-

@ 91bea5cd:1df4451c
2025-02-04 17:24:50
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 91bea5cd:1df4451c
2025-02-04 17:15:57
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ ddf03aca:5cb3bbbe
2025-02-02 13:09:27
We’re thrilled to announce the stable release of Cashu-TS v2.2! Although this update is a minor version bump, it brings significant improvements under the hood that enhance the overall developer experience. We’ve spent several weeks testing and refining these changes.
---
## What’s New in v2.2?
While there are no breaking changes in this release, there are many internal changes. If you spot any regressions or unexpected behavior, please [let us know](https://github.com/cashubtc/cashu-ts/issues). Here’s a rundown of the major updates:
- **Enhanced Proof Creation**: The way proofs are created internally has been revamped.
- **User-Controlled Outputs**: You now have full control over how outputs are created.
- **Improved Bundling**: We’ve switched our bundling tool to [vite](https://vitejs.dev) for faster and more modern builds.
- **Updated Testing Tools**: Our testing framework has migrated to [vitest](https://vitest.dev) and [msw](https://mswjs.io), with added browser testing via Playwright.
---
## New Flexibility with OutputData
In previous versions of Cashu-TS, the creation of outputs (or *BlindedMessages*) was hidden away. Even though there were options to tweak the process (like deterministic secrets or P2PK), you were always limited to the built-in logic.
### What’s Changed?
In v2.2, we’ve introduced a public interface that not only streamlines output creation but also lets you plug in your own custom logic when needed. With the new `outputData` option available on all output-creating methods, you can now bypass the automatic process and provide your own outputs.
For example, you can create two proofs tied to different public keys in a single mint operation:
```ts
const data1 = OutputData.createP2PKData({ pubkey: "key1" }, 10, keys);
const data2 = OutputData.createP2PKData({ pubkey: "key2" }, 10, keys);
const { keep, send } = await wallet.send(20, proofs, {
outputData: { send: [...data1, ...data2] },
});
```
### Customization Made Easy
The `outputData` option now accepts anything that conforms to the `OutputDataLike` interface. This means you can introduce your own output creation logic—even if it’s not natively supported by Cashu-TS yet. Here’s what the interface looks like:
```ts
export interface OutputDataLike {
blindedMessage: SerializedBlindedMessage;
blindingFactor: bigint;
secret: Uint8Array;
toProof: (signature: SerializedBlindedSignature, keyset: MintKeys) => Proof;
}
```
### Introducing OutputData Factories
While having full control is empowering, it also means you’ll need to handle tasks like fee calculation and amount selection manually. To strike a balance between control and convenience, we now support **OutputData Factories**.
A factory is simply a function that takes an amount and `MintKeys` as input and returns an `OutputDataLike` object. This way, you can define a blueprint for your output data without worrying about the nitty-gritty details. For instance, you can create separate factories for amounts you keep versus those you send:
```ts
function keepFactory(a: number, k: MintKeys) {
return OutputData.createSingleP2PKData({ pubkey: "keepPk" }, a, k.id);
}
function sendFactory(a: number, k: MintKeys) {
return OutputData.createSingleP2PKData({ pubkey: "sendPk" }, a, k.id);
}
const { send, keep } = await wallet.send(amount, proofs, {
outputData: { send: createFactory("send"), keep: createFactory("keep") },
});
```
Plus, you can now instantiate a `CashuWallet` with a default `keepFactory`, ensuring that all change amounts automatically lock to your key—streamlining your workflow even further.
---
## Bundling Improvements with Vite
Starting with v2.2, we’ve transitioned from using `tsc` to [vite](https://vitejs.dev) for transpiling and bundling the library code. Although this change is mostly behind the scenes, it brings several benefits:
- **Modern Build Target**: We’ve updated our build target to ES6.
- **Updated Exports**: The package exports now reflect the latest JavaScript standards.
- **Standalone Build Soon**: We’re working on a standalone build that bundles Cashu-TS along with all its dependencies. This will let you import Cashu-TS directly into your HTML.
If you encounter any issues with the new bundling setup, please [let us know](https://github.com/cashubtc/cashu-ts/issues).
### A Nod to Vitest
In addition to our bundling improvements, we’ve migrated our testing framework from Jest (with nock) to [vitest](https://vitest.dev) combined with [msw](https://mswjs.io). This switch gives us more flexibility in testing and mocking, plus we’ve added browser testing based on Playwright—thanks to the tip from nostr:npub16anjdksmvn5x08vtden04n64rw5k7fsjmedpw8avsx8wsh8ruhlq076pfx!
---
## In Conclusion
Although Cashu-TS v2.2 is a minor version update, it comes packed with improvements that enhance both the developer experience and the flexibility of the library. We’re excited to see how you’ll use these new features in your projects! Thanks to all the amazing contributors that add to this library.
Thank you for being a part of the Cashu-TS community. As always, if you have any questions, suggestions, or issues, don’t hesitate to [reach out to us](https://github.com/cashubtc/cashu-ts/issues).
-

@ 9e69e420:d12360c2
2025-02-01 11:16:04

Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-

@ 9e69e420:d12360c2
2025-01-26 15:26:44
Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-

@ 9e69e420:d12360c2
2025-01-26 01:31:47
## Chef's notes
# arbitray
- test
- of
- chefs notes
## hedding 2
## Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
## Ingredients
- Test ingredient
- 2nd test ingredient
## Directions
1. Bake
2. Cool
-

@ 9e69e420:d12360c2
2025-01-25 22:16:54
President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
[Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
-

@ 9e69e420:d12360c2
2025-01-25 14:32:21
| Parameters | Dry Mead | Medium Mead | Sweet Mead |
|------------|-----------|-------------|------------|
| Honey | 2 lbs (900 grams) | 3 lbs (1.36 kg) | 4 lbs (1.81 kg) |
| Yeast | ~0.07 oz (2 grams) | ~0.08 oz (2.5 grams) | ~0.10 oz (3 grams) |
| Fermentation | ~4 weeks | 4 to 6 weeks | 6 to 8 weeks |
| Racking | Fortnight or later | 1 month or after | ~2 months and after |
| Specific Gravity | <1.010 | ~1.01 to ~1.025 | >1.025 |
-

@ 9e69e420:d12360c2
2025-01-23 15:09:56
President Trump has ordered thousands of additional troops to the U.S.-Mexico border as part of an effort to address immigration and security issues. This directive builds on his initial commitment to increase military presence along the border.
Currently, around 2,200 active-duty personnel and approximately 4,500 National Guardsmen are stationed there. The new deployment aims to enhance the capabilities of Joint Task Force-North, allowing troops to assist in operations and provide intelligence support.
Details on specific units remain unclear. The situation is still developing, with updates expected.
[Sauce](https://thepostmillennial.com/breaking-president-trump-orders-thousands-of-troops-to-the-us-border-with-mexico)
-

@ 9e69e420:d12360c2
2025-01-21 19:31:48
Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
## Active Compounds
The oil's therapeutic properties stem from its key bioactive components:
- Carvacrol and thymol (primary active compounds)
- Polyphenols and other antioxidant
## Antimicrobial Properties
**Bacterial Protection**
The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
**Antifungal Effects**
It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
## Digestive Health Benefits
Oregano oil supports digestive wellness by:
- Promoting gastric juice secretion and enzyme production
- Helping treat Small Intestinal Bacterial Overgrowth (SIBO)
- Managing digestive discomfort, bloating, and IBS symptoms
## Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through:
- Powerful antioxidant activity that fights free radicals
- Reduction of inflammatory markers in the body
- Protection against oxidative stress-related conditions
## Respiratory Support
It aids respiratory health by:
- Loosening mucus and phlegm
- Suppressing coughs and throat irritation
- Supporting overall respiratory tract function
## Additional Benefits
**Skin Health**
- Improves conditions like psoriasis, acne, and eczema
- Supports wound healing through antibacterial action
- Provides anti-aging benefits through antioxidant properties
**Cardiovascular Health**
Studies show oregano oil may help:
- Reduce LDL (bad) cholesterol levels
- Support overall heart health
**Pain Management**
The oil demonstrates effectiveness in:
- Reducing inflammation-related pain
- Managing muscle discomfort
- Providing topical pain relief
## Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-

@ b17fccdf:b7211155
2025-01-21 17:02:21
The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node:
* Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
```
tor --version
```
**Example** of expected output:
```
Tor version 0.4.8.6.
This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html)
Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc.
Tor compiled with GCC version 12.2.0
```
~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update.
* Basic PoW support can be checked by running this command:
```
tor --list-modules
```
Expected output:
```
relay: yes
dirauth: yes
dircache: yes
pow: **yes**
```
~ > If you have `pow: yes`, you are **OK**
* Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
```
sudo nano /etc/tor/torrc
```
Example:
```
# Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/
HiddenServiceVersion 3
HiddenServicePoWDefensesEnabled 1
HiddenServicePort 80 127.0.0.1:3002
```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
* Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
* LND: https://github.com/bitcoin/bitcoin/issues/28499
---
More info:
* https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
* https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
---
Enjoy it MiniBolter! 💙
-

@ 3f770d65:7a745b24
2025-01-19 21:48:49
The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
**PROTOCOLS, NOT PLATFORMS.**
At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
**THIS IS POWERFUL.**
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
**AGAIN, THIS IS POWERUFL.**
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
###
-

@ 9e69e420:d12360c2
2025-01-19 04:48:31
A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-

@ 6389be64:ef439d32
2025-01-16 15:44:06
## Black Locust can grow up to 170 ft tall
## Grows 3-4 ft. per year
## Native to North America
## Cold hardy in zones 3 to 8

## Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
## Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
## Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
## Bees

- The edible flower clusters are also a top food source for honey bees
## Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
## Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
## Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-

@ 6389be64:ef439d32
2025-01-14 01:31:12
Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
# Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
# Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
# The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
# The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
# Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
# Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
# The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
# CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
# The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
# The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
# The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
# Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
# Sensor Packages
### LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
### pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
### Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
# Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
# Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
# The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-

@ 3f770d65:7a745b24
2025-01-12 21:03:36
I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool.
In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users.
I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂
Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client.
Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that?
Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr.
As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways.
Do you want an Olas feed of images? Add the media column.
Do you want a feed of live video events? Add the zap.stream column.
Do you want Nostr Nests or audio chats? Add that column to your Notedeck.
Git? Email? Books? Chat and DMs? It's all possible.
Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer.
Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility.
Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices.
> In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet.
>
> \-Will Casarin
In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild.
Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem.
Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint.
For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
-

@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
## **Necessário**
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
## **Algumas coisas que você precisa saber**
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
---
## **O tutorial será dividido em dois módulos:**
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
---
## **No final, teremos:**
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

---
## **Módulo 1 - Criando uma carteira fria/assinador**
1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade.
2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\
*(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*

5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*

---
## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.**
1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)*
2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.

3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.

4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**.
6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
---
## **Conclusão**
**Pontos positivos do setup:**
- **Simplicidade:** Basta um dispositivo Android antigo.
- **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders.
**Pontos negativos do setup:**
- **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.***
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
---
-

@ 3f770d65:7a745b24
2025-01-05 18:56:33
New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter [Olas](https://olas.app).
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
[Download on iOS](https://testflight.apple.com/join/2FMVX2yM).
[Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore.
Let's make waves together.
-

@ a4a6b584:1e05b95b
2025-01-02 18:13:31
## The Four-Layer Framework
### Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
**Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
_Once you have the big picture in mind, it’s time to start breaking it down._
---
### Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
**Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
_With your categories in place, you’re ready to dive into the details that bring them to life._
---
### Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
**Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
_Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._
---
### Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
**Example**: Learn about rare programming quirks or historical trivia about a language’s development.
- **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
---
## Pro Tips for Better Learning
### 1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
### 2. Map It Out
Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
### 3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material.
### 4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.
**Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
---
## Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-

@ 3f770d65:7a745b24
2024-12-31 17:03:46
Here are my predictions for Nostr in 2025:
**Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
**Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
**Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
**Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-

@ a367f9eb:0633efea
2024-12-22 21:35:22
I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”.
It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
> In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
>
> It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
>
> …
>
> The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
**I was at least somewhat wrong.**
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
**I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.**
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/).
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
**But I was wrong.**
When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
**Now I understand I was wrong.**
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.*
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016.
**And I was wrong again.**
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
**Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.**
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-

@ 1cb14ab3:95d52462
2024-12-17 19:24:54
*Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.*
---
The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways.
Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future.
When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal.
For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away.
This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below:
<aside>
**Inflation Rate (%)** | **Purchasing Power Halving (Years)**
- 2% | 35-40 years
- 3% | 20-25 years
- 4% | 15-20 years
- 5% | 10-15 years
- 6% | 7-12 years
- 7% | 5-10 years
- 8% | 4-8 years
- 9% | 3-6 years
- 10% | 2-5 years
</aside>
Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble.
But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation?
A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future.
Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money.
The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued.
By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world.
Bitcoin isn’t a bubble; it’s a beacon.
---
### More from Hes:
[Art](https://hes.npub.pro/tag/art/)
[Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06)
[Travel Guides](https://hes.npub.pro/tag/travel/)
[Photography](https://hes.npub.pro/tag/photography)
-

@ 6389be64:ef439d32
2024-12-09 23:50:41
Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
### **Comfrey: Nature’s Champion of Resilience**
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
### **Biochar: The Silent Powerhouse of Soil Regeneration**
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as *terra preta*, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
### **The Synergy: Comfrey and Biochar Together**
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
1. **Nutrient Cycling and Retention**\
Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
2. **Water Management**\
Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
3. **Microbial Ecosystems**\
Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
### **Lessons Beyond the Soil**
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-

@ 129f5189:3a441803
2024-11-22 03:42:42
Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario.
The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy.
After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America.
Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million.
China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions...
https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg
For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions.
In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border.
A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention.
https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg
In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere.
The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years.
https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg
The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021.
In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government.
https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg
Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues.
In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities."
https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg
The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024.
Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction.
In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government.
https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg
Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University.
"The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times.
General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country.
"We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time.
In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade."
https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg
In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues."
Under the previous administration, China had received preferential treatment.
In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan.
The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security.
No public records show that the project has progressed since then.
https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg
Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark.
"Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement.
"Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face."
https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg
The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era.
Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel."
https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg
Access to space plays a crucial role in the CCP's strategic objectives.
Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China.
According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice.
According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access.
China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely.
The big question is: what could this facility do in times of war?
https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg
Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit.
The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface.
Additionally, it offers strategic advantages for any government involved in espionage.
https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg
Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner.
However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives.
Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023.
https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg
-

@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52
Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions.
---
## Subscriptions with Cashu
One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that?
However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this:
1. **Overpaying:**
To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted.
2. **Full Interactivity:**
In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends.
---
## Enter Locking Scripts
One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone.
A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key.
To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token.
With these tools, we can now create non-interactive payment streams!
---
## One Missing Piece…
Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams.
---
## The Grand Finale: Payment Streams
Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender.
Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.
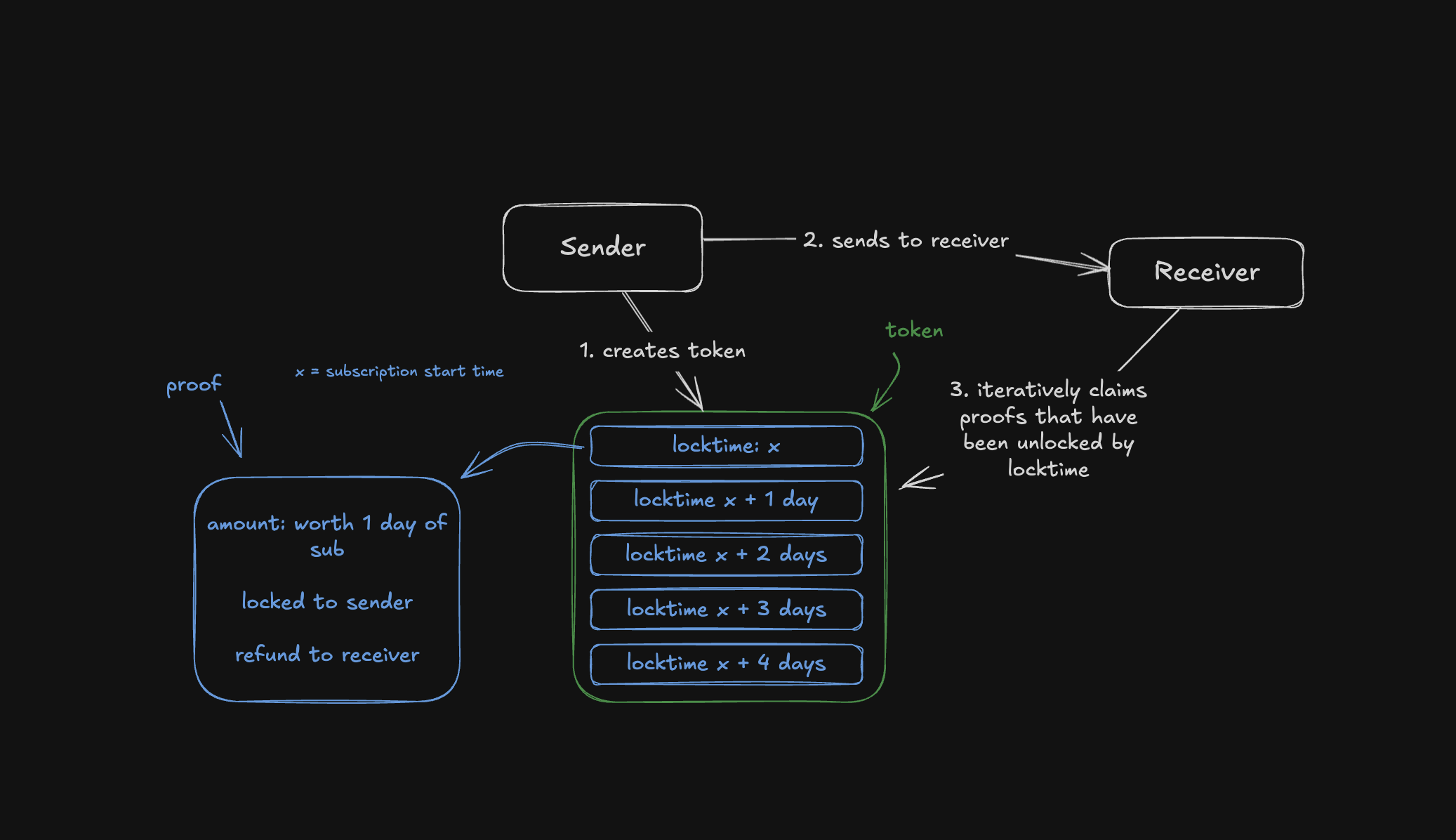
### Example: Renting a VPS
Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work:
1. Construct a token worth 7,000 sats to cover the entire week.
2. Divide the token into 7 proofs, each worth 1,000 sats.
3. Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key.
- The first proof has a locktime of `now`.
- The second proof has a locktime of `now + 1 day`.
- The third proof has a locktime of `now + 2 days`, and so on.
When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on.
At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver.
---
With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds.
Thank you for reading. Make sure to leave a nut if you enjoyed this :)
-

@ 87730827:746b7d35
2024-11-20 09:27:53
Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
===================================================================================
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
* * *
**KEY TAKEAWAYS**
* The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero.
* The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards.
* While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country.
**_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._**
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
----------------------------------
If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
> … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
>
> – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-)
The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations.
However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
------------------------------------------------
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/).
Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.

In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
----------
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
----------
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
[View all articles by Cassio Gusson](https://techreport.com/author/cassiog/)
-

@ 5e5fc143:393d5a2c
2024-11-19 10:20:25
Now test old reliable front end
Stay tuned more later
Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues
-

@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
## Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
## Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
## Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
## Directions
1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
-

@ 4ba8e86d:89d32de4
2024-11-14 09:17:14
Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade.
Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
## O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
## O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular;
• Computador com adb;
• Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular;
• Termux;
• Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular;
• Lista de bloatwares para seu dispositivo;
## Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
## Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid:
https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
## Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
```
Samsung Galaxy Note 10 Plus bloatware list
```
Provavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
### De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
## Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
## Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
## Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
## Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
```
./adb start-server
```
O resultado deve ser:
*daemon not running; starting now at tcp:5037
*daemon started successfully
E caso não apareça nada, execute:
```
./adb kill-server
```
E inicie novamente.
Com o adb conectado ao celular, execute:
```
./adb shell
```
Para poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized.
This adb server’s $ADB_VENDOR_KEYS is not set
Try ‘adb kill-server’ if that seems wrong.
Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
## No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
```
pkg install android-tools
```
Quando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
```
adb pair localhost:porta CódigoDeEmparelhamento
```
De acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
```
adb connect localhost:porta
```
Obs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
```
adb shell
```
Remoção na prática
Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
```
pm uninstall –user 0 com.google.android.apps.maps
```
E pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
```
cmd package install-existing nome.do.pacote
```
## Pós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências:
Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264
http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-

@ a10260a2:caa23e3e
2024-11-10 04:35:34
nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard.
In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW.
I took some screenshots to give you an idea of how things work.
The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).

Clicking login allows signing in with a browser extension.
The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.
Existing blog posts (i.e. long form notes) are synced.

Same for product listings. There’s a nice interface to create new ones and preview them before publishing.
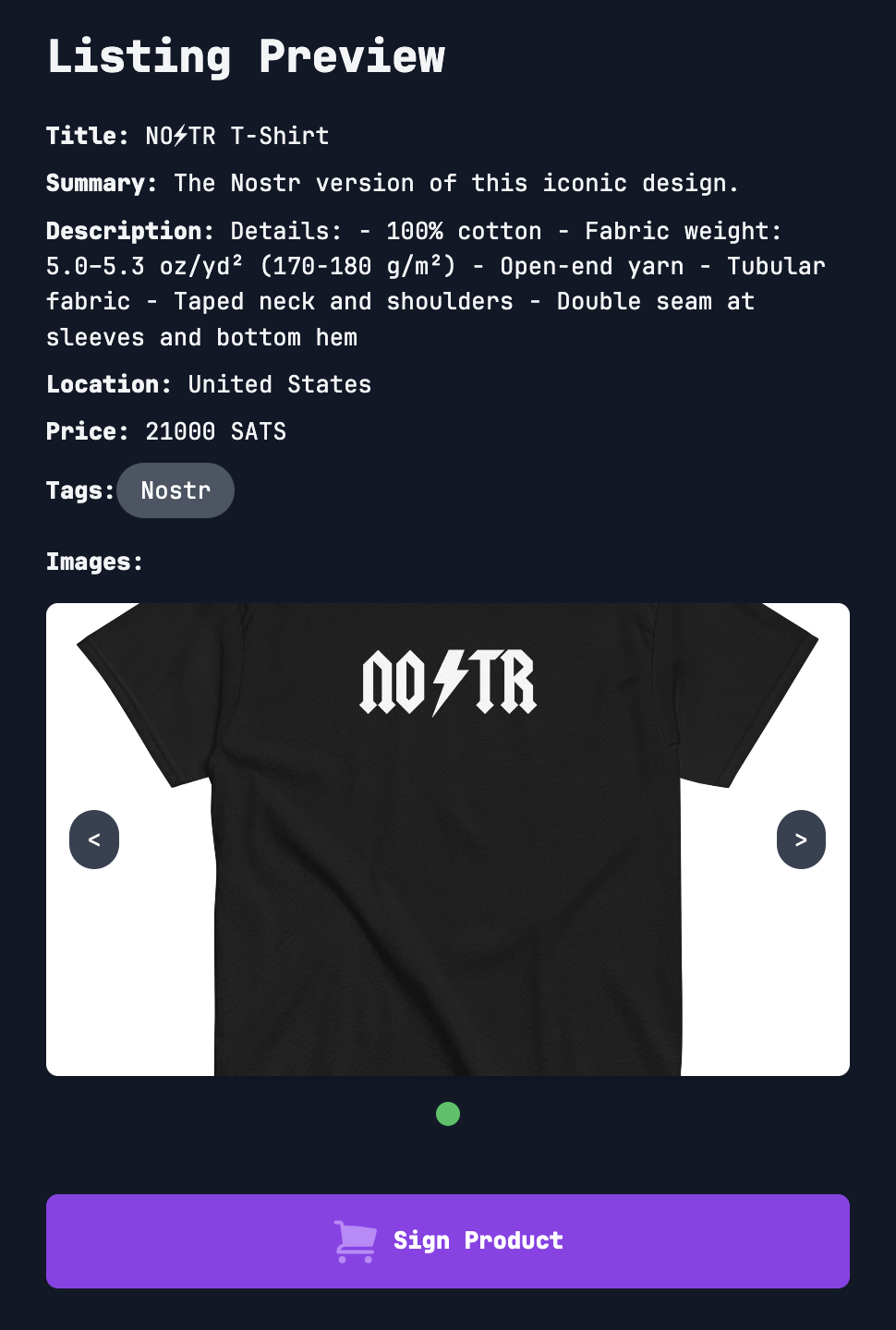
That’s all for now. As you can see, super slick stuff!
Bullish on Cypher.
So much so I had to support the project and buy a subdomain. 😎
https://bullish.cypher.space
originally posted at https://stacker.news/items/760592
-

@ bcea2b98:7ccef3c9
2024-11-09 17:01:32
Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-

@ 4ba8e86d:89d32de4
2024-11-07 13:56:21
Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas.
Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW.
Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW.
Sem mais delongas, vamos ao tutorial de fato.
## 1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P.
Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo.
Após entrar no site vá para a página '1 - Creating a mailbox'
https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos.
https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados.
https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg
https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
## 2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd.
Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso.
Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf
https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf
https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
```
sudo systemctl restart i2pd
```
Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.
Com os túneis cliente criados, vamos agora configurar o Thunderbird
## 3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir.
https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg
https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta.
https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir.
https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue'
https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta.
https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
## 4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-

@ a367f9eb:0633efea
2024-11-05 08:48:41
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
> In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
>
> The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
> In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
>
> The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)?
**As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).**
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
## **Open-source matters**
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
## **Open-source is for your friends, and enemies**
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
## **Limiting open-source threatens our own advancement**
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols.
The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
*Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).*
-

@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
> ### 第三方API合集:
---
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 |
| --- | --- | --- | --- |
| AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) |
| OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) |
| CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) |
| OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) |
` 持续更新。。。`
---
### 推广:
访问不了openai,去`低调云`购买VPN。
官网:https://didiaocloud.xyz
邀请码:`w9AjVJit`
价格低至1元。
-

@ 06639a38:655f8f71
2024-11-01 22:32:51
One year ago I wrote the article [Why Nostr resonates](https://sebastix.nl/blog/why-nostr-resonates/) in Dutch and English after I visited the Bitcoin Amsterdam 2023 conference and the Nostrdam event. It got published at [bitcoinfocus.nl](https://bitcoinfocus.nl/2023/11/02/278-waarom-nostr-resoneert/) (translated in Dutch). The main reason why I wrote that piece is that I felt that my gut feeling was tellinng me that Nostr is going to change many things on the web.
After the article was published, one of the first things I did was setting up this page on my website: [https://sebastix.nl/nostr-research-and-development](https://sebastix.nl/nostr-research-and-development). The page contains this section (which I updated on 31-10-2024):
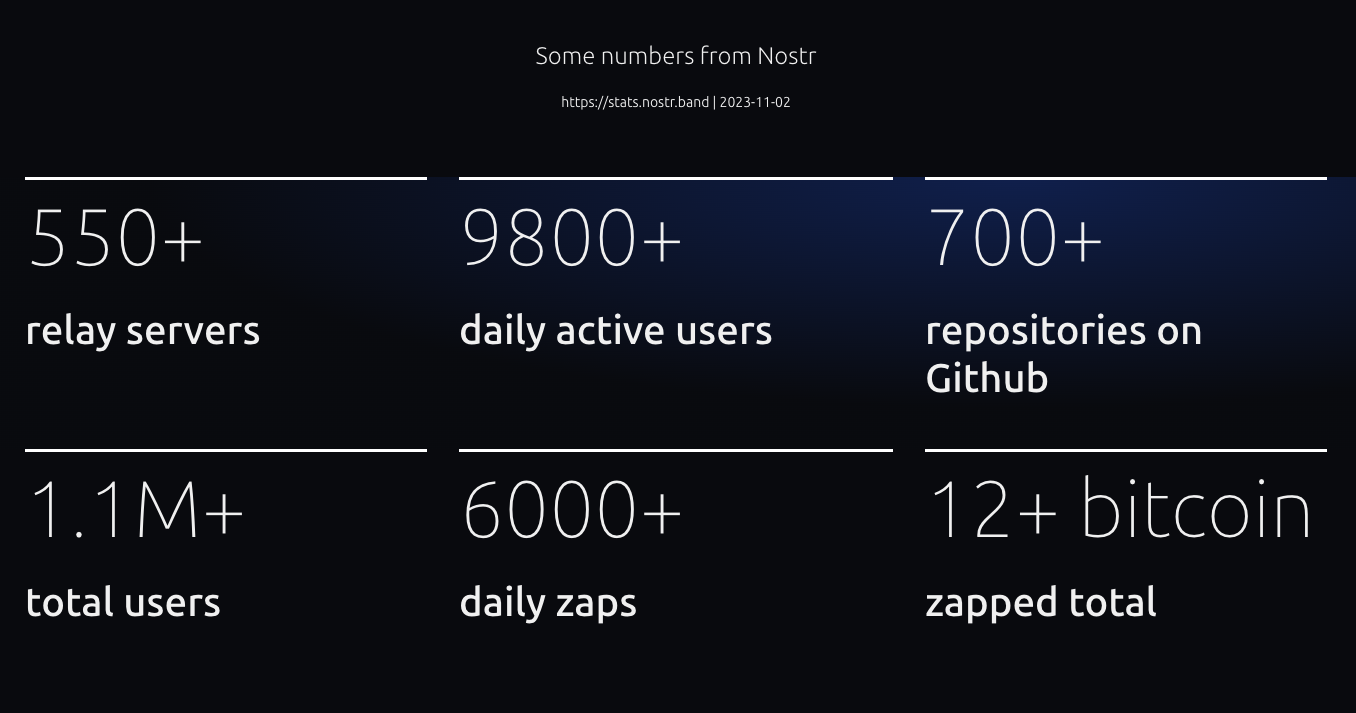
One metric I would like to highlight is the number of repositories on Github. Compared to a year ago, there are already more than 1130 repositories now on Github tagged with Nostr. Let's compare this number to other social media protocols and decentralized platforms (24-10-2024):
* Fediverse: 522
* ATProto: 159
* Scuttlebot: 49
* Farcaster: 202
* Mastodon: 1407
* ActivityPub: 444
Nostr is growing. FYI there are many Nostr repositories not hosted on Github, so the total number of Nostr reposities is higher. I know that many devs are using their own Git servers to host it. We're even capable of setting up Nostr native Git repositories (for example, see [https://gitworkshop.dev/repos](https://gitworkshop.dev/repos)). Eventually, Nostr will make Github (and other platforms) absolute.
Let me continue summarizing my personal Nostr highlights of last year.
## Organising Nostr meetups

This is me playing around with the NostrDebug tool showing how you can query data from Nostr relays. Jurjen is standing behind me. He is one of the people I've met this year who I'm sure I will have a long-term friendship with.
## OpenSats grant for Nostr-PHP


In December 2023 I submitted my application for a OpenSats grant for the further development of the Nostr-PHP helper library. After some months I finally got the message that my application was approved... When I got the message I was really stoked and excited. It's a great form of appreciation for the work I had done so far and with this grant I get the opportunity to take the work to another higher level. So please check out the work done for so far:
* [https://nostr-php.dev](https://nostr-php.dev)
* [https://github.com/nostrver-se/nostr-php](https://github.com/nostrver-se/nostr-php)
## Meeting Dries

One of my goosebumps moments I had in 2022 when I saw that the founder and tech lead of Drupal Dries Buytaert posted '[Nostr, love at first sight](https://dri.es/nostr-love-at-first-sight)' on his blog. These types of moments are very rare moment where two different worlds merge where I wouldn't expect it. Later on I noticed that Dries would come to the yearly Dutch Drupal event. For me this was a perfect opportunity to meet him in person and have some Nostr talks. I admire the work he is doing for Drupal and the community. I hope we can bridge Nostr stuff in some way to Drupal. In general this applies for any FOSS project out there.
[Here](https://sebastix.nl/blog/photodump-and-highlights-drupaljam-2024/) is my recap of that Drupal event.
## Attending Nostriga

A conference where history is made and written. I felt it immediately at the first sessions I attended. I will never forget the days I had at Nostriga. I don't have the words to describe what it brought to me.

I also pushed myself out of my comfort zone by giving a keynote called 'POSSE with Nostr - how we pivot away from API's with one of Nostr superpowers'. I'm not sure if this is something I would do again, but I've learned a lot from it.
You can find the presentation [here](https://nostriga.nostrver.se/). It is recorded, but I'm not sure if and when it gets published.
## Nostr billboard advertisement

This advertisment was shown on a billboard beside the [A58 highway in The Netherlands](https://www.google.nl/maps/@51.5544315,4.5607291,3a,75y,34.72h,93.02t/data=!3m6!1e1!3m4!1sdQv9nm3J9SdUQCD0caFR-g!2e0!7i16384!8i8192?coh=205409&entry=ttu) from September 2nd till September 16th 2024. You can find all the assets and more footage of the billboard ad here: [https://gitlab.com/sebastix-group/nostr/nostr-ads](https://gitlab.com/sebastix-group/nostr/nostr-ads). My goal was to set an example of how we could promote Nostr in more traditional ways and inspire others to do the same. In Brazil a fundraiser was achieved to do something similar there: [https://geyser.fund/project/nostrifybrazil](https://geyser.fund/project/nostrifybrazil).
## Volunteering at Nostr booths growNostr

This was such a great motivating experience. Attending as a volunteer at the Nostr booth during the Bitcoin Amsterdam 2024 conference. Please read my note with all the lessons I learned [here](https://nostrver.se/note/my-learned-nostr-lessons-nostr-booth-bitcoin-amsterdam-2024).
## The other stuff
* The Nostr related blog articles I wrote past year:
* [**Run a Nostr relay with your own policies**](https://sebastix.nl/blog/run-a-nostr-relay-with-your-own-policies/) (02-04-2024)
* [**Why social networks should be based on commons**](https://sebastix.nl/blog/why-social-networks-should-be-based-on-commons/) (03-01-2024)
* [**How could Drupal adopt Nostr?**](https://sebastix.nl/blog/how-could-drupal-adopt-nostr/) (30-12-2023)
* [**Nostr integration for CCHS.social**](https://sebastix.nl/blog/nostr-integration-for-cchs-social-drupal-cms/) (21-12-2023)
* [https://ccns.nostrver.se](https://ccns.nostrver.se)
CCNS stands for Community Curated Nostr Stuff. At the end of 2023 I started to build this project. I forked an existing Drupal project of mine (https://cchs.social) to create a link aggregation website inspired by stacker.news. At the beginning of 2024 I also joined the TopBuilder 2024 contest which was a productive period getting to know new people in the Bitcoin and Nostr space.
* [https://nuxstr.nostrver.se](https://nuxstr.nostrver.se)
PHP is not my only language I use to build stuff. As a fullstack webdeveloper I also work with Javascript. Many Nostr clients are made with Javascript frameworks or other more client-side focused tools. Vuejs is currently my Javascript framework I'm the most convenient with. With Vuejs I started to tinker around with Nuxt combined with NDK and so I created a starter template for Vue / Nuxt developers.
* [ZapLamp](nostr:npub1nfrsmpqln23ls7y3e4m29c22x3qaq9wmmr7zkfcttty2nk2kd6zs9re52s)
This is a neat DIY package from LNbits. Powered by an Arduino ESP32 dev board it was running a 24/7 livestream on zap.stream at my office. It flashes when you send a zap to the npub of the ZapLamp.
* [https://nosto.re](https://nosto.re)
Since the beginning when the Blossom spec was published by @hzrd49 and @StuartBowman I immediately took the opportunity to tinker with it. I'm also running a relay for transmitting Blossom Nostr events `wss://relay.nosto.re`.
* [Relays I maintain](https://nostrver.se/note/relays-i-maintain)
I really enjoy to tinker with different relays implementations. Relays are the fundamental base layer to let Nostr work.
I'm still sharing my contributions on [https://nostrver.se/](https://nostrver.se/) where I publish my weekly Nostr related stuff I worked on. This website is built with Drupal where I use the Nostr Simple Publish and Nostr long-form content NIP-23 modules to crosspost the notes and long-form content to the Nostr network (like this piece of content you're reading).
## The Nostr is the people
Just like the web, the web is people: [https://www.youtube.com/watch?v=WCgvkslCzTo](https://www.youtube.com/watch?v=WCgvkslCzTo)
> the people on nostr are some of the smartest and coolest i’ve ever got to know. who cares if it doesn’t take over the world. It’s done more than i could ever ask for. - [@jb55](nostr:note1fsfqja9kkvzuhe5yckff3gkkeqe7upxqljg2g4nkjzp5u9y7t25qx43uch)
Here are some Nostriches who I'm happy to have met and who influenced my journey in Nostr in a positive way.
* Jurjen
* Bitpopart
* Arjen
* Jeroen
* Alex Gleason
* Arnold Lubach
* Nathan Day
* Constant
* fiatjaf
* Sync
## Coming year
Generally I will continue doing what I've done last year. Besides the time I spent on Nostr stuff, I'm also very busy with Drupal related work for my customers. I hope I can get the opportunity to work on a paid client project related to Nostr. It will be even better when I can combine my Drupal expertise with Nostr for projects paid by customers.
### Building a new Nostr application
When I look at my Nostr backlog where I just put everything in with ideas and notes, there are quite some interesting concepts there for building new Nostr applications. Filtering out, I think these three are the most exciting ones:
* nEcho, a micro app for optimizing your reach via Nostr (NIP-65)
* Nostrides.cc platform where you can share Nostr activity events (NIP-113)
* A child-friendly video web app with parent-curated content (NIP-71)
### Nostr & Drupal
When working out a new idea for a Nostr client, I'm trying to combine my expertises into one solution. That's why I also build and maintain some Nostr contrib modules for Drupal.
* [Nostr Simple Publish](https://www.drupal.org/project/nostr_simple_publish)
Drupal module to cross-post notes from Drupal to Nostr
* [Nostr long-form content NIP-23](https://www.drupal.org/project/nostr_content_nip23)
Drupal module to cross-post Markdown formatted content from Drupal to Nostr
* [Nostr internet identifier NIP-05](https://www.drupal.org/project/nostr_id_nip05)
Drupal module to setup Nostr internet identifier addresses with Drupal.
* [Nostr NDK](https://drupal.org/project/nostr_dev_kit)
Includes the Javascript library Nostr Dev Kit (NDK) in a Drupal project.
One of my (very) ambitious goals is to build a Drupal powered Nostr (website) package with the following main features:
* Able to login into Drupal with your Nostr keypair
* Cross-post content to the Nostr network
* Fetch your Nostr content from the Nostr content
* Serve as a content management system (CMS) for your Nostr events
* Serve as a framework to build a hybrid Nostr web application
* Run and maintain a Nostr relay with custom policies
* Usable as a feature rich progressive web app
* Use it as a remote signer
These are just some random ideas as my Nostr + Drupal backlog is way longer than this.
### Nostr-PHP
With all the newly added and continues being updated NIPs in the protocol, this helper library will never be finished. As the sole maintainer of this library I would like to invite others to join as a maintainer or just be a contributor to the library. PHP is big on the web, but there are not many PHP developers active yet using Nostr. Also PHP as a programming language is really pushing forward keeping up with the latest innovations.
### Grow Nostr outside the Bitcoin community
We are working out a submission to host a Nostr stand at FOSDEM 2025. If approved, it will be the first time (as far as I know) that Nostr could be present at a conference outside the context of Bitcoin. The audience at FOSDEM is mostly technical oriented, so I'm really curious what type of feedback we will receive.
Let's finish this article with some random Nostr photos from last year. Cheers!






-

@ 3f770d65:7a745b24
2024-10-29 17:38:20
**Amber**
[Amber](https://github.com/greenart7c3/Amber) is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications.
<img src="https://cdn.satellite.earth/b42b649a16b8f51b48f482e304135ad325ec89386b5614433334431985d4d60d.jpg">
Amber is supported by a growing list of apps, including [Amethyst](https://www.amethyst.social/), [0xChat](https://0xchat.com/#/), [Voyage](https://github.com/dluvian/voyage), [Fountain](https://fountain.fm/), and [Pokey](https://github.com/KoalaSat/pokey), as well as any web application that supports NIP-46 NSEC bunkers, such as [Nostr Nests](https://nostrnests.com), [Coracle](https://coracle.social), [Nostrudel](https://nostrudel.ninja), and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms.
<img src="https://cdn.satellite.earth/5b5d4fb9925fabb0005eafa291c47c33778840438438679dfad5662a00644c90.jpg">
Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's [GitHub](https://github.com/greenart7c3/Amber) page, via [Obtainium ](https://github.com/ImranR98/Obtainium)or Zap.store.
To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com.
<img src="https://cdn.satellite.earth/ca2156bfa084ee16dceea0739e671dd65c5f8d92d0688e6e59cc97faac199c3b.jpg">
---
**Citrine**
[Citrine](https://github.com/greenart7c3/Citrine) is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control.
<img src="https://cdn.satellite.earth/46bbc10ca2efb3ca430fcb07ec3fe6629efd7e065ac9740d6079e62296e39273.jpg">
With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality.
Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration.
<img src="https://cdn.satellite.earth/6ea01b68009b291770d5b11314ccb3d7ba05fe25cb783e6e1ea977bb21d55c09.jpg">
---
**Pokey**
[Pokey](https://github.com/KoalaSat/pokey) for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device.
<img src="https://cdn.satellite.earth/62ec76cc36254176e63f97f646a33e2c7abd32e14226351fa0dd8684177b50a2.jpg">
Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem.
---
**Zap.store**
[Zap.store](https://github.com/zapstore/zapstore/) is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency.
<img src="https://cdn.satellite.earth/fd162229a404b317306916ae9f320a7280682431e933795f708d480e15affa23.jpg">
Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing [Zap.store](https://github.com/zapstore/zapstore/) on your favorite Android device, and install all of the applications mentioned above.
---
Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems.
-

@ 4ba8e86d:89d32de4
2024-10-22 23:20:59
Usar um gerenciador de senhas pode resolver vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Com o uso de um gerenciador de senhas, o usuário pode criar senhas fortes e únicas para cada conta, sem precisar se preocupar em lembrar de todas elas. Além disso,um gerenciador de senhas pode ajudar a simplificar o processo de login, economizando tempo e reduzindo a frustração.
O KeepassDX é uma versão do software de gerenciamento de senhas Keepass, desenvolvido originalmente por Dominik Reichl em 2003. O Keepass é um software gratuito e de código aberto para desktops, que permite que os usuários armazenem suas senhas em um banco de dados seguro, criptografado com algoritmos avançados. Em 2017, o desenvolvedor alemão Brian Pellmann criou o KeepassDX como uma versão para dispositivos móveis, com o objetivo de tornar mais fácil para os usuários gerenciarem suas senhas em smartphones e tablets.
O KeepassDX foi criado a partir do código-fonte do Keepass e foi projetado para ser fácil de usar, seguro e personalizável. Pellmann adicionou várias funcionalidades novas ao KeepassDX, incluindo a capacidade de importar senhas de outros gerenciadores de senhas, a organização de senhas em categorias e a compatibilidade com serviços de armazenamento em nuvem para sincronização entre dispositivos.
Algumas das funcionalidades do KeepassDX incluem a criação de senhas fortes e únicas, preenchimento automático de senhas, autenticação de dois fatores e organização de senhas por categorias. O KeepassDX também oferece uma ferramenta para importação de senhas de outros gerenciadores de senhas, o que torna a transição para o uso do KeepassDX mais fácil.
Passo a passo instalação do aplicativo KeepassDX:
1. Baixe e instale o KeepassDX em seu dispositivo móvel
https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free
2. Clique em [CRIAR NOVO BANCO DE DADOS]
3. Selecione o local do arquivo no meu caso é " transferência "
Semelhante ao KeePassXC, o KeePassDX suporta o formato de banco de dados .kbdx (por exemplo, Passwords.kdbx) para armazenar senhas de contas importantes. Você deve salvar este arquivo em um local de fácil acesso para você, mas difícil de encontrar para outras pessoas que você não deseja visualizar as informações. Em particular, evite salvar seu arquivo de banco de dados em um serviço de armazenamento online, conectado às suas contas, pois pode ser acessado por outras pessoas.
4. Digite um nome para seu banco de dados
Neste exemplo, " urso " nosso banco de dados como "urso.kdbx"; você pode escolher um nome de sua preferência. Você pode usar um nome que disfarce o arquivo e o torne menos óbvio para invasores que podem tentar acessar seu telefone e exigir que você desbloqueie o banco de dados.
Também é possível alterar a "extensão" no final do nome do arquivo. Por exemplo, você pode nomear o banco de dados de senhas "Revoltadeatlas.pdf" "primainterior.jpg " e o sistema operacional geralmente dará ao arquivo um ícone de "aparência normal". Lembre-se de que, se você der ao seu banco de dados de senhas um nome que não termine em ".kdbx", não poderá abrir o arquivo diretamente. Em vez disso, você terá que iniciar o KeePassDX primeiro e, em seguida, abrir seu banco de dados clicando no botão "Abrir banco de dados existente". Felizmente, o KeePassDX lembra o último banco de dados que você abriu, então você não terá que fazer isso com frequência.
https://github.com/Kunzisoft/KeePassDX
-

@ 460c25e6:ef85065c
2024-10-10 13:22:06
In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients:
- **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
- **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
- **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
- **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
**Super Clients**
- [amethyst](https://amethyst.social)
- [nostrudel](https://nostrudel.ninja)
- [coracle](https://coracle.social)
**Clients**
- [damus](https://damus.io) - twitter
- [primal](https://primal.net) - twitter
- [snort](https://snort.social) - twitter
- [gossip](https://github.com/mikedilger/gossip) - twitter
- [lume](https://lume.nu) - twitter
- [ditto](https://soapbox.pub/ditto/) - twitter
- [rabbit](https://rabbit.syusui.net) - twitter
- [freefrom](https://freefrom.space) - twitter
- [nos](https://nos.social) - twitter
- [flycat](https://flycat.club) - twitter
- [straylight](https://straylight.cafe) - twitter
- [nostter](https://nostter.app) - twitter
- [iris](https://iris.to) - twitter
- [nostur](https://nostur.com) - twitter
- [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter
- [yana](https://yana.do) - twitter
- [openvibe](https://openvibe.social) - twitter
- [freerse](https://freerse.com) - twitter
- [0xchat](https://0xchat.com) - chats
- [cornychat](https://cornychat.com) - chats
- [coop](https://github.com/lumehq/coop) - chats
- [nostrchat](https://nostrchat.io) - chats
- [blowater](https://blowater.deno.dev) - chats
- [habla](https://habla.news) - blogs
- [yakihonne](https://yakihonne.com) - blogs
- [highlighter](https://highlighter.com) - blogs
- [blogstack](https://blogstack.io) - blogs
- [stemstr](https://stemstr.app) - music
- [wavlake](https://wavlake.com) - music
- [fountain](https://fountain.fm) - podcasts
- [zap.stream](https://zap.stream) - live streaming
- [shopstr](https://shopstr.store) - marketplace
- [plebeian.market](https://plebeian.market) - marketplace
- [flotilla](https://flotilla.coracle.social) - communities
- [satellite](https://satellite.earth) - communities
- [zapddit](https://zapddit.com) - communities
- [nostr.kiwi](https://nostr.kiwi) - communities
- [hivetalk](https://hivetalk.org) - video calls
- [flare](https://flare.pub) - long-form videos
- [nostrnests](https://nostrnests.com) - audio spaces
- [wherostr](https://wherostr.social) - location
- [yondar](https://go.yondar.me) - location
- [stacker.news](https://stacker.news) - news
- [flockstr](https://flockstr.com) - events
- [nostrocket](https://nostrocket.org) - issue tracker
- [docstr](https://docstr.app) - docs
- [satshoot](https://satshoot.com) - freelance
- [wikifreedia](https://wikifreedia.xyz) - wiki
- [formstr](https://formstr.app) - forms
- [chesstr](https://chesstr.pages.dev) - chess
- [memestr](https://memestr.app) - meme feed
- [npub.cash](https://npub.cash) - wallet
- [npub.pro](https://npub.pro) - websites
- [gitworkshop](https://gitworkshop.dev) - dev tools
- [onosendai](https://onosendai.tech) - metaverse
- [degmods](https://degmods.com) - games
- [turdsoup](https://turdsoup.com) - prompts
**Mini Clients**
- [amber](https://github.com/greenart7c3/Amber) - signer
- [alby](https://getalby.com) - signer
- [nos2x](https://github.com/fiatjaf/nos2x) - signer
- [nsec.app](https://nsec.app) - signer
- [keys.band](https://keys.band) - signer
- [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer
- [nokakoi](https://nokakoi.com) - anon
- [zap.cooking](https://zap.cooking) - recipes
- [anonostr](https://anonostr.com) - anon
- [getwired](https://getwired.app) - anon
- [lowent](https://lowent.xyz) - anon
- [creatr](https://creatr.nostr.wine) - exclusive content
- [lightning.video](https://lightning.video) - exclusive content
- [zaplinks](https://zaplinks.lol/slides) - slides
- [listr](https://listr.lol) - lists
- [zap.store](https://zap.store) - app store
- [badges.page](https://badges.page) - badges
- [oddbean](https://oddbean.com) - news
- [dtan](https://dtan.xyz) - torrents
- [nosta](https://nosta.me) - user pages
- [pinstr](https://pinstr.app) - pinterest
- [pollerama](https://pollerama.fun) - polls
- [swarmstr](https://swarmstr.com) - trending
- [nostrapp](https://nostrapp.link) - apps manager
- [noogle](https://noogle.lol) - search
- [ostrich.work](https://ostrich.work) - job postings
- [emojito](https://emojito.meme) - emoji manager
- [nostree](https://nostree.me) - links
- [citrine](https://github.com/greenart7c3/citrine) - local relay
- [joinstr](https://joinstr.xyz) - coinjoins
- [heya](https://heya.fund) - crowdfunding
- [zapplepay](https://zapplepay.com) - zaps
- [nosbin](https://nosbin.com) - clipboard
- [shipyard](https://shipyard.pub) - scheduler
- [tunestr](https://tunestr.io) - live streams
- [filestr](https://filestr.vercel.app) - files
- [nostrcheck.me](https://nostrcheck.me/) - media hosting
- [sheetstr](https://sheetstr.amethyst.social) - spreadsheets
- [crafters](https://crafters.amethyst.social) - curriculum vitae
**Micro Clients**
- [w3](https://w3.do) - url shortener
- [nosdrive](https://nosdrive.app) - backups
- [zaplife](https://zaplife.lol) - zaps dashboard
- [zapper.fun](https://zapper.fun) - payments
- [nostrends](https://nostrends.vercel.app) - trends
- [zephyr](https://zephyr.coracle.social) - trends
- [wavman](https://wavman.app) - music player
- [nostrrr](https://nostrrr.com) - relay info
- [nosdump](https://github.com/jiftechnify/nosdump) - relay info
- [notestack](https://notestack.com) - blogs
- [nostr.build](https://nostr.build) - media hosting
- [nostr.watch](https://nostr.watch) - relay info
- [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports
- [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions
- [snakestr](https://satoshipuzzles.github.io/Snakestr) - games
- [deletestr](https://zaplinks.lol/deletestr) - deletion requests
- [2048str](https://zaplinks.lol/2048str) - games
- [nostrqr](https://zaplinks.lol/nostrqr) - qr generator
- [notanostrclient](https://zaplinks.lol/notanostrclient) - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients.
-

@ 4ba8e86d:89d32de4
2024-10-07 13:37:38
O que é Cwtch?
Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch?
Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados
Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora.
Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve
Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos
A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade
Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão
Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico.
Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
1. Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
2. Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
- Selecione um nome de exibição
- Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte:
Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil
Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
1. Selecione o lápis ao lado do perfil que você deseja editar
2. Role para baixo até a parte inferior da tela.
3. Selecione "Exportar perfil"
4. Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
1. Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
2. Selecione um arquivo de perfil Cwtch exportado para importar
3. Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO
Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo.
As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais?
Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch?
A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch?
O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos.
https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-

@ bcbb3e40:a494e501
2024-09-24 17:23:00
|[](https://amzn.to/4e8iIzx)|
|:-:|
|[BLANCO, Carlos X. y COSTALES, Jose; _España: Historia de una demolición controlada_; Letras Inquietas, 2024](https://amzn.to/4e8iIzx)|
Ya hemos publicado varias reseñas de algunas obras del Profesor [**Carlos X. Blanco**](https://hiperbolajanus.com/firmas/carlos-x.-blanco/), cuyas temáticas nos resultan totalmente familiares, y con las que coincidimos en un buen número de sus análisis y críticas del mundo actual. Recordaremos, para aquellos que estén interesados en sus obras las reseñas de [_De Covadonga a la nación española: La hispanidad en clave spengleriana_](https://hiperbolajanus.com/posts/covadonga-nacion-espanola-carlos-x-blanco/) y [_Un imperio frente al caos_](https://hiperbolajanus.com/posts/resena-un-imperio-frente-al-caos-de/), además de algunas otras que podréis encontrar en nuestro blog. La obra del autor asturiano, en este caso en coautoría con **José Costales**, resulta muy clarificadora a la hora de analizar aspectos generales de la historia de España, cuestiones que tienen que ver con nuestra historia particular, y aquellos hechos que podemos considerar como más generales y fruto de un contexto y unas coyunturas que han marcado el destino de nuestra Patria en los últimos tiempos. Es por ese motivo, que así de entrada podemos distinguir dos bloques claramente diferenciados en esta obra: Un primer bloque que aborda nuestra historia peculiar, las características que definen el «hecho hispánico» y marcan nuestro devenir histórico; un segundo bloque en el que se señalan las amenazas y peligros que se yerguen frente a la España actual, aparentemente agonizante y desahuciada por la falta de soberanía y una serie de problemas graves y trascendentales que amenazan nuestra existencia.
Hay que destacar que el prólogo que precede a la obra en sí y le sirve como presentación corre a cargo del conocido abogado, jurista e historiador **Guillermo Rocafort**. En un breve pero certero escrito delinea los grandes problemas que atenazan a un Occidente decadente en plena crisis económica, geopolítica y de valores, embarcado en una deriva suicida que hace aguas y se ha vuelto insostenible. La crisis del capitalismo unipolar y globalista enfrenta el reto de la pujanza de los BRICS, con el resurgimiento de Rusia y el desarrollo y ascenso como superpotencia de China, junto a la formación de grandes bloques geopolíticos que definen la multipolaridad que, recientemente, [autores como Aleksandr Duguin vienen teorizando desde la escuela euroasiática](https://hiperbolajanus.com/libros/geopolitica-rusia-aleksandr-duguin/). Esta situación hace que la el mundo anglosajón y sus oligarquías plutocráticas comiencen a ver resquebrajada su hegemonía, con su sistema de dinero fiat y sus organizaciones pantalla, tales como la Unión Europea, o el desarrollo de su conocida como ideología _woke_ y todas las perversas y destructivas ingenierías sociales asociadas, así como la acción de la Agenda 2030.
|[](https://www.amazon.com/dp/B0892V95MV)|
|:-:|
|[DUGUIN, Aleksandr G.; _La geopolítica de Rusia: De la revolución rusa a Putin_; Hipérbola Janus, 2015](https://www.amazon.com/dp/B0892V95MV)|
En el caso particular de España los efectos de los más de 300 años de dominio anglosajón han tenido consecuencias especialmente perniciosas con la desindustrialización, la destrucción del sector primario, las ingenierías sociales asociadas a las ideologías de género, donde España ha servido como particular conejillo de indias, o nuestras permanentes renuncias en materia de política exterior, donde nos hemos visto obligados, por imposiciones venidas del otro lado del Atlántico, a renunciar a nuestra soberanía sobre el Sahara Occidental o a las permanentes y humillantes cesiones a Marruecos.
En el escrito de Introducción, los autores trazan una genealogía de los hechos, de las circunstancias que se hallan detrás de las razones del propio título de la obra, «Historia de una demolición controlada», en la que el papel de la angloesfera ha sido fundamental para la situación de debilidad, sometimiento y negación de nuestra propia historia que vivimos en la actualidad. Somos parte de una Europa sojuzgada que actúa a remolque de las políticas estadounidenses y anglosajonas, a través de la acción de la OTAN, donde no somos más que un agregado servil, actuando en defensa de los intereses geopolíticos del Imperio. Dentro de Europa, la UE define otro tipo de jerarquías internas, en las cuales el eje franco-alemán impone sus intereses a los países con economías menos desarrolladas del sur. Al mismo tiempo, también se advierten las importantes transformaciones que el régimen constitucional de 1978 ha experimentado en las últimas décadas, especialmente a partir de [**Zapatero**](https://hiperbolajanus.com/firmas/jose-luis-rodriguez-zapatero/), con el mayor sojuzgamiento de España a la Agenda globalista.
Todas estas circunstancias adversas, y también trágicas para nuestro destino, hacen necesario un análisis de la propia historia de España, de su gestación y de los atributos que han cimentado la idea de lo español o hispánico. La historia de España ha estado condicionada por su proximidad a África, lo cual ha tenido una importancia decisiva en su configuración final. Con la invasión musulmana del 711 se produjo un episodio de dislocación dentro de nuestra historia, que a partir de ese momento experimentó una situación de dualidad étnico-religiosa y comenzó un episodio transfigurador y de construcción del ideal hispánico que se había iniciado con el reino visigodo de Toledo, y que la Reconquista contribuyó a potenciar. En este sentido, la configuración étnica que resultó de la invasión árabe hizo que las zonas del Norte, donde se refugiaron los restos de la antigua nobleza visigoda derrotada, predominó el elemento germánico que se erigió como motor inicial del proceso de Reconquista, mientras que en otras latitudes del levante y el sur peninsular se produjo un proceso de africanización y semitización sobre las antiguas poblaciones hispanorromanas. Un norte cristiano, germanizado e indoeuropeo, equiparable al Norte de Europa, representado por la monarquía asturiana frente a un sur africanizado, sumido en un caos étnico y de enfrentamientos civiles era el resultado de la entidad andalusí.
El proceso de romanización afectó de manera desigual a los territorios peninsulares, y los pueblos de las regiones noroccidentales como astures, cántabros o vascones apenas se vieron afectados, conservando un importante sustrato indoeuropeo en contraste con las regiones más mediterráneas, ocupadas por los íberos, que ya poseían un modelo de civilización elevado y en conexión con las civilizaciones clásicas mediterráneas. Estos elementos ya aparecen claramente expuestos en la interpretación spengleriana que uno de nuestros autores, Carlos X Blanco, expone en [_De Covadonga a la nación española: La hispanidad en clave spengleriana_](https://amzn.to/3BSOIEX). Es el contraste entre una España atlántica, indoeuropea y germanizada frente a otra vertiente representada por la España mediterránea, levantina y romanizada. En la confluencia de ambos modelos tenemos la definición de las sucesivos siglos en los que se forja la Reconquista, en la que, según los autores, pasamos de una etapa inicial de predominio atlántico y noroccidental, con el Reino de Asturias, y posteriormente León, capitalizando el proceso de la Reconquista, mientras que posteriormente, será Castilla, que obedecerá al modelo mediterráneo, quien llevaría la batuta en el avance hacia el Sur y la hispanización de España, porque la invasión del 711 marca un proceso de deshispanización, una idea fundamental, también en nuestra opinión, que el avance de los reinos cristianos del Norte contribuirán a erosionar y finalmente, para nuestra fortuna, destruir por completo.
Como parte de la geopolítica hispánica y su relanzamiento como Patria común, es fundamental que España vuelva a resucitar el eje atlántico y noroccidental, propiamente asturiano, frente aquel castellano, para que recupere su primacía como eje en la reconstrucción de España y revertir así la agonía y rumbo errático que nos lleva hacia la destrucción total y la desaparición como nación histórica.
No obstante, si queremos refundar España a través de un verdadero proyecto nacional debemos ser realistas, y no dejarnos embelesar por los visiones sobreexcitados que representan el modelo Imperial de los Austrias o posteriores reverberaciones del mismo a través de construcciones ideales, sino que contemplando las actuales coyunturas, con el viraje hacia la multipolaridad que está experimentando el mundo actual, quizás estaríamos llamados, o al menos existe ese gran potencial, a liderar una suerte de hispanosfera con los antiguos países que fueron parte de la América española, frente a la anglosfera, que viene perjudicando nuestra soberanía y sometiéndonos, junto al resto de Europa, como una colonia.
Blanco y Costales nos ofrecen algunas directrices para esta reconstrucción, tales como la descentralización de los centros de poder, frente a todo modelo jacobino y liberal diríamos nosotros, como parte de un modelo confederal, que incluso podría apoyarse en la fundación de centros de poder en el continente americano. Asimismo, este modelo confederal, implicaría dotar de mayor poder y protagonismo a las regiones, [tal y como habría postulado uno de los grandes teóricos del tradicionalismo español, Don](https://hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/) [**Juan Vázquez de Mella**](https://hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/), frente al actual modelo balcanizador de las 17 taifas dirigidas por las oligarquías partitocráticas y corruptas del Régimen de 1978. En cuanto al modelo político requerido, este no es la monarquía, sino la república, por el descrédito de los Borbones y la trayectoria descendente y de decadencia que han venido marcando en su reinado desde hace más de 300 años. En cualquier caso, lo que este modelo debe aportar es cohesión interna y voluntad de integración en el modelo de mundo unipolar, que se viene gestando y estructurando bajo relaciones de poder, redes económicas, comerciales y de otro tipo, que deben garantizar esa capacidad de interconexión. Y, por supuesto, en coherencia con lo sostenido con anterioridad, nuestros autores proponen que el eje atlántico y noroccidental debe representar el motor y artífice de este nuevo ciclo histórico.
Desde el advenimiento de los Borbones a comienzos del siglo XVIII, el polo mediterráneo y africanizado ha venido tomando un protagonismo creciente, que vemos reflejado el el triunfo posterior, a lo largo del siglo XIX, del liberalismo con la destrucción del Imperio y el sometimiento de España y de su historia a los dominios de la leyenda negra, urdida por la anglosfera, y que tiende a presentarnos como el producto de una hibridación de pueblos afrosemitas y mahometanos, sin identidad, y como una especie de anomalía frente a la europeidad prototípica. Un discurso que, claro está, fue aceptado por el liberalismo español con la consecuente desvalorización y rechazo de los orígenes astur-godos de la monarquía hispánica y del proceso de Reconquista por parte de unas élites corruptas, antiespañolas y endófobas, que se sometieron ideológicamente a Francia y al mundo anglosajón. En un principio, esto sirvió para provocar fragmentar la unidad interna del Imperio Español y enajenar el catolicismo de la Hispanidad, y posteriormente, una vez destruida esa unidad, someter a estos países al [capitalismo depredador y esclavizarlos por la vía de la deuda](https://hiperbolajanus.com/posts/una-reflexion-sobre-el-capitalismo-y-la/). Paralelamente, y a través de la masonería, también se introdujeron ideas profundamente destructivas entre las élites liberales y traidoras, como son el laicismo, el separatismo y otras ideas disolventes que nos vienen desnaturalizando desde hace siglos.
La acción de este capitalismo destructivo y depravado, es la que nos ha convertido en un instrumento en manos de grandes cenáculos y organizaciones que forman parte de un entramado complejo y anónimo, desde donde se interviene permanentemente en nuestros asuntos imponiendo cambios profundos en las costumbres, tradiciones e identidad, empobreciéndonos y reduciéndonos a la más pura insignificancia.
Otro elemento a destacar, podríamos decir una de las grandes piedras angulares que definen la idiosincrasia de lo Hispánico, viene representado por el Catolicismo, que en el caso peninsular también revistió un carácter peculiar, especialmente en lo que respecta, una vez más, a los contrastes internos entre la zona atlántica-noroccidental y la mediterránea, así como con la propia realidad del reino visigodo, donde la Iglesia resultó ser muy autónoma, vertebrada a través de sus concilios. Con la irrupción de la contemporaneidad, este elemento, el católico, de vital importancia durante la Reconquista y a lo largo de toda nuestra historia, se ha visto disminuido, con la propia acción del liberalismo, y especialmente [desde la izquierda](https://hiperbolajanus.com/libros/izquierda-contra-pueblo-carlos-x-blanco/), y también desde sus propios centros de poder, desde el mismo Vaticano, a raíz de su famoso Concilio Vaticano II, abdicando en sus principios y doctrina frente al liberalismo y el mundo moderno.
En el primer párrafo hemos hablado de un primer bloque, que de algún modo vendría a hablarnos de nuestra historia, de la autorepresentación que tenemos de la misma, y los elementos basales que componen su estructura. Esta sería la primera parte del libro. Una segunda parte vendría comprendida por el análisis de otros elementos más externos que definen unas coyunturas internacionales muy características, las cuales forman parte, desgraciadamente, de nuestro presente actual.
Entre los principales elementos de análisis se encuentra la acción de la anglosfera y el sometimiento que experimenta España junto al resto de naciones del orbe europeo, especialmente occidental, bajo instituciones transnacionales como la OTAN o la UE, que lastran permanentemente nuestra soberanía y nos convierten en meros cipayos al servicio de los intereses de la anglosfera (Estados Unidos y Reino Unido) en contra de nuestros propios intereses. El ejemplo más significativo lo tenemos en Ucrania, donde la OTAN está librando una guerra contra Rusia en la que viene utilizando al pueblo ucraniano como ariete de sus intereses geopolíticos a costa de la destrucción del país, en un auténtico drama humano con la muerte de miles de jóvenes en el frente de batalla. La historia de la anglosfera viene siendo la misma desde siempre, en el que sus teóricos aliados vienen siendo humillados, con multitud de traiciones, y ataques de falsa bandera, la creación de grupos terroristas, promoción de golpes de Estado, compra y soborno de políticos con aquellos países que no se sometían a los intereses del Imperio anglosajón. La base de tal poder, en la que tal imperio basa su poder el capitalismo financiero y especulador, cuyas raíces se encuentran en el siglo XVII, y que sirve a unas élites globales que se sirve de los mecanismos tales como los procesos inflacionarios para empobrecer y someter a los pueblos, a los que desprecia e instrumentaliza al servicio de Agendas globalistas. Al mismo tiempo acaparan gran parte de la riqueza global, que mantienen oculta en paraísos fiscales y de la que se sirven para sufragar el tráfico de drogas o la financiación de grupos terroristas que protagonizan los atentados de falsa bandera a los que nos hemos referido.
|[](https://amzn.to/2sR7jMM)|
|:-:|
|[MUTTI, Claudio; _Democracia y talasocracia: Antología de ensayos geopolíticos_; Hipérbola Janus, 2017](https://amzn.to/2sR7jMM)|
El enorme y desproporcionado proceso de financiarización que padece la economía del Occidente sometido a la anglosfera ha tenido consecuencias funestas sobre el complejo productivo real, redundando en la desindustrialización y la decadencia general bajo las teorías del «decrecimiento». Desde la administración Bush, a comienzos de siglo, hemos asistido a una serie de guerras de agresión en las que se han destruido países como Irak, Libia o Afganistán con el objetivo de controlar los hidrocarburos y las rutas de transporte, una tendencia que se ha venido incrementado especialmente con la administración Biden , y anteriormente con la de Obama, con la creación de organizaciones terroristas como el ISIS y la desestabilización permanente en Oriente Próximo, y el creciente y peligroso papel del complejo militar industrial.
Pero el poder y hegemonía estadounidense están menguando a pasos agigantados con la emergencia de dos grandes potencias, como son Rusia y China, frente a las que la anglosfera ve amenazada su hegemonía económica, con la colonización comercial china y el resurgir del potencial ruso, frente al cual, como decíamos, libran una guerra con intermediarios a través de Ucrania. Al mismo tiempo, tenemos a los BRICS, liderados por Rusia y China, con países emergentes como Irán, la India o Brasil con el papel de potencias regionales. La guerra de Ucrania solamente ha conseguido revigorizar a Rusia, alejarla de Europa y reforzar su alianza con China, mientras que los grandes perjudicados son Ucrania, que quedará en manos de grandes fondos de inversión como Blackrock ante una pretendida reconstrucción del país y las multinacionales que participarán en su reconstrucción, quedando en manos del globalismo. Europa es la otra gran perdedora, empobrecida y sumisa ante los designios del Imperio yanqui, al que rinde pleitesía a través de sus gobernantes, que no son más que títeres. Ante la inevitable pérdida de soberanía en el mundo, la anglosfera también pretende llevar la guerra a Asia contra China, viendo la derrota que está sufriendo en todos los frentes.
En el contexto de los intereses hispánicos, la anglosfera siempre ha representado una amenaza y un elemento especialmente dañino, responsable de la disolución del Imperio español con la introducción de las ideas liberales y masónicas entre las élites locales hispanoamericanas, practicando formas aberrantes de neocolonialismo sobre estos territorios una vez independizados, y siendo considerados como el patio trasero de Estados Unidos, quien ha practicado una política especialmente perniciosa y de desestabilización en todos estos territorios en vistas a coartar cualquier forma de desarrollo positivo.
Otro de los grandes problemas que se abordan en el libro es la amenaza que representa el enemigo del sur, Marruecos, para la integridad territorial española, sobre Ceuta, Melilla y las Islas Canarias, con el apoyo incondicional de países como Estados Unidos, Francia o Israel, tras las primeras y humillantes concesiones que ya se produjeron en 1975 con **Juan Carlos I** con el Sahara Occidental, y las posteriores, bajo mandato de [**Sánchez**](https://hiperbolajanus.com/firmas/pedro-sanchez/). Al mismo tiempo Estados Unidos e Israel especialmente, participan activamente en el rearme y fortalecimiento del reino moro, que ha desarrollado una política expansionista y agresiva contra los países vecinos. Para ello también se sirve de los lobbies marroquíes que actúan en el propio seno de la UE y dentro de España, que se sirven de las políticas cobardes y traidoras de sus políticos adheridos al Régimen del 78. Las consecuencias no se han dejado de notar en la destrucción y progresivo debilitamiento de nuestro sector primario en detrimento de los productos del país norteafricano, que entran sin ningún tipo de control en nuestro territorio, sin cumplir los requisitos mínimos a nivel fitosanitario. La ineptitud, servilismo y cobardía del actual Régimen hacia poderes globalistas y transnacionales, hacia la anglosfera, nos condenan a seguir un guión sin ninguna autonomía ni poder de decisión.
Otro de los ámbitos importantes que contempla el libro, lo encontramos en la ya mencionada Unión Europea, que no deja de ser otro instrumento de dominación y supeditación a los intereses de la anglosfera, y donde se reúnen los representantes de los grandes poderes fácticos a través de plutócratas, banqueros y poderes económicos y financieros transnacionales. Esta institución ha ido sustrayendo progresivamente el poder de las naciones que la integran con una comisión europea con atribuciones y poderes omnímodos para dictar normas y con una presidenta, **Ursula Von der Leyen**, metida en multitud de casos de corrupción, [entre los que destacan aquellos vinculados a la _Plandemia_ de 2020 y las falsas vacunas.](https://hiperbolajanus.com/posts/presentacion-despues-virus-boris-nad/) Todo ello sin contar los protocolos criminales que se impusieron durante ese periodo, la represión policial y el cercenamiento de derechos y libertades con la presión absolutamente criminal sobre los que decidieron no «vacunarse» con el producto experimental del que nadie se hacía responsable y sobre el cual reinaba toda opacidad informativa. Desde esas fechas hasta el presente los fondos de inversión globalistas, como Blackrock o Vanguard entre otros, se sirvieron de la crisis generada para enriquecerse y acaparar la compra de todo lo comprable como instrumento de las élites plutocráticas mundiales y sus ansias de dominio global.
|[](https://amzn.to/3U8QydC)|
|:-:|
|[NAD, Boris; _Después del virus: El renacimiento de un mundo multipolar_; Hipérbola Janus, 2022](https://amzn.to/3U8QydC)|
La Unión Europea no ha dejado de ser, como ya hemos dicho, parte de las organizaciones que la anglosfera, y particularmente el gobierno yanqui, ha utilizado para dominarnos y debilitarnos desde 1945, y en nuestros días también a través de la Agenda 2030, a partir de la cual pretenden reducir Europa a la nada, desindustrializando y destruyendo el sector primario, algo especialmente dramático en el caso español. La UE también nos habla de la implantación de la divisa digital con todos los peligros que esta entraña como, por ejemplo, la posibilidad de que se programe su uso y sirva como herramienta de control social para monitorear y controlar nuestras gestiones, la caducidad del dinero o limitar la compra de productos en función de la llamada «huella de carbono». A ello debemos añadir el proceso inflacionario que venimos sufriendo desde el 2020 en una farsa deliberadamente provocada por los bancos centrales (la Reserva Federal y el BCE) con la impresión masiva de dinero.
En el plano social la UE no ha dejado de implementar el modelo del caos multicultural que viene ocasionando estragos en buena parte de la Europa occidental a través del uso de recursos maquiavélicos y diferentes ingenierías sociales que se apoyan en los _mass media_. Esto ha generado una distopía social con la introducción de ideas aberrantes como las asociadas a las ideologías de género, con la castración y hormonación de niños o el odio radical y enfermizo hacia los hombres blancos heterosexuales, [convertidos en potenciales violadores con la ideología feminista institucionalizada](https://hiperbolajanus.com/posts/la-naturaleza-femenina-y-los-roles/). Y todo esto con el contraste que supone la llegada masiva de «inmigrantes» de países de África, por ejemplo, donde predominan sociedades patriarcales, en muchos casos musulmanas, cuyas tradiciones y visión de la vida chocan con las ingenierías sociales de la élite globalista.
Carlos Blanco y José Costales plantean una refundación de la Unión Europea bajo otros parámetros más democráticos y bajo unos organismos reguladores que puedan controlar los lobbies, las multinacionales y a los plutócratas y frente a los abusos de poder del eje franco-alemán. Una Europa de los pueblos, de naciones soberanas al servicio del interés ciudadano frente a las oligarquías y el gobierno mundial.
Otro de los capítulos está dedicado al papel de las oligarquías y las élites, donde reaparecen algunos de los temas ya tratados, y en los que se viene a destacar la acción perniciosa y destructiva de estos poderes anónimos que actúan a través de organizaciones pantalla y agendas planificadas perpetradas desde el llamado Occidente, bajo las premisas de una ideología misántropa y deshumanizada que es asumida por los gobiernos traidores de las naciones de la Europa occidental. Todas estas políticas se presentan bajo aspectos devastadores en el sector alimentario, con la ya referida demolición del sector primario con catastróficas consecuencias en un futuro próximo, o la fabricación de guerras, conflictos sociales y polarización de la población, junto a falsas banderas y grupos terroristas creados y financiados desde el propio Occidente. En este sentido tenemos multitud de ejemplos de desestabilización en torno a la red Gladio durante los años 70 (los famosos años del plomo en Italia) o con el tráfico de drogas, que ha servido para generar conflictividad social en Ecuador en los últimos tiempos tras quedar cortadas las redes del comercio de heroína procedente de Afganistán.
En los últimos capítulos del libro también se aborda el separatismo y la balcanización de España, un fenómeno propiamente moderno y que aparece indefectiblemente ligado al advenimiento de los liberales a lo largo del siglo XIX. A raíz de una serie de conflictos de origen dinástico, se generó una antítesis irreconciliable entre dos sistemas de gobierno, el propiamente moderno representado por el liberalismo y encarnado en la futura reina **Isabel II** y el tradicionalismo representado por los carlistas y encarnado, inicialmente, por **Carlos María Isidro** (**Carlos V**). Se libraron tres guerras devastadoras entre liberales y carlistas a lo largo del siglo XIX, en las que se dirimieron dos modelos, uno centralista (liberal) frente a otro descentralizado (carlista) con el respeto a las instituciones locales y regionales, a los Fueros. cuyas prerrogativas y vigencia se fueron perdiendo a lo largo del siglo. El siglo XIX tuvo unas consecuencias desastrosas para España, con la liquidación del Imperio y su debilitamiento en todos los ámbitos. Es a finales de susodicha centuria cuando nacen los movimientos separatistas, especialmente en [Vascongadas](https://hiperbolajanus.com/posts/territorio-caracter-orbe-hispanico-1/#vascongadas-tierra-genuinamente-hisp%C3%A1nica) y [Cataluña](https://hiperbolajanus.com/posts/territorio-caracter-orbe-hispanico-2/#catalu%C3%B1a-el-triunfo-temprano-de-la-burgues%C3%ADa), que irá cristalizando y gestándose a través de un discurso identitario cada vez más radical y antiespañol. [La decadencia política e institucional que representa el actual Régimen Constitucional del 78](https://hiperbolajanus.com/posts/espana-constitucion-idiota/), ha convertido a las formaciones políticas separatistas en los árbitros del sistema, ejerciendo de bisagras en la formación de los gobiernos centrales, con episodios vergonzantes y humillantes como los asociados a la Ley de Amnistía del PSOE en los últimos tiempos. Al mismo tiempo, el separatismo ha asumido los mismos mantras ideológicos a través de sus oligarquías regionales, que el resto de los integrantes del régimen partitocrático en relación a las políticas globalistas impulsadas desde la UE o la siniestra Agenda 2030, a la que son plenamente funcionales. En este sentido el mundo anglosajón, interesado en contribuir a la destrucción interna y fragmentación territorial de España, a través de complejas redes de financiación, como las desplegadas por [**Soros**](https://hiperbolajanus.com/firmas/george-soros/) y su _Open Society_ o las desplegadas, a través de organizaciones pantalla, por los servicios secretos ingleses y estadounidenses. Estos poderes ya tienen experiencia en esta materia, como demuestran los resultados de la Guerra de Yugoslavia durante los años 90, de la que resultó la fragmentación de su territorio en pequeñas repúblicas.
----
---
**Artículo original**: Hipérbola Janus, [_Reseña: «España: Historia de una demolición controlada», de José Costales y Carlos X Blanco_](https://www.hiperbolajanus.com/posts/resena-espana-demolicion-controlada-carlos-blanco/) [**(TOR)**](http://hiperbolam7t46pbl2fiqzaarcmw6injdru4nh2pwuhrkoub3263mpad.onion/posts/resena-espana-demolicion-controlada-carlos-blanco/), 24/Sep/2024
-

