-

@ 84b0c46a:417782f5
2024-10-12 05:51:51
- 1:nan:
- **2**
- 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p)
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2|
|:--|:--|
|test| :nan: |
---
### :nan: **:nan:**
1. 1
2. 2
- tet
- tes
3. 3
1. 1
2. 2
> t
>> te
>>> test
- 19^th^
- H~2~O
<marquee>(☝ ՞ਊ ՞)☝ウェーイ<marquee><SCRIPT>alert("( 厂˙ω˙ )厂うぇ乁( ˙ω˙ )厂ーい乁( ˙ω˙ 乁)")</SCRIPT>
<img src="xx" onerror="alert('(☝ ՞ਊ ՞)☝ウェーイ')">
<marquee onstart="document.querySelector('body').innerHTML = `<main><p>全裸デブ</p></main>`">本サイトはfirefoxのみサポートしています</marquee>
<marquee><font size=1000>うにょ</font></marquee>
<marquee scrollamount=50>:wayo:</marquee>
<marquee behavior="alternate">This text will bounce</marquee>
-

@ 0e501ec7:de5ef3a4
2024-10-09 21:38:52
PS: lees zeker eens de blog van Tim: <https://timscyclethoughts.blogspot.com/2024/09/> :))
Vandaag was onze eerste dag in het Abtshof. (Ik weet het, gisteren is overgeslagen, oeps, en ik heb nog niet uitgevonden hoe ik hier meer foto's op kan zetten, nogmaals oeps.)
Het Absthof is een coöperatieve co-housing, met een grote moestuin en een houtatelier. Het is gelegen in Borlo, een klein dorpje in de buurt van Landen. Het thuis van de wooncoöperatie is een grote vierkantshoeve, die langzaamaan helemaal gerestaureerd geraakt op (redelijk) duurzame wijze. Een heel mooie plek, waar ik al een paar keer te gast ben geweest. Hier krijgen we kost en inwoon in ruil voor mee te helpen met vanalles. Wij zijn blij om hier te zijn en ervaring op te doen, en blij dat we wat kunnen bijdragen aan duurzame/alternatieve projecten zoals deze. Ook nog belangrijk: bij een coöperatie horen ook veel beslissingen, die gedragen moeten zijn. Hier werken ze met het kader van de sociocratie. Zeer interessant, ik zal er later nog over uitweiden.
Dus: we hadden op ons gemakje een lange ochtend gehad, met een lekker ontbijtje, een goede opruimbeurt, de plantjes in de serre water geven, en een random astrix en obelix strip. Het ging over de picten, ofzoiets, en iemand die de macht wou grijoen door met de romeinen samen te werken. Bon, daarvoor zijn we hier niet. Ik zou eigenlijk in bed moeten nu, de dagen zijn lang en mijn slaap dierbaar. Toch wil ik eerst nog wat schrijven. Toch toch tocht
door de bomen, wilgen, essen, rode beuk
Net toen we buitenstapten om te vertrekken deze ochtend, begon het te regenen! Test regenkleren: gefaald. Regenbroek is zo lek alsof hij eigenlijk niet bestaat. Maakt niet uit, ik ben niet van suiker. ; ) We zullen wel nog eens kijken voor van dat eng waterdichtmaakspul, of ik gebruik hem als windstopper, ook goed. Hier aangekomen werden we meteen ontvangen door Jakob met een warm middagmaal. Heerlijke stampot, op smaak gebracht met varkenspoot. Heftig idee, maar ik en Tim konden er wel mee overweg, en waren eigenlijk wel nieuwsgierig hoe dat smaakte zo een varkenspoot. Blijkt: nogal taai, maar wel nog een goede ervaring. Would recommend.
Daarna gingen we ons installeren, en we hadden geluk! We mochten slapen in een grote tent die nog op het veld stond. Daarin zijn zelfs bedjes, en hij lijkt (redelijk) waterdicht, al had ik toch niet direct al mijn spullen moeten uitspreiden. Ons kleine tentje zou het niet gehouden hebben om de hele week in de regen opgestaan te hebben vrees ik.
Daarna bereikte mij het nieuws. Van de uitzetting in het Wondelbos. Ik was er zwaar van aangedaan, boos en verdrietig, gespannen. Machteloos. Machteloos. Ik heb toen geprobeerd mijn gevoel neer te schrijven, en heb de grote uitdaging overwonnen om dat kwetsbare tekstje te delen. (Op Facebook.) Ik was wel trots op mijn kleine overwinning, maar dat viel nogal in het grote niet bij mijn eerdere gevoel bij de grote machtsvertoning van de politie, en de start van het illegaal lijkende kap. Ik kan niet geloven dat ze een kapvergunning binnen hebben, terwijl de rechtspraak rond hun bouwvergunning nog niet rond is. Maar ja, wat weet ik ervan.
Mijn gevoel kon ik dan een beetje van me afzetten door wat te helpen bij in de verbouwing van een nieuwe woning in de co-house: plaksel van de muur halen met een drilboor, puin naar buiten krijgen, spijkers uit de muur halen. Geleerd: oude spijkers moeten uit de muur voor je opnieuw plakt, anders krijg je roestvlekken. Ook geleerd: als je glas in een raam plaatst, mag je dat niet direct op het kader laten steunen, je moet er houtjes tussensteken (voor speling voor isolatie denk ik?). Morgen doen we daarmee verder én gaan we parket schaven. Ik heb echt wel zin om met het schaafmachien te leren werken!
Daarna was het eten met alle bewoners, aan een grote lange tafel in de gemeenschappelijke zaal. Was vree gezellig, al was mijn sociale energie naar het einde een beetje op. Er was een 'mededelingrondje', om iedereen op de hoogte te brengen van belangrijk nieuws. Later op de avond hadden de bewoners ook nog een 'deel-cirkel'. Dat doen ze blijkbaar een keer in de maand, om eens samen te zitten en over zaken te kunnen praten op een meer diepgaande manier, en zonder de stress van beslissingen die gemaakt moeten worden, zoals in vergaderingen. Klinkt wel goed, al zou ik zelf niet direct weten of ik veel intieme zaken kan delen voor een groep. Ik zou in de eerste plaats stress krijgen. Maar misschien werkt het wel!
Nu, naar bed, morgen weer een volle dag!
-

@ 0e501ec7:de5ef3a4
2024-10-09 21:37:38
Ik rouw. Ik rouw om het bos, in mij groeit een grote krop van verdriet. O Wondelbos, ik zag je graag, je ontving me zo hartelijk, en ik zag hoe je de thuis was van zoveel leven, zoveel leven.
Ik rouw om het vertrouwen in de rechtbank om rechtvaardig te zijn. Hoe vaak nog meneer de rechter, zal je als speelbal van machtige instituten gebruikt worden om kleine mensen, die mooie dingen proberen te doen, te intimideren? Hoe vaak nog zal jij, zonder kans voor de andere zijde om gehoord te worden, de politiemacht oproepen? Hoe vaak nog zal een vredezame actie met groot machtsvertoon beëindigd worden? Hoevaak nog zal illegale kap straffeloos blijven terwijl beschermers vervolgd en opgepakt worden? Hoevaak nog? Alle rede, alle gevoel zegt, dit bos moet behouden blijven. O bos, ik zal je missen. O Wondelbos, ik ben blij dat jij bij ons was.
Nu komt voor jou een tijd van beton. Maar ik ben zeker dat er daaronder een kiertje openblijft, een zaadje zal liggen te wachten. Ik ben zeker dat het Imperium van beton ooit gedaan zal zijn, en dan zal Jij terug kunnen bloeien, terug kunnen groeien, thuis geven aan al die soorten, al die wezens, al dat leven. Dan zal Jij terug thuis kunnen komen, net als Wij.
Liefs,
Je liefste Aardbewoner
-

@ 4ba8e86d:89d32de4
2024-10-09 13:13:10
Recentemente, perdi minha lista de RSS, Decidi criar este texto sobre RSS pode ajudar a escapar das armadilhas do algoritmo das redes sociais.
Além disso, para facilitar a vida daqueles que também desejam adotar o RSS como uma ferramenta de leitura, fiz um fork da lista de RSS do SethForPrivacy. Você pode acessar a lista no seguinte link: https://gist.github.com/Alexemidio/2699dd82077d483849b576a908b0c444
Aproveite a lista de RSS para personalizar seu fluxo de conteúdo e desfrutar de uma experiência de leitura mais controlada e direcionada.
Utilizar um leitor de RSS bem organizado é uma estratégia eficaz para se libertar da rolagem incessante nas redes sociais e recuperar o controle sobre o conteúdo que você consome. Isso possibilita direcionar sua atenção para o conteúdo genuinamente relevante.
Você já notou que os feeds das redes sociais frequentemente são inundados com notícias que provocam emoções negativas? Esse fenômeno, chamado de "doomscrolling", persiste, e as redes sociais parecem acentuar ainda mais a sua presença. A conhecida "bolha" das redes sociais nos mantém imersos, mostrando principalmente os posts com os quais interagimos. Isso tem provocado várias consequências prejudiciais, incluindo a disseminação de notícias falsas, desinformação e o agravamento de problemas como ansiedade e depressão entre os usuários.
Mas, e se lhe disséssemos que existe uma alternativa? Uma maneira de receber informações diretamente, sem filtros ou algoritmos? É disso que vamos falar hoje: o RSS.
O Que é o RSS?
RSS é a abreviação de "Really Simple Syndication", que pode ser traduzida como "Sincronização Realmente Simples". Trata-se de um arquivo XML gerado por inúmeros sites para exibir as postagens que o site publica. Dessa forma, os leitores de RSS permitem às pessoas acompanhar diversos blogs, sites de notícias e muito mais, tudo a partir de um único local.
Quem Criou o RSS?
Uma das pessoas envolvidas na criação do RSS foi Aaron Swartz, um hacker notório por seu papel na fundação do Creative Commons e por ser um dos cofundadores da rede social Reddit.
Se desejar se aprofundar na história de Aaron, recomendamos o documentário "O Menino da Internet: A História de Aaron Swartz" dublado em português completo. https://youtu.be/qm4NRSa9T2Q?si=GXyPXVOMJX20pIo_
Para quem gosta de RSS como eu, você não precisa usar NOSTR para acompanhar meu conteúdo. Basta me adicionar ao seu RSS.
Meu RSS Nostr: nostr:npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr
Utilizar um leitor de RSS bem organizado é uma maneira eficaz de se libertar da rolagem incessante e recuperar o controle sobre o conteúdo que você consome, direcionando sua atenção para o que realmente importa.
Para pessoas interessantes como o nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 você não precisa segui-lo no Nostr, basta adicionar ao seu RSS.
nostr:naddr1qqxnzdesx5ur2vekxucrqde5qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqa282ctyhs
Leitores de RSS Recomendados:
Feeder (Mobile): O Feeder é um aplicativo de leitor de RSS de código aberto que permite que você acompanhe e leia suas fontes de notícias favoritas em um só lugar. Com recursos avançados e uma interface intuitiva.
Liferea (Desktop): Liferea é a abreviação de Linux Feed Reader, um programa agregador para leitura de notícias online. Ele suporta os principais tipos de arquivo criados para esse fim: RSS/RDF e Atom. Também pode importar e exportar no formato OPML.
-

@ 0e501ec7:de5ef3a4
2024-10-08 20:06:29
Aan het einde van een dag vol buiten zijn en fietsen en organiseren (spullen inpakken, uitpakken, drogen, eten verzamelen (letterlijk hihi), eten klaarmaken, afwas...) ben ik echt niet meer in staat om veel te schrijven. Hier komt dus een korte samenvatting van de laatste twee dagen, filosofische bedenkselen zijn voor een andere keer.
Gisteren vertrokken we bij Yannick pas tegen de middag. Hoe kwam dat? Ik heb tot 9u (!) geslapen, wat wel nodig was want ik was echt volkomen uitgeput van de dag ervoor. (Veel prikkels joh, en fysieke uitdaging om 60 km te fietsen met een zwaarbeladen fiets.) (Ik weet het, klinkt niet als zoo veel maar mijn fysieke toestand was de laatste tijd niet zo heel formidabel, veel ziek en moe geweest.) Na het ontbijt heeft Tim met mijn bedenkelijke hulp mijn cassette (de tandwielen van achter) en mijn ketting vervangen. Dat ging best wel vlot, enkel het afstellen van de versnelling was niet zo gemakkelijk. We moesten een evenwicht vinden waarbij alle 9 schakels vlot gingen, aan de ene kant moesten we telkens aanspannen, terwijl we aan de andere kant telkens weer losten. Ik wou het al opgeven, toen we het net hadden gevonden.
Na al dit geploeter begonnen we aan onze fietstocht door het mooie (en drukke) Brussel. Ik heb er zeer van genoten om door de stad te rijden op een kleine steek, een beetje foto's te maken en tussen de mensen te laveren. In Molenbeek kochten we in een lokale kruidenier wat droogvoer, en nog een brood, en toen trokken we verder: richting Meerdaalwoud! Eerst passeerden we nog het zoniën. Prachtig! Ik kon me niet inhouden om (bijna) alle paddestoelen te beginnen fotograferen en aan Het Algoritme van ObsIdentify te vragen hoe ze heten. Gelukkig vond Tim het wel sympathiek en stelde ik zijn geduld niet te veel op de proef. Ondertussen discussieerden we een beetje over de betrouwbaarheid van de media, het gewoonlijke, je weet wel.
Gedurende de namiddag voelden we de bui al hangen, en ja hoor, tegen dat we aan de rand van het mooie Meerdaalwoud aankwamen, begon het zachtjes te druppen. In de gietende regen aten we rechtstaand ons stoofpotje op. Wat een vibe! Gelukkig was het niet koud, en konden we genieten van onze ultieme herfstsfeer. In de schemering, in de regen, klaar om in de tent te kruipen. Heerlijk!
PS: Het lukt dus niet om de foto's op te laden, jammer! Ze zijn wel mooi hoor, ik verzeker het je!
PPS: Ik vind het nu een beetje cringe om zo al onze gebeurtenissen te beschrijven, interesseert iemand dat eigenlijk? Interesseert het mij wel? Ik denk/voel erover na!
-

@ 0e501ec7:de5ef3a4
2024-10-08 19:26:36
Wat een vermoeiende dag! Eerst alle spanning van vertrekken, snel nog van telefoon wisselen, afscheid, veel afscheid, traantjes, nog mijn breispullen gaan halen die ik bij roos was vergeten, en dan pas eindelijk vertrekken! Fietsen fietsen fietsen! Op dit moment ben ik zeer moe, dat merk je misschien aan deze vluchtige schrijfstijl, mijn ogen vallen toe, maar dat was ik eigenlijk vanochtend al: gisterenavond waren er twee megaleuke feestjes! Eerst het verjaardagsfeestje van roos, zo vol met warme lieve mensen, en dan nog ook het verjaardagsfeestje van mijn mama! ook vol lieve mensen.
Toen fietsen fietsen fietsen!
Ik reed eerst alleen, langs de mooie lange schelde, tussen de wilgen, het riet, de velden... Ik was verwonderd iver de schoonheid van de paarden die langs het jaagpad stonden, ik was verwonderd over een kind dat vrolijk door een veld liep, wat een beeld zobder weerga, een soort van plattelandse veiligheid/vrijheid die we biet vaak meer tegenkomen. Toen werd ik opgehouden door allerlei werken, ik probeerde een omleiding te volgen (waarbij ik een sappige grote kastanjeoogst scoorde bij een prachtig paar bomen!) maar kwam weer midden in de jaagpadwerken uit en had toen een groot avontuur voor de boeg, hoeveel keer ik met die zwaarbeladen fiets de dijk op en af moest aj aj. Daarbij had ik ook nog een stevige tegenwind, waardoor ik pas na 14u aankwam bij mijn lieve oma en opa. Tim was daar al, en had al goed gesocialiseerd! We babbelden met ons vieren over vanalles, er kwamen allerlei oude verhalen bovendrijven bij oma en opa, ze waren precies zeer verheugd om tegen een nog niet bekende, jonge avonturier zoals Tim al hun verhalen uit de doeken te doen :)). Na ons buikje meer dan rond gegeten te hebben, trokken we weer op pad, deze keer met de knooppuntenroute die Tim had uitgestippeld. Bezienswaardigheden: de eiffeltoren van Asse, een paard om een heuvelkam, een steile bergaf die plots een grindweg werd, een boze tegenligger, veel politieke (rechtse) posters. En heuvels, en veel zondagsmensen. Tegen 6 uur kwamen we dan toe in Zellik, bij Yannick, een vriend van Tim. Die ontving ons hartelijk, met een mooie radiostem (hij studeert dat!). Na het eten speelde we nog een spelletje Boonanza, zeer leuk.
Ik merk wel dat ik echt heel veel zin heb om de blog te onderhouden, het is echt zo een projectje waarmee ik iets kan brengen naar de mensen waarvan ik hou, verhalen, ideeën, foto's. Ik hoop wel dat het een beetje overkomt, ik ben nogal onzeker over het rare vreemde platformpje dat niemand kent (maar ik ben gewoon onzeker en kwetsbaar tsjah) (wat het is kan je lezen in 'een eerste poging'). Als je het leest, laat me weten wat je ervan vindt! Als mensen het leuk vinden gaat mijn motivatie om er meer op te plaatsen misschien wel overleven :).
Tijdens het fietsen moest ik regelmatig denken aan The Cyborg Manifesto van Donna Haraway. Zelf heb ik dat boekje eigenlijk nog niet gelezen, maar het idee van de cyborg, het uitgebreide lichaam/zelf met technologie zet me wel aan het denken. Ik op de fiets met al mijn warme (regen)kleren in de fietszak ben precies een soort reuze huisjesslak aan topsnelheid. We razen door het landschap, ervaren het, de wind, de zon en regen, interageren met de menselijke en botanische bewoners ervan... En aan het einde van de dag zetten we onze tent op, ons verplaatsbare huisje. Wat als nu eens stopten met de wereld, ecosystemen en natuur, ons lichaam te beschouwen als machines, als radartjes, waarin problemen kunnen opgelost worden met quick files zoals een pilletje of de inrichting van reservaten (zoals we gewoon zijn bij de machines: een beetje smeren, een tandwiel vervangen, de nieuwe update installeren). Wat als we nu eens de machines als deel van ons lichaam zagen? Een lichaam om gehecht aan te zijn, om zorg voor te dragen? Om mee in wederkerige interactie met de wezens rond ons te gaan?
Bon, ik moet er nog eens over nadenken, en dat boek lezen, misschien heb ik daar ooit wel eens tijd voor. Na een lange fietsdag ben ik er allisinds te moe voor!
-

@ e6817453:b0ac3c39
2024-10-06 11:21:27
Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias.
<iframe width="560" height="315" src="https://www.youtube.com/embed/fehgwnSUcqQ?si=nPK7UOFr19BT5ifm" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
### 1. Privacy and Ownership: Foundations of Personal AI
At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations.
In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI.
### 2. Bias and Fairness: The Ethical Dilemma of LLMs
Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values.
This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks.
Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge.
### 3. Explainability: The Need for Transparency
One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions.
Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm.
This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks.
### Addressing the Ethical Landscape of Personal AI
As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development.
Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources.
There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom.
The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development.
### Conclusion
In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values.
If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
-

@ 0e501ec7:de5ef3a4
2024-10-05 10:41:58
De kamer is stil, maar weinig verlicht met een grijs en duister schemerlicht. Ze zitten rond een vreemdsoortige tafel, aan het verste uiteinde ervan staat een beeld. Het beeld is niet goed zichtbaar, maar de vormen ervan geven je een krop in je keel, je maag keert om. Dit zijn de machtigste mannen op aarde. Mannen ja, geen seksistische veralgemening hier, het zijn effectief alleen mannen in deze ruimte. Voor zover het te ontwaren is in het duistere licht, zijn ze gezond, fit, alsof ze dagelijks naar de yogales en de basicfit gaan. Ze zijn serieus, ze lachen niet, er is werk te doen. Ze kennen elkaar, ook al praten ze amper. Ze praten over het weer.
Je weet dat dit geen leuke plek is. Je weet dat een lach je hier duur te staan kan komen. Hoe ben je hier terecht gekomen?
De Mannen zitten in hun glanzende stoelen van Fenolformaldehyde en Perfluoroctaanzuur, en de stilte wordt nog zwaarder. Je hebt het koud, er steekt een ijzige wind op in de kamer, een ijskoude luchtstroom.
\------------------------------------------------------------------------
Duizenden jaren hebben de kou en het ijs het mythische Antarctica vormgegeven. Dit deel van onze geliefde Biosfeer, van Patchamama, heeft nooit veel mensen gekend, de Pinguïns, de Walrussen en de Zeehonden leefden hun levens los van ons, soms vreedzaam, soms lang, soms kort en gruwelijk. Maar ze kenden hun land en ze kenden elkaar, ze wisten dat na het licht de duisternis kwam, dat de duisternis kou met zich meebracht, die soms dodelijk was, maar altijd weer plaats maakte voor een minder frisse tijd waarin ze makkelijker konden gaan jagen op de Vissen, die ze ook zeer goed kenden. Toen de eerste Mensen kwamen waren ze woordeloos. Dit waren nooit mensen van veel gebabbel geweest, anders waren ze niet tot hier geraakt, maar de aanblik van de prachtige witte glooiingen van Antarctica, de aanblik van kou en schoonheid, ongrijpbaar en gevaarlijk, maar toch zo verleidelijk, ontnam ze van alle woorden. Vol ontzag, getransformeerd keerden ze terug naar huis, al gebeurde dat niet altijd. Antarctica werd een belangrijk personage in vele heldenverhalen, in gedichten, schilderijen. Het duurde niet lang of alle Mensen hadden ervan gehoord, en velen waren in de ban van deze voor hun desolate plek.
Vol leven was Antarctica, een onmisbaar orgaan in het lichaam van onze Aarde. Ze reguleerde de oceaanstromen, waaronder de golfstroom, en zorgde voor een constantere verdeling van warmte en koude. Dankzij Antarctica waren veel van de plekken die wij Thuis noemden zoals ze waren. Alle organen van onze Aarde zorgden er samen voor dat het regende wanneer het moest regenen, dat de zon scheen wanneer we er zo op wachtten, dat het ene jaar een beetje op het andere leek en we ons Thuis voelden. Thuis in de Biosfeer.
\------------------------------------------------------------------------
Vandaag is er iets te vieren onder deze Mannen. Ze zijn erin geslaagd om een groot offer te brengen. Van een omvang die gewone mensen, zoals jij en ik niet kunnen omvatten.
Hun God is bloedig, van een zwart soort bloed, met een hoge energetische waarde. Een te hoge energetische waarde zou je kunnen zeggen, zo hoog, dat dit bloed al snel verslavend werkt, in een trance brengt. Een trance van productiviteit, efficiëntie, destructie. Een trance van macht en geld, en 'vrije' markt. Maar de 'vrije markt' is al ter dood gebracht. Geofferd, in een vorig decennium. Het zwarte bloed vroeg meer machtsconcentratie om te blijven stromen. Deze Godheid vroeg meer toewijding, meer opoffering, meer zweet en fragiele lonen. Meer pesticiden, meer deregulatie, meer privatisering, meer staatsteun voor multinational, meer belastingverlaging. Ten dienste van de 'vrije' markt. Ten dienste van de monopolie. Dit is een God van de marktdominantie, een God van de monopolies.
Jij moet dan misschien aan dat gezelschapsspel denken, dat je in een vorig leven met je familie speelde. Soms was dat nog leuk, maar even vaak eindigde het in ruzie, dat weet je nog goed. Je weet evengoed dat dít spel niet meer leuk is, al lang niet meer. Het zwarte bloed ontregelde de organen van de Aarde, opdat er nog meer zwart bloed zou moge vloeien.
De Mannen vieren in stilte. Het ijs van Antarctica is gesmolten, het offer is compleet. Hun leger aan loonarbeiders (meer zweet en fragiele lonen, zo had de God geboden) zijn begonnen aan de eerste boortorens, boorplatformen en pijpleidingen. Ze weten dat hun God blij zal zijn met dit offer, hij heeft er al zolang om gevraagd. Het duurde bijna te lang, de vrees begon te groeien. Deze Mannen zijn dan machtig, angst is hun niet onbekend. Angst is hun beste vriend, al is het geen zorgzame vriendschap. Eerder een verstikkende, voortduwende, trekkende vriendschap. Ze zijn bang dat ze niet genoeg kunnen geven. Als ze niet hard genoeg werken en de offers krimpen zal hun rijk instorten. Zullen zij instorten. Onder de zware zwarte Wraak van hun Godheid.
De God heeft beloofd dat Hij hun leugens voor iedereen zal uitspreiden als ze zijn offers niet kunnen brengen. Hij heeft gezworen hun Imperium te laten brokkelen wanneer zij niet hard genoeg werken en de vernietiging Hem niet tevreden stelt. Ze zijn bang. De ijzige wind kietelt in hun nek. Maar ze vieren, ze hebben iets te vieren.
-

