-

@ fd208ee8:0fd927c1
2025-02-02 10:33:19
# GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
## Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
## OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a [self-hosted OneDev instance](https://onedev.gitcitadel.eu). In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our [team's GitHub projects](https://github.com/ShadowySupercode) will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted [GitWorkshop instance](nostr:naddr1qvzqqqrhnypzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqy88wumn8ghj7mn0wvhxcmmv9uqq5emfw33kjarpv3jkcs83wav).
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
## Next Infrasteps
### Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our [Alexandria client](https://next-alexandria.gitcitadel.eu). We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based [Behave feature test](https://behave.readthedocs.io/en/latest/) for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to *Done*. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

### Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
### Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our [status page](https://status.gitcitadel.com). We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our [GitCitadel DevOps npub](nostr:npub16p0fdr2xccfs07hykx92t0cascac69xjuwaq38kjqy3aawt5hx8s82feyj), to make sure you don't miss out on the IT action.
## Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-

@ b17fccdf:b7211155
2025-02-01 18:41:27
#### **Next new resources about the MiniBolt guide have been released**:
---
* 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1)
* 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png)
* 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
* 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info)
* 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos)
* 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info)
---
Enjoy it MiniBolter! 💙
-

@ 0271e1b9:ad8cff90
2025-02-01 07:39:31
**I study the greats.**
For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better.
Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person.
> “You must value learning above everything else.”
― Robert Greene
> “Those who have a 'why' to live, can bear with almost any 'how'.”
― Viktor E. Frankl
> “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.”
― Phil Stutz
> “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.”
― Marcus Tullius Cicero
> “Error correction is the basis of all intelligence.”
― Jeff Booth
> “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living."
― Jesse Enkamp
> "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him."
— Confucius
> “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.”
― Michelangelo
> “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.”
― Marcus Tullius Cicero
> “You either bleed soul into your work, or let the work bleed out your soul.”
― Pran Yoganthan
> "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.”
― Michael Sugrue
> "The strong do what they can and the weak suffer what they must."
― Thucydides
> “The brain is the most powerful weapon in the world.”
― David Goggins
> “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.”
― Friedrich Nietzsche
> "Consciousness is awareness with a choice."
― Thomas Campbell
> “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.”
― Epictetus
> “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.”
— John Vervaeke
> “It is impossible for a man to learn what he thinks he already knows.”
― Epictetus
> “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.”
― Michael Behrens
> “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.”
― Jiddu Krishnamurti
> “This is your life. You’re accountable. What are you gonna do about that?”
― James Hollis
By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection)
*Peace & Love,*
*[Kontext](https://linktr.ee/mckontext)*
*Block height 881,748*
-

@ 82100056:e198089f
2025-01-29 14:22:06
-

@ ec42c765:328c0600
2025-01-26 00:08:54
# カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

# カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
#### 対応クライアント
- [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst)
- [FreeFrom](https://freefrom.space/)
- [nostter](https://nostter.app/)
- [Rabbit](https://rabbit.syusui.net/)
- [Snort](https://snort.social/)
- [noStrudel](https://nostrudel.ninja/)
ここではnostterを使って説明していきます。
# 準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
## Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
[ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html)
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
## 使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
[emojito](https://emojito.meme/)
右上の**Get started**からNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。
[generalJP | カスタム絵文字](nostr:naddr1qqykwetwv4exzmz22qqs6amnwvaz7tmwdaejumr0dspzpmzzcaj5rzeah8y940ln4z855wa72af4a6aac4zjypql55egcpsqqvzqqqr4fcp4fwv8)

- 右側の**Options**から**Bookmark**を選択

これでカスタム絵文字を使用するためのリストに登録できます。
# カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
[nostter](https://nostter.app/)
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
## 文章中に使用
1. **投稿**ボタンを押して投稿ウィンドウを表示
2. **顔😀**のボタンを押し、絵文字ウィンドウを表示
3. ***タブ**を押し、カスタム絵文字一覧を表示
4. カスタム絵文字を選択
5. : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

## リアクションに使用
1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示
2. ***タブ**を押し、カスタム絵文字一覧を表示
3. カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

# カスタム絵文字を探す
先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。
例えば任意のユーザーのページ [emojito ロクヨウ](nostr:npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
[日本ユーザー作 カスタム絵文字](nostr:npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx)
各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。
-----------
以上です。
次:Nostrのカスタム絵文字の**作り方**
Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439)
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
-----------
# 仕様
[NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md)
[NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
-

@ 16d11430:61640947
2025-01-21 20:40:22
In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad.
---
1. Don’t Feed the Clowns
You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat.
Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month.
---
2. Turn Off the Fiat News
Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance.
Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed.
---
3. Mock Their Inflationary Gospel
Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?"
Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror.
---
4. Celebrate the Fiat Freakshow
Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never.
---
5. Build in the Chaos
While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt.
Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats.
---
6. Adopt a Fiat-Free Lifestyle
Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.”
Every satoshi spent in the real economy is a slap in the face to the fiat overlords.
---
7. Find the Humor in Collapse
Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all.
Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold.
---
8. Stay Ruthlessly Optimistic
Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better.
So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt.
---
Final Thought: Burn the Tent Down
Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates.
But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k.
Welcome to the satirical resistance. Now go stack some sats.
-

@ b17fccdf:b7211155
2025-01-21 16:30:11
> Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap?
---
Go to the bonus guide by clicking ~ >[HERE](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel) <~
---
Enjoy it MiniBolter! 💙
-

@ b8851a06:9b120ba1
2025-01-14 15:28:32
## **It Begins with a Click**
It starts with a click: *“Do you agree to our terms and conditions?”*\
You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval?
This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life?
---
## **Welcome to Digital Serfdom**
We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system.
- Your data? Owned by the lords of Big Tech.
- Your money? Controlled by banks and bureaucrats who can freeze it on a whim.
- Your thoughts? Filtered by algorithms that reward conformity and punish dissent.
The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate.
They don’t call it control, of course. They call it *“protection.”* They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars.
---
## **Freedom in Chains**
But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence.
We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more.
---
## **The Great Unpermissioning**
It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission.
The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, *“No.”* It’s the realization that the freedom you seek won’t be granted—it must be reclaimed.
- **Stop asking.** Permission is their tool. Refusal is your weapon.
- **Start building.** Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control.
- **Stand firm.** They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply.
The path won’t be easy. Freedom never is. But it will be worth it.
---
## **The New Frontier**
The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles.
This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply.
---
## **A Final Word**
They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it.
You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
-

@ 0d97beae:c5274a14
2025-01-11 16:52:08
This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
## The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
## Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
## Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
## The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
## Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-

@ 37fe9853:bcd1b039
2025-01-11 15:04:40
yoyoaa
-

@ 62033ff8:e4471203
2025-01-11 15:00:24
收录的内容中 kind=1的部分,实话说 质量不高。
所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。
而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。
我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-

@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.*
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
#### The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-

@ 3f770d65:7a745b24
2025-01-05 18:56:33
New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter [Olas](https://olas.app).
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
[Download on iOS](https://testflight.apple.com/join/2FMVX2yM).
[Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore.
Let's make waves together.
-

@ e6817453:b0ac3c39
2025-01-05 14:29:17
## The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
## Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
* **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
* **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
## Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
* **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities.
* **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
## Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
* Handle diverse data sources with ease.
* Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
## Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
* **Defining Relationships:** Clarifying how concepts connect within a domain.
* **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
## How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
## How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance:
* **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge.
* **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
* **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures.
1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development:
* **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data.
* **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
## Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
* **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies.
* **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
## LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
* **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures.
* **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
## Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-

@ 1cb14ab3:95d52462
2025-01-05 04:18:29
*Stunning beaches, ancient temples as far as the eye can see, and lush, green mountainsides that will leave you in awe—Myanmar is a destination you NEED to add to your bucket list. This guide offers the perfect one-month itinerary to explore the hidden gems of this incredible country.*

---
## The Itinerary
#### Days 1-2:
Fly into Yangon Airport. Settle in and explore the vibrant sights and flavors of the city.
#### Day 3:
Take an overnight bus south to the coastal city of Myeik.
#### Days 4-8:
Go island hopping around the Mergui Archipelago—remote beaches and untouched islands await.
#### Day 9:
Travel to Dawei. Find a cozy place to stay and relax for the evening.
#### Days 10-13:
Rent a motorcycle and explore the stunning Dawei Peninsula. Soak up the sun on pristine beaches.
#### Day 14:
Head to Hpa An. Check into a hotel and enjoy a sunset beer.
#### Days 15-18:
Discover the limestone mountains, caves, and farmlands of Hpa An.
#### Day 19:
Travel to Bagan. The journey may be bumpy, but the destination is worth it.
#### Days 20-23:
Explore the breathtaking temples of Bagan. Sunrise hot air balloon rides are a must.
#### Day 24:
Head to Lake Inle. Settle into your accommodation and dine by the water.
#### Days 25-26:
Cruise around Lake Inle by boat. Immerse yourself in the local culture and capture the iconic fishermen in action.
#### Days 27-28:
Visit Mandalay to experience city life from a Burmese perspective.
#### Days 29-30:
Return to Yangon for a final exploration before flying home.
---
## Days 1-2: Arrival in Yangon
Myanmar's largest city is a bustling hub filled with shops, activities, and incredible food. The rapid development of this once-isolated country is evident everywhere you look.
**If you are flying internationally:**
Yangon will most likely be the cheapest and most easily accessible destination to begin the trip.
**If you are coming from Thailand:**
I would recommend altering the itinerary and going straight to Myeik via land border then working your way up the country from there.
#### Bogyoke Aung San Market
If shopping is your thing, this place is a haven for local treasures. Hundreds of stalls line the market and surrounding alleyways containing everything from art, sculptures, jewelry, antiquities, and fabrics. I spent a few hours here before jumping onto the nearby circular train for a loop around the city. There are a few small shops to get a bite to eat if you are hungry.
Remember that this itinerary will land you back in Yangon at the end of the trip if you see something you want to buy and don’t feel like lugging it around for a month.

#### Yangon Circular Train
Easily one of the most fascinating experiences of the trip is riding the Yangon Circular Train around the city for a true look at how the locals live. The train is old, slow, and packed with locals commuting to and from work. The doors are wide open, allowing you to hang your feet outside and soak in all of the sights afar. This is one of the best ways to get a true glimpse into the culture and day-to-day life of the Burmese people.
Be sure to speak with a train operator before getting on to make sure the entire loop is operational. When I went, construction stopped the train about 45 minutes into the loop, forcing us to get a taxi back to the downtown area. The full loop will take over 2 hours to complete. On the train, you can find vendors and hawkers selling little things such as water, nuts, and fruit. I’d suggest eating before jumping on.

#### Shwedagon Pagoda
Upon walking up the steep and lengthy stairway to the Shwedagon Pagoda lies Yangon’s most famous attraction. The 99-meter gold-coated pagoda can be seen all around the city but is best enjoyed up close. This is a must-visit during your time in the capital. I went about an hour before sunset and stayed well into the night. Sunset from the hill it sits atop is spectacular, and the contrast of the pagoda between day and night is striking.
Make sure to bring socks and a bag, as shoes are not allowed, and you will need to carry them or leave them at the door. After visiting, you can take a short walk to the Sky Bar in the Yangon International Hotel overlooking the pagoda. This is a wonderful place to enjoy a nice dinner and drink, ideal for soaking up more of that luxurious golden pagoda.

---
## Day 3: Bus to Myeik
The longest stretch of the trip—but well worth the sights to come. I took a 22-hour overnight bus and opted for the slight upcharge to take the VIP bus. This option is absolutely worth it. Equipped with A/C, comfortable reclining seats, and stops for three meals, it was a cheaper alternative to the costly domestic flight from Yangon and allowed me to see much more of the country.
I had a surprisingly good sleep and would do it again in a heartbeat. You can also fly directly to Myeik, but flights are infrequent and considerably more expensive. The bus I took arrived in Myeik around noon the next day, leaving me plenty of time to check into the hotel and wander around the city a bit before sunset. There weren’t many buses heading down here, so I’d recommend checking for tickets as early as possible when you arrive in Yangon. Alternatively, if you’re coming from Thailand, you can rearrange the itinerary and begin your Myanmar trip in Myeik by crossing from Thailand via bus at the land border.

---
## Days 4-8: Island Hopping in Myeik
The city of Myeik has no accessible beaches, so you’ll need to book an island-hopping tour to fully appreciate the surrounding Mergui Archipelago. While the city itself doesn’t offer much in terms of entertainment, the beaches and crystal-clear waters you’ll encounter on an island-hopping tour are truly unparalleled. Your trip to Myeik will be unforgettable and is an experience you shouldn’t miss.
There are several travel companies offering island-hopping tours, ranging from single-day trips to 14-day excursions. While you can book ahead, I found it quite easy to arrange a trip through an agency in the city. I opted for a three-day, two-night tour with Life Seeing Tours, and it was fantastic. They provided food, tents, and transportation—just bring a swimsuit and a change of clothes, and you’re ready to spend a few nights exploring the islands.




---
## Day 9: Bus to Dawei
Another travel day! This time, you’ll take a shorter bus ride heading north to Dawei. The journey takes about six hours, and tickets can be purchased from one of the travel agencies in Myeik. From what I gathered, there’s only one bus per day on this route, and it departs early in the morning.
Be prepared to wake up around 4 AM and make your way back to the same bus station where you arrived. It’s a good idea to arrange transportation to the station the night before—your hotel can help you book a ride for that morning.
---
## Days 10-13: Motorcycling the Dawei Peninsula
Dawei boasts some of the most stunning coastlines and beaches in the country. While most of these beaches are only accessible by motorcycle, there are a few small bed-and-breakfast-style accommodations at the southern end of the peninsula that offer direct beach access.
If you’d prefer not to travel 2–3 hours each day from the city, I recommend staying in that area. You can rent a motorcycle from several places in the city and ride down to the B&Bs near the beaches for an overnight stay. This approach lets you enjoy the remote, lush, and scenic motorcycle journey while avoiding the daily commute to the beaches.

#### Grandfather Beach
Surrounded by mountains and vibrant orange dirt, getting here can be a bit tricky. You’ll need to navigate a steep, loose hill to reach the area. I recommend arriving near low tide, as the beach and surrounding shops flood around noon, making the descent a wet and challenging experience. Be prepared to remove your shoes and walk through knee-deep water to access the beach. This is one of the more popular spots for locals and was among the few beaches I visited that actually had people.

#### Tizit Beach
When we arrived at Tizit Beach, there was no one else around except for the locals. The sand here is soft, and the ocean is pristine. A motorcycle is necessary to access this beach, but the breathtaking views from the mountain pass make the journey entirely worthwhile. The sand near the shore is firm enough to ride on, creating unforgettable moments of cruising along the beach at sunset.

---
## Day 14: Bus to Hpa An
One of the shorter bus rides on this trip, the fare is around $20, and it takes approximately 5 bumpy hours. Once you arrive in Hpa An, there are plenty of hostels and hotels to choose from. I booked mine on Hostelworld the night before, but you should have no trouble finding a place to stay on the day of your arrival if needed.
---
## Days 15-18: Hpa An: Farmland, Caves, and Mountains
Hpa An offers a stark contrast to the beaches and cities encountered so far on the trip. Surrounded by towering limestone mountains and lush green farmland, the region has a peaceful, rural charm. There are several caves, lakes, and one of my favorite sunrise hikes of the journey.
While I have a few recommendations and must-visit spots, Hpa An is best explored without a strict plan. A central theme of this trip has been the freedom of hopping on a motorcycle and riding wherever your heart desires.

#### Mount Zwegabin Sunrise Hike
Hiking Mount Zwegabin for sunrise is a must-do during your time in Hpa An. The mountain is located a short ride from town, about 40 minutes by motorcycle. The hike to the summit took around 35 minutes at a brisk pace, so you’ll need to leave around 4 AM to catch the sunrise, depending on the season. The highlight of the hike is the final ascent up the floating stairs to reach the peak. Be sure to have your camera ready and take in the breathtaking views.

#### Kyauk Kalat Pagoda
This is one of those places that leaves you in awe, wondering how such a unique landscape can exist. Easily one of the most unusual rock formations I’ve encountered, it’s a fantastic spot to watch the sunset. A winding staircase leads up the rock to the top of the temple, making it a great place to spend a couple of hours.

#### Saddar Cave
Filled with bats, stunning limestone formations, and statues, this short cave walk provides a refreshing escape from the heat. The path takes about 20 minutes to explore, leading to a beautiful lake at the back. Grab a drink, relax for a while, and take a small paddle boat back to the entrance for a memorable experience.

---
## Day 19: Bus to Bagan
A travel day heading north. This part of the trip is hot, bumpy, and slow, so be prepared for a longer journey than expected. Bagan has plenty of hotels and hostels, but I’d recommend booking accommodations in advance, as it’s a popular tourist destination. You’ll need to purchase an entry ticket for the area, as it’s a protected national park, but the bus driver should assist in sorting it out before you enter the park.
---
## Days 20-23: Chasing Pagodas in Bagan
Once you’ve settled into your accommodation in Bagan, the best way to explore the vast area is by pedal bike or scooter. All the scooters available for rent are electric, helping to reduce noise pollution—a refreshing change from the loud gas-powered vehicles you’ll be used to from the first half of your trip. There’s no right or wrong way to experience Bagan. The park is enormous, with thousands of pagodas scattered throughout. Most of them are open for exploration, with a few offering rooftop access (though that is being restricted more recently).
You could spend weeks here and still not see all the pagodas up close. Bagan is divided into a new town and an old town—most of the backpacker-friendly hostels are located in Old Town. You’ll find a handful of restaurants, but I often ate at my hostel or from local food carts. Several hostels and hotels offer outdoor pools, which are a great perk, especially depending on the time of year you visit. I highly recommend simply wandering the area freely, but here are a few top pagodas and experiences not to miss during your time in Bagan.

#### Hot Air Ballooning
The top attraction in Bagan is undoubtedly the daily hot air balloon tours. Almost everyone who experiences it claims it’s a must-do. I chose to watch from the ground, as the cost of a tour is quite expensive. If you decide to go for it, be sure to set aside a few hundred USD for the trip. From what I’ve heard, you’ll wake up around 4:30 AM and head to the take-off location, returning by around 9:00 AM.

#### Sunset Boat Cruise
Be sure to spend at least one evening on a slow cruise down the Ayeyarwady River. It’s a wonderful way to enjoy distant views of some of the pagodas and relax after a long day of exploration. Several companies offer these cruises at very affordable prices. Our boat included snacks, drinks, and even alcohol. The trips range from half an hour to two hours. Book through your hotel for convenience.

#### The Big Three Temples
With over a thousand pagodas to explore in Bagan, there are three main structures that hold significant importance to locals: Shwesandaw, Thatbyinnyu, and Shwezigon. Be sure to make time to visit these iconic pagodas during your trip—you’re likely to come across them without even trying.

---
## Day 24: Bus to Kalaw
Long-distance buses run the route multiple times a day, with the overnight option being the most popular. I recommend checking with a travel agent in Bagan to book your tickets before heading to the bus stop
---
## Day 25-26: Relaxing at Lake Inle
These two days take us to the stunning Lake Inle, located just outside the city of Kalaw. Unfortunately, I wasn’t able to make it to Lake Inle during this trip, but everyone I spoke to highly recommended not missing it. The lake is known for its breathtaking scenery, traditional Intha stilt houses, and the unique leg-rowing fishermen.
From what I’ve heard and seen through photos, the calm waters, floating gardens, and vibrant markets make Lake Inle a truly unforgettable destination. Huge thanks to my friend Toby for sharing those beautiful pictures and giving me a glimpse of what I missed!




---
## Day 27-28: Mandalay City
Mandalay is a fast-paced city with less tourism compared to other parts of the country. It offers a fascinating glimpse into the daily lives of the Burmese people, away from the crowds typically found in Yangon. There are several culturally significant monasteries and temples within the city limits, as well as vibrant markets perfect for shopping and exploring. Mandalay Hill is a great spot for a brisk hike and offers stunning views of the city and sunset on one of your nights. You could also visit the Mandalay Marionettes Theater to catch a local show showcasing Myanmar’s rich history and culture.
As for me, I mainly wandered the city without specific destinations in mind. Since this is the last stop before returning to Yangon, you might not feel as inclined to spend too much time here, but there are definitely some interesting sights worth exploring.

---
## Day 29-30: Return to Yangon
The final two days of the trip are a return to where it all began. The bus from Mandalay to Yangon takes about 8 hours. Alternatively, Mandalay has a large international airport if you prefer to fly, depending on your next destination.
If you return to Yangon, you’ll have plenty of time to revisit the markets and pick up any final souvenirs or trinkets you might want to take home. Enjoy these last couple of days, savor some delicious food, and take the time to reflect on the incredible month of experiences you’ve had.

---
## Concluding Thoughts
Your month-long journey through Myanmar is bound to be an unforgettable adventure, filled with stunning landscapes, rich culture, and warm hospitality. From the serene beaches of Ngapali to the ancient wonders of Bagan, and the tranquil beauty of Lake Inle to the bustling streets of Yangon and Mandalay, each destination offers its own unique charm and insight into Myanmar’s diverse culture.
The highlights of your trip—exploring historic pagodas, witnessing breathtaking sunrises, and embracing the freedom of riding a motorcycle—are sure to stay with you. Myanmar’s blend of natural beauty, vibrant traditions, and friendly locals makes every moment special. Despite the occasional long and bumpy journeys, the sense of discovery and connection with the people and places makes the experience truly worthwhile.
As you reflect on your journey, you’ll likely feel grateful for the memories, experiences, and the chance to explore a country that feels both timeless and unique. Myanmar’s beauty lies not just in its landscapes but in the people who call it home. You’ll leave with a deeper appreciation for the warmth and resilience of its people and a desire to return and explore even more of this enchanting land.
---
*Update: Unfortunately as of this time (June 2021) Myanmar is experiencing major political and civil unrest. Taken from the advice of friends on the ground there— I can not recommend traveling to Myanmar at the time of writing. Pray for Myanmar!*
*Update 2: The political situation in Myanmar has escalated (July 2022). Travel is still not recommended.*
*Update 3: As of 2025, some tourists have reported that travel is doable. However many governments still have do not travel advisories. DYOR.*
---
### Other Myanmar Guides:
[The Top 3 Hidden Beaches of Myanmar: A Guide to Tizit, Grandfather, and Mergui](https://hes.npub.pro/post/1705254252735/)
---
### More from Hes:
[Art](https://hes.npub.pro/tag/art/)
[Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06)
[Travel Guides](https://hes.npub.pro/tag/travel/)
[Photography](https://hes.npub.pro/tag/photography/)
[Writings](https://hes.npub.pro/tag/money/)
---
*Originally Published June 15, 2021. Edited with Nostr friendly images on 1/5/2025*
-

@ a4a6b584:1e05b95b
2025-01-02 18:13:31
## The Four-Layer Framework
### Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
**Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
_Once you have the big picture in mind, it’s time to start breaking it down._
---
### Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
**Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
_With your categories in place, you’re ready to dive into the details that bring them to life._
---
### Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
**Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
_Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._
---
### Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
**Example**: Learn about rare programming quirks or historical trivia about a language’s development.
- **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
---
## Pro Tips for Better Learning
### 1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
### 2. Map It Out
Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
### 3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material.
### 4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.
**Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
---
## Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-

@ 1cb14ab3:95d52462
2025-01-02 05:57:05
---
## No. 1 - The Less Touristy "Bund"

The Bund is certainly a must-see if you are traveling to Shanghai for the first time - and it will be at the top of every travel guide out there, for good reason - there are equally as stunning alternatives away from the crowds. If you want to enjoy the skyline from a more relaxed perspective, consider the Pudong side of the river. There are parks, basketball courts, and green spaces along the riverbank for you to chill at and take in the sights. You can also hop on a ferry or a sightseeing boat to cross the river and admire the views from the renowned Bund.
---
## No. 2 - Walks Along Golden Street

This one is out in Gubei, a suburban area in the west of Shanghai. It may be a bit of a trek, but it is worth it if you are looking for a more relaxing and peaceful pedestrian street in the city. Golden Street, or Jinxiu Road, is a great place to walk a dog, grab an afternoon drink, or enjoy a romantic dinner with your loved one. While it may be a bit far from downtown, it makes for a great joyride on your scooter or bicycle.
---
## No. 3 - Moganshan Road Graffiti Wall

Moganshan Road is a gem for all things art. It is home to M50, the best art district in the city, where you will find dozens of galleries, studios, and workshops showcasing a wide range of art. There are also plenty of cool spots scattered around the area, particularly the graffiti wall. The wall is a welcome contrast to some of the drab and monotonous architecture found around the city; with colorful display of street art featuring various styles and themes. Stop by and admire the works of local and international artists, and even jump in to join them in adding your own mark. The wall is constantly evolving, so you can always find something new.
---
## No. 4 - Jiaotong University in the Fall

Easily one of the best spots in town for catching rows of bright yellow and red leaves. Jiaotong University is one of the oldest and most prestigious universities in China. The campus is located in Xuhui District and has a mix of Chinese and Western architectural styles to admire as well. Try to visit in late October or early November for the best leaf-peeping. You can walk along the tree-lined paths, set up a blanket in the field for a picnic, or simply take photos and enjoy the scenery.
---
## No. 5 - Day Drinking at Highline

Hands down one of the top five rooftop bars in the city, along with Bar Rouge, Kartel, and others; Highline is a go-to-spot that offers great views of the city and excellent food. Find it on the sixth floor of the Ascott Hotel in Huaihai Road in Xintiandi. Nothing beats a laid back Saturday afternoon at Highline. I prefer the views during the day, though it is equally as nice a night. Sip cocktails, wine, or beer, and enjoy the music and vibe. Highline is a perfect place to spend an afternoon.
---
### Additional Photos





---
#### Next Guide in the Series:
[An Expats Guide to the Best Spots in Shanghai: 002](https://hes.npub.pro/post/1719708820357/)
---
### Find Me Elsewhere:
[Website](https://hes.npub.pro/)
[Art](https://hes.npub.pro/tag/art/)
[Travel Guides](https://hes.npub.pro/tag/travel/)
[Photography](https://hes.npub.pro/tag/photography/)
[Storefront](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06)
---
*All images property of Hes. Originally published as an Instagram Guide on Feb. 02, 2021. Reworked and published on Nostr on Feb. 17, 2024.*
-

@ 16d11430:61640947
2024-12-26 11:31:05
For centuries, financial markets have been shackled by an archaic mindset rooted in Newtonian physics: "What goes up must come down." This belief has dominated the thinking of old-school fiat economists, who view the rise and fall of markets as a natural cycle of gravity-bound economics. But Bitcoin, the digital phoenix, was designed to defy this outdated paradigm. It isn't just an asset class or a currency—it's a revolution in financial physics, unshackling value from centralized control and rewriting the rules of money.
The Fiat Fallacy: Gravity Economics
Fiat systems are inherently cyclical, prone to inflation, manipulation, and collapse. Central banks print money endlessly, causing value to "come down" as purchasing power erodes. For fiat thinkers, this is unavoidable—a gravitational force they accept as immutable. Yet this mindset ignores Bitcoin’s game-changing properties: its hard cap of 21 million coins, decentralized consensus, and permissionless architecture.
Bitcoin is fundamentally non-Newtonian. It doesn’t adhere to traditional financial laws because it isn't bound by the same forces of supply and control. Instead, it operates in a new paradigm: deflationary, transparent, and immune to political meddling.
Bitcoin's Escape Velocity
Bitcoin's dominance lies in its ability to achieve escape velocity. Unlike fiat currencies, which are constantly being pulled back by inflationary policies, Bitcoin is propelled by its scarcity, adoption, and network effects. Every halving event tightens the supply, creating an upward pressure that fiat systems can't replicate. And as global trust in traditional systems erodes, Bitcoin's gravitational pull grows stronger.
This phenomenon is evident in the adoption curve. Institutions, governments, and individuals worldwide are recognizing Bitcoin as a superior store of value, an inflation hedge, and the ultimate form of financial sovereignty. The more participants enter the network, the more its value compounds, creating a virtuous cycle of exponential growth.
Humiliating the Old Guard
The fiat establishment—steeped in centuries of centralized control—has long dismissed Bitcoin as a bubble, a fad, or even a Ponzi scheme. Yet, year after year, Bitcoin rises from the ashes of their predictions. Its resilience, transparency, and provable scarcity expose the fragility and corruption of fiat systems.
The ultimate humiliation for fiat thinkers is Bitcoin's ability to thrive in crises. Where traditional systems falter—be it through hyperinflation, bank failures, or geopolitical instability—Bitcoin becomes a lifeboat. It doesn’t just resist gravity; it flips the entire script. Fiat currencies are revealed as infinite-print illusions, while Bitcoin’s immutable ledger stands as the ultimate arbiter of truth and value.
A New Financial Paradigm
Bitcoin’s ascent is not merely about price; it’s about domination. It represents a shift from centralized control to individual empowerment, from opaque systems to transparent protocols, from inflationary theft to deflationary savings. It’s a financial singularity, an escape from the gravitational pull of outdated thinking.
As Bitcoin continues its trajectory, the old world of "what goes up must come down" will look increasingly absurd. In its place, a new principle will reign: what’s decentralized cannot be stopped. Bitcoin isn’t just leaving Earth’s orbit; it’s becoming the financial universe’s North Star.
So buckle up, because Bitcoin isn’t just going up—it’s transcending. And as it does, it will leave the Newtonian thinkers in the dust, staring in disbelief at the rocket that left them behind.
-

@ 16d11430:61640947
2024-12-23 16:47:01
At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence.
The Philosophical Void of Fiat
Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation.
The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence.
Theological Implications: Fiat and the Collapse of the Sacred
Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger.
This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect.
Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests.
Physics and the Infinite Growth Paradox
Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility.
In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself.
Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level.
Biology: The Fiat System and the Destruction of Human Health
Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans.
Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders.
The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse.
Finance as the Final Illusion
At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses.
This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality.
As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems.
The Ultimate Extermination
In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being.
To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
-

@ a367f9eb:0633efea
2024-12-22 21:35:22
I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”.
It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
> In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
>
> It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
>
> …
>
> The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
**I was at least somewhat wrong.**
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
**I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.**
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/).
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
**But I was wrong.**
When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
**Now I understand I was wrong.**
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.*
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016.
**And I was wrong again.**
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
**Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.**
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-

@ ec42c765:328c0600
2024-12-22 19:16:31
この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入)
前回:[Nostrのカスタム絵文字の使い方](https://yakihonne.com/article/_@lokuyow.github.io/xVMTZxHcV_NWKuTbDBUYs)
# 手順
1. 登録する画像を用意する
2. 画像をweb上にアップロードする
3. 絵文字セットに登録する
## 1. 登録する画像を用意する
以下のような方法で用意してください。
* 画像編集ソフト等を使って自分で作成する
* 絵文字作成サイトを使う([絵文字ジェネレーター](https://emoji-gen.ninja/)、[MEGAMOJI](https://zk-phi.github.io/MEGAMOJI/) など)
* フリー画像を使う([いらすとや](https://www.irasutoya.com/) など)
### データ量削減
Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。
データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。
以下は私のおすすめです。
* サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル
* ファイル形式:webp形式(webp変換おすすめサイト [toimg](https://toimg.kakechimaru.com/to-webp))
* 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる)
### その他
* 背景透過画像
* ダークモード、ライトモード両方で見やすい色
がおすすめです。
## 2. 画像をweb上にアップロードする
よく分からなければ [emojito](https://emojito.meme/) からのアップロードで問題ないです。
普段使っている画像アップロード先があるならそれでも構いません。
気になる方はアップロード先を適宜選んでください。
既に投稿されたカスタム絵文字の画像に対して
- 削除も差し替えもできない → [emojito](https://emojito.meme/) など
- 削除できるが差し替えはできない → [Gyazo](https://gyazo.com/)、[nostrcheck.me](https://nostrcheck.me/)など
- 削除も差し替えもできる → [GitHub](https://github.com/) 、セルフホスティングなど
これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。
どの方法でも新しく使われるカスタム絵文字を変更することは可能です。
同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。
## 3. 絵文字セットに登録する
[emojito](https://emojito.meme/) から登録します。
右上の**アイコン** → **+ New emoji set** から新規の絵文字セットを作成できます。


#### ① 絵文字セット名を入力
基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。
一度作った絵文字セットに後から絵文字を追加することもできます。
#### ② 画像をアップロードまたは画像URLを入力
emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。
その場合はファイル名を適当な英数字などに変更してください。
#### ③ 絵文字のショートコードを入力
ショートコードは絵文字を呼び出す時に使用する場合があります。
他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。
他と被りにくく長くなりすぎないショートコードが良いかもしれません。
ショートコードに使えるのは半角の英数字とアンダーバーのみです。
#### ④ 追加
**Add** を押してもまだ作成完了にはなりません。

一度に絵文字を複数登録できます。
最後に右上の **Save** を押すと作成完了です。

画面が切り替わるので、右側の **Options** から **Bookmark** を選択するとそのカスタム絵文字セットを自分で使えるようになります。
既存の絵文字セットを編集するには **Options** から **Edit** を選択します。
以上です。
-----------
# 仕様
[NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md)
[NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
-

@ 1cb14ab3:95d52462
2024-12-17 19:24:54
*Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.*
---
The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways.
Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future.
When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal.
For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away.
This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below:
<aside>
**Inflation Rate (%)** | **Purchasing Power Halving (Years)**
- 2% | 35-40 years
- 3% | 20-25 years
- 4% | 15-20 years
- 5% | 10-15 years
- 6% | 7-12 years
- 7% | 5-10 years
- 8% | 4-8 years
- 9% | 3-6 years
- 10% | 2-5 years
</aside>
Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble.
But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation?
A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future.
Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money.
The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued.
By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world.
Bitcoin isn’t a bubble; it’s a beacon.
---
### More from Hes:
[Art](https://hes.npub.pro/tag/art/)
[Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06)
[Travel Guides](https://hes.npub.pro/tag/travel/)
[Photography](https://hes.npub.pro/tag/photography)
-

@ fe32298e:20516265
2024-12-16 20:59:13
Today I learned how to install [NVapi](https://github.com/sammcj/NVApi) to monitor my GPUs in Home Assistant.

**NVApi** is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- **GPU Utilization Monitoring**: Utilization, memory usage, temperature, fan speed, and power consumption.
- **Automated Power Limiting**: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- **Cross-GPU Coordination**: Total power budget applies across multiple GPUs in the same system.
- **PCIe Link Speed Management**: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- **Home Assistant Integration**: Uses the built-in RESTful platform and template sensors.
## Getting the Data
```
sudo apt install golang-go
git clone https://github.com/sammcj/NVApi.git
cd NVapi
go run main.go -port 9999 -rate 1
curl http://localhost:9999/gpu
```
Response for a single GPU:
```
[
{
"index": 0,
"name": "NVIDIA GeForce RTX 4090",
"gpu_utilisation": 0,
"memory_utilisation": 0,
"power_watts": 16,
"power_limit_watts": 450,
"memory_total_gb": 23.99,
"memory_used_gb": 0.46,
"memory_free_gb": 23.52,
"memory_usage_percent": 2,
"temperature": 38,
"processes": [],
"pcie_link_state": "not managed"
}
]
```
Response for multiple GPUs:
```
[
{
"index": 0,
"name": "NVIDIA GeForce RTX 3090",
"gpu_utilisation": 0,
"memory_utilisation": 0,
"power_watts": 14,
"power_limit_watts": 350,
"memory_total_gb": 24,
"memory_used_gb": 0.43,
"memory_free_gb": 23.57,
"memory_usage_percent": 2,
"temperature": 36,
"processes": [],
"pcie_link_state": "not managed"
},
{
"index": 1,
"name": "NVIDIA RTX A4000",
"gpu_utilisation": 0,
"memory_utilisation": 0,
"power_watts": 10,
"power_limit_watts": 140,
"memory_total_gb": 15.99,
"memory_used_gb": 0.56,
"memory_free_gb": 15.43,
"memory_usage_percent": 3,
"temperature": 41,
"processes": [],
"pcie_link_state": "not managed"
}
]
```
# Start at Boot
Create `/etc/systemd/system/nvapi.service`:
```
[Unit]
Description=Run NVapi
After=network.target
[Service]
Type=simple
Environment="GOPATH=/home/ansible/go"
WorkingDirectory=/home/ansible/NVapi
ExecStart=/usr/bin/go run main.go -port 9999 -rate 1
Restart=always
User=ansible
# Environment="GPU_TEMP_CHECK_INTERVAL=5"
# Environment="GPU_TOTAL_POWER_CAP=400"
# Environment="GPU_0_LOW_TEMP=40"
# Environment="GPU_0_MEDIUM_TEMP=70"
# Environment="GPU_0_LOW_TEMP_LIMIT=135"
# Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
# Environment="GPU_0_HIGH_TEMP_LIMIT=100"
# Environment="GPU_1_LOW_TEMP=45"
# Environment="GPU_1_MEDIUM_TEMP=75"
# Environment="GPU_1_LOW_TEMP_LIMIT=140"
# Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
# Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install]
WantedBy=multi-user.target
```
## Home Assistant
Add to Home Assistant `configuration.yaml` and restart HA (completely).
For a single GPU, this works:
```
sensor:
- platform: rest
name: MYPC GPU Information
resource: http://mypc:9999
method: GET
headers:
Content-Type: application/json
value_template: "{{ value_json[0].index }}"
json_attributes:
- name
- gpu_utilisation
- memory_utilisation
- power_watts
- power_limit_watts
- memory_total_gb
- memory_used_gb
- memory_free_gb
- memory_usage_percent
- temperature
scan_interval: 1 # seconds
- platform: template
sensors:
mypc_gpu_0_gpu:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_0_memory:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_0_power:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}"
unit_of_measurement: "W"
mypc_gpu_0_power_limit:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}"
unit_of_measurement: "W"
mypc_gpu_0_temperature:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}"
unit_of_measurement: "°C"
```
For multiple GPUs:
```
rest:
scan_interval: 1
resource: http://mypc:9999
sensor:
- name: "MYPC GPU0 Information"
value_template: "{{ value_json[0].index }}"
json_attributes_path: "$.0"
json_attributes:
- name
- gpu_utilisation
- memory_utilisation
- power_watts
- power_limit_watts
- memory_total_gb
- memory_used_gb
- memory_free_gb
- memory_usage_percent
- temperature
- name: "MYPC GPU1 Information"
value_template: "{{ value_json[1].index }}"
json_attributes_path: "$.1"
json_attributes:
- name
- gpu_utilisation
- memory_utilisation
- power_watts
- power_limit_watts
- memory_total_gb
- memory_used_gb
- memory_free_gb
- memory_usage_percent
- temperature
- platform: template
sensors:
mypc_gpu_0_gpu:
friendly_name: "MYPC GPU0 GPU"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_0_memory:
friendly_name: "MYPC GPU0 Memory"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_0_power:
friendly_name: "MYPC GPU0 Power"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}"
unit_of_measurement: "W"
mypc_gpu_0_power_limit:
friendly_name: "MYPC GPU0 Power Limit"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}"
unit_of_measurement: "W"
mypc_gpu_0_temperature:
friendly_name: "MYPC GPU0 Temperature"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}"
unit_of_measurement: "C"
- platform: template
sensors:
mypc_gpu_1_gpu:
friendly_name: "MYPC GPU1 GPU"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_1_memory:
friendly_name: "MYPC GPU1 Memory"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_1_power:
friendly_name: "MYPC GPU1 Power"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}"
unit_of_measurement: "W"
mypc_gpu_1_power_limit:
friendly_name: "MYPC GPU1 Power Limit"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}"
unit_of_measurement: "W"
mypc_gpu_1_temperature:
friendly_name: "MYPC GPU1 Temperature"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}"
unit_of_measurement: "C"
```
Basic entity card:
```
type: entities
entities:
- entity: sensor.mypc_gpu_0_gpu
secondary_info: last-updated
- entity: sensor.mypc_gpu_0_memory
secondary_info: last-updated
- entity: sensor.mypc_gpu_0_power
secondary_info: last-updated
- entity: sensor.mypc_gpu_0_power_limit
secondary_info: last-updated
- entity: sensor.mypc_gpu_0_temperature
secondary_info: last-updated
```
# Ansible Role
```
---
- name: install go
become: true
package:
name: golang-go
state: present
- name: git clone
git:
repo: "https://github.com/sammcj/NVApi.git"
dest: "/home/ansible/NVapi"
update: yes
force: true
# go run main.go -port 9999 -rate 1
- name: install systemd service
become: true
copy:
src: nvapi.service
dest: /etc/systemd/system/nvapi.service
- name: Reload systemd daemons, enable, and restart nvapi
become: true
systemd:
name: nvapi
daemon_reload: yes
enabled: yes
state: restarted
```
-

@ b8851a06:9b120ba1
2024-12-16 16:38:53
Brett Scott’s recent [metaphor of Bitcoin as a wrestling gimmick](https://www.asomo.co/p/the-art-of-crypto-kayfabe), reliant on hype and dollar-dependence, reduces a groundbreaking monetary innovation to shallow theatrics. Let’s address his key missteps with hard facts.
---
### **1. Bitcoin Isn’t an Asset in the System—It’s the System**
Scott claims Bitcoin competes with stocks, bonds, and gold in a financial "wrestling ring." This misrepresents Bitcoin’s purpose: it’s not an investment vehicle but a *decentralized monetary network*. Unlike assets, Bitcoin enables **permissionless global value transfer**, censorship resistance, and self-sovereign wealth storage—capabilities fiat currencies cannot match.
**Fact:** Bitcoin processes over **$8 billion in daily transactions**, settling more value annually than PayPal and Venmo combined. It isn’t competing with assets but offering an alternative to the monetary system itself.
---
### **2. Volatility Is Growth, Not Failure**
Scott critiques Bitcoin’s price volatility as evidence of its unsuitability as "money." However, volatility is a natural stage in the adoption of transformative technology. Bitcoin is scaling from niche use to global recognition. Its growing liquidity and adoption already make it more stable than fiat in inflationary economies.
**Fact:** Bitcoin’s annualized volatility has decreased by **53% since 2013** and continues to stabilize as adoption rises. It’s the **best-performing asset of the last decade**, with an average annual ROI of **147%**—far outpacing stocks, gold, and real estate. As of February 2024, Bitcoin's volatility was lower than roughly 900 stocks in the S and P 1500 and 190 stocks in the S and P 500. It continues to stabilize as adoption rises, making it an increasingly attractive store of value.
---
### **3. Bitcoin’s Utility Extends Beyond Countertrade**
Scott diminishes Bitcoin to a "countertrade token," reliant on its dollar price. This ignores Bitcoin’s primary functions:
- **Medium of exchange:** Used in remittances, cross-border payments, and for the unbanked in Africa today (e.g., Ghana, Nigeria, Kenya).
- **Store of value:** A hedge against inflation and failing fiat systems (e.g., Argentina, Lebanon, Turkey).
- **Decentralized reserve asset:** Held by over **1,500 public and private institutions**, including Tesla, MicroStrategy, and nations like El Salvador.
**Fact:** Lightning Network adoption has grown **1,500% in capacity since 2021**, enabling microtransactions and reducing fees—making Bitcoin increasingly viable for everyday use. As of December 2024, Sub-Saharan Africa accounts for 2.7% of global cryptocurrency transaction volume, with Nigeria ranking second worldwide in crypto adoption. This demonstrates Bitcoin's real-world utility beyond mere speculation.
---
### **4. Bitcoin Isn’t Controlled by the Dollar**
Scott suggests Bitcoin strengthens the dollar system rather than challenging it. In truth, Bitcoin exists **outside the control of any nation-state**. It offers people in authoritarian regimes and hyperinflationary economies a lifeline when their local currencies fail.
**Fact:** Over **70% of Bitcoin transactions occur outside the U.S.**, with adoption highest in countries like Nigeria, India, Venezuela, China, the USA and Ukraine—where the dollar isn’t dominant but government overreach and fiat collapse are. This global distribution shows Bitcoin's independence from dollar dominance.
---
### **5. Hype vs. Adoption**
Scott mocks Bitcoin’s evangelists but fails to acknowledge its real-world traction. Bitcoin adoption isn’t driven by hype but by trustless, verifiable technology solving real-world problems. People don’t buy Bitcoin for "kayfabe"; they buy it for what it *does*.
**Fact:** Bitcoin wallets reached **500 million globally** in 2023. El Salvador’s Chivo wallet onboarded **4 million users** (60% of the population) within a year—far from a gimmick in action. As of December 2024, El Salvador's Bitcoin portfolio has crossed $632 million in value, with an unrealized profit of $362 million, demonstrating tangible benefits beyond hype.
---
### **6. The Dollar’s Coercive Monopoly vs. Bitcoin’s Freedom**
Scott defends fiat money as more than "just numbers," backed by state power. He’s correct: fiat relies on coercion, legal mandates, and inflationary extraction. Bitcoin, by contrast, derives value from **transparent scarcity** (capped at 21 million coins) and decentralized consensus, not military enforcement or political whims.
**Fact:** Bitcoin’s inflation rate is just **1.8%**—lower than gold or the U.S. dollar—and will approach **0% by 2140**. No fiat currency can match this predictability. As of December 2024, Bitcoin processes an average of 441,944 transactions per day, showcasing its growing role as a global, permissionless monetary system free from centralized control.
---
### **Conclusion: The Revolution Is Real**
Scott’s "wrestling gimmick" analogy trivializes Bitcoin’s purpose and progress. Bitcoin isn’t just a speculative asset—it’s the first truly decentralized, apolitical form of money. Whether as a hedge against inflation, a tool for financial inclusion, or a global settlement network, Bitcoin is transforming how we think about money.
Dismiss it as a gimmick at your peril. The world doesn’t need another asset—it needs Bitcoin.
> "**If you don't believe me or don't get it, I don't have time to try to convince you, sorry**." Once Satoshi said.
**There is no second best.**
-

@ 2f5de000:2f9bcef1
2024-12-15 16:44:53
This Week I immersed myself in Bitcoin from multiple angles-technical, societal and personal. The journey included a marathon 32-hours of listening to [Rabbit Hole Recap (RHR)](https://fountain.fm/show/VDaMppQRUBZioj2XkaLn), an essential resource for Bitcoin insights. It's worth noting that I started from the begining and plan to make my way through the whole catalogue. Marty and Matt's timestamps, along with contributions from their guests, served as my roadmap. Using Fountain to stream, I also streamed sats-a small but extraordinary feature that allows users to stacks sats while compensating cretors directly through fractional donations.
## Revisiting Speculative Attack by Pierre Rochard (2014)
Now that [*Speculative Attack Season 2*](https://nakamotoinstitute.org/mempool/speculative-attack-season-2/) *(which I've not read yet)* has been released. I took the time to read Pierre Rochards influential essay, [*Speculative Attack*](https://nakamotoinstitute.org/mempool/speculative-attack/) and reflected on its timeless insights. Rochard argues that Bitcoin adoption isn't dependent on technological advancements or consumer preferences, but on economic realities. As fiat currencies weaken, Bitcoin won't enter the mainstream by persuasion but by necessity.
Critics continue to underestimate Bitcoin's inevitability due to their fiat biases and lack of financial insight. This year alone, mainstream media has been compelled to discuss Bitcoin-notably to Trump's endorsement of 'crypto.' Despite their attempts to shape narratives to suit their ideal visions, they've had no choice but to engage with Bitcoin's growing influence.\
\
As Parker aptly puts it 'Gradually, The Suddenly'
## Wassabi Wallet and the Privacy Imperative
An RHR interview (from early in the catalogue) with guest Adam Ficsor, CTO and Co-founder of Wassabi Wallet, sparked a deeper consideration of my digital footprint. Like many, I've spent years online neglecting privacy in favour of convenience. The discussion on CoinJoins reminded me of the importance of prioritising privacy, not just romanticising it.
Improving operational security (opsec) is now a personal focus. Resources like Jameson's *Cypherpunk Cogitations* and the Bitcoin Optech newsletter offer valuable guidance. While I've exercised caution, I recognise a need to address my laziness with opsec and take meaningful steps to protect my privacy. Time will reveal the results of these efforts.
## Caribbean Slavery amd Centralised Platforms
While exploring historical systems of control, I delved into the brutal realities of [New World slavery in the British Caribbean](https://aeon.co/ideas/how-did-slaveholders-in-the-caribbean-maintain-control). Enslaved elites, like drivers, were granted limited privileges to maintain order, creating divisions within the community. This divide-and-rule strategy highlights the fragility of oppressive frameworks, which began to crumble with events like the Hatian Revolution and humanitarian activism.
Interestingly, similar dynamics are visible with centralised plaforms like Twitter, LinkedIn, and Instagram. Verified accounts (the "blue checks") act as mordern day 'elites' with perceived freedoms. However, their autonomy is limited by the platforms centralised authority. Challenging the rules risks censorship and cancellation, proving their freedom is an illusion subject to the will of their overseers. Enhancing the argument further for protocols like Nostr to help people win back their freedoms.
-

@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
### Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
### Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
- **Scoperta.** Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
- **Efficienza.** La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
### Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
### Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
### Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
### Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
### Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
### Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\
https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-

@ dd664d5e:5633d319
2024-12-14 15:25:56

Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-

@ 4c96d763:80c3ee30
2024-12-14 08:11:29
# Changes
## Ken Sedgwick (1):
- android: misc fixes for android
## William Casarin (14):
- theme: fallback theme should be dark
- note: add copy note json
- Introducing Damus Notedeck: a nostr browser
- android: fix issues due to rearchitecture
- lockfile: update
- tests: add --testrunner flag so that column tests dont fail on startup
- windows: amd64 installer
- osx: update bundle name
- rpm: fix rpm build
- android: change apk name to Notedeck
- deb: add name so package works again
- enostr: update ewebsock
- nostrdb: update to fix profile queries
- Fix notes note updating in profile view
## kernelkind (3):
- theme: persist across app close
- Revert "move login logic from promise to async fns"
- deps: remove reqwest
pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/1e0228e396367ddbdb3855e5622e1cf550e56782.html)
-

@ 1c19eb1a:e22fb0bc
2024-12-12 19:42:39
I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the [Google Play Store](https://play.google.com/store/apps/details?id=net.primal.android&hl=en_US), Zapstore, or by downloading it directly from Primal's [GitHub](https://github.com/PrimalHQ/primal-android-app/releases/). This review is current as of Primal Android version 2.0.21.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

## Overall Impression
Score: **3.8** / 5
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
## Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
### Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

### Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
### Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
### Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
### Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

### The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for ***any*** feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
### Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is ***not*** intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are ***fast***. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
### Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
## Can My Grandma Use It?
Score: **4.8** / 5
Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarting experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
## How do UI look?
Score: **4.9** / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me ***want*** to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

## Log In Options
Score: **1** / 5
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they ***are you*** on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
## Zap Integration
Score: **4.8** / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
## Content Discovery
Score: **4.8** / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
## Relay Management
Score: **2.5** / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on [nostr.watch](https://nostr.watch). I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
## Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to ***only*** show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
## Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-

@ e83b66a8:b0526c2b
2024-12-11 09:20:56
Can I suggest you read my book, it will tell you a lot. It is important you understand what Bitcoin is before you invest anything into it.
https://www.amazon.co.uk/dp/B0CLJP6R3F/
Firstly, Bitcoin is not like anything else you have ever experienced in your life. Everything else is based on trust and there is a higher authority you can always turn to.
If you loose access to your bank account, you can walk in to a branch with your ID papers and within half an hour or so, your account access will be restored by them. The bank control your account and the money held within it.
If you loose your passport or driving license, the government can issue you new ones. They control your identity.
If you get locked out of your house, you can call a locksmith and they will break in, legally, for you.
Bitcoin is different, it is permissionless and trustless. Nobody can stop you spending your money and you can send it to anyone anywhere in the world instantly without having to trust a third party to authorise payment for you.
By that same token, if you make a mistake and send it to the wrong address or if you lose the keys that secure your Bitcoin, it is gone, nobody can help you. You need to understand and be comfortable with that.
As for Bitcoin as a store of value, this is the first stage that all new Bitcoiners go through, but if you do it properly, it will eventually be the least significant feature.
However, as for Bitcoin price cycles. Every 4 years the supply is automatically halved. This happened on the 20th April this year, you probably saw we were in Warsaw at a halving party. It happened at 3:09am European time, so we were asleep.
Nothing actually happens for around 6 months of the halving, but from 6 - 18 months after the halving, the price rises significantly to adapt to the new supply and scarcity.
So, from the start of November the price has started to rise and will continue to do so in a saw tooth pattern for around the next year.
The price rise often overshoots the new natural price level and so expect a crash around the end of next year, it will be significant and will take a year or so to recover, but will eventually settle to a new price.
In 4 years time, around April 2028, the cycle will happen again.
Bitcoin is not a short term investment, don’t invest unless you are prepared to hold for a minimum of 4 years.
Holding bitcoin for 8 years can produce generational wealth.
The three core tenets of Bitcoin are:
Not your keys, not your coins - in other words, don’t leave them on exchanges
Don’t trust, verify - which leads to:
Do your own research
Study Bitcoin, it will give you back far more than you can imagine.
-

@ e83b66a8:b0526c2b
2024-12-11 09:16:23
I watched Tucker Carlson interview Roger Ver last night.
I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case.
We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money.
The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially).
The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines.
Part of that battle is self custody, part is tax and part are the money transmitting laws.
Roger’s case is also being used as a weapon of fear.
I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so.
Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time.
This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years.
This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
-

@ e6817453:b0ac3c39
2024-12-07 15:06:43
I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
## MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.
## Graph Basics
- A standard **graph** has a set of **nodes** (or vertices) and **edges** (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
## Hypergraph
- A **hypergraph** extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a **hyperedge**, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
## Metagraph
- A **metagraph** allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
## Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.

The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you

Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
## Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
## Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
## Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.
## Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.
Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose.
-

@ e6817453:b0ac3c39
2024-12-07 15:03:06
Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
## The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
## Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like **Lisp** emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
## Lisp: The Earlier AI-Language
**Lisp**, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
## Prolog: Formal Logic and Deductive Reasoning
In the 1970s, **Prolog** was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out **how** to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
## Solvers and Their Role in Complementing LLMs
One of the most powerful features of **Prolog** and similar logic-based systems is their use of **solvers**. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a **solver** can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling **constraint satisfaction problems** — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating **neurosymbolic methods** that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
## Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a **graph of rules**. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a **graph of rules**, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable **modular reasoning**, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of **neural fluency** with **rule-based structure** gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform **deductive reasoning** alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
## Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where **neurosymbolic approaches** shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
**Personal Knowledge Graphs (PKGs)** come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a **graph of rules** that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using **deductive databases** to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
## My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling **knowledge graphs using deductive databases**, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
**Prolog** and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a **graph of rules** that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
## Why It Matters for LLM Employment
Using **neurosymbolic RAG (retrieval-augmented generation)** in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of **neural fluency** with **symbolic accuracy and deductive power** is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-

@ e6817453:b0ac3c39
2024-12-07 14:54:46
## Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
## Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
## RDF and Advanced Topics
## Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
## Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
## Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
## Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
## Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
## Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
## Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-

@ e6817453:b0ac3c39
2024-12-07 14:52:47
The temporal semantics and **temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory** and **semantic memory**. And we also have a lot of theories, right?
## Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
> do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
## Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
## Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a **hybrid clock** or some **global clock** that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
## Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
## Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-

@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
Sometimes perspective is everything...
#[artmodel]( https://bsky.app/hashtag/artmodel)
#[nude]( https://bsky.app/hashtag/nude)
#[nudemodel]( https://bsky.app/hashtag/nudemodel)
------



-

@ 7ecd3fe6:6b52f30d
2024-12-05 10:35:57
I went to bed last night at 96k, thinking we'd have another day of sideways consolidation, maybe if we're lucky a bump on the head at 99k before the 100k dumpers come in to "take profits"
But little did I know what was waiting for me when I opened up my crusty eyes, I checked the chart as one days after their morning wee and nearly wet the entire bathroom, 102k, must be a mistake, let's check Coingecko, let's check the local exchanges, let's check social media, and it was confirmed like 6 blocks in baby, there's no going back!
Ladies and gentlemen, grab your laser-eye NFTs and dust off those 2017 memes - we've finally arrived! Bitcoin has transcended the mythical $100,000 price point that HODLers have been hallucinating about since the Obama administration.
We have succesfully meme'd the dream into a reality, can anything stop us now? The [Banana zone](https://thebitcoinmanual.com/articles/btc-banana-zone/) hath arrived
-----------

-----------
## Why the big break?
Is it unrest in France with the government collapsing, is it South Korean uncertainty with their president declaring Martial law, is it Putin coming out to admit you can't ban Bitcoin?
Is it countries trying to find a hedge against Trumps' proposed tariffs?
Who knows?
To me it's just another day of sellers exhausted and buyers are eating through the order book like hungry-hungry hippos
## Bottom of the bear to getting some serious air time
If you've been here for one full cycle, and stayed the course it's been a wild ride, we saw Terra Luna, FTX, Celsius, BlockFi blow up and a massive draining of liquidity from the market.
The dream was dead and we hit rock bottom in November 2022, at 15k, to those who nailed that absolute bottom, I salute you.
Anyhoo, it's been a slow grind upwards, the crab market of choppy consolidation normally is, but you psychos continued to hold steady and deploy capital even when number continue to go down!