@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53
I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous.
In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism.
On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important.
That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played.
Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end.
The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism:
I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.
In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore.
The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true.
The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good.
In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.”
I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
-

@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05
It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint.
I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point.
I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog.
In line with that thinking, I made two parlays this week:
1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense.
2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout.
Are there any odds you're excited about (doesn't have to be football)?
originally posted at https://stacker.news/items/679894
-

@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。
怎么自建ntfy,后面再写。
---
2024年08月13日更新:
> 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
---
### 准备工具
- Ntfy服务
- Google Script
- Google Sheets
### 操作步骤
1. 在Ntfy后台账号,设置访问令牌。
[](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌")
2. 添加订阅主题。
[](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题")
2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图:
[](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id")
3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript
function checkEmail() {
var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID
var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据
cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread');
Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) {
var threadId = thread.getId();
if (!sentEmails.includes(threadId)) {
thread.getMessages().forEach(sendNtfyNotification);
recordSentEmail(sheet, threadId);
}
});
}
function sendNtfyNotification(email) {
if (!email) {
Logger.log("Email object is undefined or null.");
return;
}
var message = `发件人: ${email.getFrom() || "未知发件人"}
主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail";
var options = {
method: "post",
payload: message,
headers: {
Authorization: "Bearer Ntfy的令牌"
},
muteHttpExceptions: true
};
try {
var response = UrlFetchApp.fetch(url, options);
Logger.log("Response: " + response.getContentText());
} catch (e) {
Logger.log("Error: " + e.message);
}
}
function getSentEmails(sheet) {
var data = sheet.getDataRange().getValues();
return data.map(row => row[0]); // Assuming email IDs are stored in the first column
}
function recordSentEmail(sheet, threadId) {
sheet.appendRow([threadId, new Date()]);
}
function cleanOldData(sheet, minutes) {
var now = new Date();
var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues();
var rowsToDelete = [];
data.forEach(function(row, index) {
var date = new Date(row[1]); // 假设日期保存在第二列
if (date < thresholdDate) {
rowsToDelete.push(index + 1); // 存储要删除的行号
}
});
// 逆序删除(从最后一行开始删除,以避免行号改变)
rowsToDelete.reverse().forEach(function(row) {
sheet.deleteRow(row);
});
}
```
4.Goole Script需要添加gmail服务,如图:
[](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务")
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:
[](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器")
[](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细")
### 结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
效果预览:
[](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览")
-

@ 6ad3e2a3:c90b7740
2024-09-10 08:37:04
While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions:
**1. Separate passengers from their bags as early as possible.**
The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences:
a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes.
b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day.
c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five.
d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier.
e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable.
The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children.
To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc.
There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.)
Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane.
**2. Eliminate Security Lines**
Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement.
a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use.
Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious.
b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side.
Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side.
**3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.**
Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal.
**4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.**
There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done.
Here are some other suggestions:
1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up.
2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges.
3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease.
4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them.
I can anticipate some objections to these ideas, and I’ll address each one in turn.
**1. This would cost too much money.**
My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.)
**2. It’s too much of a security risk.**
Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end.
Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle.
**3. I like free carry-ons because it saves me from waiting at the baggage claim.**
Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse.
The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist.
*\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.*
*\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.*
-

@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48
I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote:
*What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.*
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-

@ 6bae33c8:607272e8
2024-09-10 07:50:12
I went 1-3 in my NFFC leagues for two reasons: (1) Christian McCaffrey failed to score 17 points (because he was inactive), and I failed to bid enough on Jordan Mason because at the time of the FAAB last week, the Niners were flat-out lying about his likelihood of playing and like an idiot I believed them; and (2) I sat Mason in another league at the last minute for Jaleel McLaughlin because Fantasy Pros (that scourge of a site I swear off every year) had Mason not just lower, but absolutely buried in its RB rankings. I would have ignored a close call between the two, but I thought if he’s this low, the market must place a high likelihood on McCaffrey playing, and I don’t want to take a zero. This is the problem with being lazy and outsourcing your research to a bunch of midwits with misaligned incentives. I really should have delved deeply into all the McCaffrey reports and made my own assessment.
The problem with sites like Fantasy Pros is the grading system is different than the fantasy game itself. I imagine you’d get dinged hard for ranking Mason high if McCaffrey plays, and so it’s safer to rank him low. Moreover, one thing the fantasy industry is really bad at is pricing in that kind of risk. If everyone’s playing the market is pretty good at evaluating opportunity, per-play production and hence output, but if someone is 50/50 to get opportunities at all, they can’t handle it very well. Obviously Mason was a good bet to go for 20 points if McCaffrey were scratched, and so he should have been projected for 14 if it were 50/50 (he’d get *some* points even if McCaffrey played), but that we was projected for less than five (IIRC) made me think it was like 80/20.
But I knew it was a *very* bad sign Monday morning (after it was too late to pivot) when McCaffrey was still not deemed definite — it’s not like he got hurt last week, but he’s had a full month to heal. (Actually maybe the Achilles was last week, but because injury reporting sucks and teams lie, it’s impossible to know the real reason he missed the game. If it’s still the calf, all bets are off because if he’s not back in a month, five weeks won’t magically heal him.)
In any event, I’m glad I have Mason in two NFFC leagues, and I went all-in to get him (and I used him) in my RotoWire Dynasty one at least. But I should have been 3-1 if I had used my brain, and am instead 1-3, the win thankfully in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7).
- The 40-minute edited version of the game for God knows what reason flashed the final score (32-19) briefly after I hit play. So it spoiled the game for me, and the whole time I was just trying to figure out how they got to that number, realizing probably Jake Moody went bananas for some people, and he did.
- I love that Allen Lazard got the TDs and not Garrett Wilson. Sometimes schadenfreude is all you got. I don’t think Lazard is a priority pickup, but the Jets tree is pretty thin, and Rodgers knows and apparently still trusts him.
- Aaron Rodgers looked good to me, like his old self. He threw accurate passes, had a few drops, and the pick was bad luck. No idea why Mike Williams was ignored though.
- Breece Hall got all the work until garbage time. No surprise, but he still looks like a top-five pick despite the fumble and poor per-play output.
- Jordan Mason ran hard, looked a bit like Isiah Pacheco out there. If McCaffrey is out, that’s how I’d value him.
- Deebo Samuel benefits a little (eight carries) with McCaffrey out. Just has a slightly bigger role in the ground game.
- Brock Purdy played well, but didn’t have to do much.
- You have to love that Juaun Jennings led the 49ers in receiving yards and Kyle Juszczyk was third when you have no part of the 49ers passing game. George Kittle and Brandon Aiyuk will get theirs eventually, but you just can’t count on volume for either one.
-

@ 129f5189:3a441803
2024-09-09 23:28:41
Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration.
Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed.
https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg
This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad.
https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg
Reorienting U.S. Foreign Policy: Proposals for a Conservative Future
In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage.
Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed.
https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg
History and Structure of the State Department
Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner).
The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries).
https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg
Political Leadership and Bureaucratic Support
To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner).
Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies.
https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg
Global Threats to the U.S.
The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea.
🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner).
Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner).
https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg
🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government.
"The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner).
https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg
🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people.
"The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner).
https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg
🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests.
"The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?"
https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg
One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner).
This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines.
Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner).
It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement.
https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg
A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner).
From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives.
https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg
Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO.
https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg
🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power.
"The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner).
https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg
Detailed Policy Proposals
Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized.
"The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner).
https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg
Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities.
She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner).
https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg
Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem.
"Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis.
https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg
Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada.
"The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region.
https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg
Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India.
"Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner).
https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg
Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities.
"Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying.
https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg
Relations with Europe and Asia
Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom.
https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg
Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner).
https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg
International Organizations
Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner).
She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner).
https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg
Conclusion
Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president.
With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom.
https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
-

@ 129f5189:3a441803
2024-09-09 23:23:45
Project 2025, outlined in the "Mandate for Leadership" document by the Heritage Foundation, is a crucial guide for the next Republican administration. Crafted by conservative intellectuals from major American think tanks, this plan promises to have significant influence on a potential Donald Trump administration, even if he does not formally acknowledge it as his government plan.
https://image.nostr.build/443d69c16dc32659be2353ce48d170d397e0ee682ffc3c4108df3047fd54472d.jpg
This document presents proposals to depoliticize government agencies, increase efficiency, and reduce costs, aiming to dismantle the Deep State and combat the Woke agenda associated with the Democratic Party.
https://image.nostr.build/06de3f0de3d48e086f47d0418d30e32cbfe0d88f452a93706987b7394458952d.jpg
Dissolution of the DHS and Redistribution of Functions
The Department of Homeland Security (DHS) was established in 2002 in response to the September 11 attacks, with the goal of consolidating various agencies responsible for domestic security under a single command. The DHS includes agencies such as FEMA, TSA, ICE, and CISA.
Project 2025's proposal to dissolve the DHS and redistribute its functions to other agencies aims to address excessive bureaucracy and a lack of cohesion, arguing that centralization has failed to effectively integrate its diverse missions.
https://image.nostr.build/ffca8d274914b725183b8fb19162c1b63f4d987c24e598f2eca88901d4a1a43c.jpg
Impact on the Democratic Deep State:
The dissolution of the DHS would pose a significant threat to the Democratic Deep State, as it would redistribute the power concentrated in a single entity across multiple other agencies, making it more difficult to politicize and centralize control over domestic security operations.
This decentralization would reduce the ability to use the DHS as a political tool against opponents.
https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg
Primary Recommendations
Combining Immigration Agencies:
Merge U.S. Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), U.S. Citizenship and Immigration Services (USCIS), the Office of Refugee Resettlement (ORR) of the Department of Health and Human Services (HHS), and the Executive Office for Immigration Review (EOIR) of the Department of Justice (DOJ) into a new autonomous border and immigration agency.
https://image.nostr.build/58eef4f2eca0ed2400261ec878c1dba2ca4bca519a16751b1fb7abd45da2906b.jpg
Privatization of the TSA:
Privatize the Transportation Security Administration (TSA), drawing inspiration from Canadian and European models, to reduce costs and improve service for travelers.
Division of the Secret Service (USSS):
The U.S. Secret Service (USSS), responsible for protecting national leaders and investigating financial crimes, would be divided.
The protective element would be transferred to the Department of Justice (DOJ), while the financial investigations element would be moved to the Department of the Treasury.
https://image.nostr.build/0a065cdbf158db4bc17b9aacd4af5a94029004caaa152eebf2c557042b08a641.jpg
Impact on the Democratic Deep State:
The division of the USSS would significantly weaken centralized control over protection and financial investigations, making it more difficult to use these functions for political purposes.
Transferring the protective element to the DOJ and the financial investigations element to the Treasury would complicate efforts for any group or party to manipulate these crucial government functions for partisan objectives.
https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg
Cybersecurity and Infrastructure Security Agency (CISA)
Established in 2018, CISA is a federal agency responsible for protecting the U.S. critical infrastructure from cyber threats.
CISA's mandate includes ensuring cybersecurity for sectors such as energy, transportation, and healthcare, and it collaborates with public and private entities to strengthen the country’s cyber resilience.
Criticisms and Restructuring Proposals:
Project 2025 strongly criticizes CISA for deviating from its original mission and being used as a political tool for censoring speech and influencing elections. The proposal is to transfer CISA to the Department of Transportation (DOT) and return the agency to its statutory focus.
https://image.nostr.build/8bfb4a45053de96a775f67e3e1b83a44d9a65fee4705e3b16d3359bd799b8af2.jpg
Review of Executive Order 12333
Executive Order 12333, issued in 1981, sets guidelines for U.S. intelligence activities, including the collection, analysis, and dissemination of information.
Project 2025 proposes a review of this order to ensure that intelligence agencies are not used for political purposes but are focused on protecting national security.
Objectives of the Review:
Prevent Abuse: Ensure that intelligence collection is conducted legally, without being used to target political opponents.
Ensure Impartiality: Reaffirm that intelligence operations must be conducted impartially, with a sole focus on the country's security.
https://image.nostr.build/90d31cb35a33048d311716df2fbc65c97bd4c1972977e266133654404393fca0.jpg
Reforms in Public Service
Facilitation of Public Employee Dismissal:
Project 2025 emphasizes the need to simplify the process for dismissing public employees who do not perform their duties impartially or who promote specific political agendas.
Performance Evaluations:
The document highlights the importance of merit-based compensation, stating that performance evaluations are only effective when tied to real consequences. Research indicates that 90% of major private companies in the U.S. use a merit-based pay system linked to evaluations. However, in the federal government, compensation remains largely based on seniority, despite efforts to adopt merit-based pay.
https://image.nostr.build/1b858fd7b2a23c3c65c0677d3e69c44976721bbdcbe7facf4682ba3371562cff.jpg
Inclusion of Employees Aligned with Conservative Values:
Aligned Hiring: Establish mechanisms to hire public employees who share conservative values, ensuring that the policies and practices of agencies are consistent with the principles endorsed by the administration.
https://image.nostr.build/ddbf5c59e7bb479998433991347f9d301dd117fbca0edb0f94e98fcac90b2974.jpg
Controversial Cases and Politicization:
Hunter Biden Laptop Case:
Project 2025 harshly criticizes the FBI and the Department of Justice, accusing them of acting in a biased and politically motivated manner. The authors suggest that the agency is intimidating parents who protest by labeling them as "domestic terrorists," while simultaneously suppressing politically unfavorable speech under the guise of combating "disinformation."
Furthermore, the critique highlights that the FBI is alleged to be neglecting violent attacks on pregnancy centers and violations of laws prohibiting attempts to intimidate Supreme Court justices.
The criticism intensifies with allegations that the FBI interfered in domestic elections and engaged in propaganda operations, specifically citing the purported Russian collusion conspiracy in 2016 and the suppression of the Hunter Biden laptop case in 2020, which is seen as a threat to the Republic.
https://image.nostr.build/e4f571a14102a939164465498bef514379ec0443e71a58e12f50c518e00570c6.jpg
Politicization of the FBI:
Election Interference: Russia Hoax and Trump, Suppression of Hunter Biden’s Laptop, and Big Tech Collusion.
Revelations about the FBI’s role in the 2016 "Russia Hoax" and the suppression of Hunter Biden’s laptop in 2020 suggest that the agency may have strayed from its impartial duties.
These actions indicate concerning politicization, where the agency appears to have been used to influence the political landscape in favor of certain interests. This includes collaboration between the FBI and Big Tech companies to control discourse.
https://image.nostr.build/5dcd45fcec939b782d29d8d2e3d3b45244c525b5dbd3240f1629a4632e390a86.jpg
Comprehensive Review of FBI Investigations:
It is crucial to conduct an immediate and thorough review of all significant investigations and activities within the FBI, terminating those that are illegal or contrary to national interests.
This step is essential for restoring public trust in the FBI. A public report on the findings of this review could enhance transparency and confidence.
https://image.nostr.build/df98e2c6aff123d806187eab13d24a3ebb30a87df1f44cf57be97dc5624fff88.jpg
Structural Reorganization:
Align the FBI within the Department of Justice (DOJ) according to its purposes of national security and law enforcement.
The agency should be under the supervision of the Assistant Attorney General for the Criminal Division and the National Security Division, ensuring that the FBI does not operate as an independent entity but is instead subordinated to the DOJ’s directives.
https://image.nostr.build/0d1c0015c6b67a8afc2dd1595357ea571fcd5a9d83829065f49f9b60cf553eb0.jpg
Prohibition on Policing Speech:
Prohibit the FBI from engaging in activities related to combating "disinformation" or "misinformation" disseminated by Americans who are not linked to plausible criminal activities.
The Constitution, through the First Amendment, prohibits the government from policing speech, ensuring a healthy public debate without governmental intervention.
All these measures represent a significant attack on the "Deep State" within American institutions. These public policies have been considered a dictatorial threat by many sectors of the American press.
However, the real issue should be the politicization of unelected bureaucrats by a political faction.
https://image.nostr.build/9a44b19d15d53314f89528c1d89e2f637030ea18d8907a6a8c4e27d07064b8ec.jpg
Combating Woke Culture in the Intelligence Community
Future leadership of the Intelligence Community (IC) needs to implement a plan to replace the "woke" culture and identity politics that have spread throughout the federal government.
The goal is to restore traditional American values such as patriotism, racial impartiality, and job competence, which have been replaced by advocacy for "social justice" and identity politics.
https://image.nostr.build/7929dca5e36273c8e751f36d6ca6229f362e30792bce735f10be7e5d8581af5f.jpg
Final Considerations
The Heritage Foundation’s Project 2025 is not merely an administrative reform plan; it is a manifesto of resistance against the Washington status quo. The proposals aim to dismantle established power structures, eliminate politicization, and combat the Woke agenda. If implemented, this plan would profoundly impact how the U.S. government operates, promoting a more efficient, limited government aligned with conservative principles.
Threat to the Democratic Deep State:
A potential new administration under Donald Trump represents an existential threat to the Democratic Deep State entrenched in American institutions.
The dissolution of the DHS, depoliticization of intelligence agencies, division of the Secret Service, review of Executive Order 12333, privatization of the TSA, and the hiring of employees aligned with conservative values are all measures that would significantly weaken centralized control and the ability to use these institutions for political purposes.
By dismantling concentrated power and promoting a more transparent and accountable government, Project 2025 aims to restore public trust and ensure that government agencies serve national interests rather than partisan ones.
Of course, not all aspects of the plan may be implemented, but the prospect of several of these measures being enacted should be a cause for concern for the Democratic Deep State.
-

@ 129f5189:3a441803
2024-09-09 23:11:19
Precious metals have served as monetary backing for millennia, but this does not guarantee that gold is a safe investment or a good hedge against economic crises and monetary collapses. Since its last major rally in the 1980s, gold has been progressively demonetized.
Those who acquired gold in the late 1980s will need to rely on a significant increase in demand or a supply shock for its price to rise by 561% and regain the purchasing power it had 40 years ago.
https://image.nostr.build/dd5fec2b474ea34cd72ddf5781393b528e63a358d523c9428f3ba4649f4f42aa.jpg
If you look at the purchasing power of $1 (green line), you'll see that the depreciation is even faster. This might create the impression that gold is a good store of value. But does the fact that something loses value more slowly amidst a general decline really make it a store of value?
Unless the total demand for gold increases at the same rate as its supply has grown in recent years, the purchasing power of the metal is likely to decline.
https://image.nostr.build/9f24f6cf37780fe851746057520064ed94acd96547be53bd341c9e15b8762773.jpg
In other words, if you own an ounce of gold, that ounce will represent an increasingly smaller fraction of the total gold reserves, meaning you are being diluted. Additionally, one should also consider the cost and risk of storage, but that's another issue.
If you don't want to compare the purchasing power of gold today with the 1980s, you can consider its value from 9 years ago. Between September 2011 and November 2015, the Fed printed approximately $2.8 trillion. This also provides a perspective on gold's depreciation relative to the significant monetary expansion during that period.
https://image.nostr.build/822e0a861e16ca258e0427875a84b5c8e5420e51bcf65674b453b55ed78edefd.jpg
In other words, the Fed expanded its monetary base by about 30% during that 4-year period. However, the price of an ounce of gold fell by 45% (from $1,900 to $1,057) over the same interval. A true store of value should protect against excessive money printing. In contrast, during that same period, Bitcoin appreciated by 8,500% (from $5 to $419).
https://image.nostr.build/32a7ca39a6e69e2780f9ab49390c7b7380499fcfe54ae4ef693e6fc91686a41e.jpg
Indeed, while it is interesting to note that this was the exact period when gold derivatives were launched on CME Group, it's important to remember that correlation does not imply causation. Many factors can influence the price of gold and Bitcoin, and establishing a direct causal relationship requires more detailed analysis.
https://derivsource.com/2011/06/21/cme-group-announces-the-launch-of-three-new-short-term-gold-crude-oil-and-natural-gas-options-contracts/
In an asset where supply can only be physically verified, flooding the market with gold contracts could lead to significant issues. This might result in market manipulation, legal liabilities, fines, and potentially even imprisonment for those involved. Such actions can undermine the integrity of the market and lead to regulatory and legal consequences.
https://www.cnbc.com/2018/11/06/ex-jp-morgan-trader-pleads-guilty-to-manipulating-metals-markets.html
Over longer periods, gold has not functioned as a true "store of value" relative to the dollar for quite some time, despite recently returning to its price from 9 years ago. This suggests that, while gold may have periods of price recovery, it has struggled to maintain its value over extended horizons compared to fiat currencies.
It's worth noting that before 1980, aluminum was valued higher than gold. This reflects how market dynamics and technological advancements can significantly impact the value of commodities over time.
https://www.mgsrefining.com/blog/why-aluminum-is-no-longer-a-precious-metal/
While gold has been undergoing a gradual demonetization process since 1980, another asset appears to be experiencing the opposite—hyper-monetization. (See in red; don't be alarmed.)
https://image.nostr.build/435a5369f778a7be727b50e4c6328cfc353240bf804e1ed69313b9a8e1233f7e.jpg
With the advent of Bitcoin, you believe that gold will continue on the same path as silver since the end of the bimetallic standard in 1853: a prolonged process of demonetization, with increasing volatility and reduced liquidity.
https://image.nostr.build/5b9c8bfdb09e51d639e380df160c98beb9ee1d917ea13d28ef67711cfa5f8086.jpg
Since 1913, the dollar has lost 97% of its purchasing power. Over the same period, the gold supply has increased significantly. Since 1980, gold has lost about 82% of its purchasing power. Given that the dollar is used as the unit of account and gold's liquidity is measured in dollars, these changes reflect the complex interaction between the currency and the precious metal.
The U.S. is by far the country with the largest gold reserves in the world and is also the fourth-largest miner of the metal. Additionally, the country controls and issues the currency that serves as the unit of account for gold and has the highest liquidity in global trade.
Is gold easy to transport? Is it simple to verify its supply and authenticity? Is it practical to store? Is its industrial utility significant? Can it be disrupted? And what about the continuous increase in its supply? These are important questions to consider.
In my humble opinion, it will not be the dollar or fiat currencies that will suffer the most from the existence of Bitcoin, but rather the market cap of gold.
https://image.nostr.build/61dddefabc4b69f784631a3294bdd978e3411bba40fb52d585e13b48002389fe.jpg
-

@ 6bae33c8:607272e8
2024-09-09 16:07:43
I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote:
*What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.*
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-

@ d3052ca3:d84a170e
2024-09-09 15:43:38
I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :)
I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet.
What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds?
What is your experience? I'd love to hear about it!
-

@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24
## Chef's notes
Makes an excellent Chicken sandwich.
## Details
- ⏲️ Prep time: 6 Ish hours
- 🍳 Cook time: 40 min
- 🍽️ Servings: 1 loaf
## Ingredients
- 3 ½ - 4 cups bread flour, or more as needed
- 1 ⅓ cups warm milk (110°F – 115°F)
- 5 tablespoons honey
- 4 tablespoons salted butter, melted and slightly cooled
- 1 tablespoon instant “rapid rise” yeast
- 1 ½ teaspoons salt
- Oil or butter for greasing the bowl
- 1 tablespoon melted salted butter, for brushing the crust at the end
## Directions
1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl.
2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes.
3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours.
4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan.
5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F.
6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped.
7. Brush the top of the warm bread with melted butter.
8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
-

@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05
Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one?
Thanks
originally posted at https://stacker.news/items/677439
-

@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43
> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。
导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。
---
### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。
项目是通过cloudflare pages搭建的。
- 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed
项目的教程很详细,具体去看项目教程。
### telegram设置:
- 需要有telegram账号
- 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。
- 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。
- 一定要添加创建的机器人到频道作为管理员才能使用。
### cloudflare的设置
- 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。
- 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图:
[](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv")
- BASIC_USER 后台登陆名
- BASIC_PASS 后台密码
- AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。
### 其他
- 成人内容屏蔽
- pico 使用api接口
去项目地址看
### 最后
我搭建的地址:
https://imgbed.lepidus.me
-

@ d52f4f20:98efcdfb
2024-09-08 12:05:31
_original post 28/12/2010 .net_
Para você que se sente meio preso ao instalar o Ubuntu, pois ele já vem pronto para um usuário final, mas isso não me agrada parece que perco o espirito de liberdade.
Mas o ponto forte Ubuntu são suas atualizações, então eu fui em busca de como fazer uma instalação customizada somente com os pacotes do Ubuntu.
Depois de muita pesquisa e anos de experiência com linux desenvolvi o que chamo de instalação mínima
**Alguns conceitos da minha instalação**
– Não tem gerenciador de login gráfico.
– Precisar habilitar o root, na unha e você usa isso.
– Não tem menus, os aplicativos são chamados via tecla de atalho ou docks.
– Não tem menu para desligar.
– Não é um desktop, usa apenas um gerenciador de Janelas.
– Aqui tudo é minimalista, não é bonito também não quer dizer que é feio, é apenas simples faz o necessário.
– Não importa a versão do ubuntu, atual ou não essa técnica quase nunca mudará.
**Seria bom/Pré-Requisitos**
– Se você tem conceitos de particionamento.
– Se você já instalou um Debian.
– Se você sabe usar o vim.
– Conexão com internet via placa de rede 10/100 (sim tem que ser assim).
**Introdução**
A idéia é usar a instalação mínima do Ubuntu (https://help.ubuntu.com/community/Installation/MinimalCD), onde é bem parecida com a NetInstall do Debian. Iremos baixar a imagem(12 ~ 13MB) do link acima e queimar em um cd rom e dar boot.
Vamos usar o assistente de instalação, e não selecionaremos nenhum pacote na instalação, tudo sera instalado via linha de comando usando o apt. Pra quem já instalou usando o anaconda da RedHat não terá problemas, qualquer ser capaz de ler consegue instalar.
Esta é a primeira tela exibida após o boot, selecione o menu
Va seguindo o instalador conforme as telas, não quer que eu fique explicando tudo né?
Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.
Aqui você estara selecionando daonde pacotes serão baixados.
Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.
Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.
Após criar, FINISH!
Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.
O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.
senha é bom por né.
Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.
Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente.
Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar.
Grub é o gerenciador de boot, instale ele ai sem medo.
Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada.
Logue-se com seu usuário, meu caso “lion” (que coisa gay figura 24 ainda).
**Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI.
**Torna-se root**
Isso é primordio no linux, sempre somos o ROOT, o Ubuntu tem essa filosofia para você não fazer cagada, mas na vida uma boa técnica de aprendizado é fazendo cagada, então vamos habilitar o root.
Calma usaremos o root para tarefas como instalar novos software, mas a execução e configuração de nosso ambiente será com nosso usuário.
```
$ sudo passwd root
```
Pronto a partir de agora os comandos começados com # quer dizer que você tem que estar logado como root, e quando estiver $ você deve executar com seu usuário.
Loge-se como root vamos usar bastante de um $su ou entre num novo tty como root.
**Instalando o vim**
```
#apt-get install vim
```
(repare # você tem que estar logado como root)
**Removendo o boot-splash**
Amigos estamos falando de uma maquina limpa, o boot splash só come memória.
Faça um backup antes e depois edite o arquivo “/boot/grub/grub.cfg” procure a palavra splash e apague somente ela e salve o arquivo. É necessário dar diretos de gravação e depois volte como somente leitura.
**Removendo Mensagem de boas vindas MOTD**
Logo após o login, é exibida uma mensagem de boas vindas enorme do ubuntu, eu não gosto dela, nem do debian eu gostava e eu a removia editando o script “/etc/init.d/boot-misc.sh” mas no ubuntu esse arquivo não existe.
Depois de muito fuçar eu descobri que removendo os arquivos do diretorio “/etc/update-motd.d/” a mensagem some, pra mim basta, também removi o conteudo do arquivo /var/run/motd ;
**UPDATE**
Dica do comentário do Marcelo Godim
Ele é gerenciado pelo pam_motd basta ir em /etc/pam.d nos arquivos “login” e “sshd” e comentar essas linhas abaixo:
login:
#session optional pam_motd.so
sshd:
#session optional pam_motd.so # [1]
**Mudando mensagem da versão**
Dica velha edite o arquivo “/etc/issue” coloque o que preferir.
——Se você não precisa de modo gráfico a instalação terminou aqui.
Alterando o sources.list adicionando outros repositórios
Edite o arquivo /etc/apt/sources.list e deixe assim, basicamente adicionados pacotes do site Medibuntu, se prefereir siga esses passos é melhor do que editar o arquivo.
**Instalando o resto dos pacotes**
#apt-get install xserver-xorg xinit alsa-base alsa-utils openbox obconf obmenu feh nitrogen tint2 k3b conky gmrun pcmanfm gtk-theme-switch ssh smbfs smbclient dosfstools setserial usbutils leafpad x11-apps openbox-themes terminator chromium-browser xcompmgr gcc g++ openjdk-6-jdk mysql-server mysql-query-browser gftp gcc-avr avrdude imagemagick gparted ntfs-3g file-roller zip unrar gpicview gtk2-engines gnome-icon-theme-gartoon vim unace rar unrar zip unzip p7zip-full p7zip-rar sharutils uudeview mpack lha arj cabextract file-roller pidgin pidgin-data pidgin-lastfm pidgin-guifications msn-pecan pidgin-musictracker pidgin-plugin-pack pidgin-themes mplayer vlc cairo-dock w32codecs audacious
Vai dormir, seila vai baixar ai uns 500mb, você pode tirar ou por o que quiser ai isso é minha instalação.
Como entrar no modo gráfico?
Logue-se com seu usuário
```
$startx
```
O comando antigo, simples, que dei a primeira vez no meu conectiva 4.
Este é o resultado final, mas para isso vamos algumas dicas.
Toda incialização dos aplicativos eu concentrei no .config/openbox/autostart.sh segue o meu ai
```
# Set desktop wallpaper
nitrogen –restore &
# Enable Eyecandy – off by default
xcompmgr -cCfF -r7 -o.65 -l-10 -t-8 &
# Launch network manager applet
(sleep 4s && nm-applet) &
# Launch clipboard manager
#(sleep 1s && parcellite) &
# Uncomment to enable system updates at boot
#(sleep 180s && system-update) &
cairo-dock &
# Launch Conky
#conky -q &
# Launch panel
tint2 &
```
**Configurando teclas de atalho**, edite o arquivo .config/openbox/rc.xml, vá até a seção keybinds as minhas são essas abaixo:
```
<keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-1″><action name=”Execute”> <execute>xcompmgr -cCfF -r7 -o.65 -l-10 -t-8</execute></action></keybind><keybind key=”W-2″><action name=”Execute”> <execute>pkill xcompmgr</execute></action></keybind><keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-e”><action name=”Execute”> <execute>pcmanfm</execute></action></keybind><keybind key=”W-g”><action name=”Execute”> <startupnotify> <enabled>true</enabled> <name>transset</name> </startupnotify> <command>transset .50</command></action></keybind><keybind key=”W-h”><action name=”Execute”> <startupnotify><enabled>true</enabled><name>transset 1</name></startupnotify><command>transset 1</command></action></keybind><keybind key=”W-l”><action name=”Execute”><startupnotify><enabled>true</enabled><name>Lock screen</name></startupnotify><command>gnome-screensaver-command -l</command></action></keybind><keybind key=”W-t”><action name=”Execute”><execute>terminator</execute></action></keybind><keybind key=”W-r”> <action name=”Execute”> <execute>gmrun</execute> </action></keybind>
```
Pesquise como instalar temas GTK, configurar o TINT2 (desk bar), Cairo Dock, também tem muitas configurações de openbox na internet.
Esse tutorial vem de anos de convivio com linux, é duro passar tudo a limpo aqui, uma dica e testar o Linux Crunch-Bang aprendi muitas customizações com ele.
#blog #tech
-

@ c6f7077f:ad5d48fd
2024-09-08 01:24:03
***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further.
#### ***Consider the Most Fundamental Questions***
1. **The Origin of the Universe**
2. **The Origin of Life on Earth**
#### ***The Origin of the Universe***
You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**.
#### ***The Origin of Life on Earth***
The origin of life is even more complex. Life requires three essential components:
- **Proteins** for basic functioning
- **RNA** for storing and replicating genes
- **Lipids** (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**.
#### ***The Question of Certainty***
If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early.
#### ***Reclaiming Control of Science and Education***
The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend:
- **“A Brief History of Time”** by **Stephen Hawking** for physics
- **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-

@ 6bae33c8:607272e8
2024-09-07 22:09:27
With all five of my football drafts/auctions in the books, here's the portfolio I've amassed for 2024, not including the RotoWire Dynasty League:
**Links**: [BCL1](https://www.realmansports.com/p/beat-chris-liss-1-344), [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e?utm_source=publication-search), [BCL3](https://www.realmansports.com/p/beat-chris-liss-3-062), [Steak League](https://www.realmansports.com/p/steak-league-879), [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7)
**Players in whom I have the most shares:**
**QB**: Justin Fields (4), CJ Stroud (2), Anthony Richardson (2), Tua Tagovailoa (2)
**RB**: Jonathan Brooks (2), Brian Robinson (2), Jerome Ford (2), Jordan Mason (2), JK Dobbins (2), Khalil Herbert (2), Dalvin Cook (2)
**WR:** Stefon Diggs (5), Ja’Marr Chase (3), Rashid Shaheed (3), Ladd McConkey (2), Roman Wilson (2)
**TE:** Jonnu Smith (3)
**K**: Younghoe Koo (3), Harrison Butker (2)
**D:** Giants (4)
**Notes:**
Obviously, I thought Stefon Diggs was mispriced, though I only had to pay close to what I thought he was worth in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7) — in the rest of the leagues he fell to me at ADP or below. He and Ja’Marr Chase are massively important to me this year, and to a lesser extent CJ Stroud.
I also have Justin Fields and the Giants defense everywhere, but both were essentially free, and I could swap them out without issue. I also have a lot of Younghoe Koo, but he too could obviously be swapped out. I like having a couple key players to build around rather than five disparate teams. Of course if Diggs gets hurt or turns out to be washed up, it’ll be rough, but in some ways it’s like the old days where you had only one team, and you had to live and die with it.
**Prominent Players I Don't Have (bold is by choice):**
Bijan Robinson, Tyreek Hill, Breece Hall, Amon-Ra St. Brown, Justin Jefferson, Garrett Wilson, A.J. Brown, Jonathan Taylor, Puka Nacua, **Davante Adams**, **Saquon Barkley**, Chris Olave, Rashee Rice, **Kyren Williams**, Travis Etienne, Cooper Kupp, Isiah Pacheco, **Michael Pittman**, **Nico Collins**, **DK Metcalf**, **Mike Evans**, **Deebo Samuel, Josh Allen,** DJ Moore, Brandon Aiyuk, Derrick Henry, Zay Flowers, **James Cook**, Terry McLaurin, Kenneth Walker, **Xavier Worthy**, Amari Cooper, Josh Jacobs, Trey McBride, **George Pickens**, Lamar Jackson, **Christian Kirk**, Tee Higgins, **Calvin Ridley**, **Rachaad White,** Jayden Reed, Diontae Johnson, **Travis Kelce**, **Joe Mixon**, **Alvin Kamara**, Christian Watson, **Jalen Hurts**, Aaron Jones, Patrick Mahomes, David Montgomery, **Zamir White, Keenan Allen,** Kyle Pitts, **D’Andre Swift**, George Kittle
**Past Portfolios:**
[**2023**](https://www.realmansports.com/p/my-portfolio-ef6?utm_source=publication-search)**, [2022](https://www.realmansports.com/p/my-portfolio?utm_source=%2Fsearch%2Fmy%2520portfolio&utm_medium=reader2), [2021](https://www.rotowire.com/football/article/nfl-chris-lissrsquo-portfolio-58839), [2020](https://www.rotowire.com/football/article.php?id=52704)[, 2019](https://www.rotowire.com/blog/post.php?id=29428), [2018](https://www.rotowire.com/blog/post.php?id=26158), [2017](https://www.rotowire.com/blog/post.php?id=23069), [2016](https://www.rotowire.com/blog/post.php?id=13592), [2015](https://www.rotowire.com/blog/post.php?id=8991)**
-

@ 6bae33c8:607272e8
2024-09-07 22:07:54
I submitted my five picks for the Circa Millions contest today. I think it’s $6M in total prizes. I want to put a disclaimer here: I’m putting these behind a paywall not because you should pay for these picks — never pay for anyone’s picks.
If the picks were that good, whoever was making them could just print money and wouldn’t need yours. If you want to subscribe in earnest, do so because you’re interested to see who I chose and read the reasoning, not because you (erroneously) think it’s the way to get some easy winners. Or if you want to support my substack generally because you think it adds value to you. Those are fine reasons to subscribe, but doing so because you think copying my picks will make you money is dumb.
Okay that out of the way, here are the picks:
**Dolphins -3.5 vs Jaguars** — I like taking the Dolphins in early September, it’s hot and humid there, difficult for opposing teams to adjust to it. It’s like Lambeau Field in December, only in reverse. Moreover, the Dolphins are a veteran offense that’s played together for years, while the Jaguars are working in two new receivers.
**Falcons -3.5 vs Steelers** — Justin Fields is probably an upgrade over Russell Wilson at this point, but he’s haphazard and will have to learn the players and offense on the fly. The Falcons have a new QB too, but he’s an old pro, has better weapons and a better offensive line.
**Giants +1 vs Vikings** — The Giants have three Pro-Bowl level pass rushers, finally have a playmaking receiver and upgraded their offensive line this offseason. And yet despite facing Sam Darnold at home, they’re still getting a point.
**Cardinals +6.5 at Bills** — Kyler Murray is now another year removed from knee surgery, should be his usual spry self, and Marvin Harrison adds another dimension to the offense it sorely needed. The Bills will move the ball, but I think Arizona will hang with them and keep it close enough.
**Browns -2 vs Cowboys** — The Browns should be able to run the ball and keep the Dallas pass rush off Deshaun Watson, while Dallas’ offensive line has slipped a bit, and the Browns defense was No. 1 against the pass last year. Dak Prescott also has big home/road splits.
-

@ 6bae33c8:607272e8
2024-09-07 22:05:26
This is my main event for fantasy football, the $1700 buy-in NFFC Primetime. I wound up picking 11th (I had the fourth to last choice), and while in retrospect maybe I should have opted for ninth or 10th, I wanted to get a share of Jahmyr Gibbs which is why I chose that slot. I also ran through some scenarios beforehand — what if Ja’Marr Chase (still not signed) falls — do I take him in a fourth league? But as you’ll see, the first round was complete chalk, and no windfalls whatsoever fell to me.
But I had a plan for that, and I more or less executed it.
Without further ado, here are the results:
<img src="https://blossom.primal.net/4bbf1f4369c4eea958b04922892f9c485dcbce7d68f011e55c11997f05ae6006.png">
**1.11 Jahmyr Gibbs** — This was the most likely scenario, and it took me about two seconds to make the pick once the top three backs and seven receivers were gone. If Gibbs (who is not on the injury report) hadn’t had a hamstring injury in camp, I’d have him close to the middle of the round rather than the end. Let’s hope he doesn’t aggravate it.
**2.2 Marvin Harrison** — I would have taken either Puka Nacua or Jonathan Taylor, but no breaks here either. Both went at the turn, and I knew I was taking a receiver. Starting RB-WR is the easiest build, in my opinion, but Harrison was kind of an agnostic pick. I had considered Rashee Rice, but as Alan Seslowsky pointed out, while his suspension for hit and run might not kick in until after the season (when the legal process has run its course), that could be pushed up if his lawyers negotiate a plea. Between that an the presence of so many options for the Chiefs, I went Harrison over him narrowly. But it was a close call.
**3.2 Stefon Diggs** — I missed Malik Nabers, Cooper Kupp, (maybe Jaylen Waddle) and De’Von Achane who went with the four consecutive picks ahead of me, so it was Diggs, Nico Collins (his teammate who has a higher ADP), DeVonta Smith or (maybe) Derrick Henry. I went Diggs who I had personally ranked the highest, wouldn’t make it back to me, who I have in every league and was part of my “unfriendly” draft plan, i.e., the Plan B I had talked about.
**4.11 Tank Dell** — He’s too small to hold up, but whenever he played he produced, and he gives me a bit of a Diggs hedge. I also wanted Trey McBride on this turn (as I had Marvin Harrison and could have drafted Kyler Murray — who I love this year — later), but he went on the turn. I thought about taking McBride first, but they were side by side in ADP, and my Plan B was to stack Texans, so I went Dell and took a chance.
**5.2 Chris Godwin** — This was the one pick I kind of regret (though it’s debatable.) I like Jayden Reed a lot, but he was half a round lower per ADP, and there was *some* chance I could get him on the way back. I had Godwin everywhere last year, and he was a disappointment, but apparently he’s healthier now and is going back to the slot full time where he excels.
**6.11 Jaxon Smith-Njigba** — The other pivot off Godwin was JSN, and sure enough he made it back all the way, though he starts off as my first bench player. That’s okay though — you need at least five viable receivers throughout the year, and I didn’t have to take C.J. Stroud because if the guy at the turn took him, I would just pivot to the Kyler Murray/Harrison stack.
**7.2 C.J. Stroud** — He was there, and I executed Plan B. Yes, I have a weak first three rounds by ADP, but I have Gibbs, Harrison and a big piece of the Texans passing game which I think will lead the NFL in yardage.
**8.11 Jaylen Warren** — I needed a second back, and Warren is one. He’s a good pass catcher and should see half the snaps in Pittsburgh.
**9.2 Brian Robinson** — I like Robinson as a player, he’s the undisputed early-down option on what should be a better offense. (Think Ricky Pearsall, but at RB.) Too soon? Austin Ekeler will obviously see the passing-down work unless he proves totally washed up. The Robinson pick cost me David Njoku and Brock Bowers unfortunately, which was a gamble I knew I was making.
**10.11 Jordan Mason** — At 29 and playing into the Super Bowl, Christian McCalfinjury was already a risk, and that he’s “expected” to play Monday night rather than 100 percent fine is worrying. Mason could be a league winner if McCaffrey goes down.
**11.2 J.K. Dobbins** — The Mason pick cost me Jaleel McLaughlin, so I pivoted to Dobbins who still has a high ceiling if he can ever stay healthy.
**12.11 Dallas Goedert** — Tight ends had flown off the board, but I was happy to get Goedert who has been valuable on a per-game basis the last couple years and is still just 29 which is late prime for the position.
**13.2 Dalton Schultz** — Why not stack it even harder? The Texans could throw for 5,000-plus yards, and I have three of the four top targets and the QB.
**14.11 Andrei Iosivas** — He’s gotten a lot of buzz in camp, seems like the No. 3 receiver right now, Tee Higgins is hurt and Ja’Marr Chase is still unsigned.
**15.2 Cam Akers** — The Iosivas pick cost me Jalen McMillan who would have served as Godwin insurance, but Akers could easily take an aging Joe Mixon’s job. Maybe it’s too much Houston, but if it’s a top-three offense, I’m good with it.
**16.11 Justin Fields** — The backup QBs had flown off the board, and Fields has too much upside to pass up. Plus he might even start Week 1 with Russell Wilson already hurt, and if he plays well, he might never look back.
**17.2 Harrison Butker** — It’s either the based af kicker or a Younghoe for me. Plus he locked in a decent Week 1.
**18.11 Dalvin Cook** — He had only 67 carries last year for a bad Jets offense. What if he isn’t as washed up as we think? He could easily win that job over Zeke Elliott and Rico Dowdle.
**19.2 Jonnu Smith** — TE is my weakest position, so I took another upside gamble. What if he’s the Dolphins third target?
**20.11 Giants Defense** — I think I took them in all four NFFC leagues. They get the Darnold Vikings at home and then Jayden Daniels in his second career start. And they have three Pro Bowl level pass rushers.
**Roster By Position**
**QB** CJ Stroud
**RB** Jahmyr Gibbs/Jaylen Warren
**WR** Marvin Harrison/Stefon Diggs/Tank Dell
**TE** Dallas Goedert
**FLEX** Chris Godwin
**K** Harrison Butker
**D** Giants
**B** Jaxon Smith-Njigba/Brian Robinson/Jordan Mason/JK Dobbins/Dalton Schultz/Andrei Iosivas/Cam Akers/Justin Fields/Dalvin Cook/Jonnu Smith
-

@ 6bae33c8:607272e8
2024-09-07 22:00:17
Unfortunately, I didn’t have a ton of action in this game. I had the Packers with the points and am now 0-2 to start the week in my home picking pool. I had Xavier McKinney in the [Steak League](https://www.realmansports.com/p/steak-league-879?utm_source=publication-search) which was nice as like Roquan Smith he too started the year with a pick.
But I was missing the principal scorers namely Saquon Barkley (maybe I let the nerds talk me out of him, as I had him [ranked highly initially](https://www.realmansports.com/p/running-back-rankings?utm_source=publication-search)) and Jayden Reed. Barkley I’m okay with because the potential for Jalen Hurts TDs was something I hadn’t initially considered, but Reed was a major error and in fact I passed on him for freaking Chris Godwin in my [Primetime last night](https://www.realmansports.com/p/nffc-primetime-fa7?utm_source=publication-search)!
I had even argued with Alan Seslowsky that Reed was the [obvious choice](https://www.realmansports.com/p/week-1) among the Packers receivers. So seeing him go off (and he should have had a third TD, but it was called back due to something I’ve never seen before (both teams having 12 men on the field) was painful. Godwin is almost sure to have a terrible season now just to hammer home the lesson for me: Don’t worry about 10 spots of ADP, take the fucking guy you like. Stop listening to the consensus when you have a real lean.
I don’t know how many times I need to learn this lesson, but apparently at least one more!
- Reed looked like the most electrifying receiver on the field for the Packers. He had only six targets, not including the TD called back due to the penalties, but it’s obvious he’ll get more, and the handoff he took 33-yards to the house will incentivize them to do that again too. Year 2 after the surprisingly strong Year 1. He belongs in the second round now, along with Rashee Rice.
- Christian Watson caught a TD and will be involved, but as great an athlete as he is he doesn’t have Reed’s football skills. Romeo Doubs is just a guy, but he’s reliable, and Dontayvion Wicks had a rough game — he’s an easy cut for me.
- Jordan Love didn’t scramble much, and the Packers settled for a ton of field goals, but he looked okay. I think once they give Reed his 10 targets, Love will have his expected numbers. *(Just read on RotoWire that Love left the game for the last two plays with an unspecified leg injury, something not apparent on the 40-minute edited version. I thought they brought Malik Willis to throw a Hail Mary!* *Obviously, if he’s out for any length of time, all bets are off for the Packers receivers.)*
- Josh Jacobs got stuffed in short yardage early, fumbled (though the Packers recovered), but ran well and hard late and even caught two passes. I have zero shares, but he looks like a fine pick for the late-third/early fourth. His backup Emanuel Wilson looked pretty spry too. Marshawn Lloyd is a cut now too in most formats.
- Brayden Narveson missed a key kick off the post, but got a lot of attempts. He seems to have landed in the right place for a big season.
- Jalen Hurts was a bit sloppy with two picks and a lost fumble, never got going on the ground (seemed like the Packers were really dedicated to taking that away), and the ass-smash didn’t work as well without Jason Kelce. But his receivers are so good, and Saquon Barkley is a big upgrade too. I would downgrade him a little though as his rushing TD projection maybe went from 10 to seven.
- AJ Brown didn’t even look like he was running fast as he easily scored a 67-yard TD past the Packers defense. DeVonta Smith seemed to line up more in the slot and was automatic on key third-downs. There was no third receiver of which to speak, and even Dallas Goedert saw only five targets.
- Barkley looked great, both on his TD catch, and as a rusher. As I said I don’t have any shares despite being high on him initially, but I love Barkley as a player (and bitcoiner!), and still kind of root for him. I hope he smashes this year.
-

@ 9358c676:9f2912fc
2024-09-07 18:50:14
## Introduction
The human immunodeficiency virus (HIV) began as a pandemic in the 1980s. In its early days, it was seen as a certain death sentence, a taboo associated with marginalized groups, and it highlighted the failures of poverty in accessing healthcare. Gradually, the struggle for life and the suffering of those who are no longer with us, including both famous and anonymous individuals, became visible.
Today, 40 years later, HIV is presented as a chronic disease with effective treatment. **Patients living with HIV who receive appropriate treatment have no detectable virus in their circulating blood, enjoy a good quality of life, and are more concerned about other aspects of their health during medical consultations, almost forgetting their condition.** For these patients, daily treatment is the cure, similar to someone taking a pill every day for high blood pressure or diabetes.
## The Global Impact
HIV is a lentivirus, a subgroup of retroviruses composed of RNA. The natural history of HIV infection involves an attack on the immune system, particularly targeting CD4 cells, where chronic deterioration can lead to the acquisition of infectious and oncological diseases that may be fatal over the years, resulting in acquired immunodeficiency syndrome (AIDS).
Interestingly, there is a small group of people known as "elite controllers" who manage to control HIV infection without treatment and remain healthy for much of their lives, despite having a hidden deep viral reservoir. The primary modes of transmission are sexual, followed by blood and vertical transmission from mother to child, with the first mode predominating today.
Today, in the downward trend of the HIV epidemic, **it is estimated that 39 million people are living with HIV worldwide.** Depending on the region, nearly half of this population belongs to at-risk groups, such as men who have sex with men (MSM), transgender individuals, sex workers, and people who inject drugs. These vulnerable groups are especially important for prevention efforts. However, little is done for prevention in the general population, which sometimes represents the other half of the cake of people living with HIV (PLWH).
## Breaking the Dogma: The Concept of Undetectable = Untransmittable (U=U)
The introduction of highly effective antiretroviral therapy (HAART) in 1994 broke the curve of the HIV epidemic. The introduction of new medications with fewer side effects and greater effectiveness in controlling the virus has been crucial. In 2007, the launch of Raltegravir as the first viral integrase inhibitor marked a milestone in current treatments, **allowing patients to effectively control the virus within 3 to 6 months.**
The positive impact of these treatments led health organizations to launch the concept of **undetectable = untransmittable (U=U)** to impact the general population and at-risk groups, updating the dogma and eradicating stigma: **a patient living with HIV who maintains an undetectable viral load in their blood through treatment will not transmit HIV sexually.**
Although this concept has transformed the social dynamics and stigma surrounding the disease, adherence to treatment must be complete to achieve this new paradigm.
## Prophylaxis as a Method to Prevent HIV in Healthy Populations
The correct use of condoms has been the cornerstone of HIV prevention and other sexually transmitted infections over the years. However, it is not the only tool available today and can be complemented for comprehensive sexual health.
**Pre-exposure prophylaxis (PrEP)** is a novel strategy that involves administering antiretroviral medication to vulnerable groups before they are exposed to HIV (MSM, transgender individuals, sex workers, people who inject drugs). It involves taking medication daily, effectively reducing the risk of contracting HIV and providing protection to these groups. It is similar to taking a contraceptive pill daily. It has had a very positive impact on protecting these populations. In the Americas, it has been successfully implemented in the United States, Mexico, Peru, and Brazil. Other countries, although with some delay, are now implementing this strategy.
**Post-exposure prophylaxis (PEP),** on the other hand, is a strategy that involves administering antiretroviral treatment after a potential exposure to HIV. If the treatment is administered within the first 72 hours and maintained for 4 weeks, the chances of contracting HIV decrease substantially.
Both strategies have been remarkably successful in preventing HIV in at-risk populations and healthy populations, although their dissemination and awareness remain limited.
https://image.nostr.build/08682bf763ade56741d8e4c8c6d870cb8d71ab7d72c605b9aa805af2234348ff.jpg
## The New Horizon: Long-Acting Antiretrovirals, HIV Vaccines, and Promising Therapies
The introduction of viral integrase inhibitors and new nucleoside analogs in the last 15 years has allowed for the availability of safe drugs with minimal side effects in the treatment of HIV, **many of which are included in a single pill regimen per day.** However, the pharmaceutical industry continues to diversify the offerings in a healthy manner.
**Cabotegravir is a new long-acting integrase inhibitor that is administered via injection.** Combined with Rilpivirine, it has proven to be effective and safe in the treatment of HIV, with injections every 2 months. This has revolutionized treatment for people who are tired of taking pills daily, as well as in PrEP, where effective prevention against HIV can be achieved with injections every 2 months for at-risk groups.
Additionally, **subdermal implants of Islatravir,** a new long-acting nucleoside analog, are being tested as a PrEP strategy. Similar to monthly hormonal contraceptive injections or hormonal contraceptive implants, this strategy has proven effective in at-risk groups.
Regarding the **HIV vaccine,** we have been developing it for over two decades, with advances and setbacks. While vaccines have shown promising results in terms of safety and antibody generation, we still need to await conclusive phase III results demonstrating their effectiveness in at-risk groups and the general population.
## The Eradication of HIV and Patients Cured Without Treatment
While current treatment allows for the elimination of HIV from the bloodstream and sexual transmission, there remains a reservoir in some deep immune cells that have been infected by the retrovirus, which contain latent HIV DNA and have the potential to reactivate if daily treatment is interrupted.
However, **there are patients who have managed to eliminate HIV from their bodies, including these deep cells, and HIV is undetectable upon discontinuation of treatment.** These cases are very rare, with only 7 to 8 individuals being the subject of intensive scientific study. Among them are the "Berlin patient" of Germany and "City of Hope patient" from Argentina. Some of these cases involved patients under effective HIV treatment who underwent suppressive chemotherapy for bone marrow transplants and managed to eliminate these deep cells with latent HIV DNA.
Unfortunately, this treatment is not scalable for the entire HIV-positive population, both due to its cost and potential side effects. However, **"Shock and Kill" strategies** have been proposed, aiming to use monoclonal antibodies to activate these latent cells during HIV treatment, exposing them to antiretroviral medication for elimination, thereby eradicating these small reservoirs of HIV.
## WHO Goals
The World Health Organization (WHO) has established clear objectives that are constantly updated to achieve the eradication of HIV in the population.
**The updated goals of the WHO propose that, to end the HIV epidemic, three objectives must be met by the year 2025-2030:**
1. 95% of people living with HIV must be diagnosed through testing.
2. 95% of diagnosed individuals must be on highly effective antiretroviral therapy (HAART).
3. 95% of those on HAART must have an undetectable viral load in their blood.
Developing and underdeveloped countries currently have an effectiveness rate for these strategies that disagree significantly.
https://image.nostr.build/ac6693df57aaca6dac0b06b5db9eb1a2757e7c08511edb0f11617e12653d3db5.png
## Key Takeaways
* HIV has a cure, and the cure is permanent treatment.
* Treatment for HIV is free and accessible to the population, as it is a public health impact disease.
* A person living with HIV who receives appropriate treatment will not transmit the virus sexually, will enjoy a full life without the disease, and can have children without HIV.
* In the event of a potential HIV exposure (such as unprotected sexual contact with an infrequent partner), you can go to a hospital within the first 72 hours to receive treatment that will prevent HIV infection.
* Just as we witnessed the eradication of smallpox from the face of the earth in 1978 due to scientific advances, we will live to see the eradication of HIV.
## Autor
**Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community**
npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
## Resources
1. [World Health Organization (WHO)](https://www.who.int/en/health-topics/hiv-aids#tab=tab_1)
2. [Centers for Disease Control and Prevention (CDC)](https://www.cdc.gov/hiv/?CDC_AAref_Val=https://www.cdc.gov/hiv/default.html)
3. [UNAIDS](https://www.unaids.org/en)
## Bibliography
1. The natural history of HIV infection. DOI: 10.1097/COH.0b013e328361fa66
2. Changing Knowledge and Attitudes Towards HIV Treatment-as-Prevention and "Undetectable = Untransmittable": A Systematic Review. DOI: 10.1007/s10461-021-03296-8
3. Challenges of HIV diagnosis and management in the context of pre-exposure prophylaxis (PrEP), post-exposure prophylaxis (PEP), test and start and acute HIV infection: a scoping review. DOI: 10.1002/jia2.25419
4. Long-acting cabotegravir and rilpivirine dosed every 2 months in adults with HIV-1 infection (ATLAS-2M), 48-week results: a randomised, multicentre, open-label, phase 3b, non-inferiority study. DOI: 10.1016/S0140-6736(20)32666-0
5. Efficacy and safety of long-acting cabotegravir compared with daily oral tenofovir disoproxil fumarate plus emtricitabine to prevent HIV infection in cisgender men and transgender women who have sex with men 1 year after study unblinding: a secondary analysis of the phase 2b and 3 HPTN 083 randomised controlled trial. DOI: 10.1016/S2352-3018(23)00261-8
6. Safety and immunogenicity of a subtype C ALVAC-HIV (vCP2438) vaccine prime plus bivalent subtype C gp120 vaccine boost adjuvanted with MF59 or alum in healthy adults without HIV (HVTN 107): A phase 1/2a randomized trial. DOI: 10.1371/journal.pmed.1004360
7. Shock and kill within the CNS: A promising HIV eradication approach?. DOI: 10.1002/JLB.5VMR0122-046RRR
-

@ 41d0a715:9733c512
2024-09-07 15:27:14
>Blaise Pascal: 'I have made this letter longer than usual, only because I have not had the time to make it shorter.'
Some of you Stackers need to spend a little more time to make your posts short and sweet.
Sometimes I realize a post doesn't even have a point after wasting time reading it.
A long poorly written post is a waste of my time and yours too!
originally posted at https://stacker.news/items/676136
-

@ 3bf0c63f:aefa459d
2024-09-06 12:49:46
# Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-

@ 6bae33c8:607272e8
2024-09-06 08:16:48
I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be.
I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance.
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
. . .
In any event, let’s take a look at the slate: Here are the ownership numbers per [Officefootballpools.com](http://Officefootballpools.com).
<img src="https://blossom.primal.net/4143b814092950ec28820e3d86d7608059d8a767b14eb9e2f19821b57ccb0856.png">
The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.)
But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win.
If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose.
You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills.
But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is *supposed* to be priced in, of course, but I don’t care.)
I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now.
-

@ 6bae33c8:607272e8
2024-09-06 08:14:27
An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes.
In any event, it was an okay game, not great, but there were some interesting takeaways.
- Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff.
- Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask.
- Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.)
- Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more.
- Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot.
- Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown.
- Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though.
- Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game.
- Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role.
- After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG.
- You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night.
-

@ 84b0c46a:417782f5
2024-09-06 00:26:32
- 1:nan:
- **2**
- 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p)
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2|
|--|--|
|test|:nan:|
---
### :nan: **:nan:**
1. 1
2. 2
- tet
- tes
3. 3
1. 1
2. 2
> t
>> te
>>> test
-

@ acc925af:db9fb0bb
2024-09-05 20:26:50
While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good
**Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:**
# Prerequisites:
1. Twitter Developer Account
2. Nostr Wallet with NWC support (e.g., Alby, Nostrify)
3. Twitter API credentials (API key, API secret key, Access token, Access token secret)
4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library)
### Step 1: Set up Twitter API credentials
> Create a Twitter Developer account and obtain API credentials
> Install Tweepy using pip: pip install tweepy
### Step 2: Connect Nostr Wallet using NWC
> Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify)
> Set up the wallet and obtain the NWC credentials (e.g., public key, private key)
### Step 3: Create a Python script
> Import Tweepy and nostr-client libraries
> Authenticate with Twitter API using Tweepy
> Connect to Nostr Wallet using NWC credentials
> Define a function to send 21 satoshis for every like
> Use Tweepy to stream likes and trigger the payment function
`Python` script:
```
import tweepy
from nostr_client import Client
# Twitter API credentials
twitter_api_key = "YOUR_API_KEY"
twitter_api_secret_key = "YOUR_API_SECRET_KEY"
twitter_access_token = "YOUR_ACCESS_TOKEN"
twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET"
# Nostr Wallet NWC credentials
nwc_public_key = "YOUR_NWC_PUBLIC_KEY"
nwc_private_key = "YOUR_NWC_PRIVATE_KEY"
# Set up Tweepy
auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key)
auth.set_access_token(twitter_access_token, twitter_access_token_secret)
api = tweepy.API(auth)
# Set up Nostr Client
nwc_client = Client()
nwc_client.connect(nwc_public_key, nwc_private_key)
# Define payment function
def send_satoshis():
# Create a new Nostr event with 21 satoshis
event = nwc_client.create_event(21)
# Send the event to the Nostr network
nwc_client.send_event(event)
# Stream likes and trigger payment function
class LikeStream(tweepy.StreamListener):
def on_like(self, like):
send_satoshis()
stream = tweepy.Stream(auth, LikeStream())
stream.filter(track=["likes"])
```
##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._
originally posted at https://stacker.news/items/673795
-

@ 3b7fc823:e194354f
2024-09-04 01:33:21
Nyms, Personas, and Digital Identity
#GHOSTn
If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs.
Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see.
Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be.
Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes.
Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
-

@ 3b7fc823:e194354f
2024-09-04 00:26:48
Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
>
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled.
If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
>
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
>
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
>
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
>
>
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
>
Last point and most important:
Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-

@ 6bae33c8:607272e8
2024-09-03 10:47:55
I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track.
*(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)*
1. **Stefon Diggs leads the Texans in targets, catches and receiving yards**
Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year.
2. **CJ Stroud leads the NFL is passing yards**
This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2.
3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)**
Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens.
4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR**
Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020.
5. **The Giants will field a top-10 fantasy defense.**
I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers.
6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt**
I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua.
7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)**
Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time.
8. **Dalvin Cook will lead the Cowboys in rushing yards**
Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.)
9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.**
He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.)
10. **Dalton Kincaid (TE4) will lead all TE in catches**
I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2.
11. **Some of these predictions will be wrong**
No one’s perfect, but you never want to get shut out.
-

@ 6bae33c8:607272e8
2024-09-02 18:09:19
I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot.
Here are the results:
([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream))
<img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png">
**1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount.
**2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead.
**3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there.
**4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target.
**5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone.
**6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year.
**7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position.
**8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR.
**9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.)
**10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.)
**11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks.
**12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build.
**13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job.
**14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert.
**15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old.
**16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down.
**17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too.
**18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie.
**19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.)
**20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence.
**Roster By Position**
**QB** Anthony Richardson
**RB** James Conner/Jaleel McLaughlin
**WR** Ja’Marr Chase/Drake London/DeVonta Smith
**TE** Dalton Kincaid
**FLEX** Stefon Diggs
**K** Younghoe Koo
**D** Giants
**Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
-

@ 3b7fc823:e194354f
2024-09-02 16:26:30
First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
>
1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program.
>
2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.
BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
>
3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works.
>
4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta.
>
5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.
>
BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
>
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-

@ 266815e0:6cd408a5
2024-09-02 15:27:16
After 7 months of work and procrastination I've decided to release another version of noStrudel
There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md)
And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker
```sh
docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0
```
## New Features
### Support for NIP-49 encrypted nsec
Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...)
There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps

### Blindspot feeds
There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing

### NIP-42 Relay authentication
The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings

### Wasm relay and event verification
The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view

The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting

### Thread tabs
Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note


### Wiki articles
Its not feature complete but you can now view and edit wiki articles in the app

### Finished the launchpad
The launchpad is now usable and shows the latest notifications, messages, streams, and tools

### Blossom uploads
The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings

And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`

### Task Manager
There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app

You can see what relays the app is currently connected to

And which relays are requesting NIP-42 authentication

## Bug fixes
- Fix null relay hints in DMs
- Fix users own events being hidden by muted words
- Fix random events showing up as DM messages
- Fix app prompting NIP-07 extension to unlock when app opens
- Remove corsproxy.io as default service for CORS proxy
-

@ 3b7fc823:e194354f
2024-09-01 19:21:09
Testing articles on Yakkihonne
-

@ 6c2d68ba:846525ec
2024-09-01 13:02:53
Dear friend,
it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.
As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:
* What causes the discomfort that drives you out of the walled garden onto the open sea?
* Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?
* What are you hoping to find on the open sea that walled gardens cannot provide?
* What are you willing to sacrifice for freedom (of speech)?
* What will you need to keep the ship afloat?
* How will you react when you find yourself in the middle of a storm?
I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over.
This is about building a new world, an open world without walled gardens and data silos.
Onwards!
-

@ b2d670de:907f9d4a
2024-08-30 22:52:53
# onion-service-nostr-relays
A list of nostr relays exposed as onion services.
## The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options |
| --- | --- | --- | --- | --- | --- |
| nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A |
| relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A |
| nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A |
| nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN |
| bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A |
| relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN |
| freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) |
| inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC |
| filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC |
| N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A |
| nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A |
| nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A
| relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A |
| nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR |
## Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns.
If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub.
### Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-

@ a723805c:0342dc9c
2024-08-30 12:16:55
When I first stumbled upon Nostr back in February 2023, I was immediately drawn to the network's unique design. It was like stumbling across a hidden architectural gem - something so intricate and beautifully crafted that most people might walk past without a second glance. But for those who truly saw it, Nostr's design was mesmerizing. I didn’t know exactly what I was diving into, but I felt enthusiasm because I knew this was something entirely different from the usual legacy social media attempts at connecting people.
One of the first things that struck me was the people. Nostr wasn't just a network; it was a gathering place for a group of curious outlaws, all eager to try something new and break away from the norm. The platforms and interfaces were a bit scrappy and buggy in those early days, but that didn't matter. What stood out was the spirit of the community, people kept coming back, filled with cheer and optimism. Even more impressive was the willingness to help each other out. It wasn't just about using the platform; it was about collectively figuring it out together. This was the seed of a constructive culture that was starting to take root.
Coming from the Twitter culture, I noticed something refreshing: on Nostr, people referred to each other as friends, not followers. Twitter often felt like a toxic swamp of influencers, each trying to outdo the other with proclamations and status games. Sure, there were helpful people on Twitter, but more often than not, their "help" came with strings attached, promoting a Gumroad book, pushing a newsletter subscription, always with a personal incentive lurking in the background. Nostr, on the other hand, was different. Here, people helped each other just for the sake of it, with no expectation of anything in return. The spirit of giving was genuine, and it was contagious.
Fast forward to today, and that same spirit is alive and well. Just take a glance at the #introductions tag, and you'll see it in action: friendly users, eagerly welcoming new members into the ecosystem, offering to lend a hand, and making everyone feel at home. The constructive culture of Nostr, built on a foundation of genuine camaraderie and selflessness, is as vibrant now as it was back in the early days.
This isn't just a network; it's a community that thrives on cooperation, curiosity, and the simple joy of helping others. Nostr isn't about chasing clout or boosting follower counts; it's about building something meaningful together, one interaction at a time. And that's what makes it truly special.
-

@ 6389be64:ef439d32
2024-08-29 18:35:53
Editing of profiles and projects seems easier and laid out better and the overall responsiveness of the website feels greatly improved.
The Analytics section tho . . . whoo doggie! What an upgrade.
Try it out at geyser.fund
originally posted at https://stacker.news/items/665891
-

@ bf7973ed:841ad12a
2024-08-29 17:50:48
Posted using obsidian plugin
https://obsidian.md/plugins?search=nostr#
-

@ 1ec45473:d38df139
2024-08-29 09:55:11
Preston Pysh posted this event this morning:

Behind the scenes, the nostr event looks like this:
```
Event = {
"id":"a6fa7e1a73ce70c6fb01584a0519fd29788e59d9980402584e7a0af92cf0474a",
"pubkey":"85080d3bad70ccdcd7f74c29a44f55bb85cbcd3dd0cbb957da1d215bdb931204",
"created_at":1724494504,
"kind":1,
"tags":[
[
"p",
"6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb",
"",
"mention"
],
[
"p",
"77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c",
"",
"mention"
],
[
"p",
"c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1",
"",
"mention"
],
[
"p",
"50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63",
"",
"mention"
],
[
"p",
"20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5",
"",
"mention"
],
[
"p",
"273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2",
"",
"mention"
],
[
"t",
"BH2024"
]
],
"content":"Awesome Freedom Panel with...",
"sig":"2b64e461cd9f5a7aa8abbcbcfd953536f10a334b631a352cd4124e8e187c71aad08be9aefb6a68e5c060e676d06b61c553e821286ea42489f9e7e7107a1bf79a"
}
```
In nostr, all events have this form, so once you become familiar with the nostr event structure, things become pretty easy.
Look at the "tags" key. There are six "p" tags (pubkey) and one "t" tag (hashtag).
The p tags are public keys of people that are mentioned in the note. The t tags are for hashtags in the note.
It is common when working with NOSTR that you have to extract out certain tags. Here are some examples of how to do that with what are called JavaScript Array Methods:
### Find the first "p" tag element:
```
Event.tags.find(item => item[0] === 'p')
[
'p',
'6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb',
'',
'mention'
]
```
### Same, but just return the pubkey":
```
Event.tags.find(item => item[0] === 'p')[1]
'6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb'
```
### Filter the array so I only get "p" tags:
```
Event.tags.filter(item => item[0] === 'p')
[
[
'p',
'6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb',
'',
'mention'
],
[
'p',
'77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c',
'',
'mention'
],
[
'p',
'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1',
'',
'mention'
],
[
'p',
'50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63',
'',
'mention'
],
[
'p',
'20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5',
'',
'mention'
],
[
'p',
'273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2',
'',
'mention'
]
]
```
### Return an array with only the pubkeys in the "p" tags:
```
Event.tags.filter(item => item[0] === 'p').map(item => item[1])
[
'6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb',
'77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c',
'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1',
'50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63',
'20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5',
'273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2'
]
```
-

@ 460c25e6:ef85065c
2024-08-29 01:07:22
If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
## Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend:
- 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc.
- 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again.
- 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
## Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend:
- 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc.
- 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps.
- 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country
Terrible options include:
- nostr.wine should not be here.
- filter.nostr.wine should not be here.
- inbox.nostr.wine should not be here.
## DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are:
- inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you.
- a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details.
- a hidden, but public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
## Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
## Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today:
- nostr.wine
- relay.nostr.band
- relay.noswhere.com
## Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
## General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
## My setup
Here's what I use:
1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself.
2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription.
3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription.
4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country.
5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays:
- nostr.wine
- nos.lol or an in-country relay.
- <your.relay>.nostr1.com
Public Inbox Relays
- nos.lol or an in-country relay
- <your.relay>.nostr1.com
DM Inbox Relays
- inbox.nostr.wine
- <your.relay>.nostr1.com
Private Home Relays
- ws://localhost:4869 (Citrine)
- <your.relay>.nostr1.com (if you want)
Search Relays
- nostr.wine
- relay.nostr.band
- relay.noswhere.com
Local Relays
- ws://localhost:4869 (Citrine)
General Relays
- nos.lol
- relay.damus.io
- relay.primal.net
- nostr.mom
And a few of the recommended relays from Amethyst.
## Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-

@ b83a28b7:35919450
2024-08-28 15:03:25
Join nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and me for episode 76 of nostr:npub14kw5ygpl6fyqagh9cnrytyaqyacg46lzkq42vz7hk8txdk49kzxs04j7y0 this Friday, August 30th at 3pm ET (UTC -4)
Our guest this week is nostr:npub1xv8mzscll8vvy5rsdw7dcqtd2j268a6yupr6gzqh86f2ulhy9kkqmclk3x from nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm who joins us to provide the lowdown on the recently launched Alby Hub
You don't want to miss this one!
Set your blockclocks!
https://nostrnests.com/
[This is our first show announcement made from a long-form client, in keeping with QW and my #otherstuffchallenge]
-

@ e83b66a8:b0526c2b
2024-08-28 10:56:55
The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud.
Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data.
There is a different way.
NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol.
The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms.
Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid.
Secondly as a user, you don’t have an account, you have a private key which is used to secure your data.
Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key.
Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays.
All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it.
Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key.
Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content.
Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions.
Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant.
As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models.
The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not.
NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment.
From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed.
While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops.
If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here:
https://primal.net/downloads
It will create a private key for you and setup a Bitcoin wallet.
Once you have done this you can visit me here:
nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n
If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already.
NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here:
nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Or you can see his account like this:
https://primal.net/jack
Edward Snowden is also on the platform and you can find him here:
https://primal.net/Snowden
NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation.
Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/
Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus
or Amethyst for Android: https://nostrapps.com/amethyst
The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it.
Some of the more interesting projects right now are:
https://www.0xchat.com/#/ – Private messaging – think WhatsApp
https://zap.stream/ – Video streaming
https://fountain.fm/ – Podcasting
https://wavlake.com/ – Music streaming
https://shopstr.store/ – Online shop
https://npub.pro/ – Website creation tool
https://nostr.build/ – Media and file storage
https://relay.tools/ – Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user – Creator tools
Remember, the same keys you created for Primal can be used across the whole ecosystem.
-

@ b83a28b7:35919450
2024-08-27 18:53:46
On last week's episode of Plebchain Radio, QW and I announced something unusual - we would be taking a week off posting kind 1 notes on the Twitter clone clients - Primal, Damus, Nostur, etc. The clock started right after our show was posted on Friday, August 23rd and ends with show this Friday, August 30th.