@ 0e501ec7:de5ef3a4
2024-10-04 16:53:22
We zijn nu 2 dagen voor het gepland vertrek, 4/10/2024. Ik ben zeer blij dat ik een fietsmaatje heb, genaamd Tim, die een datum heeft vastgelegd om te vertrekken. Als ik dat niet had gehad, dan was ik het vertrek waarschijnlijk nog een hele poos blijven uitstellen, of zelfs nooit vertrokken geraakt! Nu heb ik deze week wel met wat stress rondgelopen, je weet wel hoe stressgevoelig ik ben en je klaarmaken voor een grote reis is toch wel een beetje spannend.
Onze reis heeft geen strak plan. Als mensen ernaar vragen zeg ik altijd: we vertrekken richting het zuiden. Dan vragen ze nog: 'hoelang blijf je weg' en dan moet ik bekennen dat ik het niet weet. Veel mensen reageren een beetje onbegrijpend, maar een paar snappen het meteen en zijn laaiend enthousiast. En ik moet bekennen, dat ben ik zelf ook wel! Het is dus voor het grootste deel positieve spanning. Natuurlijk ook een beetje koudwatervrees, letterlijk dan, want ik heb zo een voorgevoel dat het veél gaat regenen!
Ons plannetje is om naast fietsen ook te stoppen op interessante plekken, zoals transitie-projecten of alternatieve gemeenschappen. Daar willen we graag meewerken en helpen waar we kunnen, maar ook mensen leren kennen en veel bijleren! Ik wil bijvoorbeeld heel graag houtbewerking leren, en Tim wilt graag over moestuinen en andere landbouwtechnieken leren (denk ik). En dat komt goed uit: veel projecten hebben een houtatelier en een grote moestuin. Al moeten we dat natuurlijk zien hé. Het eerste project zal het Absthof worden, in Borlo.
Zondag vertrekken we dus in die richting. We passeren mijn grootouders in Aalst, slapen dan waarschijnlijk bij een vriend van Tim in Zellik, en gaan dan via het Meerdaalwoud naar Landen/Borlo.
Ik ben zeer benieuwd hoe het fietsen mij gaat bevallen. Ik ben de laatste tijd nogal moe geweest, moe en ziek. Van één nachtje te weinig slaap voelde ik mij telkens weer verkouden. Ik denk echter dat het vooral het teveel aan stress en te weinig mentale rust is van het laatste jaar dat daar aan de oorzaak van ligt. Ik verwacht dus dat de fietsreis mij goed gaat doen, om mijn lichaam terug te herstellen en een routine op te bouwen met minder stress. Maaar: toch spannend! In het begin zou ik wel eens te moe kunnen zijn om ver te fietsen. Hopelijk lukt het mij om op tijd te zeggen Jow ik ben echt moe we zullen vandaag toch wat minder moeten fietsen. Dat zal wel echt belangrijk zijn, want als ik mij in het begin overdoe ga ik het misschien niet lang volhouden. Komt wel goed!
De voorbereidingen van deze week waren: de fiets kuisen, versnellingen afstellen, slag uit de wielen halen (merci Tim!!!), een stuurpenverlenger installeren zodat ik minder voorovergebogen zit, regenkleren opnieuw behandelen zodat ze waterdicht zijn, en een tripje naar de Decathlon, voor waterdichte overschoenen, een achterlicht en wat waterdichte zakken. Daarnaast ben ik ook nog vandaag naar de gemeente geweest om een volmacht te regelen, voor de verkiezingen volgende week!
-

@ 0e501ec7:de5ef3a4
2024-10-04 10:54:18
Have you watched the pigeons?
have you watched the crow?
Heb je het beemdooievaarsbekje ooit al eens goed bekeken?
Heb je al eens gevraagd aan de boomkikker hoe die naar het leven kijkt?
Wat hen denkt van jouw prachtig onderhouden voortuingazon?
Every species is a soul, a fire, a story, a story that is told and retold and retold
Every species is a song
A song of love, of life of neverending trial and struggle
Trial and error they say, evolution they say, mutation and selection
But your demystification is not working
The species never stop telling their unholy wispering stories
They never stop
This is a song for the lost souls
This is a song of grief
This story tells the song ofthe species that don't
that cannot anymore
The species we lost
I love you herfstvuurspin Ik hou van je
ik hou van je ik
Ik mis je
Ik voel in heel mijn lijf dat je ontbreekt
en ik ben zeker dat ik niet de enige ben
-

@ 0e501ec7:de5ef3a4
2024-10-03 09:54:14
Dit is een eerste poging om een post te creëeren die op de oracolo html-blog verschijnt. Ik snap helemaal niet zo goed hoe dit allemaal werkt, maar het lijkt wel spannend. De blog werkt op basis van een htmlbestandje, dat je zou kunnen hosten via github. ofzo. Waarom zo en niet op een andere manier? Ik vind nostr wel cool, omdat het helemaal gedecentraliseerd is en zonder groot bedrijf. Het wordt gebouwd door een heleboel geëngageerde developpers, en is ook open-source. Joepie! Misschien is het gewoon eens iets anders dat ik wil uitproberen, dat kan ook. Allesinds, ik voel er (nog) niet de enorme weerstand tegen die ik wel voel bij alle meta-dingetjes zoals facebook enz. Als dit werkt gebruik ik het misschien wel als blog tijdens onze fietsreis, wie weet. Ah en nog iets, in navolging van de 100rabbits programeur die op een zeilboot woont: kleine apps die doen wat ze moeten doen om de computer minder te belasten en energie te besparen, dat is helemaal cool en duurzaam en heeft off-grid potentieel. (Maar daar heb ik dan wel weer een bedenking bij: nostr is wel wat verbonden met bitcoin, en die heeft niet zo een energie-zuinig imago.)
-

@ e6817453:b0ac3c39
2024-09-30 14:52:23
In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance.
<iframe width="560" height="315" src="https://www.youtube.com/embed/BkNqu51et9U?si=lne0jWxdrZPxSgd1" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
## The Vector Search and Metadata Challenge
In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results.
Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data.
## LibSQL and vector search metadata
LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points.
```
create table if not exists conversation (
id varchar(36) primary key not null,
startDate real,
endDate real,
summary text,
vectorSummary F32_BLOB(512)
);
```
It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage.
As you can see, you can access vector-like data and start date in the same query.
```
select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance
from conversation
where
${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''}
${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''}
${distance ? `and distance <= ${distance}` : ''}
order by distance
limit ${top};
```
**vector\_distance\_cos** calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data.
This approach could be calculation intensive and fail on large amounts of data.
Libsql offers a way more effective vector search based on FlashDiskANN vector indexed.
```
vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i
```
**vector\_top\_k** is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies.
Now we get a classical problem of integration vector search results with metadata queries.
## Post-Filtering: A Common Approach
The most widely adopted method in these pipelines is **post-filtering**. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.

Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter.
```
const sqlQuery = `
select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance
from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i
inner join conversation c on i.id = c.rowid
where
${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''}
${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''}
${distance ? `and distance <= ${distance}` : ''}
order by distance
limit ${top};
```
However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results.
One working strategy is to make the top value in vector\_top\_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows.
## Pre-Filtering: A More Complex Approach
Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning.
While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.

In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data.
## Pre-filtering with distance-based filtering
So, we are getting back to an old concept. We do prefiltering instead of using a vector index.
```
WITH FilteredDates AS (
SELECT
c.id,
c.startDate,
c.endDate,
c.summary,
c.vectorSummary
FROM
YourTable c
WHERE
${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''}
${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''}
),
DistanceCalculation AS (
SELECT
fd.id,
fd.startDate,
fd.endDate,
fd.summary,
fd.vectorSummary,
vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance
FROM
FilteredDates fd
)
SELECT
dc.id,
dc.startDate,
dc.endDate,
dc.summary,
dc.distance
FROM
DistanceCalculation dc
WHERE
1=1
${distance ? `AND dc.distance <= ${distance}` : ''}
ORDER BY
dc.distance
LIMIT ${top};
```
It makes sense if the filter produces small data and distance calculation happens on the smaller data set.
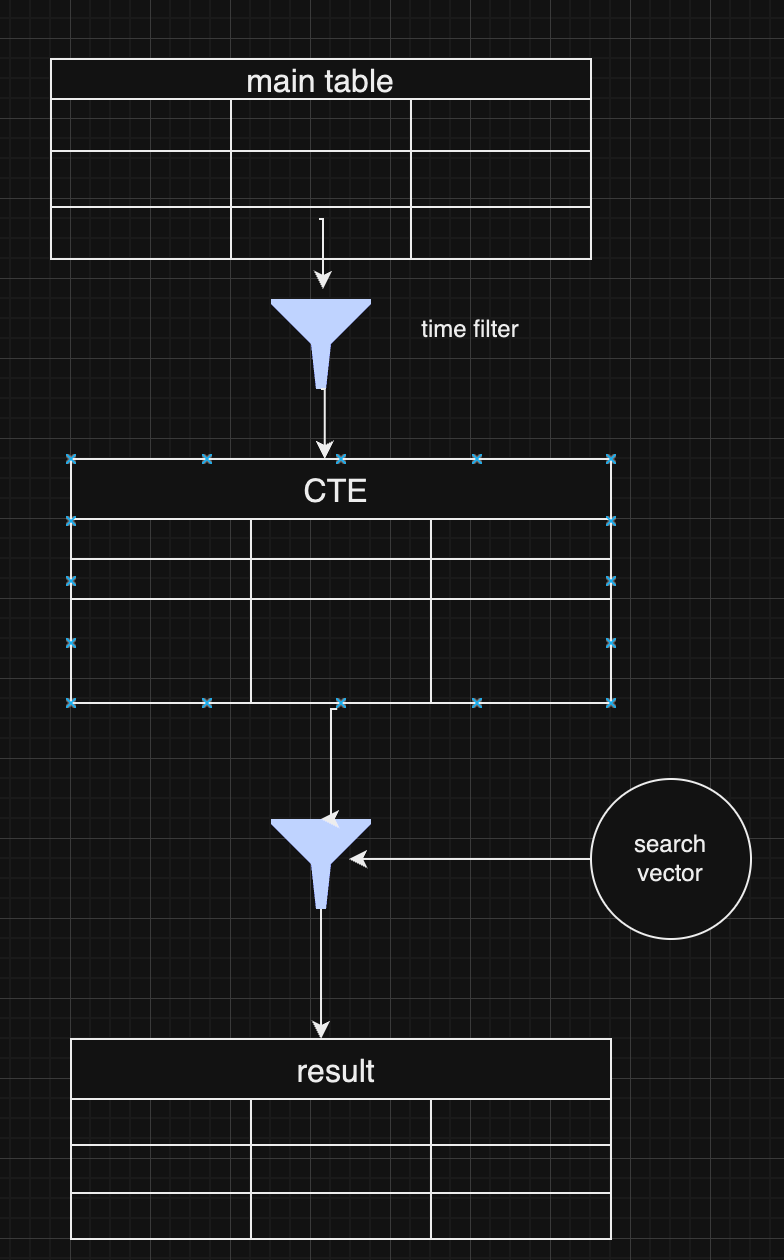
As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches.
## Choosing Between Pre and Post-Filtering
Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization.
In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further.
## **Conclusion**
Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further.
-

@ c4f5e7a7:8856cac7
2024-09-27 08:20:16
Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x).
# TL;DR
This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/).
The following concepts are explored:
1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust).
2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse.
3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
[Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
# Cognitive Dissonance
Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data).
In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
# Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k).
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
# Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g).
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons).
The remainder of this article explores how we can:
1. Verify ownership of a physical place in the real world;
2. Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation\!) states that:
> "The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
# Places and Web-of-Trust
[@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace).
2. Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
# Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with:
1. Your social graph;
2. The type or subject of the content being attested and by whom;
3. Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
[NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive.
**‘This is true’** resonates more strongly than **‘I like this.’**.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
# Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential):
> "A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
[@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that:
> "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
# Check-ins
Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\!
Check-ins could also be used as a signal for bonafide Place ownership over time.
# Summary: Trust Your Bros
So, to recap, we have:
**Places**: Digital representations of physical locations on Nostr.
**Check-ins**: Users signalling their presence at a location.
**Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left\! We have:
**Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
**Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
**Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
# Thanks
With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\!
-

@ e83b66a8:b0526c2b
2024-09-26 19:29:43
If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining.
Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully.
Solo mining pools exist, such as: https://solo.ckpool.org/
It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool.
You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power.
There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely.
A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine.
So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning.
So here’s my recommendation.
Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin.
Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join.
If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools.
Bear in mind that many of the other smaller pools are still controlled by Bitmain.
If you're still interested in lottery mining, here are your chances of winning a block:
Represented as Hash rates of different miners:
Nerdminer: 20 KH/s = 20,000 H/s
Bitaxe: 750 GH/s = 750,000,000,000 H/s
Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s
Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s
Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s
Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000
If you're running a Bitaxe, your percentage chance of winning a block is:
0.000000119426751592357%
Over a year, your chances increase to:
0.00627707006369428%
Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one):
0.000005%
Over a year, your chances increase to:
0.00026%
Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions:
https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/
https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx
https://www.youtube.com/watch?v=Wo91DWvZRs8
https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
-

@ 01d0bbf9:91130d4c
2024-09-26 17:58:10
## Chef's notes
Amazingly tangy, firey hot, but still mellow and bright.
I use this on everything– Use it to dress salads, dip (honey mustard) for fried chicken, elevate your taco nights, heck a spoonful first thing in the morning will wake you up better than coffee!
Don't forget to use up those delicious chilis and garlic, they are so good!
## Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 1-2 weeks
- 🍽️ Servings: (12x) 8oz jars
## Ingredients
- 16oz fresh chili peppers
- 8oz red onion
- 8oz garlic
- 96oz honey
- Fresh thyme
## Directions
1. Thinly slice peppers, garlic, shallots and fresh thyme
2. Add chopped ingredients to the honey
3. Leave to ferment (loosely covered) for 1-2 weeks
4. Drizzle that amazing pungent firey gold liquid over EVERYTHING. (Don't forget to use up those amazing chilis and garlic too.)
-

@ e83b66a8:b0526c2b
2024-09-21 16:29:23
Here are some of the more interesting projects that I like:
Messaging:
https://www.0xchat.com/#/ - Private messaging - think WhatsApp
Xitter Like Clients:
https://damus.io/ - iPhone client
https://nostrapps.com/amethyst - Android client
https://primal.net/downloads - Android, iPhone & Desktop
https://shipyard.pub/posts - Schedule future posts
Interesting sites:
https://zap.stream/ - Video streaming
https://fountain.fm/ - Podcasting
https://wavlake.com/ - Music streaming
https://shopstr.store/ - Online shop
https://zap.cooking/recent - Cooking recipes
https://ostrich.work/ - NOSTR jobs board
NOSTR tools
https://nostr.band/ - Powerful search tool
https://nostr.wine/ - Powerful, but centralised paid relay
https://npub.pro/ - Website creation tool
https://nostr.build/ - Media and file storage
https://relay.tools/ - Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user - Creator tools
List of NOSTR apps:
https://nostrapps.com/
-

@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53
I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous.
In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism.
On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important.
That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played.
Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end.
The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism:
I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.
In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore.
The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true.
The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good.
In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.”
I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
-

@ ee11a5df:b76c4e49
2024-09-11 08:16:37
# Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays.
Or at the very least by DVMs. I concur. In this way, once you configure what you want to see,
it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
## Strategies in Short
1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering.
3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity
6. **PROOF OF WORK**: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
## filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai
// This is a sample spam filtering script for the gossip nostr
// client. The language is called Rhai, details are at:
// https://rhai.rs/book/
//
// For gossip to find your spam filtering script, put it in
// your gossip profile directory. See
// https://docs.rs/dirs/latest/dirs/fn.data_dir.html
// to find the base directory. A subdirectory "gossip" is your
// gossip data directory which for most people is their profile
// directory too. (Note: if you use a GOSSIP_PROFILE, you'll
// need to put it one directory deeper into that profile
// directory).
//
// This filter is used to filter out and refuse to process
// incoming events as they flow in from relays, and also to
// filter which events get/ displayed in certain circumstances.
// It is only run on feed-displayable event kinds, and only by
// authors you are not following. In case of error, nothing is
// filtered.
//
// You must define a function called 'filter' which returns one
// of these constant values:
// DENY (the event is filtered out)
// ALLOW (the event is allowed through)
// MUTE (the event is filtered out, and the author is
// automatically muted)
//
// Your script will be provided the following global variables:
// 'caller' - a string that is one of "Process",
// "Thread", "Inbox" or "Global" indicating
// which part of the code is running your
// script
// 'content' - the event content as a string
// 'id' - the event ID, as a hex string
// 'kind' - the event kind as an integer
// 'muted' - if the author is in your mute list
// 'name' - if we have it, the name of the author
// (or your petname), else an empty string
// 'nip05valid' - whether nip05 is valid for the author,
// as a boolean
// 'pow' - the Proof of Work on the event
// 'pubkey' - the event author public key, as a hex
// string
// 'seconds_known' - the number of seconds that the author
// of the event has been known to gossip
// 'spamsafe' - true only if the event came in from a
// relay marked as SpamSafe during Process
// (even if the global setting for SpamSafe
// is off)
fn filter() {
// Show spam on global
// (global events are ephemeral; these won't grow the
// database)
if caller=="Global" {
return ALLOW;
}
// Block ReplyGuy
if name.contains("ReplyGuy") || name.contains("ReplyGal") {
return DENY;
}
// Block known DM spam
// (giftwraps are unwrapped before the content is passed to
// this script)
if content.to_lower().contains(
"Mr. Gift and Mrs. Wrap under the tree, KISSING!"
) {
return DENY;
}
// Reject events from new pubkeys, unless they have a high
// PoW or we somehow already have a nip05valid for them
//
// If this turns out to be a legit person, we will start
// hearing their events 2 seconds from now, so we will
// only miss their very first event.
if seconds_known <= 2 && pow < 25 && !nip05valid {
return DENY;
}
// Mute offensive people
if content.to_lower().contains(" kike") ||
content.to_lower().contains("kike ") ||
content.to_lower().contains(" nigger") ||
content.to_lower().contains("nigger ")
{
return MUTE;
}
// Reject events from muted people
//
// Gossip already does this internally, and since we are
// not Process, this is rather redundant. But this works
// as an example.
if muted {
return DENY;
}
// Accept if the PoW is large enough
if pow >= 25 {
return ALLOW;
}
// Accept if their NIP-05 is valid
if nip05valid {
return ALLOW;
}
// Accept if the event came through a spamsafe relay
if spamsafe {
return ALLOW;
}
// Reject the rest
DENY
}
```
-

@ bf95e1a4:ebdcc848
2024-09-11 06:31:05
This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good!
If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/>
# Intro
**Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us.
**Paolo:** Thank you for having us.
**Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we?
**Luke:** Sounds like that's the plan. So thank you again, both for joining us.
# Introducing Paolo and Mathias
**Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you
**Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate.
**Luke:** And, Mathias, over to you.
**Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use.
P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that.
And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here.
**Luke:** Oh, fantastic.
# Introduction to Holepunch
**Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch.
What is Holepunch and what are you doing?
**Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us.
but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy.
It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God.
that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks.
Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use,
Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it?
and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world.
And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company.
And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand.
anything, super exciting and, encourage everybody to try to check it out.
**Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product?
What is the easiest way that you would explain what it is?
# The Vision Behind Keet
**Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer
People don't care about technology. We loved it, but don't have that surface off too much to the user.
Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it.
It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard.
And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that.
# Keet vs Nostr
**Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here.
**Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform.
And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly.
You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users.
So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays.
and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology.
It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace.
Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly.
**Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that.
# Pear Runtime
**Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform,
**Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So
We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it.
And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications.
We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that.
So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve.
But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything.
So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view.
and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard.
so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example.
It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app.
So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place.
But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that.
And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone.
And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached.
Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like
**Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective.
And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that?
**Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective.
And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things.
I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point.
# Decentralization vs. Centralization
**Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor?
**Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias.
I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right?
Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions.
and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers.
That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there.
And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far.
Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features.
And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users.
And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is.
It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that.
And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key
**Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites.
But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept.
over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud.
And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers.
the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on.
is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole.
And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before.
Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize.
And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system.
And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country.
So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to.
**Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives.
So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right?
**Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all.
So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting.
yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why
# Challenges and Future of Decentralization
**Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company.
And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing.
So is there a limitation to how far this can go?
**Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world.
Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling.
So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house.
I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created.
imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you.
Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure.
So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another.
And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example.
**Knut:** Yeah.
**Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money.
And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook?
it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way.
And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it.
We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback.
# Bitcoin and Holepunch: Drawing Parallels
**Mathias:** I think, that's the main thing to think about in that. Discussion.
**Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line.
And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin?
**Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange.
For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government.
and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right?
Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them.
and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them.
**Luke:** Yeah, fantastic.
# The Future of Decentralized Communication
**Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet.
So is, that a goal? Is that on the roadmap?
**Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world.
But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind.
**Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly.
And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app.
And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly,
# Interoperability and User Experience
**Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong,
**Mathias:** Very, true.
**Luke:** you backups with the same 1224 words.
Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be
**Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it.
**Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life.
You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build.
Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible.
**Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems?
What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that?
**Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us.
The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity.
No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful.
**Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever.
but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera.
But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem.
And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it.
**Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options.
Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right?
you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion.
so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai.
So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that.
And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself.
And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center.
**Knut:** Yeah.
# The Role of Tether in the Crypto Ecosystem
**Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo?
And, what, made this thing happen? Can you give us the story here about Tether?
# Tether's Origin and Evolution
**Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014.
it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat.
That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000.
But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right?
International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin.
For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic.
# USDT's Impact on Emerging Markets
**Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries.
Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap.
So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time.
we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world.
At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right?
you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others.
And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT.
If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right?
So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U.
S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant.
# Bitcoin as a Savings Account
**Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend.
The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies.
we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining.
We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other.
I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math.
That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin.
**Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother.
**Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether.
So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right?
So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education.
**Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic.
I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke.
**Luke:** Always say the title, Knut. Always say the title.
**Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course.
**Paolo:** Oh, with pleasure, with great pleasure, with a nice, education.
**Luke:** Absolutely. Yep.
# Plan B Forum and Future Events
**Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year.
so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event.
**Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year.
I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world.
And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing.
**Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time.
And I think we're even playing this year, aren't we, Luke?
**Paolo:** You're
**Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos.
Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague?
**Knut:** paranoid and,
**Paolo:** Can I commission a
**Knut:** What song would you like to hear?
**Paolo:** I have two that I would suggest. One is Nothing Else Matters.
**Knut:** Alright.
**Paolo:** So I think that, is very inspiring, right?
**Knut:** Bitcoin, for sure.
Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke?
**Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference,
**Knut:** Yeah.
**Mathias:** not so much music, but yeah, that's peer to
**Knut:** Nothing else matters.
**Luke:** looking forward to that.
**Knut:** Sorry, brain fart. Sad but true is about the dollar still being around,
**Paolo:** Yeah, you can say that.
**Luke:** Okay.
# Final Thoughts and Closing Remarks
**Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that?
**Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms.
There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out.
**Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting.
**Mathias:** Just those things, that's all.
**Paolo:** Yeah, we can piss off more than this. Thanks.
**Mathias:** a
**Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners?
**Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them.
**Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good.
**Luke:** So that's, all at Keet. Is that correct? For Keet?
**Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer.
**Knut:** Alright,
**Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah.
**Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano.
**Paolo:** Likewise, I
**Knut:** But yeah, worth saying again.
**Paolo:** Thank you for having an invitation.
**Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
-

@ 8cb60e21:5f2deaea
2024-09-10 21:14:08
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05
It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint.
I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point.
I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog.
In line with that thinking, I made two parlays this week:
1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense.
2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout.
Are there any odds you're excited about (doesn't have to be football)?
originally posted at https://stacker.news/items/679894
-

@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。
怎么自建ntfy,后面再写。
---
2024年08月13日更新:
> 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
---
### 准备工具
- Ntfy服务
- Google Script
- Google Sheets
### 操作步骤
1. 在Ntfy后台账号,设置访问令牌。
[](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌")
2. 添加订阅主题。
[](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题")
2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图:
[](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id")
3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript
function checkEmail() {
var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID
var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据
cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread');
Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) {
var threadId = thread.getId();
if (!sentEmails.includes(threadId)) {
thread.getMessages().forEach(sendNtfyNotification);
recordSentEmail(sheet, threadId);
}
});
}
function sendNtfyNotification(email) {
if (!email) {
Logger.log("Email object is undefined or null.");
return;
}
var message = `发件人: ${email.getFrom() || "未知发件人"}
主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail";
var options = {
method: "post",
payload: message,
headers: {
Authorization: "Bearer Ntfy的令牌"
},
muteHttpExceptions: true
};
try {
var response = UrlFetchApp.fetch(url, options);
Logger.log("Response: " + response.getContentText());
} catch (e) {
Logger.log("Error: " + e.message);
}
}
function getSentEmails(sheet) {
var data = sheet.getDataRange().getValues();
return data.map(row => row[0]); // Assuming email IDs are stored in the first column
}
function recordSentEmail(sheet, threadId) {
sheet.appendRow([threadId, new Date()]);
}
function cleanOldData(sheet, minutes) {
var now = new Date();
var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues();
var rowsToDelete = [];
data.forEach(function(row, index) {
var date = new Date(row[1]); // 假设日期保存在第二列
if (date < thresholdDate) {
rowsToDelete.push(index + 1); // 存储要删除的行号
}
});
// 逆序删除(从最后一行开始删除,以避免行号改变)
rowsToDelete.reverse().forEach(function(row) {
sheet.deleteRow(row);
});
}
```
4.Goole Script需要添加gmail服务,如图:
[](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务")
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:
[](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器")
[](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细")
### 结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
效果预览:
[](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览")
-