## The meme, the dream and now the cream
The bitcoin maximalists who've been sporting perpetual laser-eye Twitter and nostr profiles can now collectively exhale.
Those same folks who've been predicting "$100K by EOY" every single year since 2017 can now do a victory lap, wearing their tinfoil-lined Gucci tracksuits.
You were wrong many times, only to be proven right eventually!
Remember when explaining Bitcoin's potential value used to involve complex blockchain narratives and decentralization lectures?
## Call up the cry babies
When Bitcoin looked down and out there were no shortage of doom and gloomers writing another failed obituary, Dan Pena, Charlie Munger, Warren Buffer, Peter Schiff and Peter Zeihan all had to yap and we listened and laughed
<iframe width="560" height="315" src="https://www.youtube.com/embed/SrSj2RmRtbs?si=sNU_XUX2izkDFngj" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
Let's hear what mama has to say on the subject of Bitcoin?
<blockquote class="twitter-tweet"><p lang="en" dir="ltr">Keep dreaming. Bitcoin is never going to hit $100,000!</p>— Peter Schiff (@PeterSchiff) <a href="https://twitter.com/PeterSchiff/status/1192802503856984064?ref_src=twsrc%5Etfw">November 8, 2019</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script>
Now it's just: "Told ya so" - accompanied by shitcoiners and nocoiners are angry coz of dey enlarged medulla oblongata
-----------
Times like this, I often think of the wise and eloquent words of MSTR Gigachad Saylor
<blockquote>
Put money into Bitcoin and wait for number to go up biggly, if number go down put more money in and wait for number to go up bigglier - Michael Saylor
</blockquote>
-----------
## Setting up base camp for the march up Mount Milli-manjaro
The journey to $1 million feels eerily similar. We'll witness another brain-melting crypto pilgrimage - let's call it Mount Milli-manjaro - where every Reddit thread and Twitter space will sound like a combination of economic prophecy and sci-fi fever dream.
Pro tip for newcomers: Pack extra copium, a sense of humor, and maybe some popcorn.
This ride is just getting started.
To the moon? 🚀🤡₿ Looks likely bar a massive black swan, 2025, looks like this thing is going to run with big Usain Bolt strides as we enjoy a year of price discovery, speculation and all the scams that will fester as retail comes piling in to make their overnight fortunes.
I know it's fun to hand out I told you so's and you should enjoy it, take the victory lap but even that gets old, while it's hard to do, try to stay humble and enjoy stack the perpetual top!
-

@ b2d670de:907f9d4a
2024-12-02 21:25:18
This is a list of nostr clients exposed as onion services. The list is currently actively maintained on [GitHub](https://github.com/0xtrr/onion-service-nostr-clients). Contributions are always appreciated!
| Client name | Onion URL | Source code URL | Admin | Description |
| --- | --- | --- | --- | --- |
| Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | [operator](nostr:nprofile1qyvhwumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdshszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmg9umdvr) | N/A |
| moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | [operator](nostr:nprofile1qyv8wumn8ghj7un9d3shjtnddaehgctjvshx7un89uq36amnwvaz7tmzdaehgu3wvf5hgcm0d9h8g7r0ddhjucm0d5hsqgy8wvyzw6l9pn5m47n7tcm5un7t7h5ctx3pjx8nfwh06qq8g6max5zadtyx) | minimalist monero friendly nostrudel fork |
| Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostrnpub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest tagged docker image |
| Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest "next" tagged docker image |
| Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | [operator](nostr:nprofile1qqszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsxx2q3a) | Runs nsite. You can read more about nsite [here](https://github.com/lez/nsite). |
-

@ b2d670de:907f9d4a
2024-12-02 21:24:45
# onion-service-nostr-relays
A list of nostr relays exposed as onion services.
## The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options |
| --- | --- | --- | --- | --- | --- |
| nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A |
| relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A |
| nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A |
| nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN |
| bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A |
| relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN |
| freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) |
| inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC |
| filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC |
| N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A |
| nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A |
| nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A
| relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A |
| nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR |
| nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A |
| Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A |
## Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns.
If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub.
### Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-

@ e31e84c4:77bbabc0
2024-12-02 10:44:07
*Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net*
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
> An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
- A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
- The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
- These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
- U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
- This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
- The current debt situation raises concerns about sustainability.
- The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
- This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
### Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
- Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
- Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
- Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
- Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
- Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
- There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
- Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
- Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
- Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
- There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
- The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
- While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
- Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
- [River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.](http://bitcoin%20and%20fixed%20ihttps//blog.river.com/bitcoin-interest-on-cash/ncome)
- [Onramp: Bitcoin, The Emergent Asset Class](https://onrampbitcoin.docsend.com/view/j4wje7kgvw357tt9)
- [MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes](https://www.microstrategy.com/press/microstrategy-announces-pricing-of-offering-of-convertible-senior-notes_09-18-2024)
---
*Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net*
-

@ 9cb3545c:2ff47bca
2024-12-01 00:18:45
Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process.
In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! **I highly recommend reading this post fully before starting the migration process.**
Before we dive in, [here](https://community.umbrel.com/t/how-to-update-from-umbrelos-0-5-to-umbrelos-1-1-on-linux-devices/16704#how-to-update-from-umbrelos-05-on-a-linux-device-3) is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully.
**With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.**
## The Order of Steps
### Tip #1:
In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups.
## Creating the Bootable USB Stick
### TIP #2:
After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route.
### TIP #3:
Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.
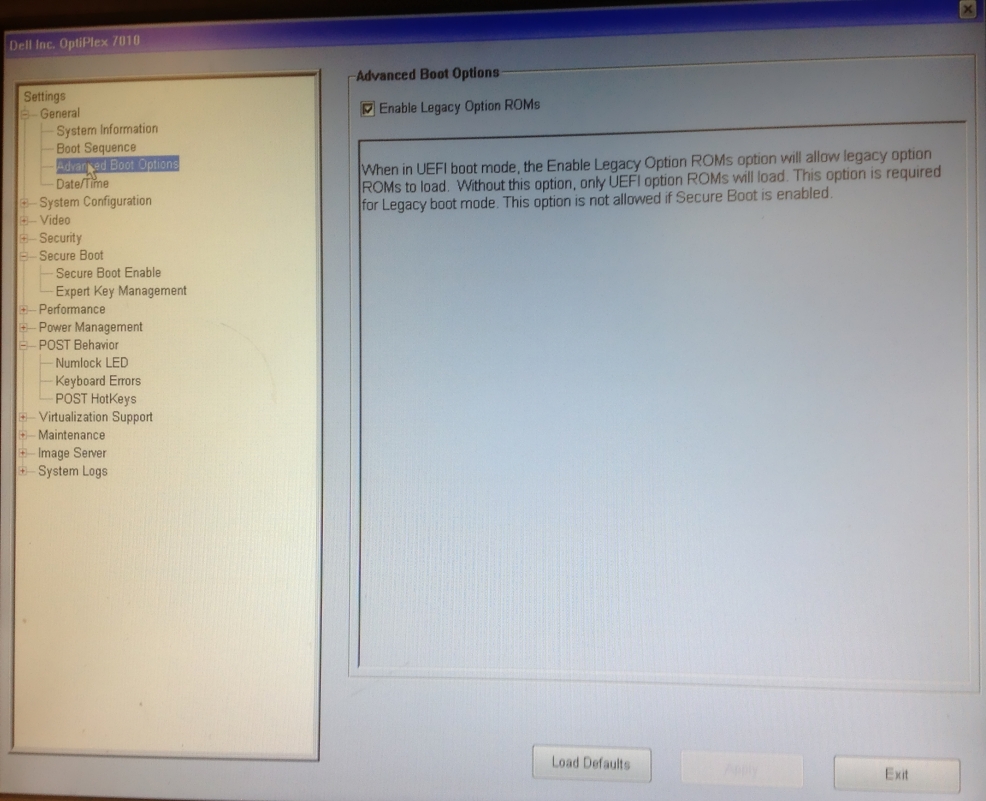
### Tip #4:
Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node.
**If all is good, you are ready to get back to the guide and walk through the steps.**
## Preparing the Hardware
### Tip #5:
In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences.
## The Migration Process
### Tip #6:
Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. **you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again.** If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this.
But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again.
### Tip #7:
This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it.
### Tip #8:
If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues.
### Tip #9:
During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D
### Tip #10:
I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help.
# Have Fun, and Good Luck!
-

@ 1ef695e1:15351d5f
2024-11-29 14:21:00
After getting my ham licence in 2013 I found out about SOTA. I was enthusiastic as I have a long history of hiking in the mountains while a scout and then as a Scoutmaster. Now I was going to combine the two yet I immediately encountered a big problem. Very few South African summits were listed on the SOTA database and some of those listed did not even qualify as summits. I enquired of SOTA management and was told that "South Africa is on hold until all the summits are correctly mapped and checked." Only then could the summits be loaded to the database.
Using GIS software and my 1:50000 topographic maps I began mapping summits in my home province Limpopo that qualified according to the SOTA criteria.
An individual prominence of 150m or more was easy to determine. Doing the mapping I found a lot of summits that were obvious, but finding the key col of each summit was more difficult. The older maps in South Africa actually had a lot of the key cols displayed and using my combined methods I proceeded to map summits one by one and add the data to a spreadsheet. Taking approximately 8 minutes to map a summit it took me months to map Limpopo. I missed summits where the summit is spread over a large area and though it qualifies due to a 150m or more prominence it does not look like a summit and these we added later.
I sent my mapping data to OM Andrew VK3ARR in Australia and received a thumbs up as to my data accuracy. I was pleasantly surprised when my Limpopo summits appeared on the SOTA database even though the rest of the country was still not done. I immediately started mapping the next province of Mpumalanga using my manual methods.
Sid Tylor ZS5AYC from Kwazulu - Natal, who became SOTA manager for South Africa, and I had been discussing the processes and he arranged access to online software with automated summit processing where we could just check key col position and all the data per summit was processed much quicker. Frustrating for me was that I could not see what the software was doing and we just checked key cols without knowing where the summit was or its other data.
I completed the remaining Mpumalanga summits using the software access and then completed the Western Cape summits after which Sid and I split the Northern Cape summits between us. The other provinces were processed by various operators including some much appreciated assistance from Australian hams.
A big thank you to all in SOTA management, in South Africa, those that assisted from Australia, as well as SOTA UK, for making it possible for us to enjoy the adventures of SOTA.
Activating Renosterkop ZS/NC-272 in the Northern Cape

-

@ fe7f6bc6:c42539a3
2024-11-29 01:54:31
A few weeks ago, I sat down with Chad ([full podcast](https://creators.spotify.com/pod/show/proofofhealth/episodes/1-How-Muay-Thai-Fighting-Saved-My-Life---Chad-Mane-e2pnbmp)), a seasoned Muay Thai fighter with over a decade of experience, to talk about life inside and outside the ring. Chad’s story is raw, intense, and unfiltered—a journey of struggle, discipline, and transformation. His insights left me reflecting on how combat sports, especially Muay Thai, can teach us profound lessons about resilience, focus, and the human spirit.
### **The Fight Beyond the Ring**
What struck me most was how Muay Thai isn’t just a sport for Chad—it’s a way of life. He began his journey as a teenager, struggling with family issues and uncertainty about his future. A chance meeting led him to Thailand, where he trained intensely and fought his first bout just 28 days later. Chad told me, “Muay Thai saved my life,” and I could feel the weight behind those words.
For Chad, the ring became a space to confront not just opponents but his own fears and insecurities. The process of training—the relentless hill sprints, countless kicks, and sparring sessions—taught him how to face challenges head-on. Fighting wasn’t about aggression; it was about finding strength in adversity.
---
### **The Beauty in the Brutality**
One of the most fascinating things Chad shared was his perspective on pain and sacrifice. During his career, he’s endured broken ribs, countless stitches, and even fought with a broken nose for eight years before getting it fixed. “Pain is the best teacher,” he said, explaining how injuries forced him to adapt and improve.
What I found most compelling was how this physical suffering seemed to heighten his appreciation for life. Chad described moments after brutal training sessions when even a sunset or a simple breeze felt extraordinary. It’s as if the harshness of the ring makes the world outside it feel brighter, sharper, and more alive. “When you’re ready to die in the ring,” he said, “you start seeing life differently.”
---
### **The Mental Battle**
Chad emphasized the mental aspect of fighting, something I hadn’t fully appreciated before. He talked about the mindset required to step into the ring: the inner dialogue where you convince yourself you’re ready to endure pain and push beyond limits. “You can play football or tennis, but you can’t play Muay Thai,” he said, driving home the seriousness of the sport.
Before a fight, Chad uses visualization to prepare himself for the intensity of combat. He doesn’t shy away from the danger but instead leans into it, fully accepting the risks. This mindset, he believes, is what separates good fighters from great ones.
---
### **Lessons for Life**
While most of us won’t step into a Muay Thai ring, Chad’s experiences offer valuable lessons that apply to all areas of life:
- **Discipline Creates Freedom**: The structure of relentless training gave Chad a sense of purpose and control over his life.
- **Face Your Fears**: Whether it’s an elbow to the face or a difficult decision in life, avoidance only makes things worse.
- **Surround Yourself with the Right People**: Chad stressed the importance of training with people who push you to be better. “Energy matters,” he said, and I couldn’t agree more.
---
### **Final Thoughts**
Chad’s story reminded me why I wanted to take on my own Muay Thai journey. It’s not just about fighting; it’s about testing yourself in ways that reveal who you really are. For Chad, the ring isn’t just a place to compete—it’s a place to grow, to learn, and to become a better version of himself.
After our conversation, I realized that the lessons of Muay Thai go beyond the gym. Whether you’re training for a fight or tackling challenges in everyday life, the principles of resilience, discipline, and self-reflection are universal.
If you’re curious to learn more about Chad’s journey, I highly recommend watching the [documentary](https://youtu.be/GPug-MuCKKY) we worked on together. It’s a glimpse into the raw, unforgiving world of Muay Thai—and the unshakable spirit of those who live it.
Stay Healthy - Max
-

@ e31e84c4:77bbabc0
2024-11-27 11:32:57
‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
### Childhood Lessons
As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny.
### Definitions of Security
Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs.
Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis.
When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change.
## How Bitcoin Changed Me
The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights.
Here are just a few examples:
### Freedom of Expression
Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions.
### Adequate Living Standards
Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards.
Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards.
### Freedom of Association
Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions.
Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code.
Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power.
### Right to Information
The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use.
## Personal Context
For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code.
In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon…
## A Modern Necessity
These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview:
*“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” ([https://www.youtube.com/watch?v=K4ciiDyUvUo](https://www.youtube.com/watch?v=K4ciiDyUvUo))*
As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society.
The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities.
## Bitcoin’s True Security
Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it.
Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections.
Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times.
---
‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
-

@ 129f5189:3a441803
2024-11-22 03:42:42
Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario.
The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy.
After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America.
Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million.
China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions...
https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg
For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions.
In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border.
A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention.
https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg
In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere.
The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years.
https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg
The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021.
In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government.
https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg
Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues.
In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities."
https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg
The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024.
Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction.
In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government.
https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg
Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University.
"The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times.
General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country.
"We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time.
In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade."
https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg
In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues."
Under the previous administration, China had received preferential treatment.
In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan.
The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security.
No public records show that the project has progressed since then.
https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg
Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark.
"Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement.
"Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face."
https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg
The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era.
Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel."
https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg
Access to space plays a crucial role in the CCP's strategic objectives.
Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China.
According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice.
According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access.
China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely.
The big question is: what could this facility do in times of war?
https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg
Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit.
The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface.
Additionally, it offers strategic advantages for any government involved in espionage.
https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg
Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner.
However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives.
Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023.
https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg
-

@ a39d19ec:3d88f61e
2024-11-21 12:05:09
A state-controlled money supply can influence the development of socialist policies and practices in various ways. Although the relationship is not deterministic, state control over the money supply can contribute to a larger role of the state in the economy and facilitate the implementation of socialist ideals.
## Fiscal Policy Capabilities
When the state manages the money supply, it gains the ability to implement fiscal policies that can lead to an expansion of social programs and welfare initiatives. Funding these programs by creating money can enhance the state's influence over the economy and move it closer to a socialist model. The Soviet Union, for instance, had a centralized banking system that enabled the state to fund massive industrialization and social programs, significantly expanding the state's role in the economy.
## Wealth Redistribution
Controlling the money supply can also allow the state to influence economic inequality through monetary policies, effectively redistributing wealth and reducing income disparities. By implementing low-interest loans or providing financial assistance to disadvantaged groups, the state can narrow the wealth gap and promote social equality, as seen in many European welfare states.
## Central Planning
A state-controlled money supply can contribute to increased central planning, as the state gains more influence over the economy. Central banks, which are state-owned or heavily influenced by the state, play a crucial role in managing the money supply and facilitating central planning. This aligns with socialist principles that advocate for a planned economy where resources are allocated according to social needs rather than market forces.
## Incentives for Staff
Staff members working in state institutions responsible for managing the money supply have various incentives to keep the system going. These incentives include job security, professional expertise and reputation, political alignment, regulatory capture, institutional inertia, and legal and administrative barriers. While these factors can differ among individuals, they can collectively contribute to the persistence of a state-controlled money supply system.
In conclusion, a state-controlled money supply can facilitate the development of socialist policies and practices by enabling fiscal policies, wealth redistribution, and central planning. The staff responsible for managing the money supply have diverse incentives to maintain the system, further ensuring its continuation. However, it is essential to note that many factors influence the trajectory of an economic system, and the relationship between state control over the money supply and socialism is not inevitable.
-

@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
### Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
### Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
#### The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
### Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
#### Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
### Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3).
Here's how you set it up at a high level–
1. Buy yourself some NFC cards
2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
3. Write the nencryptsec to the NFC card as a custom URI
4. Tap to load the login screen, and enter your password to login
Here it is in detail–
#### Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
#### Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
1. Login to Amethyst with your nsec,
2. Open the sidebar and click "Backup Keys",
3. Enter a password, and click "Encrypt and my secret key",
4. It will add the password-protected key to your clipboard in the format "ncryptsec1...",
5. Remember to backup your password.
#### Write the ncryptsec to the NFC card
1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it,
2. Click "Write" and "Add a record", then click "Custom URL / URI",
3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
5. Place your NFC card against your phone, and it will write to the card,
6. Your card is ready.
#### Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
### Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
1. Buy yourself some NFC cards,
2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it,
2. Click "Write" and "Add a record", then click "Custom URL / URI",
3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
4. Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
### What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
### What's Next
Over my first four blogs I have explored creating a good Nostr setup
- [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw)
- [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je)
- [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0)
- [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e)
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-

@ fd208ee8:0fd927c1
2024-11-08 10:27:40
## You have no idea
I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.

It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse.
I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._
But you were always apart. You were always two different people. You just didn't notice, until now.

I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship.
## I was raised by relaxed revolutionaries
Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics.
It's like magic, but it's the result of a mindset, not a worldview.
Or, as I like to quip:
> The best way to stay married, is to not get divorced.

My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live.
My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.

The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on.
And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer.
You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.

We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something.
Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
-

@ a367f9eb:0633efea
2024-11-05 08:48:41
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
> In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
>
> The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
> In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
>
> The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)?
**As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).**
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
## **Open-source matters**
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
## **Open-source is for your friends, and enemies**
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
## **Limiting open-source threatens our own advancement**
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols.
The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
*Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).*
-

@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
> ### 第三方API合集:
---
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 |
| --- | --- | --- | --- |
| AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) |
| OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) |
| CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) |
| OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) |
` 持续更新。。。`
---
### 推广:
访问不了openai,去`低调云`购买VPN。
官网:https://didiaocloud.xyz
邀请码:`w9AjVJit`
价格低至1元。
-

@ 0e501ec7:de5ef3a4
2024-10-30 17:25:51
From now on, when, i open my phibe for distraction, i will write something, anything, cheers
Okay, daarnet heeft het niet gewerkt. Nu wel? of houdt het me nu tegen van iets anders te gaan doen? bof ook oke. Het ruikt hier naar kak en da stoort mij zohard, zeer afleidend. Vandaag was een goeie dag, we zijn in de voormiddag een walbootboom tegen gekomen, en later, in Vailly sur aisne, heb ik die allemaal gekraakt terwijl Tim de kettingen kuiste. Was wel leuk, al kreeg ik er rugpijn van, net als nu. Zitten geeft mij meer rugpijn dan fietsen deze dagen, surtout zitten en iets doen met mijn handen, mijn rug sen schouders gaan dan als een egeltje poef inelkaar.
We zitten nu een beetje in een maanlandschap, temidden industriele velden, bij een kleine haag, sleedoorn. We hebben iets te lang doorgefietst, we passeerden een goeie plek on half zes, maar toen kwam de schemering en sloeg de vermoeidheid toe net voor we toekwamen. Ik ben moe, ook al hebben we niet zoveel gefietst vandaag, nog geen 50km. We hebben batuurlijk wel 3 uur op het kerkplein van Vailly gezeten. Was heel leuk om het rustige dorpje, waar nog wel een beetje leven was, een bakker, een traiteur, een paar winkels, zo te zien. Mensen passeerden, zeiden goeiendag, smakelijk, of kwamen een hele babbel doen. Tussendoor luisterde ik wat muziek. Een heel leuk werkke, walnoten kraken, ik denk dat ik nog niet vaak zo van de herfst genoten heb als daar, op dat bankje. De kleuren in het bos, en de dans van de spreeuwen stonden mij nog kevendig voor. De mensen wensten ons veel succes, je zag dat ze ons zot vonden om door de grijze herfst te fietsen.
Vanaf hier is er een grote oranje vlek op de horizon te zien, de stad van licht. Parijs!
-

@ 0e501ec7:de5ef3a4
2024-10-30 17:21:46
Buizerd in de mist. Spreeuwen op een elektriciteitspaal. Je komt een beetje dichter, ze zwermen op in een dansende wolk. Zwerm voor mij niet identificeerbaar, tsjirpende vogels. Een blaadje valt, bijna in je pot met thee. Aan een hoge tak, maar toch de onderste, hangt een verloren vissershaak. Het water aan de kant ziet er vies en slijmerig uit. Vannacht was ik bang erin te vallen, slaapdronken op tocht naar een plek om pipi te doen. Het verlangen naar een middagmaal zonder pindakaas. Een klein lapje kleinschalige landbouw, met groentebedden op mensenmaat, in de zee van industrie-veld. In de verte een boer die met zijn halve oorlogsmachine zijn gewas beschermd. In de bossen hangt het vol lianen, veel meer dan thuis. Op de weg een overreden marter. Naast de weg, dappere kamille, teder bloeiend. Als de schemering valt: vermoeidheid. In de nacht stilte, gepruttel van ons stoofpotje, aangevuurd met brandalcool. In de ochtend: mist. Een buizerd.
-

@ 4c48cf05:07f52b80
2024-10-30 01:03:42
> I believe that five years from now, access to artificial intelligence will be akin to what access to the Internet represents today. It will be the greatest differentiator between the haves and have nots. Unequal access to artificial intelligence will exacerbate societal inequalities and limit opportunities for those without access to it.
Back in April, the AI Index Steering Committee at the Institute for Human-Centered AI from Stanford University released [The AI Index 2024 Annual Report](https://aiindex.stanford.edu/report/).
Out of the extensive report (502 pages), I chose to focus on the chapter dedicated to Public Opinion. People involved with AI live in a bubble. We all know and understand AI and therefore assume that everyone else does. But, is that really the case once you step out of your regular circles in Seattle or Silicon Valley and hit Main Street?
# Two thirds of global respondents have a good understanding of what AI is
The exact number is 67%. My gut feeling is that this number is way too high to be realistic. At the same time, 63% of respondents are aware of ChatGPT so maybe people are confounding AI with ChatGPT?
If so, there is so much more that they won't see coming.
This number is important because you need to see every other questions and response of the survey through the lens of a respondent who believes to have a good understanding of what AI is.
# A majority are nervous about AI products and services
52% of global respondents are nervous about products and services that use AI. Leading the pack are Australians at 69% and the least worried are Japanise at 23%. U.S.A. is up there at the top at 63%.
Japan is truly an outlier, with most countries moving between 40% and 60%.
# Personal data is the clear victim
Exaclty half of the respondents believe that AI companies will protect their personal data. And the other half believes they won't.
# Expected benefits
Again a majority of people (57%) think that it will change how they do their jobs. As for impact on your life, top hitters are getting things done faster (54%) and more entertainment options (51%).
The last one is a head scratcher for me. Are people looking forward to AI generated movies?

# Concerns
Remember the 57% that thought that AI will change how they do their jobs? Well, it looks like 37% of them expect to lose it. Whether or not this is what will happen, that is a very high number of people who have a direct incentive to oppose AI.
Other key concerns include:
- Misuse for nefarious purposes: 49%
- Violation of citizens' privacy: 45%
# Conclusion
This is the first time I come across this report and I wil make sure to follow future annual reports to see how these trends evolve.
**Overall, people are worried about AI. There are many things that could go wrong and people perceive that both jobs and privacy are on the line.**
---
Full citation: *Nestor Maslej, Loredana Fattorini, Raymond Perrault, Vanessa Parli, Anka Reuel, Erik Brynjolfsson, John Etchemendy, Katrina Ligett, Terah Lyons, James Manyika, Juan Carlos Niebles, Yoav Shoham, Russell Wald, and Jack Clark, “The AI Index 2024 Annual Report,” AI Index Steering Committee, Institute for Human-Centered AI, Stanford University, Stanford, CA, April 2024.*
The AI Index 2024 Annual Report by Stanford University is licensed under [Attribution-NoDerivatives 4.0 International](https://creativecommons.org/licenses/by-nd/4.0/?ref=chooser-v1).
-

@ 4ba8e86d:89d32de4
2024-10-25 11:40:05
A loja Aurora vem com um excelente design, interface de usuário amigável para iniciantes e muitos recursos.
A loja Aurora foi originalmente baseada na loja Yalp de Sergei Yeriomin, mas a versão 3.0 passou do zero para a conclusão seguindo o Material Design reescrito para rodar em todos os dispositivos Android 5.0.
Dentre as diversas características oferecidas pela Aurora Store, destacam-se:
- Login Anônimo: Para garantir sua privacidade, você pode fazer login anonimamente, assegurando que suas atividades permaneçam confidenciais.
- Login do Google: Além do anonimato, a opção de login do Google permite acessar aplicativos pagos e instalar versões beta.
- Falsificação de Dispositivo: Caso um aplicativo não esteja disponível para o seu dispositivo, você pode recorrer à funcionalidade de falsificação de dispositivo, permitindo a instalação.
- Filtragem de Aplicativos F-Droid: A possibilidade de filtrar aplicativos do F-Droid evita que eles apareçam em sua lista de atualizações.
- Aplicativos na Lista Negra: Ao adicionar aplicativos à lista negra, você mantém o Google no escuro quanto aos aplicativos instalados.
A loja de aplicativos se apresenta com um design clássico, apresentando uma capa de apps e jogos em destaque, proporcionando um visual convidativo. A aba de aplicativos instalados permite uma gestão mais eficiente, possibilitando atualizações automáticas para a versão mais recente disponível.
A busca por aplicativos é facilitada por categorias que abrangem diversos interesses, como fotografia, música e áudio, compras, personalização, livros e quadrinhos, entre outras. A eficaz função de busca permite localizar aplicativos específicos de maneira rápida e fácil.
A Aurora Store se diferencia pela tecnologia de pesquisa única, agilizando a descoberta de aplicativos em questão de segundos. Além disso, a loja vem com a licença GPLv3, reforçando seu compromisso com o software livre.
Privacidade é um foco central da Aurora Store, sendo considerada uma excelente alternativa para quem preza por manter suas informações pessoais protegidas. O aplicativo suporta contas pessoais e permite downloads com contas anônimas, assegurando que suas atividades não estejam vinculadas a você.
Com a integração do Exodus, a Aurora Store verifica rastreadores presentes nos códigos dos aplicativos, proporcionando uma visão mais transparente das informações coletadas.
O aplicativo se destaca por ser livre de anúncios e pop-ups, proporcionando uma experiência de uso mais limpa. O suporte ao modo escuro oferece conforto visual em ambientes com pouca luz ou durante a noite.
A Aurora Store é uma alternativa valiosa à Google Play Store, oferecendo um ambiente mais privado, recursos robustos e um design elegante que visa aprimorar a experiência do usuário em busca e gerenciamento de aplicativos.
https://github.com/whyorean/AuroraStore
https://f-droid.org/packages/com.aurora.store/
https://gitlab.com/AuroraOSS/AuroraStore/-/releases
-

@ 0e501ec7:de5ef3a4
2024-10-24 20:03:28
Ik maak even een kleine sprong in de tijd, stichting Elzeard bespreek ik later nog ;)
Vandaag (24/10) vertrokken we bij Patsy en Els. Patsy is de meter van Tim, en hij heeft een kleine traditie om altijd bij hun langs te gaan als hij in de Ardennen fietst. Ze kochten ongeveer tien jaar geleden een wei in Marcourt, en besloten op een gegeven moment om daar te gaan wonen en een huis te bouwen. Ze hebben een bijna-passief woning, een leuke moestuin en veel fruitbomen, en op de wei staan er schapen van een zekere Eddy. Ze spreken aardig wat frans, en zijn zeer betrokken bij het sociale leven in het dorp! Niet zoals de tweede-verblijf-vlamingen die in grote getallen rust opzoeken in de Ardennen dus. We hielpen bij hun in de tuin, brandhout zagen en kappen, hooi leggen in de moestuin (ze doen geen bodembewerking! Voeren enkel hooi aan om de structuur te verbeteren en kruid tegen te werken). Daarnaast hielpen we ook met wat bomen en struiken te verplanten, en deed Tim zijn job als fietsenmaker. We aten verrukkelijk in de avond, van de heerlijke kookkunsten van Els. Een van de avonden (triggerwarning: vlees eten) was het een gerecht met vlees van een Lam, een van de diertjes die op de wei zelf geboren was en gegroeid. Tot het dus geslacht werd, en Patsy en Els er hun deeltje van kregen/kochten. Ik vond het wel een heftige ervaring om dat te eten, maar het voelde niet persé slecht. Denk ik. Al zag ik wel af en toe een Lammetje door een veld huppelen als ik met mijn ogen knipperde.
Het waren fijne dagen bij hun, maar het deed ook deugd om weer verder te gaan: gewoon op de fiets, en niet meer te hoeven socialiseren. In het begin van de dag moest ik nog even op gang komen, had wat pijn aan mijn rug van een forse beklimming zonder opgewarmd te zijn (het was ook een koude ochtend). Ook was Tim een paar keer een beetje fors (ms was het ook voor hem ochtend, kan zijn :) )waardoor ik mij even niet heel top voelde, moe en wat verdrietig, niet zo geborgen en energiek. Ik begon te twijfelen of ik wel sterk genoeg was voor deze reis, om met Tim mee te kunnen, om zonder veilige haven te zijn. Na een tijdje chieken en tobben, probeerde ik naar het landschap te kijken, en dat als veilige haven te zien. Niet zo heel makkelijk, geen vanzelfsprekende veilige haven, je moet eerst voorbij het landschap als decor, en het landschap als vluchtige voorbijgaandheid. Maar het hielp wel. De glooiingen van de Aarde, hun heuvels, de Bomen in de wind, de zachte Wolken met hun zwevende texturen, de verbaasde Koeien, het is ook wel thuis. Ik ben ook hier thuis. (Deze avond toen we begonnen te koken kwam een Reetje op bezoek, keek even heel doordringend en stoof rond ons weg. Dag Reetje; tot ziens.) Daarna overwon ik mijn obsakels en begon ik erover tegen Tim, niet gemakkelijk, maar was wel heel fijn, hij begreep het wel, luisterde wel. Zei ook dat hij zich al afvroeg of er iets was (zie je wel). Daarna voelte ik mij dus helemaal beter, en hadden we nog een zalige fietstocht. De zon kwam erdoor, het was warm, de heuvels gingen omhoog en omlaag, zoeffff. Ergens verloor ik mijn handschoenen, die had ik los op mijn bagage gelegd en was dan vertrokken. Dus: terug! Gelukkig lagen ze niet al te ver weg, ze waren pas bij een grote boebel van mijn bagage gekieperd. We fietsten uiteindelijk 67km, en stegen bijna 1000m. Echt wel de zwaarste tocht tot nu, maar fysiek voelde het al een pak minder lastig als in de eerste weken. Mischief ben ik dan toch (fysiek) sterk genoeg? We passeerden onderweg nog het meest cute (cuteste?) Bio-winkeltje ooit, een klein kamertje vol met verse groenten, waar we waterkers en eitjes en nog een brood voor morgenvroeg kochten. Nu liggen we hier in een bos naast Sovet, en gaan we morgen weer verder. Slaapwel!
-

@ 4ba8e86d:89d32de4
2024-10-24 14:03:14
O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais.
Recursos e Funcionalidades.
O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório.
Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes.
O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets.
Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo:
1. Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional.
2. Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes.
3. Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações.
O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável.
https://www.collaboraoffice.com/
https://github.com/CollaboraOnline/online
-

@ 0e501ec7:de5ef3a4
2024-10-23 20:28:38
Het is al een hele tijd geleden dat ik nog eens een blogpost heb gemaakt, mijn excuses hiervoor. Het is nog niet zo eenvoudig om een rustig moment te vinden en daar dan ook het initiatief te verzamelen om te beginnen schrijven. We zijn ondertussen alweer wat opgeschoten, richting het zuiden. Het voelt ook al zo, de laatste dagen is het prachtig weer, een heerlijk zonnetje! Gisteren had ik zelfs al te warm! Maar ik ben hmm redelijk zeker dat het niet ligt aan onze zeer zuidelijke positie (de Ardennen), maar gewoon aan geluk met het weer. Denk je niet?
Ik maak even een recap van wat er allemaal gebeurd is sinds de vorige keer, dan zijn jullie weer op de hoogte. Of toch voor degene die niet ondertussen stiekem Tim zijn blog hebben gelezen, want daar zijn er actuelere updates te vinden. Tim is een gedisciplineerd en trouwe blogger, niet zoals mijn getruntel en uitgestel. Dus na de fameuze vrijdag waarin we houtverbindingen leerden maken, kwam de werkdag op het Abtshof. We hielpen eerst met Pieter en Evelien in de tuin: winterwortels en patatten oogsten! De Woelratten zouden er anders spoedig aan beginnen, eigenlijk waren ze al begonnen. Dus de wortels moesten uit de grond, om dan ingekuild in de kelder gezet te worden (dat zouden we uiteindelijk maandag doen). We probeerden ook zoveel mogelijk kruid weg te halen (niet on, gewoon kruid, veel eetbaar, sommigen medicinaal, maar ook in de weg van de zo gewenste groentjes!) (er stond zelfs oregano tussen!). Vele wortels en aardappels kwamen beschadigd uit te grond, die hielden we apart omdat ze niet meer bewaard konden worden. Daar aten we dan de komende 4 dagen van. Telkens op een andere wijze: aardappelpuree met wortels, patatjes met wortels in de oven, in de pan gebakken worteltjes... Na het oogsten en wieden kwam Pieter af met een freesmachien: om de bovenste tien centimeter helemaal los te werken en om te woelen. Dat was een vreselijke dieselduivel, lawaai, stank, doodsangst voor de freesmessen (met een eerste keer zo een machien te gebruiken komen er natuurlijk ook gruwelverhalen, dan pas je beter op), maar wel een coole ervaring! Zo lag de Bodem los voor de tere spinazieplantjes. Evelien wou liever niet frezen, omdat de bodemstructuur op lange termijn minder goed wordt, dus deden we bepaalde stukken wel en andere niet. Daarna gingen we helpen binnen: ramen sappen. Blijkbaar een ander woord voor in-oliën :). Wel een leuk werkje, zorgzaam voor het hout, zachtjes met de borstel heen en weer.
Zondag rustdag! Iedereen gaan stemmen, wij niets te doen. Ik heb dan maar de tijd genomen een beetje te lezen in The Flowering Wand (zeer goed boek, "Rewilding the sacred masculine"), en een paar brieven te schrijven en te versturen via mail. Daarna ging ik Tim vergezellen, die naarstig in de weer was in het houtatelier. Onze 'introductiecursus' had als eindwerk het maken van een rek met houtverbindingen, dus dan moest dat af geraken! Tim ging daar echt hard in: uiteindelijk heeft hij maandagavond tot 1u 's nachts doorgewerkt! Zotte kerel, respect. Na het houtatelier-werk, en avondeten, gingen Tim en Teo nog naar de Kat, een traditioneel dorpscafé om de hoek. Daar leerden ze de lokale bevolking wat kennen, keken ze een dartswedstrijd, en babbelden er gretig op los. Ik was ondertussen al naar bed, natuurlijk. De dagen erna werkten we ook verder aan onze kast, daar kwam wel wat bij kijken! Het was ook nooit heel gemakkelijk om allemaal op elkaar afgestemd te zijn, en te begrijpen wat de andere juist bedoelt bij besprekingen over hoe in godsnaam we dat aanpakken. Maar uiteindelijk zijn we allemaal wel heel trots op het resultaat, en hij is al in gebruik :)). Jakob was ondertussen bezig met parket te leggen in de toekomstige woning van Pieter en Kim. Toen de stagiair weg was, mocht ik vervang-stagair spelen. Leuk! Parket leggen is uiteindelijk helemaal niet zo moeilijk, al is het soms wat gepruts. Of, Jakob heeft het gewoon heel goed uitgelegd, waardoor ik er snel mee weg was. Jakob was de echte held van onze week bij het Abtshof, met zoveel geduld en enthousiasme heeft hij ons echt een beetje in zijn vak geïntroduceerd. Hij was ook zeer gelukkig dat wij enthousiast waren, en zei dat we zeker terug mochten komen om meer te leren en te helpen. Klinkt niet slecht :)
Helemaal op het einde van de laatste dag vroeg Pieter of we nog konden helpen iets te dragen. Zware steen was dat! Ik stond aan de buitenkant, en met mijn lange benen kwam er natuurlijk veel gewicht op mij. Te zwaar! Dat was niet goed voor mijn rug, en dat heb ik de dag erna nog sterk gevoeld bij het fietsen. Het is wel wat lastig met die rug, ik hoop dat die na verloop van tijd toch terug wat sterker wordt. Ik heb niet al te veel pijn, maar voel wel snel als iets niet goed is. Opzich niet slecht, maar ik wil ook wel gewoon eens kunnen meehelpen en meewerken zonder dat die rug lastig doet. We zullen zien!
Ondertussen heb ik ook van Bien toestemming gekregen om haar prachtige schriften over het Wondelbos hier te delen, ik deel een fragment dat mij roerde.
"Een veldje met uitdovende zomerbloemen, een moerassig stukje land. Goud. Goud. Het veldje en mij omringend: Esdoorns. Groot en torenend, alwetend. Wilgen, bos en schiet en treur, die wiegden in de zachte wind. Sommigen sterk en doorleefd, anderen nog maar net omhooggeschoten maar toch al zoveel wijzer dan ik.
Ik herinner
Ik herinner me hoe ik tussen de Japanse Duizendknoop (die ondeugende doorzetter!!) wandelde ik haar daar zag. Een kloeke moeder. Grootvader van al wat leeft. Een Eik die daar zomaar stond. Hij maakte geen Eikels wat ik gek vond, want de andere Eiken doen dat wel dit jaar. Maar misschien wist deze Eik al wat er zou komen. Misschien had zij de toekomst gevoeld in haar mycelium-gebonden wortels, in their worldly, buried lungs.
Maybe this Oaktree knew that their everlasting cyclic time would soon be brutally destroyed by powers beyond her.
I remember looking for other Oaks. En ja hoor, een beetje verder stonden nog twee grote exemplaren. Ik vroeg de Mensen of deze drie de enige Eiken waren en zij beaamden dat. Maar Leven meet je niet volgens tijd. Tussen verschillende Grassen en ander Wild, stonden op sommigen plekken kleine stekken Eikjes, nog maar net verbonden met de Aarde.
Ik herinner"
Langzaam aan haal ik de achterstand in hé, nu nog maar een week.
Liefs
PS: blog van Tim [hier](https://timscyclethoughts.blogspot.com)! :))
-

@ dc4cd086:cee77c06
2024-10-18 17:41:42
Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
## Key Features:
### Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
### Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
### Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
## Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine.
Will support multiple open and closed language models for user choice
Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
## Screenshots
### Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
### Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
## Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
## Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle
https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-

@ 8947a945:9bfcf626
2024-10-17 08:06:55
[](https://stock.adobe.com/stock-photo/id/1010191703)
**สวัสดีทุกคนบน Nostr ครับ** รวมไปถึง **watchers**และ **ผู้ติดตาม**ของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
**เมื่อวันที่ 16 กย.2024** มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ

### นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint **0.15 - 0.2 ETH** … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

- Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
1. ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
2. ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
3. ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
4. ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT **0.2 ETH**
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
**Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก** เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea
แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง
ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ
ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ
เขา : 2ETH นี่มัน 5000$ เลยนะ
ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้
เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู
ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย
เขา : จะเอา address เขาไปทำไม
ผม : ตัดจบ รำคาญ ไม่ขายให้ละ
เขา : 2ETH = 5000 USD เลยนะ
ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
-----------
### ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
[](https://stock.adobe.com/stock-photo/id/1010196295)
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH **"code is law"** smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
## Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ
- Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon)
- [HikariHarmony on Nostr](https://shorturl.at/I8Nu4)
- General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen)
- KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-

@ 8947a945:9bfcf626
2024-10-17 07:33:00
[](https://stock.adobe.com/stock-photo/id/1010191703)
**Hello everyone on Nostr** and all my **watchers**and **followers**from DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
**On September 16**, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.

### Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece.
They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later.
The minting gas fees were quite expensive, ranging from **0.15 to 0.2 ETH**

- The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose.
Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
1. I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
2. I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
3. I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
4. I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of **0.2 ETH**. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
**This raised a red flag**, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms
If you find yourself in a similar situation, be aware that scammers may be targeting you.
-----------
### My Perspective why I Believe This is a Scam and What the Scammers Gain
[](https://stock.adobe.com/stock-photo/id/1010196295)
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time
Take care
## Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery
- Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon)
- [HikariHarmony on Nostr](https://shorturl.at/I8Nu4)
- General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen)
-

@ 0e501ec7:de5ef3a4
2024-10-14 21:36:26
blog van Tim: <https://timscyclethoughts.blogspot.com>
We zijn nu al bijna een week in het Abtshof! Wat een drukke week is het geweest. Je denkt dan, we zijn op reis, we zijn op vakantie, op het gemak. Helemaal niet waar! We hebben heel veel mee gewerkt aan het project. Vorige keer las je al dat we de namiddag dat we toekwamen hier al bij het verwijderen van plaaster hadden gehad geholpen.
Dat hebben we de dag erna ook gedaan, in de ochtend. Ging allemaal goed, tot ik op een bepaald moment op een bepaald moment een stukje plaatster in mijn oog kreeg, dat pikte enorm! Ik kreeg het er ook niet uit, en toen na wat gegoogle, besloot ik om het zo grondig mogelijk uit te spoelen. Een half uur heb ik toen mijn oog onder de kraan gehouden, ik ben nu officieel expert in het oog uitspoelen met water. Het was er toen wel uit en deed geen zeer meer. Maar ik had toch geen zin meer om plaaster uit te breken. Daarom ben ik Jakob gaan helpen met de afwerking van de unit waar Ivan naartoe ging verhuizen. In de namiddag hebben we pieter zijn parket geschaafd: die had een koopje gedaan op het internet, maar het was nogal donker behandeld. We hebben er dus het bovenste laagje van gehaalt, met een groot schaafmachien. Een heel gemakkelijk en handig apparaat, maar wel een beetje eng. Heel goed oppassen wanneer je het hout erin steekt!
Er is hier ook een andere wwoof'er, die Teo noemt. Hij komt uit Canada, en maakt een grote reis van België tot naar Spanje, een beetje gelijk ons, maar dan zonder fiets! Echt een leuke jongen, mijn Frans is eventjes niet top genoeg om echt te kunnen babbelen, maar we hebben wel veel fun samen, zeker de laatste dagen. Tim en hij kunnen helemaal opgaan in hun muziek en filmbesprekingen, en morgen doen we zelfs een filmavondje om hem een goeie Belgische film te tonen.
Vrijdag heb ik weer bij de afwerking van Ivan's unit geholpen. ik heb de rand van een velux helpen isoleren, en plinten opgemeten en gezaagd. Dat was zo moeilijk, om juist te meten en te zagen! Uiteindelijk had ik er maar 2 van de 8 juist, de anderen waren allemaal 3 mm te lang :( dju toch, volgende keer beter! Gelukkig konden ze makkelijk bijgewerkt worden. Tim en Teo waren ondertussen nog aan het uitbreken, ook leuk, maar ik was blij dat ik daar even aan kon ontlopen.
Daarna kregen we onze eerste les van de gloednieuw geimproviseerde houtbewerkingsxursus, gegeven door de meestermeubelmaker-schrijnwerker Jakob! Hij legde ons uit hoe we hout verbindingen kunnen maken, toonde er een heleboel en ging meer in detail bij een redelijk simpele: de half-hout verbinding. Hij legde uit hoe we een beitel moeten hanteren en hoe we zeer recht kunnen zagen (belangrijk als je een verbinding maakt!). Na de uitleg gingen we direct aan de slag: we zouden een rek gaan bouwen voor in de voorraadkamer. Er staan langs 2 muren al rekken, en ons rek zou de stijl van de anderen een beetje volgen de de derde muur helemaal bedekken. Nog niet zo gemakkelijk: de muur en de vloer zijn er nogal ruw en hobbelig, hoe begin je daar te meten? In het rek kunnen we elk 10 keer een halfhout verbinding maken, goeie oefening!
Je merkt dat ik vooral heel veel vertel over wat we allemaal gedaan hebben. Niet zo heel veel mijmeringen en emotie. Dat is eigenlijk ook logisch, we zijn vooral heel de tijd bezig. En als je bezig bent mijmer je niet en worden je emoties ook niet zo groot. Ik vind het fantastisch om bezig te zijn. Ik miste dat ook echt de laatste maand, maar nu mis ik ook wel weer het mijmeren. Denk ik? Alleszins, ik wou dat ik ook andere dingen had om op te schrijven.
Ik ben wel ook veel bezig geweest met het Bos, het Wondelbos, O Wondelbos, en hoe om te gaan met het verdriet en de boosheid die geboren wordt uit het verlies, hoe te rouwen. Dat is niet zo gemakkelijk. Ik denk dat het belangrijkste is dat ik graag die gevoelens wil eren. Het Bos eren, ook al is die er niet meer. Bien schreef erover, en ik vond het zo mooi, dat ik het heel graag hier zou quoteren. Maar ik weet niet of dat oké is, dus zal het voor later houden.
Vetrouw je lichaam, vertrouw je gevoel, ik probeer het zo te zeggen tegen mezelf. Ik vertrouw mijn lichaam. Ik denk dat we veel kunnen vinden in onszelf, als we maar het lef hebben om te luistern. Nu en simpel: ik voel me uitgeput, ik vertrouw erop dat het een goede keuze is om nu te gaan slapen.
De dagen na vrijdag zal ik later wel vertellen, of niet. Liefs!
-

@ 84b0c46a:417782f5
2024-10-12 05:51:51
- 1:nan:
- **2**
- 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p)
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2|
|:--|:--|
|test| :nan: |
---
### :nan: **:nan:**
1. 1
2. 2
- tet
- tes
3. 3
1. 1
2. 2
> t
>> te
>>> test
- 19^th^
- H~2~O
<marquee>(☝ ՞ਊ ՞)☝ウェーイ<marquee><SCRIPT>alert("( 厂˙ω˙ )厂うぇ乁( ˙ω˙ )厂ーい乁( ˙ω˙ 乁)")</SCRIPT>
<img src="xx" onerror="alert('(☝ ՞ਊ ՞)☝ウェーイ')">
<marquee onstart="document.querySelector('body').innerHTML = `<main><p>全裸デブ</p></main>`">本サイトはfirefoxのみサポートしています</marquee>
<marquee><font size=1000>うにょ</font></marquee>
<marquee scrollamount=50>:wayo:</marquee>
<marquee behavior="alternate">This text will bounce</marquee>
-

@ 0e501ec7:de5ef3a4
2024-10-09 21:38:52
PS: lees zeker eens de blog van Tim: <https://timscyclethoughts.blogspot.com/2024/09/> :))
Vandaag was onze eerste dag in het Abtshof. (Ik weet het, gisteren is overgeslagen, oeps, en ik heb nog niet uitgevonden hoe ik hier meer foto's op kan zetten, nogmaals oeps.)
Het Absthof is een coöperatieve co-housing, met een grote moestuin en een houtatelier. Het is gelegen in Borlo, een klein dorpje in de buurt van Landen. Het thuis van de wooncoöperatie is een grote vierkantshoeve, die langzaamaan helemaal gerestaureerd geraakt op (redelijk) duurzame wijze. Een heel mooie plek, waar ik al een paar keer te gast ben geweest. Hier krijgen we kost en inwoon in ruil voor mee te helpen met vanalles. Wij zijn blij om hier te zijn en ervaring op te doen, en blij dat we wat kunnen bijdragen aan duurzame/alternatieve projecten zoals deze. Ook nog belangrijk: bij een coöperatie horen ook veel beslissingen, die gedragen moeten zijn. Hier werken ze met het kader van de sociocratie. Zeer interessant, ik zal er later nog over uitweiden.
Dus: we hadden op ons gemakje een lange ochtend gehad, met een lekker ontbijtje, een goede opruimbeurt, de plantjes in de serre water geven, en een random astrix en obelix strip. Het ging over de picten, ofzoiets, en iemand die de macht wou grijoen door met de romeinen samen te werken. Bon, daarvoor zijn we hier niet. Ik zou eigenlijk in bed moeten nu, de dagen zijn lang en mijn slaap dierbaar. Toch wil ik eerst nog wat schrijven. Toch toch tocht
door de bomen, wilgen, essen, rode beuk
Net toen we buitenstapten om te vertrekken deze ochtend, begon het te regenen! Test regenkleren: gefaald. Regenbroek is zo lek alsof hij eigenlijk niet bestaat. Maakt niet uit, ik ben niet van suiker. ; ) We zullen wel nog eens kijken voor van dat eng waterdichtmaakspul, of ik gebruik hem als windstopper, ook goed. Hier aangekomen werden we meteen ontvangen door Jakob met een warm middagmaal. Heerlijke stampot, op smaak gebracht met varkenspoot. Heftig idee, maar ik en Tim konden er wel mee overweg, en waren eigenlijk wel nieuwsgierig hoe dat smaakte zo een varkenspoot. Blijkt: nogal taai, maar wel nog een goede ervaring. Would recommend.
Daarna gingen we ons installeren, en we hadden geluk! We mochten slapen in een grote tent die nog op het veld stond. Daarin zijn zelfs bedjes, en hij lijkt (redelijk) waterdicht, al had ik toch niet direct al mijn spullen moeten uitspreiden. Ons kleine tentje zou het niet gehouden hebben om de hele week in de regen opgestaan te hebben vrees ik.
Daarna bereikte mij het nieuws. Van de uitzetting in het Wondelbos. Ik was er zwaar van aangedaan, boos en verdrietig, gespannen. Machteloos. Machteloos. Ik heb toen geprobeerd mijn gevoel neer te schrijven, en heb de grote uitdaging overwonnen om dat kwetsbare tekstje te delen. (Op Facebook.) Ik was wel trots op mijn kleine overwinning, maar dat viel nogal in het grote niet bij mijn eerdere gevoel bij de grote machtsvertoning van de politie, en de start van het illegaal lijkende kap. Ik kan niet geloven dat ze een kapvergunning binnen hebben, terwijl de rechtspraak rond hun bouwvergunning nog niet rond is. Maar ja, wat weet ik ervan.
Mijn gevoel kon ik dan een beetje van me afzetten door wat te helpen bij in de verbouwing van een nieuwe woning in de co-house: plaksel van de muur halen met een drilboor, puin naar buiten krijgen, spijkers uit de muur halen. Geleerd: oude spijkers moeten uit de muur voor je opnieuw plakt, anders krijg je roestvlekken. Ook geleerd: als je glas in een raam plaatst, mag je dat niet direct op het kader laten steunen, je moet er houtjes tussensteken (voor speling voor isolatie denk ik?). Morgen doen we daarmee verder én gaan we parket schaven. Ik heb echt wel zin om met het schaafmachien te leren werken!
Daarna was het eten met alle bewoners, aan een grote lange tafel in de gemeenschappelijke zaal. Was vree gezellig, al was mijn sociale energie naar het einde een beetje op. Er was een 'mededelingrondje', om iedereen op de hoogte te brengen van belangrijk nieuws. Later op de avond hadden de bewoners ook nog een 'deel-cirkel'. Dat doen ze blijkbaar een keer in de maand, om eens samen te zitten en over zaken te kunnen praten op een meer diepgaande manier, en zonder de stress van beslissingen die gemaakt moeten worden, zoals in vergaderingen. Klinkt wel goed, al zou ik zelf niet direct weten of ik veel intieme zaken kan delen voor een groep. Ik zou in de eerste plaats stress krijgen. Maar misschien werkt het wel!
Nu, naar bed, morgen weer een volle dag!
-

@ 0e501ec7:de5ef3a4
2024-10-09 21:37:38
Ik rouw. Ik rouw om het bos, in mij groeit een grote krop van verdriet. O Wondelbos, ik zag je graag, je ontving me zo hartelijk, en ik zag hoe je de thuis was van zoveel leven, zoveel leven.
Ik rouw om het vertrouwen in de rechtbank om rechtvaardig te zijn. Hoe vaak nog meneer de rechter, zal je als speelbal van machtige instituten gebruikt worden om kleine mensen, die mooie dingen proberen te doen, te intimideren? Hoe vaak nog zal jij, zonder kans voor de andere zijde om gehoord te worden, de politiemacht oproepen? Hoe vaak nog zal een vredezame actie met groot machtsvertoon beëindigd worden? Hoevaak nog zal illegale kap straffeloos blijven terwijl beschermers vervolgd en opgepakt worden? Hoevaak nog? Alle rede, alle gevoel zegt, dit bos moet behouden blijven. O bos, ik zal je missen. O Wondelbos, ik ben blij dat jij bij ons was.
Nu komt voor jou een tijd van beton. Maar ik ben zeker dat er daaronder een kiertje openblijft, een zaadje zal liggen te wachten. Ik ben zeker dat het Imperium van beton ooit gedaan zal zijn, en dan zal Jij terug kunnen bloeien, terug kunnen groeien, thuis geven aan al die soorten, al die wezens, al dat leven. Dan zal Jij terug thuis kunnen komen, net als Wij.
Liefs,
Je liefste Aardbewoner
-

@ 4ba8e86d:89d32de4
2024-10-09 13:13:10
Recentemente, perdi minha lista de RSS, Decidi criar este texto sobre RSS pode ajudar a escapar das armadilhas do algoritmo das redes sociais.
Além disso, para facilitar a vida daqueles que também desejam adotar o RSS como uma ferramenta de leitura, fiz um fork da lista de RSS do SethForPrivacy. Você pode acessar a lista no seguinte link: https://gist.github.com/Alexemidio/2699dd82077d483849b576a908b0c444
Aproveite a lista de RSS para personalizar seu fluxo de conteúdo e desfrutar de uma experiência de leitura mais controlada e direcionada.
Utilizar um leitor de RSS bem organizado é uma estratégia eficaz para se libertar da rolagem incessante nas redes sociais e recuperar o controle sobre o conteúdo que você consome. Isso possibilita direcionar sua atenção para o conteúdo genuinamente relevante.
Você já notou que os feeds das redes sociais frequentemente são inundados com notícias que provocam emoções negativas? Esse fenômeno, chamado de "doomscrolling", persiste, e as redes sociais parecem acentuar ainda mais a sua presença. A conhecida "bolha" das redes sociais nos mantém imersos, mostrando principalmente os posts com os quais interagimos. Isso tem provocado várias consequências prejudiciais, incluindo a disseminação de notícias falsas, desinformação e o agravamento de problemas como ansiedade e depressão entre os usuários.
Mas, e se lhe disséssemos que existe uma alternativa? Uma maneira de receber informações diretamente, sem filtros ou algoritmos? É disso que vamos falar hoje: o RSS.
O Que é o RSS?
RSS é a abreviação de "Really Simple Syndication", que pode ser traduzida como "Sincronização Realmente Simples". Trata-se de um arquivo XML gerado por inúmeros sites para exibir as postagens que o site publica. Dessa forma, os leitores de RSS permitem às pessoas acompanhar diversos blogs, sites de notícias e muito mais, tudo a partir de um único local.
Quem Criou o RSS?
Uma das pessoas envolvidas na criação do RSS foi Aaron Swartz, um hacker notório por seu papel na fundação do Creative Commons e por ser um dos cofundadores da rede social Reddit.
Se desejar se aprofundar na história de Aaron, recomendamos o documentário "O Menino da Internet: A História de Aaron Swartz" dublado em português completo. https://youtu.be/qm4NRSa9T2Q?si=GXyPXVOMJX20pIo_
Para quem gosta de RSS como eu, você não precisa usar NOSTR para acompanhar meu conteúdo. Basta me adicionar ao seu RSS.
Meu RSS Nostr: nostr:npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr
Utilizar um leitor de RSS bem organizado é uma maneira eficaz de se libertar da rolagem incessante e recuperar o controle sobre o conteúdo que você consome, direcionando sua atenção para o que realmente importa.
Para pessoas interessantes como o nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 você não precisa segui-lo no Nostr, basta adicionar ao seu RSS.
nostr:naddr1qqxnzdesx5ur2vekxucrqde5qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqa282ctyhs
Leitores de RSS Recomendados:
Feeder (Mobile): O Feeder é um aplicativo de leitor de RSS de código aberto que permite que você acompanhe e leia suas fontes de notícias favoritas em um só lugar. Com recursos avançados e uma interface intuitiva.
Liferea (Desktop): Liferea é a abreviação de Linux Feed Reader, um programa agregador para leitura de notícias online. Ele suporta os principais tipos de arquivo criados para esse fim: RSS/RDF e Atom. Também pode importar e exportar no formato OPML.
-

@ 0e501ec7:de5ef3a4
2024-10-08 20:06:29
Aan het einde van een dag vol buiten zijn en fietsen en organiseren (spullen inpakken, uitpakken, drogen, eten verzamelen (letterlijk hihi), eten klaarmaken, afwas...) ben ik echt niet meer in staat om veel te schrijven. Hier komt dus een korte samenvatting van de laatste twee dagen, filosofische bedenkselen zijn voor een andere keer.
Gisteren vertrokken we bij Yannick pas tegen de middag. Hoe kwam dat? Ik heb tot 9u (!) geslapen, wat wel nodig was want ik was echt volkomen uitgeput van de dag ervoor. (Veel prikkels joh, en fysieke uitdaging om 60 km te fietsen met een zwaarbeladen fiets.) (Ik weet het, klinkt niet als zoo veel maar mijn fysieke toestand was de laatste tijd niet zo heel formidabel, veel ziek en moe geweest.) Na het ontbijt heeft Tim met mijn bedenkelijke hulp mijn cassette (de tandwielen van achter) en mijn ketting vervangen. Dat ging best wel vlot, enkel het afstellen van de versnelling was niet zo gemakkelijk. We moesten een evenwicht vinden waarbij alle 9 schakels vlot gingen, aan de ene kant moesten we telkens aanspannen, terwijl we aan de andere kant telkens weer losten. Ik wou het al opgeven, toen we het net hadden gevonden.
Na al dit geploeter begonnen we aan onze fietstocht door het mooie (en drukke) Brussel. Ik heb er zeer van genoten om door de stad te rijden op een kleine steek, een beetje foto's te maken en tussen de mensen te laveren. In Molenbeek kochten we in een lokale kruidenier wat droogvoer, en nog een brood, en toen trokken we verder: richting Meerdaalwoud! Eerst passeerden we nog het zoniën. Prachtig! Ik kon me niet inhouden om (bijna) alle paddestoelen te beginnen fotograferen en aan Het Algoritme van ObsIdentify te vragen hoe ze heten. Gelukkig vond Tim het wel sympathiek en stelde ik zijn geduld niet te veel op de proef. Ondertussen discussieerden we een beetje over de betrouwbaarheid van de media, het gewoonlijke, je weet wel.
Gedurende de namiddag voelden we de bui al hangen, en ja hoor, tegen dat we aan de rand van het mooie Meerdaalwoud aankwamen, begon het zachtjes te druppen. In de gietende regen aten we rechtstaand ons stoofpotje op. Wat een vibe! Gelukkig was het niet koud, en konden we genieten van onze ultieme herfstsfeer. In de schemering, in de regen, klaar om in de tent te kruipen. Heerlijk!
PS: Het lukt dus niet om de foto's op te laden, jammer! Ze zijn wel mooi hoor, ik verzeker het je!
PPS: Ik vind het nu een beetje cringe om zo al onze gebeurtenissen te beschrijven, interesseert iemand dat eigenlijk? Interesseert het mij wel? Ik denk/voel erover na!
-

@ 0e501ec7:de5ef3a4
2024-10-08 19:26:36
Wat een vermoeiende dag! Eerst alle spanning van vertrekken, snel nog van telefoon wisselen, afscheid, veel afscheid, traantjes, nog mijn breispullen gaan halen die ik bij roos was vergeten, en dan pas eindelijk vertrekken! Fietsen fietsen fietsen! Op dit moment ben ik zeer moe, dat merk je misschien aan deze vluchtige schrijfstijl, mijn ogen vallen toe, maar dat was ik eigenlijk vanochtend al: gisterenavond waren er twee megaleuke feestjes! Eerst het verjaardagsfeestje van roos, zo vol met warme lieve mensen, en dan nog ook het verjaardagsfeestje van mijn mama! ook vol lieve mensen.
Toen fietsen fietsen fietsen!
Ik reed eerst alleen, langs de mooie lange schelde, tussen de wilgen, het riet, de velden... Ik was verwonderd iver de schoonheid van de paarden die langs het jaagpad stonden, ik was verwonderd over een kind dat vrolijk door een veld liep, wat een beeld zobder weerga, een soort van plattelandse veiligheid/vrijheid die we biet vaak meer tegenkomen. Toen werd ik opgehouden door allerlei werken, ik probeerde een omleiding te volgen (waarbij ik een sappige grote kastanjeoogst scoorde bij een prachtig paar bomen!) maar kwam weer midden in de jaagpadwerken uit en had toen een groot avontuur voor de boeg, hoeveel keer ik met die zwaarbeladen fiets de dijk op en af moest aj aj. Daarbij had ik ook nog een stevige tegenwind, waardoor ik pas na 14u aankwam bij mijn lieve oma en opa. Tim was daar al, en had al goed gesocialiseerd! We babbelden met ons vieren over vanalles, er kwamen allerlei oude verhalen bovendrijven bij oma en opa, ze waren precies zeer verheugd om tegen een nog niet bekende, jonge avonturier zoals Tim al hun verhalen uit de doeken te doen :)). Na ons buikje meer dan rond gegeten te hebben, trokken we weer op pad, deze keer met de knooppuntenroute die Tim had uitgestippeld. Bezienswaardigheden: de eiffeltoren van Asse, een paard om een heuvelkam, een steile bergaf die plots een grindweg werd, een boze tegenligger, veel politieke (rechtse) posters. En heuvels, en veel zondagsmensen. Tegen 6 uur kwamen we dan toe in Zellik, bij Yannick, een vriend van Tim. Die ontving ons hartelijk, met een mooie radiostem (hij studeert dat!). Na het eten speelde we nog een spelletje Boonanza, zeer leuk.
Ik merk wel dat ik echt heel veel zin heb om de blog te onderhouden, het is echt zo een projectje waarmee ik iets kan brengen naar de mensen waarvan ik hou, verhalen, ideeën, foto's. Ik hoop wel dat het een beetje overkomt, ik ben nogal onzeker over het rare vreemde platformpje dat niemand kent (maar ik ben gewoon onzeker en kwetsbaar tsjah) (wat het is kan je lezen in 'een eerste poging'). Als je het leest, laat me weten wat je ervan vindt! Als mensen het leuk vinden gaat mijn motivatie om er meer op te plaatsen misschien wel overleven :).
Tijdens het fietsen moest ik regelmatig denken aan The Cyborg Manifesto van Donna Haraway. Zelf heb ik dat boekje eigenlijk nog niet gelezen, maar het idee van de cyborg, het uitgebreide lichaam/zelf met technologie zet me wel aan het denken. Ik op de fiets met al mijn warme (regen)kleren in de fietszak ben precies een soort reuze huisjesslak aan topsnelheid. We razen door het landschap, ervaren het, de wind, de zon en regen, interageren met de menselijke en botanische bewoners ervan... En aan het einde van de dag zetten we onze tent op, ons verplaatsbare huisje. Wat als nu eens stopten met de wereld, ecosystemen en natuur, ons lichaam te beschouwen als machines, als radartjes, waarin problemen kunnen opgelost worden met quick files zoals een pilletje of de inrichting van reservaten (zoals we gewoon zijn bij de machines: een beetje smeren, een tandwiel vervangen, de nieuwe update installeren). Wat als we nu eens de machines als deel van ons lichaam zagen? Een lichaam om gehecht aan te zijn, om zorg voor te dragen? Om mee in wederkerige interactie met de wezens rond ons te gaan?
Bon, ik moet er nog eens over nadenken, en dat boek lezen, misschien heb ik daar ooit wel eens tijd voor. Na een lange fietsdag ben ik er allisinds te moe voor!
-

