domestic security operations. This decentralization would reduce the ability to use the DHS as a political tool against opponents. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Primary Recommendations Combining Immigration Agencies: Merge U.S. Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), U.S. Citizenship and Immigration Services (USCIS), the Office of Refugee Resettlement (ORR) of the Department of Health and Human Services (HHS), and the Executive Office for Immigration Review (EOIR) of the Department of Justice (DOJ) into a new autonomous border and immigration agency. https://image.nostr.build/58eef4f2eca0ed2400261ec878c1dba2ca4bca519a16751b1fb7abd45da2906b.jpg Privatization of the TSA: Privatize the Transportation Security Administration (TSA), drawing inspiration from Canadian and European models, to reduce costs and improve service for travelers. Division of the Secret Service (USSS): The U.S. Secret Service (USSS), responsible for protecting national leaders and investigating financial crimes, would be divided. The protective element would be transferred to the Department of Justice (DOJ), while the financial investigations element would be moved to the Department of the Treasury. https://image.nostr.build/0a065cdbf158db4bc17b9aacd4af5a94029004caaa152eebf2c557042b08a641.jpg Impact on the Democratic Deep State: The division of the USSS would significantly weaken centralized control over protection and financial investigations, making it more difficult to use these functions for political purposes. Transferring the protective element to the DOJ and the financial investigations element to the Treasury would complicate efforts for any group or party to manipulate these crucial government functions for partisan objectives. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Cybersecurity and Infrastructure Security Agency (CISA) Established in 2018, CISA is a federal agency responsible for protecting the U.S. critical infrastructure from cyber threats. CISA's mandate includes ensuring cybersecurity for sectors such as energy, transportation, and healthcare, and it collaborates with public and private entities to strengthen the country’s cyber resilience. Criticisms and Restructuring Proposals: Project 2025 strongly criticizes CISA for deviating from its original mission and being used as a political tool for censoring speech and influencing elections. The proposal is to transfer CISA to the Department of Transportation (DOT) and return the agency to its statutory focus. https://image.nostr.build/8bfb4a45053de96a775f67e3e1b83a44d9a65fee4705e3b16d3359bd799b8af2.jpg Review of Executive Order 12333 Executive Order 12333, issued in 1981, sets guidelines for U.S. intelligence activities, including the collection, analysis, and dissemination of information. Project 2025 proposes a review of this order to ensure that intelligence agencies are not used for political purposes but are focused on protecting national security. Objectives of the Review: Prevent Abuse: Ensure that intelligence collection is conducted legally, without being used to target political opponents. Ensure Impartiality: Reaffirm that intelligence operations must be conducted impartially, with a sole focus on the country's security. https://image.nostr.build/90d31cb35a33048d311716df2fbc65c97bd4c1972977e266133654404393fca0.jpg Reforms in Public Service Facilitation of Public Employee Dismissal: Project 2025 emphasizes the need to simplify the process for dismissing public employees who do not perform their duties impartially or who promote specific political agendas. Performance Evaluations: The document highlights the importance of merit-based compensation, stating that performance evaluations are only effective when tied to real consequences. Research indicates that 90% of major private companies in the U.S. use a merit-based pay system linked to evaluations. However, in the federal government, compensation remains largely based on seniority, despite efforts to adopt merit-based pay. https://image.nostr.build/1b858fd7b2a23c3c65c0677d3e69c44976721bbdcbe7facf4682ba3371562cff.jpg Inclusion of Employees Aligned with Conservative Values: Aligned Hiring: Establish mechanisms to hire public employees who share conservative values, ensuring that the policies and practices of agencies are consistent with the principles endorsed by the administration. https://image.nostr.build/ddbf5c59e7bb479998433991347f9d301dd117fbca0edb0f94e98fcac90b2974.jpg Controversial Cases and Politicization: Hunter Biden Laptop Case: Project 2025 harshly criticizes the FBI and the Department of Justice, accusing them of acting in a biased and politically motivated manner. The authors suggest that the agency is intimidating parents who protest by labeling them as "domestic terrorists," while simultaneously suppressing politically unfavorable speech under the guise of combating "disinformation." Furthermore, the critique highlights that the FBI is alleged to be neglecting violent attacks on pregnancy centers and violations of laws prohibiting attempts to intimidate Supreme Court justices. The criticism intensifies with allegations that the FBI interfered in domestic elections and engaged in propaganda operations, specifically citing the purported Russian collusion conspiracy in 2016 and the suppression of the Hunter Biden laptop case in 2020, which is seen as a threat to the Republic. https://image.nostr.build/e4f571a14102a939164465498bef514379ec0443e71a58e12f50c518e00570c6.jpg Politicization of the FBI: Election Interference: Russia Hoax and Trump, Suppression of Hunter Biden’s Laptop, and Big Tech Collusion. Revelations about the FBI’s role in the 2016 "Russia Hoax" and the suppression of Hunter Biden’s laptop in 2020 suggest that the agency may have strayed from its impartial duties. These actions indicate concerning politicization, where the agency appears to have been used to influence the political landscape in favor of certain interests. This includes collaboration between the FBI and Big Tech companies to control discourse. https://image.nostr.build/5dcd45fcec939b782d29d8d2e3d3b45244c525b5dbd3240f1629a4632e390a86.jpg Comprehensive Review of FBI Investigations: It is crucial to conduct an immediate and thorough review of all significant investigations and activities within the FBI, terminating those that are illegal or contrary to national interests. This step is essential for restoring public trust in the FBI. A public report on the findings of this review could enhance transparency and confidence. https://image.nostr.build/df98e2c6aff123d806187eab13d24a3ebb30a87df1f44cf57be97dc5624fff88.jpg Structural Reorganization: Align the FBI within the Department of Justice (DOJ) according to its purposes of national security and law enforcement. The agency should be under the supervision of the Assistant Attorney General for the Criminal Division and the National Security Division, ensuring that the FBI does not operate as an independent entity but is instead subordinated to the DOJ’s directives. https://image.nostr.build/0d1c0015c6b67a8afc2dd1595357ea571fcd5a9d83829065f49f9b60cf553eb0.jpg Prohibition on Policing Speech: Prohibit the FBI from engaging in activities related to combating "disinformation" or "misinformation" disseminated by Americans who are not linked to plausible criminal activities. The Constitution, through the First Amendment, prohibits the government from policing speech, ensuring a healthy public debate without governmental intervention. All these measures represent a significant attack on the "Deep State" within American institutions. These public policies have been considered a dictatorial threat by many sectors of the American press. However, the real issue should be the politicization of unelected bureaucrats by a political faction. https://image.nostr.build/9a44b19d15d53314f89528c1d89e2f637030ea18d8907a6a8c4e27d07064b8ec.jpg Combating Woke Culture in the Intelligence Community Future leadership of the Intelligence Community (IC) needs to implement a plan to replace the "woke" culture and identity politics that have spread throughout the federal government. The goal is to restore traditional American values such as patriotism, racial impartiality, and job competence, which have been replaced by advocacy for "social justice" and identity politics. https://image.nostr.build/7929dca5e36273c8e751f36d6ca6229f362e30792bce735f10be7e5d8581af5f.jpg Final Considerations The Heritage Foundation’s Project 2025 is not merely an administrative reform plan; it is a manifesto of resistance against the Washington status quo. The proposals aim to dismantle established power structures, eliminate politicization, and combat the Woke agenda. If implemented, this plan would profoundly impact how the U.S. government operates, promoting a more efficient, limited government aligned with conservative principles. Threat to the Democratic Deep State: A potential new administration under Donald Trump represents an existential threat to the Democratic Deep State entrenched in American institutions. The dissolution of the DHS, depoliticization of intelligence agencies, division of the Secret Service, review of Executive Order 12333, privatization of the TSA, and the hiring of employees aligned with conservative values are all measures that would significantly weaken centralized control and the ability to use these institutions for political purposes. By dismantling concentrated power and promoting a more transparent and accountable government, Project 2025 aims to restore public trust and ensure that government agencies serve national interests rather than partisan ones. Of course, not all aspects of the plan may be implemented, but the prospect of several of these measures being enacted should be a cause for concern for the Democratic Deep State.
@ 129f5189:3a441803
2024-09-09 23:23:45Project 2025, outlined in the "Mandate for Leadership" document by the Heritage Foundation, is a crucial guide for the next Republican administration. Crafted by conservative intellectuals from major American think tanks, this plan promises to have significant influence on a potential Donald Trump administration, even if he does not formally acknowledge it as his government plan. https://image.nostr.build/443d69c16dc32659be2353ce48d170d397e0ee682ffc3c4108df3047fd54472d.jpg This document presents proposals to depoliticize government agencies, increase efficiency, and reduce costs, aiming to dismantle the Deep State and combat the Woke agenda associated with the Democratic Party. https://image.nostr.build/06de3f0de3d48e086f47d0418d30e32cbfe0d88f452a93706987b7394458952d.jpg Dissolution of the DHS and Redistribution of Functions The Department of Homeland Security (DHS) was established in 2002 in response to the September 11 attacks, with the goal of consolidating various agencies responsible for domestic security under a single command. The DHS includes agencies such as FEMA, TSA, ICE, and CISA. Project 2025's proposal to dissolve the DHS and redistribute its functions to other agencies aims to address excessive bureaucracy and a lack of cohesion, arguing that centralization has failed to effectively integrate its diverse missions. https://image.nostr.build/ffca8d274914b725183b8fb19162c1b63f4d987c24e598f2eca88901d4a1a43c.jpg Impact on the Democratic Deep State: The dissolution of the DHS would pose a significant threat to the Democratic Deep State, as it would redistribute the power concentrated in a single entity across multiple other agencies, making it more difficult to politicize and centralize control over domestic security operations. This decentralization would reduce the ability to use the DHS as a political tool against opponents. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Primary Recommendations Combining Immigration Agencies: Merge U.S. Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), U.S. Citizenship and Immigration Services (USCIS), the Office of Refugee Resettlement (ORR) of the Department of Health and Human Services (HHS), and the Executive Office for Immigration Review (EOIR) of the Department of Justice (DOJ) into a new autonomous border and immigration agency. https://image.nostr.build/58eef4f2eca0ed2400261ec878c1dba2ca4bca519a16751b1fb7abd45da2906b.jpg Privatization of the TSA: Privatize the Transportation Security Administration (TSA), drawing inspiration from Canadian and European models, to reduce costs and improve service for travelers. Division of the Secret Service (USSS): The U.S. Secret Service (USSS), responsible for protecting national leaders and investigating financial crimes, would be divided. The protective element would be transferred to the Department of Justice (DOJ), while the financial investigations element would be moved to the Department of the Treasury. https://image.nostr.build/0a065cdbf158db4bc17b9aacd4af5a94029004caaa152eebf2c557042b08a641.jpg Impact on the Democratic Deep State: The division of the USSS would significantly weaken centralized control over protection and financial investigations, making it more difficult to use these functions for political purposes. Transferring the protective element to the DOJ and the financial investigations element to the Treasury would complicate efforts for any group or party to manipulate these crucial government functions for partisan objectives. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Cybersecurity and Infrastructure Security Agency (CISA) Established in 2018, CISA is a federal agency responsible for protecting the U.S. critical infrastructure from cyber threats. CISA's mandate includes ensuring cybersecurity for sectors such as energy, transportation, and healthcare, and it collaborates with public and private entities to strengthen the country’s cyber resilience. Criticisms and Restructuring Proposals: Project 2025 strongly criticizes CISA for deviating from its original mission and being used as a political tool for censoring speech and influencing elections. The proposal is to transfer CISA to the Department of Transportation (DOT) and return the agency to its statutory focus. https://image.nostr.build/8bfb4a45053de96a775f67e3e1b83a44d9a65fee4705e3b16d3359bd799b8af2.jpg Review of Executive Order 12333 Executive Order 12333, issued in 1981, sets guidelines for U.S. intelligence activities, including the collection, analysis, and dissemination of information. Project 2025 proposes a review of this order to ensure that intelligence agencies are not used for political purposes but are focused on protecting national security. Objectives of the Review: Prevent Abuse: Ensure that intelligence collection is conducted legally, without being used to target political opponents. Ensure Impartiality: Reaffirm that intelligence operations must be conducted impartially, with a sole focus on the country's security. https://image.nostr.build/90d31cb35a33048d311716df2fbc65c97bd4c1972977e266133654404393fca0.jpg Reforms in Public Service Facilitation of Public Employee Dismissal: Project 2025 emphasizes the need to simplify the process for dismissing public employees who do not perform their duties impartially or who promote specific political agendas. Performance Evaluations: The document highlights the importance of merit-based compensation, stating that performance evaluations are only effective when tied to real consequences. Research indicates that 90% of major private companies in the U.S. use a merit-based pay system linked to evaluations. However, in the federal government, compensation remains largely based on seniority, despite efforts to adopt merit-based pay. https://image.nostr.build/1b858fd7b2a23c3c65c0677d3e69c44976721bbdcbe7facf4682ba3371562cff.jpg Inclusion of Employees Aligned with Conservative Values: Aligned Hiring: Establish mechanisms to hire public employees who share conservative values, ensuring that the policies and practices of agencies are consistent with the principles endorsed by the administration. https://image.nostr.build/ddbf5c59e7bb479998433991347f9d301dd117fbca0edb0f94e98fcac90b2974.jpg Controversial Cases and Politicization: Hunter Biden Laptop Case: Project 2025 harshly criticizes the FBI and the Department of Justice, accusing them of acting in a biased and politically motivated manner. The authors suggest that the agency is intimidating parents who protest by labeling them as "domestic terrorists," while simultaneously suppressing politically unfavorable speech under the guise of combating "disinformation." Furthermore, the critique highlights that the FBI is alleged to be neglecting violent attacks on pregnancy centers and violations of laws prohibiting attempts to intimidate Supreme Court justices. The criticism intensifies with allegations that the FBI interfered in domestic elections and engaged in propaganda operations, specifically citing the purported Russian collusion conspiracy in 2016 and the suppression of the Hunter Biden laptop case in 2020, which is seen as a threat to the Republic. https://image.nostr.build/e4f571a14102a939164465498bef514379ec0443e71a58e12f50c518e00570c6.jpg Politicization of the FBI: Election Interference: Russia Hoax and Trump, Suppression of Hunter Biden’s Laptop, and Big Tech Collusion. Revelations about the FBI’s role in the 2016 "Russia Hoax" and the suppression of Hunter Biden’s laptop in 2020 suggest that the agency may have strayed from its impartial duties. These actions indicate concerning politicization, where the agency appears to have been used to influence the political landscape in favor of certain interests. This includes collaboration between the FBI and Big Tech companies to control discourse. https://image.nostr.build/5dcd45fcec939b782d29d8d2e3d3b45244c525b5dbd3240f1629a4632e390a86.jpg Comprehensive Review of FBI Investigations: It is crucial to conduct an immediate and thorough review of all significant investigations and activities within the FBI, terminating those that are illegal or contrary to national interests. This step is essential for restoring public trust in the FBI. A public report on the findings of this review could enhance transparency and confidence. https://image.nostr.build/df98e2c6aff123d806187eab13d24a3ebb30a87df1f44cf57be97dc5624fff88.jpg Structural Reorganization: Align the FBI within the Department of Justice (DOJ) according to its purposes of national security and law enforcement. The agency should be under the supervision of the Assistant Attorney General for the Criminal Division and the National Security Division, ensuring that the FBI does not operate as an independent entity but is instead subordinated to the DOJ’s directives. https://image.nostr.build/0d1c0015c6b67a8afc2dd1595357ea571fcd5a9d83829065f49f9b60cf553eb0.jpg Prohibition on Policing Speech: Prohibit the FBI from engaging in activities related to combating "disinformation" or "misinformation" disseminated by Americans who are not linked to plausible criminal activities. The Constitution, through the First Amendment, prohibits the government from policing speech, ensuring a healthy public debate without governmental intervention. All these measures represent a significant attack on the "Deep State" within American institutions. These public policies have been considered a dictatorial threat by many sectors of the American press. However, the real issue should be the politicization of unelected bureaucrats by a political faction. https://image.nostr.build/9a44b19d15d53314f89528c1d89e2f637030ea18d8907a6a8c4e27d07064b8ec.jpg Combating Woke Culture in the Intelligence Community Future leadership of the Intelligence Community (IC) needs to implement a plan to replace the "woke" culture and identity politics that have spread throughout the federal government. The goal is to restore traditional American values such as patriotism, racial impartiality, and job competence, which have been replaced by advocacy for "social justice" and identity politics. https://image.nostr.build/7929dca5e36273c8e751f36d6ca6229f362e30792bce735f10be7e5d8581af5f.jpg Final Considerations The Heritage Foundation’s Project 2025 is not merely an administrative reform plan; it is a manifesto of resistance against the Washington status quo. The proposals aim to dismantle established power structures, eliminate politicization, and combat the Woke agenda. If implemented, this plan would profoundly impact how the U.S. government operates, promoting a more efficient, limited government aligned with conservative principles. Threat to the Democratic Deep State: A potential new administration under Donald Trump represents an existential threat to the Democratic Deep State entrenched in American institutions. The dissolution of the DHS, depoliticization of intelligence agencies, division of the Secret Service, review of Executive Order 12333, privatization of the TSA, and the hiring of employees aligned with conservative values are all measures that would significantly weaken centralized control and the ability to use these institutions for political purposes. By dismantling concentrated power and promoting a more transparent and accountable government, Project 2025 aims to restore public trust and ensure that government agencies serve national interests rather than partisan ones. Of course, not all aspects of the plan may be implemented, but the prospect of several of these measures being enacted should be a cause for concern for the Democratic Deep State. @ 129f5189:3a441803
2024-09-09 23:18:44Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario. The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy. After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America. Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million. China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions... https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions. In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border. A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention. https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere. The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years. https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021. In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government. https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues. In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities." https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024. Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction. In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government. https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University. "The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times. General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country. "We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time. In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade." https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues." Under the previous administration, China had received preferential treatment. In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan. The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security. No public records show that the project has progressed since then. https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark. "Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement. "Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face." https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era. Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel." https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg Access to space plays a crucial role in the CCP's strategic objectives. Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China. According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice. According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access. China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely. The big question is: what could this facility do in times of war? https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit. The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface. Additionally, it offers strategic advantages for any government involved in espionage. https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner. However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives. Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023. https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg
@ 129f5189:3a441803
2024-09-09 23:18:44Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario. The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy. After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America. Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million. China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions... https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions. In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border. A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention. https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere. The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years. https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021. In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government. https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues. In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities." https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024. Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction. In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government. https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University. "The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times. General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country. "We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time. In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade." https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues." Under the previous administration, China had received preferential treatment. In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan. The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security. No public records show that the project has progressed since then. https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark. "Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement. "Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face." https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era. Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel." https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg Access to space plays a crucial role in the CCP's strategic objectives. Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China. According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice. According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access. China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely. The big question is: what could this facility do in times of war? https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit. The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface. Additionally, it offers strategic advantages for any government involved in espionage. https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner. However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives. Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023. https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg @ 129f5189:3a441803