@ 655a7cf1:d0510794
2024-09-10 13:16:15
Currently have kyc BTC, huge fan of lightning Network. Because I am a constant user of lightning. Plan on doing my business with lightning as well , peer-to-peer I'm not sure if I'm so worried about kyc I might be misguided in this situation.
originally posted at https://stacker.news/items/679520
-

@ 6ad3e2a3:c90b7740
2024-09-10 09:26:37
While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions:
**1. Separate passengers from their bags as early as possible.**
The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences:
a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes.
b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day.
c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five.
d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier.
e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable.
The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children.
To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc.
There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.)
Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane.
**2. Eliminate Security Lines**
Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement.
a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use.
Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious.
b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side.
Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side.
**3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.**
Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal.
**4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.**
There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done.
Here are some other suggestions:
1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up.
2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges.
3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease.
4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them.
I can anticipate some objections to these ideas, and I’ll address each one in turn.
**1. This would cost too much money.**
My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.)
**2. It’s too much of a security risk.**
Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end.
Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle.
**3. I like free carry-ons because it saves me from waiting at the baggage claim.**
Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse.
The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist.
*\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.*
*\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.*
-

@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48
I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote:
*What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.*
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-

@ 129f5189:3a441803
2024-09-09 23:28:41
Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration.
Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed.
https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg
This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad.
https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg
Reorienting U.S. Foreign Policy: Proposals for a Conservative Future
In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage.
Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed.
https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg
History and Structure of the State Department
Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner).
The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries).
https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg
Political Leadership and Bureaucratic Support
To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner).
Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies.
https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg
Global Threats to the U.S.
The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea.
🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner).
Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner).
https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg
🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government.
"The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner).
https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg
🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people.
"The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner).
https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg
🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests.
"The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?"
https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg
One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner).
This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines.
Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner).
It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement.
https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg
A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner).
From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives.
https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg
Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO.
https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg
🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power.
"The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner).
https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg
Detailed Policy Proposals
Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized.
"The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner).
https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg
Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities.
She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner).
https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg
Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem.
"Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis.
https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg
Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada.
"The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region.
https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg
Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India.
"Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner).
https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg
Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities.
"Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying.
https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg
Relations with Europe and Asia
Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom.
https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg
Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner).
https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg
International Organizations
Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner).
She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner).
https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg
Conclusion
Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president.
With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom.
https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
-

@ e83b66a8:b0526c2b
2024-09-09 20:30:30
We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect.
Therefore, I strongly advise you to run multiple clients.
On iPhone, I run:
Damus: https://nostrapps.com/damus
Primal: https://primal.net/downloads
Nostur: https://nostrapps.com/nostur
On Android I run:
Primal: https://primal.net/downloads
Amethyst: https://nostrapps.com/amethyst
On desktop I run:
Primal: https://primal.net/downloads
noStrudel: https://nostrapps.com/nostrudel
Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay.
If you haven’t taken the plunge to run a node, now might be a good time to think about it.
There are many, many options for clients, the “Social” section of
https://nostrapps.com/
lists 23 currently.
Play with them, see what they do, if you’re a developer, you could even consider building or forking your own.
Have fun and realise we are building freedom tech, not just running it.
-

@ e83b66a8:b0526c2b
2024-09-09 20:27:41
First,
Key management.
When you “created” your NOSTR account, what you actually created was a cryptographic key pair.
This consists of a private key, which starts “nsec” and a public key which starts with “npub”.
As the names suggest, your “nsec” key is private and you should never reveal it to anyone.
Your “npub” key is your public key, feel free to share that everywhere.
Your “npub” key is used by others to verify your identity, through the signature added to your messages.
It is also used by others to encrypt private messages to you.
We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary.
For the moment, consider using software key management options, some of which are listed under “signers” here:
https://nostrapps.com/
N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted:
Secondly,
Lightning wallets.
It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile
N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key.
You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet.
Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason….
It also allows you to send small micropayments to posts or people you like.
Thirdly,
Paid Services
As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability.
I, for example choose to pay for the following services:
https://nostr.wine/ - 120,000 Sats for 2 years relay
https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month
https://nostr.build/ - Media storage - 69,000 Sats for 1 year
Total: 22,750 Sats per month
Approx $15 per month
This is not strictly necessary, but I decided to support the various developers behind these projects.
Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward.
-

@ c11cf5f8:4928464d
2024-09-09 18:45:16

originally posted at https://stacker.news/items/678432
-

@ e968e50b:db2a803a
2024-09-09 18:21:54

Open the frozen pizza bay doors, Hal.
originally posted at https://stacker.news/items/678403
-

@ 6bae33c8:607272e8
2024-09-09 16:07:43
I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote:
*What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.*
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-

@ d3052ca3:d84a170e
2024-09-09 15:43:38
I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :)
I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet.
What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds?
What is your experience? I'd love to hear about it!
-

@ 3875a16c:988456c9
2024-09-09 14:50:15
**ORIGINAL PANEL TITLE:**
MAKING BITCOIN MORE PRIVATE WITH CISA
**SPEAKERS:**
NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP
**CONFERENCE:**
BITCOIN NASHVILLE 2024
**ORIGINALLY PUBLISHED ON:**
BITLYRICS.CO
## Introduction
This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/).
Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development.
---
### NiftyNei (Moderator):
Hey everyone, my name is Nifty, and I’m going to be moderating this panel today.
We’re here to talk about CISA (cross-input signature aggregation).
Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage.
We’re excited to be talking to you guys about this.
I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA.
Craig, do you want to start?
---
### Craig Raw (Sparrow Wallet):
I built Sparrow Wallet. It’s a security and privacy-focused wallet.
The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen.
When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically.
So, that was the first time I really started to look at it from the privacy angle.
---
### Fabian Jahr (Brink):
I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it.
Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core.
Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months.
I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller.
I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it.
---
### Jameson Lopp (Casa):
I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups.
I think the first time I heard about CISA was in an Andrew Poelstra talk.
I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted.
This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics.
---
### NiftyNei (Moderator):
That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for.
Does anyone have a good explanation of how it works?
---
### Fabian Jahr (Brink):
I can start off.
So, it’s really already all in the name: cross-input signature aggregation.
If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated.
What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction.
So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before.
Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea.
---
### NiftyNei (Moderator):
I have a quick question about that.
So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right?
So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature.
Is that a good summary of what you’re explaining?
---
### Fabian Jahr (Brink):
Yeah, I would say so.
---
### Craig Raw (Sparrow Wallet):
So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it.
That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one.
Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it.
Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones.
Unfortunately, the downside of that is that you have to do the interaction while you sign.
The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing.
As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient.
---
### NiftyNei (Moderator):
Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right?
You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level?
---
### Jameson Lopp (Casa):
Well, there’s also full-block aggregation, right?
This is going really far down the rabbit hole, and I think it’s not even something that’s on the table.
There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations.
My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized.
If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again.
---
### NiftyNei (Moderator):
So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation.
We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there.
One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right?
Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated.
---
### Jameson Lopp (Casa):
Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically.
If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount.
It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO.
You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet.
It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot.
It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before.
So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so.
---
### Fabian Jahr (Brink):
And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy.
The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property.
Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.”
Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it.
Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature.
---
### Jameson Lopp (Casa):
Yeah, we have to think about the incentives, right?
I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are.
But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late.
We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so.
It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software.
Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money?
---
### Craig Raw (Sparrow):
So you might be wondering at this stage what the savings actually look like.
It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block.
You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage.
Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%.
But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space.
So that’s how I would encourage you to think about it from the start.
For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride.
We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about.
---
### NiftyNei (Moderator):
I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy.
I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal?
What was it about the Taproot process where this proposal didn’t make it over the line?
---
### Fabian Jahr (Brink):
I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed.
From what I can see, I don’t think there was any direct opposition.
The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller.
I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding.
I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much.
---
### Craig Raw (Sparrow):
Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough.
There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.”
That’s an interesting point of view.
---
### Jameson Lopp (Casa):
It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet.
---
### Craig Raw (Sparrow):
Yeah, so we’re in a very different space now.
Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine.
I’m talking about the well-understood half-signature aggregation form of it.
From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that.
So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing.
If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down.
So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line.
---
### Jameson Lopp (Casa):
I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin.
With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process.
As far as I’m aware, there’s been limited adoption of Schnorr so far.
I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility.
I care about this a lot, operating a multi-signature self-custody wallet.
We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature.
That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out.
So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block.
---
### NiftyNei (Moderator):
So, we only have a few minutes left.
Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in.
---
### Fabian Jahr (Brink):
There are still quite a few things to hammer out in terms of all the details, like defining a spec.
For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open.
However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity.
We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now.
---
### Jameson Lopp (Casa):
Yeah, call your local developer and demand signature aggregation today.
---
### Craig Raw (Sparrow):
Fabian has developed a great site where you can learn more.
If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it.
It’s very easy to read, not overly technical, and I think it gives a good grounding in these things.
Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not.
As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now.
So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not.
---
### Jameson Lopp (Casa):
I don’t know, do you want to save money? It should be an easy question.
---
### Fabian Jahr (Brink):
And have better privacy.
---
### NiftyNei (Moderator):
Great! Thanks y’all.
---
**Follow the speakers: **
[NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr)
**Watch the original content: **
[Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107)
**Also read: Build It Right: **
[Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/)
**Disclaimer: **
Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/).
-

@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24
## Chef's notes
Makes an excellent Chicken sandwich.
## Details
- ⏲️ Prep time: 6 Ish hours
- 🍳 Cook time: 40 min
- 🍽️ Servings: 1 loaf
## Ingredients
- 3 ½ - 4 cups bread flour, or more as needed
- 1 ⅓ cups warm milk (110°F – 115°F)
- 5 tablespoons honey
- 4 tablespoons salted butter, melted and slightly cooled
- 1 tablespoon instant “rapid rise” yeast
- 1 ½ teaspoons salt
- Oil or butter for greasing the bowl
- 1 tablespoon melted salted butter, for brushing the crust at the end
## Directions
1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl.
2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes.
3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours.
4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan.
5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F.
6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped.
7. Brush the top of the warm bread with melted butter.
8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
-

@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05
Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one?
Thanks
originally posted at https://stacker.news/items/677439
-

@ eed76ece:afa98124
2024-09-08 21:13:37
Seems like if you want to sell an item on SN using @AGORA makes logical sense.
Perhaps if your a manufacturer, importer, exporter, stocking distributor, wholesaler etc. you should also consider using @Import_Export or both @AGORA and see if they help each other. Being totally upfront
Import_Export is probably a better use case especially if you are running over 75% B2B.
We are note promoting the use of B2C on SN. We're 100% focused on interactions between businesses only. Our primary markets are in Asia and Southeast Asia. Europe and the UK are dying a slow death, and the last straw was the Telegram event.
So I am endorsing you to please at least on SN refer to @AGORA for basic B2C (retail).
Thank you,
https://www.globalmerchant.io
originally posted at https://stacker.news/items/677390
-

@ e8b86bc1:3503c58f
2024-09-08 19:37:36
Opinion about Freewallet Multi Crypto Wallet (iphone)
<!--HEADER END-->
Freewallet is now charging inactivity fees, a sneaky method to take money from users who aren’t regularly using the app. Avoid this scam wallet!
<!--FOOTER START-->
#WalletScrutiny #nostrOpinion
[Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
-

@ c11cf5f8:4928464d
2024-09-08 19:10:39
Considering the "whatever" item in question is a random item, a unique piece --not something you produce or need to market-- which platform, website or which strategy you'll put in place to get the value of your item in sats, immediately, anonymously, via the Lightning Network?
originally posted at https://stacker.news/items/677270
-

@ 6f170f27:711e26dd
2024-09-08 17:45:46
> Far too many people:
"GDP is bad. I prefer [thing correlated at 0.9 with GDP]."
Manufacturing:
Life expectancy:
Happiness:
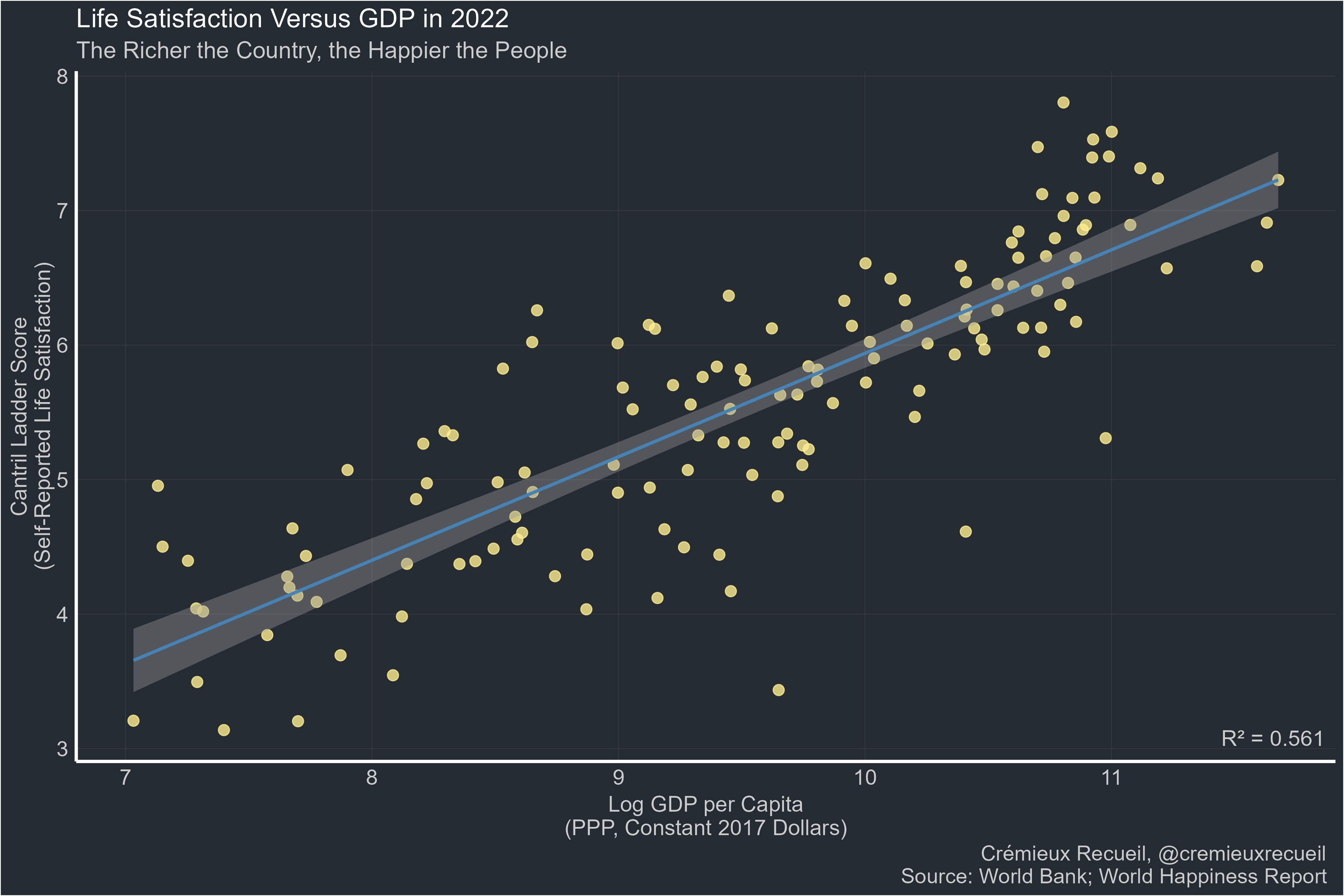
Many other metrics & discussion in the source:
https://x.com/cremieuxrecueil/status/1832588128084730334
originally posted at https://stacker.news/items/677211
-

@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43
> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。
导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。
---
### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。
项目是通过cloudflare pages搭建的。
- 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed
项目的教程很详细,具体去看项目教程。
### telegram设置:
- 需要有telegram账号
- 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。
- 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。
- 一定要添加创建的机器人到频道作为管理员才能使用。
### cloudflare的设置
- 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。
- 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图:
[](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv")
- BASIC_USER 后台登陆名
- BASIC_PASS 后台密码
- AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。
### 其他
- 成人内容屏蔽
- pico 使用api接口
去项目地址看
### 最后
我搭建的地址:
https://imgbed.lepidus.me
-