@ e6817453:b0ac3c39
2024-10-06 11:21:27
Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias.
<iframe width="560" height="315" src="https://www.youtube.com/embed/fehgwnSUcqQ?si=nPK7UOFr19BT5ifm" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
### 1. Privacy and Ownership: Foundations of Personal AI
At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations.
In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI.
### 2. Bias and Fairness: The Ethical Dilemma of LLMs
Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values.
This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks.
Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge.
### 3. Explainability: The Need for Transparency
One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions.
Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm.
This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks.
### Addressing the Ethical Landscape of Personal AI
As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development.
Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources.
There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom.
The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development.
### Conclusion
In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values.
If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
-

@ 0e501ec7:de5ef3a4
2024-10-05 10:41:58
De kamer is stil, maar weinig verlicht met een grijs en duister schemerlicht. Ze zitten rond een vreemdsoortige tafel, aan het verste uiteinde ervan staat een beeld. Het beeld is niet goed zichtbaar, maar de vormen ervan geven je een krop in je keel, je maag keert om. Dit zijn de machtigste mannen op aarde. Mannen ja, geen seksistische veralgemening hier, het zijn effectief alleen mannen in deze ruimte. Voor zover het te ontwaren is in het duistere licht, zijn ze gezond, fit, alsof ze dagelijks naar de yogales en de basicfit gaan. Ze zijn serieus, ze lachen niet, er is werk te doen. Ze kennen elkaar, ook al praten ze amper. Ze praten over het weer.
Je weet dat dit geen leuke plek is. Je weet dat een lach je hier duur te staan kan komen. Hoe ben je hier terecht gekomen?
De Mannen zitten in hun glanzende stoelen van Fenolformaldehyde en Perfluoroctaanzuur, en de stilte wordt nog zwaarder. Je hebt het koud, er steekt een ijzige wind op in de kamer, een ijskoude luchtstroom.
\------------------------------------------------------------------------
Duizenden jaren hebben de kou en het ijs het mythische Antarctica vormgegeven. Dit deel van onze geliefde Biosfeer, van Patchamama, heeft nooit veel mensen gekend, de Pinguïns, de Walrussen en de Zeehonden leefden hun levens los van ons, soms vreedzaam, soms lang, soms kort en gruwelijk. Maar ze kenden hun land en ze kenden elkaar, ze wisten dat na het licht de duisternis kwam, dat de duisternis kou met zich meebracht, die soms dodelijk was, maar altijd weer plaats maakte voor een minder frisse tijd waarin ze makkelijker konden gaan jagen op de Vissen, die ze ook zeer goed kenden. Toen de eerste Mensen kwamen waren ze woordeloos. Dit waren nooit mensen van veel gebabbel geweest, anders waren ze niet tot hier geraakt, maar de aanblik van de prachtige witte glooiingen van Antarctica, de aanblik van kou en schoonheid, ongrijpbaar en gevaarlijk, maar toch zo verleidelijk, ontnam ze van alle woorden. Vol ontzag, getransformeerd keerden ze terug naar huis, al gebeurde dat niet altijd. Antarctica werd een belangrijk personage in vele heldenverhalen, in gedichten, schilderijen. Het duurde niet lang of alle Mensen hadden ervan gehoord, en velen waren in de ban van deze voor hun desolate plek.
Vol leven was Antarctica, een onmisbaar orgaan in het lichaam van onze Aarde. Ze reguleerde de oceaanstromen, waaronder de golfstroom, en zorgde voor een constantere verdeling van warmte en koude. Dankzij Antarctica waren veel van de plekken die wij Thuis noemden zoals ze waren. Alle organen van onze Aarde zorgden er samen voor dat het regende wanneer het moest regenen, dat de zon scheen wanneer we er zo op wachtten, dat het ene jaar een beetje op het andere leek en we ons Thuis voelden. Thuis in de Biosfeer.
\------------------------------------------------------------------------
Vandaag is er iets te vieren onder deze Mannen. Ze zijn erin geslaagd om een groot offer te brengen. Van een omvang die gewone mensen, zoals jij en ik niet kunnen omvatten.
Hun God is bloedig, van een zwart soort bloed, met een hoge energetische waarde. Een te hoge energetische waarde zou je kunnen zeggen, zo hoog, dat dit bloed al snel verslavend werkt, in een trance brengt. Een trance van productiviteit, efficiëntie, destructie. Een trance van macht en geld, en 'vrije' markt. Maar de 'vrije markt' is al ter dood gebracht. Geofferd, in een vorig decennium. Het zwarte bloed vroeg meer machtsconcentratie om te blijven stromen. Deze Godheid vroeg meer toewijding, meer opoffering, meer zweet en fragiele lonen. Meer pesticiden, meer deregulatie, meer privatisering, meer staatsteun voor multinational, meer belastingverlaging. Ten dienste van de 'vrije' markt. Ten dienste van de monopolie. Dit is een God van de marktdominantie, een God van de monopolies.
Jij moet dan misschien aan dat gezelschapsspel denken, dat je in een vorig leven met je familie speelde. Soms was dat nog leuk, maar even vaak eindigde het in ruzie, dat weet je nog goed. Je weet evengoed dat dít spel niet meer leuk is, al lang niet meer. Het zwarte bloed ontregelde de organen van de Aarde, opdat er nog meer zwart bloed zou moge vloeien.
De Mannen vieren in stilte. Het ijs van Antarctica is gesmolten, het offer is compleet. Hun leger aan loonarbeiders (meer zweet en fragiele lonen, zo had de God geboden) zijn begonnen aan de eerste boortorens, boorplatformen en pijpleidingen. Ze weten dat hun God blij zal zijn met dit offer, hij heeft er al zolang om gevraagd. Het duurde bijna te lang, de vrees begon te groeien. Deze Mannen zijn dan machtig, angst is hun niet onbekend. Angst is hun beste vriend, al is het geen zorgzame vriendschap. Eerder een verstikkende, voortduwende, trekkende vriendschap. Ze zijn bang dat ze niet genoeg kunnen geven. Als ze niet hard genoeg werken en de offers krimpen zal hun rijk instorten. Zullen zij instorten. Onder de zware zwarte Wraak van hun Godheid.
De God heeft beloofd dat Hij hun leugens voor iedereen zal uitspreiden als ze zijn offers niet kunnen brengen. Hij heeft gezworen hun Imperium te laten brokkelen wanneer zij niet hard genoeg werken en de vernietiging Hem niet tevreden stelt. Ze zijn bang. De ijzige wind kietelt in hun nek. Maar ze vieren, ze hebben iets te vieren.
-

@ 0e501ec7:de5ef3a4
2024-10-04 16:53:22
We zijn nu 2 dagen voor het gepland vertrek, 4/10/2024. Ik ben zeer blij dat ik een fietsmaatje heb, genaamd Tim, die een datum heeft vastgelegd om te vertrekken. Als ik dat niet had gehad, dan was ik het vertrek waarschijnlijk nog een hele poos blijven uitstellen, of zelfs nooit vertrokken geraakt! Nu heb ik deze week wel met wat stress rondgelopen, je weet wel hoe stressgevoelig ik ben en je klaarmaken voor een grote reis is toch wel een beetje spannend.
Onze reis heeft geen strak plan. Als mensen ernaar vragen zeg ik altijd: we vertrekken richting het zuiden. Dan vragen ze nog: 'hoelang blijf je weg' en dan moet ik bekennen dat ik het niet weet. Veel mensen reageren een beetje onbegrijpend, maar een paar snappen het meteen en zijn laaiend enthousiast. En ik moet bekennen, dat ben ik zelf ook wel! Het is dus voor het grootste deel positieve spanning. Natuurlijk ook een beetje koudwatervrees, letterlijk dan, want ik heb zo een voorgevoel dat het veél gaat regenen!
Ons plannetje is om naast fietsen ook te stoppen op interessante plekken, zoals transitie-projecten of alternatieve gemeenschappen. Daar willen we graag meewerken en helpen waar we kunnen, maar ook mensen leren kennen en veel bijleren! Ik wil bijvoorbeeld heel graag houtbewerking leren, en Tim wilt graag over moestuinen en andere landbouwtechnieken leren (denk ik). En dat komt goed uit: veel projecten hebben een houtatelier en een grote moestuin. Al moeten we dat natuurlijk zien hé. Het eerste project zal het Absthof worden, in Borlo.
Zondag vertrekken we dus in die richting. We passeren mijn grootouders in Aalst, slapen dan waarschijnlijk bij een vriend van Tim in Zellik, en gaan dan via het Meerdaalwoud naar Landen/Borlo.
Ik ben zeer benieuwd hoe het fietsen mij gaat bevallen. Ik ben de laatste tijd nogal moe geweest, moe en ziek. Van één nachtje te weinig slaap voelde ik mij telkens weer verkouden. Ik denk echter dat het vooral het teveel aan stress en te weinig mentale rust is van het laatste jaar dat daar aan de oorzaak van ligt. Ik verwacht dus dat de fietsreis mij goed gaat doen, om mijn lichaam terug te herstellen en een routine op te bouwen met minder stress. Maaar: toch spannend! In het begin zou ik wel eens te moe kunnen zijn om ver te fietsen. Hopelijk lukt het mij om op tijd te zeggen Jow ik ben echt moe we zullen vandaag toch wat minder moeten fietsen. Dat zal wel echt belangrijk zijn, want als ik mij in het begin overdoe ga ik het misschien niet lang volhouden. Komt wel goed!
De voorbereidingen van deze week waren: de fiets kuisen, versnellingen afstellen, slag uit de wielen halen (merci Tim!!!), een stuurpenverlenger installeren zodat ik minder voorovergebogen zit, regenkleren opnieuw behandelen zodat ze waterdicht zijn, en een tripje naar de Decathlon, voor waterdichte overschoenen, een achterlicht en wat waterdichte zakken. Daarnaast ben ik ook nog vandaag naar de gemeente geweest om een volmacht te regelen, voor de verkiezingen volgende week!
-

@ 0e501ec7:de5ef3a4
2024-10-04 10:54:18
Have you watched the pigeons?
have you watched the crow?
Heb je het beemdooievaarsbekje ooit al eens goed bekeken?
Heb je al eens gevraagd aan de boomkikker hoe die naar het leven kijkt?
Wat hen denkt van jouw prachtig onderhouden voortuingazon?
Every species is a soul, a fire, a story, a story that is told and retold and retold
Every species is a song
A song of love, of life of neverending trial and struggle
Trial and error they say, evolution they say, mutation and selection
But your demystification is not working
The species never stop telling their unholy wispering stories
They never stop
This is a song for the lost souls
This is a song of grief
This story tells the song ofthe species that don't
that cannot anymore
The species we lost
I love you herfstvuurspin Ik hou van je
ik hou van je ik
Ik mis je
Ik voel in heel mijn lijf dat je ontbreekt
en ik ben zeker dat ik niet de enige ben
-

@ 0e501ec7:de5ef3a4
2024-10-03 09:54:14
Dit is een eerste poging om een post te creëeren die op de oracolo html-blog verschijnt. Ik snap helemaal niet zo goed hoe dit allemaal werkt, maar het lijkt wel spannend. De blog werkt op basis van een htmlbestandje, dat je zou kunnen hosten via github. ofzo. Waarom zo en niet op een andere manier? Ik vind nostr wel cool, omdat het helemaal gedecentraliseerd is en zonder groot bedrijf. Het wordt gebouwd door een heleboel geëngageerde developpers, en is ook open-source. Joepie! Misschien is het gewoon eens iets anders dat ik wil uitproberen, dat kan ook. Allesinds, ik voel er (nog) niet de enorme weerstand tegen die ik wel voel bij alle meta-dingetjes zoals facebook enz. Als dit werkt gebruik ik het misschien wel als blog tijdens onze fietsreis, wie weet. Ah en nog iets, in navolging van de 100rabbits programeur die op een zeilboot woont: kleine apps die doen wat ze moeten doen om de computer minder te belasten en energie te besparen, dat is helemaal cool en duurzaam en heeft off-grid potentieel. (Maar daar heb ik dan wel weer een bedenking bij: nostr is wel wat verbonden met bitcoin, en die heeft niet zo een energie-zuinig imago.)
-

@ e6817453:b0ac3c39
2024-09-30 14:52:23
In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance.
<iframe width="560" height="315" src="https://www.youtube.com/embed/BkNqu51et9U?si=lne0jWxdrZPxSgd1" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
## The Vector Search and Metadata Challenge
In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results.
Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data.
## LibSQL and vector search metadata
LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points.
```
create table if not exists conversation (
id varchar(36) primary key not null,
startDate real,
endDate real,
summary text,
vectorSummary F32_BLOB(512)
);
```
It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage.
As you can see, you can access vector-like data and start date in the same query.
```
select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance
from conversation
where
${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''}
${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''}
${distance ? `and distance <= ${distance}` : ''}
order by distance
limit ${top};
```
**vector\_distance\_cos** calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data.
This approach could be calculation intensive and fail on large amounts of data.
Libsql offers a way more effective vector search based on FlashDiskANN vector indexed.
```
vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i
```
**vector\_top\_k** is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies.
Now we get a classical problem of integration vector search results with metadata queries.
## Post-Filtering: A Common Approach
The most widely adopted method in these pipelines is **post-filtering**. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.

Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter.
```
const sqlQuery = `
select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance
from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i
inner join conversation c on i.id = c.rowid
where
${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''}
${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''}
${distance ? `and distance <= ${distance}` : ''}
order by distance
limit ${top};
```
However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results.
One working strategy is to make the top value in vector\_top\_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows.
## Pre-Filtering: A More Complex Approach
Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning.
While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.

In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data.
## Pre-filtering with distance-based filtering
So, we are getting back to an old concept. We do prefiltering instead of using a vector index.
```
WITH FilteredDates AS (
SELECT
c.id,
c.startDate,
c.endDate,
c.summary,
c.vectorSummary
FROM
YourTable c
WHERE
${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''}
${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''}
),
DistanceCalculation AS (
SELECT
fd.id,
fd.startDate,
fd.endDate,
fd.summary,
fd.vectorSummary,
vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance
FROM
FilteredDates fd
)
SELECT
dc.id,
dc.startDate,
dc.endDate,
dc.summary,
dc.distance
FROM
DistanceCalculation dc
WHERE
1=1
${distance ? `AND dc.distance <= ${distance}` : ''}
ORDER BY
dc.distance
LIMIT ${top};
```
It makes sense if the filter produces small data and distance calculation happens on the smaller data set.
As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches.
## Choosing Between Pre and Post-Filtering
Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization.
In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further.
## **Conclusion**
Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further.
-

@ c4f5e7a7:8856cac7
2024-09-27 08:20:16
Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x).
# TL;DR
This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/).
The following concepts are explored:
1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust).
2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse.
3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
[Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
# Cognitive Dissonance
Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data).
In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
# Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k).
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
# Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g).
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons).
The remainder of this article explores how we can:
1. Verify ownership of a physical place in the real world;
2. Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation\!) states that:
> "The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
# Places and Web-of-Trust
[@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace).
2. Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
# Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with:
1. Your social graph;
2. The type or subject of the content being attested and by whom;
3. Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
[NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive.
**‘This is true’** resonates more strongly than **‘I like this.’**.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
# Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential):
> "A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
[@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that:
> "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
# Check-ins
Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\!
Check-ins could also be used as a signal for bonafide Place ownership over time.
# Summary: Trust Your Bros
So, to recap, we have:
**Places**: Digital representations of physical locations on Nostr.
**Check-ins**: Users signalling their presence at a location.
**Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left\! We have:
**Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
**Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
**Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
# Thanks
With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\!
-

@ e83b66a8:b0526c2b
2024-09-26 19:29:43
If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining.
Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully.
Solo mining pools exist, such as: https://solo.ckpool.org/
It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool.
You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power.
There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely.
A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine.
So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning.
So here’s my recommendation.
Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin.
Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join.
If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools.
Bear in mind that many of the other smaller pools are still controlled by Bitmain.
If you're still interested in lottery mining, here are your chances of winning a block:
Represented as Hash rates of different miners:
Nerdminer: 20 KH/s = 20,000 H/s
Bitaxe: 750 GH/s = 750,000,000,000 H/s
Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s
Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s
Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s
Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000
If you're running a Bitaxe, your percentage chance of winning a block is:
0.000000119426751592357%
Over a year, your chances increase to:
0.00627707006369428%
Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one):
0.000005%
Over a year, your chances increase to:
0.00026%
Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions:
https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/
https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx
https://www.youtube.com/watch?v=Wo91DWvZRs8
https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
-

@ 01d0bbf9:91130d4c
2024-09-26 17:58:10
## Chef's notes
Amazingly tangy, firey hot, but still mellow and bright.
I use this on everything– Use it to dress salads, dip (honey mustard) for fried chicken, elevate your taco nights, heck a spoonful first thing in the morning will wake you up better than coffee!
Don't forget to use up those delicious chilis and garlic, they are so good!
## Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 1-2 weeks
- 🍽️ Servings: (12x) 8oz jars
## Ingredients
- 16oz fresh chili peppers
- 8oz red onion
- 8oz garlic
- 96oz honey
- Fresh thyme
## Directions
1. Thinly slice peppers, garlic, shallots and fresh thyme
2. Add chopped ingredients to the honey
3. Leave to ferment (loosely covered) for 1-2 weeks
4. Drizzle that amazing pungent firey gold liquid over EVERYTHING. (Don't forget to use up those amazing chilis and garlic too.)
-

@ e83b66a8:b0526c2b
2024-09-21 16:29:23
Here are some of the more interesting projects that I like:
Messaging:
https://www.0xchat.com/#/ - Private messaging - think WhatsApp
Xitter Like Clients:
https://damus.io/ - iPhone client
https://nostrapps.com/amethyst - Android client
https://primal.net/downloads - Android, iPhone & Desktop
https://shipyard.pub/posts - Schedule future posts
Interesting sites:
https://zap.stream/ - Video streaming
https://fountain.fm/ - Podcasting
https://wavlake.com/ - Music streaming
https://shopstr.store/ - Online shop
https://zap.cooking/recent - Cooking recipes
https://ostrich.work/ - NOSTR jobs board
NOSTR tools
https://nostr.band/ - Powerful search tool
https://nostr.wine/ - Powerful, but centralised paid relay
https://npub.pro/ - Website creation tool
https://nostr.build/ - Media and file storage
https://relay.tools/ - Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user - Creator tools
List of NOSTR apps:
https://nostrapps.com/
-

@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53
I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous.
In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism.
On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important.
That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played.
Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end.
The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism:
I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.
In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore.
The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true.
The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good.
In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.”
I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
-

@ ee11a5df:b76c4e49
2024-09-11 08:16:37
# Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays.
Or at the very least by DVMs. I concur. In this way, once you configure what you want to see,
it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
## Strategies in Short
1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering.
3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity
6. **PROOF OF WORK**: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
## filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai
// This is a sample spam filtering script for the gossip nostr
// client. The language is called Rhai, details are at:
// https://rhai.rs/book/
//
// For gossip to find your spam filtering script, put it in
// your gossip profile directory. See
// https://docs.rs/dirs/latest/dirs/fn.data_dir.html
// to find the base directory. A subdirectory "gossip" is your
// gossip data directory which for most people is their profile
// directory too. (Note: if you use a GOSSIP_PROFILE, you'll
// need to put it one directory deeper into that profile
// directory).
//
// This filter is used to filter out and refuse to process
// incoming events as they flow in from relays, and also to
// filter which events get/ displayed in certain circumstances.
// It is only run on feed-displayable event kinds, and only by
// authors you are not following. In case of error, nothing is
// filtered.
//
// You must define a function called 'filter' which returns one
// of these constant values:
// DENY (the event is filtered out)
// ALLOW (the event is allowed through)
// MUTE (the event is filtered out, and the author is
// automatically muted)
//
// Your script will be provided the following global variables:
// 'caller' - a string that is one of "Process",
// "Thread", "Inbox" or "Global" indicating
// which part of the code is running your
// script
// 'content' - the event content as a string
// 'id' - the event ID, as a hex string
// 'kind' - the event kind as an integer
// 'muted' - if the author is in your mute list
// 'name' - if we have it, the name of the author
// (or your petname), else an empty string
// 'nip05valid' - whether nip05 is valid for the author,
// as a boolean
// 'pow' - the Proof of Work on the event
// 'pubkey' - the event author public key, as a hex
// string
// 'seconds_known' - the number of seconds that the author
// of the event has been known to gossip
// 'spamsafe' - true only if the event came in from a
// relay marked as SpamSafe during Process
// (even if the global setting for SpamSafe
// is off)
fn filter() {
// Show spam on global
// (global events are ephemeral; these won't grow the
// database)
if caller=="Global" {
return ALLOW;
}
// Block ReplyGuy
if name.contains("ReplyGuy") || name.contains("ReplyGal") {
return DENY;
}
// Block known DM spam
// (giftwraps are unwrapped before the content is passed to
// this script)
if content.to_lower().contains(
"Mr. Gift and Mrs. Wrap under the tree, KISSING!"
) {
return DENY;
}
// Reject events from new pubkeys, unless they have a high
// PoW or we somehow already have a nip05valid for them
//
// If this turns out to be a legit person, we will start
// hearing their events 2 seconds from now, so we will
// only miss their very first event.
if seconds_known <= 2 && pow < 25 && !nip05valid {
return DENY;
}
// Mute offensive people
if content.to_lower().contains(" kike") ||
content.to_lower().contains("kike ") ||
content.to_lower().contains(" nigger") ||
content.to_lower().contains("nigger ")
{
return MUTE;
}
// Reject events from muted people
//
// Gossip already does this internally, and since we are
// not Process, this is rather redundant. But this works
// as an example.
if muted {
return DENY;
}
// Accept if the PoW is large enough
if pow >= 25 {
return ALLOW;
}
// Accept if their NIP-05 is valid
if nip05valid {
return ALLOW;
}
// Accept if the event came through a spamsafe relay
if spamsafe {
return ALLOW;
}
// Reject the rest
DENY
}
```
-

@ bf95e1a4:ebdcc848
2024-09-11 06:31:05
This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good!
If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/>
# Intro
**Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us.
**Paolo:** Thank you for having us.
**Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we?
**Luke:** Sounds like that's the plan. So thank you again, both for joining us.
# Introducing Paolo and Mathias
**Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you
**Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate.
**Luke:** And, Mathias, over to you.
**Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use.
P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that.
And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here.
**Luke:** Oh, fantastic.
# Introduction to Holepunch
**Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch.
What is Holepunch and what are you doing?
**Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us.
but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy.
It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God.
that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks.
Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use,
Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it?
and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world.
And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company.
And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand.
anything, super exciting and, encourage everybody to try to check it out.
**Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product?
What is the easiest way that you would explain what it is?
# The Vision Behind Keet
**Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer
People don't care about technology. We loved it, but don't have that surface off too much to the user.
Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it.
It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard.
And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that.
# Keet vs Nostr
**Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here.
**Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform.
And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly.
You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users.
So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays.
and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology.
It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace.
Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly.
**Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that.
# Pear Runtime
**Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform,
**Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So
We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it.
And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications.
We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that.
So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve.
But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything.
So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view.
and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard.
so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example.
It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app.
So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place.
But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that.
And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone.
And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached.
Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like
**Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective.
And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that?
**Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective.
And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things.
I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point.
# Decentralization vs. Centralization
**Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor?
**Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias.
I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right?
Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions.
and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers.
That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there.
And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far.
Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features.
And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users.
And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is.
It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that.
And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key
**Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites.
But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept.
over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud.
And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers.
the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on.
is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole.
And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before.
Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize.
And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system.
And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country.
So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to.
**Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives.
So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right?
**Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all.
So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting.
yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why
# Challenges and Future of Decentralization
**Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company.
And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing.
So is there a limitation to how far this can go?
**Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world.
Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling.
So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house.
I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created.
imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you.
Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure.
So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another.
And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example.
**Knut:** Yeah.
**Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money.
And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook?
it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way.
And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it.
We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback.
# Bitcoin and Holepunch: Drawing Parallels
**Mathias:** I think, that's the main thing to think about in that. Discussion.
**Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line.
And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin?
**Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange.
For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government.
and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right?
Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them.
and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them.
**Luke:** Yeah, fantastic.
# The Future of Decentralized Communication
**Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet.
So is, that a goal? Is that on the roadmap?
**Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world.
But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind.
**Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly.
And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app.
And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly,
# Interoperability and User Experience
**Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong,
**Mathias:** Very, true.
**Luke:** you backups with the same 1224 words.
Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be
**Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it.
**Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life.
You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build.
Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible.
**Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems?
What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that?
**Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us.
The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity.
No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful.
**Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever.
but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera.
But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem.
And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it.
**Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options.
Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right?
you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion.
so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai.
So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that.
And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself.
And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center.
**Knut:** Yeah.
# The Role of Tether in the Crypto Ecosystem
**Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo?
And, what, made this thing happen? Can you give us the story here about Tether?
# Tether's Origin and Evolution
**Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014.
it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat.
That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000.
But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right?
International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin.
For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic.
# USDT's Impact on Emerging Markets
**Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries.
Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap.
So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time.
we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world.
At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right?
you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others.
And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT.
If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right?
So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U.
S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant.
# Bitcoin as a Savings Account
**Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend.
The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies.
we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining.
We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other.
I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math.
That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin.
**Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother.
**Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether.
So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right?
So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education.
**Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic.
I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke.
**Luke:** Always say the title, Knut. Always say the title.
**Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course.
**Paolo:** Oh, with pleasure, with great pleasure, with a nice, education.
**Luke:** Absolutely. Yep.
# Plan B Forum and Future Events
**Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year.
so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event.
**Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year.
I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world.
And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing.
**Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time.
And I think we're even playing this year, aren't we, Luke?
**Paolo:** You're
**Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos.
Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague?
**Knut:** paranoid and,
**Paolo:** Can I commission a
**Knut:** What song would you like to hear?
**Paolo:** I have two that I would suggest. One is Nothing Else Matters.
**Knut:** Alright.
**Paolo:** So I think that, is very inspiring, right?
**Knut:** Bitcoin, for sure.
Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke?
**Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference,
**Knut:** Yeah.
**Mathias:** not so much music, but yeah, that's peer to
**Knut:** Nothing else matters.
**Luke:** looking forward to that.
**Knut:** Sorry, brain fart. Sad but true is about the dollar still being around,
**Paolo:** Yeah, you can say that.
**Luke:** Okay.
# Final Thoughts and Closing Remarks
**Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that?
**Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms.
There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out.
**Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting.
**Mathias:** Just those things, that's all.
**Paolo:** Yeah, we can piss off more than this. Thanks.
**Mathias:** a
**Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners?
**Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them.
**Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good.
**Luke:** So that's, all at Keet. Is that correct? For Keet?
**Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer.
**Knut:** Alright,
**Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah.
**Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano.
**Paolo:** Likewise, I
**Knut:** But yeah, worth saying again.
**Paolo:** Thank you for having an invitation.
**Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
-

@ 8cb60e21:5f2deaea
2024-09-10 21:14:08
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05
It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint.
I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point.
I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog.
In line with that thinking, I made two parlays this week:
1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense.
2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout.
Are there any odds you're excited about (doesn't have to be football)?
originally posted at https://stacker.news/items/679894
-

@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。
怎么自建ntfy,后面再写。
---
2024年08月13日更新:
> 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
---
### 准备工具
- Ntfy服务
- Google Script
- Google Sheets
### 操作步骤
1. 在Ntfy后台账号,设置访问令牌。
[](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌")
2. 添加订阅主题。
[](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题")
2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图:
[](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id")
3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript
function checkEmail() {
var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID
var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据
cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread');
Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) {
var threadId = thread.getId();
if (!sentEmails.includes(threadId)) {
thread.getMessages().forEach(sendNtfyNotification);
recordSentEmail(sheet, threadId);
}
});
}
function sendNtfyNotification(email) {
if (!email) {
Logger.log("Email object is undefined or null.");
return;
}
var message = `发件人: ${email.getFrom() || "未知发件人"}
主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail";
var options = {
method: "post",
payload: message,
headers: {
Authorization: "Bearer Ntfy的令牌"
},
muteHttpExceptions: true
};
try {
var response = UrlFetchApp.fetch(url, options);
Logger.log("Response: " + response.getContentText());
} catch (e) {
Logger.log("Error: " + e.message);
}
}
function getSentEmails(sheet) {
var data = sheet.getDataRange().getValues();
return data.map(row => row[0]); // Assuming email IDs are stored in the first column
}
function recordSentEmail(sheet, threadId) {
sheet.appendRow([threadId, new Date()]);
}
function cleanOldData(sheet, minutes) {
var now = new Date();
var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues();
var rowsToDelete = [];
data.forEach(function(row, index) {
var date = new Date(row[1]); // 假设日期保存在第二列
if (date < thresholdDate) {
rowsToDelete.push(index + 1); // 存储要删除的行号
}
});
// 逆序删除(从最后一行开始删除,以避免行号改变)
rowsToDelete.reverse().forEach(function(row) {
sheet.deleteRow(row);
});
}
```
4.Goole Script需要添加gmail服务,如图:
[](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务")
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:
[](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器")
[](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细")
### 结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
效果预览:
[](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览")
-

@ 655a7cf1:d0510794
2024-09-10 13:16:15
Currently have kyc BTC, huge fan of lightning Network. Because I am a constant user of lightning. Plan on doing my business with lightning as well , peer-to-peer I'm not sure if I'm so worried about kyc I might be misguided in this situation.
originally posted at https://stacker.news/items/679520
-

@ 6ad3e2a3:c90b7740
2024-09-10 09:26:37
While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions:
**1. Separate passengers from their bags as early as possible.**
The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences:
a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes.
b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day.
c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five.
d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier.
e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable.
The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children.
To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc.
There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.)
Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane.
**2. Eliminate Security Lines**
Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement.
a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use.
Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious.
b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side.
Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side.
**3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.**
Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal.
**4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.**
There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done.
Here are some other suggestions:
1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up.
2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges.
3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease.
4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them.
I can anticipate some objections to these ideas, and I’ll address each one in turn.
**1. This would cost too much money.**
My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.)
**2. It’s too much of a security risk.**
Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end.
Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle.
**3. I like free carry-ons because it saves me from waiting at the baggage claim.**
Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse.
The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist.
*\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.*
*\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.*
-

@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48
I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote:
*What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.*
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-

@ 129f5189:3a441803
2024-09-09 23:28:41
Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration.
Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed.
https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg
This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad.
https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg
Reorienting U.S. Foreign Policy: Proposals for a Conservative Future
In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage.
Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed.
https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg
History and Structure of the State Department
Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner).
The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries).
https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg
Political Leadership and Bureaucratic Support
To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner).
Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies.
https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg
Global Threats to the U.S.
The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea.
🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner).
Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner).
https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg
🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government.
"The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner).
https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg
🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people.
"The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner).
https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg
🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests.
"The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?"
https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg
One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner).
This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines.
Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner).
It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement.
https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg
A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner).
From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives.
https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg
Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO.
https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg
🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power.
"The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner).
https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg
Detailed Policy Proposals
Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized.
"The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner).
https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg
Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities.
She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner).
https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg
Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem.
"Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis.
https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg
Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada.
"The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region.
https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg
Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India.
"Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner).
https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg
Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities.
"Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying.
https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg
Relations with Europe and Asia
Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom.
https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg
Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner).
https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg
International Organizations
Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner).
She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner).
https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg
Conclusion
Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president.
With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom.
https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
-

@ e83b66a8:b0526c2b
2024-09-09 20:30:30
We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect.
Therefore, I strongly advise you to run multiple clients.
On iPhone, I run:
Damus: https://nostrapps.com/damus
Primal: https://primal.net/downloads
Nostur: https://nostrapps.com/nostur
On Android I run:
Primal: https://primal.net/downloads
Amethyst: https://nostrapps.com/amethyst
On desktop I run:
Primal: https://primal.net/downloads
noStrudel: https://nostrapps.com/nostrudel
Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay.
If you haven’t taken the plunge to run a node, now might be a good time to think about it.
There are many, many options for clients, the “Social” section of
https://nostrapps.com/
lists 23 currently.
Play with them, see what they do, if you’re a developer, you could even consider building or forking your own.
Have fun and realise we are building freedom tech, not just running it.
-

@ e83b66a8:b0526c2b
2024-09-09 20:27:41
First,
Key management.
When you “created” your NOSTR account, what you actually created was a cryptographic key pair.
This consists of a private key, which starts “nsec” and a public key which starts with “npub”.
As the names suggest, your “nsec” key is private and you should never reveal it to anyone.
Your “npub” key is your public key, feel free to share that everywhere.
Your “npub” key is used by others to verify your identity, through the signature added to your messages.
It is also used by others to encrypt private messages to you.
We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary.
For the moment, consider using software key management options, some of which are listed under “signers” here:
https://nostrapps.com/
N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted:
Secondly,
Lightning wallets.
It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile
N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key.
You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet.
Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason….
It also allows you to send small micropayments to posts or people you like.
Thirdly,
Paid Services
As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability.
I, for example choose to pay for the following services:
https://nostr.wine/ - 120,000 Sats for 2 years relay
https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month
https://nostr.build/ - Media storage - 69,000 Sats for 1 year
Total: 22,750 Sats per month
Approx $15 per month
This is not strictly necessary, but I decided to support the various developers behind these projects.
Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward.
-

@ c11cf5f8:4928464d
2024-09-09 18:45:16

originally posted at https://stacker.news/items/678432
-

@ e968e50b:db2a803a
2024-09-09 18:21:54

Open the frozen pizza bay doors, Hal.
originally posted at https://stacker.news/items/678403
-

@ 6bae33c8:607272e8
2024-09-09 16:07:43
I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote:
*What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.*
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-

@ d3052ca3:d84a170e
2024-09-09 15:43:38
I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :)
I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet.
What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds?
What is your experience? I'd love to hear about it!
-

@ 3875a16c:988456c9
2024-09-09 14:50:15
**ORIGINAL PANEL TITLE:**
MAKING BITCOIN MORE PRIVATE WITH CISA
**SPEAKERS:**
NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP
**CONFERENCE:**
BITCOIN NASHVILLE 2024
**ORIGINALLY PUBLISHED ON:**
BITLYRICS.CO
## Introduction
This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/).
Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development.
---
### NiftyNei (Moderator):
Hey everyone, my name is Nifty, and I’m going to be moderating this panel today.
We’re here to talk about CISA (cross-input signature aggregation).
Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage.
We’re excited to be talking to you guys about this.
I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA.
Craig, do you want to start?
---
### Craig Raw (Sparrow Wallet):
I built Sparrow Wallet. It’s a security and privacy-focused wallet.
The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen.
When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically.
So, that was the first time I really started to look at it from the privacy angle.
---
### Fabian Jahr (Brink):
I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it.
Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core.
Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months.
I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller.
I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it.
---
### Jameson Lopp (Casa):
I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups.
I think the first time I heard about CISA was in an Andrew Poelstra talk.
I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted.
This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics.
---
### NiftyNei (Moderator):
That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for.
Does anyone have a good explanation of how it works?
---
### Fabian Jahr (Brink):
I can start off.
So, it’s really already all in the name: cross-input signature aggregation.
If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated.
What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction.
So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before.
Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea.
---
### NiftyNei (Moderator):
I have a quick question about that.
So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right?
So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature.
Is that a good summary of what you’re explaining?
---
### Fabian Jahr (Brink):
Yeah, I would say so.
---
### Craig Raw (Sparrow Wallet):
So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it.
That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one.
Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it.
Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones.
Unfortunately, the downside of that is that you have to do the interaction while you sign.
The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing.
As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient.
---
### NiftyNei (Moderator):
Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right?
You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level?
---
### Jameson Lopp (Casa):
Well, there’s also full-block aggregation, right?
This is going really far down the rabbit hole, and I think it’s not even something that’s on the table.
There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations.
My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized.
If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again.
---
### NiftyNei (Moderator):
So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation.
We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there.
One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right?
Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated.
---
### Jameson Lopp (Casa):
Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically.
If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount.
It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO.
You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet.
It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot.
It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before.
So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so.
---
### Fabian Jahr (Brink):
And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy.
The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property.
Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.”
Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it.
Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature.
---
### Jameson Lopp (Casa):
Yeah, we have to think about the incentives, right?
I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are.
But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late.
We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so.
It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software.
Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money?
---
### Craig Raw (Sparrow):
So you might be wondering at this stage what the savings actually look like.
It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block.
You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage.
Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%.
But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space.
So that’s how I would encourage you to think about it from the start.
For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride.
We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about.
---
### NiftyNei (Moderator):
I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy.
I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal?
What was it about the Taproot process where this proposal didn’t make it over the line?
---
### Fabian Jahr (Brink):
I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed.
From what I can see, I don’t think there was any direct opposition.
The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller.
I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding.
I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much.
---
### Craig Raw (Sparrow):
Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough.
There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.”
That’s an interesting point of view.
---
### Jameson Lopp (Casa):
It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet.
---
### Craig Raw (Sparrow):
Yeah, so we’re in a very different space now.
Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine.
I’m talking about the well-understood half-signature aggregation form of it.
From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that.
So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing.
If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down.
So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line.
---
### Jameson Lopp (Casa):
I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin.
With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process.
As far as I’m aware, there’s been limited adoption of Schnorr so far.
I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility.
I care about this a lot, operating a multi-signature self-custody wallet.
We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature.
That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out.
So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block.
---
### NiftyNei (Moderator):
So, we only have a few minutes left.
Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in.
---
### Fabian Jahr (Brink):
There are still quite a few things to hammer out in terms of all the details, like defining a spec.
For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open.
However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity.
We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now.
---
### Jameson Lopp (Casa):
Yeah, call your local developer and demand signature aggregation today.
---
### Craig Raw (Sparrow):
Fabian has developed a great site where you can learn more.
If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it.
It’s very easy to read, not overly technical, and I think it gives a good grounding in these things.
Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not.
As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now.
So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not.
---
### Jameson Lopp (Casa):
I don’t know, do you want to save money? It should be an easy question.
---
### Fabian Jahr (Brink):
And have better privacy.
---
### NiftyNei (Moderator):
Great! Thanks y’all.
---
**Follow the speakers: **
[NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr)
**Watch the original content: **
[Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107)
**Also read: Build It Right: **
[Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/)
**Disclaimer: **
Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/).
-

@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24
## Chef's notes
Makes an excellent Chicken sandwich.
## Details
- ⏲️ Prep time: 6 Ish hours
- 🍳 Cook time: 40 min
- 🍽️ Servings: 1 loaf
## Ingredients
- 3 ½ - 4 cups bread flour, or more as needed
- 1 ⅓ cups warm milk (110°F – 115°F)
- 5 tablespoons honey
- 4 tablespoons salted butter, melted and slightly cooled
- 1 tablespoon instant “rapid rise” yeast
- 1 ½ teaspoons salt
- Oil or butter for greasing the bowl
- 1 tablespoon melted salted butter, for brushing the crust at the end
## Directions
1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl.
2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes.
3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours.
4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan.
5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F.
6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped.
7. Brush the top of the warm bread with melted butter.
8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
-

@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05
Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one?
Thanks
originally posted at https://stacker.news/items/677439
-

@ eed76ece:afa98124
2024-09-08 21:13:37
Seems like if you want to sell an item on SN using @AGORA makes logical sense.
Perhaps if your a manufacturer, importer, exporter, stocking distributor, wholesaler etc. you should also consider using @Import_Export or both @AGORA and see if they help each other. Being totally upfront
Import_Export is probably a better use case especially if you are running over 75% B2B.
We are note promoting the use of B2C on SN. We're 100% focused on interactions between businesses only. Our primary markets are in Asia and Southeast Asia. Europe and the UK are dying a slow death, and the last straw was the Telegram event.
So I am endorsing you to please at least on SN refer to @AGORA for basic B2C (retail).
Thank you,
https://www.globalmerchant.io
originally posted at https://stacker.news/items/677390
-

@ e8b86bc1:3503c58f
2024-09-08 19:37:36
Opinion about Freewallet Multi Crypto Wallet (iphone)
<!--HEADER END-->
Freewallet is now charging inactivity fees, a sneaky method to take money from users who aren’t regularly using the app. Avoid this scam wallet!
<!--FOOTER START-->
#WalletScrutiny #nostrOpinion
[Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
-

@ c11cf5f8:4928464d
2024-09-08 19:10:39
Considering the "whatever" item in question is a random item, a unique piece --not something you produce or need to market-- which platform, website or which strategy you'll put in place to get the value of your item in sats, immediately, anonymously, via the Lightning Network?
originally posted at https://stacker.news/items/677270
-