2024-09-09 23:11:19Precious metals have served as monetary backing for millennia, but this does not guarantee that gold is a safe investment or a good hedge against economic crises and monetary collapses. Since its last major rally in the 1980s, gold has been progressively demonetized. Those who acquired gold in the late 1980s will need to rely on a significant increase in demand or a supply shock for its price to rise by 561% and regain the purchasing power it had 40 years ago. https://image.nostr.build/dd5fec2b474ea34cd72ddf5781393b528e63a358d523c9428f3ba4649f4f42aa.jpg If you look at the purchasing power of $1 (green line), you'll see that the depreciation is even faster. This might create the impression that gold is a good store of value. But does the fact that something loses value more slowly amidst a general decline really make it a store of value? Unless the total demand for gold increases at the same rate as its supply has grown in recent years, the purchasing power of the metal is likely to decline. https://image.nostr.build/9f24f6cf37780fe851746057520064ed94acd96547be53bd341c9e15b8762773.jpg In other words, if you own an ounce of gold, that ounce will represent an increasingly smaller fraction of the total gold reserves, meaning you are being diluted. Additionally, one should also consider the cost and risk of storage, but that's another issue. If you don't want to compare the purchasing power of gold today with the 1980s, you can consider its value from 9 years ago. Between September 2011 and November 2015, the Fed printed approximately $2.8 trillion. This also provides a perspective on gold's depreciation relative to the significant monetary expansion during that period. https://image.nostr.build/822e0a861e16ca258e0427875a84b5c8e5420e51bcf65674b453b55ed78edefd.jpg In other words, the Fed expanded its monetary base by about 30% during that 4-year period. However, the price of an ounce of gold fell by 45% (from $1,900 to $1,057) over the same interval. A true store of value should protect against excessive money printing. In contrast, during that same period, Bitcoin appreciated by 8,500% (from $5 to $419). https://image.nostr.build/32a7ca39a6e69e2780f9ab49390c7b7380499fcfe54ae4ef693e6fc91686a41e.jpg Indeed, while it is interesting to note that this was the exact period when gold derivatives were launched on CME Group, it's important to remember that correlation does not imply causation. Many factors can influence the price of gold and Bitcoin, and establishing a direct causal relationship requires more detailed analysis. https://derivsource.com/2011/06/21/cme-group-announces-the-launch-of-three-new-short-term-gold-crude-oil-and-natural-gas-options-contracts/ In an asset where supply can only be physically verified, flooding the market with gold contracts could lead to significant issues. This might result in market manipulation, legal liabilities, fines, and potentially even imprisonment for those involved. Such actions can undermine the integrity of the market and lead to regulatory and legal consequences. https://www.cnbc.com/2018/11/06/ex-jp-morgan-trader-pleads-guilty-to-manipulating-metals-markets.html Over longer periods, gold has not functioned as a true "store of value" relative to the dollar for quite some time, despite recently returning to its price from 9 years ago. This suggests that, while gold may have periods of price recovery, it has struggled to maintain its value over extended horizons compared to fiat currencies. It's worth noting that before 1980, aluminum was valued higher than gold. This reflects how market dynamics and technological advancements can significantly impact the value of commodities over time. https://www.mgsrefining.com/blog/why-aluminum-is-no-longer-a-precious-metal/ While gold has been undergoing a gradual demonetization process since 1980, another asset appears to be experiencing the opposite—hyper-monetization. (See in red; don't be alarmed.) https://image.nostr.build/435a5369f778a7be727b50e4c6328cfc353240bf804e1ed69313b9a8e1233f7e.jpg With the advent of Bitcoin, you believe that gold will continue on the same path as silver since the end of the bimetallic standard in 1853: a prolonged process of demonetization, with increasing volatility and reduced liquidity. https://image.nostr.build/5b9c8bfdb09e51d639e380df160c98beb9ee1d917ea13d28ef67711cfa5f8086.jpg Since 1913, the dollar has lost 97% of its purchasing power. Over the same period, the gold supply has increased significantly. Since 1980, gold has lost about 82% of its purchasing power. Given that the dollar is used as the unit of account and gold's liquidity is measured in dollars, these changes reflect the complex interaction between the currency and the precious metal. The U.S. is by far the country with the largest gold reserves in the world and is also the fourth-largest miner of the metal. Additionally, the country controls and issues the currency that serves as the unit of account for gold and has the highest liquidity in global trade. Is gold easy to transport? Is it simple to verify its supply and authenticity? Is it practical to store? Is its industrial utility significant? Can it be disrupted? And what about the continuous increase in its supply? These are important questions to consider. In my humble opinion, it will not be the dollar or fiat currencies that will suffer the most from the existence of Bitcoin, but rather the market cap of gold. https://image.nostr.build/61dddefabc4b69f784631a3294bdd978e3411bba40fb52d585e13b48002389fe.jpg
@ 129f5189:3a441803
2024-09-09 23:11:19Precious metals have served as monetary backing for millennia, but this does not guarantee that gold is a safe investment or a good hedge against economic crises and monetary collapses. Since its last major rally in the 1980s, gold has been progressively demonetized. Those who acquired gold in the late 1980s will need to rely on a significant increase in demand or a supply shock for its price to rise by 561% and regain the purchasing power it had 40 years ago. https://image.nostr.build/dd5fec2b474ea34cd72ddf5781393b528e63a358d523c9428f3ba4649f4f42aa.jpg If you look at the purchasing power of $1 (green line), you'll see that the depreciation is even faster. This might create the impression that gold is a good store of value. But does the fact that something loses value more slowly amidst a general decline really make it a store of value? Unless the total demand for gold increases at the same rate as its supply has grown in recent years, the purchasing power of the metal is likely to decline. https://image.nostr.build/9f24f6cf37780fe851746057520064ed94acd96547be53bd341c9e15b8762773.jpg In other words, if you own an ounce of gold, that ounce will represent an increasingly smaller fraction of the total gold reserves, meaning you are being diluted. Additionally, one should also consider the cost and risk of storage, but that's another issue. If you don't want to compare the purchasing power of gold today with the 1980s, you can consider its value from 9 years ago. Between September 2011 and November 2015, the Fed printed approximately $2.8 trillion. This also provides a perspective on gold's depreciation relative to the significant monetary expansion during that period. https://image.nostr.build/822e0a861e16ca258e0427875a84b5c8e5420e51bcf65674b453b55ed78edefd.jpg In other words, the Fed expanded its monetary base by about 30% during that 4-year period. However, the price of an ounce of gold fell by 45% (from $1,900 to $1,057) over the same interval. A true store of value should protect against excessive money printing. In contrast, during that same period, Bitcoin appreciated by 8,500% (from $5 to $419). https://image.nostr.build/32a7ca39a6e69e2780f9ab49390c7b7380499fcfe54ae4ef693e6fc91686a41e.jpg Indeed, while it is interesting to note that this was the exact period when gold derivatives were launched on CME Group, it's important to remember that correlation does not imply causation. Many factors can influence the price of gold and Bitcoin, and establishing a direct causal relationship requires more detailed analysis. https://derivsource.com/2011/06/21/cme-group-announces-the-launch-of-three-new-short-term-gold-crude-oil-and-natural-gas-options-contracts/ In an asset where supply can only be physically verified, flooding the market with gold contracts could lead to significant issues. This might result in market manipulation, legal liabilities, fines, and potentially even imprisonment for those involved. Such actions can undermine the integrity of the market and lead to regulatory and legal consequences. https://www.cnbc.com/2018/11/06/ex-jp-morgan-trader-pleads-guilty-to-manipulating-metals-markets.html Over longer periods, gold has not functioned as a true "store of value" relative to the dollar for quite some time, despite recently returning to its price from 9 years ago. This suggests that, while gold may have periods of price recovery, it has struggled to maintain its value over extended horizons compared to fiat currencies. It's worth noting that before 1980, aluminum was valued higher than gold. This reflects how market dynamics and technological advancements can significantly impact the value of commodities over time. https://www.mgsrefining.com/blog/why-aluminum-is-no-longer-a-precious-metal/ While gold has been undergoing a gradual demonetization process since 1980, another asset appears to be experiencing the opposite—hyper-monetization. (See in red; don't be alarmed.) https://image.nostr.build/435a5369f778a7be727b50e4c6328cfc353240bf804e1ed69313b9a8e1233f7e.jpg With the advent of Bitcoin, you believe that gold will continue on the same path as silver since the end of the bimetallic standard in 1853: a prolonged process of demonetization, with increasing volatility and reduced liquidity. https://image.nostr.build/5b9c8bfdb09e51d639e380df160c98beb9ee1d917ea13d28ef67711cfa5f8086.jpg Since 1913, the dollar has lost 97% of its purchasing power. Over the same period, the gold supply has increased significantly. Since 1980, gold has lost about 82% of its purchasing power. Given that the dollar is used as the unit of account and gold's liquidity is measured in dollars, these changes reflect the complex interaction between the currency and the precious metal. The U.S. is by far the country with the largest gold reserves in the world and is also the fourth-largest miner of the metal. Additionally, the country controls and issues the currency that serves as the unit of account for gold and has the highest liquidity in global trade. Is gold easy to transport? Is it simple to verify its supply and authenticity? Is it practical to store? Is its industrial utility significant? Can it be disrupted? And what about the continuous increase in its supply? These are important questions to consider. In my humble opinion, it will not be the dollar or fiat currencies that will suffer the most from the existence of Bitcoin, but rather the market cap of gold. https://image.nostr.build/61dddefabc4b69f784631a3294bdd978e3411bba40fb52d585e13b48002389fe.jpg @ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect. Therefore, I strongly advise you to run multiple clients. On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay. If you haven’t taken the plunge to run a node, now might be a good time to think about it. There are many, many options for clients, the “Social” section of https://nostrapps.com/ lists 23 currently. Play with them, see what they do, if you’re a developer, you could even consider building or forking your own. Have fun and realise we are building freedom tech, not just running it.
@ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect. Therefore, I strongly advise you to run multiple clients. On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay. If you haven’t taken the plunge to run a node, now might be a good time to think about it. There are many, many options for clients, the “Social” section of https://nostrapps.com/ lists 23 currently. Play with them, see what they do, if you’re a developer, you could even consider building or forking your own. Have fun and realise we are building freedom tech, not just running it. @ e83b66a8:b0526c2b
2024-09-09 20:27:41First, Key management. When you “created” your NOSTR account, what you actually created was a cryptographic key pair. This consists of a private key, which starts “nsec” and a public key which starts with “npub”. As the names suggest, your “nsec” key is private and you should never reveal it to anyone. Your “npub” key is your public key, feel free to share that everywhere. Your “npub” key is used by others to verify your identity, through the signature added to your messages. It is also used by others to encrypt private messages to you. We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary. For the moment, consider using software key management options, some of which are listed under “signers” here: https://nostrapps.com/ N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted: Secondly, Lightning wallets. It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key. You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet. Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason…. It also allows you to send small micropayments to posts or people you like. Thirdly, Paid Services As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability. I, for example choose to pay for the following services: https://nostr.wine/ - 120,000 Sats for 2 years relay https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month https://nostr.build/ - Media storage - 69,000 Sats for 1 year Total: 22,750 Sats per month Approx $15 per month This is not strictly necessary, but I decided to support the various developers behind these projects. Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward.
@ e83b66a8:b0526c2b
2024-09-09 20:27:41First, Key management. When you “created” your NOSTR account, what you actually created was a cryptographic key pair. This consists of a private key, which starts “nsec” and a public key which starts with “npub”. As the names suggest, your “nsec” key is private and you should never reveal it to anyone. Your “npub” key is your public key, feel free to share that everywhere. Your “npub” key is used by others to verify your identity, through the signature added to your messages. It is also used by others to encrypt private messages to you. We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary. For the moment, consider using software key management options, some of which are listed under “signers” here: https://nostrapps.com/ N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted: Secondly, Lightning wallets. It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key. You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet. Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason…. It also allows you to send small micropayments to posts or people you like. Thirdly, Paid Services As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability. I, for example choose to pay for the following services: https://nostr.wine/ - 120,000 Sats for 2 years relay https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month https://nostr.build/ - Media storage - 69,000 Sats for 1 year Total: 22,750 Sats per month Approx $15 per month This is not strictly necessary, but I decided to support the various developers behind these projects. Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward. @ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :) I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet. What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds? What is your experience? I'd love to hear about it!
@ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :) I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet. What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds? What is your experience? I'd love to hear about it! @ 3875a16c:988456c9
2024-09-09 14:45:55**ORIGINAL PANEL TITLE:** MAKING BITCOIN MORE PRIVATE WITH CISA **SPEAKERS:** NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP **CONFERENCE:** BITCOIN NASHVILLE 2024 **ORIGINALLY PUBLISHED ON:** BITLYRICS.CO ## Introduction This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/). Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development. --- ### NiftyNei (Moderator): Hey everyone, my name is Nifty, and I’m going to be moderating this panel today. We’re here to talk about CISA (cross-input signature aggregation). Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage. We’re excited to be talking to you guys about this. I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA. Craig, do you want to start? --- ### Craig Raw (Sparrow Wallet): I built Sparrow Wallet. It’s a security and privacy-focused wallet. The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen. When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically. So, that was the first time I really started to look at it from the privacy angle. --- ### Fabian Jahr (Brink): I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it. Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core. Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months. I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller. I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it. --- ### Jameson Lopp (Casa): I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups. I think the first time I heard about CISA was in an Andrew Poelstra talk. I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted. This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics. --- ### NiftyNei (Moderator): That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for. Does anyone have a good explanation of how it works? --- ### Fabian Jahr (Brink): I can start off. So, it’s really already all in the name: cross-input signature aggregation. If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated. What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction. So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before. Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea. --- ### NiftyNei (Moderator): I have a quick question about that. So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right? So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature. Is that a good summary of what you’re explaining? --- ### Fabian Jahr (Brink): Yeah, I would say so. --- ### Craig Raw (Sparrow Wallet): So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it. That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one. Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it. Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones. Unfortunately, the downside of that is that you have to do the interaction while you sign. The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing. As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient. --- ### NiftyNei (Moderator): Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right? You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level? --- ### Jameson Lopp (Casa): Well, there’s also full-block aggregation, right? This is going really far down the rabbit hole, and I think it’s not even something that’s on the table. There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations. My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized. If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again. --- ### NiftyNei (Moderator): So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation. We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there. One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right? Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated. --- ### Jameson Lopp (Casa): Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically. If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount. It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO. You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet. It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot. It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before. So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so. --- ### Fabian Jahr (Brink): And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy. The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property. Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.” Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it. Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature. --- ### Jameson Lopp (Casa): Yeah, we have to think about the incentives, right? I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are. But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late. We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so. It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software. Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money? --- ### Craig Raw (Sparrow): So you might be wondering at this stage what the savings actually look like. It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block. You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage. Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%. But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space. So that’s how I would encourage you to think about it from the start. For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride. We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about. --- ### NiftyNei (Moderator): I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy. I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal? What was it about the Taproot process where this proposal didn’t make it over the line? --- ### Fabian Jahr (Brink): I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed. From what I can see, I don’t think there was any direct opposition. The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller. I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding. I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much. --- ### Craig Raw (Sparrow): Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough. There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.” That’s an interesting point of view. --- ### Jameson Lopp (Casa): It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet. --- ### Craig Raw (Sparrow): Yeah, so we’re in a very different space now. Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine. I’m talking about the well-understood half-signature aggregation form of it. From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that. So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing. If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down. So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line. --- ### Jameson Lopp (Casa): I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin. With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process. As far as I’m aware, there’s been limited adoption of Schnorr so far. I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility. I care about this a lot, operating a multi-signature self-custody wallet. We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature. That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out. So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block. --- ### NiftyNei (Moderator): So, we only have a few minutes left. Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in. --- ### Fabian Jahr (Brink): There are still quite a few things to hammer out in terms of all the details, like defining a spec. For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open. However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity. We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now. --- ### Jameson Lopp (Casa): Yeah, call your local developer and demand signature aggregation today. --- ### Craig Raw (Sparrow): Fabian has developed a great site where you can learn more. If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it. It’s very easy to read, not overly technical, and I think it gives a good grounding in these things. Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not. As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now. So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not. --- ### Jameson Lopp (Casa): I don’t know, do you want to save money? It should be an easy question. --- ### Fabian Jahr (Brink): And have better privacy. --- ### NiftyNei (Moderator): Great! Thanks y’all. --- **Follow the speakers: ** [NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr) **Watch the original content: ** [Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107) **Also read: Build It Right: ** [Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/) **Disclaimer: ** Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/).