@ d52f4f20:98efcdfb
2024-09-08 12:05:31
_original post 28/12/2010 .net_
Para você que se sente meio preso ao instalar o Ubuntu, pois ele já vem pronto para um usuário final, mas isso não me agrada parece que perco o espirito de liberdade.
Mas o ponto forte Ubuntu são suas atualizações, então eu fui em busca de como fazer uma instalação customizada somente com os pacotes do Ubuntu.
Depois de muita pesquisa e anos de experiência com linux desenvolvi o que chamo de instalação mínima
**Alguns conceitos da minha instalação**
– Não tem gerenciador de login gráfico.
– Precisar habilitar o root, na unha e você usa isso.
– Não tem menus, os aplicativos são chamados via tecla de atalho ou docks.
– Não tem menu para desligar.
– Não é um desktop, usa apenas um gerenciador de Janelas.
– Aqui tudo é minimalista, não é bonito também não quer dizer que é feio, é apenas simples faz o necessário.
– Não importa a versão do ubuntu, atual ou não essa técnica quase nunca mudará.
**Seria bom/Pré-Requisitos**
– Se você tem conceitos de particionamento.
– Se você já instalou um Debian.
– Se você sabe usar o vim.
– Conexão com internet via placa de rede 10/100 (sim tem que ser assim).
**Introdução**
A idéia é usar a instalação mínima do Ubuntu (https://help.ubuntu.com/community/Installation/MinimalCD), onde é bem parecida com a NetInstall do Debian. Iremos baixar a imagem(12 ~ 13MB) do link acima e queimar em um cd rom e dar boot.
Vamos usar o assistente de instalação, e não selecionaremos nenhum pacote na instalação, tudo sera instalado via linha de comando usando o apt. Pra quem já instalou usando o anaconda da RedHat não terá problemas, qualquer ser capaz de ler consegue instalar.
Esta é a primeira tela exibida após o boot, selecione o menu
Va seguindo o instalador conforme as telas, não quer que eu fique explicando tudo né?
Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.
Aqui você estara selecionando daonde pacotes serão baixados.
Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.
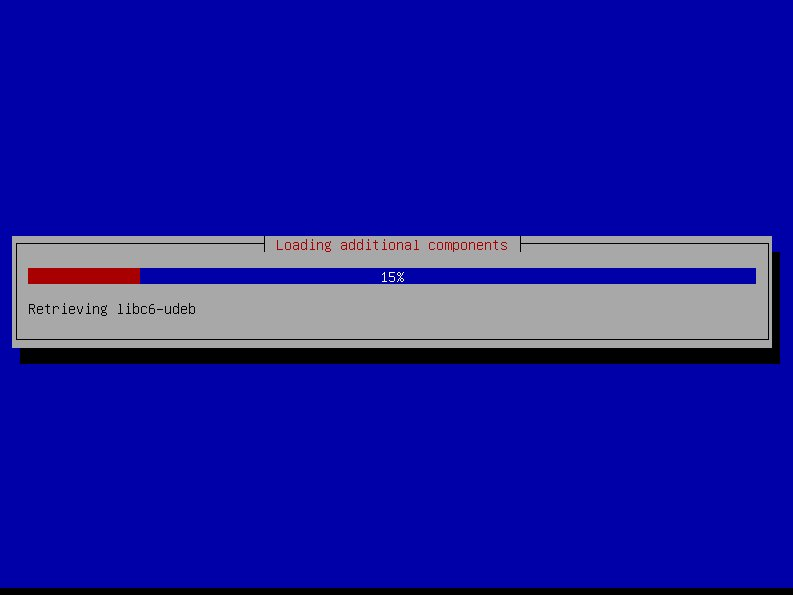
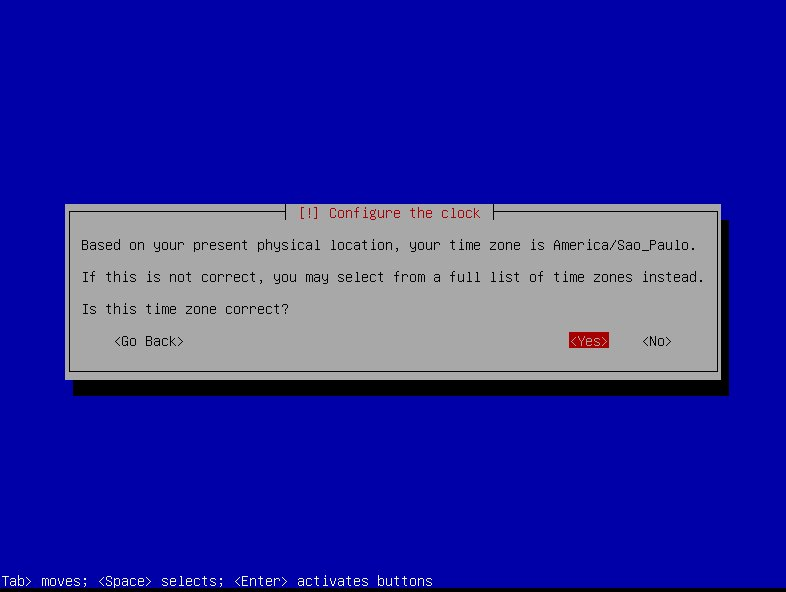
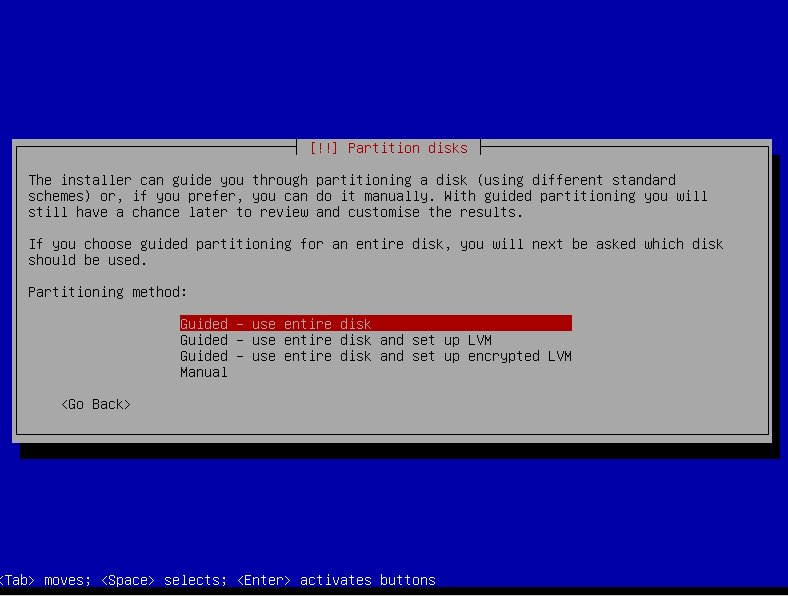
Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.
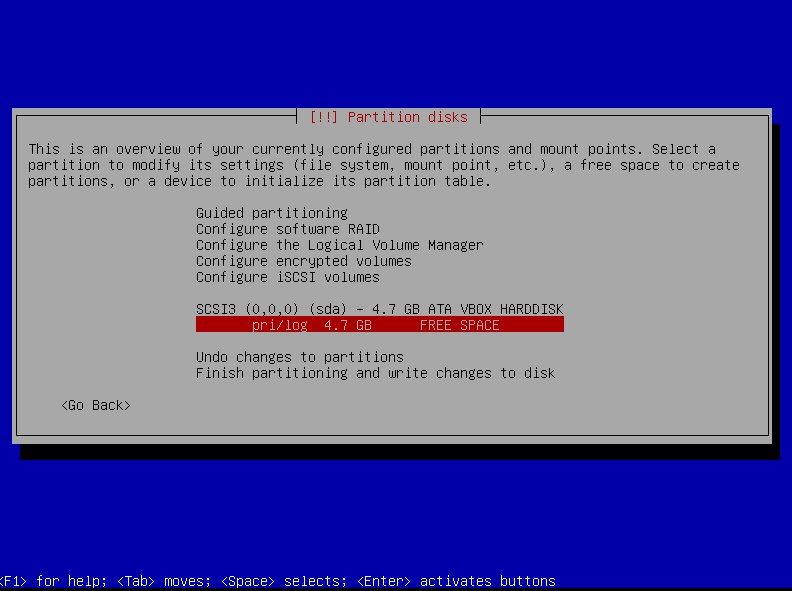
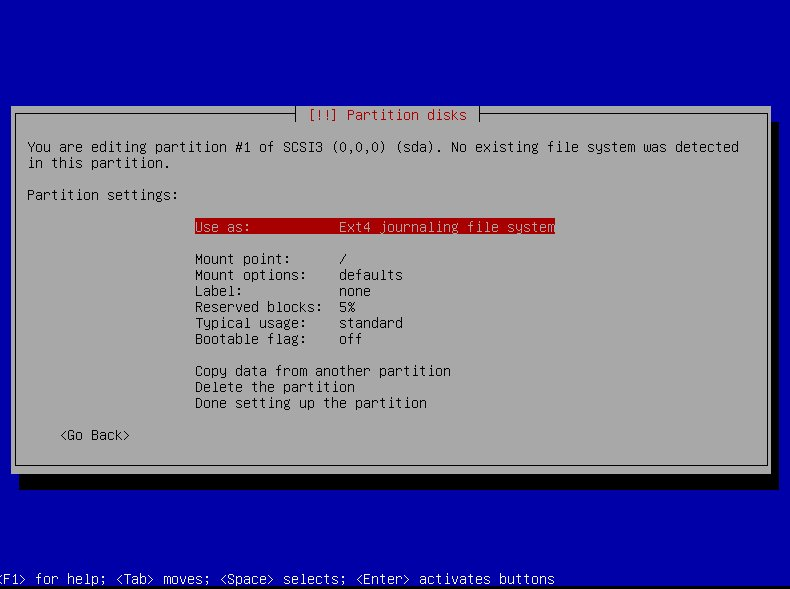
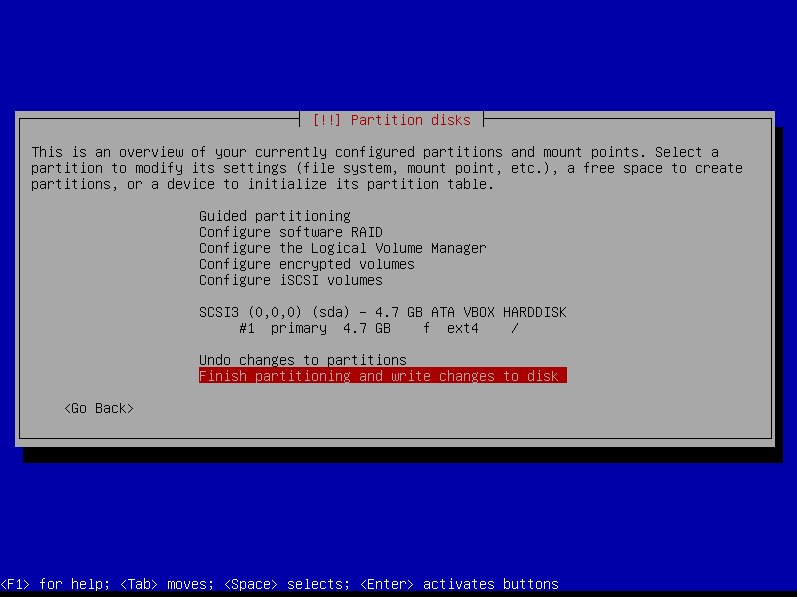
Após criar, FINISH!
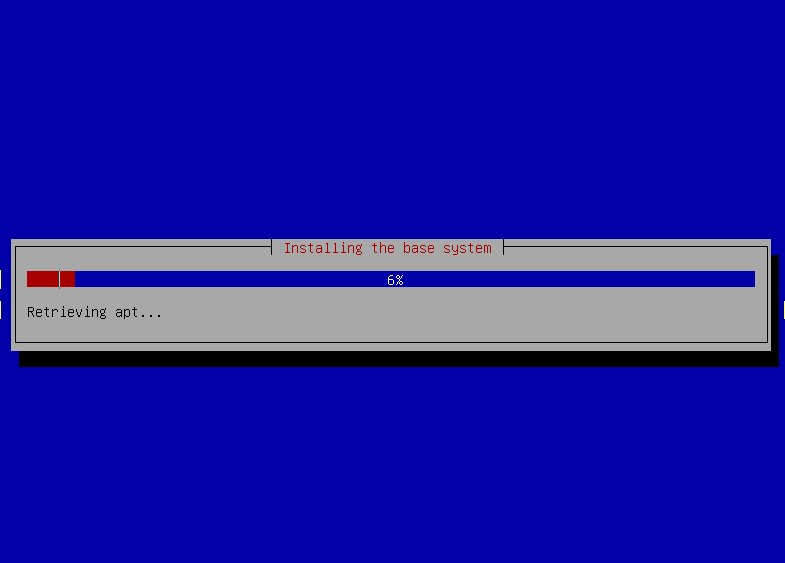
Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.
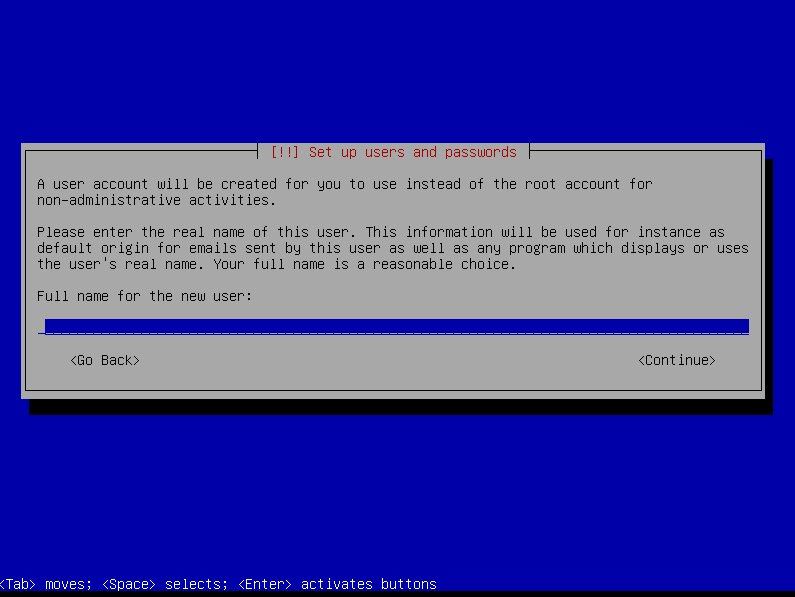
O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.
senha é bom por né.
Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.
Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente.
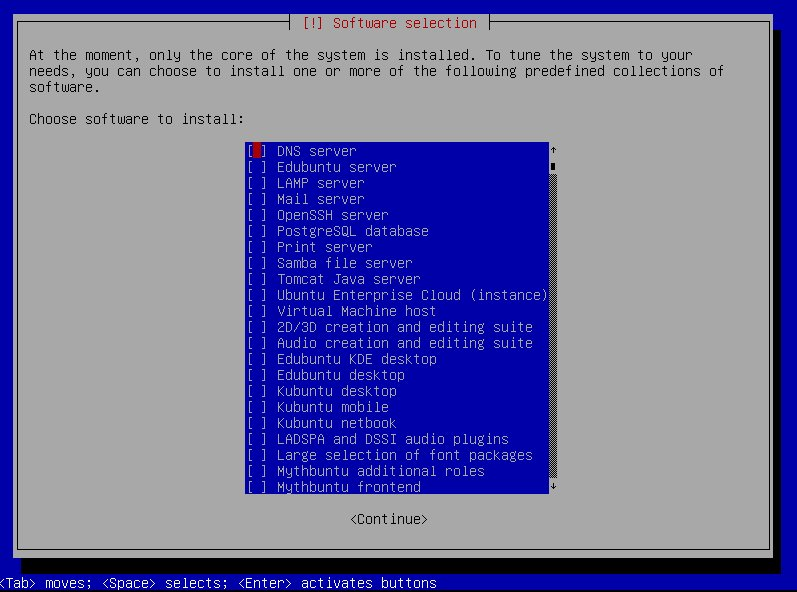
Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar.
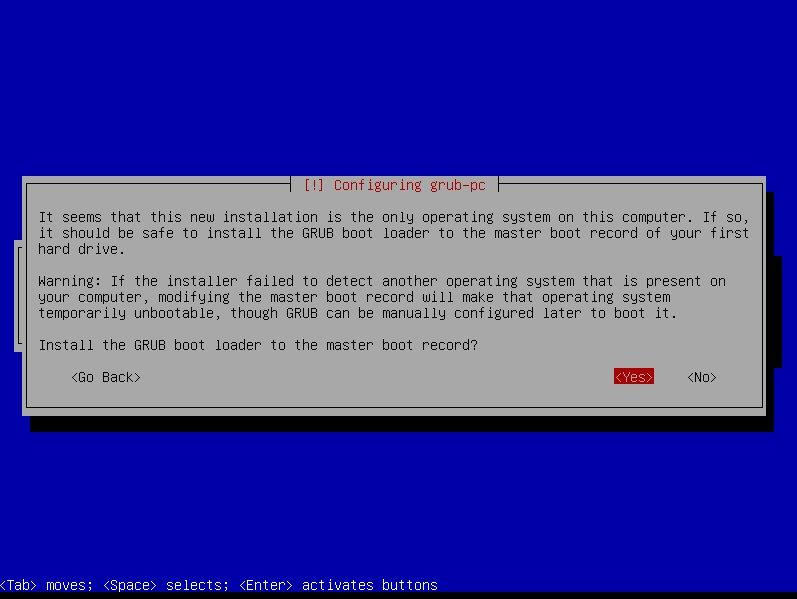
Grub é o gerenciador de boot, instale ele ai sem medo.
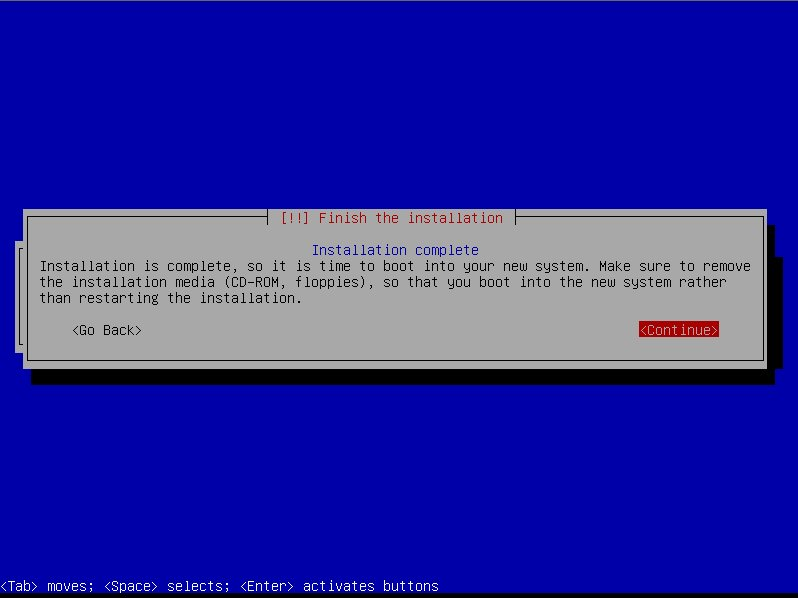
Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada.
Logue-se com seu usuário, meu caso “lion” (que coisa gay figura 24 ainda).
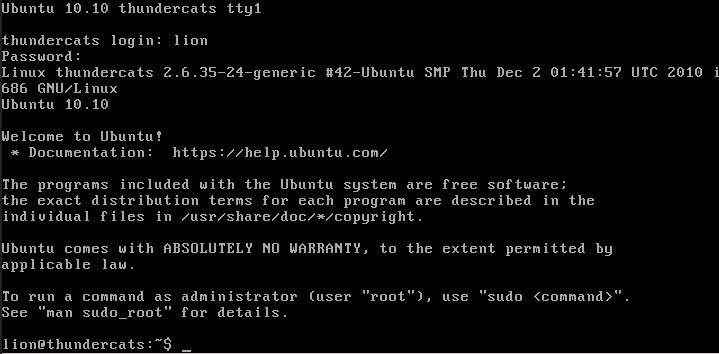
**Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI.
**Torna-se root**
Isso é primordio no linux, sempre somos o ROOT, o Ubuntu tem essa filosofia para você não fazer cagada, mas na vida uma boa técnica de aprendizado é fazendo cagada, então vamos habilitar o root.
Calma usaremos o root para tarefas como instalar novos software, mas a execução e configuração de nosso ambiente será com nosso usuário.
```
$ sudo passwd root
```
Pronto a partir de agora os comandos começados com # quer dizer que você tem que estar logado como root, e quando estiver $ você deve executar com seu usuário.
Loge-se como root vamos usar bastante de um $su ou entre num novo tty como root.
**Instalando o vim**
```
#apt-get install vim
```
(repare # você tem que estar logado como root)
**Removendo o boot-splash**
Amigos estamos falando de uma maquina limpa, o boot splash só come memória.
Faça um backup antes e depois edite o arquivo “/boot/grub/grub.cfg” procure a palavra splash e apague somente ela e salve o arquivo. É necessário dar diretos de gravação e depois volte como somente leitura.
**Removendo Mensagem de boas vindas MOTD**
Logo após o login, é exibida uma mensagem de boas vindas enorme do ubuntu, eu não gosto dela, nem do debian eu gostava e eu a removia editando o script “/etc/init.d/boot-misc.sh” mas no ubuntu esse arquivo não existe.
Depois de muito fuçar eu descobri que removendo os arquivos do diretorio “/etc/update-motd.d/” a mensagem some, pra mim basta, também removi o conteudo do arquivo /var/run/motd ;
**UPDATE**
Dica do comentário do Marcelo Godim
Ele é gerenciado pelo pam_motd basta ir em /etc/pam.d nos arquivos “login” e “sshd” e comentar essas linhas abaixo:
login:
#session optional pam_motd.so
sshd:
#session optional pam_motd.so # [1]
**Mudando mensagem da versão**
Dica velha edite o arquivo “/etc/issue” coloque o que preferir.
——Se você não precisa de modo gráfico a instalação terminou aqui.
Alterando o sources.list adicionando outros repositórios
Edite o arquivo /etc/apt/sources.list e deixe assim, basicamente adicionados pacotes do site Medibuntu, se prefereir siga esses passos é melhor do que editar o arquivo.
**Instalando o resto dos pacotes**
#apt-get install xserver-xorg xinit alsa-base alsa-utils openbox obconf obmenu feh nitrogen tint2 k3b conky gmrun pcmanfm gtk-theme-switch ssh smbfs smbclient dosfstools setserial usbutils leafpad x11-apps openbox-themes terminator chromium-browser xcompmgr gcc g++ openjdk-6-jdk mysql-server mysql-query-browser gftp gcc-avr avrdude imagemagick gparted ntfs-3g file-roller zip unrar gpicview gtk2-engines gnome-icon-theme-gartoon vim unace rar unrar zip unzip p7zip-full p7zip-rar sharutils uudeview mpack lha arj cabextract file-roller pidgin pidgin-data pidgin-lastfm pidgin-guifications msn-pecan pidgin-musictracker pidgin-plugin-pack pidgin-themes mplayer vlc cairo-dock w32codecs audacious
Vai dormir, seila vai baixar ai uns 500mb, você pode tirar ou por o que quiser ai isso é minha instalação.
Como entrar no modo gráfico?
Logue-se com seu usuário
```
$startx
```
O comando antigo, simples, que dei a primeira vez no meu conectiva 4.
Este é o resultado final, mas para isso vamos algumas dicas.
Toda incialização dos aplicativos eu concentrei no .config/openbox/autostart.sh segue o meu ai
```
# Set desktop wallpaper
nitrogen –restore &
# Enable Eyecandy – off by default
xcompmgr -cCfF -r7 -o.65 -l-10 -t-8 &
# Launch network manager applet
(sleep 4s && nm-applet) &
# Launch clipboard manager
#(sleep 1s && parcellite) &
# Uncomment to enable system updates at boot
#(sleep 180s && system-update) &
cairo-dock &
# Launch Conky
#conky -q &
# Launch panel
tint2 &
```
**Configurando teclas de atalho**, edite o arquivo .config/openbox/rc.xml, vá até a seção keybinds as minhas são essas abaixo:
```
<keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-1″><action name=”Execute”> <execute>xcompmgr -cCfF -r7 -o.65 -l-10 -t-8</execute></action></keybind><keybind key=”W-2″><action name=”Execute”> <execute>pkill xcompmgr</execute></action></keybind><keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-e”><action name=”Execute”> <execute>pcmanfm</execute></action></keybind><keybind key=”W-g”><action name=”Execute”> <startupnotify> <enabled>true</enabled> <name>transset</name> </startupnotify> <command>transset .50</command></action></keybind><keybind key=”W-h”><action name=”Execute”> <startupnotify><enabled>true</enabled><name>transset 1</name></startupnotify><command>transset 1</command></action></keybind><keybind key=”W-l”><action name=”Execute”><startupnotify><enabled>true</enabled><name>Lock screen</name></startupnotify><command>gnome-screensaver-command -l</command></action></keybind><keybind key=”W-t”><action name=”Execute”><execute>terminator</execute></action></keybind><keybind key=”W-r”> <action name=”Execute”> <execute>gmrun</execute> </action></keybind>
```
Pesquise como instalar temas GTK, configurar o TINT2 (desk bar), Cairo Dock, também tem muitas configurações de openbox na internet.
Esse tutorial vem de anos de convivio com linux, é duro passar tudo a limpo aqui, uma dica e testar o Linux Crunch-Bang aprendi muitas customizações com ele.
#blog #tech
-

@ c11cf5f8:4928464d
2024-09-08 09:08:04

- - -
Here we are again with our [The Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times), trying to give you a hit of what you missed this past month in the ~AGORA territory.
- - -
### Top-Performing Ads
Drumroll please 🥁 ... for the most engaging ones:
* `01` [[SELL] 1 Million Products, Travel Agency, Concierge and Cars - ShopinBit.com](https://stacker.news/items/673616/r/AG) by @shopinbit
* `02` [[SELL] Satoffee⚡️☕️ Cafeteras automáticas que aceptan Bitcoin Lightning 🇪🇸 🌐](https://stacker.news/items/675680/r/AG) by @VEINTIUNO
* `03` [[⚖️SELL] Hand-Made Flecktarn Pouch(es)](https://stacker.news/items/650741/r/AG) by Fabs
* `04` [[OFFER] Proton Wallet - 3 invites left](https://stacker.news/items/656656/r/AG) by @npub1q67p49masrcjf__d7qaq6mwh0q
* `05` [[SELL] Bitcoin Accepted Here – Unisex organic cotton Black T-shirt](https://stacker.news/items/666650/r/AG) by @VEINTIUNO
* `06` [[FOR SALE] Playstation 2 (PS2) Games - Excellent Condition - Pay In SATS!!!](https://stacker.news/items/647968/r/AG) by @watchmancbiz
* `07` [[OFFER] Happy Bitcoin Infinity Day](https://stacker.news/items/657338/r/AG) by @thebullishbitcoiner
- - -
##### In case you missed
Here some interesting post opening conversation and free speech:
This edition winner look's @proofoftaste, with his request for help finding a way to get a local product delivered to his country. The challenge was that the producer, required an ID number on checkout! Pretty unusual... or it will be soon the norm?
Thanks a lot for @supratic for being so active in the territory and sharing so many topics and articles about commerce and law, basically giving us a hit on how the world is currently ruled, pretty fascinating!
* `01` [Can someone in Italy help me get my favourite sauce to Germany?](https://stacker.news/items/644918/r/AG) by @proofoftaste
* `02` [The History of Banking – Ernest Rauthschild](https://stacker.news/items/643333/r/AG) by @supratic
* `03` [10 Hidden Rules of Commerce](https://stacker.news/items/654215/r/AG) by @supratic
* `04` [How to Start Your Own Micronation](https://stacker.news/items/647294/r/AG) by @supratic
* `05` [Understanding the One People's Public Trust: A Beginner's Guide to the OPPT(https://stacker.news/items/641554/r/AG) by @supratic
* `06` [A Bank Whistleblower called me...](https://stacker.news/items/646118/r/AG) by @supratic
* `07` [One Stupid Fu*K 🥒 Contract Killer Course 2.0 - Brandon Joe Williams](https://stacker.news/items/675943/r/AG) by @02a0eb55b5
- - -
##### 🏷️ Spending Sunday is back! https://stacker.news/items/653241/r/AG
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats!
- - -
##### Just a reminder for you all
To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting.
- - -
### Create your Ads now!

This territory aims to connect stackers and curious buyers online and IRL for exclusive P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it!
Let's start something new? Hit one of the links below to free your mind:
* [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation,
* [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or,
* if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)!
* [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners
* [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats
* [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item
* [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else
* [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift!
* [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to
- - -
Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we'll help you publish a personalized post.
originally posted at https://stacker.news/items/676777
-

@ c11cf5f8:4928464d
2024-09-08 08:35:16
Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, [here](https://stacker.news/items/668607/r/AG) are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/676757
-

@ c6f7077f:ad5d48fd
2024-09-08 01:24:03
***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further.
#### ***Consider the Most Fundamental Questions***
1. **The Origin of the Universe**
2. **The Origin of Life on Earth**
#### ***The Origin of the Universe***
You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**.
#### ***The Origin of Life on Earth***
The origin of life is even more complex. Life requires three essential components:
- **Proteins** for basic functioning
- **RNA** for storing and replicating genes
- **Lipids** (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**.
#### ***The Question of Certainty***
If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early.
#### ***Reclaiming Control of Science and Education***
The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend:
- **“A Brief History of Time”** by **Stephen Hawking** for physics
- **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-

@ 6bae33c8:607272e8
2024-09-07 22:09:27
With all five of my football drafts/auctions in the books, here's the portfolio I've amassed for 2024, not including the RotoWire Dynasty League:
**Links**: [BCL1](https://www.realmansports.com/p/beat-chris-liss-1-344), [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e?utm_source=publication-search), [BCL3](https://www.realmansports.com/p/beat-chris-liss-3-062), [Steak League](https://www.realmansports.com/p/steak-league-879), [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7)
**Players in whom I have the most shares:**
**QB**: Justin Fields (4), CJ Stroud (2), Anthony Richardson (2), Tua Tagovailoa (2)
**RB**: Jonathan Brooks (2), Brian Robinson (2), Jerome Ford (2), Jordan Mason (2), JK Dobbins (2), Khalil Herbert (2), Dalvin Cook (2)
**WR:** Stefon Diggs (5), Ja’Marr Chase (3), Rashid Shaheed (3), Ladd McConkey (2), Roman Wilson (2)
**TE:** Jonnu Smith (3)
**K**: Younghoe Koo (3), Harrison Butker (2)
**D:** Giants (4)
**Notes:**
Obviously, I thought Stefon Diggs was mispriced, though I only had to pay close to what I thought he was worth in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7) — in the rest of the leagues he fell to me at ADP or below. He and Ja’Marr Chase are massively important to me this year, and to a lesser extent CJ Stroud.
I also have Justin Fields and the Giants defense everywhere, but both were essentially free, and I could swap them out without issue. I also have a lot of Younghoe Koo, but he too could obviously be swapped out. I like having a couple key players to build around rather than five disparate teams. Of course if Diggs gets hurt or turns out to be washed up, it’ll be rough, but in some ways it’s like the old days where you had only one team, and you had to live and die with it.
**Prominent Players I Don't Have (bold is by choice):**
Bijan Robinson, Tyreek Hill, Breece Hall, Amon-Ra St. Brown, Justin Jefferson, Garrett Wilson, A.J. Brown, Jonathan Taylor, Puka Nacua, **Davante Adams**, **Saquon Barkley**, Chris Olave, Rashee Rice, **Kyren Williams**, Travis Etienne, Cooper Kupp, Isiah Pacheco, **Michael Pittman**, **Nico Collins**, **DK Metcalf**, **Mike Evans**, **Deebo Samuel, Josh Allen,** DJ Moore, Brandon Aiyuk, Derrick Henry, Zay Flowers, **James Cook**, Terry McLaurin, Kenneth Walker, **Xavier Worthy**, Amari Cooper, Josh Jacobs, Trey McBride, **George Pickens**, Lamar Jackson, **Christian Kirk**, Tee Higgins, **Calvin Ridley**, **Rachaad White,** Jayden Reed, Diontae Johnson, **Travis Kelce**, **Joe Mixon**, **Alvin Kamara**, Christian Watson, **Jalen Hurts**, Aaron Jones, Patrick Mahomes, David Montgomery, **Zamir White, Keenan Allen,** Kyle Pitts, **D’Andre Swift**, George Kittle
**Past Portfolios:**
[**2023**](https://www.realmansports.com/p/my-portfolio-ef6?utm_source=publication-search)**, [2022](https://www.realmansports.com/p/my-portfolio?utm_source=%2Fsearch%2Fmy%2520portfolio&utm_medium=reader2), [2021](https://www.rotowire.com/football/article/nfl-chris-lissrsquo-portfolio-58839), [2020](https://www.rotowire.com/football/article.php?id=52704)[, 2019](https://www.rotowire.com/blog/post.php?id=29428), [2018](https://www.rotowire.com/blog/post.php?id=26158), [2017](https://www.rotowire.com/blog/post.php?id=23069), [2016](https://www.rotowire.com/blog/post.php?id=13592), [2015](https://www.rotowire.com/blog/post.php?id=8991)**
-

@ 6bae33c8:607272e8
2024-09-07 22:07:54
I submitted my five picks for the Circa Millions contest today. I think it’s $6M in total prizes. I want to put a disclaimer here: I’m putting these behind a paywall not because you should pay for these picks — never pay for anyone’s picks.
If the picks were that good, whoever was making them could just print money and wouldn’t need yours. If you want to subscribe in earnest, do so because you’re interested to see who I chose and read the reasoning, not because you (erroneously) think it’s the way to get some easy winners. Or if you want to support my substack generally because you think it adds value to you. Those are fine reasons to subscribe, but doing so because you think copying my picks will make you money is dumb.
Okay that out of the way, here are the picks:
**Dolphins -3.5 vs Jaguars** — I like taking the Dolphins in early September, it’s hot and humid there, difficult for opposing teams to adjust to it. It’s like Lambeau Field in December, only in reverse. Moreover, the Dolphins are a veteran offense that’s played together for years, while the Jaguars are working in two new receivers.
**Falcons -3.5 vs Steelers** — Justin Fields is probably an upgrade over Russell Wilson at this point, but he’s haphazard and will have to learn the players and offense on the fly. The Falcons have a new QB too, but he’s an old pro, has better weapons and a better offensive line.
**Giants +1 vs Vikings** — The Giants have three Pro-Bowl level pass rushers, finally have a playmaking receiver and upgraded their offensive line this offseason. And yet despite facing Sam Darnold at home, they’re still getting a point.
**Cardinals +6.5 at Bills** — Kyler Murray is now another year removed from knee surgery, should be his usual spry self, and Marvin Harrison adds another dimension to the offense it sorely needed. The Bills will move the ball, but I think Arizona will hang with them and keep it close enough.
**Browns -2 vs Cowboys** — The Browns should be able to run the ball and keep the Dallas pass rush off Deshaun Watson, while Dallas’ offensive line has slipped a bit, and the Browns defense was No. 1 against the pass last year. Dak Prescott also has big home/road splits.
-