@ 6f170f27:711e26dd
2024-09-08 17:45:46
> Far too many people:
"GDP is bad. I prefer [thing correlated at 0.9 with GDP]."
Manufacturing:
Life expectancy:
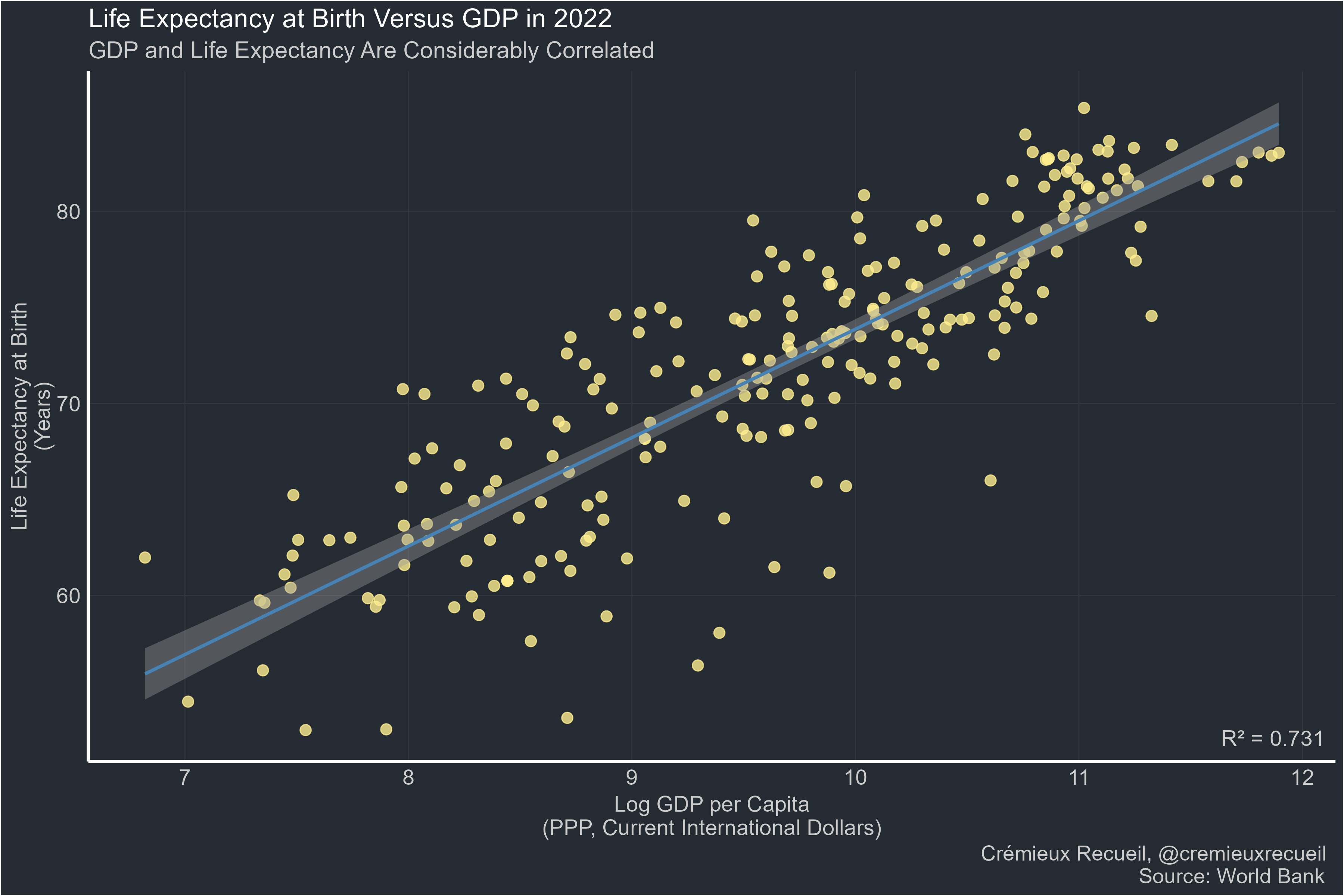
Happiness:
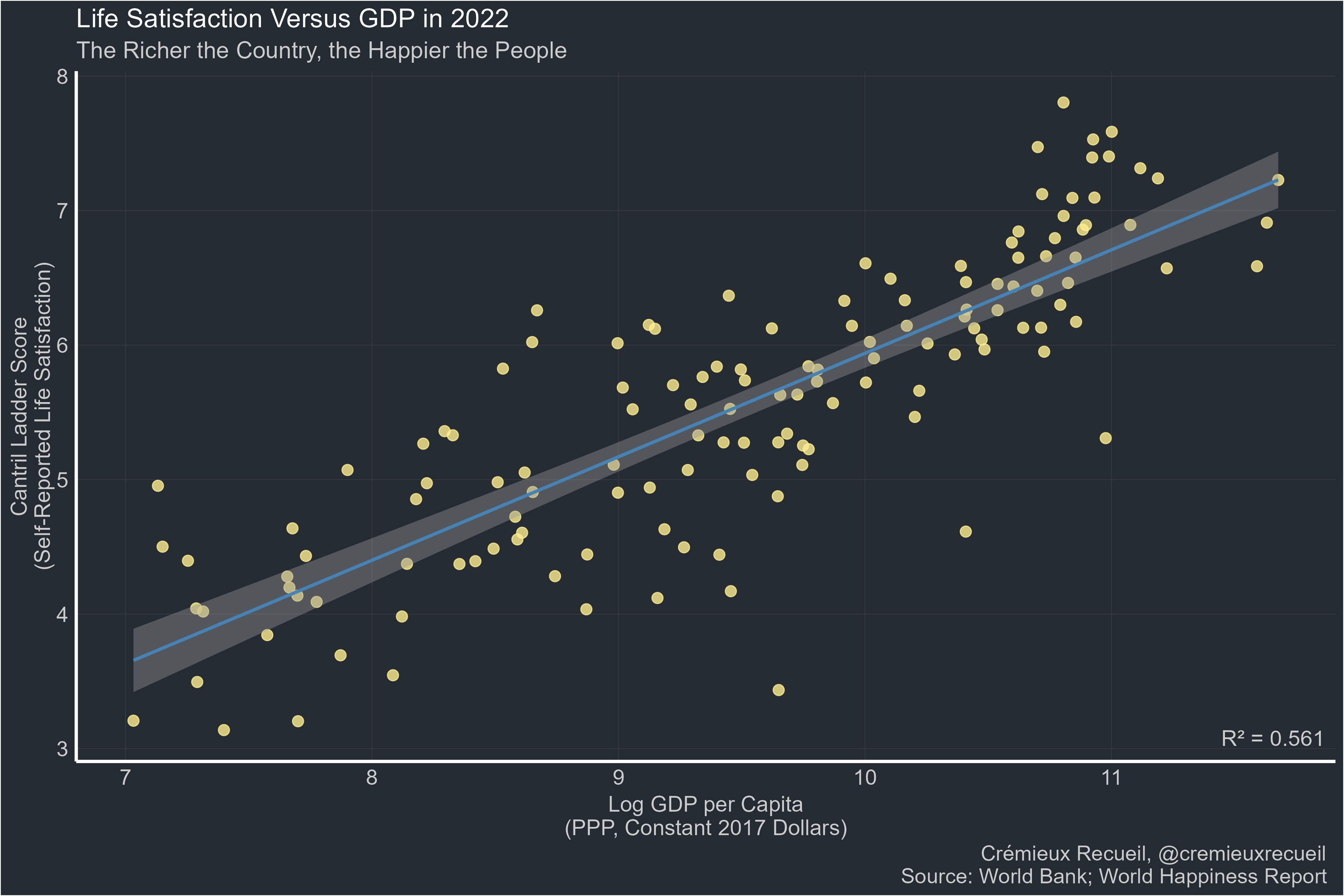
Many other metrics & discussion in the source:
https://x.com/cremieuxrecueil/status/1832588128084730334
originally posted at https://stacker.news/items/677211
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19# GitCitadel Development Operations We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes. ## Supplier Coordination  Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide. ## OneDev Implementation  Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a [self-hosted OneDev instance](https://onedev.gitcitadel.eu). In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers. Our [team's GitHub projects](https://github.com/ShadowySupercode) will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted [GitWorkshop instance](nostr:naddr1qvzqqqrhnypzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqy88wumn8ghj7mn0wvhxcmmv9uqq5emfw33kjarpv3jkcs83wav). We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay! ## Next Infrasteps ### Automated Testing Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our [Alexandria client](https://next-alexandria.gitcitadel.eu). We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers). We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive. After that, a Gherkin-based [Behave feature test](https://behave.readthedocs.io/en/latest/) for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next. The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to *Done*. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.  ### Automated Builds As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.  We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:  This will make it easier for us to work and collaborate asynchronously and without unnecessary delays. ### Expanding the Status Page  And, finally, we get to the point of all of this busyness: reporting. We are going to have beautiful reports, and we are going to post them online, on our [status page](https://status.gitcitadel.com). We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our [GitCitadel DevOps npub](nostr:npub16p0fdr2xccfs07hykx92t0cascac69xjuwaq38kjqy3aawt5hx8s82feyj), to make sure you don't miss out on the IT action. ## Building on stone All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation. Happy building!
@ fd208ee8:0fd927c1
2025-02-02 10:33:19# GitCitadel Development Operations We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes. ## Supplier Coordination  Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide. ## OneDev Implementation  Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a [self-hosted OneDev instance](https://onedev.gitcitadel.eu). In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers. Our [team's GitHub projects](https://github.com/ShadowySupercode) will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted [GitWorkshop instance](nostr:naddr1qvzqqqrhnypzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqy88wumn8ghj7mn0wvhxcmmv9uqq5emfw33kjarpv3jkcs83wav). We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay! ## Next Infrasteps ### Automated Testing Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our [Alexandria client](https://next-alexandria.gitcitadel.eu). We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers). We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive. After that, a Gherkin-based [Behave feature test](https://behave.readthedocs.io/en/latest/) for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next. The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to *Done*. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.  ### Automated Builds As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.  We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:  This will make it easier for us to work and collaborate asynchronously and without unnecessary delays. ### Expanding the Status Page  And, finally, we get to the point of all of this busyness: reporting. We are going to have beautiful reports, and we are going to post them online, on our [status page](https://status.gitcitadel.com). We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our [GitCitadel DevOps npub](nostr:npub16p0fdr2xccfs07hykx92t0cascac69xjuwaq38kjqy3aawt5hx8s82feyj), to make sure you don't miss out on the IT action. ## Building on stone All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation. Happy building! @ b17fccdf:b7211155
2025-02-01 18:41:27#### **Next new resources about the MiniBolt guide have been released**: --- * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) * 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-02-01 18:41:27#### **Next new resources about the MiniBolt guide have been released**: --- * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) * 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) --- Enjoy it MiniBolter! 💙 @ 0271e1b9:ad8cff90
2025-02-01 07:39:31**I study the greats.** For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better. Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person. > “You must value learning above everything else.” ― Robert Greene > “Those who have a 'why' to live, can bear with almost any 'how'.” ― Viktor E. Frankl > “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.” ― Phil Stutz > “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.” ― Marcus Tullius Cicero > “Error correction is the basis of all intelligence.” ― Jeff Booth > “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living." ― Jesse Enkamp > "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him." — Confucius > “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.” ― Michelangelo > “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.” ― Marcus Tullius Cicero > “You either bleed soul into your work, or let the work bleed out your soul.” ― Pran Yoganthan > "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.” ― Michael Sugrue > "The strong do what they can and the weak suffer what they must." ― Thucydides > “The brain is the most powerful weapon in the world.” ― David Goggins > “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.” ― Friedrich Nietzsche > "Consciousness is awareness with a choice." ― Thomas Campbell > “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.” ― Epictetus > “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.” — John Vervaeke > “It is impossible for a man to learn what he thinks he already knows.” ― Epictetus > “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.” ― Michael Behrens > “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.” ― Jiddu Krishnamurti > “This is your life. You’re accountable. What are you gonna do about that?” ― James Hollis By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection) *Peace & Love,* *[Kontext](https://linktr.ee/mckontext)* *Block height 881,748*
@ 0271e1b9:ad8cff90
2025-02-01 07:39:31**I study the greats.** For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better. Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person. > “You must value learning above everything else.” ― Robert Greene > “Those who have a 'why' to live, can bear with almost any 'how'.” ― Viktor E. Frankl > “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.” ― Phil Stutz > “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.” ― Marcus Tullius Cicero > “Error correction is the basis of all intelligence.” ― Jeff Booth > “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living." ― Jesse Enkamp > "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him." — Confucius > “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.” ― Michelangelo > “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.” ― Marcus Tullius Cicero > “You either bleed soul into your work, or let the work bleed out your soul.” ― Pran Yoganthan > "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.” ― Michael Sugrue > "The strong do what they can and the weak suffer what they must." ― Thucydides > “The brain is the most powerful weapon in the world.” ― David Goggins > “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.” ― Friedrich Nietzsche > "Consciousness is awareness with a choice." ― Thomas Campbell > “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.” ― Epictetus > “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.” — John Vervaeke > “It is impossible for a man to learn what he thinks he already knows.” ― Epictetus > “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.” ― Michael Behrens > “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.” ― Jiddu Krishnamurti > “This is your life. You’re accountable. What are you gonna do about that?” ― James Hollis By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection) *Peace & Love,* *[Kontext](https://linktr.ee/mckontext)* *Block height 881,748* @ 82100056:e198089f
2025-01-29 14:22:06
@ 82100056:e198089f
2025-01-29 14:22:06 @ ec42c765:328c0600
2025-01-26 00:08:54# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2024/02/05)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](nostr:naddr1qqykwetwv4exzmz22qqs6amnwvaz7tmwdaejumr0dspzpmzzcaj5rzeah8y940ln4z855wa72af4a6aac4zjypql55egcpsqqvzqqqr4fcp4fwv8)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](nostr:npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](nostr:npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
@ ec42c765:328c0600
2025-01-26 00:08:54# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2024/02/05)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](nostr:naddr1qqykwetwv4exzmz22qqs6amnwvaz7tmwdaejumr0dspzpmzzcaj5rzeah8y940ln4z855wa72af4a6aac4zjypql55egcpsqqvzqqqr4fcp4fwv8)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](nostr:npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](nostr:npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md) @ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad. --- 1. Don’t Feed the Clowns You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat. Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month. --- 2. Turn Off the Fiat News Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance. Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed. --- 3. Mock Their Inflationary Gospel Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?" Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror. --- 4. Celebrate the Fiat Freakshow Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never. --- 5. Build in the Chaos While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt. Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats. --- 6. Adopt a Fiat-Free Lifestyle Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.” Every satoshi spent in the real economy is a slap in the face to the fiat overlords. --- 7. Find the Humor in Collapse Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all. Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold. --- 8. Stay Ruthlessly Optimistic Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better. So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt. --- Final Thought: Burn the Tent Down Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates. But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k. Welcome to the satirical resistance. Now go stack some sats.
@ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad. --- 1. Don’t Feed the Clowns You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat. Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month. --- 2. Turn Off the Fiat News Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance. Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed. --- 3. Mock Their Inflationary Gospel Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?" Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror. --- 4. Celebrate the Fiat Freakshow Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never. --- 5. Build in the Chaos While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt. Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats. --- 6. Adopt a Fiat-Free Lifestyle Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.” Every satoshi spent in the real economy is a slap in the face to the fiat overlords. --- 7. Find the Humor in Collapse Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all. Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold. --- 8. Stay Ruthlessly Optimistic Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better. So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt. --- Final Thought: Burn the Tent Down Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates. But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k. Welcome to the satirical resistance. Now go stack some sats. @ b17fccdf:b7211155
2025-01-21 16:30:11> Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap? --- Go to the bonus guide by clicking ~ >[HERE](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel) <~ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 16:30:11> Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap? --- Go to the bonus guide by clicking ~ >[HERE](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel) <~ --- Enjoy it MiniBolter! 💙 @ b8851a06:9b120ba1
2025-01-14 15:28:32## **It Begins with a Click** It starts with a click: *“Do you agree to our terms and conditions?”*\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval? This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life? --- ## **Welcome to Digital Serfdom** We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system. - Your data? Owned by the lords of Big Tech. - Your money? Controlled by banks and bureaucrats who can freeze it on a whim. - Your thoughts? Filtered by algorithms that reward conformity and punish dissent. The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate. They don’t call it control, of course. They call it *“protection.”* They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars. --- ## **Freedom in Chains** But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence. We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more. --- ## **The Great Unpermissioning** It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission. The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, *“No.”* It’s the realization that the freedom you seek won’t be granted—it must be reclaimed. - **Stop asking.** Permission is their tool. Refusal is your weapon. - **Start building.** Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control. - **Stand firm.** They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply. The path won’t be easy. Freedom never is. But it will be worth it. --- ## **The New Frontier** The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles. This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply. --- ## **A Final Word** They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it. You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
@ b8851a06:9b120ba1
2025-01-14 15:28:32## **It Begins with a Click** It starts with a click: *“Do you agree to our terms and conditions?”*\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval? This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life? --- ## **Welcome to Digital Serfdom** We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system. - Your data? Owned by the lords of Big Tech. - Your money? Controlled by banks and bureaucrats who can freeze it on a whim. - Your thoughts? Filtered by algorithms that reward conformity and punish dissent. The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate. They don’t call it control, of course. They call it *“protection.”* They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars. --- ## **Freedom in Chains** But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence. We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more. --- ## **The Great Unpermissioning** It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission. The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, *“No.”* It’s the realization that the freedom you seek won’t be granted—it must be reclaimed. - **Stop asking.** Permission is their tool. Refusal is your weapon. - **Start building.** Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control. - **Stand firm.** They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply. The path won’t be easy. Freedom never is. But it will be worth it. --- ## **The New Frontier** The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles. This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply. --- ## **A Final Word** They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it. You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours. @ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs ## The reason why we have broken money Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world. In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes. However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore. Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too. Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it. ## Bitcoin overcomes the "transfer of hard money" problem Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design. Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it. Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive. Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold. ## Bitcoin blurs the line between commodity and technology Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules. At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable. Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases. ## The dangers of derivatives A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold. In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin. Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense. ## Learn for yourself If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody". There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs ## The reason why we have broken money Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world. In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes. However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore. Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too. Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it. ## Bitcoin overcomes the "transfer of hard money" problem Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design. Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it. Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive. Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold. ## Bitcoin blurs the line between commodity and technology Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules. At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable. Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases. ## The dangers of derivatives A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold. In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin. Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense. ## Learn for yourself If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody". There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance. @ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa @ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。 所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。 https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。 我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛 幸运的是npub.pro 建站这样的,我觉得有点意思。 yakihonne 智能widget 也有意思 我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。 所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。 https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。 我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛 幸运的是npub.pro 建站这样的,我觉得有点意思。 yakihonne 智能widget 也有意思 我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。 @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.* Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end. Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:  and after a number of outputs, selected this one to work on:  The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.  The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.  At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.  At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:  Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story. #### The AI Generated Elephant in the Room If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it. I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points. I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.* Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end. Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:  and after a number of outputs, selected this one to work on:  The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.  The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.  At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.  At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:  Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story. #### The AI Generated Elephant in the Room If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it. I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points. I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs. @ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse. That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions. Enter [Olas](https://olas.app). If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer. Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health. Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts. Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild. Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers. Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!). [Download on iOS](https://testflight.apple.com/join/2FMVX2yM). [Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore. Let's make waves together.
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse. That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions. Enter [Olas](https://olas.app). If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer. Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health. Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts. Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild. Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers. Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!). [Download on iOS](https://testflight.apple.com/join/2FMVX2yM). [Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore. Let's make waves together. @ e6817453:b0ac3c39
2025-01-05 14:29:17## The Rise of Graph RAGs and the Quest for Data Quality As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence. ## Booming Interest in Graph RAGs Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can: * **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations. * **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving. Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs? ## Data Quality: The Foundation of Effective Graphs A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why: * **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities. * **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them. Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs. ## Hybrid Graph RAGs and Variations While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that: * Handle diverse data sources with ease. * Offer improved adaptability to complex queries. Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing. ## Ontology: The Key to Graph Construction Quality Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for: * **Defining Relationships:** Clarifying how concepts connect within a domain. * **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities. Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs? ## How to Build Ontology Expertise in a Startup Team For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach: 1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering. 2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation. 3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks. 4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process. 5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing. So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts. You could read about barefoot experts in my article : Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise. ## How to Find or Create Ontologies For teams venturing into Graph RAGs, several strategies can help address the ontology gap: 1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance: * **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge. * **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields. * **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures. 1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation. 2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development: * **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data. * **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies. ## Parallel Ontology and Graph Extraction An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as: * **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies. * **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction. Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method. ## LLMs as Ontologists While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to: * **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures. * **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance. However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes. ## Final Thoughts: Unlocking the Power of Graph RAGs The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools. As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding. Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
@ e6817453:b0ac3c39
2025-01-05 14:29:17## The Rise of Graph RAGs and the Quest for Data Quality As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence. ## Booming Interest in Graph RAGs Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can: * **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations. * **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving. Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs? ## Data Quality: The Foundation of Effective Graphs A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why: * **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities. * **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them. Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs. ## Hybrid Graph RAGs and Variations While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that: * Handle diverse data sources with ease. * Offer improved adaptability to complex queries. Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing. ## Ontology: The Key to Graph Construction Quality Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for: * **Defining Relationships:** Clarifying how concepts connect within a domain. * **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities. Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs? ## How to Build Ontology Expertise in a Startup Team For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach: 1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering. 2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation. 3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks. 4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process. 5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing. So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts. You could read about barefoot experts in my article : Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise. ## How to Find or Create Ontologies For teams venturing into Graph RAGs, several strategies can help address the ontology gap: 1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance: * **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge. * **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields. * **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures. 1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation. 2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development: * **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data. * **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies. ## Parallel Ontology and Graph Extraction An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as: * **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies. * **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction. Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method. ## LLMs as Ontologists While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to: * **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures. * **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance. However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes. ## Final Thoughts: Unlocking the Power of Graph RAGs The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools. As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding. Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation! @ 1cb14ab3:95d52462
2025-01-05 04:18:29*Stunning beaches, ancient temples as far as the eye can see, and lush, green mountainsides that will leave you in awe—Myanmar is a destination you NEED to add to your bucket list. This guide offers the perfect one-month itinerary to explore the hidden gems of this incredible country.*  --- ## The Itinerary #### Days 1-2: Fly into Yangon Airport. Settle in and explore the vibrant sights and flavors of the city. #### Day 3: Take an overnight bus south to the coastal city of Myeik. #### Days 4-8: Go island hopping around the Mergui Archipelago—remote beaches and untouched islands await. #### Day 9: Travel to Dawei. Find a cozy place to stay and relax for the evening. #### Days 10-13: Rent a motorcycle and explore the stunning Dawei Peninsula. Soak up the sun on pristine beaches. #### Day 14: Head to Hpa An. Check into a hotel and enjoy a sunset beer. #### Days 15-18: Discover the limestone mountains, caves, and farmlands of Hpa An. #### Day 19: Travel to Bagan. The journey may be bumpy, but the destination is worth it. #### Days 20-23: Explore the breathtaking temples of Bagan. Sunrise hot air balloon rides are a must. #### Day 24: Head to Lake Inle. Settle into your accommodation and dine by the water. #### Days 25-26: Cruise around Lake Inle by boat. Immerse yourself in the local culture and capture the iconic fishermen in action. #### Days 27-28: Visit Mandalay to experience city life from a Burmese perspective. #### Days 29-30: Return to Yangon for a final exploration before flying home. --- ## Days 1-2: Arrival in Yangon Myanmar's largest city is a bustling hub filled with shops, activities, and incredible food. The rapid development of this once-isolated country is evident everywhere you look. **If you are flying internationally:** Yangon will most likely be the cheapest and most easily accessible destination to begin the trip. **If you are coming from Thailand:** I would recommend altering the itinerary and going straight to Myeik via land border then working your way up the country from there. #### Bogyoke Aung San Market If shopping is your thing, this place is a haven for local treasures. Hundreds of stalls line the market and surrounding alleyways containing everything from art, sculptures, jewelry, antiquities, and fabrics. I spent a few hours here before jumping onto the nearby circular train for a loop around the city. There are a few small shops to get a bite to eat if you are hungry. Remember that this itinerary will land you back in Yangon at the end of the trip if you see something you want to buy and don’t feel like lugging it around for a month.  #### Yangon Circular Train Easily one of the most fascinating experiences of the trip is riding the Yangon Circular Train around the city for a true look at how the locals live. The train is old, slow, and packed with locals commuting to and from work. The doors are wide open, allowing you to hang your feet outside and soak in all of the sights afar. This is one of the best ways to get a true glimpse into the culture and day-to-day life of the Burmese people. Be sure to speak with a train operator before getting on to make sure the entire loop is operational. When I went, construction stopped the train about 45 minutes into the loop, forcing us to get a taxi back to the downtown area. The full loop will take over 2 hours to complete. On the train, you can find vendors and hawkers selling little things such as water, nuts, and fruit. I’d suggest eating before jumping on.  #### Shwedagon Pagoda Upon walking up the steep and lengthy stairway to the Shwedagon Pagoda lies Yangon’s most famous attraction. The 99-meter gold-coated pagoda can be seen all around the city but is best enjoyed up close. This is a must-visit during your time in the capital. I went about an hour before sunset and stayed well into the night. Sunset from the hill it sits atop is spectacular, and the contrast of the pagoda between day and night is striking. Make sure to bring socks and a bag, as shoes are not allowed, and you will need to carry them or leave them at the door. After visiting, you can take a short walk to the Sky Bar in the Yangon International Hotel overlooking the pagoda. This is a wonderful place to enjoy a nice dinner and drink, ideal for soaking up more of that luxurious golden pagoda.  --- ## Day 3: Bus to Myeik The longest stretch of the trip—but well worth the sights to come. I took a 22-hour overnight bus and opted for the slight upcharge to take the VIP bus. This option is absolutely worth it. Equipped with A/C, comfortable reclining seats, and stops for three meals, it was a cheaper alternative to the costly domestic flight from Yangon and allowed me to see much more of the country. I had a surprisingly good sleep and would do it again in a heartbeat. You can also fly directly to Myeik, but flights are infrequent and considerably more expensive. The bus I took arrived in Myeik around noon the next day, leaving me plenty of time to check into the hotel and wander around the city a bit before sunset. There weren’t many buses heading down here, so I’d recommend checking for tickets as early as possible when you arrive in Yangon. Alternatively, if you’re coming from Thailand, you can rearrange the itinerary and begin your Myanmar trip in Myeik by crossing from Thailand via bus at the land border.  --- ## Days 4-8: Island Hopping in Myeik The city of Myeik has no accessible beaches, so you’ll need to book an island-hopping tour to fully appreciate the surrounding Mergui Archipelago. While the city itself doesn’t offer much in terms of entertainment, the beaches and crystal-clear waters you’ll encounter on an island-hopping tour are truly unparalleled. Your trip to Myeik will be unforgettable and is an experience you shouldn’t miss. There are several travel companies offering island-hopping tours, ranging from single-day trips to 14-day excursions. While you can book ahead, I found it quite easy to arrange a trip through an agency in the city. I opted for a three-day, two-night tour with Life Seeing Tours, and it was fantastic. They provided food, tents, and transportation—just bring a swimsuit and a change of clothes, and you’re ready to spend a few nights exploring the islands.     --- ## Day 9: Bus to Dawei Another travel day! This time, you’ll take a shorter bus ride heading north to Dawei. The journey takes about six hours, and tickets can be purchased from one of the travel agencies in Myeik. From what I gathered, there’s only one bus per day on this route, and it departs early in the morning. Be prepared to wake up around 4 AM and make your way back to the same bus station where you arrived. It’s a good idea to arrange transportation to the station the night before—your hotel can help you book a ride for that morning. --- ## Days 10-13: Motorcycling the Dawei Peninsula Dawei boasts some of the most stunning coastlines and beaches in the country. While most of these beaches are only accessible by motorcycle, there are a few small bed-and-breakfast-style accommodations at the southern end of the peninsula that offer direct beach access. If you’d prefer not to travel 2–3 hours each day from the city, I recommend staying in that area. You can rent a motorcycle from several places in the city and ride down to the B&Bs near the beaches for an overnight stay. This approach lets you enjoy the remote, lush, and scenic motorcycle journey while avoiding the daily commute to the beaches.  #### Grandfather Beach Surrounded by mountains and vibrant orange dirt, getting here can be a bit tricky. You’ll need to navigate a steep, loose hill to reach the area. I recommend arriving near low tide, as the beach and surrounding shops flood around noon, making the descent a wet and challenging experience. Be prepared to remove your shoes and walk through knee-deep water to access the beach. This is one of the more popular spots for locals and was among the few beaches I visited that actually had people.  #### Tizit Beach When we arrived at Tizit Beach, there was no one else around except for the locals. The sand here is soft, and the ocean is pristine. A motorcycle is necessary to access this beach, but the breathtaking views from the mountain pass make the journey entirely worthwhile. The sand near the shore is firm enough to ride on, creating unforgettable moments of cruising along the beach at sunset.  --- ## Day 14: Bus to Hpa An One of the shorter bus rides on this trip, the fare is around $20, and it takes approximately 5 bumpy hours. Once you arrive in Hpa An, there are plenty of hostels and hotels to choose from. I booked mine on Hostelworld the night before, but you should have no trouble finding a place to stay on the day of your arrival if needed. --- ## Days 15-18: Hpa An: Farmland, Caves, and Mountains Hpa An offers a stark contrast to the beaches and cities encountered so far on the trip. Surrounded by towering limestone mountains and lush green farmland, the region has a peaceful, rural charm. There are several caves, lakes, and one of my favorite sunrise hikes of the journey. While I have a few recommendations and must-visit spots, Hpa An is best explored without a strict plan. A central theme of this trip has been the freedom of hopping on a motorcycle and riding wherever your heart desires.  #### Mount Zwegabin Sunrise Hike Hiking Mount Zwegabin for sunrise is a must-do during your time in Hpa An. The mountain is located a short ride from town, about 40 minutes by motorcycle. The hike to the summit took around 35 minutes at a brisk pace, so you’ll need to leave around 4 AM to catch the sunrise, depending on the season. The highlight of the hike is the final ascent up the floating stairs to reach the peak. Be sure to have your camera ready and take in the breathtaking views.  #### Kyauk Kalat Pagoda This is one of those places that leaves you in awe, wondering how such a unique landscape can exist. Easily one of the most unusual rock formations I’ve encountered, it’s a fantastic spot to watch the sunset. A winding staircase leads up the rock to the top of the temple, making it a great place to spend a couple of hours.  #### Saddar Cave Filled with bats, stunning limestone formations, and statues, this short cave walk provides a refreshing escape from the heat. The path takes about 20 minutes to explore, leading to a beautiful lake at the back. Grab a drink, relax for a while, and take a small paddle boat back to the entrance for a memorable experience.  --- ## Day 19: Bus to Bagan A travel day heading north. This part of the trip is hot, bumpy, and slow, so be prepared for a longer journey than expected. Bagan has plenty of hotels and hostels, but I’d recommend booking accommodations in advance, as it’s a popular tourist destination. You’ll need to purchase an entry ticket for the area, as it’s a protected national park, but the bus driver should assist in sorting it out before you enter the park. --- ## Days 20-23: Chasing Pagodas in Bagan Once you’ve settled into your accommodation in Bagan, the best way to explore the vast area is by pedal bike or scooter. All the scooters available for rent are electric, helping to reduce noise pollution—a refreshing change from the loud gas-powered vehicles you’ll be used to from the first half of your trip. There’s no right or wrong way to experience Bagan. The park is enormous, with thousands of pagodas scattered throughout. Most of them are open for exploration, with a few offering rooftop access (though that is being restricted more recently). You could spend weeks here and still not see all the pagodas up close. Bagan is divided into a new town and an old town—most of the backpacker-friendly hostels are located in Old Town. You’ll find a handful of restaurants, but I often ate at my hostel or from local food carts. Several hostels and hotels offer outdoor pools, which are a great perk, especially depending on the time of year you visit. I highly recommend simply wandering the area freely, but here are a few top pagodas and experiences not to miss during your time in Bagan.  #### Hot Air Ballooning The top attraction in Bagan is undoubtedly the daily hot air balloon tours. Almost everyone who experiences it claims it’s a must-do. I chose to watch from the ground, as the cost of a tour is quite expensive. If you decide to go for it, be sure to set aside a few hundred USD for the trip. From what I’ve heard, you’ll wake up around 4:30 AM and head to the take-off location, returning by around 9:00 AM.  #### Sunset Boat Cruise Be sure to spend at least one evening on a slow cruise down the Ayeyarwady River. It’s a wonderful way to enjoy distant views of some of the pagodas and relax after a long day of exploration. Several companies offer these cruises at very affordable prices. Our boat included snacks, drinks, and even alcohol. The trips range from half an hour to two hours. Book through your hotel for convenience.  #### The Big Three Temples With over a thousand pagodas to explore in Bagan, there are three main structures that hold significant importance to locals: Shwesandaw, Thatbyinnyu, and Shwezigon. Be sure to make time to visit these iconic pagodas during your trip—you’re likely to come across them without even trying.  --- ## Day 24: Bus to Kalaw Long-distance buses run the route multiple times a day, with the overnight option being the most popular. I recommend checking with a travel agent in Bagan to book your tickets before heading to the bus stop --- ## Day 25-26: Relaxing at Lake Inle These two days take us to the stunning Lake Inle, located just outside the city of Kalaw. Unfortunately, I wasn’t able to make it to Lake Inle during this trip, but everyone I spoke to highly recommended not missing it. The lake is known for its breathtaking scenery, traditional Intha stilt houses, and the unique leg-rowing fishermen. From what I’ve heard and seen through photos, the calm waters, floating gardens, and vibrant markets make Lake Inle a truly unforgettable destination. Huge thanks to my friend Toby for sharing those beautiful pictures and giving me a glimpse of what I missed!     --- ## Day 27-28: Mandalay City Mandalay is a fast-paced city with less tourism compared to other parts of the country. It offers a fascinating glimpse into the daily lives of the Burmese people, away from the crowds typically found in Yangon. There are several culturally significant monasteries and temples within the city limits, as well as vibrant markets perfect for shopping and exploring. Mandalay Hill is a great spot for a brisk hike and offers stunning views of the city and sunset on one of your nights. You could also visit the Mandalay Marionettes Theater to catch a local show showcasing Myanmar’s rich history and culture. As for me, I mainly wandered the city without specific destinations in mind. Since this is the last stop before returning to Yangon, you might not feel as inclined to spend too much time here, but there are definitely some interesting sights worth exploring.  --- ## Day 29-30: Return to Yangon The final two days of the trip are a return to where it all began. The bus from Mandalay to Yangon takes about 8 hours. Alternatively, Mandalay has a large international airport if you prefer to fly, depending on your next destination. If you return to Yangon, you’ll have plenty of time to revisit the markets and pick up any final souvenirs or trinkets you might want to take home. Enjoy these last couple of days, savor some delicious food, and take the time to reflect on the incredible month of experiences you’ve had.  --- ## Concluding Thoughts Your month-long journey through Myanmar is bound to be an unforgettable adventure, filled with stunning landscapes, rich culture, and warm hospitality. From the serene beaches of Ngapali to the ancient wonders of Bagan, and the tranquil beauty of Lake Inle to the bustling streets of Yangon and Mandalay, each destination offers its own unique charm and insight into Myanmar’s diverse culture. The highlights of your trip—exploring historic pagodas, witnessing breathtaking sunrises, and embracing the freedom of riding a motorcycle—are sure to stay with you. Myanmar’s blend of natural beauty, vibrant traditions, and friendly locals makes every moment special. Despite the occasional long and bumpy journeys, the sense of discovery and connection with the people and places makes the experience truly worthwhile. As you reflect on your journey, you’ll likely feel grateful for the memories, experiences, and the chance to explore a country that feels both timeless and unique. Myanmar’s beauty lies not just in its landscapes but in the people who call it home. You’ll leave with a deeper appreciation for the warmth and resilience of its people and a desire to return and explore even more of this enchanting land. --- *Update: Unfortunately as of this time (June 2021) Myanmar is experiencing major political and civil unrest. Taken from the advice of friends on the ground there— I can not recommend traveling to Myanmar at the time of writing. Pray for Myanmar!* *Update 2: The political situation in Myanmar has escalated (July 2022). Travel is still not recommended.* *Update 3: As of 2025, some tourists have reported that travel is doable. However many governments still have do not travel advisories. DYOR.* --- ### Other Myanmar Guides: [The Top 3 Hidden Beaches of Myanmar: A Guide to Tizit, Grandfather, and Mergui](https://hes.npub.pro/post/1705254252735/) --- ### More from Hes: [Art](https://hes.npub.pro/tag/art/) [Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography/) [Writings](https://hes.npub.pro/tag/money/) --- *Originally Published June 15, 2021. Edited with Nostr friendly images on 1/5/2025*
@ 1cb14ab3:95d52462
2025-01-05 04:18:29*Stunning beaches, ancient temples as far as the eye can see, and lush, green mountainsides that will leave you in awe—Myanmar is a destination you NEED to add to your bucket list. This guide offers the perfect one-month itinerary to explore the hidden gems of this incredible country.*  --- ## The Itinerary #### Days 1-2: Fly into Yangon Airport. Settle in and explore the vibrant sights and flavors of the city. #### Day 3: Take an overnight bus south to the coastal city of Myeik. #### Days 4-8: Go island hopping around the Mergui Archipelago—remote beaches and untouched islands await. #### Day 9: Travel to Dawei. Find a cozy place to stay and relax for the evening. #### Days 10-13: Rent a motorcycle and explore the stunning Dawei Peninsula. Soak up the sun on pristine beaches. #### Day 14: Head to Hpa An. Check into a hotel and enjoy a sunset beer. #### Days 15-18: Discover the limestone mountains, caves, and farmlands of Hpa An. #### Day 19: Travel to Bagan. The journey may be bumpy, but the destination is worth it. #### Days 20-23: Explore the breathtaking temples of Bagan. Sunrise hot air balloon rides are a must. #### Day 24: Head to Lake Inle. Settle into your accommodation and dine by the water. #### Days 25-26: Cruise around Lake Inle by boat. Immerse yourself in the local culture and capture the iconic fishermen in action. #### Days 27-28: Visit Mandalay to experience city life from a Burmese perspective. #### Days 29-30: Return to Yangon for a final exploration before flying home. --- ## Days 1-2: Arrival in Yangon Myanmar's largest city is a bustling hub filled with shops, activities, and incredible food. The rapid development of this once-isolated country is evident everywhere you look. **If you are flying internationally:** Yangon will most likely be the cheapest and most easily accessible destination to begin the trip. **If you are coming from Thailand:** I would recommend altering the itinerary and going straight to Myeik via land border then working your way up the country from there. #### Bogyoke Aung San Market If shopping is your thing, this place is a haven for local treasures. Hundreds of stalls line the market and surrounding alleyways containing everything from art, sculptures, jewelry, antiquities, and fabrics. I spent a few hours here before jumping onto the nearby circular train for a loop around the city. There are a few small shops to get a bite to eat if you are hungry. Remember that this itinerary will land you back in Yangon at the end of the trip if you see something you want to buy and don’t feel like lugging it around for a month.  #### Yangon Circular Train Easily one of the most fascinating experiences of the trip is riding the Yangon Circular Train around the city for a true look at how the locals live. The train is old, slow, and packed with locals commuting to and from work. The doors are wide open, allowing you to hang your feet outside and soak in all of the sights afar. This is one of the best ways to get a true glimpse into the culture and day-to-day life of the Burmese people. Be sure to speak with a train operator before getting on to make sure the entire loop is operational. When I went, construction stopped the train about 45 minutes into the loop, forcing us to get a taxi back to the downtown area. The full loop will take over 2 hours to complete. On the train, you can find vendors and hawkers selling little things such as water, nuts, and fruit. I’d suggest eating before jumping on.  #### Shwedagon Pagoda Upon walking up the steep and lengthy stairway to the Shwedagon Pagoda lies Yangon’s most famous attraction. The 99-meter gold-coated pagoda can be seen all around the city but is best enjoyed up close. This is a must-visit during your time in the capital. I went about an hour before sunset and stayed well into the night. Sunset from the hill it sits atop is spectacular, and the contrast of the pagoda between day and night is striking. Make sure to bring socks and a bag, as shoes are not allowed, and you will need to carry them or leave them at the door. After visiting, you can take a short walk to the Sky Bar in the Yangon International Hotel overlooking the pagoda. This is a wonderful place to enjoy a nice dinner and drink, ideal for soaking up more of that luxurious golden pagoda.  --- ## Day 3: Bus to Myeik The longest stretch of the trip—but well worth the sights to come. I took a 22-hour overnight bus and opted for the slight upcharge to take the VIP bus. This option is absolutely worth it. Equipped with A/C, comfortable reclining seats, and stops for three meals, it was a cheaper alternative to the costly domestic flight from Yangon and allowed me to see much more of the country. I had a surprisingly good sleep and would do it again in a heartbeat. You can also fly directly to Myeik, but flights are infrequent and considerably more expensive. The bus I took arrived in Myeik around noon the next day, leaving me plenty of time to check into the hotel and wander around the city a bit before sunset. There weren’t many buses heading down here, so I’d recommend checking for tickets as early as possible when you arrive in Yangon. Alternatively, if you’re coming from Thailand, you can rearrange the itinerary and begin your Myanmar trip in Myeik by crossing from Thailand via bus at the land border.  --- ## Days 4-8: Island Hopping in Myeik The city of Myeik has no accessible beaches, so you’ll need to book an island-hopping tour to fully appreciate the surrounding Mergui Archipelago. While the city itself doesn’t offer much in terms of entertainment, the beaches and crystal-clear waters you’ll encounter on an island-hopping tour are truly unparalleled. Your trip to Myeik will be unforgettable and is an experience you shouldn’t miss. There are several travel companies offering island-hopping tours, ranging from single-day trips to 14-day excursions. While you can book ahead, I found it quite easy to arrange a trip through an agency in the city. I opted for a three-day, two-night tour with Life Seeing Tours, and it was fantastic. They provided food, tents, and transportation—just bring a swimsuit and a change of clothes, and you’re ready to spend a few nights exploring the islands.     --- ## Day 9: Bus to Dawei Another travel day! This time, you’ll take a shorter bus ride heading north to Dawei. The journey takes about six hours, and tickets can be purchased from one of the travel agencies in Myeik. From what I gathered, there’s only one bus per day on this route, and it departs early in the morning. Be prepared to wake up around 4 AM and make your way back to the same bus station where you arrived. It’s a good idea to arrange transportation to the station the night before—your hotel can help you book a ride for that morning. --- ## Days 10-13: Motorcycling the Dawei Peninsula Dawei boasts some of the most stunning coastlines and beaches in the country. While most of these beaches are only accessible by motorcycle, there are a few small bed-and-breakfast-style accommodations at the southern end of the peninsula that offer direct beach access. If you’d prefer not to travel 2–3 hours each day from the city, I recommend staying in that area. You can rent a motorcycle from several places in the city and ride down to the B&Bs near the beaches for an overnight stay. This approach lets you enjoy the remote, lush, and scenic motorcycle journey while avoiding the daily commute to the beaches.  #### Grandfather Beach Surrounded by mountains and vibrant orange dirt, getting here can be a bit tricky. You’ll need to navigate a steep, loose hill to reach the area. I recommend arriving near low tide, as the beach and surrounding shops flood around noon, making the descent a wet and challenging experience. Be prepared to remove your shoes and walk through knee-deep water to access the beach. This is one of the more popular spots for locals and was among the few beaches I visited that actually had people.  #### Tizit Beach When we arrived at Tizit Beach, there was no one else around except for the locals. The sand here is soft, and the ocean is pristine. A motorcycle is necessary to access this beach, but the breathtaking views from the mountain pass make the journey entirely worthwhile. The sand near the shore is firm enough to ride on, creating unforgettable moments of cruising along the beach at sunset.  --- ## Day 14: Bus to Hpa An One of the shorter bus rides on this trip, the fare is around $20, and it takes approximately 5 bumpy hours. Once you arrive in Hpa An, there are plenty of hostels and hotels to choose from. I booked mine on Hostelworld the night before, but you should have no trouble finding a place to stay on the day of your arrival if needed. --- ## Days 15-18: Hpa An: Farmland, Caves, and Mountains Hpa An offers a stark contrast to the beaches and cities encountered so far on the trip. Surrounded by towering limestone mountains and lush green farmland, the region has a peaceful, rural charm. There are several caves, lakes, and one of my favorite sunrise hikes of the journey. While I have a few recommendations and must-visit spots, Hpa An is best explored without a strict plan. A central theme of this trip has been the freedom of hopping on a motorcycle and riding wherever your heart desires.  #### Mount Zwegabin Sunrise Hike Hiking Mount Zwegabin for sunrise is a must-do during your time in Hpa An. The mountain is located a short ride from town, about 40 minutes by motorcycle. The hike to the summit took around 35 minutes at a brisk pace, so you’ll need to leave around 4 AM to catch the sunrise, depending on the season. The highlight of the hike is the final ascent up the floating stairs to reach the peak. Be sure to have your camera ready and take in the breathtaking views.  #### Kyauk Kalat Pagoda This is one of those places that leaves you in awe, wondering how such a unique landscape can exist. Easily one of the most unusual rock formations I’ve encountered, it’s a fantastic spot to watch the sunset. A winding staircase leads up the rock to the top of the temple, making it a great place to spend a couple of hours.  #### Saddar Cave Filled with bats, stunning limestone formations, and statues, this short cave walk provides a refreshing escape from the heat. The path takes about 20 minutes to explore, leading to a beautiful lake at the back. Grab a drink, relax for a while, and take a small paddle boat back to the entrance for a memorable experience.  --- ## Day 19: Bus to Bagan A travel day heading north. This part of the trip is hot, bumpy, and slow, so be prepared for a longer journey than expected. Bagan has plenty of hotels and hostels, but I’d recommend booking accommodations in advance, as it’s a popular tourist destination. You’ll need to purchase an entry ticket for the area, as it’s a protected national park, but the bus driver should assist in sorting it out before you enter the park. --- ## Days 20-23: Chasing Pagodas in Bagan Once you’ve settled into your accommodation in Bagan, the best way to explore the vast area is by pedal bike or scooter. All the scooters available for rent are electric, helping to reduce noise pollution—a refreshing change from the loud gas-powered vehicles you’ll be used to from the first half of your trip. There’s no right or wrong way to experience Bagan. The park is enormous, with thousands of pagodas scattered throughout. Most of them are open for exploration, with a few offering rooftop access (though that is being restricted more recently). You could spend weeks here and still not see all the pagodas up close. Bagan is divided into a new town and an old town—most of the backpacker-friendly hostels are located in Old Town. You’ll find a handful of restaurants, but I often ate at my hostel or from local food carts. Several hostels and hotels offer outdoor pools, which are a great perk, especially depending on the time of year you visit. I highly recommend simply wandering the area freely, but here are a few top pagodas and experiences not to miss during your time in Bagan.  #### Hot Air Ballooning The top attraction in Bagan is undoubtedly the daily hot air balloon tours. Almost everyone who experiences it claims it’s a must-do. I chose to watch from the ground, as the cost of a tour is quite expensive. If you decide to go for it, be sure to set aside a few hundred USD for the trip. From what I’ve heard, you’ll wake up around 4:30 AM and head to the take-off location, returning by around 9:00 AM.  #### Sunset Boat Cruise Be sure to spend at least one evening on a slow cruise down the Ayeyarwady River. It’s a wonderful way to enjoy distant views of some of the pagodas and relax after a long day of exploration. Several companies offer these cruises at very affordable prices. Our boat included snacks, drinks, and even alcohol. The trips range from half an hour to two hours. Book through your hotel for convenience.  #### The Big Three Temples With over a thousand pagodas to explore in Bagan, there are three main structures that hold significant importance to locals: Shwesandaw, Thatbyinnyu, and Shwezigon. Be sure to make time to visit these iconic pagodas during your trip—you’re likely to come across them without even trying.  --- ## Day 24: Bus to Kalaw Long-distance buses run the route multiple times a day, with the overnight option being the most popular. I recommend checking with a travel agent in Bagan to book your tickets before heading to the bus stop --- ## Day 25-26: Relaxing at Lake Inle These two days take us to the stunning Lake Inle, located just outside the city of Kalaw. Unfortunately, I wasn’t able to make it to Lake Inle during this trip, but everyone I spoke to highly recommended not missing it. The lake is known for its breathtaking scenery, traditional Intha stilt houses, and the unique leg-rowing fishermen. From what I’ve heard and seen through photos, the calm waters, floating gardens, and vibrant markets make Lake Inle a truly unforgettable destination. Huge thanks to my friend Toby for sharing those beautiful pictures and giving me a glimpse of what I missed!     --- ## Day 27-28: Mandalay City Mandalay is a fast-paced city with less tourism compared to other parts of the country. It offers a fascinating glimpse into the daily lives of the Burmese people, away from the crowds typically found in Yangon. There are several culturally significant monasteries and temples within the city limits, as well as vibrant markets perfect for shopping and exploring. Mandalay Hill is a great spot for a brisk hike and offers stunning views of the city and sunset on one of your nights. You could also visit the Mandalay Marionettes Theater to catch a local show showcasing Myanmar’s rich history and culture. As for me, I mainly wandered the city without specific destinations in mind. Since this is the last stop before returning to Yangon, you might not feel as inclined to spend too much time here, but there are definitely some interesting sights worth exploring.  --- ## Day 29-30: Return to Yangon The final two days of the trip are a return to where it all began. The bus from Mandalay to Yangon takes about 8 hours. Alternatively, Mandalay has a large international airport if you prefer to fly, depending on your next destination. If you return to Yangon, you’ll have plenty of time to revisit the markets and pick up any final souvenirs or trinkets you might want to take home. Enjoy these last couple of days, savor some delicious food, and take the time to reflect on the incredible month of experiences you’ve had.  --- ## Concluding Thoughts Your month-long journey through Myanmar is bound to be an unforgettable adventure, filled with stunning landscapes, rich culture, and warm hospitality. From the serene beaches of Ngapali to the ancient wonders of Bagan, and the tranquil beauty of Lake Inle to the bustling streets of Yangon and Mandalay, each destination offers its own unique charm and insight into Myanmar’s diverse culture. The highlights of your trip—exploring historic pagodas, witnessing breathtaking sunrises, and embracing the freedom of riding a motorcycle—are sure to stay with you. Myanmar’s blend of natural beauty, vibrant traditions, and friendly locals makes every moment special. Despite the occasional long and bumpy journeys, the sense of discovery and connection with the people and places makes the experience truly worthwhile. As you reflect on your journey, you’ll likely feel grateful for the memories, experiences, and the chance to explore a country that feels both timeless and unique. Myanmar’s beauty lies not just in its landscapes but in the people who call it home. You’ll leave with a deeper appreciation for the warmth and resilience of its people and a desire to return and explore even more of this enchanting land. --- *Update: Unfortunately as of this time (June 2021) Myanmar is experiencing major political and civil unrest. Taken from the advice of friends on the ground there— I can not recommend traveling to Myanmar at the time of writing. Pray for Myanmar!* *Update 2: The political situation in Myanmar has escalated (July 2022). Travel is still not recommended.* *Update 3: As of 2025, some tourists have reported that travel is doable. However many governments still have do not travel advisories. DYOR.* --- ### Other Myanmar Guides: [The Top 3 Hidden Beaches of Myanmar: A Guide to Tizit, Grandfather, and Mergui](https://hes.npub.pro/post/1705254252735/) --- ### More from Hes: [Art](https://hes.npub.pro/tag/art/) [Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography/) [Writings](https://hes.npub.pro/tag/money/) --- *Originally Published June 15, 2021. Edited with Nostr friendly images on 1/5/2025* @ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
@ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence. @ 1cb14ab3:95d52462
2025-01-02 05:57:05--- ## No. 1 - The Less Touristy "Bund"  The Bund is certainly a must-see if you are traveling to Shanghai for the first time - and it will be at the top of every travel guide out there, for good reason - there are equally as stunning alternatives away from the crowds. If you want to enjoy the skyline from a more relaxed perspective, consider the Pudong side of the river. There are parks, basketball courts, and green spaces along the riverbank for you to chill at and take in the sights. You can also hop on a ferry or a sightseeing boat to cross the river and admire the views from the renowned Bund. --- ## No. 2 - Walks Along Golden Street  This one is out in Gubei, a suburban area in the west of Shanghai. It may be a bit of a trek, but it is worth it if you are looking for a more relaxing and peaceful pedestrian street in the city. Golden Street, or Jinxiu Road, is a great place to walk a dog, grab an afternoon drink, or enjoy a romantic dinner with your loved one. While it may be a bit far from downtown, it makes for a great joyride on your scooter or bicycle. --- ## No. 3 - Moganshan Road Graffiti Wall  Moganshan Road is a gem for all things art. It is home to M50, the best art district in the city, where you will find dozens of galleries, studios, and workshops showcasing a wide range of art. There are also plenty of cool spots scattered around the area, particularly the graffiti wall. The wall is a welcome contrast to some of the drab and monotonous architecture found around the city; with colorful display of street art featuring various styles and themes. Stop by and admire the works of local and international artists, and even jump in to join them in adding your own mark. The wall is constantly evolving, so you can always find something new. --- ## No. 4 - Jiaotong University in the Fall  Easily one of the best spots in town for catching rows of bright yellow and red leaves. Jiaotong University is one of the oldest and most prestigious universities in China. The campus is located in Xuhui District and has a mix of Chinese and Western architectural styles to admire as well. Try to visit in late October or early November for the best leaf-peeping. You can walk along the tree-lined paths, set up a blanket in the field for a picnic, or simply take photos and enjoy the scenery. --- ## No. 5 - Day Drinking at Highline  Hands down one of the top five rooftop bars in the city, along with Bar Rouge, Kartel, and others; Highline is a go-to-spot that offers great views of the city and excellent food. Find it on the sixth floor of the Ascott Hotel in Huaihai Road in Xintiandi. Nothing beats a laid back Saturday afternoon at Highline. I prefer the views during the day, though it is equally as nice a night. Sip cocktails, wine, or beer, and enjoy the music and vibe. Highline is a perfect place to spend an afternoon. --- ### Additional Photos      --- #### Next Guide in the Series: [An Expats Guide to the Best Spots in Shanghai: 002](https://hes.npub.pro/post/1719708820357/) --- ### Find Me Elsewhere: [Website](https://hes.npub.pro/) [Art](https://hes.npub.pro/tag/art/) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography/) [Storefront](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06) --- *All images property of Hes. Originally published as an Instagram Guide on Feb. 02, 2021. Reworked and published on Nostr on Feb. 17, 2024.*
@ 1cb14ab3:95d52462
2025-01-02 05:57:05--- ## No. 1 - The Less Touristy "Bund"  The Bund is certainly a must-see if you are traveling to Shanghai for the first time - and it will be at the top of every travel guide out there, for good reason - there are equally as stunning alternatives away from the crowds. If you want to enjoy the skyline from a more relaxed perspective, consider the Pudong side of the river. There are parks, basketball courts, and green spaces along the riverbank for you to chill at and take in the sights. You can also hop on a ferry or a sightseeing boat to cross the river and admire the views from the renowned Bund. --- ## No. 2 - Walks Along Golden Street  This one is out in Gubei, a suburban area in the west of Shanghai. It may be a bit of a trek, but it is worth it if you are looking for a more relaxing and peaceful pedestrian street in the city. Golden Street, or Jinxiu Road, is a great place to walk a dog, grab an afternoon drink, or enjoy a romantic dinner with your loved one. While it may be a bit far from downtown, it makes for a great joyride on your scooter or bicycle. --- ## No. 3 - Moganshan Road Graffiti Wall  Moganshan Road is a gem for all things art. It is home to M50, the best art district in the city, where you will find dozens of galleries, studios, and workshops showcasing a wide range of art. There are also plenty of cool spots scattered around the area, particularly the graffiti wall. The wall is a welcome contrast to some of the drab and monotonous architecture found around the city; with colorful display of street art featuring various styles and themes. Stop by and admire the works of local and international artists, and even jump in to join them in adding your own mark. The wall is constantly evolving, so you can always find something new. --- ## No. 4 - Jiaotong University in the Fall  Easily one of the best spots in town for catching rows of bright yellow and red leaves. Jiaotong University is one of the oldest and most prestigious universities in China. The campus is located in Xuhui District and has a mix of Chinese and Western architectural styles to admire as well. Try to visit in late October or early November for the best leaf-peeping. You can walk along the tree-lined paths, set up a blanket in the field for a picnic, or simply take photos and enjoy the scenery. --- ## No. 5 - Day Drinking at Highline  Hands down one of the top five rooftop bars in the city, along with Bar Rouge, Kartel, and others; Highline is a go-to-spot that offers great views of the city and excellent food. Find it on the sixth floor of the Ascott Hotel in Huaihai Road in Xintiandi. Nothing beats a laid back Saturday afternoon at Highline. I prefer the views during the day, though it is equally as nice a night. Sip cocktails, wine, or beer, and enjoy the music and vibe. Highline is a perfect place to spend an afternoon. --- ### Additional Photos      --- #### Next Guide in the Series: [An Expats Guide to the Best Spots in Shanghai: 002](https://hes.npub.pro/post/1719708820357/) --- ### Find Me Elsewhere: [Website](https://hes.npub.pro/) [Art](https://hes.npub.pro/tag/art/) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography/) [Storefront](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06) --- *All images property of Hes. Originally published as an Instagram Guide on Feb. 02, 2021. Reworked and published on Nostr on Feb. 17, 2024.* @ 16d11430:61640947
2024-12-26 11:31:05For centuries, financial markets have been shackled by an archaic mindset rooted in Newtonian physics: "What goes up must come down." This belief has dominated the thinking of old-school fiat economists, who view the rise and fall of markets as a natural cycle of gravity-bound economics. But Bitcoin, the digital phoenix, was designed to defy this outdated paradigm. It isn't just an asset class or a currency—it's a revolution in financial physics, unshackling value from centralized control and rewriting the rules of money. The Fiat Fallacy: Gravity Economics Fiat systems are inherently cyclical, prone to inflation, manipulation, and collapse. Central banks print money endlessly, causing value to "come down" as purchasing power erodes. For fiat thinkers, this is unavoidable—a gravitational force they accept as immutable. Yet this mindset ignores Bitcoin’s game-changing properties: its hard cap of 21 million coins, decentralized consensus, and permissionless architecture. Bitcoin is fundamentally non-Newtonian. It doesn’t adhere to traditional financial laws because it isn't bound by the same forces of supply and control. Instead, it operates in a new paradigm: deflationary, transparent, and immune to political meddling. Bitcoin's Escape Velocity Bitcoin's dominance lies in its ability to achieve escape velocity. Unlike fiat currencies, which are constantly being pulled back by inflationary policies, Bitcoin is propelled by its scarcity, adoption, and network effects. Every halving event tightens the supply, creating an upward pressure that fiat systems can't replicate. And as global trust in traditional systems erodes, Bitcoin's gravitational pull grows stronger. This phenomenon is evident in the adoption curve. Institutions, governments, and individuals worldwide are recognizing Bitcoin as a superior store of value, an inflation hedge, and the ultimate form of financial sovereignty. The more participants enter the network, the more its value compounds, creating a virtuous cycle of exponential growth. Humiliating the Old Guard The fiat establishment—steeped in centuries of centralized control—has long dismissed Bitcoin as a bubble, a fad, or even a Ponzi scheme. Yet, year after year, Bitcoin rises from the ashes of their predictions. Its resilience, transparency, and provable scarcity expose the fragility and corruption of fiat systems. The ultimate humiliation for fiat thinkers is Bitcoin's ability to thrive in crises. Where traditional systems falter—be it through hyperinflation, bank failures, or geopolitical instability—Bitcoin becomes a lifeboat. It doesn’t just resist gravity; it flips the entire script. Fiat currencies are revealed as infinite-print illusions, while Bitcoin’s immutable ledger stands as the ultimate arbiter of truth and value. A New Financial Paradigm Bitcoin’s ascent is not merely about price; it’s about domination. It represents a shift from centralized control to individual empowerment, from opaque systems to transparent protocols, from inflationary theft to deflationary savings. It’s a financial singularity, an escape from the gravitational pull of outdated thinking. As Bitcoin continues its trajectory, the old world of "what goes up must come down" will look increasingly absurd. In its place, a new principle will reign: what’s decentralized cannot be stopped. Bitcoin isn’t just leaving Earth’s orbit; it’s becoming the financial universe’s North Star. So buckle up, because Bitcoin isn’t just going up—it’s transcending. And as it does, it will leave the Newtonian thinkers in the dust, staring in disbelief at the rocket that left them behind.
@ 16d11430:61640947
2024-12-26 11:31:05For centuries, financial markets have been shackled by an archaic mindset rooted in Newtonian physics: "What goes up must come down." This belief has dominated the thinking of old-school fiat economists, who view the rise and fall of markets as a natural cycle of gravity-bound economics. But Bitcoin, the digital phoenix, was designed to defy this outdated paradigm. It isn't just an asset class or a currency—it's a revolution in financial physics, unshackling value from centralized control and rewriting the rules of money. The Fiat Fallacy: Gravity Economics Fiat systems are inherently cyclical, prone to inflation, manipulation, and collapse. Central banks print money endlessly, causing value to "come down" as purchasing power erodes. For fiat thinkers, this is unavoidable—a gravitational force they accept as immutable. Yet this mindset ignores Bitcoin’s game-changing properties: its hard cap of 21 million coins, decentralized consensus, and permissionless architecture. Bitcoin is fundamentally non-Newtonian. It doesn’t adhere to traditional financial laws because it isn't bound by the same forces of supply and control. Instead, it operates in a new paradigm: deflationary, transparent, and immune to political meddling. Bitcoin's Escape Velocity Bitcoin's dominance lies in its ability to achieve escape velocity. Unlike fiat currencies, which are constantly being pulled back by inflationary policies, Bitcoin is propelled by its scarcity, adoption, and network effects. Every halving event tightens the supply, creating an upward pressure that fiat systems can't replicate. And as global trust in traditional systems erodes, Bitcoin's gravitational pull grows stronger. This phenomenon is evident in the adoption curve. Institutions, governments, and individuals worldwide are recognizing Bitcoin as a superior store of value, an inflation hedge, and the ultimate form of financial sovereignty. The more participants enter the network, the more its value compounds, creating a virtuous cycle of exponential growth. Humiliating the Old Guard The fiat establishment—steeped in centuries of centralized control—has long dismissed Bitcoin as a bubble, a fad, or even a Ponzi scheme. Yet, year after year, Bitcoin rises from the ashes of their predictions. Its resilience, transparency, and provable scarcity expose the fragility and corruption of fiat systems. The ultimate humiliation for fiat thinkers is Bitcoin's ability to thrive in crises. Where traditional systems falter—be it through hyperinflation, bank failures, or geopolitical instability—Bitcoin becomes a lifeboat. It doesn’t just resist gravity; it flips the entire script. Fiat currencies are revealed as infinite-print illusions, while Bitcoin’s immutable ledger stands as the ultimate arbiter of truth and value. A New Financial Paradigm Bitcoin’s ascent is not merely about price; it’s about domination. It represents a shift from centralized control to individual empowerment, from opaque systems to transparent protocols, from inflationary theft to deflationary savings. It’s a financial singularity, an escape from the gravitational pull of outdated thinking. As Bitcoin continues its trajectory, the old world of "what goes up must come down" will look increasingly absurd. In its place, a new principle will reign: what’s decentralized cannot be stopped. Bitcoin isn’t just leaving Earth’s orbit; it’s becoming the financial universe’s North Star. So buckle up, because Bitcoin isn’t just going up—it’s transcending. And as it does, it will leave the Newtonian thinkers in the dust, staring in disbelief at the rocket that left them behind. @ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence. The Philosophical Void of Fiat Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation. The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence. Theological Implications: Fiat and the Collapse of the Sacred Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger. This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect. Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests. Physics and the Infinite Growth Paradox Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility. In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself. Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level. Biology: The Fiat System and the Destruction of Human Health Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans. Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders. The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse. Finance as the Final Illusion At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses. This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality. As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems. The Ultimate Extermination In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being. To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
@ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence. The Philosophical Void of Fiat Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation. The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence. Theological Implications: Fiat and the Collapse of the Sacred Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger. This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect. Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests. Physics and the Infinite Growth Paradox Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility. In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself. Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level. Biology: The Fiat System and the Destruction of Human Health Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans. Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders. The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse. Finance as the Final Illusion At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses. This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality. As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems. The Ultimate Extermination In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being. To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace. @ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today. Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”. I’ve had my own stumbles on the way. In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear. In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”. It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”. As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it: > In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth. > > It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs. > > … > > The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases. While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis. What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship. And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well. The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me. Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something. **I was at least somewhat wrong.** My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU). I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak. **I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.** The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase. I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/). Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between. **But I was wrong.** When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road. My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm. While the price was irrelevant, it was all about buying and selling goods without permission or license. **Now I understand I was wrong.** Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack. What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.* The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time. Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later. In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague. My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse. This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016. **And I was wrong again.** Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike. While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable. Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces. In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships. This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not. Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation. **Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.** When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash. There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today. Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”. I’ve had my own stumbles on the way. In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear. In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”. It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”. As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it: > In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth. > > It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs. > > … > > The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases. While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis. What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship. And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well. The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me. Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something. **I was at least somewhat wrong.** My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU). I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak. **I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.** The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase. I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/). Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between. **But I was wrong.** When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road. My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm. While the price was irrelevant, it was all about buying and selling goods without permission or license. **Now I understand I was wrong.** Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack. What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.* The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time. Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later. In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague. My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse. This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016. **And I was wrong again.** Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike. While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable. Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces. In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships. This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not. Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation. **Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.** When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash. There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it. @ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入) 前回:[Nostrのカスタム絵文字の使い方](https://yakihonne.com/article/_@lokuyow.github.io/xVMTZxHcV_NWKuTbDBUYs) # 手順 1. 登録する画像を用意する 2. 画像をweb上にアップロードする 3. 絵文字セットに登録する ## 1. 登録する画像を用意する 以下のような方法で用意してください。 * 画像編集ソフト等を使って自分で作成する * 絵文字作成サイトを使う([絵文字ジェネレーター](https://emoji-gen.ninja/)、[MEGAMOJI](https://zk-phi.github.io/MEGAMOJI/) など) * フリー画像を使う([いらすとや](https://www.irasutoya.com/) など) ### データ量削減 Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。 データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。 以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト [toimg](https://toimg.kakechimaru.com/to-webp)) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる) ### その他 * 背景透過画像 * ダークモード、ライトモード両方で見やすい色 がおすすめです。 ## 2. 画像をweb上にアップロードする よく分からなければ [emojito](https://emojito.meme/) からのアップロードで問題ないです。 普段使っている画像アップロード先があるならそれでも構いません。 気になる方はアップロード先を適宜選んでください。 既に投稿されたカスタム絵文字の画像に対して - 削除も差し替えもできない → [emojito](https://emojito.meme/) など - 削除できるが差し替えはできない → [Gyazo](https://gyazo.com/)、[nostrcheck.me](https://nostrcheck.me/)など - 削除も差し替えもできる → [GitHub](https://github.com/) 、セルフホスティングなど これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。 どの方法でも新しく使われるカスタム絵文字を変更することは可能です。 同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。 ## 3. 絵文字セットに登録する [emojito](https://emojito.meme/) から登録します。 右上の**アイコン** → **+ New emoji set** から新規の絵文字セットを作成できます。   #### ① 絵文字セット名を入力 基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。 一度作った絵文字セットに後から絵文字を追加することもできます。 #### ② 画像をアップロードまたは画像URLを入力 emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。 その場合はファイル名を適当な英数字などに変更してください。 #### ③ 絵文字のショートコードを入力 ショートコードは絵文字を呼び出す時に使用する場合があります。 他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。 他と被りにくく長くなりすぎないショートコードが良いかもしれません。 ショートコードに使えるのは半角の英数字とアンダーバーのみです。 #### ④ 追加 **Add** を押してもまだ作成完了にはなりません。  一度に絵文字を複数登録できます。 最後に右上の **Save** を押すと作成完了です。  画面が切り替わるので、右側の **Options** から **Bookmark** を選択するとそのカスタム絵文字セットを自分で使えるようになります。 既存の絵文字セットを編集するには **Options** から **Edit** を選択します。 以上です。 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
@ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入) 前回:[Nostrのカスタム絵文字の使い方](https://yakihonne.com/article/_@lokuyow.github.io/xVMTZxHcV_NWKuTbDBUYs) # 手順 1. 登録する画像を用意する 2. 画像をweb上にアップロードする 3. 絵文字セットに登録する ## 1. 登録する画像を用意する 以下のような方法で用意してください。 * 画像編集ソフト等を使って自分で作成する * 絵文字作成サイトを使う([絵文字ジェネレーター](https://emoji-gen.ninja/)、[MEGAMOJI](https://zk-phi.github.io/MEGAMOJI/) など) * フリー画像を使う([いらすとや](https://www.irasutoya.com/) など) ### データ量削減 Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。 データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。 以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト [toimg](https://toimg.kakechimaru.com/to-webp)) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる) ### その他 * 背景透過画像 * ダークモード、ライトモード両方で見やすい色 がおすすめです。 ## 2. 画像をweb上にアップロードする よく分からなければ [emojito](https://emojito.meme/) からのアップロードで問題ないです。 普段使っている画像アップロード先があるならそれでも構いません。 気になる方はアップロード先を適宜選んでください。 既に投稿されたカスタム絵文字の画像に対して - 削除も差し替えもできない → [emojito](https://emojito.meme/) など - 削除できるが差し替えはできない → [Gyazo](https://gyazo.com/)、[nostrcheck.me](https://nostrcheck.me/)など - 削除も差し替えもできる → [GitHub](https://github.com/) 、セルフホスティングなど これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。 どの方法でも新しく使われるカスタム絵文字を変更することは可能です。 同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。 ## 3. 絵文字セットに登録する [emojito](https://emojito.meme/) から登録します。 右上の**アイコン** → **+ New emoji set** から新規の絵文字セットを作成できます。   #### ① 絵文字セット名を入力 基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。 一度作った絵文字セットに後から絵文字を追加することもできます。 #### ② 画像をアップロードまたは画像URLを入力 emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。 その場合はファイル名を適当な英数字などに変更してください。 #### ③ 絵文字のショートコードを入力 ショートコードは絵文字を呼び出す時に使用する場合があります。 他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。 他と被りにくく長くなりすぎないショートコードが良いかもしれません。 ショートコードに使えるのは半角の英数字とアンダーバーのみです。 #### ④ 追加 **Add** を押してもまだ作成完了にはなりません。  一度に絵文字を複数登録できます。 最後に右上の **Save** を押すと作成完了です。  画面が切り替わるので、右側の **Options** から **Bookmark** を選択するとそのカスタム絵文字セットを自分で使えるようになります。 既存の絵文字セットを編集するには **Options** から **Edit** を選択します。 以上です。 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md) @ 1cb14ab3:95d52462