@ 3875a16c:988456c9
2024-09-09 14:45:55**ORIGINAL PANEL TITLE:** MAKING BITCOIN MORE PRIVATE WITH CISA **SPEAKERS:** NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP **CONFERENCE:** BITCOIN NASHVILLE 2024 **ORIGINALLY PUBLISHED ON:** BITLYRICS.CO ## Introduction This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/). Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development. --- ### NiftyNei (Moderator): Hey everyone, my name is Nifty, and I’m going to be moderating this panel today. We’re here to talk about CISA (cross-input signature aggregation). Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage. We’re excited to be talking to you guys about this. I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA. Craig, do you want to start? --- ### Craig Raw (Sparrow Wallet): I built Sparrow Wallet. It’s a security and privacy-focused wallet. The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen. When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically. So, that was the first time I really started to look at it from the privacy angle. --- ### Fabian Jahr (Brink): I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it. Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core. Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months. I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller. I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it. --- ### Jameson Lopp (Casa): I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups. I think the first time I heard about CISA was in an Andrew Poelstra talk. I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted. This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics. --- ### NiftyNei (Moderator): That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for. Does anyone have a good explanation of how it works? --- ### Fabian Jahr (Brink): I can start off. So, it’s really already all in the name: cross-input signature aggregation. If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated. What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction. So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before. Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea. --- ### NiftyNei (Moderator): I have a quick question about that. So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right? So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature. Is that a good summary of what you’re explaining? --- ### Fabian Jahr (Brink): Yeah, I would say so. --- ### Craig Raw (Sparrow Wallet): So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it. That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one. Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it. Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones. Unfortunately, the downside of that is that you have to do the interaction while you sign. The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing. As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient. --- ### NiftyNei (Moderator): Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right? You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level? --- ### Jameson Lopp (Casa): Well, there’s also full-block aggregation, right? This is going really far down the rabbit hole, and I think it’s not even something that’s on the table. There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations. My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized. If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again. --- ### NiftyNei (Moderator): So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation. We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there. One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right? Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated. --- ### Jameson Lopp (Casa): Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically. If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount. It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO. You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet. It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot. It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before. So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so. --- ### Fabian Jahr (Brink): And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy. The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property. Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.” Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it. Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature. --- ### Jameson Lopp (Casa): Yeah, we have to think about the incentives, right? I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are. But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late. We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so. It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software. Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money? --- ### Craig Raw (Sparrow): So you might be wondering at this stage what the savings actually look like. It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block. You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage. Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%. But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space. So that’s how I would encourage you to think about it from the start. For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride. We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about. --- ### NiftyNei (Moderator): I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy. I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal? What was it about the Taproot process where this proposal didn’t make it over the line? --- ### Fabian Jahr (Brink): I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed. From what I can see, I don’t think there was any direct opposition. The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller. I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding. I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much. --- ### Craig Raw (Sparrow): Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough. There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.” That’s an interesting point of view. --- ### Jameson Lopp (Casa): It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet. --- ### Craig Raw (Sparrow): Yeah, so we’re in a very different space now. Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine. I’m talking about the well-understood half-signature aggregation form of it. From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that. So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing. If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down. So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line. --- ### Jameson Lopp (Casa): I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin. With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process. As far as I’m aware, there’s been limited adoption of Schnorr so far. I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility. I care about this a lot, operating a multi-signature self-custody wallet. We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature. That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out. So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block. --- ### NiftyNei (Moderator): So, we only have a few minutes left. Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in. --- ### Fabian Jahr (Brink): There are still quite a few things to hammer out in terms of all the details, like defining a spec. For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open. However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity. We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now. --- ### Jameson Lopp (Casa): Yeah, call your local developer and demand signature aggregation today. --- ### Craig Raw (Sparrow): Fabian has developed a great site where you can learn more. If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it. It’s very easy to read, not overly technical, and I think it gives a good grounding in these things. Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not. As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now. So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not. --- ### Jameson Lopp (Casa): I don’t know, do you want to save money? It should be an easy question. --- ### Fabian Jahr (Brink): And have better privacy. --- ### NiftyNei (Moderator): Great! Thanks y’all. --- **Follow the speakers: ** [NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr) **Watch the original content: ** [Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107) **Also read: Build It Right: ** [Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/) **Disclaimer: ** Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/). @ 44dc1c2d:31c74f0b
2024-09-09 01:55:24## Chef's notes Makes an excellent Chicken sandwich. ## Details - ⏲️ Prep time: 6 Ish hours - 🍳 Cook time: 40 min - 🍽️ Servings: 1 loaf ## Ingredients - 3 ½ - 4 cups bread flour, or more as needed - 1 ⅓ cups warm milk (110°F – 115°F) - 5 tablespoons honey - 4 tablespoons salted butter, melted and slightly cooled - 1 tablespoon instant “rapid rise” yeast - 1 ½ teaspoons salt - Oil or butter for greasing the bowl - 1 tablespoon melted salted butter, for brushing the crust at the end ## Directions 1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl. 2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes. 3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours. 4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan. 5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F. 6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped. 7. Brush the top of the warm bread with melted butter. 8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24## Chef's notes Makes an excellent Chicken sandwich. ## Details - ⏲️ Prep time: 6 Ish hours - 🍳 Cook time: 40 min - 🍽️ Servings: 1 loaf ## Ingredients - 3 ½ - 4 cups bread flour, or more as needed - 1 ⅓ cups warm milk (110°F – 115°F) - 5 tablespoons honey - 4 tablespoons salted butter, melted and slightly cooled - 1 tablespoon instant “rapid rise” yeast - 1 ½ teaspoons salt - Oil or butter for greasing the bowl - 1 tablespoon melted salted butter, for brushing the crust at the end ## Directions 1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl. 2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes. 3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours. 4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan. 5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F. 6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped. 7. Brush the top of the warm bread with melted butter. 8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing. @ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one? Thanks originally posted at https://stacker.news/items/677439
@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one? Thanks originally posted at https://stacker.news/items/677439 @ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。 --- ### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。 项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed 项目的教程很详细,具体去看项目教程。 ### telegram设置: - 需要有telegram账号 - 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。 - 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。 - 一定要添加创建的机器人到频道作为管理员才能使用。 ### cloudflare的设置 - 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。 - 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图: [](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv") - BASIC_USER 后台登陆名 - BASIC_PASS 后台密码 - AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。 ### 其他 - 成人内容屏蔽 - pico 使用api接口 去项目地址看 ### 最后 我搭建的地址: https://imgbed.lepidus.me
@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。 --- ### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。 项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed 项目的教程很详细,具体去看项目教程。 ### telegram设置: - 需要有telegram账号 - 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。 - 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。 - 一定要添加创建的机器人到频道作为管理员才能使用。 ### cloudflare的设置 - 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。 - 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图: [](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv") - BASIC_USER 后台登陆名 - BASIC_PASS 后台密码 - AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。 ### 其他 - 成人内容屏蔽 - pico 使用api接口 去项目地址看 ### 最后 我搭建的地址: https://imgbed.lepidus.me @ c6f7077f:ad5d48fd
2024-09-08 01:24:03***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further. #### ***Consider the Most Fundamental Questions*** 1. **The Origin of the Universe** 2. **The Origin of Life on Earth** #### ***The Origin of the Universe*** You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding. The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding. Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**. #### ***The Origin of Life on Earth*** The origin of life is even more complex. Life requires three essential components: - **Proteins** for basic functioning - **RNA** for storing and replicating genes - **Lipids** (cell walls) to create separation from the environment Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**. #### ***The Question of Certainty*** If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early. #### ***Reclaiming Control of Science and Education*** The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend: - **“A Brief History of Time”** by **Stephen Hawking** for physics - **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further. #### ***Consider the Most Fundamental Questions*** 1. **The Origin of the Universe** 2. **The Origin of Life on Earth** #### ***The Origin of the Universe*** You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding. The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding. Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**. #### ***The Origin of Life on Earth*** The origin of life is even more complex. Life requires three essential components: - **Proteins** for basic functioning - **RNA** for storing and replicating genes - **Lipids** (cell walls) to create separation from the environment Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**. #### ***The Question of Certainty*** If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early. #### ***Reclaiming Control of Science and Education*** The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend: - **“A Brief History of Time”** by **Stephen Hawking** for physics - **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner. @ 655a7cf1:d0510794
2024-09-06 23:45:52I can't stop thinking about it. When I go to clear out a cave in Skyrim I always find the troll the spider some version of some enemy with gold. I ask myself how did they get this gold.? Is there someone in the cities that goes to and fro to have commerce with underworld. If so what would this market look like. Would it be trade based or commodity based. Sometimes in these caves I can find upwards of 100 gold I can also find individuals with upwards of 20 gold on them. Assuming they live paycheck to paycheck this is a moderate size of money they're carrying around from week to week. It tells me that the trade is doing well. Am I completely psychotic for constantly thinking about this? Does anybody else thought about this or done any research or have any links that I can find? originally posted at https://stacker.news/items/673609
@ 655a7cf1:d0510794
2024-09-06 23:45:52I can't stop thinking about it. When I go to clear out a cave in Skyrim I always find the troll the spider some version of some enemy with gold. I ask myself how did they get this gold.? Is there someone in the cities that goes to and fro to have commerce with underworld. If so what would this market look like. Would it be trade based or commodity based. Sometimes in these caves I can find upwards of 100 gold I can also find individuals with upwards of 20 gold on them. Assuming they live paycheck to paycheck this is a moderate size of money they're carrying around from week to week. It tells me that the trade is doing well. Am I completely psychotic for constantly thinking about this? Does anybody else thought about this or done any research or have any links that I can find? originally posted at https://stacker.news/items/673609 @ 8cb60e21:5f2deaea
2024-09-06 22:28:24JavaScript For Cats An introduction for new programmers cat So easy your human companion could do it too! JavaScript is a programming language or, in other words, a means by which a computer is instructed to do things. Just the same as one controls humans with hisses and meows, one controls computers with statements written in a programming language. All web browsers understand JavaScript and you can take advantage of that to make web pages do crazy things! JavaScript started as a way to make web pages more interactive. Nowadays JavaScript runs in more places than just web browsers — it runs on web servers, phones and even robots! This page will teach you some JavaScript basics so that you can get up and running in no time*. * Actual time: more than none. Probably an hour or two. Also since you are a cat you are less likely to run and more likely to lay around in the sun Table of contents The console Strings Values and variables Using functions Built in JS functions Download new JS functions Writing new functions Loops Arrays Objects Callbacks Recommended reading Don't be a scaredy-cat cat You will always land on your feet — even when programming! Unlike pawing over a glass of water on your laptop, nothing in these tutorials will damage your computer in any way, even if you mistype a command or click the wrong button. Like cats, computer programmers make mistakes all time: misspelling things, forgetting quotes or brackets, and being forgetful of how basic functions (and yarn, lasers) work. Programmers care more about making it work eventually rather than trying to make it work the very first time. The best way to learn is by making mistakes! So don't be a scaredy-cat! The absolute worst thing that will happen is that you might have to refresh this page in your web browser if you get stuck. Don't worry though, this will happen very rarely. # The basics There is JavaScript running on this page right now. Let's play around with it a little. For the sake of simplicity I'll assume you are using Google Chrome to read this page (if you aren't it's probably easier on both of us if you follow along with Chrome). First, right click anywhere on the screen and hit Inspect Element, then click on the Console tab. You should see a thingy that looks like this: console This is a console, otherwise known as a "command line" or "terminal". Basically it's a way to type one thing at a time into a computer and immediately get the computers answer back. They are super useful as a learning tool (I still use the console nearly every day that I'm coding). The console does some pretty cool stuff. Here I have started to type something and the console is helping me out by giving me a list of all the possible things I could continue to type! Another thing you could do is type 1 + 1 into the console and then hit the Enter key and watch what happens. Using the console is a very important part of learning JavaScript. If you don't know if something works or what the command is for something, go to the console and figure it out! Here's an example: # Strings Since I am a cat I want to replace every instance of the word dog on the Internet with those blasted dogs. First go into your console and type in a few sentences that contain the word dog at least once. In JavaScript a bunch of letters, numbers, words or anything else is known as a String (as in a string of characters). Strings have to begin AND end with a quotation mark. Single ' or double " is fine, just make sure you use the same at the beginning as you do at the end. console See the nasty error message? Don't worry - you didn't break any laws. SyntaxError ILLEGAL is just the way it sounds when robots tell you that your program has a problem. The first two sentences had matching quotation marks at the beginning and end, but when I mixed single and double quotation marks it freaked out on me. OK, to fix up one of these sentences (by replacing dog with our enhanced version) we have to first save the original sentence so that we can call it up later when we do our replacing magic. Notice how the string gets repeated in red when we type it into the console? This is because we haven't told it to save the sentence anywhere so it just gives it right back (or it gives us an Error back if we messed something up). # Values and variables Values are the simplest components in JavaScript. 1 is a value, true is a value, "hello" is a value, function() {} is a value, the list goes on! There are a handful of different types of values in JavaScript but we don't need to go over them all right away — you will learn them naturally the more you code! To store values we use things called variables. The word 'variable' means 'can change' and is used because variables can store many different types of values and can change their value many times. They are pretty much like mailboxes. We put something in a variable, like our sentence, and then give the variable an address that we can use to look up the sentence later. In real life mailboxes have to have PO Box numbers but in JavaScript you usually just use lowercase letters or numbers without any spaces. console var is shorthand for variable and the = means store the thing on the right-hand side in the thing on the left-hand side. Also as you can see, now that we are storing our sentence in a variable the console doesn't just return our sentence right away, but instead gives us undefined which means there was nothing to return. If you simply type a variable name into the console it will print out the value stored in that variable. A note about variables is that by default they go away when you switch to a different page. If I were to hit the Refresh button in Chrome, for example, my dogSentence variable would get wiped and it would be like it never existed. But don't worry about this too much for now — you can just hit the up or down arrows on your keyboard while in the console to go through everything you've entered in recently. # Functions Now that we have our sentence stored in a variable, let's change a word stored in it! We can do this by performing a function. Functions are a type of value that, well, serve a specific function (AKA purpose or action) for us. Calling them "actions" sounded weird I guess so they went with the word "function" instead. JavaScript has a function called replace that does exactly what we want! Functions take in any number of values in their parentheses (zero, one or many) and return either nothing (undefined) or the changed string. The replace function is available to use on any strings and takes in two values: the characters to take out and the characters to swap in. It gets confusing to describe these things so here is a visual example: console Notice how the value of dogSentence is the same even after we run replace on it? This is because the replace function, (and most JavaScript functions for that matter) takes the value we give it and returns a new value, without modifying the value we passed in. Since we didn't store the result (there is no = on the left side of the replace function) it just printed out the return value in our console. # The "standard library" You might be wondering what other functions are available in JavaScript. The answer: A TON. There are lots built in, standard libraries that you can learn about at MDN (A site run by Mozilla that has lotsa nifty information about web technologies). For example here is the MDN page on JavaScript's Math object. # Third-party JavaScript There is also a lot of JavaScript code available that is not built in. JavaScript from third parties is usually referred to as a "library" or "plugin". One of my favorites is called Underscore.js. Let's go and grab it and load it into our page! First go to the Underscore site, http://underscorejs.org/, click on the download link (I usually use development versions because they are easier to read but both will give you the same basic functionality), and then copy all the code onto your clipboard (you can use Select All from the Edit menu to select everything). Then paste it into your console and hit enter. Now your browser has a new variable in it: _. Underscore gives you a ton of helpful functions to play with. We'll learn more about how to use them later. console # Making new functions You aren't limited to using other peoples functions — you can also write them yourself. It's pretty easy! Let's make a function called makeMoreExciting that adds a bunch of exclamation points to the end of a string. function makeMoreExciting(string) { return string + '!!!!' } In my head I read it out loud like this: "there's a function called 'make more exciting' that takes in a string and returns a new copy of that string that has a bunch of exclamation points at the end". Here is how we would write this in the console manually if we weren't using a function: console The expression string + '!!!!' returns a new string and our variable called string stays the same as before (since we never updated it to anything else with =). Let's use our function instead of doing it manually. First, paste the function into the console and then call the function by passing in a string: console You could also call the same function by passing in a variable that points to a string (in the above example we just typed the string straight in there as a value instead of saving it to a variable first): console The line makeMoreExciting(sentence) is equivalent to saying sentence + '!!!!'. What if we wanted to modify in-place (aka update) the value of sentence? Simply save the return value of the function back into our sentence variable: var sentence = "time for a nap" sentence = makeMoreExciting(sentence) Now sentence will have the exclamation marks in it! Note that you only have to use var when you are initializing a variable — the first time you ever use it. After that you shouldn't use var unless you want to re-initialize (reset/clear/empty) the variable. What would happen if we took out the return statement in our function? console Why is sentence empty? Because functions return undefined by default! You can choose to return a value by returning something. Functions should take in a value and, if they change the value or create a new value that is supposed to be used later, return a value (fun fact: a fancy term for this style is functional programming). Here is another function that doesn't return anything but instead uses a different method to show us the output: function yellIt(string) { string = string.toUpperCase() string = makeMoreExciting(string) console.log(string) } This function, yellIt, uses our previous function makeMoreExciting as well as the built-in String method toUpperCase. Methods are just a name for a function when it belongs to something — in this case toUpperCase is a function that belongs to String so we can refer to it as either a method or a function. makeMoreExciting on the other hand doesn't belong to anyone so it would be technically incorrect to refer to it as a method (confusing, I know). The last line of the function is another built-in that simply takes in any values that you give it and prints them out into the console. console So is there something wrong with the above yellIt function? It depends! Here are the two major types of functions: functions that modify or create values and return them functions take in values and perform some action that cannot be returned console.log is an example of the second type of function: it prints things out to your console — an action that you can see with your eyes but that cannot be represented as a JavaScript value. My own rule of thumb is to try to keep the two types of functions separate from each other, so here's how I would rewrite the yellIt function: function yellIt(string) { string = string.toUpperCase() return makeMoreExciting(string) } console.log(yellIt("i fear no human")) This way yellIt becomes more generic, meaning it only does one or two simple little things and doesn't know anything about printing itself to a console — that part can always be programmed later, outside the function definition. # Loops Now that we have some basic skills under our belt (Author's note: do cats even wear belts?) we can start being lazy. What?! Yes, that's right: programming is about being lazy. Larry Wall, inventor of the Perl programming language, called laziness the most important virtue of a good programmer. If computers didn't exist you would have to do all sorts of tedious tasks by hand, but if you learn to program you can lay in the sun all day while a computer somewhere runs your programs for you. It is a glorious lifestyle filled with relaxation! Loops are one of the most important ways to harness the power of a computer. Remember Underscore.js from earlier? Make sure you have it loaded in the page (remember: you can just hit the up arrow on your keyboard a few times and then hit Enter to load it in again if you need to) and try copy/pasting this into your console: function logANumber(someNumber) { console.log(someNumber) } _.times(10, logANumber) This code uses the times method of Underscore which takes in 1 number and 1 function and then starts from 0 and for 10 steps counts up by 1, calling the function with the number each step of the way. console If we were to manually write out what times is doing in the above code it would look like this: logANumber(0) logANumber(1) logANumber(2) logANumber(3) logANumber(4) logANumber(5) logANumber(6) logANumber(7) logANumber(8) logANumber(9) But cats refuse to do unnecessary manual work like this so we must always ask ourselves, "am I doing this in the laziest way possible?". So why is this called looping? Think of it like this: If we were to write out a list of 10 numbers (from 0 to 9) using a JavaScript Array it would look like this: var zeroThroughTen = [0, 1, 2, 3, 4, 5, 6, 7, 8, 9] What times really does is visit each number and repeat a task: in the example above the task was to call the logANumber function with the current number. Repeating tasks in this way is referred to as looping over the Array. # Arrays I've mentioned these a few times but let's spend a