https://video.nostr.build/741cd7a0dd33e1ce815490d14069af96579ce47c92ea04240592c7bbb2de3a65.mp4
The idea behind the challenge is to see how much we can participate in the network without resorting to it's most accessible form of communication - kind 1 notes (the equivalent of tweets/replies).
Halfway into the challenge, we've boosted and commented on shows on Fountain, zapped songs on Wavlake, commented on recipes on zap.cooking, watched videos on zap.stream and tunestr, and written the odd long-form note (oh, alright, just this one so far). It's been fun, but has also created an odd sense of sensory deprivation.
We will share more details on our experience on this week's Plebchain Radio episode. Right, I'm off to explore the rest of the other-stuff-verse. I'd urge everyone to give this challenge a try. It might change how you view nostr.
-

@ bcbb3e40:a494e501
2024-08-27 18:33:08
||
|:-:|
|Escena del corto de animación [«I, Pet Goat II»](https://youtu.be/6n_xCI-peq0) del estudio Heliofant, en el que una pantalla con un siniestro personaje en su interior está conectada al cráneo hueco de otro personaje.|
Los que tenemos ya algunos años y empezamos a peinar canas, con toda la profundidad de enfoque y perspectiva que ello implica, hemos vivido cambios muy trascendentales en las últimas décadas. De alguna manera, aquello que considerábamos imposible o, en su defecto, poco probable, se ha venido materializando en el tiempo causando nuestro asombro y, por qué no decirlo, nuestro temor e inquietud. [Los acontecimientos vividos a raíz de la **Plandemia**](https://hiperbolajanus.com/posts/presentacion-despues-virus-boris-nad/), por ejemplo, nos hicieron ver claramente que el sistema ha abandonado sus posiciones anteriores, el disimulo que caracterizaba a su proceder, ese velo de «normalidad», para intercambiarlo por otra «normalidad», una «nueva normalidad» en la que todo es posible, y esto en el sentido más negativo que pueda imaginarse.
Durante el último lustro hemos asistido a encierros obligatorios, a la imposición de pinchazos con sustancias desconocidas de las que nadie se hacía (ni se sigue haciendo) responsable y cuyos efectos nocivos se han constatado con posterioridad, a un creciente y desmesurado control social a través de diversas vías, que ha colocado el mismo concepto de «Verdad» y «Realidad» en entredicho, sustituyendo la Verdad en un sentido eminente, metafísico si se quiere, en la presa de un relato, de una construcción ideológica de ínfimo nivel intelectual diseñado para mantener a la masa en el redil, acallando cualquier tipo de discrepancia, y especialmente de disidencia, que pudiera romper con ese relato hegemónico, custodiado como si del Santo Grial se tratase, frente a cualquier evidencia objetiva. De hecho, [se ha hablado mucho de la **«posverdad»**](https://hiperbolajanus.com/posts/breviarios-contra-modernidad/).
Pero todos estos temas no son nuevos, pese a que su concreción práctica en los tiempos presentes, con las democracias de libre mercado, que venían presumiendo de su «estado de derecho», de sus «garantías» y «libertades», sino que ya venían anunciados en cierta tradición literaria que podemos remontar a las décadas 30-40 del pasado siglo. Ahí tenemos a dos notables autores: **Aldous Huxley** (1894-1963) y **George Orwell** (1903-1950), autores de [_Un mundo feliz_](https://amzn.to/3MnR1Gz) y [_1984_](https://hiperbolajanus.com/posts/resena-1984-de-george-orwell/) respectivamente. Ambos trabajos pueden encuadrarse dentro de esa corriente distópica tan característica donde también podríamos encuadrar, entre otras obras, aquella de **Ray Bradbury** (1920-2012), la famosa [_Fahrenheit 451_](https://amzn.to/4dDfAuV). No obstante, vamos a fijar nuestra atención en los dos primeros autores, Huxley y Orwell, cuyos modelos de dictadura propuestos difieren significativamente entre sí, mientras que el primero nos presenta una «dictadura blanda» o «dulce», edulcorada por las drogas y el transhumanismo, el segundo nos dibuja un orden dictatorial cruel y sádico, enfermizo e investido de una diabólica voluntad de poseer al individuo en su interior más profundo.
||
|:-:|
|George Orwell y Aldous Huxley, los autores de literatura fantástica más visionarios y famosos del siglo XX|
Tras la publicación de _1984_, Huxley, agradecía a Orwell el envío de su mítica obra y en una especie de predicción o vaticinio de futuro confrontaba esta obra con la suya propia:
«La filosofía de la clase en el poder en 1984 es una forma de sadismo llevado a las consecuencias extremas y hacia su solución lógica: ir más allá del sexo y negarlo. Creo que las oligarquías encontrarán formas más eficientes de gobernar y satisfacer su sed de poder y serán similares a las descritas en Un mundo feliz».
Siendo fiel a los dictámenes de su propia obra, Huxley consideraba que se impondría una «dictadura dulce», con el uso masivo y generalizado de drogas farmacológicas y técnicas de hipnotismo a través del desarrollo de poderosas herramientas psicológicas para plegar el control de la mente y la voluntad de las masas al poder imperante. De hecho, este proceso era calificado por Huxley como «la última revolución». Además preconizaba una caída de las masas en un estado de esclavitud voluntaria y adaptada, formulada en aras de una mayor eficiencia en el ejercicio del poder.
Otros autores posteriores como **Elémire Zolla** (1926-2002), se hacían eco del poder de la hipnosis y de la manipulación de las mentes como un proyecto real a gran escala, con siniestros propósitos. Y de algún modo el [liberal-capitalismo ha utilizado este tipo de técnicas a través del mercado](https://hiperbolajanus.com/libros/mos-maiorum-7/), con la estandarización de comportamientos y modas a través del uso de la publicidad en una voluntad de estandarización y uniformización con una voluntad inequívoca de alcanzar la psique profunda del hombre, el subconsciente, para dominar al hombre allí donde el pensamiento lógico y la voluntad se encuentran desdibujados y anulados.
En la misma dirección tenemos a **Herbert Marcuse** (1898-1979), en cuya obra también vemos alusiones a las agresiones y limitaciones de la libertad en [el contexto de la civilización industrial avanzada como parte del progreso técnico](https://hiperbolajanus.com/posts/resena-hanno-cambiato-faccia/). Empieza a delinear en su obra la imagen de un régimen totalitario en el que todos los aspectos de la vida del individuo, y especialmente del pueblo trabajador, se encuentran alienados, encerrados en la lógica del producir y consumir, sin resistencia posible. El hombre reducido a esa condición y cuya única libertad se reduce a elegir entre diferentes productos. En este sentido Marcuse condenaba a la tecnología y delata sus cualidades totalmente funcionales a una ideología de poder. Este es el sentido que otorga a su «hombre unidimensional» cuya definición antropológica se desarrolla sobre un único plano, y bajo ese condicionamiento mental que vemos en la obra orwelliana.
De algún modo, a partir de cierto momento, las herramientas de control de masas se hacen más sutiles, y sustituyen la violencia que el incipiente Estado liberal utilizaba durante el siglo XIX para mantener el orden frente a revueltas o revoluciones adversas, por el uso de elementos de control social y vigilancia, y esto en los últimos tiempos se ha venido desarrollando bajo múltiples excusas, como, por ejemplo, la denominada «Agenda verde», que bajo la premisa de unos hipotéticos cambios dramáticos y catastróficos de raíz antropogénica en el devenir terrestre, debemos aceptar las «ciudades de los 15 minutos», funcionando como «guetos» con contingentes de población estabulados, con movimientos limitados en un espacio reducido, donde prácticamente haya que pedir permiso para salir. Todo por salvar el planeta, por esa ridícula y grotesca teoría de la «huella de carbono», promocionada por bancos y otras instituciones del sistema.
La estrategia del miedo ha dado frutos siguiendo el plan de las élites globalistas, lo vimos con la _Plandemia_ y ha seguido manteniendo su continuidad bajo la apariencia de diferentes amenazas, la emergencia permanente que supone una guerra, como la que [la OTAN libra con Rusia utilizando a Ucrania como ariete](https://hiperbolajanus.com/libros/geopolitica-rusia-aleksandr-duguin/). Las masas, desestabilizadas han venido aceptando todas las imposiciones en nombre de un «consenso común», convirtiéndose en vigilantes solícitos y aceptando restricciones que antes del 2020 nunca hubieran aceptado.
En este contexto, filósofos como Marcuse hablaban de la necesidad de reapropiarse de la imaginación, mientras que Huxley enfocaba toda la atención en la idea de las «distracciones» proyectadas sobre la masa, anticipando el papel decisivo de los _mass media_ en todo este proceso de control mental, como un auténtico brazo armado de los gobiernos al servicio del Nuevo Orden Mundial y su siniestra Agenda. Y de ahí deriva precisamente la situación que estamos viviendo en torno a los «bulos» y las «fake news», utilizadas como excusa para uniformar y aplacar toda crítica, acusando de «desinformación» a quienes en el ejercicio de una teórica libertad de expresión hacen lo propio. De ahí que se imponga la necesidad de encajar toda realidad en el relato oficial, construido _ex profeso_ para desvincular al hombre de toda realidad, y de ahí la teoría de los metaversos o centrar el foco en asuntos anecdóticos o de escasa importancia, que en el caso de [nuestra democracia liberal al amparo de la dictadura del Régimen del 78](https://hiperbolajanus.com/posts/espana-constitucion-idiota/), ha proporcionado notables beneficios a los líderes partitocráticos.
Y lo más curioso del asunto está en que mencionemos a un filósofo como Marcuse, desde un discurso pretendidamente «anti-autoritario», enemigo de la represión y de la violencia en cualquiera de sus formas, cuando [la generación sobre la que influyó preparó las bases de las múltiples ingenierías sociales con las que se debilita y destruye a las sociedades europeas actuales](https://hiperbolajanus.com/posts/presentacion-izquierda-contra-pueblo-carlos-blanco/).
En este sentido, hubo otro pensador más reciente que recogió el testigo de Marcuse, como fue el caso de **Hans-Georg Gadamer** (1900-2002), discípulo de **Heidegger**, que mantiene una postura especialmente crítica con la acción de los _mass media_ sobre la masa, destacando la capacidad de éstos para hacer apáticos a los individuos, de domesticarlos y adormecer su capacidad de juicio y del gusto, de hacerlas pasivas y poco receptivas al diálogo y al hábito de pensar, además de su capacidad de lanzar mensajes al subconsciente. Estas consideraciones condujeron al filósofo alemán a definir la televisión como [«la cadena de esclavos a la cual está vinculada la humanidad actual»](https://hiperbolajanus.com/posts/posmodernidad-y-orden-moral/).
El contexto del mundo en el que se concibieron los discursos distópicos de Huxley y Orwell, pese a la clarividencia y agudo juicio de sus autores, no tenía en cuenta elementos que hoy se antojan indispensables para juzgar los tiempos actuales. Nos referimos a la aparición de internet, una herramienta tecnológica, de uso masivo y quizás con una doble vertiente, pues al mismo tiempo que permite identificarnos, entregar nuestros datos y opiniones voluntariamente, con la posibilidad de elaborar estudios de mercado y perfiles específicos, como herramienta de control, también hace posible estrechar vínculos y construir redes que pueden ser utilizadas en contra del propio sistema, algo que ya apuntamos en un artículo precedente.
Pero profundizando más en el ámbito de la manipulación mental, es obvio que se han trabajado desde hace décadas técnicas de manipulación relacionadas con la llamada «programación neurolingüística», utilizadas en los comicios electorales, relacionados con técnicas específicas de los discursos y de las propias campañas de mercadotecnia. En este sentido son famosas las técnicas desarrolladas por el psiquiatra estadounidense **Milton Erickson** (1901-1980), en cuya obra desvela el uso de «trucos» relacionados con el lenguaje corporal, sugestiones, y otras técnicas de control mental. La programación neurolingüística (PNL) fue desarrollada a partir de 1975, con objetivos pretendidamente «terapéuticos» por el psicólogo Richard Bandler y el lingüista John Grinder. El nombre de la disciplina deriva de una conexión entre los procesos neurológicos, el lenguaje y los esquemas de comportamiento aprendidos de la experiencia, cuya síntesis podría alcanzar resultados específicos, y útiles, en la vida psicológica de los individuos. La técnica desarrollada por ambos autores, Bandler y Grinder, se basa en una programación de la realidad mediante la programación de la realidad a través de la introducción de información en los tres canales perceptibles principales: el visual, el auditivo y el cinestésico (piel, emociones etc). La idea era que el hombre crea su imagen del mundo a través de estos tres canales de entrada, aunque el principal medio para inducir a la programación es el lenguaje: el poder de las palabras es fundamental para generar esa «alucinación» perceptiva.
|[](https://hiperbolajanus.com/libros/cibergeopolitica-organizaciones-alma-rusa-leonid-savin/)|
|:-:|
|[SAVIN, Leonid; _Cibergeopolítica, organizaciones y alma rusa_, Hipérbola Janus, 2015](https://hiperbolajanus.com/libros/cibergeopolitica-organizaciones-alma-rusa-leonid-savin/)|
Esta técnica se ha venido difundiendo desde los años 70 hasta el presente en diferentes sectores, como la psicoterapia o la mercadotecnia y en general en el ámbito empresarial. No olvidemos el famoso _coaching_, y terapias de tipo motivacional por el estilo, hasta alcanzar a la propia política y a su inescindible aparato mediático (televisión, prensa etc). Es evidente que su uso ha trascendido esa dimensión «terapéutica» y «curativa» para ser instrumentalizada con propósitos más siniestros, que venimos describiendo en este artículo, y cuya intención no es otra que la de someter las mentes de la masa. El ejemplo más paradigmático, hemos de insistir en ello, fue la _Plandemia_.
Obviamente, este tipo de condicionamientos que nos señala la Programación Neurolingüística, no nacieron de la forma inocente y altruista de los orígenes, sino que viene a ser una parte esencial de una serie de investigaciones que se iniciaron durante los años 50 y 60, por parte de psiquiatras y otros especialistas y financiadas por la CIA y que recibieron el nombre de **Proyecto MK-ULTRA**. En este sentido, Huxley, en su función visionaria, hablaba de la posibilidad de inducir al individuo a creer en cualquier doctrina, convirtiendo al individuo en un ser moldeable hasta extremos hasta entonces inconcebibles.
Este proyecto, enmarcado en un conjunto de investigaciones que se estaban desarrollando en ambos bandos, también en la parte soviética, por parte de rusos, chinos y coreanos, en torno al «control mental», no tenía, obviamente, como propósito ningún tipo de fin humanitarismo ni terapéutico, sino la posibilidad de dañar al bloque geopolítico opuesto, en pruebas que contaron, a modo de conejillos de indias, con prostitutas, enfermos mentales y personas comunes e incluía el uso de radiaciones, hipnosis e incluso la administración de drogas psicotrópicas como el LSD. No vamos a relatar el largo historial que la CIA y Estados Unidos tiene en susodichos experimentos, con notables perjuicios contra terceros países, puesto que supondría otro artículo en sí mismo. También se habla de prisioneros de la guerra de Corea y de otras guerras anglosionistas, junto a centros de internamiento como Guantánamo, donde se usaron conejillos de indias para estos experimentos.
Una de las consecuencias de estos experimentos e investigaciones los encontramos también en la estrategia del _Shock Economy_, elaborada por el autor liberal y premio nobel de economía **Milton Friedman** (1912-2006) que proponía la explotación de los momentos de crisis y traumas colectivos para ir implementando medidas radicales de ingeniería social y económica. Y es que el propio Friedman era consciente de que solamente en momentos dramáticos y de urgencia era posible inducir cambios a nivel colectivo, de tal modo que lo que se consideraba hasta entonces imposible se hacía posible. En este sentido, y vuelve a ser inevitable, debemos dirigir nuestra mirada, una vez más, a la _Plandemia_ y la aceleración que ha venido protagonizando la Agenda 2030 en los últimos tiempos. Pero los efectos de las doctrinas de Friedman ya se dejaron sentir mucho antes con los golpes de Estado y torturas perpetradas frente a aquellos países y personas relevantes que se oponían a la Agenda liberal, o neoliberal, que desde los años 60-70 pudieran representar algún tipo de oposición o forma de resistencia al avance implacable del globalismo y sus adláteres.
Friedman ha sido el fundador de la **Escuela de Chicago** y sus directrices y teorías económicas han sido utilizadas tanto por la Reserva Federal estadounidense como por el Banco Central Europeo, así como durante los años 80 ejerció una notable influencia en los gobiernos de **Ronald Reagan** (1911-2004) y **Margaret Thatcher** (1925-2013), así como también conviene destacar su influencia anterior, a comienzos de los años 70, sobre las reformas de corte liberal del gobierno de **Pinochet** en Chile. Quizás haya alguna relación entre estas teorías y las continuas crisis económicas y el creciente control de las economías nacionales por parte de organizaciones transnacionales a través de la deuda, de esa deuda que el propio **George Soros** (1930) querría que fuese a perpetuidad.
De este modo, tampoco es muy complicado trazar una vía de conexión entre los experimentos de la CIA en torno al «control mental» desde los primeros años de Guerra Fría, y las teorías del neoliberalismo globalista que se han sistematizado desde esa época hasta nuestros días, y lo peor es que lejos de ser aceptadas libremente, algo imposible por su carácter nocivo y autodestructivo, vienen a imponerse de manera violenta, eliminando toda resistencia. Recordemos que el miedo es una herramienta especialmente poderosa, que permite ablandar las mentes y hacerlas moldeables y receptivas a cualquier discurso, abandonando con ello toda función lógica y racional, generando una suerte de impacto psicológico, una experiencia traumática que hace que el mundo de convicciones e ideas hasta entonces aceptado se rompa en mil pedazos. Ante esa situación, cuando las personas se encuentran en situación de _shock_, es cuando se muestran más dóciles y serviles ante quienes se presentan como benefactores o autoridad en la que depositar toda la confianza. Y nos podemos imaginar que en sociedades sobresocializadas como las nuestras, es mucho más fácil porque la identidad del individuo demoliberal es especialmente frágil y débil.

Hay indicios que nos invitan a pensar que es posible que Aldous Huxley pudo haber participado del **Proyecto MK-ULTRA**, tema en el que ahora mismo tampoco podemos profundizar. No obstante, se han proporcionado detalles sobre la participación del novelista inglés en este programa secreto, y con mayores atribuciones que mucho personal militar de alto rango. Huxley ya había colaborado previamente con los servicios secretos británicos y posteriormente con los estadounidenses, a partir de 1937, trasladándose a California, donde residiría por el resto de sus días. Durante esa época empezó a experimentar con drogas psicotrópicas, como la mescalina, influenciado por la sociedad de magia ceremonial **Golden Dawn**, siendo un gran promotor de las drogas psicodélicas desde entonces. Así lo confirma también el testimonio de otros autores como **Aleister Crowley** (1875-1947). Las experiencias con estas drogas serían posteriormente relatadas por el propio autor de _Un mundo feliz_ en otra obra, quizás menos conocida, bajo el título de _Las puertas de la percepción_, publicado en 1954. Incluso se habla de su sometimiento a experimentos relacionados con la esquizofrenia y la alteración de la percepción relacionados con el citado programa bajo la supervisión del psiquiatra Humpry Osmond, para quien trató de conseguir financiación a través de organizaciones globalistas como la _Ford Foundation_ y la _Round Table_, ésta última una organización pantalla de la propia CIA. Muchas de las conclusiones de estos estudios, experimentos y programas de manipulación a gran escala son relatados con todo lujo de detalles por el periodista y escritor italiano **Maurizio Blondet**, a través de la obra, publicada por nuestro sello editorial, [_Complots_](https://hiperbolajanus.com/libros/complots-maurizio-blondet/).
|[](https://hiperbolajanus.com/libros/complots-maurizio-blondet/)|
|:-:|
|[BLONDET, Maurizio; _Complots_, Hipérbola Janus, 2020](https://hiperbolajanus.com/libros/complots-maurizio-blondet/)|
Los últimos atisbos o señales de esta manipulación masiva en el presente, cuya responsabilidad ya hemos atribuido a los _mass media_, los tenemos en la Europa occidental del presente, con sus democracias liberales cooptadas por los poderes globalistas y supeditados al cumplimiento de una Agenda. Así, por ejemplo, el tema de la «inmigración»[^1] masiva y no tan descontrolada como muchos creen, sino más bien planificada, con los enfrentamientos de los que estamos siendo testigos en el Reino Unido en las últimas semanas, también responden a complejas ingenierías sociales de manipulación mental, donde el elemento distópico, ciertamente, no se encuentra ausente. Las autoridades británicas, destruyendo durante décadas toda forma de cohesión social y entregado al experimento multicultural de cuño globalista, han dividido y polarizado su país, como en el resto de la Europa Occidental, utilizando con toda probabilidad las herramientas de las que hemos estado hablando, refinadas técnicas de manipulación y control mental, para convencer a la masa de que renunciar a sus raíces, a su Patria, a su propia idiosincrasia como pueblos, y convertirse en territorios sin identidad, con individuos atomizados e intercambiables, es algo deseable en nombre de un «progreso», totalmente abstracto y vendido como una especie de Arcadia feliz, con esa misma proyección teleológica que ha sido característica del liberalismo desde sus discursos decimonónicos.
||
|:-:|
|Protestas en el Reino Unido por el aumento de la inseguridad en las calles|
[^1]: Nótese la manipulación del lenguaje en el término que recientemente utiliza la prensa: «migración» o «migrante», prescindiendo de los prefijos _in-_ o _e-_, para dar a entender de forma indirecta que ni se entra (_in_-migrante) ni se sale (_e_-migrante) de ninguna parte porque «no existen fronteras», si no que la gente simplemente se desplaza.
---
**Artículo original**: Hipérbola Janus, [_Distopía y manipulación de mentes_](https://www.hiperbolajanus.com/posts/distopia-manipulacion-mentes/) [**(TOR)**](http://hiperbolam7t46pbl2fiqzaarcmw6injdru4nh2pwuhrkoub3263mpad.onion/posts/distopia-manipulacion-mentes/), 27/Ago/2024
-

@ af9c48b7:a3f7aaf4
2024-08-27 16:51:52
## Chef's notes
Easy recipe with simple ingredients. This recipe uses some store bought, precooked items as way to cut down on cook time. I recommend letting the vegetables thaw if you don't like them on the firm/crunchy side.Feel free to substitute fresh ingredients if you have the time and want to make the extra effort.
## Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 50 min
- 🍽️ Servings: 8-10
## Ingredients
- 2 (8 oz) packages refrigerated crescent rolls (dough sheets preferred)
- 1 pound cooked rotisserie chicken (deboned and chopped)
- 2 table spoons of butter
- 2 (10 once) packages of frozen mixed vegetables
- 1 (15 once can sliced potatoes (drained)
- 1 (10.5 once) can condensed cream of chicken soup
- 1 (10.5 once) can condensed cream of mushroom soup
- 1/2 cup milk
- salt and ground pepper to taste
## Directions
1. Preheat oven to 350 degrees F (175 degrees C). Line the botton of 9x13-inch baking dish with one can of crescent roll dough. If you don't get the sheet dough, be sure to pinch the seams together.
2. Melt the butter in a sauce pan over medium heat. Then add the chicken, mixed vegetables, and sliced potatoes (recommend cutting into smaller pieces). Cook, stirring frequently, until vegetables are thawed and mixture is heated through, 5 to 7 minutes.
3. While the mixed vegetables are heating, warm both cans of condensed soup in a seperate pan over medium-low heat. Slowly add milk and cook, stirring frequently, until combined and heated through, about 3 minutes.
4. Add the soup mixture to the chicken mixture, then pour into the baking dish. Top with the second can of crescent roll dough. Feel free to cut some slits in dough if you are using the dough sheets. Cover lightly with foil to prevent the crescent roll dough from browning too quickly.
5. Bake in oven until heated through and dough is a golden brown. Cook time should be around 45-50 minutes I reommend removing the foil for the last 10 minutes to get a golden crust. Be sure to keep a close watch on the crust after removing the foil because it will brown quickly.
-

@ b83a28b7:35919450
2024-08-27 16:48:28
https://image.nostr.build/df0721d6d45d82db35d06663a0318ffe68c0b2b3c694888d23694efcc4255de5.gif
-

@ 0861144c:e68a1caf
2024-08-27 14:01:14
On Sunday afternoon, while I was taking a nap, my phone started buzzing with notifications. In the various groups where I share my views and words, I saw that Pavel Durov had been arrested by the French police. There wasn’t much to analyze yet, but alarms were raised, and theories began to circulate, and those theories were not far from reality.
Pavel is practically accused of every digital crime one can commit, from criminal association to pedophilia. My eyes kept scrolling down, unable to believe all the accusations. Could even 10% of what they’re questioning him about be true? And unfortunately, the worst blind person is the one who doesn’t want to see.
Detractors claimed that Telegram served totalitarian regimes and handed over data, when in reality, the opposite is true, as this social network served as a reference point when people in Belarus were protesting for their civil rights. They also alleged that Telegram collaborated with the Russian government to evade sanctions or promote disinformation campaigns, but if anyone takes the trouble to [watch the 60-minute interview with Tucker Carlson](https://x.com/TuckerCarlson/status/1780355490964283565), they’ll see that one of the reasons Pavel left his homeland (Russia) is because the government pressure simply became unbearable; Putin took over VK because Pavel refused to be part of it.

So, we already know that Russia has no interest in Telegram, nor is it anti-democratic, as the movements have already demonstrated, which leads us to the question of whether the French really have interests with Telegram.
And my first response after reading Macron’s statements was precisely that they were seeking his arrest until we read that Macron [is an avid user of this social network](https://www.politico.eu/article/telegram-pavel-durov-arrest-emmanuel-macron-france-social-media/), but also that it was [Macron himself who _encouraged_](https://www.lemonde.fr/en/france/article/2023/06/26/the-telegram-founder-s-mysterious-french-passport_6037748_7.html) Pavel to obtain his French passport. So, let’s ask a long question:
> **What leads a European liberal democracy to arrest the CEO of a social network with charges that could easily apply to other social networks?**
Try a simple experiment: take out the word Telegram and insert your social network of choice in the accusatory libel. It has the same effect, and the previous question arises again, and I’d like to offer an alternative perspective on this process. To this day, and I’ve mentioned this before in other posts in this same place, but I’ll emphasize it: we no longer have democracy as such. You can forget about the liberal style that was once promised to us or that we learned about in our educational institutions. This has been replaced with Dataism.
### Dataism and How Pavel Doesn’t Cooperate
[Dataism](https://en.wikipedia.org/wiki/Dataism) is a new form of governance. The word data comes from the Latin *datum*, which means "to give," meaning we, the citizens, *give* our data to the companies that manage social networks. These companies, while using us as a product for other companies, also see governments trying to dip their spoon into the pot, so they start talking about *speech regulations*, *hate content*, among other accusations, to maintain a *clean social network*.
I’m guilty first. In the old days, when the chief censors operated in the former Soviet Union (as Coetzee tells us), folders were created with the data of suspects, documenting their *revolutionary* activities, and when the time came, *measures* could be taken that affected the welfare state.
Today, this type of persecution no longer exists, but by handing over my data, companies no longer talk about tracking me, since we’ve given them free access to our location and GPS, in addition to exposing our lives on every platform; today, profiles are made, and now there’s a marketing department that creates *behavior profiles* and bombards me with products and services that *might interest me*.
The government’s intrusion into social networks has become so great that now they had to react, showing a sort of repentance. As I write this, I find it really hard to react to the letter sent by Meta (signed by Zuckerberg himself) in which [he regrets the censorship](https://x.com/JudiciaryGOP/status/1828201780544504064) carried out during the pandemic. And I vividly remember the hundreds of people whose accounts were censored, rightly or wrongly, for not aligning with the government’s *scientific* stance.
### And Telegram?
Telegram [doesn’t hand over data](https://www.dw.com/en/brazil-court-lifts-telegram-suspension-despite-non-compliance-for-neo-nazi-group-data/a-65474168#:~:text=Brazil%20had%20temporarily%20banned%20Telegram,prioritizes%20the%20privacy%20of%20users.&text=A%20federal%20judge%20in%20Brazil,Telegram%2C%20an%20encrypted%20messaging%20app.) and paid the price. It refused to do so in the past and stood against the current regime, against dataism. The French justice system wants Pavel to spend time in prison for daring to use encrypted products that don’t allow them to listen to/see/read their *possible suspects*. The KGB would blush at such a move. And the most ironic thing is that a person who flees his own country for not wanting to cooperate with values contrary to freedom is now arrested by a country that was once the center of debates on liberty, fraternity, and equality, where they rose up against the oppressive regime.
I don’t know how the process will continue on French soil, and I also don’t know if the Russians are really using USDT networks to move *sanctioned* money. I only know that this kind of arrest proves and gives reason to those who argue that freedom, as we knew it, no longer makes sense.
### And I don’t know what else to tell you, my friend.
Unfortunately, I have no conclusion. I wish I could end this article and give you hope that justice will respond to see what they’re accusing him of, but it [would be a lie on my part](https://stacker.news/items/560694). I can tell you, however, that if you’re reading this and have a NOSTR account and use bitcoin as part of your economy, you’re on the right path.
Sites like Stacker News and others, as well as protocols like NOSTR, will gain greater importance as we open our eyes to fight the regime that seeks to abolish privacy as a human right. Today we can fight, and it doesn’t require much of us, other than to promote what we are doing now.
And I’ll end by asking the same question that @FmpPerspective did: [*are we still allowed to ask questions?*](https://stacker.news/items/662413)
originally posted at https://stacker.news/items/663527
-

@ 5d4b6c8d:8a1c1ee3
2024-08-26 17:50:00
This was my first year betting on preseason football and I came out about 20% ahead. My operating assumption was just that no one should be a heavy preseason favorite, so I took any team that was at least +200 to win outright.
I'm really looking forward to the real season starting. I've got my eyes on that Raiders vs Chargers opener. Every year the Bolts underachieve, while the Raiders overachieve (based on expected wins).
Nitrobetting got some NBA futures up. I took OKC at +750 and the Bucks at +1200 to win the title.
What are the upcoming events you're looking forward to?
originally posted at https://stacker.news/items/662590
-

@ 5d4b6c8d:8a1c1ee3
2024-08-26 17:01:11
There's a very interesting dynamic developing in the American political media landscape. Don't worry, this post isn't explicitly political.
One of the huge incentive problems in media is needing access to important people in order to cover them. Objective, or otherwise critical, journalists may be denied access, while favorably biased journalists are granted it. This is known as "access journalism". Despite being a very well-known problem, it remains an intractable issue for the industry.
The Kamala Harris campaign has been blatantly denying access to even friendly outlets, which violates the basic logic of access journalism. The expectation then is that she'll get more objective or critical coverage, and I think we've been seeing that.
Part of why this is so interesting to me is that the American corporate press has a dramatic bias towards Democrats and against Trump (even more so than a generic Republican). Bias and incentives are clashing.
I often say that outcomes follow incentives. If so, then we should expect to see even more critical coverage of Kamala, unless she begins granting more press access.
originally posted at https://stacker.news/items/662537
-

@ 0271e1b9:ad8cff90
2024-08-26 16:33:28
Hey everyone,
So during the weekend I launched a little side project called:
# "A Stoic Resurrection"
https://image.nostr.build/682ddced4e4c823dcdc28bd34cc920ce0802964b170f9fa08295a89afe08df6c.jpg
For now I will be sharing my favorite quotes from both historical and contemporary thinkers in the form of photos or short videos, plus some of my own thoughts, as I have noticed they seem to be very much aligned with the Stoic philosophy in general.
I played around with some ideas regarding the design and aesthetics, and settled on this kind of style for now:
*Photo examples*
https://image.nostr.build/878bf80e40c522320820e766723dcd7b2ea5a4029dc8effd9c66a56f0fbbbc54.jpg
https://image.nostr.build/3d994d3fb52def142d4b331ef0edb53a9862c8ab071d57da580a8fa08430198a.jpg
https://image.nostr.build/d583755e9065cc5c49357ead1734e7e2ab5d43c56bd3345cb14331cab61cd505.jpg
*Video examples*
https://youtube.com/shorts/OMKKRQ4zNLM
https://youtube.com/shorts/UkFBFBniCp8
For now I'm using copyright free images from [Unsplash](https://unsplash.com/) plus copyright free recordings of classical music via [Musopen](https://musopen.org/) (starting off with Chopin) for the content as per my *Open Source Culture* philosophy.
**The current goal is to post 1 quote per day on average.**
I do have some additional ideas for the future, but as I said, this is a side project and how much time & energy I'm going to invest in this will depend both on the amount of free(ish) time I have on hand, my current level of interest in the subject, as well as how much demand & audience there is (or isn't) for this kind of content.
### Please feel free to share your thoughts, criticisms, suggestions, and perhaps some of your personal favorite Stoic thinkers / ideas from both past and the present that have caught your attention.
**Oh, and of course, if stoic philosophy sounds like your cup of tea, please feel free to give the project a follow on your preferred social media platform(s) and/or show your appreciation with zaps:**
nostr:
nostr:npub1angxrnwzujemyzkhgef2gwcy0s4ayjh62574p8g2xwnlfp8pxeaq4frrpe
[X](https://x.com/stoic_resurrect)
[YouTube](https://www.youtube.com/channel/UCb5MZ0YL7BlBLFKHpLVAHkg)
[Instagram](https://www.instagram.com/stoic_resurrection/)
[TikTok](https://www.tiktok.com/@stoic_resurrection)
### Peace & love,
### Kontext
-

@ 5d4b6c8d:8a1c1ee3
2024-08-26 16:27:09
This is your chance to update your predictions from July: https://stacker.news/items/619305/r/Undisciplined. August picks are due before the end of August.
If you're new, check out the [June post](https://stacker.news/items/585231/r/Undisciplined) for details. This contest will be open to new entrants all the way through the end of the NBA regular season.
If you want to join, put your predictions in the comments for MVP, Champion, and All NBA 1st Team.
## Current Predictions
| | @Undisciplined | @grayruby | @gnilma | @BitcoinAbhi | @Bell_curve | @0xbitcoiner |
|-|------------------|---------------|--------------|---------------------|-------------------|-----------------|
| Champ | OKC | Pacers | OKC | Denver | Celtics | Pacers |
| MVP | Luka | Giannis | SGA | Luka | Luka | Jokic |
| All NBA | Jokic | Jokic | SGA | Jokic | Jokic | Jokic |
| | Giannis | Giannis | Jokic | Giannis | Giannis | Giannis |
| | Luka | Luka | Luka | Luka | Luka | Luka |
| | Ant | Mitchell | Brunson | Ant | Ant | Ant |
| | SGA | Brunson | Wemby | SGA | SGA | Brunson |
The only change last month was me switching my title pick to OKC.
# Prize
1334 sats (plus all future zaps)
originally posted at https://stacker.news/items/662489
-

@ dd664d5e:5633d319
2024-08-24 07:57:16
# We can talk about something else, now.
Making boosts/quotes the primary way new users find a variety of topics is a fundamental flaw. We don't need boosts (which merely results in the main trending list trending even harder, as people feel safer boosting something that is already popular), and hashtags have become the mess they naturally will become.
## We need topical forums and relay-based community boards.
This would actively encourage those of us who want to write on OtherTopics to write more on them, as we would have some chance of the material being found by those interested in it. And it would spare us having to win some general popularity contest, just to be able to converse about golfing, Hinduism, or veganism.
Scrollable "timeline" feeds, even with AI assistance (like DVMs), don't accomplish this as well, as they eliminate the ability to skim the top-level and selectively read. You have to scroll, scroll, scroll.
It would also reduce the overloading of the original posts with videos, which is starting to give Nostr a Tik-Tok vibe. There's nothing wrong with that, per se, and we should probably have clients like that, but it makes life hard for anyone who wants to have a deeper discussion. People scrolling have trouble even "seeing" a text-based OP, but using the written word is a true signal to the other people, that you are capable of carrying a conversation through text.
## Examples for other styles of client
(I am including the Communities in Nostrudel and Satellite, even though they don't yet work, effectively.)
Some of the things that set these clients apart, is that:
1. they are topic-first or thread-first, not person-first,
2. they sometimes allow voting (I suppose we could rank by zaps),
3. they often allow the user to override the default order and simply look at whatever is newest, most popular, or where their friends are currently active (i.e. they allow for easy sorting and filtering),
4. they cap the depth of threads to one or two levels, keep the indentation tiny, or offer a "flat" view,
5. they are primarily text-based (Reddit broke with this and now their main pages look really spammy),
6. they allow you to see all of the entries in the thread, at once, and simply actualize to display the entries that pop up in-between,
7. they often have some indication of what you have already read (this is application data) and allow you to sort for "stuff I haven't looked at, yet".
https://i.nostr.build/uCx5YKMOsjhKBU5c.png
https://i.nostr.build/hMkm2oKpos0pWaV9.png
https://i.nostr.build/mGQONMw5RC8XKtph.png
https://i.nostr.build/TCSkG1bPuMOL0jja.webp
https://i.nostr.build/3fLjCSNdtefiZmAH.png
https://i.nostr.build/BHgo7EKTK5FRIsVl.png
-

@ 91687725:a0de48ea
2024-08-24 05:40:14
こんにちは。Kateです。
最近ちょっとお休みしていますが、日本でビットコインを専門に扱う[Diamond Hands Magazine](https://diamondhandscommunity.substack.com/)に寄稿したりしてます。
私がビットコインと出会ったのは2011年、まだビットコイン利用者はとても少なかった時代です。たまたま身内にビットコイン界隈の人がいました。もしかしたら今でいうビト妻だったかも?
まだビットコインが1ドル以下でおもちゃみたいな存在だった頃に知ったわけですが、その後勢いづいて、100ドル、1000ドルと価値が上がっていきました。
それを見て、ビットコインを少しずつ買って貯めておけば、将来リタイヤの蓄えになるかもと思ってお小遣い程度のビットコインを積立してました。でも、アクシデントで失くしちゃったんですよね。
その後、身内のごたごたで自分の生活が天地がひっくり返るように一変し、気がつけばカナダでただお金がないアジア系移民シングルマザー、しかも周りに家族が誰もいないという、非常にマイノリティな立場になりました。
人生、何事も経験。一度ビットコインを失くし、傷心もあり、数年はビットコインから離れました。でも気がつけばビットコインは冬の時代を終えて、また元気になっていたんですね。自分は海外でひとり子育てに追われ、なんとか生きてた感じですが!
ビットコインが500ドルくらいになっていた時に困窮していた私は、ふとペーパーウォレットと呼ばれた当時の携帯可能ウォレット?に0.5btc 残っていたのを発見して速攻換金しましたね。悔やまれます。
その後、2017年頃、カナダで当時大手の割と使い勝手のいい取引所があることを知って、再度ビットコイン貯蓄にチャレンジしました。2年ほどで、ほぼ1ビットコインと10ETHくらいあったんですけどね、今度は取引所の代表者が行方不明になり、またもやビットコインを失くしました。
ふつうだったら、もうやめますよね。2回もなくしたら。
けれど、自分はかつてインターネットが始まったころのワクワクを経験していました。90年代半ば、新宿にできたばかりのインターネットカフェで、GIFがかろうじて表示できるグレーのブラウザ画面と対面しました。世界を変える技術を体験した時の感動は今でも忘れられません。
(こう書くと立派なオバサンなのがバレちゃいますね。ビットコインネイティブ世代の中では年長者)
それから15年以上たって、初めてサトシナカモトのホワイトペーパーを読んだ時に、同じ衝撃を受けたのです。初めて実用化されたインターネット上で世界の誰とでも送り合えるマネー。その可能性は無限∞。
そのビットコインの進化を、実際に買ってみたり、使ってみたり、なくしたりしつつ、より深く知ろうと付き合ってきた自分は、いつの間にかビットコインを通して世の中のいろいろを見て考えるようになりました。
ビットコインが生まれ、実験段階を経て、すでに15年が経ちます。けれども、ビットコインは今でも多くの人から最も誤解されている技術・発明のように見えます。ここまで来たら、自分が生きている間に、ビットコインが世界とどう関わっていくのか見届けたいと思います!
そして、私自身がビットコインを知ることで発見した世界や新しい価値観を、誰かに伝えられたらいいなと願って、このブログをスタートすることにしました。
今回は自己紹介という形になりましたが、私がビットコインを通して学んだことや気づいたことをこれから少しづつアップしてみます!
週1くらいのペースで投稿が目標です。よろしくお願いします。
-

@ f8e6c643:03328ca9
2024-08-23 16:15:50
Quality, authentic, original human artistic expression is always in demand. It has always been in demand, and it will continue to be in demand even beyond the age of AI. The internet today calls it “content.” It is how we seek to encapsulate and communicate ideas more richly, and it comes in various forms including written, audio, and visual.
Anyone who creates content in any form knows that it is time consuming and costly to create and produce good content, especially to do so consistently. However, because of digital distribution methods, once released that content that was so costly to create is suddenly infinitely RE-producible with perfect fidelity for very little cost. The conundrum for artists/creators is that even though the demand for their work exists, and even though that work is costly to create, each final product they produce is infinite in supply as soon as they release it in digital form. Infinity has no value.
Starting with the presumption that demand exists for art, and that it is reasonable for an artist to want to afford things like food, housing, and clothes, how do you make the work of creating content economically sustainable for those creating it? We find value in scarcity, and the scarce resources in the equation of content creation are ultimately the time, talent, and skill of the person doing the creating.
People often want what a particular artist can produce. Perhaps it’s the artist’s skill, style, and precision; or perhaps it’s the artist’s particular interpretation and personality they find valuable. The skill, time, and talent/personality employed to create artistic expressions are valuable, and their supply cannot be easily reproduced/replicated even though the individual manifestations of them (the works of art) can be. This is, ultimately, what creators must figure out how to monetize if they are to make their work economically sustainable.
So how much is an artist’s skill worth? How much is their time or their talent worth? How do you put a price tag on personality? Probably nobody, especially the artist, can really answer that objectively. However, with #value4value the consumers of an artist’s content can subjectively and individually decide for themselves how much it is worth to them.
Nostr and Bitcoin give creators of every type of content the opportunity to directly own and control the distribution and monetization of their time, skill, and talent, more so than any other service or platform on the Internet. The #value4value approach to monetizing that content allows consumers to immediately have access to a creator’s work, and to individually place a subjective value on what it provides to them. The approach allows artists to focus on the work of creating art and building a reputation and relationship with their audience instead of worrying about how to control access to their work. And by using Nostr and Bitcoin, this approach allows artists to be free of the arbitrary rules and manipulation they face on other corporate ad-driven platforms.
If you are a digital content creator, I think #value4value is worth giving a chance. The alternatives are increasingly less promising.
-

@ e5272de9:a16a102f
2024-08-22 22:16:43
One of the highlights for me at the first day of nostriga [nostriga](https://nostr.world) was a [panel discussion on web of trust](https://www.youtube.com/live/Zv766SV840k?t=8265) with [@Stuart Bowman](nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj), [@Pip the social graph guy](nostr:npub176p7sup477k5738qhxx0hk2n0cty2k5je5uvalzvkvwmw4tltmeqw7vgup), [@PABLOF7z](nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft), [@hzrd149](nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr), and [@ODELL](nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx). This to me is one of the most important topics in all of freedom tech, so I'd like to write up a few thoughts I had while they're still fresh on my mind, most of which revolve around the calculation of trust scores. Apologies if it's a bit long winded, don't seem to have the time to make it shorter.
## What do we use for raw data?
There has been and on again, off again discussion during my time working in nostr over the sources of data that we should be using to calculate trust. In my mind we can think of the raw data as existing on a spectrum between two extremes. On one extreme, we have what I call *proxy indicators* of trust: follows, mutes, zaps, reactions, etc. People don't create this content with trust scores in mind, but we can and do use them as imperfect proxy indicators nontheless. And on the other extreme we have what I call *explicit trust attestations*, exemplified by the [proposed NIP-77](https://github.com/nostr-protocol/nips/pull/1208), authored by [Lez](nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume), the heart and soul of which is that a fully explicit contextual trust attestation should have 3 fields: a context, a score, and a confidence. You fill in these fields, you say what you mean, and you mean what you say, leaving as little room for interpretation as possible. And then there is data that's in between these two extremes. A five star rating for a host on a couchsurfing platform or a vendor on an ecommerce site? A "superfollow" option in addition to a follow? These lie somewhere on the spectrum between proxy indicators on one end and explicit attestations of trust on the other.
During the panel today, Pablo and pippellia expressed the opinion that explicit trust attestations are not the way to go. Two reasons that I recall: first, that no one wants to put an exact number to trust; and second, that no one will update those numbers even if their assessment changes. These critiques have some merit to them. But I believe they miss the bigger picture.
# The bigger picture
In the real world, there are two ways I can communicate trust: I can SHOW you, or I can TELL you. I can *demonstrate trust through the actions that I take*, such as following someone, or I can just straight up tell you that I trust someone in some context.
So here's the question: on nostr, which is the correct method to communicate trust? Proxy indicators, or explicit attestations? Do we SHOW or do we TELL?

My view is that we don't have to pick. We have to use all relevant and available raw data across the entire spectrum from one extreme to the other.

Each of these two options has its advantages and its disadvantages. The advantage of proxy indicators is that users issue them freely and easily, the result being that we are awash in a sea of data. The primary disadvantage of proxy indicators is that they often don't mean what we want them to mean. If Alice follows Bob, does that mean she trusts him? Maybe. Or maybe not. More often not. And what about context? Do we have any way of knowing?
So we use proxy indicators as a trust indicators because ... if it's the best or maybe even the only data we have, what else are we gonna do?
To do better, I argue that we need to give users more options when it comes to issuing explicit indicators of trust. But of course they're not going to do that without a reason. So to give them a reason, we have to figure out *ahead of time* how we're going to use the data once it's available. We have to know how to incorporate explicit trust indicators into our web of trust calculations. For the sake of argument, let's assume that we have a large dataset of proxy trust indicators (SHOW ME data) plus a small but nontrivial dataset with explicit trust attestations (TELL ME data). What we want to do is to pool *all available relevant data together* when we calculate trust scores. But how exactly do we do that? Which brings me to my next topic.
## The calculation of trust scores
How are we even calculating the "web of trust scores" that we see today? Wikifreedia, Coracle, and a growing list of other clients have such scores. I wish I had seen more discussion in today's panel about HOW these calculation are performed. To the best of my knowledge, most clients use the same or a similar method: fetch my follows; fetch Bob's followers; calculate the set of users who are in both sets; and count up how many you get. Sometimes adjustments are made, usually a ding based on mutes. But usually, that's it. That's the WoT score.
I'll call this the "legacy WoT score" since it is basically the state of the art in nostr. The legacy WoT score can be a useful way to eliminate bots and bad actors. But it has a few disadvantages: it is, arguably, a bit of a popularity contest. It cannot see more than two hops away on your social graph. It's not very useful to new users who haven't yet built up their follows. And it's not clear how to use it to differentiate trust in different contexts.
It seems strange to me that so many clients use this single method to calculate WoT scores, but with relatively little discussion on the merits of this method as opposed to other methods. Or whether other methods even exist, for that matter.
Indeed, I believe there is another method to calculate trust scores that in most circumstances will turn out to be much more meaningful and useful. For the sake of this article, I will call this the "Grapevine WoT score" to distinguish it from the legacy WoT score. (Elsewhere I have used the phrase "influence score" in place of "Grapevine WoT score.")
The Grapevine method is (currently) based on follows and mutes, but calculated using a method entirely distinct from the legacy method, detailed [here](https://brainstorm.ninja/#/grapevine/influenceScore) (where it is called simply the "influence score"). The Grapevine method has several advantages over the legacy method, but one in particular on the topic of SHOW versus TELL: the Grapevine method can take multiple distinct classes of data following distinct formats and pool them together, synthesizing and distilling them into a single Grapevine WoT score. By choosing different datasets, different scores corresponding to different contexts can be generated.
## The future
So here's my prediction on how the future will play out.
1. The Grapevine method of trust score calculation is going to rely -- at first -- primarily on proxy indicators of trust (follows, mutes, zaps, reactions, etc) -- SHOW ME data -- because that’s the data that’s available to us in large quantities.
2. These contextual Grapevine scores will turn out to be surprisingly useful.
3. *People will learn to game the scores by changing their behavior.*
5. Consumers of trust data will gradually discover that SHOW ME data is becoming less and less reliable.
6. Authors of raw trust data will gradually learn that if they want their voices to be heard, they will need to communicate trust more explicitly. In ways that are harder to game. They will begin to move the needle ever so gradually towards TELL ME data.
7. Over time, larger datasets of TELL ME data will be available for input into Grapevine WoT scores.
8. As SHOW ME data becomes less reliable, and TELL ME data becomes more available, contextual Grapevine WoT scores will become more fine grained in terms of context and more reliable.
Of course, none of this will happen unless and until we start calculating Grapevine WoT scores and putting them to good use. To that end, several of us are working on the generation of these scores at [brainSToRm](https://brainstorm.ninja). Right now, it's a slog to download the data to the browser. But we're working on improving the UX. And if you make it through the slog, you can export a NIP-51 list of the top-scoring pubkeys, minus the ones you're already following, and use them at clients like Amethyst or Coracle to generate a feed of content coming from the most highly "trusted" users whom you're not already following. A feed that is CUSTOMIZED by YOUR Grapevine.
So there you have it, my defense of explicit trust attestations.
-

@ 6ad3e2a3:c90b7740
2024-08-21 17:42:18
When I used to pick NFL games against the spread for [RotoWire](https://www.rotowire.com/), I would joke after a bad week that my picks were perfect, but it was the games that got themselves wrong.
I’ve touched on this concept quite a bit here too — [But My Process Was Good](https://www.chrisliss.com/p/but-my-process-was-good) and [Why Blake Snell Should Win The NL Cy Young Award This Year](https://www.realmansports.com/p/why-blake-snell-should-win-the-nl) both highlight the category error of speciously applying tools of prediction toward the past. Tldr: the past is in no need of predicting because it already happened.
The error stems in part from mistaking the map for the territory — once the forecasts are substituted for reality itself, the future has already happened, so to speak — it’s right there on the spread sheet! — so it is no different than the past which has also already happened. So any tool that can be applied to the future can equally be applied to the past.
This is how we get [Sam Harris arguing that mRNA shot mandates were correct](https://x.com/KanekoaTheGreat/status/1615951624882782209?s=20) because covid *could have been* more deadly (and implicitly that the shots could have been safe and effective.) It’s one thing to model a possible future (with the requisite humility your forecasts might be off base), and quite another to force your failed model onto past events as though they were still in any doubt.
If this is confusing, that’s because a lot of us have been so trained to think this way we don’t even notice we’re doing it. Examples are legion where we identify what we deem an optimal process to achieve a desired result, then substitute that process for that result.
If the local police department believes it needs to arrest 50 people per month to reduce violent crime and incentivizes its officers to make those arrests, pretty soon arrests will be the goal, and people will get arrested for more and more non-violent offenses to make the quota.
If mass-vaccination is believed to be the key to good public health policy, then authorities will incentivize uptake, disincentivize bodily autonomy and not care one bit whether a person had prior immunity from the virus already, if the injection actually stops the spread or has myriad serious side effects. If the result (public health) were still the goal, the idea of forcing someone with natural immunity to inject himself with an experimental technology [would be ludicrous](https://x.com/goddeketal/status/1708104013936222641?s=20). But once the goal shifted to the process (mass vaccination), it made perfect sense.
Once we substitute the process by which we achieve something for the achievement itself (which might temporarily be sound, if you’re, say, training for a marathon), we create distortions in our thought processes and policies.
But I want to go back to where the bait and switch of process and result gets most absurd, and that’s when it comes to time. In this case, you’re not arresting jaywalkers to make your quota, you’re lamenting that had jaywalking correlated better with domestic violence, your policy would have been the correct one.
In other words, you’re not only substituting the process for the result in a forward-looking way, you are doing so even though you now have complete access to the result because it has already happened. And yet you are still grasping via your spread sheet for some other reality that might have been!
You do not need to forecast events that have already happened. The probability of the Chiefs winning the Super Bowl last year is 100 percent. We no longer need your tools to tell us how much to bet on them. The game is over, and whatever we believed the probability to have been before the fact is irrelevant.
That’s why I wrote about [Blake Snell’s Cy Young Award case](https://www.realmansports.com/p/why-blake-snell-should-win-the-nl) — despite Snell allowing 42 percent fewer runs on his watch than Spencer Strider — people are still arguing for Strider because the way Strider pitched *portended* fewer runs allowed than Snell. It is not enough for them that the results (runs allowed) are already in. They argue that because Strider’s profile forecasts a better result than Snell’s, Strider should win. Or, put differently, had we simulated 1000 seasons for each, Strider’s would on average be better. They are upset Snell got “lucky” as though reality must be stripped of all the effects for which we can’t attribute to particular causes and normalized in order to fit our model.
. . .
Mistaking the past for the future is one form of this category error, but it can also happen in reverse wherein one mistakes the future for the past. You see it when people treat future events at fait accompli and proceed as such. The notion of talking past the sale, e.g., if the car salesman says: “You’ll love this car and be thanking yourself for saving so much money on gas!” he’s treating your possible future agreement on a price as something that’s already happened.
People also do this to avoid responsibility, pretending as though there’s nothing one can do about some injustice or that it’s too late to make amends for wrongdoing. They think and talk about the future as though it’s the past.
When our dog Oscar got poisoned from a particular kind of caterpillar ([Largata do Pinheiro](https://www.setubalambiente.pt/lagarta-do-pinheiro/)) last winter, we brought him to the hospital with his tongue swelling so much it was stuck outside his mouth. The hospital treated him for a day, saying they could only wait and see, and he might lose his tongue (to necrosis) and have to get put down.
We could have taken their approach of it not being in our hands, but instead we convinced them to let us break him out and took him to our holistic vet who sedated him, drained his salivary gland, massaged the tongue extensively with ozone and anti-bacterial herbs and sent him home with us that evening.
[Oscar](https://njump.me/nevent1qqst6clec39drun4k97xyqy4ln06t9uc9g09fpa5fg5zruee3hvw8mszyzyujjulkrquksyekd5dkv6hdzv2n5zjstv3thywa844gtl4qplksqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyxhwumn8ghj7mn0wvhxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqt46763) who is passed out on the sofa next to me as I type this, only lost about 10 percent of the tongue, but otherwise made a full recovery.
. . .
I’m not sure why people so easily mistake cause for effect, process for results, future for past and vice-versa. If I had to speculate I’d say when our emotions get involved, we go from logical thinking to association, and associations work in both directions — effects and causes are associated without regard for which is which.
The modus operandi of most advertising (and propaganda) is to seed associations in your mind between things it wants you to associate — it’s certainly not to convince you rationally which is a much more difficult task. Maybe the influencers, marketers and propagandists have simply found an angle they can exploit. Once those associations take hold, they can be powerful, and often no amount of rational argument will un-cement them.
But I think that’s only part of the story. The other part is how most of us have been educated, and that's to focus on process not results. To be “process-oriented” not stuck in “results-based thinking.” This is a mark of erudition, of belonging to a certain class of people who have mastered this lesson. The class who trusts in modelers, forecasters and data-scientists waiting at the ready to be of service to The Science, even if it means treating the future as though it’s already happened and the past as though it can be re-forecast according to their models, conjugating reality, as it were, in the wrong tense.
-

@ ec09d831:42c80ce4
2024-08-21 17:27:14
## Nostr Nedir?
Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım:
### Basitlik
Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar.
### Esneklik
Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim.
### Doğrulanabilirlik
Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır.
### Anahtarları Anlamak
Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun.
### Protokol vs İstemci
Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım.
İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri:
[Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.]
[Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.]
[Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.]
[Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.]
[Habla](https://habla.news/) (Web) [Kolay blog yaratımı.]
[Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.]
[Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.]
[Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.]
Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz
#### Adım 1: Uygulama yükleme
* Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
* Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır.
* Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz.
* Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın.
#### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma
* “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin.
* “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın.
* Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz!
* Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz.
* Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır.
* “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın.
* “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir.
* Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz.
* “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır.
* “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur.
* “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz.
* “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin.
* Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin.
#### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın
Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın.
Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır.
Röle listesi:
140.f7z.io
astral.ninja
bevo.nostr1.com
bitcoiner.social
brb.io
carnivore-diet-relay.denizenid.com
eu.purplerelay.com
expensive-relay.fiatjaf.com
feeds.nostr.band/popular
fiatjaf.com
n.wingu.se
nos.lol
nostr-pub.semisol.dev
nostr-relay.wlvs.space
nostr.21l.st
nostr.band
nostr.bitcoiner.social
nostr.blipme.app
nostr.kollider.xyz
nostr.liberty.fans
nostr.mutinywallet.com
nostr.orangepill.dev
nostr.pleb.network
nostr.plebchain.org
nostr.relayer.se
nostr.satoshi.fun
nostr.walletofsatoshi.com
nostr.yuv.al
nostr.zbd.gg
nostr.zebedee.cloud
nostr.zerofiat.world
nostr1.tunnelsats.com
nostream.denizenid.com
nostria.space
offchain.pub
purplepag.es
pyramid.fiatjaf.com
relay.0xchat.com
relay.benthecarman.com
relay.bitcoinpark.com
relay.current.fyi
relay.damus.io
relay.f7z.io
relay.geyser.fund
relay.mutinywallet.com
relay.nostr.band
relay.nostr.bg
relay.nostr.net
relay.nostr3.io
relay.nostrati.com
relay.nostrplebs.com
relay.orangepill.dev
relay.plebstr.com
relay.primal.net
relay.snort.band
relay.snort.social
relay.utxo.one
relayable.org
relayer.fiatjaf.com
satstacker.cloud
snort.social
soloco.nl
sound-money-relay.denizenid.com

**Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü.
Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın:
Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9
Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6
Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm
Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj
Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm
Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp
Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u
Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3
Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6
Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte
Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p
Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh
Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn
Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p
Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg
Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw
Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h
Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh
Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8
Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj

-

@ 5d4b6c8d:8a1c1ee3
2024-08-21 15:29:03
I had something of an epiphany recently about needing to work for a cause I believe in, rather than just fiat mining. I was up all night thinking about the right fit and what my value proposition is.
You all have helped me realize that there's real interest in my perspective (thank you), so that's part of the proposition.
I was also reflecting on how limited the presence of most prominent libertarians is in the bitcoin ecosystem, despite the immense interest in their insights. That made me realize I can make at least a two-fold impact for a libertarian/free-market organization: my own content and integrating them into the bitcoin community.
This is the first draft of a letter I'm planning on sending to the Libertarian Institute, which is run by the great Scott Horton. I'd love your feedback on this letter. The aim of it is simply to pique their interest and generate a follow up conversation.
As it happens, the Libertarian Institute is based in Austin, so perhaps this will enable me to drop in on the SN HQ occasionally.
----------
Dear Libertarian Institute,
I'm reaching out to express my interest in joining your amazing institute. I’ve been following Scott’s work since 2007 and deeply admired the late Will Grigg’s articles. I believe I can add to the impressive scholarship you're already doing, while also helping you reach an audience that is very interested in your work and opening new fundraising opportunities.
I finished my economics PhD during the pandemic. Like most new graduates, I took what work was available, but now I’m looking to dedicate myself to spreading libertarianism and sound economics full-time. Some of my interests are economic geography (voting with your feet, jurisdictional arbitrage, secession, etc), political polarization, parallel institutions, bitcoin, and climate science. My academic training and research in those areas would give the Libertarian Institute another person to dissect the relentless stream of propaganda that comes out on those and other topics.
For my own sanity, I've been writing about libertarianism and economics at Stacker News, on the side, for the past couple of years. The positive reception to Rothbardian libertarianism and economics there has made me realize that our ideological camp is missing out on some low-hanging fruit. This site is part of the bitcoin ecosystem, where demand for Austro-libertarian thought is very high, but our scholars have a very limited presence.
I’ve found bitcoiners to be eager and willing to donate to those who are adding value in their spaces. I can help the Libertarian Institute establish itself as one of the intellectual pillars in this emerging libertarian community, both through my own contributions and by making your existing scholarship more visible there, as well as setting up the necessary technology to receive bitcoin donations and interact with their social media spaces.
I wish you all the very best. Thank you for your work. Hopefully, I'll have a chance to continue this discussion with you soon.
Sincerely,
Undisciplined (not how I plan to sign the real letter)
originally posted at https://stacker.news/items/657036
-

@ 4c96d763:80c3ee30
2024-08-21 04:00:40
# Changes
## William Casarin (10):
- temp ownership fix
- fix FilterBuilder
- update bindings
- Add filter iteration
- update build.rs to rusty's ccan rework
- filter: expose more builder options
- update bindings
- filter: mutable since
- filter: add from_json
- since/limit mut methods
pushed to [nostrdb-rs:refs/heads/master](http://git.jb55.com/nostrdb-rs/commit/4c89dcbca13168758eb41752225b4e486dbc9d20.html)
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 91bea5cd:1df4451c
2025-02-04 17:15:57### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:15:57### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ ddf03aca:5cb3bbbe
2025-02-02 13:09:27We’re thrilled to announce the stable release of Cashu-TS v2.2! Although this update is a minor version bump, it brings significant improvements under the hood that enhance the overall developer experience. We’ve spent several weeks testing and refining these changes. --- ## What’s New in v2.2? While there are no breaking changes in this release, there are many internal changes. If you spot any regressions or unexpected behavior, please [let us know](https://github.com/cashubtc/cashu-ts/issues). Here’s a rundown of the major updates: - **Enhanced Proof Creation**: The way proofs are created internally has been revamped. - **User-Controlled Outputs**: You now have full control over how outputs are created. - **Improved Bundling**: We’ve switched our bundling tool to [vite](https://vitejs.dev) for faster and more modern builds. - **Updated Testing Tools**: Our testing framework has migrated to [vitest](https://vitest.dev) and [msw](https://mswjs.io), with added browser testing via Playwright. --- ## New Flexibility with OutputData In previous versions of Cashu-TS, the creation of outputs (or *BlindedMessages*) was hidden away. Even though there were options to tweak the process (like deterministic secrets or P2PK), you were always limited to the built-in logic. ### What’s Changed? In v2.2, we’ve introduced a public interface that not only streamlines output creation but also lets you plug in your own custom logic when needed. With the new `outputData` option available on all output-creating methods, you can now bypass the automatic process and provide your own outputs. For example, you can create two proofs tied to different public keys in a single mint operation: ```ts const data1 = OutputData.createP2PKData({ pubkey: "key1" }, 10, keys); const data2 = OutputData.createP2PKData({ pubkey: "key2" }, 10, keys); const { keep, send } = await wallet.send(20, proofs, { outputData: { send: [...data1, ...data2] }, }); ``` ### Customization Made Easy The `outputData` option now accepts anything that conforms to the `OutputDataLike` interface. This means you can introduce your own output creation logic—even if it’s not natively supported by Cashu-TS yet. Here’s what the interface looks like: ```ts export interface OutputDataLike { blindedMessage: SerializedBlindedMessage; blindingFactor: bigint; secret: Uint8Array; toProof: (signature: SerializedBlindedSignature, keyset: MintKeys) => Proof; } ``` ### Introducing OutputData Factories While having full control is empowering, it also means you’ll need to handle tasks like fee calculation and amount selection manually. To strike a balance between control and convenience, we now support **OutputData Factories**. A factory is simply a function that takes an amount and `MintKeys` as input and returns an `OutputDataLike` object. This way, you can define a blueprint for your output data without worrying about the nitty-gritty details. For instance, you can create separate factories for amounts you keep versus those you send: ```ts function keepFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "keepPk" }, a, k.id); } function sendFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "sendPk" }, a, k.id); } const { send, keep } = await wallet.send(amount, proofs, { outputData: { send: createFactory("send"), keep: createFactory("keep") }, }); ``` Plus, you can now instantiate a `CashuWallet` with a default `keepFactory`, ensuring that all change amounts automatically lock to your key—streamlining your workflow even further. --- ## Bundling Improvements with Vite Starting with v2.2, we’ve transitioned from using `tsc` to [vite](https://vitejs.dev) for transpiling and bundling the library code. Although this change is mostly behind the scenes, it brings several benefits: - **Modern Build Target**: We’ve updated our build target to ES6. - **Updated Exports**: The package exports now reflect the latest JavaScript standards. - **Standalone Build Soon**: We’re working on a standalone build that bundles Cashu-TS along with all its dependencies. This will let you import Cashu-TS directly into your HTML. If you encounter any issues with the new bundling setup, please [let us know](https://github.com/cashubtc/cashu-ts/issues). ### A Nod to Vitest In addition to our bundling improvements, we’ve migrated our testing framework from Jest (with nock) to [vitest](https://vitest.dev) combined with [msw](https://mswjs.io). This switch gives us more flexibility in testing and mocking, plus we’ve added browser testing based on Playwright—thanks to the tip from nostr:npub16anjdksmvn5x08vtden04n64rw5k7fsjmedpw8avsx8wsh8ruhlq076pfx! --- ## In Conclusion Although Cashu-TS v2.2 is a minor version update, it comes packed with improvements that enhance both the developer experience and the flexibility of the library. We’re excited to see how you’ll use these new features in your projects! Thanks to all the amazing contributors that add to this library. Thank you for being a part of the Cashu-TS community. As always, if you have any questions, suggestions, or issues, don’t hesitate to [reach out to us](https://github.com/cashubtc/cashu-ts/issues).
@ ddf03aca:5cb3bbbe
2025-02-02 13:09:27We’re thrilled to announce the stable release of Cashu-TS v2.2! Although this update is a minor version bump, it brings significant improvements under the hood that enhance the overall developer experience. We’ve spent several weeks testing and refining these changes. --- ## What’s New in v2.2? While there are no breaking changes in this release, there are many internal changes. If you spot any regressions or unexpected behavior, please [let us know](https://github.com/cashubtc/cashu-ts/issues). Here’s a rundown of the major updates: - **Enhanced Proof Creation**: The way proofs are created internally has been revamped. - **User-Controlled Outputs**: You now have full control over how outputs are created. - **Improved Bundling**: We’ve switched our bundling tool to [vite](https://vitejs.dev) for faster and more modern builds. - **Updated Testing Tools**: Our testing framework has migrated to [vitest](https://vitest.dev) and [msw](https://mswjs.io), with added browser testing via Playwright. --- ## New Flexibility with OutputData In previous versions of Cashu-TS, the creation of outputs (or *BlindedMessages*) was hidden away. Even though there were options to tweak the process (like deterministic secrets or P2PK), you were always limited to the built-in logic. ### What’s Changed? In v2.2, we’ve introduced a public interface that not only streamlines output creation but also lets you plug in your own custom logic when needed. With the new `outputData` option available on all output-creating methods, you can now bypass the automatic process and provide your own outputs. For example, you can create two proofs tied to different public keys in a single mint operation: ```ts const data1 = OutputData.createP2PKData({ pubkey: "key1" }, 10, keys); const data2 = OutputData.createP2PKData({ pubkey: "key2" }, 10, keys); const { keep, send } = await wallet.send(20, proofs, { outputData: { send: [...data1, ...data2] }, }); ``` ### Customization Made Easy The `outputData` option now accepts anything that conforms to the `OutputDataLike` interface. This means you can introduce your own output creation logic—even if it’s not natively supported by Cashu-TS yet. Here’s what the interface looks like: ```ts export interface OutputDataLike { blindedMessage: SerializedBlindedMessage; blindingFactor: bigint; secret: Uint8Array; toProof: (signature: SerializedBlindedSignature, keyset: MintKeys) => Proof; } ``` ### Introducing OutputData Factories While having full control is empowering, it also means you’ll need to handle tasks like fee calculation and amount selection manually. To strike a balance between control and convenience, we now support **OutputData Factories**. A factory is simply a function that takes an amount and `MintKeys` as input and returns an `OutputDataLike` object. This way, you can define a blueprint for your output data without worrying about the nitty-gritty details. For instance, you can create separate factories for amounts you keep versus those you send: ```ts function keepFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "keepPk" }, a, k.id); } function sendFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "sendPk" }, a, k.id); } const { send, keep } = await wallet.send(amount, proofs, { outputData: { send: createFactory("send"), keep: createFactory("keep") }, }); ``` Plus, you can now instantiate a `CashuWallet` with a default `keepFactory`, ensuring that all change amounts automatically lock to your key—streamlining your workflow even further. --- ## Bundling Improvements with Vite Starting with v2.2, we’ve transitioned from using `tsc` to [vite](https://vitejs.dev) for transpiling and bundling the library code. Although this change is mostly behind the scenes, it brings several benefits: - **Modern Build Target**: We’ve updated our build target to ES6. - **Updated Exports**: The package exports now reflect the latest JavaScript standards. - **Standalone Build Soon**: We’re working on a standalone build that bundles Cashu-TS along with all its dependencies. This will let you import Cashu-TS directly into your HTML. If you encounter any issues with the new bundling setup, please [let us know](https://github.com/cashubtc/cashu-ts/issues). ### A Nod to Vitest In addition to our bundling improvements, we’ve migrated our testing framework from Jest (with nock) to [vitest](https://vitest.dev) combined with [msw](https://mswjs.io). This switch gives us more flexibility in testing and mocking, plus we’ve added browser testing based on Playwright—thanks to the tip from nostr:npub16anjdksmvn5x08vtden04n64rw5k7fsjmedpw8avsx8wsh8ruhlq076pfx! --- ## In Conclusion Although Cashu-TS v2.2 is a minor version update, it comes packed with improvements that enhance both the developer experience and the flexibility of the library. We’re excited to see how you’ll use these new features in your projects! Thanks to all the amazing contributors that add to this library. Thank you for being a part of the Cashu-TS community. As always, if you have any questions, suggestions, or issues, don’t hesitate to [reach out to us](https://github.com/cashubtc/cashu-ts/issues). @ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
@ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse. @ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue.
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue. @ 9e69e420:d12360c2
2025-01-26 01:31:47## Chef's notes # arbitray - test - of - chefs notes ## hedding 2 ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 1 hour - 🍽️ Servings: 5 ## Ingredients - Test ingredient - 2nd test ingredient ## Directions 1. Bake 2. Cool
@ 9e69e420:d12360c2
2025-01-26 01:31:47## Chef's notes # arbitray - test - of - chefs notes ## hedding 2 ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 1 hour - 🍽️ Servings: 5 ## Ingredients - Test ingredient - 2nd test ingredient ## Directions 1. Bake 2. Cool @ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html) @ 9e69e420:d12360c2
2025-01-25 14:32:21| Parameters | Dry Mead | Medium Mead | Sweet Mead | |------------|-----------|-------------|------------| | Honey | 2 lbs (900 grams) | 3 lbs (1.36 kg) | 4 lbs (1.81 kg) | | Yeast | ~0.07 oz (2 grams) | ~0.08 oz (2.5 grams) | ~0.10 oz (3 grams) | | Fermentation | ~4 weeks | 4 to 6 weeks | 6 to 8 weeks | | Racking | Fortnight or later | 1 month or after | ~2 months and after | | Specific Gravity | <1.010 | ~1.01 to ~1.025 | >1.025 |
@ 9e69e420:d12360c2
2025-01-25 14:32:21| Parameters | Dry Mead | Medium Mead | Sweet Mead | |------------|-----------|-------------|------------| | Honey | 2 lbs (900 grams) | 3 lbs (1.36 kg) | 4 lbs (1.81 kg) | | Yeast | ~0.07 oz (2 grams) | ~0.08 oz (2.5 grams) | ~0.10 oz (3 grams) | | Fermentation | ~4 weeks | 4 to 6 weeks | 6 to 8 weeks | | Racking | Fortnight or later | 1 month or after | ~2 months and after | | Specific Gravity | <1.010 | ~1.01 to ~1.025 | >1.025 | @ 9e69e420:d12360c2
2025-01-23 15:09:56President Trump has ordered thousands of additional troops to the U.S.-Mexico border as part of an effort to address immigration and security issues. This directive builds on his initial commitment to increase military presence along the border. Currently, around 2,200 active-duty personnel and approximately 4,500 National Guardsmen are stationed there. The new deployment aims to enhance the capabilities of Joint Task Force-North, allowing troops to assist in operations and provide intelligence support. Details on specific units remain unclear. The situation is still developing, with updates expected. [Sauce](https://thepostmillennial.com/breaking-president-trump-orders-thousands-of-troops-to-the-us-border-with-mexico)
@ 9e69e420:d12360c2
2025-01-23 15:09:56President Trump has ordered thousands of additional troops to the U.S.-Mexico border as part of an effort to address immigration and security issues. This directive builds on his initial commitment to increase military presence along the border. Currently, around 2,200 active-duty personnel and approximately 4,500 National Guardsmen are stationed there. The new deployment aims to enhance the capabilities of Joint Task Force-North, allowing troops to assist in operations and provide intelligence support. Details on specific units remain unclear. The situation is still developing, with updates expected. [Sauce](https://thepostmillennial.com/breaking-president-trump-orders-thousands-of-troops-to-the-us-border-with-mexico) @ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications. @ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙 @ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ###
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ### @ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market. Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market. Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws. @ 6389be64:ef439d32
2025-01-16 15:44:06## Black Locust can grow up to 170 ft tall ## Grows 3-4 ft. per year ## Native to North America ## Cold hardy in zones 3 to 8  ## Firewood - BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal - Since its growth is fast, firewood can be plentiful ## Timber  - Rot resistant due to a naturally produced robinin in the wood - 100 year life span in full soil contact! (better than cedar performance) - Fence posts - Outdoor furniture - Outdoor decking - Sustainable due to its fast growth and spread - Can be coppiced (cut to the ground) - Can be pollarded (cut above ground) - Its dense wood makes durable tool handles, boxes (tool), and furniture - The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak. - A very low rate of expansion and contraction - Hardwood flooring - The highest tensile beam strength of any American tree - The wood is beautiful ## Legume - Nitrogen fixer - Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn - Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]] ## Bees  - The edible flower clusters are also a top food source for honey bees ## Shade Provider  - Its light, airy overstory provides dappled shade - Planted on the west side of a garden it provides relief during the hottest part of the day - (nitrogen provider) - Planted on the west side of a house, its quick growth soon shades that side from the sun ## Wind-break  - Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters ## Fodder - Over 20% crude protein - 4.1 kcal/g of energy - Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
@ 6389be64:ef439d32
2025-01-16 15:44:06## Black Locust can grow up to 170 ft tall ## Grows 3-4 ft. per year ## Native to North America ## Cold hardy in zones 3 to 8  ## Firewood - BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal - Since its growth is fast, firewood can be plentiful ## Timber  - Rot resistant due to a naturally produced robinin in the wood - 100 year life span in full soil contact! (better than cedar performance) - Fence posts - Outdoor furniture - Outdoor decking - Sustainable due to its fast growth and spread - Can be coppiced (cut to the ground) - Can be pollarded (cut above ground) - Its dense wood makes durable tool handles, boxes (tool), and furniture - The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak. - A very low rate of expansion and contraction - Hardwood flooring - The highest tensile beam strength of any American tree - The wood is beautiful ## Legume - Nitrogen fixer - Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn - Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]] ## Bees  - The edible flower clusters are also a top food source for honey bees ## Shade Provider  - Its light, airy overstory provides dappled shade - Planted on the west side of a garden it provides relief during the hottest part of the day - (nitrogen provider) - Planted on the west side of a house, its quick growth soon shades that side from the sun ## Wind-break  - Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters ## Fodder - Over 20% crude protein - 4.1 kcal/g of energy - Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043 @ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker  For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper  When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier  The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste  Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste  Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine  Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth  Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones  During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner  Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network  What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain  Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR  The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing  The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data  Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression  Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety  A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap  How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker  For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper  When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier  The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste  Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste  Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine  Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth  Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones  During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner  Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network  What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain  Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR  The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing  The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data  Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression  Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety  A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap  How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next. @ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool. In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users. I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂 Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client. Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that? Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr. As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways. Do you want an Olas feed of images? Add the media column. Do you want a feed of live video events? Add the zap.stream column. Do you want Nostr Nests or audio chats? Add that column to your Notedeck. Git? Email? Books? Chat and DMs? It's all possible. Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer. Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility. Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices. > In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet. > > \-Will Casarin In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild. Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem. Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint. For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
@ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool. In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users. I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂 Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client. Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that? Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr. As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways. Do you want an Olas feed of images? Add the media column. Do you want a feed of live video events? Add the zap.stream column. Do you want Nostr Nests or audio chats? Add that column to your Notedeck. Git? Email? Books? Chat and DMs? It's all possible. Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer. Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility. Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices. > In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet. > > \-Will Casarin In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild. Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem. Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint. For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year. @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. ---
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. --- @ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse. That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions. Enter [Olas](https://olas.app). If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer. Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health. Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts. Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild. Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers. Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!). [Download on iOS](https://testflight.apple.com/join/2FMVX2yM). [Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore. Let's make waves together.
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse. That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions. Enter [Olas](https://olas.app). If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer. Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health. Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts. Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild. Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers. Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!). [Download on iOS](https://testflight.apple.com/join/2FMVX2yM). [Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore. Let's make waves together. @ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
@ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence. @ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025: **Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems. **Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications. **Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem. **Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025: **Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems. **Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications. **Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem. **Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies. @ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today. Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”. I’ve had my own stumbles on the way. In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear. In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”. It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”. As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it: > In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth. > > It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs. > > … > > The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases. While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis. What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship. And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well. The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me. Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something. **I was at least somewhat wrong.** My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU). I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak. **I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.** The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase. I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/). Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between. **But I was wrong.** When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road. My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm. While the price was irrelevant, it was all about buying and selling goods without permission or license. **Now I understand I was wrong.** Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack. What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.* The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time. Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later. In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague. My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse. This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016. **And I was wrong again.** Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike. While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable. Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces. In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships. This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not. Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation. **Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.** When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash. There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today. Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”. I’ve had my own stumbles on the way. In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear. In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”. It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”. As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it: > In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth. > > It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs. > > … > > The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases. While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis. What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship. And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well. The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me. Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something. **I was at least somewhat wrong.** My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU). I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak. **I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.** The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase. I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/). Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between. **But I was wrong.** When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road. My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm. While the price was irrelevant, it was all about buying and selling goods without permission or license. **Now I understand I was wrong.** Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack. What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.* The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time. Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later. In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague. My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse. This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016. **And I was wrong again.** Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike. While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable. Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces. In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships. This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not. Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation. **Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.** When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash. There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it. @ 1cb14ab3:95d52462
2024-12-17 19:24:54*Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.* --- The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways. Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future. When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal. For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away. This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below: <aside> **Inflation Rate (%)** | **Purchasing Power Halving (Years)** - 2% | 35-40 years - 3% | 20-25 years - 4% | 15-20 years - 5% | 10-15 years - 6% | 7-12 years - 7% | 5-10 years - 8% | 4-8 years - 9% | 3-6 years - 10% | 2-5 years </aside> Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble. But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation? A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future. Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money. The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued. By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world. Bitcoin isn’t a bubble; it’s a beacon. --- ### More from Hes: [Art](https://hes.npub.pro/tag/art/) [Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography)
@ 1cb14ab3:95d52462
2024-12-17 19:24:54*Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.* --- The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways. Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future. When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal. For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away. This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below: <aside> **Inflation Rate (%)** | **Purchasing Power Halving (Years)** - 2% | 35-40 years - 3% | 20-25 years - 4% | 15-20 years - 5% | 10-15 years - 6% | 7-12 years - 7% | 5-10 years - 8% | 4-8 years - 9% | 3-6 years - 10% | 2-5 years </aside> Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble. But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation? A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future. Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money. The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued. By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world. Bitcoin isn’t a bubble; it’s a beacon. --- ### More from Hes: [Art](https://hes.npub.pro/tag/art/) [Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography) @ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge. ### **Comfrey: Nature’s Champion of Resilience** Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants. Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar. ### **Biochar: The Silent Powerhouse of Soil Regeneration** Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience. Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as *terra preta*, these soils remain productive centuries later, highlighting biochar’s remarkable staying power. Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system. ### **The Synergy: Comfrey and Biochar Together** Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that. 1. **Nutrient Cycling and Retention**\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness. 2. **Water Management**\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell. 3. **Microbial Ecosystems**\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season. Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges. This synergy demonstrates the power of designing systems that don’t just survive—they thrive. ### **Lessons Beyond the Soil** The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure. Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge. ### **Comfrey: Nature’s Champion of Resilience** Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants. Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar. ### **Biochar: The Silent Powerhouse of Soil Regeneration** Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience. Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as *terra preta*, these soils remain productive centuries later, highlighting biochar’s remarkable staying power. Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system. ### **The Synergy: Comfrey and Biochar Together** Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that. 1. **Nutrient Cycling and Retention**\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness. 2. **Water Management**\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell. 3. **Microbial Ecosystems**\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season. Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges. This synergy demonstrates the power of designing systems that don’t just survive—they thrive. ### **Lessons Beyond the Soil** The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure. Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward. @ 129f5189:3a441803
2024-11-22 03:42:42Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario. The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy. After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America. Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million. China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions... https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions. In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border. A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention. https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere. The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years. https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021. In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government. https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues. In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities." https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024. Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction. In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government. https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University. "The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times. General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country. "We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time. In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade." https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues." Under the previous administration, China had received preferential treatment. In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan. The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security. No public records show that the project has progressed since then. https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark. "Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement. "Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face." https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era. Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel." https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg Access to space plays a crucial role in the CCP's strategic objectives. Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China. According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice. According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access. China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely. The big question is: what could this facility do in times of war? https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit. The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface. Additionally, it offers strategic advantages for any government involved in espionage. https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner. However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives. Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023. https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg
@ 129f5189:3a441803
2024-11-22 03:42:42Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario. The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy. After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America. Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million. China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions... https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions. In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border. A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention. https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere. The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years. https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021. In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government. https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues. In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities." https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024. Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction. In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government. https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University. "The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times. General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country. "We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time. In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade." https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues." Under the previous administration, China had received preferential treatment. In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan. The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security. No public records show that the project has progressed since then. https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark. "Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement. "Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face." https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era. Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel." https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg Access to space plays a crucial role in the CCP's strategic objectives. Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China. According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice. According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access. China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely. The big question is: what could this facility do in times of war? https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit. The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface. Additionally, it offers strategic advantages for any government involved in espionage. https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner. However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives. Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023. https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg @ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions. --- ## Subscriptions with Cashu One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that? However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this: 1. **Overpaying:** To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. 2. **Full Interactivity:** In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends. --- ## Enter Locking Scripts One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone. A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key. To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token. With these tools, we can now create non-interactive payment streams! --- ## One Missing Piece… Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams. --- ## The Grand Finale: Payment Streams Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender. Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.  ### Example: Renting a VPS Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work: 1. Construct a token worth 7,000 sats to cover the entire week. 2. Divide the token into 7 proofs, each worth 1,000 sats. 3. Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key. - The first proof has a locktime of `now`. - The second proof has a locktime of `now + 1 day`. - The third proof has a locktime of `now + 2 days`, and so on. When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on. At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver. --- With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds. Thank you for reading. Make sure to leave a nut if you enjoyed this :)
@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions. --- ## Subscriptions with Cashu One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that? However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this: 1. **Overpaying:** To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. 2. **Full Interactivity:** In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends. --- ## Enter Locking Scripts One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone. A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key. To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token. With these tools, we can now create non-interactive payment streams! --- ## One Missing Piece… Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams. --- ## The Grand Finale: Payment Streams Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender. Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.  ### Example: Renting a VPS Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work: 1. Construct a token worth 7,000 sats to cover the entire week. 2. Divide the token into 7 proofs, each worth 1,000 sats. 3. Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key. - The first proof has a locktime of `now`. - The second proof has a locktime of `now + 1 day`. - The third proof has a locktime of `now + 2 days`, and so on. When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on. At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver. --- With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds. Thank you for reading. Make sure to leave a nut if you enjoyed this :) @ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/ Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country =================================================================================== Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges. * * * **KEY TAKEAWAYS** * The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero. * The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards. * While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.  In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country. **_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._** Let’s unpack what effect these regulations will have. Brazil’s Crackdown on Crypto Fraud ---------------------------------- If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets. The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism. According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances. > … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder. > > – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-) The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars. The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations. However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil. Monero: What Is It and Why Is Brazil Banning It? ------------------------------------------------ Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain. Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR. Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/). Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.  In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset. In Closing ---------- Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing. Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell. References ---------- Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems. [View all articles by Cassio Gusson](https://techreport.com/author/cassiog/)
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/ Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country =================================================================================== Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges. * * * **KEY TAKEAWAYS** * The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero. * The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards. * While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.  In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country. **_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._** Let’s unpack what effect these regulations will have. Brazil’s Crackdown on Crypto Fraud ---------------------------------- If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets. The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism. According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances. > … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder. > > – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-) The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars. The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations. However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil. Monero: What Is It and Why Is Brazil Banning It? ------------------------------------------------ Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain. Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR. Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/). Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.  In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset. In Closing ---------- Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing. Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell. References ---------- Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems. [View all articles by Cassio Gusson](https://techreport.com/author/cassiog/) @ 5e5fc143:393d5a2c
2024-11-19 10:20:25Now test old reliable front end Stay tuned more later Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues
@ 5e5fc143:393d5a2c
2024-11-19 10:20:25Now test old reliable front end Stay tuned more later Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07## Chef's notes This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is. ## Details - ⏲️ Prep time: 30 - 🍳 Cook time: 0 - 🍽️ Servings: 8 ## Ingredients - 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates - 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates - 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates - 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates - 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates ## Directions 1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake. 2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07## Chef's notes This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is. ## Details - ⏲️ Prep time: 30 - 🍳 Cook time: 0 - 🍽️ Servings: 8 ## Ingredients - 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates - 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates - 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates - 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates - 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates ## Directions 1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake. 2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving. @ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo: Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1 Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2 Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb. ## O que são bloatwares? Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades. ## O que é o adb? O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode. Requisitos: Para computadores: • Depuração USB ativa no celular; • Computador com adb; • Cabo USB; Para celulares: • Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior; Para ambos: • Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo; ## Ativação de depuração: Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux. ## Instalação e configuração do NetGuard O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria. F-Droid: https://f-droid.org/packages/eu.faircode.netguard/ Github: https://github.com/M66B/NetGuard/releases Após instalado, configure da seguinte maneira: Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’); Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet); Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo. ## Lista de bloatwares Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região. Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por: ``` Samsung Galaxy Note 10 Plus bloatware list ``` Provavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica. Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível. ### De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente. ## Download do adb em computadores Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux. Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb. ## Download do adb em celulares com Termux. Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto. F-Droid: https://f-droid.org/en/packages/com.termux/ Github: https://github.com/termux/termux-app/releases ## Processo de debloat Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis. Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid. Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover. Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard. MTP tentando comunicação com servidores externos: ## Executando o adb shell No computador Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular. Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando: ``` ./adb start-server ``` O resultado deve ser: *daemon not running; starting now at tcp:5037 *daemon started successfully E caso não apareça nada, execute: ``` ./adb kill-server ``` E inicie novamente. Com o adb conectado ao celular, execute: ``` ./adb shell ``` Para poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia. Logo o resultado deve ser: begonia:/ $ Caso ocorra algum erro do tipo: adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device. Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo. ## No celular Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando: ``` pkg install android-tools ``` Quando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux. Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir: Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute: ``` adb pair localhost:porta CódigoDeEmparelhamento ``` De acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”. Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute: ``` adb connect localhost:porta ``` Obs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio. Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell: ``` adb shell ``` Remoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote. Dentro do NetGuard, verificando as informações do Google Maps: Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar: ``` pm uninstall –user 0 com.google.android.apps.maps ``` E pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote. Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro. Exemplo de lista: Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando: ``` cmd package install-existing nome.do.pacote ``` ## Pós-debloat Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade? Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store. Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23 Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo: Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1 Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2 Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb. ## O que são bloatwares? Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades. ## O que é o adb? O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode. Requisitos: Para computadores: • Depuração USB ativa no celular; • Computador com adb; • Cabo USB; Para celulares: • Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior; Para ambos: • Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo; ## Ativação de depuração: Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux. ## Instalação e configuração do NetGuard O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria. F-Droid: https://f-droid.org/packages/eu.faircode.netguard/ Github: https://github.com/M66B/NetGuard/releases Após instalado, configure da seguinte maneira: Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’); Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet); Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo. ## Lista de bloatwares Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região. Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por: ``` Samsung Galaxy Note 10 Plus bloatware list ``` Provavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica. Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível. ### De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente. ## Download do adb em computadores Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux. Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb. ## Download do adb em celulares com Termux. Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto. F-Droid: https://f-droid.org/en/packages/com.termux/ Github: https://github.com/termux/termux-app/releases ## Processo de debloat Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis. Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid. Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover. Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard. MTP tentando comunicação com servidores externos: ## Executando o adb shell No computador Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular. Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando: ``` ./adb start-server ``` O resultado deve ser: *daemon not running; starting now at tcp:5037 *daemon started successfully E caso não apareça nada, execute: ``` ./adb kill-server ``` E inicie novamente. Com o adb conectado ao celular, execute: ``` ./adb shell ``` Para poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia. Logo o resultado deve ser: begonia:/ $ Caso ocorra algum erro do tipo: adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device. Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo. ## No celular Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando: ``` pkg install android-tools ``` Quando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux. Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir: Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute: ``` adb pair localhost:porta CódigoDeEmparelhamento ``` De acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”. Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute: ``` adb connect localhost:porta ``` Obs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio. Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell: ``` adb shell ``` Remoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote. Dentro do NetGuard, verificando as informações do Google Maps: Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar: ``` pm uninstall –user 0 com.google.android.apps.maps ``` E pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote. Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro. Exemplo de lista: Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando: ``` cmd package install-existing nome.do.pacote ``` ## Pós-debloat Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade? Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store. Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23 Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms @ a10260a2:caa23e3e
2024-11-10 04:35:34nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard. In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW. I took some screenshots to give you an idea of how things work. The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).  Clicking login allows signing in with a browser extension.  The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.  Existing blog posts (i.e. long form notes) are synced.  Same for product listings. There’s a nice interface to create new ones and preview them before publishing.   That’s all for now. As you can see, super slick stuff! Bullish on Cypher. So much so I had to support the project and buy a subdomain. 😎 https://bullish.cypher.space originally posted at https://stacker.news/items/760592
@ a10260a2:caa23e3e
2024-11-10 04:35:34nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard. In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW. I took some screenshots to give you an idea of how things work. The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).  Clicking login allows signing in with a browser extension.  The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.  Existing blog posts (i.e. long form notes) are synced.  Same for product listings. There’s a nice interface to create new ones and preview them before publishing.   That’s all for now. As you can see, super slick stuff! Bullish on Cypher. So much so I had to support the project and buy a subdomain. 😎 https://bullish.cypher.space originally posted at https://stacker.news/items/760592 @ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima. @ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history? As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times. At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols. The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)? **As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).** At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. ## **Open-source matters** When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. ## **Open-source is for your friends, and enemies** In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. ## **Limiting open-source threatens our own advancement** If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols. The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. *Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).*
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history? As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times. At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols. The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)? **As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).** At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. ## **Open-source matters** When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. ## **Open-source is for your friends, and enemies** In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. ## **Limiting open-source threatens our own advancement** If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols. The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. *Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).* @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集: --- 免责申明: 在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。 | 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) | ` 持续更新。。。` --- ### 推广: 访问不了openai,去`低调云`购买VPN。 官网:https://didiaocloud.xyz 邀请码:`w9AjVJit` 价格低至1元。
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集: --- 免责申明: 在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。 | 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) | ` 持续更新。。。` --- ### 推广: 访问不了openai,去`低调云`购买VPN。 官网:https://didiaocloud.xyz 邀请码:`w9AjVJit` 价格低至1元。 @ 06639a38:655f8f71
2024-11-01 22:32:51One year ago I wrote the article [Why Nostr resonates](https://sebastix.nl/blog/why-nostr-resonates/) in Dutch and English after I visited the Bitcoin Amsterdam 2023 conference and the Nostrdam event. It got published at [bitcoinfocus.nl](https://bitcoinfocus.nl/2023/11/02/278-waarom-nostr-resoneert/) (translated in Dutch). The main reason why I wrote that piece is that I felt that my gut feeling was tellinng me that Nostr is going to change many things on the web. After the article was published, one of the first things I did was setting up this page on my website: [https://sebastix.nl/nostr-research-and-development](https://sebastix.nl/nostr-research-and-development). The page contains this section (which I updated on 31-10-2024):  One metric I would like to highlight is the number of repositories on Github. Compared to a year ago, there are already more than 1130 repositories now on Github tagged with Nostr. Let's compare this number to other social media protocols and decentralized platforms (24-10-2024): * Fediverse: 522 * ATProto: 159 * Scuttlebot: 49 * Farcaster: 202 * Mastodon: 1407 * ActivityPub: 444 Nostr is growing. FYI there are many Nostr repositories not hosted on Github, so the total number of Nostr reposities is higher. I know that many devs are using their own Git servers to host it. We're even capable of setting up Nostr native Git repositories (for example, see [https://gitworkshop.dev/repos](https://gitworkshop.dev/repos)). Eventually, Nostr will make Github (and other platforms) absolute. Let me continue summarizing my personal Nostr highlights of last year. ## Organising Nostr meetups  This is me playing around with the NostrDebug tool showing how you can query data from Nostr relays. Jurjen is standing behind me. He is one of the people I've met this year who I'm sure I will have a long-term friendship with. ## OpenSats grant for Nostr-PHP   In December 2023 I submitted my application for a OpenSats grant for the further development of the Nostr-PHP helper library. After some months I finally got the message that my application was approved... When I got the message I was really stoked and excited. It's a great form of appreciation for the work I had done so far and with this grant I get the opportunity to take the work to another higher level. So please check out the work done for so far: * [https://nostr-php.dev](https://nostr-php.dev) * [https://github.com/nostrver-se/nostr-php](https://github.com/nostrver-se/nostr-php) ## Meeting Dries  One of my goosebumps moments I had in 2022 when I saw that the founder and tech lead of Drupal Dries Buytaert posted '[Nostr, love at first sight](https://dri.es/nostr-love-at-first-sight)' on his blog. These types of moments are very rare moment where two different worlds merge where I wouldn't expect it. Later on I noticed that Dries would come to the yearly Dutch Drupal event. For me this was a perfect opportunity to meet him in person and have some Nostr talks. I admire the work he is doing for Drupal and the community. I hope we can bridge Nostr stuff in some way to Drupal. In general this applies for any FOSS project out there. [Here](https://sebastix.nl/blog/photodump-and-highlights-drupaljam-2024/) is my recap of that Drupal event. ## Attending Nostriga  A conference where history is made and written. I felt it immediately at the first sessions I attended. I will never forget the days I had at Nostriga. I don't have the words to describe what it brought to me.  I also pushed myself out of my comfort zone by giving a keynote called 'POSSE with Nostr - how we pivot away from API's with one of Nostr superpowers'. I'm not sure if this is something I would do again, but I've learned a lot from it. You can find the presentation [here](https://nostriga.nostrver.se/). It is recorded, but I'm not sure if and when it gets published. ## Nostr billboard advertisement  This advertisment was shown on a billboard beside the [A58 highway in The Netherlands](https://www.google.nl/maps/@51.5544315,4.5607291,3a,75y,34.72h,93.02t/data=!3m6!1e1!3m4!1sdQv9nm3J9SdUQCD0caFR-g!2e0!7i16384!8i8192?coh=205409&entry=ttu) from September 2nd till September 16th 2024. You can find all the assets and more footage of the billboard ad here: [https://gitlab.com/sebastix-group/nostr/nostr-ads](https://gitlab.com/sebastix-group/nostr/nostr-ads). My goal was to set an example of how we could promote Nostr in more traditional ways and inspire others to do the same. In Brazil a fundraiser was achieved to do something similar there: [https://geyser.fund/project/nostrifybrazil](https://geyser.fund/project/nostrifybrazil). ## Volunteering at Nostr booths growNostr  This was such a great motivating experience. Attending as a volunteer at the Nostr booth during the Bitcoin Amsterdam 2024 conference. Please read my note with all the lessons I learned [here](https://nostrver.se/note/my-learned-nostr-lessons-nostr-booth-bitcoin-amsterdam-2024). ## The other stuff * The Nostr related blog articles I wrote past year: * [**Run a Nostr relay with your own policies**](https://sebastix.nl/blog/run-a-nostr-relay-with-your-own-policies/) (02-04-2024) * [**Why social networks should be based on commons**](https://sebastix.nl/blog/why-social-networks-should-be-based-on-commons/) (03-01-2024) * [**How could Drupal adopt Nostr?**](https://sebastix.nl/blog/how-could-drupal-adopt-nostr/) (30-12-2023) * [**Nostr integration for CCHS.social**](https://sebastix.nl/blog/nostr-integration-for-cchs-social-drupal-cms/) (21-12-2023) * [https://ccns.nostrver.se](https://ccns.nostrver.se) CCNS stands for Community Curated Nostr Stuff. At the end of 2023 I started to build this project. I forked an existing Drupal project of mine (https://cchs.social) to create a link aggregation website inspired by stacker.news. At the beginning of 2024 I also joined the TopBuilder 2024 contest which was a productive period getting to know new people in the Bitcoin and Nostr space. * [https://nuxstr.nostrver.se](https://nuxstr.nostrver.se) PHP is not my only language I use to build stuff. As a fullstack webdeveloper I also work with Javascript. Many Nostr clients are made with Javascript frameworks or other more client-side focused tools. Vuejs is currently my Javascript framework I'm the most convenient with. With Vuejs I started to tinker around with Nuxt combined with NDK and so I created a starter template for Vue / Nuxt developers. * [ZapLamp](nostr:npub1nfrsmpqln23ls7y3e4m29c22x3qaq9wmmr7zkfcttty2nk2kd6zs9re52s) This is a neat DIY package from LNbits. Powered by an Arduino ESP32 dev board it was running a 24/7 livestream on zap.stream at my office. It flashes when you send a zap to the npub of the ZapLamp. * [https://nosto.re](https://nosto.re) Since the beginning when the Blossom spec was published by @hzrd49 and @StuartBowman I immediately took the opportunity to tinker with it. I'm also running a relay for transmitting Blossom Nostr events `wss://relay.nosto.re`. * [Relays I maintain](https://nostrver.se/note/relays-i-maintain) I really enjoy to tinker with different relays implementations. Relays are the fundamental base layer to let Nostr work. I'm still sharing my contributions on [https://nostrver.se/](https://nostrver.se/) where I publish my weekly Nostr related stuff I worked on. This website is built with Drupal where I use the Nostr Simple Publish and Nostr long-form content NIP-23 modules to crosspost the notes and long-form content to the Nostr network (like this piece of content you're reading).  ## The Nostr is the people Just like the web, the web is people: [https://www.youtube.com/watch?v=WCgvkslCzTo](https://www.youtube.com/watch?v=WCgvkslCzTo) > the people on nostr are some of the smartest and coolest i’ve ever got to know. who cares if it doesn’t take over the world. It’s done more than i could ever ask for. - [@jb55](nostr:note1fsfqja9kkvzuhe5yckff3gkkeqe7upxqljg2g4nkjzp5u9y7t25qx43uch) Here are some Nostriches who I'm happy to have met and who influenced my journey in Nostr in a positive way. * Jurjen * Bitpopart * Arjen * Jeroen * Alex Gleason * Arnold Lubach * Nathan Day * Constant * fiatjaf * Sync ## Coming year Generally I will continue doing what I've done last year. Besides the time I spent on Nostr stuff, I'm also very busy with Drupal related work for my customers. I hope I can get the opportunity to work on a paid client project related to Nostr. It will be even better when I can combine my Drupal expertise with Nostr for projects paid by customers. ### Building a new Nostr application When I look at my Nostr backlog where I just put everything in with ideas and notes, there are quite some interesting concepts there for building new Nostr applications. Filtering out, I think these three are the most exciting ones: * nEcho, a micro app for optimizing your reach via Nostr (NIP-65) * Nostrides.cc platform where you can share Nostr activity events (NIP-113) * A child-friendly video web app with parent-curated content (NIP-71) ### Nostr & Drupal When working out a new idea for a Nostr client, I'm trying to combine my expertises into one solution. That's why I also build and maintain some Nostr contrib modules for Drupal. * [Nostr Simple Publish](https://www.drupal.org/project/nostr_simple_publish) Drupal module to cross-post notes from Drupal to Nostr * [Nostr long-form content NIP-23](https://www.drupal.org/project/nostr_content_nip23) Drupal module to cross-post Markdown formatted content from Drupal to Nostr * [Nostr internet identifier NIP-05](https://www.drupal.org/project/nostr_id_nip05) Drupal module to setup Nostr internet identifier addresses with Drupal. * [Nostr NDK](https://drupal.org/project/nostr_dev_kit) Includes the Javascript library Nostr Dev Kit (NDK) in a Drupal project. One of my (very) ambitious goals is to build a Drupal powered Nostr (website) package with the following main features: * Able to login into Drupal with your Nostr keypair * Cross-post content to the Nostr network * Fetch your Nostr content from the Nostr content * Serve as a content management system (CMS) for your Nostr events * Serve as a framework to build a hybrid Nostr web application * Run and maintain a Nostr relay with custom policies * Usable as a feature rich progressive web app * Use it as a remote signer These are just some random ideas as my Nostr + Drupal backlog is way longer than this. ### Nostr-PHP With all the newly added and continues being updated NIPs in the protocol, this helper library will never be finished. As the sole maintainer of this library I would like to invite others to join as a maintainer or just be a contributor to the library. PHP is big on the web, but there are not many PHP developers active yet using Nostr. Also PHP as a programming language is really pushing forward keeping up with the latest innovations. ### Grow Nostr outside the Bitcoin community We are working out a submission to host a Nostr stand at FOSDEM 2025. If approved, it will be the first time (as far as I know) that Nostr could be present at a conference outside the context of Bitcoin. The audience at FOSDEM is mostly technical oriented, so I'm really curious what type of feedback we will receive. Let's finish this article with some random Nostr photos from last year. Cheers!       
@ 06639a38:655f8f71
2024-11-01 22:32:51One year ago I wrote the article [Why Nostr resonates](https://sebastix.nl/blog/why-nostr-resonates/) in Dutch and English after I visited the Bitcoin Amsterdam 2023 conference and the Nostrdam event. It got published at [bitcoinfocus.nl](https://bitcoinfocus.nl/2023/11/02/278-waarom-nostr-resoneert/) (translated in Dutch). The main reason why I wrote that piece is that I felt that my gut feeling was tellinng me that Nostr is going to change many things on the web. After the article was published, one of the first things I did was setting up this page on my website: [https://sebastix.nl/nostr-research-and-development](https://sebastix.nl/nostr-research-and-development). The page contains this section (which I updated on 31-10-2024):  One metric I would like to highlight is the number of repositories on Github. Compared to a year ago, there are already more than 1130 repositories now on Github tagged with Nostr. Let's compare this number to other social media protocols and decentralized platforms (24-10-2024): * Fediverse: 522 * ATProto: 159 * Scuttlebot: 49 * Farcaster: 202 * Mastodon: 1407 * ActivityPub: 444 Nostr is growing. FYI there are many Nostr repositories not hosted on Github, so the total number of Nostr reposities is higher. I know that many devs are using their own Git servers to host it. We're even capable of setting up Nostr native Git repositories (for example, see [https://gitworkshop.dev/repos](https://gitworkshop.dev/repos)). Eventually, Nostr will make Github (and other platforms) absolute. Let me continue summarizing my personal Nostr highlights of last year. ## Organising Nostr meetups  This is me playing around with the NostrDebug tool showing how you can query data from Nostr relays. Jurjen is standing behind me. He is one of the people I've met this year who I'm sure I will have a long-term friendship with. ## OpenSats grant for Nostr-PHP   In December 2023 I submitted my application for a OpenSats grant for the further development of the Nostr-PHP helper library. After some months I finally got the message that my application was approved... When I got the message I was really stoked and excited. It's a great form of appreciation for the work I had done so far and with this grant I get the opportunity to take the work to another higher level. So please check out the work done for so far: * [https://nostr-php.dev](https://nostr-php.dev) * [https://github.com/nostrver-se/nostr-php](https://github.com/nostrver-se/nostr-php) ## Meeting Dries  One of my goosebumps moments I had in 2022 when I saw that the founder and tech lead of Drupal Dries Buytaert posted '[Nostr, love at first sight](https://dri.es/nostr-love-at-first-sight)' on his blog. These types of moments are very rare moment where two different worlds merge where I wouldn't expect it. Later on I noticed that Dries would come to the yearly Dutch Drupal event. For me this was a perfect opportunity to meet him in person and have some Nostr talks. I admire the work he is doing for Drupal and the community. I hope we can bridge Nostr stuff in some way to Drupal. In general this applies for any FOSS project out there. [Here](https://sebastix.nl/blog/photodump-and-highlights-drupaljam-2024/) is my recap of that Drupal event. ## Attending Nostriga  A conference where history is made and written. I felt it immediately at the first sessions I attended. I will never forget the days I had at Nostriga. I don't have the words to describe what it brought to me.  I also pushed myself out of my comfort zone by giving a keynote called 'POSSE with Nostr - how we pivot away from API's with one of Nostr superpowers'. I'm not sure if this is something I would do again, but I've learned a lot from it. You can find the presentation [here](https://nostriga.nostrver.se/). It is recorded, but I'm not sure if and when it gets published. ## Nostr billboard advertisement  This advertisment was shown on a billboard beside the [A58 highway in The Netherlands](https://www.google.nl/maps/@51.5544315,4.5607291,3a,75y,34.72h,93.02t/data=!3m6!1e1!3m4!1sdQv9nm3J9SdUQCD0caFR-g!2e0!7i16384!8i8192?coh=205409&entry=ttu) from September 2nd till September 16th 2024. You can find all the assets and more footage of the billboard ad here: [https://gitlab.com/sebastix-group/nostr/nostr-ads](https://gitlab.com/sebastix-group/nostr/nostr-ads). My goal was to set an example of how we could promote Nostr in more traditional ways and inspire others to do the same. In Brazil a fundraiser was achieved to do something similar there: [https://geyser.fund/project/nostrifybrazil](https://geyser.fund/project/nostrifybrazil). ## Volunteering at Nostr booths growNostr  This was such a great motivating experience. Attending as a volunteer at the Nostr booth during the Bitcoin Amsterdam 2024 conference. Please read my note with all the lessons I learned [here](https://nostrver.se/note/my-learned-nostr-lessons-nostr-booth-bitcoin-amsterdam-2024). ## The other stuff * The Nostr related blog articles I wrote past year: * [**Run a Nostr relay with your own policies**](https://sebastix.nl/blog/run-a-nostr-relay-with-your-own-policies/) (02-04-2024) * [**Why social networks should be based on commons**](https://sebastix.nl/blog/why-social-networks-should-be-based-on-commons/) (03-01-2024) * [**How could Drupal adopt Nostr?**](https://sebastix.nl/blog/how-could-drupal-adopt-nostr/) (30-12-2023) * [**Nostr integration for CCHS.social**](https://sebastix.nl/blog/nostr-integration-for-cchs-social-drupal-cms/) (21-12-2023) * [https://ccns.nostrver.se](https://ccns.nostrver.se) CCNS stands for Community Curated Nostr Stuff. At the end of 2023 I started to build this project. I forked an existing Drupal project of mine (https://cchs.social) to create a link aggregation website inspired by stacker.news. At the beginning of 2024 I also joined the TopBuilder 2024 contest which was a productive period getting to know new people in the Bitcoin and Nostr space. * [https://nuxstr.nostrver.se](https://nuxstr.nostrver.se) PHP is not my only language I use to build stuff. As a fullstack webdeveloper I also work with Javascript. Many Nostr clients are made with Javascript frameworks or other more client-side focused tools. Vuejs is currently my Javascript framework I'm the most convenient with. With Vuejs I started to tinker around with Nuxt combined with NDK and so I created a starter template for Vue / Nuxt developers. * [ZapLamp](nostr:npub1nfrsmpqln23ls7y3e4m29c22x3qaq9wmmr7zkfcttty2nk2kd6zs9re52s) This is a neat DIY package from LNbits. Powered by an Arduino ESP32 dev board it was running a 24/7 livestream on zap.stream at my office. It flashes when you send a zap to the npub of the ZapLamp. * [https://nosto.re](https://nosto.re) Since the beginning when the Blossom spec was published by @hzrd49 and @StuartBowman I immediately took the opportunity to tinker with it. I'm also running a relay for transmitting Blossom Nostr events `wss://relay.nosto.re`. * [Relays I maintain](https://nostrver.se/note/relays-i-maintain) I really enjoy to tinker with different relays implementations. Relays are the fundamental base layer to let Nostr work. I'm still sharing my contributions on [https://nostrver.se/](https://nostrver.se/) where I publish my weekly Nostr related stuff I worked on. This website is built with Drupal where I use the Nostr Simple Publish and Nostr long-form content NIP-23 modules to crosspost the notes and long-form content to the Nostr network (like this piece of content you're reading).  ## The Nostr is the people Just like the web, the web is people: [https://www.youtube.com/watch?v=WCgvkslCzTo](https://www.youtube.com/watch?v=WCgvkslCzTo) > the people on nostr are some of the smartest and coolest i’ve ever got to know. who cares if it doesn’t take over the world. It’s done more than i could ever ask for. - [@jb55](nostr:note1fsfqja9kkvzuhe5yckff3gkkeqe7upxqljg2g4nkjzp5u9y7t25qx43uch) Here are some Nostriches who I'm happy to have met and who influenced my journey in Nostr in a positive way. * Jurjen * Bitpopart * Arjen * Jeroen * Alex Gleason * Arnold Lubach * Nathan Day * Constant * fiatjaf * Sync ## Coming year Generally I will continue doing what I've done last year. Besides the time I spent on Nostr stuff, I'm also very busy with Drupal related work for my customers. I hope I can get the opportunity to work on a paid client project related to Nostr. It will be even better when I can combine my Drupal expertise with Nostr for projects paid by customers. ### Building a new Nostr application When I look at my Nostr backlog where I just put everything in with ideas and notes, there are quite some interesting concepts there for building new Nostr applications. Filtering out, I think these three are the most exciting ones: * nEcho, a micro app for optimizing your reach via Nostr (NIP-65) * Nostrides.cc platform where you can share Nostr activity events (NIP-113) * A child-friendly video web app with parent-curated content (NIP-71) ### Nostr & Drupal When working out a new idea for a Nostr client, I'm trying to combine my expertises into one solution. That's why I also build and maintain some Nostr contrib modules for Drupal. * [Nostr Simple Publish](https://www.drupal.org/project/nostr_simple_publish) Drupal module to cross-post notes from Drupal to Nostr * [Nostr long-form content NIP-23](https://www.drupal.org/project/nostr_content_nip23) Drupal module to cross-post Markdown formatted content from Drupal to Nostr * [Nostr internet identifier NIP-05](https://www.drupal.org/project/nostr_id_nip05) Drupal module to setup Nostr internet identifier addresses with Drupal. * [Nostr NDK](https://drupal.org/project/nostr_dev_kit) Includes the Javascript library Nostr Dev Kit (NDK) in a Drupal project. One of my (very) ambitious goals is to build a Drupal powered Nostr (website) package with the following main features: * Able to login into Drupal with your Nostr keypair * Cross-post content to the Nostr network * Fetch your Nostr content from the Nostr content * Serve as a content management system (CMS) for your Nostr events * Serve as a framework to build a hybrid Nostr web application * Run and maintain a Nostr relay with custom policies * Usable as a feature rich progressive web app * Use it as a remote signer These are just some random ideas as my Nostr + Drupal backlog is way longer than this. ### Nostr-PHP With all the newly added and continues being updated NIPs in the protocol, this helper library will never be finished. As the sole maintainer of this library I would like to invite others to join as a maintainer or just be a contributor to the library. PHP is big on the web, but there are not many PHP developers active yet using Nostr. Also PHP as a programming language is really pushing forward keeping up with the latest innovations. ### Grow Nostr outside the Bitcoin community We are working out a submission to host a Nostr stand at FOSDEM 2025. If approved, it will be the first time (as far as I know) that Nostr could be present at a conference outside the context of Bitcoin. The audience at FOSDEM is mostly technical oriented, so I'm really curious what type of feedback we will receive. Let's finish this article with some random Nostr photos from last year. Cheers!        @ 3f770d65:7a745b24
2024-10-29 17:38:20**Amber** [Amber](https://github.com/greenart7c3/Amber) is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications. <img src="https://cdn.satellite.earth/b42b649a16b8f51b48f482e304135ad325ec89386b5614433334431985d4d60d.jpg"> Amber is supported by a growing list of apps, including [Amethyst](https://www.amethyst.social/), [0xChat](https://0xchat.com/#/), [Voyage](https://github.com/dluvian/voyage), [Fountain](https://fountain.fm/), and [Pokey](https://github.com/KoalaSat/pokey), as well as any web application that supports NIP-46 NSEC bunkers, such as [Nostr Nests](https://nostrnests.com), [Coracle](https://coracle.social), [Nostrudel](https://nostrudel.ninja), and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms. <img src="https://cdn.satellite.earth/5b5d4fb9925fabb0005eafa291c47c33778840438438679dfad5662a00644c90.jpg"> Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's [GitHub](https://github.com/greenart7c3/Amber) page, via [Obtainium ](https://github.com/ImranR98/Obtainium)or Zap.store. To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com. <img src="https://cdn.satellite.earth/ca2156bfa084ee16dceea0739e671dd65c5f8d92d0688e6e59cc97faac199c3b.jpg"> --- **Citrine** [Citrine](https://github.com/greenart7c3/Citrine) is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control. <img src="https://cdn.satellite.earth/46bbc10ca2efb3ca430fcb07ec3fe6629efd7e065ac9740d6079e62296e39273.jpg"> With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality. Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration. <img src="https://cdn.satellite.earth/6ea01b68009b291770d5b11314ccb3d7ba05fe25cb783e6e1ea977bb21d55c09.jpg"> --- **Pokey** [Pokey](https://github.com/KoalaSat/pokey) for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device. <img src="https://cdn.satellite.earth/62ec76cc36254176e63f97f646a33e2c7abd32e14226351fa0dd8684177b50a2.jpg"> Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem. --- **Zap.store** [Zap.store](https://github.com/zapstore/zapstore/) is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency. <img src="https://cdn.satellite.earth/fd162229a404b317306916ae9f320a7280682431e933795f708d480e15affa23.jpg"> Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing [Zap.store](https://github.com/zapstore/zapstore/) on your favorite Android device, and install all of the applications mentioned above. --- Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems.
@ 3f770d65:7a745b24
2024-10-29 17:38:20**Amber** [Amber](https://github.com/greenart7c3/Amber) is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications. <img src="https://cdn.satellite.earth/b42b649a16b8f51b48f482e304135ad325ec89386b5614433334431985d4d60d.jpg"> Amber is supported by a growing list of apps, including [Amethyst](https://www.amethyst.social/), [0xChat](https://0xchat.com/#/), [Voyage](https://github.com/dluvian/voyage), [Fountain](https://fountain.fm/), and [Pokey](https://github.com/KoalaSat/pokey), as well as any web application that supports NIP-46 NSEC bunkers, such as [Nostr Nests](https://nostrnests.com), [Coracle](https://coracle.social), [Nostrudel](https://nostrudel.ninja), and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms. <img src="https://cdn.satellite.earth/5b5d4fb9925fabb0005eafa291c47c33778840438438679dfad5662a00644c90.jpg"> Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's [GitHub](https://github.com/greenart7c3/Amber) page, via [Obtainium ](https://github.com/ImranR98/Obtainium)or Zap.store. To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com. <img src="https://cdn.satellite.earth/ca2156bfa084ee16dceea0739e671dd65c5f8d92d0688e6e59cc97faac199c3b.jpg"> --- **Citrine** [Citrine](https://github.com/greenart7c3/Citrine) is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control. <img src="https://cdn.satellite.earth/46bbc10ca2efb3ca430fcb07ec3fe6629efd7e065ac9740d6079e62296e39273.jpg"> With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality. Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration. <img src="https://cdn.satellite.earth/6ea01b68009b291770d5b11314ccb3d7ba05fe25cb783e6e1ea977bb21d55c09.jpg"> --- **Pokey** [Pokey](https://github.com/KoalaSat/pokey) for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device. <img src="https://cdn.satellite.earth/62ec76cc36254176e63f97f646a33e2c7abd32e14226351fa0dd8684177b50a2.jpg"> Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem. --- **Zap.store** [Zap.store](https://github.com/zapstore/zapstore/) is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency. <img src="https://cdn.satellite.earth/fd162229a404b317306916ae9f320a7280682431e933795f708d480e15affa23.jpg"> Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing [Zap.store](https://github.com/zapstore/zapstore/) on your favorite Android device, and install all of the applications mentioned above. --- Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems. @ 4ba8e86d:89d32de4
2024-10-22 23:20:59Usar um gerenciador de senhas pode resolver vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Com o uso de um gerenciador de senhas, o usuário pode criar senhas fortes e únicas para cada conta, sem precisar se preocupar em lembrar de todas elas. Além disso,um gerenciador de senhas pode ajudar a simplificar o processo de login, economizando tempo e reduzindo a frustração. O KeepassDX é uma versão do software de gerenciamento de senhas Keepass, desenvolvido originalmente por Dominik Reichl em 2003. O Keepass é um software gratuito e de código aberto para desktops, que permite que os usuários armazenem suas senhas em um banco de dados seguro, criptografado com algoritmos avançados. Em 2017, o desenvolvedor alemão Brian Pellmann criou o KeepassDX como uma versão para dispositivos móveis, com o objetivo de tornar mais fácil para os usuários gerenciarem suas senhas em smartphones e tablets. O KeepassDX foi criado a partir do código-fonte do Keepass e foi projetado para ser fácil de usar, seguro e personalizável. Pellmann adicionou várias funcionalidades novas ao KeepassDX, incluindo a capacidade de importar senhas de outros gerenciadores de senhas, a organização de senhas em categorias e a compatibilidade com serviços de armazenamento em nuvem para sincronização entre dispositivos. Algumas das funcionalidades do KeepassDX incluem a criação de senhas fortes e únicas, preenchimento automático de senhas, autenticação de dois fatores e organização de senhas por categorias. O KeepassDX também oferece uma ferramenta para importação de senhas de outros gerenciadores de senhas, o que torna a transição para o uso do KeepassDX mais fácil. Passo a passo instalação do aplicativo KeepassDX: 1. Baixe e instale o KeepassDX em seu dispositivo móvel https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free 2. Clique em [CRIAR NOVO BANCO DE DADOS] 3. Selecione o local do arquivo no meu caso é " transferência " Semelhante ao KeePassXC, o KeePassDX suporta o formato de banco de dados .kbdx (por exemplo, Passwords.kdbx) para armazenar senhas de contas importantes. Você deve salvar este arquivo em um local de fácil acesso para você, mas difícil de encontrar para outras pessoas que você não deseja visualizar as informações. Em particular, evite salvar seu arquivo de banco de dados em um serviço de armazenamento online, conectado às suas contas, pois pode ser acessado por outras pessoas. 4. Digite um nome para seu banco de dados Neste exemplo, " urso " nosso banco de dados como "urso.kdbx"; você pode escolher um nome de sua preferência. Você pode usar um nome que disfarce o arquivo e o torne menos óbvio para invasores que podem tentar acessar seu telefone e exigir que você desbloqueie o banco de dados. Também é possível alterar a "extensão" no final do nome do arquivo. Por exemplo, você pode nomear o banco de dados de senhas "Revoltadeatlas.pdf" "primainterior.jpg " e o sistema operacional geralmente dará ao arquivo um ícone de "aparência normal". Lembre-se de que, se você der ao seu banco de dados de senhas um nome que não termine em ".kdbx", não poderá abrir o arquivo diretamente. Em vez disso, você terá que iniciar o KeePassDX primeiro e, em seguida, abrir seu banco de dados clicando no botão "Abrir banco de dados existente". Felizmente, o KeePassDX lembra o último banco de dados que você abriu, então você não terá que fazer isso com frequência. https://github.com/Kunzisoft/KeePassDX
@ 4ba8e86d:89d32de4
2024-10-22 23:20:59Usar um gerenciador de senhas pode resolver vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Com o uso de um gerenciador de senhas, o usuário pode criar senhas fortes e únicas para cada conta, sem precisar se preocupar em lembrar de todas elas. Além disso,um gerenciador de senhas pode ajudar a simplificar o processo de login, economizando tempo e reduzindo a frustração. O KeepassDX é uma versão do software de gerenciamento de senhas Keepass, desenvolvido originalmente por Dominik Reichl em 2003. O Keepass é um software gratuito e de código aberto para desktops, que permite que os usuários armazenem suas senhas em um banco de dados seguro, criptografado com algoritmos avançados. Em 2017, o desenvolvedor alemão Brian Pellmann criou o KeepassDX como uma versão para dispositivos móveis, com o objetivo de tornar mais fácil para os usuários gerenciarem suas senhas em smartphones e tablets. O KeepassDX foi criado a partir do código-fonte do Keepass e foi projetado para ser fácil de usar, seguro e personalizável. Pellmann adicionou várias funcionalidades novas ao KeepassDX, incluindo a capacidade de importar senhas de outros gerenciadores de senhas, a organização de senhas em categorias e a compatibilidade com serviços de armazenamento em nuvem para sincronização entre dispositivos. Algumas das funcionalidades do KeepassDX incluem a criação de senhas fortes e únicas, preenchimento automático de senhas, autenticação de dois fatores e organização de senhas por categorias. O KeepassDX também oferece uma ferramenta para importação de senhas de outros gerenciadores de senhas, o que torna a transição para o uso do KeepassDX mais fácil. Passo a passo instalação do aplicativo KeepassDX: 1. Baixe e instale o KeepassDX em seu dispositivo móvel https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free 2. Clique em [CRIAR NOVO BANCO DE DADOS] 3. Selecione o local do arquivo no meu caso é " transferência " Semelhante ao KeePassXC, o KeePassDX suporta o formato de banco de dados .kbdx (por exemplo, Passwords.kdbx) para armazenar senhas de contas importantes. Você deve salvar este arquivo em um local de fácil acesso para você, mas difícil de encontrar para outras pessoas que você não deseja visualizar as informações. Em particular, evite salvar seu arquivo de banco de dados em um serviço de armazenamento online, conectado às suas contas, pois pode ser acessado por outras pessoas. 4. Digite um nome para seu banco de dados Neste exemplo, " urso " nosso banco de dados como "urso.kdbx"; você pode escolher um nome de sua preferência. Você pode usar um nome que disfarce o arquivo e o torne menos óbvio para invasores que podem tentar acessar seu telefone e exigir que você desbloqueie o banco de dados. Também é possível alterar a "extensão" no final do nome do arquivo. Por exemplo, você pode nomear o banco de dados de senhas "Revoltadeatlas.pdf" "primainterior.jpg " e o sistema operacional geralmente dará ao arquivo um ícone de "aparência normal". Lembre-se de que, se você der ao seu banco de dados de senhas um nome que não termine em ".kdbx", não poderá abrir o arquivo diretamente. Em vez disso, você terá que iniciar o KeePassDX primeiro e, em seguida, abrir seu banco de dados clicando no botão "Abrir banco de dados existente". Felizmente, o KeePassDX lembra o último banco de dados que você abriu, então você não terá que fazer isso com frequência. https://github.com/Kunzisoft/KeePassDX @ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever. nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees: nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp But how big is too big? How can we better understand the range of options available for devs out there? I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof. - **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports. - **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them. - **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped. Based on my made-up categories described at the end, this is how I would split our most known apps. **Super Clients** - [amethyst](https://amethyst.social) - [nostrudel](https://nostrudel.ninja) - [coracle](https://coracle.social) **Clients** - [damus](https://damus.io) - twitter - [primal](https://primal.net) - twitter - [snort](https://snort.social) - twitter - [gossip](https://github.com/mikedilger/gossip) - twitter - [lume](https://lume.nu) - twitter - [ditto](https://soapbox.pub/ditto/) - twitter - [rabbit](https://rabbit.syusui.net) - twitter - [freefrom](https://freefrom.space) - twitter - [nos](https://nos.social) - twitter - [flycat](https://flycat.club) - twitter - [straylight](https://straylight.cafe) - twitter - [nostter](https://nostter.app) - twitter - [iris](https://iris.to) - twitter - [nostur](https://nostur.com) - twitter - [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter - [yana](https://yana.do) - twitter - [openvibe](https://openvibe.social) - twitter - [freerse](https://freerse.com) - twitter - [0xchat](https://0xchat.com) - chats - [cornychat](https://cornychat.com) - chats - [coop](https://github.com/lumehq/coop) - chats - [nostrchat](https://nostrchat.io) - chats - [blowater](https://blowater.deno.dev) - chats - [habla](https://habla.news) - blogs - [yakihonne](https://yakihonne.com) - blogs - [highlighter](https://highlighter.com) - blogs - [blogstack](https://blogstack.io) - blogs - [stemstr](https://stemstr.app) - music - [wavlake](https://wavlake.com) - music - [fountain](https://fountain.fm) - podcasts - [zap.stream](https://zap.stream) - live streaming - [shopstr](https://shopstr.store) - marketplace - [plebeian.market](https://plebeian.market) - marketplace - [flotilla](https://flotilla.coracle.social) - communities - [satellite](https://satellite.earth) - communities - [zapddit](https://zapddit.com) - communities - [nostr.kiwi](https://nostr.kiwi) - communities - [hivetalk](https://hivetalk.org) - video calls - [flare](https://flare.pub) - long-form videos - [nostrnests](https://nostrnests.com) - audio spaces - [wherostr](https://wherostr.social) - location - [yondar](https://go.yondar.me) - location - [stacker.news](https://stacker.news) - news - [flockstr](https://flockstr.com) - events - [nostrocket](https://nostrocket.org) - issue tracker - [docstr](https://docstr.app) - docs - [satshoot](https://satshoot.com) - freelance - [wikifreedia](https://wikifreedia.xyz) - wiki - [formstr](https://formstr.app) - forms - [chesstr](https://chesstr.pages.dev) - chess - [memestr](https://memestr.app) - meme feed - [npub.cash](https://npub.cash) - wallet - [npub.pro](https://npub.pro) - websites - [gitworkshop](https://gitworkshop.dev) - dev tools - [onosendai](https://onosendai.tech) - metaverse - [degmods](https://degmods.com) - games - [turdsoup](https://turdsoup.com) - prompts **Mini Clients** - [amber](https://github.com/greenart7c3/Amber) - signer - [alby](https://getalby.com) - signer - [nos2x](https://github.com/fiatjaf/nos2x) - signer - [nsec.app](https://nsec.app) - signer - [keys.band](https://keys.band) - signer - [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer - [nokakoi](https://nokakoi.com) - anon - [zap.cooking](https://zap.cooking) - recipes - [anonostr](https://anonostr.com) - anon - [getwired](https://getwired.app) - anon - [lowent](https://lowent.xyz) - anon - [creatr](https://creatr.nostr.wine) - exclusive content - [lightning.video](https://lightning.video) - exclusive content - [zaplinks](https://zaplinks.lol/slides) - slides - [listr](https://listr.lol) - lists - [zap.store](https://zap.store) - app store - [badges.page](https://badges.page) - badges - [oddbean](https://oddbean.com) - news - [dtan](https://dtan.xyz) - torrents - [nosta](https://nosta.me) - user pages - [pinstr](https://pinstr.app) - pinterest - [pollerama](https://pollerama.fun) - polls - [swarmstr](https://swarmstr.com) - trending - [nostrapp](https://nostrapp.link) - apps manager - [noogle](https://noogle.lol) - search - [ostrich.work](https://ostrich.work) - job postings - [emojito](https://emojito.meme) - emoji manager - [nostree](https://nostree.me) - links - [citrine](https://github.com/greenart7c3/citrine) - local relay - [joinstr](https://joinstr.xyz) - coinjoins - [heya](https://heya.fund) - crowdfunding - [zapplepay](https://zapplepay.com) - zaps - [nosbin](https://nosbin.com) - clipboard - [shipyard](https://shipyard.pub) - scheduler - [tunestr](https://tunestr.io) - live streams - [filestr](https://filestr.vercel.app) - files - [nostrcheck.me](https://nostrcheck.me/) - media hosting - [sheetstr](https://sheetstr.amethyst.social) - spreadsheets - [crafters](https://crafters.amethyst.social) - curriculum vitae **Micro Clients** - [w3](https://w3.do) - url shortener - [nosdrive](https://nosdrive.app) - backups - [zaplife](https://zaplife.lol) - zaps dashboard - [zapper.fun](https://zapper.fun) - payments - [nostrends](https://nostrends.vercel.app) - trends - [zephyr](https://zephyr.coracle.social) - trends - [wavman](https://wavman.app) - music player - [nostrrr](https://nostrrr.com) - relay info - [nosdump](https://github.com/jiftechnify/nosdump) - relay info - [notestack](https://notestack.com) - blogs - [nostr.build](https://nostr.build) - media hosting - [nostr.watch](https://nostr.watch) - relay info - [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports - [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions - [snakestr](https://satoshipuzzles.github.io/Snakestr) - games - [deletestr](https://zaplinks.lol/deletestr) - deletion requests - [2048str](https://zaplinks.lol/2048str) - games - [nostrqr](https://zaplinks.lol/nostrqr) - qr generator - [notanostrclient](https://zaplinks.lol/notanostrclient) - anon Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients.
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever. nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees: nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp But how big is too big? How can we better understand the range of options available for devs out there? I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof. - **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports. - **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them. - **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped. Based on my made-up categories described at the end, this is how I would split our most known apps. **Super Clients** - [amethyst](https://amethyst.social) - [nostrudel](https://nostrudel.ninja) - [coracle](https://coracle.social) **Clients** - [damus](https://damus.io) - twitter - [primal](https://primal.net) - twitter - [snort](https://snort.social) - twitter - [gossip](https://github.com/mikedilger/gossip) - twitter - [lume](https://lume.nu) - twitter - [ditto](https://soapbox.pub/ditto/) - twitter - [rabbit](https://rabbit.syusui.net) - twitter - [freefrom](https://freefrom.space) - twitter - [nos](https://nos.social) - twitter - [flycat](https://flycat.club) - twitter - [straylight](https://straylight.cafe) - twitter - [nostter](https://nostter.app) - twitter - [iris](https://iris.to) - twitter - [nostur](https://nostur.com) - twitter - [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter - [yana](https://yana.do) - twitter - [openvibe](https://openvibe.social) - twitter - [freerse](https://freerse.com) - twitter - [0xchat](https://0xchat.com) - chats - [cornychat](https://cornychat.com) - chats - [coop](https://github.com/lumehq/coop) - chats - [nostrchat](https://nostrchat.io) - chats - [blowater](https://blowater.deno.dev) - chats - [habla](https://habla.news) - blogs - [yakihonne](https://yakihonne.com) - blogs - [highlighter](https://highlighter.com) - blogs - [blogstack](https://blogstack.io) - blogs - [stemstr](https://stemstr.app) - music - [wavlake](https://wavlake.com) - music - [fountain](https://fountain.fm) - podcasts - [zap.stream](https://zap.stream) - live streaming - [shopstr](https://shopstr.store) - marketplace - [plebeian.market](https://plebeian.market) - marketplace - [flotilla](https://flotilla.coracle.social) - communities - [satellite](https://satellite.earth) - communities - [zapddit](https://zapddit.com) - communities - [nostr.kiwi](https://nostr.kiwi) - communities - [hivetalk](https://hivetalk.org) - video calls - [flare](https://flare.pub) - long-form videos - [nostrnests](https://nostrnests.com) - audio spaces - [wherostr](https://wherostr.social) - location - [yondar](https://go.yondar.me) - location - [stacker.news](https://stacker.news) - news - [flockstr](https://flockstr.com) - events - [nostrocket](https://nostrocket.org) - issue tracker - [docstr](https://docstr.app) - docs - [satshoot](https://satshoot.com) - freelance - [wikifreedia](https://wikifreedia.xyz) - wiki - [formstr](https://formstr.app) - forms - [chesstr](https://chesstr.pages.dev) - chess - [memestr](https://memestr.app) - meme feed - [npub.cash](https://npub.cash) - wallet - [npub.pro](https://npub.pro) - websites - [gitworkshop](https://gitworkshop.dev) - dev tools - [onosendai](https://onosendai.tech) - metaverse - [degmods](https://degmods.com) - games - [turdsoup](https://turdsoup.com) - prompts **Mini Clients** - [amber](https://github.com/greenart7c3/Amber) - signer - [alby](https://getalby.com) - signer - [nos2x](https://github.com/fiatjaf/nos2x) - signer - [nsec.app](https://nsec.app) - signer - [keys.band](https://keys.band) - signer - [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer - [nokakoi](https://nokakoi.com) - anon - [zap.cooking](https://zap.cooking) - recipes - [anonostr](https://anonostr.com) - anon - [getwired](https://getwired.app) - anon - [lowent](https://lowent.xyz) - anon - [creatr](https://creatr.nostr.wine) - exclusive content - [lightning.video](https://lightning.video) - exclusive content - [zaplinks](https://zaplinks.lol/slides) - slides - [listr](https://listr.lol) - lists - [zap.store](https://zap.store) - app store - [badges.page](https://badges.page) - badges - [oddbean](https://oddbean.com) - news - [dtan](https://dtan.xyz) - torrents - [nosta](https://nosta.me) - user pages - [pinstr](https://pinstr.app) - pinterest - [pollerama](https://pollerama.fun) - polls - [swarmstr](https://swarmstr.com) - trending - [nostrapp](https://nostrapp.link) - apps manager - [noogle](https://noogle.lol) - search - [ostrich.work](https://ostrich.work) - job postings - [emojito](https://emojito.meme) - emoji manager - [nostree](https://nostree.me) - links - [citrine](https://github.com/greenart7c3/citrine) - local relay - [joinstr](https://joinstr.xyz) - coinjoins - [heya](https://heya.fund) - crowdfunding - [zapplepay](https://zapplepay.com) - zaps - [nosbin](https://nosbin.com) - clipboard - [shipyard](https://shipyard.pub) - scheduler - [tunestr](https://tunestr.io) - live streams - [filestr](https://filestr.vercel.app) - files - [nostrcheck.me](https://nostrcheck.me/) - media hosting - [sheetstr](https://sheetstr.amethyst.social) - spreadsheets - [crafters](https://crafters.amethyst.social) - curriculum vitae **Micro Clients** - [w3](https://w3.do) - url shortener - [nosdrive](https://nosdrive.app) - backups - [zaplife](https://zaplife.lol) - zaps dashboard - [zapper.fun](https://zapper.fun) - payments - [nostrends](https://nostrends.vercel.app) - trends - [zephyr](https://zephyr.coracle.social) - trends - [wavman](https://wavman.app) - music player - [nostrrr](https://nostrrr.com) - relay info - [nosdump](https://github.com/jiftechnify/nosdump) - relay info - [notestack](https://notestack.com) - blogs - [nostr.build](https://nostr.build) - media hosting - [nostr.watch](https://nostr.watch) - relay info - [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports - [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions - [snakestr](https://satoshipuzzles.github.io/Snakestr) - games - [deletestr](https://zaplinks.lol/deletestr) - deletion requests - [2048str](https://zaplinks.lol/2048str) - games - [nostrqr](https://zaplinks.lol/nostrqr) - qr generator - [notanostrclient](https://zaplinks.lol/notanostrclient) - anon Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients. @ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados. Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch". Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch. Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3. Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras. No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar. Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações. Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo. Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline. Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe. Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição. Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados. O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos. Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes. Modelo de Risco. Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas. https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável. Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch. Modelo de ameaça. É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações. Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação. Procuramos proteger os seguintes contextos de comunicação: • Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”. • Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”. • Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”. • Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã." Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior: • Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas. • Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si. • Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam). • Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos Ataques de deturpação. O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas: O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos: •Alice tem um amigo chamado Bob e outro chamado Eve • Eve descobre que Alice tem um amigo chamado Bob • Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos) • Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga. • Eve então muda seu nome em "Eve New Account" para "Bob" • Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá . Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários. Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão. Um perfil Cwtch. Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor. Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas). Conversões entre duas partes: ponto a ponto https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola). Após a conexão, ambas as partes adotam um protocolo de autenticação que: • Afirma que cada parte tem acesso à chave privada associada à sua identidade pública. • Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão. Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma. Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente. Conversas em Grupo e Comunicação Ponto a Servidor Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros. Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura. Detalhamento do Ecossistema de Componentes O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem: - abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor. - cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos. - cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch. - cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI. TAPIR: Uma Visão Detalhada Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos. Está dividido em várias camadas: • Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par. • Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services. • Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado. • Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação. Identidade. Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer. InitializeIdentity - de um par de chaves conhecido e persistente:i,I InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie Aplicativos de transcrição. Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição). Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos. Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para: • protocolos multi-round com fases alternadas de commit e desafio; • separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas; • enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso; • e composição do protocolo, usando uma transcrição comum para vários protocolos. Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo. Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós. Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor. Criptografia e armazenamento de perfil. Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2). Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha. Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato . Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil. Vulnerabilidades Relacionadas a Imagens e Entrada de Dados Imagens Maliciosas O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória. Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem. Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple. Riscos de Entrada de Dados Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais. Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel. Servidor Cwtch. O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável . Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança. O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem: • O Cwtch Server pode ser usado por vários grupos ou apenas um. • Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo. • Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação. • Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas. Melhorias na Eficiência e Segurança Eficiência do Protocolo Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas. Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas. Mitigação de Análise de Metadados Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores: 1. Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor. 2. Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo. Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl. Proteção contra Pares Maliciosos Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos. Pacotes de Chaves Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass. Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais. Configuração prévia do aplicativo para ativar o Relé do Cwtch. No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops. No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch. Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch. Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil. https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4 Próximo passo é Criar um perfil. Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil. - Selecione um nome de exibição - Selecione se deseja proteger este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil. Preencha sua senha e digite-a novamente Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2). Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha. https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4 O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento. Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad. Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável. https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4 Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa. Uma introdução aos perfis Cwtch. Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor. Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch. Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente. Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode: - Crie um novo perfil. - Desbloquear perfis. - Criptografados existentes. - Gerenciar perfis carregados. - Alterando o nome de exibição de um perfil. - Alterando a senha de um perfil Excluindo um perfil. - Alterando uma imagem de perfil. Backup ou exportação de um perfil. Na tela de gerenciamento de perfil: 1. Selecione o lápis ao lado do perfil que você deseja editar 2. Role para baixo até a parte inferior da tela. 3. Selecione "Exportar perfil" 4. Escolha um local e um nome de arquivo. 5.confirme. Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil. Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo. Importando um perfil. 1. Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil" 2. Selecione um arquivo de perfil Cwtch exportado para importar 3. Digite a senha associada ao perfil e confirme. Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso. OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens. Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch? As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens. Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo. Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional. Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo . https://git.openprivacy.ca/cwtch.im/server https://docs.openprivacy.ca/cwtch-security-handbook/server.html Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados. Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação https://openprivacy.ca/donate/ onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/ Link sobre Cwtch https://cwtch.im/ https://git.openprivacy.ca/cwtch.im/cwtch https://docs.cwtch.im/docs/intro https://docs.openprivacy.ca/cwtch-security-handbook/ Baixar #CwtchDev cwtch.im/download/ https://play.google.com/store/apps/details?id=im.cwtch.flwtch