2024-12-17 19:24:54*Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.* --- The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways. Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future. When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal. For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away. This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below: <aside> **Inflation Rate (%)** | **Purchasing Power Halving (Years)** - 2% | 35-40 years - 3% | 20-25 years - 4% | 15-20 years - 5% | 10-15 years - 6% | 7-12 years - 7% | 5-10 years - 8% | 4-8 years - 9% | 3-6 years - 10% | 2-5 years </aside> Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble. But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation? A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future. Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money. The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued. By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world. Bitcoin isn’t a bubble; it’s a beacon. --- ### More from Hes: [Art](https://hes.npub.pro/tag/art/) [Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography)
@ 1cb14ab3:95d52462
2024-12-17 19:24:54*Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.* --- The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways. Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future. When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal. For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away. This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below: <aside> **Inflation Rate (%)** | **Purchasing Power Halving (Years)** - 2% | 35-40 years - 3% | 20-25 years - 4% | 15-20 years - 5% | 10-15 years - 6% | 7-12 years - 7% | 5-10 years - 8% | 4-8 years - 9% | 3-6 years - 10% | 2-5 years </aside> Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble. But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation? A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future. Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money. The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued. By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world. Bitcoin isn’t a bubble; it’s a beacon. --- ### More from Hes: [Art](https://hes.npub.pro/tag/art/) [Store](https://plebeian.market/p/517d6542a081d61ecd8900ad9e2640290e2cf06f516c5e5f3edadfbde446bff4/stall/1db0cdfe0e39c4bd81b903902eeda74e6aa0f0b56e30851f327e6d0c292c5c06) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography) @ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install [NVapi](https://github.com/sammcj/NVApi) to monitor my GPUs in Home Assistant.  **NVApi** is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions. - **GPU Utilization Monitoring**: Utilization, memory usage, temperature, fan speed, and power consumption. - **Automated Power Limiting**: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally. - **Cross-GPU Coordination**: Total power budget applies across multiple GPUs in the same system. - **PCIe Link Speed Management**: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization. - **Home Assistant Integration**: Uses the built-in RESTful platform and template sensors. ## Getting the Data ``` sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpu ``` Response for a single GPU: ``` [ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ] ``` Response for multiple GPUs: ``` [ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ] ``` # Start at Boot Create `/etc/systemd/system/nvapi.service`: ``` [Unit] Description=Run NVapi After=network.target [Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible # Environment="GPU_TEMP_CHECK_INTERVAL=5" # Environment="GPU_TOTAL_POWER_CAP=400" # Environment="GPU_0_LOW_TEMP=40" # Environment="GPU_0_MEDIUM_TEMP=70" # Environment="GPU_0_LOW_TEMP_LIMIT=135" # Environment="GPU_0_MEDIUM_TEMP_LIMIT=120" # Environment="GPU_0_HIGH_TEMP_LIMIT=100" # Environment="GPU_1_LOW_TEMP=45" # Environment="GPU_1_MEDIUM_TEMP=75" # Environment="GPU_1_LOW_TEMP_LIMIT=140" # Environment="GPU_1_MEDIUM_TEMP_LIMIT=125" # Environment="GPU_1_HIGH_TEMP_LIMIT=110" [Install] WantedBy=multi-user.target ``` ## Home Assistant Add to Home Assistant `configuration.yaml` and restart HA (completely). For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds - platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ``` For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C" - platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C" ``` Basic entity card: ``` type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updated ``` # Ansible Role ``` --- - name: install go become: true package: name: golang-go state: present - name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true # go run main.go -port 9999 -rate 1 - name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service - name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install [NVapi](https://github.com/sammcj/NVApi) to monitor my GPUs in Home Assistant.  **NVApi** is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions. - **GPU Utilization Monitoring**: Utilization, memory usage, temperature, fan speed, and power consumption. - **Automated Power Limiting**: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally. - **Cross-GPU Coordination**: Total power budget applies across multiple GPUs in the same system. - **PCIe Link Speed Management**: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization. - **Home Assistant Integration**: Uses the built-in RESTful platform and template sensors. ## Getting the Data ``` sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpu ``` Response for a single GPU: ``` [ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ] ``` Response for multiple GPUs: ``` [ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ] ``` # Start at Boot Create `/etc/systemd/system/nvapi.service`: ``` [Unit] Description=Run NVapi After=network.target [Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible # Environment="GPU_TEMP_CHECK_INTERVAL=5" # Environment="GPU_TOTAL_POWER_CAP=400" # Environment="GPU_0_LOW_TEMP=40" # Environment="GPU_0_MEDIUM_TEMP=70" # Environment="GPU_0_LOW_TEMP_LIMIT=135" # Environment="GPU_0_MEDIUM_TEMP_LIMIT=120" # Environment="GPU_0_HIGH_TEMP_LIMIT=100" # Environment="GPU_1_LOW_TEMP=45" # Environment="GPU_1_MEDIUM_TEMP=75" # Environment="GPU_1_LOW_TEMP_LIMIT=140" # Environment="GPU_1_MEDIUM_TEMP_LIMIT=125" # Environment="GPU_1_HIGH_TEMP_LIMIT=110" [Install] WantedBy=multi-user.target ``` ## Home Assistant Add to Home Assistant `configuration.yaml` and restart HA (completely). For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds - platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ``` For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C" - platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C" ``` Basic entity card: ``` type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updated ``` # Ansible Role ``` --- - name: install go become: true package: name: golang-go state: present - name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true # go run main.go -port 9999 -rate 1 - name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service - name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ``` @ b8851a06:9b120ba1
2024-12-16 16:38:53Brett Scott’s recent [metaphor of Bitcoin as a wrestling gimmick](https://www.asomo.co/p/the-art-of-crypto-kayfabe), reliant on hype and dollar-dependence, reduces a groundbreaking monetary innovation to shallow theatrics. Let’s address his key missteps with hard facts. --- ### **1. Bitcoin Isn’t an Asset in the System—It’s the System** Scott claims Bitcoin competes with stocks, bonds, and gold in a financial "wrestling ring." This misrepresents Bitcoin’s purpose: it’s not an investment vehicle but a *decentralized monetary network*. Unlike assets, Bitcoin enables **permissionless global value transfer**, censorship resistance, and self-sovereign wealth storage—capabilities fiat currencies cannot match. **Fact:** Bitcoin processes over **$8 billion in daily transactions**, settling more value annually than PayPal and Venmo combined. It isn’t competing with assets but offering an alternative to the monetary system itself. --- ### **2. Volatility Is Growth, Not Failure** Scott critiques Bitcoin’s price volatility as evidence of its unsuitability as "money." However, volatility is a natural stage in the adoption of transformative technology. Bitcoin is scaling from niche use to global recognition. Its growing liquidity and adoption already make it more stable than fiat in inflationary economies. **Fact:** Bitcoin’s annualized volatility has decreased by **53% since 2013** and continues to stabilize as adoption rises. It’s the **best-performing asset of the last decade**, with an average annual ROI of **147%**—far outpacing stocks, gold, and real estate. As of February 2024, Bitcoin's volatility was lower than roughly 900 stocks in the S and P 1500 and 190 stocks in the S and P 500. It continues to stabilize as adoption rises, making it an increasingly attractive store of value. --- ### **3. Bitcoin’s Utility Extends Beyond Countertrade** Scott diminishes Bitcoin to a "countertrade token," reliant on its dollar price. This ignores Bitcoin’s primary functions: - **Medium of exchange:** Used in remittances, cross-border payments, and for the unbanked in Africa today (e.g., Ghana, Nigeria, Kenya). - **Store of value:** A hedge against inflation and failing fiat systems (e.g., Argentina, Lebanon, Turkey). - **Decentralized reserve asset:** Held by over **1,500 public and private institutions**, including Tesla, MicroStrategy, and nations like El Salvador. **Fact:** Lightning Network adoption has grown **1,500% in capacity since 2021**, enabling microtransactions and reducing fees—making Bitcoin increasingly viable for everyday use. As of December 2024, Sub-Saharan Africa accounts for 2.7% of global cryptocurrency transaction volume, with Nigeria ranking second worldwide in crypto adoption. This demonstrates Bitcoin's real-world utility beyond mere speculation. --- ### **4. Bitcoin Isn’t Controlled by the Dollar** Scott suggests Bitcoin strengthens the dollar system rather than challenging it. In truth, Bitcoin exists **outside the control of any nation-state**. It offers people in authoritarian regimes and hyperinflationary economies a lifeline when their local currencies fail. **Fact:** Over **70% of Bitcoin transactions occur outside the U.S.**, with adoption highest in countries like Nigeria, India, Venezuela, China, the USA and Ukraine—where the dollar isn’t dominant but government overreach and fiat collapse are. This global distribution shows Bitcoin's independence from dollar dominance. --- ### **5. Hype vs. Adoption** Scott mocks Bitcoin’s evangelists but fails to acknowledge its real-world traction. Bitcoin adoption isn’t driven by hype but by trustless, verifiable technology solving real-world problems. People don’t buy Bitcoin for "kayfabe"; they buy it for what it *does*. **Fact:** Bitcoin wallets reached **500 million globally** in 2023. El Salvador’s Chivo wallet onboarded **4 million users** (60% of the population) within a year—far from a gimmick in action. As of December 2024, El Salvador's Bitcoin portfolio has crossed $632 million in value, with an unrealized profit of $362 million, demonstrating tangible benefits beyond hype. --- ### **6. The Dollar’s Coercive Monopoly vs. Bitcoin’s Freedom** Scott defends fiat money as more than "just numbers," backed by state power. He’s correct: fiat relies on coercion, legal mandates, and inflationary extraction. Bitcoin, by contrast, derives value from **transparent scarcity** (capped at 21 million coins) and decentralized consensus, not military enforcement or political whims. **Fact:** Bitcoin’s inflation rate is just **1.8%**—lower than gold or the U.S. dollar—and will approach **0% by 2140**. No fiat currency can match this predictability. As of December 2024, Bitcoin processes an average of 441,944 transactions per day, showcasing its growing role as a global, permissionless monetary system free from centralized control. --- ### **Conclusion: The Revolution Is Real** Scott’s "wrestling gimmick" analogy trivializes Bitcoin’s purpose and progress. Bitcoin isn’t just a speculative asset—it’s the first truly decentralized, apolitical form of money. Whether as a hedge against inflation, a tool for financial inclusion, or a global settlement network, Bitcoin is transforming how we think about money. Dismiss it as a gimmick at your peril. The world doesn’t need another asset—it needs Bitcoin. > "**If you don't believe me or don't get it, I don't have time to try to convince you, sorry**." Once Satoshi said. **There is no second best.**
@ b8851a06:9b120ba1
2024-12-16 16:38:53Brett Scott’s recent [metaphor of Bitcoin as a wrestling gimmick](https://www.asomo.co/p/the-art-of-crypto-kayfabe), reliant on hype and dollar-dependence, reduces a groundbreaking monetary innovation to shallow theatrics. Let’s address his key missteps with hard facts. --- ### **1. Bitcoin Isn’t an Asset in the System—It’s the System** Scott claims Bitcoin competes with stocks, bonds, and gold in a financial "wrestling ring." This misrepresents Bitcoin’s purpose: it’s not an investment vehicle but a *decentralized monetary network*. Unlike assets, Bitcoin enables **permissionless global value transfer**, censorship resistance, and self-sovereign wealth storage—capabilities fiat currencies cannot match. **Fact:** Bitcoin processes over **$8 billion in daily transactions**, settling more value annually than PayPal and Venmo combined. It isn’t competing with assets but offering an alternative to the monetary system itself. --- ### **2. Volatility Is Growth, Not Failure** Scott critiques Bitcoin’s price volatility as evidence of its unsuitability as "money." However, volatility is a natural stage in the adoption of transformative technology. Bitcoin is scaling from niche use to global recognition. Its growing liquidity and adoption already make it more stable than fiat in inflationary economies. **Fact:** Bitcoin’s annualized volatility has decreased by **53% since 2013** and continues to stabilize as adoption rises. It’s the **best-performing asset of the last decade**, with an average annual ROI of **147%**—far outpacing stocks, gold, and real estate. As of February 2024, Bitcoin's volatility was lower than roughly 900 stocks in the S and P 1500 and 190 stocks in the S and P 500. It continues to stabilize as adoption rises, making it an increasingly attractive store of value. --- ### **3. Bitcoin’s Utility Extends Beyond Countertrade** Scott diminishes Bitcoin to a "countertrade token," reliant on its dollar price. This ignores Bitcoin’s primary functions: - **Medium of exchange:** Used in remittances, cross-border payments, and for the unbanked in Africa today (e.g., Ghana, Nigeria, Kenya). - **Store of value:** A hedge against inflation and failing fiat systems (e.g., Argentina, Lebanon, Turkey). - **Decentralized reserve asset:** Held by over **1,500 public and private institutions**, including Tesla, MicroStrategy, and nations like El Salvador. **Fact:** Lightning Network adoption has grown **1,500% in capacity since 2021**, enabling microtransactions and reducing fees—making Bitcoin increasingly viable for everyday use. As of December 2024, Sub-Saharan Africa accounts for 2.7% of global cryptocurrency transaction volume, with Nigeria ranking second worldwide in crypto adoption. This demonstrates Bitcoin's real-world utility beyond mere speculation. --- ### **4. Bitcoin Isn’t Controlled by the Dollar** Scott suggests Bitcoin strengthens the dollar system rather than challenging it. In truth, Bitcoin exists **outside the control of any nation-state**. It offers people in authoritarian regimes and hyperinflationary economies a lifeline when their local currencies fail. **Fact:** Over **70% of Bitcoin transactions occur outside the U.S.**, with adoption highest in countries like Nigeria, India, Venezuela, China, the USA and Ukraine—where the dollar isn’t dominant but government overreach and fiat collapse are. This global distribution shows Bitcoin's independence from dollar dominance. --- ### **5. Hype vs. Adoption** Scott mocks Bitcoin’s evangelists but fails to acknowledge its real-world traction. Bitcoin adoption isn’t driven by hype but by trustless, verifiable technology solving real-world problems. People don’t buy Bitcoin for "kayfabe"; they buy it for what it *does*. **Fact:** Bitcoin wallets reached **500 million globally** in 2023. El Salvador’s Chivo wallet onboarded **4 million users** (60% of the population) within a year—far from a gimmick in action. As of December 2024, El Salvador's Bitcoin portfolio has crossed $632 million in value, with an unrealized profit of $362 million, demonstrating tangible benefits beyond hype. --- ### **6. The Dollar’s Coercive Monopoly vs. Bitcoin’s Freedom** Scott defends fiat money as more than "just numbers," backed by state power. He’s correct: fiat relies on coercion, legal mandates, and inflationary extraction. Bitcoin, by contrast, derives value from **transparent scarcity** (capped at 21 million coins) and decentralized consensus, not military enforcement or political whims. **Fact:** Bitcoin’s inflation rate is just **1.8%**—lower than gold or the U.S. dollar—and will approach **0% by 2140**. No fiat currency can match this predictability. As of December 2024, Bitcoin processes an average of 441,944 transactions per day, showcasing its growing role as a global, permissionless monetary system free from centralized control. --- ### **Conclusion: The Revolution Is Real** Scott’s "wrestling gimmick" analogy trivializes Bitcoin’s purpose and progress. Bitcoin isn’t just a speculative asset—it’s the first truly decentralized, apolitical form of money. Whether as a hedge against inflation, a tool for financial inclusion, or a global settlement network, Bitcoin is transforming how we think about money. Dismiss it as a gimmick at your peril. The world doesn’t need another asset—it needs Bitcoin. > "**If you don't believe me or don't get it, I don't have time to try to convince you, sorry**." Once Satoshi said. **There is no second best.** @ 2f5de000:2f9bcef1
2024-12-15 16:44:53This Week I immersed myself in Bitcoin from multiple angles-technical, societal and personal. The journey included a marathon 32-hours of listening to [Rabbit Hole Recap (RHR)](https://fountain.fm/show/VDaMppQRUBZioj2XkaLn), an essential resource for Bitcoin insights. It's worth noting that I started from the begining and plan to make my way through the whole catalogue. Marty and Matt's timestamps, along with contributions from their guests, served as my roadmap. Using Fountain to stream, I also streamed sats-a small but extraordinary feature that allows users to stacks sats while compensating cretors directly through fractional donations. ## Revisiting Speculative Attack by Pierre Rochard (2014) Now that [*Speculative Attack Season 2*](https://nakamotoinstitute.org/mempool/speculative-attack-season-2/) *(which I've not read yet)* has been released. I took the time to read Pierre Rochards influential essay, [*Speculative Attack*](https://nakamotoinstitute.org/mempool/speculative-attack/) and reflected on its timeless insights. Rochard argues that Bitcoin adoption isn't dependent on technological advancements or consumer preferences, but on economic realities. As fiat currencies weaken, Bitcoin won't enter the mainstream by persuasion but by necessity. Critics continue to underestimate Bitcoin's inevitability due to their fiat biases and lack of financial insight. This year alone, mainstream media has been compelled to discuss Bitcoin-notably to Trump's endorsement of 'crypto.' Despite their attempts to shape narratives to suit their ideal visions, they've had no choice but to engage with Bitcoin's growing influence.\ \ As Parker aptly puts it 'Gradually, The Suddenly' ## Wassabi Wallet and the Privacy Imperative An RHR interview (from early in the catalogue) with guest Adam Ficsor, CTO and Co-founder of Wassabi Wallet, sparked a deeper consideration of my digital footprint. Like many, I've spent years online neglecting privacy in favour of convenience. The discussion on CoinJoins reminded me of the importance of prioritising privacy, not just romanticising it. Improving operational security (opsec) is now a personal focus. Resources like Jameson's *Cypherpunk Cogitations* and the Bitcoin Optech newsletter offer valuable guidance. While I've exercised caution, I recognise a need to address my laziness with opsec and take meaningful steps to protect my privacy. Time will reveal the results of these efforts. ## Caribbean Slavery amd Centralised Platforms While exploring historical systems of control, I delved into the brutal realities of [New World slavery in the British Caribbean](https://aeon.co/ideas/how-did-slaveholders-in-the-caribbean-maintain-control). Enslaved elites, like drivers, were granted limited privileges to maintain order, creating divisions within the community. This divide-and-rule strategy highlights the fragility of oppressive frameworks, which began to crumble with events like the Hatian Revolution and humanitarian activism. Interestingly, similar dynamics are visible with centralised plaforms like Twitter, LinkedIn, and Instagram. Verified accounts (the "blue checks") act as mordern day 'elites' with perceived freedoms. However, their autonomy is limited by the platforms centralised authority. Challenging the rules risks censorship and cancellation, proving their freedom is an illusion subject to the will of their overseers. Enhancing the argument further for protocols like Nostr to help people win back their freedoms.
@ 2f5de000:2f9bcef1
2024-12-15 16:44:53This Week I immersed myself in Bitcoin from multiple angles-technical, societal and personal. The journey included a marathon 32-hours of listening to [Rabbit Hole Recap (RHR)](https://fountain.fm/show/VDaMppQRUBZioj2XkaLn), an essential resource for Bitcoin insights. It's worth noting that I started from the begining and plan to make my way through the whole catalogue. Marty and Matt's timestamps, along with contributions from their guests, served as my roadmap. Using Fountain to stream, I also streamed sats-a small but extraordinary feature that allows users to stacks sats while compensating cretors directly through fractional donations. ## Revisiting Speculative Attack by Pierre Rochard (2014) Now that [*Speculative Attack Season 2*](https://nakamotoinstitute.org/mempool/speculative-attack-season-2/) *(which I've not read yet)* has been released. I took the time to read Pierre Rochards influential essay, [*Speculative Attack*](https://nakamotoinstitute.org/mempool/speculative-attack/) and reflected on its timeless insights. Rochard argues that Bitcoin adoption isn't dependent on technological advancements or consumer preferences, but on economic realities. As fiat currencies weaken, Bitcoin won't enter the mainstream by persuasion but by necessity. Critics continue to underestimate Bitcoin's inevitability due to their fiat biases and lack of financial insight. This year alone, mainstream media has been compelled to discuss Bitcoin-notably to Trump's endorsement of 'crypto.' Despite their attempts to shape narratives to suit their ideal visions, they've had no choice but to engage with Bitcoin's growing influence.\ \ As Parker aptly puts it 'Gradually, The Suddenly' ## Wassabi Wallet and the Privacy Imperative An RHR interview (from early in the catalogue) with guest Adam Ficsor, CTO and Co-founder of Wassabi Wallet, sparked a deeper consideration of my digital footprint. Like many, I've spent years online neglecting privacy in favour of convenience. The discussion on CoinJoins reminded me of the importance of prioritising privacy, not just romanticising it. Improving operational security (opsec) is now a personal focus. Resources like Jameson's *Cypherpunk Cogitations* and the Bitcoin Optech newsletter offer valuable guidance. While I've exercised caution, I recognise a need to address my laziness with opsec and take meaningful steps to protect my privacy. Time will reveal the results of these efforts. ## Caribbean Slavery amd Centralised Platforms While exploring historical systems of control, I delved into the brutal realities of [New World slavery in the British Caribbean](https://aeon.co/ideas/how-did-slaveholders-in-the-caribbean-maintain-control). Enslaved elites, like drivers, were granted limited privileges to maintain order, creating divisions within the community. This divide-and-rule strategy highlights the fragility of oppressive frameworks, which began to crumble with events like the Hatian Revolution and humanitarian activism. Interestingly, similar dynamics are visible with centralised plaforms like Twitter, LinkedIn, and Instagram. Verified accounts (the "blue checks") act as mordern day 'elites' with perceived freedoms. However, their autonomy is limited by the platforms centralised authority. Challenging the rules risks censorship and cancellation, proving their freedom is an illusion subject to the will of their overseers. Enhancing the argument further for protocols like Nostr to help people win back their freedoms. @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona? Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità. La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo? La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso? La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli? Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare. ### Metafore per l’interazione Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso. La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito. Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli. Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer. ### Usare un’IA come un computer Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer. Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona: - **Scoperta.** Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini. - **Efficienza.** La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente. A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio. ### Una bicicletta della mente proteiforme La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te. Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente. Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose. Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo. La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare. ### Un nuovo paradigma per l’informatica? I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità. All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale. Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle. Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi? Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona? Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità. La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo? La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso? La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli? Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare. ### Metafore per l’interazione Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso. La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito. Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli. Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer. ### Usare un’IA come un computer Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer. Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona: Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini. Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente. A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio. ### Una bicicletta della mente proteiforme La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te. Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente. Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose. Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo. La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare. ### Un nuovo paradigma per l’informatica? I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità. All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale. Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle. Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi? Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo! Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona? Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità. La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo? La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso? La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli? Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare. ### Metafore per l’interazione Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso. La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito. Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli. Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer. ### Usare un’IA come un computer Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer. Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona: - **Scoperta.** Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini. - **Efficienza.** La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente. A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio. ### Una bicicletta della mente proteiforme La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te. Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente. Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose. Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo. La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare. ### Un nuovo paradigma per l’informatica? I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità. All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale. Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle. Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi? Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona? Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità. La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo? La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso? La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli? Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare. ### Metafore per l’interazione Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso. La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito. Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli. Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer. ### Usare un’IA come un computer Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer. Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona: Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini. Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente. A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio. ### Una bicicletta della mente proteiforme La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te. Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente. Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose. Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo. La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare. ### Un nuovo paradigma per l’informatica? I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità. All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale. Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle. Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi? Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo! Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html @ dd664d5e:5633d319
2024-12-14 15:25:56 Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.  It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).  That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.  Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.  The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.  Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.  They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask. They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.  As an interesting aside: The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
@ dd664d5e:5633d319
2024-12-14 15:25:56 Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.  It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).  That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.  Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.  The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.  Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.  They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask. They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.  As an interesting aside: The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter. @ 4c96d763:80c3ee30
2024-12-14 08:11:29# Changes ## Ken Sedgwick (1): - android: misc fixes for android ## William Casarin (14): - theme: fallback theme should be dark - note: add copy note json - Introducing Damus Notedeck: a nostr browser - android: fix issues due to rearchitecture - lockfile: update - tests: add --testrunner flag so that column tests dont fail on startup - windows: amd64 installer - osx: update bundle name - rpm: fix rpm build - android: change apk name to Notedeck - deb: add name so package works again - enostr: update ewebsock - nostrdb: update to fix profile queries - Fix notes note updating in profile view ## kernelkind (3): - theme: persist across app close - Revert "move login logic from promise to async fns" - deps: remove reqwest pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/1e0228e396367ddbdb3855e5622e1cf550e56782.html)
@ 4c96d763:80c3ee30
2024-12-14 08:11:29# Changes ## Ken Sedgwick (1): - android: misc fixes for android ## William Casarin (14): - theme: fallback theme should be dark - note: add copy note json - Introducing Damus Notedeck: a nostr browser - android: fix issues due to rearchitecture - lockfile: update - tests: add --testrunner flag so that column tests dont fail on startup - windows: amd64 installer - osx: update bundle name - rpm: fix rpm build - android: change apk name to Notedeck - deb: add name so package works again - enostr: update ewebsock - nostrdb: update to fix profile queries - Fix notes note updating in profile view ## kernelkind (3): - theme: persist across app close - Revert "move login logic from promise to async fns" - deps: remove reqwest pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/1e0228e396367ddbdb3855e5622e1cf550e56782.html) @ 1c19eb1a:e22fb0bc
2024-12-12 19:42:39I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android! Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet. Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review. The application can be installed through the [Google Play Store](https://play.google.com/store/apps/details?id=net.primal.android&hl=en_US), Zapstore, or by downloading it directly from Primal's [GitHub](https://github.com/PrimalHQ/primal-android-app/releases/). This review is current as of Primal Android version 2.0.21. In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.  ## Overall Impression Score: **3.8** / 5 Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet. Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions. Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5. Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging. ## Features Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience. ### Home Feed By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.  Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection. Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.  ### Interacting With Notes Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note. Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.  Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂. It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one. Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that. ### Post Creation Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.  Your device's default keyboard loads immediately, and the you can start typing away. There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post. There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.  This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle. Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results. Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen. ### Feed Selector and Marketplace Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.  The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.  Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app. One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again. This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use. Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen. The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed. I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead. ### Long-Form "Reads" Feed A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles. This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.  Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor. Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks. While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client. Primal Web:  Primal Android:  ### The Explore Tab Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones! The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material. Indeed, it does not appear that filters for sensitive content are available in Primal for ***any*** feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.  The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content. This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit. The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in. If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag. The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice. Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with. ### Built-In Wallet While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.  Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users. Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is ***not*** intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried. In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know. Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet. Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are ***fast***. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client. One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed. Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration. ### Advanced Search Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible. Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar. As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.  You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery. The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more. ## Can My Grandma Use It? Score: **4.8** / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square. To begin with, the onboarting experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."  From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out. At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.  That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics. Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all. The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users. We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing. Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so. ## How do UI look? Score: **4.9** / 5 Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me ***want*** to use it.  It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding. First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.  The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.  Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.      At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app. This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.  ## Log In Options Score: **1** / 5 Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications. This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they ***are you*** on Nostr for all intents and purposes. This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users. That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below: nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl No word yet on whether this will be Android signer or remote signer support, or both. This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users. ## Zap Integration Score: **4.8** / 5 As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption. But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.  How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history. The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.  An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet. ## Content Discovery Score: **4.8** / 5 Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats. First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking. Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker. Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab. ## Relay Management Score: **2.5** / 5 For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect. However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on [nostr.watch](https://nostr.watch). I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs. That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.  However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay. One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice. By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address. ## Current Users' Questions The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0: nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client. nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though. nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to ***only*** show replies, but there is no corresponding filter to only show original notes. nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6 Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile. nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque. nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future. nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6 Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though. nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it. There is good news on this front, though: nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh ## Wrap Up All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary. There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release. So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments. I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows. Thank you for reading! PV 🤙
@ 1c19eb1a:e22fb0bc
2024-12-12 19:42:39I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android! Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet. Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review. The application can be installed through the [Google Play Store](https://play.google.com/store/apps/details?id=net.primal.android&hl=en_US), Zapstore, or by downloading it directly from Primal's [GitHub](https://github.com/PrimalHQ/primal-android-app/releases/). This review is current as of Primal Android version 2.0.21. In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.  ## Overall Impression Score: **3.8** / 5 Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet. Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions. Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5. Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging. ## Features Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience. ### Home Feed By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.  Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection. Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.  ### Interacting With Notes Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note. Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.  Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂. It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one. Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that. ### Post Creation Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.  Your device's default keyboard loads immediately, and the you can start typing away. There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post. There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.  This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle. Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results. Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen. ### Feed Selector and Marketplace Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.  The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.  Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app. One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again. This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use. Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen. The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed. I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead. ### Long-Form "Reads" Feed A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles. This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.  Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor. Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks. While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client. Primal Web:  Primal Android:  ### The Explore Tab Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones! The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material. Indeed, it does not appear that filters for sensitive content are available in Primal for ***any*** feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.  The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content. This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit. The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in. If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag. The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice. Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with. ### Built-In Wallet While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.  Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users. Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is ***not*** intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried. In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know. Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet. Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are ***fast***. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client. One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed. Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration. ### Advanced Search Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible. Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar. As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.  You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery. The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more. ## Can My Grandma Use It? Score: **4.8** / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square. To begin with, the onboarting experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."  From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out. At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.  That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics. Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all. The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users. We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing. Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so. ## How do UI look? Score: **4.9** / 5 Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me ***want*** to use it.  It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding. First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.  The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.  Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.      At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app. This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.  ## Log In Options Score: **1** / 5 Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications. This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they ***are you*** on Nostr for all intents and purposes. This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users. That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below: nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl No word yet on whether this will be Android signer or remote signer support, or both. This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users. ## Zap Integration Score: **4.8** / 5 As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption. But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.  How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history. The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.  An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet. ## Content Discovery Score: **4.8** / 5 Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats. First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking. Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker. Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab. ## Relay Management Score: **2.5** / 5 For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect. However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on [nostr.watch](https://nostr.watch). I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs. That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.  However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay. One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice. By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address. ## Current Users' Questions The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0: nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client. nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though. nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to ***only*** show replies, but there is no corresponding filter to only show original notes. nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6 Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile. nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque. nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future. nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6 Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though. nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it. There is good news on this front, though: nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh ## Wrap Up All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary. There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release. So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments. I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows. Thank you for reading! PV 🤙 @ e83b66a8:b0526c2b
2024-12-11 09:20:56Can I suggest you read my book, it will tell you a lot. It is important you understand what Bitcoin is before you invest anything into it. https://www.amazon.co.uk/dp/B0CLJP6R3F/ Firstly, Bitcoin is not like anything else you have ever experienced in your life. Everything else is based on trust and there is a higher authority you can always turn to. If you loose access to your bank account, you can walk in to a branch with your ID papers and within half an hour or so, your account access will be restored by them. The bank control your account and the money held within it. If you loose your passport or driving license, the government can issue you new ones. They control your identity. If you get locked out of your house, you can call a locksmith and they will break in, legally, for you. Bitcoin is different, it is permissionless and trustless. Nobody can stop you spending your money and you can send it to anyone anywhere in the world instantly without having to trust a third party to authorise payment for you. By that same token, if you make a mistake and send it to the wrong address or if you lose the keys that secure your Bitcoin, it is gone, nobody can help you. You need to understand and be comfortable with that. As for Bitcoin as a store of value, this is the first stage that all new Bitcoiners go through, but if you do it properly, it will eventually be the least significant feature. However, as for Bitcoin price cycles. Every 4 years the supply is automatically halved. This happened on the 20th April this year, you probably saw we were in Warsaw at a halving party. It happened at 3:09am European time, so we were asleep. Nothing actually happens for around 6 months of the halving, but from 6 - 18 months after the halving, the price rises significantly to adapt to the new supply and scarcity. So, from the start of November the price has started to rise and will continue to do so in a saw tooth pattern for around the next year. The price rise often overshoots the new natural price level and so expect a crash around the end of next year, it will be significant and will take a year or so to recover, but will eventually settle to a new price. In 4 years time, around April 2028, the cycle will happen again. Bitcoin is not a short term investment, don’t invest unless you are prepared to hold for a minimum of 4 years. Holding bitcoin for 8 years can produce generational wealth. The three core tenets of Bitcoin are: Not your keys, not your coins - in other words, don’t leave them on exchanges Don’t trust, verify - which leads to: Do your own research Study Bitcoin, it will give you back far more than you can imagine.
@ e83b66a8:b0526c2b
2024-12-11 09:20:56Can I suggest you read my book, it will tell you a lot. It is important you understand what Bitcoin is before you invest anything into it. https://www.amazon.co.uk/dp/B0CLJP6R3F/ Firstly, Bitcoin is not like anything else you have ever experienced in your life. Everything else is based on trust and there is a higher authority you can always turn to. If you loose access to your bank account, you can walk in to a branch with your ID papers and within half an hour or so, your account access will be restored by them. The bank control your account and the money held within it. If you loose your passport or driving license, the government can issue you new ones. They control your identity. If you get locked out of your house, you can call a locksmith and they will break in, legally, for you. Bitcoin is different, it is permissionless and trustless. Nobody can stop you spending your money and you can send it to anyone anywhere in the world instantly without having to trust a third party to authorise payment for you. By that same token, if you make a mistake and send it to the wrong address or if you lose the keys that secure your Bitcoin, it is gone, nobody can help you. You need to understand and be comfortable with that. As for Bitcoin as a store of value, this is the first stage that all new Bitcoiners go through, but if you do it properly, it will eventually be the least significant feature. However, as for Bitcoin price cycles. Every 4 years the supply is automatically halved. This happened on the 20th April this year, you probably saw we were in Warsaw at a halving party. It happened at 3:09am European time, so we were asleep. Nothing actually happens for around 6 months of the halving, but from 6 - 18 months after the halving, the price rises significantly to adapt to the new supply and scarcity. So, from the start of November the price has started to rise and will continue to do so in a saw tooth pattern for around the next year. The price rise often overshoots the new natural price level and so expect a crash around the end of next year, it will be significant and will take a year or so to recover, but will eventually settle to a new price. In 4 years time, around April 2028, the cycle will happen again. Bitcoin is not a short term investment, don’t invest unless you are prepared to hold for a minimum of 4 years. Holding bitcoin for 8 years can produce generational wealth. The three core tenets of Bitcoin are: Not your keys, not your coins - in other words, don’t leave them on exchanges Don’t trust, verify - which leads to: Do your own research Study Bitcoin, it will give you back far more than you can imagine. @ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night. I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case. We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money. The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially). The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines. Part of that battle is self custody, part is tax and part are the money transmitting laws. Roger’s case is also being used as a weapon of fear. I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so. Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time. This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years. This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
@ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night. I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case. We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money. The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially). The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines. Part of that battle is self custody, part is tax and part are the money transmitting laws. Roger’s case is also being used as a weapon of fear. I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so. Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time. This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years. This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification. @ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible. We model-directed graphs Also, graphs of entities We even model hypergraphs Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge. So why do we need metagraphs, and what kind of challenge could they help us to solve? - complex and nested event and temporal context and temporal relations as edges - multi-mode and multilingual knowledge - human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks ## MetaGraphs A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context. Also, in some cases, edges could be referenced as nodes. This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs. ## Graph Basics - A standard **graph** has a set of **nodes** (or vertices) and **edges** (connections between nodes). - Edges are generally simple and typically represent a binary relationship between two nodes. - For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes). ## Hypergraph - A **hypergraph** extends the concept of an edge by allowing it to connect any number of nodes, not just two. - Each connection, called a **hyperedge**, can link multiple nodes. - This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation. - Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge. ## Metagraph - A **metagraph** allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures. - In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph. - This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship. ## Named Graphs and Graph of Graphs As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem. If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.  The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature. It looks complex, but it is not so hard to model it with a slight modification of a directed graph. So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you  Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free ## Meta Graphs in Relational Model Let’s try to make several attempts to model different meta-graphs with some constraints. ## Directed Metagraph where edges are not used as nodes and could not contain subgraphs  In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases. ## Directed Metagraph where edges are not used as nodes and could contain subgraphs  Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert. I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case. ## Directed Metagraph where edges are used as nodes and could contain subgraphs As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.  A full-scale metagraph model is way too complex for a relational database. So we need a better model. Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs. Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose.
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible. We model-directed graphs Also, graphs of entities We even model hypergraphs Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge. So why do we need metagraphs, and what kind of challenge could they help us to solve? - complex and nested event and temporal context and temporal relations as edges - multi-mode and multilingual knowledge - human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks ## MetaGraphs A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context. Also, in some cases, edges could be referenced as nodes. This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs. ## Graph Basics - A standard **graph** has a set of **nodes** (or vertices) and **edges** (connections between nodes). - Edges are generally simple and typically represent a binary relationship between two nodes. - For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes). ## Hypergraph - A **hypergraph** extends the concept of an edge by allowing it to connect any number of nodes, not just two. - Each connection, called a **hyperedge**, can link multiple nodes. - This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation. - Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge. ## Metagraph - A **metagraph** allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures. - In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph. - This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship. ## Named Graphs and Graph of Graphs As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem. If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.  The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature. It looks complex, but it is not so hard to model it with a slight modification of a directed graph. So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you  Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free ## Meta Graphs in Relational Model Let’s try to make several attempts to model different meta-graphs with some constraints. ## Directed Metagraph where edges are not used as nodes and could not contain subgraphs  In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases. ## Directed Metagraph where edges are not used as nodes and could contain subgraphs  Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert. I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case. ## Directed Metagraph where edges are used as nodes and could contain subgraphs As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.  A full-scale metagraph model is way too complex for a relational database. So we need a better model. Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs. Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. @ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans. ## The Neurosymbolic Approach: What It Means ? Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning. While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in. ## Symbolic Calculations and the Early Vision of AI If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like **Lisp** emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations. ## Lisp: The Earlier AI-Language **Lisp**, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.” Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches. ## Prolog: Formal Logic and Deductive Reasoning In the 1970s, **Prolog** was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning. Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s. The language is declarative in nature, meaning that you define the problem, and Prolog figures out **how** to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved. ## Solvers and Their Role in Complementing LLMs One of the most powerful features of **Prolog** and similar logic-based systems is their use of **solvers**. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning. For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a **solver** can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers. Solvers are also ideal for handling **constraint satisfaction problems** — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone. By integrating **neurosymbolic methods** that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints. ## Graph of Rules for Enhanced Reasoning Another powerful concept that complements LLMs is using a **graph of rules**. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge. In a **graph of rules**, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust. For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses. Graphs of rules also enable **modular reasoning**, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of **neural fluency** with **rule-based structure** gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical. By implementing a graph of rules, LLMs are empowered to perform **deductive reasoning** alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence. ## Enhancing LLMs with Symbolic Reasoning Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where **neurosymbolic approaches** shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks. **Personal Knowledge Graphs (PKGs)** come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers. Imagine combining an LLM with a **graph of rules** that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using **deductive databases** to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving. ## My Research on Deductive Databases and Knowledge Graphs I recently did some research on modeling **knowledge graphs using deductive databases**, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning. **Prolog** and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a **graph of rules** that governs how relationships are formed or how logical deductions can be performed. The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence. ## Why It Matters for LLM Employment Using **neurosymbolic RAG (retrieval-augmented generation)** in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules. This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of **neural fluency** with **symbolic accuracy and deductive power** is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems. Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate! Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans. ## The Neurosymbolic Approach: What It Means ? Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning. While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in. ## Symbolic Calculations and the Early Vision of AI If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like **Lisp** emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations. ## Lisp: The Earlier AI-Language **Lisp**, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.” Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches. ## Prolog: Formal Logic and Deductive Reasoning In the 1970s, **Prolog** was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning. Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s. The language is declarative in nature, meaning that you define the problem, and Prolog figures out **how** to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved. ## Solvers and Their Role in Complementing LLMs One of the most powerful features of **Prolog** and similar logic-based systems is their use of **solvers**. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning. For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a **solver** can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers. Solvers are also ideal for handling **constraint satisfaction problems** — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone. By integrating **neurosymbolic methods** that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints. ## Graph of Rules for Enhanced Reasoning Another powerful concept that complements LLMs is using a **graph of rules**. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge. In a **graph of rules**, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust. For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses. Graphs of rules also enable **modular reasoning**, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of **neural fluency** with **rule-based structure** gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical. By implementing a graph of rules, LLMs are empowered to perform **deductive reasoning** alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence. ## Enhancing LLMs with Symbolic Reasoning Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where **neurosymbolic approaches** shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks. **Personal Knowledge Graphs (PKGs)** come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers. Imagine combining an LLM with a **graph of rules** that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using **deductive databases** to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving. ## My Research on Deductive Databases and Knowledge Graphs I recently did some research on modeling **knowledge graphs using deductive databases**, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning. **Prolog** and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a **graph of rules** that governs how relationships are formed or how logical deductions can be performed. The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence. ## Why It Matters for LLM Employment Using **neurosymbolic RAG (retrieval-augmented generation)** in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules. This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of **neural fluency** with **symbolic accuracy and deductive power** is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems. Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate! Until next time, folks. Stay curious, and keep pushing the boundaries of AI! @ e6817453:b0ac3c39
2024-12-07 14:54:46## Introduction: Personal Knowledge Graphs and Linked Data We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points. The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management. In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started. ## Intro to RDF The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent. RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph. ## RDF and Advanced Topics ## Lists and Sets in RDF RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data. ## Graph of Graphs A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling. ## Property Graphs While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges. For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges). The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other. ## Graph of Graphs and Subgraphs for Entity Modeling A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties. For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added. ## Hypergraphs and Metagraphs When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships. Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts. ## Balancing Structure and Properties One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity. So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools. The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage? ## Conclusion Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings. In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
@ e6817453:b0ac3c39
2024-12-07 14:54:46## Introduction: Personal Knowledge Graphs and Linked Data We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points. The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management. In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started. ## Intro to RDF The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent. RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph. ## RDF and Advanced Topics ## Lists and Sets in RDF RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data. ## Graph of Graphs A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling. ## Property Graphs While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges. For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges). The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other. ## Graph of Graphs and Subgraphs for Entity Modeling A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties. For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added. ## Hypergraphs and Metagraphs When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships. Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts. ## Balancing Structure and Properties One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity. So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools. The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage? ## Conclusion Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings. In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects. @ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and **temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory** and **semantic memory**. And we also have a lot of theories, right? ## Declarative Memory of the Human Brain How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic: - hippocampus indexing and retrieval - sanitization of episodic memories - episodic-semantic shift theory They all give a different perspective on how different parts of declarative memory cooperate. We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed. But, you know, it’s still an open question: > do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different? It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah? Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected. So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory. ## Temporal Semantics It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it. There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts. ## Time in a Semantic context is not a timestamp. What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that. You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah. Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things. For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events. I’m more about thinking about the time of semantics, where you have a time model as a **hybrid clock** or some **global clock** that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts. We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between. ## Blockchain of connected events and facts I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events. ## Time anchors We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles. Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and **temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory** and **semantic memory**. And we also have a lot of theories, right? ## Declarative Memory of the Human Brain How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic: - hippocampus indexing and retrieval - sanitization of episodic memories - episodic-semantic shift theory They all give a different perspective on how different parts of declarative memory cooperate. We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed. But, you know, it’s still an open question: > do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different? It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah? Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected. So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory. ## Temporal Semantics It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it. There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts. ## Time in a Semantic context is not a timestamp. What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that. You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah. Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things. For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events. I’m more about thinking about the time of semantics, where you have a time model as a **hybrid clock** or some **global clock** that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts. We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between. ## Blockchain of connected events and facts I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events. ## Time anchors We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles. Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.” @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46Sometimes perspective is everything... #[artmodel]( https://bsky.app/hashtag/artmodel) #[nude]( https://bsky.app/hashtag/nude) #[nudemodel]( https://bsky.app/hashtag/nudemodel) ------   
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46Sometimes perspective is everything... #[artmodel]( https://bsky.app/hashtag/artmodel) #[nude]( https://bsky.app/hashtag/nude) #[nudemodel]( https://bsky.app/hashtag/nudemodel) ------    @ 7ecd3fe6:6b52f30d
2024-12-05 10:35:57I went to bed last night at 96k, thinking we'd have another day of sideways consolidation, maybe if we're lucky a bump on the head at 99k before the 100k dumpers come in to "take profits" But little did I know what was waiting for me when I opened up my crusty eyes, I checked the chart as one days after their morning wee and nearly wet the entire bathroom, 102k, must be a mistake, let's check Coingecko, let's check the local exchanges, let's check social media, and it was confirmed like 6 blocks in baby, there's no going back! Ladies and gentlemen, grab your laser-eye NFTs and dust off those 2017 memes - we've finally arrived! Bitcoin has transcended the mythical $100,000 price point that HODLers have been hallucinating about since the Obama administration. We have succesfully meme'd the dream into a reality, can anything stop us now? The [Banana zone](https://thebitcoinmanual.com/articles/btc-banana-zone/) hath arrived -----------  ----------- ## Why the big break? Is it unrest in France with the government collapsing, is it South Korean uncertainty with their president declaring Martial law, is it Putin coming out to admit you can't ban Bitcoin? Is it countries trying to find a hedge against Trumps' proposed tariffs? Who knows? To me it's just another day of sellers exhausted and buyers are eating through the order book like hungry-hungry hippos ## Bottom of the bear to getting some serious air time If you've been here for one full cycle, and stayed the course it's been a wild ride, we saw Terra Luna, FTX, Celsius, BlockFi blow up and a massive draining of liquidity from the market. The dream was dead and we hit rock bottom in November 2022, at 15k, to those who nailed that absolute bottom, I salute you. Anyhoo, it's been a slow grind upwards, the crab market of choppy consolidation normally is, but you psychos continued to hold steady and deploy capital even when number continue to go down!  ## The meme, the dream and now the cream The bitcoin maximalists who've been sporting perpetual laser-eye Twitter and nostr profiles can now collectively exhale. Those same folks who've been predicting "$100K by EOY" every single year since 2017 can now do a victory lap, wearing their tinfoil-lined Gucci tracksuits. You were wrong many times, only to be proven right eventually! Remember when explaining Bitcoin's potential value used to involve complex blockchain narratives and decentralization lectures? ## Call up the cry babies When Bitcoin looked down and out there were no shortage of doom and gloomers writing another failed obituary, Dan Pena, Charlie Munger, Warren Buffer, Peter Schiff and Peter Zeihan all had to yap and we listened and laughed <iframe width="560" height="315" src="https://www.youtube.com/embed/SrSj2RmRtbs?si=sNU_XUX2izkDFngj" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> Let's hear what mama has to say on the subject of Bitcoin? <blockquote class="twitter-tweet"><p lang="en" dir="ltr">Keep dreaming. Bitcoin is never going to hit $100,000!</p>— Peter Schiff (@PeterSchiff) <a href="https://twitter.com/PeterSchiff/status/1192802503856984064?ref_src=twsrc%5Etfw">November 8, 2019</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script> Now it's just: "Told ya so" - accompanied by shitcoiners and nocoiners are angry coz of dey enlarged medulla oblongata ----------- Times like this, I often think of the wise and eloquent words of MSTR Gigachad Saylor <blockquote> Put money into Bitcoin and wait for number to go up biggly, if number go down put more money in and wait for number to go up bigglier - Michael Saylor </blockquote> ----------- ## Setting up base camp for the march up Mount Milli-manjaro The journey to $1 million feels eerily similar. We'll witness another brain-melting crypto pilgrimage - let's call it Mount Milli-manjaro - where every Reddit thread and Twitter space will sound like a combination of economic prophecy and sci-fi fever dream. Pro tip for newcomers: Pack extra copium, a sense of humor, and maybe some popcorn. This ride is just getting started. To the moon? 🚀🤡₿ Looks likely bar a massive black swan, 2025, looks like this thing is going to run with big Usain Bolt strides as we enjoy a year of price discovery, speculation and all the scams that will fester as retail comes piling in to make their overnight fortunes. I know it's fun to hand out I told you so's and you should enjoy it, take the victory lap but even that gets old, while it's hard to do, try to stay humble and enjoy stack the perpetual top!
@ 7ecd3fe6:6b52f30d
2024-12-05 10:35:57I went to bed last night at 96k, thinking we'd have another day of sideways consolidation, maybe if we're lucky a bump on the head at 99k before the 100k dumpers come in to "take profits" But little did I know what was waiting for me when I opened up my crusty eyes, I checked the chart as one days after their morning wee and nearly wet the entire bathroom, 102k, must be a mistake, let's check Coingecko, let's check the local exchanges, let's check social media, and it was confirmed like 6 blocks in baby, there's no going back! Ladies and gentlemen, grab your laser-eye NFTs and dust off those 2017 memes - we've finally arrived! Bitcoin has transcended the mythical $100,000 price point that HODLers have been hallucinating about since the Obama administration. We have succesfully meme'd the dream into a reality, can anything stop us now? The [Banana zone](https://thebitcoinmanual.com/articles/btc-banana-zone/) hath arrived -----------  ----------- ## Why the big break? Is it unrest in France with the government collapsing, is it South Korean uncertainty with their president declaring Martial law, is it Putin coming out to admit you can't ban Bitcoin? Is it countries trying to find a hedge against Trumps' proposed tariffs? Who knows? To me it's just another day of sellers exhausted and buyers are eating through the order book like hungry-hungry hippos ## Bottom of the bear to getting some serious air time If you've been here for one full cycle, and stayed the course it's been a wild ride, we saw Terra Luna, FTX, Celsius, BlockFi blow up and a massive draining of liquidity from the market. The dream was dead and we hit rock bottom in November 2022, at 15k, to those who nailed that absolute bottom, I salute you. Anyhoo, it's been a slow grind upwards, the crab market of choppy consolidation normally is, but you psychos continued to hold steady and deploy capital even when number continue to go down!  ## The meme, the dream and now the cream The bitcoin maximalists who've been sporting perpetual laser-eye Twitter and nostr profiles can now collectively exhale. Those same folks who've been predicting "$100K by EOY" every single year since 2017 can now do a victory lap, wearing their tinfoil-lined Gucci tracksuits. You were wrong many times, only to be proven right eventually! Remember when explaining Bitcoin's potential value used to involve complex blockchain narratives and decentralization lectures? ## Call up the cry babies When Bitcoin looked down and out there were no shortage of doom and gloomers writing another failed obituary, Dan Pena, Charlie Munger, Warren Buffer, Peter Schiff and Peter Zeihan all had to yap and we listened and laughed <iframe width="560" height="315" src="https://www.youtube.com/embed/SrSj2RmRtbs?si=sNU_XUX2izkDFngj" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> Let's hear what mama has to say on the subject of Bitcoin? <blockquote class="twitter-tweet"><p lang="en" dir="ltr">Keep dreaming. Bitcoin is never going to hit $100,000!</p>— Peter Schiff (@PeterSchiff) <a href="https://twitter.com/PeterSchiff/status/1192802503856984064?ref_src=twsrc%5Etfw">November 8, 2019</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script> Now it's just: "Told ya so" - accompanied by shitcoiners and nocoiners are angry coz of dey enlarged medulla oblongata ----------- Times like this, I often think of the wise and eloquent words of MSTR Gigachad Saylor <blockquote> Put money into Bitcoin and wait for number to go up biggly, if number go down put more money in and wait for number to go up bigglier - Michael Saylor </blockquote> ----------- ## Setting up base camp for the march up Mount Milli-manjaro The journey to $1 million feels eerily similar. We'll witness another brain-melting crypto pilgrimage - let's call it Mount Milli-manjaro - where every Reddit thread and Twitter space will sound like a combination of economic prophecy and sci-fi fever dream. Pro tip for newcomers: Pack extra copium, a sense of humor, and maybe some popcorn. This ride is just getting started. To the moon? 🚀🤡₿ Looks likely bar a massive black swan, 2025, looks like this thing is going to run with big Usain Bolt strides as we enjoy a year of price discovery, speculation and all the scams that will fester as retail comes piling in to make their overnight fortunes. I know it's fun to hand out I told you so's and you should enjoy it, take the victory lap but even that gets old, while it's hard to do, try to stay humble and enjoy stack the perpetual top! @ b2d670de:907f9d4a
2024-12-02 21:25:18This is a list of nostr clients exposed as onion services. The list is currently actively maintained on [GitHub](https://github.com/0xtrr/onion-service-nostr-clients). Contributions are always appreciated! | Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | [operator](nostr:nprofile1qyvhwumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdshszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmg9umdvr) | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | [operator](nostr:nprofile1qyv8wumn8ghj7un9d3shjtnddaehgctjvshx7un89uq36amnwvaz7tmzdaehgu3wvf5hgcm0d9h8g7r0ddhjucm0d5hsqgy8wvyzw6l9pn5m47n7tcm5un7t7h5ctx3pjx8nfwh06qq8g6max5zadtyx) | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostrnpub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | [operator](nostr:nprofile1qqszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsxx2q3a) | Runs nsite. You can read more about nsite [here](https://github.com/lez/nsite). |
@ b2d670de:907f9d4a
2024-12-02 21:25:18This is a list of nostr clients exposed as onion services. The list is currently actively maintained on [GitHub](https://github.com/0xtrr/onion-service-nostr-clients). Contributions are always appreciated! | Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | [operator](nostr:nprofile1qyvhwumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdshszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmg9umdvr) | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | [operator](nostr:nprofile1qyv8wumn8ghj7un9d3shjtnddaehgctjvshx7un89uq36amnwvaz7tmzdaehgu3wvf5hgcm0d9h8g7r0ddhjucm0d5hsqgy8wvyzw6l9pn5m47n7tcm5un7t7h5ctx3pjx8nfwh06qq8g6max5zadtyx) | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostrnpub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | [operator](nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0) | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | [operator](nostr:nprofile1qqszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsxx2q3a) | Runs nsite. You can read more about nsite [here](https://github.com/lez/nsite). | @ b2d670de:907f9d4a
2024-12-02 21:24:45# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
@ b2d670de:907f9d4a
2024-12-02 21:24:45# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url). @ e31e84c4:77bbabc0