@ 6bae33c8:607272e8
2024-09-07 22:05:26
This is my main event for fantasy football, the $1700 buy-in NFFC Primetime. I wound up picking 11th (I had the fourth to last choice), and while in retrospect maybe I should have opted for ninth or 10th, I wanted to get a share of Jahmyr Gibbs which is why I chose that slot. I also ran through some scenarios beforehand — what if Ja’Marr Chase (still not signed) falls — do I take him in a fourth league? But as you’ll see, the first round was complete chalk, and no windfalls whatsoever fell to me.
But I had a plan for that, and I more or less executed it.
Without further ado, here are the results:
<img src="https://blossom.primal.net/4bbf1f4369c4eea958b04922892f9c485dcbce7d68f011e55c11997f05ae6006.png">
**1.11 Jahmyr Gibbs** — This was the most likely scenario, and it took me about two seconds to make the pick once the top three backs and seven receivers were gone. If Gibbs (who is not on the injury report) hadn’t had a hamstring injury in camp, I’d have him close to the middle of the round rather than the end. Let’s hope he doesn’t aggravate it.
**2.2 Marvin Harrison** — I would have taken either Puka Nacua or Jonathan Taylor, but no breaks here either. Both went at the turn, and I knew I was taking a receiver. Starting RB-WR is the easiest build, in my opinion, but Harrison was kind of an agnostic pick. I had considered Rashee Rice, but as Alan Seslowsky pointed out, while his suspension for hit and run might not kick in until after the season (when the legal process has run its course), that could be pushed up if his lawyers negotiate a plea. Between that an the presence of so many options for the Chiefs, I went Harrison over him narrowly. But it was a close call.
**3.2 Stefon Diggs** — I missed Malik Nabers, Cooper Kupp, (maybe Jaylen Waddle) and De’Von Achane who went with the four consecutive picks ahead of me, so it was Diggs, Nico Collins (his teammate who has a higher ADP), DeVonta Smith or (maybe) Derrick Henry. I went Diggs who I had personally ranked the highest, wouldn’t make it back to me, who I have in every league and was part of my “unfriendly” draft plan, i.e., the Plan B I had talked about.
**4.11 Tank Dell** — He’s too small to hold up, but whenever he played he produced, and he gives me a bit of a Diggs hedge. I also wanted Trey McBride on this turn (as I had Marvin Harrison and could have drafted Kyler Murray — who I love this year — later), but he went on the turn. I thought about taking McBride first, but they were side by side in ADP, and my Plan B was to stack Texans, so I went Dell and took a chance.
**5.2 Chris Godwin** — This was the one pick I kind of regret (though it’s debatable.) I like Jayden Reed a lot, but he was half a round lower per ADP, and there was *some* chance I could get him on the way back. I had Godwin everywhere last year, and he was a disappointment, but apparently he’s healthier now and is going back to the slot full time where he excels.
**6.11 Jaxon Smith-Njigba** — The other pivot off Godwin was JSN, and sure enough he made it back all the way, though he starts off as my first bench player. That’s okay though — you need at least five viable receivers throughout the year, and I didn’t have to take C.J. Stroud because if the guy at the turn took him, I would just pivot to the Kyler Murray/Harrison stack.
**7.2 C.J. Stroud** — He was there, and I executed Plan B. Yes, I have a weak first three rounds by ADP, but I have Gibbs, Harrison and a big piece of the Texans passing game which I think will lead the NFL in yardage.
**8.11 Jaylen Warren** — I needed a second back, and Warren is one. He’s a good pass catcher and should see half the snaps in Pittsburgh.
**9.2 Brian Robinson** — I like Robinson as a player, he’s the undisputed early-down option on what should be a better offense. (Think Ricky Pearsall, but at RB.) Too soon? Austin Ekeler will obviously see the passing-down work unless he proves totally washed up. The Robinson pick cost me David Njoku and Brock Bowers unfortunately, which was a gamble I knew I was making.
**10.11 Jordan Mason** — At 29 and playing into the Super Bowl, Christian McCalfinjury was already a risk, and that he’s “expected” to play Monday night rather than 100 percent fine is worrying. Mason could be a league winner if McCaffrey goes down.
**11.2 J.K. Dobbins** — The Mason pick cost me Jaleel McLaughlin, so I pivoted to Dobbins who still has a high ceiling if he can ever stay healthy.
**12.11 Dallas Goedert** — Tight ends had flown off the board, but I was happy to get Goedert who has been valuable on a per-game basis the last couple years and is still just 29 which is late prime for the position.
**13.2 Dalton Schultz** — Why not stack it even harder? The Texans could throw for 5,000-plus yards, and I have three of the four top targets and the QB.
**14.11 Andrei Iosivas** — He’s gotten a lot of buzz in camp, seems like the No. 3 receiver right now, Tee Higgins is hurt and Ja’Marr Chase is still unsigned.
**15.2 Cam Akers** — The Iosivas pick cost me Jalen McMillan who would have served as Godwin insurance, but Akers could easily take an aging Joe Mixon’s job. Maybe it’s too much Houston, but if it’s a top-three offense, I’m good with it.
**16.11 Justin Fields** — The backup QBs had flown off the board, and Fields has too much upside to pass up. Plus he might even start Week 1 with Russell Wilson already hurt, and if he plays well, he might never look back.
**17.2 Harrison Butker** — It’s either the based af kicker or a Younghoe for me. Plus he locked in a decent Week 1.
**18.11 Dalvin Cook** — He had only 67 carries last year for a bad Jets offense. What if he isn’t as washed up as we think? He could easily win that job over Zeke Elliott and Rico Dowdle.
**19.2 Jonnu Smith** — TE is my weakest position, so I took another upside gamble. What if he’s the Dolphins third target?
**20.11 Giants Defense** — I think I took them in all four NFFC leagues. They get the Darnold Vikings at home and then Jayden Daniels in his second career start. And they have three Pro Bowl level pass rushers.
**Roster By Position**
**QB** CJ Stroud
**RB** Jahmyr Gibbs/Jaylen Warren
**WR** Marvin Harrison/Stefon Diggs/Tank Dell
**TE** Dallas Goedert
**FLEX** Chris Godwin
**K** Harrison Butker
**D** Giants
**B** Jaxon Smith-Njigba/Brian Robinson/Jordan Mason/JK Dobbins/Dalton Schultz/Andrei Iosivas/Cam Akers/Justin Fields/Dalvin Cook/Jonnu Smith
-

@ 6bae33c8:607272e8
2024-09-07 22:00:17
Unfortunately, I didn’t have a ton of action in this game. I had the Packers with the points and am now 0-2 to start the week in my home picking pool. I had Xavier McKinney in the [Steak League](https://www.realmansports.com/p/steak-league-879?utm_source=publication-search) which was nice as like Roquan Smith he too started the year with a pick.
But I was missing the principal scorers namely Saquon Barkley (maybe I let the nerds talk me out of him, as I had him [ranked highly initially](https://www.realmansports.com/p/running-back-rankings?utm_source=publication-search)) and Jayden Reed. Barkley I’m okay with because the potential for Jalen Hurts TDs was something I hadn’t initially considered, but Reed was a major error and in fact I passed on him for freaking Chris Godwin in my [Primetime last night](https://www.realmansports.com/p/nffc-primetime-fa7?utm_source=publication-search)!
I had even argued with Alan Seslowsky that Reed was the [obvious choice](https://www.realmansports.com/p/week-1) among the Packers receivers. So seeing him go off (and he should have had a third TD, but it was called back due to something I’ve never seen before (both teams having 12 men on the field) was painful. Godwin is almost sure to have a terrible season now just to hammer home the lesson for me: Don’t worry about 10 spots of ADP, take the fucking guy you like. Stop listening to the consensus when you have a real lean.
I don’t know how many times I need to learn this lesson, but apparently at least one more!
- Reed looked like the most electrifying receiver on the field for the Packers. He had only six targets, not including the TD called back due to the penalties, but it’s obvious he’ll get more, and the handoff he took 33-yards to the house will incentivize them to do that again too. Year 2 after the surprisingly strong Year 1. He belongs in the second round now, along with Rashee Rice.
- Christian Watson caught a TD and will be involved, but as great an athlete as he is he doesn’t have Reed’s football skills. Romeo Doubs is just a guy, but he’s reliable, and Dontayvion Wicks had a rough game — he’s an easy cut for me.
- Jordan Love didn’t scramble much, and the Packers settled for a ton of field goals, but he looked okay. I think once they give Reed his 10 targets, Love will have his expected numbers. *(Just read on RotoWire that Love left the game for the last two plays with an unspecified leg injury, something not apparent on the 40-minute edited version. I thought they brought Malik Willis to throw a Hail Mary!* *Obviously, if he’s out for any length of time, all bets are off for the Packers receivers.)*
- Josh Jacobs got stuffed in short yardage early, fumbled (though the Packers recovered), but ran well and hard late and even caught two passes. I have zero shares, but he looks like a fine pick for the late-third/early fourth. His backup Emanuel Wilson looked pretty spry too. Marshawn Lloyd is a cut now too in most formats.
- Brayden Narveson missed a key kick off the post, but got a lot of attempts. He seems to have landed in the right place for a big season.
- Jalen Hurts was a bit sloppy with two picks and a lost fumble, never got going on the ground (seemed like the Packers were really dedicated to taking that away), and the ass-smash didn’t work as well without Jason Kelce. But his receivers are so good, and Saquon Barkley is a big upgrade too. I would downgrade him a little though as his rushing TD projection maybe went from 10 to seven.
- AJ Brown didn’t even look like he was running fast as he easily scored a 67-yard TD past the Packers defense. DeVonta Smith seemed to line up more in the slot and was automatic on key third-downs. There was no third receiver of which to speak, and even Dallas Goedert saw only five targets.
- Barkley looked great, both on his TD catch, and as a rusher. As I said I don’t have any shares despite being high on him initially, but I love Barkley as a player (and bitcoiner!), and still kind of root for him. I hope he smashes this year.
-

@ 9358c676:9f2912fc
2024-09-07 18:50:14
## Introduction
The human immunodeficiency virus (HIV) began as a pandemic in the 1980s. In its early days, it was seen as a certain death sentence, a taboo associated with marginalized groups, and it highlighted the failures of poverty in accessing healthcare. Gradually, the struggle for life and the suffering of those who are no longer with us, including both famous and anonymous individuals, became visible.
Today, 40 years later, HIV is presented as a chronic disease with effective treatment. **Patients living with HIV who receive appropriate treatment have no detectable virus in their circulating blood, enjoy a good quality of life, and are more concerned about other aspects of their health during medical consultations, almost forgetting their condition.** For these patients, daily treatment is the cure, similar to someone taking a pill every day for high blood pressure or diabetes.
## The Global Impact
HIV is a lentivirus, a subgroup of retroviruses composed of RNA. The natural history of HIV infection involves an attack on the immune system, particularly targeting CD4 cells, where chronic deterioration can lead to the acquisition of infectious and oncological diseases that may be fatal over the years, resulting in acquired immunodeficiency syndrome (AIDS).
Interestingly, there is a small group of people known as "elite controllers" who manage to control HIV infection without treatment and remain healthy for much of their lives, despite having a hidden deep viral reservoir. The primary modes of transmission are sexual, followed by blood and vertical transmission from mother to child, with the first mode predominating today.
Today, in the downward trend of the HIV epidemic, **it is estimated that 39 million people are living with HIV worldwide.** Depending on the region, nearly half of this population belongs to at-risk groups, such as men who have sex with men (MSM), transgender individuals, sex workers, and people who inject drugs. These vulnerable groups are especially important for prevention efforts. However, little is done for prevention in the general population, which sometimes represents the other half of the cake of people living with HIV (PLWH).
## Breaking the Dogma: The Concept of Undetectable = Untransmittable (U=U)
The introduction of highly effective antiretroviral therapy (HAART) in 1994 broke the curve of the HIV epidemic. The introduction of new medications with fewer side effects and greater effectiveness in controlling the virus has been crucial. In 2007, the launch of Raltegravir as the first viral integrase inhibitor marked a milestone in current treatments, **allowing patients to effectively control the virus within 3 to 6 months.**
The positive impact of these treatments led health organizations to launch the concept of **undetectable = untransmittable (U=U)** to impact the general population and at-risk groups, updating the dogma and eradicating stigma: **a patient living with HIV who maintains an undetectable viral load in their blood through treatment will not transmit HIV sexually.**
Although this concept has transformed the social dynamics and stigma surrounding the disease, adherence to treatment must be complete to achieve this new paradigm.
## Prophylaxis as a Method to Prevent HIV in Healthy Populations
The correct use of condoms has been the cornerstone of HIV prevention and other sexually transmitted infections over the years. However, it is not the only tool available today and can be complemented for comprehensive sexual health.
**Pre-exposure prophylaxis (PrEP)** is a novel strategy that involves administering antiretroviral medication to vulnerable groups before they are exposed to HIV (MSM, transgender individuals, sex workers, people who inject drugs). It involves taking medication daily, effectively reducing the risk of contracting HIV and providing protection to these groups. It is similar to taking a contraceptive pill daily. It has had a very positive impact on protecting these populations. In the Americas, it has been successfully implemented in the United States, Mexico, Peru, and Brazil. Other countries, although with some delay, are now implementing this strategy.
**Post-exposure prophylaxis (PEP),** on the other hand, is a strategy that involves administering antiretroviral treatment after a potential exposure to HIV. If the treatment is administered within the first 72 hours and maintained for 4 weeks, the chances of contracting HIV decrease substantially.
Both strategies have been remarkably successful in preventing HIV in at-risk populations and healthy populations, although their dissemination and awareness remain limited.
https://image.nostr.build/08682bf763ade56741d8e4c8c6d870cb8d71ab7d72c605b9aa805af2234348ff.jpg
## The New Horizon: Long-Acting Antiretrovirals, HIV Vaccines, and Promising Therapies
The introduction of viral integrase inhibitors and new nucleoside analogs in the last 15 years has allowed for the availability of safe drugs with minimal side effects in the treatment of HIV, **many of which are included in a single pill regimen per day.** However, the pharmaceutical industry continues to diversify the offerings in a healthy manner.
**Cabotegravir is a new long-acting integrase inhibitor that is administered via injection.** Combined with Rilpivirine, it has proven to be effective and safe in the treatment of HIV, with injections every 2 months. This has revolutionized treatment for people who are tired of taking pills daily, as well as in PrEP, where effective prevention against HIV can be achieved with injections every 2 months for at-risk groups.
Additionally, **subdermal implants of Islatravir,** a new long-acting nucleoside analog, are being tested as a PrEP strategy. Similar to monthly hormonal contraceptive injections or hormonal contraceptive implants, this strategy has proven effective in at-risk groups.
Regarding the **HIV vaccine,** we have been developing it for over two decades, with advances and setbacks. While vaccines have shown promising results in terms of safety and antibody generation, we still need to await conclusive phase III results demonstrating their effectiveness in at-risk groups and the general population.
## The Eradication of HIV and Patients Cured Without Treatment
While current treatment allows for the elimination of HIV from the bloodstream and sexual transmission, there remains a reservoir in some deep immune cells that have been infected by the retrovirus, which contain latent HIV DNA and have the potential to reactivate if daily treatment is interrupted.
However, **there are patients who have managed to eliminate HIV from their bodies, including these deep cells, and HIV is undetectable upon discontinuation of treatment.** These cases are very rare, with only 7 to 8 individuals being the subject of intensive scientific study. Among them are the "Berlin patient" of Germany and "City of Hope patient" from Argentina. Some of these cases involved patients under effective HIV treatment who underwent suppressive chemotherapy for bone marrow transplants and managed to eliminate these deep cells with latent HIV DNA.
Unfortunately, this treatment is not scalable for the entire HIV-positive population, both due to its cost and potential side effects. However, **"Shock and Kill" strategies** have been proposed, aiming to use monoclonal antibodies to activate these latent cells during HIV treatment, exposing them to antiretroviral medication for elimination, thereby eradicating these small reservoirs of HIV.
## WHO Goals
The World Health Organization (WHO) has established clear objectives that are constantly updated to achieve the eradication of HIV in the population.
**The updated goals of the WHO propose that, to end the HIV epidemic, three objectives must be met by the year 2025-2030:**
1. 95% of people living with HIV must be diagnosed through testing.
2. 95% of diagnosed individuals must be on highly effective antiretroviral therapy (HAART).
3. 95% of those on HAART must have an undetectable viral load in their blood.
Developing and underdeveloped countries currently have an effectiveness rate for these strategies that disagree significantly.
https://image.nostr.build/ac6693df57aaca6dac0b06b5db9eb1a2757e7c08511edb0f11617e12653d3db5.png
## Key Takeaways
* HIV has a cure, and the cure is permanent treatment.
* Treatment for HIV is free and accessible to the population, as it is a public health impact disease.
* A person living with HIV who receives appropriate treatment will not transmit the virus sexually, will enjoy a full life without the disease, and can have children without HIV.
* In the event of a potential HIV exposure (such as unprotected sexual contact with an infrequent partner), you can go to a hospital within the first 72 hours to receive treatment that will prevent HIV infection.
* Just as we witnessed the eradication of smallpox from the face of the earth in 1978 due to scientific advances, we will live to see the eradication of HIV.
## Autor
**Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community**
npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
## Resources
1. [World Health Organization (WHO)](https://www.who.int/en/health-topics/hiv-aids#tab=tab_1)
2. [Centers for Disease Control and Prevention (CDC)](https://www.cdc.gov/hiv/?CDC_AAref_Val=https://www.cdc.gov/hiv/default.html)
3. [UNAIDS](https://www.unaids.org/en)
## Bibliography
1. The natural history of HIV infection. DOI: 10.1097/COH.0b013e328361fa66
2. Changing Knowledge and Attitudes Towards HIV Treatment-as-Prevention and "Undetectable = Untransmittable": A Systematic Review. DOI: 10.1007/s10461-021-03296-8
3. Challenges of HIV diagnosis and management in the context of pre-exposure prophylaxis (PrEP), post-exposure prophylaxis (PEP), test and start and acute HIV infection: a scoping review. DOI: 10.1002/jia2.25419
4. Long-acting cabotegravir and rilpivirine dosed every 2 months in adults with HIV-1 infection (ATLAS-2M), 48-week results: a randomised, multicentre, open-label, phase 3b, non-inferiority study. DOI: 10.1016/S0140-6736(20)32666-0
5. Efficacy and safety of long-acting cabotegravir compared with daily oral tenofovir disoproxil fumarate plus emtricitabine to prevent HIV infection in cisgender men and transgender women who have sex with men 1 year after study unblinding: a secondary analysis of the phase 2b and 3 HPTN 083 randomised controlled trial. DOI: 10.1016/S2352-3018(23)00261-8
6. Safety and immunogenicity of a subtype C ALVAC-HIV (vCP2438) vaccine prime plus bivalent subtype C gp120 vaccine boost adjuvanted with MF59 or alum in healthy adults without HIV (HVTN 107): A phase 1/2a randomized trial. DOI: 10.1371/journal.pmed.1004360
7. Shock and kill within the CNS: A promising HIV eradication approach?. DOI: 10.1002/JLB.5VMR0122-046RRR
-

@ 41d0a715:9733c512
2024-09-07 15:27:14
>Blaise Pascal: 'I have made this letter longer than usual, only because I have not had the time to make it shorter.'
Some of you Stackers need to spend a little more time to make your posts short and sweet.
Sometimes I realize a post doesn't even have a point after wasting time reading it.
A long poorly written post is a waste of my time and yours too!
originally posted at https://stacker.news/items/676136
-

@ 655a7cf1:d0510794
2024-09-06 23:45:52
I can't stop thinking about it. When I go to clear out a cave in Skyrim I always find the troll the spider some version of some enemy with gold.
I ask myself how did they get this gold.? Is there someone in the cities that goes to and fro to have commerce with underworld. If so what would this market look like. Would it be trade based or commodity based. Sometimes in these caves I can find upwards of 100 gold I can also find individuals with upwards of 20 gold on them. Assuming they live paycheck to paycheck this is a moderate size of money they're carrying around from week to week. It tells me that the trade is doing well. Am I completely psychotic for constantly thinking about this? Does anybody else thought about this or done any research or have any links that I can find?
originally posted at https://stacker.news/items/673609
-