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados. Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch". Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch. Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3. Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras. No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar. Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações. Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo. Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline. Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe. Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição. Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados. O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos. Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes. Modelo de Risco. Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas. https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável. Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch. Modelo de ameaça. É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações. Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação. Procuramos proteger os seguintes contextos de comunicação: • Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”. • Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”. • Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”. • Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã." Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior: • Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas. • Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si. • Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam). • Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos Ataques de deturpação. O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas: O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos: •Alice tem um amigo chamado Bob e outro chamado Eve • Eve descobre que Alice tem um amigo chamado Bob • Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos) • Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga. • Eve então muda seu nome em "Eve New Account" para "Bob" • Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá . Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários. Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão. Um perfil Cwtch. Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor. Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas). Conversões entre duas partes: ponto a ponto https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola). Após a conexão, ambas as partes adotam um protocolo de autenticação que: • Afirma que cada parte tem acesso à chave privada associada à sua identidade pública. • Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão. Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma. Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente. Conversas em Grupo e Comunicação Ponto a Servidor Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros. Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura. Detalhamento do Ecossistema de Componentes O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem: - abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor. - cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos. - cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch. - cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI. TAPIR: Uma Visão Detalhada Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos. Está dividido em várias camadas: • Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par. • Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services. • Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado. • Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação. Identidade. Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer. InitializeIdentity - de um par de chaves conhecido e persistente:i,I InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie Aplicativos de transcrição. Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição). Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos. Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para: • protocolos multi-round com fases alternadas de commit e desafio; • separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas; • enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso; • e composição do protocolo, usando uma transcrição comum para vários protocolos. Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo. Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós. Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor. Criptografia e armazenamento de perfil. Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2). Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha. Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato . Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil. Vulnerabilidades Relacionadas a Imagens e Entrada de Dados Imagens Maliciosas O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória. Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem. Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple. Riscos de Entrada de Dados Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais. Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel. Servidor Cwtch. O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável . Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança. O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem: • O Cwtch Server pode ser usado por vários grupos ou apenas um. • Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo. • Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação. • Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas. Melhorias na Eficiência e Segurança Eficiência do Protocolo Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas. Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas. Mitigação de Análise de Metadados Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores: 1. Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor. 2. Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo. Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl. Proteção contra Pares Maliciosos Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos. Pacotes de Chaves Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass. Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais. Configuração prévia do aplicativo para ativar o Relé do Cwtch. No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops. No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch. Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch. Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil. https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4 Próximo passo é Criar um perfil. Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil. - Selecione um nome de exibição - Selecione se deseja proteger este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil. Preencha sua senha e digite-a novamente Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2). Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha. https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4 O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento. Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad. Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável. https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4 Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa. Uma introdução aos perfis Cwtch. Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor. Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch. Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente. Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode: - Crie um novo perfil. - Desbloquear perfis. - Criptografados existentes. - Gerenciar perfis carregados. - Alterando o nome de exibição de um perfil. - Alterando a senha de um perfil Excluindo um perfil. - Alterando uma imagem de perfil. Backup ou exportação de um perfil. Na tela de gerenciamento de perfil: 1. Selecione o lápis ao lado do perfil que você deseja editar 2. Role para baixo até a parte inferior da tela. 3. Selecione "Exportar perfil" 4. Escolha um local e um nome de arquivo. 5.confirme. Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil. Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo. Importando um perfil. 1. Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil" 2. Selecione um arquivo de perfil Cwtch exportado para importar 3. Digite a senha associada ao perfil e confirme. Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso. OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens. Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch? As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens. Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo. Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional. Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo . https://git.openprivacy.ca/cwtch.im/server https://docs.openprivacy.ca/cwtch-security-handbook/server.html Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados. Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação https://openprivacy.ca/donate/ onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/ Link sobre Cwtch https://cwtch.im/ https://git.openprivacy.ca/cwtch.im/cwtch https://docs.cwtch.im/docs/intro https://docs.openprivacy.ca/cwtch-security-handbook/ Baixar #CwtchDev cwtch.im/download/ https://play.google.com/store/apps/details?id=im.cwtch.flwtch @ bcbb3e40:a494e501
2024-09-24 17:23:00|[](https://amzn.to/4e8iIzx)| |:-:| |[BLANCO, Carlos X. y COSTALES, Jose; _España: Historia de una demolición controlada_; Letras Inquietas, 2024](https://amzn.to/4e8iIzx)| Ya hemos publicado varias reseñas de algunas obras del Profesor [**Carlos X. Blanco**](https://hiperbolajanus.com/firmas/carlos-x.-blanco/), cuyas temáticas nos resultan totalmente familiares, y con las que coincidimos en un buen número de sus análisis y críticas del mundo actual. Recordaremos, para aquellos que estén interesados en sus obras las reseñas de [_De Covadonga a la nación española: La hispanidad en clave spengleriana_](https://hiperbolajanus.com/posts/covadonga-nacion-espanola-carlos-x-blanco/) y [_Un imperio frente al caos_](https://hiperbolajanus.com/posts/resena-un-imperio-frente-al-caos-de/), además de algunas otras que podréis encontrar en nuestro blog. La obra del autor asturiano, en este caso en coautoría con **José Costales**, resulta muy clarificadora a la hora de analizar aspectos generales de la historia de España, cuestiones que tienen que ver con nuestra historia particular, y aquellos hechos que podemos considerar como más generales y fruto de un contexto y unas coyunturas que han marcado el destino de nuestra Patria en los últimos tiempos. Es por ese motivo, que así de entrada podemos distinguir dos bloques claramente diferenciados en esta obra: Un primer bloque que aborda nuestra historia peculiar, las características que definen el «hecho hispánico» y marcan nuestro devenir histórico; un segundo bloque en el que se señalan las amenazas y peligros que se yerguen frente a la España actual, aparentemente agonizante y desahuciada por la falta de soberanía y una serie de problemas graves y trascendentales que amenazan nuestra existencia. Hay que destacar que el prólogo que precede a la obra en sí y le sirve como presentación corre a cargo del conocido abogado, jurista e historiador **Guillermo Rocafort**. En un breve pero certero escrito delinea los grandes problemas que atenazan a un Occidente decadente en plena crisis económica, geopolítica y de valores, embarcado en una deriva suicida que hace aguas y se ha vuelto insostenible. La crisis del capitalismo unipolar y globalista enfrenta el reto de la pujanza de los BRICS, con el resurgimiento de Rusia y el desarrollo y ascenso como superpotencia de China, junto a la formación de grandes bloques geopolíticos que definen la multipolaridad que, recientemente, [autores como Aleksandr Duguin vienen teorizando desde la escuela euroasiática](https://hiperbolajanus.com/libros/geopolitica-rusia-aleksandr-duguin/). Esta situación hace que la el mundo anglosajón y sus oligarquías plutocráticas comiencen a ver resquebrajada su hegemonía, con su sistema de dinero fiat y sus organizaciones pantalla, tales como la Unión Europea, o el desarrollo de su conocida como ideología _woke_ y todas las perversas y destructivas ingenierías sociales asociadas, así como la acción de la Agenda 2030. |[](https://www.amazon.com/dp/B0892V95MV)| |:-:| |[DUGUIN, Aleksandr G.; _La geopolítica de Rusia: De la revolución rusa a Putin_; Hipérbola Janus, 2015](https://www.amazon.com/dp/B0892V95MV)| En el caso particular de España los efectos de los más de 300 años de dominio anglosajón han tenido consecuencias especialmente perniciosas con la desindustrialización, la destrucción del sector primario, las ingenierías sociales asociadas a las ideologías de género, donde España ha servido como particular conejillo de indias, o nuestras permanentes renuncias en materia de política exterior, donde nos hemos visto obligados, por imposiciones venidas del otro lado del Atlántico, a renunciar a nuestra soberanía sobre el Sahara Occidental o a las permanentes y humillantes cesiones a Marruecos. En el escrito de Introducción, los autores trazan una genealogía de los hechos, de las circunstancias que se hallan detrás de las razones del propio título de la obra, «Historia de una demolición controlada», en la que el papel de la angloesfera ha sido fundamental para la situación de debilidad, sometimiento y negación de nuestra propia historia que vivimos en la actualidad. Somos parte de una Europa sojuzgada que actúa a remolque de las políticas estadounidenses y anglosajonas, a través de la acción de la OTAN, donde no somos más que un agregado servil, actuando en defensa de los intereses geopolíticos del Imperio. Dentro de Europa, la UE define otro tipo de jerarquías internas, en las cuales el eje franco-alemán impone sus intereses a los países con economías menos desarrolladas del sur. Al mismo tiempo, también se advierten las importantes transformaciones que el régimen constitucional de 1978 ha experimentado en las últimas décadas, especialmente a partir de [**Zapatero**](https://hiperbolajanus.com/firmas/jose-luis-rodriguez-zapatero/), con el mayor sojuzgamiento de España a la Agenda globalista. Todas estas circunstancias adversas, y también trágicas para nuestro destino, hacen necesario un análisis de la propia historia de España, de su gestación y de los atributos que han cimentado la idea de lo español o hispánico. La historia de España ha estado condicionada por su proximidad a África, lo cual ha tenido una importancia decisiva en su configuración final. Con la invasión musulmana del 711 se produjo un episodio de dislocación dentro de nuestra historia, que a partir de ese momento experimentó una situación de dualidad étnico-religiosa y comenzó un episodio transfigurador y de construcción del ideal hispánico que se había iniciado con el reino visigodo de Toledo, y que la Reconquista contribuyó a potenciar. En este sentido, la configuración étnica que resultó de la invasión árabe hizo que las zonas del Norte, donde se refugiaron los restos de la antigua nobleza visigoda derrotada, predominó el elemento germánico que se erigió como motor inicial del proceso de Reconquista, mientras que en otras latitudes del levante y el sur peninsular se produjo un proceso de africanización y semitización sobre las antiguas poblaciones hispanorromanas. Un norte cristiano, germanizado e indoeuropeo, equiparable al Norte de Europa, representado por la monarquía asturiana frente a un sur africanizado, sumido en un caos étnico y de enfrentamientos civiles era el resultado de la entidad andalusí. El proceso de romanización afectó de manera desigual a los territorios peninsulares, y los pueblos de las regiones noroccidentales como astures, cántabros o vascones apenas se vieron afectados, conservando un importante sustrato indoeuropeo en contraste con las regiones más mediterráneas, ocupadas por los íberos, que ya poseían un modelo de civilización elevado y en conexión con las civilizaciones clásicas mediterráneas. Estos elementos ya aparecen claramente expuestos en la interpretación spengleriana que uno de nuestros autores, Carlos X Blanco, expone en [_De Covadonga a la nación española: La hispanidad en clave spengleriana_](https://amzn.to/3BSOIEX). Es el contraste entre una España atlántica, indoeuropea y germanizada frente a otra vertiente representada por la España mediterránea, levantina y romanizada. En la confluencia de ambos modelos tenemos la definición de las sucesivos siglos en los que se forja la Reconquista, en la que, según los autores, pasamos de una etapa inicial de predominio atlántico y noroccidental, con el Reino de Asturias, y posteriormente León, capitalizando el proceso de la Reconquista, mientras que posteriormente, será Castilla, que obedecerá al modelo mediterráneo, quien llevaría la batuta en el avance hacia el Sur y la hispanización de España, porque la invasión del 711 marca un proceso de deshispanización, una idea fundamental, también en nuestra opinión, que el avance de los reinos cristianos del Norte contribuirán a erosionar y finalmente, para nuestra fortuna, destruir por completo. Como parte de la geopolítica hispánica y su relanzamiento como Patria común, es fundamental que España vuelva a resucitar el eje atlántico y noroccidental, propiamente asturiano, frente aquel castellano, para que recupere su primacía como eje en la reconstrucción de España y revertir así la agonía y rumbo errático que nos lleva hacia la destrucción total y la desaparición como nación histórica. No obstante, si queremos refundar España a través de un verdadero proyecto nacional debemos ser realistas, y no dejarnos embelesar por los visiones sobreexcitados que representan el modelo Imperial de los Austrias o posteriores reverberaciones del mismo a través de construcciones ideales, sino que contemplando las actuales coyunturas, con el viraje hacia la multipolaridad que está experimentando el mundo actual, quizás estaríamos llamados, o al menos existe ese gran potencial, a liderar una suerte de hispanosfera con los antiguos países que fueron parte de la América española, frente a la anglosfera, que viene perjudicando nuestra soberanía y sometiéndonos, junto al resto de Europa, como una colonia. Blanco y Costales nos ofrecen algunas directrices para esta reconstrucción, tales como la descentralización de los centros de poder, frente a todo modelo jacobino y liberal diríamos nosotros, como parte de un modelo confederal, que incluso podría apoyarse en la fundación de centros de poder en el continente americano. Asimismo, este modelo confederal, implicaría dotar de mayor poder y protagonismo a las regiones, [tal y como habría postulado uno de los grandes teóricos del tradicionalismo español, Don](https://hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/) [**Juan Vázquez de Mella**](https://hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/), frente al actual modelo balcanizador de las 17 taifas dirigidas por las oligarquías partitocráticas y corruptas del Régimen de 1978. En cuanto al modelo político requerido, este no es la monarquía, sino la república, por el descrédito de los Borbones y la trayectoria descendente y de decadencia que han venido marcando en su reinado desde hace más de 300 años. En cualquier caso, lo que este modelo debe aportar es cohesión interna y voluntad de integración en el modelo de mundo unipolar, que se viene gestando y estructurando bajo relaciones de poder, redes económicas, comerciales y de otro tipo, que deben garantizar esa capacidad de interconexión. Y, por supuesto, en coherencia con lo sostenido con anterioridad, nuestros autores proponen que el eje atlántico y noroccidental debe representar el motor y artífice de este nuevo ciclo histórico. Desde el advenimiento de los Borbones a comienzos del siglo XVIII, el polo mediterráneo y africanizado ha venido tomando un protagonismo creciente, que vemos reflejado el el triunfo posterior, a lo largo del siglo XIX, del liberalismo con la destrucción del Imperio y el sometimiento de España y de su historia a los dominios de la leyenda negra, urdida por la anglosfera, y que tiende a presentarnos como el producto de una hibridación de pueblos afrosemitas y mahometanos, sin identidad, y como una especie de anomalía frente a la europeidad prototípica. Un discurso que, claro está, fue aceptado por el liberalismo español con la consecuente desvalorización y rechazo de los orígenes astur-godos de la monarquía hispánica y del proceso de Reconquista por parte de unas élites corruptas, antiespañolas y endófobas, que se sometieron ideológicamente a Francia y al mundo anglosajón. En un principio, esto sirvió para provocar fragmentar la unidad interna del Imperio Español y enajenar el catolicismo de la Hispanidad, y posteriormente, una vez destruida esa unidad, someter a estos países al [capitalismo depredador y esclavizarlos por la vía de la deuda](https://hiperbolajanus.com/posts/una-reflexion-sobre-el-capitalismo-y-la/). Paralelamente, y a través de la masonería, también se introdujeron ideas profundamente destructivas entre las élites liberales y traidoras, como son el laicismo, el separatismo y otras ideas disolventes que nos vienen desnaturalizando desde hace siglos. La acción de este capitalismo destructivo y depravado, es la que nos ha convertido en un instrumento en manos de grandes cenáculos y organizaciones que forman parte de un entramado complejo y anónimo, desde donde se interviene permanentemente en nuestros asuntos imponiendo cambios profundos en las costumbres, tradiciones e identidad, empobreciéndonos y reduciéndonos a la más pura insignificancia. Otro elemento a destacar, podríamos decir una de las grandes piedras angulares que definen la idiosincrasia de lo Hispánico, viene representado por el Catolicismo, que en el caso peninsular también revistió un carácter peculiar, especialmente en lo que respecta, una vez más, a los contrastes internos entre la zona atlántica-noroccidental y la mediterránea, así como con la propia realidad del reino visigodo, donde la Iglesia resultó ser muy autónoma, vertebrada a través de sus concilios. Con la irrupción de la contemporaneidad, este elemento, el católico, de vital importancia durante la Reconquista y a lo largo de toda nuestra historia, se ha visto disminuido, con la propia acción del liberalismo, y especialmente [desde la izquierda](https://hiperbolajanus.com/libros/izquierda-contra-pueblo-carlos-x-blanco/), y también desde sus propios centros de poder, desde el mismo Vaticano, a raíz de su famoso Concilio Vaticano II, abdicando en sus principios y doctrina frente al liberalismo y el mundo moderno. En el primer párrafo hemos hablado de un primer bloque, que de algún modo vendría a hablarnos de nuestra historia, de la autorepresentación que tenemos de la misma, y los elementos basales que componen su estructura. Esta sería la primera parte del libro. Una segunda parte vendría comprendida por el análisis de otros elementos más externos que definen unas coyunturas internacionales muy características, las cuales forman parte, desgraciadamente, de nuestro presente actual. Entre los principales elementos de análisis se encuentra la acción de la anglosfera y el sometimiento que experimenta España junto al resto de naciones del orbe europeo, especialmente occidental, bajo instituciones transnacionales como la OTAN o la UE, que lastran permanentemente nuestra soberanía y nos convierten en meros cipayos al servicio de los intereses de la anglosfera (Estados Unidos y Reino Unido) en contra de nuestros propios intereses. El ejemplo más significativo lo tenemos en Ucrania, donde la OTAN está librando una guerra contra Rusia en la que viene utilizando al pueblo ucraniano como ariete de sus intereses geopolíticos a costa de la destrucción del país, en un auténtico drama humano con la muerte de miles de jóvenes en el frente de batalla. La historia de la anglosfera viene siendo la misma desde siempre, en el que sus teóricos aliados vienen siendo humillados, con multitud de traiciones, y ataques de falsa bandera, la creación de grupos terroristas, promoción de golpes de Estado, compra y soborno de políticos con aquellos países que no se sometían a los intereses del Imperio anglosajón. La base de tal poder, en la que tal imperio basa su poder el capitalismo financiero y especulador, cuyas raíces se encuentran en el siglo XVII, y que sirve a unas élites globales que se sirve de los mecanismos tales como los procesos inflacionarios para empobrecer y someter a los pueblos, a los que desprecia e instrumentaliza al servicio de Agendas globalistas. Al mismo tiempo acaparan gran parte de la riqueza global, que mantienen oculta en paraísos fiscales y de la que se sirven para sufragar el tráfico de drogas o la financiación de grupos terroristas que protagonizan los atentados de falsa bandera a los que nos hemos referido. |[](https://amzn.to/2sR7jMM)| |:-:| |[MUTTI, Claudio; _Democracia y talasocracia: Antología de ensayos geopolíticos_; Hipérbola Janus, 2017](https://amzn.to/2sR7jMM)| El enorme y desproporcionado proceso de financiarización que padece la economía del Occidente sometido a la anglosfera ha tenido consecuencias funestas sobre el complejo productivo real, redundando en la desindustrialización y la decadencia general bajo las teorías del «decrecimiento». Desde la administración Bush, a comienzos de siglo, hemos asistido a una serie de guerras de agresión en las que se han destruido países como Irak, Libia o Afganistán con el objetivo de controlar los hidrocarburos y las rutas de transporte, una tendencia que se ha venido incrementado especialmente con la administración Biden , y anteriormente con la de Obama, con la creación de organizaciones terroristas como el ISIS y la desestabilización permanente en Oriente Próximo, y el creciente y peligroso papel del complejo militar industrial. Pero el poder y hegemonía estadounidense están menguando a pasos agigantados con la emergencia de dos grandes potencias, como son Rusia y China, frente a las que la anglosfera ve amenazada su hegemonía económica, con la colonización comercial china y el resurgir del potencial ruso, frente al cual, como decíamos, libran una guerra con intermediarios a través de Ucrania. Al mismo tiempo, tenemos a los BRICS, liderados por Rusia y China, con países emergentes como Irán, la India o Brasil con el papel de potencias regionales. La guerra de Ucrania solamente ha conseguido revigorizar a Rusia, alejarla de Europa y reforzar su alianza con China, mientras que los grandes perjudicados son Ucrania, que quedará en manos de grandes fondos de inversión como Blackrock ante una pretendida reconstrucción del país y las multinacionales que participarán en su reconstrucción, quedando en manos del globalismo. Europa es la otra gran perdedora, empobrecida y sumisa ante los designios del Imperio yanqui, al que rinde pleitesía a través de sus gobernantes, que no son más que títeres. Ante la inevitable pérdida de soberanía en el mundo, la anglosfera también pretende llevar la guerra a Asia contra China, viendo la derrota que está sufriendo en todos los frentes. En el contexto de los intereses hispánicos, la anglosfera siempre ha representado una amenaza y un elemento especialmente dañino, responsable de la disolución del Imperio español con la introducción de las ideas liberales y masónicas entre las élites locales hispanoamericanas, practicando formas aberrantes de neocolonialismo sobre estos territorios una vez independizados, y siendo considerados como el patio trasero de Estados Unidos, quien ha practicado una política especialmente perniciosa y de desestabilización en todos estos territorios en vistas a coartar cualquier forma de desarrollo positivo. Otro de los grandes problemas que se abordan en el libro es la amenaza que representa el enemigo del sur, Marruecos, para la integridad territorial española, sobre Ceuta, Melilla y las Islas Canarias, con el apoyo incondicional de países como Estados Unidos, Francia o Israel, tras las primeras y humillantes concesiones que ya se produjeron en 1975 con **Juan Carlos I** con el Sahara Occidental, y las posteriores, bajo mandato de [**Sánchez**](https://hiperbolajanus.com/firmas/pedro-sanchez/). Al mismo tiempo Estados Unidos e Israel especialmente, participan activamente en el rearme y fortalecimiento del reino moro, que ha desarrollado una política expansionista y agresiva contra los países vecinos. Para ello también se sirve de los lobbies marroquíes que actúan en el propio seno de la UE y dentro de España, que se sirven de las políticas cobardes y traidoras de sus políticos adheridos al Régimen del 78. Las consecuencias no se han dejado de notar en la destrucción y progresivo debilitamiento de nuestro sector primario en detrimento de los productos del país norteafricano, que entran sin ningún tipo de control en nuestro territorio, sin cumplir los requisitos mínimos a nivel fitosanitario. La ineptitud, servilismo y cobardía del actual Régimen hacia poderes globalistas y transnacionales, hacia la anglosfera, nos condenan a seguir un guión sin ninguna autonomía ni poder de decisión. Otro de los ámbitos importantes que contempla el libro, lo encontramos en la ya mencionada Unión Europea, que no deja de ser otro instrumento de dominación y supeditación a los intereses de la anglosfera, y donde se reúnen los representantes de los grandes poderes fácticos a través de plutócratas, banqueros y poderes económicos y financieros transnacionales. Esta institución ha ido sustrayendo progresivamente el poder de las naciones que la integran con una comisión europea con atribuciones y poderes omnímodos para dictar normas y con una presidenta, **Ursula Von der Leyen**, metida en multitud de casos de corrupción, [entre los que destacan aquellos vinculados a la _Plandemia_ de 2020 y las falsas vacunas.](https://hiperbolajanus.com/posts/presentacion-despues-virus-boris-nad/) Todo ello sin contar los protocolos criminales que se impusieron durante ese periodo, la represión policial y el cercenamiento de derechos y libertades con la presión absolutamente criminal sobre los que decidieron no «vacunarse» con el producto experimental del que nadie se hacía responsable y sobre el cual reinaba toda opacidad informativa. Desde esas fechas hasta el presente los fondos de inversión globalistas, como Blackrock o Vanguard entre otros, se sirvieron de la crisis generada para enriquecerse y acaparar la compra de todo lo comprable como instrumento de las élites plutocráticas mundiales y sus ansias de dominio global. |[](https://amzn.to/3U8QydC)| |:-:| |[NAD, Boris; _Después del virus: El renacimiento de un mundo multipolar_; Hipérbola Janus, 2022](https://amzn.to/3U8QydC)| La Unión Europea no ha dejado de ser, como ya hemos dicho, parte de las organizaciones que la anglosfera, y particularmente el gobierno yanqui, ha utilizado para dominarnos y debilitarnos desde 1945, y en nuestros días también a través de la Agenda 2030, a partir de la cual pretenden reducir Europa a la nada, desindustrializando y destruyendo el sector primario, algo especialmente dramático en el caso español. La UE también nos habla de la implantación de la divisa digital con todos los peligros que esta entraña como, por ejemplo, la posibilidad de que se programe su uso y sirva como herramienta de control social para monitorear y controlar nuestras gestiones, la caducidad del dinero o limitar la compra de productos en función de la llamada «huella de carbono». A ello debemos añadir el proceso inflacionario que venimos sufriendo desde el 2020 en una farsa deliberadamente provocada por los bancos centrales (la Reserva Federal y el BCE) con la impresión masiva de dinero. En el plano social la UE no ha dejado de implementar el modelo del caos multicultural que viene ocasionando estragos en buena parte de la Europa occidental a través del uso de recursos maquiavélicos y diferentes ingenierías sociales que se apoyan en los _mass media_. Esto ha generado una distopía social con la introducción de ideas aberrantes como las asociadas a las ideologías de género, con la castración y hormonación de niños o el odio radical y enfermizo hacia los hombres blancos heterosexuales, [convertidos en potenciales violadores con la ideología feminista institucionalizada](https://hiperbolajanus.com/posts/la-naturaleza-femenina-y-los-roles/). Y todo esto con el contraste que supone la llegada masiva de «inmigrantes» de países de África, por ejemplo, donde predominan sociedades patriarcales, en muchos casos musulmanas, cuyas tradiciones y visión de la vida chocan con las ingenierías sociales de la élite globalista. Carlos Blanco y José Costales plantean una refundación de la Unión Europea bajo otros parámetros más democráticos y bajo unos organismos reguladores que puedan controlar los lobbies, las multinacionales y a los plutócratas y frente a los abusos de poder del eje franco-alemán. Una Europa de los pueblos, de naciones soberanas al servicio del interés ciudadano frente a las oligarquías y el gobierno mundial. Otro de los capítulos está dedicado al papel de las oligarquías y las élites, donde reaparecen algunos de los temas ya tratados, y en los que se viene a destacar la acción perniciosa y destructiva de estos poderes anónimos que actúan a través de organizaciones pantalla y agendas planificadas perpetradas desde el llamado Occidente, bajo las premisas de una ideología misántropa y deshumanizada que es asumida por los gobiernos traidores de las naciones de la Europa occidental. Todas estas políticas se presentan bajo aspectos devastadores en el sector alimentario, con la ya referida demolición del sector primario con catastróficas consecuencias en un futuro próximo, o la fabricación de guerras, conflictos sociales y polarización de la población, junto a falsas banderas y grupos terroristas creados y financiados desde el propio Occidente. En este sentido tenemos multitud de ejemplos de desestabilización en torno a la red Gladio durante los años 70 (los famosos años del plomo en Italia) o con el tráfico de drogas, que ha servido para generar conflictividad social en Ecuador en los últimos tiempos tras quedar cortadas las redes del comercio de heroína procedente de Afganistán. En los últimos capítulos del libro también se aborda el separatismo y la balcanización de España, un fenómeno propiamente moderno y que aparece indefectiblemente ligado al advenimiento de los liberales a lo largo del siglo XIX. A raíz de una serie de conflictos de origen dinástico, se generó una antítesis irreconciliable entre dos sistemas de gobierno, el propiamente moderno representado por el liberalismo y encarnado en la futura reina **Isabel II** y el tradicionalismo representado por los carlistas y encarnado, inicialmente, por **Carlos María Isidro** (**Carlos V**). Se libraron tres guerras devastadoras entre liberales y carlistas a lo largo del siglo XIX, en las que se dirimieron dos modelos, uno centralista (liberal) frente a otro descentralizado (carlista) con el respeto a las instituciones locales y regionales, a los Fueros. cuyas prerrogativas y vigencia se fueron perdiendo a lo largo del siglo. El siglo XIX tuvo unas consecuencias desastrosas para España, con la liquidación del Imperio y su debilitamiento en todos los ámbitos. Es a finales de susodicha centuria cuando nacen los movimientos separatistas, especialmente en [Vascongadas](https://hiperbolajanus.com/posts/territorio-caracter-orbe-hispanico-1/#vascongadas-tierra-genuinamente-hisp%C3%A1nica) y [Cataluña](https://hiperbolajanus.com/posts/territorio-caracter-orbe-hispanico-2/#catalu%C3%B1a-el-triunfo-temprano-de-la-burgues%C3%ADa), que irá cristalizando y gestándose a través de un discurso identitario cada vez más radical y antiespañol. [La decadencia política e institucional que representa el actual Régimen Constitucional del 78](https://hiperbolajanus.com/posts/espana-constitucion-idiota/), ha convertido a las formaciones políticas separatistas en los árbitros del sistema, ejerciendo de bisagras en la formación de los gobiernos centrales, con episodios vergonzantes y humillantes como los asociados a la Ley de Amnistía del PSOE en los últimos tiempos. Al mismo tiempo, el separatismo ha asumido los mismos mantras ideológicos a través de sus oligarquías regionales, que el resto de los integrantes del régimen partitocrático en relación a las políticas globalistas impulsadas desde la UE o la siniestra Agenda 2030, a la que son plenamente funcionales. En este sentido el mundo anglosajón, interesado en contribuir a la destrucción interna y fragmentación territorial de España, a través de complejas redes de financiación, como las desplegadas por [**Soros**](https://hiperbolajanus.com/firmas/george-soros/) y su _Open Society_ o las desplegadas, a través de organizaciones pantalla, por los servicios secretos ingleses y estadounidenses. Estos poderes ya tienen experiencia en esta materia, como demuestran los resultados de la Guerra de Yugoslavia durante los años 90, de la que resultó la fragmentación de su territorio en pequeñas repúblicas. ---- --- **Artículo original**: Hipérbola Janus, [_Reseña: «España: Historia de una demolición controlada», de José Costales y Carlos X Blanco_](https://www.hiperbolajanus.com/posts/resena-espana-demolicion-controlada-carlos-blanco/) [**(TOR)**](http://hiperbolam7t46pbl2fiqzaarcmw6injdru4nh2pwuhrkoub3263mpad.onion/posts/resena-espana-demolicion-controlada-carlos-blanco/), 24/Sep/2024
@ bcbb3e40:a494e501
2024-09-24 17:23:00|[](https://amzn.to/4e8iIzx)| |:-:| |[BLANCO, Carlos X. y COSTALES, Jose; _España: Historia de una demolición controlada_; Letras Inquietas, 2024](https://amzn.to/4e8iIzx)| Ya hemos publicado varias reseñas de algunas obras del Profesor [**Carlos X. Blanco**](https://hiperbolajanus.com/firmas/carlos-x.-blanco/), cuyas temáticas nos resultan totalmente familiares, y con las que coincidimos en un buen número de sus análisis y críticas del mundo actual. Recordaremos, para aquellos que estén interesados en sus obras las reseñas de [_De Covadonga a la nación española: La hispanidad en clave spengleriana_](https://hiperbolajanus.com/posts/covadonga-nacion-espanola-carlos-x-blanco/) y [_Un imperio frente al caos_](https://hiperbolajanus.com/posts/resena-un-imperio-frente-al-caos-de/), además de algunas otras que podréis encontrar en nuestro blog. La obra del autor asturiano, en este caso en coautoría con **José Costales**, resulta muy clarificadora a la hora de analizar aspectos generales de la historia de España, cuestiones que tienen que ver con nuestra historia particular, y aquellos hechos que podemos considerar como más generales y fruto de un contexto y unas coyunturas que han marcado el destino de nuestra Patria en los últimos tiempos. Es por ese motivo, que así de entrada podemos distinguir dos bloques claramente diferenciados en esta obra: Un primer bloque que aborda nuestra historia peculiar, las características que definen el «hecho hispánico» y marcan nuestro devenir histórico; un segundo bloque en el que se señalan las amenazas y peligros que se yerguen frente a la España actual, aparentemente agonizante y desahuciada por la falta de soberanía y una serie de problemas graves y trascendentales que amenazan nuestra existencia. Hay que destacar que el prólogo que precede a la obra en sí y le sirve como presentación corre a cargo del conocido abogado, jurista e historiador **Guillermo Rocafort**. En un breve pero certero escrito delinea los grandes problemas que atenazan a un Occidente decadente en plena crisis económica, geopolítica y de valores, embarcado en una deriva suicida que hace aguas y se ha vuelto insostenible. La crisis del capitalismo unipolar y globalista enfrenta el reto de la pujanza de los BRICS, con el resurgimiento de Rusia y el desarrollo y ascenso como superpotencia de China, junto a la formación de grandes bloques geopolíticos que definen la multipolaridad que, recientemente, [autores como Aleksandr Duguin vienen teorizando desde la escuela euroasiática](https://hiperbolajanus.com/libros/geopolitica-rusia-aleksandr-duguin/). Esta situación hace que la el mundo anglosajón y sus oligarquías plutocráticas comiencen a ver resquebrajada su hegemonía, con su sistema de dinero fiat y sus organizaciones pantalla, tales como la Unión Europea, o el desarrollo de su conocida como ideología _woke_ y todas las perversas y destructivas ingenierías sociales asociadas, así como la acción de la Agenda 2030. |[](https://www.amazon.com/dp/B0892V95MV)| |:-:| |[DUGUIN, Aleksandr G.; _La geopolítica de Rusia: De la revolución rusa a Putin_; Hipérbola Janus, 2015](https://www.amazon.com/dp/B0892V95MV)| En el caso particular de España los efectos de los más de 300 años de dominio anglosajón han tenido consecuencias especialmente perniciosas con la desindustrialización, la destrucción del sector primario, las ingenierías sociales asociadas a las ideologías de género, donde España ha servido como particular conejillo de indias, o nuestras permanentes renuncias en materia de política exterior, donde nos hemos visto obligados, por imposiciones venidas del otro lado del Atlántico, a renunciar a nuestra soberanía sobre el Sahara Occidental o a las permanentes y humillantes cesiones a Marruecos. En el escrito de Introducción, los autores trazan una genealogía de los hechos, de las circunstancias que se hallan detrás de las razones del propio título de la obra, «Historia de una demolición controlada», en la que el papel de la angloesfera ha sido fundamental para la situación de debilidad, sometimiento y negación de nuestra propia historia que vivimos en la actualidad. Somos parte de una Europa sojuzgada que actúa a remolque de las políticas estadounidenses y anglosajonas, a través de la acción de la OTAN, donde no somos más que un agregado servil, actuando en defensa de los intereses geopolíticos del Imperio. Dentro de Europa, la UE define otro tipo de jerarquías internas, en las cuales el eje franco-alemán impone sus intereses a los países con economías menos desarrolladas del sur. Al mismo tiempo, también se advierten las importantes transformaciones que el régimen constitucional de 1978 ha experimentado en las últimas décadas, especialmente a partir de [**Zapatero**](https://hiperbolajanus.com/firmas/jose-luis-rodriguez-zapatero/), con el mayor sojuzgamiento de España a la Agenda globalista. Todas estas circunstancias adversas, y también trágicas para nuestro destino, hacen necesario un análisis de la propia historia de España, de su gestación y de los atributos que han cimentado la idea de lo español o hispánico. La historia de España ha estado condicionada por su proximidad a África, lo cual ha tenido una importancia decisiva en su configuración final. Con la invasión musulmana del 711 se produjo un episodio de dislocación dentro de nuestra historia, que a partir de ese momento experimentó una situación de dualidad étnico-religiosa y comenzó un episodio transfigurador y de construcción del ideal hispánico que se había iniciado con el reino visigodo de Toledo, y que la Reconquista contribuyó a potenciar. En este sentido, la configuración étnica que resultó de la invasión árabe hizo que las zonas del Norte, donde se refugiaron los restos de la antigua nobleza visigoda derrotada, predominó el elemento germánico que se erigió como motor inicial del proceso de Reconquista, mientras que en otras latitudes del levante y el sur peninsular se produjo un proceso de africanización y semitización sobre las antiguas poblaciones hispanorromanas. Un norte cristiano, germanizado e indoeuropeo, equiparable al Norte de Europa, representado por la monarquía asturiana frente a un sur africanizado, sumido en un caos étnico y de enfrentamientos civiles era el resultado de la entidad andalusí. El proceso de romanización afectó de manera desigual a los territorios peninsulares, y los pueblos de las regiones noroccidentales como astures, cántabros o vascones apenas se vieron afectados, conservando un importante sustrato indoeuropeo en contraste con las regiones más mediterráneas, ocupadas por los íberos, que ya poseían un modelo de civilización elevado y en conexión con las civilizaciones clásicas mediterráneas. Estos elementos ya aparecen claramente expuestos en la interpretación spengleriana que uno de nuestros autores, Carlos X Blanco, expone en [_De Covadonga a la nación española: La hispanidad en clave spengleriana_](https://amzn.to/3BSOIEX). Es el contraste entre una España atlántica, indoeuropea y germanizada frente a otra vertiente representada por la España mediterránea, levantina y romanizada. En la confluencia de ambos modelos tenemos la definición de las sucesivos siglos en los que se forja la Reconquista, en la que, según los autores, pasamos de una etapa inicial de predominio atlántico y noroccidental, con el Reino de Asturias, y posteriormente León, capitalizando el proceso de la Reconquista, mientras que posteriormente, será Castilla, que obedecerá al modelo mediterráneo, quien llevaría la batuta en el avance hacia el Sur y la hispanización de España, porque la invasión del 711 marca un proceso de deshispanización, una idea fundamental, también en nuestra opinión, que el avance de los reinos cristianos del Norte contribuirán a erosionar y finalmente, para nuestra fortuna, destruir por completo. Como parte de la geopolítica hispánica y su relanzamiento como Patria común, es fundamental que España vuelva a resucitar el eje atlántico y noroccidental, propiamente asturiano, frente aquel castellano, para que recupere su primacía como eje en la reconstrucción de España y revertir así la agonía y rumbo errático que nos lleva hacia la destrucción total y la desaparición como nación histórica. No obstante, si queremos refundar España a través de un verdadero proyecto nacional debemos ser realistas, y no dejarnos embelesar por los visiones sobreexcitados que representan el modelo Imperial de los Austrias o posteriores reverberaciones del mismo a través de construcciones ideales, sino que contemplando las actuales coyunturas, con el viraje hacia la multipolaridad que está experimentando el mundo actual, quizás estaríamos llamados, o al menos existe ese gran potencial, a liderar una suerte de hispanosfera con los antiguos países que fueron parte de la América española, frente a la anglosfera, que viene perjudicando nuestra soberanía y sometiéndonos, junto al resto de Europa, como una colonia. Blanco y Costales nos ofrecen algunas directrices para esta reconstrucción, tales como la descentralización de los centros de poder, frente a todo modelo jacobino y liberal diríamos nosotros, como parte de un modelo confederal, que incluso podría apoyarse en la fundación de centros de poder en el continente americano. Asimismo, este modelo confederal, implicaría dotar de mayor poder y protagonismo a las regiones, [tal y como habría postulado uno de los grandes teóricos del tradicionalismo español, Don](https://hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/) [**Juan Vázquez de Mella**](https://hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/), frente al actual modelo balcanizador de las 17 taifas dirigidas por las oligarquías partitocráticas y corruptas del Régimen de 1978. En cuanto al modelo político requerido, este no es la monarquía, sino la república, por el descrédito de los Borbones y la trayectoria descendente y de decadencia que han venido marcando en su reinado desde hace más de 300 años. En cualquier caso, lo que este modelo debe aportar es cohesión interna y voluntad de integración en el modelo de mundo unipolar, que se viene gestando y estructurando bajo relaciones de poder, redes económicas, comerciales y de otro tipo, que deben garantizar esa capacidad de interconexión. Y, por supuesto, en coherencia con lo sostenido con anterioridad, nuestros autores proponen que el eje atlántico y noroccidental debe representar el motor y artífice de este nuevo ciclo histórico. Desde el advenimiento de los Borbones a comienzos del siglo XVIII, el polo mediterráneo y africanizado ha venido tomando un protagonismo creciente, que vemos reflejado el el triunfo posterior, a lo largo del siglo XIX, del liberalismo con la destrucción del Imperio y el sometimiento de España y de su historia a los dominios de la leyenda negra, urdida por la anglosfera, y que tiende a presentarnos como el producto de una hibridación de pueblos afrosemitas y mahometanos, sin identidad, y como una especie de anomalía frente a la europeidad prototípica. Un discurso que, claro está, fue aceptado por el liberalismo español con la consecuente desvalorización y rechazo de los orígenes astur-godos de la monarquía hispánica y del proceso de Reconquista por parte de unas élites corruptas, antiespañolas y endófobas, que se sometieron ideológicamente a Francia y al mundo anglosajón. En un principio, esto sirvió para provocar fragmentar la unidad interna del Imperio Español y enajenar el catolicismo de la Hispanidad, y posteriormente, una vez destruida esa unidad, someter a estos países al [capitalismo depredador y esclavizarlos por la vía de la deuda](https://hiperbolajanus.com/posts/una-reflexion-sobre-el-capitalismo-y-la/). Paralelamente, y a través de la masonería, también se introdujeron ideas profundamente destructivas entre las élites liberales y traidoras, como son el laicismo, el separatismo y otras ideas disolventes que nos vienen desnaturalizando desde hace siglos. La acción de este capitalismo destructivo y depravado, es la que nos ha convertido en un instrumento en manos de grandes cenáculos y organizaciones que forman parte de un entramado complejo y anónimo, desde donde se interviene permanentemente en nuestros asuntos imponiendo cambios profundos en las costumbres, tradiciones e identidad, empobreciéndonos y reduciéndonos a la más pura insignificancia. Otro elemento a destacar, podríamos decir una de las grandes piedras angulares que definen la idiosincrasia de lo Hispánico, viene representado por el Catolicismo, que en el caso peninsular también revistió un carácter peculiar, especialmente en lo que respecta, una vez más, a los contrastes internos entre la zona atlántica-noroccidental y la mediterránea, así como con la propia realidad del reino visigodo, donde la Iglesia resultó ser muy autónoma, vertebrada a través de sus concilios. Con la irrupción de la contemporaneidad, este elemento, el católico, de vital importancia durante la Reconquista y a lo largo de toda nuestra historia, se ha visto disminuido, con la propia acción del liberalismo, y especialmente [desde la izquierda](https://hiperbolajanus.com/libros/izquierda-contra-pueblo-carlos-x-blanco/), y también desde sus propios centros de poder, desde el mismo Vaticano, a raíz de su famoso Concilio Vaticano II, abdicando en sus principios y doctrina frente al liberalismo y el mundo moderno. En el primer párrafo hemos hablado de un primer bloque, que de algún modo vendría a hablarnos de nuestra historia, de la autorepresentación que tenemos de la misma, y los elementos basales que componen su estructura. Esta sería la primera parte del libro. Una segunda parte vendría comprendida por el análisis de otros elementos más externos que definen unas coyunturas internacionales muy características, las cuales forman parte, desgraciadamente, de nuestro presente actual. Entre los principales elementos de análisis se encuentra la acción de la anglosfera y el sometimiento que experimenta España junto al resto de naciones del orbe europeo, especialmente occidental, bajo instituciones transnacionales como la OTAN o la UE, que lastran permanentemente nuestra soberanía y nos convierten en meros cipayos al servicio de los intereses de la anglosfera (Estados Unidos y Reino Unido) en contra de nuestros propios intereses. El ejemplo más significativo lo tenemos en Ucrania, donde la OTAN está librando una guerra contra Rusia en la que viene utilizando al pueblo ucraniano como ariete de sus intereses geopolíticos a costa de la destrucción del país, en un auténtico drama humano con la muerte de miles de jóvenes en el frente de batalla. La historia de la anglosfera viene siendo la misma desde siempre, en el que sus teóricos aliados vienen siendo humillados, con multitud de traiciones, y ataques de falsa bandera, la creación de grupos terroristas, promoción de golpes de Estado, compra y soborno de políticos con aquellos países que no se sometían a los intereses del Imperio anglosajón. La base de tal poder, en la que tal imperio basa su poder el capitalismo financiero y especulador, cuyas raíces se encuentran en el siglo XVII, y que sirve a unas élites globales que se sirve de los mecanismos tales como los procesos inflacionarios para empobrecer y someter a los pueblos, a los que desprecia e instrumentaliza al servicio de Agendas globalistas. Al mismo tiempo acaparan gran parte de la riqueza global, que mantienen oculta en paraísos fiscales y de la que se sirven para sufragar el tráfico de drogas o la financiación de grupos terroristas que protagonizan los atentados de falsa bandera a los que nos hemos referido. |[](https://amzn.to/2sR7jMM)| |:-:| |[MUTTI, Claudio; _Democracia y talasocracia: Antología de ensayos geopolíticos_; Hipérbola Janus, 2017](https://amzn.to/2sR7jMM)| El enorme y desproporcionado proceso de financiarización que padece la economía del Occidente sometido a la anglosfera ha tenido consecuencias funestas sobre el complejo productivo real, redundando en la desindustrialización y la decadencia general bajo las teorías del «decrecimiento». Desde la administración Bush, a comienzos de siglo, hemos asistido a una serie de guerras de agresión en las que se han destruido países como Irak, Libia o Afganistán con el objetivo de controlar los hidrocarburos y las rutas de transporte, una tendencia que se ha venido incrementado especialmente con la administración Biden , y anteriormente con la de Obama, con la creación de organizaciones terroristas como el ISIS y la desestabilización permanente en Oriente Próximo, y el creciente y peligroso papel del complejo militar industrial. Pero el poder y hegemonía estadounidense están menguando a pasos agigantados con la emergencia de dos grandes potencias, como son Rusia y China, frente a las que la anglosfera ve amenazada su hegemonía económica, con la colonización comercial china y el resurgir del potencial ruso, frente al cual, como decíamos, libran una guerra con intermediarios a través de Ucrania. Al mismo tiempo, tenemos a los BRICS, liderados por Rusia y China, con países emergentes como Irán, la India o Brasil con el papel de potencias regionales. La guerra de Ucrania solamente ha conseguido revigorizar a Rusia, alejarla de Europa y reforzar su alianza con China, mientras que los grandes perjudicados son Ucrania, que quedará en manos de grandes fondos de inversión como Blackrock ante una pretendida reconstrucción del país y las multinacionales que participarán en su reconstrucción, quedando en manos del globalismo. Europa es la otra gran perdedora, empobrecida y sumisa ante los designios del Imperio yanqui, al que rinde pleitesía a través de sus gobernantes, que no son más que títeres. Ante la inevitable pérdida de soberanía en el mundo, la anglosfera también pretende llevar la guerra a Asia contra China, viendo la derrota que está sufriendo en todos los frentes. En el contexto de los intereses hispánicos, la anglosfera siempre ha representado una amenaza y un elemento especialmente dañino, responsable de la disolución del Imperio español con la introducción de las ideas liberales y masónicas entre las élites locales hispanoamericanas, practicando formas aberrantes de neocolonialismo sobre estos territorios una vez independizados, y siendo considerados como el patio trasero de Estados Unidos, quien ha practicado una política especialmente perniciosa y de desestabilización en todos estos territorios en vistas a coartar cualquier forma de desarrollo positivo. Otro de los grandes problemas que se abordan en el libro es la amenaza que representa el enemigo del sur, Marruecos, para la integridad territorial española, sobre Ceuta, Melilla y las Islas Canarias, con el apoyo incondicional de países como Estados Unidos, Francia o Israel, tras las primeras y humillantes concesiones que ya se produjeron en 1975 con **Juan Carlos I** con el Sahara Occidental, y las posteriores, bajo mandato de [**Sánchez**](https://hiperbolajanus.com/firmas/pedro-sanchez/). Al mismo tiempo Estados Unidos e Israel especialmente, participan activamente en el rearme y fortalecimiento del reino moro, que ha desarrollado una política expansionista y agresiva contra los países vecinos. Para ello también se sirve de los lobbies marroquíes que actúan en el propio seno de la UE y dentro de España, que se sirven de las políticas cobardes y traidoras de sus políticos adheridos al Régimen del 78. Las consecuencias no se han dejado de notar en la destrucción y progresivo debilitamiento de nuestro sector primario en detrimento de los productos del país norteafricano, que entran sin ningún tipo de control en nuestro territorio, sin cumplir los requisitos mínimos a nivel fitosanitario. La ineptitud, servilismo y cobardía del actual Régimen hacia poderes globalistas y transnacionales, hacia la anglosfera, nos condenan a seguir un guión sin ninguna autonomía ni poder de decisión. Otro de los ámbitos importantes que contempla el libro, lo encontramos en la ya mencionada Unión Europea, que no deja de ser otro instrumento de dominación y supeditación a los intereses de la anglosfera, y donde se reúnen los representantes de los grandes poderes fácticos a través de plutócratas, banqueros y poderes económicos y financieros transnacionales. Esta institución ha ido sustrayendo progresivamente el poder de las naciones que la integran con una comisión europea con atribuciones y poderes omnímodos para dictar normas y con una presidenta, **Ursula Von der Leyen**, metida en multitud de casos de corrupción, [entre los que destacan aquellos vinculados a la _Plandemia_ de 2020 y las falsas vacunas.](https://hiperbolajanus.com/posts/presentacion-despues-virus-boris-nad/) Todo ello sin contar los protocolos criminales que se impusieron durante ese periodo, la represión policial y el cercenamiento de derechos y libertades con la presión absolutamente criminal sobre los que decidieron no «vacunarse» con el producto experimental del que nadie se hacía responsable y sobre el cual reinaba toda opacidad informativa. Desde esas fechas hasta el presente los fondos de inversión globalistas, como Blackrock o Vanguard entre otros, se sirvieron de la crisis generada para enriquecerse y acaparar la compra de todo lo comprable como instrumento de las élites plutocráticas mundiales y sus ansias de dominio global. |[](https://amzn.to/3U8QydC)| |:-:| |[NAD, Boris; _Después del virus: El renacimiento de un mundo multipolar_; Hipérbola Janus, 2022](https://amzn.to/3U8QydC)| La Unión Europea no ha dejado de ser, como ya hemos dicho, parte de las organizaciones que la anglosfera, y particularmente el gobierno yanqui, ha utilizado para dominarnos y debilitarnos desde 1945, y en nuestros días también a través de la Agenda 2030, a partir de la cual pretenden reducir Europa a la nada, desindustrializando y destruyendo el sector primario, algo especialmente dramático en el caso español. La UE también nos habla de la implantación de la divisa digital con todos los peligros que esta entraña como, por ejemplo, la posibilidad de que se programe su uso y sirva como herramienta de control social para monitorear y controlar nuestras gestiones, la caducidad del dinero o limitar la compra de productos en función de la llamada «huella de carbono». A ello debemos añadir el proceso inflacionario que venimos sufriendo desde el 2020 en una farsa deliberadamente provocada por los bancos centrales (la Reserva Federal y el BCE) con la impresión masiva de dinero. En el plano social la UE no ha dejado de implementar el modelo del caos multicultural que viene ocasionando estragos en buena parte de la Europa occidental a través del uso de recursos maquiavélicos y diferentes ingenierías sociales que se apoyan en los _mass media_. Esto ha generado una distopía social con la introducción de ideas aberrantes como las asociadas a las ideologías de género, con la castración y hormonación de niños o el odio radical y enfermizo hacia los hombres blancos heterosexuales, [convertidos en potenciales violadores con la ideología feminista institucionalizada](https://hiperbolajanus.com/posts/la-naturaleza-femenina-y-los-roles/). Y todo esto con el contraste que supone la llegada masiva de «inmigrantes» de países de África, por ejemplo, donde predominan sociedades patriarcales, en muchos casos musulmanas, cuyas tradiciones y visión de la vida chocan con las ingenierías sociales de la élite globalista. Carlos Blanco y José Costales plantean una refundación de la Unión Europea bajo otros parámetros más democráticos y bajo unos organismos reguladores que puedan controlar los lobbies, las multinacionales y a los plutócratas y frente a los abusos de poder del eje franco-alemán. Una Europa de los pueblos, de naciones soberanas al servicio del interés ciudadano frente a las oligarquías y el gobierno mundial. Otro de los capítulos está dedicado al papel de las oligarquías y las élites, donde reaparecen algunos de los temas ya tratados, y en los que se viene a destacar la acción perniciosa y destructiva de estos poderes anónimos que actúan a través de organizaciones pantalla y agendas planificadas perpetradas desde el llamado Occidente, bajo las premisas de una ideología misántropa y deshumanizada que es asumida por los gobiernos traidores de las naciones de la Europa occidental. Todas estas políticas se presentan bajo aspectos devastadores en el sector alimentario, con la ya referida demolición del sector primario con catastróficas consecuencias en un futuro próximo, o la fabricación de guerras, conflictos sociales y polarización de la población, junto a falsas banderas y grupos terroristas creados y financiados desde el propio Occidente. En este sentido tenemos multitud de ejemplos de desestabilización en torno a la red Gladio durante los años 70 (los famosos años del plomo en Italia) o con el tráfico de drogas, que ha servido para generar conflictividad social en Ecuador en los últimos tiempos tras quedar cortadas las redes del comercio de heroína procedente de Afganistán. En los últimos capítulos del libro también se aborda el separatismo y la balcanización de España, un fenómeno propiamente moderno y que aparece indefectiblemente ligado al advenimiento de los liberales a lo largo del siglo XIX. A raíz de una serie de conflictos de origen dinástico, se generó una antítesis irreconciliable entre dos sistemas de gobierno, el propiamente moderno representado por el liberalismo y encarnado en la futura reina **Isabel II** y el tradicionalismo representado por los carlistas y encarnado, inicialmente, por **Carlos María Isidro** (**Carlos V**). Se libraron tres guerras devastadoras entre liberales y carlistas a lo largo del siglo XIX, en las que se dirimieron dos modelos, uno centralista (liberal) frente a otro descentralizado (carlista) con el respeto a las instituciones locales y regionales, a los Fueros. cuyas prerrogativas y vigencia se fueron perdiendo a lo largo del siglo. El siglo XIX tuvo unas consecuencias desastrosas para España, con la liquidación del Imperio y su debilitamiento en todos los ámbitos. Es a finales de susodicha centuria cuando nacen los movimientos separatistas, especialmente en [Vascongadas](https://hiperbolajanus.com/posts/territorio-caracter-orbe-hispanico-1/#vascongadas-tierra-genuinamente-hisp%C3%A1nica) y [Cataluña](https://hiperbolajanus.com/posts/territorio-caracter-orbe-hispanico-2/#catalu%C3%B1a-el-triunfo-temprano-de-la-burgues%C3%ADa), que irá cristalizando y gestándose a través de un discurso identitario cada vez más radical y antiespañol. [La decadencia política e institucional que representa el actual Régimen Constitucional del 78](https://hiperbolajanus.com/posts/espana-constitucion-idiota/), ha convertido a las formaciones políticas separatistas en los árbitros del sistema, ejerciendo de bisagras en la formación de los gobiernos centrales, con episodios vergonzantes y humillantes como los asociados a la Ley de Amnistía del PSOE en los últimos tiempos. Al mismo tiempo, el separatismo ha asumido los mismos mantras ideológicos a través de sus oligarquías regionales, que el resto de los integrantes del régimen partitocrático en relación a las políticas globalistas impulsadas desde la UE o la siniestra Agenda 2030, a la que son plenamente funcionales. En este sentido el mundo anglosajón, interesado en contribuir a la destrucción interna y fragmentación territorial de España, a través de complejas redes de financiación, como las desplegadas por [**Soros**](https://hiperbolajanus.com/firmas/george-soros/) y su _Open Society_ o las desplegadas, a través de organizaciones pantalla, por los servicios secretos ingleses y estadounidenses. Estos poderes ya tienen experiencia en esta materia, como demuestran los resultados de la Guerra de Yugoslavia durante los años 90, de la que resultó la fragmentación de su territorio en pequeñas repúblicas. ---- --- **Artículo original**: Hipérbola Janus, [_Reseña: «España: Historia de una demolición controlada», de José Costales y Carlos X Blanco_](https://www.hiperbolajanus.com/posts/resena-espana-demolicion-controlada-carlos-blanco/) [**(TOR)**](http://hiperbolam7t46pbl2fiqzaarcmw6injdru4nh2pwuhrkoub3263mpad.onion/posts/resena-espana-demolicion-controlada-carlos-blanco/), 24/Sep/2024 @ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous. In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism. On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important. That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played. Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end. The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism: I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is. In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore. The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true. The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good. In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.” I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous. In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism. On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important. That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played. Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end. The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism: I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is. In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore. The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true. The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good. In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.” I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it. @ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint. I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point. I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog. In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout. Are there any odds you're excited about (doesn't have to be football)? originally posted at https://stacker.news/items/679894
@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint. I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point. I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog. In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout. Are there any odds you're excited about (doesn't have to be football)? originally posted at https://stacker.news/items/679894 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。 通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。 --- 2024年08月13日更新: > 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。 为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。 --- ### 准备工具 - Ntfy服务 - Google Script - Google Sheets ### 操作步骤 1. 在Ntfy后台账号,设置访问令牌。 [](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌") 2. 添加订阅主题。 [](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题") 2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图: [](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id") 3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌): ```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet(); // 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据 var sentEmails = getSentEmails(sheet); var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length); if (threads.length === 0) return; threads.forEach(function(thread) { var threadId = thread.getId(); if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); } }); } function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; } var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"} 内容: ${email.getPlainBody() || "无内容"}`; var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true }; try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } } function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column } function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); } function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间 var data = sheet.getDataRange().getValues(); var rowsToDelete = []; data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } }); // 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); } ``` 4.Goole Script需要添加gmail服务,如图: [](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务") 5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图: [](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器") [](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细") ### 结尾 本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。 如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。 效果预览: [](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览")
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。 通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。 --- 2024年08月13日更新: > 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。 为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。 --- ### 准备工具 - Ntfy服务 - Google Script - Google Sheets ### 操作步骤 1. 在Ntfy后台账号,设置访问令牌。 [](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌") 2. 添加订阅主题。 [](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题") 2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图: [](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id") 3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌): ```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet(); // 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据 var sentEmails = getSentEmails(sheet); var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length); if (threads.length === 0) return; threads.forEach(function(thread) { var threadId = thread.getId(); if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); } }); } function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; } var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"} 内容: ${email.getPlainBody() || "无内容"}`; var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true }; try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } } function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column } function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); } function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间 var data = sheet.getDataRange().getValues(); var rowsToDelete = []; data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } }); // 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); } ``` 4.Goole Script需要添加gmail服务,如图: [](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务") 5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图: [](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器") [](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细") ### 结尾 本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。 如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。 效果预览: [](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览") @ 6ad3e2a3:c90b7740
2024-09-10 08:37:04While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions: **1. Separate passengers from their bags as early as possible.** The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences: a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes. b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day. c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five. d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier. e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable. The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children. To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc. There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.) Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane. **2. Eliminate Security Lines** Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement. a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use. Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious. b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side. Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side. **3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.** Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal. **4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.** There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done. Here are some other suggestions: 1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up. 2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges. 3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease. 4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them. I can anticipate some objections to these ideas, and I’ll address each one in turn. **1. This would cost too much money.** My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.) **2. It’s too much of a security risk.** Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end. Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle. **3. I like free carry-ons because it saves me from waiting at the baggage claim.** Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse. The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist. *\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.* *\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.*
@ 6ad3e2a3:c90b7740
2024-09-10 08:37:04While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions: **1. Separate passengers from their bags as early as possible.** The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences: a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes. b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day. c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five. d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier. e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable. The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children. To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc. There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.) Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane. **2. Eliminate Security Lines** Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement. a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use. Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious. b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side. Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side. **3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.** Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal. **4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.** There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done. Here are some other suggestions: 1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up. 2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges. 3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease. 4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them. I can anticipate some objections to these ideas, and I’ll address each one in turn. **1. This would cost too much money.** My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.) **2. It’s too much of a security risk.** Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end. Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle. **3. I like free carry-ons because it saves me from waiting at the baggage claim.** Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse. The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist. *\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.* *\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.* @ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed. @ 6bae33c8:607272e8
2024-09-10 07:50:12I went 1-3 in my NFFC leagues for two reasons: (1) Christian McCaffrey failed to score 17 points (because he was inactive), and I failed to bid enough on Jordan Mason because at the time of the FAAB last week, the Niners were flat-out lying about his likelihood of playing and like an idiot I believed them; and (2) I sat Mason in another league at the last minute for Jaleel McLaughlin because Fantasy Pros (that scourge of a site I swear off every year) had Mason not just lower, but absolutely buried in its RB rankings. I would have ignored a close call between the two, but I thought if he’s this low, the market must place a high likelihood on McCaffrey playing, and I don’t want to take a zero. This is the problem with being lazy and outsourcing your research to a bunch of midwits with misaligned incentives. I really should have delved deeply into all the McCaffrey reports and made my own assessment. The problem with sites like Fantasy Pros is the grading system is different than the fantasy game itself. I imagine you’d get dinged hard for ranking Mason high if McCaffrey plays, and so it’s safer to rank him low. Moreover, one thing the fantasy industry is really bad at is pricing in that kind of risk. If everyone’s playing the market is pretty good at evaluating opportunity, per-play production and hence output, but if someone is 50/50 to get opportunities at all, they can’t handle it very well. Obviously Mason was a good bet to go for 20 points if McCaffrey were scratched, and so he should have been projected for 14 if it were 50/50 (he’d get *some* points even if McCaffrey played), but that we was projected for less than five (IIRC) made me think it was like 80/20. But I knew it was a *very* bad sign Monday morning (after it was too late to pivot) when McCaffrey was still not deemed definite — it’s not like he got hurt last week, but he’s had a full month to heal. (Actually maybe the Achilles was last week, but because injury reporting sucks and teams lie, it’s impossible to know the real reason he missed the game. If it’s still the calf, all bets are off because if he’s not back in a month, five weeks won’t magically heal him.) In any event, I’m glad I have Mason in two NFFC leagues, and I went all-in to get him (and I used him) in my RotoWire Dynasty one at least. But I should have been 3-1 if I had used my brain, and am instead 1-3, the win thankfully in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7). - The 40-minute edited version of the game for God knows what reason flashed the final score (32-19) briefly after I hit play. So it spoiled the game for me, and the whole time I was just trying to figure out how they got to that number, realizing probably Jake Moody went bananas for some people, and he did. - I love that Allen Lazard got the TDs and not Garrett Wilson. Sometimes schadenfreude is all you got. I don’t think Lazard is a priority pickup, but the Jets tree is pretty thin, and Rodgers knows and apparently still trusts him. - Aaron Rodgers looked good to me, like his old self. He threw accurate passes, had a few drops, and the pick was bad luck. No idea why Mike Williams was ignored though. - Breece Hall got all the work until garbage time. No surprise, but he still looks like a top-five pick despite the fumble and poor per-play output. - Jordan Mason ran hard, looked a bit like Isiah Pacheco out there. If McCaffrey is out, that’s how I’d value him. - Deebo Samuel benefits a little (eight carries) with McCaffrey out. Just has a slightly bigger role in the ground game. - Brock Purdy played well, but didn’t have to do much. - You have to love that Juaun Jennings led the 49ers in receiving yards and Kyle Juszczyk was third when you have no part of the 49ers passing game. George Kittle and Brandon Aiyuk will get theirs eventually, but you just can’t count on volume for either one.
@ 6bae33c8:607272e8
2024-09-10 07:50:12I went 1-3 in my NFFC leagues for two reasons: (1) Christian McCaffrey failed to score 17 points (because he was inactive), and I failed to bid enough on Jordan Mason because at the time of the FAAB last week, the Niners were flat-out lying about his likelihood of playing and like an idiot I believed them; and (2) I sat Mason in another league at the last minute for Jaleel McLaughlin because Fantasy Pros (that scourge of a site I swear off every year) had Mason not just lower, but absolutely buried in its RB rankings. I would have ignored a close call between the two, but I thought if he’s this low, the market must place a high likelihood on McCaffrey playing, and I don’t want to take a zero. This is the problem with being lazy and outsourcing your research to a bunch of midwits with misaligned incentives. I really should have delved deeply into all the McCaffrey reports and made my own assessment. The problem with sites like Fantasy Pros is the grading system is different than the fantasy game itself. I imagine you’d get dinged hard for ranking Mason high if McCaffrey plays, and so it’s safer to rank him low. Moreover, one thing the fantasy industry is really bad at is pricing in that kind of risk. If everyone’s playing the market is pretty good at evaluating opportunity, per-play production and hence output, but if someone is 50/50 to get opportunities at all, they can’t handle it very well. Obviously Mason was a good bet to go for 20 points if McCaffrey were scratched, and so he should have been projected for 14 if it were 50/50 (he’d get *some* points even if McCaffrey played), but that we was projected for less than five (IIRC) made me think it was like 80/20. But I knew it was a *very* bad sign Monday morning (after it was too late to pivot) when McCaffrey was still not deemed definite — it’s not like he got hurt last week, but he’s had a full month to heal. (Actually maybe the Achilles was last week, but because injury reporting sucks and teams lie, it’s impossible to know the real reason he missed the game. If it’s still the calf, all bets are off because if he’s not back in a month, five weeks won’t magically heal him.) In any event, I’m glad I have Mason in two NFFC leagues, and I went all-in to get him (and I used him) in my RotoWire Dynasty one at least. But I should have been 3-1 if I had used my brain, and am instead 1-3, the win thankfully in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7). - The 40-minute edited version of the game for God knows what reason flashed the final score (32-19) briefly after I hit play. So it spoiled the game for me, and the whole time I was just trying to figure out how they got to that number, realizing probably Jake Moody went bananas for some people, and he did. - I love that Allen Lazard got the TDs and not Garrett Wilson. Sometimes schadenfreude is all you got. I don’t think Lazard is a priority pickup, but the Jets tree is pretty thin, and Rodgers knows and apparently still trusts him. - Aaron Rodgers looked good to me, like his old self. He threw accurate passes, had a few drops, and the pick was bad luck. No idea why Mike Williams was ignored though. - Breece Hall got all the work until garbage time. No surprise, but he still looks like a top-five pick despite the fumble and poor per-play output. - Jordan Mason ran hard, looked a bit like Isiah Pacheco out there. If McCaffrey is out, that’s how I’d value him. - Deebo Samuel benefits a little (eight carries) with McCaffrey out. Just has a slightly bigger role in the ground game. - Brock Purdy played well, but didn’t have to do much. - You have to love that Juaun Jennings led the 49ers in receiving yards and Kyle Juszczyk was third when you have no part of the 49ers passing game. George Kittle and Brandon Aiyuk will get theirs eventually, but you just can’t count on volume for either one. @ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
@ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg @ 129f5189:3a441803
2024-09-09 23:23:45Project 2025, outlined in the "Mandate for Leadership" document by the Heritage Foundation, is a crucial guide for the next Republican administration. Crafted by conservative intellectuals from major American think tanks, this plan promises to have significant influence on a potential Donald Trump administration, even if he does not formally acknowledge it as his government plan. https://image.nostr.build/443d69c16dc32659be2353ce48d170d397e0ee682ffc3c4108df3047fd54472d.jpg This document presents proposals to depoliticize government agencies, increase efficiency, and reduce costs, aiming to dismantle the Deep State and combat the Woke agenda associated with the Democratic Party. https://image.nostr.build/06de3f0de3d48e086f47d0418d30e32cbfe0d88f452a93706987b7394458952d.jpg Dissolution of the DHS and Redistribution of Functions The Department of Homeland Security (DHS) was established in 2002 in response to the September 11 attacks, with the goal of consolidating various agencies responsible for domestic security under a single command. The DHS includes agencies such as FEMA, TSA, ICE, and CISA. Project 2025's proposal to dissolve the DHS and redistribute its functions to other agencies aims to address excessive bureaucracy and a lack of cohesion, arguing that centralization has failed to effectively integrate its diverse missions. https://image.nostr.build/ffca8d274914b725183b8fb19162c1b63f4d987c24e598f2eca88901d4a1a43c.jpg Impact on the Democratic Deep State: The dissolution of the DHS would pose a significant threat to the Democratic Deep State, as it would redistribute the power concentrated in a single entity across multiple other agencies, making it more difficult to politicize and centralize control over domestic security operations. This decentralization would reduce the ability to use the DHS as a political tool against opponents. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Primary Recommendations Combining Immigration Agencies: Merge U.S. Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), U.S. Citizenship and Immigration Services (USCIS), the Office of Refugee Resettlement (ORR) of the Department of Health and Human Services (HHS), and the Executive Office for Immigration Review (EOIR) of the Department of Justice (DOJ) into a new autonomous border and immigration agency. https://image.nostr.build/58eef4f2eca0ed2400261ec878c1dba2ca4bca519a16751b1fb7abd45da2906b.jpg Privatization of the TSA: Privatize the Transportation Security Administration (TSA), drawing inspiration from Canadian and European models, to reduce costs and improve service for travelers. Division of the Secret Service (USSS): The U.S. Secret Service (USSS), responsible for protecting national leaders and investigating financial crimes, would be divided. The protective element would be transferred to the Department of Justice (DOJ), while the financial investigations element would be moved to the Department of the Treasury. https://image.nostr.build/0a065cdbf158db4bc17b9aacd4af5a94029004caaa152eebf2c557042b08a641.jpg Impact on the Democratic Deep State: The division of the USSS would significantly weaken centralized control over protection and financial investigations, making it more difficult to use these functions for political purposes. Transferring the protective element to the DOJ and the financial investigations element to the Treasury would complicate efforts for any group or party to manipulate these crucial government functions for partisan objectives. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Cybersecurity and Infrastructure Security Agency (CISA) Established in 2018, CISA is a federal agency responsible for protecting the U.S. critical infrastructure from cyber threats. CISA's mandate includes ensuring cybersecurity for sectors such as energy, transportation, and healthcare, and it collaborates with public and private entities to strengthen the country’s cyber resilience. Criticisms and Restructuring Proposals: Project 2025 strongly criticizes CISA for deviating from its original mission and being used as a political tool for censoring speech and influencing elections. The proposal is to transfer CISA to the Department of Transportation (DOT) and return the agency to its statutory focus. https://image.nostr.build/8bfb4a45053de96a775f67e3e1b83a44d9a65fee4705e3b16d3359bd799b8af2.jpg Review of Executive Order 12333 Executive Order 12333, issued in 1981, sets guidelines for U.S. intelligence activities, including the collection, analysis, and dissemination of information. Project 2025 proposes a review of this order to ensure that intelligence agencies are not used for political purposes but are focused on protecting national security. Objectives of the Review: Prevent Abuse: Ensure that intelligence collection is conducted legally, without being used to target political opponents. Ensure Impartiality: Reaffirm that intelligence operations must be conducted impartially, with a sole focus on the country's security. https://image.nostr.build/90d31cb35a33048d311716df2fbc65c97bd4c1972977e266133654404393fca0.jpg Reforms in Public Service Facilitation of Public Employee Dismissal: Project 2025 emphasizes the need to simplify the process for dismissing public employees who do not perform their duties impartially or who promote specific political agendas. Performance Evaluations: The document highlights the importance of merit-based compensation, stating that performance evaluations are only effective when tied to real consequences. Research indicates that 90% of major private companies in the U.S. use a merit-based pay system linked to evaluations. However, in the federal government, compensation remains largely based on seniority, despite efforts to adopt merit-based pay. https://image.nostr.build/1b858fd7b2a23c3c65c0677d3e69c44976721bbdcbe7facf4682ba3371562cff.jpg Inclusion of Employees Aligned with Conservative Values: Aligned Hiring: Establish mechanisms to hire public employees who share conservative values, ensuring that the policies and practices of agencies are consistent with the principles endorsed by the administration. https://image.nostr.build/ddbf5c59e7bb479998433991347f9d301dd117fbca0edb0f94e98fcac90b2974.jpg Controversial Cases and Politicization: Hunter Biden Laptop Case: Project 2025 harshly criticizes the FBI and the Department of Justice, accusing them of acting in a biased and politically motivated manner. The authors suggest that the agency is intimidating parents who protest by labeling them as "domestic terrorists," while simultaneously suppressing politically unfavorable speech under the guise of combating "disinformation." Furthermore, the critique highlights that the FBI is alleged to be neglecting violent attacks on pregnancy centers and violations of laws prohibiting attempts to intimidate Supreme Court justices. The criticism intensifies with allegations that the FBI interfered in domestic elections and engaged in propaganda operations, specifically citing the purported Russian collusion conspiracy in 2016 and the suppression of the Hunter Biden laptop case in 2020, which is seen as a threat to the Republic. https://image.nostr.build/e4f571a14102a939164465498bef514379ec0443e71a58e12f50c518e00570c6.jpg Politicization of the FBI: Election Interference: Russia Hoax and Trump, Suppression of Hunter Biden’s Laptop, and Big Tech Collusion. Revelations about the FBI’s role in the 2016 "Russia Hoax" and the suppression of Hunter Biden’s laptop in 2020 suggest that the agency may have strayed from its impartial duties. These actions indicate concerning politicization, where the agency appears to have been used to influence the political landscape in favor of certain interests. This includes collaboration between the FBI and Big Tech companies to control discourse. https://image.nostr.build/5dcd45fcec939b782d29d8d2e3d3b45244c525b5dbd3240f1629a4632e390a86.jpg Comprehensive Review of FBI Investigations: It is crucial to conduct an immediate and thorough review of all significant investigations and activities within the FBI, terminating those that are illegal or contrary to national interests. This step is essential for restoring public trust in the FBI. A public report on the findings of this review could enhance transparency and confidence. https://image.nostr.build/df98e2c6aff123d806187eab13d24a3ebb30a87df1f44cf57be97dc5624fff88.jpg Structural Reorganization: Align the FBI within the Department of Justice (DOJ) according to its purposes of national security and law enforcement. The agency should be under the supervision of the Assistant Attorney General for the Criminal Division and the National Security Division, ensuring that the FBI does not operate as an independent entity but is instead subordinated to the DOJ’s directives. https://image.nostr.build/0d1c0015c6b67a8afc2dd1595357ea571fcd5a9d83829065f49f9b60cf553eb0.jpg Prohibition on Policing Speech: Prohibit the FBI from engaging in activities related to combating "disinformation" or "misinformation" disseminated by Americans who are not linked to plausible criminal activities. The Constitution, through the First Amendment, prohibits the government from policing speech, ensuring a healthy public debate without governmental intervention. All these measures represent a significant attack on the "Deep State" within American institutions. These public policies have been considered a dictatorial threat by many sectors of the American press. However, the real issue should be the politicization of unelected bureaucrats by a political faction. https://image.nostr.build/9a44b19d15d53314f89528c1d89e2f637030ea18d8907a6a8c4e27d07064b8ec.jpg Combating Woke Culture in the Intelligence Community Future leadership of the Intelligence Community (IC) needs to implement a plan to replace the "woke" culture and identity politics that have spread throughout the federal government. The goal is to restore traditional American values such as patriotism, racial impartiality, and job competence, which have been replaced by advocacy for "social justice" and identity politics. https://image.nostr.build/7929dca5e36273c8e751f36d6ca6229f362e30792bce735f10be7e5d8581af5f.jpg Final Considerations The Heritage Foundation’s Project 2025 is not merely an administrative reform plan; it is a manifesto of resistance against the Washington status quo. The proposals aim to dismantle established power structures, eliminate politicization, and combat the Woke agenda. If implemented, this plan would profoundly impact how the U.S. government operates, promoting a more efficient, limited government aligned with conservative principles. Threat to the Democratic Deep State: A potential new administration under Donald Trump represents an existential threat to the Democratic Deep State entrenched in American institutions. The dissolution of the DHS, depoliticization of intelligence agencies, division of the Secret Service, review of Executive Order 12333, privatization of the TSA, and the hiring of employees aligned with conservative values are all measures that would significantly weaken centralized control and the ability to use these institutions for political purposes. By dismantling concentrated power and promoting a more transparent and accountable government, Project 2025 aims to restore public trust and ensure that government agencies serve national interests rather than partisan ones. Of course, not all aspects of the plan may be implemented, but the prospect of several of these measures being enacted should be a cause for concern for the Democratic Deep State.
@ 129f5189:3a441803