minute learning about them. Imagine you need to keep track of all your buddies. Well, an Array will do just fine. Think of an Array like a sorted list that you can keep tons of stuff in. This is how you make one: var myCatFriends = ["bill", "tabby", "ceiling"] Sweet! Now you have a list of your cat buddies. Elements (that is what you call a single item in an array) that are stored within arrays start at 0 and count up from there. So myCatFriends[0] returns bill and myCatFriends[1] returns tabby... etc etc. To get buddies out of your brand new Array you can just access an element directly like so: console.log(myCatFriends[0]) console If you made a brand new cat friend at the hippest cat club the other night and you want to add them to your list it is super simple: myCatFriends.push("super hip cat"). To check that the new cat made it into your array you can use .length: console Notice how push returned the length? Handy! Also take note that arrays will always preserve ordering which means they will remember the order in which you added or defined things. Not everything in JavaScript preserves ordering so remember this special property of Arrays! # Objects Arrays are good for lists, but for other tasks they can be hard to work with. Consider our array of cat friends. What if you also wanted to store more than just names? var myCatFriends = ["bill", "tabby", "ceiling"] var lastNames = ["the cat", "cat", "cat"] var addresses = ["The Alley", "Grandmas House", "Attic"] Sometimes it is nice to have all of the addresses or names in one variable. But sometimes you have a cat in mind, let's say Bill, and you just want to look up that cat's address. With arrays it takes a lot of work because you can't just say 'hey array, give me Bill's address' because 'Bill' is in one array and his address is in a totally different array. console This can be brittle because if our arrays change and we add a new cat to the beginning we would have to also update our billsPosition variable to point to the new location of Bill's information in the arrays! Here is a easier to maintain way to store information like this using objects: var firstCat = { name: "bill", lastName: "the cat", address: "The Alley" } var secondCat = { name: "tabby", lastName: "cat", address: "Grandmas House" } var thirdCat = { name: "ceiling", lastName: "cat", address: "Attic" } Why would we do it this way? Because now we have a variable for each cat that we can use to get that cats values in a more convenient and readable way. console You can think of Objects like keys on a keyring. Each one is for a specific door and if you have nice labels on your keys you can open doors very fast. In fact, the things on the left hand side of the : are called keys (are also known as properties) and the things on the right hand side are values. // an object with a single key 'name' and single value 'bill' { name: 'bill' } So why would you ever use arrays if you can just put your data in objects? Because objects don't remember the order of the keys that you set. You might enter in an object like this: { date: "10/20/2012", diary: "slept a bit today", name: "Charles" } But the computer could give it back to you like this: { diary: "slept a bit today", name: "Charles", date: "10/20/2012" } Or like this! { name: "Charles", diary: "slept a bit today", date: "10/20/2012" } So you can't ever trust the order of keys in objects. If you wanna get REALLY fancy you can make an array filled with objects, or an object filled with arrays! var moodLog = [ { date: "10/20/2012", mood: "catnipped" }, { date: "10/21/2012", mood: "nonplussed" }, { date: "10/22/2012", mood: "purring" } ] // ordered from least to most favorite var favorites = { treats: ["bird sighting", "belly rub", "catnip"], napSpots: ["couch", "planter box", "human face"] } When you combine different things like this you are making data structures, just like legos! # Callbacks Callbacks aren't really a feature of JavaScript like Object or Array, but instead just a certain way to use functions. To understand why callbacks are useful you first have to learn about asynchronous (often shortened to async) programming. Asynchronous code by definition is code written in a way that is not synchronous. Synchronous code is easy to understand and write. Here is an example to illustrate: var photo = download('http://foo-chan.com/images/sp.jpg') uploadPhotoTweet(photo, '@maxogden') This synchronous pseudo-code downloads an adorable cat photo and then uploads the photo to twitter and tweets the photo at @maxogden. Pretty straightforward! (Author's note: I @maxogden do happily accept random cat photo tweets) This code is synchronous because in order for photo to get uploaded to the tweet, the photo download must be completed. This means that line 2 cannot run until the task on line 1 is totally finished. If we were to actually implement this pseudo-code we would want to make sure that download 'blocked' execution until the download was finished, meaning it would prevent any other JavaScript from being executed until it finished, and then when the download completes it would un-block the JavaScript execution and line 2 would execute. Synchronous code is fine for things that happen fast, but it's horrible for things that require saving, loading, downloading or uploading. What if the server you're downloading the photo from is slow, or the internet connection you are using is slow, or the computer you are running the code on has too many youtube cat video tabs open and is running slowly? It means that it could potentially take minutes of waiting before line 2 gets around to running. Meanwhile, because all JavaScript on the page is being blocked from being run while the download is happening, the webpage would totally freeze up and become unresponsive until the download is done. Blocking execution should be avoided at all costs, especially when doing so makes your program freeze up or become unresponsive. Let's assume the photo above takes one second to download. To illustrate how long one second is to a modern computer, here is a program that tests to see how many tasks JavaScript can process in one second. function measureLoopSpeed() { var count = 0 function addOne() { count = count + 1 } // Date.now() returns a big number representing the number of // milliseconds that have elapsed since Jan 01 1970 var now = Date.now() // Loop until Date.now() is 1000 milliseconds (1 second) or more into // the future from when we started looping. On each loop, call addOne while (Date.now() - now < 1000) addOne() // Finally it has been >= 1000ms, so let's print out our total count console.log(count) } measureLoopSpeed() Copy-paste the above code into your JavaScript console and after one second it should print out a number. On my computer I got 8527360, approximately 8.5 million. In one second JavaScript can call the addOne function 8.5 million times! So if you have synchronous code for downloading a photo, and the photo download takes one second, it means you are potentially preventing 8.5 million operations from happening while JavaScript execution is blocked. Some languages have a function called sleep that blocks execution for some number of seconds. For example here is some bash code running in Terminal.app on Mac OS that uses sleep. When you run the command sleep 3 && echo 'done sleeping now' it blocks for 3 seconds before printing out done sleeping now. console JavaScript doesn't have a sleep function. Since you are a cat you are probably asking yourself, "Why am I learning a programming language that does not involve sleeping?". But stay with me. Instead of relying on sleep to wait for things to happen the design of JavaScript encourages use of functions instead. If you have to wait for task A to finish before doing task B, you put all of the code for task B into a function and you only call that function when A is done. For example, this is blocking-style code: a() b() And this is in a non-blocking style: a(b) In the non-blocking version b is a callback to a. In the blocking version a and b are both called/invoked (they both have () after them which executes the functions immediately). In the non-blocking version you will notice that only a gets invoked, and b is simply passed in to a as an argument. In the blocking version, there is no explicit relationship between a and b. In the non-blocking version it becomes a's job to do what it needs to do and then call b when it is done. Using functions in this way is called callbacks because your callback function, in this case b, gets called later on when a is all done. Here is a pseudocode implementation of what a might look like: function a(done) { download('https://pbs.twimg.com/media/B4DDWBrCEAA8u4O.jpg:large', function doneDownloading(error, png) { // handle error if there was one if (err) console.log('uh-oh!', error) // call done when you are all done done() }) } Think back to our non-blocking example, a(b), where we call a and pass in b as the first argument. In the function definition for a above the done argument is our b function that we pass in. This behavior is something that is hard to wrap your head around at first. When you call a function, the arguments you pass in won't have the same variable names when they are in the function. In this case what we call b is called done inside the function. But b and done are just variable names that point to the same underlying function. Usually callback functions are labelled something like done or callback to make it clear that they are functions that should be called when the current function is done. So, as long as a does it's job and called b when it is done, both a and b get called in both the non-blocking and blocking versions. The difference is that in the non-blocking version we don't have to halt execution of JavaScript. In general non-blocking style is where you write every function so that it can return as soon as possible, without ever blocking. To drive the point home even further: If a takes one second to complete, and you use the blocking version, it means you can only do one thing. If you use the non-blocking version (aka use callbacks) you can do literally millions of other things in that same second, which means you can finish your work millions of times faster and sleep the rest of the day. Remember: programming is all about laziness and you should be the one sleeping, not your computer. Hopefully you can see now that callbacks are just functions that call other functions after some asynchronous task. Common examples of asynchronous tasks are things like reading a photo, downloading a song, uploading a picture, talking to a database, waiting for a user to hit a key or click on someone, etc. Anything that takes time. JavaScript is really great at handling asynchronous tasks like these as long as you take the time to learn how to use callbacks and keep your JavaScript from being blocked. The end! This is just the beginning of your relationship with JavaScript! You can't learn it all at once, but you should find what works for you and try to learn all of the concepts here. I'd recommend coming back again tomorrow and going through the entire thing again from the beginning! It might take a few times through before you get everything (programming is hard). Just try to avoid reading this page in any rooms that contain shiny objects . . . they can be incredibly distracting. Got another topic you wanna see covered? Open an issue for it on github. # Recommended reading JavaScript For Cats skips over lots of details that aren't important for getting started (cats are not known for their attention spans), but if you feel like you need to dive in deeper then check these out: NodeSchool.io is a community driven, open source educational software that teaches various web development skills in an interactive, self-guided format. I helped make NodeSchool! Sadly it features fewer cats than this page. Eloquent Javascript is a free book that teaches you JavaScript! It's pretty good! Especially the chapter on values, variables, and control flow Mozilla's JavaScript Guide also has a pretty sweet intro chapter called values, variables and literals standard JS Style Guide is a "zero configuration" linter for JS style that I use Let's Write Code by @shama a great series of YouTube coding tutorials made by a friend of mine # Satisfied customers satisfied customer satisfied customer satisfied customer satisfied customer satisfied customer JSForCats.com is a labor of love and work in progress by @maxogden. If you would like to contribute and make this tutorial better there is a Github repo right over here. console
@ 8cb60e21:5f2deaea
2024-09-06 22:28:24JavaScript For Cats An introduction for new programmers cat So easy your human companion could do it too! JavaScript is a programming language or, in other words, a means by which a computer is instructed to do things. Just the same as one controls humans with hisses and meows, one controls computers with statements written in a programming language. All web browsers understand JavaScript and you can take advantage of that to make web pages do crazy things! JavaScript started as a way to make web pages more interactive. Nowadays JavaScript runs in more places than just web browsers — it runs on web servers, phones and even robots! This page will teach you some JavaScript basics so that you can get up and running in no time*. * Actual time: more than none. Probably an hour or two. Also since you are a cat you are less likely to run and more likely to lay around in the sun Table of contents The console Strings Values and variables Using functions Built in JS functions Download new JS functions Writing new functions Loops Arrays Objects Callbacks Recommended reading Don't be a scaredy-cat cat You will always land on your feet — even when programming! Unlike pawing over a glass of water on your laptop, nothing in these tutorials will damage your computer in any way, even if you mistype a command or click the wrong button. Like cats, computer programmers make mistakes all time: misspelling things, forgetting quotes or brackets, and being forgetful of how basic functions (and yarn, lasers) work. Programmers care more about making it work eventually rather than trying to make it work the very first time. The best way to learn is by making mistakes! So don't be a scaredy-cat! The absolute worst thing that will happen is that you might have to refresh this page in your web browser if you get stuck. Don't worry though, this will happen very rarely. # The basics There is JavaScript running on this page right now. Let's play around with it a little. For the sake of simplicity I'll assume you are using Google Chrome to read this page (if you aren't it's probably easier on both of us if you follow along with Chrome). First, right click anywhere on the screen and hit Inspect Element, then click on the Console tab. You should see a thingy that looks like this: console This is a console, otherwise known as a "command line" or "terminal". Basically it's a way to type one thing at a time into a computer and immediately get the computers answer back. They are super useful as a learning tool (I still use the console nearly every day that I'm coding). The console does some pretty cool stuff. Here I have started to type something and the console is helping me out by giving me a list of all the possible things I could continue to type! Another thing you could do is type 1 + 1 into the console and then hit the Enter key and watch what happens. Using the console is a very important part of learning JavaScript. If you don't know if something works or what the command is for something, go to the console and figure it out! Here's an example: # Strings Since I am a cat I want to replace every instance of the word dog on the Internet with those blasted dogs. First go into your console and type in a few sentences that contain the word dog at least once. In JavaScript a bunch of letters, numbers, words or anything else is known as a String (as in a string of characters). Strings have to begin AND end with a quotation mark. Single ' or double " is fine, just make sure you use the same at the beginning as you do at the end. console See the nasty error message? Don't worry - you didn't break any laws. SyntaxError ILLEGAL is just the way it sounds when robots tell you that your program has a problem. The first two sentences had matching quotation marks at the beginning and end, but when I mixed single and double quotation marks it freaked out on me. OK, to fix up one of these sentences (by replacing dog with our enhanced version) we have to first save the original sentence so that we can call it up later when we do our replacing magic. Notice how the string gets repeated in red when we type it into the console? This is because we haven't told it to save the sentence anywhere so it just gives it right back (or it gives us an Error back if we messed something up). # Values and variables Values are the simplest components in JavaScript. 1 is a value, true is a value, "hello" is a value, function() {} is a value, the list goes on! There are a handful of different types of values in JavaScript but we don't need to go over them all right away — you will learn them naturally the more you code! To store values we use things called variables. The word 'variable' means 'can change' and is used because variables can store many different types of values and can change their value many times. They are pretty much like mailboxes. We put something in a variable, like our sentence, and then give the variable an address that we can use to look up the sentence later. In real life mailboxes have to have PO Box numbers but in JavaScript you usually just use lowercase letters or numbers without any spaces. console var is shorthand for variable and the = means store the thing on the right-hand side in the thing on the left-hand side. Also as you can see, now that we are storing our sentence in a variable the console doesn't just return our sentence right away, but instead gives us undefined which means there was nothing to return. If you simply type a variable name into the console it will print out the value stored in that variable. A note about variables is that by default they go away when you switch to a different page. If I were to hit the Refresh button in Chrome, for example, my dogSentence variable would get wiped and it would be like it never existed. But don't worry about this too much for now — you can just hit the up or down arrows on your keyboard while in the console to go through everything you've entered in recently. # Functions Now that we have our sentence stored in a variable, let's change a word stored in it! We can do this by performing a function. Functions are a type of value that, well, serve a specific function (AKA purpose or action) for us. Calling them "actions" sounded weird I guess so they went with the word "function" instead. JavaScript has a function called replace that does exactly what we want! Functions take in any number of values in their parentheses (zero, one or many) and return either nothing (undefined) or the changed string. The replace function is available to use on any strings and takes in two values: the characters to take out and the characters to swap in. It gets confusing to describe these things so here is a visual example: console Notice how the value of dogSentence is the same even after we run replace on it? This is because the replace function, (and most JavaScript functions for that matter) takes the value we give it and returns a new value, without modifying the value we passed in. Since we didn't store the result (there is no = on the left side of the replace function) it just printed out the return value in our console. # The "standard library" You might be wondering what other functions are available in JavaScript. The answer: A TON. There are lots built in, standard libraries that you can learn about at MDN (A site run by Mozilla that has lotsa nifty information about web technologies). For example here is the MDN page on JavaScript's Math object. # Third-party JavaScript There is also a lot of JavaScript code available that is not built in. JavaScript from third parties is usually referred to as a "library" or "plugin". One of my favorites is called Underscore.js. Let's go and grab it and load it into our page! First go to the Underscore site, http://underscorejs.org/, click on the download link (I usually use development versions because they are easier to read but both will give you the same basic functionality), and then copy all the code onto your clipboard (you can use Select All from the Edit menu to select everything). Then paste it into your console and hit enter. Now your browser has a new variable in it: _. Underscore gives you a ton of helpful functions to play with. We'll learn more about how to use them later. console # Making new functions You aren't limited to using other peoples functions — you can also write them yourself. It's pretty easy! Let's make a function called makeMoreExciting that adds a bunch of exclamation points to the end of a string. function makeMoreExciting(string) { return string + '!!!!' } In my head I read it out loud like this: "there's a function called 'make more exciting' that takes in a string and returns a new copy of that string that has a bunch of exclamation points at the end". Here is how we would write this in the console manually if we weren't using a function: console The expression string + '!!!!' returns a new string and our variable called string stays the same as before (since we never updated it to anything else with =). Let's use our function instead of doing it manually. First, paste the function into the console and then call the function by passing in a string: console You could also call the same function by passing in a variable that points to a string (in the above example we just typed the string straight in there as a value instead of saving it to a variable first): console The line makeMoreExciting(sentence) is equivalent to saying sentence + '!!!!'. What if we wanted to modify in-place (aka update) the value of sentence? Simply save the return value of the function back into our sentence variable: var sentence = "time for a nap" sentence = makeMoreExciting(sentence) Now sentence will have the exclamation marks in it! Note that you only have to use var when you are initializing a variable — the first time you ever use it. After that you shouldn't use var unless you want to re-initialize (reset/clear/empty) the variable. What would happen if we took out the return statement in our function? console Why is sentence empty? Because functions return undefined by default! You can choose to return a value by returning something. Functions should take in a value and, if they change the value or create a new value that is supposed to be used later, return a value (fun fact: a fancy term for this style is functional programming). Here is another function that doesn't return anything but instead uses a different method to show us the output: function yellIt(string) { string = string.toUpperCase() string = makeMoreExciting(string) console.log(string) } This function, yellIt, uses our previous function makeMoreExciting as well as the built-in String method toUpperCase. Methods are just a name for a function when it belongs to something — in this case toUpperCase is a function that belongs to String so we can refer to it as either a method or a function. makeMoreExciting on the other hand doesn't belong to anyone so it would be technically incorrect to refer to it as a method (confusing, I know). The last line of the function is another built-in that simply takes in any values that you give it and prints them out into the console. console So is there something wrong with the above yellIt function? It depends! Here are the two major types of functions: functions that modify or create values and return them functions take in values and perform some action that cannot be returned console.log is an example of the second type of function: it prints things out to your console — an action that you can see with your eyes but that cannot be represented as a JavaScript value. My own rule of thumb is to try to keep the two types of functions separate from each other, so here's how I would rewrite the yellIt function: function yellIt(string) { string = string.toUpperCase() return makeMoreExciting(string) } console.log(yellIt("i fear no human")) This way yellIt becomes more generic, meaning it only does one or two simple little things and doesn't know anything about printing itself to a console — that part can always be programmed later, outside the function definition. # Loops Now that we have some basic skills under our belt (Author's note: do cats even wear belts?) we can start being lazy. What?! Yes, that's right: programming is about being lazy. Larry Wall, inventor of the Perl programming language, called laziness the most important virtue of a good programmer. If computers didn't exist you would have to do all sorts of tedious tasks by hand, but if you learn to program you can lay in the sun all day while a computer somewhere runs your programs for you. It is a glorious lifestyle filled with relaxation! Loops are one of the most important ways to harness the power of a computer. Remember Underscore.js from earlier? Make sure you have it loaded in the page (remember: you can just hit the up arrow on your keyboard a few times and then hit Enter to load it in again if you need to) and try copy/pasting this into your console: function logANumber(someNumber) { console.log(someNumber) } _.times(10, logANumber) This code uses the times method of Underscore which takes in 1 number and 1 function and then starts from 0 and for 10 steps counts up by 1, calling the function with the number each step of the way. console If we were to manually write out what times is doing in the above code it would look like this: logANumber(0) logANumber(1) logANumber(2) logANumber(3) logANumber(4) logANumber(5) logANumber(6) logANumber(7) logANumber(8) logANumber(9) But cats refuse to do unnecessary manual work like this so we must always ask ourselves, "am I doing this in the laziest way possible?". So why is this called looping? Think of it like this: If we were to write out a list of 10 numbers (from 0 to 9) using a JavaScript Array it would look like this: var zeroThroughTen = [0, 1, 2, 3, 4, 5, 6, 7, 8, 9] What times really does is visit each number and repeat a task: in the example above the task was to call the logANumber function with the current number. Repeating tasks in this way is referred to as looping over the Array. # Arrays I've mentioned these a few times but let's spend a minute learning about them. Imagine you need to keep track of all your buddies. Well, an Array will do just fine. Think of an Array like a sorted list that you can keep tons of stuff in. This is how you make one: var myCatFriends = ["bill", "tabby", "ceiling"] Sweet! Now you have a list of your cat buddies. Elements (that is what you call a single item in an array) that are stored within arrays start at 0 and count up from there. So myCatFriends[0] returns bill and myCatFriends[1] returns tabby... etc etc. To get buddies out of your brand new Array you can just access an element directly like so: console.log(myCatFriends[0]) console If you made a brand new cat friend at the hippest cat club the other night and you want to add them to your list it is super simple: myCatFriends.push("super hip cat"). To check that the new cat made it into your array you can use .length: console Notice how push returned the length? Handy! Also take note that arrays will always preserve ordering which means they will remember the order in which you added or defined things. Not everything in JavaScript preserves ordering so remember this special property of Arrays! # Objects Arrays are good for lists, but for other tasks they can be hard to work with. Consider our array of cat friends. What if you also wanted to store more than just names? var myCatFriends = ["bill", "tabby", "ceiling"] var lastNames = ["the cat", "cat", "cat"] var addresses = ["The Alley", "Grandmas House", "Attic"] Sometimes it is nice to have all of the addresses or names in one variable. But sometimes you have a cat in mind, let's say Bill, and you just want to look up that cat's address. With arrays it takes a lot of work because you can't just say 'hey array, give me Bill's address' because 'Bill' is in one array and his address is in a totally different array. console This can be brittle because if our arrays change and we add a new cat to the beginning we would have to also update our billsPosition variable to point to the new location of Bill's information in the arrays! Here is a easier to maintain way to store information like this using objects: var firstCat = { name: "bill", lastName: "the cat", address: "The Alley" } var secondCat = { name: "tabby", lastName: "cat", address: "Grandmas House" } var thirdCat = { name: "ceiling", lastName: "cat", address: "Attic" } Why would we do it this way? Because now we have a variable for each cat that we can use to get that cats values in a more convenient and readable way. console You can think of Objects like keys on a keyring. Each one is for a specific door and if you have nice labels on your keys you can open doors very fast. In fact, the things on the left hand side of the : are called keys (are also known as properties) and the things on the right hand side are values. // an object with a single key 'name' and single value 'bill' { name: 'bill' } So why would you ever use arrays if you can just put your data in objects? Because objects don't remember the order of the keys that you set. You might enter in an object like this: { date: "10/20/2012", diary: "slept a bit today", name: "Charles" } But the computer could give it back to you like this: { diary: "slept a bit today", name: "Charles", date: "10/20/2012" } Or like this! { name: "Charles", diary: "slept a bit today", date: "10/20/2012" } So you can't ever trust the order of keys in objects. If you wanna get REALLY fancy you can make an array filled with objects, or an object filled with arrays! var moodLog = [ { date: "10/20/2012", mood: "catnipped" }, { date: "10/21/2012", mood: "nonplussed" }, { date: "10/22/2012", mood: "purring" } ] // ordered from least to