@ 8cb60e21:5f2deaea
2024-09-06 22:28:24
JavaScript For Cats
An introduction for new programmers cat
So easy your human companion could do it too!
JavaScript is a programming language or, in other words, a means by which a computer is instructed to do things. Just the same as one controls humans with hisses and meows, one controls computers with statements written in a programming language. All web browsers understand JavaScript and you can take advantage of that to make web pages do crazy things!
JavaScript started as a way to make web pages more interactive. Nowadays JavaScript runs in more places than just web browsers — it runs on web servers, phones and even robots! This page will teach you some JavaScript basics so that you can get up and running in no time*.
* Actual time: more than none. Probably an hour or two. Also since you are a cat you are less likely to run and more likely to lay around in the sun
Table of contents
The console
Strings
Values and variables
Using functions
Built in JS functions
Download new JS functions
Writing new functions
Loops
Arrays
Objects
Callbacks
Recommended reading
Don't be a scaredy-cat
cat
You will always land on your feet — even when programming! Unlike pawing over a glass of water on your laptop, nothing in these tutorials will damage your computer in any way, even if you mistype a command or click the wrong button. Like cats, computer programmers make mistakes all time: misspelling things, forgetting quotes or brackets, and being forgetful of how basic functions (and yarn, lasers) work. Programmers care more about making it work eventually rather than trying to make it work the very first time. The best way to learn is by making mistakes!
So don't be a scaredy-cat! The absolute worst thing that will happen is that you might have to refresh this page in your web browser if you get stuck. Don't worry though, this will happen very rarely.
# The basics
There is JavaScript running on this page right now. Let's play around with it a little. For the sake of simplicity I'll assume you are using Google Chrome to read this page (if you aren't it's probably easier on both of us if you follow along with Chrome).
First, right click anywhere on the screen and hit Inspect Element, then click on the Console tab. You should see a thingy that looks like this:
console
This is a console, otherwise known as a "command line" or "terminal". Basically it's a way to type one thing at a time into a computer and immediately get the computers answer back. They are super useful as a learning tool (I still use the console nearly every day that I'm coding).
The console does some pretty cool stuff. Here I have started to type something and the console is helping me out by giving me a list of all the possible things I could continue to type! Another thing you could do is type 1 + 1 into the console and then hit the Enter key and watch what happens.
Using the console is a very important part of learning JavaScript. If you don't know if something works or what the command is for something, go to the console and figure it out! Here's an example:
# Strings
Since I am a cat I want to replace every instance of the word dog on the Internet with those blasted dogs. First go into your console and type in a few sentences that contain the word dog at least once. In JavaScript a bunch of letters, numbers, words or anything else is known as a String (as in a string of characters). Strings have to begin AND end with a quotation mark. Single ' or double " is fine, just make sure you use the same at the beginning as you do at the end.
console
See the nasty error message? Don't worry - you didn't break any laws. SyntaxError ILLEGAL is just the way it sounds when robots tell you that your program has a problem. The first two sentences had matching quotation marks at the beginning and end, but when I mixed single and double quotation marks it freaked out on me.
OK, to fix up one of these sentences (by replacing dog with our enhanced version) we have to first save the original sentence so that we can call it up later when we do our replacing magic. Notice how the string gets repeated in red when we type it into the console? This is because we haven't told it to save the sentence anywhere so it just gives it right back (or it gives us an Error back if we messed something up).
# Values and variables
Values are the simplest components in JavaScript. 1 is a value, true is a value, "hello" is a value, function() {} is a value, the list goes on! There are a handful of different types of values in JavaScript but we don't need to go over them all right away — you will learn them naturally the more you code!
To store values we use things called variables. The word 'variable' means 'can change' and is used because variables can store many different types of values and can change their value many times. They are pretty much like mailboxes. We put something in a variable, like our sentence, and then give the variable an address that we can use to look up the sentence later. In real life mailboxes have to have PO Box numbers but in JavaScript you usually just use lowercase letters or numbers without any spaces.
console
var is shorthand for variable and the = means store the thing on the right-hand side in the thing on the left-hand side. Also as you can see, now that we are storing our sentence in a variable the console doesn't just return our sentence right away, but instead gives us undefined which means there was nothing to return.
If you simply type a variable name into the console it will print out the value stored in that variable. A note about variables is that by default they go away when you switch to a different page. If I were to hit the Refresh button in Chrome, for example, my dogSentence variable would get wiped and it would be like it never existed. But don't worry about this too much for now — you can just hit the up or down arrows on your keyboard while in the console to go through everything you've entered in recently.
# Functions
Now that we have our sentence stored in a variable, let's change a word stored in it! We can do this by performing a function. Functions are a type of value that, well, serve a specific function (AKA purpose or action) for us. Calling them "actions" sounded weird I guess so they went with the word "function" instead.
JavaScript has a function called replace that does exactly what we want! Functions take in any number of values in their parentheses (zero, one or many) and return either nothing (undefined) or the changed string. The replace function is available to use on any strings and takes in two values: the characters to take out and the characters to swap in. It gets confusing to describe these things so here is a visual example:
console
Notice how the value of dogSentence is the same even after we run replace on it? This is because the replace function, (and most JavaScript functions for that matter) takes the value we give it and returns a new value, without modifying the value we passed in. Since we didn't store the result (there is no = on the left side of the replace function) it just printed out the return value in our console.
# The "standard library"
You might be wondering what other functions are available in JavaScript. The answer: A TON. There are lots built in, standard libraries that you can learn about at MDN (A site run by Mozilla that has lotsa nifty information about web technologies). For example here is the MDN page on JavaScript's Math object.
# Third-party JavaScript
There is also a lot of JavaScript code available that is not built in. JavaScript from third parties is usually referred to as a "library" or "plugin". One of my favorites is called Underscore.js. Let's go and grab it and load it into our page! First go to the Underscore site, http://underscorejs.org/, click on the download link (I usually use development versions because they are easier to read but both will give you the same basic functionality), and then copy all the code onto your clipboard (you can use Select All from the Edit menu to select everything). Then paste it into your console and hit enter. Now your browser has a new variable in it: _. Underscore gives you a ton of helpful functions to play with. We'll learn more about how to use them later.
console
# Making new functions
You aren't limited to using other peoples functions — you can also write them yourself. It's pretty easy! Let's make a function called makeMoreExciting that adds a bunch of exclamation points to the end of a string.
function makeMoreExciting(string) {
return string + '!!!!'
}
In my head I read it out loud like this: "there's a function called 'make more exciting' that takes in a string and returns a new copy of that string that has a bunch of exclamation points at the end". Here is how we would write this in the console manually if we weren't using a function:
console
The expression string + '!!!!' returns a new string and our variable called string stays the same as before (since we never updated it to anything else with =).
Let's use our function instead of doing it manually. First, paste the function into the console and then call the function by passing in a string:
console
You could also call the same function by passing in a variable that points to a string (in the above example we just typed the string straight in there as a value instead of saving it to a variable first):
console
The line makeMoreExciting(sentence) is equivalent to saying sentence + '!!!!'. What if we wanted to modify in-place (aka update) the value of sentence? Simply save the return value of the function back into our sentence variable:
var sentence = "time for a nap"
sentence = makeMoreExciting(sentence)
Now sentence will have the exclamation marks in it! Note that you only have to use var when you are initializing a variable — the first time you ever use it. After that you shouldn't use var unless you want to re-initialize (reset/clear/empty) the variable.
What would happen if we took out the return statement in our function?
console
Why is sentence empty? Because functions return undefined by default! You can choose to return a value by returning something. Functions should take in a value and, if they change the value or create a new value that is supposed to be used later, return a value (fun fact: a fancy term for this style is functional programming). Here is another function that doesn't return anything but instead uses a different method to show us the output:
function yellIt(string) {
string = string.toUpperCase()
string = makeMoreExciting(string)
console.log(string)
}
This function, yellIt, uses our previous function makeMoreExciting as well as the built-in String method toUpperCase. Methods are just a name for a function when it belongs to something — in this case toUpperCase is a function that belongs to String so we can refer to it as either a method or a function. makeMoreExciting on the other hand doesn't belong to anyone so it would be technically incorrect to refer to it as a method (confusing, I know).
The last line of the function is another built-in that simply takes in any values that you give it and prints them out into the console.
console
So is there something wrong with the above yellIt function? It depends! Here are the two major types of functions:
functions that modify or create values and return them
functions take in values and perform some action that cannot be returned
console.log is an example of the second type of function: it prints things out to your console — an action that you can see with your eyes but that cannot be represented as a JavaScript value. My own rule of thumb is to try to keep the two types of functions separate from each other, so here's how I would rewrite the yellIt function:
function yellIt(string) {
string = string.toUpperCase()
return makeMoreExciting(string)
}
console.log(yellIt("i fear no human"))
This way yellIt becomes more generic, meaning it only does one or two simple little things and doesn't know anything about printing itself to a console — that part can always be programmed later, outside the function definition.
# Loops
Now that we have some basic skills under our belt (Author's note: do cats even wear belts?) we can start being lazy. What?! Yes, that's right: programming is about being lazy. Larry Wall, inventor of the Perl programming language, called laziness the most important virtue of a good programmer. If computers didn't exist you would have to do all sorts of tedious tasks by hand, but if you learn to program you can lay in the sun all day while a computer somewhere runs your programs for you. It is a glorious lifestyle filled with relaxation!
Loops are one of the most important ways to harness the power of a computer. Remember Underscore.js from earlier? Make sure you have it loaded in the page (remember: you can just hit the up arrow on your keyboard a few times and then hit Enter to load it in again if you need to) and try copy/pasting this into your console:
function logANumber(someNumber) {
console.log(someNumber)
}
_.times(10, logANumber)
This code uses the times method of Underscore which takes in 1 number and 1 function and then starts from 0 and for 10 steps counts up by 1, calling the function with the number each step of the way.
console
If we were to manually write out what times is doing in the above code it would look like this:
logANumber(0)
logANumber(1)
logANumber(2)
logANumber(3)
logANumber(4)
logANumber(5)
logANumber(6)
logANumber(7)
logANumber(8)
logANumber(9)
But cats refuse to do unnecessary manual work like this so we must always ask ourselves, "am I doing this in the laziest way possible?".
So why is this called looping? Think of it like this: If we were to write out a list of 10 numbers (from 0 to 9) using a JavaScript Array it would look like this:
var zeroThroughTen = [0, 1, 2, 3, 4, 5, 6, 7, 8, 9]
What times really does is visit each number and repeat a task: in the example above the task was to call the logANumber function with the current number. Repeating tasks in this way is referred to as looping over the Array.
# Arrays
I've mentioned these a few times but let's spend a minute learning about them. Imagine you need to keep track of all your buddies. Well, an Array will do just fine. Think of an Array like a sorted list that you can keep tons of stuff in.
This is how you make one:
var myCatFriends = ["bill", "tabby", "ceiling"]
Sweet! Now you have a list of your cat buddies.
Elements (that is what you call a single item in an array) that are stored within arrays start at 0 and count up from there. So myCatFriends[0] returns bill and myCatFriends[1] returns tabby... etc etc.
To get buddies out of your brand new Array you can just access an element directly like so:
console.log(myCatFriends[0])
console
If you made a brand new cat friend at the hippest cat club the other night and you want to add them to your list it is super simple: myCatFriends.push("super hip cat").
To check that the new cat made it into your array you can use .length:
console
Notice how push returned the length? Handy! Also take note that arrays will always preserve ordering which means they will remember the order in which you added or defined things. Not everything in JavaScript preserves ordering so remember this special property of Arrays!
# Objects
Arrays are good for lists, but for other tasks they can be hard to work with. Consider our array of cat friends. What if you also wanted to store more than just names?
var myCatFriends = ["bill", "tabby", "ceiling"]
var lastNames = ["the cat", "cat", "cat"]
var addresses = ["The Alley", "Grandmas House", "Attic"]
Sometimes it is nice to have all of the addresses or names in one variable. But sometimes you have a cat in mind, let's say Bill, and you just want to look up that cat's address. With arrays it takes a lot of work because you can't just say 'hey array, give me Bill's address' because 'Bill' is in one array and his address is in a totally different array.
console
This can be brittle because if our arrays change and we add a new cat to the beginning we would have to also update our billsPosition variable to point to the new location of Bill's information in the arrays! Here is a easier to maintain way to store information like this using objects:
var firstCat = { name: "bill", lastName: "the cat", address: "The Alley" }
var secondCat = { name: "tabby", lastName: "cat", address: "Grandmas House" }
var thirdCat = { name: "ceiling", lastName: "cat", address: "Attic" }
Why would we do it this way? Because now we have a variable for each cat that we can use to get that cats values in a more convenient and readable way.
console
You can think of Objects like keys on a keyring. Each one is for a specific door and if you have nice labels on your keys you can open doors very fast. In fact, the things on the left hand side of the : are called keys (are also known as properties) and the things on the right hand side are values.
// an object with a single key 'name' and single value 'bill'
{ name: 'bill' }
So why would you ever use arrays if you can just put your data in objects? Because objects don't remember the order of the keys that you set. You might enter in an object like this:
{ date: "10/20/2012", diary: "slept a bit today", name: "Charles" }
But the computer could give it back to you like this:
{ diary: "slept a bit today", name: "Charles", date: "10/20/2012" }
Or like this!
{ name: "Charles", diary: "slept a bit today", date: "10/20/2012" }
So you can't ever trust the order of keys in objects. If you wanna get REALLY fancy you can make an array filled with objects, or an object filled with arrays!
var moodLog = [
{
date: "10/20/2012",
mood: "catnipped"
},
{
date: "10/21/2012",
mood: "nonplussed"
},
{
date: "10/22/2012",
mood: "purring"
}
]
// ordered from least to most favorite
var favorites = {
treats: ["bird sighting", "belly rub", "catnip"],
napSpots: ["couch", "planter box", "human face"]
}
When you combine different things like this you are making data structures, just like legos!
# Callbacks
Callbacks aren't really a feature of JavaScript like Object or Array, but instead just a certain way to use functions. To understand why callbacks are useful you first have to learn about asynchronous (often shortened to async) programming. Asynchronous code by definition is code written in a way that is not synchronous. Synchronous code is easy to understand and write. Here is an example to illustrate:
var photo = download('http://foo-chan.com/images/sp.jpg')
uploadPhotoTweet(photo, '@maxogden')
This synchronous pseudo-code downloads an adorable cat photo and then uploads the photo to twitter and tweets the photo at @maxogden. Pretty straightforward!
(Author's note: I @maxogden do happily accept random cat photo tweets)
This code is synchronous because in order for photo to get uploaded to the tweet, the photo download must be completed. This means that line 2 cannot run until the task on line 1 is totally finished. If we were to actually implement this pseudo-code we would want to make sure that download 'blocked' execution until the download was finished, meaning it would prevent any other JavaScript from being executed until it finished, and then when the download completes it would un-block the JavaScript execution and line 2 would execute.
Synchronous code is fine for things that happen fast, but it's horrible for things that require saving, loading, downloading or uploading. What if the server you're downloading the photo from is slow, or the internet connection you are using is slow, or the computer you are running the code on has too many youtube cat video tabs open and is running slowly? It means that it could potentially take minutes of waiting before line 2 gets around to running. Meanwhile, because all JavaScript on the page is being blocked from being run while the download is happening, the webpage would totally freeze up and become unresponsive until the download is done.
Blocking execution should be avoided at all costs, especially when doing so makes your program freeze up or become unresponsive. Let's assume the photo above takes one second to download. To illustrate how long one second is to a modern computer, here is a program that tests to see how many tasks JavaScript can process in one second.
function measureLoopSpeed() {
var count = 0
function addOne() { count = count + 1 }
// Date.now() returns a big number representing the number of
// milliseconds that have elapsed since Jan 01 1970
var now = Date.now()
// Loop until Date.now() is 1000 milliseconds (1 second) or more into
// the future from when we started looping. On each loop, call addOne
while (Date.now() - now < 1000) addOne()
// Finally it has been >= 1000ms, so let's print out our total count
console.log(count)
}
measureLoopSpeed()
Copy-paste the above code into your JavaScript console and after one second it should print out a number. On my computer I got 8527360, approximately 8.5 million. In one second JavaScript can call the addOne function 8.5 million times! So if you have synchronous code for downloading a photo, and the photo download takes one second, it means you are potentially preventing 8.5 million operations from happening while JavaScript execution is blocked.
Some languages have a function called sleep that blocks execution for some number of seconds. For example here is some bash code running in Terminal.app on Mac OS that uses sleep. When you run the command sleep 3 && echo 'done sleeping now' it blocks for 3 seconds before printing out done sleeping now.
console
JavaScript doesn't have a sleep function. Since you are a cat you are probably asking yourself, "Why am I learning a programming language that does not involve sleeping?". But stay with me. Instead of relying on sleep to wait for things to happen the design of JavaScript encourages use of functions instead. If you have to wait for task A to finish before doing task B, you put all of the code for task B into a function and you only call that function when A is done.
For example, this is blocking-style code:
a()
b()
And this is in a non-blocking style:
a(b)
In the non-blocking version b is a callback to a. In the blocking version a and b are both called/invoked (they both have () after them which executes the functions immediately). In the non-blocking version you will notice that only a gets invoked, and b is simply passed in to a as an argument.
In the blocking version, there is no explicit relationship between a and b. In the non-blocking version it becomes a's job to do what it needs to do and then call b when it is done. Using functions in this way is called callbacks because your callback function, in this case b, gets called later on when a is all done.
Here is a pseudocode implementation of what a might look like:
function a(done) {
download('https://pbs.twimg.com/media/B4DDWBrCEAA8u4O.jpg:large', function doneDownloading(error, png) {
// handle error if there was one
if (err) console.log('uh-oh!', error)
// call done when you are all done
done()
})
}
Think back to our non-blocking example, a(b), where we call a and pass in b as the first argument. In the function definition for a above the done argument is our b function that we pass in. This behavior is something that is hard to wrap your head around at first. When you call a function, the arguments you pass in won't have the same variable names when they are in the function. In this case what we call b is called done inside the function. But b and done are just variable names that point to the same underlying function. Usually callback functions are labelled something like done or callback to make it clear that they are functions that should be called when the current function is done.
So, as long as a does it's job and called b when it is done, both a and b get called in both the non-blocking and blocking versions. The difference is that in the non-blocking version we don't have to halt execution of JavaScript. In general non-blocking style is where you write every function so that it can return as soon as possible, without ever blocking.
To drive the point home even further: If a takes one second to complete, and you use the blocking version, it means you can only do one thing. If you use the non-blocking version (aka use callbacks) you can do literally millions of other things in that same second, which means you can finish your work millions of times faster and sleep the rest of the day.
Remember: programming is all about laziness and you should be the one sleeping, not your computer.
Hopefully you can see now that callbacks are just functions that call other functions after some asynchronous task. Common examples of asynchronous tasks are things like reading a photo, downloading a song, uploading a picture, talking to a database, waiting for a user to hit a key or click on someone, etc. Anything that takes time. JavaScript is really great at handling asynchronous tasks like these as long as you take the time to learn how to use callbacks and keep your JavaScript from being blocked.
The end!
This is just the beginning of your relationship with JavaScript! You can't learn it all at once, but you should find what works for you and try to learn all of the concepts here.
I'd recommend coming back again tomorrow and going through the entire thing again from the beginning! It might take a few times through before you get everything (programming is hard). Just try to avoid reading this page in any rooms that contain shiny objects . . . they can be incredibly distracting.
Got another topic you wanna see covered? Open an issue for it on github.
# Recommended reading
JavaScript For Cats skips over lots of details that aren't important for getting started (cats are not known for their attention spans), but if you feel like you need to dive in deeper then check these out:
NodeSchool.io is a community driven, open source educational software that teaches various web development skills in an interactive, self-guided format. I helped make NodeSchool! Sadly it features fewer cats than this page.
Eloquent Javascript is a free book that teaches you JavaScript! It's pretty good! Especially the chapter on values, variables, and control flow
Mozilla's JavaScript Guide also has a pretty sweet intro chapter called values, variables and literals
standard JS Style Guide is a "zero configuration" linter for JS style that I use
Let's Write Code by @shama a great series of YouTube coding tutorials made by a friend of mine
# Satisfied customers
satisfied customer
satisfied customer
satisfied customer
satisfied customer
satisfied customer
JSForCats.com is a labor of love and work in progress by @maxogden. If you would like to contribute and make this tutorial better there is a Github repo right over here.
console
-

@ 8cb60e21:5f2deaea
2024-09-06 22:23:03
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 472f440f:5669301e
2024-09-06 21:56:48
I had the pleasure of sitting back down with Will Reeves, Founder and CEO of Fold, on TFTC last week to discuss Fold's journey from a startup to (soon to be) a publicly listed company. I particularly liked this conversation because it was a great lens into the grit it takes to run a successful bitcoin company.
https://fountain.fm/episode/1FrspxmpK5bsoReGx73n
Building a successful company is extremely hard in its own right. Building a successful bitcoin company is significantly harder considering the fact that you're building a company in parallel with a nascent and volatile monetary asset that is monetizing in real time. Bitcoin adoption comes in waves. People flood in when the price is ripping and fade out when the price corrects and goes into a multi-year bear market before the tide comes back in. This means that your potential user base is expanding and contracting more than it would be in other industries. As a company you need to be able to absorb the incoming waves of new adopters and then capture and retain the users who stick around for the bear market.
To do this correctly, a founder and their team needs to thread many needles. First, can you assemble a team that can actually build something? Second, can you bring a product to market that people actually use because it provides value to them? Third, can you stick out against the crowd? So on and so forth.
One of the most important aspects of building a bitcoin company during bitcoin's monetization phase is timing. There are many great ideas that people have in terms of companies, products and tools that can built using bitcoin. There are sci-fi futures that can be built today on bitcoin if people really wanted to.
The problem that arises is that adoption and understanding of bitcoin are at a point where, even though a functional product could be brought to market, it won't be adopted by a large number of people because there 1.) aren't enough people who would understand how to use it and 2.) for the people who do understand how to use it and could benefit from it, the universe of people they can interact with using that product is minuscule.
Timing is everything. And I think Fold nailed the timing of their product. Allowing people to passively stack sats by offering a product that enables them to go about their daily spending and get sats back instead of cash back rewards is a great first-touch bitcoin experience. Once Fold found their sticky user base and perfected their sats back experience, they began expanding their product offering to provide their users with more bitcoin services. Buy/sell bitcoin in-app, bill pay for sats back, and more. They'll eventually roll out a credit card and additional financial services. Start simple, provide something of value, nail the timing and then expand from there. That seems to be the recipe.
For any founders in the space reading this, I highly recommend you listen to the episode. Particularly for the advice Will gives about knowing when to sprint on product and when to lean into growth. Bear markets are for building and bull markets are for casting the widest net possible and capturing as many new users as possible.
At Ten31 we are extremely proud to back Fold and a number of other companies in the bitcoin space that understand the intricacies described above. We work with some of the best founders in the world. Founders who know how to eat glass with the best of them. Bitcoin can be a cruel mistress and no one knows that more intimately than the founders building bitcoin companies.
---
Final thought...
The NFL having a week 1 game in Brazil should get Roger Godell fired.
Enjoy your weekend, freaks.
-

@ e83b66a8:b0526c2b
2024-09-06 19:16:04
The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud.
Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data.
There is a different way.
NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol.
The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms.
Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid.
Secondly as a user, you don’t have an account, you have a private key which is used to secure your data.
Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key.
Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays.
All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it.
Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key.
Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content.
Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions.
Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant.
As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models.
The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not.
NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment.
From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed.
While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops.
If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here:
https://primal.net/downloads
It will create a private key for you and setup a Bitcoin wallet.
Once you have done this you can visit me here:
nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n
If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already.
NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here:
nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Or you can see his account like this:
https://primal.net/jack
Edward Snowden is also on the platform and you can find him here:
https://primal.net/Snowden
NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation.
Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/
Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus
or Amethyst for Android: https://nostrapps.com/amethyst
The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it.
Some of the more interesting projects right now are:
https://www.0xchat.com/#/ – Private messaging – think WhatsApp
https://zap.stream/ – Video streaming
https://fountain.fm/ – Podcasting
https://wavlake.com/ – Music streaming
https://shopstr.store/ – Online shop
https://npub.pro/ – Website creation tool
https://nostr.build/ – Media and file storage
https://relay.tools/ – Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user – Creator tools
Remember, the same keys you created for Primal can be used across the whole ecosystem.
If you want to see some of the other apps that have been built on the NOSTR protocol visit:
https://nostrapps.com/
-

@ ffd375eb:4529ed08
2024-09-06 15:39:31
## Chef's notes
Watch the video 🇫🇷: https://youtu.be/cYl4Lb0vbyc
## Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 3 months
- 🍽️ Servings: Many
## Ingredients
- 1 fennel bulb
- 1 large onion
- 3 garlic cloves
- 1/2 tsp salt per fennel bulb
- 1 tbsp turmeric powder per fennel bulb
- 1 tbsp oil per fennel bulb
- 1 tsp black pepper per fennel bulb
- 1 tbsp honey per fennel bulb
## Directions
1. Thinly slice the fennel bulb, onion, and garlic using a mandoline slicer.
2. In a bowl, mix the sliced fennel, onion, garlic, and salt. Let sit for a bit to allow the salt to act on the ingredients.
3. In a separate bowl, mix the turmeric, oil, black pepper, and honey to make a sauce.
4. Combine the fennel, onion, garlic mixture with the turmeric sauce and mix well.
-

@ 3bf0c63f:aefa459d
2024-09-06 12:49:46
# Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-

@ 6bae33c8:607272e8
2024-09-06 08:14:27
An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes.
In any event, it was an okay game, not great, but there were some interesting takeaways.
- Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff.
- Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask.
- Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.)
- Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more.
- Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot.
- Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown.
- Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though.
- Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game.
- Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role.
- After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG.
- You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night.
-

@ c7eadcf0:7821e562
2024-09-06 00:10:23
Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck.
Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis.
Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin.
This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite?
Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out.
-

@ 472f440f:5669301e
2024-09-05 22:25:15
[https://x.com/parkeralewis/status/1831746160781938947]()
Here's a startling chart from an American staple, Walgreens. The convenience store and pharmacy chain has seen its stock price plummet by more than 67% this year and by more than 90% from its all time high, which was reached in 2015.
The combination of the COVID lock downs and the lax laws around theft that followed were materially detrimental to Walgreens business. The crux of their problem at the moment, however, is a double whammy of those disruptions in their business coupled with the "higher for longer" interest rate policy from the Fed over the last couple of years. As Tuur points out in the tweet above, Walgreens has $34B in debt, which means they definitely have significant interest rate payments they need to make on a monthly basis. Tuur also points out that Walgreens has very little cash compared to their debt obligations. Let's take a look at their balance sheet as of May of this year.
![https://www.tftc.io/content/images/2024/09/Screenshot-2024-09-05-at-3.59.46-PM.png]()
Less than $1B in cash for $34B debt with $67.56B in total liabilities. Even worse, their cash balance was drained by more than 27% over the course of the year between May 2023 and May 2024. As you may notice their total assets fell by more than 15% over the same period. This is because Walgreens understands the dire financial straits it finds itself in and has begun shutting down thousands of their locations across the country.
![https://www.tftc.io/content/images/2024/09/Screenshot-2024-09-05-at-4.49.58-PM.png]()
The recent efforts of Walgreens to sell off their assets to raise cash to pay down their debts seem to be completely ineffective as their cash balance is falling faster than their total assets, which is falling 7x faster than their total liabilities. These numbers are most definitely going to get worse as cascading sell pressure in commercial real estate markets (which is the bucket that Walgreens locations fall into) drive down the value of their assets. Leaving them with less cash to pay down their debts as time goes on.
To make matters worse, it puts the institutions that lent money to Walgreens in a terrible position. How many commercial and investment banks has Walgreens tapped to fund their operations with expensive debt? How exposed to Walgreens is any individual lender? Could a default on some or all of their loans catch these financial institutions off sides? If it isn't Walgreens that pushes them off sides, how many more bad borrowers would it take to push them off sides?
As our good friend Parker Lewis points out, the only way the hemorrhaging can be stopped is if the Federal Reserve and Federal Government step in with bail outs in the form of massive liquidity injections via quantitative easing and other emergency measures. On top of this, the Fed and the Federal Government find themselves in a classic catch-22. If they let Walgreens fall into bankruptcy it could set off a domino effect that could exacerbate inflation. Riteaid, a similar retail convenience store and pharmacy chain, filed for bankruptcy last October and is still wading its way through that process. Part of that process has been shuttering many of their storefronts. One has to imagine that since Walgreens and Riteaid are having these problems, some of their other competitors must be feeling the pain as well. If enough of these convenience stores, which tens of millions of Americans depend on for everyday goods, find themselves in a position where they have to shut down their stores it could lead to a supply crunch. People will obviously not be able to get their goods from Riteaid or Walgreens and will flee to alternatives, exacerbating the stress on their supplies, which will drive prices higher.
This is a catch-22 because the only way to avoid this mad dash for consumer goods in the midst of a convenience store Armageddon is to re-introduce ZIRP and flood the market with freshly printed dollars, which will drive prices up as well.
Talk about a rock and a hard place. You better get yourself some bitcoin.
---
Final thought...
Zach Bryan radio crushes.
-