2024-12-02 10:44:07*Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net* Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions. This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme. As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio. The ‘40’ represents fixed income, defined as… > An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital. Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond. First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits. There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis: - A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time. - The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted. - These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy - U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts. - This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating. - The current debt situation raises concerns about sustainability. - The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt. - This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens. In the words of Lyn Alden “Nothing stops this train” Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money. As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer. To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone. ### Now the fun part. How does bitcoin fix this? Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income. Here are some new developments – Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income. Dynamics - Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio. - Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund. Pros - The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin. Cons - The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this. Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer. Dynamics - Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin. - Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance. - Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings. Pros - Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt. - Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios. Cons - There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk. - Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors. Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin. Dynamics - Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time. - Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged. Pros - There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time. - The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments. Cons - While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return. - Interest rate payments are on the lower side Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard. Additional Resources - [River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.](http://bitcoin%20and%20fixed%20ihttps//blog.river.com/bitcoin-interest-on-cash/ncome) - [Onramp: Bitcoin, The Emergent Asset Class](https://onrampbitcoin.docsend.com/view/j4wje7kgvw357tt9) - [MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes](https://www.microstrategy.com/press/microstrategy-announces-pricing-of-offering-of-convertible-senior-notes_09-18-2024) --- *Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net*
@ e31e84c4:77bbabc0
2024-12-02 10:44:07*Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net* Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions. This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme. As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio. The ‘40’ represents fixed income, defined as… > An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital. Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond. First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits. There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis: - A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time. - The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted. - These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy - U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts. - This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating. - The current debt situation raises concerns about sustainability. - The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt. - This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens. In the words of Lyn Alden “Nothing stops this train” Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money. As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer. To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone. ### Now the fun part. How does bitcoin fix this? Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income. Here are some new developments – Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income. Dynamics - Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio. - Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund. Pros - The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin. Cons - The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this. Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer. Dynamics - Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin. - Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance. - Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings. Pros - Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt. - Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios. Cons - There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk. - Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors. Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin. Dynamics - Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time. - Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged. Pros - There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time. - The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments. Cons - While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return. - Interest rate payments are on the lower side Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard. Additional Resources - [River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.](http://bitcoin%20and%20fixed%20ihttps//blog.river.com/bitcoin-interest-on-cash/ncome) - [Onramp: Bitcoin, The Emergent Asset Class](https://onrampbitcoin.docsend.com/view/j4wje7kgvw357tt9) - [MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes](https://www.microstrategy.com/press/microstrategy-announces-pricing-of-offering-of-convertible-senior-notes_09-18-2024) --- *Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net* @ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process. In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! **I highly recommend reading this post fully before starting the migration process.** Before we dive in, [here](https://community.umbrel.com/t/how-to-update-from-umbrelos-0-5-to-umbrelos-1-1-on-linux-devices/16704#how-to-update-from-umbrelos-05-on-a-linux-device-3) is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully. **With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.** ## The Order of Steps ### Tip #1: In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups. ## Creating the Bootable USB Stick ### TIP #2: After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route. ### TIP #3: Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.  ### Tip #4: Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node. **If all is good, you are ready to get back to the guide and walk through the steps.** ## Preparing the Hardware ### Tip #5: In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences. ## The Migration Process ### Tip #6: Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. **you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again.** If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this. But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again. ### Tip #7: This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it. ### Tip #8: If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues. ### Tip #9: During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D ### Tip #10: I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help. # Have Fun, and Good Luck!
@ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process. In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! **I highly recommend reading this post fully before starting the migration process.** Before we dive in, [here](https://community.umbrel.com/t/how-to-update-from-umbrelos-0-5-to-umbrelos-1-1-on-linux-devices/16704#how-to-update-from-umbrelos-05-on-a-linux-device-3) is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully. **With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.** ## The Order of Steps ### Tip #1: In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups. ## Creating the Bootable USB Stick ### TIP #2: After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route. ### TIP #3: Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.  ### Tip #4: Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node. **If all is good, you are ready to get back to the guide and walk through the steps.** ## Preparing the Hardware ### Tip #5: In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences. ## The Migration Process ### Tip #6: Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. **you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again.** If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this. But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again. ### Tip #7: This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it. ### Tip #8: If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues. ### Tip #9: During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D ### Tip #10: I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help. # Have Fun, and Good Luck! @ 1ef695e1:15351d5f
2024-11-29 14:21:00After getting my ham licence in 2013 I found out about SOTA. I was enthusiastic as I have a long history of hiking in the mountains while a scout and then as a Scoutmaster. Now I was going to combine the two yet I immediately encountered a big problem. Very few South African summits were listed on the SOTA database and some of those listed did not even qualify as summits. I enquired of SOTA management and was told that "South Africa is on hold until all the summits are correctly mapped and checked." Only then could the summits be loaded to the database. Using GIS software and my 1:50000 topographic maps I began mapping summits in my home province Limpopo that qualified according to the SOTA criteria. An individual prominence of 150m or more was easy to determine. Doing the mapping I found a lot of summits that were obvious, but finding the key col of each summit was more difficult. The older maps in South Africa actually had a lot of the key cols displayed and using my combined methods I proceeded to map summits one by one and add the data to a spreadsheet. Taking approximately 8 minutes to map a summit it took me months to map Limpopo. I missed summits where the summit is spread over a large area and though it qualifies due to a 150m or more prominence it does not look like a summit and these we added later. I sent my mapping data to OM Andrew VK3ARR in Australia and received a thumbs up as to my data accuracy. I was pleasantly surprised when my Limpopo summits appeared on the SOTA database even though the rest of the country was still not done. I immediately started mapping the next province of Mpumalanga using my manual methods. Sid Tylor ZS5AYC from Kwazulu - Natal, who became SOTA manager for South Africa, and I had been discussing the processes and he arranged access to online software with automated summit processing where we could just check key col position and all the data per summit was processed much quicker. Frustrating for me was that I could not see what the software was doing and we just checked key cols without knowing where the summit was or its other data. I completed the remaining Mpumalanga summits using the software access and then completed the Western Cape summits after which Sid and I split the Northern Cape summits between us. The other provinces were processed by various operators including some much appreciated assistance from Australian hams. A big thank you to all in SOTA management, in South Africa, those that assisted from Australia, as well as SOTA UK, for making it possible for us to enjoy the adventures of SOTA. Activating Renosterkop ZS/NC-272 in the Northern Cape 
@ 1ef695e1:15351d5f
2024-11-29 14:21:00After getting my ham licence in 2013 I found out about SOTA. I was enthusiastic as I have a long history of hiking in the mountains while a scout and then as a Scoutmaster. Now I was going to combine the two yet I immediately encountered a big problem. Very few South African summits were listed on the SOTA database and some of those listed did not even qualify as summits. I enquired of SOTA management and was told that "South Africa is on hold until all the summits are correctly mapped and checked." Only then could the summits be loaded to the database. Using GIS software and my 1:50000 topographic maps I began mapping summits in my home province Limpopo that qualified according to the SOTA criteria. An individual prominence of 150m or more was easy to determine. Doing the mapping I found a lot of summits that were obvious, but finding the key col of each summit was more difficult. The older maps in South Africa actually had a lot of the key cols displayed and using my combined methods I proceeded to map summits one by one and add the data to a spreadsheet. Taking approximately 8 minutes to map a summit it took me months to map Limpopo. I missed summits where the summit is spread over a large area and though it qualifies due to a 150m or more prominence it does not look like a summit and these we added later. I sent my mapping data to OM Andrew VK3ARR in Australia and received a thumbs up as to my data accuracy. I was pleasantly surprised when my Limpopo summits appeared on the SOTA database even though the rest of the country was still not done. I immediately started mapping the next province of Mpumalanga using my manual methods. Sid Tylor ZS5AYC from Kwazulu - Natal, who became SOTA manager for South Africa, and I had been discussing the processes and he arranged access to online software with automated summit processing where we could just check key col position and all the data per summit was processed much quicker. Frustrating for me was that I could not see what the software was doing and we just checked key cols without knowing where the summit was or its other data. I completed the remaining Mpumalanga summits using the software access and then completed the Western Cape summits after which Sid and I split the Northern Cape summits between us. The other provinces were processed by various operators including some much appreciated assistance from Australian hams. A big thank you to all in SOTA management, in South Africa, those that assisted from Australia, as well as SOTA UK, for making it possible for us to enjoy the adventures of SOTA. Activating Renosterkop ZS/NC-272 in the Northern Cape  @ fe7f6bc6:c42539a3
2024-11-29 01:54:31A few weeks ago, I sat down with Chad ([full podcast](https://creators.spotify.com/pod/show/proofofhealth/episodes/1-How-Muay-Thai-Fighting-Saved-My-Life---Chad-Mane-e2pnbmp)), a seasoned Muay Thai fighter with over a decade of experience, to talk about life inside and outside the ring. Chad’s story is raw, intense, and unfiltered—a journey of struggle, discipline, and transformation. His insights left me reflecting on how combat sports, especially Muay Thai, can teach us profound lessons about resilience, focus, and the human spirit. ### **The Fight Beyond the Ring** What struck me most was how Muay Thai isn’t just a sport for Chad—it’s a way of life. He began his journey as a teenager, struggling with family issues and uncertainty about his future. A chance meeting led him to Thailand, where he trained intensely and fought his first bout just 28 days later. Chad told me, “Muay Thai saved my life,” and I could feel the weight behind those words. For Chad, the ring became a space to confront not just opponents but his own fears and insecurities. The process of training—the relentless hill sprints, countless kicks, and sparring sessions—taught him how to face challenges head-on. Fighting wasn’t about aggression; it was about finding strength in adversity. --- ### **The Beauty in the Brutality** One of the most fascinating things Chad shared was his perspective on pain and sacrifice. During his career, he’s endured broken ribs, countless stitches, and even fought with a broken nose for eight years before getting it fixed. “Pain is the best teacher,” he said, explaining how injuries forced him to adapt and improve. What I found most compelling was how this physical suffering seemed to heighten his appreciation for life. Chad described moments after brutal training sessions when even a sunset or a simple breeze felt extraordinary. It’s as if the harshness of the ring makes the world outside it feel brighter, sharper, and more alive. “When you’re ready to die in the ring,” he said, “you start seeing life differently.” --- ### **The Mental Battle** Chad emphasized the mental aspect of fighting, something I hadn’t fully appreciated before. He talked about the mindset required to step into the ring: the inner dialogue where you convince yourself you’re ready to endure pain and push beyond limits. “You can play football or tennis, but you can’t play Muay Thai,” he said, driving home the seriousness of the sport. Before a fight, Chad uses visualization to prepare himself for the intensity of combat. He doesn’t shy away from the danger but instead leans into it, fully accepting the risks. This mindset, he believes, is what separates good fighters from great ones. --- ### **Lessons for Life** While most of us won’t step into a Muay Thai ring, Chad’s experiences offer valuable lessons that apply to all areas of life: - **Discipline Creates Freedom**: The structure of relentless training gave Chad a sense of purpose and control over his life. - **Face Your Fears**: Whether it’s an elbow to the face or a difficult decision in life, avoidance only makes things worse. - **Surround Yourself with the Right People**: Chad stressed the importance of training with people who push you to be better. “Energy matters,” he said, and I couldn’t agree more. --- ### **Final Thoughts** Chad’s story reminded me why I wanted to take on my own Muay Thai journey. It’s not just about fighting; it’s about testing yourself in ways that reveal who you really are. For Chad, the ring isn’t just a place to compete—it’s a place to grow, to learn, and to become a better version of himself. After our conversation, I realized that the lessons of Muay Thai go beyond the gym. Whether you’re training for a fight or tackling challenges in everyday life, the principles of resilience, discipline, and self-reflection are universal. If you’re curious to learn more about Chad’s journey, I highly recommend watching the [documentary](https://youtu.be/GPug-MuCKKY) we worked on together. It’s a glimpse into the raw, unforgiving world of Muay Thai—and the unshakable spirit of those who live it. Stay Healthy - Max
@ fe7f6bc6:c42539a3
2024-11-29 01:54:31A few weeks ago, I sat down with Chad ([full podcast](https://creators.spotify.com/pod/show/proofofhealth/episodes/1-How-Muay-Thai-Fighting-Saved-My-Life---Chad-Mane-e2pnbmp)), a seasoned Muay Thai fighter with over a decade of experience, to talk about life inside and outside the ring. Chad’s story is raw, intense, and unfiltered—a journey of struggle, discipline, and transformation. His insights left me reflecting on how combat sports, especially Muay Thai, can teach us profound lessons about resilience, focus, and the human spirit. ### **The Fight Beyond the Ring** What struck me most was how Muay Thai isn’t just a sport for Chad—it’s a way of life. He began his journey as a teenager, struggling with family issues and uncertainty about his future. A chance meeting led him to Thailand, where he trained intensely and fought his first bout just 28 days later. Chad told me, “Muay Thai saved my life,” and I could feel the weight behind those words. For Chad, the ring became a space to confront not just opponents but his own fears and insecurities. The process of training—the relentless hill sprints, countless kicks, and sparring sessions—taught him how to face challenges head-on. Fighting wasn’t about aggression; it was about finding strength in adversity. --- ### **The Beauty in the Brutality** One of the most fascinating things Chad shared was his perspective on pain and sacrifice. During his career, he’s endured broken ribs, countless stitches, and even fought with a broken nose for eight years before getting it fixed. “Pain is the best teacher,” he said, explaining how injuries forced him to adapt and improve. What I found most compelling was how this physical suffering seemed to heighten his appreciation for life. Chad described moments after brutal training sessions when even a sunset or a simple breeze felt extraordinary. It’s as if the harshness of the ring makes the world outside it feel brighter, sharper, and more alive. “When you’re ready to die in the ring,” he said, “you start seeing life differently.” --- ### **The Mental Battle** Chad emphasized the mental aspect of fighting, something I hadn’t fully appreciated before. He talked about the mindset required to step into the ring: the inner dialogue where you convince yourself you’re ready to endure pain and push beyond limits. “You can play football or tennis, but you can’t play Muay Thai,” he said, driving home the seriousness of the sport. Before a fight, Chad uses visualization to prepare himself for the intensity of combat. He doesn’t shy away from the danger but instead leans into it, fully accepting the risks. This mindset, he believes, is what separates good fighters from great ones. --- ### **Lessons for Life** While most of us won’t step into a Muay Thai ring, Chad’s experiences offer valuable lessons that apply to all areas of life: - **Discipline Creates Freedom**: The structure of relentless training gave Chad a sense of purpose and control over his life. - **Face Your Fears**: Whether it’s an elbow to the face or a difficult decision in life, avoidance only makes things worse. - **Surround Yourself with the Right People**: Chad stressed the importance of training with people who push you to be better. “Energy matters,” he said, and I couldn’t agree more. --- ### **Final Thoughts** Chad’s story reminded me why I wanted to take on my own Muay Thai journey. It’s not just about fighting; it’s about testing yourself in ways that reveal who you really are. For Chad, the ring isn’t just a place to compete—it’s a place to grow, to learn, and to become a better version of himself. After our conversation, I realized that the lessons of Muay Thai go beyond the gym. Whether you’re training for a fight or tackling challenges in everyday life, the principles of resilience, discipline, and self-reflection are universal. If you’re curious to learn more about Chad’s journey, I highly recommend watching the [documentary](https://youtu.be/GPug-MuCKKY) we worked on together. It’s a glimpse into the raw, unforgiving world of Muay Thai—and the unshakable spirit of those who live it. Stay Healthy - Max @ e31e84c4:77bbabc0
2024-11-27 11:32:57‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com ### Childhood Lessons As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny. ### Definitions of Security Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs. Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis. When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change. ## How Bitcoin Changed Me The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights. Here are just a few examples: ### Freedom of Expression Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions. ### Adequate Living Standards Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards. Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards. ### Freedom of Association Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions. Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code. Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power. ### Right to Information The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use. ## Personal Context For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code. In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon… ## A Modern Necessity These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview: *“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” ([https://www.youtube.com/watch?v=K4ciiDyUvUo](https://www.youtube.com/watch?v=K4ciiDyUvUo))* As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society. The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities. ## Bitcoin’s True Security Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it. Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections. Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times. --- ‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
@ e31e84c4:77bbabc0
2024-11-27 11:32:57‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com ### Childhood Lessons As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny. ### Definitions of Security Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs. Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis. When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change. ## How Bitcoin Changed Me The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights. Here are just a few examples: ### Freedom of Expression Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions. ### Adequate Living Standards Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards. Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards. ### Freedom of Association Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions. Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code. Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power. ### Right to Information The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use. ## Personal Context For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code. In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon… ## A Modern Necessity These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview: *“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” ([https://www.youtube.com/watch?v=K4ciiDyUvUo](https://www.youtube.com/watch?v=K4ciiDyUvUo))* As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society. The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities. ## Bitcoin’s True Security Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it. Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections. Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times. --- ‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com @ 129f5189:3a441803
2024-11-22 03:42:42Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario. The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy. After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America. Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million. China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions... https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions. In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border. A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention. https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere. The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years. https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021. In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government. https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues. In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities." https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024. Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction. In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government. https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University. "The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times. General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country. "We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time. In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade." https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues." Under the previous administration, China had received preferential treatment. In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan. The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security. No public records show that the project has progressed since then. https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark. "Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement. "Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face." https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era. Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel." https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg Access to space plays a crucial role in the CCP's strategic objectives. Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China. According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice. According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access. China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely. The big question is: what could this facility do in times of war? https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit. The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface. Additionally, it offers strategic advantages for any government involved in espionage. https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner. However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives. Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023. https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg
@ 129f5189:3a441803
2024-11-22 03:42:42Today we will understand how Argentina, when under the control of the Foro de São Paulo, was an important asset for the Chinese Communist Party in South America and how Javier Milei is charting paths to change this scenario. The Chinese government has been making diplomatic overtures to areas near the polar regions as part of its maritime strategy. After a "strategic retreat," the Southern Hemisphere has assumed a new dimension for Chinese interests in South America. Beijing has been increasing its diplomatic engagement with countries in the region, especially Argentina in recent times, through a series of economic, sociocultural, and to a lesser extent, military agreements. This includes the delivery of vaccines and the intention to accelerate an investment plan worth $30 million. China has focused on several geopolitically sensitive projects in Argentina, all strategic: controlling air and maritime space and strategic facilities in territorial areas monitored by Beijing over Antarctica and the South Atlantic. However, doubts arise about China's intentions... https://image.nostr.build/f55fc5464d8d09cbbddd0fe803b264a5e885da387c2c6c1702f021875beb18c2.jpg For Xi Jinping's government, Argentina stands out for its strategic location, the influential posture of its leaders, and its alignment with China's economic and military power expansion. China has made significant investments and infrastructure initiatives in various Argentine regions. In addition to establishing a presence in the province of Neuquén, China has targeted the port city of Ushuaia in Tierra del Fuego, Antarctica, the South Atlantic islands, and the San Juan region near the Chilean border. A 2012 agreement between authorities in Argentina's Neuquén province and Beijing allowed the construction of a deep space tracking station near the Chilean border, which caught Washington's attention. https://image.nostr.build/a3fa7f2c7174ee9d90aaecd9eadb69a2ef82c04c94584165a213b29d2ae8a66e.jpg In 2014, through a bilateral agreement between the Chinese Lunar Exploration Program, represented by the Satellite Launch and Tracking Control General (CLTC) of the People's Liberation Army (PLA) and Argentina's National Commission on Space Activities (CONAE), the agreement identified the Argentine space station at Bajada del Agrio as the most favorable location for hosting a Chinese base in the Southern Hemisphere. The project became operational in 2017 on a 200-hectare area and represents the third in a global network and the first outside China. It features a 110-ton, 35-meter-diameter antenna for deep space exploration (telemetry and technology for "terrestrial tracking, command, and data acquisition"), with the CLTC having a special exploration license for a period of 50 years. https://image.nostr.build/0a469d8bab900c7cefa854594dfdb934febf2758e1a77c7639d394f14cd98491.jpg The 50-year contract grants the Chinese Communist Party (CCP) the ability to operate freely on Argentine soil. The facility, known as Espacio Lejano, set a precedent for a Chinese ground tracking station in Río Gallegos, on the southeastern coast of Argentina, which was formally announced in 2021. In 2016, a document issued by the U.S. State Council Information Office raised concerns among the U.S. government and European Union (EU) countries about the potential military and geopolitical uses of the base in the Southern Hemisphere and Antarctica. Another element fueling suspicion is the existence of "secret clauses" in a document signed by the General Directorate of Legal Advisory (DICOL) of Argentina’s Ministry of Foreign Affairs, International Trade, and Worship with the Chinese government. https://image.nostr.build/1733ba03475755ddf9be4eafc3e9eb838ba8f9fa6e783a4b060f12b89c3f4165.jpg Since the Espacio Lejano contract was signed, U.S. analysts and authorities have repeatedly expressed concern about China's growing collaboration with Argentina on security and surveillance issues. In 2023, a general from the U.S. Southern Command stated during a hearing of the House Armed Services Committee: "The PRC [People's Republic of China] has expanded its capacity to extract resources, establish ports, manipulate governments through predatory investment practices, and build potential dual-use space facilities." https://image.nostr.build/16bbdeae11247d47a97637402866a0414d235d41fe8039218e26c9d11392b487.jpg The shift in the Argentine government from a leftist spectrum, led by leaders of the São Paulo Forum, to a Milei administration, which has always advocated for libertarian and pro-Western rhetoric, has altered the dynamics of Chinese-Argentine relations in 2024. Milei assumed office on December 10, 2023, replacing the progressive president Alberto Fernández, who had strengthened ties with China and signed an agreement in 2022 to join the CCP’s Belt and Road Initiative. During his campaign, Milei did not hide his disdain for communist regimes and signaled his intention to move away from socialist policies in favor of a more libertarian direction. In the nearly seven months since taking office, Milei has implemented major economic reforms and streamlined the government. https://image.nostr.build/1d534b254529bf10834d81e2ae35ce2698eda2453d5e2b39d98fa50b45c00a59.jpg Other recent "positive indicators" suggest that the Milei administration is prioritizing defense relations with the United States over China, according to Leland Lazarus, Associate Director of National Security at the Jack D. Gordon Institute for Public Policy at Florida International University. "The fact is that, in just six months, he has already visited the United States several times. He has met with Secretary [Antony] Blinken, been to the White House... all of this is like absolute music to General Richardson's ears; to President [Joe] Biden's ears," Lazarus told Epoch Times. General Richardson visited Argentina in April, a trip that included the donation of a C-130H Hercules transport aircraft to the Argentine Air Force and a visit to a naval facility in Ushuaia, Tierra del Fuego, at the southern tip of the country. "We are committed to working closely with Argentina so that our collaborative security efforts benefit our citizens, our countries, and our hemisphere in enduring and positive ways," she said in a statement at the time. In Ushuaia, General Richardson met with local military personnel to discuss their role in "safeguarding vital maritime routes for global trade." https://image.nostr.build/f6d80fee8a7bba03bf11235d86c4f72435ae4be7d201dba81cc8598551e5ed24.jpg In a statement from the Argentine Ministry of Defense, Milei confirmed that General Richardson also reviewed the progress of an "integrated naval base" at the Ushuaia naval facility. Argentine officials said they also discussed "legislative modernization on defense issues." Under the previous administration, China had received preferential treatment. In June 2023, Tierra del Fuego Governor Gustavo Melella approved China's plans to build a "multi-use" port facility near the Strait of Magellan. The project was met with legislative backlash, as three national deputies and members of the Civic Coalition filed an official complaint against the governor's provincial decree to build the port with Beijing. The same group also accused Melella of compromising Argentina’s national security. No public records show that the project has progressed since then. https://image.nostr.build/3b2b57875dc7ac162ab2b198df238cb8479a7d0bbce32b4042e11063b5e2779b.jpg Argentina's desire for deeper security cooperation with Western partners was also evident in April when Argentine Defense Minister Luis Petri signed a historic agreement to purchase 24 F-16 fighter jets from Denmark. "Today we are concluding the most important military aviation acquisition since 1983," Petri said in an official statement. "Thanks to this investment in defense, I can proudly say that we are beginning to restore our air sovereignty and that our entire society is better protected against all the threats we face." https://image.nostr.build/8aa0a6261e61e35c888d022a537f03a0fb7a963a78bf2f1bec9bf0a242289dba.jpg The purchase occurred after several media reports in 2022 indicated that the previous Fernández administration was considering buying JF-17 fighter jets made in China and Pakistan. A former minister from ex-president Mauricio Macri's government, who requested anonymity, confirmed to Epoch Times that a deal to acquire JF-17 jets was being considered during the Fernández era. Chinese investment did not occur only in Argentina. According to a document from the U.S. House Foreign Affairs Committee: "From 2009 to 2019, China transferred a total of $634 million in significant military equipment to five South American countries—Argentina, Bolivia, Ecuador, Peru, and Venezuela. The governments of Venezuela, Ecuador, Bolivia, and Argentina purchased defense equipment from the PRC, cooperated in military exercises, and engaged in educational exchanges and training for their military personnel." https://image.nostr.build/ed6d8daeea418b7e233ef97c90dee5074be64bd572f1fd0a5452b5960617c9ca.jpg Access to space plays a crucial role in the CCP's strategic objectives. Thus, when reports emerged in early April that Milei's government wanted to inspect Espacio Lejano, experts suggested it supported his national security moves away from China. According to the Espacio Lejano contract, signed under Cristina Fernández de Kirchner's Peronist regime, CCP officials are not required to let anyone—including the Argentine president—enter the facility without prior notice. According to Article 3, the agreement stipulates that Argentine authorities cannot interfere with or interrupt the "normal activities" of the facility and must explore alternative options and provide an unspecified amount of notice before being granted access. China has maintained that Espacio Lejano is for deep space exploration, lunar missions, and communication with satellites already in orbit. However, there is deep skepticism that the claim of space exploration alone is highly unlikely. The big question is: what could this facility do in times of war? https://image.nostr.build/f46a2807c02c512e70b14981f07a7e669223a42f3907cbddec952d5b27da9895.jpg Neuquén is just one of 11 ground stations and space research facilities China has in Latin America and the Caribbean. This represents the largest concentration of space equipment China has outside its own country. According to data from the Gordon Institute, the Chinese Espacio Lejano station and the Río Gallegos facility provide an ideal surveillance position near the polar orbit. The polar orbit is useful for data collection, transmission, and tracking because it allows for observation of the entire planet from space. The resolution of communications is also improved due to the proximity of satellites in orbit to the Earth's surface. Additionally, it offers strategic advantages for any government involved in espionage. https://image.nostr.build/39215a4c9f84cbbaf517c4fda8a562bba9e0cd3af3d453a24d3a9b454c5d015d.jpg Regarding deeper security collaboration with the United States, the trend is that Milei’s government will do as much as possible without jeopardizing its contracts with China, which is currently Argentina's second-largest trading partner. However, if Argentina's defense cooperation with China cools, the communist regime might wait for another Argentine government to continue its expansion—a government that could be more favorable to the CCP's objectives. Everything will depend on the continued success of Javier Milei's economic miracle, ensuring his government is re-elected and he can appoint a successor, making it more challenging for China, and avoiding a situation similar to what occurred in Brazil starting in 2023. https://image.nostr.build/a5dd3e59a703c553be60534ac5a539b1e50496c71904d01b16471086e9843cd4.jpg @ a39d19ec:3d88f61e
2024-11-21 12:05:09A state-controlled money supply can influence the development of socialist policies and practices in various ways. Although the relationship is not deterministic, state control over the money supply can contribute to a larger role of the state in the economy and facilitate the implementation of socialist ideals. ## Fiscal Policy Capabilities When the state manages the money supply, it gains the ability to implement fiscal policies that can lead to an expansion of social programs and welfare initiatives. Funding these programs by creating money can enhance the state's influence over the economy and move it closer to a socialist model. The Soviet Union, for instance, had a centralized banking system that enabled the state to fund massive industrialization and social programs, significantly expanding the state's role in the economy. ## Wealth Redistribution Controlling the money supply can also allow the state to influence economic inequality through monetary policies, effectively redistributing wealth and reducing income disparities. By implementing low-interest loans or providing financial assistance to disadvantaged groups, the state can narrow the wealth gap and promote social equality, as seen in many European welfare states. ## Central Planning A state-controlled money supply can contribute to increased central planning, as the state gains more influence over the economy. Central banks, which are state-owned or heavily influenced by the state, play a crucial role in managing the money supply and facilitating central planning. This aligns with socialist principles that advocate for a planned economy where resources are allocated according to social needs rather than market forces. ## Incentives for Staff Staff members working in state institutions responsible for managing the money supply have various incentives to keep the system going. These incentives include job security, professional expertise and reputation, political alignment, regulatory capture, institutional inertia, and legal and administrative barriers. While these factors can differ among individuals, they can collectively contribute to the persistence of a state-controlled money supply system. In conclusion, a state-controlled money supply can facilitate the development of socialist policies and practices by enabling fiscal policies, wealth redistribution, and central planning. The staff responsible for managing the money supply have diverse incentives to maintain the system, further ensuring its continuation. However, it is essential to note that many factors influence the trajectory of an economic system, and the relationship between state control over the money supply and socialism is not inevitable.
@ a39d19ec:3d88f61e
2024-11-21 12:05:09A state-controlled money supply can influence the development of socialist policies and practices in various ways. Although the relationship is not deterministic, state control over the money supply can contribute to a larger role of the state in the economy and facilitate the implementation of socialist ideals. ## Fiscal Policy Capabilities When the state manages the money supply, it gains the ability to implement fiscal policies that can lead to an expansion of social programs and welfare initiatives. Funding these programs by creating money can enhance the state's influence over the economy and move it closer to a socialist model. The Soviet Union, for instance, had a centralized banking system that enabled the state to fund massive industrialization and social programs, significantly expanding the state's role in the economy. ## Wealth Redistribution Controlling the money supply can also allow the state to influence economic inequality through monetary policies, effectively redistributing wealth and reducing income disparities. By implementing low-interest loans or providing financial assistance to disadvantaged groups, the state can narrow the wealth gap and promote social equality, as seen in many European welfare states. ## Central Planning A state-controlled money supply can contribute to increased central planning, as the state gains more influence over the economy. Central banks, which are state-owned or heavily influenced by the state, play a crucial role in managing the money supply and facilitating central planning. This aligns with socialist principles that advocate for a planned economy where resources are allocated according to social needs rather than market forces. ## Incentives for Staff Staff members working in state institutions responsible for managing the money supply have various incentives to keep the system going. These incentives include job security, professional expertise and reputation, political alignment, regulatory capture, institutional inertia, and legal and administrative barriers. While these factors can differ among individuals, they can collectively contribute to the persistence of a state-controlled money supply system. In conclusion, a state-controlled money supply can facilitate the development of socialist policies and practices by enabling fiscal policies, wealth redistribution, and central planning. The staff responsible for managing the money supply have diverse incentives to maintain the system, further ensuring its continuation. However, it is essential to note that many factors influence the trajectory of an economic system, and the relationship between state control over the money supply and socialism is not inevitable. @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08### Tldr - Nostr is an open protocol which is interoperable with all kinds of other technologies - You can use this interoperability to create custom solutions - Nostr apps define a custom URI scheme handler "nostr:" - In this blog I use this to integrate Nostr with NFC cards - I create a Nostr NFC "login card" which allows me to log into Amethyst client - I create a Nostr NFC "business card" which allows anyone to find my profile with a tap ### Inter-Op All The Things! Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities. - A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"), - A lightweight data distribution network (Nostr relays), - A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post. The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network. Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover– - NFC cards integrated with Nostr (in this post), - Workflow Automations integrated with Nostr, - AI LLMs integrated with Nostr. #### The "Nostr:" URI One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that? A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet. A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network. This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies. ### Nostr and NFC Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing. NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery). When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event. This inter-op allows us to bridge the physical world to Nostr with just a tap. #### Many useful ideas There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle? - Nostr NFC "login cards" – tap to log into Amethyst on Android, - Nostr NFC "business cards" – give to connections so they can tap to load your npub, - Nostr NFC "payment cards" – integrating lightning network or ecash, - Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat, - Integrations with other access control systems, - Integrations with other home automation systems, - Many more ... To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same. ### Nostr Login Card You can use an NFC card to log into your Nostr client. Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login. - A secure method for logging in - Optionally keeps no log in history on the device after logout - Does not require users to know or understand how keys work - Keys are kept secure on a physically-separated card to reduce risk of compromise Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards. I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3). Here's how you set it up at a high level– 1. Buy yourself some NFC cards 2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec" 3. Write the nencryptsec to the NFC card as a custom URI 4. Tap to load the login screen, and enter your password to login Here it is in detail– #### Buy yourself some NFC cards I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary. #### Get your Nostr key ready Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us. 1. Login to Amethyst with your nsec, 2. Open the sidebar and click "Backup Keys", 3. Enter a password, and click "Encrypt and my secret key", 4. It will add the password-protected key to your clipboard in the format "ncryptsec1...", 5. Remember to backup your password. #### Write the ncryptsec to the NFC card 1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK, 4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag", 5. Place your NFC card against your phone, and it will write to the card, 6. Your card is ready. #### Tap to load the login screen Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password. Once you enter your password, Amethyst will decrypt your nsec and log you in. Optionally, you can also set the app to forget you once you log out. You have created a Nostr NFC "login card". ### Nostr Business Card You can use another NFC card to give anyone you meet a link straight to your Nostr profile. I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same. To create your Nostr NFC "business card" is even easier than your NFC "login card". 1. Buy yourself some NFC cards, 2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"), 4. Your card is ready. Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page. You have created a Nostr NFC "business card". ### What I Did Wrong I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general - When password-protecting your nsec, don't forget the password! - When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work. ### What's Next Over my first four blogs I have explored creating a good Nostr setup - [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw) - [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je) - [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0) - [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e) Over the next few blogs I will be exploring different types of Nostr inter-op - NFC cards integrated with Nostr (this post) - Workflow Automations integrated with Nostr - AI LLMs integrated with Nostr Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr.
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08### Tldr - Nostr is an open protocol which is interoperable with all kinds of other technologies - You can use this interoperability to create custom solutions - Nostr apps define a custom URI scheme handler "nostr:" - In this blog I use this to integrate Nostr with NFC cards - I create a Nostr NFC "login card" which allows me to log into Amethyst client - I create a Nostr NFC "business card" which allows anyone to find my profile with a tap ### Inter-Op All The Things! Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities. - A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"), - A lightweight data distribution network (Nostr relays), - A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post. The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network. Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover– - NFC cards integrated with Nostr (in this post), - Workflow Automations integrated with Nostr, - AI LLMs integrated with Nostr. #### The "Nostr:" URI One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that? A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet. A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network. This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies. ### Nostr and NFC Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing. NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery). When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event. This inter-op allows us to bridge the physical world to Nostr with just a tap. #### Many useful ideas There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle? - Nostr NFC "login cards" – tap to log into Amethyst on Android, - Nostr NFC "business cards" – give to connections so they can tap to load your npub, - Nostr NFC "payment cards" – integrating lightning network or ecash, - Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat, - Integrations with other access control systems, - Integrations with other home automation systems, - Many more ... To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same. ### Nostr Login Card You can use an NFC card to log into your Nostr client. Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login. - A secure method for logging in - Optionally keeps no log in history on the device after logout - Does not require users to know or understand how keys work - Keys are kept secure on a physically-separated card to reduce risk of compromise Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards. I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3). Here's how you set it up at a high level– 1. Buy yourself some NFC cards 2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec" 3. Write the nencryptsec to the NFC card as a custom URI 4. Tap to load the login screen, and enter your password to login Here it is in detail– #### Buy yourself some NFC cards I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary. #### Get your Nostr key ready Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us. 1. Login to Amethyst with your nsec, 2. Open the sidebar and click "Backup Keys", 3. Enter a password, and click "Encrypt and my secret key", 4. It will add the password-protected key to your clipboard in the format "ncryptsec1...", 5. Remember to backup your password. #### Write the ncryptsec to the NFC card 1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK, 4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag", 5. Place your NFC card against your phone, and it will write to the card, 6. Your card is ready. #### Tap to load the login screen Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password. Once you enter your password, Amethyst will decrypt your nsec and log you in. Optionally, you can also set the app to forget you once you log out. You have created a Nostr NFC "login card". ### Nostr Business Card You can use another NFC card to give anyone you meet a link straight to your Nostr profile. I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same. To create your Nostr NFC "business card" is even easier than your NFC "login card". 1. Buy yourself some NFC cards, 2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"), 4. Your card is ready. Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page. You have created a Nostr NFC "business card". ### What I Did Wrong I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general - When password-protecting your nsec, don't forget the password! - When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work. ### What's Next Over my first four blogs I have explored creating a good Nostr setup - [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw) - [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je) - [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0) - [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e) Over the next few blogs I will be exploring different types of Nostr inter-op - NFC cards integrated with Nostr (this post) - Workflow Automations integrated with Nostr - AI LLMs integrated with Nostr Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr. @ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
@ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart. @ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history? As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times. At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols. The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)? **As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).** At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. ## **Open-source matters** When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. ## **Open-source is for your friends, and enemies** In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. ## **Limiting open-source threatens our own advancement** If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols. The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. *Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).*
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history? As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times. At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols. The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)? **As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).** At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. ## **Open-source matters** When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. ## **Open-source is for your friends, and enemies** In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. ## **Limiting open-source threatens our own advancement** If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols. The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. *Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).* @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集: --- 免责申明: 在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。 | 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) | ` 持续更新。。。` --- ### 推广: 访问不了openai,去`低调云`购买VPN。 官网:https://didiaocloud.xyz 邀请码:`w9AjVJit` 价格低至1元。
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集: --- 免责申明: 在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。 | 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) | ` 持续更新。。。` --- ### 推广: 访问不了openai,去`低调云`购买VPN。 官网:https://didiaocloud.xyz 邀请码:`w9AjVJit` 价格低至1元。 @ 0e501ec7:de5ef3a4
2024-10-30 17:25:51From now on, when, i open my phibe for distraction, i will write something, anything, cheers Okay, daarnet heeft het niet gewerkt. Nu wel? of houdt het me nu tegen van iets anders te gaan doen? bof ook oke. Het ruikt hier naar kak en da stoort mij zohard, zeer afleidend. Vandaag was een goeie dag, we zijn in de voormiddag een walbootboom tegen gekomen, en later, in Vailly sur aisne, heb ik die allemaal gekraakt terwijl Tim de kettingen kuiste. Was wel leuk, al kreeg ik er rugpijn van, net als nu. Zitten geeft mij meer rugpijn dan fietsen deze dagen, surtout zitten en iets doen met mijn handen, mijn rug sen schouders gaan dan als een egeltje poef inelkaar. We zitten nu een beetje in een maanlandschap, temidden industriele velden, bij een kleine haag, sleedoorn. We hebben iets te lang doorgefietst, we passeerden een goeie plek on half zes, maar toen kwam de schemering en sloeg de vermoeidheid toe net voor we toekwamen. Ik ben moe, ook al hebben we niet zoveel gefietst vandaag, nog geen 50km. We hebben batuurlijk wel 3 uur op het kerkplein van Vailly gezeten. Was heel leuk om het rustige dorpje, waar nog wel een beetje leven was, een bakker, een traiteur, een paar winkels, zo te zien. Mensen passeerden, zeiden goeiendag, smakelijk, of kwamen een hele babbel doen. Tussendoor luisterde ik wat muziek. Een heel leuk werkke, walnoten kraken, ik denk dat ik nog niet vaak zo van de herfst genoten heb als daar, op dat bankje. De kleuren in het bos, en de dans van de spreeuwen stonden mij nog kevendig voor. De mensen wensten ons veel succes, je zag dat ze ons zot vonden om door de grijze herfst te fietsen. Vanaf hier is er een grote oranje vlek op de horizon te zien, de stad van licht. Parijs!
@ 0e501ec7:de5ef3a4
2024-10-30 17:25:51From now on, when, i open my phibe for distraction, i will write something, anything, cheers Okay, daarnet heeft het niet gewerkt. Nu wel? of houdt het me nu tegen van iets anders te gaan doen? bof ook oke. Het ruikt hier naar kak en da stoort mij zohard, zeer afleidend. Vandaag was een goeie dag, we zijn in de voormiddag een walbootboom tegen gekomen, en later, in Vailly sur aisne, heb ik die allemaal gekraakt terwijl Tim de kettingen kuiste. Was wel leuk, al kreeg ik er rugpijn van, net als nu. Zitten geeft mij meer rugpijn dan fietsen deze dagen, surtout zitten en iets doen met mijn handen, mijn rug sen schouders gaan dan als een egeltje poef inelkaar. We zitten nu een beetje in een maanlandschap, temidden industriele velden, bij een kleine haag, sleedoorn. We hebben iets te lang doorgefietst, we passeerden een goeie plek on half zes, maar toen kwam de schemering en sloeg de vermoeidheid toe net voor we toekwamen. Ik ben moe, ook al hebben we niet zoveel gefietst vandaag, nog geen 50km. We hebben batuurlijk wel 3 uur op het kerkplein van Vailly gezeten. Was heel leuk om het rustige dorpje, waar nog wel een beetje leven was, een bakker, een traiteur, een paar winkels, zo te zien. Mensen passeerden, zeiden goeiendag, smakelijk, of kwamen een hele babbel doen. Tussendoor luisterde ik wat muziek. Een heel leuk werkke, walnoten kraken, ik denk dat ik nog niet vaak zo van de herfst genoten heb als daar, op dat bankje. De kleuren in het bos, en de dans van de spreeuwen stonden mij nog kevendig voor. De mensen wensten ons veel succes, je zag dat ze ons zot vonden om door de grijze herfst te fietsen. Vanaf hier is er een grote oranje vlek op de horizon te zien, de stad van licht. Parijs! @ 0e501ec7:de5ef3a4
2024-10-30 17:21:46Buizerd in de mist. Spreeuwen op een elektriciteitspaal. Je komt een beetje dichter, ze zwermen op in een dansende wolk. Zwerm voor mij niet identificeerbaar, tsjirpende vogels. Een blaadje valt, bijna in je pot met thee. Aan een hoge tak, maar toch de onderste, hangt een verloren vissershaak. Het water aan de kant ziet er vies en slijmerig uit. Vannacht was ik bang erin te vallen, slaapdronken op tocht naar een plek om pipi te doen. Het verlangen naar een middagmaal zonder pindakaas. Een klein lapje kleinschalige landbouw, met groentebedden op mensenmaat, in de zee van industrie-veld. In de verte een boer die met zijn halve oorlogsmachine zijn gewas beschermd. In de bossen hangt het vol lianen, veel meer dan thuis. Op de weg een overreden marter. Naast de weg, dappere kamille, teder bloeiend. Als de schemering valt: vermoeidheid. In de nacht stilte, gepruttel van ons stoofpotje, aangevuurd met brandalcool. In de ochtend: mist. Een buizerd.
@ 0e501ec7:de5ef3a4
2024-10-30 17:21:46Buizerd in de mist. Spreeuwen op een elektriciteitspaal. Je komt een beetje dichter, ze zwermen op in een dansende wolk. Zwerm voor mij niet identificeerbaar, tsjirpende vogels. Een blaadje valt, bijna in je pot met thee. Aan een hoge tak, maar toch de onderste, hangt een verloren vissershaak. Het water aan de kant ziet er vies en slijmerig uit. Vannacht was ik bang erin te vallen, slaapdronken op tocht naar een plek om pipi te doen. Het verlangen naar een middagmaal zonder pindakaas. Een klein lapje kleinschalige landbouw, met groentebedden op mensenmaat, in de zee van industrie-veld. In de verte een boer die met zijn halve oorlogsmachine zijn gewas beschermd. In de bossen hangt het vol lianen, veel meer dan thuis. Op de weg een overreden marter. Naast de weg, dappere kamille, teder bloeiend. Als de schemering valt: vermoeidheid. In de nacht stilte, gepruttel van ons stoofpotje, aangevuurd met brandalcool. In de ochtend: mist. Een buizerd. @ 4c48cf05:07f52b80
2024-10-30 01:03:42> I believe that five years from now, access to artificial intelligence will be akin to what access to the Internet represents today. It will be the greatest differentiator between the haves and have nots. Unequal access to artificial intelligence will exacerbate societal inequalities and limit opportunities for those without access to it. Back in April, the AI Index Steering Committee at the Institute for Human-Centered AI from Stanford University released [The AI Index 2024 Annual Report](https://aiindex.stanford.edu/report/). Out of the extensive report (502 pages), I chose to focus on the chapter dedicated to Public Opinion. People involved with AI live in a bubble. We all know and understand AI and therefore assume that everyone else does. But, is that really the case once you step out of your regular circles in Seattle or Silicon Valley and hit Main Street? # Two thirds of global respondents have a good understanding of what AI is The exact number is 67%. My gut feeling is that this number is way too high to be realistic. At the same time, 63% of respondents are aware of ChatGPT so maybe people are confounding AI with ChatGPT? If so, there is so much more that they won't see coming. This number is important because you need to see every other questions and response of the survey through the lens of a respondent who believes to have a good understanding of what AI is. # A majority are nervous about AI products and services 52% of global respondents are nervous about products and services that use AI. Leading the pack are Australians at 69% and the least worried are Japanise at 23%. U.S.A. is up there at the top at 63%. Japan is truly an outlier, with most countries moving between 40% and 60%. # Personal data is the clear victim Exaclty half of the respondents believe that AI companies will protect their personal data. And the other half believes they won't. # Expected benefits Again a majority of people (57%) think that it will change how they do their jobs. As for impact on your life, top hitters are getting things done faster (54%) and more entertainment options (51%). The last one is a head scratcher for me. Are people looking forward to AI generated movies?  # Concerns Remember the 57% that thought that AI will change how they do their jobs? Well, it looks like 37% of them expect to lose it. Whether or not this is what will happen, that is a very high number of people who have a direct incentive to oppose AI. Other key concerns include: - Misuse for nefarious purposes: 49% - Violation of citizens' privacy: 45% # Conclusion This is the first time I come across this report and I wil make sure to follow future annual reports to see how these trends evolve. **Overall, people are worried about AI. There are many things that could go wrong and people perceive that both jobs and privacy are on the line.** --- Full citation: *Nestor Maslej, Loredana Fattorini, Raymond Perrault, Vanessa Parli, Anka Reuel, Erik Brynjolfsson, John Etchemendy, Katrina Ligett, Terah Lyons, James Manyika, Juan Carlos Niebles, Yoav Shoham, Russell Wald, and Jack Clark, “The AI Index 2024 Annual Report,” AI Index Steering Committee, Institute for Human-Centered AI, Stanford University, Stanford, CA, April 2024.* The AI Index 2024 Annual Report by Stanford University is licensed under [Attribution-NoDerivatives 4.0 International](https://creativecommons.org/licenses/by-nd/4.0/?ref=chooser-v1).
@ 4c48cf05:07f52b80
2024-10-30 01:03:42> I believe that five years from now, access to artificial intelligence will be akin to what access to the Internet represents today. It will be the greatest differentiator between the haves and have nots. Unequal access to artificial intelligence will exacerbate societal inequalities and limit opportunities for those without access to it. Back in April, the AI Index Steering Committee at the Institute for Human-Centered AI from Stanford University released [The AI Index 2024 Annual Report](https://aiindex.stanford.edu/report/). Out of the extensive report (502 pages), I chose to focus on the chapter dedicated to Public Opinion. People involved with AI live in a bubble. We all know and understand AI and therefore assume that everyone else does. But, is that really the case once you step out of your regular circles in Seattle or Silicon Valley and hit Main Street? # Two thirds of global respondents have a good understanding of what AI is The exact number is 67%. My gut feeling is that this number is way too high to be realistic. At the same time, 63% of respondents are aware of ChatGPT so maybe people are confounding AI with ChatGPT? If so, there is so much more that they won't see coming. This number is important because you need to see every other questions and response of the survey through the lens of a respondent who believes to have a good understanding of what AI is. # A majority are nervous about AI products and services 52% of global respondents are nervous about products and services that use AI. Leading the pack are Australians at 69% and the least worried are Japanise at 23%. U.S.A. is up there at the top at 63%. Japan is truly an outlier, with most countries moving between 40% and 60%. # Personal data is the clear victim Exaclty half of the respondents believe that AI companies will protect their personal data. And the other half believes they won't. # Expected benefits Again a majority of people (57%) think that it will change how they do their jobs. As for impact on your life, top hitters are getting things done faster (54%) and more entertainment options (51%). The last one is a head scratcher for me. Are people looking forward to AI generated movies?  # Concerns Remember the 57% that thought that AI will change how they do their jobs? Well, it looks like 37% of them expect to lose it. Whether or not this is what will happen, that is a very high number of people who have a direct incentive to oppose AI. Other key concerns include: - Misuse for nefarious purposes: 49% - Violation of citizens' privacy: 45% # Conclusion This is the first time I come across this report and I wil make sure to follow future annual reports to see how these trends evolve. **Overall, people are worried about AI. There are many things that could go wrong and people perceive that both jobs and privacy are on the line.** --- Full citation: *Nestor Maslej, Loredana Fattorini, Raymond Perrault, Vanessa Parli, Anka Reuel, Erik Brynjolfsson, John Etchemendy, Katrina Ligett, Terah Lyons, James Manyika, Juan Carlos Niebles, Yoav Shoham, Russell Wald, and Jack Clark, “The AI Index 2024 Annual Report,” AI Index Steering Committee, Institute for Human-Centered AI, Stanford University, Stanford, CA, April 2024.* The AI Index 2024 Annual Report by Stanford University is licensed under [Attribution-NoDerivatives 4.0 International](https://creativecommons.org/licenses/by-nd/4.0/?ref=chooser-v1). @ 4ba8e86d:89d32de4
2024-10-25 11:40:05A loja Aurora vem com um excelente design, interface de usuário amigável para iniciantes e muitos recursos. A loja Aurora foi originalmente baseada na loja Yalp de Sergei Yeriomin, mas a versão 3.0 passou do zero para a conclusão seguindo o Material Design reescrito para rodar em todos os dispositivos Android 5.0. Dentre as diversas características oferecidas pela Aurora Store, destacam-se: - Login Anônimo: Para garantir sua privacidade, você pode fazer login anonimamente, assegurando que suas atividades permaneçam confidenciais. - Login do Google: Além do anonimato, a opção de login do Google permite acessar aplicativos pagos e instalar versões beta. - Falsificação de Dispositivo: Caso um aplicativo não esteja disponível para o seu dispositivo, você pode recorrer à funcionalidade de falsificação de dispositivo, permitindo a instalação. - Filtragem de Aplicativos F-Droid: A possibilidade de filtrar aplicativos do F-Droid evita que eles apareçam em sua lista de atualizações. - Aplicativos na Lista Negra: Ao adicionar aplicativos à lista negra, você mantém o Google no escuro quanto aos aplicativos instalados. A loja de aplicativos se apresenta com um design clássico, apresentando uma capa de apps e jogos em destaque, proporcionando um visual convidativo. A aba de aplicativos instalados permite uma gestão mais eficiente, possibilitando atualizações automáticas para a versão mais recente disponível. A busca por aplicativos é facilitada por categorias que abrangem diversos interesses, como fotografia, música e áudio, compras, personalização, livros e quadrinhos, entre outras. A eficaz função de busca permite localizar aplicativos específicos de maneira rápida e fácil. A Aurora Store se diferencia pela tecnologia de pesquisa única, agilizando a descoberta de aplicativos em questão de segundos. Além disso, a loja vem com a licença GPLv3, reforçando seu compromisso com o software livre. Privacidade é um foco central da Aurora Store, sendo considerada uma excelente alternativa para quem preza por manter suas informações pessoais protegidas. O aplicativo suporta contas pessoais e permite downloads com contas anônimas, assegurando que suas atividades não estejam vinculadas a você. Com a integração do Exodus, a Aurora Store verifica rastreadores presentes nos códigos dos aplicativos, proporcionando uma visão mais transparente das informações coletadas. O aplicativo se destaca por ser livre de anúncios e pop-ups, proporcionando uma experiência de uso mais limpa. O suporte ao modo escuro oferece conforto visual em ambientes com pouca luz ou durante a noite. A Aurora Store é uma alternativa valiosa à Google Play Store, oferecendo um ambiente mais privado, recursos robustos e um design elegante que visa aprimorar a experiência do usuário em busca e gerenciamento de aplicativos. https://github.com/whyorean/AuroraStore https://f-droid.org/packages/com.aurora.store/ https://gitlab.com/AuroraOSS/AuroraStore/-/releases
@ 4ba8e86d:89d32de4
2024-10-25 11:40:05A loja Aurora vem com um excelente design, interface de usuário amigável para iniciantes e muitos recursos. A loja Aurora foi originalmente baseada na loja Yalp de Sergei Yeriomin, mas a versão 3.0 passou do zero para a conclusão seguindo o Material Design reescrito para rodar em todos os dispositivos Android 5.0. Dentre as diversas características oferecidas pela Aurora Store, destacam-se: - Login Anônimo: Para garantir sua privacidade, você pode fazer login anonimamente, assegurando que suas atividades permaneçam confidenciais. - Login do Google: Além do anonimato, a opção de login do Google permite acessar aplicativos pagos e instalar versões beta. - Falsificação de Dispositivo: Caso um aplicativo não esteja disponível para o seu dispositivo, você pode recorrer à funcionalidade de falsificação de dispositivo, permitindo a instalação. - Filtragem de Aplicativos F-Droid: A possibilidade de filtrar aplicativos do F-Droid evita que eles apareçam em sua lista de atualizações. - Aplicativos na Lista Negra: Ao adicionar aplicativos à lista negra, você mantém o Google no escuro quanto aos aplicativos instalados. A loja de aplicativos se apresenta com um design clássico, apresentando uma capa de apps e jogos em destaque, proporcionando um visual convidativo. A aba de aplicativos instalados permite uma gestão mais eficiente, possibilitando atualizações automáticas para a versão mais recente disponível. A busca por aplicativos é facilitada por categorias que abrangem diversos interesses, como fotografia, música e áudio, compras, personalização, livros e quadrinhos, entre outras. A eficaz função de busca permite localizar aplicativos específicos de maneira rápida e fácil. A Aurora Store se diferencia pela tecnologia de pesquisa única, agilizando a descoberta de aplicativos em questão de segundos. Além disso, a loja vem com a licença GPLv3, reforçando seu compromisso com o software livre. Privacidade é um foco central da Aurora Store, sendo considerada uma excelente alternativa para quem preza por manter suas informações pessoais protegidas. O aplicativo suporta contas pessoais e permite downloads com contas anônimas, assegurando que suas atividades não estejam vinculadas a você. Com a integração do Exodus, a Aurora Store verifica rastreadores presentes nos códigos dos aplicativos, proporcionando uma visão mais transparente das informações coletadas. O aplicativo se destaca por ser livre de anúncios e pop-ups, proporcionando uma experiência de uso mais limpa. O suporte ao modo escuro oferece conforto visual em ambientes com pouca luz ou durante a noite. A Aurora Store é uma alternativa valiosa à Google Play Store, oferecendo um ambiente mais privado, recursos robustos e um design elegante que visa aprimorar a experiência do usuário em busca e gerenciamento de aplicativos. https://github.com/whyorean/AuroraStore https://f-droid.org/packages/com.aurora.store/ https://gitlab.com/AuroraOSS/AuroraStore/-/releases @ 0e501ec7:de5ef3a4
2024-10-24 20:03:28Ik maak even een kleine sprong in de tijd, stichting Elzeard bespreek ik later nog ;) Vandaag (24/10) vertrokken we bij Patsy en Els. Patsy is de meter van Tim, en hij heeft een kleine traditie om altijd bij hun langs te gaan als hij in de Ardennen fietst. Ze kochten ongeveer tien jaar geleden een wei in Marcourt, en besloten op een gegeven moment om daar te gaan wonen en een huis te bouwen. Ze hebben een bijna-passief woning, een leuke moestuin en veel fruitbomen, en op de wei staan er schapen van een zekere Eddy. Ze spreken aardig wat frans, en zijn zeer betrokken bij het sociale leven in het dorp! Niet zoals de tweede-verblijf-vlamingen die in grote getallen rust opzoeken in de Ardennen dus. We hielpen bij hun in de tuin, brandhout zagen en kappen, hooi leggen in de moestuin (ze doen geen bodembewerking! Voeren enkel hooi aan om de structuur te verbeteren en kruid tegen te werken). Daarnaast hielpen we ook met wat bomen en struiken te verplanten, en deed Tim zijn job als fietsenmaker. We aten verrukkelijk in de avond, van de heerlijke kookkunsten van Els. Een van de avonden (triggerwarning: vlees eten) was het een gerecht met vlees van een Lam, een van de diertjes die op de wei zelf geboren was en gegroeid. Tot het dus geslacht werd, en Patsy en Els er hun deeltje van kregen/kochten. Ik vond het wel een heftige ervaring om dat te eten, maar het voelde niet persé slecht. Denk ik. Al zag ik wel af en toe een Lammetje door een veld huppelen als ik met mijn ogen knipperde. Het waren fijne dagen bij hun, maar het deed ook deugd om weer verder te gaan: gewoon op de fiets, en niet meer te hoeven socialiseren. In het begin van de dag moest ik nog even op gang komen, had wat pijn aan mijn rug van een forse beklimming zonder opgewarmd te zijn (het was ook een koude ochtend). Ook was Tim een paar keer een beetje fors (ms was het ook voor hem ochtend, kan zijn :) )waardoor ik mij even niet heel top voelde, moe en wat verdrietig, niet zo geborgen en energiek. Ik begon te twijfelen of ik wel sterk genoeg was voor deze reis, om met Tim mee te kunnen, om zonder veilige haven te zijn. Na een tijdje chieken en tobben, probeerde ik naar het landschap te kijken, en dat als veilige haven te zien. Niet zo heel makkelijk, geen vanzelfsprekende veilige haven, je moet eerst voorbij het landschap als decor, en het landschap als vluchtige voorbijgaandheid. Maar het hielp wel. De glooiingen van de Aarde, hun heuvels, de Bomen in de wind, de zachte Wolken met hun zwevende texturen, de verbaasde Koeien, het is ook wel thuis. Ik ben ook hier thuis. (Deze avond toen we begonnen te koken kwam een Reetje op bezoek, keek even heel doordringend en stoof rond ons weg. Dag Reetje; tot ziens.) Daarna overwon ik mijn obsakels en begon ik erover tegen Tim, niet gemakkelijk, maar was wel heel fijn, hij begreep het wel, luisterde wel. Zei ook dat hij zich al afvroeg of er iets was (zie je wel). Daarna voelte ik mij dus helemaal beter, en hadden we nog een zalige fietstocht. De zon kwam erdoor, het was warm, de heuvels gingen omhoog en omlaag, zoeffff. Ergens verloor ik mijn handschoenen, die had ik los op mijn bagage gelegd en was dan vertrokken. Dus: terug! Gelukkig lagen ze niet al te ver weg, ze waren pas bij een grote boebel van mijn bagage gekieperd. We fietsten uiteindelijk 67km, en stegen bijna 1000m. Echt wel de zwaarste tocht tot nu, maar fysiek voelde het al een pak minder lastig als in de eerste weken. Mischief ben ik dan toch (fysiek) sterk genoeg? We passeerden onderweg nog het meest cute (cuteste?) Bio-winkeltje ooit, een klein kamertje vol met verse groenten, waar we waterkers en eitjes en nog een brood voor morgenvroeg kochten. Nu liggen we hier in een bos naast Sovet, en gaan we morgen weer verder. Slaapwel!
@ 0e501ec7:de5ef3a4
2024-10-24 20:03:28Ik maak even een kleine sprong in de tijd, stichting Elzeard bespreek ik later nog ;) Vandaag (24/10) vertrokken we bij Patsy en Els. Patsy is de meter van Tim, en hij heeft een kleine traditie om altijd bij hun langs te gaan als hij in de Ardennen fietst. Ze kochten ongeveer tien jaar geleden een wei in Marcourt, en besloten op een gegeven moment om daar te gaan wonen en een huis te bouwen. Ze hebben een bijna-passief woning, een leuke moestuin en veel fruitbomen, en op de wei staan er schapen van een zekere Eddy. Ze spreken aardig wat frans, en zijn zeer betrokken bij het sociale leven in het dorp! Niet zoals de tweede-verblijf-vlamingen die in grote getallen rust opzoeken in de Ardennen dus. We hielpen bij hun in de tuin, brandhout zagen en kappen, hooi leggen in de moestuin (ze doen geen bodembewerking! Voeren enkel hooi aan om de structuur te verbeteren en kruid tegen te werken). Daarnaast hielpen we ook met wat bomen en struiken te verplanten, en deed Tim zijn job als fietsenmaker. We aten verrukkelijk in de avond, van de heerlijke kookkunsten van Els. Een van de avonden (triggerwarning: vlees eten) was het een gerecht met vlees van een Lam, een van de diertjes die op de wei zelf geboren was en gegroeid. Tot het dus geslacht werd, en Patsy en Els er hun deeltje van kregen/kochten. Ik vond het wel een heftige ervaring om dat te eten, maar het voelde niet persé slecht. Denk ik. Al zag ik wel af en toe een Lammetje door een veld huppelen als ik met mijn ogen knipperde. Het waren fijne dagen bij hun, maar het deed ook deugd om weer verder te gaan: gewoon op de fiets, en niet meer te hoeven socialiseren. In het begin van de dag moest ik nog even op gang komen, had wat pijn aan mijn rug van een forse beklimming zonder opgewarmd te zijn (het was ook een koude ochtend). Ook was Tim een paar keer een beetje fors (ms was het ook voor hem ochtend, kan zijn :) )waardoor ik mij even niet heel top voelde, moe en wat verdrietig, niet zo geborgen en energiek. Ik begon te twijfelen of ik wel sterk genoeg was voor deze reis, om met Tim mee te kunnen, om zonder veilige haven te zijn. Na een tijdje chieken en tobben, probeerde ik naar het landschap te kijken, en dat als veilige haven te zien. Niet zo heel makkelijk, geen vanzelfsprekende veilige haven, je moet eerst voorbij het landschap als decor, en het landschap als vluchtige voorbijgaandheid. Maar het hielp wel. De glooiingen van de Aarde, hun heuvels, de Bomen in de wind, de zachte Wolken met hun zwevende texturen, de verbaasde Koeien, het is ook wel thuis. Ik ben ook hier thuis. (Deze avond toen we begonnen te koken kwam een Reetje op bezoek, keek even heel doordringend en stoof rond ons weg. Dag Reetje; tot ziens.) Daarna overwon ik mijn obsakels en begon ik erover tegen Tim, niet gemakkelijk, maar was wel heel fijn, hij begreep het wel, luisterde wel. Zei ook dat hij zich al afvroeg of er iets was (zie je wel). Daarna voelte ik mij dus helemaal beter, en hadden we nog een zalige fietstocht. De zon kwam erdoor, het was warm, de heuvels gingen omhoog en omlaag, zoeffff. Ergens verloor ik mijn handschoenen, die had ik los op mijn bagage gelegd en was dan vertrokken. Dus: terug! Gelukkig lagen ze niet al te ver weg, ze waren pas bij een grote boebel van mijn bagage gekieperd. We fietsten uiteindelijk 67km, en stegen bijna 1000m. Echt wel de zwaarste tocht tot nu, maar fysiek voelde het al een pak minder lastig als in de eerste weken. Mischief ben ik dan toch (fysiek) sterk genoeg? We passeerden onderweg nog het meest cute (cuteste?) Bio-winkeltje ooit, een klein kamertje vol met verse groenten, waar we waterkers en eitjes en nog een brood voor morgenvroeg kochten. Nu liggen we hier in een bos naast Sovet, en gaan we morgen weer verder. Slaapwel! @ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais. Recursos e Funcionalidades. O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório. Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes. O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets. Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo: 1. Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional. 2. Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes. 3. Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações. O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável. https://www.collaboraoffice.com/ https://github.com/CollaboraOnline/online
@ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais. Recursos e Funcionalidades. O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório. Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes. O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets. Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo: 1. Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional. 2. Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes. 3. Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações. O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável. https://www.collaboraoffice.com/ https://github.com/CollaboraOnline/online @ 0e501ec7:de5ef3a4
2024-10-23 20:28:38Het is al een hele tijd geleden dat ik nog eens een blogpost heb gemaakt, mijn excuses hiervoor. Het is nog niet zo eenvoudig om een rustig moment te vinden en daar dan ook het initiatief te verzamelen om te beginnen schrijven. We zijn ondertussen alweer wat opgeschoten, richting het zuiden. Het voelt ook al zo, de laatste dagen is het prachtig weer, een heerlijk zonnetje! Gisteren had ik zelfs al te warm! Maar ik ben hmm redelijk zeker dat het niet ligt aan onze zeer zuidelijke positie (de Ardennen), maar gewoon aan geluk met het weer. Denk je niet? Ik maak even een recap van wat er allemaal gebeurd is sinds de vorige keer, dan zijn jullie weer op de hoogte. Of toch voor degene die niet ondertussen stiekem Tim zijn blog hebben gelezen, want daar zijn er actuelere updates te vinden. Tim is een gedisciplineerd en trouwe blogger, niet zoals mijn getruntel en uitgestel. Dus na de fameuze vrijdag waarin we houtverbindingen leerden maken, kwam de werkdag op het Abtshof. We hielpen eerst met Pieter en Evelien in de tuin: winterwortels en patatten oogsten! De Woelratten zouden er anders spoedig aan beginnen, eigenlijk waren ze al begonnen. Dus de wortels moesten uit de grond, om dan ingekuild in de kelder gezet te worden (dat zouden we uiteindelijk maandag doen). We probeerden ook zoveel mogelijk kruid weg te halen (niet on, gewoon kruid, veel eetbaar, sommigen medicinaal, maar ook in de weg van de zo gewenste groentjes!) (er stond zelfs oregano tussen!). Vele wortels en aardappels kwamen beschadigd uit te grond, die hielden we apart omdat ze niet meer bewaard konden worden. Daar aten we dan de komende 4 dagen van. Telkens op een andere wijze: aardappelpuree met wortels, patatjes met wortels in de oven, in de pan gebakken worteltjes... Na het oogsten en wieden kwam Pieter af met een freesmachien: om de bovenste tien centimeter helemaal los te werken en om te woelen. Dat was een vreselijke dieselduivel, lawaai, stank, doodsangst voor de freesmessen (met een eerste keer zo een machien te gebruiken komen er natuurlijk ook gruwelverhalen, dan pas je beter op), maar wel een coole ervaring! Zo lag de Bodem los voor de tere spinazieplantjes. Evelien wou liever niet frezen, omdat de bodemstructuur op lange termijn minder goed wordt, dus deden we bepaalde stukken wel en andere niet. Daarna gingen we helpen binnen: ramen sappen. Blijkbaar een ander woord voor in-oliën :). Wel een leuk werkje, zorgzaam voor het hout, zachtjes met de borstel heen en weer. Zondag rustdag! Iedereen gaan stemmen, wij niets te doen. Ik heb dan maar de tijd genomen een beetje te lezen in The Flowering Wand (zeer goed boek, "Rewilding the sacred masculine"), en een paar brieven te schrijven en te versturen via mail. Daarna ging ik Tim vergezellen, die naarstig in de weer was in het houtatelier. Onze 'introductiecursus' had als eindwerk het maken van een rek met houtverbindingen, dus dan moest dat af geraken! Tim ging daar echt hard in: uiteindelijk heeft hij maandagavond tot 1u 's nachts doorgewerkt! Zotte kerel, respect. Na het houtatelier-werk, en avondeten, gingen Tim en Teo nog naar de Kat, een traditioneel dorpscafé om de hoek. Daar leerden ze de lokale bevolking wat kennen, keken ze een dartswedstrijd, en babbelden er gretig op los. Ik was ondertussen al naar bed, natuurlijk. De dagen erna werkten we ook verder aan onze kast, daar kwam wel wat bij kijken! Het was ook nooit heel gemakkelijk om allemaal op elkaar afgestemd te zijn, en te begrijpen wat de andere juist bedoelt bij besprekingen over hoe in godsnaam we dat aanpakken. Maar uiteindelijk zijn we allemaal wel heel trots op het resultaat, en hij is al in gebruik :)). Jakob was ondertussen bezig met parket te leggen in de toekomstige woning van Pieter en Kim. Toen de stagiair weg was, mocht ik vervang-stagair spelen. Leuk! Parket leggen is uiteindelijk helemaal niet zo moeilijk, al is het soms wat gepruts. Of, Jakob heeft het gewoon heel goed uitgelegd, waardoor ik er snel mee weg was. Jakob was de echte held van onze week bij het Abtshof, met zoveel geduld en enthousiasme heeft hij ons echt een beetje in zijn vak geïntroduceerd. Hij was ook zeer gelukkig dat wij enthousiast waren, en zei dat we zeker terug mochten komen om meer te leren en te helpen. Klinkt niet slecht :) Helemaal op het einde van de laatste dag vroeg Pieter of we nog konden helpen iets te dragen. Zware steen was dat! Ik stond aan de buitenkant, en met mijn lange benen kwam er natuurlijk veel gewicht op mij. Te zwaar! Dat was niet goed voor mijn rug, en dat heb ik de dag erna nog sterk gevoeld bij het fietsen. Het is wel wat lastig met die rug, ik hoop dat die na verloop van tijd toch terug wat sterker wordt. Ik heb niet al te veel pijn, maar voel wel snel als iets niet goed is. Opzich niet slecht, maar ik wil ook wel gewoon eens kunnen meehelpen en meewerken zonder dat die rug lastig doet. We zullen zien! Ondertussen heb ik ook van Bien toestemming gekregen om haar prachtige schriften over het Wondelbos hier te delen, ik deel een fragment dat mij roerde. "Een veldje met uitdovende zomerbloemen, een moerassig stukje land. Goud. Goud. Het veldje en mij omringend: Esdoorns. Groot en torenend, alwetend. Wilgen, bos en schiet en treur, die wiegden in de zachte wind. Sommigen sterk en doorleefd, anderen nog maar net omhooggeschoten maar toch al zoveel wijzer dan ik. Ik herinner Ik herinner me hoe ik tussen de Japanse Duizendknoop (die ondeugende doorzetter!!) wandelde ik haar daar zag. Een kloeke moeder. Grootvader van al wat leeft. Een Eik die daar zomaar stond. Hij maakte geen Eikels wat ik gek vond, want de andere Eiken doen dat wel dit jaar. Maar misschien wist deze Eik al wat er zou komen. Misschien had zij de toekomst gevoeld in haar mycelium-gebonden wortels, in their worldly, buried lungs. Maybe this Oaktree knew that their everlasting cyclic time would soon be brutally destroyed by powers beyond her. I remember looking for other Oaks. En ja hoor, een beetje verder stonden nog twee grote exemplaren. Ik vroeg de Mensen of deze drie de enige Eiken waren en zij beaamden dat. Maar Leven meet je niet volgens tijd. Tussen verschillende Grassen en ander Wild, stonden op sommigen plekken kleine stekken Eikjes, nog maar net verbonden met de Aarde. Ik herinner" Langzaam aan haal ik de achterstand in hé, nu nog maar een week. Liefs PS: blog van Tim [hier](https://timscyclethoughts.blogspot.com)! :))