most favorite var favorites = { treats: ["bird sighting", "belly rub", "catnip"], napSpots: ["couch", "planter box", "human face"] } When you combine different things like this you are making data structures, just like legos! # Callbacks Callbacks aren't really a feature of JavaScript like Object or Array, but instead just a certain way to use functions. To understand why callbacks are useful you first have to learn about asynchronous (often shortened to async) programming. Asynchronous code by definition is code written in a way that is not synchronous. Synchronous code is easy to understand and write. Here is an example to illustrate: var photo = download('http://foo-chan.com/images/sp.jpg') uploadPhotoTweet(photo, '@maxogden') This synchronous pseudo-code downloads an adorable cat photo and then uploads the photo to twitter and tweets the photo at @maxogden. Pretty straightforward! (Author's note: I @maxogden do happily accept random cat photo tweets) This code is synchronous because in order for photo to get uploaded to the tweet, the photo download must be completed. This means that line 2 cannot run until the task on line 1 is totally finished. If we were to actually implement this pseudo-code we would want to make sure that download 'blocked' execution until the download was finished, meaning it would prevent any other JavaScript from being executed until it finished, and then when the download completes it would un-block the JavaScript execution and line 2 would execute. Synchronous code is fine for things that happen fast, but it's horrible for things that require saving, loading, downloading or uploading. What if the server you're downloading the photo from is slow, or the internet connection you are using is slow, or the computer you are running the code on has too many youtube cat video tabs open and is running slowly? It means that it could potentially take minutes of waiting before line 2 gets around to running. Meanwhile, because all JavaScript on the page is being blocked from being run while the download is happening, the webpage would totally freeze up and become unresponsive until the download is done. Blocking execution should be avoided at all costs, especially when doing so makes your program freeze up or become unresponsive. Let's assume the photo above takes one second to download. To illustrate how long one second is to a modern computer, here is a program that tests to see how many tasks JavaScript can process in one second. function measureLoopSpeed() { var count = 0 function addOne() { count = count + 1 } // Date.now() returns a big number representing the number of // milliseconds that have elapsed since Jan 01 1970 var now = Date.now() // Loop until Date.now() is 1000 milliseconds (1 second) or more into // the future from when we started looping. On each loop, call addOne while (Date.now() - now < 1000) addOne() // Finally it has been >= 1000ms, so let's print out our total count console.log(count) } measureLoopSpeed() Copy-paste the above code into your JavaScript console and after one second it should print out a number. On my computer I got 8527360, approximately 8.5 million. In one second JavaScript can call the addOne function 8.5 million times! So if you have synchronous code for downloading a photo, and the photo download takes one second, it means you are potentially preventing 8.5 million operations from happening while JavaScript execution is blocked. Some languages have a function called sleep that blocks execution for some number of seconds. For example here is some bash code running in Terminal.app on Mac OS that uses sleep. When you run the command sleep 3 && echo 'done sleeping now' it blocks for 3 seconds before printing out done sleeping now. console JavaScript doesn't have a sleep function. Since you are a cat you are probably asking yourself, "Why am I learning a programming language that does not involve sleeping?". But stay with me. Instead of relying on sleep to wait for things to happen the design of JavaScript encourages use of functions instead. If you have to wait for task A to finish before doing task B, you put all of the code for task B into a function and you only call that function when A is done. For example, this is blocking-style code: a() b() And this is in a non-blocking style: a(b) In the non-blocking version b is a callback to a. In the blocking version a and b are both called/invoked (they both have () after them which executes the functions immediately). In the non-blocking version you will notice that only a gets invoked, and b is simply passed in to a as an argument. In the blocking version, there is no explicit relationship between a and b. In the non-blocking version it becomes a's job to do what it needs to do and then call b when it is done. Using functions in this way is called callbacks because your callback function, in this case b, gets called later on when a is all done. Here is a pseudocode implementation of what a might look like: function a(done) { download('https://pbs.twimg.com/media/B4DDWBrCEAA8u4O.jpg:large', function doneDownloading(error, png) { // handle error if there was one if (err) console.log('uh-oh!', error) // call done when you are all done done() }) } Think back to our non-blocking example, a(b), where we call a and pass in b as the first argument. In the function definition for a above the done argument is our b function that we pass in. This behavior is something that is hard to wrap your head around at first. When you call a function, the arguments you pass in won't have the same variable names when they are in the function. In this case what we call b is called done inside the function. But b and done are just variable names that point to the same underlying function. Usually callback functions are labelled something like done or callback to make it clear that they are functions that should be called when the current function is done. So, as long as a does it's job and called b when it is done, both a and b get called in both the non-blocking and blocking versions. The difference is that in the non-blocking version we don't have to halt execution of JavaScript. In general non-blocking style is where you write every function so that it can return as soon as possible, without ever blocking. To drive the point home even further: If a takes one second to complete, and you use the blocking version, it means you can only do one thing. If you use the non-blocking version (aka use callbacks) you can do literally millions of other things in that same second, which means you can finish your work millions of times faster and sleep the rest of the day. Remember: programming is all about laziness and you should be the one sleeping, not your computer. Hopefully you can see now that callbacks are just functions that call other functions after some asynchronous task. Common examples of asynchronous tasks are things like reading a photo, downloading a song, uploading a picture, talking to a database, waiting for a user to hit a key or click on someone, etc. Anything that takes time. JavaScript is really great at handling asynchronous tasks like these as long as you take the time to learn how to use callbacks and keep your JavaScript from being blocked. The end! This is just the beginning of your relationship with JavaScript! You can't learn it all at once, but you should find what works for you and try to learn all of the concepts here. I'd recommend coming back again tomorrow and going through the entire thing again from the beginning! It might take a few times through before you get everything (programming is hard). Just try to avoid reading this page in any rooms that contain shiny objects . . . they can be incredibly distracting. Got another topic you wanna see covered? Open an issue for it on github. # Recommended reading JavaScript For Cats skips over lots of details that aren't important for getting started (cats are not known for their attention spans), but if you feel like you need to dive in deeper then check these out: NodeSchool.io is a community driven, open source educational software that teaches various web development skills in an interactive, self-guided format. I helped make NodeSchool! Sadly it features fewer cats than this page. Eloquent Javascript is a free book that teaches you JavaScript! It's pretty good! Especially the chapter on values, variables, and control flow Mozilla's JavaScript Guide also has a pretty sweet intro chapter called values, variables and literals standard JS Style Guide is a "zero configuration" linter for JS style that I use Let's Write Code by @shama a great series of YouTube coding tutorials made by a friend of mine # Satisfied customers satisfied customer satisfied customer satisfied customer satisfied customer satisfied customer JSForCats.com is a labor of love and work in progress by @maxogden. If you would like to contribute and make this tutorial better there is a Github repo right over here. console @ 8cb60e21:5f2deaea
2024-09-06 22:23:03<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-06 22:23:03<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 472f440f:5669301e
2024-09-06 21:56:48I had the pleasure of sitting back down with Will Reeves, Founder and CEO of Fold, on TFTC last week to discuss Fold's journey from a startup to (soon to be) a publicly listed company. I particularly liked this conversation because it was a great lens into the grit it takes to run a successful bitcoin company. https://fountain.fm/episode/1FrspxmpK5bsoReGx73n Building a successful company is extremely hard in its own right. Building a successful bitcoin company is significantly harder considering the fact that you're building a company in parallel with a nascent and volatile monetary asset that is monetizing in real time. Bitcoin adoption comes in waves. People flood in when the price is ripping and fade out when the price corrects and goes into a multi-year bear market before the tide comes back in. This means that your potential user base is expanding and contracting more than it would be in other industries. As a company you need to be able to absorb the incoming waves of new adopters and then capture and retain the users who stick around for the bear market. To do this correctly, a founder and their team needs to thread many needles. First, can you assemble a team that can actually build something? Second, can you bring a product to market that people actually use because it provides value to them? Third, can you stick out against the crowd? So on and so forth. One of the most important aspects of building a bitcoin company during bitcoin's monetization phase is timing. There are many great ideas that people have in terms of companies, products and tools that can built using bitcoin. There are sci-fi futures that can be built today on bitcoin if people really wanted to. The problem that arises is that adoption and understanding of bitcoin are at a point where, even though a functional product could be brought to market, it won't be adopted by a large number of people because there 1.) aren't enough people who would understand how to use it and 2.) for the people who do understand how to use it and could benefit from it, the universe of people they can interact with using that product is minuscule. Timing is everything. And I think Fold nailed the timing of their product. Allowing people to passively stack sats by offering a product that enables them to go about their daily spending and get sats back instead of cash back rewards is a great first-touch bitcoin experience. Once Fold found their sticky user base and perfected their sats back experience, they began expanding their product offering to provide their users with more bitcoin services. Buy/sell bitcoin in-app, bill pay for sats back, and more. They'll eventually roll out a credit card and additional financial services. Start simple, provide something of value, nail the timing and then expand from there. That seems to be the recipe. For any founders in the space reading this, I highly recommend you listen to the episode. Particularly for the advice Will gives about knowing when to sprint on product and when to lean into growth. Bear markets are for building and bull markets are for casting the widest net possible and capturing as many new users as possible. At Ten31 we are extremely proud to back Fold and a number of other companies in the bitcoin space that understand the intricacies described above. We work with some of the best founders in the world. Founders who know how to eat glass with the best of them. Bitcoin can be a cruel mistress and no one knows that more intimately than the founders building bitcoin companies. --- Final thought... The NFL having a week 1 game in Brazil should get Roger Godell fired. Enjoy your weekend, freaks.
@ 472f440f:5669301e
2024-09-06 21:56:48I had the pleasure of sitting back down with Will Reeves, Founder and CEO of Fold, on TFTC last week to discuss Fold's journey from a startup to (soon to be) a publicly listed company. I particularly liked this conversation because it was a great lens into the grit it takes to run a successful bitcoin company. https://fountain.fm/episode/1FrspxmpK5bsoReGx73n Building a successful company is extremely hard in its own right. Building a successful bitcoin company is significantly harder considering the fact that you're building a company in parallel with a nascent and volatile monetary asset that is monetizing in real time. Bitcoin adoption comes in waves. People flood in when the price is ripping and fade out when the price corrects and goes into a multi-year bear market before the tide comes back in. This means that your potential user base is expanding and contracting more than it would be in other industries. As a company you need to be able to absorb the incoming waves of new adopters and then capture and retain the users who stick around for the bear market. To do this correctly, a founder and their team needs to thread many needles. First, can you assemble a team that can actually build something? Second, can you bring a product to market that people actually use because it provides value to them? Third, can you stick out against the crowd? So on and so forth. One of the most important aspects of building a bitcoin company during bitcoin's monetization phase is timing. There are many great ideas that people have in terms of companies, products and tools that can built using bitcoin. There are sci-fi futures that can be built today on bitcoin if people really wanted to. The problem that arises is that adoption and understanding of bitcoin are at a point where, even though a functional product could be brought to market, it won't be adopted by a large number of people because there 1.) aren't enough people who would understand how to use it and 2.) for the people who do understand how to use it and could benefit from it, the universe of people they can interact with using that product is minuscule. Timing is everything. And I think Fold nailed the timing of their product. Allowing people to passively stack sats by offering a product that enables them to go about their daily spending and get sats back instead of cash back rewards is a great first-touch bitcoin experience. Once Fold found their sticky user base and perfected their sats back experience, they began expanding their product offering to provide their users with more bitcoin services. Buy/sell bitcoin in-app, bill pay for sats back, and more. They'll eventually roll out a credit card and additional financial services. Start simple, provide something of value, nail the timing and then expand from there. That seems to be the recipe. For any founders in the space reading this, I highly recommend you listen to the episode. Particularly for the advice Will gives about knowing when to sprint on product and when to lean into growth. Bear markets are for building and bull markets are for casting the widest net possible and capturing as many new users as possible. At Ten31 we are extremely proud to back Fold and a number of other companies in the bitcoin space that understand the intricacies described above. We work with some of the best founders in the world. Founders who know how to eat glass with the best of them. Bitcoin can be a cruel mistress and no one knows that more intimately than the founders building bitcoin companies. --- Final thought... The NFL having a week 1 game in Brazil should get Roger Godell fired. Enjoy your weekend, freaks. @ e83b66a8:b0526c2b
2024-09-06 19:16:04The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud. Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data. There is a different way. NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol. The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms. Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid. Secondly as a user, you don’t have an account, you have a private key which is used to secure your data. Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key. Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays. All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it. Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key. Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content. Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions. Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant. As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models. The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not. NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment. From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed. While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops. If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here: https://primal.net/downloads It will create a private key for you and setup a Bitcoin wallet. Once you have done this you can visit me here: nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already. NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here: nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Or you can see his account like this: https://primal.net/jack Edward Snowden is also on the platform and you can find him here: https://primal.net/Snowden NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation. Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/ Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus or Amethyst for Android: https://nostrapps.com/amethyst The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it. Some of the more interesting projects right now are: https://www.0xchat.com/#/ – Private messaging – think WhatsApp https://zap.stream/ – Video streaming https://fountain.fm/ – Podcasting https://wavlake.com/ – Music streaming https://shopstr.store/ – Online shop https://npub.pro/ – Website creation tool https://nostr.build/ – Media and file storage https://relay.tools/ – Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user – Creator tools Remember, the same keys you created for Primal can be used across the whole ecosystem. If you want to see some of the other apps that have been built on the NOSTR protocol visit: https://nostrapps.com/
@ e83b66a8:b0526c2b
2024-09-06 19:16:04The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud. Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data. There is a different way. NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol. The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms. Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid. Secondly as a user, you don’t have an account, you have a private key which is used to secure your data. Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key. Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays. All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it. Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key. Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content. Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions. Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant. As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models. The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not. NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment. From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed. While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops. If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here: https://primal.net/downloads It will create a private key for you and setup a Bitcoin wallet. Once you have done this you can visit me here: nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already. NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here: nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Or you can see his account like this: https://primal.net/jack Edward Snowden is also on the platform and you can find him here: https://primal.net/Snowden NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation. Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/ Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus or Amethyst for Android: https://nostrapps.com/amethyst The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it. Some of the more interesting projects right now are: https://www.0xchat.com/#/ – Private messaging – think WhatsApp https://zap.stream/ – Video streaming https://fountain.fm/ – Podcasting https://wavlake.com/ – Music streaming https://shopstr.store/ – Online shop https://npub.pro/ – Website creation tool https://nostr.build/ – Media and file storage https://relay.tools/ – Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user – Creator tools Remember, the same keys you created for Primal can be used across the whole ecosystem. If you want to see some of the other apps that have been built on the NOSTR protocol visit: https://nostrapps.com/ @ e968e50b:db2a803a
2024-09-06 19:13:32https://www.youtube.com/watch?v=mn4whdycgxQ I'm about to go play with a swing band from Pittsburg at an Italian music festival and am reviewing my Louis Prima for tonight. I thought I'd share a silly take on Body and Soul by the band's trombone player. The first chorus is ballad style, and then a romp through anything you can imagine (including the Hall of the Mountain King over Body and Soul changes)! Happy weekend! originally posted at https://stacker.news/items/675086
@ e968e50b:db2a803a
2024-09-06 19:13:32https://www.youtube.com/watch?v=mn4whdycgxQ I'm about to go play with a swing band from Pittsburg at an Italian music festival and am reviewing my Louis Prima for tonight. I thought I'd share a silly take on Body and Soul by the band's trombone player. The first chorus is ballad style, and then a romp through anything you can imagine (including the Hall of the Mountain King over Body and Soul changes)! Happy weekend! originally posted at https://stacker.news/items/675086 @ b6dcdddf:dfee5ee7
2024-09-06 17:46:11Hey Frens, This is the Geyser team, coming at you with a spicy idea: a grant for proper journalism. **Issue:** Journalism is broken. Independent journalism is emerging with the work of [The Rage](https://geyser.fund/project/therage/), Whitney Webb and so forth. They deal with issues like privacy, political corruption, economics, ESG, medicine and many other issues that are not discussed by mainstream media. The problem is that not many people know about their work and there are very few grant programs that support their work. **Proposed Solution:** Geyser would like to host a Grant supporting independent journalists using 'community voting mechanism'. See here for how [Community Voting Grants work](https://geyser.fund/grants/thailandbitcoinconference). However, we need more companies to partner up and sponsor this initiative with us. Ideas of more sponsors: - Stacker news: SN has become a great repository of independent/indie journalism. I think they'd fit in great as sponsors for this type of grant. cc: @k00b - [Bitesize media](https://www.bitesizebitcoin.xyz): A new independent media house that wants to focus on the signal Bitcoin brings to our world. They expressed interest already. - Bitcoin Magazine: might be interested as well in this effort. Would love the community's feedback on this idea and propose additional thoughts! originally posted at https://stacker.news/items/674951
@ b6dcdddf:dfee5ee7
2024-09-06 17:46:11Hey Frens, This is the Geyser team, coming at you with a spicy idea: a grant for proper journalism. **Issue:** Journalism is broken. Independent journalism is emerging with the work of [The Rage](https://geyser.fund/project/therage/), Whitney Webb and so forth. They deal with issues like privacy, political corruption, economics, ESG, medicine and many other issues that are not discussed by mainstream media. The problem is that not many people know about their work and there are very few grant programs that support their work. **Proposed Solution:** Geyser would like to host a Grant supporting independent journalists using 'community voting mechanism'. See here for how [Community Voting Grants work](https://geyser.fund/grants/thailandbitcoinconference). However, we need more companies to partner up and sponsor this initiative with us. Ideas of more sponsors: - Stacker news: SN has become a great repository of independent/indie journalism. I think they'd fit in great as sponsors for this type of grant. cc: @k00b - [Bitesize media](https://www.bitesizebitcoin.xyz): A new independent media house that wants to focus on the signal Bitcoin brings to our world. They expressed interest already. - Bitcoin Magazine: might be interested as well in this effort. Would love the community's feedback on this idea and propose additional thoughts! originally posted at https://stacker.news/items/674951 @ ffd375eb:4529ed08
2024-09-06 15:39:31## Chef's notes Watch the video 🇫🇷: https://youtu.be/cYl4Lb0vbyc ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 3 months - 🍽️ Servings: Many ## Ingredients - 1 fennel bulb - 1 large onion - 3 garlic cloves - 1/2 tsp salt per fennel bulb - 1 tbsp turmeric powder per fennel bulb - 1 tbsp oil per fennel bulb - 1 tsp black pepper per fennel bulb - 1 tbsp honey per fennel bulb ## Directions 1. Thinly slice the fennel bulb, onion, and garlic using a mandoline slicer. 2. In a bowl, mix the sliced fennel, onion, garlic, and salt. Let sit for a bit to allow the salt to act on the ingredients. 3. In a separate bowl, mix the turmeric, oil, black pepper, and honey to make a sauce. 4. Combine the fennel, onion, garlic mixture with the turmeric sauce and mix well.
@ ffd375eb:4529ed08
2024-09-06 15:39:31## Chef's notes Watch the video 🇫🇷: https://youtu.be/cYl4Lb0vbyc ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 3 months - 🍽️ Servings: Many ## Ingredients - 1 fennel bulb - 1 large onion - 3 garlic cloves - 1/2 tsp salt per fennel bulb - 1 tbsp turmeric powder per fennel bulb - 1 tbsp oil per fennel bulb - 1 tsp black pepper per fennel bulb - 1 tbsp honey per fennel bulb ## Directions 1. Thinly slice the fennel bulb, onion, and garlic using a mandoline slicer. 2. In a bowl, mix the sliced fennel, onion, garlic, and salt. Let sit for a bit to allow the salt to act on the ingredients. 3. In a separate bowl, mix the turmeric, oil, black pepper, and honey to make a sauce. 4. Combine the fennel, onion, garlic mixture with the turmeric sauce and mix well. @ 3bf0c63f:aefa459d
2024-09-06 12:49:46# Nostr: a quick introduction, attempt #2 Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else. Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services. (Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation). More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46# Nostr: a quick introduction, attempt #2 Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else. Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services. (Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation). More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback". @ 6bae33c8:607272e8
2024-09-06 08:16:48I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be. I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance. What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed. . . . In any event, let’s take a look at the slate: Here are the ownership numbers per [Officefootballpools.com](http://Officefootballpools.com). <img src="https://blossom.primal.net/4143b814092950ec28820e3d86d7608059d8a767b14eb9e2f19821b57ccb0856.png"> The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.) But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win. If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose. You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills. But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is *supposed* to be priced in, of course, but I don’t care.) I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now.
@ 6bae33c8:607272e8
2024-09-06 08:16:48I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be. I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance. What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed. . . . In any event, let’s take a look at the slate: Here are the ownership numbers per [Officefootballpools.com](http://Officefootballpools.com). <img src="https://blossom.primal.net/4143b814092950ec28820e3d86d7608059d8a767b14eb9e2f19821b57ccb0856.png"> The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.) But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win. If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose. You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills. But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is *supposed* to be priced in, of course, but I don’t care.) I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now. @ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes. In any event, it was an okay game, not great, but there were some interesting takeaways. - Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff. - Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask. - Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.) - Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more. - Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot. - Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown. - Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though. - Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game. - Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role. - After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG. - You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night.
@ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes. In any event, it was an okay game, not great, but there were some interesting takeaways. - Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff. - Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask. - Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.) - Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more. - Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot. - Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown. - Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though. - Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game. - Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role. - After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG. - You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night. @ a30cdfee:2d2f97ff
2024-09-06 06:50:05# Orqestra: Converting Business Sales to Bitcoin [Orqestra](https://orqestra.io/) lets businesses automatically convert portions of their sales to bitcoin! What is Orqestra and how can it be useful for businesses? ## Protect Against Inflation with Bitcoin Long-term saving in bitcoin is a good way to hedge against inflation. Not just for individuals, but also for companies. Case in point: MicroStrategy  Bitcoin's strong liquidity also allows quick conversions to fiat if needed, giving companies financial flexibility. ## Converts Portions of Sales to Bitcoin Orqestra simplifies Bitcoin acquisition, targeting small and medium-sized businesses. You can connect your payment providers, and the platform will automatically convert portions of your sales to bitcoin. Start small or go all in, it's up to you!  Orqestra integrates with e.g. PayPal, QuickBooks, Square and Stripe. You can also link e.g. [Clams](https://clams.tech/), a Bitcoin-focused accounting software for automated bookkeeping. You can learn more about Clams here: https://stacker.news/items/552799 ## Custodial, but You Can Withdraw to Your Own Wallet Orqestra states that it partners with industry-leading custodians to store the BTC. You can also withdraw the BTC to your own wallet, or convert it to US dollars. The platform is currently only supporting businesses in the United States. ## KYC Required Orqestra was founded by João Almeida, former CTO and co-founder of a Bitcoin payment infrastructure provider [OpenNode](https://opennode.com/). Orqestra can give tax-ready reports that meet industry standards on demand. To use the platform, businesses need to provide proof of legal existence of the company, proof of address and all beneficiaries with over 25% ownership in the company need to perform KYC. ## Project Links [Website](https://orqestra.io/) [X (Twitter)](https://x.com/orqestraio) originally posted at https://stacker.news/items/674222
@ a30cdfee:2d2f97ff
2024-09-06 06:50:05# Orqestra: Converting Business Sales to Bitcoin [Orqestra](https://orqestra.io/) lets businesses automatically convert portions of their sales to bitcoin! What is Orqestra and how can it be useful for businesses? ## Protect Against Inflation with Bitcoin Long-term saving in bitcoin is a good way to hedge against inflation. Not just for individuals, but also for companies. Case in point: MicroStrategy  Bitcoin's strong liquidity also allows quick conversions to fiat if needed, giving companies financial flexibility. ## Converts Portions of Sales to Bitcoin Orqestra simplifies Bitcoin acquisition, targeting small and medium-sized businesses. You can connect your payment providers, and the platform will automatically convert portions of your sales to bitcoin. Start small or go all in, it's up to you!  Orqestra integrates with e.g. PayPal, QuickBooks, Square and Stripe. You can also link e.g. [Clams](https://clams.tech/), a Bitcoin-focused accounting software for automated bookkeeping. You can learn more about Clams here: https://stacker.news/items/552799 ## Custodial, but You Can Withdraw to Your Own Wallet Orqestra states that it partners with industry-leading custodians to store the BTC. You can also withdraw the BTC to your own wallet, or convert it to US dollars. The platform is currently only supporting businesses in the United States. ## KYC Required Orqestra was founded by João Almeida, former CTO and co-founder of a Bitcoin payment infrastructure provider [OpenNode](https://opennode.com/). Orqestra can give tax-ready reports that meet industry standards on demand. To use the platform, businesses need to provide proof of legal existence of the company, proof of address and all beneficiaries with over 25% ownership in the company need to perform KYC. ## Project Links [Website](https://orqestra.io/) [X (Twitter)](https://x.com/orqestraio) originally posted at https://stacker.news/items/674222 @ 84b0c46a:417782f5
2024-09-06 00:26:32- 1:nan: - **2** - 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p) - 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw - 2 - 2 - 3 - 3 - 2 - 1 |1|2| |--|--| |test|:nan:| --- ### :nan: **:nan:** 1. 1 2. 2 - tet - tes 3. 3 1. 1 2. 2 > t >> te >>> test
@ 84b0c46a:417782f5
2024-09-06 00:26:32- 1:nan: - **2** - 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p) - 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw - 2 - 2 - 3 - 3 - 2 - 1 |1|2| |--|--| |test|:nan:| --- ### :nan: **:nan:** 1. 1 2. 2 - tet - tes 3. 3 1. 1 2. 2 > t >> te >>> test @ c7eadcf0:7821e562
2024-09-06 00:10:23Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck. Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis. Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin. This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite? Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out.
@ c7eadcf0:7821e562
2024-09-06 00:10:23Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck. Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis. Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin. This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite? Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out. @ acc925af:db9fb0bb
2024-09-05 20:26:50While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good **Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:** # Prerequisites: 1. Twitter Developer Account 2. Nostr Wallet with NWC support (e.g., Alby, Nostrify) 3. Twitter API credentials (API key, API secret key, Access token, Access token secret) 4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library) ### Step 1: Set up Twitter API credentials > Create a Twitter Developer account and obtain API credentials > Install Tweepy using pip: pip install tweepy ### Step 2: Connect Nostr Wallet using NWC > Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify) > Set up the wallet and obtain the NWC credentials (e.g., public key, private key) ### Step 3: Create a Python script > Import Tweepy and nostr-client libraries > Authenticate with Twitter API using Tweepy > Connect to Nostr Wallet using NWC credentials > Define a function to send 21 satoshis for every like > Use Tweepy to stream likes and trigger the payment function `Python` script: ``` import tweepy from nostr_client import Client # Twitter API credentials twitter_api_key = "YOUR_API_KEY" twitter_api_secret_key = "YOUR_API_SECRET_KEY" twitter_access_token = "YOUR_ACCESS_TOKEN" twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET" # Nostr Wallet NWC credentials nwc_public_key = "YOUR_NWC_PUBLIC_KEY" nwc_private_key = "YOUR_NWC_PRIVATE_KEY" # Set up Tweepy auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key) auth.set_access_token(twitter_access_token, twitter_access_token_secret) api = tweepy.API(auth) # Set up Nostr Client nwc_client = Client() nwc_client.connect(nwc_public_key, nwc_private_key) # Define payment function def send_satoshis(): # Create a new Nostr event with 21 satoshis event = nwc_client.create_event(21) # Send the event to the Nostr network nwc_client.send_event(event) # Stream likes and trigger payment function class LikeStream(tweepy.StreamListener): def on_like(self, like): send_satoshis() stream = tweepy.Stream(auth, LikeStream()) stream.filter(track=["likes"]) ``` ##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._ originally posted at https://stacker.news/items/673795
@ acc925af:db9fb0bb
2024-09-05 20:26:50While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good **Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:** # Prerequisites: 1. Twitter Developer Account 2. Nostr Wallet with NWC support (e.g., Alby, Nostrify) 3. Twitter API credentials (API key, API secret key, Access token, Access token secret) 4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library) ### Step 1: Set up Twitter API credentials > Create a Twitter Developer account and obtain API credentials > Install Tweepy using pip: pip install tweepy ### Step 2: Connect Nostr Wallet using NWC > Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify) > Set up the wallet and obtain the NWC credentials (e.g., public key, private key) ### Step 3: Create a Python script > Import Tweepy and nostr-client libraries > Authenticate with Twitter API using Tweepy > Connect to Nostr Wallet using NWC credentials > Define a function to send 21 satoshis for every like > Use Tweepy to stream likes and trigger the payment function `Python` script: ``` import tweepy from nostr_client import Client # Twitter API credentials twitter_api_key = "YOUR_API_KEY" twitter_api_secret_key = "YOUR_API_SECRET_KEY" twitter_access_token = "YOUR_ACCESS_TOKEN" twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET" # Nostr Wallet NWC credentials nwc_public_key = "YOUR_NWC_PUBLIC_KEY" nwc_private_key = "YOUR_NWC_PRIVATE_KEY" # Set up Tweepy auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key) auth.set_access_token(twitter_access_token, twitter_access_token_secret) api = tweepy.API(auth) # Set up Nostr Client nwc_client = Client() nwc_client.connect(nwc_public_key, nwc_private_key) # Define payment function def send_satoshis(): # Create a new Nostr event with 21 satoshis event = nwc_client.create_event(21) # Send the event to the Nostr network nwc_client.send_event(event) # Stream likes and trigger payment function class LikeStream(tweepy.StreamListener): def on_like(self, like): send_satoshis() stream = tweepy.Stream(auth, LikeStream()) stream.filter(track=["likes"]) ``` ##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._ originally posted at https://stacker.news/items/673795 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32## Part 1: Fundamentum Javascripti ### 1.1 Introductionis Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nullam euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. Sed euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. ```javascript console.log("Salve, mundi!"); ``` ### 1.2 Variabiles et Typi Datorum Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Integer convallis, nunc ac blandit tincidunt, ipsum augue tincidunt nunc, vitae tincidunt nisl nunc euismod nunc. ```javascript var numerus = 42; let textus = "Lorem ipsum"; const CONSTANTIA = true; ``` #### 1.2.1 Typi Numerorum Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. ```javascript let integer = 10; let floatinum = 3.14; let scientificum = 2.998e8; ``` #### 1.2.2 Typi Textuum Maecenas tristique, est et tempus semper, est quam pharetra magna, ac consequat metus sapien ut nunc. ```javascript let textusBrevis = 'Carpe diem'; let textusLongus = "Quod erat demonstrandum"; let textusTemplatum = `Cogito, ${textusBrevis.toLowerCase()}, sum`; ``` ### 1.3 Operatores Donec dapibus. Duis at velit eu est congue elementum. In hac habitasse platea dictumst. ```javascript let a = 5; let b = 3; console.log(a + b); // Additio console.log(a - b); // Subtractio console.log(a * b); // Multiplicatio console.log(a / b); // Divisio console.log(a % b); // Modulus console.log(a ** b); // Potentia ``` ### 1.4 Structurae Controli Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis. #### 1.4.1 Conditionales ```javascript let aetas = 20; if (aetas >= 18) { console.log("Adultus es"); } else if (aetas >= 13) { console.log("Adolescens es"); } else { console.log("Puer es"); } ``` #### 1.4.2 Iterationes ```javascript for (let i = 0; i < 5; i++) { console.log(`Iteratio ${i}`); } let j = 0; while (j < 5) { console.log(`Dum iteratio ${j}`); j++; } ``` ### 1.5 Exercitia Parti I 1. Scribe programma quod convertat gradus Celsius in Fahrenheit. 2. Crea algorithmum qui determinat si numerus est par vel impar. 3. Implementa "FizzBuzz" pro numeris 1 ad 100.
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32## Part 1: Fundamentum Javascripti ### 1.1 Introductionis Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nullam euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. Sed euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. ```javascript console.log("Salve, mundi!"); ``` ### 1.2 Variabiles et Typi Datorum Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Integer convallis, nunc ac blandit tincidunt, ipsum augue tincidunt nunc, vitae tincidunt nisl nunc euismod nunc. ```javascript var numerus = 42; let textus = "Lorem ipsum"; const CONSTANTIA = true; ``` #### 1.2.1 Typi Numerorum Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. ```javascript let integer = 10; let floatinum = 3.14; let scientificum = 2.998e8; ``` #### 1.2.2 Typi Textuum Maecenas tristique, est et tempus semper, est quam pharetra magna, ac consequat metus sapien ut nunc. ```javascript let textusBrevis = 'Carpe diem'; let textusLongus = "Quod erat demonstrandum"; let textusTemplatum = `Cogito, ${textusBrevis.toLowerCase()}, sum`; ``` ### 1.3 Operatores Donec dapibus. Duis at velit eu est congue elementum. In hac habitasse platea dictumst. ```javascript let a = 5; let b = 3; console.log(a + b); // Additio console.log(a - b); // Subtractio console.log(a * b); // Multiplicatio console.log(a / b); // Divisio console.log(a % b); // Modulus console.log(a ** b); // Potentia ``` ### 1.4 Structurae Controli Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis. #### 1.4.1 Conditionales ```javascript let aetas = 20; if (aetas >= 18) { console.log("Adultus es"); } else if (aetas >= 13) { console.log("Adolescens es"); } else { console.log("Puer es"); } ``` #### 1.4.2 Iterationes ```javascript for (let i = 0; i < 5; i++) { console.log(`Iteratio ${i}`); } let j = 0; while (j < 5) { console.log(`Dum iteratio ${j}`); j++; } ``` ### 1.5 Exercitia Parti I 1. Scribe programma quod convertat gradus Celsius in Fahrenheit. 2. Crea algorithmum qui determinat si numerus est par vel impar. 3. Implementa "FizzBuzz" pro numeris 1 ad 100. @ 8cb60e21:5f2deaea
2024-09-05 19:48:32## Part 3: Asynchroni et DOM Manipulatio ### 3.1 Promissa et Async/Await Praesent blandit. Nam nulla. Integer pede justo, lacinia eget, tincidunt eget, tempus vel, pede. ```javascript function simulaRequest(data, probabilitasErroris = 0.1) { return new Promise((resolve, reject) => { setTimeout(() => { if (Math.random() < probabilitasErroris) { reject("Error: Aliquid mali accidit"); } else { resolve(`Data accepta: ${data}`); } }, 1000); }); } simulaRequest("Lorem ipsum") .then((responsum) => console.log(responsum)) .catch((error) => console.error(error)); async function fetchData() { try { const responsum = await simulaRequest("Dolor sit amet"); console.log(responsum); } catch (error) { console.error(error); } } fetchData(); ``` ### 3.2 DOM Manipulatio Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis. ```javascript document.addEventListener("DOMContentLoaded", () => { const titulus = document.createElement("h1"); titulus.textContent = "Lorem Ipsum JavaScript"; document.body.appendChild(titulus); const paragraphus = document.createElement("p"); paragraphus.textContent = "Neque porro quisquam est qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit..."; document.body.appendChild(paragraphus); const button = document.createElement("button"); button.textContent = "Fac Clic Me"; button.addEventListener("click", () => { alert("Gratias tibi ago pro clic!"); }); document.body.appendChild(button); }); ``` ### 3.3 Fetch API Maecenas leo odio, condimentum id, luctus nec, molestie sed, justo. Pellentesque viverra pede ac diam. ```javascript async function fetchLoremIpsum() { try { const responsum = await fetch("https://api.lorem.space/image/game?w=150&h=220"); if (!responsum.ok) { throw new Error(`HTTP error! status: ${responsum.status}`); } const data = await responsum.blob(); const imago = document.createElement("img"); imago.src = URL.createObjectURL(data); document.body.appendChild(imago); } catch (error) { console.error("Problema cum fetching imagine:", error); } } fetchLoremIpsum(); ``` ### 3.4 Local Storage Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. ```javascript function salvaPreferentias(clavis, valor) { localStorage.setItem(clavis, JSON.stringify(valor)); } function accipePreferentias(clavis) { const valor = localStorage.getItem(clavis); return valor ? JSON.parse(valor) : null; } const preferentiae = { thema: "clarus", lingua: "Latina", notificationes: true }; salvaPreferentias("userPrefs", preferentiae); const salvataePreferentiae = accipePreferentias("userPrefs"); console.log(salvataePreferentiae); ``` ### 3.5 Exercitia Parti III 1. Crea paginam web simplicem quae utitur fetch API ad exhibendum datos ex API publica. 2. Implementa functionalitatem "drag and drop" utens DOM API. 3. Construe applicationem "todo list" quae persistit datos in local storage. ## Conclusio Vivamus vestibulum sagittis sapien. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Etiam vel augue. Vestibulum rutrum rutrum neque. Aenean auctor gravida sem. Praesent id massa id nisl venenatis lacinia. Aenean sit amet justo. Morbi ut odio. Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Proin interdum mauris non ligula pellentesque ultrices. Phasellus id sapien in sapien iaculis congue. Vivamus metus arcu, adipiscing molestie, hendrerit at, vulputate vitae, nisl. Aenean lectus. Pellentesque eget nunc. Donec quis orci eget orci vehicula condimentum. Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. Maecenas pulvinar lobortis est. Phasellus sit amet erat. Nulla tempus. Vivamus in felis eu sapien cursus vestibulum. Proin eu mi. Nulla ac enim. In tempor, turpis nec euismod scelerisque, quam turpis adipiscing lorem, vitae mattis nibh ligula nec sem. Duis aliquam convallis nunc. Proin at turpis a pede posuere nonummy. Integer non velit. Donec diam neque, vestibulum eget, vulputate ut, ultrices vel, augue. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec pharetra, magna vestibulum aliquet ultrices, erat tortor sollicitudin mi, sit amet lobortis sapien sapien non mi. Integer ac neque. Duis bibendum. Morbi non quam nec dui luctus rutrum. Nulla tellus. In sagittis dui vel nisl. Duis ac nibh. Fusce lacus purus, aliquet at, feugiat non, pretium quis, lectus. Suspendisse potenti. In eleifend quam a odio. In hac habitasse platea dictumst. Maecenas ut massa quis augue luctus tincidunt. Nulla mollis molestie lorem. Quisque ut erat. Curabitur gravida nisi at nibh. In hac habitasse platea dictumst. Aliquam augue quam, sollicitudin vitae, consectetuer eget, rutrum at, lorem. Integer tincidunt ante vel ipsum. Praesent blandit lacinia erat. Vestibulum sed magna at nunc commodo placerat. Praesent blandit. Nam nulla.
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32## Part 3: Asynchroni et DOM Manipulatio ### 3.1 Promissa et Async/Await Praesent blandit. Nam nulla. Integer pede justo, lacinia eget, tincidunt eget, tempus vel, pede. ```javascript function simulaRequest(data, probabilitasErroris = 0.1) { return new Promise((resolve, reject) => { setTimeout(() => { if (Math.random() < probabilitasErroris) { reject("Error: Aliquid mali accidit"); } else { resolve(`Data accepta: ${data}`); } }, 1000); }); } simulaRequest("Lorem ipsum") .then((responsum) => console.log(responsum)) .catch((error) => console.error(error)); async function fetchData() { try { const responsum = await simulaRequest("Dolor sit amet"); console.log(responsum); } catch (error) { console.error(error); } } fetchData(); ``` ### 3.2 DOM Manipulatio Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis. ```javascript document.addEventListener("DOMContentLoaded", () => { const titulus = document.createElement("h1"); titulus.textContent = "Lorem Ipsum JavaScript"; document.body.appendChild(titulus); const paragraphus = document.createElement("p"); paragraphus.textContent = "Neque porro quisquam est qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit..."; document.body.appendChild(paragraphus); const button = document.createElement("button"); button.textContent = "Fac Clic Me"; button.addEventListener("click", () => { alert("Gratias tibi ago pro clic!"); }); document.body.appendChild(button); }); ``` ### 3.3 Fetch API Maecenas leo odio, condimentum id, luctus nec, molestie sed, justo. Pellentesque viverra pede ac diam. ```javascript async function fetchLoremIpsum() { try { const responsum = await fetch("https://api.lorem.space/image/game?w=150&h=220"); if (!responsum.ok) { throw new Error(`HTTP error! status: ${responsum.status}`); } const data = await responsum.blob(); const imago = document.createElement("img"); imago.src = URL.createObjectURL(data); document.body.appendChild(imago); } catch (error) { console.error("Problema cum fetching imagine:", error); } } fetchLoremIpsum(); ``` ### 3.4 Local Storage Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. ```javascript function salvaPreferentias(clavis, valor) { localStorage.setItem(clavis, JSON.stringify(valor)); } function accipePreferentias(clavis) { const valor = localStorage.getItem(clavis); return valor ? JSON.parse(valor) : null; } const preferentiae = { thema: "clarus", lingua: "Latina", notificationes: true }; salvaPreferentias("userPrefs", preferentiae); const salvataePreferentiae = accipePreferentias("userPrefs"); console.log(salvataePreferentiae); ``` ### 3.5 Exercitia Parti III 1. Crea paginam web simplicem quae utitur fetch API ad exhibendum datos ex API publica. 2. Implementa functionalitatem "drag and drop" utens DOM API. 3. Construe applicationem "todo list" quae persistit datos in local storage. ## Conclusio Vivamus vestibulum sagittis sapien. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Etiam vel augue. Vestibulum rutrum rutrum neque. Aenean auctor gravida sem. Praesent id massa id nisl venenatis lacinia. Aenean sit amet justo. Morbi ut odio. Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Proin interdum mauris non ligula pellentesque ultrices. Phasellus id sapien in sapien iaculis congue. Vivamus metus arcu, adipiscing molestie, hendrerit at, vulputate vitae, nisl. Aenean lectus. Pellentesque eget nunc. Donec quis orci eget orci vehicula condimentum. Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. Maecenas pulvinar lobortis est. Phasellus sit amet erat. Nulla tempus. Vivamus in felis eu sapien cursus vestibulum. Proin eu mi. Nulla ac enim. In tempor, turpis nec euismod scelerisque, quam turpis adipiscing lorem, vitae mattis nibh ligula nec sem. Duis aliquam convallis nunc. Proin at turpis a pede posuere nonummy. Integer non velit. Donec diam neque, vestibulum eget, vulputate ut, ultrices vel, augue. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec pharetra, magna vestibulum aliquet ultrices, erat tortor sollicitudin mi, sit amet lobortis sapien sapien non mi. Integer ac neque. Duis bibendum. Morbi non quam nec dui luctus rutrum. Nulla tellus. In sagittis dui vel nisl. Duis ac nibh. Fusce lacus purus, aliquet at, feugiat non, pretium quis, lectus. Suspendisse potenti. In eleifend quam a odio. In hac habitasse platea dictumst. Maecenas ut massa quis augue luctus tincidunt. Nulla mollis molestie lorem. Quisque ut erat. Curabitur gravida nisi at nibh. In hac habitasse platea dictumst. Aliquam augue quam, sollicitudin vitae, consectetuer eget, rutrum at, lorem. Integer tincidunt ante vel ipsum. Praesent blandit lacinia erat. Vestibulum sed magna at nunc commodo placerat. Praesent blandit. Nam nulla. @ 8cb60e21:5f2deaea
2024-09-05 19:48:32## Part 2: Functiones et Objecta ### 2.1 Functiones Fusce posuere felis sed lacus. Morbi sem mauris, laoreet ut, rhoncus aliquet, pulvinar sed, nisl. ```javascript function salutatio(nomen) { return `Salve, ${nomen}!`; } console.log(salutatio("Cicero")); const valedictio = (nomen) => { console.log(`Vale, ${nomen}!`); }; valedictio("Seneca"); ``` #### 2.1.1 Parametri Default et Rest Nunc purus. Phasellus in felis. Donec semper sapien a libero. ```javascript function congregatio(primus, secundus = "mundi", ...ceteri) { console.log(`${primus} ${secundus}`); console.log(`Ceteri: ${ceteri.join(", ")}`); } congregatio("Salve"); congregatio("Lorem", "ipsum"); congregatio("Veni", "vidi", "vici", "et", "cetera"); ``` ### 2.2 Objecta Nam congue, risus semper porta volutpat, quam pede lobortis ligula, sit amet eleifend pede libero quis orci. ```javascript const persona = { nomen: "Iulius", cognomen: "Caesar", aetas: 55, salutatio: function() { return `Salve, ${this.nomen} ${this.cognomen}!`; } }; console.log(persona.salutatio()); ``` #### 2.2.1 Methodi Object Nullam porttitor lacus at turpis. Donec posuere metus vitae ipsum. Aliquam non mauris. ```javascript const claves = Object.keys(persona); console.log(claves); const valores = Object.values(persona); console.log(valores); const paria = Object.entries(persona); console.log(paria); ``` ### 2.3 Arrays Morbi porttitor lorem id ligula. Suspendisse ornare consequat lectus. In est risus, auctor sed, tristique in, tempus sit amet, sem. ```javascript const fructus = ["malum", "pirum", "uva", "cerasum"]; fructus.forEach((fructus) => { console.log(fructus); }); const longiFructus = fructus.filter((fructus) => fructus.length > 4); console.log(longiFructus); const maiusculaFructus = fructus.map((fructus) => fructus.toUpperCase()); console.log(maiusculaFructus); ``` ### 2.4 Exercitia Parti II 1. Crea functionem quae calculat factorialem numeri. 2. Implementa methodum quae invenit maximum valorem in array. 3. Scribe programma quod ordinat objecta in array secundum proprietatem specificam.