@ acc925af:db9fb0bb
2024-09-05 20:26:50
While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good
**Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:**
# Prerequisites:
1. Twitter Developer Account
2. Nostr Wallet with NWC support (e.g., Alby, Nostrify)
3. Twitter API credentials (API key, API secret key, Access token, Access token secret)
4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library)
### Step 1: Set up Twitter API credentials
> Create a Twitter Developer account and obtain API credentials
> Install Tweepy using pip: pip install tweepy
### Step 2: Connect Nostr Wallet using NWC
> Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify)
> Set up the wallet and obtain the NWC credentials (e.g., public key, private key)
### Step 3: Create a Python script
> Import Tweepy and nostr-client libraries
> Authenticate with Twitter API using Tweepy
> Connect to Nostr Wallet using NWC credentials
> Define a function to send 21 satoshis for every like
> Use Tweepy to stream likes and trigger the payment function
`Python` script:
```
import tweepy
from nostr_client import Client
# Twitter API credentials
twitter_api_key = "YOUR_API_KEY"
twitter_api_secret_key = "YOUR_API_SECRET_KEY"
twitter_access_token = "YOUR_ACCESS_TOKEN"
twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET"
# Nostr Wallet NWC credentials
nwc_public_key = "YOUR_NWC_PUBLIC_KEY"
nwc_private_key = "YOUR_NWC_PRIVATE_KEY"
# Set up Tweepy
auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key)
auth.set_access_token(twitter_access_token, twitter_access_token_secret)
api = tweepy.API(auth)
# Set up Nostr Client
nwc_client = Client()
nwc_client.connect(nwc_public_key, nwc_private_key)
# Define payment function
def send_satoshis():
# Create a new Nostr event with 21 satoshis
event = nwc_client.create_event(21)
# Send the event to the Nostr network
nwc_client.send_event(event)
# Stream likes and trigger payment function
class LikeStream(tweepy.StreamListener):
def on_like(self, like):
send_satoshis()
stream = tweepy.Stream(auth, LikeStream())
stream.filter(track=["likes"])
```
##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._
originally posted at https://stacker.news/items/673795
-

@ e968e50b:db2a803a
2024-09-05 19:33:33
ATTENTION PARENTS!
I have revamped my LNBITS [bitcoin piggy bank](http://bitcoinpiggybank.vercel.app) so you don't need to deploy it yourself. Check it out at http://bitcoinpiggybank.vercel.app. All you need now is a LNBITS wallet. I've deployed a website that you can just log into with that and nothing else. I'm thinking about actually renting out my own domain for this one if people find it useful.
https://www.youtube.com/watch?v=X-MNqJiLCM4
Teach your kids about sound money while they're actually stacking sats and using a fun interface.
originally posted at https://stacker.news/items/673739
-

@ 469fa704:2b6cb760
2024-09-05 15:06:49
## The Evolution of Web 3.0: Bitcoin's Role in Decentralizing the Internet
### Introduction to Web 3.0
Web 3.0, often referred to as the decentralized web, represents the next phase in the evolution of the internet. Unlike its predecessors, Web 3.0 aims to redistribute control from centralized entities back to individual users through technologies like blockchain, cryptocurrencies, and decentralized applications (dApps). This shift promises a more democratic internet where users control their data, identity, and digital destiny.
## The Bitcoin Protocol: A Foundation for Web 3.0
### Bitcoin's Influence on Decentralization
Bitcoin, introduced in 2008, can be seen as a precursor to Web 3.0 due to its decentralized nature. The Bitcoin protocol introduced the world to blockchain technology, a decentralized ledger that records all transactions across a network of computers. This technology underpins Web 3.0's ethos by:
* **Promoting Decentralization**: Bitcoin's network operates without a central authority, showcasing how internet services could run on similar principles, reducing the power of centralized tech giants.
* **Enhancing Security and Privacy**: Through cryptographic means, Bitcoin ensures that transactions are secure and pseudonymus, a feature integral to Web 3.0's vision of user-controlled data.
### Scalability and Functionality Challenges
However, Bitcoin's protocol wasn't designed on the base layer with the complex applications of Web 3.0 in mind. Its primary function as a digital currency means:
* **Scalability Issues**: Bitcoin's blockchain has limitations in transaction speed and volume, which might not suffice for a fully realized Web 3.0 environment where millions of micro-transactions could occur seamlessly.
* **Limited Smart Contract Capabilities**: Bitcoin's scripting language isn't as versatile as platforms like Ethereum, which are designed to support a broader range of decentralized applications.
### Expanding Bitcoin's Role with Layer 2 Solutions
To bridge these gaps, developers are working on Layer 2 solutions like the Lightning Network for faster transactions, and projects like Stacks aim to bring smart contract functionality directly to Bitcoin. These innovations suggest that while Bitcoin might not be the sole backbone of Web 3.0 yet, it can significantly contribute to its infrastructure. In the long term, the question is whether we need more than one network, I mean, we don't have multiple Internets today. The market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that.
## Web 3.0 Beyond Bitcoin
### A Broader Blockchain Ecosystem
At the moment Web 3.0 encompasses by far more than just Bitcoin. It includes:
* **Ethereum and Smart Contracts**: Ethereum's introduction of smart contracts has been pivotal, allowing for decentralized applications that can interact in complex ways, far beyond simple transactions.
* **Other Blockchains**: Platforms like Solana, Sui, and Near are gaining traction for their high throughput and lower costs, addressing some of Bitcoin's limitations on the base layer.
## The Cultural and Economic Shift
The move towards Web 3.0 isn't just technological but cultural. There's a growing sentiment, reflected in posts on platforms like X, that users are ready for a change where they own their digital presence. Here's some background based on general knowledge and trends up to 2024:
### Cultural Shift:
* **Distrust in Centralized Institutions**: There's been a growing distrust in traditional centralized institutions like banks, governments, and large corporations. This distrust stems from various scandals, data breaches, privacy concerns, and perceived inefficiencies or corruption. Posts on platforms like X or even more on Nostr reflect this sentiment, where users often discuss the diminishing trust in these institutions.
* **Rise of Individual Empowerment**: Culturally, there's a move towards empowerment of the individual, facilitated by technology. Social media, blockchain, and other decentralized technologies give individuals tools to bypass traditional gatekeepers in finance, media, and more. This shift champions the idea that individuals should have more control over their data, finances, and digital identity.
* **Identity and Community**: Decentralization also touches on identity politics and community governance. There's a trend towards localism or regionalism where communities seek more control over their governance, which can be seen in movements for local autonomy or even secessionist sentiments in various parts of the world.
* **Cultural Movements**: Movements like the maker culture, DIY (Do It Yourself), open-source software, and even the gig economy reflect a cultural shift towards decentralization where individuals or small groups can produce, create, or work independently of large entities.
### Economic Shift:
* **Decentralized Finance (DeFi)**: DeFi represents one of the most tangible shifts, aiming to recreate and potentially improve financial systems outside of traditional banking. This includes lending, borrowing, and earning interest in a trustless, permissionless environment, primarily using blockchain technology.
* **Cryptocurrencies and Tokenization**: The rise of cryptocurrencies like Bitcoin and Ethereum symbolizes a move away from centralized monetary systems. Tokenization of assets, from art (NFTs - Non-Fungible Tokens) to real estate, embodies this shift, allowing for fractional ownership and reducing the barriers to investment.
* **Globalization vs. Localism**: While globalization has interconnected economies, there's a counter-trend where economic decentralization supports local economies. This can be seen in the push for local currencies, community-supported agriculture, or local energy production like solar microgrids.
* **Work and Employment**: The gig economy, remote work, and digital nomadism are part of this economic shift. Platforms enabling freelance work decentralize employment, moving away from traditional office environments and 9-to-5 jobs.
### General Observations:
* **Technology as an Enabler**: Blockchain, the internet, and advancements in communication technology are pivotal in this shift. They provide the infrastructure necessary for decentralization to occur at scale.
* **Political Implications**: Economically, this shift maybe challenges existing power structures, potentially leading to regulatory battles as seen with cryptocurrencies. Culturally, it might lead to a redefinition of nationalism, community, and individual rights in the digital age.
* **Challenges**: Despite its promise, decentralization faces hurdles like scalability issues, regulatory pushback, the digital divide, and the potential for new forms of centralization (e.g., large crypto exchanges becoming new central authorities).
## Conclusion: Bitcoin's Place in Web 3.0
Bitcoin's protocol ignited the spark for a decentralized internet, but Web 3.0 is evolving into a multifaceted ecosystem where Bitcoin might play a crucial, though not yet exclusive, role. The integration of Bitcoin with newer technologies and platforms could see it becoming a fundamental layer in the Web 3.0 stack, particularly in areas of value transfer and as a store of value within decentralized finance (DeFi).
As we progress, the synergy between Bitcoin's proven security and stability, combined with the innovation of other blockchain technologies, might just be the blend needed for Web 3.0 to achieve mainstream adoption, ensuring the internet becomes more open, secure, and user-centric.
*As stated before, the market will probably decide in favor of the strongest and most secure network, and **Bitcoin** is by far that.*
-

@ 9977c3ad:43a20d63
2024-09-05 11:21:09
## Details
- 🍽️ Servings: 2
## Ingredients
- 1 cup Jasmine rice
- 1 Tbsp. lavender flowers, crushed with mortar and pestle
- 1/4 cup apple cider vinegar
- 2 Tbsp. fine cane sugar
- 2 Tbsp. honey
- 1 sprig rosemary
- 1/4 tsp angostura bitters
- 1/2 cup blackberries
- 1/2 cup blueberries
- 4 cups trimmed and quartered shiitake mushrooms
- 1 tsp fresh coriander crushed
- 1/4 tsp fresh cumin ground
- 1/2 tsp red pepper flakes
- 3 sprigs of thyme
- 2 Tbsp. olive oil
- 1 tsp soy sauce
- 1 cup creamy coconut milk
## Directions
1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes.
2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside.
3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
-

@ 472f440f:5669301e
2024-09-04 22:54:11
For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam.
However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash.
Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin.
BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now.
https://strike.me/blog/bolt12-offers/
As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented.
Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology".
The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack.
This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential.
Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust.
Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin.
---
Final thought...
Vibes are high.
-