2024-09-09 23:23:45Project 2025, outlined in the "Mandate for Leadership" document by the Heritage Foundation, is a crucial guide for the next Republican administration. Crafted by conservative intellectuals from major American think tanks, this plan promises to have significant influence on a potential Donald Trump administration, even if he does not formally acknowledge it as his government plan. https://image.nostr.build/443d69c16dc32659be2353ce48d170d397e0ee682ffc3c4108df3047fd54472d.jpg This document presents proposals to depoliticize government agencies, increase efficiency, and reduce costs, aiming to dismantle the Deep State and combat the Woke agenda associated with the Democratic Party. https://image.nostr.build/06de3f0de3d48e086f47d0418d30e32cbfe0d88f452a93706987b7394458952d.jpg Dissolution of the DHS and Redistribution of Functions The Department of Homeland Security (DHS) was established in 2002 in response to the September 11 attacks, with the goal of consolidating various agencies responsible for domestic security under a single command. The DHS includes agencies such as FEMA, TSA, ICE, and CISA. Project 2025's proposal to dissolve the DHS and redistribute its functions to other agencies aims to address excessive bureaucracy and a lack of cohesion, arguing that centralization has failed to effectively integrate its diverse missions. https://image.nostr.build/ffca8d274914b725183b8fb19162c1b63f4d987c24e598f2eca88901d4a1a43c.jpg Impact on the Democratic Deep State: The dissolution of the DHS would pose a significant threat to the Democratic Deep State, as it would redistribute the power concentrated in a single entity across multiple other agencies, making it more difficult to politicize and centralize control over domestic security operations. This decentralization would reduce the ability to use the DHS as a political tool against opponents. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Primary Recommendations Combining Immigration Agencies: Merge U.S. Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), U.S. Citizenship and Immigration Services (USCIS), the Office of Refugee Resettlement (ORR) of the Department of Health and Human Services (HHS), and the Executive Office for Immigration Review (EOIR) of the Department of Justice (DOJ) into a new autonomous border and immigration agency. https://image.nostr.build/58eef4f2eca0ed2400261ec878c1dba2ca4bca519a16751b1fb7abd45da2906b.jpg Privatization of the TSA: Privatize the Transportation Security Administration (TSA), drawing inspiration from Canadian and European models, to reduce costs and improve service for travelers. Division of the Secret Service (USSS): The U.S. Secret Service (USSS), responsible for protecting national leaders and investigating financial crimes, would be divided. The protective element would be transferred to the Department of Justice (DOJ), while the financial investigations element would be moved to the Department of the Treasury. https://image.nostr.build/0a065cdbf158db4bc17b9aacd4af5a94029004caaa152eebf2c557042b08a641.jpg Impact on the Democratic Deep State: The division of the USSS would significantly weaken centralized control over protection and financial investigations, making it more difficult to use these functions for political purposes. Transferring the protective element to the DOJ and the financial investigations element to the Treasury would complicate efforts for any group or party to manipulate these crucial government functions for partisan objectives. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Cybersecurity and Infrastructure Security Agency (CISA) Established in 2018, CISA is a federal agency responsible for protecting the U.S. critical infrastructure from cyber threats. CISA's mandate includes ensuring cybersecurity for sectors such as energy, transportation, and healthcare, and it collaborates with public and private entities to strengthen the country’s cyber resilience. Criticisms and Restructuring Proposals: Project 2025 strongly criticizes CISA for deviating from its original mission and being used as a political tool for censoring speech and influencing elections. The proposal is to transfer CISA to the Department of Transportation (DOT) and return the agency to its statutory focus. https://image.nostr.build/8bfb4a45053de96a775f67e3e1b83a44d9a65fee4705e3b16d3359bd799b8af2.jpg Review of Executive Order 12333 Executive Order 12333, issued in 1981, sets guidelines for U.S. intelligence activities, including the collection, analysis, and dissemination of information. Project 2025 proposes a review of this order to ensure that intelligence agencies are not used for political purposes but are focused on protecting national security. Objectives of the Review: Prevent Abuse: Ensure that intelligence collection is conducted legally, without being used to target political opponents. Ensure Impartiality: Reaffirm that intelligence operations must be conducted impartially, with a sole focus on the country's security. https://image.nostr.build/90d31cb35a33048d311716df2fbc65c97bd4c1972977e266133654404393fca0.jpg Reforms in Public Service Facilitation of Public Employee Dismissal: Project 2025 emphasizes the need to simplify the process for dismissing public employees who do not perform their duties impartially or who promote specific political agendas. Performance Evaluations: The document highlights the importance of merit-based compensation, stating that performance evaluations are only effective when tied to real consequences. Research indicates that 90% of major private companies in the U.S. use a merit-based pay system linked to evaluations. However, in the federal government, compensation remains largely based on seniority, despite efforts to adopt merit-based pay. https://image.nostr.build/1b858fd7b2a23c3c65c0677d3e69c44976721bbdcbe7facf4682ba3371562cff.jpg Inclusion of Employees Aligned with Conservative Values: Aligned Hiring: Establish mechanisms to hire public employees who share conservative values, ensuring that the policies and practices of agencies are consistent with the principles endorsed by the administration. https://image.nostr.build/ddbf5c59e7bb479998433991347f9d301dd117fbca0edb0f94e98fcac90b2974.jpg Controversial Cases and Politicization: Hunter Biden Laptop Case: Project 2025 harshly criticizes the FBI and the Department of Justice, accusing them of acting in a biased and politically motivated manner. The authors suggest that the agency is intimidating parents who protest by labeling them as "domestic terrorists," while simultaneously suppressing politically unfavorable speech under the guise of combating "disinformation." Furthermore, the critique highlights that the FBI is alleged to be neglecting violent attacks on pregnancy centers and violations of laws prohibiting attempts to intimidate Supreme Court justices. The criticism intensifies with allegations that the FBI interfered in domestic elections and engaged in propaganda operations, specifically citing the purported Russian collusion conspiracy in 2016 and the suppression of the Hunter Biden laptop case in 2020, which is seen as a threat to the Republic. https://image.nostr.build/e4f571a14102a939164465498bef514379ec0443e71a58e12f50c518e00570c6.jpg Politicization of the FBI: Election Interference: Russia Hoax and Trump, Suppression of Hunter Biden’s Laptop, and Big Tech Collusion. Revelations about the FBI’s role in the 2016 "Russia Hoax" and the suppression of Hunter Biden’s laptop in 2020 suggest that the agency may have strayed from its impartial duties. These actions indicate concerning politicization, where the agency appears to have been used to influence the political landscape in favor of certain interests. This includes collaboration between the FBI and Big Tech companies to control discourse. https://image.nostr.build/5dcd45fcec939b782d29d8d2e3d3b45244c525b5dbd3240f1629a4632e390a86.jpg Comprehensive Review of FBI Investigations: It is crucial to conduct an immediate and thorough review of all significant investigations and activities within the FBI, terminating those that are illegal or contrary to national interests. This step is essential for restoring public trust in the FBI. A public report on the findings of this review could enhance transparency and confidence. https://image.nostr.build/df98e2c6aff123d806187eab13d24a3ebb30a87df1f44cf57be97dc5624fff88.jpg Structural Reorganization: Align the FBI within the Department of Justice (DOJ) according to its purposes of national security and law enforcement. The agency should be under the supervision of the Assistant Attorney General for the Criminal Division and the National Security Division, ensuring that the FBI does not operate as an independent entity but is instead subordinated to the DOJ’s directives. https://image.nostr.build/0d1c0015c6b67a8afc2dd1595357ea571fcd5a9d83829065f49f9b60cf553eb0.jpg Prohibition on Policing Speech: Prohibit the FBI from engaging in activities related to combating "disinformation" or "misinformation" disseminated by Americans who are not linked to plausible criminal activities. The Constitution, through the First Amendment, prohibits the government from policing speech, ensuring a healthy public debate without governmental intervention. All these measures represent a significant attack on the "Deep State" within American institutions. These public policies have been considered a dictatorial threat by many sectors of the American press. However, the real issue should be the politicization of unelected bureaucrats by a political faction. https://image.nostr.build/9a44b19d15d53314f89528c1d89e2f637030ea18d8907a6a8c4e27d07064b8ec.jpg Combating Woke Culture in the Intelligence Community Future leadership of the Intelligence Community (IC) needs to implement a plan to replace the "woke" culture and identity politics that have spread throughout the federal government. The goal is to restore traditional American values such as patriotism, racial impartiality, and job competence, which have been replaced by advocacy for "social justice" and identity politics. https://image.nostr.build/7929dca5e36273c8e751f36d6ca6229f362e30792bce735f10be7e5d8581af5f.jpg Final Considerations The Heritage Foundation’s Project 2025 is not merely an administrative reform plan; it is a manifesto of resistance against the Washington status quo. The proposals aim to dismantle established power structures, eliminate politicization, and combat the Woke agenda. If implemented, this plan would profoundly impact how the U.S. government operates, promoting a more efficient, limited government aligned with conservative principles. Threat to the Democratic Deep State: A potential new administration under Donald Trump represents an existential threat to the Democratic Deep State entrenched in American institutions. The dissolution of the DHS, depoliticization of intelligence agencies, division of the Secret Service, review of Executive Order 12333, privatization of the TSA, and the hiring of employees aligned with conservative values are all measures that would significantly weaken centralized control and the ability to use these institutions for political purposes. By dismantling concentrated power and promoting a more transparent and accountable government, Project 2025 aims to restore public trust and ensure that government agencies serve national interests rather than partisan ones. Of course, not all aspects of the plan may be implemented, but the prospect of several of these measures being enacted should be a cause for concern for the Democratic Deep State. @ 129f5189:3a441803
2024-09-09 23:11:19Precious metals have served as monetary backing for millennia, but this does not guarantee that gold is a safe investment or a good hedge against economic crises and monetary collapses. Since its last major rally in the 1980s, gold has been progressively demonetized. Those who acquired gold in the late 1980s will need to rely on a significant increase in demand or a supply shock for its price to rise by 561% and regain the purchasing power it had 40 years ago. https://image.nostr.build/dd5fec2b474ea34cd72ddf5781393b528e63a358d523c9428f3ba4649f4f42aa.jpg If you look at the purchasing power of $1 (green line), you'll see that the depreciation is even faster. This might create the impression that gold is a good store of value. But does the fact that something loses value more slowly amidst a general decline really make it a store of value? Unless the total demand for gold increases at the same rate as its supply has grown in recent years, the purchasing power of the metal is likely to decline. https://image.nostr.build/9f24f6cf37780fe851746057520064ed94acd96547be53bd341c9e15b8762773.jpg In other words, if you own an ounce of gold, that ounce will represent an increasingly smaller fraction of the total gold reserves, meaning you are being diluted. Additionally, one should also consider the cost and risk of storage, but that's another issue. If you don't want to compare the purchasing power of gold today with the 1980s, you can consider its value from 9 years ago. Between September 2011 and November 2015, the Fed printed approximately $2.8 trillion. This also provides a perspective on gold's depreciation relative to the significant monetary expansion during that period. https://image.nostr.build/822e0a861e16ca258e0427875a84b5c8e5420e51bcf65674b453b55ed78edefd.jpg In other words, the Fed expanded its monetary base by about 30% during that 4-year period. However, the price of an ounce of gold fell by 45% (from $1,900 to $1,057) over the same interval. A true store of value should protect against excessive money printing. In contrast, during that same period, Bitcoin appreciated by 8,500% (from $5 to $419). https://image.nostr.build/32a7ca39a6e69e2780f9ab49390c7b7380499fcfe54ae4ef693e6fc91686a41e.jpg Indeed, while it is interesting to note that this was the exact period when gold derivatives were launched on CME Group, it's important to remember that correlation does not imply causation. Many factors can influence the price of gold and Bitcoin, and establishing a direct causal relationship requires more detailed analysis. https://derivsource.com/2011/06/21/cme-group-announces-the-launch-of-three-new-short-term-gold-crude-oil-and-natural-gas-options-contracts/ In an asset where supply can only be physically verified, flooding the market with gold contracts could lead to significant issues. This might result in market manipulation, legal liabilities, fines, and potentially even imprisonment for those involved. Such actions can undermine the integrity of the market and lead to regulatory and legal consequences. https://www.cnbc.com/2018/11/06/ex-jp-morgan-trader-pleads-guilty-to-manipulating-metals-markets.html Over longer periods, gold has not functioned as a true "store of value" relative to the dollar for quite some time, despite recently returning to its price from 9 years ago. This suggests that, while gold may have periods of price recovery, it has struggled to maintain its value over extended horizons compared to fiat currencies. It's worth noting that before 1980, aluminum was valued higher than gold. This reflects how market dynamics and technological advancements can significantly impact the value of commodities over time. https://www.mgsrefining.com/blog/why-aluminum-is-no-longer-a-precious-metal/ While gold has been undergoing a gradual demonetization process since 1980, another asset appears to be experiencing the opposite—hyper-monetization. (See in red; don't be alarmed.) https://image.nostr.build/435a5369f778a7be727b50e4c6328cfc353240bf804e1ed69313b9a8e1233f7e.jpg With the advent of Bitcoin, you believe that gold will continue on the same path as silver since the end of the bimetallic standard in 1853: a prolonged process of demonetization, with increasing volatility and reduced liquidity. https://image.nostr.build/5b9c8bfdb09e51d639e380df160c98beb9ee1d917ea13d28ef67711cfa5f8086.jpg Since 1913, the dollar has lost 97% of its purchasing power. Over the same period, the gold supply has increased significantly. Since 1980, gold has lost about 82% of its purchasing power. Given that the dollar is used as the unit of account and gold's liquidity is measured in dollars, these changes reflect the complex interaction between the currency and the precious metal. The U.S. is by far the country with the largest gold reserves in the world and is also the fourth-largest miner of the metal. Additionally, the country controls and issues the currency that serves as the unit of account for gold and has the highest liquidity in global trade. Is gold easy to transport? Is it simple to verify its supply and authenticity? Is it practical to store? Is its industrial utility significant? Can it be disrupted? And what about the continuous increase in its supply? These are important questions to consider. In my humble opinion, it will not be the dollar or fiat currencies that will suffer the most from the existence of Bitcoin, but rather the market cap of gold. https://image.nostr.build/61dddefabc4b69f784631a3294bdd978e3411bba40fb52d585e13b48002389fe.jpg
@ 129f5189:3a441803
2024-09-09 23:11:19Precious metals have served as monetary backing for millennia, but this does not guarantee that gold is a safe investment or a good hedge against economic crises and monetary collapses. Since its last major rally in the 1980s, gold has been progressively demonetized. Those who acquired gold in the late 1980s will need to rely on a significant increase in demand or a supply shock for its price to rise by 561% and regain the purchasing power it had 40 years ago. https://image.nostr.build/dd5fec2b474ea34cd72ddf5781393b528e63a358d523c9428f3ba4649f4f42aa.jpg If you look at the purchasing power of $1 (green line), you'll see that the depreciation is even faster. This might create the impression that gold is a good store of value. But does the fact that something loses value more slowly amidst a general decline really make it a store of value? Unless the total demand for gold increases at the same rate as its supply has grown in recent years, the purchasing power of the metal is likely to decline. https://image.nostr.build/9f24f6cf37780fe851746057520064ed94acd96547be53bd341c9e15b8762773.jpg In other words, if you own an ounce of gold, that ounce will represent an increasingly smaller fraction of the total gold reserves, meaning you are being diluted. Additionally, one should also consider the cost and risk of storage, but that's another issue. If you don't want to compare the purchasing power of gold today with the 1980s, you can consider its value from 9 years ago. Between September 2011 and November 2015, the Fed printed approximately $2.8 trillion. This also provides a perspective on gold's depreciation relative to the significant monetary expansion during that period. https://image.nostr.build/822e0a861e16ca258e0427875a84b5c8e5420e51bcf65674b453b55ed78edefd.jpg In other words, the Fed expanded its monetary base by about 30% during that 4-year period. However, the price of an ounce of gold fell by 45% (from $1,900 to $1,057) over the same interval. A true store of value should protect against excessive money printing. In contrast, during that same period, Bitcoin appreciated by 8,500% (from $5 to $419). https://image.nostr.build/32a7ca39a6e69e2780f9ab49390c7b7380499fcfe54ae4ef693e6fc91686a41e.jpg Indeed, while it is interesting to note that this was the exact period when gold derivatives were launched on CME Group, it's important to remember that correlation does not imply causation. Many factors can influence the price of gold and Bitcoin, and establishing a direct causal relationship requires more detailed analysis. https://derivsource.com/2011/06/21/cme-group-announces-the-launch-of-three-new-short-term-gold-crude-oil-and-natural-gas-options-contracts/ In an asset where supply can only be physically verified, flooding the market with gold contracts could lead to significant issues. This might result in market manipulation, legal liabilities, fines, and potentially even imprisonment for those involved. Such actions can undermine the integrity of the market and lead to regulatory and legal consequences. https://www.cnbc.com/2018/11/06/ex-jp-morgan-trader-pleads-guilty-to-manipulating-metals-markets.html Over longer periods, gold has not functioned as a true "store of value" relative to the dollar for quite some time, despite recently returning to its price from 9 years ago. This suggests that, while gold may have periods of price recovery, it has struggled to maintain its value over extended horizons compared to fiat currencies. It's worth noting that before 1980, aluminum was valued higher than gold. This reflects how market dynamics and technological advancements can significantly impact the value of commodities over time. https://www.mgsrefining.com/blog/why-aluminum-is-no-longer-a-precious-metal/ While gold has been undergoing a gradual demonetization process since 1980, another asset appears to be experiencing the opposite—hyper-monetization. (See in red; don't be alarmed.) https://image.nostr.build/435a5369f778a7be727b50e4c6328cfc353240bf804e1ed69313b9a8e1233f7e.jpg With the advent of Bitcoin, you believe that gold will continue on the same path as silver since the end of the bimetallic standard in 1853: a prolonged process of demonetization, with increasing volatility and reduced liquidity. https://image.nostr.build/5b9c8bfdb09e51d639e380df160c98beb9ee1d917ea13d28ef67711cfa5f8086.jpg Since 1913, the dollar has lost 97% of its purchasing power. Over the same period, the gold supply has increased significantly. Since 1980, gold has lost about 82% of its purchasing power. Given that the dollar is used as the unit of account and gold's liquidity is measured in dollars, these changes reflect the complex interaction between the currency and the precious metal. The U.S. is by far the country with the largest gold reserves in the world and is also the fourth-largest miner of the metal. Additionally, the country controls and issues the currency that serves as the unit of account for gold and has the highest liquidity in global trade. Is gold easy to transport? Is it simple to verify its supply and authenticity? Is it practical to store? Is its industrial utility significant? Can it be disrupted? And what about the continuous increase in its supply? These are important questions to consider. In my humble opinion, it will not be the dollar or fiat currencies that will suffer the most from the existence of Bitcoin, but rather the market cap of gold. https://image.nostr.build/61dddefabc4b69f784631a3294bdd978e3411bba40fb52d585e13b48002389fe.jpg @ 6bae33c8:607272e8
2024-09-09 16:07:43I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
@ 6bae33c8:607272e8
2024-09-09 16:07:43I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed. @ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :) I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet. What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds? What is your experience? I'd love to hear about it!
@ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :) I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet. What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds? What is your experience? I'd love to hear about it! @ 44dc1c2d:31c74f0b
2024-09-09 01:55:24## Chef's notes Makes an excellent Chicken sandwich. ## Details - ⏲️ Prep time: 6 Ish hours - 🍳 Cook time: 40 min - 🍽️ Servings: 1 loaf ## Ingredients - 3 ½ - 4 cups bread flour, or more as needed - 1 ⅓ cups warm milk (110°F – 115°F) - 5 tablespoons honey - 4 tablespoons salted butter, melted and slightly cooled - 1 tablespoon instant “rapid rise” yeast - 1 ½ teaspoons salt - Oil or butter for greasing the bowl - 1 tablespoon melted salted butter, for brushing the crust at the end ## Directions 1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl. 2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes. 3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours. 4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan. 5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F. 6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped. 7. Brush the top of the warm bread with melted butter. 8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24## Chef's notes Makes an excellent Chicken sandwich. ## Details - ⏲️ Prep time: 6 Ish hours - 🍳 Cook time: 40 min - 🍽️ Servings: 1 loaf ## Ingredients - 3 ½ - 4 cups bread flour, or more as needed - 1 ⅓ cups warm milk (110°F – 115°F) - 5 tablespoons honey - 4 tablespoons salted butter, melted and slightly cooled - 1 tablespoon instant “rapid rise” yeast - 1 ½ teaspoons salt - Oil or butter for greasing the bowl - 1 tablespoon melted salted butter, for brushing the crust at the end ## Directions 1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl. 2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes. 3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours. 4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan. 5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F. 6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped. 7. Brush the top of the warm bread with melted butter. 8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing. @ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one? Thanks originally posted at https://stacker.news/items/677439
@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one? Thanks originally posted at https://stacker.news/items/677439 @ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。 --- ### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。 项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed 项目的教程很详细,具体去看项目教程。 ### telegram设置: - 需要有telegram账号 - 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。 - 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。 - 一定要添加创建的机器人到频道作为管理员才能使用。 ### cloudflare的设置 - 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。 - 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图: [](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv") - BASIC_USER 后台登陆名 - BASIC_PASS 后台密码 - AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。 ### 其他 - 成人内容屏蔽 - pico 使用api接口 去项目地址看 ### 最后 我搭建的地址: https://imgbed.lepidus.me
@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。 --- ### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。 项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed 项目的教程很详细,具体去看项目教程。 ### telegram设置: - 需要有telegram账号 - 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。 - 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。 - 一定要添加创建的机器人到频道作为管理员才能使用。 ### cloudflare的设置 - 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。 - 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图: [](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv") - BASIC_USER 后台登陆名 - BASIC_PASS 后台密码 - AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。 ### 其他 - 成人内容屏蔽 - pico 使用api接口 去项目地址看 ### 最后 我搭建的地址: https://imgbed.lepidus.me @ d52f4f20:98efcdfb
2024-09-08 12:05:31_original post 28/12/2010 .net_ Para você que se sente meio preso ao instalar o Ubuntu, pois ele já vem pronto para um usuário final, mas isso não me agrada parece que perco o espirito de liberdade. Mas o ponto forte Ubuntu são suas atualizações, então eu fui em busca de como fazer uma instalação customizada somente com os pacotes do Ubuntu. Depois de muita pesquisa e anos de experiência com linux desenvolvi o que chamo de instalação mínima **Alguns conceitos da minha instalação** – Não tem gerenciador de login gráfico. – Precisar habilitar o root, na unha e você usa isso. – Não tem menus, os aplicativos são chamados via tecla de atalho ou docks. – Não tem menu para desligar. – Não é um desktop, usa apenas um gerenciador de Janelas. – Aqui tudo é minimalista, não é bonito também não quer dizer que é feio, é apenas simples faz o necessário. – Não importa a versão do ubuntu, atual ou não essa técnica quase nunca mudará. **Seria bom/Pré-Requisitos** – Se você tem conceitos de particionamento. – Se você já instalou um Debian. – Se você sabe usar o vim. – Conexão com internet via placa de rede 10/100 (sim tem que ser assim). **Introdução** A idéia é usar a instalação mínima do Ubuntu (https://help.ubuntu.com/community/Installation/MinimalCD), onde é bem parecida com a NetInstall do Debian. Iremos baixar a imagem(12 ~ 13MB) do link acima e queimar em um cd rom e dar boot. Vamos usar o assistente de instalação, e não selecionaremos nenhum pacote na instalação, tudo sera instalado via linha de comando usando o apt. Pra quem já instalou usando o anaconda da RedHat não terá problemas, qualquer ser capaz de ler consegue instalar.  Esta é a primeira tela exibida após o boot, selecione o menu  Va seguindo o instalador conforme as telas, não quer que eu fique explicando tudo né?    Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.  Aqui você estara selecionando daonde pacotes serão baixados.  Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.    Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.    Após criar, FINISH!  Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.  O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.  senha é bom por né.  Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.   Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente.  Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar.  Grub é o gerenciador de boot, instale ele ai sem medo.  Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada. Logue-se com seu usuário, meu caso “lion” (que coisa gay figura 24 ainda).  **Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI. **Torna-se root** Isso é primordio no linux, sempre somos o ROOT, o Ubuntu tem essa filosofia para você não fazer cagada, mas na vida uma boa técnica de aprendizado é fazendo cagada, então vamos habilitar o root. Calma usaremos o root para tarefas como instalar novos software, mas a execução e configuração de nosso ambiente será com nosso usuário. ``` $ sudo passwd root ``` Pronto a partir de agora os comandos começados com # quer dizer que você tem que estar logado como root, e quando estiver $ você deve executar com seu usuário. Loge-se como root vamos usar bastante de um $su ou entre num novo tty como root. **Instalando o vim** ``` #apt-get install vim ``` (repare # você tem que estar logado como root) **Removendo o boot-splash** Amigos estamos falando de uma maquina limpa, o boot splash só come memória. Faça um backup antes e depois edite o arquivo “/boot/grub/grub.cfg” procure a palavra splash e apague somente ela e salve o arquivo. É necessário dar diretos de gravação e depois volte como somente leitura. **Removendo Mensagem de boas vindas MOTD** Logo após o login, é exibida uma mensagem de boas vindas enorme do ubuntu, eu não gosto dela, nem do debian eu gostava e eu a removia editando o script “/etc/init.d/boot-misc.sh” mas no ubuntu esse arquivo não existe. Depois de muito fuçar eu descobri que removendo os arquivos do diretorio “/etc/update-motd.d/” a mensagem some, pra mim basta, também removi o conteudo do arquivo /var/run/motd ; **UPDATE** Dica do comentário do Marcelo Godim Ele é gerenciado pelo pam_motd basta ir em /etc/pam.d nos arquivos “login” e “sshd” e comentar essas linhas abaixo: login: #session optional pam_motd.so sshd: #session optional pam_motd.so # [1] **Mudando mensagem da versão** Dica velha edite o arquivo “/etc/issue” coloque o que preferir. ——Se você não precisa de modo gráfico a instalação terminou aqui. Alterando o sources.list adicionando outros repositórios Edite o arquivo /etc/apt/sources.list e deixe assim, basicamente adicionados pacotes do site Medibuntu, se prefereir siga esses passos é melhor do que editar o arquivo. **Instalando o resto dos pacotes** #apt-get install xserver-xorg xinit alsa-base alsa-utils openbox obconf obmenu feh nitrogen tint2 k3b conky gmrun pcmanfm gtk-theme-switch ssh smbfs smbclient dosfstools setserial usbutils leafpad x11-apps openbox-themes terminator chromium-browser xcompmgr gcc g++ openjdk-6-jdk mysql-server mysql-query-browser gftp gcc-avr avrdude imagemagick gparted ntfs-3g file-roller zip unrar gpicview gtk2-engines gnome-icon-theme-gartoon vim unace rar unrar zip unzip p7zip-full p7zip-rar sharutils uudeview mpack lha arj cabextract file-roller pidgin pidgin-data pidgin-lastfm pidgin-guifications msn-pecan pidgin-musictracker pidgin-plugin-pack pidgin-themes mplayer vlc cairo-dock w32codecs audacious Vai dormir, seila vai baixar ai uns 500mb, você pode tirar ou por o que quiser ai isso é minha instalação. Como entrar no modo gráfico? Logue-se com seu usuário ``` $startx ``` O comando antigo, simples, que dei a primeira vez no meu conectiva 4.  Este é o resultado final, mas para isso vamos algumas dicas. Toda incialização dos aplicativos eu concentrei no .config/openbox/autostart.sh segue o meu ai ``` # Set desktop wallpaper nitrogen –restore & # Enable Eyecandy – off by default xcompmgr -cCfF -r7 -o.65 -l-10 -t-8 & # Launch network manager applet (sleep 4s && nm-applet) & # Launch clipboard manager #(sleep 1s && parcellite) & # Uncomment to enable system updates at boot #(sleep 180s && system-update) & cairo-dock & # Launch Conky #conky -q & # Launch panel tint2 & ``` **Configurando teclas de atalho**, edite o arquivo .config/openbox/rc.xml, vá até a seção keybinds as minhas são essas abaixo: ``` <keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-1″><action name=”Execute”> <execute>xcompmgr -cCfF -r7 -o.65 -l-10 -t-8</execute></action></keybind><keybind key=”W-2″><action name=”Execute”> <execute>pkill xcompmgr</execute></action></keybind><keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-e”><action name=”Execute”> <execute>pcmanfm</execute></action></keybind><keybind key=”W-g”><action name=”Execute”> <startupnotify> <enabled>true</enabled> <name>transset</name> </startupnotify> <command>transset .50</command></action></keybind><keybind key=”W-h”><action name=”Execute”> <startupnotify><enabled>true</enabled><name>transset 1</name></startupnotify><command>transset 1</command></action></keybind><keybind key=”W-l”><action name=”Execute”><startupnotify><enabled>true</enabled><name>Lock screen</name></startupnotify><command>gnome-screensaver-command -l</command></action></keybind><keybind key=”W-t”><action name=”Execute”><execute>terminator</execute></action></keybind><keybind key=”W-r”> <action name=”Execute”> <execute>gmrun</execute> </action></keybind> ``` Pesquise como instalar temas GTK, configurar o TINT2 (desk bar), Cairo Dock, também tem muitas configurações de openbox na internet. Esse tutorial vem de anos de convivio com linux, é duro passar tudo a limpo aqui, uma dica e testar o Linux Crunch-Bang aprendi muitas customizações com ele. #blog #tech
@ d52f4f20:98efcdfb
2024-09-08 12:05:31_original post 28/12/2010 .net_ Para você que se sente meio preso ao instalar o Ubuntu, pois ele já vem pronto para um usuário final, mas isso não me agrada parece que perco o espirito de liberdade. Mas o ponto forte Ubuntu são suas atualizações, então eu fui em busca de como fazer uma instalação customizada somente com os pacotes do Ubuntu. Depois de muita pesquisa e anos de experiência com linux desenvolvi o que chamo de instalação mínima **Alguns conceitos da minha instalação** – Não tem gerenciador de login gráfico. – Precisar habilitar o root, na unha e você usa isso. – Não tem menus, os aplicativos são chamados via tecla de atalho ou docks. – Não tem menu para desligar. – Não é um desktop, usa apenas um gerenciador de Janelas. – Aqui tudo é minimalista, não é bonito também não quer dizer que é feio, é apenas simples faz o necessário. – Não importa a versão do ubuntu, atual ou não essa técnica quase nunca mudará. **Seria bom/Pré-Requisitos** – Se você tem conceitos de particionamento. – Se você já instalou um Debian. – Se você sabe usar o vim. – Conexão com internet via placa de rede 10/100 (sim tem que ser assim). **Introdução** A idéia é usar a instalação mínima do Ubuntu (https://help.ubuntu.com/community/Installation/MinimalCD), onde é bem parecida com a NetInstall do Debian. Iremos baixar a imagem(12 ~ 13MB) do link acima e queimar em um cd rom e dar boot. Vamos usar o assistente de instalação, e não selecionaremos nenhum pacote na instalação, tudo sera instalado via linha de comando usando o apt. Pra quem já instalou usando o anaconda da RedHat não terá problemas, qualquer ser capaz de ler consegue instalar.  Esta é a primeira tela exibida após o boot, selecione o menu  Va seguindo o instalador conforme as telas, não quer que eu fique explicando tudo né?    Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.  Aqui você estara selecionando daonde pacotes serão baixados.  Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.    Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.    Após criar, FINISH!  Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.  O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.  senha é bom por né.  Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.   Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente.  Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar.  Grub é o gerenciador de boot, instale ele ai sem medo.  Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada. Logue-se com seu usuário, meu caso “lion” (que coisa gay figura 24 ainda).  **Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI. **Torna-se root** Isso é primordio no linux, sempre somos o ROOT, o Ubuntu tem essa filosofia para você não fazer cagada, mas na vida uma boa técnica de aprendizado é fazendo cagada, então vamos habilitar o root. Calma usaremos o root para tarefas como instalar novos software, mas a execução e configuração de nosso ambiente será com nosso usuário. ``` $ sudo passwd root ``` Pronto a partir de agora os comandos começados com # quer dizer que você tem que estar logado como root, e quando estiver $ você deve executar com seu usuário. Loge-se como root vamos usar bastante de um $su ou entre num novo tty como root. **Instalando o vim** ``` #apt-get install vim ``` (repare # você tem que estar logado como root) **Removendo o boot-splash** Amigos estamos falando de uma maquina limpa, o boot splash só come memória. Faça um backup antes e depois edite o arquivo “/boot/grub/grub.cfg” procure a palavra splash e apague somente ela e salve o arquivo. É necessário dar diretos de gravação e depois volte como somente leitura. **Removendo Mensagem de boas vindas MOTD** Logo após o login, é exibida uma mensagem de boas vindas enorme do ubuntu, eu não gosto dela, nem do debian eu gostava e eu a removia editando o script “/etc/init.d/boot-misc.sh” mas no ubuntu esse arquivo não existe. Depois de muito fuçar eu descobri que removendo os arquivos do diretorio “/etc/update-motd.d/” a mensagem some, pra mim basta, também removi o conteudo do arquivo /var/run/motd ; **UPDATE** Dica do comentário do Marcelo Godim Ele é gerenciado pelo pam_motd basta ir em /etc/pam.d nos arquivos “login” e “sshd” e comentar essas linhas abaixo: login: #session optional pam_motd.so sshd: #session optional pam_motd.so # [1] **Mudando mensagem da versão** Dica velha edite o arquivo “/etc/issue” coloque o que preferir. ——Se você não precisa de modo gráfico a instalação terminou aqui. Alterando o sources.list adicionando outros repositórios Edite o arquivo /etc/apt/sources.list e deixe assim, basicamente adicionados pacotes do site Medibuntu, se prefereir siga esses passos é melhor do que editar o arquivo. **Instalando o resto dos pacotes** #apt-get install xserver-xorg xinit alsa-base alsa-utils openbox obconf obmenu feh nitrogen tint2 k3b conky gmrun pcmanfm gtk-theme-switch ssh smbfs smbclient dosfstools setserial usbutils leafpad x11-apps openbox-themes terminator chromium-browser xcompmgr gcc g++ openjdk-6-jdk mysql-server mysql-query-browser gftp gcc-avr avrdude imagemagick gparted ntfs-3g file-roller zip unrar gpicview gtk2-engines gnome-icon-theme-gartoon vim unace rar unrar zip unzip p7zip-full p7zip-rar sharutils uudeview mpack lha arj cabextract file-roller pidgin pidgin-data pidgin-lastfm pidgin-guifications msn-pecan pidgin-musictracker pidgin-plugin-pack pidgin-themes mplayer vlc cairo-dock w32codecs audacious Vai dormir, seila vai baixar ai uns 500mb, você pode tirar ou por o que quiser ai isso é minha instalação. Como entrar no modo gráfico? Logue-se com seu usuário ``` $startx ``` O comando antigo, simples, que dei a primeira vez no meu conectiva 4.  Este é o resultado final, mas para isso vamos algumas dicas. Toda incialização dos aplicativos eu concentrei no .config/openbox/autostart.sh segue o meu ai ``` # Set desktop wallpaper nitrogen –restore & # Enable Eyecandy – off by default xcompmgr -cCfF -r7 -o.65 -l-10 -t-8 & # Launch network manager applet (sleep 4s && nm-applet) & # Launch clipboard manager #(sleep 1s && parcellite) & # Uncomment to enable system updates at boot #(sleep 180s && system-update) & cairo-dock & # Launch Conky #conky -q & # Launch panel tint2 & ``` **Configurando teclas de atalho**, edite o arquivo .config/openbox/rc.xml, vá até a seção keybinds as minhas são essas abaixo: ``` <keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-1″><action name=”Execute”> <execute>xcompmgr -cCfF -r7 -o.65 -l-10 -t-8</execute></action></keybind><keybind key=”W-2″><action name=”Execute”> <execute>pkill xcompmgr</execute></action></keybind><keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-e”><action name=”Execute”> <execute>pcmanfm</execute></action></keybind><keybind key=”W-g”><action name=”Execute”> <startupnotify> <enabled>true</enabled> <name>transset</name> </startupnotify> <command>transset .50</command></action></keybind><keybind key=”W-h”><action name=”Execute”> <startupnotify><enabled>true</enabled><name>transset 1</name></startupnotify><command>transset 1</command></action></keybind><keybind key=”W-l”><action name=”Execute”><startupnotify><enabled>true</enabled><name>Lock screen</name></startupnotify><command>gnome-screensaver-command -l</command></action></keybind><keybind key=”W-t”><action name=”Execute”><execute>terminator</execute></action></keybind><keybind key=”W-r”> <action name=”Execute”> <execute>gmrun</execute> </action></keybind> ``` Pesquise como instalar temas GTK, configurar o TINT2 (desk bar), Cairo Dock, também tem muitas configurações de openbox na internet. Esse tutorial vem de anos de convivio com linux, é duro passar tudo a limpo aqui, uma dica e testar o Linux Crunch-Bang aprendi muitas customizações com ele. #blog #tech @ c6f7077f:ad5d48fd
2024-09-08 01:24:03***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further. #### ***Consider the Most Fundamental Questions*** 1. **The Origin of the Universe** 2. **The Origin of Life on Earth** #### ***The Origin of the Universe*** You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding. The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding. Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**. #### ***The Origin of Life on Earth*** The origin of life is even more complex. Life requires three essential components: - **Proteins** for basic functioning - **RNA** for storing and replicating genes - **Lipids** (cell walls) to create separation from the environment Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**. #### ***The Question of Certainty*** If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early. #### ***Reclaiming Control of Science and Education*** The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend: - **“A Brief History of Time”** by **Stephen Hawking** for physics - **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further. #### ***Consider the Most Fundamental Questions*** 1. **The Origin of the Universe** 2. **The Origin of Life on Earth** #### ***The Origin of the Universe*** You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding. The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding. Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**. #### ***The Origin of Life on Earth*** The origin of life is even more complex. Life requires three essential components: - **Proteins** for basic functioning - **RNA** for storing and replicating genes - **Lipids** (cell walls) to create separation from the environment Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**. #### ***The Question of Certainty*** If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early. #### ***Reclaiming Control of Science and Education*** The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend: - **“A Brief History of Time”** by **Stephen Hawking** for physics - **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner. @ 6bae33c8:607272e8
2024-09-07 22:09:27With all five of my football drafts/auctions in the books, here's the portfolio I've amassed for 2024, not including the RotoWire Dynasty League: **Links**: [BCL1](https://www.realmansports.com/p/beat-chris-liss-1-344), [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e?utm_source=publication-search), [BCL3](https://www.realmansports.com/p/beat-chris-liss-3-062), [Steak League](https://www.realmansports.com/p/steak-league-879), [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7)  **Players in whom I have the most shares:** **QB**: Justin Fields (4), CJ Stroud (2), Anthony Richardson (2), Tua Tagovailoa (2) **RB**: Jonathan Brooks (2), Brian Robinson (2), Jerome Ford (2), Jordan Mason (2), JK Dobbins (2), Khalil Herbert (2), Dalvin Cook (2) **WR:** Stefon Diggs (5), Ja’Marr Chase (3), Rashid Shaheed (3), Ladd McConkey (2), Roman Wilson (2) **TE:** Jonnu Smith (3) **K**: Younghoe Koo (3), Harrison Butker (2) **D:** Giants (4) **Notes:** Obviously, I thought Stefon Diggs was mispriced, though I only had to pay close to what I thought he was worth in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7) — in the rest of the leagues he fell to me at ADP or below. He and Ja’Marr Chase are massively important to me this year, and to a lesser extent CJ Stroud. I also have Justin Fields and the Giants defense everywhere, but both were essentially free, and I could swap them out without issue. I also have a lot of Younghoe Koo, but he too could obviously be swapped out. I like having a couple key players to build around rather than five disparate teams. Of course if Diggs gets hurt or turns out to be washed up, it’ll be rough, but in some ways it’s like the old days where you had only one team, and you had to live and die with it. **Prominent Players I Don't Have (bold is by choice):** Bijan Robinson, Tyreek Hill, Breece Hall, Amon-Ra St. Brown, Justin Jefferson, Garrett Wilson, A.J. Brown, Jonathan Taylor, Puka Nacua, **Davante Adams**, **Saquon Barkley**, Chris Olave, Rashee Rice, **Kyren Williams**, Travis Etienne, Cooper Kupp, Isiah Pacheco, **Michael Pittman**, **Nico Collins**, **DK Metcalf**, **Mike Evans**, **Deebo Samuel, Josh Allen,** DJ Moore, Brandon Aiyuk, Derrick Henry, Zay Flowers, **James Cook**, Terry McLaurin, Kenneth Walker, **Xavier Worthy**, Amari Cooper, Josh Jacobs, Trey McBride, **George Pickens**, Lamar Jackson, **Christian Kirk**, Tee Higgins, **Calvin Ridley**, **Rachaad White,** Jayden Reed, Diontae Johnson, **Travis Kelce**, **Joe Mixon**, **Alvin Kamara**, Christian Watson, **Jalen Hurts**, Aaron Jones, Patrick Mahomes, David Montgomery, **Zamir White, Keenan Allen,** Kyle Pitts, **D’Andre Swift**, George Kittle **Past Portfolios:** [**2023**](https://www.realmansports.com/p/my-portfolio-ef6?utm_source=publication-search)**, [2022](https://www.realmansports.com/p/my-portfolio?utm_source=%2Fsearch%2Fmy%2520portfolio&utm_medium=reader2), [2021](https://www.rotowire.com/football/article/nfl-chris-lissrsquo-portfolio-58839), [2020](https://www.rotowire.com/football/article.php?id=52704)[, 2019](https://www.rotowire.com/blog/post.php?id=29428), [2018](https://www.rotowire.com/blog/post.php?id=26158), [2017](https://www.rotowire.com/blog/post.php?id=23069), [2016](https://www.rotowire.com/blog/post.php?id=13592), [2015](https://www.rotowire.com/blog/post.php?id=8991)**
@ 6bae33c8:607272e8
2024-09-07 22:09:27With all five of my football drafts/auctions in the books, here's the portfolio I've amassed for 2024, not including the RotoWire Dynasty League: **Links**: [BCL1](https://www.realmansports.com/p/beat-chris-liss-1-344), [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e?utm_source=publication-search), [BCL3](https://www.realmansports.com/p/beat-chris-liss-3-062), [Steak League](https://www.realmansports.com/p/steak-league-879), [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7)  **Players in whom I have the most shares:** **QB**: Justin Fields (4), CJ Stroud (2), Anthony Richardson (2), Tua Tagovailoa (2) **RB**: Jonathan Brooks (2), Brian Robinson (2), Jerome Ford (2), Jordan Mason (2), JK Dobbins (2), Khalil Herbert (2), Dalvin Cook (2) **WR:** Stefon Diggs (5), Ja’Marr Chase (3), Rashid Shaheed (3), Ladd McConkey (2), Roman Wilson (2) **TE:** Jonnu Smith (3) **K**: Younghoe Koo (3), Harrison Butker (2) **D:** Giants (4) **Notes:** Obviously, I thought Stefon Diggs was mispriced, though I only had to pay close to what I thought he was worth in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7) — in the rest of the leagues he fell to me at ADP or below. He and Ja’Marr Chase are massively important to me this year, and to a lesser extent CJ Stroud. I also have Justin Fields and the Giants defense everywhere, but both were essentially free, and I could swap them out without issue. I also have a lot of Younghoe Koo, but he too could obviously be swapped out. I like having a couple key players to build around rather than five disparate teams. Of course if Diggs gets hurt or turns out to be washed up, it’ll be rough, but in some ways it’s like the old days where you had only one team, and you had to live and die with it. **Prominent Players I Don't Have (bold is by choice):** Bijan Robinson, Tyreek Hill, Breece Hall, Amon-Ra St. Brown, Justin Jefferson, Garrett Wilson, A.J. Brown, Jonathan Taylor, Puka Nacua, **Davante Adams**, **Saquon Barkley**, Chris Olave, Rashee Rice, **Kyren Williams**, Travis Etienne, Cooper Kupp, Isiah Pacheco, **Michael Pittman**, **Nico Collins**, **DK Metcalf**, **Mike Evans**, **Deebo Samuel, Josh Allen,** DJ Moore, Brandon Aiyuk, Derrick Henry, Zay Flowers, **James Cook**, Terry McLaurin, Kenneth Walker, **Xavier Worthy**, Amari Cooper, Josh Jacobs, Trey McBride, **George Pickens**, Lamar Jackson, **Christian Kirk**, Tee Higgins, **Calvin Ridley**, **Rachaad White,** Jayden Reed, Diontae Johnson, **Travis Kelce**, **Joe Mixon**, **Alvin Kamara**, Christian Watson, **Jalen Hurts**, Aaron Jones, Patrick Mahomes, David Montgomery, **Zamir White, Keenan Allen,** Kyle Pitts, **D’Andre Swift**, George Kittle **Past Portfolios:** [**2023**](https://www.realmansports.com/p/my-portfolio-ef6?utm_source=publication-search)**, [2022](https://www.realmansports.com/p/my-portfolio?utm_source=%2Fsearch%2Fmy%2520portfolio&utm_medium=reader2), [2021](https://www.rotowire.com/football/article/nfl-chris-lissrsquo-portfolio-58839), [2020](https://www.rotowire.com/football/article.php?id=52704)[, 2019](https://www.rotowire.com/blog/post.php?id=29428), [2018](https://www.rotowire.com/blog/post.php?id=26158), [2017](https://www.rotowire.com/blog/post.php?id=23069), [2016](https://www.rotowire.com/blog/post.php?id=13592), [2015](https://www.rotowire.com/blog/post.php?id=8991)** @ 6bae33c8:607272e8
2024-09-07 22:07:54I submitted my five picks for the Circa Millions contest today. I think it’s $6M in total prizes. I want to put a disclaimer here: I’m putting these behind a paywall not because you should pay for these picks — never pay for anyone’s picks. If the picks were that good, whoever was making them could just print money and wouldn’t need yours. If you want to subscribe in earnest, do so because you’re interested to see who I chose and read the reasoning, not because you (erroneously) think it’s the way to get some easy winners. Or if you want to support my substack generally because you think it adds value to you. Those are fine reasons to subscribe, but doing so because you think copying my picks will make you money is dumb. Okay that out of the way, here are the picks:  **Dolphins -3.5 vs Jaguars** — I like taking the Dolphins in early September, it’s hot and humid there, difficult for opposing teams to adjust to it. It’s like Lambeau Field in December, only in reverse. Moreover, the Dolphins are a veteran offense that’s played together for years, while the Jaguars are working in two new receivers. **Falcons -3.5 vs Steelers** — Justin Fields is probably an upgrade over Russell Wilson at this point, but he’s haphazard and will have to learn the players and offense on the fly. The Falcons have a new QB too, but he’s an old pro, has better weapons and a better offensive line. **Giants +1 vs Vikings** — The Giants have three Pro-Bowl level pass rushers, finally have a playmaking receiver and upgraded their offensive line this offseason. And yet despite facing Sam Darnold at home, they’re still getting a point. **Cardinals +6.5 at Bills** — Kyler Murray is now another year removed from knee surgery, should be his usual spry self, and Marvin Harrison adds another dimension to the offense it sorely needed. The Bills will move the ball, but I think Arizona will hang with them and keep it close enough. **Browns -2 vs Cowboys** — The Browns should be able to run the ball and keep the Dallas pass rush off Deshaun Watson, while Dallas’ offensive line has slipped a bit, and the Browns defense was No. 1 against the pass last year. Dak Prescott also has big home/road splits.
@ 6bae33c8:607272e8
2024-09-07 22:07:54I submitted my five picks for the Circa Millions contest today. I think it’s $6M in total prizes. I want to put a disclaimer here: I’m putting these behind a paywall not because you should pay for these picks — never pay for anyone’s picks. If the picks were that good, whoever was making them could just print money and wouldn’t need yours. If you want to subscribe in earnest, do so because you’re interested to see who I chose and read the reasoning, not because you (erroneously) think it’s the way to get some easy winners. Or if you want to support my substack generally because you think it adds value to you. Those are fine reasons to subscribe, but doing so because you think copying my picks will make you money is dumb. Okay that out of the way, here are the picks:  **Dolphins -3.5 vs Jaguars** — I like taking the Dolphins in early September, it’s hot and humid there, difficult for opposing teams to adjust to it. It’s like Lambeau Field in December, only in reverse. Moreover, the Dolphins are a veteran offense that’s played together for years, while the Jaguars are working in two new receivers. **Falcons -3.5 vs Steelers** — Justin Fields is probably an upgrade over Russell Wilson at this point, but he’s haphazard and will have to learn the players and offense on the fly. The Falcons have a new QB too, but he’s an old pro, has better weapons and a better offensive line. **Giants +1 vs Vikings** — The Giants have three Pro-Bowl level pass rushers, finally have a playmaking receiver and upgraded their offensive line this offseason. And yet despite facing Sam Darnold at home, they’re still getting a point. **Cardinals +6.5 at Bills** — Kyler Murray is now another year removed from knee surgery, should be his usual spry self, and Marvin Harrison adds another dimension to the offense it sorely needed. The Bills will move the ball, but I think Arizona will hang with them and keep it close enough. **Browns -2 vs Cowboys** — The Browns should be able to run the ball and keep the Dallas pass rush off Deshaun Watson, while Dallas’ offensive line has slipped a bit, and the Browns defense was No. 1 against the pass last year. Dak Prescott also has big home/road splits. @ 6bae33c8:607272e8
2024-09-07 22:05:26This is my main event for fantasy football, the $1700 buy-in NFFC Primetime. I wound up picking 11th (I had the fourth to last choice), and while in retrospect maybe I should have opted for ninth or 10th, I wanted to get a share of Jahmyr Gibbs which is why I chose that slot. I also ran through some scenarios beforehand — what if Ja’Marr Chase (still not signed) falls — do I take him in a fourth league? But as you’ll see, the first round was complete chalk, and no windfalls whatsoever fell to me. But I had a plan for that, and I more or less executed it. Without further ado, here are the results: <img src="https://blossom.primal.net/4bbf1f4369c4eea958b04922892f9c485dcbce7d68f011e55c11997f05ae6006.png"> **1.11 Jahmyr Gibbs** — This was the most likely scenario, and it took me about two seconds to make the pick once the top three backs and seven receivers were gone. If Gibbs (who is not on the injury report) hadn’t had a hamstring injury in camp, I’d have him close to the middle of the round rather than the end. Let’s hope he doesn’t aggravate it. **2.2 Marvin Harrison** — I would have taken either Puka Nacua or Jonathan Taylor, but no breaks here either. Both went at the turn, and I knew I was taking a receiver. Starting RB-WR is the easiest build, in my opinion, but Harrison was kind of an agnostic pick. I had considered Rashee Rice, but as Alan Seslowsky pointed out, while his suspension for hit and run might not kick in until after the season (when the legal process has run its course), that could be pushed up if his lawyers negotiate a plea. Between that an the presence of so many options for the Chiefs, I went Harrison over him narrowly. But it was a close call. **3.2 Stefon Diggs** — I missed Malik Nabers, Cooper Kupp, (maybe Jaylen Waddle) and De’Von Achane who went with the four consecutive picks ahead of me, so it was Diggs, Nico Collins (his teammate who has a higher ADP), DeVonta Smith or (maybe) Derrick Henry. I went Diggs who I had personally ranked the highest, wouldn’t make it back to me, who I have in every league and was part of my “unfriendly” draft plan, i.e., the Plan B I had talked about. **4.11 Tank Dell** — He’s too small to hold up, but whenever he played he produced, and he gives me a bit of a Diggs hedge. I also wanted Trey McBride on this turn (as I had Marvin Harrison and could have drafted Kyler Murray — who I love this year — later), but he went on the turn. I thought about taking McBride first, but they were side by side in ADP, and my Plan B was to stack Texans, so I went Dell and took a chance. **5.2 Chris Godwin** — This was the one pick I kind of regret (though it’s debatable.) I like Jayden Reed a lot, but he was half a round lower per ADP, and there was *some* chance I could get him on the way back. I had Godwin everywhere last year, and he was a disappointment, but apparently he’s healthier now and is going back to the slot full time where he excels. **6.11 Jaxon Smith-Njigba** — The other pivot off Godwin was JSN, and sure enough he made it back all the way, though he starts off as my first bench player. That’s okay though — you need at least five viable receivers throughout the year, and I didn’t have to take C.J. Stroud because if the guy at the turn took him, I would just pivot to the Kyler Murray/Harrison stack. **7.2 C.J. Stroud** — He was there, and I executed Plan B. Yes, I have a weak first three rounds by ADP, but I have Gibbs, Harrison and a big piece of the Texans passing game which I think will lead the NFL in yardage. **8.11 Jaylen Warren** — I needed a second back, and Warren is one. He’s a good pass catcher and should see half the snaps in Pittsburgh. **9.2 Brian Robinson** — I like Robinson as a player, he’s the undisputed early-down option on what should be a better offense. (Think Ricky Pearsall, but at RB.) Too soon? Austin Ekeler will obviously see the passing-down work unless he proves totally washed up. The Robinson pick cost me David Njoku and Brock Bowers unfortunately, which was a gamble I knew I was making. **10.11 Jordan Mason** — At 29 and playing into the Super Bowl, Christian McCalfinjury was already a risk, and that he’s “expected” to play Monday night rather than 100 percent fine is worrying. Mason could be a league winner if McCaffrey goes down. **11.2 J.K. Dobbins** — The Mason pick cost me Jaleel McLaughlin, so I pivoted to Dobbins who still has a high ceiling if he can ever stay healthy. **12.11 Dallas Goedert** — Tight ends had flown off the board, but I was happy to get Goedert who has been valuable on a per-game basis the last couple years and is still just 29 which is late prime for the position. **13.2 Dalton Schultz** — Why not stack it even harder? The Texans could throw for 5,000-plus yards, and I have three of the four top targets and the QB. **14.11 Andrei Iosivas** — He’s gotten a lot of buzz in camp, seems like the No. 3 receiver right now, Tee Higgins is hurt and Ja’Marr Chase is still unsigned. **15.2 Cam Akers** — The Iosivas pick cost me Jalen McMillan who would have served as Godwin insurance, but Akers could easily take an aging Joe Mixon’s job. Maybe it’s too much Houston, but if it’s a top-three offense, I’m good with it. **16.11 Justin Fields** — The backup QBs had flown off the board, and Fields has too much upside to pass up. Plus he might even start Week 1 with Russell Wilson already hurt, and if he plays well, he might never look back. **17.2 Harrison Butker** — It’s either the based af kicker or a Younghoe for me. Plus he locked in a decent Week 1. **18.11 Dalvin Cook** — He had only 67 carries last year for a bad Jets offense. What if he isn’t as washed up as we think? He could easily win that job over Zeke Elliott and Rico Dowdle. **19.2 Jonnu Smith** — TE is my weakest position, so I took another upside gamble. What if he’s the Dolphins third target? **20.11 Giants Defense** — I think I took them in all four NFFC leagues. They get the Darnold Vikings at home and then Jayden Daniels in his second career start. And they have three Pro Bowl level pass rushers. **Roster By Position** **QB** CJ Stroud **RB** Jahmyr Gibbs/Jaylen Warren **WR** Marvin Harrison/Stefon Diggs/Tank Dell **TE** Dallas Goedert **FLEX** Chris Godwin **K** Harrison Butker **D** Giants **B** Jaxon Smith-Njigba/Brian Robinson/Jordan Mason/JK Dobbins/Dalton Schultz/Andrei Iosivas/Cam Akers/Justin Fields/Dalvin Cook/Jonnu Smith
@ 6bae33c8:607272e8
2024-09-07 22:05:26This is my main event for fantasy football, the $1700 buy-in NFFC Primetime. I wound up picking 11th (I had the fourth to last choice), and while in retrospect maybe I should have opted for ninth or 10th, I wanted to get a share of Jahmyr Gibbs which is why I chose that slot. I also ran through some scenarios beforehand — what if Ja’Marr Chase (still not signed) falls — do I take him in a fourth league? But as you’ll see, the first round was complete chalk, and no windfalls whatsoever fell to me. But I had a plan for that, and I more or less executed it. Without further ado, here are the results: <img src="https://blossom.primal.net/4bbf1f4369c4eea958b04922892f9c485dcbce7d68f011e55c11997f05ae6006.png"> **1.11 Jahmyr Gibbs** — This was the most likely scenario, and it took me about two seconds to make the pick once the top three backs and seven receivers were gone. If Gibbs (who is not on the injury report) hadn’t had a hamstring injury in camp, I’d have him close to the middle of the round rather than the end. Let’s hope he doesn’t aggravate it. **2.2 Marvin Harrison** — I would have taken either Puka Nacua or Jonathan Taylor, but no breaks here either. Both went at the turn, and I knew I was taking a receiver. Starting RB-WR is the easiest build, in my opinion, but Harrison was kind of an agnostic pick. I had considered Rashee Rice, but as Alan Seslowsky pointed out, while his suspension for hit and run might not kick in until after the season (when the legal process has run its course), that could be pushed up if his lawyers negotiate a plea. Between that an the presence of so many options for the Chiefs, I went Harrison over him narrowly. But it was a close call. **3.2 Stefon Diggs** — I missed Malik Nabers, Cooper Kupp, (maybe Jaylen Waddle) and De’Von Achane who went with the four consecutive picks ahead of me, so it was Diggs, Nico Collins (his teammate who has a higher ADP), DeVonta Smith or (maybe) Derrick Henry. I went Diggs who I had personally ranked the highest, wouldn’t make it back to me, who I have in every league and was part of my “unfriendly” draft plan, i.e., the Plan B I had talked about. **4.11 Tank Dell** — He’s too small to hold up, but whenever he played he produced, and he gives me a bit of a Diggs hedge. I also wanted Trey McBride on this turn (as I had Marvin Harrison and could have drafted Kyler Murray — who I love this year — later), but he went on the turn. I thought about taking McBride first, but they were side by side in ADP, and my Plan B was to stack Texans, so I went Dell and took a chance. **5.2 Chris Godwin** — This was the one pick I kind of regret (though it’s debatable.) I like Jayden Reed a lot, but he was half a round lower per ADP, and there was *some* chance I could get him on the way back. I had Godwin everywhere last year, and he was a disappointment, but apparently he’s healthier now and is going back to the slot full time where he excels. **6.11 Jaxon Smith-Njigba** — The other pivot off Godwin was JSN, and sure enough he made it back all the way, though he starts off as my first bench player. That’s okay though — you need at least five viable receivers throughout the year, and I didn’t have to take C.J. Stroud because if the guy at the turn took him, I would just pivot to the Kyler Murray/Harrison stack. **7.2 C.J. Stroud** — He was there, and I executed Plan B. Yes, I have a weak first three rounds by ADP, but I have Gibbs, Harrison and a big piece of the Texans passing game which I think will lead the NFL in yardage. **8.11 Jaylen Warren** — I needed a second back, and Warren is one. He’s a good pass catcher and should see half the snaps in Pittsburgh. **9.2 Brian Robinson** — I like Robinson as a player, he’s the undisputed early-down option on what should be a better offense. (Think Ricky Pearsall, but at RB.) Too soon? Austin Ekeler will obviously see the passing-down work unless he proves totally washed up. The Robinson pick cost me David Njoku and Brock Bowers unfortunately, which was a gamble I knew I was making. **10.11 Jordan Mason** — At 29 and playing into the Super Bowl, Christian McCalfinjury was already a risk, and that he’s “expected” to play Monday night rather than 100 percent fine is worrying. Mason could be a league winner if McCaffrey goes down. **11.2 J.K. Dobbins** — The Mason pick cost me Jaleel McLaughlin, so I pivoted to Dobbins who still has a high ceiling if he can ever stay healthy. **12.11 Dallas Goedert** — Tight ends had flown off the board, but I was happy to get Goedert who has been valuable on a per-game basis the last couple years and is still just 29 which is late prime for the position. **13.2 Dalton Schultz** — Why not stack it even harder? The Texans could throw for 5,000-plus yards, and I have three of the four top targets and the QB. **14.11 Andrei Iosivas** — He’s gotten a lot of buzz in camp, seems like the No. 3 receiver right now, Tee Higgins is hurt and Ja’Marr Chase is still unsigned. **15.2 Cam Akers** — The Iosivas pick cost me Jalen McMillan who would have served as Godwin insurance, but Akers could easily take an aging Joe Mixon’s job. Maybe it’s too much Houston, but if it’s a top-three offense, I’m good with it. **16.11 Justin Fields** — The backup QBs had flown off the board, and Fields has too much upside to pass up. Plus he might even start Week 1 with Russell Wilson already hurt, and if he plays well, he might never look back. **17.2 Harrison Butker** — It’s either the based af kicker or a Younghoe for me. Plus he locked in a decent Week 1. **18.11 Dalvin Cook** — He had only 67 carries last year for a bad Jets offense. What if he isn’t as washed up as we think? He could easily win that job over Zeke Elliott and Rico Dowdle. **19.2 Jonnu Smith** — TE is my weakest position, so I took another upside gamble. What if he’s the Dolphins third target? **20.11 Giants Defense** — I think I took them in all four NFFC leagues. They get the Darnold Vikings at home and then Jayden Daniels in his second career start. And they have three Pro Bowl level pass rushers. **Roster By Position** **QB** CJ Stroud **RB** Jahmyr Gibbs/Jaylen Warren **WR** Marvin Harrison/Stefon Diggs/Tank Dell **TE** Dallas Goedert **FLEX** Chris Godwin **K** Harrison Butker **D** Giants **B** Jaxon Smith-Njigba/Brian Robinson/Jordan Mason/JK Dobbins/Dalton Schultz/Andrei Iosivas/Cam Akers/Justin Fields/Dalvin Cook/Jonnu Smith @ 6bae33c8:607272e8
2024-09-07 22:00:17Unfortunately, I didn’t have a ton of action in this game. I had the Packers with the points and am now 0-2 to start the week in my home picking pool. I had Xavier McKinney in the [Steak League](https://www.realmansports.com/p/steak-league-879?utm_source=publication-search) which was nice as like Roquan Smith he too started the year with a pick. But I was missing the principal scorers namely Saquon Barkley (maybe I let the nerds talk me out of him, as I had him [ranked highly initially](https://www.realmansports.com/p/running-back-rankings?utm_source=publication-search)) and Jayden Reed. Barkley I’m okay with because the potential for Jalen Hurts TDs was something I hadn’t initially considered, but Reed was a major error and in fact I passed on him for freaking Chris Godwin in my [Primetime last night](https://www.realmansports.com/p/nffc-primetime-fa7?utm_source=publication-search)! I had even argued with Alan Seslowsky that Reed was the [obvious choice](https://www.realmansports.com/p/week-1) among the Packers receivers. So seeing him go off (and he should have had a third TD, but it was called back due to something I’ve never seen before (both teams having 12 men on the field) was painful. Godwin is almost sure to have a terrible season now just to hammer home the lesson for me: Don’t worry about 10 spots of ADP, take the fucking guy you like. Stop listening to the consensus when you have a real lean. I don’t know how many times I need to learn this lesson, but apparently at least one more! - Reed looked like the most electrifying receiver on the field for the Packers. He had only six targets, not including the TD called back due to the penalties, but it’s obvious he’ll get more, and the handoff he took 33-yards to the house will incentivize them to do that again too. Year 2 after the surprisingly strong Year 1. He belongs in the second round now, along with Rashee Rice. - Christian Watson caught a TD and will be involved, but as great an athlete as he is he doesn’t have Reed’s football skills. Romeo Doubs is just a guy, but he’s reliable, and Dontayvion Wicks had a rough game — he’s an easy cut for me. - Jordan Love didn’t scramble much, and the Packers settled for a ton of field goals, but he looked okay. I think once they give Reed his 10 targets, Love will have his expected numbers. *(Just read on RotoWire that Love left the game for the last two plays with an unspecified leg injury, something not apparent on the 40-minute edited version. I thought they brought Malik Willis to throw a Hail Mary!* *Obviously, if he’s out for any length of time, all bets are off for the Packers receivers.)* - Josh Jacobs got stuffed in short yardage early, fumbled (though the Packers recovered), but ran well and hard late and even caught two passes. I have zero shares, but he looks like a fine pick for the late-third/early fourth. His backup Emanuel Wilson looked pretty spry too. Marshawn Lloyd is a cut now too in most formats. - Brayden Narveson missed a key kick off the post, but got a lot of attempts. He seems to have landed in the right place for a big season. - Jalen Hurts was a bit sloppy with two picks and a lost fumble, never got going on the ground (seemed like the Packers were really dedicated to taking that away), and the ass-smash didn’t work as well without Jason Kelce. But his receivers are so good, and Saquon Barkley is a big upgrade too. I would downgrade him a little though as his rushing TD projection maybe went from 10 to seven. - AJ Brown didn’t even look like he was running fast as he easily scored a 67-yard TD past the Packers defense. DeVonta Smith seemed to line up more in the slot and was automatic on key third-downs. There was no third receiver of which to speak, and even Dallas Goedert saw only five targets. - Barkley looked great, both on his TD catch, and as a rusher. As I said I don’t have any shares despite being high on him initially, but I love Barkley as a player (and bitcoiner!), and still kind of root for him. I hope he smashes this year.
@ 6bae33c8:607272e8
2024-09-07 22:00:17Unfortunately, I didn’t have a ton of action in this game. I had the Packers with the points and am now 0-2 to start the week in my home picking pool. I had Xavier McKinney in the [Steak League](https://www.realmansports.com/p/steak-league-879?utm_source=publication-search) which was nice as like Roquan Smith he too started the year with a pick. But I was missing the principal scorers namely Saquon Barkley (maybe I let the nerds talk me out of him, as I had him [ranked highly initially](https://www.realmansports.com/p/running-back-rankings?utm_source=publication-search)) and Jayden Reed. Barkley I’m okay with because the potential for Jalen Hurts TDs was something I hadn’t initially considered, but Reed was a major error and in fact I passed on him for freaking Chris Godwin in my [Primetime last night](https://www.realmansports.com/p/nffc-primetime-fa7?utm_source=publication-search)! I had even argued with Alan Seslowsky that Reed was the [obvious choice](https://www.realmansports.com/p/week-1) among the Packers receivers. So seeing him go off (and he should have had a third TD, but it was called back due to something I’ve never seen before (both teams having 12 men on the field) was painful. Godwin is almost sure to have a terrible season now just to hammer home the lesson for me: Don’t worry about 10 spots of ADP, take the fucking guy you like. Stop listening to the consensus when you have a real lean. I don’t know how many times I need to learn this lesson, but apparently at least one more! - Reed looked like the most electrifying receiver on the field for the Packers. He had only six targets, not including the TD called back due to the penalties, but it’s obvious he’ll get more, and the handoff he took 33-yards to the house will incentivize them to do that again too. Year 2 after the surprisingly strong Year 1. He belongs in the second round now, along with Rashee Rice. - Christian Watson caught a TD and will be involved, but as great an athlete as he is he doesn’t have Reed’s football skills. Romeo Doubs is just a guy, but he’s reliable, and Dontayvion Wicks had a rough game — he’s an easy cut for me. - Jordan Love didn’t scramble much, and the Packers settled for a ton of field goals, but he looked okay. I think once they give Reed his 10 targets, Love will have his expected numbers. *(Just read on RotoWire that Love left the game for the last two plays with an unspecified leg injury, something not apparent on the 40-minute edited version. I thought they brought Malik Willis to throw a Hail Mary!* *Obviously, if he’s out for any length of time, all bets are off for the Packers receivers.)* - Josh Jacobs got stuffed in short yardage early, fumbled (though the Packers recovered), but ran well and hard late and even caught two passes. I have zero shares, but he looks like a fine pick for the late-third/early fourth. His backup Emanuel Wilson looked pretty spry too. Marshawn Lloyd is a cut now too in most formats. - Brayden Narveson missed a key kick off the post, but got a lot of attempts. He seems to have landed in the right place for a big season. - Jalen Hurts was a bit sloppy with two picks and a lost fumble, never got going on the ground (seemed like the Packers were really dedicated to taking that away), and the ass-smash didn’t work as well without Jason Kelce. But his receivers are so good, and Saquon Barkley is a big upgrade too. I would downgrade him a little though as his rushing TD projection maybe went from 10 to seven. - AJ Brown didn’t even look like he was running fast as he easily scored a 67-yard TD past the Packers defense. DeVonta Smith seemed to line up more in the slot and was automatic on key third-downs. There was no third receiver of which to speak, and even Dallas Goedert saw only five targets. - Barkley looked great, both on his TD catch, and as a rusher. As I said I don’t have any shares despite being high on him initially, but I love Barkley as a player (and bitcoiner!), and still kind of root for him. I hope he smashes this year. @ 9358c676:9f2912fc
2024-09-07 18:50:14## Introduction The human immunodeficiency virus (HIV) began as a pandemic in the 1980s. In its early days, it was seen as a certain death sentence, a taboo associated with marginalized groups, and it highlighted the failures of poverty in accessing healthcare. Gradually, the struggle for life and the suffering of those who are no longer with us, including both famous and anonymous individuals, became visible. Today, 40 years later, HIV is presented as a chronic disease with effective treatment. **Patients living with HIV who receive appropriate treatment have no detectable virus in their circulating blood, enjoy a good quality of life, and are more concerned about other aspects of their health during medical consultations, almost forgetting their condition.** For these patients, daily treatment is the cure, similar to someone taking a pill every day for high blood pressure or diabetes. ## The Global Impact HIV is a lentivirus, a subgroup of retroviruses composed of RNA. The natural history of HIV infection involves an attack on the immune system, particularly targeting CD4 cells, where chronic deterioration can lead to the acquisition of infectious and oncological diseases that may be fatal over the years, resulting in acquired immunodeficiency syndrome (AIDS). Interestingly, there is a small group of people known as "elite controllers" who manage to control HIV infection without treatment and remain healthy for much of their lives, despite having a hidden deep viral reservoir. The primary modes of transmission are sexual, followed by blood and vertical transmission from mother to child, with the first mode predominating today. Today, in the downward trend of the HIV epidemic, **it is estimated that 39 million people are living with HIV worldwide.** Depending on the region, nearly half of this population belongs to at-risk groups, such as men who have sex with men (MSM), transgender individuals, sex workers, and people who inject drugs. These vulnerable groups are especially important for prevention efforts. However, little is done for prevention in the general population, which sometimes represents the other half of the cake of people living with HIV (PLWH). ## Breaking the Dogma: The Concept of Undetectable = Untransmittable (U=U) The introduction of highly effective antiretroviral therapy (HAART) in 1994 broke the curve of the HIV epidemic. The introduction of new medications with fewer side effects and greater effectiveness in controlling the virus has been crucial. In 2007, the launch of Raltegravir as the first viral integrase inhibitor marked a milestone in current treatments, **allowing patients to effectively control the virus within 3 to 6 months.** The positive impact of these treatments led health organizations to launch the concept of **undetectable = untransmittable (U=U)** to impact the general population and at-risk groups, updating the dogma and eradicating stigma: **a patient living with HIV who maintains an undetectable viral load in their blood through treatment will not transmit HIV sexually.** Although this concept has transformed the social dynamics and stigma surrounding the disease, adherence to treatment must be complete to achieve this new paradigm. ## Prophylaxis as a Method to Prevent HIV in Healthy Populations The correct use of condoms has been the cornerstone of HIV prevention and other sexually transmitted infections over the years. However, it is not the only tool available today and can be complemented for comprehensive sexual health. **Pre-exposure prophylaxis (PrEP)** is a novel strategy that involves administering antiretroviral medication to vulnerable groups before they are exposed to HIV (MSM, transgender individuals, sex workers, people who inject drugs). It involves taking medication daily, effectively reducing the risk of contracting HIV and providing protection to these groups. It is similar to taking a contraceptive pill daily. It has had a very positive impact on protecting these populations. In the Americas, it has been successfully implemented in the United States, Mexico, Peru, and Brazil. Other countries, although with some delay, are now implementing this strategy. **Post-exposure prophylaxis (PEP),** on the other hand, is a strategy that involves administering antiretroviral treatment after a potential exposure to HIV. If the treatment is administered within the first 72 hours and maintained for 4 weeks, the chances of contracting HIV decrease substantially. Both strategies have been remarkably successful in preventing HIV in at-risk populations and healthy populations, although their dissemination and awareness remain limited. https://image.nostr.build/08682bf763ade56741d8e4c8c6d870cb8d71ab7d72c605b9aa805af2234348ff.jpg ## The New Horizon: Long-Acting Antiretrovirals, HIV Vaccines, and Promising Therapies The introduction of viral integrase inhibitors and new nucleoside analogs in the last 15 years has allowed for the availability of safe drugs with minimal side effects in the treatment of HIV, **many of which are included in a single pill regimen per day.** However, the pharmaceutical industry continues to diversify the offerings in a healthy manner. **Cabotegravir is a new long-acting integrase inhibitor that is administered via injection.** Combined with Rilpivirine, it has proven to be effective and safe in the treatment of HIV, with injections every 2 months. This has revolutionized treatment for people who are tired of taking pills daily, as well as in PrEP, where effective prevention against HIV can be achieved with injections every 2 months for at-risk groups. Additionally, **subdermal implants of Islatravir,** a new long-acting nucleoside analog, are being tested as a PrEP strategy. Similar to monthly hormonal contraceptive injections or hormonal contraceptive implants, this strategy has proven effective in at-risk groups. Regarding the **HIV vaccine,** we have been developing it for over two decades, with advances and setbacks. While vaccines have shown promising results in terms of safety and antibody generation, we still need to await conclusive phase III results demonstrating their effectiveness in at-risk groups and the general population. ## The Eradication of HIV and Patients Cured Without Treatment While current treatment allows for the elimination of HIV from the bloodstream and sexual transmission, there remains a reservoir in some deep immune cells that have been infected by the retrovirus, which contain latent HIV DNA and have the potential to reactivate if daily treatment is interrupted. However, **there are patients who have managed to eliminate HIV from their bodies, including these deep cells, and HIV is undetectable upon discontinuation of treatment.** These cases are very rare, with only 7 to 8 individuals being the subject of intensive scientific study. Among them are the "Berlin patient" of Germany and "City of Hope patient" from Argentina. Some of these cases involved patients under effective HIV treatment who underwent suppressive chemotherapy for bone marrow transplants and managed to eliminate these deep cells with latent HIV DNA. Unfortunately, this treatment is not scalable for the entire HIV-positive population, both due to its cost and potential side effects. However, **"Shock and Kill" strategies** have been proposed, aiming to use monoclonal antibodies to activate these latent cells during HIV treatment, exposing them to antiretroviral medication for elimination, thereby eradicating these small reservoirs of HIV. ## WHO Goals The World Health Organization (WHO) has established clear objectives that are constantly updated to achieve the eradication of HIV in the population. **The updated goals of the WHO propose that, to end the HIV epidemic, three objectives must be met by the year 2025-2030:** 1. 95% of people living with HIV must be diagnosed through testing. 2. 95% of diagnosed individuals must be on highly effective antiretroviral therapy (HAART). 3. 95% of those on HAART must have an undetectable viral load in their blood. Developing and underdeveloped countries currently have an effectiveness rate for these strategies that disagree significantly. https://image.nostr.build/ac6693df57aaca6dac0b06b5db9eb1a2757e7c08511edb0f11617e12653d3db5.png ## Key Takeaways * HIV has a cure, and the cure is permanent treatment. * Treatment for HIV is free and accessible to the population, as it is a public health impact disease. * A person living with HIV who receives appropriate treatment will not transmit the virus sexually, will enjoy a full life without the disease, and can have children without HIV. * In the event of a potential HIV exposure (such as unprotected sexual contact with an infrequent partner), you can go to a hospital within the first 72 hours to receive treatment that will prevent HIV infection. * Just as we witnessed the eradication of smallpox from the face of the earth in 1978 due to scientific advances, we will live to see the eradication of HIV. ## Autor **Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community** npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj ## Resources 1. [World Health Organization (WHO)](https://www.who.int/en/health-topics/hiv-aids#tab=tab_1) 2. [Centers for Disease Control and Prevention (CDC)](https://www.cdc.gov/hiv/?CDC_AAref_Val=https://www.cdc.gov/hiv/default.html) 3. [UNAIDS](https://www.unaids.org/en) ## Bibliography 1. The natural history of HIV infection. DOI: 10.1097/COH.0b013e328361fa66 2. Changing Knowledge and Attitudes Towards HIV Treatment-as-Prevention and "Undetectable = Untransmittable": A Systematic Review. DOI: 10.1007/s10461-021-03296-8 3. Challenges of HIV diagnosis and management in the context of pre-exposure prophylaxis (PrEP), post-exposure prophylaxis (PEP), test and start and acute HIV infection: a scoping review. DOI: 10.1002/jia2.25419 4. Long-acting cabotegravir and rilpivirine dosed every 2 months in adults with HIV-1 infection (ATLAS-2M), 48-week results: a randomised, multicentre, open-label, phase 3b, non-inferiority study. DOI: 10.1016/S0140-6736(20)32666-0 5. Efficacy and safety of long-acting cabotegravir compared with daily oral tenofovir disoproxil fumarate plus emtricitabine to prevent HIV infection in cisgender men and transgender women who have sex with men 1 year after study unblinding: a secondary analysis of the phase 2b and 3 HPTN 083 randomised controlled trial. DOI: 10.1016/S2352-3018(23)00261-8 6. Safety and immunogenicity of a subtype C ALVAC-HIV (vCP2438) vaccine prime plus bivalent subtype C gp120 vaccine boost adjuvanted with MF59 or alum in healthy adults without HIV (HVTN 107): A phase 1/2a randomized trial. DOI: 10.1371/journal.pmed.1004360 7. Shock and kill within the CNS: A promising HIV eradication approach?. DOI: 10.1002/JLB.5VMR0122-046RRR
@ 9358c676:9f2912fc
2024-09-07 18:50:14## Introduction The human immunodeficiency virus (HIV) began as a pandemic in the 1980s. In its early days, it was seen as a certain death sentence, a taboo associated with marginalized groups, and it highlighted the failures of poverty in accessing healthcare. Gradually, the struggle for life and the suffering of those who are no longer with us, including both famous and anonymous individuals, became visible. Today, 40 years later, HIV is presented as a chronic disease with effective treatment. **Patients living with HIV who receive appropriate treatment have no detectable virus in their circulating blood, enjoy a good quality of life, and are more concerned about other aspects of their health during medical consultations, almost forgetting their condition.** For these patients, daily treatment is the cure, similar to someone taking a pill every day for high blood pressure or diabetes. ## The Global Impact HIV is a lentivirus, a subgroup of retroviruses composed of RNA. The natural history of HIV infection involves an attack on the immune system, particularly targeting CD4 cells, where chronic deterioration can lead to the acquisition of infectious and oncological diseases that may be fatal over the years, resulting in acquired immunodeficiency syndrome (AIDS). Interestingly, there is a small group of people known as "elite controllers" who manage to control HIV infection without treatment and remain healthy for much of their lives, despite having a hidden deep viral reservoir. The primary modes of transmission are sexual, followed by blood and vertical transmission from mother to child, with the first mode predominating today. Today, in the downward trend of the HIV epidemic, **it is estimated that 39 million people are living with HIV worldwide.** Depending on the region, nearly half of this population belongs to at-risk groups, such as men who have sex with men (MSM), transgender individuals, sex workers, and people who inject drugs. These vulnerable groups are especially important for prevention efforts. However, little is done for prevention in the general population, which sometimes represents the other half of the cake of people living with HIV (PLWH). ## Breaking the Dogma: The Concept of Undetectable = Untransmittable (U=U) The introduction of highly effective antiretroviral therapy (HAART) in 1994 broke the curve of the HIV epidemic. The introduction of new medications with fewer side effects and greater effectiveness in controlling the virus has been crucial. In 2007, the launch of Raltegravir as the first viral integrase inhibitor marked a milestone in current treatments, **allowing patients to effectively control the virus within 3 to 6 months.** The positive impact of these treatments led health organizations to launch the concept of **undetectable = untransmittable (U=U)** to impact the general population and at-risk groups, updating the dogma and eradicating stigma: **a patient living with HIV who maintains an undetectable viral load in their blood through treatment will not transmit HIV sexually.** Although this concept has transformed the social dynamics and stigma surrounding the disease, adherence to treatment must be complete to achieve this new paradigm. ## Prophylaxis as a Method to Prevent HIV in Healthy Populations The correct use of condoms has been the cornerstone of HIV prevention and other sexually transmitted infections over the years. However, it is not the only tool available today and can be complemented for comprehensive sexual health. **Pre-exposure prophylaxis (PrEP)** is a novel strategy that involves administering antiretroviral medication to vulnerable groups before they are exposed to HIV (MSM, transgender individuals, sex workers, people who inject drugs). It involves taking medication daily, effectively reducing the risk of contracting HIV and providing protection to these groups. It is similar to taking a contraceptive pill daily. It has had a very positive impact on protecting these populations. In the Americas, it has been successfully implemented in the United States, Mexico, Peru, and Brazil. Other countries, although with some delay, are now implementing this strategy. **Post-exposure prophylaxis (PEP),** on the other hand, is a strategy that involves administering antiretroviral treatment after a potential exposure to HIV. If the treatment is administered within the first 72 hours and maintained for 4 weeks, the chances of contracting HIV decrease substantially. Both strategies have been remarkably successful in preventing HIV in at-risk populations and healthy populations, although their dissemination and awareness remain limited. https://image.nostr.build/08682bf763ade56741d8e4c8c6d870cb8d71ab7d72c605b9aa805af2234348ff.jpg ## The New Horizon: Long-Acting Antiretrovirals, HIV Vaccines, and Promising Therapies The introduction of viral integrase inhibitors and new nucleoside analogs in the last 15 years has allowed for the availability of safe drugs with minimal side effects in the treatment of HIV, **many of which are included in a single pill regimen per day.** However, the pharmaceutical industry continues to diversify the offerings in a healthy manner. **Cabotegravir is a new long-acting integrase inhibitor that is administered via injection.** Combined with Rilpivirine, it has proven to be effective and safe in the treatment of HIV, with injections every 2 months. This has revolutionized treatment for people who are tired of taking pills daily, as well as in PrEP, where effective prevention against HIV can be achieved with injections every 2 months for at-risk groups. Additionally, **subdermal implants of Islatravir,** a new long-acting nucleoside analog, are being tested as a PrEP strategy. Similar to monthly hormonal contraceptive injections or hormonal contraceptive implants, this strategy has proven effective in at-risk groups. Regarding the **HIV vaccine,** we have been developing it for over two decades, with advances and setbacks. While vaccines have shown promising results in terms of safety and antibody generation, we still need to await conclusive phase III results demonstrating their effectiveness in at-risk groups and the general population. ## The Eradication of HIV and Patients Cured Without Treatment While current treatment allows for the elimination of HIV from the bloodstream and sexual transmission, there remains a reservoir in some deep immune cells that have been infected by the retrovirus, which contain latent HIV DNA and have the potential to reactivate if daily treatment is interrupted. However, **there are patients who have managed to eliminate HIV from their bodies, including these deep cells, and HIV is undetectable upon discontinuation of treatment.** These cases are very rare, with only 7 to 8 individuals being the subject of intensive scientific study. Among them are the "Berlin patient" of Germany and "City of Hope patient" from Argentina. Some of these cases involved patients under effective HIV treatment who underwent suppressive chemotherapy for bone marrow transplants and managed to eliminate these deep cells with latent HIV DNA. Unfortunately, this treatment is not scalable for the entire HIV-positive population, both due to its cost and potential side effects. However, **"Shock and Kill" strategies** have been proposed, aiming to use monoclonal antibodies to activate these latent cells during HIV treatment, exposing them to antiretroviral medication for elimination, thereby eradicating these small reservoirs of HIV. ## WHO Goals The World Health Organization (WHO) has established clear objectives that are constantly updated to achieve the eradication of HIV in the population. **The updated goals of the WHO propose that, to end the HIV epidemic, three objectives must be met by the year 2025-2030:** 1. 95% of people living with HIV must be diagnosed through testing. 2. 95% of diagnosed individuals must be on highly effective antiretroviral therapy (HAART). 3. 95% of those on HAART must have an undetectable viral load in their blood. Developing and underdeveloped countries currently have an effectiveness rate for these strategies that disagree significantly. https://image.nostr.build/ac6693df57aaca6dac0b06b5db9eb1a2757e7c08511edb0f11617e12653d3db5.png ## Key Takeaways * HIV has a cure, and the cure is permanent treatment. * Treatment for HIV is free and accessible to the population, as it is a public health impact disease. * A person living with HIV who receives appropriate treatment will not transmit the virus sexually, will enjoy a full life without the disease, and can have children without HIV. * In the event of a potential HIV exposure (such as unprotected sexual contact with an infrequent partner), you can go to a hospital within the first 72 hours to receive treatment that will prevent HIV infection. * Just as we witnessed the eradication of smallpox from the face of the earth in 1978 due to scientific advances, we will live to see the eradication of HIV. ## Autor **Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community** npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj ## Resources 1. [World Health Organization (WHO)](https://www.who.int/en/health-topics/hiv-aids#tab=tab_1) 2. [Centers for Disease Control and Prevention (CDC)](https://www.cdc.gov/hiv/?CDC_AAref_Val=https://www.cdc.gov/hiv/default.html) 3. [UNAIDS](https://www.unaids.org/en) ## Bibliography 1. The natural history of HIV infection. DOI: 10.1097/COH.0b013e328361fa66 2. Changing Knowledge and Attitudes Towards HIV Treatment-as-Prevention and "Undetectable = Untransmittable": A Systematic Review. DOI: 10.1007/s10461-021-03296-8 3. Challenges of HIV diagnosis and management in the context of pre-exposure prophylaxis (PrEP), post-exposure prophylaxis (PEP), test and start and acute HIV infection: a scoping review. DOI: 10.1002/jia2.25419 4. Long-acting cabotegravir and rilpivirine dosed every 2 months in adults with HIV-1 infection (ATLAS-2M), 48-week results: a randomised, multicentre, open-label, phase 3b, non-inferiority study. DOI: 10.1016/S0140-6736(20)32666-0 5. Efficacy and safety of long-acting cabotegravir compared with daily oral tenofovir disoproxil fumarate plus emtricitabine to prevent HIV infection in cisgender men and transgender women who have sex with men 1 year after study unblinding: a secondary analysis of the phase 2b and 3 HPTN 083 randomised controlled trial. DOI: 10.1016/S2352-3018(23)00261-8 6. Safety and immunogenicity of a subtype C ALVAC-HIV (vCP2438) vaccine prime plus bivalent subtype C gp120 vaccine boost adjuvanted with MF59 or alum in healthy adults without HIV (HVTN 107): A phase 1/2a randomized trial. DOI: 10.1371/journal.pmed.1004360 7. Shock and kill within the CNS: A promising HIV eradication approach?. DOI: 10.1002/JLB.5VMR0122-046RRR @ 41d0a715:9733c512