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32## Part 2: Functiones et Objecta ### 2.1 Functiones Fusce posuere felis sed lacus. Morbi sem mauris, laoreet ut, rhoncus aliquet, pulvinar sed, nisl. ```javascript function salutatio(nomen) { return `Salve, ${nomen}!`; } console.log(salutatio("Cicero")); const valedictio = (nomen) => { console.log(`Vale, ${nomen}!`); }; valedictio("Seneca"); ``` #### 2.1.1 Parametri Default et Rest Nunc purus. Phasellus in felis. Donec semper sapien a libero. ```javascript function congregatio(primus, secundus = "mundi", ...ceteri) { console.log(`${primus} ${secundus}`); console.log(`Ceteri: ${ceteri.join(", ")}`); } congregatio("Salve"); congregatio("Lorem", "ipsum"); congregatio("Veni", "vidi", "vici", "et", "cetera"); ``` ### 2.2 Objecta Nam congue, risus semper porta volutpat, quam pede lobortis ligula, sit amet eleifend pede libero quis orci. ```javascript const persona = { nomen: "Iulius", cognomen: "Caesar", aetas: 55, salutatio: function() { return `Salve, ${this.nomen} ${this.cognomen}!`; } }; console.log(persona.salutatio()); ``` #### 2.2.1 Methodi Object Nullam porttitor lacus at turpis. Donec posuere metus vitae ipsum. Aliquam non mauris. ```javascript const claves = Object.keys(persona); console.log(claves); const valores = Object.values(persona); console.log(valores); const paria = Object.entries(persona); console.log(paria); ``` ### 2.3 Arrays Morbi porttitor lorem id ligula. Suspendisse ornare consequat lectus. In est risus, auctor sed, tristique in, tempus sit amet, sem. ```javascript const fructus = ["malum", "pirum", "uva", "cerasum"]; fructus.forEach((fructus) => { console.log(fructus); }); const longiFructus = fructus.filter((fructus) => fructus.length > 4); console.log(longiFructus); const maiusculaFructus = fructus.map((fructus) => fructus.toUpperCase()); console.log(maiusculaFructus); ``` ### 2.4 Exercitia Parti II 1. Crea functionem quae calculat factorialem numeri. 2. Implementa methodum quae invenit maximum valorem in array. 3. Scribe programma quod ordinat objecta in array secundum proprietatem specificam. @ e8b86bc1:3503c58f
2024-09-05 19:38:11Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> Another method Freewallet uses to rob customers: inactivity fees. They charge you for not using the app, wiping out your assets slowly. Avoid Freewallet! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
@ e8b86bc1:3503c58f
2024-09-05 19:38:11Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> Another method Freewallet uses to rob customers: inactivity fees. They charge you for not using the app, wiping out your assets slowly. Avoid Freewallet! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app) @ e968e50b:db2a803a
2024-09-05 19:33:33ATTENTION PARENTS! I have revamped my LNBITS [bitcoin piggy bank](http://bitcoinpiggybank.vercel.app) so you don't need to deploy it yourself. Check it out at http://bitcoinpiggybank.vercel.app. All you need now is a LNBITS wallet. I've deployed a website that you can just log into with that and nothing else. I'm thinking about actually renting out my own domain for this one if people find it useful. https://www.youtube.com/watch?v=X-MNqJiLCM4 Teach your kids about sound money while they're actually stacking sats and using a fun interface. originally posted at https://stacker.news/items/673739
@ e968e50b:db2a803a
2024-09-05 19:33:33ATTENTION PARENTS! I have revamped my LNBITS [bitcoin piggy bank](http://bitcoinpiggybank.vercel.app) so you don't need to deploy it yourself. Check it out at http://bitcoinpiggybank.vercel.app. All you need now is a LNBITS wallet. I've deployed a website that you can just log into with that and nothing else. I'm thinking about actually renting out my own domain for this one if people find it useful. https://www.youtube.com/watch?v=X-MNqJiLCM4 Teach your kids about sound money while they're actually stacking sats and using a fun interface. originally posted at https://stacker.news/items/673739 @ 9977c3ad:43a20d63
2024-09-05 11:21:09## Details - 🍽️ Servings: 2 ## Ingredients - 1 cup Jasmine rice - 1 Tbsp. lavender flowers, crushed with mortar and pestle - 1/4 cup apple cider vinegar - 2 Tbsp. fine cane sugar - 2 Tbsp. honey - 1 sprig rosemary - 1/4 tsp angostura bitters - 1/2 cup blackberries - 1/2 cup blueberries - 4 cups trimmed and quartered shiitake mushrooms - 1 tsp fresh coriander crushed - 1/4 tsp fresh cumin ground - 1/2 tsp red pepper flakes - 3 sprigs of thyme - 2 Tbsp. olive oil - 1 tsp soy sauce - 1 cup creamy coconut milk ## Directions 1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes. 2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside. 3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
@ 9977c3ad:43a20d63
2024-09-05 11:21:09## Details - 🍽️ Servings: 2 ## Ingredients - 1 cup Jasmine rice - 1 Tbsp. lavender flowers, crushed with mortar and pestle - 1/4 cup apple cider vinegar - 2 Tbsp. fine cane sugar - 2 Tbsp. honey - 1 sprig rosemary - 1/4 tsp angostura bitters - 1/2 cup blackberries - 1/2 cup blueberries - 4 cups trimmed and quartered shiitake mushrooms - 1 tsp fresh coriander crushed - 1/4 tsp fresh cumin ground - 1/2 tsp red pepper flakes - 3 sprigs of thyme - 2 Tbsp. olive oil - 1 tsp soy sauce - 1 cup creamy coconut milk ## Directions 1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes. 2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside. 3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens. @ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam. However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash. Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin. BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now. https://strike.me/blog/bolt12-offers/ As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented. Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology". The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack. This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential. Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust. Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin. --- Final thought... Vibes are high.
@ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam. However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash. Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin. BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now. https://strike.me/blog/bolt12-offers/ As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented. Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology". The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack. This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential. Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust. Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin. --- Final thought... Vibes are high. @ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17When I have stale bread, I often use it to make a bread salad. The base is croutons of stale bread and then there are no limits to your imagination. In this salad there was also - Onions stewed in balsamic vinegar - Spring onions (raw) - Cherry tomatoes - Eggplants and sweetcorn (fried, lukewarm) - Pine nuts - Finely sliced cheese - Basil https://image.nostr.build/ce0c7490f2adbd2aa4ccdfe80203a15dbb10686859a3256a0147d5f423478fd0.jpg https://image.nostr.build/f930e0984ec9603b84c7a7868a97486140ee44590590102f7e460bfbfd3d70be.jpg originally posted at https://stacker.news/items/672404
@ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17When I have stale bread, I often use it to make a bread salad. The base is croutons of stale bread and then there are no limits to your imagination. In this salad there was also - Onions stewed in balsamic vinegar - Spring onions (raw) - Cherry tomatoes - Eggplants and sweetcorn (fried, lukewarm) - Pine nuts - Finely sliced cheese - Basil https://image.nostr.build/ce0c7490f2adbd2aa4ccdfe80203a15dbb10686859a3256a0147d5f423478fd0.jpg https://image.nostr.build/f930e0984ec9603b84c7a7868a97486140ee44590590102f7e460bfbfd3d70be.jpg originally posted at https://stacker.news/items/672404 @ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ ## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks** ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา.. เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่ ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน.. ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ ## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน** ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core Blockstream สนับสนุน "Small Blocks" เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้ ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา ## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน** ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB** แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น.. ## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว** ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement" ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ ## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash** ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017 SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา.. อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"** ## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ** ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้ Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้ Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย ## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright** ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)** การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔 ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer" การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย ## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี** หลังจากการ Hard Fork ของ Bitcoin Cash Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value) การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin ## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ** ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป # **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง** ## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล** Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า ### **SegWit (Segregated Witness)** เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network ### **Taproot** เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ ## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่** ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่ ### **Bitcoin XT (2015)** เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ ### **Bitcoin Classic (2016)** เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน ### **Bitcoin Unlimited (2016)** เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง ### **Bitcoin Cash (BCH) (2017)** เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง ### **Bitcoin SV (BSV) (2018)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin ### **Bitcoin ABC (2020)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง ## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?** หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"** Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น.. ### **การไม่ยอมเพิ่ม Blocksize Limit** Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream ### **การเซ็นเซอร์ข้อมูล** Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ ### **การต่อต้านนวัตกรรม** Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น ### **การควบคุมโดยกลุ่มเล็กๆ** Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto ## **บทสรุป:** การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด **"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่.. ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย.. เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง.. — Jakk Goodday
@ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ ## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks** ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา.. เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่ ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน.. ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ ## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน** ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core Blockstream สนับสนุน "Small Blocks" เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้ ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา ## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน** ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB** แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น.. ## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว** ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement" ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ ## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash** ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017 SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา.. อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"** ## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ** ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้ Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้ Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย ## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright** ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)** การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔 ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer" การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย ## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี** หลังจากการ Hard Fork ของ Bitcoin Cash Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value) การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin ## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ** ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป # **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง** ## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล** Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า ### **SegWit (Segregated Witness)** เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network ### **Taproot** เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ ## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่** ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่ ### **Bitcoin XT (2015)** เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ ### **Bitcoin Classic (2016)** เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน ### **Bitcoin Unlimited (2016)** เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง ### **Bitcoin Cash (BCH) (2017)** เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง ### **Bitcoin SV (BSV) (2018)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin ### **Bitcoin ABC (2020)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง ## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?** หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"** Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น.. ### **การไม่ยอมเพิ่ม Blocksize Limit** Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream ### **การเซ็นเซอร์ข้อมูล** Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ ### **การต่อต้านนวัตกรรม** Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น ### **การควบคุมโดยกลุ่มเล็กๆ** Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto ## **บทสรุป:** การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด **"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่.. ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย.. เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง.. — Jakk Goodday @ 1739d937:3e3136ef
2024-09-04 07:23:12This is the sixth in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr. ## Previous Updates - [June 28th 2024](https://habla.news/u/jeffg.fyi/1719562889267) - [July 6th 2024](https://habla.news/u/jeffg.fyi/1720256910765) - [July 12th 2024](https://habla.news/u/jeffg.fyi/1720778880538) - [July 19th 2024](https://habla.news/u/jeffg.fyi/1721419437737) - [August 16th 2024](https://habla.news/u/jeffg.fyi/1723802138254) ## Progress this week Sorry about the very late update this week. Catching up on everything after a week in Riga for Nostriga and Baltic Honeybadger took a bunch of time, every other moment was spent coding. 👨💻 The response at Nostriga to NIP-104 and my two talks on the subject were overwhelmingly positive. It was very helpful to spend time with other devs going through the spec in detail. We found a few minor improvements and clarifications but no major issues surfaced. Thanks to nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49, nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj, and nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr in particular for the lengthly interrogations and nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 for the introductions. Last week, I started work on a reference implementation of the spec. It's still early but going quickly. My PR adding support for secp256k1 was also merged into the hpke-rs library yesterday. That's one more step in the right direction towards having secp256k1 ciphersuite support. ### The NIP If you haven't already, check out my talk; [The Past and Future of DMs and Group messaging on Nostr](https://www.youtube.com/watch?v=PWKd9aoZ-Cg). This was a basic overview of the various DM and group messaging schemes and talks a little about the progress on NIP-104. I _believe_ there is a recording of the technical talk on the spec but it hasn't yet been released. I'll link it up when it is. At this point I've been discouraging anyone from trying to implement the NIP quite yet. As I mentioned above there are a few adjustments that need to be made and a few open questions that I'm working on answering with my implementation (which I'm very happy to have contributors on). My plan at the moment is to do this first implementation with the default ciphersuite that MLS already supports while I continue to work on the dependencies to get secp256k1 support across the board. ### The Implementation I've started on a cross-platform native client that will run on Mac, Windows, Linux, iOS, and Android. Think of it as Signal or Telegram but over Nostr. I hope that this will not only become the reference implementation for other client developers but also will be one of the most secure and privacy focused clients in the Nostr ecosystem. Building it has already been helpful in clarifying some of the more complex implementation details in the NIP. It's still early but I'll have more to share on this in the coming weeks. ### HPKE-RS My [PR](https://github.com/franziskuskiefer/hpke-rs/pull/66) to add support for secp256k1 is merged! ## Onward and Upward Thanks again to everyone for the support and feedback on this stuff at Nostriga. It was hugely motivating to hear the kind words, have you introducing me to people that could help, and spending time giving me feedback! This community is the best. 🫂
@ 1739d937:3e3136ef
2024-09-04 07:23:12This is the sixth in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr. ## Previous Updates - [June 28th 2024](https://habla.news/u/jeffg.fyi/1719562889267) - [July 6th 2024](https://habla.news/u/jeffg.fyi/1720256910765) - [July 12th 2024](https://habla.news/u/jeffg.fyi/1720778880538) - [July 19th 2024](https://habla.news/u/jeffg.fyi/1721419437737) - [August 16th 2024](https://habla.news/u/jeffg.fyi/1723802138254) ## Progress this week Sorry about the very late update this week. Catching up on everything after a week in Riga for Nostriga and Baltic Honeybadger took a bunch of time, every other moment was spent coding. 👨💻 The response at Nostriga to NIP-104 and my two talks on the subject were overwhelmingly positive. It was very helpful to spend time with other devs going through the spec in detail. We found a few minor improvements and clarifications but no major issues surfaced. Thanks to nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49, nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj, and nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr in particular for the lengthly interrogations and nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 for the introductions. Last week, I started work on a reference implementation of the spec. It's still early but going quickly. My PR adding support for secp256k1 was also merged into the hpke-rs library yesterday. That's one more step in the right direction towards having secp256k1 ciphersuite support. ### The NIP If you haven't already, check out my talk; [The Past and Future of DMs and Group messaging on Nostr](https://www.youtube.com/watch?v=PWKd9aoZ-Cg). This was a basic overview of the various DM and group messaging schemes and talks a little about the progress on NIP-104. I _believe_ there is a recording of the technical talk on the spec but it hasn't yet been released. I'll link it up when it is. At this point I've been discouraging anyone from trying to implement the NIP quite yet. As I mentioned above there are a few adjustments that need to be made and a few open questions that I'm working on answering with my implementation (which I'm very happy to have contributors on). My plan at the moment is to do this first implementation with the default ciphersuite that MLS already supports while I continue to work on the dependencies to get secp256k1 support across the board. ### The Implementation I've started on a cross-platform native client that will run on Mac, Windows, Linux, iOS, and Android. Think of it as Signal or Telegram but over Nostr. I hope that this will not only become the reference implementation for other client developers but also will be one of the most secure and privacy focused clients in the Nostr ecosystem. Building it has already been helpful in clarifying some of the more complex implementation details in the NIP. It's still early but I'll have more to share on this in the coming weeks. ### HPKE-RS My [PR](https://github.com/franziskuskiefer/hpke-rs/pull/66) to add support for secp256k1 is merged! ## Onward and Upward Thanks again to everyone for the support and feedback on this stuff at Nostriga. It was hugely motivating to hear the kind words, have you introducing me to people that could help, and spending time giving me feedback! This community is the best. 🫂 @ e0e92e54:d630dfaa
2024-09-04 04:13:19_This is a copy of the email received from newsletter@Rumble.com_  # Free Speech Under Attack -- A Note from the CEO of Rumble Dear Rumble Users, I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble. Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court. World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them. There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it. Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people. The people keep us alive and keep us going. If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression. We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil". Sincerely, Chris Pavlovski Chairman and CEO of Rumble  444 Gulf of Mexico Dr. Longboat Key, FL 34228, USA.