@ 0e501ec7:de5ef3a4
2024-10-23 20:28:38Het is al een hele tijd geleden dat ik nog eens een blogpost heb gemaakt, mijn excuses hiervoor. Het is nog niet zo eenvoudig om een rustig moment te vinden en daar dan ook het initiatief te verzamelen om te beginnen schrijven. We zijn ondertussen alweer wat opgeschoten, richting het zuiden. Het voelt ook al zo, de laatste dagen is het prachtig weer, een heerlijk zonnetje! Gisteren had ik zelfs al te warm! Maar ik ben hmm redelijk zeker dat het niet ligt aan onze zeer zuidelijke positie (de Ardennen), maar gewoon aan geluk met het weer. Denk je niet? Ik maak even een recap van wat er allemaal gebeurd is sinds de vorige keer, dan zijn jullie weer op de hoogte. Of toch voor degene die niet ondertussen stiekem Tim zijn blog hebben gelezen, want daar zijn er actuelere updates te vinden. Tim is een gedisciplineerd en trouwe blogger, niet zoals mijn getruntel en uitgestel. Dus na de fameuze vrijdag waarin we houtverbindingen leerden maken, kwam de werkdag op het Abtshof. We hielpen eerst met Pieter en Evelien in de tuin: winterwortels en patatten oogsten! De Woelratten zouden er anders spoedig aan beginnen, eigenlijk waren ze al begonnen. Dus de wortels moesten uit de grond, om dan ingekuild in de kelder gezet te worden (dat zouden we uiteindelijk maandag doen). We probeerden ook zoveel mogelijk kruid weg te halen (niet on, gewoon kruid, veel eetbaar, sommigen medicinaal, maar ook in de weg van de zo gewenste groentjes!) (er stond zelfs oregano tussen!). Vele wortels en aardappels kwamen beschadigd uit te grond, die hielden we apart omdat ze niet meer bewaard konden worden. Daar aten we dan de komende 4 dagen van. Telkens op een andere wijze: aardappelpuree met wortels, patatjes met wortels in de oven, in de pan gebakken worteltjes... Na het oogsten en wieden kwam Pieter af met een freesmachien: om de bovenste tien centimeter helemaal los te werken en om te woelen. Dat was een vreselijke dieselduivel, lawaai, stank, doodsangst voor de freesmessen (met een eerste keer zo een machien te gebruiken komen er natuurlijk ook gruwelverhalen, dan pas je beter op), maar wel een coole ervaring! Zo lag de Bodem los voor de tere spinazieplantjes. Evelien wou liever niet frezen, omdat de bodemstructuur op lange termijn minder goed wordt, dus deden we bepaalde stukken wel en andere niet. Daarna gingen we helpen binnen: ramen sappen. Blijkbaar een ander woord voor in-oliën :). Wel een leuk werkje, zorgzaam voor het hout, zachtjes met de borstel heen en weer. Zondag rustdag! Iedereen gaan stemmen, wij niets te doen. Ik heb dan maar de tijd genomen een beetje te lezen in The Flowering Wand (zeer goed boek, "Rewilding the sacred masculine"), en een paar brieven te schrijven en te versturen via mail. Daarna ging ik Tim vergezellen, die naarstig in de weer was in het houtatelier. Onze 'introductiecursus' had als eindwerk het maken van een rek met houtverbindingen, dus dan moest dat af geraken! Tim ging daar echt hard in: uiteindelijk heeft hij maandagavond tot 1u 's nachts doorgewerkt! Zotte kerel, respect. Na het houtatelier-werk, en avondeten, gingen Tim en Teo nog naar de Kat, een traditioneel dorpscafé om de hoek. Daar leerden ze de lokale bevolking wat kennen, keken ze een dartswedstrijd, en babbelden er gretig op los. Ik was ondertussen al naar bed, natuurlijk. De dagen erna werkten we ook verder aan onze kast, daar kwam wel wat bij kijken! Het was ook nooit heel gemakkelijk om allemaal op elkaar afgestemd te zijn, en te begrijpen wat de andere juist bedoelt bij besprekingen over hoe in godsnaam we dat aanpakken. Maar uiteindelijk zijn we allemaal wel heel trots op het resultaat, en hij is al in gebruik :)). Jakob was ondertussen bezig met parket te leggen in de toekomstige woning van Pieter en Kim. Toen de stagiair weg was, mocht ik vervang-stagair spelen. Leuk! Parket leggen is uiteindelijk helemaal niet zo moeilijk, al is het soms wat gepruts. Of, Jakob heeft het gewoon heel goed uitgelegd, waardoor ik er snel mee weg was. Jakob was de echte held van onze week bij het Abtshof, met zoveel geduld en enthousiasme heeft hij ons echt een beetje in zijn vak geïntroduceerd. Hij was ook zeer gelukkig dat wij enthousiast waren, en zei dat we zeker terug mochten komen om meer te leren en te helpen. Klinkt niet slecht :) Helemaal op het einde van de laatste dag vroeg Pieter of we nog konden helpen iets te dragen. Zware steen was dat! Ik stond aan de buitenkant, en met mijn lange benen kwam er natuurlijk veel gewicht op mij. Te zwaar! Dat was niet goed voor mijn rug, en dat heb ik de dag erna nog sterk gevoeld bij het fietsen. Het is wel wat lastig met die rug, ik hoop dat die na verloop van tijd toch terug wat sterker wordt. Ik heb niet al te veel pijn, maar voel wel snel als iets niet goed is. Opzich niet slecht, maar ik wil ook wel gewoon eens kunnen meehelpen en meewerken zonder dat die rug lastig doet. We zullen zien! Ondertussen heb ik ook van Bien toestemming gekregen om haar prachtige schriften over het Wondelbos hier te delen, ik deel een fragment dat mij roerde. "Een veldje met uitdovende zomerbloemen, een moerassig stukje land. Goud. Goud. Het veldje en mij omringend: Esdoorns. Groot en torenend, alwetend. Wilgen, bos en schiet en treur, die wiegden in de zachte wind. Sommigen sterk en doorleefd, anderen nog maar net omhooggeschoten maar toch al zoveel wijzer dan ik. Ik herinner Ik herinner me hoe ik tussen de Japanse Duizendknoop (die ondeugende doorzetter!!) wandelde ik haar daar zag. Een kloeke moeder. Grootvader van al wat leeft. Een Eik die daar zomaar stond. Hij maakte geen Eikels wat ik gek vond, want de andere Eiken doen dat wel dit jaar. Maar misschien wist deze Eik al wat er zou komen. Misschien had zij de toekomst gevoeld in haar mycelium-gebonden wortels, in their worldly, buried lungs. Maybe this Oaktree knew that their everlasting cyclic time would soon be brutally destroyed by powers beyond her. I remember looking for other Oaks. En ja hoor, een beetje verder stonden nog twee grote exemplaren. Ik vroeg de Mensen of deze drie de enige Eiken waren en zij beaamden dat. Maar Leven meet je niet volgens tijd. Tussen verschillende Grassen en ander Wild, stonden op sommigen plekken kleine stekken Eikjes, nog maar net verbonden met de Aarde. Ik herinner" Langzaam aan haal ik de achterstand in hé, nu nog maar een week. Liefs PS: blog van Tim [hier](https://timscyclethoughts.blogspot.com)! :)) @ dc4cd086:cee77c06
2024-10-18 17:41:42Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content. ## Key Features: ### Video Processing: - Automatically downloads YouTube videos, transcripts, and chapter information - Splits transcripts into sections based on video chapters ### Content Summarization: - Utilizes language models to transform spoken content into clear, readable text - Formats output in AsciiDoc for improved readability and navigation - Highlights key terms and concepts with [[term]] notation for potential cross-referencing ### Diagram Extraction: - Analyzes video entropy to identify static diagram/slide sections - Provides a user-friendly GUI for manual selection of relevant time ranges - Allows users to pick representative frames from selected ranges ## Going Forward: Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care. While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs. ## Screenshots ### Frame Selection  This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection. ### Diagram Extraction  This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save. ## Links - repo: https://github.com/limina1/video_article_converter - Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE ## Output And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
@ dc4cd086:cee77c06
2024-10-18 17:41:42Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content. ## Key Features: ### Video Processing: - Automatically downloads YouTube videos, transcripts, and chapter information - Splits transcripts into sections based on video chapters ### Content Summarization: - Utilizes language models to transform spoken content into clear, readable text - Formats output in AsciiDoc for improved readability and navigation - Highlights key terms and concepts with [[term]] notation for potential cross-referencing ### Diagram Extraction: - Analyzes video entropy to identify static diagram/slide sections - Provides a user-friendly GUI for manual selection of relevant time ranges - Allows users to pick representative frames from selected ranges ## Going Forward: Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care. While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs. ## Screenshots ### Frame Selection  This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection. ### Diagram Extraction  This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save. ## Links - repo: https://github.com/limina1/video_article_converter - Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE ## Output And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3 @ 8947a945:9bfcf626
2024-10-17 08:06:55[](https://stock.adobe.com/stock-photo/id/1010191703) **สวัสดีทุกคนบน Nostr ครับ** รวมไปถึง **watchers**และ **ผู้ติดตาม**ของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย **เมื่อวันที่ 16 กย.2024** มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ  ### นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ (หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)  - Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint **0.15 - 0.2 ETH** … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ  - Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ : 1. ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา 2. ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา 3. ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา 4. ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT **0.2 ETH** ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้ **Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก** เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ) ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม ----------- ### ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร [](https://stock.adobe.com/stock-photo/id/1010196295) อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ) บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน บบโลกของ ETH **"code is law"** smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน ## Note - ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock - อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน ผลงานของผมครับ - Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon) - [HikariHarmony on Nostr](https://shorturl.at/I8Nu4) - General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen) - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
@ 8947a945:9bfcf626
2024-10-17 08:06:55[](https://stock.adobe.com/stock-photo/id/1010191703) **สวัสดีทุกคนบน Nostr ครับ** รวมไปถึง **watchers**และ **ผู้ติดตาม**ของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย **เมื่อวันที่ 16 กย.2024** มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ  ### นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ (หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)  - Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint **0.15 - 0.2 ETH** … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ  - Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ : 1. ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา 2. ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา 3. ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา 4. ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT **0.2 ETH** ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้ **Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก** เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ) ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม ----------- ### ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร [](https://stock.adobe.com/stock-photo/id/1010196295) อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ) บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน บบโลกของ ETH **"code is law"** smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน ## Note - ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock - อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน ผลงานของผมครับ - Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon) - [HikariHarmony on Nostr](https://shorturl.at/I8Nu4) - General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen) - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ @ 8947a945:9bfcf626
2024-10-17 07:33:00[](https://stock.adobe.com/stock-photo/id/1010191703) **Hello everyone on Nostr** and all my **watchers**and **followers**from DeviantArt, as well as those from other art platforms I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon. I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing **On September 16**, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.  ### Here’s a brief overview of what happened  - The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from **0.15 to 0.2 ETH**  - The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows: 1. I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused. 2. I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused. 3. I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused. 4. I asked them to wait until I could secure the funds, and they agreed to wait. The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website. This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of **0.2 ETH**. However, the site provided a wallet address for me instead of connecting a MetaMask wallet. I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying. **This raised a red flag**, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction. I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam. After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it. They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds. Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you. ----------- ### My Perspective why I Believe This is a Scam and What the Scammers Gain [](https://stock.adobe.com/stock-photo/id/1010196295) From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees. I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made. In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party. In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says. I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance. However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes. If you found this article helpful, please share it with your fellow artists. Until next time Take care ## Note - Both cyber security images are mine , I created and approved by AdobeStock to put on sale - I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw Link to my full gallery - Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon) - [HikariHarmony on Nostr](https://shorturl.at/I8Nu4) - General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen)
@ 8947a945:9bfcf626
2024-10-17 07:33:00[](https://stock.adobe.com/stock-photo/id/1010191703) **Hello everyone on Nostr** and all my **watchers**and **followers**from DeviantArt, as well as those from other art platforms I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon. I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing **On September 16**, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.  ### Here’s a brief overview of what happened  - The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from **0.15 to 0.2 ETH**  - The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows: 1. I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused. 2. I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused. 3. I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused. 4. I asked them to wait until I could secure the funds, and they agreed to wait. The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website. This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of **0.2 ETH**. However, the site provided a wallet address for me instead of connecting a MetaMask wallet. I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying. **This raised a red flag**, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction. I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam. After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it. They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds. Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you. ----------- ### My Perspective why I Believe This is a Scam and What the Scammers Gain [](https://stock.adobe.com/stock-photo/id/1010196295) From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees. I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made. In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party. In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says. I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance. However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes. If you found this article helpful, please share it with your fellow artists. Until next time Take care ## Note - Both cyber security images are mine , I created and approved by AdobeStock to put on sale - I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw Link to my full gallery - Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon) - [HikariHarmony on Nostr](https://shorturl.at/I8Nu4) - General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen) @ 0e501ec7:de5ef3a4
2024-10-14 21:36:26blog van Tim: <https://timscyclethoughts.blogspot.com> We zijn nu al bijna een week in het Abtshof! Wat een drukke week is het geweest. Je denkt dan, we zijn op reis, we zijn op vakantie, op het gemak. Helemaal niet waar! We hebben heel veel mee gewerkt aan het project. Vorige keer las je al dat we de namiddag dat we toekwamen hier al bij het verwijderen van plaaster hadden gehad geholpen. Dat hebben we de dag erna ook gedaan, in de ochtend. Ging allemaal goed, tot ik op een bepaald moment op een bepaald moment een stukje plaatster in mijn oog kreeg, dat pikte enorm! Ik kreeg het er ook niet uit, en toen na wat gegoogle, besloot ik om het zo grondig mogelijk uit te spoelen. Een half uur heb ik toen mijn oog onder de kraan gehouden, ik ben nu officieel expert in het oog uitspoelen met water. Het was er toen wel uit en deed geen zeer meer. Maar ik had toch geen zin meer om plaaster uit te breken. Daarom ben ik Jakob gaan helpen met de afwerking van de unit waar Ivan naartoe ging verhuizen. In de namiddag hebben we pieter zijn parket geschaafd: die had een koopje gedaan op het internet, maar het was nogal donker behandeld. We hebben er dus het bovenste laagje van gehaalt, met een groot schaafmachien. Een heel gemakkelijk en handig apparaat, maar wel een beetje eng. Heel goed oppassen wanneer je het hout erin steekt! Er is hier ook een andere wwoof'er, die Teo noemt. Hij komt uit Canada, en maakt een grote reis van België tot naar Spanje, een beetje gelijk ons, maar dan zonder fiets! Echt een leuke jongen, mijn Frans is eventjes niet top genoeg om echt te kunnen babbelen, maar we hebben wel veel fun samen, zeker de laatste dagen. Tim en hij kunnen helemaal opgaan in hun muziek en filmbesprekingen, en morgen doen we zelfs een filmavondje om hem een goeie Belgische film te tonen. Vrijdag heb ik weer bij de afwerking van Ivan's unit geholpen. ik heb de rand van een velux helpen isoleren, en plinten opgemeten en gezaagd. Dat was zo moeilijk, om juist te meten en te zagen! Uiteindelijk had ik er maar 2 van de 8 juist, de anderen waren allemaal 3 mm te lang :( dju toch, volgende keer beter! Gelukkig konden ze makkelijk bijgewerkt worden. Tim en Teo waren ondertussen nog aan het uitbreken, ook leuk, maar ik was blij dat ik daar even aan kon ontlopen. Daarna kregen we onze eerste les van de gloednieuw geimproviseerde houtbewerkingsxursus, gegeven door de meestermeubelmaker-schrijnwerker Jakob! Hij legde ons uit hoe we hout verbindingen kunnen maken, toonde er een heleboel en ging meer in detail bij een redelijk simpele: de half-hout verbinding. Hij legde uit hoe we een beitel moeten hanteren en hoe we zeer recht kunnen zagen (belangrijk als je een verbinding maakt!). Na de uitleg gingen we direct aan de slag: we zouden een rek gaan bouwen voor in de voorraadkamer. Er staan langs 2 muren al rekken, en ons rek zou de stijl van de anderen een beetje volgen de de derde muur helemaal bedekken. Nog niet zo gemakkelijk: de muur en de vloer zijn er nogal ruw en hobbelig, hoe begin je daar te meten? In het rek kunnen we elk 10 keer een halfhout verbinding maken, goeie oefening! Je merkt dat ik vooral heel veel vertel over wat we allemaal gedaan hebben. Niet zo heel veel mijmeringen en emotie. Dat is eigenlijk ook logisch, we zijn vooral heel de tijd bezig. En als je bezig bent mijmer je niet en worden je emoties ook niet zo groot. Ik vind het fantastisch om bezig te zijn. Ik miste dat ook echt de laatste maand, maar nu mis ik ook wel weer het mijmeren. Denk ik? Alleszins, ik wou dat ik ook andere dingen had om op te schrijven. Ik ben wel ook veel bezig geweest met het Bos, het Wondelbos, O Wondelbos, en hoe om te gaan met het verdriet en de boosheid die geboren wordt uit het verlies, hoe te rouwen. Dat is niet zo gemakkelijk. Ik denk dat het belangrijkste is dat ik graag die gevoelens wil eren. Het Bos eren, ook al is die er niet meer. Bien schreef erover, en ik vond het zo mooi, dat ik het heel graag hier zou quoteren. Maar ik weet niet of dat oké is, dus zal het voor later houden. Vetrouw je lichaam, vertrouw je gevoel, ik probeer het zo te zeggen tegen mezelf. Ik vertrouw mijn lichaam. Ik denk dat we veel kunnen vinden in onszelf, als we maar het lef hebben om te luistern. Nu en simpel: ik voel me uitgeput, ik vertrouw erop dat het een goede keuze is om nu te gaan slapen. De dagen na vrijdag zal ik later wel vertellen, of niet. Liefs!
@ 0e501ec7:de5ef3a4
2024-10-14 21:36:26blog van Tim: <https://timscyclethoughts.blogspot.com> We zijn nu al bijna een week in het Abtshof! Wat een drukke week is het geweest. Je denkt dan, we zijn op reis, we zijn op vakantie, op het gemak. Helemaal niet waar! We hebben heel veel mee gewerkt aan het project. Vorige keer las je al dat we de namiddag dat we toekwamen hier al bij het verwijderen van plaaster hadden gehad geholpen. Dat hebben we de dag erna ook gedaan, in de ochtend. Ging allemaal goed, tot ik op een bepaald moment op een bepaald moment een stukje plaatster in mijn oog kreeg, dat pikte enorm! Ik kreeg het er ook niet uit, en toen na wat gegoogle, besloot ik om het zo grondig mogelijk uit te spoelen. Een half uur heb ik toen mijn oog onder de kraan gehouden, ik ben nu officieel expert in het oog uitspoelen met water. Het was er toen wel uit en deed geen zeer meer. Maar ik had toch geen zin meer om plaaster uit te breken. Daarom ben ik Jakob gaan helpen met de afwerking van de unit waar Ivan naartoe ging verhuizen. In de namiddag hebben we pieter zijn parket geschaafd: die had een koopje gedaan op het internet, maar het was nogal donker behandeld. We hebben er dus het bovenste laagje van gehaalt, met een groot schaafmachien. Een heel gemakkelijk en handig apparaat, maar wel een beetje eng. Heel goed oppassen wanneer je het hout erin steekt! Er is hier ook een andere wwoof'er, die Teo noemt. Hij komt uit Canada, en maakt een grote reis van België tot naar Spanje, een beetje gelijk ons, maar dan zonder fiets! Echt een leuke jongen, mijn Frans is eventjes niet top genoeg om echt te kunnen babbelen, maar we hebben wel veel fun samen, zeker de laatste dagen. Tim en hij kunnen helemaal opgaan in hun muziek en filmbesprekingen, en morgen doen we zelfs een filmavondje om hem een goeie Belgische film te tonen. Vrijdag heb ik weer bij de afwerking van Ivan's unit geholpen. ik heb de rand van een velux helpen isoleren, en plinten opgemeten en gezaagd. Dat was zo moeilijk, om juist te meten en te zagen! Uiteindelijk had ik er maar 2 van de 8 juist, de anderen waren allemaal 3 mm te lang :( dju toch, volgende keer beter! Gelukkig konden ze makkelijk bijgewerkt worden. Tim en Teo waren ondertussen nog aan het uitbreken, ook leuk, maar ik was blij dat ik daar even aan kon ontlopen. Daarna kregen we onze eerste les van de gloednieuw geimproviseerde houtbewerkingsxursus, gegeven door de meestermeubelmaker-schrijnwerker Jakob! Hij legde ons uit hoe we hout verbindingen kunnen maken, toonde er een heleboel en ging meer in detail bij een redelijk simpele: de half-hout verbinding. Hij legde uit hoe we een beitel moeten hanteren en hoe we zeer recht kunnen zagen (belangrijk als je een verbinding maakt!). Na de uitleg gingen we direct aan de slag: we zouden een rek gaan bouwen voor in de voorraadkamer. Er staan langs 2 muren al rekken, en ons rek zou de stijl van de anderen een beetje volgen de de derde muur helemaal bedekken. Nog niet zo gemakkelijk: de muur en de vloer zijn er nogal ruw en hobbelig, hoe begin je daar te meten? In het rek kunnen we elk 10 keer een halfhout verbinding maken, goeie oefening! Je merkt dat ik vooral heel veel vertel over wat we allemaal gedaan hebben. Niet zo heel veel mijmeringen en emotie. Dat is eigenlijk ook logisch, we zijn vooral heel de tijd bezig. En als je bezig bent mijmer je niet en worden je emoties ook niet zo groot. Ik vind het fantastisch om bezig te zijn. Ik miste dat ook echt de laatste maand, maar nu mis ik ook wel weer het mijmeren. Denk ik? Alleszins, ik wou dat ik ook andere dingen had om op te schrijven. Ik ben wel ook veel bezig geweest met het Bos, het Wondelbos, O Wondelbos, en hoe om te gaan met het verdriet en de boosheid die geboren wordt uit het verlies, hoe te rouwen. Dat is niet zo gemakkelijk. Ik denk dat het belangrijkste is dat ik graag die gevoelens wil eren. Het Bos eren, ook al is die er niet meer. Bien schreef erover, en ik vond het zo mooi, dat ik het heel graag hier zou quoteren. Maar ik weet niet of dat oké is, dus zal het voor later houden. Vetrouw je lichaam, vertrouw je gevoel, ik probeer het zo te zeggen tegen mezelf. Ik vertrouw mijn lichaam. Ik denk dat we veel kunnen vinden in onszelf, als we maar het lef hebben om te luistern. Nu en simpel: ik voel me uitgeput, ik vertrouw erop dat het een goede keuze is om nu te gaan slapen. De dagen na vrijdag zal ik later wel vertellen, of niet. Liefs! @ 84b0c46a:417782f5
2024-10-12 05:51:51- 1:nan: - **2** - 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p) - 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw - 2 - 2 - 3 - 3 - 2 - 1 |1|2| |:--|:--| |test| :nan: | --- ### :nan: **:nan:** 1. 1 2. 2 - tet - tes 3. 3 1. 1 2. 2 > t >> te >>> test - 19^th^ - H~2~O <marquee>(☝ ՞ਊ ՞)☝ウェーイ<marquee><SCRIPT>alert("( 厂˙ω˙ )厂うぇ乁( ˙ω˙ )厂ーい乁( ˙ω˙ 乁)")</SCRIPT> <img src="xx" onerror="alert('(☝ ՞ਊ ՞)☝ウェーイ')"> <marquee onstart="document.querySelector('body').innerHTML = `<main><p>全裸デブ</p></main>`">本サイトはfirefoxのみサポートしています</marquee> <marquee><font size=1000>うにょ</font></marquee> <marquee scrollamount=50>:wayo:</marquee> <marquee behavior="alternate">This text will bounce</marquee>
@ 84b0c46a:417782f5
2024-10-12 05:51:51- 1:nan: - **2** - 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p) - 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw - 2 - 2 - 3 - 3 - 2 - 1 |1|2| |:--|:--| |test| :nan: | --- ### :nan: **:nan:** 1. 1 2. 2 - tet - tes 3. 3 1. 1 2. 2 > t >> te >>> test - 19^th^ - H~2~O <marquee>(☝ ՞ਊ ՞)☝ウェーイ<marquee><SCRIPT>alert("( 厂˙ω˙ )厂うぇ乁( ˙ω˙ )厂ーい乁( ˙ω˙ 乁)")</SCRIPT> <img src="xx" onerror="alert('(☝ ՞ਊ ՞)☝ウェーイ')"> <marquee onstart="document.querySelector('body').innerHTML = `<main><p>全裸デブ</p></main>`">本サイトはfirefoxのみサポートしています</marquee> <marquee><font size=1000>うにょ</font></marquee> <marquee scrollamount=50>:wayo:</marquee> <marquee behavior="alternate">This text will bounce</marquee> @ 0e501ec7:de5ef3a4
2024-10-09 21:38:52PS: lees zeker eens de blog van Tim: <https://timscyclethoughts.blogspot.com/2024/09/> :)) Vandaag was onze eerste dag in het Abtshof. (Ik weet het, gisteren is overgeslagen, oeps, en ik heb nog niet uitgevonden hoe ik hier meer foto's op kan zetten, nogmaals oeps.) Het Absthof is een coöperatieve co-housing, met een grote moestuin en een houtatelier. Het is gelegen in Borlo, een klein dorpje in de buurt van Landen. Het thuis van de wooncoöperatie is een grote vierkantshoeve, die langzaamaan helemaal gerestaureerd geraakt op (redelijk) duurzame wijze. Een heel mooie plek, waar ik al een paar keer te gast ben geweest. Hier krijgen we kost en inwoon in ruil voor mee te helpen met vanalles. Wij zijn blij om hier te zijn en ervaring op te doen, en blij dat we wat kunnen bijdragen aan duurzame/alternatieve projecten zoals deze. Ook nog belangrijk: bij een coöperatie horen ook veel beslissingen, die gedragen moeten zijn. Hier werken ze met het kader van de sociocratie. Zeer interessant, ik zal er later nog over uitweiden. Dus: we hadden op ons gemakje een lange ochtend gehad, met een lekker ontbijtje, een goede opruimbeurt, de plantjes in de serre water geven, en een random astrix en obelix strip. Het ging over de picten, ofzoiets, en iemand die de macht wou grijoen door met de romeinen samen te werken. Bon, daarvoor zijn we hier niet. Ik zou eigenlijk in bed moeten nu, de dagen zijn lang en mijn slaap dierbaar. Toch wil ik eerst nog wat schrijven. Toch toch tocht door de bomen, wilgen, essen, rode beuk Net toen we buitenstapten om te vertrekken deze ochtend, begon het te regenen! Test regenkleren: gefaald. Regenbroek is zo lek alsof hij eigenlijk niet bestaat. Maakt niet uit, ik ben niet van suiker. ; ) We zullen wel nog eens kijken voor van dat eng waterdichtmaakspul, of ik gebruik hem als windstopper, ook goed. Hier aangekomen werden we meteen ontvangen door Jakob met een warm middagmaal. Heerlijke stampot, op smaak gebracht met varkenspoot. Heftig idee, maar ik en Tim konden er wel mee overweg, en waren eigenlijk wel nieuwsgierig hoe dat smaakte zo een varkenspoot. Blijkt: nogal taai, maar wel nog een goede ervaring. Would recommend. Daarna gingen we ons installeren, en we hadden geluk! We mochten slapen in een grote tent die nog op het veld stond. Daarin zijn zelfs bedjes, en hij lijkt (redelijk) waterdicht, al had ik toch niet direct al mijn spullen moeten uitspreiden. Ons kleine tentje zou het niet gehouden hebben om de hele week in de regen opgestaan te hebben vrees ik. Daarna bereikte mij het nieuws. Van de uitzetting in het Wondelbos. Ik was er zwaar van aangedaan, boos en verdrietig, gespannen. Machteloos. Machteloos. Ik heb toen geprobeerd mijn gevoel neer te schrijven, en heb de grote uitdaging overwonnen om dat kwetsbare tekstje te delen. (Op Facebook.) Ik was wel trots op mijn kleine overwinning, maar dat viel nogal in het grote niet bij mijn eerdere gevoel bij de grote machtsvertoning van de politie, en de start van het illegaal lijkende kap. Ik kan niet geloven dat ze een kapvergunning binnen hebben, terwijl de rechtspraak rond hun bouwvergunning nog niet rond is. Maar ja, wat weet ik ervan. Mijn gevoel kon ik dan een beetje van me afzetten door wat te helpen bij in de verbouwing van een nieuwe woning in de co-house: plaksel van de muur halen met een drilboor, puin naar buiten krijgen, spijkers uit de muur halen. Geleerd: oude spijkers moeten uit de muur voor je opnieuw plakt, anders krijg je roestvlekken. Ook geleerd: als je glas in een raam plaatst, mag je dat niet direct op het kader laten steunen, je moet er houtjes tussensteken (voor speling voor isolatie denk ik?). Morgen doen we daarmee verder én gaan we parket schaven. Ik heb echt wel zin om met het schaafmachien te leren werken! Daarna was het eten met alle bewoners, aan een grote lange tafel in de gemeenschappelijke zaal. Was vree gezellig, al was mijn sociale energie naar het einde een beetje op. Er was een 'mededelingrondje', om iedereen op de hoogte te brengen van belangrijk nieuws. Later op de avond hadden de bewoners ook nog een 'deel-cirkel'. Dat doen ze blijkbaar een keer in de maand, om eens samen te zitten en over zaken te kunnen praten op een meer diepgaande manier, en zonder de stress van beslissingen die gemaakt moeten worden, zoals in vergaderingen. Klinkt wel goed, al zou ik zelf niet direct weten of ik veel intieme zaken kan delen voor een groep. Ik zou in de eerste plaats stress krijgen. Maar misschien werkt het wel! Nu, naar bed, morgen weer een volle dag!
@ 0e501ec7:de5ef3a4
2024-10-09 21:38:52PS: lees zeker eens de blog van Tim: <https://timscyclethoughts.blogspot.com/2024/09/> :)) Vandaag was onze eerste dag in het Abtshof. (Ik weet het, gisteren is overgeslagen, oeps, en ik heb nog niet uitgevonden hoe ik hier meer foto's op kan zetten, nogmaals oeps.) Het Absthof is een coöperatieve co-housing, met een grote moestuin en een houtatelier. Het is gelegen in Borlo, een klein dorpje in de buurt van Landen. Het thuis van de wooncoöperatie is een grote vierkantshoeve, die langzaamaan helemaal gerestaureerd geraakt op (redelijk) duurzame wijze. Een heel mooie plek, waar ik al een paar keer te gast ben geweest. Hier krijgen we kost en inwoon in ruil voor mee te helpen met vanalles. Wij zijn blij om hier te zijn en ervaring op te doen, en blij dat we wat kunnen bijdragen aan duurzame/alternatieve projecten zoals deze. Ook nog belangrijk: bij een coöperatie horen ook veel beslissingen, die gedragen moeten zijn. Hier werken ze met het kader van de sociocratie. Zeer interessant, ik zal er later nog over uitweiden. Dus: we hadden op ons gemakje een lange ochtend gehad, met een lekker ontbijtje, een goede opruimbeurt, de plantjes in de serre water geven, en een random astrix en obelix strip. Het ging over de picten, ofzoiets, en iemand die de macht wou grijoen door met de romeinen samen te werken. Bon, daarvoor zijn we hier niet. Ik zou eigenlijk in bed moeten nu, de dagen zijn lang en mijn slaap dierbaar. Toch wil ik eerst nog wat schrijven. Toch toch tocht door de bomen, wilgen, essen, rode beuk Net toen we buitenstapten om te vertrekken deze ochtend, begon het te regenen! Test regenkleren: gefaald. Regenbroek is zo lek alsof hij eigenlijk niet bestaat. Maakt niet uit, ik ben niet van suiker. ; ) We zullen wel nog eens kijken voor van dat eng waterdichtmaakspul, of ik gebruik hem als windstopper, ook goed. Hier aangekomen werden we meteen ontvangen door Jakob met een warm middagmaal. Heerlijke stampot, op smaak gebracht met varkenspoot. Heftig idee, maar ik en Tim konden er wel mee overweg, en waren eigenlijk wel nieuwsgierig hoe dat smaakte zo een varkenspoot. Blijkt: nogal taai, maar wel nog een goede ervaring. Would recommend. Daarna gingen we ons installeren, en we hadden geluk! We mochten slapen in een grote tent die nog op het veld stond. Daarin zijn zelfs bedjes, en hij lijkt (redelijk) waterdicht, al had ik toch niet direct al mijn spullen moeten uitspreiden. Ons kleine tentje zou het niet gehouden hebben om de hele week in de regen opgestaan te hebben vrees ik. Daarna bereikte mij het nieuws. Van de uitzetting in het Wondelbos. Ik was er zwaar van aangedaan, boos en verdrietig, gespannen. Machteloos. Machteloos. Ik heb toen geprobeerd mijn gevoel neer te schrijven, en heb de grote uitdaging overwonnen om dat kwetsbare tekstje te delen. (Op Facebook.) Ik was wel trots op mijn kleine overwinning, maar dat viel nogal in het grote niet bij mijn eerdere gevoel bij de grote machtsvertoning van de politie, en de start van het illegaal lijkende kap. Ik kan niet geloven dat ze een kapvergunning binnen hebben, terwijl de rechtspraak rond hun bouwvergunning nog niet rond is. Maar ja, wat weet ik ervan. Mijn gevoel kon ik dan een beetje van me afzetten door wat te helpen bij in de verbouwing van een nieuwe woning in de co-house: plaksel van de muur halen met een drilboor, puin naar buiten krijgen, spijkers uit de muur halen. Geleerd: oude spijkers moeten uit de muur voor je opnieuw plakt, anders krijg je roestvlekken. Ook geleerd: als je glas in een raam plaatst, mag je dat niet direct op het kader laten steunen, je moet er houtjes tussensteken (voor speling voor isolatie denk ik?). Morgen doen we daarmee verder én gaan we parket schaven. Ik heb echt wel zin om met het schaafmachien te leren werken! Daarna was het eten met alle bewoners, aan een grote lange tafel in de gemeenschappelijke zaal. Was vree gezellig, al was mijn sociale energie naar het einde een beetje op. Er was een 'mededelingrondje', om iedereen op de hoogte te brengen van belangrijk nieuws. Later op de avond hadden de bewoners ook nog een 'deel-cirkel'. Dat doen ze blijkbaar een keer in de maand, om eens samen te zitten en over zaken te kunnen praten op een meer diepgaande manier, en zonder de stress van beslissingen die gemaakt moeten worden, zoals in vergaderingen. Klinkt wel goed, al zou ik zelf niet direct weten of ik veel intieme zaken kan delen voor een groep. Ik zou in de eerste plaats stress krijgen. Maar misschien werkt het wel! Nu, naar bed, morgen weer een volle dag! @ 0e501ec7:de5ef3a4
2024-10-09 21:37:38Ik rouw. Ik rouw om het bos, in mij groeit een grote krop van verdriet. O Wondelbos, ik zag je graag, je ontving me zo hartelijk, en ik zag hoe je de thuis was van zoveel leven, zoveel leven. Ik rouw om het vertrouwen in de rechtbank om rechtvaardig te zijn. Hoe vaak nog meneer de rechter, zal je als speelbal van machtige instituten gebruikt worden om kleine mensen, die mooie dingen proberen te doen, te intimideren? Hoe vaak nog zal jij, zonder kans voor de andere zijde om gehoord te worden, de politiemacht oproepen? Hoe vaak nog zal een vredezame actie met groot machtsvertoon beëindigd worden? Hoevaak nog zal illegale kap straffeloos blijven terwijl beschermers vervolgd en opgepakt worden? Hoevaak nog? Alle rede, alle gevoel zegt, dit bos moet behouden blijven. O bos, ik zal je missen. O Wondelbos, ik ben blij dat jij bij ons was. Nu komt voor jou een tijd van beton. Maar ik ben zeker dat er daaronder een kiertje openblijft, een zaadje zal liggen te wachten. Ik ben zeker dat het Imperium van beton ooit gedaan zal zijn, en dan zal Jij terug kunnen bloeien, terug kunnen groeien, thuis geven aan al die soorten, al die wezens, al dat leven. Dan zal Jij terug thuis kunnen komen, net als Wij. Liefs, Je liefste Aardbewoner
@ 0e501ec7:de5ef3a4
2024-10-09 21:37:38Ik rouw. Ik rouw om het bos, in mij groeit een grote krop van verdriet. O Wondelbos, ik zag je graag, je ontving me zo hartelijk, en ik zag hoe je de thuis was van zoveel leven, zoveel leven. Ik rouw om het vertrouwen in de rechtbank om rechtvaardig te zijn. Hoe vaak nog meneer de rechter, zal je als speelbal van machtige instituten gebruikt worden om kleine mensen, die mooie dingen proberen te doen, te intimideren? Hoe vaak nog zal jij, zonder kans voor de andere zijde om gehoord te worden, de politiemacht oproepen? Hoe vaak nog zal een vredezame actie met groot machtsvertoon beëindigd worden? Hoevaak nog zal illegale kap straffeloos blijven terwijl beschermers vervolgd en opgepakt worden? Hoevaak nog? Alle rede, alle gevoel zegt, dit bos moet behouden blijven. O bos, ik zal je missen. O Wondelbos, ik ben blij dat jij bij ons was. Nu komt voor jou een tijd van beton. Maar ik ben zeker dat er daaronder een kiertje openblijft, een zaadje zal liggen te wachten. Ik ben zeker dat het Imperium van beton ooit gedaan zal zijn, en dan zal Jij terug kunnen bloeien, terug kunnen groeien, thuis geven aan al die soorten, al die wezens, al dat leven. Dan zal Jij terug thuis kunnen komen, net als Wij. Liefs, Je liefste Aardbewoner @ 4ba8e86d:89d32de4
2024-10-09 13:13:10Recentemente, perdi minha lista de RSS, Decidi criar este texto sobre RSS pode ajudar a escapar das armadilhas do algoritmo das redes sociais. Além disso, para facilitar a vida daqueles que também desejam adotar o RSS como uma ferramenta de leitura, fiz um fork da lista de RSS do SethForPrivacy. Você pode acessar a lista no seguinte link: https://gist.github.com/Alexemidio/2699dd82077d483849b576a908b0c444 Aproveite a lista de RSS para personalizar seu fluxo de conteúdo e desfrutar de uma experiência de leitura mais controlada e direcionada. Utilizar um leitor de RSS bem organizado é uma estratégia eficaz para se libertar da rolagem incessante nas redes sociais e recuperar o controle sobre o conteúdo que você consome. Isso possibilita direcionar sua atenção para o conteúdo genuinamente relevante. Você já notou que os feeds das redes sociais frequentemente são inundados com notícias que provocam emoções negativas? Esse fenômeno, chamado de "doomscrolling", persiste, e as redes sociais parecem acentuar ainda mais a sua presença. A conhecida "bolha" das redes sociais nos mantém imersos, mostrando principalmente os posts com os quais interagimos. Isso tem provocado várias consequências prejudiciais, incluindo a disseminação de notícias falsas, desinformação e o agravamento de problemas como ansiedade e depressão entre os usuários. Mas, e se lhe disséssemos que existe uma alternativa? Uma maneira de receber informações diretamente, sem filtros ou algoritmos? É disso que vamos falar hoje: o RSS. O Que é o RSS? RSS é a abreviação de "Really Simple Syndication", que pode ser traduzida como "Sincronização Realmente Simples". Trata-se de um arquivo XML gerado por inúmeros sites para exibir as postagens que o site publica. Dessa forma, os leitores de RSS permitem às pessoas acompanhar diversos blogs, sites de notícias e muito mais, tudo a partir de um único local. Quem Criou o RSS? Uma das pessoas envolvidas na criação do RSS foi Aaron Swartz, um hacker notório por seu papel na fundação do Creative Commons e por ser um dos cofundadores da rede social Reddit. Se desejar se aprofundar na história de Aaron, recomendamos o documentário "O Menino da Internet: A História de Aaron Swartz" dublado em português completo. https://youtu.be/qm4NRSa9T2Q?si=GXyPXVOMJX20pIo_ Para quem gosta de RSS como eu, você não precisa usar NOSTR para acompanhar meu conteúdo. Basta me adicionar ao seu RSS. Meu RSS Nostr: nostr:npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr Utilizar um leitor de RSS bem organizado é uma maneira eficaz de se libertar da rolagem incessante e recuperar o controle sobre o conteúdo que você consome, direcionando sua atenção para o que realmente importa. Para pessoas interessantes como o nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 você não precisa segui-lo no Nostr, basta adicionar ao seu RSS. nostr:naddr1qqxnzdesx5ur2vekxucrqde5qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqa282ctyhs Leitores de RSS Recomendados: Feeder (Mobile): O Feeder é um aplicativo de leitor de RSS de código aberto que permite que você acompanhe e leia suas fontes de notícias favoritas em um só lugar. Com recursos avançados e uma interface intuitiva. Liferea (Desktop): Liferea é a abreviação de Linux Feed Reader, um programa agregador para leitura de notícias online. Ele suporta os principais tipos de arquivo criados para esse fim: RSS/RDF e Atom. Também pode importar e exportar no formato OPML.
@ 4ba8e86d:89d32de4
2024-10-09 13:13:10Recentemente, perdi minha lista de RSS, Decidi criar este texto sobre RSS pode ajudar a escapar das armadilhas do algoritmo das redes sociais. Além disso, para facilitar a vida daqueles que também desejam adotar o RSS como uma ferramenta de leitura, fiz um fork da lista de RSS do SethForPrivacy. Você pode acessar a lista no seguinte link: https://gist.github.com/Alexemidio/2699dd82077d483849b576a908b0c444 Aproveite a lista de RSS para personalizar seu fluxo de conteúdo e desfrutar de uma experiência de leitura mais controlada e direcionada. Utilizar um leitor de RSS bem organizado é uma estratégia eficaz para se libertar da rolagem incessante nas redes sociais e recuperar o controle sobre o conteúdo que você consome. Isso possibilita direcionar sua atenção para o conteúdo genuinamente relevante. Você já notou que os feeds das redes sociais frequentemente são inundados com notícias que provocam emoções negativas? Esse fenômeno, chamado de "doomscrolling", persiste, e as redes sociais parecem acentuar ainda mais a sua presença. A conhecida "bolha" das redes sociais nos mantém imersos, mostrando principalmente os posts com os quais interagimos. Isso tem provocado várias consequências prejudiciais, incluindo a disseminação de notícias falsas, desinformação e o agravamento de problemas como ansiedade e depressão entre os usuários. Mas, e se lhe disséssemos que existe uma alternativa? Uma maneira de receber informações diretamente, sem filtros ou algoritmos? É disso que vamos falar hoje: o RSS. O Que é o RSS? RSS é a abreviação de "Really Simple Syndication", que pode ser traduzida como "Sincronização Realmente Simples". Trata-se de um arquivo XML gerado por inúmeros sites para exibir as postagens que o site publica. Dessa forma, os leitores de RSS permitem às pessoas acompanhar diversos blogs, sites de notícias e muito mais, tudo a partir de um único local. Quem Criou o RSS? Uma das pessoas envolvidas na criação do RSS foi Aaron Swartz, um hacker notório por seu papel na fundação do Creative Commons e por ser um dos cofundadores da rede social Reddit. Se desejar se aprofundar na história de Aaron, recomendamos o documentário "O Menino da Internet: A História de Aaron Swartz" dublado em português completo. https://youtu.be/qm4NRSa9T2Q?si=GXyPXVOMJX20pIo_ Para quem gosta de RSS como eu, você não precisa usar NOSTR para acompanhar meu conteúdo. Basta me adicionar ao seu RSS. Meu RSS Nostr: nostr:npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr Utilizar um leitor de RSS bem organizado é uma maneira eficaz de se libertar da rolagem incessante e recuperar o controle sobre o conteúdo que você consome, direcionando sua atenção para o que realmente importa. Para pessoas interessantes como o nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 você não precisa segui-lo no Nostr, basta adicionar ao seu RSS. nostr:naddr1qqxnzdesx5ur2vekxucrqde5qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqa282ctyhs Leitores de RSS Recomendados: Feeder (Mobile): O Feeder é um aplicativo de leitor de RSS de código aberto que permite que você acompanhe e leia suas fontes de notícias favoritas em um só lugar. Com recursos avançados e uma interface intuitiva. Liferea (Desktop): Liferea é a abreviação de Linux Feed Reader, um programa agregador para leitura de notícias online. Ele suporta os principais tipos de arquivo criados para esse fim: RSS/RDF e Atom. Também pode importar e exportar no formato OPML. @ 0e501ec7:de5ef3a4
2024-10-08 20:06:29Aan het einde van een dag vol buiten zijn en fietsen en organiseren (spullen inpakken, uitpakken, drogen, eten verzamelen (letterlijk hihi), eten klaarmaken, afwas...) ben ik echt niet meer in staat om veel te schrijven. Hier komt dus een korte samenvatting van de laatste twee dagen, filosofische bedenkselen zijn voor een andere keer. Gisteren vertrokken we bij Yannick pas tegen de middag. Hoe kwam dat? Ik heb tot 9u (!) geslapen, wat wel nodig was want ik was echt volkomen uitgeput van de dag ervoor. (Veel prikkels joh, en fysieke uitdaging om 60 km te fietsen met een zwaarbeladen fiets.) (Ik weet het, klinkt niet als zoo veel maar mijn fysieke toestand was de laatste tijd niet zo heel formidabel, veel ziek en moe geweest.) Na het ontbijt heeft Tim met mijn bedenkelijke hulp mijn cassette (de tandwielen van achter) en mijn ketting vervangen. Dat ging best wel vlot, enkel het afstellen van de versnelling was niet zo gemakkelijk. We moesten een evenwicht vinden waarbij alle 9 schakels vlot gingen, aan de ene kant moesten we telkens aanspannen, terwijl we aan de andere kant telkens weer losten. Ik wou het al opgeven, toen we het net hadden gevonden. Na al dit geploeter begonnen we aan onze fietstocht door het mooie (en drukke) Brussel. Ik heb er zeer van genoten om door de stad te rijden op een kleine steek, een beetje foto's te maken en tussen de mensen te laveren. In Molenbeek kochten we in een lokale kruidenier wat droogvoer, en nog een brood, en toen trokken we verder: richting Meerdaalwoud! Eerst passeerden we nog het zoniën. Prachtig! Ik kon me niet inhouden om (bijna) alle paddestoelen te beginnen fotograferen en aan Het Algoritme van ObsIdentify te vragen hoe ze heten. Gelukkig vond Tim het wel sympathiek en stelde ik zijn geduld niet te veel op de proef. Ondertussen discussieerden we een beetje over de betrouwbaarheid van de media, het gewoonlijke, je weet wel. Gedurende de namiddag voelden we de bui al hangen, en ja hoor, tegen dat we aan de rand van het mooie Meerdaalwoud aankwamen, begon het zachtjes te druppen. In de gietende regen aten we rechtstaand ons stoofpotje op. Wat een vibe! Gelukkig was het niet koud, en konden we genieten van onze ultieme herfstsfeer. In de schemering, in de regen, klaar om in de tent te kruipen. Heerlijk! PS: Het lukt dus niet om de foto's op te laden, jammer! Ze zijn wel mooi hoor, ik verzeker het je! PPS: Ik vind het nu een beetje cringe om zo al onze gebeurtenissen te beschrijven, interesseert iemand dat eigenlijk? Interesseert het mij wel? Ik denk/voel erover na!
@ 0e501ec7:de5ef3a4
2024-10-08 20:06:29Aan het einde van een dag vol buiten zijn en fietsen en organiseren (spullen inpakken, uitpakken, drogen, eten verzamelen (letterlijk hihi), eten klaarmaken, afwas...) ben ik echt niet meer in staat om veel te schrijven. Hier komt dus een korte samenvatting van de laatste twee dagen, filosofische bedenkselen zijn voor een andere keer. Gisteren vertrokken we bij Yannick pas tegen de middag. Hoe kwam dat? Ik heb tot 9u (!) geslapen, wat wel nodig was want ik was echt volkomen uitgeput van de dag ervoor. (Veel prikkels joh, en fysieke uitdaging om 60 km te fietsen met een zwaarbeladen fiets.) (Ik weet het, klinkt niet als zoo veel maar mijn fysieke toestand was de laatste tijd niet zo heel formidabel, veel ziek en moe geweest.) Na het ontbijt heeft Tim met mijn bedenkelijke hulp mijn cassette (de tandwielen van achter) en mijn ketting vervangen. Dat ging best wel vlot, enkel het afstellen van de versnelling was niet zo gemakkelijk. We moesten een evenwicht vinden waarbij alle 9 schakels vlot gingen, aan de ene kant moesten we telkens aanspannen, terwijl we aan de andere kant telkens weer losten. Ik wou het al opgeven, toen we het net hadden gevonden. Na al dit geploeter begonnen we aan onze fietstocht door het mooie (en drukke) Brussel. Ik heb er zeer van genoten om door de stad te rijden op een kleine steek, een beetje foto's te maken en tussen de mensen te laveren. In Molenbeek kochten we in een lokale kruidenier wat droogvoer, en nog een brood, en toen trokken we verder: richting Meerdaalwoud! Eerst passeerden we nog het zoniën. Prachtig! Ik kon me niet inhouden om (bijna) alle paddestoelen te beginnen fotograferen en aan Het Algoritme van ObsIdentify te vragen hoe ze heten. Gelukkig vond Tim het wel sympathiek en stelde ik zijn geduld niet te veel op de proef. Ondertussen discussieerden we een beetje over de betrouwbaarheid van de media, het gewoonlijke, je weet wel. Gedurende de namiddag voelden we de bui al hangen, en ja hoor, tegen dat we aan de rand van het mooie Meerdaalwoud aankwamen, begon het zachtjes te druppen. In de gietende regen aten we rechtstaand ons stoofpotje op. Wat een vibe! Gelukkig was het niet koud, en konden we genieten van onze ultieme herfstsfeer. In de schemering, in de regen, klaar om in de tent te kruipen. Heerlijk! PS: Het lukt dus niet om de foto's op te laden, jammer! Ze zijn wel mooi hoor, ik verzeker het je! PPS: Ik vind het nu een beetje cringe om zo al onze gebeurtenissen te beschrijven, interesseert iemand dat eigenlijk? Interesseert het mij wel? Ik denk/voel erover na! @ 0e501ec7:de5ef3a4
2024-10-08 19:26:36Wat een vermoeiende dag! Eerst alle spanning van vertrekken, snel nog van telefoon wisselen, afscheid, veel afscheid, traantjes, nog mijn breispullen gaan halen die ik bij roos was vergeten, en dan pas eindelijk vertrekken! Fietsen fietsen fietsen! Op dit moment ben ik zeer moe, dat merk je misschien aan deze vluchtige schrijfstijl, mijn ogen vallen toe, maar dat was ik eigenlijk vanochtend al: gisterenavond waren er twee megaleuke feestjes! Eerst het verjaardagsfeestje van roos, zo vol met warme lieve mensen, en dan nog ook het verjaardagsfeestje van mijn mama! ook vol lieve mensen. Toen fietsen fietsen fietsen! Ik reed eerst alleen, langs de mooie lange schelde, tussen de wilgen, het riet, de velden... Ik was verwonderd iver de schoonheid van de paarden die langs het jaagpad stonden, ik was verwonderd over een kind dat vrolijk door een veld liep, wat een beeld zobder weerga, een soort van plattelandse veiligheid/vrijheid die we biet vaak meer tegenkomen. Toen werd ik opgehouden door allerlei werken, ik probeerde een omleiding te volgen (waarbij ik een sappige grote kastanjeoogst scoorde bij een prachtig paar bomen!) maar kwam weer midden in de jaagpadwerken uit en had toen een groot avontuur voor de boeg, hoeveel keer ik met die zwaarbeladen fiets de dijk op en af moest aj aj. Daarbij had ik ook nog een stevige tegenwind, waardoor ik pas na 14u aankwam bij mijn lieve oma en opa. Tim was daar al, en had al goed gesocialiseerd! We babbelden met ons vieren over vanalles, er kwamen allerlei oude verhalen bovendrijven bij oma en opa, ze waren precies zeer verheugd om tegen een nog niet bekende, jonge avonturier zoals Tim al hun verhalen uit de doeken te doen :)). Na ons buikje meer dan rond gegeten te hebben, trokken we weer op pad, deze keer met de knooppuntenroute die Tim had uitgestippeld. Bezienswaardigheden: de eiffeltoren van Asse, een paard om een heuvelkam, een steile bergaf die plots een grindweg werd, een boze tegenligger, veel politieke (rechtse) posters. En heuvels, en veel zondagsmensen. Tegen 6 uur kwamen we dan toe in Zellik, bij Yannick, een vriend van Tim. Die ontving ons hartelijk, met een mooie radiostem (hij studeert dat!). Na het eten speelde we nog een spelletje Boonanza, zeer leuk. Ik merk wel dat ik echt heel veel zin heb om de blog te onderhouden, het is echt zo een projectje waarmee ik iets kan brengen naar de mensen waarvan ik hou, verhalen, ideeën, foto's. Ik hoop wel dat het een beetje overkomt, ik ben nogal onzeker over het rare vreemde platformpje dat niemand kent (maar ik ben gewoon onzeker en kwetsbaar tsjah) (wat het is kan je lezen in 'een eerste poging'). Als je het leest, laat me weten wat je ervan vindt! Als mensen het leuk vinden gaat mijn motivatie om er meer op te plaatsen misschien wel overleven :). Tijdens het fietsen moest ik regelmatig denken aan The Cyborg Manifesto van Donna Haraway. Zelf heb ik dat boekje eigenlijk nog niet gelezen, maar het idee van de cyborg, het uitgebreide lichaam/zelf met technologie zet me wel aan het denken. Ik op de fiets met al mijn warme (regen)kleren in de fietszak ben precies een soort reuze huisjesslak aan topsnelheid. We razen door het landschap, ervaren het, de wind, de zon en regen, interageren met de menselijke en botanische bewoners ervan... En aan het einde van de dag zetten we onze tent op, ons verplaatsbare huisje. Wat als nu eens stopten met de wereld, ecosystemen en natuur, ons lichaam te beschouwen als machines, als radartjes, waarin problemen kunnen opgelost worden met quick files zoals een pilletje of de inrichting van reservaten (zoals we gewoon zijn bij de machines: een beetje smeren, een tandwiel vervangen, de nieuwe update installeren). Wat als we nu eens de machines als deel van ons lichaam zagen? Een lichaam om gehecht aan te zijn, om zorg voor te dragen? Om mee in wederkerige interactie met de wezens rond ons te gaan? Bon, ik moet er nog eens over nadenken, en dat boek lezen, misschien heb ik daar ooit wel eens tijd voor. Na een lange fietsdag ben ik er allisinds te moe voor!
@ 0e501ec7:de5ef3a4
2024-10-08 19:26:36Wat een vermoeiende dag! Eerst alle spanning van vertrekken, snel nog van telefoon wisselen, afscheid, veel afscheid, traantjes, nog mijn breispullen gaan halen die ik bij roos was vergeten, en dan pas eindelijk vertrekken! Fietsen fietsen fietsen! Op dit moment ben ik zeer moe, dat merk je misschien aan deze vluchtige schrijfstijl, mijn ogen vallen toe, maar dat was ik eigenlijk vanochtend al: gisterenavond waren er twee megaleuke feestjes! Eerst het verjaardagsfeestje van roos, zo vol met warme lieve mensen, en dan nog ook het verjaardagsfeestje van mijn mama! ook vol lieve mensen. Toen fietsen fietsen fietsen! Ik reed eerst alleen, langs de mooie lange schelde, tussen de wilgen, het riet, de velden... Ik was verwonderd iver de schoonheid van de paarden die langs het jaagpad stonden, ik was verwonderd over een kind dat vrolijk door een veld liep, wat een beeld zobder weerga, een soort van plattelandse veiligheid/vrijheid die we biet vaak meer tegenkomen. Toen werd ik opgehouden door allerlei werken, ik probeerde een omleiding te volgen (waarbij ik een sappige grote kastanjeoogst scoorde bij een prachtig paar bomen!) maar kwam weer midden in de jaagpadwerken uit en had toen een groot avontuur voor de boeg, hoeveel keer ik met die zwaarbeladen fiets de dijk op en af moest aj aj. Daarbij had ik ook nog een stevige tegenwind, waardoor ik pas na 14u aankwam bij mijn lieve oma en opa. Tim was daar al, en had al goed gesocialiseerd! We babbelden met ons vieren over vanalles, er kwamen allerlei oude verhalen bovendrijven bij oma en opa, ze waren precies zeer verheugd om tegen een nog niet bekende, jonge avonturier zoals Tim al hun verhalen uit de doeken te doen :)). Na ons buikje meer dan rond gegeten te hebben, trokken we weer op pad, deze keer met de knooppuntenroute die Tim had uitgestippeld. Bezienswaardigheden: de eiffeltoren van Asse, een paard om een heuvelkam, een steile bergaf die plots een grindweg werd, een boze tegenligger, veel politieke (rechtse) posters. En heuvels, en veel zondagsmensen. Tegen 6 uur kwamen we dan toe in Zellik, bij Yannick, een vriend van Tim. Die ontving ons hartelijk, met een mooie radiostem (hij studeert dat!). Na het eten speelde we nog een spelletje Boonanza, zeer leuk. Ik merk wel dat ik echt heel veel zin heb om de blog te onderhouden, het is echt zo een projectje waarmee ik iets kan brengen naar de mensen waarvan ik hou, verhalen, ideeën, foto's. Ik hoop wel dat het een beetje overkomt, ik ben nogal onzeker over het rare vreemde platformpje dat niemand kent (maar ik ben gewoon onzeker en kwetsbaar tsjah) (wat het is kan je lezen in 'een eerste poging'). Als je het leest, laat me weten wat je ervan vindt! Als mensen het leuk vinden gaat mijn motivatie om er meer op te plaatsen misschien wel overleven :). Tijdens het fietsen moest ik regelmatig denken aan The Cyborg Manifesto van Donna Haraway. Zelf heb ik dat boekje eigenlijk nog niet gelezen, maar het idee van de cyborg, het uitgebreide lichaam/zelf met technologie zet me wel aan het denken. Ik op de fiets met al mijn warme (regen)kleren in de fietszak ben precies een soort reuze huisjesslak aan topsnelheid. We razen door het landschap, ervaren het, de wind, de zon en regen, interageren met de menselijke en botanische bewoners ervan... En aan het einde van de dag zetten we onze tent op, ons verplaatsbare huisje. Wat als nu eens stopten met de wereld, ecosystemen en natuur, ons lichaam te beschouwen als machines, als radartjes, waarin problemen kunnen opgelost worden met quick files zoals een pilletje of de inrichting van reservaten (zoals we gewoon zijn bij de machines: een beetje smeren, een tandwiel vervangen, de nieuwe update installeren). Wat als we nu eens de machines als deel van ons lichaam zagen? Een lichaam om gehecht aan te zijn, om zorg voor te dragen? Om mee in wederkerige interactie met de wezens rond ons te gaan? Bon, ik moet er nog eens over nadenken, en dat boek lezen, misschien heb ik daar ooit wel eens tijd voor. Na een lange fietsdag ben ik er allisinds te moe voor! @ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias. <iframe width="560" height="315" src="https://www.youtube.com/embed/fehgwnSUcqQ?si=nPK7UOFr19BT5ifm" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ### 1. Privacy and Ownership: Foundations of Personal AI At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations. In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI. ### 2. Bias and Fairness: The Ethical Dilemma of LLMs Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values. This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks. Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge. ### 3. Explainability: The Need for Transparency One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions. Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm. This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks. ### Addressing the Ethical Landscape of Personal AI As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development. Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources. There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom. The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development. ### Conclusion In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values. If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
@ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias. <iframe width="560" height="315" src="https://www.youtube.com/embed/fehgwnSUcqQ?si=nPK7UOFr19BT5ifm" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ### 1. Privacy and Ownership: Foundations of Personal AI At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations. In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI. ### 2. Bias and Fairness: The Ethical Dilemma of LLMs Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values. This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks. Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge. ### 3. Explainability: The Need for Transparency One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions. Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm. This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks. ### Addressing the Ethical Landscape of Personal AI As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development. Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources. There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom. The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development. ### Conclusion In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values. If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation! @ 0e501ec7:de5ef3a4
2024-10-05 10:41:58De kamer is stil, maar weinig verlicht met een grijs en duister schemerlicht. Ze zitten rond een vreemdsoortige tafel, aan het verste uiteinde ervan staat een beeld. Het beeld is niet goed zichtbaar, maar de vormen ervan geven je een krop in je keel, je maag keert om. Dit zijn de machtigste mannen op aarde. Mannen ja, geen seksistische veralgemening hier, het zijn effectief alleen mannen in deze ruimte. Voor zover het te ontwaren is in het duistere licht, zijn ze gezond, fit, alsof ze dagelijks naar de yogales en de basicfit gaan. Ze zijn serieus, ze lachen niet, er is werk te doen. Ze kennen elkaar, ook al praten ze amper. Ze praten over het weer. Je weet dat dit geen leuke plek is. Je weet dat een lach je hier duur te staan kan komen. Hoe ben je hier terecht gekomen? De Mannen zitten in hun glanzende stoelen van Fenolformaldehyde en Perfluoroctaanzuur, en de stilte wordt nog zwaarder. Je hebt het koud, er steekt een ijzige wind op in de kamer, een ijskoude luchtstroom. \------------------------------------------------------------------------ Duizenden jaren hebben de kou en het ijs het mythische Antarctica vormgegeven. Dit deel van onze geliefde Biosfeer, van Patchamama, heeft nooit veel mensen gekend, de Pinguïns, de Walrussen en de Zeehonden leefden hun levens los van ons, soms vreedzaam, soms lang, soms kort en gruwelijk. Maar ze kenden hun land en ze kenden elkaar, ze wisten dat na het licht de duisternis kwam, dat de duisternis kou met zich meebracht, die soms dodelijk was, maar altijd weer plaats maakte voor een minder frisse tijd waarin ze makkelijker konden gaan jagen op de Vissen, die ze ook zeer goed kenden. Toen de eerste Mensen kwamen waren ze woordeloos. Dit waren nooit mensen van veel gebabbel geweest, anders waren ze niet tot hier geraakt, maar de aanblik van de prachtige witte glooiingen van Antarctica, de aanblik van kou en schoonheid, ongrijpbaar en gevaarlijk, maar toch zo verleidelijk, ontnam ze van alle woorden. Vol ontzag, getransformeerd keerden ze terug naar huis, al gebeurde dat niet altijd. Antarctica werd een belangrijk personage in vele heldenverhalen, in gedichten, schilderijen. Het duurde niet lang of alle Mensen hadden ervan gehoord, en velen waren in de ban van deze voor hun desolate plek. Vol leven was Antarctica, een onmisbaar orgaan in het lichaam van onze Aarde. Ze reguleerde de oceaanstromen, waaronder de golfstroom, en zorgde voor een constantere verdeling van warmte en koude. Dankzij Antarctica waren veel van de plekken die wij Thuis noemden zoals ze waren. Alle organen van onze Aarde zorgden er samen voor dat het regende wanneer het moest regenen, dat de zon scheen wanneer we er zo op wachtten, dat het ene jaar een beetje op het andere leek en we ons Thuis voelden. Thuis in de Biosfeer. \------------------------------------------------------------------------ Vandaag is er iets te vieren onder deze Mannen. Ze zijn erin geslaagd om een groot offer te brengen. Van een omvang die gewone mensen, zoals jij en ik niet kunnen omvatten. Hun God is bloedig, van een zwart soort bloed, met een hoge energetische waarde. Een te hoge energetische waarde zou je kunnen zeggen, zo hoog, dat dit bloed al snel verslavend werkt, in een trance brengt. Een trance van productiviteit, efficiëntie, destructie. Een trance van macht en geld, en 'vrije' markt. Maar de 'vrije markt' is al ter dood gebracht. Geofferd, in een vorig decennium. Het zwarte bloed vroeg meer machtsconcentratie om te blijven stromen. Deze Godheid vroeg meer toewijding, meer opoffering, meer zweet en fragiele lonen. Meer pesticiden, meer deregulatie, meer privatisering, meer staatsteun voor multinational, meer belastingverlaging. Ten dienste van de 'vrije' markt. Ten dienste van de monopolie. Dit is een God van de marktdominantie, een God van de monopolies. Jij moet dan misschien aan dat gezelschapsspel denken, dat je in een vorig leven met je familie speelde. Soms was dat nog leuk, maar even vaak eindigde het in ruzie, dat weet je nog goed. Je weet evengoed dat dít spel niet meer leuk is, al lang niet meer. Het zwarte bloed ontregelde de organen van de Aarde, opdat er nog meer zwart bloed zou moge vloeien. De Mannen vieren in stilte. Het ijs van Antarctica is gesmolten, het offer is compleet. Hun leger aan loonarbeiders (meer zweet en fragiele lonen, zo had de God geboden) zijn begonnen aan de eerste boortorens, boorplatformen en pijpleidingen. Ze weten dat hun God blij zal zijn met dit offer, hij heeft er al zolang om gevraagd. Het duurde bijna te lang, de vrees begon te groeien. Deze Mannen zijn dan machtig, angst is hun niet onbekend. Angst is hun beste vriend, al is het geen zorgzame vriendschap. Eerder een verstikkende, voortduwende, trekkende vriendschap. Ze zijn bang dat ze niet genoeg kunnen geven. Als ze niet hard genoeg werken en de offers krimpen zal hun rijk instorten. Zullen zij instorten. Onder de zware zwarte Wraak van hun Godheid. De God heeft beloofd dat Hij hun leugens voor iedereen zal uitspreiden als ze zijn offers niet kunnen brengen. Hij heeft gezworen hun Imperium te laten brokkelen wanneer zij niet hard genoeg werken en de vernietiging Hem niet tevreden stelt. Ze zijn bang. De ijzige wind kietelt in hun nek. Maar ze vieren, ze hebben iets te vieren.
@ 0e501ec7:de5ef3a4
2024-10-05 10:41:58De kamer is stil, maar weinig verlicht met een grijs en duister schemerlicht. Ze zitten rond een vreemdsoortige tafel, aan het verste uiteinde ervan staat een beeld. Het beeld is niet goed zichtbaar, maar de vormen ervan geven je een krop in je keel, je maag keert om. Dit zijn de machtigste mannen op aarde. Mannen ja, geen seksistische veralgemening hier, het zijn effectief alleen mannen in deze ruimte. Voor zover het te ontwaren is in het duistere licht, zijn ze gezond, fit, alsof ze dagelijks naar de yogales en de basicfit gaan. Ze zijn serieus, ze lachen niet, er is werk te doen. Ze kennen elkaar, ook al praten ze amper. Ze praten over het weer. Je weet dat dit geen leuke plek is. Je weet dat een lach je hier duur te staan kan komen. Hoe ben je hier terecht gekomen? De Mannen zitten in hun glanzende stoelen van Fenolformaldehyde en Perfluoroctaanzuur, en de stilte wordt nog zwaarder. Je hebt het koud, er steekt een ijzige wind op in de kamer, een ijskoude luchtstroom. \------------------------------------------------------------------------ Duizenden jaren hebben de kou en het ijs het mythische Antarctica vormgegeven. Dit deel van onze geliefde Biosfeer, van Patchamama, heeft nooit veel mensen gekend, de Pinguïns, de Walrussen en de Zeehonden leefden hun levens los van ons, soms vreedzaam, soms lang, soms kort en gruwelijk. Maar ze kenden hun land en ze kenden elkaar, ze wisten dat na het licht de duisternis kwam, dat de duisternis kou met zich meebracht, die soms dodelijk was, maar altijd weer plaats maakte voor een minder frisse tijd waarin ze makkelijker konden gaan jagen op de Vissen, die ze ook zeer goed kenden. Toen de eerste Mensen kwamen waren ze woordeloos. Dit waren nooit mensen van veel gebabbel geweest, anders waren ze niet tot hier geraakt, maar de aanblik van de prachtige witte glooiingen van Antarctica, de aanblik van kou en schoonheid, ongrijpbaar en gevaarlijk, maar toch zo verleidelijk, ontnam ze van alle woorden. Vol ontzag, getransformeerd keerden ze terug naar huis, al gebeurde dat niet altijd. Antarctica werd een belangrijk personage in vele heldenverhalen, in gedichten, schilderijen. Het duurde niet lang of alle Mensen hadden ervan gehoord, en velen waren in de ban van deze voor hun desolate plek. Vol leven was Antarctica, een onmisbaar orgaan in het lichaam van onze Aarde. Ze reguleerde de oceaanstromen, waaronder de golfstroom, en zorgde voor een constantere verdeling van warmte en koude. Dankzij Antarctica waren veel van de plekken die wij Thuis noemden zoals ze waren. Alle organen van onze Aarde zorgden er samen voor dat het regende wanneer het moest regenen, dat de zon scheen wanneer we er zo op wachtten, dat het ene jaar een beetje op het andere leek en we ons Thuis voelden. Thuis in de Biosfeer. \------------------------------------------------------------------------ Vandaag is er iets te vieren onder deze Mannen. Ze zijn erin geslaagd om een groot offer te brengen. Van een omvang die gewone mensen, zoals jij en ik niet kunnen omvatten. Hun God is bloedig, van een zwart soort bloed, met een hoge energetische waarde. Een te hoge energetische waarde zou je kunnen zeggen, zo hoog, dat dit bloed al snel verslavend werkt, in een trance brengt. Een trance van productiviteit, efficiëntie, destructie. Een trance van macht en geld, en 'vrije' markt. Maar de 'vrije markt' is al ter dood gebracht. Geofferd, in een vorig decennium. Het zwarte bloed vroeg meer machtsconcentratie om te blijven stromen. Deze Godheid vroeg meer toewijding, meer opoffering, meer zweet en fragiele lonen. Meer pesticiden, meer deregulatie, meer privatisering, meer staatsteun voor multinational, meer belastingverlaging. Ten dienste van de 'vrije' markt. Ten dienste van de monopolie. Dit is een God van de marktdominantie, een God van de monopolies. Jij moet dan misschien aan dat gezelschapsspel denken, dat je in een vorig leven met je familie speelde. Soms was dat nog leuk, maar even vaak eindigde het in ruzie, dat weet je nog goed. Je weet evengoed dat dít spel niet meer leuk is, al lang niet meer. Het zwarte bloed ontregelde de organen van de Aarde, opdat er nog meer zwart bloed zou moge vloeien. De Mannen vieren in stilte. Het ijs van Antarctica is gesmolten, het offer is compleet. Hun leger aan loonarbeiders (meer zweet en fragiele lonen, zo had de God geboden) zijn begonnen aan de eerste boortorens, boorplatformen en pijpleidingen. Ze weten dat hun God blij zal zijn met dit offer, hij heeft er al zolang om gevraagd. Het duurde bijna te lang, de vrees begon te groeien. Deze Mannen zijn dan machtig, angst is hun niet onbekend. Angst is hun beste vriend, al is het geen zorgzame vriendschap. Eerder een verstikkende, voortduwende, trekkende vriendschap. Ze zijn bang dat ze niet genoeg kunnen geven. Als ze niet hard genoeg werken en de offers krimpen zal hun rijk instorten. Zullen zij instorten. Onder de zware zwarte Wraak van hun Godheid. De God heeft beloofd dat Hij hun leugens voor iedereen zal uitspreiden als ze zijn offers niet kunnen brengen. Hij heeft gezworen hun Imperium te laten brokkelen wanneer zij niet hard genoeg werken en de vernietiging Hem niet tevreden stelt. Ze zijn bang. De ijzige wind kietelt in hun nek. Maar ze vieren, ze hebben iets te vieren. @ 0e501ec7:de5ef3a4
2024-10-04 16:53:22We zijn nu 2 dagen voor het gepland vertrek, 4/10/2024. Ik ben zeer blij dat ik een fietsmaatje heb, genaamd Tim, die een datum heeft vastgelegd om te vertrekken. Als ik dat niet had gehad, dan was ik het vertrek waarschijnlijk nog een hele poos blijven uitstellen, of zelfs nooit vertrokken geraakt! Nu heb ik deze week wel met wat stress rondgelopen, je weet wel hoe stressgevoelig ik ben en je klaarmaken voor een grote reis is toch wel een beetje spannend. Onze reis heeft geen strak plan. Als mensen ernaar vragen zeg ik altijd: we vertrekken richting het zuiden. Dan vragen ze nog: 'hoelang blijf je weg' en dan moet ik bekennen dat ik het niet weet. Veel mensen reageren een beetje onbegrijpend, maar een paar snappen het meteen en zijn laaiend enthousiast. En ik moet bekennen, dat ben ik zelf ook wel! Het is dus voor het grootste deel positieve spanning. Natuurlijk ook een beetje koudwatervrees, letterlijk dan, want ik heb zo een voorgevoel dat het veél gaat regenen! Ons plannetje is om naast fietsen ook te stoppen op interessante plekken, zoals transitie-projecten of alternatieve gemeenschappen. Daar willen we graag meewerken en helpen waar we kunnen, maar ook mensen leren kennen en veel bijleren! Ik wil bijvoorbeeld heel graag houtbewerking leren, en Tim wilt graag over moestuinen en andere landbouwtechnieken leren (denk ik). En dat komt goed uit: veel projecten hebben een houtatelier en een grote moestuin. Al moeten we dat natuurlijk zien hé. Het eerste project zal het Absthof worden, in Borlo. Zondag vertrekken we dus in die richting. We passeren mijn grootouders in Aalst, slapen dan waarschijnlijk bij een vriend van Tim in Zellik, en gaan dan via het Meerdaalwoud naar Landen/Borlo. Ik ben zeer benieuwd hoe het fietsen mij gaat bevallen. Ik ben de laatste tijd nogal moe geweest, moe en ziek. Van één nachtje te weinig slaap voelde ik mij telkens weer verkouden. Ik denk echter dat het vooral het teveel aan stress en te weinig mentale rust is van het laatste jaar dat daar aan de oorzaak van ligt. Ik verwacht dus dat de fietsreis mij goed gaat doen, om mijn lichaam terug te herstellen en een routine op te bouwen met minder stress. Maaar: toch spannend! In het begin zou ik wel eens te moe kunnen zijn om ver te fietsen. Hopelijk lukt het mij om op tijd te zeggen Jow ik ben echt moe we zullen vandaag toch wat minder moeten fietsen. Dat zal wel echt belangrijk zijn, want als ik mij in het begin overdoe ga ik het misschien niet lang volhouden. Komt wel goed! De voorbereidingen van deze week waren: de fiets kuisen, versnellingen afstellen, slag uit de wielen halen (merci Tim!!!), een stuurpenverlenger installeren zodat ik minder voorovergebogen zit, regenkleren opnieuw behandelen zodat ze waterdicht zijn, en een tripje naar de Decathlon, voor waterdichte overschoenen, een achterlicht en wat waterdichte zakken. Daarnaast ben ik ook nog vandaag naar de gemeente geweest om een volmacht te regelen, voor de verkiezingen volgende week!
@ 0e501ec7:de5ef3a4
2024-10-04 16:53:22We zijn nu 2 dagen voor het gepland vertrek, 4/10/2024. Ik ben zeer blij dat ik een fietsmaatje heb, genaamd Tim, die een datum heeft vastgelegd om te vertrekken. Als ik dat niet had gehad, dan was ik het vertrek waarschijnlijk nog een hele poos blijven uitstellen, of zelfs nooit vertrokken geraakt! Nu heb ik deze week wel met wat stress rondgelopen, je weet wel hoe stressgevoelig ik ben en je klaarmaken voor een grote reis is toch wel een beetje spannend. Onze reis heeft geen strak plan. Als mensen ernaar vragen zeg ik altijd: we vertrekken richting het zuiden. Dan vragen ze nog: 'hoelang blijf je weg' en dan moet ik bekennen dat ik het niet weet. Veel mensen reageren een beetje onbegrijpend, maar een paar snappen het meteen en zijn laaiend enthousiast. En ik moet bekennen, dat ben ik zelf ook wel! Het is dus voor het grootste deel positieve spanning. Natuurlijk ook een beetje koudwatervrees, letterlijk dan, want ik heb zo een voorgevoel dat het veél gaat regenen! Ons plannetje is om naast fietsen ook te stoppen op interessante plekken, zoals transitie-projecten of alternatieve gemeenschappen. Daar willen we graag meewerken en helpen waar we kunnen, maar ook mensen leren kennen en veel bijleren! Ik wil bijvoorbeeld heel graag houtbewerking leren, en Tim wilt graag over moestuinen en andere landbouwtechnieken leren (denk ik). En dat komt goed uit: veel projecten hebben een houtatelier en een grote moestuin. Al moeten we dat natuurlijk zien hé. Het eerste project zal het Absthof worden, in Borlo. Zondag vertrekken we dus in die richting. We passeren mijn grootouders in Aalst, slapen dan waarschijnlijk bij een vriend van Tim in Zellik, en gaan dan via het Meerdaalwoud naar Landen/Borlo. Ik ben zeer benieuwd hoe het fietsen mij gaat bevallen. Ik ben de laatste tijd nogal moe geweest, moe en ziek. Van één nachtje te weinig slaap voelde ik mij telkens weer verkouden. Ik denk echter dat het vooral het teveel aan stress en te weinig mentale rust is van het laatste jaar dat daar aan de oorzaak van ligt. Ik verwacht dus dat de fietsreis mij goed gaat doen, om mijn lichaam terug te herstellen en een routine op te bouwen met minder stress. Maaar: toch spannend! In het begin zou ik wel eens te moe kunnen zijn om ver te fietsen. Hopelijk lukt het mij om op tijd te zeggen Jow ik ben echt moe we zullen vandaag toch wat minder moeten fietsen. Dat zal wel echt belangrijk zijn, want als ik mij in het begin overdoe ga ik het misschien niet lang volhouden. Komt wel goed! De voorbereidingen van deze week waren: de fiets kuisen, versnellingen afstellen, slag uit de wielen halen (merci Tim!!!), een stuurpenverlenger installeren zodat ik minder voorovergebogen zit, regenkleren opnieuw behandelen zodat ze waterdicht zijn, en een tripje naar de Decathlon, voor waterdichte overschoenen, een achterlicht en wat waterdichte zakken. Daarnaast ben ik ook nog vandaag naar de gemeente geweest om een volmacht te regelen, voor de verkiezingen volgende week! @ 0e501ec7:de5ef3a4
2024-10-04 10:54:18Have you watched the pigeons? have you watched the crow? Heb je het beemdooievaarsbekje ooit al eens goed bekeken? Heb je al eens gevraagd aan de boomkikker hoe die naar het leven kijkt? Wat hen denkt van jouw prachtig onderhouden voortuingazon? Every species is a soul, a fire, a story, a story that is told and retold and retold Every species is a song A song of love, of life of neverending trial and struggle Trial and error they say, evolution they say, mutation and selection But your demystification is not working The species never stop telling their unholy wispering stories They never stop This is a song for the lost souls This is a song of grief This story tells the song ofthe species that don't that cannot anymore The species we lost I love you herfstvuurspin Ik hou van je ik hou van je ik Ik mis je Ik voel in heel mijn lijf dat je ontbreekt en ik ben zeker dat ik niet de enige ben
@ 0e501ec7:de5ef3a4
2024-10-04 10:54:18Have you watched the pigeons? have you watched the crow? Heb je het beemdooievaarsbekje ooit al eens goed bekeken? Heb je al eens gevraagd aan de boomkikker hoe die naar het leven kijkt? Wat hen denkt van jouw prachtig onderhouden voortuingazon? Every species is a soul, a fire, a story, a story that is told and retold and retold Every species is a song A song of love, of life of neverending trial and struggle Trial and error they say, evolution they say, mutation and selection But your demystification is not working The species never stop telling their unholy wispering stories They never stop This is a song for the lost souls This is a song of grief This story tells the song ofthe species that don't that cannot anymore The species we lost I love you herfstvuurspin Ik hou van je ik hou van je ik Ik mis je Ik voel in heel mijn lijf dat je ontbreekt en ik ben zeker dat ik niet de enige ben @ 0e501ec7:de5ef3a4
2024-10-03 09:54:14Dit is een eerste poging om een post te creëeren die op de oracolo html-blog verschijnt. Ik snap helemaal niet zo goed hoe dit allemaal werkt, maar het lijkt wel spannend. De blog werkt op basis van een htmlbestandje, dat je zou kunnen hosten via github. ofzo. Waarom zo en niet op een andere manier? Ik vind nostr wel cool, omdat het helemaal gedecentraliseerd is en zonder groot bedrijf. Het wordt gebouwd door een heleboel geëngageerde developpers, en is ook open-source. Joepie! Misschien is het gewoon eens iets anders dat ik wil uitproberen, dat kan ook. Allesinds, ik voel er (nog) niet de enorme weerstand tegen die ik wel voel bij alle meta-dingetjes zoals facebook enz. Als dit werkt gebruik ik het misschien wel als blog tijdens onze fietsreis, wie weet. Ah en nog iets, in navolging van de 100rabbits programeur die op een zeilboot woont: kleine apps die doen wat ze moeten doen om de computer minder te belasten en energie te besparen, dat is helemaal cool en duurzaam en heeft off-grid potentieel. (Maar daar heb ik dan wel weer een bedenking bij: nostr is wel wat verbonden met bitcoin, en die heeft niet zo een energie-zuinig imago.)
@ 0e501ec7:de5ef3a4
2024-10-03 09:54:14Dit is een eerste poging om een post te creëeren die op de oracolo html-blog verschijnt. Ik snap helemaal niet zo goed hoe dit allemaal werkt, maar het lijkt wel spannend. De blog werkt op basis van een htmlbestandje, dat je zou kunnen hosten via github. ofzo. Waarom zo en niet op een andere manier? Ik vind nostr wel cool, omdat het helemaal gedecentraliseerd is en zonder groot bedrijf. Het wordt gebouwd door een heleboel geëngageerde developpers, en is ook open-source. Joepie! Misschien is het gewoon eens iets anders dat ik wil uitproberen, dat kan ook. Allesinds, ik voel er (nog) niet de enorme weerstand tegen die ik wel voel bij alle meta-dingetjes zoals facebook enz. Als dit werkt gebruik ik het misschien wel als blog tijdens onze fietsreis, wie weet. Ah en nog iets, in navolging van de 100rabbits programeur die op een zeilboot woont: kleine apps die doen wat ze moeten doen om de computer minder te belasten en energie te besparen, dat is helemaal cool en duurzaam en heeft off-grid potentieel. (Maar daar heb ik dan wel weer een bedenking bij: nostr is wel wat verbonden met bitcoin, en die heeft niet zo een energie-zuinig imago.) @ e6817453:b0ac3c39
2024-09-30 14:52:23In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance. <iframe width="560" height="315" src="https://www.youtube.com/embed/BkNqu51et9U?si=lne0jWxdrZPxSgd1" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ## The Vector Search and Metadata Challenge In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results. Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data. ## LibSQL and vector search metadata LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points. ``` create table if not exists conversation ( id varchar(36) primary key not null, startDate real, endDate real, summary text, vectorSummary F32_BLOB(512) ); ``` It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage. As you can see, you can access vector-like data and start date in the same query. ``` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from conversation where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top}; ``` **vector\_distance\_cos** calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data. This approach could be calculation intensive and fail on large amounts of data. Libsql offers a way more effective vector search based on FlashDiskANN vector indexed. ``` vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i ``` **vector\_top\_k** is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies. Now we get a classical problem of integration vector search results with metadata queries. ## Post-Filtering: A Common Approach The most widely adopted method in these pipelines is **post-filtering**. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.  Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter. ``` const sqlQuery = ` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i inner join conversation c on i.id = c.rowid where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top}; ``` However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results. One working strategy is to make the top value in vector\_top\_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows. ## Pre-Filtering: A More Complex Approach Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning. While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.  In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data. ## Pre-filtering with distance-based filtering So, we are getting back to an old concept. We do prefiltering instead of using a vector index. ``` WITH FilteredDates AS ( SELECT c.id, c.startDate, c.endDate, c.summary, c.vectorSummary FROM YourTable c WHERE ${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''} ), DistanceCalculation AS ( SELECT fd.id, fd.startDate, fd.endDate, fd.summary, fd.vectorSummary, vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance FROM FilteredDates fd ) SELECT dc.id, dc.startDate, dc.endDate, dc.summary, dc.distance FROM DistanceCalculation dc WHERE 1=1 ${distance ? `AND dc.distance <= ${distance}` : ''} ORDER BY dc.distance LIMIT ${top}; ``` It makes sense if the filter produces small data and distance calculation happens on the smaller data set.  As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches. ## Choosing Between Pre and Post-Filtering Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization. In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further. ## **Conclusion** Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further.
@ e6817453:b0ac3c39