2024-09-07 15:27:14>Blaise Pascal: 'I have made this letter longer than usual, only because I have not had the time to make it shorter.' Some of you Stackers need to spend a little more time to make your posts short and sweet. Sometimes I realize a post doesn't even have a point after wasting time reading it. A long poorly written post is a waste of my time and yours too! originally posted at https://stacker.news/items/676136
@ 41d0a715:9733c512
2024-09-07 15:27:14>Blaise Pascal: 'I have made this letter longer than usual, only because I have not had the time to make it shorter.' Some of you Stackers need to spend a little more time to make your posts short and sweet. Sometimes I realize a post doesn't even have a point after wasting time reading it. A long poorly written post is a waste of my time and yours too! originally posted at https://stacker.news/items/676136 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46# Nostr: a quick introduction, attempt #2 Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else. Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services. (Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation). More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46# Nostr: a quick introduction, attempt #2 Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else. Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services. (Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation). More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback". @ 6bae33c8:607272e8
2024-09-06 08:16:48I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be. I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance. What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed. . . . In any event, let’s take a look at the slate: Here are the ownership numbers per [Officefootballpools.com](http://Officefootballpools.com). <img src="https://blossom.primal.net/4143b814092950ec28820e3d86d7608059d8a767b14eb9e2f19821b57ccb0856.png"> The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.) But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win. If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose. You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills. But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is *supposed* to be priced in, of course, but I don’t care.) I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now.
@ 6bae33c8:607272e8
2024-09-06 08:16:48I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be. I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance. What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed. . . . In any event, let’s take a look at the slate: Here are the ownership numbers per [Officefootballpools.com](http://Officefootballpools.com). <img src="https://blossom.primal.net/4143b814092950ec28820e3d86d7608059d8a767b14eb9e2f19821b57ccb0856.png"> The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.) But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win. If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose. You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills. But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is *supposed* to be priced in, of course, but I don’t care.) I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now. @ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes. In any event, it was an okay game, not great, but there were some interesting takeaways. - Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff. - Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask. - Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.) - Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more. - Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot. - Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown. - Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though. - Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game. - Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role. - After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG. - You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night.
@ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes. In any event, it was an okay game, not great, but there were some interesting takeaways. - Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff. - Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask. - Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.) - Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more. - Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot. - Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown. - Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though. - Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game. - Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role. - After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG. - You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night. @ 84b0c46a:417782f5
2024-09-06 00:26:32- 1:nan: - **2** - 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p) - 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw - 2 - 2 - 3 - 3 - 2 - 1 |1|2| |--|--| |test|:nan:| --- ### :nan: **:nan:** 1. 1 2. 2 - tet - tes 3. 3 1. 1 2. 2 > t >> te >>> test
@ 84b0c46a:417782f5
2024-09-06 00:26:32- 1:nan: - **2** - 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p) - 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw - 2 - 2 - 3 - 3 - 2 - 1 |1|2| |--|--| |test|:nan:| --- ### :nan: **:nan:** 1. 1 2. 2 - tet - tes 3. 3 1. 1 2. 2 > t >> te >>> test @ acc925af:db9fb0bb
2024-09-05 20:26:50While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good **Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:** # Prerequisites: 1. Twitter Developer Account 2. Nostr Wallet with NWC support (e.g., Alby, Nostrify) 3. Twitter API credentials (API key, API secret key, Access token, Access token secret) 4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library) ### Step 1: Set up Twitter API credentials > Create a Twitter Developer account and obtain API credentials > Install Tweepy using pip: pip install tweepy ### Step 2: Connect Nostr Wallet using NWC > Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify) > Set up the wallet and obtain the NWC credentials (e.g., public key, private key) ### Step 3: Create a Python script > Import Tweepy and nostr-client libraries > Authenticate with Twitter API using Tweepy > Connect to Nostr Wallet using NWC credentials > Define a function to send 21 satoshis for every like > Use Tweepy to stream likes and trigger the payment function `Python` script: ``` import tweepy from nostr_client import Client # Twitter API credentials twitter_api_key = "YOUR_API_KEY" twitter_api_secret_key = "YOUR_API_SECRET_KEY" twitter_access_token = "YOUR_ACCESS_TOKEN" twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET" # Nostr Wallet NWC credentials nwc_public_key = "YOUR_NWC_PUBLIC_KEY" nwc_private_key = "YOUR_NWC_PRIVATE_KEY" # Set up Tweepy auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key) auth.set_access_token(twitter_access_token, twitter_access_token_secret) api = tweepy.API(auth) # Set up Nostr Client nwc_client = Client() nwc_client.connect(nwc_public_key, nwc_private_key) # Define payment function def send_satoshis(): # Create a new Nostr event with 21 satoshis event = nwc_client.create_event(21) # Send the event to the Nostr network nwc_client.send_event(event) # Stream likes and trigger payment function class LikeStream(tweepy.StreamListener): def on_like(self, like): send_satoshis() stream = tweepy.Stream(auth, LikeStream()) stream.filter(track=["likes"]) ``` ##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._ originally posted at https://stacker.news/items/673795
@ acc925af:db9fb0bb
2024-09-05 20:26:50While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good **Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:** # Prerequisites: 1. Twitter Developer Account 2. Nostr Wallet with NWC support (e.g., Alby, Nostrify) 3. Twitter API credentials (API key, API secret key, Access token, Access token secret) 4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library) ### Step 1: Set up Twitter API credentials > Create a Twitter Developer account and obtain API credentials > Install Tweepy using pip: pip install tweepy ### Step 2: Connect Nostr Wallet using NWC > Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify) > Set up the wallet and obtain the NWC credentials (e.g., public key, private key) ### Step 3: Create a Python script > Import Tweepy and nostr-client libraries > Authenticate with Twitter API using Tweepy > Connect to Nostr Wallet using NWC credentials > Define a function to send 21 satoshis for every like > Use Tweepy to stream likes and trigger the payment function `Python` script: ``` import tweepy from nostr_client import Client # Twitter API credentials twitter_api_key = "YOUR_API_KEY" twitter_api_secret_key = "YOUR_API_SECRET_KEY" twitter_access_token = "YOUR_ACCESS_TOKEN" twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET" # Nostr Wallet NWC credentials nwc_public_key = "YOUR_NWC_PUBLIC_KEY" nwc_private_key = "YOUR_NWC_PRIVATE_KEY" # Set up Tweepy auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key) auth.set_access_token(twitter_access_token, twitter_access_token_secret) api = tweepy.API(auth) # Set up Nostr Client nwc_client = Client() nwc_client.connect(nwc_public_key, nwc_private_key) # Define payment function def send_satoshis(): # Create a new Nostr event with 21 satoshis event = nwc_client.create_event(21) # Send the event to the Nostr network nwc_client.send_event(event) # Stream likes and trigger payment function class LikeStream(tweepy.StreamListener): def on_like(self, like): send_satoshis() stream = tweepy.Stream(auth, LikeStream()) stream.filter(track=["likes"]) ``` ##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._ originally posted at https://stacker.news/items/673795 @ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity #GHOSTn If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs. Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see. Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be. Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes. Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
@ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity #GHOSTn If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs. Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see. Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be. Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes. Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do. @ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn. So what is encryption? It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with. > BEGINNER LEVEL - Encrypt your phone and computer. People walk around with their whole lives on their phone. Protect it. -phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password. After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive. -Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts. -Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault". -Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution. Awesome sauce. You have achieved minimum status. > ADVANCED LEVEL - Encrypt individual files. You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you. What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted. I will share with you one of my favorite small programs: Picocrypt. Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away. Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own. > EXPERT LEVEL - Encrypt containers and hidden containers. What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful. Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives. Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container. This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that. These features allow you to do all sorts of interesting things only limited by your need and imagination. What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun. > NEMO - Failsafe Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot. Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone. > > Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc > Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn. So what is encryption? It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with. > BEGINNER LEVEL - Encrypt your phone and computer. People walk around with their whole lives on their phone. Protect it. -phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password. After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive. -Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts. -Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault". -Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution. Awesome sauce. You have achieved minimum status. > ADVANCED LEVEL - Encrypt individual files. You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you. What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted. I will share with you one of my favorite small programs: Picocrypt. Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away. Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own. > EXPERT LEVEL - Encrypt containers and hidden containers. What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful. Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives. Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container. This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that. These features allow you to do all sorts of interesting things only limited by your need and imagination. What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun. > NEMO - Failsafe Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot. Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone. > > Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc > Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is. @ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track. *(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)* 1. **Stefon Diggs leads the Texans in targets, catches and receiving yards** Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year. 2. **CJ Stroud leads the NFL is passing yards** This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2. 3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)** Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens. 4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR** Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020. 5. **The Giants will field a top-10 fantasy defense.** I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers. 6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt** I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua. 7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)** Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time. 8. **Dalvin Cook will lead the Cowboys in rushing yards** Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.) 9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.** He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.) 10. **Dalton Kincaid (TE4) will lead all TE in catches** I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. 11. **Some of these predictions will be wrong** No one’s perfect, but you never want to get shut out.
@ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track. *(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)* 1. **Stefon Diggs leads the Texans in targets, catches and receiving yards** Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year. 2. **CJ Stroud leads the NFL is passing yards** This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2. 3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)** Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens. 4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR** Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020. 5. **The Giants will field a top-10 fantasy defense.** I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers. 6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt** I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua. 7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)** Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time. 8. **Dalvin Cook will lead the Cowboys in rushing yards** Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.) 9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.** He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.) 10. **Dalton Kincaid (TE4) will lead all TE in catches** I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. 11. **Some of these predictions will be wrong** No one’s perfect, but you never want to get shut out. @ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot. Here are the results: ([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream)) <img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png"> **1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount. **2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead. **3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there. **4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target. **5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone. **6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year. **7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position. **8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR. **9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.) **10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.) **11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks. **12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build. **13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job. **14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert. **15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old. **16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down. **17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too. **18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie. **19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.) **20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence. **Roster By Position** **QB** Anthony Richardson **RB** James Conner/Jaleel McLaughlin **WR** Ja’Marr Chase/Drake London/DeVonta Smith **TE** Dalton Kincaid **FLEX** Stefon Diggs **K** Younghoe Koo **D** Giants **Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
@ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot. Here are the results: ([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream)) <img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png"> **1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount. **2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead. **3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there. **4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target. **5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone. **6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year. **7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position. **8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR. **9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.) **10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.) **11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks. **12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build. **13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job. **14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert. **15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old. **16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down. **17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too. **18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie. **19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.) **20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence. **Roster By Position** **QB** Anthony Richardson **RB** James Conner/Jaleel McLaughlin **WR** Ja’Marr Chase/Drake London/DeVonta Smith **TE** Dalton Kincaid **FLEX** Stefon Diggs **K** Younghoe Koo **D** Giants **Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston @ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy. You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start. Don't worry, here are some absolute beginner first steps that will make a big difference. > 1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. > 2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data. BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS. > 3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. > 4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. > 5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice. > BONUS TIP: Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population. > OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security. What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone. The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure? There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
@ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy. You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start. Don't worry, here are some absolute beginner first steps that will make a big difference. > 1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. > 2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data. BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS. > 3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. > 4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. > 5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice. > BONUS TIP: Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population. > OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security. What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone. The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure? There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later. @ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md) And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker ```sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0 ``` ## New Features ### Support for NIP-49 encrypted nsec Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...) There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps  ### Blindspot feeds There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing  ### NIP-42 Relay authentication The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings  ### Wasm relay and event verification The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view  The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting  ### Thread tabs Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note   ### Wiki articles Its not feature complete but you can now view and edit wiki articles in the app  ### Finished the launchpad The launchpad is now usable and shows the latest notifications, messages, streams, and tools  ### Blossom uploads The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings  And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`  ### Task Manager There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app  You can see what relays the app is currently connected to  And which relays are requesting NIP-42 authentication  ## Bug fixes - Fix null relay hints in DMs - Fix users own events being hidden by muted words - Fix random events showing up as DM messages - Fix app prompting NIP-07 extension to unlock when app opens - Remove corsproxy.io as default service for CORS proxy
@ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md) And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker ```sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0 ``` ## New Features ### Support for NIP-49 encrypted nsec Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...) There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps  ### Blindspot feeds There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing  ### NIP-42 Relay authentication The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings  ### Wasm relay and event verification The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view  The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting  ### Thread tabs Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note   ### Wiki articles Its not feature complete but you can now view and edit wiki articles in the app  ### Finished the launchpad The launchpad is now usable and shows the latest notifications, messages, streams, and tools  ### Blossom uploads The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings  And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`  ### Task Manager There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app  You can see what relays the app is currently connected to  And which relays are requesting NIP-42 authentication  ## Bug fixes - Fix null relay hints in DMs - Fix users own events being hidden by muted words - Fix random events showing up as DM messages - Fix app prompting NIP-07 extension to unlock when app opens - Remove corsproxy.io as default service for CORS proxy @ 3b7fc823:e194354f
2024-09-01 19:21:09Testing articles on Yakkihonne
@ 3b7fc823:e194354f
2024-09-01 19:21:09Testing articles on Yakkihonne @ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend, it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart. As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you: * What causes the discomfort that drives you out of the walled garden onto the open sea? * Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall? * What are you hoping to find on the open sea that walled gardens cannot provide? * What are you willing to sacrifice for freedom (of speech)? * What will you need to keep the ship afloat? * How will you react when you find yourself in the middle of a storm? I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over. This is about building a new world, an open world without walled gardens and data silos. Onwards!
@ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend, it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart. As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you: * What causes the discomfort that drives you out of the walled garden onto the open sea? * Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall? * What are you hoping to find on the open sea that walled gardens cannot provide? * What are you willing to sacrifice for freedom (of speech)? * What will you need to keep the ship afloat? * How will you react when you find yourself in the middle of a storm? I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over. This is about building a new world, an open world without walled gardens and data silos. Onwards! @ b2d670de:907f9d4a
2024-08-30 22:52:53# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
@ b2d670de:907f9d4a
2024-08-30 22:52:53# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url). @ a723805c:0342dc9c
2024-08-30 12:16:55When I first stumbled upon Nostr back in February 2023, I was immediately drawn to the network's unique design. It was like stumbling across a hidden architectural gem - something so intricate and beautifully crafted that most people might walk past without a second glance. But for those who truly saw it, Nostr's design was mesmerizing. I didn’t know exactly what I was diving into, but I felt enthusiasm because I knew this was something entirely different from the usual legacy social media attempts at connecting people. One of the first things that struck me was the people. Nostr wasn't just a network; it was a gathering place for a group of curious outlaws, all eager to try something new and break away from the norm. The platforms and interfaces were a bit scrappy and buggy in those early days, but that didn't matter. What stood out was the spirit of the community, people kept coming back, filled with cheer and optimism. Even more impressive was the willingness to help each other out. It wasn't just about using the platform; it was about collectively figuring it out together. This was the seed of a constructive culture that was starting to take root. Coming from the Twitter culture, I noticed something refreshing: on Nostr, people referred to each other as friends, not followers. Twitter often felt like a toxic swamp of influencers, each trying to outdo the other with proclamations and status games. Sure, there were helpful people on Twitter, but more often than not, their "help" came with strings attached, promoting a Gumroad book, pushing a newsletter subscription, always with a personal incentive lurking in the background. Nostr, on the other hand, was different. Here, people helped each other just for the sake of it, with no expectation of anything in return. The spirit of giving was genuine, and it was contagious. Fast forward to today, and that same spirit is alive and well. Just take a glance at the #introductions tag, and you'll see it in action: friendly users, eagerly welcoming new members into the ecosystem, offering to lend a hand, and making everyone feel at home. The constructive culture of Nostr, built on a foundation of genuine camaraderie and selflessness, is as vibrant now as it was back in the early days. This isn't just a network; it's a community that thrives on cooperation, curiosity, and the simple joy of helping others. Nostr isn't about chasing clout or boosting follower counts; it's about building something meaningful together, one interaction at a time. And that's what makes it truly special.
@ a723805c:0342dc9c
2024-08-30 12:16:55When I first stumbled upon Nostr back in February 2023, I was immediately drawn to the network's unique design. It was like stumbling across a hidden architectural gem - something so intricate and beautifully crafted that most people might walk past without a second glance. But for those who truly saw it, Nostr's design was mesmerizing. I didn’t know exactly what I was diving into, but I felt enthusiasm because I knew this was something entirely different from the usual legacy social media attempts at connecting people. One of the first things that struck me was the people. Nostr wasn't just a network; it was a gathering place for a group of curious outlaws, all eager to try something new and break away from the norm. The platforms and interfaces were a bit scrappy and buggy in those early days, but that didn't matter. What stood out was the spirit of the community, people kept coming back, filled with cheer and optimism. Even more impressive was the willingness to help each other out. It wasn't just about using the platform; it was about collectively figuring it out together. This was the seed of a constructive culture that was starting to take root. Coming from the Twitter culture, I noticed something refreshing: on Nostr, people referred to each other as friends, not followers. Twitter often felt like a toxic swamp of influencers, each trying to outdo the other with proclamations and status games. Sure, there were helpful people on Twitter, but more often than not, their "help" came with strings attached, promoting a Gumroad book, pushing a newsletter subscription, always with a personal incentive lurking in the background. Nostr, on the other hand, was different. Here, people helped each other just for the sake of it, with no expectation of anything in return. The spirit of giving was genuine, and it was contagious. Fast forward to today, and that same spirit is alive and well. Just take a glance at the #introductions tag, and you'll see it in action: friendly users, eagerly welcoming new members into the ecosystem, offering to lend a hand, and making everyone feel at home. The constructive culture of Nostr, built on a foundation of genuine camaraderie and selflessness, is as vibrant now as it was back in the early days. This isn't just a network; it's a community that thrives on cooperation, curiosity, and the simple joy of helping others. Nostr isn't about chasing clout or boosting follower counts; it's about building something meaningful together, one interaction at a time. And that's what makes it truly special. @ 6389be64:ef439d32
2024-08-29 18:35:53Editing of profiles and projects seems easier and laid out better and the overall responsiveness of the website feels greatly improved. The Analytics section tho . . . whoo doggie! What an upgrade. Try it out at geyser.fund originally posted at https://stacker.news/items/665891
@ 6389be64:ef439d32
2024-08-29 18:35:53Editing of profiles and projects seems easier and laid out better and the overall responsiveness of the website feels greatly improved. The Analytics section tho . . . whoo doggie! What an upgrade. Try it out at geyser.fund originally posted at https://stacker.news/items/665891 @ bf7973ed:841ad12a
2024-08-29 17:50:48Posted using obsidian plugin https://obsidian.md/plugins?search=nostr#
@ bf7973ed:841ad12a
2024-08-29 17:50:48Posted using obsidian plugin https://obsidian.md/plugins?search=nostr# @ 1ec45473:d38df139
2024-08-29 09:55:11Preston Pysh posted this event this morning:  Behind the scenes, the nostr event looks like this: ``` Event = { "id":"a6fa7e1a73ce70c6fb01584a0519fd29788e59d9980402584e7a0af92cf0474a", "pubkey":"85080d3bad70ccdcd7f74c29a44f55bb85cbcd3dd0cbb957da1d215bdb931204", "created_at":1724494504, "kind":1, "tags":[ [ "p", "6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb", "", "mention" ], [ "p", "77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c", "", "mention" ], [ "p", "c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1", "", "mention" ], [ "p", "50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63", "", "mention" ], [ "p", "20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5", "", "mention" ], [ "p", "273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2", "", "mention" ], [ "t", "BH2024" ] ], "content":"Awesome Freedom Panel with...", "sig":"2b64e461cd9f5a7aa8abbcbcfd953536f10a334b631a352cd4124e8e187c71aad08be9aefb6a68e5c060e676d06b61c553e821286ea42489f9e7e7107a1bf79a" } ``` In nostr, all events have this form, so once you become familiar with the nostr event structure, things become pretty easy. Look at the "tags" key. There are six "p" tags (pubkey) and one "t" tag (hashtag). The p tags are public keys of people that are mentioned in the note. The t tags are for hashtags in the note. It is common when working with NOSTR that you have to extract out certain tags. Here are some examples of how to do that with what are called JavaScript Array Methods: ### Find the first "p" tag element: ``` Event.tags.find(item => item[0] === 'p') [ 'p', '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '', 'mention' ] ``` ### Same, but just return the pubkey": ``` Event.tags.find(item => item[0] === 'p')[1] '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb' ``` ### Filter the array so I only get "p" tags: ``` Event.tags.filter(item => item[0] === 'p') [ [ 'p', '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '', 'mention' ], [ 'p', '77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c', '', 'mention' ], [ 'p', 'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1', '', 'mention' ], [ 'p', '50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63', '', 'mention' ], [ 'p', '20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5', '', 'mention' ], [ 'p', '273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2', '', 'mention' ] ] ``` ### Return an array with only the pubkeys in the "p" tags: ``` Event.tags.filter(item => item[0] === 'p').map(item => item[1]) [ '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c', 'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1', '50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63', '20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5', '273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2' ] ```
@ 1ec45473:d38df139
2024-08-29 09:55:11Preston Pysh posted this event this morning:  Behind the scenes, the nostr event looks like this: ``` Event = { "id":"a6fa7e1a73ce70c6fb01584a0519fd29788e59d9980402584e7a0af92cf0474a", "pubkey":"85080d3bad70ccdcd7f74c29a44f55bb85cbcd3dd0cbb957da1d215bdb931204", "created_at":1724494504, "kind":1, "tags":[ [ "p", "6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb", "", "mention" ], [ "p", "77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c", "", "mention" ], [ "p", "c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1", "", "mention" ], [ "p", "50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63", "", "mention" ], [ "p", "20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5", "", "mention" ], [ "p", "273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2", "", "mention" ], [ "t", "BH2024" ] ], "content":"Awesome Freedom Panel with...", "sig":"2b64e461cd9f5a7aa8abbcbcfd953536f10a334b631a352cd4124e8e187c71aad08be9aefb6a68e5c060e676d06b61c553e821286ea42489f9e7e7107a1bf79a" } ``` In nostr, all events have this form, so once you become familiar with the nostr event structure, things become pretty easy. Look at the "tags" key. There are six "p" tags (pubkey) and one "t" tag (hashtag). The p tags are public keys of people that are mentioned in the note. The t tags are for hashtags in the note. It is common when working with NOSTR that you have to extract out certain tags. Here are some examples of how to do that with what are called JavaScript Array Methods: ### Find the first "p" tag element: ``` Event.tags.find(item => item[0] === 'p') [ 'p', '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '', 'mention' ] ``` ### Same, but just return the pubkey": ``` Event.tags.find(item => item[0] === 'p')[1] '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb' ``` ### Filter the array so I only get "p" tags: ``` Event.tags.filter(item => item[0] === 'p') [ [ 'p', '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '', 'mention' ], [ 'p', '77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c', '', 'mention' ], [ 'p', 'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1', '', 'mention' ], [ 'p', '50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63', '', 'mention' ], [ 'p', '20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5', '', 'mention' ], [ 'p', '273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2', '', 'mention' ] ] ``` ### Return an array with only the pubkeys in the "p" tags: ``` Event.tags.filter(item => item[0] === 'p').map(item => item[1]) [ '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c', 'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1', '50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63', '20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5', '273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2' ] ``` @ 460c25e6:ef85065c
2024-08-29 01:07:22If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one. ## Public Home/Outbox Relays Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**. Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience. This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts. ## Public Inbox Relays This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out. Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience. This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here. ## DM Inbox Relays These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them. Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy. Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a hidden, but public relay if you want DM notifications from our servers. Make sure to add at least one public relay if you want to see DM notifications. ## Private Home Relays Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools. Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa. ## Search relays: This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com ## Local Relays: This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option. ## General Relays: This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each. Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible. Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them. ## My setup Here's what I use: 1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself. 2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription. 3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription. 4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country. 5. Download Citrine to your phone. Then, on your relay lists, put: Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. - <your.relay>.nostr1.com Public Inbox Relays - nos.lol or an in-country relay - <your.relay>.nostr1.com DM Inbox Relays - inbox.nostr.wine - <your.relay>.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) - <your.relay>.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com Local Relays - ws://localhost:4869 (Citrine) General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom And a few of the recommended relays from Amethyst. ## Final Considerations Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
@ 460c25e6:ef85065c
2024-08-29 01:07:22If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one. ## Public Home/Outbox Relays Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**. Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience. This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts. ## Public Inbox Relays This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out. Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience. This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here. ## DM Inbox Relays These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them. Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy. Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a hidden, but public relay if you want DM notifications from our servers. Make sure to add at least one public relay if you want to see DM notifications. ## Private Home Relays Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools. Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa. ## Search relays: This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com ## Local Relays: This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option. ## General Relays: This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each. Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible. Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them. ## My setup Here's what I use: 1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself. 2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription. 3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription. 4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country. 5. Download Citrine to your phone. Then, on your relay lists, put: Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. - <your.relay>.nostr1.com Public Inbox Relays - nos.lol or an in-country relay - <your.relay>.nostr1.com DM Inbox Relays - inbox.nostr.wine - <your.relay>.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) - <your.relay>.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com Local Relays - ws://localhost:4869 (Citrine) General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom And a few of the recommended relays from Amethyst. ## Final Considerations Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies. @ b83a28b7:35919450
2024-08-28 15:03:25Join nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and me for episode 76 of nostr:npub14kw5ygpl6fyqagh9cnrytyaqyacg46lzkq42vz7hk8txdk49kzxs04j7y0 this Friday, August 30th at 3pm ET (UTC -4) Our guest this week is nostr:npub1xv8mzscll8vvy5rsdw7dcqtd2j268a6yupr6gzqh86f2ulhy9kkqmclk3x from nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm who joins us to provide the lowdown on the recently launched Alby Hub You don't want to miss this one! Set your blockclocks! https://nostrnests.com/ [This is our first show announcement made from a long-form client, in keeping with QW and my #otherstuffchallenge]
@ b83a28b7:35919450
2024-08-28 15:03:25Join nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and me for episode 76 of nostr:npub14kw5ygpl6fyqagh9cnrytyaqyacg46lzkq42vz7hk8txdk49kzxs04j7y0 this Friday, August 30th at 3pm ET (UTC -4) Our guest this week is nostr:npub1xv8mzscll8vvy5rsdw7dcqtd2j268a6yupr6gzqh86f2ulhy9kkqmclk3x from nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm who joins us to provide the lowdown on the recently launched Alby Hub You don't want to miss this one! Set your blockclocks! https://nostrnests.com/ [This is our first show announcement made from a long-form client, in keeping with QW and my #otherstuffchallenge] @ e83b66a8:b0526c2b
2024-08-28 10:56:55The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud. Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data. There is a different way. NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol. The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms. Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid. Secondly as a user, you don’t have an account, you have a private key which is used to secure your data. Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key. Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays. All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it. Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key. Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content. Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions. Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant. As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models. The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not. NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment. From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed. While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops. If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here: https://primal.net/downloads It will create a private key for you and setup a Bitcoin wallet. Once you have done this you can visit me here: nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already. NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here: nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Or you can see his account like this: https://primal.net/jack Edward Snowden is also on the platform and you can find him here: https://primal.net/Snowden NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation. Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/ Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus or Amethyst for Android: https://nostrapps.com/amethyst The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it. Some of the more interesting projects right now are: https://www.0xchat.com/#/ – Private messaging – think WhatsApp https://zap.stream/ – Video streaming https://fountain.fm/ – Podcasting https://wavlake.com/ – Music streaming https://shopstr.store/ – Online shop https://npub.pro/ – Website creation tool https://nostr.build/ – Media and file storage https://relay.tools/ – Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user – Creator tools Remember, the same keys you created for Primal can be used across the whole ecosystem.
@ e83b66a8:b0526c2b
2024-08-28 10:56:55The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud. Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data. There is a different way. NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol. The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms. Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid. Secondly as a user, you don’t have an account, you have a private key which is used to secure your data. Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key. Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays. All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it. Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key. Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content. Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions. Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant. As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models. The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not. NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment. From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed. While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops. If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here: https://primal.net/downloads It will create a private key for you and setup a Bitcoin wallet. Once you have done this you can visit me here: nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already. NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here: nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Or you can see his account like this: https://primal.net/jack Edward Snowden is also on the platform and you can find him here: https://primal.net/Snowden NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation. Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/ Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus or Amethyst for Android: https://nostrapps.com/amethyst The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it. Some of the more interesting projects right now are: https://www.0xchat.com/#/ – Private messaging – think WhatsApp https://zap.stream/ – Video streaming https://fountain.fm/ – Podcasting https://wavlake.com/ – Music streaming https://shopstr.store/ – Online shop https://npub.pro/ – Website creation tool https://nostr.build/ – Media and file storage https://relay.tools/ – Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user – Creator tools Remember, the same keys you created for Primal can be used across the whole ecosystem. @ b83a28b7:35919450
2024-08-27 18:53:46On last week's episode of Plebchain Radio, QW and I announced something unusual - we would be taking a week off posting kind 1 notes on the Twitter clone clients - Primal, Damus, Nostur, etc. The clock started right after our show was posted on Friday, August 23rd and ends with show this Friday, August 30th. https://video.nostr.build/741cd7a0dd33e1ce815490d14069af96579ce47c92ea04240592c7bbb2de3a65.mp4 The idea behind the challenge is to see how much we can participate in the network without resorting to it's most accessible form of communication - kind 1 notes (the equivalent of tweets/replies). Halfway into the challenge, we've boosted and commented on shows on Fountain, zapped songs on Wavlake, commented on recipes on zap.cooking, watched videos on zap.stream and tunestr, and written the odd long-form note (oh, alright, just this one so far). It's been fun, but has also created an odd sense of sensory deprivation. We will share more details on our experience on this week's Plebchain Radio episode. Right, I'm off to explore the rest of the other-stuff-verse. I'd urge everyone to give this challenge a try. It might change how you view nostr.
@ b83a28b7:35919450
2024-08-27 18:53:46On last week's episode of Plebchain Radio, QW and I announced something unusual - we would be taking a week off posting kind 1 notes on the Twitter clone clients - Primal, Damus, Nostur, etc. The clock started right after our show was posted on Friday, August 23rd and ends with show this Friday, August 30th. https://video.nostr.build/741cd7a0dd33e1ce815490d14069af96579ce47c92ea04240592c7bbb2de3a65.mp4 The idea behind the challenge is to see how much we can participate in the network without resorting to it's most accessible form of communication - kind 1 notes (the equivalent of tweets/replies). Halfway into the challenge, we've boosted and commented on shows on Fountain, zapped songs on Wavlake, commented on recipes on zap.cooking, watched videos on zap.stream and tunestr, and written the odd long-form note (oh, alright, just this one so far). It's been fun, but has also created an odd sense of sensory deprivation. We will share more details on our experience on this week's Plebchain Radio episode. Right, I'm off to explore the rest of the other-stuff-verse. I'd urge everyone to give this challenge a try. It might change how you view nostr. @ bcbb3e40:a494e501
2024-08-27 18:33:08|| |:-:| |Escena del corto de animación [«I, Pet Goat II»](https://youtu.be/6n_xCI-peq0) del estudio Heliofant, en el que una pantalla con un siniestro personaje en su interior está conectada al cráneo hueco de otro personaje.| Los que tenemos ya algunos años y empezamos a peinar canas, con toda la profundidad de enfoque y perspectiva que ello implica, hemos vivido cambios muy trascendentales en las últimas décadas. De alguna manera, aquello que considerábamos imposible o, en su defecto, poco probable, se ha venido materializando en el tiempo causando nuestro asombro y, por qué no decirlo, nuestro temor e inquietud. [Los acontecimientos vividos a raíz de la **Plandemia**](https://hiperbolajanus.com/posts/presentacion-despues-virus-boris-nad/), por ejemplo, nos hicieron ver claramente que el sistema ha abandonado sus posiciones anteriores, el disimulo que caracterizaba a su proceder, ese velo de «normalidad», para intercambiarlo por otra «normalidad», una «nueva normalidad» en la que todo es posible, y esto en el sentido más negativo que pueda imaginarse. Durante el último lustro hemos asistido a encierros obligatorios, a la imposición de pinchazos con sustancias desconocidas de las que nadie se hacía (ni se sigue haciendo) responsable y cuyos efectos nocivos se han constatado con posterioridad, a un creciente y desmesurado control social a través de diversas vías, que ha colocado el mismo concepto de «Verdad» y «Realidad» en entredicho, sustituyendo la Verdad en un sentido eminente, metafísico si se quiere, en la presa de un relato, de una construcción ideológica de ínfimo nivel intelectual diseñado para mantener a la masa en el redil, acallando cualquier tipo de discrepancia, y especialmente de disidencia, que pudiera romper con ese relato hegemónico, custodiado como si del Santo Grial se tratase, frente a cualquier evidencia objetiva. De hecho, [se ha hablado mucho de la **«posverdad»**](https://hiperbolajanus.com/posts/breviarios-contra-modernidad/). Pero todos estos temas no son nuevos, pese a que su concreción práctica en los tiempos presentes, con las democracias de libre mercado, que venían presumiendo de su «estado de derecho», de sus «garantías» y «libertades», sino que ya venían anunciados en cierta tradición literaria que podemos remontar a las décadas 30-40 del pasado siglo. Ahí tenemos a dos notables autores: **Aldous Huxley** (1894-1963) y **George Orwell** (1903-1950), autores de [_Un mundo feliz_](https://amzn.to/3MnR1Gz) y [_1984_](https://hiperbolajanus.com/posts/resena-1984-de-george-orwell/) respectivamente. Ambos trabajos pueden encuadrarse dentro de esa corriente distópica tan característica donde también podríamos encuadrar, entre otras obras, aquella de **Ray Bradbury** (1920-2012), la famosa [_Fahrenheit 451_](https://amzn.to/4dDfAuV). No obstante, vamos a fijar nuestra atención en los dos primeros autores, Huxley y Orwell, cuyos modelos de dictadura propuestos difieren significativamente entre sí, mientras que el primero nos presenta una «dictadura blanda» o «dulce», edulcorada por las drogas y el transhumanismo, el segundo nos dibuja un orden dictatorial cruel y sádico, enfermizo e investido de una diabólica voluntad de poseer al individuo en su interior más profundo. || |:-:| |George Orwell y Aldous Huxley, los autores de literatura fantástica más visionarios y famosos del siglo XX| Tras la publicación de _1984_, Huxley, agradecía a Orwell el envío de su mítica obra y en una especie de predicción o vaticinio de futuro confrontaba esta obra con la suya propia: «La filosofía de la clase en el poder en 1984 es una forma de sadismo llevado a las consecuencias extremas y hacia su solución lógica: ir más allá del sexo y negarlo. Creo que las oligarquías encontrarán formas más eficientes de gobernar y satisfacer su sed de poder y serán similares a las descritas en Un mundo feliz». Siendo fiel a los dictámenes de su propia obra, Huxley consideraba que se impondría una «dictadura dulce», con el uso masivo y generalizado de drogas farmacológicas y técnicas de hipnotismo a través del desarrollo de poderosas herramientas psicológicas para plegar el control de la mente y la voluntad de las masas al poder imperante. De hecho, este proceso era calificado por Huxley como «la última revolución». Además preconizaba una caída de las masas en un estado de esclavitud voluntaria y adaptada, formulada en aras de una mayor eficiencia en el ejercicio del poder. Otros autores posteriores como **Elémire Zolla** (1926-2002), se hacían eco del poder de la hipnosis y de la manipulación de las mentes como un proyecto real a gran escala, con siniestros propósitos. Y de algún modo el [liberal-capitalismo ha utilizado este tipo de técnicas a través del mercado](https://hiperbolajanus.com/libros/mos-maiorum-7/), con la estandarización de comportamientos y modas a través del uso de la publicidad en una voluntad de estandarización y uniformización con una voluntad inequívoca de alcanzar la psique profunda del hombre, el subconsciente, para dominar al hombre allí donde el pensamiento lógico y la voluntad se encuentran desdibujados y anulados. En la misma dirección tenemos a **Herbert Marcuse** (1898-1979), en cuya obra también vemos alusiones a las agresiones y limitaciones de la libertad en [el contexto de la civilización industrial avanzada como parte del progreso técnico](https://hiperbolajanus.com/posts/resena-hanno-cambiato-faccia/). Empieza a delinear en su obra la imagen de un régimen totalitario en el que todos los aspectos de la vida del individuo, y especialmente del pueblo trabajador, se encuentran alienados, encerrados en la lógica del producir y consumir, sin resistencia posible. El hombre reducido a esa condición y cuya única libertad se reduce a elegir entre diferentes productos. En este sentido Marcuse condenaba a la tecnología y delata sus cualidades totalmente funcionales a una ideología de poder. Este es el sentido que otorga a su «hombre unidimensional» cuya definición antropológica se desarrolla sobre un único plano, y bajo ese condicionamiento mental que vemos en la obra orwelliana. De algún modo, a partir de cierto momento, las herramientas de control de masas se hacen más sutiles, y sustituyen la violencia que el incipiente Estado liberal utilizaba durante el siglo XIX para mantener el orden frente a revueltas o revoluciones adversas, por el uso de elementos de control social y vigilancia, y esto en los últimos tiempos se ha venido desarrollando bajo múltiples excusas, como, por ejemplo, la denominada «Agenda verde», que bajo la premisa de unos hipotéticos cambios dramáticos y catastróficos de raíz antropogénica en el devenir terrestre, debemos aceptar las «ciudades de los 15 minutos», funcionando como «guetos» con contingentes de población estabulados, con movimientos limitados en un espacio reducido, donde prácticamente haya que pedir permiso para salir. Todo por salvar el planeta, por esa ridícula y grotesca teoría de la «huella de carbono», promocionada por bancos y otras instituciones del sistema. La estrategia del miedo ha dado frutos siguiendo el plan de las élites globalistas, lo vimos con la _Plandemia_ y ha seguido manteniendo su continuidad bajo la apariencia de diferentes amenazas, la emergencia permanente que supone una guerra, como la que [la OTAN libra con Rusia utilizando a Ucrania como ariete](https://hiperbolajanus.com/libros/geopolitica-rusia-aleksandr-duguin/). Las masas, desestabilizadas han venido aceptando todas las imposiciones en nombre de un «consenso común», convirtiéndose en vigilantes solícitos y aceptando restricciones que antes del 2020 nunca hubieran aceptado. En este contexto, filósofos como Marcuse hablaban de la necesidad de reapropiarse de la imaginación, mientras que Huxley enfocaba toda la atención en la idea de las «distracciones» proyectadas sobre la masa, anticipando el papel decisivo de los _mass media_ en todo este proceso de control mental, como un auténtico brazo armado de los gobiernos al servicio del Nuevo Orden Mundial y su siniestra Agenda. Y de ahí deriva precisamente la situación que estamos viviendo en torno a los «bulos» y las «fake news», utilizadas como excusa para uniformar y aplacar toda crítica, acusando de «desinformación» a quienes en el ejercicio de una teórica libertad de expresión hacen lo propio. De ahí que se imponga la necesidad de encajar toda realidad en el relato oficial, construido _ex profeso_ para desvincular al hombre de toda realidad, y de ahí la teoría de los metaversos o centrar el foco en asuntos anecdóticos o de escasa importancia, que en el caso de [nuestra democracia liberal al amparo de la dictadura del Régimen del 78](https://hiperbolajanus.com/posts/espana-constitucion-idiota/), ha proporcionado notables beneficios a los líderes partitocráticos. Y lo más curioso del asunto está en que mencionemos a un filósofo como Marcuse, desde un discurso pretendidamente «anti-autoritario», enemigo de la represión y de la violencia en cualquiera de sus formas, cuando [la generación sobre la que influyó preparó las bases de las múltiples ingenierías sociales con las que se debilita y destruye a las sociedades europeas actuales](https://hiperbolajanus.com/posts/presentacion-izquierda-contra-pueblo-carlos-blanco/). En este sentido, hubo otro pensador más reciente que recogió el testigo de Marcuse, como fue el caso de **Hans-Georg Gadamer** (1900-2002), discípulo de **Heidegger**, que mantiene una postura especialmente crítica con la acción de los _mass media_ sobre la masa, destacando la capacidad de éstos para hacer apáticos a los individuos, de domesticarlos y adormecer su capacidad de juicio y del gusto, de hacerlas pasivas y poco receptivas al diálogo y al hábito de pensar, además de su capacidad de lanzar mensajes al subconsciente. Estas consideraciones condujeron al filósofo alemán a definir la televisión como [«la cadena de esclavos a la cual está vinculada la humanidad actual»](https://hiperbolajanus.com/posts/posmodernidad-y-orden-moral/). El contexto del mundo en el que se concibieron los discursos distópicos de Huxley y Orwell, pese a la clarividencia y agudo juicio de sus autores, no tenía en cuenta elementos que hoy se antojan indispensables para juzgar los tiempos actuales. Nos referimos a la aparición de internet, una herramienta tecnológica, de uso masivo y quizás con una doble vertiente, pues al mismo tiempo que permite identificarnos, entregar nuestros datos y opiniones voluntariamente, con la posibilidad de elaborar estudios de mercado y perfiles específicos, como herramienta de control, también hace posible estrechar vínculos y construir redes que pueden ser utilizadas en contra del propio sistema, algo que ya apuntamos en un artículo precedente. Pero profundizando más en el ámbito de la manipulación mental, es obvio que se han trabajado desde hace décadas técnicas de manipulación relacionadas con la llamada «programación neurolingüística», utilizadas en los comicios electorales, relacionados con técnicas específicas de los discursos y de las propias campañas de mercadotecnia. En este sentido son famosas las técnicas desarrolladas por el psiquiatra estadounidense **Milton Erickson** (1901-1980), en cuya obra desvela el uso de «trucos» relacionados con el lenguaje corporal, sugestiones, y otras técnicas de control mental. La programación neurolingüística (PNL) fue desarrollada a partir de 1975, con objetivos pretendidamente «terapéuticos» por el psicólogo Richard Bandler y el lingüista John Grinder. El nombre de la disciplina deriva de una conexión entre los procesos neurológicos, el lenguaje y los esquemas de comportamiento aprendidos de la experiencia, cuya síntesis podría alcanzar resultados específicos, y útiles, en la vida psicológica de los individuos. La técnica desarrollada por ambos autores, Bandler y Grinder, se basa en una programación de la realidad mediante la programación de la realidad a través de la introducción de información en los tres canales perceptibles principales: el visual, el auditivo y el cinestésico (piel, emociones etc). La idea era que el hombre crea su imagen del mundo a través de estos tres canales de entrada, aunque el principal medio para inducir a la programación es el lenguaje: el poder de las palabras es fundamental para generar esa «alucinación» perceptiva. |[](https://hiperbolajanus.com/libros/cibergeopolitica-organizaciones-alma-rusa-leonid-savin/)| |:-:| |[SAVIN, Leonid; _Cibergeopolítica, organizaciones y alma rusa_, Hipérbola Janus, 2015](https://hiperbolajanus.com/libros/cibergeopolitica-organizaciones-alma-rusa-leonid-savin/)| Esta técnica se ha venido difundiendo desde los años 70 hasta el presente en diferentes sectores, como la psicoterapia o la mercadotecnia y en general en el ámbito empresarial. No olvidemos el famoso _coaching_, y terapias de tipo motivacional por el estilo, hasta alcanzar a la propia política y a su inescindible aparato mediático (televisión, prensa etc). Es evidente que su uso ha trascendido esa dimensión «terapéutica» y «curativa» para ser instrumentalizada con propósitos más siniestros, que venimos describiendo en este artículo, y cuya intención no es otra que la de someter las mentes de la masa. El ejemplo más paradigmático, hemos de insistir en ello, fue la _Plandemia_. Obviamente, este tipo de condicionamientos que nos señala la Programación Neurolingüística, no nacieron de la forma inocente y altruista de los orígenes, sino que viene a ser una parte esencial de una serie de investigaciones que se iniciaron durante los años 50 y 60, por parte de psiquiatras y otros especialistas y financiadas por la CIA y que recibieron el nombre de **Proyecto MK-ULTRA**. En este sentido, Huxley, en su función visionaria, hablaba de la posibilidad de inducir al individuo a creer en cualquier doctrina, convirtiendo al individuo en un ser moldeable hasta extremos hasta entonces inconcebibles. Este proyecto, enmarcado en un conjunto de investigaciones que se estaban desarrollando en ambos bandos, también en la parte soviética, por parte de rusos, chinos y coreanos, en torno al «control mental», no tenía, obviamente, como propósito ningún tipo de fin humanitarismo ni terapéutico, sino la posibilidad de dañar al bloque geopolítico opuesto, en pruebas que contaron, a modo de conejillos de indias, con prostitutas, enfermos mentales y personas comunes e incluía el uso de radiaciones, hipnosis e incluso la administración de drogas psicotrópicas como el LSD. No vamos a relatar el largo historial que la CIA y Estados Unidos tiene en susodichos experimentos, con notables perjuicios contra terceros países, puesto que supondría otro artículo en sí mismo. También se habla de prisioneros de la guerra de Corea y de otras guerras anglosionistas, junto a centros de internamiento como Guantánamo, donde se usaron conejillos de indias para estos experimentos. Una de las consecuencias de estos experimentos e investigaciones los encontramos también en la estrategia del _Shock Economy_, elaborada por el autor liberal y premio nobel de economía **Milton Friedman** (1912-2006) que proponía la explotación de los momentos de crisis y traumas colectivos para ir implementando medidas radicales de ingeniería social y económica. Y es que el propio Friedman era consciente de que solamente en momentos dramáticos y de urgencia era posible inducir cambios a nivel colectivo, de tal modo que lo que se consideraba hasta entonces imposible se hacía posible. En este sentido, y vuelve a ser inevitable, debemos dirigir nuestra mirada, una vez más, a la _Plandemia_ y la aceleración que ha venido protagonizando la Agenda 2030 en los últimos tiempos. Pero los efectos de las doctrinas de Friedman ya se dejaron sentir mucho antes con los golpes de Estado y torturas perpetradas frente a aquellos países y personas relevantes que se oponían a la Agenda liberal, o neoliberal, que desde los años 60-70 pudieran representar algún tipo de oposición o forma de resistencia al avance implacable del globalismo y sus adláteres. Friedman ha sido el fundador de la **Escuela de Chicago** y sus directrices y teorías económicas han sido utilizadas tanto por la Reserva Federal estadounidense como por el Banco Central Europeo, así como durante los años 80 ejerció una notable influencia en los gobiernos de **Ronald Reagan** (1911-2004) y **Margaret Thatcher** (1925-2013), así como también conviene destacar su influencia anterior, a comienzos de los años 70, sobre las reformas de corte liberal del gobierno de **Pinochet** en Chile. Quizás haya alguna relación entre estas teorías y las continuas crisis económicas y el creciente control de las economías nacionales por parte de organizaciones transnacionales a través de la deuda, de esa deuda que el propio **George Soros** (1930) querría que fuese a perpetuidad. De este modo, tampoco es muy complicado trazar una vía de conexión entre los experimentos de la CIA en torno al «control mental» desde los primeros años de Guerra Fría, y las teorías del neoliberalismo globalista que se han sistematizado desde esa época hasta nuestros días, y lo peor es que lejos de ser aceptadas libremente, algo imposible por su carácter nocivo y autodestructivo, vienen a imponerse de manera violenta, eliminando toda resistencia. Recordemos que el miedo es una herramienta especialmente poderosa, que permite ablandar las mentes y hacerlas moldeables y receptivas a cualquier discurso, abandonando con ello toda función lógica y racional, generando una suerte de impacto psicológico, una experiencia traumática que hace que el mundo de convicciones e ideas hasta entonces aceptado se rompa en mil pedazos. Ante esa situación, cuando las personas se encuentran en situación de _shock_, es cuando se muestran más dóciles y serviles ante quienes se presentan como benefactores o autoridad en la que depositar toda la confianza. Y nos podemos imaginar que en sociedades sobresocializadas como las nuestras, es mucho más fácil porque la identidad del individuo demoliberal es especialmente frágil y débil.  Hay indicios que nos invitan a pensar que es posible que Aldous Huxley pudo haber participado del **Proyecto MK-ULTRA**, tema en el que ahora mismo tampoco podemos profundizar. No obstante, se han proporcionado detalles sobre la participación del novelista inglés en este programa secreto, y con mayores atribuciones que mucho personal militar de alto rango. Huxley ya había colaborado previamente con los servicios secretos británicos y posteriormente con los estadounidenses, a partir de 1937, trasladándose a California, donde residiría por el resto de sus días. Durante esa época empezó a experimentar con drogas psicotrópicas, como la mescalina, influenciado por la sociedad de magia ceremonial **Golden Dawn**, siendo un gran promotor de las drogas psicodélicas desde entonces. Así lo confirma también el testimonio de otros autores como **Aleister Crowley** (1875-1947). Las experiencias con estas drogas serían posteriormente relatadas por el propio autor de _Un mundo feliz_ en otra obra, quizás menos conocida, bajo el título de _Las puertas de la percepción_, publicado en 1954. Incluso se habla de su sometimiento a experimentos relacionados con la esquizofrenia y la alteración de la percepción relacionados con el citado programa bajo la supervisión del psiquiatra Humpry Osmond, para quien trató de conseguir financiación a través de organizaciones globalistas como la _Ford Foundation_ y la _Round Table_, ésta última una organización pantalla de la propia CIA. Muchas de las conclusiones de estos estudios, experimentos y programas de manipulación a gran escala son relatados con todo lujo de detalles por el periodista y escritor italiano **Maurizio Blondet**, a través de la obra, publicada por nuestro sello editorial, [_Complots_](https://hiperbolajanus.com/libros/complots-maurizio-blondet/). |[](https://hiperbolajanus.com/libros/complots-maurizio-blondet/)| |:-:| |[BLONDET, Maurizio; _Complots_, Hipérbola Janus, 2020](https://hiperbolajanus.com/libros/complots-maurizio-blondet/)| Los últimos atisbos o señales de esta manipulación masiva en el presente, cuya responsabilidad ya hemos atribuido a los _mass media_, los tenemos en la Europa occidental del presente, con sus democracias liberales cooptadas por los poderes globalistas y supeditados al cumplimiento de una Agenda. Así, por ejemplo, el tema de la «inmigración»[^1] masiva y no tan descontrolada como muchos creen, sino más bien planificada, con los enfrentamientos de los que estamos siendo testigos en el Reino Unido en las últimas semanas, también responden a complejas ingenierías sociales de manipulación mental, donde el elemento distópico, ciertamente, no se encuentra ausente. Las autoridades británicas, destruyendo durante décadas toda forma de cohesión social y entregado al experimento multicultural de cuño globalista, han dividido y polarizado su país, como en el resto de la Europa Occidental, utilizando con toda probabilidad las herramientas de las que hemos estado hablando, refinadas técnicas de manipulación y control mental, para convencer a la masa de que renunciar a sus raíces, a su Patria, a su propia idiosincrasia como pueblos, y convertirse en territorios sin identidad, con individuos atomizados e intercambiables, es algo deseable en nombre de un «progreso», totalmente abstracto y vendido como una especie de Arcadia feliz, con esa misma proyección teleológica que ha sido característica del liberalismo desde sus discursos decimonónicos. || |:-:| |Protestas en el Reino Unido por el aumento de la inseguridad en las calles| [^1]: Nótese la manipulación del lenguaje en el término que recientemente utiliza la prensa: «migración» o «migrante», prescindiendo de los prefijos _in-_ o _e-_, para dar a entender de forma indirecta que ni se entra (_in_-migrante) ni se sale (_e_-migrante) de ninguna parte porque «no existen fronteras», si no que la gente simplemente se desplaza. --- **Artículo original**: Hipérbola Janus, [_Distopía y manipulación de mentes_](https://www.hiperbolajanus.com/posts/distopia-manipulacion-mentes/) [**(TOR)**](http://hiperbolam7t46pbl2fiqzaarcmw6injdru4nh2pwuhrkoub3263mpad.onion/posts/distopia-manipulacion-mentes/), 27/Ago/2024
@ bcbb3e40:a494e501
2024-08-27 18:33:08|| |:-:| |Escena del corto de animación [«I, Pet Goat II»](https://youtu.be/6n_xCI-peq0) del estudio Heliofant, en el que una pantalla con un siniestro personaje en su interior está conectada al cráneo hueco de otro personaje.| Los que tenemos ya algunos años y empezamos a peinar canas, con toda la profundidad de enfoque y perspectiva que ello implica, hemos vivido cambios muy trascendentales en las últimas décadas. De alguna manera, aquello que considerábamos imposible o, en su defecto, poco probable, se ha venido materializando en el tiempo causando nuestro asombro y, por qué no decirlo, nuestro temor e inquietud. [Los acontecimientos vividos a raíz de la **Plandemia**](https://hiperbolajanus.com/posts/presentacion-despues-virus-boris-nad/), por ejemplo, nos hicieron ver claramente que el sistema ha abandonado sus posiciones anteriores, el disimulo que caracterizaba a su proceder, ese velo de «normalidad», para intercambiarlo por otra «normalidad», una «nueva normalidad» en la que todo es posible, y esto en el sentido más negativo que pueda imaginarse. Durante el último lustro hemos asistido a encierros obligatorios, a la imposición de pinchazos con sustancias desconocidas de las que nadie se hacía (ni se sigue haciendo) responsable y cuyos efectos nocivos se han constatado con posterioridad, a un creciente y desmesurado control social a través de diversas vías, que ha colocado el mismo concepto de «Verdad» y «Realidad» en entredicho, sustituyendo la Verdad en un sentido eminente, metafísico si se quiere, en la presa de un relato, de una construcción ideológica de ínfimo nivel intelectual diseñado para mantener a la masa en el redil, acallando cualquier tipo de discrepancia, y especialmente de disidencia, que pudiera romper con ese relato hegemónico, custodiado como si del Santo Grial se tratase, frente a cualquier evidencia objetiva. De hecho, [se ha hablado mucho de la **«posverdad»**](https://hiperbolajanus.com/posts/breviarios-contra-modernidad/). Pero todos estos temas no son nuevos, pese a que su concreción práctica en los tiempos presentes, con las democracias de libre mercado, que venían presumiendo de su «estado de derecho», de sus «garantías» y «libertades», sino que ya venían anunciados en cierta tradición literaria que podemos remontar a las décadas 30-40 del pasado siglo. Ahí tenemos a dos notables autores: **Aldous Huxley** (1894-1963) y **George Orwell** (1903-1950), autores de [_Un mundo feliz_](https://amzn.to/3MnR1Gz) y [_1984_](https://hiperbolajanus.com/posts/resena-1984-de-george-orwell/) respectivamente. Ambos trabajos pueden encuadrarse dentro de esa corriente distópica tan característica donde también podríamos encuadrar, entre otras obras, aquella de **Ray Bradbury** (1920-2012), la famosa [_Fahrenheit 451_](https://amzn.to/4dDfAuV). No obstante, vamos a fijar nuestra atención en los dos primeros autores, Huxley y Orwell, cuyos modelos de dictadura propuestos difieren significativamente entre sí, mientras que el primero nos presenta una «dictadura blanda» o «dulce», edulcorada por las drogas y el transhumanismo, el segundo nos dibuja un orden dictatorial cruel y sádico, enfermizo e investido de una diabólica voluntad de poseer al individuo en su interior más profundo. || |:-:| |George Orwell y Aldous Huxley, los autores de literatura fantástica más visionarios y famosos del siglo XX| Tras la publicación de _1984_, Huxley, agradecía a Orwell el envío de su mítica obra y en una especie de predicción o vaticinio de futuro confrontaba esta obra con la suya propia: «La filosofía de la clase en el poder en 1984 es una forma de sadismo llevado a las consecuencias extremas y hacia su solución lógica: ir más allá del sexo y negarlo. Creo que las oligarquías encontrarán formas más eficientes de gobernar y satisfacer su sed de poder y serán similares a las descritas en Un mundo feliz». Siendo fiel a los dictámenes de su propia obra, Huxley consideraba que se impondría una «dictadura dulce», con el uso masivo y generalizado de drogas farmacológicas y técnicas de hipnotismo a través del desarrollo de poderosas herramientas psicológicas para plegar el control de la mente y la voluntad de las masas al poder imperante. De hecho, este proceso era calificado por Huxley como «la última revolución». Además preconizaba una caída de las masas en un estado de esclavitud voluntaria y adaptada, formulada en aras de una mayor eficiencia en el ejercicio del poder. Otros autores posteriores como **Elémire Zolla** (1926-2002), se hacían eco del poder de la hipnosis y de la manipulación de las mentes como un proyecto real a gran escala, con siniestros propósitos. Y de algún modo el [liberal-capitalismo ha utilizado este tipo de técnicas a través del mercado](https://hiperbolajanus.com/libros/mos-maiorum-7/), con la estandarización de comportamientos y modas a través del uso de la publicidad en una voluntad de estandarización y uniformización con una voluntad inequívoca de alcanzar la psique profunda del hombre, el subconsciente, para dominar al hombre allí donde el pensamiento lógico y la voluntad se encuentran desdibujados y anulados. En la misma dirección tenemos a **Herbert Marcuse** (1898-1979), en cuya obra también vemos alusiones a las agresiones y limitaciones de la libertad en [el contexto de la civilización industrial avanzada como parte del progreso técnico](https://hiperbolajanus.com/posts/resena-hanno-cambiato-faccia/). Empieza a delinear en su obra la imagen de un régimen totalitario en el que todos los aspectos de la vida del individuo, y especialmente del pueblo trabajador, se encuentran alienados, encerrados en la lógica del producir y consumir, sin resistencia posible. El hombre reducido a esa condición y cuya única libertad se reduce a elegir entre diferentes productos. En este sentido Marcuse condenaba a la tecnología y delata sus cualidades totalmente funcionales a una ideología de poder. Este es el sentido que otorga a su «hombre unidimensional» cuya definición antropológica se desarrolla sobre un único plano, y bajo ese condicionamiento mental que vemos en la obra orwelliana. De algún modo, a partir de cierto momento, las herramientas de control de masas se hacen más sutiles, y sustituyen la violencia que el incipiente Estado liberal utilizaba durante el siglo XIX para mantener el orden frente a revueltas o revoluciones adversas, por el uso de elementos de control social y vigilancia, y esto en los últimos tiempos se ha venido desarrollando bajo múltiples excusas, como, por ejemplo, la denominada «Agenda verde», que bajo la premisa de unos hipotéticos cambios dramáticos y catastróficos de raíz antropogénica en el devenir terrestre, debemos aceptar las «ciudades de los 15 minutos», funcionando como «guetos» con contingentes de población estabulados, con movimientos limitados en un espacio reducido, donde prácticamente haya que pedir permiso para salir. Todo por salvar el planeta, por esa ridícula y grotesca teoría de la «huella de carbono», promocionada por bancos y otras instituciones del sistema. La estrategia del miedo ha dado frutos siguiendo el plan de las élites globalistas, lo vimos con la _Plandemia_ y ha seguido manteniendo su continuidad bajo la apariencia de diferentes amenazas, la emergencia permanente que supone una guerra, como la que [la OTAN libra con Rusia utilizando a Ucrania como ariete](https://hiperbolajanus.com/libros/geopolitica-rusia-aleksandr-duguin/). Las masas, desestabilizadas han venido aceptando todas las imposiciones en nombre de un «consenso común», convirtiéndose en vigilantes solícitos y aceptando restricciones que antes del 2020 nunca hubieran aceptado. En este contexto, filósofos como Marcuse hablaban de la necesidad de reapropiarse de la imaginación, mientras que Huxley enfocaba toda la atención en la idea de las «distracciones» proyectadas sobre la masa, anticipando el papel decisivo de los _mass media_ en todo este proceso de control mental, como un auténtico brazo armado de los gobiernos al servicio del Nuevo Orden Mundial y su siniestra Agenda. Y de ahí deriva precisamente la situación que estamos viviendo en torno a los «bulos» y las «fake news», utilizadas como excusa para uniformar y aplacar toda crítica, acusando de «desinformación» a quienes en el ejercicio de una teórica libertad de expresión hacen lo propio. De ahí que se imponga la necesidad de encajar toda realidad en el relato oficial, construido _ex profeso_ para desvincular al hombre de toda realidad, y de ahí la teoría de los metaversos o centrar el foco en asuntos anecdóticos o de escasa importancia, que en el caso de [nuestra democracia liberal al amparo de la dictadura del Régimen del 78](https://hiperbolajanus.com/posts/espana-constitucion-idiota/), ha proporcionado notables beneficios a los líderes partitocráticos. Y lo más curioso del asunto está en que mencionemos a un filósofo como Marcuse, desde un discurso pretendidamente «anti-autoritario», enemigo de la represión y de la violencia en cualquiera de sus formas, cuando [la generación sobre la que influyó preparó las bases de las múltiples ingenierías sociales con las que se debilita y destruye a las sociedades europeas actuales](https://hiperbolajanus.com/posts/presentacion-izquierda-contra-pueblo-carlos-blanco/). En este sentido, hubo otro pensador más reciente que recogió el testigo de Marcuse, como fue el caso de **Hans-Georg Gadamer** (1900-2002), discípulo de **Heidegger**, que mantiene una postura especialmente crítica con la acción de los _mass media_ sobre la masa, destacando la capacidad de éstos para hacer apáticos a los individuos, de domesticarlos y adormecer su capacidad de juicio y del gusto, de hacerlas pasivas y poco receptivas al diálogo y al hábito de pensar, además de su capacidad de lanzar mensajes al subconsciente. Estas consideraciones condujeron al filósofo alemán a definir la televisión como [«la cadena de esclavos a la cual está vinculada la humanidad actual»](https://hiperbolajanus.com/posts/posmodernidad-y-orden-moral/). El contexto del mundo en el que se concibieron los discursos distópicos de Huxley y Orwell, pese a la clarividencia y agudo juicio de sus autores, no tenía en cuenta elementos que hoy se antojan indispensables para juzgar los tiempos actuales. Nos referimos a la aparición de internet, una herramienta tecnológica, de uso masivo y quizás con una doble vertiente, pues al mismo tiempo que permite identificarnos, entregar nuestros datos y opiniones voluntariamente, con la posibilidad de elaborar estudios de mercado y perfiles específicos, como herramienta de control, también hace posible estrechar vínculos y construir redes que pueden ser utilizadas en contra del propio sistema, algo que ya apuntamos en un artículo precedente. Pero profundizando más en el ámbito de la manipulación mental, es obvio que se han trabajado desde hace décadas técnicas de manipulación relacionadas con la llamada «programación neurolingüística», utilizadas en los comicios electorales, relacionados con técnicas específicas de los discursos y de las propias campañas de mercadotecnia. En este sentido son famosas las técnicas desarrolladas por el psiquiatra estadounidense **Milton Erickson** (1901-1980), en cuya obra desvela el uso de «trucos» relacionados con el lenguaje corporal, sugestiones, y otras técnicas de control mental. La programación neurolingüística (PNL) fue desarrollada a partir de 1975, con objetivos pretendidamente «terapéuticos» por el psicólogo Richard Bandler y el lingüista John Grinder. El nombre de la disciplina deriva de una conexión entre los procesos neurológicos, el lenguaje y los esquemas de comportamiento aprendidos de la experiencia, cuya síntesis podría alcanzar resultados específicos, y útiles, en la vida psicológica de los individuos. La técnica desarrollada por ambos autores, Bandler y Grinder, se basa en una programación de la realidad mediante la programación de la realidad a través de la introducción de información en los tres canales perceptibles principales: el visual, el auditivo y el cinestésico (piel, emociones etc). La idea era que el hombre crea su imagen del mundo a través de estos tres canales de entrada, aunque el principal medio para inducir a la programación es el lenguaje: el poder de las palabras es fundamental para generar esa «alucinación» perceptiva. |[](https://hiperbolajanus.com/libros/cibergeopolitica-organizaciones-alma-rusa-leonid-savin/)| |:-:| |[SAVIN, Leonid; _Cibergeopolítica, organizaciones y alma rusa_, Hipérbola Janus, 2015](https://hiperbolajanus.com/libros/cibergeopolitica-organizaciones-alma-rusa-leonid-savin/)| Esta técnica se ha venido difundiendo desde los años 70 hasta el presente en diferentes sectores, como la psicoterapia o la mercadotecnia y en general en el ámbito empresarial. No olvidemos el famoso _coaching_, y terapias de tipo motivacional por el estilo, hasta alcanzar a la propia política y a su inescindible aparato mediático (televisión, prensa etc). Es evidente que su uso ha trascendido esa dimensión «terapéutica» y «curativa» para ser instrumentalizada con propósitos más siniestros, que venimos describiendo en este artículo, y cuya intención no es otra que la de someter las mentes de la masa. El ejemplo más paradigmático, hemos de insistir en ello, fue la _Plandemia_. Obviamente, este tipo de condicionamientos que nos señala la Programación Neurolingüística, no nacieron de la forma inocente y altruista de los orígenes, sino que viene a ser una parte esencial de una serie de investigaciones que se iniciaron durante los años 50 y 60, por parte de psiquiatras y otros especialistas y financiadas por la CIA y que recibieron el nombre de **Proyecto MK-ULTRA**. En este sentido, Huxley, en su función visionaria, hablaba de la posibilidad de inducir al individuo a creer en cualquier doctrina, convirtiendo al individuo en un ser moldeable hasta extremos hasta entonces inconcebibles. Este proyecto, enmarcado en un conjunto de investigaciones que se estaban desarrollando en ambos bandos, también en la parte soviética, por parte de rusos, chinos y coreanos, en torno al «control mental», no tenía, obviamente, como propósito ningún tipo de fin humanitarismo ni terapéutico, sino la posibilidad de dañar al bloque geopolítico opuesto, en pruebas que contaron, a modo de conejillos de indias, con prostitutas, enfermos mentales y personas comunes e incluía el uso de radiaciones, hipnosis e incluso la administración de drogas psicotrópicas como el LSD. No vamos a relatar el largo historial que la CIA y Estados Unidos tiene en susodichos experimentos, con notables perjuicios contra terceros países, puesto que supondría otro artículo en sí mismo. También se habla de prisioneros de la guerra de Corea y de otras guerras anglosionistas, junto a centros de internamiento como Guantánamo, donde se usaron conejillos de indias para estos experimentos. Una de las consecuencias de estos experimentos e investigaciones los encontramos también en la estrategia del _Shock Economy_, elaborada por el autor liberal y premio nobel de economía **Milton Friedman** (1912-2006) que proponía la explotación de los momentos de crisis y traumas colectivos para ir implementando medidas radicales de ingeniería social y económica. Y es que el propio Friedman era consciente de que solamente en momentos dramáticos y de urgencia era posible inducir cambios a nivel colectivo, de tal modo que lo que se consideraba hasta entonces imposible se hacía posible. En este sentido, y vuelve a ser inevitable, debemos dirigir nuestra mirada, una vez más, a la _Plandemia_ y la aceleración que ha venido protagonizando la Agenda 2030 en los últimos tiempos. Pero los efectos de las doctrinas de Friedman ya se dejaron sentir mucho antes con los golpes de Estado y torturas perpetradas frente a aquellos países y personas relevantes que se oponían a la Agenda liberal, o neoliberal, que desde los años 60-70 pudieran representar algún tipo de oposición o forma de resistencia al avance implacable del globalismo y sus adláteres. Friedman ha sido el fundador de la **Escuela de Chicago** y sus directrices y teorías económicas han sido utilizadas tanto por la Reserva Federal estadounidense como por el Banco Central Europeo, así como durante los años 80 ejerció una notable influencia en los gobiernos de **Ronald Reagan** (1911-2004) y **Margaret Thatcher** (1925-2013), así como también conviene destacar su influencia anterior, a comienzos de los años 70, sobre las reformas de corte liberal del gobierno de **Pinochet** en Chile. Quizás haya alguna relación entre estas teorías y las continuas crisis económicas y el creciente control de las economías nacionales por parte de organizaciones transnacionales a través de la deuda, de esa deuda que el propio **George Soros** (1930) querría que fuese a perpetuidad. De este modo, tampoco es muy complicado trazar una vía de conexión entre los experimentos de la CIA en torno al «control mental» desde los primeros años de Guerra Fría, y las teorías del neoliberalismo globalista que se han sistematizado desde esa época hasta nuestros días, y lo peor es que lejos de ser aceptadas libremente, algo imposible por su carácter nocivo y autodestructivo, vienen a imponerse de manera violenta, eliminando toda resistencia. Recordemos que el miedo es una herramienta especialmente poderosa, que permite ablandar las mentes y hacerlas moldeables y receptivas a cualquier discurso, abandonando con ello toda función lógica y racional, generando una suerte de impacto psicológico, una experiencia traumática que hace que el mundo de convicciones e ideas hasta entonces aceptado se rompa en mil pedazos. Ante esa situación, cuando las personas se encuentran en situación de _shock_, es cuando se muestran más dóciles y serviles ante quienes se presentan como benefactores o autoridad en la que depositar toda la confianza. Y nos podemos imaginar que en sociedades sobresocializadas como las nuestras, es mucho más fácil porque la identidad del individuo demoliberal es especialmente frágil y débil.  Hay indicios que nos invitan a pensar que es posible que Aldous Huxley pudo haber participado del **Proyecto MK-ULTRA**, tema en el que ahora mismo tampoco podemos profundizar. No obstante, se han proporcionado detalles sobre la participación del novelista inglés en este programa secreto, y con mayores atribuciones que mucho personal militar de alto rango. Huxley ya había colaborado previamente con los servicios secretos británicos y posteriormente con los estadounidenses, a partir de 1937, trasladándose a California, donde residiría por el resto de sus días. Durante esa época empezó a experimentar con drogas psicotrópicas, como la mescalina, influenciado por la sociedad de magia ceremonial **Golden Dawn**, siendo un gran promotor de las drogas psicodélicas desde entonces. Así lo confirma también el testimonio de otros autores como **Aleister Crowley** (1875-1947). Las experiencias con estas drogas serían posteriormente relatadas por el propio autor de _Un mundo feliz_ en otra obra, quizás menos conocida, bajo el título de _Las puertas de la percepción_, publicado en 1954. Incluso se habla de su sometimiento a experimentos relacionados con la esquizofrenia y la alteración de la percepción relacionados con el citado programa bajo la supervisión del psiquiatra Humpry Osmond, para quien trató de conseguir financiación a través de organizaciones globalistas como la _Ford Foundation_ y la _Round Table_, ésta última una organización pantalla de la propia CIA. Muchas de las conclusiones de estos estudios, experimentos y programas de manipulación a gran escala son relatados con todo lujo de detalles por el periodista y escritor italiano **Maurizio Blondet**, a través de la obra, publicada por nuestro sello editorial, [_Complots_](https://hiperbolajanus.com/libros/complots-maurizio-blondet/). |[](https://hiperbolajanus.com/libros/complots-maurizio-blondet/)| |:-:| |[BLONDET, Maurizio; _Complots_, Hipérbola Janus, 2020](https://hiperbolajanus.com/libros/complots-maurizio-blondet/)| Los últimos atisbos o señales de esta manipulación masiva en el presente, cuya responsabilidad ya hemos atribuido a los _mass media_, los tenemos en la Europa occidental del presente, con sus democracias liberales cooptadas por los poderes globalistas y supeditados al cumplimiento de una Agenda. Así, por ejemplo, el tema de la «inmigración»[^1] masiva y no tan descontrolada como muchos creen, sino más bien planificada, con los enfrentamientos de los que estamos siendo testigos en el Reino Unido en las últimas semanas, también responden a complejas ingenierías sociales de manipulación mental, donde el elemento distópico, ciertamente, no se encuentra ausente. Las autoridades británicas, destruyendo durante décadas toda forma de cohesión social y entregado al experimento multicultural de cuño globalista, han dividido y polarizado su país, como en el resto de la Europa Occidental, utilizando con toda probabilidad las herramientas de las que hemos estado hablando, refinadas técnicas de manipulación y control mental, para convencer a la masa de que renunciar a sus raíces, a su Patria, a su propia idiosincrasia como pueblos, y convertirse en territorios sin identidad, con individuos atomizados e intercambiables, es algo deseable en nombre de un «progreso», totalmente abstracto y vendido como una especie de Arcadia feliz, con esa misma proyección teleológica que ha sido característica del liberalismo desde sus discursos decimonónicos. || |:-:| |Protestas en el Reino Unido por el aumento de la inseguridad en las calles| [^1]: Nótese la manipulación del lenguaje en el término que recientemente utiliza la prensa: «migración» o «migrante», prescindiendo de los prefijos _in-_ o _e-_, para dar a entender de forma indirecta que ni se entra (_in_-migrante) ni se sale (_e_-migrante) de ninguna parte porque «no existen fronteras», si no que la gente simplemente se desplaza. --- **Artículo original**: Hipérbola Janus, [_Distopía y manipulación de mentes_](https://www.hiperbolajanus.com/posts/distopia-manipulacion-mentes/) [**(TOR)**](http://hiperbolam7t46pbl2fiqzaarcmw6injdru4nh2pwuhrkoub3263mpad.onion/posts/distopia-manipulacion-mentes/), 27/Ago/2024 @ af9c48b7:a3f7aaf4