@ e0e92e54:d630dfaa
2024-09-04 04:13:19_This is a copy of the email received from newsletter@Rumble.com_  # Free Speech Under Attack -- A Note from the CEO of Rumble Dear Rumble Users, I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble. Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court. World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them. There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it. Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people. The people keep us alive and keep us going. If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression. We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil". Sincerely, Chris Pavlovski Chairman and CEO of Rumble  444 Gulf of Mexico Dr. Longboat Key, FL 34228, USA. @ 862fda7e:02a8268b
2024-09-04 01:45:14It is true that I often dream about James Corbett from CorbettReport.com. Somehow James is always finding his way to my mind. James Corbett intimidates me, I feel like he would heavily dislike me because I am not serious enough. Anytime I see James Corbett smile or laugh it feels like I'm watching an alien try to be human. I wish James the best with his family life and career, but he looks like he is always one second away from either crying hyterically or beating a defensless Japanese man sensless. I am indreasibly grateful for all the hard work he's put out all these years, he's a great person in the truth circle. However, he's like a caracatiure in my head. Anytime he whips out his guitar, I start to cringe. I just know what's about to come will only be the truth about how bad his singing is. But yet, I still love when he plays his guitar. It's awful in a great way, it brings genuine joy to me. Did you know he has a band? He has one song called "Screw Youtube", and in his music video he was sitting on this tall wooden fence and he was wearing these SHORTS WITH SANDALS and he was SWINGING HIS LEGS. I'm sorry, but I expect James to wear white caykies at all times. It felt so gross to see his legs in that state. But then again, here I am getting genuine joy out of seeing that atrosity. I remember one time watching a James Corbett episode where he has the James Evan Pilatto from MediaMonarchy.com on, and the other James always looks like he's super fucking cracked up. Like he has a ton of energy. Well anyways, one time the other James was his usual self, looking super cracked out excited, talking about the reppies (reptilians) and James Corbett looked so tight lipped, red faced, like he was about to burst out crying. It was so funny to see the two polar opposites, the other James totally oblivious that real James looked like he was about to cry for seemingly no reason. I know this sounds mean of me to say, but I really appreciate these guys for all they do. I just think this is funny. Anyways, I have a lot of dreams with James Corbett in them. I think it's because he's a teacher and my vagina has a fondness for male teachers. Sadly, none of my good looking male teachers never slept with me. That being said, I think James is good looking for possibly being an English teacher in Japan. I would let him teach me about the reptilians and Klaus Schwab, just let the teaching session see where it goes. Would his gap teeth feel good over my clitty? I dunno. Okay but here is the most memorable and hilarious dream I had invovling James Corbett. You know how he makes content very often? One day he got extremely fed up with making videos. At the time I think it's because he mentioned in a video how he was annoyed that people kept saying him and Andrew Caufman. So one day he just flipped out, got extremely angry, made one last video saying how he was never coming back and how he's leaving his wife and kids. He deletes everything and is unheard of for months. A few months pass and he uploads a new video. The new video is James obsessively showing and talking about his highly advanced chicken coop he made in Minecraft. He had hundreds of chickens lined up maybe 80 feet in the air, each chicken had a 1x1 square to fit in. Below the chicken was a long tube in which their egg would drop down, and a catcher at the base of the ground. James was fantically showing this contraption, rocking back and forth, had a headset on. He looked awful too. I actually emailed James Corbett about this dream, but he never responded. Speaking of James Corbett, why do so many people look like him? I feel like they make middle aged bald, bearded men in a DUMB and just release them into the wild, but give them balding genetics so they know how to keep track of them. Like they probably made James Corbett and Andrew Caufman from the same test tube. They fucked up with them, at least like give one of them hair or good eyesight.
@ 862fda7e:02a8268b
2024-09-04 01:45:14It is true that I often dream about James Corbett from CorbettReport.com. Somehow James is always finding his way to my mind. James Corbett intimidates me, I feel like he would heavily dislike me because I am not serious enough. Anytime I see James Corbett smile or laugh it feels like I'm watching an alien try to be human. I wish James the best with his family life and career, but he looks like he is always one second away from either crying hyterically or beating a defensless Japanese man sensless. I am indreasibly grateful for all the hard work he's put out all these years, he's a great person in the truth circle. However, he's like a caracatiure in my head. Anytime he whips out his guitar, I start to cringe. I just know what's about to come will only be the truth about how bad his singing is. But yet, I still love when he plays his guitar. It's awful in a great way, it brings genuine joy to me. Did you know he has a band? He has one song called "Screw Youtube", and in his music video he was sitting on this tall wooden fence and he was wearing these SHORTS WITH SANDALS and he was SWINGING HIS LEGS. I'm sorry, but I expect James to wear white caykies at all times. It felt so gross to see his legs in that state. But then again, here I am getting genuine joy out of seeing that atrosity. I remember one time watching a James Corbett episode where he has the James Evan Pilatto from MediaMonarchy.com on, and the other James always looks like he's super fucking cracked up. Like he has a ton of energy. Well anyways, one time the other James was his usual self, looking super cracked out excited, talking about the reppies (reptilians) and James Corbett looked so tight lipped, red faced, like he was about to burst out crying. It was so funny to see the two polar opposites, the other James totally oblivious that real James looked like he was about to cry for seemingly no reason. I know this sounds mean of me to say, but I really appreciate these guys for all they do. I just think this is funny. Anyways, I have a lot of dreams with James Corbett in them. I think it's because he's a teacher and my vagina has a fondness for male teachers. Sadly, none of my good looking male teachers never slept with me. That being said, I think James is good looking for possibly being an English teacher in Japan. I would let him teach me about the reptilians and Klaus Schwab, just let the teaching session see where it goes. Would his gap teeth feel good over my clitty? I dunno. Okay but here is the most memorable and hilarious dream I had invovling James Corbett. You know how he makes content very often? One day he got extremely fed up with making videos. At the time I think it's because he mentioned in a video how he was annoyed that people kept saying him and Andrew Caufman. So one day he just flipped out, got extremely angry, made one last video saying how he was never coming back and how he's leaving his wife and kids. He deletes everything and is unheard of for months. A few months pass and he uploads a new video. The new video is James obsessively showing and talking about his highly advanced chicken coop he made in Minecraft. He had hundreds of chickens lined up maybe 80 feet in the air, each chicken had a 1x1 square to fit in. Below the chicken was a long tube in which their egg would drop down, and a catcher at the base of the ground. James was fantically showing this contraption, rocking back and forth, had a headset on. He looked awful too. I actually emailed James Corbett about this dream, but he never responded. Speaking of James Corbett, why do so many people look like him? I feel like they make middle aged bald, bearded men in a DUMB and just release them into the wild, but give them balding genetics so they know how to keep track of them. Like they probably made James Corbett and Andrew Caufman from the same test tube. They fucked up with them, at least like give one of them hair or good eyesight. @ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity #GHOSTn If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs. Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see. Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be. Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes. Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
@ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity #GHOSTn If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs. Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see. Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be. Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes. Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do. @ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn. So what is encryption? It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with. > BEGINNER LEVEL - Encrypt your phone and computer. People walk around with their whole lives on their phone. Protect it. -phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password. After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive. -Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts. -Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault". -Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution. Awesome sauce. You have achieved minimum status. > ADVANCED LEVEL - Encrypt individual files. You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you. What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted. I will share with you one of my favorite small programs: Picocrypt. Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away. Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own. > EXPERT LEVEL - Encrypt containers and hidden containers. What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful. Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives. Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container. This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that. These features allow you to do all sorts of interesting things only limited by your need and imagination. What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun. > NEMO - Failsafe Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot. Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone. > > Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc > Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn. So what is encryption? It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with. > BEGINNER LEVEL - Encrypt your phone and computer. People walk around with their whole lives on their phone. Protect it. -phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password. After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive. -Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts. -Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault". -Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution. Awesome sauce. You have achieved minimum status. > ADVANCED LEVEL - Encrypt individual files. You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you. What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted. I will share with you one of my favorite small programs: Picocrypt. Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away. Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own. > EXPERT LEVEL - Encrypt containers and hidden containers. What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful. Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives. Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container. This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that. These features allow you to do all sorts of interesting things only limited by your need and imagination. What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun. > NEMO - Failsafe Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot. Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone. > > Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc > Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is. @ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 2: Functions and Loops ### Functions: Your Own Commands Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick: ```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } } meow(3); // This will print "Meow!" three times ``` ### Built-in Functions JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console: ```javascript console.log("I'm a cat!"); ``` ### Loops: Repeating Tasks Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds: ```javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); } ``` This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 2: Functions and Loops ### Functions: Your Own Commands Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick: ```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } } meow(3); // This will print "Meow!" three times ``` ### Built-in Functions JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console: ```javascript console.log("I'm a cat!"); ``` ### Loops: Repeating Tasks Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds: ```javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); } ``` This will print "Chasing tail, round X" five times, where X goes from 1 to 5. @ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 3: Arrays, Objects, and Callbacks ### Arrays: Lists of Things Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys: ```javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse" ``` ### Objects: Grouping Related Information Objects allow you to group related information together. They're like detailed profiles for each of your cat friends: ```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" }; console.log(myCat.name); // Prints "Fluffy" ``` ### Callbacks: Doing Things Later Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat: ```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); } feedCat(function() { console.log("Time for a treat!"); }); ``` This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat. Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 3: Arrays, Objects, and Callbacks ### Arrays: Lists of Things Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys: ```javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse" ``` ### Objects: Grouping Related Information Objects allow you to group related information together. They're like detailed profiles for each of your cat friends: ```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" }; console.log(myCat.name); // Prints "Fluffy" ``` ### Callbacks: Doing Things Later Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat: ```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); } feedCat(function() { console.log("Time for a treat!"); }); ``` This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat. Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat! @ 4c96d763:80c3ee30
2024-09-03 18:46:10# Changes ## William Casarin (7): - debug: add subid debugging - fix bug where it was subscribing too many times - arg: add -c profile{,:pubkey} arg column - env: add some test npubs - arg: add -c universe column - appease clippy - fonts: add thai support pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/989f88c989f5d6ec85f719efab6f80fb1a95ee00.html)
@ 4c96d763:80c3ee30
2024-09-03 18:46:10# Changes ## William Casarin (7): - debug: add subid debugging - fix bug where it was subscribing too many times - arg: add -c profile{,:pubkey} arg column - env: add some test npubs - arg: add -c universe column - appease clippy - fonts: add thai support pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/989f88c989f5d6ec85f719efab6f80fb1a95ee00.html) @ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track. *(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)* 1. **Stefon Diggs leads the Texans in targets, catches and receiving yards** Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year. 2. **CJ Stroud leads the NFL is passing yards** This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2. 3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)** Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens. 4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR** Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020. 5. **The Giants will field a top-10 fantasy defense.** I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers. 6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt** I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua. 7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)** Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time. 8. **Dalvin Cook will lead the Cowboys in rushing yards** Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.) 9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.** He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.) 10. **Dalton Kincaid (TE4) will lead all TE in catches** I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. 11. **Some of these predictions will be wrong** No one’s perfect, but you never want to get shut out.
@ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track. *(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)* 1. **Stefon Diggs leads the Texans in targets, catches and receiving yards** Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year. 2. **CJ Stroud leads the NFL is passing yards** This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2. 3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)** Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens. 4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR** Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020. 5. **The Giants will field a top-10 fantasy defense.** I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers. 6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt** I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua. 7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)** Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time. 8. **Dalvin Cook will lead the Cowboys in rushing yards** Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.) 9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.** He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.) 10. **Dalton Kincaid (TE4) will lead all TE in catches** I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. 11. **Some of these predictions will be wrong** No one’s perfect, but you never want to get shut out. @ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
@ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app) @ eed76ece:afa98124
2024-09-02 18:58:30As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously. Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online. SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West. Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway. Examples Customers in these regions I deal with primarily communicate with me in Japan, Thailand using LINE and Tik Tok daily. Most of the rest of the World communicate with me using WhatsApp. Certain parts of Eastern Europe and Asia Telegram. Interestingly my resellers in the USA primarily post on WhatsApp. Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again". "So I will always have free speech, the politicians told me so". originally posted at https://stacker.news/items/670041
@ eed76ece:afa98124
2024-09-02 18:58:30As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously. Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online. SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West. Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway. Examples Customers in these regions I deal with primarily communicate with me in Japan, Thailand using LINE and Tik Tok daily. Most of the rest of the World communicate with me using WhatsApp. Certain parts of Eastern Europe and Asia Telegram. Interestingly my resellers in the USA primarily post on WhatsApp. Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again". "So I will always have free speech, the politicians told me so". originally posted at https://stacker.news/items/670041 @ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot. Here are the results: ([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream)) <img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png"> **1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount. **2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead. **3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there. **4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target. **5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone. **6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year. **7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position. **8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR. **9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.) **10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.) **11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks. **12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build. **13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job. **14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert. **15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old. **16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down. **17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too. **18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie. **19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.) **20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence. **Roster By Position** **QB** Anthony Richardson **RB** James Conner/Jaleel McLaughlin **WR** Ja’Marr Chase/Drake London/DeVonta Smith **TE** Dalton Kincaid **FLEX** Stefon Diggs **K** Younghoe Koo **D** Giants **Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
@ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot. Here are the results: ([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream)) <img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png"> **1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount. **2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead. **3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there. **4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target. **5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone. **6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year. **7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position. **8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR. **9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.) **10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.) **11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks. **12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build. **13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job. **14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert. **15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old. **16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down. **17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too. **18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie. **19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.) **20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence. **Roster By Position** **QB** Anthony Richardson **RB** James Conner/Jaleel McLaughlin **WR** Ja’Marr Chase/Drake London/DeVonta Smith **TE** Dalton Kincaid **FLEX** Stefon Diggs **K** Younghoe Koo **D** Giants **Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston @ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy. You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start. Don't worry, here are some absolute beginner first steps that will make a big difference. > 1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. > 2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data. BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS. > 3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. > 4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. > 5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice. > BONUS TIP: Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population. > OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security. What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone. The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure? There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
@ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy. You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start. Don't worry, here are some absolute beginner first steps that will make a big difference. > 1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. > 2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data. BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS. > 3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. > 4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. > 5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice. > BONUS TIP: Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population. > OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security. What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone. The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure? There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later. @ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md) And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker ```sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0 ``` ## New Features ### Support for NIP-49 encrypted nsec Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...) There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps  ### Blindspot feeds There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing  ### NIP-42 Relay authentication The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings  ### Wasm relay and event verification The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view  The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting  ### Thread tabs Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note   ### Wiki articles Its not feature complete but you can now view and edit wiki articles in the app  ### Finished the launchpad The launchpad is now usable and shows the latest notifications, messages, streams, and tools  ### Blossom uploads The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings  And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`  ### Task Manager There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app  You can see what relays the app is currently connected to  And which relays are requesting NIP-42 authentication  ## Bug fixes - Fix null relay hints in DMs - Fix users own events being hidden by muted words - Fix random events showing up as DM messages - Fix app prompting NIP-07 extension to unlock when app opens - Remove corsproxy.io as default service for CORS proxy
@ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md) And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker ```sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0 ``` ## New Features ### Support for NIP-49 encrypted nsec Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...) There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps  ### Blindspot feeds There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing  ### NIP-42 Relay authentication The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings  ### Wasm relay and event verification The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view  The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting  ### Thread tabs Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note   ### Wiki articles Its not feature complete but you can now view and edit wiki articles in the app  ### Finished the launchpad The launchpad is now usable and shows the latest notifications, messages, streams, and tools  ### Blossom uploads The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings  And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`  ### Task Manager There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app  You can see what relays the app is currently connected to  And which relays are requesting NIP-42 authentication  ## Bug fixes - Fix null relay hints in DMs - Fix users own events being hidden by muted words - Fix random events showing up as DM messages - Fix app prompting NIP-07 extension to unlock when app opens - Remove corsproxy.io as default service for CORS proxy @ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment. A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding. It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
@ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment. A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding. It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment. @ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope. But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin. For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right? I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours? She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw. I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else. So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore. We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent? The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them. Extreme situations, I know. But no one thinks it will happen to them—until it does. So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why? What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time. Time with your kids. Time with your family. Time with yourself. There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work. But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here. So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here. I just need to get through the withdrawal phase. originally posted at https://stacker.news/items/662939
@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope. But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin. For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right? I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours? She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw. I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else. So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore. We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent? The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them. Extreme situations, I know. But no one thinks it will happen to them—until it does. So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why? What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time. Time with your kids. Time with your family. Time with yourself. There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work. But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here. So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here. I just need to get through the withdrawal phase. originally posted at https://stacker.news/items/662939 @ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.  originally posted at https://stacker.news/items/669464
@ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.  originally posted at https://stacker.news/items/669464 @ 8125b911:a8400883
2024-09-02 07:18:52曾经有一款热门插件 dmooji(弹幕君),它让 YouTube 拥有了像其他弹幕网站一样的互动体验。看着屏幕上飞过的评论和吐槽,仿佛能和全世界的观众一起欢笑、感动、吐槽,那些弹幕不仅仅是文字,更是观众们在某个时刻留下的心情。但随着 dmooji 的开发者停止了维护,插件无法使用,用户的弹幕数据也随之丢失。那些在无数个夜晚留下的感触和笑点都被抹去,曾经与他人共享的回忆也随之消逝。这样的教训提醒我们,依赖于单一平台和维护团队的产品,总有脆弱的一天,可能我们珍视的东西就会悄然不再。 大约两年前,我偶然间了解到了一个去中心化的社交网络协议——nostr。当时我就萌生了一个想法:如果能基于这个协议做一款弹幕插件,那该有多好!然而,因为我主要从事后端开发,对前端几乎一窍不通,再加上拖延症的“加持”,这个想法一直被搁置。直到最近,我终于下定决心完成了这个项目,并将它命名为 danmakustr。 下载地址:https://chromewebstore.google.com/detail/mohbdimkkpjjibdfipfajpgpmegnglhb 源码地址:https://github.com/CodyTseng/danmakustr 最近弹幕墙:https://danmaku.nostr-relay.app/  ## danmakustr 有什么特点? 基于去中心化社交网络协议 nostr。你的弹幕会被发送并存储到你指定的服务器上,而非依赖单一服务器。即使插件未来不再维护,只要 nostr 网络仍然存在,插件就能继续正常使用!如果你非常珍视自己的弹幕,可以在本地运行 nostr-relay-tray 并将其添加到 relay 列表中。 danmakustr 目前已经在 YouTube 上实现了基本的弹幕功能,支持自定义弹幕的颜色和显示位置。未来还会支持一些弹幕互动功能,和支持更多的视频平台。 ## 结语 在这个越来越注重个人表达和数据隐私的时代,danmakustr 带来了 YouTube 弹幕互动的新可能。它既保留了我们熟悉的乐趣,又为我们提供了前所未有的自由和控制权。如果你也对弹幕文化情有独钟,或者想要尝试一种全新的互动方式,那就赶紧体验 danmakustr 吧!让我们一起在弹幕的世界里畅所欲言,留下属于自己的印记。
@ 8125b911:a8400883
2024-09-02 07:18:52曾经有一款热门插件 dmooji(弹幕君),它让 YouTube 拥有了像其他弹幕网站一样的互动体验。看着屏幕上飞过的评论和吐槽,仿佛能和全世界的观众一起欢笑、感动、吐槽,那些弹幕不仅仅是文字,更是观众们在某个时刻留下的心情。但随着 dmooji 的开发者停止了维护,插件无法使用,用户的弹幕数据也随之丢失。那些在无数个夜晚留下的感触和笑点都被抹去,曾经与他人共享的回忆也随之消逝。这样的教训提醒我们,依赖于单一平台和维护团队的产品,总有脆弱的一天,可能我们珍视的东西就会悄然不再。 大约两年前,我偶然间了解到了一个去中心化的社交网络协议——nostr。当时我就萌生了一个想法:如果能基于这个协议做一款弹幕插件,那该有多好!然而,因为我主要从事后端开发,对前端几乎一窍不通,再加上拖延症的“加持”,这个想法一直被搁置。直到最近,我终于下定决心完成了这个项目,并将它命名为 danmakustr。 下载地址:https://chromewebstore.google.com/detail/mohbdimkkpjjibdfipfajpgpmegnglhb 源码地址:https://github.com/CodyTseng/danmakustr 最近弹幕墙:https://danmaku.nostr-relay.app/  ## danmakustr 有什么特点? 基于去中心化社交网络协议 nostr。你的弹幕会被发送并存储到你指定的服务器上,而非依赖单一服务器。即使插件未来不再维护,只要 nostr 网络仍然存在,插件就能继续正常使用!如果你非常珍视自己的弹幕,可以在本地运行 nostr-relay-tray 并将其添加到 relay 列表中。 danmakustr 目前已经在 YouTube 上实现了基本的弹幕功能,支持自定义弹幕的颜色和显示位置。未来还会支持一些弹幕互动功能,和支持更多的视频平台。 ## 结语 在这个越来越注重个人表达和数据隐私的时代,danmakustr 带来了 YouTube 弹幕互动的新可能。它既保留了我们熟悉的乐趣,又为我们提供了前所未有的自由和控制权。如果你也对弹幕文化情有独钟,或者想要尝试一种全新的互动方式,那就赶紧体验 danmakustr 吧!让我们一起在弹幕的世界里畅所欲言,留下属于自己的印记。