2024-09-30 14:52:23In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance. <iframe width="560" height="315" src="https://www.youtube.com/embed/BkNqu51et9U?si=lne0jWxdrZPxSgd1" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ## The Vector Search and Metadata Challenge In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results. Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data. ## LibSQL and vector search metadata LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points. ``` create table if not exists conversation ( id varchar(36) primary key not null, startDate real, endDate real, summary text, vectorSummary F32_BLOB(512) ); ``` It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage. As you can see, you can access vector-like data and start date in the same query. ``` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from conversation where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top}; ``` **vector\_distance\_cos** calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data. This approach could be calculation intensive and fail on large amounts of data. Libsql offers a way more effective vector search based on FlashDiskANN vector indexed. ``` vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i ``` **vector\_top\_k** is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies. Now we get a classical problem of integration vector search results with metadata queries. ## Post-Filtering: A Common Approach The most widely adopted method in these pipelines is **post-filtering**. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.  Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter. ``` const sqlQuery = ` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i inner join conversation c on i.id = c.rowid where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top}; ``` However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results. One working strategy is to make the top value in vector\_top\_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows. ## Pre-Filtering: A More Complex Approach Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning. While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.  In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data. ## Pre-filtering with distance-based filtering So, we are getting back to an old concept. We do prefiltering instead of using a vector index. ``` WITH FilteredDates AS ( SELECT c.id, c.startDate, c.endDate, c.summary, c.vectorSummary FROM YourTable c WHERE ${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''} ), DistanceCalculation AS ( SELECT fd.id, fd.startDate, fd.endDate, fd.summary, fd.vectorSummary, vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance FROM FilteredDates fd ) SELECT dc.id, dc.startDate, dc.endDate, dc.summary, dc.distance FROM DistanceCalculation dc WHERE 1=1 ${distance ? `AND dc.distance <= ${distance}` : ''} ORDER BY dc.distance LIMIT ${top}; ``` It makes sense if the filter produces small data and distance calculation happens on the smaller data set.  As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches. ## Choosing Between Pre and Post-Filtering Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization. In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further. ## **Conclusion** Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further. @ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x). # TL;DR This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/). The following concepts are explored: 1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust). 2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse. 3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time. The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems. [Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater. # Cognitive Dissonance Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol. I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement. The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership. For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data). In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned. How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data? # Self-sovereign Identity Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity. All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money. Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state. Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k). https://i.nostr.build/xpcCSkDg3uVw0yku.png While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this. Nostr is PGP for the masses and will take cryptographic identities mainstream. # Full NOSTARD? Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons. We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be. https://i.nostr.build/s3So2JVAqoY4E1dI.png There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap. While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g). https://i.nostr.build/ot9jtM5cZtDHNKWc.png So, how do we appropriately blend cryptographically owned data with the commons? If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons). The remainder of this article explores how we can: 1. Verify ownership of a physical place in the real world; 2. Link that ownership to the corresponding digital place in cyberspace. As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0. And as we all know, the Second Law of Infodynamics (no citation\!) states that: > "The total amount of sensitive information leaked will always increase over time." This especially holds true if that data is centralised. Not your keys, not your notes. Not your keys, not your identity. # Places and Web-of-Trust [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)). However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world. Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop. This requires users to: 1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace). 2. Signal this verification to their social graph. Let's look at the latter idea first with the concept of Attestations ... # Attestations A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false. Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too. However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc). Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation: https://i.nostr.build/lZAXOEwvRIghgFY4.png Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with: 1. Your social graph; 2. The type or subject of the content being attested and by whom; 3. Your personal preferences. They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places. [NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive. **‘This is true’** resonates more strongly than **‘I like this.’**. https://i.nostr.build/s8NIG2kXzUCLcoax.jpg There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP? https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust. # Proof of Place Attestations handle the signalling of your truth, but what about the initial verification itself? We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth. Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace. One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location. Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places). In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential): > "A failure to understand Proof of Work, is a failure to understand Bitcoin." In the Nostrverse, Proof of Place helps bridge the digital and physical worlds. [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that: > "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone." https://i.nostr.build/dOnpxfI4u7EL2v4e.png This isn’t true for Nostr. In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯 # Check-ins Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes). For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used. Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices. Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am. Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable. How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\! Check-ins could also be used as a signal for bonafide Place ownership over time. # Summary: Trust Your Bros So, to recap, we have: **Places**: Digital representations of physical locations on Nostr. **Check-ins**: Users signalling their presence at a location. **Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim. You can visualise how these three concepts combine in the diagram below: https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg And, as always, top right trumps bottom left\! We have: **Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all. **Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL. **Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph. https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map? Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide. As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities. # Thanks With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\!
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x). # TL;DR This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/). The following concepts are explored: 1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust). 2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse. 3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time. The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems. [Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater. # Cognitive Dissonance Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol. I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement. The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership. For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data). In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned. How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data? # Self-sovereign Identity Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity. All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money. Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state. Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k). https://i.nostr.build/xpcCSkDg3uVw0yku.png While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this. Nostr is PGP for the masses and will take cryptographic identities mainstream. # Full NOSTARD? Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons. We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be. https://i.nostr.build/s3So2JVAqoY4E1dI.png There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap. While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g). https://i.nostr.build/ot9jtM5cZtDHNKWc.png So, how do we appropriately blend cryptographically owned data with the commons? If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons). The remainder of this article explores how we can: 1. Verify ownership of a physical place in the real world; 2. Link that ownership to the corresponding digital place in cyberspace. As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0. And as we all know, the Second Law of Infodynamics (no citation\!) states that: > "The total amount of sensitive information leaked will always increase over time." This especially holds true if that data is centralised. Not your keys, not your notes. Not your keys, not your identity. # Places and Web-of-Trust [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)). However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world. Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop. This requires users to: 1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace). 2. Signal this verification to their social graph. Let's look at the latter idea first with the concept of Attestations ... # Attestations A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false. Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too. However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc). Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation: https://i.nostr.build/lZAXOEwvRIghgFY4.png Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with: 1. Your social graph; 2. The type or subject of the content being attested and by whom; 3. Your personal preferences. They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places. [NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive. **‘This is true’** resonates more strongly than **‘I like this.’**. https://i.nostr.build/s8NIG2kXzUCLcoax.jpg There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP? https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust. # Proof of Place Attestations handle the signalling of your truth, but what about the initial verification itself? We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth. Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace. One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location. Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places). In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential): > "A failure to understand Proof of Work, is a failure to understand Bitcoin." In the Nostrverse, Proof of Place helps bridge the digital and physical worlds. [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that: > "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone." https://i.nostr.build/dOnpxfI4u7EL2v4e.png This isn’t true for Nostr. In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯 # Check-ins Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes). For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used. Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices. Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am. Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable. How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\! Check-ins could also be used as a signal for bonafide Place ownership over time. # Summary: Trust Your Bros So, to recap, we have: **Places**: Digital representations of physical locations on Nostr. **Check-ins**: Users signalling their presence at a location. **Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim. You can visualise how these three concepts combine in the diagram below: https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg And, as always, top right trumps bottom left\! We have: **Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all. **Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL. **Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph. https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map? Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide. As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities. # Thanks With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\! @ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining. Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully. Solo mining pools exist, such as: https://solo.ckpool.org/ It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool. You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power. There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely. A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine. So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning. So here’s my recommendation. Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin. Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join. If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools. Bear in mind that many of the other smaller pools are still controlled by Bitmain. If you're still interested in lottery mining, here are your chances of winning a block: Represented as Hash rates of different miners: Nerdminer: 20 KH/s = 20,000 H/s Bitaxe: 750 GH/s = 750,000,000,000 H/s Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000 If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357% Over a year, your chances increase to: 0.00627707006369428% Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one): 0.000005% Over a year, your chances increase to: 0.00026% Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions: https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/ https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx https://www.youtube.com/watch?v=Wo91DWvZRs8 https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
@ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining. Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully. Solo mining pools exist, such as: https://solo.ckpool.org/ It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool. You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power. There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely. A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine. So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning. So here’s my recommendation. Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin. Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join. If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools. Bear in mind that many of the other smaller pools are still controlled by Bitmain. If you're still interested in lottery mining, here are your chances of winning a block: Represented as Hash rates of different miners: Nerdminer: 20 KH/s = 20,000 H/s Bitaxe: 750 GH/s = 750,000,000,000 H/s Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000 If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357% Over a year, your chances increase to: 0.00627707006369428% Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one): 0.000005% Over a year, your chances increase to: 0.00026% Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions: https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/ https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx https://www.youtube.com/watch?v=Wo91DWvZRs8 https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg @ 01d0bbf9:91130d4c
2024-09-26 17:58:10## Chef's notes Amazingly tangy, firey hot, but still mellow and bright. I use this on everything– Use it to dress salads, dip (honey mustard) for fried chicken, elevate your taco nights, heck a spoonful first thing in the morning will wake you up better than coffee! Don't forget to use up those delicious chilis and garlic, they are so good! ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 1-2 weeks - 🍽️ Servings: (12x) 8oz jars ## Ingredients - 16oz fresh chili peppers - 8oz red onion - 8oz garlic - 96oz honey - Fresh thyme ## Directions 1. Thinly slice peppers, garlic, shallots and fresh thyme 2. Add chopped ingredients to the honey 3. Leave to ferment (loosely covered) for 1-2 weeks 4. Drizzle that amazing pungent firey gold liquid over EVERYTHING. (Don't forget to use up those amazing chilis and garlic too.)
@ 01d0bbf9:91130d4c
2024-09-26 17:58:10## Chef's notes Amazingly tangy, firey hot, but still mellow and bright. I use this on everything– Use it to dress salads, dip (honey mustard) for fried chicken, elevate your taco nights, heck a spoonful first thing in the morning will wake you up better than coffee! Don't forget to use up those delicious chilis and garlic, they are so good! ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 1-2 weeks - 🍽️ Servings: (12x) 8oz jars ## Ingredients - 16oz fresh chili peppers - 8oz red onion - 8oz garlic - 96oz honey - Fresh thyme ## Directions 1. Thinly slice peppers, garlic, shallots and fresh thyme 2. Add chopped ingredients to the honey 3. Leave to ferment (loosely covered) for 1-2 weeks 4. Drizzle that amazing pungent firey gold liquid over EVERYTHING. (Don't forget to use up those amazing chilis and garlic too.) @ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like: Messaging: https://www.0xchat.com/#/ - Private messaging - think WhatsApp Xitter Like Clients: https://damus.io/ - iPhone client https://nostrapps.com/amethyst - Android client https://primal.net/downloads - Android, iPhone & Desktop https://shipyard.pub/posts - Schedule future posts Interesting sites: https://zap.stream/ - Video streaming https://fountain.fm/ - Podcasting https://wavlake.com/ - Music streaming https://shopstr.store/ - Online shop https://zap.cooking/recent - Cooking recipes https://ostrich.work/ - NOSTR jobs board NOSTR tools https://nostr.band/ - Powerful search tool https://nostr.wine/ - Powerful, but centralised paid relay https://npub.pro/ - Website creation tool https://nostr.build/ - Media and file storage https://relay.tools/ - Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user - Creator tools List of NOSTR apps: https://nostrapps.com/
@ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like: Messaging: https://www.0xchat.com/#/ - Private messaging - think WhatsApp Xitter Like Clients: https://damus.io/ - iPhone client https://nostrapps.com/amethyst - Android client https://primal.net/downloads - Android, iPhone & Desktop https://shipyard.pub/posts - Schedule future posts Interesting sites: https://zap.stream/ - Video streaming https://fountain.fm/ - Podcasting https://wavlake.com/ - Music streaming https://shopstr.store/ - Online shop https://zap.cooking/recent - Cooking recipes https://ostrich.work/ - NOSTR jobs board NOSTR tools https://nostr.band/ - Powerful search tool https://nostr.wine/ - Powerful, but centralised paid relay https://npub.pro/ - Website creation tool https://nostr.build/ - Media and file storage https://relay.tools/ - Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user - Creator tools List of NOSTR apps: https://nostrapps.com/ @ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous. In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism. On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important. That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played. Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end. The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism: I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is. In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore. The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true. The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good. In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.” I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous. In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism. On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important. That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played. Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end. The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism: I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is. In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore. The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true. The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good. In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.” I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it. @ ee11a5df:b76c4e49
2024-09-11 08:16:37# Bye-Bye Reply Guy There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients. But we are not there yet. In the mean time we have ReplyGuy, and gossip needed some changes to deal with it. ## Strategies in Short 1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people. 2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering. 3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post) 4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more. 5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity 6. **PROOF OF WORK**: Require a minimum proof-of-work All of these strategies are useful, but they have to be combined properly. ## filter.rhai Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam. This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release. Here is an example using all of the techniques listed above: ```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off) fn filter() { // Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY } ```
@ ee11a5df:b76c4e49
2024-09-11 08:16:37# Bye-Bye Reply Guy There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients. But we are not there yet. In the mean time we have ReplyGuy, and gossip needed some changes to deal with it. ## Strategies in Short 1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people. 2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering. 3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post) 4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more. 5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity 6. **PROOF OF WORK**: Require a minimum proof-of-work All of these strategies are useful, but they have to be combined properly. ## filter.rhai Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam. This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release. Here is an example using all of the techniques listed above: ```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off) fn filter() { // Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY } ``` @ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good! If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/> # Intro **Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us. **Paolo:** Thank you for having us. **Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we? **Luke:** Sounds like that's the plan. So thank you again, both for joining us. # Introducing Paolo and Mathias **Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you **Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate. **Luke:** And, Mathias, over to you. **Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use. P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that. And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here. **Luke:** Oh, fantastic. # Introduction to Holepunch **Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch. What is Holepunch and what are you doing? **Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us. but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy. It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God. that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks. Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use, Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it? and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world. And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company. And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand. anything, super exciting and, encourage everybody to try to check it out. **Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product? What is the easiest way that you would explain what it is? # The Vision Behind Keet **Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer People don't care about technology. We loved it, but don't have that surface off too much to the user. Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it. It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard. And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that. # Keet vs Nostr **Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here. **Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform. And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly. You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users. So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays. and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology. It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace. Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly. **Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that. # Pear Runtime **Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform, **Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it. And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications. We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that. So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve. But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything. So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view. and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard. so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example. It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app. So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place. But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that. And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone. And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached. Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like **Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective. And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that? **Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective. And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things. I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point. # Decentralization vs. Centralization **Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor? **Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias. I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right? Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions. and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers. That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there. And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far. Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features. And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users. And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is. It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that. And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key **Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites. But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept. over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud. And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers. the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on. is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole. And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before. Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize. And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system. And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country. So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to. **Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives. So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right? **Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all. So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting. yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why # Challenges and Future of Decentralization **Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company. And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing. So is there a limitation to how far this can go? **Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world. Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling. So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house. I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created. imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you. Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure. So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another. And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example. **Knut:** Yeah. **Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money. And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook? it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way. And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it. We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback. # Bitcoin and Holepunch: Drawing Parallels **Mathias:** I think, that's the main thing to think about in that. Discussion. **Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line. And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin? **Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange. For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government. and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right? Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them. and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them. **Luke:** Yeah, fantastic. # The Future of Decentralized Communication **Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet. So is, that a goal? Is that on the roadmap? **Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world. But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind. **Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly. And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app. And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly, # Interoperability and User Experience **Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong, **Mathias:** Very, true. **Luke:** you backups with the same 1224 words. Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be **Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it. **Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life. You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build. Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible. **Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems? What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that? **Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us. The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity. No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful. **Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever. but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera. But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem. And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it. **Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options. Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right? you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion. so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai. So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that. And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself. And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center. **Knut:** Yeah. # The Role of Tether in the Crypto Ecosystem **Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo? And, what, made this thing happen? Can you give us the story here about Tether? # Tether's Origin and Evolution **Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014. it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat. That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000. But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right? International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin. For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic. # USDT's Impact on Emerging Markets **Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries. Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap. So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time. we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world. At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right? you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others. And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT. If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right? So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U. S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant. # Bitcoin as a Savings Account **Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend. The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies. we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining. We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other. I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math. That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin. **Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother. **Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether. So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right? So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education. **Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic. I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke. **Luke:** Always say the title, Knut. Always say the title. **Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course. **Paolo:** Oh, with pleasure, with great pleasure, with a nice, education. **Luke:** Absolutely. Yep. # Plan B Forum and Future Events **Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year. so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event. **Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year. I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world. And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing. **Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time. And I think we're even playing this year, aren't we, Luke? **Paolo:** You're **Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos. Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague? **Knut:** paranoid and, **Paolo:** Can I commission a **Knut:** What song would you like to hear? **Paolo:** I have two that I would suggest. One is Nothing Else Matters. **Knut:** Alright. **Paolo:** So I think that, is very inspiring, right? **Knut:** Bitcoin, for sure. Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke? **Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference, **Knut:** Yeah. **Mathias:** not so much music, but yeah, that's peer to **Knut:** Nothing else matters. **Luke:** looking forward to that. **Knut:** Sorry, brain fart. Sad but true is about the dollar still being around, **Paolo:** Yeah, you can say that. **Luke:** Okay. # Final Thoughts and Closing Remarks **Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that? **Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms. There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out. **Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting. **Mathias:** Just those things, that's all. **Paolo:** Yeah, we can piss off more than this. Thanks. **Mathias:** a **Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners? **Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them. **Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good. **Luke:** So that's, all at Keet. Is that correct? For Keet? **Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer. **Knut:** Alright, **Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah. **Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano. **Paolo:** Likewise, I **Knut:** But yeah, worth saying again. **Paolo:** Thank you for having an invitation. **Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
@ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good! If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/> # Intro **Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us. **Paolo:** Thank you for having us. **Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we? **Luke:** Sounds like that's the plan. So thank you again, both for joining us. # Introducing Paolo and Mathias **Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you **Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate. **Luke:** And, Mathias, over to you. **Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use. P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that. And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here. **Luke:** Oh, fantastic. # Introduction to Holepunch **Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch. What is Holepunch and what are you doing? **Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us. but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy. It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God. that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks. Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use, Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it? and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world. And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company. And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand. anything, super exciting and, encourage everybody to try to check it out. **Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product? What is the easiest way that you would explain what it is? # The Vision Behind Keet **Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer People don't care about technology. We loved it, but don't have that surface off too much to the user. Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it. It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard. And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that. # Keet vs Nostr **Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here. **Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform. And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly. You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users. So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays. and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology. It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace. Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly. **Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that. # Pear Runtime **Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform, **Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it. And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications. We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that. So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve. But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything. So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view. and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard. so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example. It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app. So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place. But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that. And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone. And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached. Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like **Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective. And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that? **Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective. And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things. I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point. # Decentralization vs. Centralization **Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor? **Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias. I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right? Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions. and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers. That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there. And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far. Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features. And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users. And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is. It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that. And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key **Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites. But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept. over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud. And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers. the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on. is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole. And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before. Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize. And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system. And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country. So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to. **Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives. So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right? **Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all. So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting. yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why # Challenges and Future of Decentralization **Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company. And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing. So is there a limitation to how far this can go? **Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world. Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling. So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house. I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created. imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you. Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure. So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another. And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example. **Knut:** Yeah. **Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money. And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook? it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way. And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it. We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback. # Bitcoin and Holepunch: Drawing Parallels **Mathias:** I think, that's the main thing to think about in that. Discussion. **Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line. And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin? **Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange. For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government. and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right? Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them. and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them. **Luke:** Yeah, fantastic. # The Future of Decentralized Communication **Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet. So is, that a goal? Is that on the roadmap? **Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world. But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind. **Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly. And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app. And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly, # Interoperability and User Experience **Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong, **Mathias:** Very, true. **Luke:** you backups with the same 1224 words. Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be **Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it. **Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life. You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build. Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible. **Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems? What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that? **Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us. The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity. No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful. **Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever. but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera. But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem. And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it. **Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options. Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right? you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion. so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai. So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that. And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself. And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center. **Knut:** Yeah. # The Role of Tether in the Crypto Ecosystem **Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo? And, what, made this thing happen? Can you give us the story here about Tether? # Tether's Origin and Evolution **Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014. it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat. That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000. But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right? International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin. For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic. # USDT's Impact on Emerging Markets **Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries. Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap. So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time. we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world. At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right? you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others. And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT. If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right? So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U. S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant. # Bitcoin as a Savings Account **Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend. The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies. we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining. We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other. I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math. That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin. **Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother. **Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether. So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right? So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education. **Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic. I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke. **Luke:** Always say the title, Knut. Always say the title. **Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course. **Paolo:** Oh, with pleasure, with great pleasure, with a nice, education. **Luke:** Absolutely. Yep. # Plan B Forum and Future Events **Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year. so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event. **Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year. I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world. And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing. **Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time. And I think we're even playing this year, aren't we, Luke? **Paolo:** You're **Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos. Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague? **Knut:** paranoid and, **Paolo:** Can I commission a **Knut:** What song would you like to hear? **Paolo:** I have two that I would suggest. One is Nothing Else Matters. **Knut:** Alright. **Paolo:** So I think that, is very inspiring, right? **Knut:** Bitcoin, for sure. Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke? **Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference, **Knut:** Yeah. **Mathias:** not so much music, but yeah, that's peer to **Knut:** Nothing else matters. **Luke:** looking forward to that. **Knut:** Sorry, brain fart. Sad but true is about the dollar still being around, **Paolo:** Yeah, you can say that. **Luke:** Okay. # Final Thoughts and Closing Remarks **Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that? **Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms. There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out. **Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting. **Mathias:** Just those things, that's all. **Paolo:** Yeah, we can piss off more than this. Thanks. **Mathias:** a **Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners? **Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them. **Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good. **Luke:** So that's, all at Keet. Is that correct? For Keet? **Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer. **Knut:** Alright, **Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah. **Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano. **Paolo:** Likewise, I **Knut:** But yeah, worth saying again. **Paolo:** Thank you for having an invitation. **Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show. @ 8cb60e21:5f2deaea
2024-09-10 21:14:08<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-10 21:14:08<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint. I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point. I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog. In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout. Are there any odds you're excited about (doesn't have to be football)? originally posted at https://stacker.news/items/679894
@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint. I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point. I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog. In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout. Are there any odds you're excited about (doesn't have to be football)? originally posted at https://stacker.news/items/679894 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。 通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。 --- 2024年08月13日更新: > 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。 为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。 --- ### 准备工具 - Ntfy服务 - Google Script - Google Sheets ### 操作步骤 1. 在Ntfy后台账号,设置访问令牌。 [](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌") 2. 添加订阅主题。 [](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题") 2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图: [](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id") 3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌): ```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet(); // 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据 var sentEmails = getSentEmails(sheet); var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length); if (threads.length === 0) return; threads.forEach(function(thread) { var threadId = thread.getId(); if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); } }); } function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; } var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"} 内容: ${email.getPlainBody() || "无内容"}`; var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true }; try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } } function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column } function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); } function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间 var data = sheet.getDataRange().getValues(); var rowsToDelete = []; data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } }); // 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); } ``` 4.Goole Script需要添加gmail服务,如图: [](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务") 5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图: [](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器") [](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细") ### 结尾 本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。 如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。 效果预览: [](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览")
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。 通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。 --- 2024年08月13日更新: > 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。 为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。 --- ### 准备工具 - Ntfy服务 - Google Script - Google Sheets ### 操作步骤 1. 在Ntfy后台账号,设置访问令牌。 [](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌") 2. 添加订阅主题。 [](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题") 2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图: [](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id") 3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌): ```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet(); // 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据 var sentEmails = getSentEmails(sheet); var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length); if (threads.length === 0) return; threads.forEach(function(thread) { var threadId = thread.getId(); if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); } }); } function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; } var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"} 内容: ${email.getPlainBody() || "无内容"}`; var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true }; try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } } function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column } function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); } function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间 var data = sheet.getDataRange().getValues(); var rowsToDelete = []; data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } }); // 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); } ``` 4.Goole Script需要添加gmail服务,如图: [](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务") 5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图: [](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器") [](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细") ### 结尾 本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。 如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。 效果预览: [](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览") @ 655a7cf1:d0510794
2024-09-10 13:16:15Currently have kyc BTC, huge fan of lightning Network. Because I am a constant user of lightning. Plan on doing my business with lightning as well , peer-to-peer I'm not sure if I'm so worried about kyc I might be misguided in this situation. originally posted at https://stacker.news/items/679520
@ 655a7cf1:d0510794
2024-09-10 13:16:15Currently have kyc BTC, huge fan of lightning Network. Because I am a constant user of lightning. Plan on doing my business with lightning as well , peer-to-peer I'm not sure if I'm so worried about kyc I might be misguided in this situation. originally posted at https://stacker.news/items/679520 @ 6ad3e2a3:c90b7740
2024-09-10 09:26:37While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions: **1. Separate passengers from their bags as early as possible.** The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences: a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes. b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day. c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five. d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier. e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable. The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children. To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc. There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.) Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane. **2. Eliminate Security Lines** Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement. a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use. Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious. b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side. Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side. **3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.** Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal. **4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.** There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done. Here are some other suggestions: 1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up. 2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges. 3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease. 4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them. I can anticipate some objections to these ideas, and I’ll address each one in turn. **1. This would cost too much money.** My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.) **2. It’s too much of a security risk.** Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end. Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle. **3. I like free carry-ons because it saves me from waiting at the baggage claim.** Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse. The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist. *\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.* *\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.*
@ 6ad3e2a3:c90b7740
2024-09-10 09:26:37While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions: **1. Separate passengers from their bags as early as possible.** The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences: a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes. b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day. c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five. d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier. e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable. The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children. To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc. There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.) Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane. **2. Eliminate Security Lines** Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement. a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use. Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious. b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side. Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side. **3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.** Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal. **4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.** There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done. Here are some other suggestions: 1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up. 2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges. 3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease. 4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them. I can anticipate some objections to these ideas, and I’ll address each one in turn. **1. This would cost too much money.** My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.) **2. It’s too much of a security risk.** Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end. Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle. **3. I like free carry-ons because it saves me from waiting at the baggage claim.** Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse. The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist. *\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.* *\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.* @ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed. @ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
@ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg @ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect. Therefore, I strongly advise you to run multiple clients. On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay. If you haven’t taken the plunge to run a node, now might be a good time to think about it. There are many, many options for clients, the “Social” section of https://nostrapps.com/ lists 23 currently. Play with them, see what they do, if you’re a developer, you could even consider building or forking your own. Have fun and realise we are building freedom tech, not just running it.
@ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect. Therefore, I strongly advise you to run multiple clients. On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay. If you haven’t taken the plunge to run a node, now might be a good time to think about it. There are many, many options for clients, the “Social” section of https://nostrapps.com/ lists 23 currently. Play with them, see what they do, if you’re a developer, you could even consider building or forking your own. Have fun and realise we are building freedom tech, not just running it. @ e83b66a8:b0526c2b
2024-09-09 20:27:41First, Key management. When you “created” your NOSTR account, what you actually created was a cryptographic key pair. This consists of a private key, which starts “nsec” and a public key which starts with “npub”. As the names suggest, your “nsec” key is private and you should never reveal it to anyone. Your “npub” key is your public key, feel free to share that everywhere. Your “npub” key is used by others to verify your identity, through the signature added to your messages. It is also used by others to encrypt private messages to you. We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary. For the moment, consider using software key management options, some of which are listed under “signers” here: https://nostrapps.com/ N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted: Secondly, Lightning wallets. It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key. You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet. Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason…. It also allows you to send small micropayments to posts or people you like. Thirdly, Paid Services As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability. I, for example choose to pay for the following services: https://nostr.wine/ - 120,000 Sats for 2 years relay https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month https://nostr.build/ - Media storage - 69,000 Sats for 1 year Total: 22,750 Sats per month Approx $15 per month This is not strictly necessary, but I decided to support the various developers behind these projects. Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward.
@ e83b66a8:b0526c2b
2024-09-09 20:27:41First, Key management. When you “created” your NOSTR account, what you actually created was a cryptographic key pair. This consists of a private key, which starts “nsec” and a public key which starts with “npub”. As the names suggest, your “nsec” key is private and you should never reveal it to anyone. Your “npub” key is your public key, feel free to share that everywhere. Your “npub” key is used by others to verify your identity, through the signature added to your messages. It is also used by others to encrypt private messages to you. We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary. For the moment, consider using software key management options, some of which are listed under “signers” here: https://nostrapps.com/ N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted: Secondly, Lightning wallets. It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key. You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet. Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason…. It also allows you to send small micropayments to posts or people you like. Thirdly, Paid Services As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability. I, for example choose to pay for the following services: https://nostr.wine/ - 120,000 Sats for 2 years relay https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month https://nostr.build/ - Media storage - 69,000 Sats for 1 year Total: 22,750 Sats per month Approx $15 per month This is not strictly necessary, but I decided to support the various developers behind these projects. Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward. @ c11cf5f8:4928464d
2024-09-09 18:45:16 originally posted at https://stacker.news/items/678432
@ c11cf5f8:4928464d
2024-09-09 18:45:16 originally posted at https://stacker.news/items/678432 @ e968e50b:db2a803a
2024-09-09 18:21:54 Open the frozen pizza bay doors, Hal. originally posted at https://stacker.news/items/678403
@ e968e50b:db2a803a
2024-09-09 18:21:54 Open the frozen pizza bay doors, Hal. originally posted at https://stacker.news/items/678403 @ 6bae33c8:607272e8
2024-09-09 16:07:43I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
@ 6bae33c8:607272e8
2024-09-09 16:07:43I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed. @ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :) I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet. What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds? What is your experience? I'd love to hear about it!
@ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :) I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet. What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds? What is your experience? I'd love to hear about it! @ 3875a16c:988456c9
2024-09-09 14:50:15**ORIGINAL PANEL TITLE:** MAKING BITCOIN MORE PRIVATE WITH CISA **SPEAKERS:** NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP **CONFERENCE:** BITCOIN NASHVILLE 2024 **ORIGINALLY PUBLISHED ON:** BITLYRICS.CO ## Introduction This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/). Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development. --- ### NiftyNei (Moderator): Hey everyone, my name is Nifty, and I’m going to be moderating this panel today. We’re here to talk about CISA (cross-input signature aggregation). Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage. We’re excited to be talking to you guys about this. I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA. Craig, do you want to start? --- ### Craig Raw (Sparrow Wallet): I built Sparrow Wallet. It’s a security and privacy-focused wallet. The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen. When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically. So, that was the first time I really started to look at it from the privacy angle. --- ### Fabian Jahr (Brink): I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it. Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core. Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months. I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller. I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it. --- ### Jameson Lopp (Casa): I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups. I think the first time I heard about CISA was in an Andrew Poelstra talk. I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted. This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics. --- ### NiftyNei (Moderator): That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for. Does anyone have a good explanation of how it works? --- ### Fabian Jahr (Brink): I can start off. So, it’s really already all in the name: cross-input signature aggregation. If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated. What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction. So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before. Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea. --- ### NiftyNei (Moderator): I have a quick question about that. So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right? So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature. Is that a good summary of what you’re explaining? --- ### Fabian Jahr (Brink): Yeah, I would say so. --- ### Craig Raw (Sparrow Wallet): So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it. That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one. Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it. Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones. Unfortunately, the downside of that is that you have to do the interaction while you sign. The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing. As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient. --- ### NiftyNei (Moderator): Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right? You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level? --- ### Jameson Lopp (Casa): Well, there’s also full-block aggregation, right? This is going really far down the rabbit hole, and I think it’s not even something that’s on the table. There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations. My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized. If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again. --- ### NiftyNei (Moderator): So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation. We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there. One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right? Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated. --- ### Jameson Lopp (Casa): Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically. If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount. It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO. You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet. It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot. It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before. So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so. --- ### Fabian Jahr (Brink): And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy. The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property. Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.” Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it. Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature. --- ### Jameson Lopp (Casa): Yeah, we have to think about the incentives, right? I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are. But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late. We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so. It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software. Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money? --- ### Craig Raw (Sparrow): So you might be wondering at this stage what the savings actually look like. It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block. You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage. Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%. But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space. So that’s how I would encourage you to think about it from the start. For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride. We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about. --- ### NiftyNei (Moderator): I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy. I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal? What was it about the Taproot process where this proposal didn’t make it over the line? --- ### Fabian Jahr (Brink): I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed. From what I can see, I don’t think there was any direct opposition. The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller. I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding. I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much. --- ### Craig Raw (Sparrow): Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough. There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.” That’s an interesting point of view. --- ### Jameson Lopp (Casa): It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet. --- ### Craig Raw (Sparrow): Yeah, so we’re in a very different space now. Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine. I’m talking about the well-understood half-signature aggregation form of it. From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that. So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing. If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down. So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line. --- ### Jameson Lopp (Casa): I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin. With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process. As far as I’m aware, there’s been limited adoption of Schnorr so far. I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility. I care about this a lot, operating a multi-signature self-custody wallet. We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature. That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out. So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block. --- ### NiftyNei (Moderator): So, we only have a few minutes left. Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in. --- ### Fabian Jahr (Brink): There are still quite a few things to hammer out in terms of all the details, like defining a spec. For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open. However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity. We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now. --- ### Jameson Lopp (Casa): Yeah, call your local developer and demand signature aggregation today. --- ### Craig Raw (Sparrow): Fabian has developed a great site where you can learn more. If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it. It’s very easy to read, not overly technical, and I think it gives a good grounding in these things. Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not. As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now. So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not. --- ### Jameson Lopp (Casa): I don’t know, do you want to save money? It should be an easy question. --- ### Fabian Jahr (Brink): And have better privacy. --- ### NiftyNei (Moderator): Great! Thanks y’all. --- **Follow the speakers: ** [NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr) **Watch the original content: ** [Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107) **Also read: Build It Right: ** [Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/) **Disclaimer: ** Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/).
@ 3875a16c:988456c9
2024-09-09 14:50:15**ORIGINAL PANEL TITLE:** MAKING BITCOIN MORE PRIVATE WITH CISA **SPEAKERS:** NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP **CONFERENCE:** BITCOIN NASHVILLE 2024 **ORIGINALLY PUBLISHED ON:** BITLYRICS.CO ## Introduction This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/). Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development. --- ### NiftyNei (Moderator): Hey everyone, my name is Nifty, and I’m going to be moderating this panel today. We’re here to talk about CISA (cross-input signature aggregation). Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage. We’re excited to be talking to you guys about this. I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA. Craig, do you want to start? --- ### Craig Raw (Sparrow Wallet): I built Sparrow Wallet. It’s a security and privacy-focused wallet. The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen. When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically. So, that was the first time I really started to look at it from the privacy angle. --- ### Fabian Jahr (Brink): I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it. Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core. Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months. I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller. I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it. --- ### Jameson Lopp (Casa): I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups. I think the first time I heard about CISA was in an Andrew Poelstra talk. I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted. This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics. --- ### NiftyNei (Moderator): That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for. Does anyone have a good explanation of how it works? --- ### Fabian Jahr (Brink): I can start off. So, it’s really already all in the name: cross-input signature aggregation. If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated. What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction. So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before. Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea. --- ### NiftyNei (Moderator): I have a quick question about that. So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right? So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature. Is that a good summary of what you’re explaining? --- ### Fabian Jahr (Brink): Yeah, I would say so. --- ### Craig Raw (Sparrow Wallet): So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it. That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one. Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it. Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones. Unfortunately, the downside of that is that you have to do the interaction while you sign. The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing. As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient. --- ### NiftyNei (Moderator): Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right? You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level? --- ### Jameson Lopp (Casa): Well, there’s also full-block aggregation, right? This is going really far down the rabbit hole, and I think it’s not even something that’s on the table. There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations. My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized. If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again. --- ### NiftyNei (Moderator): So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation. We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there. One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right? Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated. --- ### Jameson Lopp (Casa): Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically. If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount. It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO. You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet. It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot. It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before. So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so. --- ### Fabian Jahr (Brink): And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy. The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property. Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.” Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it. Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature. --- ### Jameson Lopp (Casa): Yeah, we have to think about the incentives, right? I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are. But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late. We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so. It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software. Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money? --- ### Craig Raw (Sparrow): So you might be wondering at this stage what the savings actually look like. It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block. You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage. Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%. But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space. So that’s how I would encourage you to think about it from the start. For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride. We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about. --- ### NiftyNei (Moderator): I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy. I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal? What was it about the Taproot process where this proposal didn’t make it over the line? --- ### Fabian Jahr (Brink): I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed. From what I can see, I don’t think there was any direct opposition. The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller. I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding. I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much. --- ### Craig Raw (Sparrow): Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough. There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.” That’s an interesting point of view. --- ### Jameson Lopp (Casa): It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet. --- ### Craig Raw (Sparrow): Yeah, so we’re in a very different space now. Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine. I’m talking about the well-understood half-signature aggregation form of it. From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that. So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing. If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down. So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line. --- ### Jameson Lopp (Casa): I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin. With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process. As far as I’m aware, there’s been limited adoption of Schnorr so far. I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility. I care about this a lot, operating a multi-signature self-custody wallet. We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature. That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out. So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block. --- ### NiftyNei (Moderator): So, we only have a few minutes left. Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in. --- ### Fabian Jahr (Brink): There are still quite a few things to hammer out in terms of all the details, like defining a spec. For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open. However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity. We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now. --- ### Jameson Lopp (Casa): Yeah, call your local developer and demand signature aggregation today. --- ### Craig Raw (Sparrow): Fabian has developed a great site where you can learn more. If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it. It’s very easy to read, not overly technical, and I think it gives a good grounding in these things. Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not. As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now. So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not. --- ### Jameson Lopp (Casa): I don’t know, do you want to save money? It should be an easy question. --- ### Fabian Jahr (Brink): And have better privacy. --- ### NiftyNei (Moderator): Great! Thanks y’all. --- **Follow the speakers: ** [NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr) **Watch the original content: ** [Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107) **Also read: Build It Right: ** [Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/) **Disclaimer: ** Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/). @ 44dc1c2d:31c74f0b
2024-09-09 01:55:24## Chef's notes Makes an excellent Chicken sandwich. ## Details - ⏲️ Prep time: 6 Ish hours - 🍳 Cook time: 40 min - 🍽️ Servings: 1 loaf ## Ingredients - 3 ½ - 4 cups bread flour, or more as needed - 1 ⅓ cups warm milk (110°F – 115°F) - 5 tablespoons honey - 4 tablespoons salted butter, melted and slightly cooled - 1 tablespoon instant “rapid rise” yeast - 1 ½ teaspoons salt - Oil or butter for greasing the bowl - 1 tablespoon melted salted butter, for brushing the crust at the end ## Directions 1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl. 2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes. 3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours. 4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan. 5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F. 6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped. 7. Brush the top of the warm bread with melted butter. 8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24## Chef's notes Makes an excellent Chicken sandwich. ## Details - ⏲️ Prep time: 6 Ish hours - 🍳 Cook time: 40 min - 🍽️ Servings: 1 loaf ## Ingredients - 3 ½ - 4 cups bread flour, or more as needed - 1 ⅓ cups warm milk (110°F – 115°F) - 5 tablespoons honey - 4 tablespoons salted butter, melted and slightly cooled - 1 tablespoon instant “rapid rise” yeast - 1 ½ teaspoons salt - Oil or butter for greasing the bowl - 1 tablespoon melted salted butter, for brushing the crust at the end ## Directions 1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl. 2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes. 3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours. 4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan. 5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F. 6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped. 7. Brush the top of the warm bread with melted butter. 8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing. @ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one? Thanks originally posted at https://stacker.news/items/677439
@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one? Thanks originally posted at https://stacker.news/items/677439 @ eed76ece:afa98124
2024-09-08 21:13:37Seems like if you want to sell an item on SN using @AGORA makes logical sense. Perhaps if your a manufacturer, importer, exporter, stocking distributor, wholesaler etc. you should also consider using @Import_Export or both @AGORA and see if they help each other. Being totally upfront Import_Export is probably a better use case especially if you are running over 75% B2B. We are note promoting the use of B2C on SN. We're 100% focused on interactions between businesses only. Our primary markets are in Asia and Southeast Asia. Europe and the UK are dying a slow death, and the last straw was the Telegram event. So I am endorsing you to please at least on SN refer to @AGORA for basic B2C (retail). Thank you, https://www.globalmerchant.io originally posted at https://stacker.news/items/677390
@ eed76ece:afa98124
2024-09-08 21:13:37Seems like if you want to sell an item on SN using @AGORA makes logical sense. Perhaps if your a manufacturer, importer, exporter, stocking distributor, wholesaler etc. you should also consider using @Import_Export or both @AGORA and see if they help each other. Being totally upfront Import_Export is probably a better use case especially if you are running over 75% B2B. We are note promoting the use of B2C on SN. We're 100% focused on interactions between businesses only. Our primary markets are in Asia and Southeast Asia. Europe and the UK are dying a slow death, and the last straw was the Telegram event. So I am endorsing you to please at least on SN refer to @AGORA for basic B2C (retail). Thank you, https://www.globalmerchant.io originally posted at https://stacker.news/items/677390 @ e8b86bc1:3503c58f
2024-09-08 19:37:36Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> Freewallet is now charging inactivity fees, a sneaky method to take money from users who aren’t regularly using the app. Avoid this scam wallet! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
@ e8b86bc1:3503c58f
2024-09-08 19:37:36Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> Freewallet is now charging inactivity fees, a sneaky method to take money from users who aren’t regularly using the app. Avoid this scam wallet! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app) @ c11cf5f8:4928464d
2024-09-08 19:10:39Considering the "whatever" item in question is a random item, a unique piece --not something you produce or need to market-- which platform, website or which strategy you'll put in place to get the value of your item in sats, immediately, anonymously, via the Lightning Network? originally posted at https://stacker.news/items/677270
@ c11cf5f8:4928464d
2024-09-08 19:10:39Considering the "whatever" item in question is a random item, a unique piece --not something you produce or need to market-- which platform, website or which strategy you'll put in place to get the value of your item in sats, immediately, anonymously, via the Lightning Network? originally posted at https://stacker.news/items/677270 @ 6f170f27:711e26dd
2024-09-08 17:45:46 > Far too many people: "GDP is bad. I prefer [thing correlated at 0.9 with GDP]." Manufacturing:  Life expectancy:  Happiness:  Many other metrics & discussion in the source: https://x.com/cremieuxrecueil/status/1832588128084730334 originally posted at https://stacker.news/items/677211
@ 6f170f27:711e26dd
2024-09-08 17:45:46 > Far too many people: "GDP is bad. I prefer [thing correlated at 0.9 with GDP]." Manufacturing:  Life expectancy:  Happiness:  Many other metrics & discussion in the source: https://x.com/cremieuxrecueil/status/1832588128084730334 originally posted at https://stacker.news/items/677211