2024-08-27 16:51:52## Chef's notes Easy recipe with simple ingredients. This recipe uses some store bought, precooked items as way to cut down on cook time. I recommend letting the vegetables thaw if you don't like them on the firm/crunchy side.Feel free to substitute fresh ingredients if you have the time and want to make the extra effort. ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 50 min - 🍽️ Servings: 8-10 ## Ingredients - 2 (8 oz) packages refrigerated crescent rolls (dough sheets preferred) - 1 pound cooked rotisserie chicken (deboned and chopped) - 2 table spoons of butter - 2 (10 once) packages of frozen mixed vegetables - 1 (15 once can sliced potatoes (drained) - 1 (10.5 once) can condensed cream of chicken soup - 1 (10.5 once) can condensed cream of mushroom soup - 1/2 cup milk - salt and ground pepper to taste ## Directions 1. Preheat oven to 350 degrees F (175 degrees C). Line the botton of 9x13-inch baking dish with one can of crescent roll dough. If you don't get the sheet dough, be sure to pinch the seams together. 2. Melt the butter in a sauce pan over medium heat. Then add the chicken, mixed vegetables, and sliced potatoes (recommend cutting into smaller pieces). Cook, stirring frequently, until vegetables are thawed and mixture is heated through, 5 to 7 minutes. 3. While the mixed vegetables are heating, warm both cans of condensed soup in a seperate pan over medium-low heat. Slowly add milk and cook, stirring frequently, until combined and heated through, about 3 minutes. 4. Add the soup mixture to the chicken mixture, then pour into the baking dish. Top with the second can of crescent roll dough. Feel free to cut some slits in dough if you are using the dough sheets. Cover lightly with foil to prevent the crescent roll dough from browning too quickly. 5. Bake in oven until heated through and dough is a golden brown. Cook time should be around 45-50 minutes I reommend removing the foil for the last 10 minutes to get a golden crust. Be sure to keep a close watch on the crust after removing the foil because it will brown quickly.
@ af9c48b7:a3f7aaf4
2024-08-27 16:51:52## Chef's notes Easy recipe with simple ingredients. This recipe uses some store bought, precooked items as way to cut down on cook time. I recommend letting the vegetables thaw if you don't like them on the firm/crunchy side.Feel free to substitute fresh ingredients if you have the time and want to make the extra effort. ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 50 min - 🍽️ Servings: 8-10 ## Ingredients - 2 (8 oz) packages refrigerated crescent rolls (dough sheets preferred) - 1 pound cooked rotisserie chicken (deboned and chopped) - 2 table spoons of butter - 2 (10 once) packages of frozen mixed vegetables - 1 (15 once can sliced potatoes (drained) - 1 (10.5 once) can condensed cream of chicken soup - 1 (10.5 once) can condensed cream of mushroom soup - 1/2 cup milk - salt and ground pepper to taste ## Directions 1. Preheat oven to 350 degrees F (175 degrees C). Line the botton of 9x13-inch baking dish with one can of crescent roll dough. If you don't get the sheet dough, be sure to pinch the seams together. 2. Melt the butter in a sauce pan over medium heat. Then add the chicken, mixed vegetables, and sliced potatoes (recommend cutting into smaller pieces). Cook, stirring frequently, until vegetables are thawed and mixture is heated through, 5 to 7 minutes. 3. While the mixed vegetables are heating, warm both cans of condensed soup in a seperate pan over medium-low heat. Slowly add milk and cook, stirring frequently, until combined and heated through, about 3 minutes. 4. Add the soup mixture to the chicken mixture, then pour into the baking dish. Top with the second can of crescent roll dough. Feel free to cut some slits in dough if you are using the dough sheets. Cover lightly with foil to prevent the crescent roll dough from browning too quickly. 5. Bake in oven until heated through and dough is a golden brown. Cook time should be around 45-50 minutes I reommend removing the foil for the last 10 minutes to get a golden crust. Be sure to keep a close watch on the crust after removing the foil because it will brown quickly. @ b83a28b7:35919450
2024-08-27 16:48:28https://image.nostr.build/df0721d6d45d82db35d06663a0318ffe68c0b2b3c694888d23694efcc4255de5.gif
@ b83a28b7:35919450
2024-08-27 16:48:28https://image.nostr.build/df0721d6d45d82db35d06663a0318ffe68c0b2b3c694888d23694efcc4255de5.gif @ 0861144c:e68a1caf
2024-08-27 14:01:14On Sunday afternoon, while I was taking a nap, my phone started buzzing with notifications. In the various groups where I share my views and words, I saw that Pavel Durov had been arrested by the French police. There wasn’t much to analyze yet, but alarms were raised, and theories began to circulate, and those theories were not far from reality. Pavel is practically accused of every digital crime one can commit, from criminal association to pedophilia. My eyes kept scrolling down, unable to believe all the accusations. Could even 10% of what they’re questioning him about be true? And unfortunately, the worst blind person is the one who doesn’t want to see. Detractors claimed that Telegram served totalitarian regimes and handed over data, when in reality, the opposite is true, as this social network served as a reference point when people in Belarus were protesting for their civil rights. They also alleged that Telegram collaborated with the Russian government to evade sanctions or promote disinformation campaigns, but if anyone takes the trouble to [watch the 60-minute interview with Tucker Carlson](https://x.com/TuckerCarlson/status/1780355490964283565), they’ll see that one of the reasons Pavel left his homeland (Russia) is because the government pressure simply became unbearable; Putin took over VK because Pavel refused to be part of it.  So, we already know that Russia has no interest in Telegram, nor is it anti-democratic, as the movements have already demonstrated, which leads us to the question of whether the French really have interests with Telegram. And my first response after reading Macron’s statements was precisely that they were seeking his arrest until we read that Macron [is an avid user of this social network](https://www.politico.eu/article/telegram-pavel-durov-arrest-emmanuel-macron-france-social-media/), but also that it was [Macron himself who _encouraged_](https://www.lemonde.fr/en/france/article/2023/06/26/the-telegram-founder-s-mysterious-french-passport_6037748_7.html) Pavel to obtain his French passport. So, let’s ask a long question: > **What leads a European liberal democracy to arrest the CEO of a social network with charges that could easily apply to other social networks?** Try a simple experiment: take out the word Telegram and insert your social network of choice in the accusatory libel. It has the same effect, and the previous question arises again, and I’d like to offer an alternative perspective on this process. To this day, and I’ve mentioned this before in other posts in this same place, but I’ll emphasize it: we no longer have democracy as such. You can forget about the liberal style that was once promised to us or that we learned about in our educational institutions. This has been replaced with Dataism. ### Dataism and How Pavel Doesn’t Cooperate [Dataism](https://en.wikipedia.org/wiki/Dataism) is a new form of governance. The word data comes from the Latin *datum*, which means "to give," meaning we, the citizens, *give* our data to the companies that manage social networks. These companies, while using us as a product for other companies, also see governments trying to dip their spoon into the pot, so they start talking about *speech regulations*, *hate content*, among other accusations, to maintain a *clean social network*. I’m guilty first. In the old days, when the chief censors operated in the former Soviet Union (as Coetzee tells us), folders were created with the data of suspects, documenting their *revolutionary* activities, and when the time came, *measures* could be taken that affected the welfare state. Today, this type of persecution no longer exists, but by handing over my data, companies no longer talk about tracking me, since we’ve given them free access to our location and GPS, in addition to exposing our lives on every platform; today, profiles are made, and now there’s a marketing department that creates *behavior profiles* and bombards me with products and services that *might interest me*. The government’s intrusion into social networks has become so great that now they had to react, showing a sort of repentance. As I write this, I find it really hard to react to the letter sent by Meta (signed by Zuckerberg himself) in which [he regrets the censorship](https://x.com/JudiciaryGOP/status/1828201780544504064) carried out during the pandemic. And I vividly remember the hundreds of people whose accounts were censored, rightly or wrongly, for not aligning with the government’s *scientific* stance. ### And Telegram? Telegram [doesn’t hand over data](https://www.dw.com/en/brazil-court-lifts-telegram-suspension-despite-non-compliance-for-neo-nazi-group-data/a-65474168#:~:text=Brazil%20had%20temporarily%20banned%20Telegram,prioritizes%20the%20privacy%20of%20users.&text=A%20federal%20judge%20in%20Brazil,Telegram%2C%20an%20encrypted%20messaging%20app.) and paid the price. It refused to do so in the past and stood against the current regime, against dataism. The French justice system wants Pavel to spend time in prison for daring to use encrypted products that don’t allow them to listen to/see/read their *possible suspects*. The KGB would blush at such a move. And the most ironic thing is that a person who flees his own country for not wanting to cooperate with values contrary to freedom is now arrested by a country that was once the center of debates on liberty, fraternity, and equality, where they rose up against the oppressive regime. I don’t know how the process will continue on French soil, and I also don’t know if the Russians are really using USDT networks to move *sanctioned* money. I only know that this kind of arrest proves and gives reason to those who argue that freedom, as we knew it, no longer makes sense. ### And I don’t know what else to tell you, my friend. Unfortunately, I have no conclusion. I wish I could end this article and give you hope that justice will respond to see what they’re accusing him of, but it [would be a lie on my part](https://stacker.news/items/560694). I can tell you, however, that if you’re reading this and have a NOSTR account and use bitcoin as part of your economy, you’re on the right path. Sites like Stacker News and others, as well as protocols like NOSTR, will gain greater importance as we open our eyes to fight the regime that seeks to abolish privacy as a human right. Today we can fight, and it doesn’t require much of us, other than to promote what we are doing now. And I’ll end by asking the same question that @FmpPerspective did: [*are we still allowed to ask questions?*](https://stacker.news/items/662413) originally posted at https://stacker.news/items/663527
@ 0861144c:e68a1caf
2024-08-27 14:01:14On Sunday afternoon, while I was taking a nap, my phone started buzzing with notifications. In the various groups where I share my views and words, I saw that Pavel Durov had been arrested by the French police. There wasn’t much to analyze yet, but alarms were raised, and theories began to circulate, and those theories were not far from reality. Pavel is practically accused of every digital crime one can commit, from criminal association to pedophilia. My eyes kept scrolling down, unable to believe all the accusations. Could even 10% of what they’re questioning him about be true? And unfortunately, the worst blind person is the one who doesn’t want to see. Detractors claimed that Telegram served totalitarian regimes and handed over data, when in reality, the opposite is true, as this social network served as a reference point when people in Belarus were protesting for their civil rights. They also alleged that Telegram collaborated with the Russian government to evade sanctions or promote disinformation campaigns, but if anyone takes the trouble to [watch the 60-minute interview with Tucker Carlson](https://x.com/TuckerCarlson/status/1780355490964283565), they’ll see that one of the reasons Pavel left his homeland (Russia) is because the government pressure simply became unbearable; Putin took over VK because Pavel refused to be part of it.  So, we already know that Russia has no interest in Telegram, nor is it anti-democratic, as the movements have already demonstrated, which leads us to the question of whether the French really have interests with Telegram. And my first response after reading Macron’s statements was precisely that they were seeking his arrest until we read that Macron [is an avid user of this social network](https://www.politico.eu/article/telegram-pavel-durov-arrest-emmanuel-macron-france-social-media/), but also that it was [Macron himself who _encouraged_](https://www.lemonde.fr/en/france/article/2023/06/26/the-telegram-founder-s-mysterious-french-passport_6037748_7.html) Pavel to obtain his French passport. So, let’s ask a long question: > **What leads a European liberal democracy to arrest the CEO of a social network with charges that could easily apply to other social networks?** Try a simple experiment: take out the word Telegram and insert your social network of choice in the accusatory libel. It has the same effect, and the previous question arises again, and I’d like to offer an alternative perspective on this process. To this day, and I’ve mentioned this before in other posts in this same place, but I’ll emphasize it: we no longer have democracy as such. You can forget about the liberal style that was once promised to us or that we learned about in our educational institutions. This has been replaced with Dataism. ### Dataism and How Pavel Doesn’t Cooperate [Dataism](https://en.wikipedia.org/wiki/Dataism) is a new form of governance. The word data comes from the Latin *datum*, which means "to give," meaning we, the citizens, *give* our data to the companies that manage social networks. These companies, while using us as a product for other companies, also see governments trying to dip their spoon into the pot, so they start talking about *speech regulations*, *hate content*, among other accusations, to maintain a *clean social network*. I’m guilty first. In the old days, when the chief censors operated in the former Soviet Union (as Coetzee tells us), folders were created with the data of suspects, documenting their *revolutionary* activities, and when the time came, *measures* could be taken that affected the welfare state. Today, this type of persecution no longer exists, but by handing over my data, companies no longer talk about tracking me, since we’ve given them free access to our location and GPS, in addition to exposing our lives on every platform; today, profiles are made, and now there’s a marketing department that creates *behavior profiles* and bombards me with products and services that *might interest me*. The government’s intrusion into social networks has become so great that now they had to react, showing a sort of repentance. As I write this, I find it really hard to react to the letter sent by Meta (signed by Zuckerberg himself) in which [he regrets the censorship](https://x.com/JudiciaryGOP/status/1828201780544504064) carried out during the pandemic. And I vividly remember the hundreds of people whose accounts were censored, rightly or wrongly, for not aligning with the government’s *scientific* stance. ### And Telegram? Telegram [doesn’t hand over data](https://www.dw.com/en/brazil-court-lifts-telegram-suspension-despite-non-compliance-for-neo-nazi-group-data/a-65474168#:~:text=Brazil%20had%20temporarily%20banned%20Telegram,prioritizes%20the%20privacy%20of%20users.&text=A%20federal%20judge%20in%20Brazil,Telegram%2C%20an%20encrypted%20messaging%20app.) and paid the price. It refused to do so in the past and stood against the current regime, against dataism. The French justice system wants Pavel to spend time in prison for daring to use encrypted products that don’t allow them to listen to/see/read their *possible suspects*. The KGB would blush at such a move. And the most ironic thing is that a person who flees his own country for not wanting to cooperate with values contrary to freedom is now arrested by a country that was once the center of debates on liberty, fraternity, and equality, where they rose up against the oppressive regime. I don’t know how the process will continue on French soil, and I also don’t know if the Russians are really using USDT networks to move *sanctioned* money. I only know that this kind of arrest proves and gives reason to those who argue that freedom, as we knew it, no longer makes sense. ### And I don’t know what else to tell you, my friend. Unfortunately, I have no conclusion. I wish I could end this article and give you hope that justice will respond to see what they’re accusing him of, but it [would be a lie on my part](https://stacker.news/items/560694). I can tell you, however, that if you’re reading this and have a NOSTR account and use bitcoin as part of your economy, you’re on the right path. Sites like Stacker News and others, as well as protocols like NOSTR, will gain greater importance as we open our eyes to fight the regime that seeks to abolish privacy as a human right. Today we can fight, and it doesn’t require much of us, other than to promote what we are doing now. And I’ll end by asking the same question that @FmpPerspective did: [*are we still allowed to ask questions?*](https://stacker.news/items/662413) originally posted at https://stacker.news/items/663527 @ 5d4b6c8d:8a1c1ee3
2024-08-26 17:50:00This was my first year betting on preseason football and I came out about 20% ahead. My operating assumption was just that no one should be a heavy preseason favorite, so I took any team that was at least +200 to win outright. I'm really looking forward to the real season starting. I've got my eyes on that Raiders vs Chargers opener. Every year the Bolts underachieve, while the Raiders overachieve (based on expected wins). Nitrobetting got some NBA futures up. I took OKC at +750 and the Bucks at +1200 to win the title. What are the upcoming events you're looking forward to? originally posted at https://stacker.news/items/662590
@ 5d4b6c8d:8a1c1ee3
2024-08-26 17:50:00This was my first year betting on preseason football and I came out about 20% ahead. My operating assumption was just that no one should be a heavy preseason favorite, so I took any team that was at least +200 to win outright. I'm really looking forward to the real season starting. I've got my eyes on that Raiders vs Chargers opener. Every year the Bolts underachieve, while the Raiders overachieve (based on expected wins). Nitrobetting got some NBA futures up. I took OKC at +750 and the Bucks at +1200 to win the title. What are the upcoming events you're looking forward to? originally posted at https://stacker.news/items/662590 @ 5d4b6c8d:8a1c1ee3
2024-08-26 17:01:11There's a very interesting dynamic developing in the American political media landscape. Don't worry, this post isn't explicitly political. One of the huge incentive problems in media is needing access to important people in order to cover them. Objective, or otherwise critical, journalists may be denied access, while favorably biased journalists are granted it. This is known as "access journalism". Despite being a very well-known problem, it remains an intractable issue for the industry. The Kamala Harris campaign has been blatantly denying access to even friendly outlets, which violates the basic logic of access journalism. The expectation then is that she'll get more objective or critical coverage, and I think we've been seeing that. Part of why this is so interesting to me is that the American corporate press has a dramatic bias towards Democrats and against Trump (even more so than a generic Republican). Bias and incentives are clashing. I often say that outcomes follow incentives. If so, then we should expect to see even more critical coverage of Kamala, unless she begins granting more press access. originally posted at https://stacker.news/items/662537
@ 5d4b6c8d:8a1c1ee3
2024-08-26 17:01:11There's a very interesting dynamic developing in the American political media landscape. Don't worry, this post isn't explicitly political. One of the huge incentive problems in media is needing access to important people in order to cover them. Objective, or otherwise critical, journalists may be denied access, while favorably biased journalists are granted it. This is known as "access journalism". Despite being a very well-known problem, it remains an intractable issue for the industry. The Kamala Harris campaign has been blatantly denying access to even friendly outlets, which violates the basic logic of access journalism. The expectation then is that she'll get more objective or critical coverage, and I think we've been seeing that. Part of why this is so interesting to me is that the American corporate press has a dramatic bias towards Democrats and against Trump (even more so than a generic Republican). Bias and incentives are clashing. I often say that outcomes follow incentives. If so, then we should expect to see even more critical coverage of Kamala, unless she begins granting more press access. originally posted at https://stacker.news/items/662537 @ 0271e1b9:ad8cff90
2024-08-26 16:33:28Hey everyone, So during the weekend I launched a little side project called: # "A Stoic Resurrection" https://image.nostr.build/682ddced4e4c823dcdc28bd34cc920ce0802964b170f9fa08295a89afe08df6c.jpg For now I will be sharing my favorite quotes from both historical and contemporary thinkers in the form of photos or short videos, plus some of my own thoughts, as I have noticed they seem to be very much aligned with the Stoic philosophy in general. I played around with some ideas regarding the design and aesthetics, and settled on this kind of style for now: *Photo examples* https://image.nostr.build/878bf80e40c522320820e766723dcd7b2ea5a4029dc8effd9c66a56f0fbbbc54.jpg https://image.nostr.build/3d994d3fb52def142d4b331ef0edb53a9862c8ab071d57da580a8fa08430198a.jpg https://image.nostr.build/d583755e9065cc5c49357ead1734e7e2ab5d43c56bd3345cb14331cab61cd505.jpg *Video examples* https://youtube.com/shorts/OMKKRQ4zNLM https://youtube.com/shorts/UkFBFBniCp8 For now I'm using copyright free images from [Unsplash](https://unsplash.com/) plus copyright free recordings of classical music via [Musopen](https://musopen.org/) (starting off with Chopin) for the content as per my *Open Source Culture* philosophy. **The current goal is to post 1 quote per day on average.** I do have some additional ideas for the future, but as I said, this is a side project and how much time & energy I'm going to invest in this will depend both on the amount of free(ish) time I have on hand, my current level of interest in the subject, as well as how much demand & audience there is (or isn't) for this kind of content. ### Please feel free to share your thoughts, criticisms, suggestions, and perhaps some of your personal favorite Stoic thinkers / ideas from both past and the present that have caught your attention. **Oh, and of course, if stoic philosophy sounds like your cup of tea, please feel free to give the project a follow on your preferred social media platform(s) and/or show your appreciation with zaps:** nostr: nostr:npub1angxrnwzujemyzkhgef2gwcy0s4ayjh62574p8g2xwnlfp8pxeaq4frrpe [X](https://x.com/stoic_resurrect) [YouTube](https://www.youtube.com/channel/UCb5MZ0YL7BlBLFKHpLVAHkg) [Instagram](https://www.instagram.com/stoic_resurrection/) [TikTok](https://www.tiktok.com/@stoic_resurrection) ### Peace & love, ### Kontext
@ 0271e1b9:ad8cff90
2024-08-26 16:33:28Hey everyone, So during the weekend I launched a little side project called: # "A Stoic Resurrection" https://image.nostr.build/682ddced4e4c823dcdc28bd34cc920ce0802964b170f9fa08295a89afe08df6c.jpg For now I will be sharing my favorite quotes from both historical and contemporary thinkers in the form of photos or short videos, plus some of my own thoughts, as I have noticed they seem to be very much aligned with the Stoic philosophy in general. I played around with some ideas regarding the design and aesthetics, and settled on this kind of style for now: *Photo examples* https://image.nostr.build/878bf80e40c522320820e766723dcd7b2ea5a4029dc8effd9c66a56f0fbbbc54.jpg https://image.nostr.build/3d994d3fb52def142d4b331ef0edb53a9862c8ab071d57da580a8fa08430198a.jpg https://image.nostr.build/d583755e9065cc5c49357ead1734e7e2ab5d43c56bd3345cb14331cab61cd505.jpg *Video examples* https://youtube.com/shorts/OMKKRQ4zNLM https://youtube.com/shorts/UkFBFBniCp8 For now I'm using copyright free images from [Unsplash](https://unsplash.com/) plus copyright free recordings of classical music via [Musopen](https://musopen.org/) (starting off with Chopin) for the content as per my *Open Source Culture* philosophy. **The current goal is to post 1 quote per day on average.** I do have some additional ideas for the future, but as I said, this is a side project and how much time & energy I'm going to invest in this will depend both on the amount of free(ish) time I have on hand, my current level of interest in the subject, as well as how much demand & audience there is (or isn't) for this kind of content. ### Please feel free to share your thoughts, criticisms, suggestions, and perhaps some of your personal favorite Stoic thinkers / ideas from both past and the present that have caught your attention. **Oh, and of course, if stoic philosophy sounds like your cup of tea, please feel free to give the project a follow on your preferred social media platform(s) and/or show your appreciation with zaps:** nostr: nostr:npub1angxrnwzujemyzkhgef2gwcy0s4ayjh62574p8g2xwnlfp8pxeaq4frrpe [X](https://x.com/stoic_resurrect) [YouTube](https://www.youtube.com/channel/UCb5MZ0YL7BlBLFKHpLVAHkg) [Instagram](https://www.instagram.com/stoic_resurrection/) [TikTok](https://www.tiktok.com/@stoic_resurrection) ### Peace & love, ### Kontext @ 5d4b6c8d:8a1c1ee3
2024-08-26 16:27:09This is your chance to update your predictions from July: https://stacker.news/items/619305/r/Undisciplined. August picks are due before the end of August. If you're new, check out the [June post](https://stacker.news/items/585231/r/Undisciplined) for details. This contest will be open to new entrants all the way through the end of the NBA regular season. If you want to join, put your predictions in the comments for MVP, Champion, and All NBA 1st Team. ## Current Predictions | | @Undisciplined | @grayruby | @gnilma | @BitcoinAbhi | @Bell_curve | @0xbitcoiner | |-|------------------|---------------|--------------|---------------------|-------------------|-----------------| | Champ | OKC | Pacers | OKC | Denver | Celtics | Pacers | | MVP | Luka | Giannis | SGA | Luka | Luka | Jokic | | All NBA | Jokic | Jokic | SGA | Jokic | Jokic | Jokic | | | Giannis | Giannis | Jokic | Giannis | Giannis | Giannis | | | Luka | Luka | Luka | Luka | Luka | Luka | | | Ant | Mitchell | Brunson | Ant | Ant | Ant | | | SGA | Brunson | Wemby | SGA | SGA | Brunson | The only change last month was me switching my title pick to OKC. # Prize 1334 sats (plus all future zaps) originally posted at https://stacker.news/items/662489
@ 5d4b6c8d:8a1c1ee3
2024-08-26 16:27:09This is your chance to update your predictions from July: https://stacker.news/items/619305/r/Undisciplined. August picks are due before the end of August. If you're new, check out the [June post](https://stacker.news/items/585231/r/Undisciplined) for details. This contest will be open to new entrants all the way through the end of the NBA regular season. If you want to join, put your predictions in the comments for MVP, Champion, and All NBA 1st Team. ## Current Predictions | | @Undisciplined | @grayruby | @gnilma | @BitcoinAbhi | @Bell_curve | @0xbitcoiner | |-|------------------|---------------|--------------|---------------------|-------------------|-----------------| | Champ | OKC | Pacers | OKC | Denver | Celtics | Pacers | | MVP | Luka | Giannis | SGA | Luka | Luka | Jokic | | All NBA | Jokic | Jokic | SGA | Jokic | Jokic | Jokic | | | Giannis | Giannis | Jokic | Giannis | Giannis | Giannis | | | Luka | Luka | Luka | Luka | Luka | Luka | | | Ant | Mitchell | Brunson | Ant | Ant | Ant | | | SGA | Brunson | Wemby | SGA | SGA | Brunson | The only change last month was me switching my title pick to OKC. # Prize 1334 sats (plus all future zaps) originally posted at https://stacker.news/items/662489 @ dd664d5e:5633d319
2024-08-24 07:57:16# We can talk about something else, now. Making boosts/quotes the primary way new users find a variety of topics is a fundamental flaw. We don't need boosts (which merely results in the main trending list trending even harder, as people feel safer boosting something that is already popular), and hashtags have become the mess they naturally will become. ## We need topical forums and relay-based community boards. This would actively encourage those of us who want to write on OtherTopics to write more on them, as we would have some chance of the material being found by those interested in it. And it would spare us having to win some general popularity contest, just to be able to converse about golfing, Hinduism, or veganism. Scrollable "timeline" feeds, even with AI assistance (like DVMs), don't accomplish this as well, as they eliminate the ability to skim the top-level and selectively read. You have to scroll, scroll, scroll. It would also reduce the overloading of the original posts with videos, which is starting to give Nostr a Tik-Tok vibe. There's nothing wrong with that, per se, and we should probably have clients like that, but it makes life hard for anyone who wants to have a deeper discussion. People scrolling have trouble even "seeing" a text-based OP, but using the written word is a true signal to the other people, that you are capable of carrying a conversation through text. ## Examples for other styles of client (I am including the Communities in Nostrudel and Satellite, even though they don't yet work, effectively.) Some of the things that set these clients apart, is that: 1. they are topic-first or thread-first, not person-first, 2. they sometimes allow voting (I suppose we could rank by zaps), 3. they often allow the user to override the default order and simply look at whatever is newest, most popular, or where their friends are currently active (i.e. they allow for easy sorting and filtering), 4. they cap the depth of threads to one or two levels, keep the indentation tiny, or offer a "flat" view, 5. they are primarily text-based (Reddit broke with this and now their main pages look really spammy), 6. they allow you to see all of the entries in the thread, at once, and simply actualize to display the entries that pop up in-between, 7. they often have some indication of what you have already read (this is application data) and allow you to sort for "stuff I haven't looked at, yet". https://i.nostr.build/uCx5YKMOsjhKBU5c.png https://i.nostr.build/hMkm2oKpos0pWaV9.png https://i.nostr.build/mGQONMw5RC8XKtph.png https://i.nostr.build/TCSkG1bPuMOL0jja.webp https://i.nostr.build/3fLjCSNdtefiZmAH.png https://i.nostr.build/BHgo7EKTK5FRIsVl.png
@ dd664d5e:5633d319
2024-08-24 07:57:16# We can talk about something else, now. Making boosts/quotes the primary way new users find a variety of topics is a fundamental flaw. We don't need boosts (which merely results in the main trending list trending even harder, as people feel safer boosting something that is already popular), and hashtags have become the mess they naturally will become. ## We need topical forums and relay-based community boards. This would actively encourage those of us who want to write on OtherTopics to write more on them, as we would have some chance of the material being found by those interested in it. And it would spare us having to win some general popularity contest, just to be able to converse about golfing, Hinduism, or veganism. Scrollable "timeline" feeds, even with AI assistance (like DVMs), don't accomplish this as well, as they eliminate the ability to skim the top-level and selectively read. You have to scroll, scroll, scroll. It would also reduce the overloading of the original posts with videos, which is starting to give Nostr a Tik-Tok vibe. There's nothing wrong with that, per se, and we should probably have clients like that, but it makes life hard for anyone who wants to have a deeper discussion. People scrolling have trouble even "seeing" a text-based OP, but using the written word is a true signal to the other people, that you are capable of carrying a conversation through text. ## Examples for other styles of client (I am including the Communities in Nostrudel and Satellite, even though they don't yet work, effectively.) Some of the things that set these clients apart, is that: 1. they are topic-first or thread-first, not person-first, 2. they sometimes allow voting (I suppose we could rank by zaps), 3. they often allow the user to override the default order and simply look at whatever is newest, most popular, or where their friends are currently active (i.e. they allow for easy sorting and filtering), 4. they cap the depth of threads to one or two levels, keep the indentation tiny, or offer a "flat" view, 5. they are primarily text-based (Reddit broke with this and now their main pages look really spammy), 6. they allow you to see all of the entries in the thread, at once, and simply actualize to display the entries that pop up in-between, 7. they often have some indication of what you have already read (this is application data) and allow you to sort for "stuff I haven't looked at, yet". https://i.nostr.build/uCx5YKMOsjhKBU5c.png https://i.nostr.build/hMkm2oKpos0pWaV9.png https://i.nostr.build/mGQONMw5RC8XKtph.png https://i.nostr.build/TCSkG1bPuMOL0jja.webp https://i.nostr.build/3fLjCSNdtefiZmAH.png https://i.nostr.build/BHgo7EKTK5FRIsVl.png @ 91687725:a0de48ea
2024-08-24 05:40:14こんにちは。Kateです。 最近ちょっとお休みしていますが、日本でビットコインを専門に扱う[Diamond Hands Magazine](https://diamondhandscommunity.substack.com/)に寄稿したりしてます。 私がビットコインと出会ったのは2011年、まだビットコイン利用者はとても少なかった時代です。たまたま身内にビットコイン界隈の人がいました。もしかしたら今でいうビト妻だったかも? まだビットコインが1ドル以下でおもちゃみたいな存在だった頃に知ったわけですが、その後勢いづいて、100ドル、1000ドルと価値が上がっていきました。 それを見て、ビットコインを少しずつ買って貯めておけば、将来リタイヤの蓄えになるかもと思ってお小遣い程度のビットコインを積立してました。でも、アクシデントで失くしちゃったんですよね。 その後、身内のごたごたで自分の生活が天地がひっくり返るように一変し、気がつけばカナダでただお金がないアジア系移民シングルマザー、しかも周りに家族が誰もいないという、非常にマイノリティな立場になりました。 人生、何事も経験。一度ビットコインを失くし、傷心もあり、数年はビットコインから離れました。でも気がつけばビットコインは冬の時代を終えて、また元気になっていたんですね。自分は海外でひとり子育てに追われ、なんとか生きてた感じですが! ビットコインが500ドルくらいになっていた時に困窮していた私は、ふとペーパーウォレットと呼ばれた当時の携帯可能ウォレット?に0.5btc 残っていたのを発見して速攻換金しましたね。悔やまれます。 その後、2017年頃、カナダで当時大手の割と使い勝手のいい取引所があることを知って、再度ビットコイン貯蓄にチャレンジしました。2年ほどで、ほぼ1ビットコインと10ETHくらいあったんですけどね、今度は取引所の代表者が行方不明になり、またもやビットコインを失くしました。 ふつうだったら、もうやめますよね。2回もなくしたら。 けれど、自分はかつてインターネットが始まったころのワクワクを経験していました。90年代半ば、新宿にできたばかりのインターネットカフェで、GIFがかろうじて表示できるグレーのブラウザ画面と対面しました。世界を変える技術を体験した時の感動は今でも忘れられません。 (こう書くと立派なオバサンなのがバレちゃいますね。ビットコインネイティブ世代の中では年長者) それから15年以上たって、初めてサトシナカモトのホワイトペーパーを読んだ時に、同じ衝撃を受けたのです。初めて実用化されたインターネット上で世界の誰とでも送り合えるマネー。その可能性は無限∞。 そのビットコインの進化を、実際に買ってみたり、使ってみたり、なくしたりしつつ、より深く知ろうと付き合ってきた自分は、いつの間にかビットコインを通して世の中のいろいろを見て考えるようになりました。 ビットコインが生まれ、実験段階を経て、すでに15年が経ちます。けれども、ビットコインは今でも多くの人から最も誤解されている技術・発明のように見えます。ここまで来たら、自分が生きている間に、ビットコインが世界とどう関わっていくのか見届けたいと思います! そして、私自身がビットコインを知ることで発見した世界や新しい価値観を、誰かに伝えられたらいいなと願って、このブログをスタートすることにしました。 今回は自己紹介という形になりましたが、私がビットコインを通して学んだことや気づいたことをこれから少しづつアップしてみます! 週1くらいのペースで投稿が目標です。よろしくお願いします。
@ 91687725:a0de48ea
2024-08-24 05:40:14こんにちは。Kateです。 最近ちょっとお休みしていますが、日本でビットコインを専門に扱う[Diamond Hands Magazine](https://diamondhandscommunity.substack.com/)に寄稿したりしてます。 私がビットコインと出会ったのは2011年、まだビットコイン利用者はとても少なかった時代です。たまたま身内にビットコイン界隈の人がいました。もしかしたら今でいうビト妻だったかも? まだビットコインが1ドル以下でおもちゃみたいな存在だった頃に知ったわけですが、その後勢いづいて、100ドル、1000ドルと価値が上がっていきました。 それを見て、ビットコインを少しずつ買って貯めておけば、将来リタイヤの蓄えになるかもと思ってお小遣い程度のビットコインを積立してました。でも、アクシデントで失くしちゃったんですよね。 その後、身内のごたごたで自分の生活が天地がひっくり返るように一変し、気がつけばカナダでただお金がないアジア系移民シングルマザー、しかも周りに家族が誰もいないという、非常にマイノリティな立場になりました。 人生、何事も経験。一度ビットコインを失くし、傷心もあり、数年はビットコインから離れました。でも気がつけばビットコインは冬の時代を終えて、また元気になっていたんですね。自分は海外でひとり子育てに追われ、なんとか生きてた感じですが! ビットコインが500ドルくらいになっていた時に困窮していた私は、ふとペーパーウォレットと呼ばれた当時の携帯可能ウォレット?に0.5btc 残っていたのを発見して速攻換金しましたね。悔やまれます。 その後、2017年頃、カナダで当時大手の割と使い勝手のいい取引所があることを知って、再度ビットコイン貯蓄にチャレンジしました。2年ほどで、ほぼ1ビットコインと10ETHくらいあったんですけどね、今度は取引所の代表者が行方不明になり、またもやビットコインを失くしました。 ふつうだったら、もうやめますよね。2回もなくしたら。 けれど、自分はかつてインターネットが始まったころのワクワクを経験していました。90年代半ば、新宿にできたばかりのインターネットカフェで、GIFがかろうじて表示できるグレーのブラウザ画面と対面しました。世界を変える技術を体験した時の感動は今でも忘れられません。 (こう書くと立派なオバサンなのがバレちゃいますね。ビットコインネイティブ世代の中では年長者) それから15年以上たって、初めてサトシナカモトのホワイトペーパーを読んだ時に、同じ衝撃を受けたのです。初めて実用化されたインターネット上で世界の誰とでも送り合えるマネー。その可能性は無限∞。 そのビットコインの進化を、実際に買ってみたり、使ってみたり、なくしたりしつつ、より深く知ろうと付き合ってきた自分は、いつの間にかビットコインを通して世の中のいろいろを見て考えるようになりました。 ビットコインが生まれ、実験段階を経て、すでに15年が経ちます。けれども、ビットコインは今でも多くの人から最も誤解されている技術・発明のように見えます。ここまで来たら、自分が生きている間に、ビットコインが世界とどう関わっていくのか見届けたいと思います! そして、私自身がビットコインを知ることで発見した世界や新しい価値観を、誰かに伝えられたらいいなと願って、このブログをスタートすることにしました。 今回は自己紹介という形になりましたが、私がビットコインを通して学んだことや気づいたことをこれから少しづつアップしてみます! 週1くらいのペースで投稿が目標です。よろしくお願いします。 @ f8e6c643:03328ca9
2024-08-23 16:15:50Quality, authentic, original human artistic expression is always in demand. It has always been in demand, and it will continue to be in demand even beyond the age of AI. The internet today calls it “content.” It is how we seek to encapsulate and communicate ideas more richly, and it comes in various forms including written, audio, and visual. Anyone who creates content in any form knows that it is time consuming and costly to create and produce good content, especially to do so consistently. However, because of digital distribution methods, once released that content that was so costly to create is suddenly infinitely RE-producible with perfect fidelity for very little cost. The conundrum for artists/creators is that even though the demand for their work exists, and even though that work is costly to create, each final product they produce is infinite in supply as soon as they release it in digital form. Infinity has no value. Starting with the presumption that demand exists for art, and that it is reasonable for an artist to want to afford things like food, housing, and clothes, how do you make the work of creating content economically sustainable for those creating it? We find value in scarcity, and the scarce resources in the equation of content creation are ultimately the time, talent, and skill of the person doing the creating. People often want what a particular artist can produce. Perhaps it’s the artist’s skill, style, and precision; or perhaps it’s the artist’s particular interpretation and personality they find valuable. The skill, time, and talent/personality employed to create artistic expressions are valuable, and their supply cannot be easily reproduced/replicated even though the individual manifestations of them (the works of art) can be. This is, ultimately, what creators must figure out how to monetize if they are to make their work economically sustainable. So how much is an artist’s skill worth? How much is their time or their talent worth? How do you put a price tag on personality? Probably nobody, especially the artist, can really answer that objectively. However, with #value4value the consumers of an artist’s content can subjectively and individually decide for themselves how much it is worth to them. Nostr and Bitcoin give creators of every type of content the opportunity to directly own and control the distribution and monetization of their time, skill, and talent, more so than any other service or platform on the Internet. The #value4value approach to monetizing that content allows consumers to immediately have access to a creator’s work, and to individually place a subjective value on what it provides to them. The approach allows artists to focus on the work of creating art and building a reputation and relationship with their audience instead of worrying about how to control access to their work. And by using Nostr and Bitcoin, this approach allows artists to be free of the arbitrary rules and manipulation they face on other corporate ad-driven platforms. If you are a digital content creator, I think #value4value is worth giving a chance. The alternatives are increasingly less promising.
@ f8e6c643:03328ca9
2024-08-23 16:15:50Quality, authentic, original human artistic expression is always in demand. It has always been in demand, and it will continue to be in demand even beyond the age of AI. The internet today calls it “content.” It is how we seek to encapsulate and communicate ideas more richly, and it comes in various forms including written, audio, and visual. Anyone who creates content in any form knows that it is time consuming and costly to create and produce good content, especially to do so consistently. However, because of digital distribution methods, once released that content that was so costly to create is suddenly infinitely RE-producible with perfect fidelity for very little cost. The conundrum for artists/creators is that even though the demand for their work exists, and even though that work is costly to create, each final product they produce is infinite in supply as soon as they release it in digital form. Infinity has no value. Starting with the presumption that demand exists for art, and that it is reasonable for an artist to want to afford things like food, housing, and clothes, how do you make the work of creating content economically sustainable for those creating it? We find value in scarcity, and the scarce resources in the equation of content creation are ultimately the time, talent, and skill of the person doing the creating. People often want what a particular artist can produce. Perhaps it’s the artist’s skill, style, and precision; or perhaps it’s the artist’s particular interpretation and personality they find valuable. The skill, time, and talent/personality employed to create artistic expressions are valuable, and their supply cannot be easily reproduced/replicated even though the individual manifestations of them (the works of art) can be. This is, ultimately, what creators must figure out how to monetize if they are to make their work economically sustainable. So how much is an artist’s skill worth? How much is their time or their talent worth? How do you put a price tag on personality? Probably nobody, especially the artist, can really answer that objectively. However, with #value4value the consumers of an artist’s content can subjectively and individually decide for themselves how much it is worth to them. Nostr and Bitcoin give creators of every type of content the opportunity to directly own and control the distribution and monetization of their time, skill, and talent, more so than any other service or platform on the Internet. The #value4value approach to monetizing that content allows consumers to immediately have access to a creator’s work, and to individually place a subjective value on what it provides to them. The approach allows artists to focus on the work of creating art and building a reputation and relationship with their audience instead of worrying about how to control access to their work. And by using Nostr and Bitcoin, this approach allows artists to be free of the arbitrary rules and manipulation they face on other corporate ad-driven platforms. If you are a digital content creator, I think #value4value is worth giving a chance. The alternatives are increasingly less promising. @ e5272de9:a16a102f
2024-08-22 22:16:43One of the highlights for me at the first day of nostriga [nostriga](https://nostr.world) was a [panel discussion on web of trust](https://www.youtube.com/live/Zv766SV840k?t=8265) with [@Stuart Bowman](nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj), [@Pip the social graph guy](nostr:npub176p7sup477k5738qhxx0hk2n0cty2k5je5uvalzvkvwmw4tltmeqw7vgup), [@PABLOF7z](nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft), [@hzrd149](nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr), and [@ODELL](nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx). This to me is one of the most important topics in all of freedom tech, so I'd like to write up a few thoughts I had while they're still fresh on my mind, most of which revolve around the calculation of trust scores. Apologies if it's a bit long winded, don't seem to have the time to make it shorter. ## What do we use for raw data? There has been and on again, off again discussion during my time working in nostr over the sources of data that we should be using to calculate trust. In my mind we can think of the raw data as existing on a spectrum between two extremes. On one extreme, we have what I call *proxy indicators* of trust: follows, mutes, zaps, reactions, etc. People don't create this content with trust scores in mind, but we can and do use them as imperfect proxy indicators nontheless. And on the other extreme we have what I call *explicit trust attestations*, exemplified by the [proposed NIP-77](https://github.com/nostr-protocol/nips/pull/1208), authored by [Lez](nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume), the heart and soul of which is that a fully explicit contextual trust attestation should have 3 fields: a context, a score, and a confidence. You fill in these fields, you say what you mean, and you mean what you say, leaving as little room for interpretation as possible. And then there is data that's in between these two extremes. A five star rating for a host on a couchsurfing platform or a vendor on an ecommerce site? A "superfollow" option in addition to a follow? These lie somewhere on the spectrum between proxy indicators on one end and explicit attestations of trust on the other. During the panel today, Pablo and pippellia expressed the opinion that explicit trust attestations are not the way to go. Two reasons that I recall: first, that no one wants to put an exact number to trust; and second, that no one will update those numbers even if their assessment changes. These critiques have some merit to them. But I believe they miss the bigger picture. # The bigger picture In the real world, there are two ways I can communicate trust: I can SHOW you, or I can TELL you. I can *demonstrate trust through the actions that I take*, such as following someone, or I can just straight up tell you that I trust someone in some context. So here's the question: on nostr, which is the correct method to communicate trust? Proxy indicators, or explicit attestations? Do we SHOW or do we TELL?  My view is that we don't have to pick. We have to use all relevant and available raw data across the entire spectrum from one extreme to the other.  Each of these two options has its advantages and its disadvantages. The advantage of proxy indicators is that users issue them freely and easily, the result being that we are awash in a sea of data. The primary disadvantage of proxy indicators is that they often don't mean what we want them to mean. If Alice follows Bob, does that mean she trusts him? Maybe. Or maybe not. More often not. And what about context? Do we have any way of knowing? So we use proxy indicators as a trust indicators because ... if it's the best or maybe even the only data we have, what else are we gonna do? To do better, I argue that we need to give users more options when it comes to issuing explicit indicators of trust. But of course they're not going to do that without a reason. So to give them a reason, we have to figure out *ahead of time* how we're going to use the data once it's available. We have to know how to incorporate explicit trust indicators into our web of trust calculations. For the sake of argument, let's assume that we have a large dataset of proxy trust indicators (SHOW ME data) plus a small but nontrivial dataset with explicit trust attestations (TELL ME data). What we want to do is to pool *all available relevant data together* when we calculate trust scores. But how exactly do we do that? Which brings me to my next topic. ## The calculation of trust scores How are we even calculating the "web of trust scores" that we see today? Wikifreedia, Coracle, and a growing list of other clients have such scores. I wish I had seen more discussion in today's panel about HOW these calculation are performed. To the best of my knowledge, most clients use the same or a similar method: fetch my follows; fetch Bob's followers; calculate the set of users who are in both sets; and count up how many you get. Sometimes adjustments are made, usually a ding based on mutes. But usually, that's it. That's the WoT score. I'll call this the "legacy WoT score" since it is basically the state of the art in nostr. The legacy WoT score can be a useful way to eliminate bots and bad actors. But it has a few disadvantages: it is, arguably, a bit of a popularity contest. It cannot see more than two hops away on your social graph. It's not very useful to new users who haven't yet built up their follows. And it's not clear how to use it to differentiate trust in different contexts. It seems strange to me that so many clients use this single method to calculate WoT scores, but with relatively little discussion on the merits of this method as opposed to other methods. Or whether other methods even exist, for that matter. Indeed, I believe there is another method to calculate trust scores that in most circumstances will turn out to be much more meaningful and useful. For the sake of this article, I will call this the "Grapevine WoT score" to distinguish it from the legacy WoT score. (Elsewhere I have used the phrase "influence score" in place of "Grapevine WoT score.") The Grapevine method is (currently) based on follows and mutes, but calculated using a method entirely distinct from the legacy method, detailed [here](https://brainstorm.ninja/#/grapevine/influenceScore) (where it is called simply the "influence score"). The Grapevine method has several advantages over the legacy method, but one in particular on the topic of SHOW versus TELL: the Grapevine method can take multiple distinct classes of data following distinct formats and pool them together, synthesizing and distilling them into a single Grapevine WoT score. By choosing different datasets, different scores corresponding to different contexts can be generated. ## The future So here's my prediction on how the future will play out. 1. The Grapevine method of trust score calculation is going to rely -- at first -- primarily on proxy indicators of trust (follows, mutes, zaps, reactions, etc) -- SHOW ME data -- because that’s the data that’s available to us in large quantities. 2. These contextual Grapevine scores will turn out to be surprisingly useful. 3. *People will learn to game the scores by changing their behavior.* 5. Consumers of trust data will gradually discover that SHOW ME data is becoming less and less reliable. 6. Authors of raw trust data will gradually learn that if they want their voices to be heard, they will need to communicate trust more explicitly. In ways that are harder to game. They will begin to move the needle ever so gradually towards TELL ME data. 7. Over time, larger datasets of TELL ME data will be available for input into Grapevine WoT scores. 8. As SHOW ME data becomes less reliable, and TELL ME data becomes more available, contextual Grapevine WoT scores will become more fine grained in terms of context and more reliable. Of course, none of this will happen unless and until we start calculating Grapevine WoT scores and putting them to good use. To that end, several of us are working on the generation of these scores at [brainSToRm](https://brainstorm.ninja). Right now, it's a slog to download the data to the browser. But we're working on improving the UX. And if you make it through the slog, you can export a NIP-51 list of the top-scoring pubkeys, minus the ones you're already following, and use them at clients like Amethyst or Coracle to generate a feed of content coming from the most highly "trusted" users whom you're not already following. A feed that is CUSTOMIZED by YOUR Grapevine. So there you have it, my defense of explicit trust attestations.
@ e5272de9:a16a102f
2024-08-22 22:16:43One of the highlights for me at the first day of nostriga [nostriga](https://nostr.world) was a [panel discussion on web of trust](https://www.youtube.com/live/Zv766SV840k?t=8265) with [@Stuart Bowman](nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj), [@Pip the social graph guy](nostr:npub176p7sup477k5738qhxx0hk2n0cty2k5je5uvalzvkvwmw4tltmeqw7vgup), [@PABLOF7z](nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft), [@hzrd149](nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr), and [@ODELL](nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx). This to me is one of the most important topics in all of freedom tech, so I'd like to write up a few thoughts I had while they're still fresh on my mind, most of which revolve around the calculation of trust scores. Apologies if it's a bit long winded, don't seem to have the time to make it shorter. ## What do we use for raw data? There has been and on again, off again discussion during my time working in nostr over the sources of data that we should be using to calculate trust. In my mind we can think of the raw data as existing on a spectrum between two extremes. On one extreme, we have what I call *proxy indicators* of trust: follows, mutes, zaps, reactions, etc. People don't create this content with trust scores in mind, but we can and do use them as imperfect proxy indicators nontheless. And on the other extreme we have what I call *explicit trust attestations*, exemplified by the [proposed NIP-77](https://github.com/nostr-protocol/nips/pull/1208), authored by [Lez](nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume), the heart and soul of which is that a fully explicit contextual trust attestation should have 3 fields: a context, a score, and a confidence. You fill in these fields, you say what you mean, and you mean what you say, leaving as little room for interpretation as possible. And then there is data that's in between these two extremes. A five star rating for a host on a couchsurfing platform or a vendor on an ecommerce site? A "superfollow" option in addition to a follow? These lie somewhere on the spectrum between proxy indicators on one end and explicit attestations of trust on the other. During the panel today, Pablo and pippellia expressed the opinion that explicit trust attestations are not the way to go. Two reasons that I recall: first, that no one wants to put an exact number to trust; and second, that no one will update those numbers even if their assessment changes. These critiques have some merit to them. But I believe they miss the bigger picture. # The bigger picture In the real world, there are two ways I can communicate trust: I can SHOW you, or I can TELL you. I can *demonstrate trust through the actions that I take*, such as following someone, or I can just straight up tell you that I trust someone in some context. So here's the question: on nostr, which is the correct method to communicate trust? Proxy indicators, or explicit attestations? Do we SHOW or do we TELL?  My view is that we don't have to pick. We have to use all relevant and available raw data across the entire spectrum from one extreme to the other.  Each of these two options has its advantages and its disadvantages. The advantage of proxy indicators is that users issue them freely and easily, the result being that we are awash in a sea of data. The primary disadvantage of proxy indicators is that they often don't mean what we want them to mean. If Alice follows Bob, does that mean she trusts him? Maybe. Or maybe not. More often not. And what about context? Do we have any way of knowing? So we use proxy indicators as a trust indicators because ... if it's the best or maybe even the only data we have, what else are we gonna do? To do better, I argue that we need to give users more options when it comes to issuing explicit indicators of trust. But of course they're not going to do that without a reason. So to give them a reason, we have to figure out *ahead of time* how we're going to use the data once it's available. We have to know how to incorporate explicit trust indicators into our web of trust calculations. For the sake of argument, let's assume that we have a large dataset of proxy trust indicators (SHOW ME data) plus a small but nontrivial dataset with explicit trust attestations (TELL ME data). What we want to do is to pool *all available relevant data together* when we calculate trust scores. But how exactly do we do that? Which brings me to my next topic. ## The calculation of trust scores How are we even calculating the "web of trust scores" that we see today? Wikifreedia, Coracle, and a growing list of other clients have such scores. I wish I had seen more discussion in today's panel about HOW these calculation are performed. To the best of my knowledge, most clients use the same or a similar method: fetch my follows; fetch Bob's followers; calculate the set of users who are in both sets; and count up how many you get. Sometimes adjustments are made, usually a ding based on mutes. But usually, that's it. That's the WoT score. I'll call this the "legacy WoT score" since it is basically the state of the art in nostr. The legacy WoT score can be a useful way to eliminate bots and bad actors. But it has a few disadvantages: it is, arguably, a bit of a popularity contest. It cannot see more than two hops away on your social graph. It's not very useful to new users who haven't yet built up their follows. And it's not clear how to use it to differentiate trust in different contexts. It seems strange to me that so many clients use this single method to calculate WoT scores, but with relatively little discussion on the merits of this method as opposed to other methods. Or whether other methods even exist, for that matter. Indeed, I believe there is another method to calculate trust scores that in most circumstances will turn out to be much more meaningful and useful. For the sake of this article, I will call this the "Grapevine WoT score" to distinguish it from the legacy WoT score. (Elsewhere I have used the phrase "influence score" in place of "Grapevine WoT score.") The Grapevine method is (currently) based on follows and mutes, but calculated using a method entirely distinct from the legacy method, detailed [here](https://brainstorm.ninja/#/grapevine/influenceScore) (where it is called simply the "influence score"). The Grapevine method has several advantages over the legacy method, but one in particular on the topic of SHOW versus TELL: the Grapevine method can take multiple distinct classes of data following distinct formats and pool them together, synthesizing and distilling them into a single Grapevine WoT score. By choosing different datasets, different scores corresponding to different contexts can be generated. ## The future So here's my prediction on how the future will play out. 1. The Grapevine method of trust score calculation is going to rely -- at first -- primarily on proxy indicators of trust (follows, mutes, zaps, reactions, etc) -- SHOW ME data -- because that’s the data that’s available to us in large quantities. 2. These contextual Grapevine scores will turn out to be surprisingly useful. 3. *People will learn to game the scores by changing their behavior.* 5. Consumers of trust data will gradually discover that SHOW ME data is becoming less and less reliable. 6. Authors of raw trust data will gradually learn that if they want their voices to be heard, they will need to communicate trust more explicitly. In ways that are harder to game. They will begin to move the needle ever so gradually towards TELL ME data. 7. Over time, larger datasets of TELL ME data will be available for input into Grapevine WoT scores. 8. As SHOW ME data becomes less reliable, and TELL ME data becomes more available, contextual Grapevine WoT scores will become more fine grained in terms of context and more reliable. Of course, none of this will happen unless and until we start calculating Grapevine WoT scores and putting them to good use. To that end, several of us are working on the generation of these scores at [brainSToRm](https://brainstorm.ninja). Right now, it's a slog to download the data to the browser. But we're working on improving the UX. And if you make it through the slog, you can export a NIP-51 list of the top-scoring pubkeys, minus the ones you're already following, and use them at clients like Amethyst or Coracle to generate a feed of content coming from the most highly "trusted" users whom you're not already following. A feed that is CUSTOMIZED by YOUR Grapevine. So there you have it, my defense of explicit trust attestations. @ 6ad3e2a3:c90b7740
2024-08-21 17:42:18When I used to pick NFL games against the spread for [RotoWire](https://www.rotowire.com/), I would joke after a bad week that my picks were perfect, but it was the games that got themselves wrong. I’ve touched on this concept quite a bit here too — [But My Process Was Good](https://www.chrisliss.com/p/but-my-process-was-good) and [Why Blake Snell Should Win The NL Cy Young Award This Year](https://www.realmansports.com/p/why-blake-snell-should-win-the-nl) both highlight the category error of speciously applying tools of prediction toward the past. Tldr: the past is in no need of predicting because it already happened. The error stems in part from mistaking the map for the territory — once the forecasts are substituted for reality itself, the future has already happened, so to speak — it’s right there on the spread sheet! — so it is no different than the past which has also already happened. So any tool that can be applied to the future can equally be applied to the past. This is how we get [Sam Harris arguing that mRNA shot mandates were correct](https://x.com/KanekoaTheGreat/status/1615951624882782209?s=20) because covid *could have been* more deadly (and implicitly that the shots could have been safe and effective.) It’s one thing to model a possible future (with the requisite humility your forecasts might be off base), and quite another to force your failed model onto past events as though they were still in any doubt. If this is confusing, that’s because a lot of us have been so trained to think this way we don’t even notice we’re doing it. Examples are legion where we identify what we deem an optimal process to achieve a desired result, then substitute that process for that result. If the local police department believes it needs to arrest 50 people per month to reduce violent crime and incentivizes its officers to make those arrests, pretty soon arrests will be the goal, and people will get arrested for more and more non-violent offenses to make the quota. If mass-vaccination is believed to be the key to good public health policy, then authorities will incentivize uptake, disincentivize bodily autonomy and not care one bit whether a person had prior immunity from the virus already, if the injection actually stops the spread or has myriad serious side effects. If the result (public health) were still the goal, the idea of forcing someone with natural immunity to inject himself with an experimental technology [would be ludicrous](https://x.com/goddeketal/status/1708104013936222641?s=20). But once the goal shifted to the process (mass vaccination), it made perfect sense. Once we substitute the process by which we achieve something for the achievement itself (which might temporarily be sound, if you’re, say, training for a marathon), we create distortions in our thought processes and policies. But I want to go back to where the bait and switch of process and result gets most absurd, and that’s when it comes to time. In this case, you’re not arresting jaywalkers to make your quota, you’re lamenting that had jaywalking correlated better with domestic violence, your policy would have been the correct one. In other words, you’re not only substituting the process for the result in a forward-looking way, you are doing so even though you now have complete access to the result because it has already happened. And yet you are still grasping via your spread sheet for some other reality that might have been! You do not need to forecast events that have already happened. The probability of the Chiefs winning the Super Bowl last year is 100 percent. We no longer need your tools to tell us how much to bet on them. The game is over, and whatever we believed the probability to have been before the fact is irrelevant. That’s why I wrote about [Blake Snell’s Cy Young Award case](https://www.realmansports.com/p/why-blake-snell-should-win-the-nl) — despite Snell allowing 42 percent fewer runs on his watch than Spencer Strider — people are still arguing for Strider because the way Strider pitched *portended* fewer runs allowed than Snell. It is not enough for them that the results (runs allowed) are already in. They argue that because Strider’s profile forecasts a better result than Snell’s, Strider should win. Or, put differently, had we simulated 1000 seasons for each, Strider’s would on average be better. They are upset Snell got “lucky” as though reality must be stripped of all the effects for which we can’t attribute to particular causes and normalized in order to fit our model. . . . Mistaking the past for the future is one form of this category error, but it can also happen in reverse wherein one mistakes the future for the past. You see it when people treat future events at fait accompli and proceed as such. The notion of talking past the sale, e.g., if the car salesman says: “You’ll love this car and be thanking yourself for saving so much money on gas!” he’s treating your possible future agreement on a price as something that’s already happened. People also do this to avoid responsibility, pretending as though there’s nothing one can do about some injustice or that it’s too late to make amends for wrongdoing. They think and talk about the future as though it’s the past. When our dog Oscar got poisoned from a particular kind of caterpillar ([Largata do Pinheiro](https://www.setubalambiente.pt/lagarta-do-pinheiro/)) last winter, we brought him to the hospital with his tongue swelling so much it was stuck outside his mouth. The hospital treated him for a day, saying they could only wait and see, and he might lose his tongue (to necrosis) and have to get put down. We could have taken their approach of it not being in our hands, but instead we convinced them to let us break him out and took him to our holistic vet who sedated him, drained his salivary gland, massaged the tongue extensively with ozone and anti-bacterial herbs and sent him home with us that evening. [Oscar](https://njump.me/nevent1qqst6clec39drun4k97xyqy4ln06t9uc9g09fpa5fg5zruee3hvw8mszyzyujjulkrquksyekd5dkv6hdzv2n5zjstv3thywa844gtl4qplksqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyxhwumn8ghj7mn0wvhxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqt46763) who is passed out on the sofa next to me as I type this, only lost about 10 percent of the tongue, but otherwise made a full recovery. . . . I’m not sure why people so easily mistake cause for effect, process for results, future for past and vice-versa. If I had to speculate I’d say when our emotions get involved, we go from logical thinking to association, and associations work in both directions — effects and causes are associated without regard for which is which. The modus operandi of most advertising (and propaganda) is to seed associations in your mind between things it wants you to associate — it’s certainly not to convince you rationally which is a much more difficult task. Maybe the influencers, marketers and propagandists have simply found an angle they can exploit. Once those associations take hold, they can be powerful, and often no amount of rational argument will un-cement them. But I think that’s only part of the story. The other part is how most of us have been educated, and that's to focus on process not results. To be “process-oriented” not stuck in “results-based thinking.” This is a mark of erudition, of belonging to a certain class of people who have mastered this lesson. The class who trusts in modelers, forecasters and data-scientists waiting at the ready to be of service to The Science, even if it means treating the future as though it’s already happened and the past as though it can be re-forecast according to their models, conjugating reality, as it were, in the wrong tense.
@ 6ad3e2a3:c90b7740
2024-08-21 17:42:18When I used to pick NFL games against the spread for [RotoWire](https://www.rotowire.com/), I would joke after a bad week that my picks were perfect, but it was the games that got themselves wrong. I’ve touched on this concept quite a bit here too — [But My Process Was Good](https://www.chrisliss.com/p/but-my-process-was-good) and [Why Blake Snell Should Win The NL Cy Young Award This Year](https://www.realmansports.com/p/why-blake-snell-should-win-the-nl) both highlight the category error of speciously applying tools of prediction toward the past. Tldr: the past is in no need of predicting because it already happened. The error stems in part from mistaking the map for the territory — once the forecasts are substituted for reality itself, the future has already happened, so to speak — it’s right there on the spread sheet! — so it is no different than the past which has also already happened. So any tool that can be applied to the future can equally be applied to the past. This is how we get [Sam Harris arguing that mRNA shot mandates were correct](https://x.com/KanekoaTheGreat/status/1615951624882782209?s=20) because covid *could have been* more deadly (and implicitly that the shots could have been safe and effective.) It’s one thing to model a possible future (with the requisite humility your forecasts might be off base), and quite another to force your failed model onto past events as though they were still in any doubt. If this is confusing, that’s because a lot of us have been so trained to think this way we don’t even notice we’re doing it. Examples are legion where we identify what we deem an optimal process to achieve a desired result, then substitute that process for that result. If the local police department believes it needs to arrest 50 people per month to reduce violent crime and incentivizes its officers to make those arrests, pretty soon arrests will be the goal, and people will get arrested for more and more non-violent offenses to make the quota. If mass-vaccination is believed to be the key to good public health policy, then authorities will incentivize uptake, disincentivize bodily autonomy and not care one bit whether a person had prior immunity from the virus already, if the injection actually stops the spread or has myriad serious side effects. If the result (public health) were still the goal, the idea of forcing someone with natural immunity to inject himself with an experimental technology [would be ludicrous](https://x.com/goddeketal/status/1708104013936222641?s=20). But once the goal shifted to the process (mass vaccination), it made perfect sense. Once we substitute the process by which we achieve something for the achievement itself (which might temporarily be sound, if you’re, say, training for a marathon), we create distortions in our thought processes and policies. But I want to go back to where the bait and switch of process and result gets most absurd, and that’s when it comes to time. In this case, you’re not arresting jaywalkers to make your quota, you’re lamenting that had jaywalking correlated better with domestic violence, your policy would have been the correct one. In other words, you’re not only substituting the process for the result in a forward-looking way, you are doing so even though you now have complete access to the result because it has already happened. And yet you are still grasping via your spread sheet for some other reality that might have been! You do not need to forecast events that have already happened. The probability of the Chiefs winning the Super Bowl last year is 100 percent. We no longer need your tools to tell us how much to bet on them. The game is over, and whatever we believed the probability to have been before the fact is irrelevant. That’s why I wrote about [Blake Snell’s Cy Young Award case](https://www.realmansports.com/p/why-blake-snell-should-win-the-nl) — despite Snell allowing 42 percent fewer runs on his watch than Spencer Strider — people are still arguing for Strider because the way Strider pitched *portended* fewer runs allowed than Snell. It is not enough for them that the results (runs allowed) are already in. They argue that because Strider’s profile forecasts a better result than Snell’s, Strider should win. Or, put differently, had we simulated 1000 seasons for each, Strider’s would on average be better. They are upset Snell got “lucky” as though reality must be stripped of all the effects for which we can’t attribute to particular causes and normalized in order to fit our model. . . . Mistaking the past for the future is one form of this category error, but it can also happen in reverse wherein one mistakes the future for the past. You see it when people treat future events at fait accompli and proceed as such. The notion of talking past the sale, e.g., if the car salesman says: “You’ll love this car and be thanking yourself for saving so much money on gas!” he’s treating your possible future agreement on a price as something that’s already happened. People also do this to avoid responsibility, pretending as though there’s nothing one can do about some injustice or that it’s too late to make amends for wrongdoing. They think and talk about the future as though it’s the past. When our dog Oscar got poisoned from a particular kind of caterpillar ([Largata do Pinheiro](https://www.setubalambiente.pt/lagarta-do-pinheiro/)) last winter, we brought him to the hospital with his tongue swelling so much it was stuck outside his mouth. The hospital treated him for a day, saying they could only wait and see, and he might lose his tongue (to necrosis) and have to get put down. We could have taken their approach of it not being in our hands, but instead we convinced them to let us break him out and took him to our holistic vet who sedated him, drained his salivary gland, massaged the tongue extensively with ozone and anti-bacterial herbs and sent him home with us that evening. [Oscar](https://njump.me/nevent1qqst6clec39drun4k97xyqy4ln06t9uc9g09fpa5fg5zruee3hvw8mszyzyujjulkrquksyekd5dkv6hdzv2n5zjstv3thywa844gtl4qplksqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyxhwumn8ghj7mn0wvhxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqt46763) who is passed out on the sofa next to me as I type this, only lost about 10 percent of the tongue, but otherwise made a full recovery. . . . I’m not sure why people so easily mistake cause for effect, process for results, future for past and vice-versa. If I had to speculate I’d say when our emotions get involved, we go from logical thinking to association, and associations work in both directions — effects and causes are associated without regard for which is which. The modus operandi of most advertising (and propaganda) is to seed associations in your mind between things it wants you to associate — it’s certainly not to convince you rationally which is a much more difficult task. Maybe the influencers, marketers and propagandists have simply found an angle they can exploit. Once those associations take hold, they can be powerful, and often no amount of rational argument will un-cement them. But I think that’s only part of the story. The other part is how most of us have been educated, and that's to focus on process not results. To be “process-oriented” not stuck in “results-based thinking.” This is a mark of erudition, of belonging to a certain class of people who have mastered this lesson. The class who trusts in modelers, forecasters and data-scientists waiting at the ready to be of service to The Science, even if it means treating the future as though it’s already happened and the past as though it can be re-forecast according to their models, conjugating reality, as it were, in the wrong tense. @ ec09d831:42c80ce4
2024-08-21 17:27:14## Nostr Nedir? Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım: ### Basitlik Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar. ### Esneklik Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim. ### Doğrulanabilirlik Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır. ### Anahtarları Anlamak Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun. ### Protokol vs İstemci Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım. İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri: [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.] [Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.] [Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.] [Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.] [Habla](https://habla.news/) (Web) [Kolay blog yaratımı.] [Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.] [Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.] [Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.] Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz #### Adım 1: Uygulama yükleme * Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst * Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır. * Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz. * Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. #### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma * “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin. * “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. * Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz! * Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz. * Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır. * “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın. * “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir. * Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz. * “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır. * “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur. * “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz. * “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin. * Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin. #### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın. Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır. Röle listesi: 140.f7z.io astral.ninja bevo.nostr1.com bitcoiner.social brb.io carnivore-diet-relay.denizenid.com eu.purplerelay.com expensive-relay.fiatjaf.com feeds.nostr.band/popular fiatjaf.com n.wingu.se nos.lol nostr-pub.semisol.dev nostr-relay.wlvs.space nostr.21l.st nostr.band nostr.bitcoiner.social nostr.blipme.app nostr.kollider.xyz nostr.liberty.fans nostr.mutinywallet.com nostr.orangepill.dev nostr.pleb.network nostr.plebchain.org nostr.relayer.se nostr.satoshi.fun nostr.walletofsatoshi.com nostr.yuv.al nostr.zbd.gg nostr.zebedee.cloud nostr.zerofiat.world nostr1.tunnelsats.com nostream.denizenid.com nostria.space offchain.pub purplepag.es pyramid.fiatjaf.com relay.0xchat.com relay.benthecarman.com relay.bitcoinpark.com relay.current.fyi relay.damus.io relay.f7z.io relay.geyser.fund relay.mutinywallet.com relay.nostr.band relay.nostr.bg relay.nostr.net relay.nostr3.io relay.nostrati.com relay.nostrplebs.com relay.orangepill.dev relay.plebstr.com relay.primal.net relay.snort.band relay.snort.social relay.utxo.one relayable.org relayer.fiatjaf.com satstacker.cloud snort.social soloco.nl sound-money-relay.denizenid.com  **Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü. Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın: Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9 Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6 Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3 Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6 Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8 Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj 
@ ec09d831:42c80ce4
2024-08-21 17:27:14## Nostr Nedir? Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım: ### Basitlik Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar. ### Esneklik Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim. ### Doğrulanabilirlik Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır. ### Anahtarları Anlamak Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun. ### Protokol vs İstemci Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım. İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri: [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.] [Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.] [Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.] [Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.] [Habla](https://habla.news/) (Web) [Kolay blog yaratımı.] [Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.] [Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.] [Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.] Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz #### Adım 1: Uygulama yükleme * Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst * Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır. * Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz. * Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. #### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma * “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin. * “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. * Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz! * Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz. * Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır. * “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın. * “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir. * Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz. * “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır. * “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur. * “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz. * “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin. * Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin. #### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın. Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır. Röle listesi: 140.f7z.io astral.ninja bevo.nostr1.com bitcoiner.social brb.io carnivore-diet-relay.denizenid.com eu.purplerelay.com expensive-relay.fiatjaf.com feeds.nostr.band/popular fiatjaf.com n.wingu.se nos.lol nostr-pub.semisol.dev nostr-relay.wlvs.space nostr.21l.st nostr.band nostr.bitcoiner.social nostr.blipme.app nostr.kollider.xyz nostr.liberty.fans nostr.mutinywallet.com nostr.orangepill.dev nostr.pleb.network nostr.plebchain.org nostr.relayer.se nostr.satoshi.fun nostr.walletofsatoshi.com nostr.yuv.al nostr.zbd.gg nostr.zebedee.cloud nostr.zerofiat.world nostr1.tunnelsats.com nostream.denizenid.com nostria.space offchain.pub purplepag.es pyramid.fiatjaf.com relay.0xchat.com relay.benthecarman.com relay.bitcoinpark.com relay.current.fyi relay.damus.io relay.f7z.io relay.geyser.fund relay.mutinywallet.com relay.nostr.band relay.nostr.bg relay.nostr.net relay.nostr3.io relay.nostrati.com relay.nostrplebs.com relay.orangepill.dev relay.plebstr.com relay.primal.net relay.snort.band relay.snort.social relay.utxo.one relayable.org relayer.fiatjaf.com satstacker.cloud snort.social soloco.nl sound-money-relay.denizenid.com  **Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü. Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın: Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9 Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6 Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3 Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6 Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8 Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj  @ 5d4b6c8d:8a1c1ee3
2024-08-21 15:29:03I had something of an epiphany recently about needing to work for a cause I believe in, rather than just fiat mining. I was up all night thinking about the right fit and what my value proposition is. You all have helped me realize that there's real interest in my perspective (thank you), so that's part of the proposition. I was also reflecting on how limited the presence of most prominent libertarians is in the bitcoin ecosystem, despite the immense interest in their insights. That made me realize I can make at least a two-fold impact for a libertarian/free-market organization: my own content and integrating them into the bitcoin community. This is the first draft of a letter I'm planning on sending to the Libertarian Institute, which is run by the great Scott Horton. I'd love your feedback on this letter. The aim of it is simply to pique their interest and generate a follow up conversation. As it happens, the Libertarian Institute is based in Austin, so perhaps this will enable me to drop in on the SN HQ occasionally. ---------- Dear Libertarian Institute, I'm reaching out to express my interest in joining your amazing institute. I’ve been following Scott’s work since 2007 and deeply admired the late Will Grigg’s articles. I believe I can add to the impressive scholarship you're already doing, while also helping you reach an audience that is very interested in your work and opening new fundraising opportunities. I finished my economics PhD during the pandemic. Like most new graduates, I took what work was available, but now I’m looking to dedicate myself to spreading libertarianism and sound economics full-time. Some of my interests are economic geography (voting with your feet, jurisdictional arbitrage, secession, etc), political polarization, parallel institutions, bitcoin, and climate science. My academic training and research in those areas would give the Libertarian Institute another person to dissect the relentless stream of propaganda that comes out on those and other topics. For my own sanity, I've been writing about libertarianism and economics at Stacker News, on the side, for the past couple of years. The positive reception to Rothbardian libertarianism and economics there has made me realize that our ideological camp is missing out on some low-hanging fruit. This site is part of the bitcoin ecosystem, where demand for Austro-libertarian thought is very high, but our scholars have a very limited presence. I’ve found bitcoiners to be eager and willing to donate to those who are adding value in their spaces. I can help the Libertarian Institute establish itself as one of the intellectual pillars in this emerging libertarian community, both through my own contributions and by making your existing scholarship more visible there, as well as setting up the necessary technology to receive bitcoin donations and interact with their social media spaces. I wish you all the very best. Thank you for your work. Hopefully, I'll have a chance to continue this discussion with you soon. Sincerely, Undisciplined (not how I plan to sign the real letter) originally posted at https://stacker.news/items/657036
@ 5d4b6c8d:8a1c1ee3
2024-08-21 15:29:03I had something of an epiphany recently about needing to work for a cause I believe in, rather than just fiat mining. I was up all night thinking about the right fit and what my value proposition is. You all have helped me realize that there's real interest in my perspective (thank you), so that's part of the proposition. I was also reflecting on how limited the presence of most prominent libertarians is in the bitcoin ecosystem, despite the immense interest in their insights. That made me realize I can make at least a two-fold impact for a libertarian/free-market organization: my own content and integrating them into the bitcoin community. This is the first draft of a letter I'm planning on sending to the Libertarian Institute, which is run by the great Scott Horton. I'd love your feedback on this letter. The aim of it is simply to pique their interest and generate a follow up conversation. As it happens, the Libertarian Institute is based in Austin, so perhaps this will enable me to drop in on the SN HQ occasionally. ---------- Dear Libertarian Institute, I'm reaching out to express my interest in joining your amazing institute. I’ve been following Scott’s work since 2007 and deeply admired the late Will Grigg’s articles. I believe I can add to the impressive scholarship you're already doing, while also helping you reach an audience that is very interested in your work and opening new fundraising opportunities. I finished my economics PhD during the pandemic. Like most new graduates, I took what work was available, but now I’m looking to dedicate myself to spreading libertarianism and sound economics full-time. Some of my interests are economic geography (voting with your feet, jurisdictional arbitrage, secession, etc), political polarization, parallel institutions, bitcoin, and climate science. My academic training and research in those areas would give the Libertarian Institute another person to dissect the relentless stream of propaganda that comes out on those and other topics. For my own sanity, I've been writing about libertarianism and economics at Stacker News, on the side, for the past couple of years. The positive reception to Rothbardian libertarianism and economics there has made me realize that our ideological camp is missing out on some low-hanging fruit. This site is part of the bitcoin ecosystem, where demand for Austro-libertarian thought is very high, but our scholars have a very limited presence. I’ve found bitcoiners to be eager and willing to donate to those who are adding value in their spaces. I can help the Libertarian Institute establish itself as one of the intellectual pillars in this emerging libertarian community, both through my own contributions and by making your existing scholarship more visible there, as well as setting up the necessary technology to receive bitcoin donations and interact with their social media spaces. I wish you all the very best. Thank you for your work. Hopefully, I'll have a chance to continue this discussion with you soon. Sincerely, Undisciplined (not how I plan to sign the real letter) originally posted at https://stacker.news/items/657036 @ 4c96d763:80c3ee30
2024-08-21 04:00:40# Changes ## William Casarin (10): - temp ownership fix - fix FilterBuilder - update bindings - Add filter iteration - update build.rs to rusty's ccan rework - filter: expose more builder options - update bindings - filter: mutable since - filter: add from_json - since/limit mut methods pushed to [nostrdb-rs:refs/heads/master](http://git.jb55.com/nostrdb-rs/commit/4c89dcbca13168758eb41752225b4e486dbc9d20.html)
@ 4c96d763:80c3ee30
2024-08-21 04:00:40# Changes ## William Casarin (10): - temp ownership fix - fix FilterBuilder - update bindings - Add filter iteration - update build.rs to rusty's ccan rework - filter: expose more builder options - update bindings - filter: mutable since - filter: add from_json - since/limit mut methods pushed to [nostrdb-rs:refs/heads/master](http://git.jb55.com/nostrdb-rs/commit/4c89dcbca13168758eb41752225b4e486dbc9d20.html)