@ 572aa884:e266a569
2024-09-04 19:46:40
# STAR TREK TNG: INCOMPATIBLE IDEALS
*by Luke Parker*
---
**Premise**: *This screenplay is for an episode of Star Trek: The Next Generation, set near the end of Season 7. It imagines a first contact encounter between Picard’s Enterprise and a fully Anarcho-Capitalist planet with no government nor belief in authority.*
---
**Scene 1: Bridge**
---
*Exterior views of the Starship Enterprise give way to Captain Jean-Luc Picard standing at his command station on the bridge, his gaze steady and contemplative as he records his log.*
**Picard:** (voiceover) "Captain's log, Stardate 48881.4. We were on our way to Deep Space 9 to provide support for the upcoming Bajoran elections when we received an audio-only distress call from a person on the planet Anarak, just outside of Cardassian space. The planet has yet to be contacted by the Federation, and in fact very little is known about it other than how it has a highly unusual social structure; one that appears to function without any form of central government or hierarchical leadership. It is a society that, despite its relatively high level of technological sophistication, has yet to achieve warp capability. The message is urgently requesting help from any peaceful civilization in range to defend his people against Cardassian invaders. It is difficult to imagine even the Cardassians violating the Prime Directive in such a manner. We are changing course to investigate."
*Picard finishes his log entry and looks up, his expression thoughtful. The rest of the bridge crew is attentive with the memory of the Cardassain conquest of Bajor fresh in their minds.*
**Data:** [turning from his console to face Picard] "Captain, Starfleet's lone anthropological record on Anarak indicates that it has a relatively large population and is advanced in various scientific fields. However, there are no reports of warp capability nor a leadership structure for us to contact there. Their society’s structure might challenge our usual protocols for contact."
**Riker:** [with a hint of curiosity] "An advanced society with no central government? That's a first."
**Picard:** [nodding] "Indeed, Number One. The distress call came from an individual named Bas T'yat, who identifies himself only as an entrepreneur. Our intelligence suggests that Anarak's society is structured in a way that is not only hostile to hierarchies but completely devoid of any form of leadership or authority. They seem to operate on a principle of total autonomy. This would seem to indicate an absence of a planetary defense system."
**Troi:** [thoughtful, with concern] "Without a central authority, how do they respond to any external threats? A society like this could be quite vulnerable to more aggressive powers, like the Cardassians."
**Picard:** [grimly] "It seems that may already be the case. The distress signal implied that a hostile force, likely Cardassian, has targeted them. Without a unified defense, they could be easy prey."
**Worf:** [sternly] "If the Cardassians are involved, Captain, they will not hesitate to exploit such a weakness. We must be prepared for hostilities."
**Data:** [analyzing the implications] "However, the lack of formal governance could complicate any assistance we offer. Without a government to negotiate with, we may face challenges in determining how to intervene appropriately."
**Picard:** [resolute, yet cautious] "We will treat Anarak as we would any other planet sending a distress call, regardless of their social structure. However, we must tread carefully. If we arrive to find Cardassians engaged in hostile acts, we may be forced to intervene. But in Federation space, our priority remains the protection of life and the maintenance of Federation principles."
*The bridge crew exchanges looks of determination, each officer understanding the complexities of the mission ahead.*
**Picard:** [decisive, raising his voice slightly] "Set course for Anarak. Engage at warp seven."
**Data:** [acknowledging] "Course plotted, Captain. Engaging warp seven."
*The familiar hum of the warp engines intensifies as the stars on the viewscreen stretch into streaks of light, and the Enterprise leaps into warp, speeding towards the strange planet and the potential conflict awaiting them.*
---
**Scene 2: Bridge**
---
*The Enterprise emerges from warp above the planet Anarak, the planet’s blue-green surface appearing deceptively peaceful below.*
**Worf:** [at tactical, scanning the area] "Captain, no alien vessels are currently in the vicinity, only artificial satellites. However, I'm detecting signs of recent battle on the planet's surface."
**Picard:** [moving closer to Worf's station] "Specify, Lieutenant."
**Worf:** [analyzing the data] "There is minor damage to infrastructure in multiple locations, consistent with Cardassian disruptor fire. Several structures show signs of targeted attacks, but the damage is localized and not extensive."
**Data:** [at the science station] "Captain, I'm detecting several warp signatures leading to and from the planet. However, one of these signatures does not match any known Cardassian engine profile and is not in our warp signature database."
**Riker:** [concerned, looking to Picard] "An unknown vessel in the area right around the time of a Cardassian attack? This could complicate matters."
**Troi:** [sensing the tension, her voice calm but alert] "Whoever they are, they may not have the best intentions. The people of Anarak could be more vulnerable than we initially thought."
*Picard ponders this information, his expression thoughtful yet wary. The bridge crew continues their scans, tension mounting as they try to make sense of the situation.*
**Worf:** [interrupting the silence] "Captain, we are being hailed from the surface."
**Picard:** [decisive, nodding] "On screen."
*The viewscreen flickers to life, revealing the image of a middle-aged man with a rugged, practical look. He exudes an air of cautious relief, though his eyes betray a deep-seated wariness.*
**Bas T'yat:** "Alien vessel, thank you for coming so quickly. My name is Bas T'yat, and I’m an entrepreneur and concerned family man. Please, can you tell me, are you an ally of the Cardassians?"
**Picard:** [calm and reassuring] "Mr. T'yat, I am Captain Jean-Luc Picard of the Federation starship Enterprise. I assure you, the Federation is not aligned with the Cardassians, although we have dealt with them before, and are aware of their transgressions."
**Bas T'yat:** [sighs in relief] "Thank goodness. We desperately need your help. An alien ship identifying itself as Cardassian has been harassing us for weeks. I fear they'll return soon, and we have little defense against their matter transportation technology. I'm a successful inventor and businessman, Captain. I have resources and tech that could be of value to your Federation, and I'm prepared to trade anything you want in order to help protect my people."
**Picard:** [curious, leaning slightly forward] "Tell me more about these attacks. What exactly have the Cardassians done?"
**Bas T'yat:** [his tone shifting to one of frustration mixed with guilt] "It started about a month ago. One of our companies, my own company, in fact, launched a new type of vessel that can travel faster than light using a warp field, the first one we've ever built. Within an hour of it's maiden voyage the Cardassians showed up. At first, they demanded to know who was in charge of the planet. They didn't like the answer they got: We are a free people and no one commands us."
**Riker:** [sharing a knowing glance with Picard] "A society without centralized leadership would be difficult for the Cardassians to understand or even tolerate."
**Bas T'yat:** [nodding] "That was my conclusion. They treated us like a lawless frontier, moving in to take whatever they wanted. They attacked our resource stockpiles, dematerialising and I assume stealing whatever they could before we even knew what was happening. Our ground-based defense missiles successfully took out their two smaller fighter crafts that came down into our sirspace, but we have no defense against their transporter technology. Their last visit was just a raid from orbit. They just grabbed what they could without even entering the atmosphere and left within minutes."
**Picard:** [thoughtful, with a hint of concern] "I see. There are widely-agreed-upon rules against this type of behavior, I assure you. However, since the Federation has never made contact with your people before now, we are unfamiliar with the proper etiquette for such a first encounter. How do you suggest we proceed safely for an official meeting?"
*Bas pauses, visibly perplexed by the concept of "official" procedures, his expression almost amused.*
**Bas T'yat:** [with a chuckle] "Official meeting? Captain, just come on down and park your craft outside my coordinates. My wife will make us all some refreshments."
**Picard:** [with a slight smile, yet maintaining formality] "We appreciate the hospitality, Mr. T'yat, but we prefer to beam down if that's acceptable to you. We can be there in a few minutes."
**Bas T'yat:** [nervous but agreeable] "Beam down? Uh, sure, that's fine. I was wondering if that technology worked on people. Love to see it in action."
**Picard:** [nodding respectfully] "Understood. I'll be down with a small team to meet you outside your building shortly. Picard out."
*The screen goes dark as the connection ends, leaving the bridge crew to process the encounter.*
**Riker:** [with a wry smile] "Drinks with the locals; sounds like fun."
**Troi:** [softly, but with insight] "He's nervous, but also hopeful. I'm sensing some hurt pride in him, too, Captain. This is likely the first time his people have ever had to reach out to anyone off-world for help. His pride may cloud his ability to fully grasp the dangers they’re facing."
**Picard:** [serious, standing up to address the crew] "On top of being an official first contact, the Cardassians have made this a very delicate situation. We must be prepared for anything. Counselor Troi, Data, and La Forge, you're with me. Number one, you have the bridge."
*The crew nods in understanding as the away team heads to the turbolift. The tension in the air is palpable as they ready themselves for what may be a challenging first contact and a possible hostile encounter with the Cardassians.*
---
**Scene 3: Bas T’yat’s Front Lawn**
---
*The team materializes on the surface of Anarak, just outside of a large, elegant house set in a lush, rural landscape. The area is a blend of modern luxury and natural beauty, though signs of recent damage are evident. Smoke still rises from a nearby hangar, the aftermath of the Cardassian attack clear in the smoldering ruins.
As the team takes in their surroundings, a group of locals approaches. At the forefront is Bas T'yat, flanked by a few colleagues. He's a middle-aged man with a commanding presence, dressed in practical yet fine clothing. His stride is confident, and his eyes sharp with the determination of a man used to getting what he wants. Bas’s face lights up with a mixture of curiosity and enthusiasm as he sees the away team.*
**Bas T'yat:** [warmly, holding his palms upwards and then extending one hand towards Picard in a greeting] "Captain Picard! Welcome to Anarak! I'm Bas T'yat. It is my honor to meet you."
**Picard:** [imitating the hand motion, with a polite smile] "The honor is ours, Mr. T'yat. Thank you for your hospitality. May our two peoples forever live in harmony."
*Bas gestures to the smoldering hangar in the distance, his tone tinged with frustration.*
**Bas T'yat:** [with a sigh] "That would be wonderful. I do wish the circumstances for your visit were better. [clenching his fists] That's my hangar over there, or what's left of it, anyway. The Cardassians destroyed it and the spacecraft I designed and built there. It was our first warp vessel, one that the whole world cheered on at launch just last month. We were going to colonize the asteroids with it."
**Geordi:** [To Picard, gesturing towards the wreckage] "If I may, Captain?"
**Picard:** "Certainly." [To Bas T'yat] "This is my head engineer, Commander Geordi La Forge."
**Geordi:** [stepping forward] "Mr. T'yat, if it's alright with you, I'd like to examine the wreckage. I might be able to determine if anything is salvageable."
**Bas T'yat:** [nodding, gesturing to a colleague] "Of course. Lar Kinn here is our chief pilot. He made the historic first flight and he'll take you to the hangar and help with anything you need."
*Geordi and Lar Kinn head towards the hangar, with Geordi hoping to confirm if this was the source of the warp signature detected in orbit. Meanwhile, Bas leads Picard, Troi, and Data toward his house. As they walk, Bas impatiently answers a few questions about his planet, his voice tinged with annoyance and concern.*
**Data:** “Mr. T’yat, if I may, I notice that your neighborhood’s infrastructure is well taken care of. If Anarak has no central authority of any kind, who is responsible for keeping the roads and infrastructure?”
**Bas T'yat:** ”Well, as a rule of thumb, if it’s on my land, I am. If it’s not on my land, then someone else is, but I may have to pay them to use it. They look so nice because we all get better insurance rates for keeping them that way.”
**Data:** “Curious. And who initiates larger projects like mass transportation and research?”
**Bas T'yat:** [slightly annoyed] “They are all risky endeavors taken by entrepreneurs like myself. Sometimes profits take decades to appear, but like with my new warp engine, I’m sure they’ll make me a huge fortune one day.” [turning to ensure Picard can hear him] "Anyway, I fear the Cardassians aren't done with us. They've stopped even trying to make demands of us, which makes me think they're planning something bigger. Perhaps a larger assault. We've been able to fend them off so far, but I have no clue how to defend against those transporter devices."
**Picard:** [impressed] "It is remarkable that your society, with no planetary defense force, was able to repel Cardassian military forces, even if only temporarily. Cardassian ships are known for their significant weapons and shields."
**Bas T'yat:** [with a hint of pride] "The people of Anarak are no strangers to defending themselves. We have numerous private protection agencies, each with advanced missile fortifications and other kinds of defenses to protect every inch of this planet. But these were designed to fend off terrorists or rival companies, not an alien invader."
*They reach the entrance to Bas's home. He pauses before entering, turning to Picard with a serious expression.*
**Bas T'yat:** [earnestly] "Captain, I'm prepared to trade for whatever defensive technology you can provide, especially something to counter the Cardassian's transporter technology. I am confident that our ground defenses can take out their shuttlecraft, but we're helpless against their ability to beam in and out at will."
*Picard pauses, his face reflecting the weight of his decision before he speaks.*
**Picard:** [in his most diplomatic tone] "Mr. T'yat, the Federation is committed to helping those in need, and we don't tolerate bullies. However, there are restrictions on the technology we can share, particularly weaponry. Also, the Federation's assistance often depends on whether a planet is on the path to becoming a member. We must ensure that our values align. In this case, a diplomatic approach might bring a far more lasting peace than simply escalating an arms race."
*Bas considers this, his optimism tinged with caution. The group moves into a large room with lots of seating where a warm drink much like tea is offered. Picard partakes graciously.*
**Bas T'yat:** [thoughtfully] "I see. Federation membership is... a complicated idea. I'm sure many heads of companies like myself would welcome it, but for the whole planet to become a singular member of any larger federation is hard to imagine. Our society values individual freedom above all else, and I'm not sure how compatible everyone here is with the Federation's ideals."
**Data:** "The benefits of Federation membership are considerable. Could not your people one day vote on the issue to see if a majority wants to join after taking ample time to research membership?"
**Bas T'yat:** [skeptically] "Voting is something that hasn't been done here for tens of thousands of years. We consider it to be archaic, a form of slavery of the minority. Honestly, I'm surprised your culture still practices it."
**Picard:** [nodding, a little embarrassed] "I see. Rest assured that we try to only vote on things that have every participant's full consent. You'll find that this is very common among the races you meet as your people start to explore the stars. But until then, know that the Federation's primary concern is the safety of everyone in Federation space, including your people."
*While inside Bas's home, Data discreetly connects to an open network connection, accessing Anarak's version of the internet called the Openlink. His eyes flicker left to right at an inhuman speed as he analyzes the planet's defenses and infrastructure.*
**Data:** [quietly, to Picard as he processes the data] "Captain, while there are many advanced technologies in the hands of individuals and companies, I find no evidence of any kind of unified military infrastructure. The defense efforts are completely decentralized, which will surely prove problematic in the event of a full-scale Cardassian invasion."
**Picard:** [grimly] "Given the Cardassians' history, we must prepare for the worst."
*Just then, Geordi returns from the hangar, his expression a mix of curiosity and concern.*
**Geordi:** "Captain, I've confirmed that Bas's ship was the source of the warp signature we detected. Unfortunately, the wreckage isn't salvageable. It could be a long time before Anarak returns to the stars."
**Bas T'yat:** [with a determined grin] "I wouldn't say that. My first flight was widely publicized. Lar Kinn and I are celebrities now. Hundreds of other companies are likely working on similar technology already. Some of us refer to it as 'the great space race,' with the goal of creating the first off-world colony, and my company is currently in the lead."
**Picard:** [with a slight smile, impressed by the resilience] "It seems the people of Anarak are not to be counted out yet. Your intrepid spirit will serve you well as Anarakans start exploring the Galaxy."
**Troi:** [warmly] "Your optimism is admirable, Mr. T'yat. But remember, resilience is strongest when combined with caution."
**Bas T'yat:** [nodding, appreciatively] "Wise words, Miss Troi. Hopefully with your help we'll be ready for whatever comes next."
**Picard:** [ready to leave] "This tea is delicious, thank you for your hospitality. Next I'll need to talk to my superiors at Starfleet headquarters before we can proceed any further. I'll be sure and pass your concerns and needs on to them and then we'll contact you again later today."
*The away team prepares to depart, with Bas expressing his thanks once more. As they beam back to the Enterprise, each member reflects on the unique challenges of Anarak.*
---
**Scene 4: Picard’s ready room**
---
*Minutes later, Captain Picard sits alone in his ready room, the vast starscape of space visible through the window behind him. His posture is straight, and the weight of the decision before him is clear in his eyes. He taps a command into his desk console, and the screen flickers to life with the familiar stern face of Vice Admiral Alynna Nechayev. Her image on the screen is as imposing as ever.*
**Picard:** [calmly, but with underlying urgency] "Admiral, I've just concluded a preliminary contact with a representative of Anarak, just a few light years this side of Cardassian space. The situation is more complex than anticipated. The planet is under threat from the Cardassians; specifically Gul Bankar, who's been making increasingly aggressive moves from orbit. Meanwhile, the society on Anarak is... unconventional. They have no central government, no formal leadership nor military structure. The entire planet operates under a decentralized, anarchic, commerce-based system."
**Nechayev:** [eyes narrowing] "Anarchists? No structure? That's not exactly an encouraging environment for a first contact, Jean-Luc.
**Picard:** “Admiral, they’ve managed to develop warp technology without either a government or military. It’s a remarkable feat, but one that leaves them vulnerable.”
**Nechayev:** “Are you certain there’s no one in authority at all? Not even an ambassador?"
**Picard:** [nodding] "Precisely. Their social structure wouldn’t allow it. Our first contact has been with an individual and his family, one Bas T'yat; a wealthy businessman and the inventor of their first warp-capable ship. He's requesting assistance to defend against further Cardassian attacks, but without a central authority, assisting one individual could have unpredictable consequences."
**Nechayev:** [questioning sharply] "Hmm. And what of the Cardassians? Is there any evidence of their involvement?"
**Picard:** [gravely] "Plenty. The Cardassians have already raided the planet, seizing valuable resources. Their ship left orbit shortly before our arrival, but the threat of their return looms large. Bas T'yat is convinced they'll come back with a larger force."
*Nechayev pauses, her expression hardening as she considers the situation.*
**Nechayev:** [warningly] "Starfleet cannot afford to be drawn into deeper hostilities with the Cardassian Union, Jean-Luc. Especially not over a non-member world. You must tread carefully. A diplomatic solution is paramount, and under no circumstances should you provide this Bas T'yat with advanced defensive technology. The Prime Directive is clear; we don't interfere with the internal affairs of non-member worlds, and besides, you haven't even made proper first contact with the planet, only with one family."
**Picard:** [measured, but firm] "Admiral, with respect, Anarak is far more advanced than many worlds we've encountered. Their technological capabilities, while decentralized, are impressive. Now that they are getting their space legs it won't be long before Anarakans are showing up in ports across the quadrant. And if the Cardassians establish a foothold here, it could destabilize the entire region."
*Nechayev's face softens slightly, recognizing the gravity of the situation. She sighs, her resolve shifting as she weighs the options.*
**Nechayev:** [reluctantly] "Alright, Jean-Luc. I don’t like this, but I trust your judgement. You may share transport inhibitor technology. Only enough to help them counter the Cardassians' beaming technology, but nothing more. And remember, this Bas T'yat doesn't speak for his whole planet. Try to treat his family like you would if you found them alone in a spaceship."
**Picard:** "Understood, Admiral. I'll proceed with caution."
**Nechayev:** [more sternly] "Just don't start another war, Jean-Luc."
*The screen goes dark. Picard leans back in his chair, the weight of the decision pressing on him. He stands, smoothing his uniform, and exits the ready room onto the bridge.*
---
**Scene 5: Bridge**
---
*On the bridge, the atmosphere is tense as the crew processes the situation. Picard steps up to his command chair, addressing the senior officers who have gathered.*
**Picard:** [seriously] "Admiral Nechayev has authorized us to share transport inhibitor technology with Anarak to help them defend against further Cardassian raids. But we must be mindful of the ethical implications of our actions."
**Dr. Crusher:**: [concerned] "Captain, I'm worried about the consequences of becoming involved in this situation. If we assist Anarak, it could escalate into a larger conflict--one that could draw the Federation into another war with the Cardassians."
**Worf:** [gruffly, with resolve] "But allowing the Cardassians to plunder a defenseless society is equally unacceptable, Doctor. We have a responsibility to protect the vulnerable."
**Picard:** [thoughtfully, considering both viewpoints] "I'm inclined to agree with Worf on this one, Beverly. We must work fast to deploy the inhibitors wherever we can, but that does bring up another problem. The Prime Directive prevents us from interfering in the internal affairs of non-member worlds. And giving one individual on Anarak access to advanced technology could upset the delicate balance of their society. What if Bas T'yat's company gains a monopoly on defense technology? It could shift the power dynamics on the entire planet."
**Troi:** [insightfully, her voice calm] "Captain, I sense that Bas T'yat is deeply worried about his planet's future. He feels a strong sense of responsibility and guilt for the attacks... I don't think that he had any way to know that their warp signature would act as a beacon to those seeking resources. They didn't even know other life forms existed until the Cardassians arrived. It's clear that Anarakans weren't prepared for the reality of interstellar contact."
**Picard:** [resolved] "I agree, Counselor. We're dealing with a society that is both advanced and vulnerable. A dangerous combination. We must proceed carefully."
*Picard considers this, his brow furrowed in thought. Finally, he makes a decision.*
**Picard:** [decisively] "We must proceed, however. I'll invite Bas T'yat to the Enterprise to discuss the situation further. We will ensure that any assistance we provide doesn't destabilize their society, or escalate the conflict."
*Picard hails Bas T'yat from his command station.*
**Picard:** [calmly] "Mr. T'yat, I'd like to invite you aboard the Enterprise to discuss our options in person."
*The main screen fills with T'yat's face again.*
**Bas T'yat:** [with a hint of hesitation] "Thank you, Captain, I accept. But I'd prefer to take my own craft... Still not quite comfortable with the transporter technology, if you'll understand. I'll bring my wife, L'anna, and my pilot, Lar Kinn."
**Picard:** [diplomatic, nodding slightly] "Understood. We'll be ready to receive you in the shuttlebay.”
---
**Scene 6: Main Shuttlebay**
---
*In the Enterprise's shuttlebay, the crew prepares to greet their visitors. The doors slide open, and a sleek, streamlined skysled enters the bay, guided by Lar Kinn at the controls. The craft settles gently onto the deck, and the hatch opens. Bas T'yat steps out, accompanied by his wife, L'anna, and Lar Kinn, who looks around the shuttlebay with wide-eyed curiosity.
Picard, Troi, and Data are there to meet them, offering warm greetings as the Anarakans take in the impressive sight of the Enterprise's interior.*
**Picard:** [welcoming, with a gesture towards the ship] "Welcome aboard the Enterprise, Mr. and Mrs. T'yat. I trust your journey was smooth?"
**Bas T'yat:** [grinning, clearly impressed] "Very much so, Captain. Your ship is... well, it's more than I imagined. Thank you for having us."
*Troi steps forward, offering a kind smile.*
**Troi:** [invitingly] "If you'd like, I can give you a tour of the ship. We're quite proud of our vessel, and I think you'll find it fascinating."
*L'anna's eyes widen with excitement, and she nods eagerly. Bas exchanges a look with Lar Kinn, just catching up to the group. He seems just as eager to explore as the others, and nods excitedly to Troi.*
**Bas T'yat:** [appreciatively] "We'd be honored. Lead the way, Counselor."
**Lar Kinn:** So can all these shuttles go faster than light?
*With that, the group sets off on a tour of the Enterprise, the Anarakans marveling at the advanced technology and seamless design of the Federation starship. As they walk, Troi can't help but notice the mix of awe and determination in Bas T'yat an inventor and leader who knows that his world's future may very well depend on the choices made in the hours to come.*
---
**Scene 7: Bridge**
---
*The scene opens as Counselor Troi leads Bas T'yat, L'anna, and Lar Kinn onto the bridge of the Enterprise. The visitor's awe is palpable as they take in the grandeur of the ship's command center. Picard, standing near the captain's chair, barely has a moment to welcome them when a sudden alert draws everyone's attention.*
**Data:** [at his station, voice urgent] "Captain, I'm detecting the return of the Cardassian battle cruiser. It is registered as the Kolarak. It just popped out from behind the home star and is entering orbit around Anarak."
**Riker:** "Yellow alert. On screen."
*Picard immediately straightens, his expression shifting from welcoming to resolute. The tension on the bridge heightens as the viewscreen flickers to life, displaying the imposing sight of the Kolarak. The Cardassian vessel looms in space, its dark hull bristling with weaponry.*
**Picard:** [calmly, but with authority] "Mr. Worf, open a channel to the Kolarak."
*The screen quickly reveals the stern visage of a Cardassian Gul in his command chair. His eyes narrow as he takes in the sight of the bridge crew and the unfamiliar faces of Bas and his companions.*
**Picard:** [with measured politeness] "I am Captain Jean-Luc Picard of the Federation starship Enterprise. With whom am I speaking?"
**Gul Bankar:** [with a sneer, his voice dripping with condescension] "You may address me as Gul Bankar."
**Picard:** "Gul Bankar, there have been reports of your vessel causing harm and stealing resources from the planet below. With me is Bas T'yat, the owner of the warp-capable vessel that it appears your forces destroyed on the surface. We request an explanation for these hostilities."
**Gul Bankar:** "Captain Picard, your presence here is an unwelcome interference. This planet, and its inhabitants, are under Cardassian protection. You will withdraw immediately, leaving Anarak to our care."
*Picard's gaze hardens, but his tone remains calm and firm.*
**Picard:** [skeptically] "Cardassian protection? Anarak lies within Federation territory. We received a distress call and are here to provide assistance."
*Bankar's expression darkens, his eyes flashing with anger.*
**Gul Bankar:** [coldly] "The Federation's meddling in this region is all too well documented, Picard, but Anarak is too close to Cardassian space for your interference to be tolerated. I find your so-called assistance nothing more than another prelude to annexation."
*Bas, standing beside Troi, listens intently, his face reflecting a mixture of concern and frustration. Picard, sensing the rising tension, steps closer to the viewscreen.*
**Picard:** [with resolve] "The Federation respects the sovereignty of all worlds. We are only here because of your aggressive actions, not to claim this planet. We have long worked to maintain peace in this sector, and I would hate to see that peace jeopardized by your reckless actions here."
**Gul Bankar:** [sarcastically] "Peace? The Federation's control of Terok Nor and the Bajoran wormhole is hardly a gesture of peace. It was a clear power grab, one that we will not allow to extend to Anarak."
*Picard's eyes narrow, his voice taking on a steely edge.*
**Picard:** [firmly] "Gul Bankar, a conflict between the Federation and the Cardassian Union would serve no one's interests, especially not over a planet that is so new to the neighborhood. I suggest you contact your superiors before taking any further aggressive actions."
*There's a tense silence as Bankar considers Picard's words, his eyes flicking to Bas and then back to Picard. Finally, he lowers his head in a slight nod, though his expression remains hostile.*
**Gul Bankar:** [grudgingly] "Very well, Captain. I will contact Central Command. But understand this; Anarak will not fall under Federation control, and I will ensure that Cardassia's interests are protected. I will contact you again in 4 hours."
*The transmission abruptly cuts off, leaving the bridge in a heavy silence. The Kolarak remains on the viewscreen, hovering ominously in space, nose to nose with the Enterprise now. Picard exhales, turning to face his crew.*
**Picard:** [calmly, but with an undertone of urgency] "Maintain our position and yellow alert, Mr. Worf, and monitor the Kolarak for any signs of hostile activity."
*Worf gives a curt nod, his eyes never leaving the tactical display.*
**Worf:** [with determination] "Aye, Captain. Shields at maximum, weapons ready."
*Picard then turns to Bas, who is visibly shaken but trying to maintain his composure.*
**Picard:** [reassuringly] "Mr. T'yat, I understand this is a difficult situation and you don't yet know who to trust, but I assure you that we aim to keep the peace in this sector and will do everything in our power to ensure your planet's safety. We ask nothing in return from the Anarakan people. However, it is crucial that we handle this matter diplomatically."
*Bas nods, though his expression is one of deep concern.*
**Bas T'yat:** [uneasily] "I appreciate that, Captain, and don't worry, nothing that Gul Bankar says will make me trust his offer of "protection" after he destroyed my ship and stole resources from all over the planet. But I do worry that he’s using this time to call for reinforcements."
*Picard places a reassuring hand on Bas's shoulder, his voice steady.*
**Picard:** [confidently] "If he attacks, we'll face that challenge together, Mr. T'yat. You are free to return to the surface at any time but for now, I think it best that we consider how fast we could deploy our transporter inhibitor technology on your planet."
**Bas T'yat:** [enthusiastically] "You mean you're willing to sell us devices that can stop them from beaming up our resources?"
**Picard:** "Or beaming their troops down. And we wouldn't sell it to you, it is our gift. The Federation doesn't sell it's assistance to those in need."
*The visitors faces all brighten in unison with relief.*
**L'anna:** "I don't know how we could ever thank you enough, Captain. This means everything to our people."
**Picard:** "Don't thank us yet, there is still the issue of deploying enough of them in time. If they're going to attack in 4 hours you'd need them set up near all the most valuable targets at the very least. They'll need a steady supply of energy, too."
*Bas furls his lips in concerned thought.*
**Data:** "Captain, I've analyzed all of the planet's most valuable resource depots that our scanners can detect and I see 168 unique locations that we should set up transport inhibitors. There may, of course, be other targets too that they would want."
**Riker:** [apprehensively] "That's way too many for us to replicate in time, much less visit each location to install within the next 4 hours."
**Picard:** "We need a way to speed up that deployment, at least to enough sites that will show Gul Bankar that things have changed... And hopefully without him detecting our movements."
**Bas T'yat:** "If I may captain, I think I know a better way to deploy them if I can just make a detailed scan of one and save it to our printer file format... We don't have your transporter technology, but our device printers are able to scan and quickly reproduce any technological device that we can identify the components of."
**Riker:** "And how will that help distribute them to everyone in time?"
**Bas T'yat:** "Simple, every business and household has one of these printers. I can upload the scanned file to our Openlink and tell all of Anarak in one broadcast about the imminent threat and how to protect themselves from it with one of these inhibitors. They'll pop out thousands of them in time."
**Picard:** "That sounds very promising, Mr. T’yat. But I want your assurance that your company will not hold any sort of monopoly on this technology or otherwise profit from it; In lieu of a government, the Federation requires that this gift be made to your whole planet at once."
**Bas T'yat:** [after some hesitation] "Alright, Captain. You have my promise. Giving up some profits is the least I can do to make up for attracting the Cardassians to Anarak."
*Picard looks visibly relieved, giving a curt nod to Bas.*
**Picard:** "Data, take our guests to engineering and grab whomever you may need to assist you with making this happen in time. Remember, you’ll also need to show the Anarakans how to use these devices."
**Data:** "Aye sir." [To the visitors] "If you'll follow me please, we'll be able to work on this in engineering."
*Data, Bas, Lar Kinn, and L'anna walk briskly to the turbolift. The scene closes with Picard returning to his command chair, the bridge crew resuming their stations as the standoff between the Enterprise and the Kolarak continues. The two ships remain locked in silence, nose to nose, as the 4-hour countdown begins.*
---
**Scene 8: Main Engineering**
---
*The scene opens in Main Engineering, where Geordi La Forge, Data, and Ensign Sam Lavelle are putting the final touches on the scan for their transport inhibitor device. Bas T'yat and Lar Kinn stand nearby, observing the process with keen interest. The atmosphere is tense, underscored by the ticking clock counting down the hours until Gul Bankar's deadline.*
**Geordi:** [focused as he works] "All right, that should do it. The scan of this transport inhibitor is ready, and the data's been formatted for your printers."
*He hands a datapad to Bas, who takes it with a mix of curiosity and nervousness.*
**Geordi:** [reassuringly] "You'll be able to upload the complete plans from this device, including an adapter for your power source. Once it's on your network, anyone with Openlink access will be able to build and deploy these inhibitors in a matter of minutes. It's up to you, however, to convince them to do that."
**Bas T'yat:** [relieved] "Thank you, Commander. I'm sure many will manage it in time, but I just hope it's enough."
**Lavelle:** [chiming in, pointing to the datapad] "Also I've included a detailed instruction set too. It explains how to set the units up and operate them."
*Bas nods his thanks, flipping through the instructions as Lar Kinn looks over his shoulder.*
**Data:** [ever precise, offering a suggestion] "Mr. T'yat, given the standoff outside, it may be prudent to avoid the use of the transporter. The Kolarak is likely monitoring our actions closely. Sending the plans with you aboard the skysled would appear less provocative."
*Bas looks visibly relieved at the suggestion, nodding in agreement.*
**Bas T'yat:** [grateful] "Thank you, we'd prefer not having our atoms scattered throughout the atmosphere today anyway."
**Geordi:** [nodding, humorously] "No problem. We'll make sure the skysled is ready to go."
*Data gestures toward the exit of Engineering, indicating it's time to depart.*
**Data:** [calmly, but with urgency] "We should make our way to the shuttlebay. There's less than two hours remaining before the Gul's deadline. It's imperative that as many Anarakans as possible receive these plans in time."
*Bas and Lar Kinn exchange a look, their expressions set with determination as they follow Data out of Engineering. The camera follows the group as they walk briskly through the corridors of the Enterprise.*
**L'anna:** "You'll be sure to tell the Captain and Councilor Troi that we said goodbye?"
**Data:** "Of course. And let me say that I find your culture truly intriguing, and hope we get the chance to visit again in the future, no matter if Anarak chooses Federation membership or otherwise."
**Bas T'yat:** "You'd be our welcome guest anytime, Mr. Data. I think you'd most enjoy seeing the progress my people have made with robotics and artificial intelligence. My company produces one of the best-selling android assistants on the market."
**Data:** "Fascinating. I look forward to it. Here we are."
*As they reach the shuttlebay, the large bay doors slide open, revealing the sleek skysled waiting for them. The ship is prepped and ready for launch, its engines humming with quiet power.*
**Data:** [pausing as their ship's door opens] "We wish you a safe journey, Mr. T'yat, L'anna, Mr. Kinn."
**Bas T'yat:** [nodding, with resolve] "We'll make sure everyone gets these plans. Thank you, Commander Data."
*Lar Kinn gives Data a respectful nod before they step onto the skysled. Data watches as they take their positions inside the cockpit.
Data then taps his communicator, his voice steady.*
**Data:** "Data to the Bridge, our visitors are ready to depart."
*The camera cuts to the exterior of the Enterprise, where the massive shuttlebay doors slide open. The skysled, with its sleek design and glowing engines, slowly backs out of the bay, the vastness of space stretching out behind it.
As the skysled turns on its main engines, the camera shifts to an interior cabin view, showing Bas and Lar Kinn exchanging a final, determined nod before the vessel speeds downwards towards Anarak.*
---
**Scene 9: Bridge**
---
*The scene opens 30 minutes later. The tension on the Enterprise bridge is palpable as the Openlink broadcasts Bas's message and the transport inhibitor plans worldwide. The crew watches anxiously as the first inhibitors are swiftly deployed across Anarak.
Suddenly, the ship's sensors beep urgently. Worf glances at his console, eyes narrowing.*
**Worf:** [alarmed] "Captain, seven additional Cardassian battle cruisers have exited warp and joined Gul Bankar's ship. They're forming up and preparing to engage."
**Riker:** "Red alert, forward shields to maximum."
*Picard's expression hardens as the Kolarak hails them. Gul Bankar's visage appears on the viewscreen, eyes burning with fury.*
**Gul Bankar:** [accusatory] "We've detected the inhibitor plans on their planet-wide network, Picard. You've broken our gentleman's agreement by sharing advanced technology with a primitive civilization. So much for Starfleet ideals! You're no match for us now. Try and stop us at your own peril."
*With that, Bankar cuts off communications. Picard stands, frustration etched into his features as the fleet of eight warships begins its descent toward Anarak.*
**Data:** [urgently] "Captain, the Cardassian ships are gaining speed and appear to be initiating an attack run on the planet's largest population center. Tens of millions of civilian lives are at risk, more than usual because the defensive turrets are spread out among the greater population. It is not uncommon for them to be placed on rooftops and around housing here."
*The crew's tension escalates as the gravity of the situation sinks in. Picard, feeling the weight of command, turns to his officers.*
**Picard:** [steady but intense] "Ideas?"
**Worf:** "Captain, we could attempt to disable their weapons and transporters, focusing on minimizing their capacity to attack."
**Riker:** [shaking his head] "Even so, we're outmatched. Enterprise won't survive against eight battle cruisers."
**Troi:** [calm but urgent] "We just need to buy time. To give the Anarakans a chance to fully deploy their defense net. But any kind of engagement from us still risks re-igniting a war with the Cardassians."
*Data, ever analytical, speaks up with a grim tone.*
**Data:** "Captain, I've run millions of battle scenarios. None result in the Enterprise surviving while saving more than a few dozen lives on the surface. Our current position is untenable."
*As the Cardassian warships break through the planet's stratosphere, Ensign Lavelle, stationed at comms, suddenly speaks up.*
**Lavelle:** [urgently] "Captain, Bas T'yat has just sent out another message across the planet, warning of the incoming Cardassian fleet."
*Picard opens his mouth and lifts his index finger to respond, but he's cut off by a sudden, blinding array of light erupting from the planet's surface, filling up the viewscreen. The bridge crew shields their eyes as the screen fills with thousands of pinpricks of light; an overwhelming launch of nuclear-armed missiles aimed directly at the Cardassian fleet.*
**Worf:** [stunned] "Captain, these are nuclear-fission warheads, each with a 10-megaton yield. I've never seen a civilization with this many dirty weapons in active deployment."
*The bridge falls silent as the sheer scale of the Anarakan response becomes clear. The entire hemisphere of Anarak has mobilized, proving their incredible capacity for defense, despite the lack of a centralized government.*
**Data:** "Fascinating. It could be that no central authority is needed for coordination when the threat is dire. These people all appear to be responding individually with their own weapons."
*The first few dozen warheads impact the Cardassian shields, which manage to absorb their blasts. But the onslaught is unrelenting. Hundreds, then thousands of warheads detonate in rapid succession, creating a cataclysmic, sustained explosion. The Cardassian ships, though formidable, are utterly overwhelmed. The viewscreen shows an apocalyptic display; a temporary star forms in Anarak's upper atmosphere, engulfing the entire Cardassian flotilla in an unprecedented, blinding flash.*
**Picard:** "Helm, back off our position."
*The bridge crew watches in stunned silence as the massive explosion slowly dissipates, leaving nothing but a red afterglow and the eerie silence of space. Power has gone out across the hemisphere on the planet below, but not a single molecule of the Cardassian ships remain.
Picard and his crew are left in awe, mingled with a deep sense of disappointment. The enormity of what they've witnessed sinks in; a civilization so welcoming, yet still capable of such destructive power... Sso fundamentally different from the Federation's ideals.
Troi closes her eyes tightly and winces, blocking out the pain of all those Cardassian deaths. Picard stands, staring out at the aftermath, the weight of the moment heavy on his shoulders.*
**Picard:** [quietly, with a great sense of loss] "Such utter destruction..."
*The camera pulls back, showing the Enterprise as a small silhouette against the reddish glow below.*
---
**Scene 10: Bridge**
---
*The scene opens minutes later with the Enterprise bridge crew still processing the aftermath of the overwhelming display of destructive power. The mood is somber as the reality of what they've witnessed lingers. Suddenly, Bas T'yat's face appears on the viewscreen, his expression a mixture of relief and satisfaction.*
**Bas T'yat:** [earnestly] "Captain Picard, I wanted to thank you and your crew for everything. It seems our future is secure now, thanks to the defense network and your assistance. We're eager to move forward and hope the Federation will allow us to engage in commerce with your worlds and other peaceful civilizations."
*Picard stands, his gaze steady, though his tone reflects the weight of what has transpired. He pauses for a moment, as if searching for the right words, the bridge falling into a brief, tense silence.*
**Picard:** [measured, but firm] "Mister T'yat, I must be candid. While the Enterprise is pleased to have assisted in safeguarding your world, the events of today have left us with grave concerns. The way Anarak handled the Cardassians… particularly the use of nuclear warheads, demonstrates a fundamental difference in values between our societies. We cannot endorse methods that pose such a grave risk to all life, even in defence. The Federation could not, in good conscience, approve your planet for membership given these circumstances."
*Bas's expression shifts to one of slight disappointment, but he remains composed.*
**Bas T'yat:** "I understand, Captain. We've always been a world that does things our own way. Federation membership would have been a tough sell to my people anyway. But what about trade? Surely we can still establish commerce with Federation worlds?"
*Picard nods, his tone softening slightly.*
**Picard:** "Trade remains an option. We won't turn away peaceful commerce between Anarak and Federation planets. However, I must stress that the use of nuclear weapons is fundamentally at odds with Federation ethics. While I recognize their role in your planet's defense, I hope that over time, your people will explore more sophisticated and less destructive means of protection."
*Bas nods again, understanding the implications of Picard's words.*
**Bas T'yat:** "It's clear that today's events were... extreme. The fallout, the EMP blackouts, the atmospheric damage; we've already seen unacceptable cost. I'll do my best to guide my people toward more advanced defenses, and away from reliance on such careless weapons. It will be my penance for leading the Cardassians here."
*Troi senses his guilt once again and takes a deep breath. Clearly still shaken by the loss of life, she steadies herself before offering a supportive smile.*
**Troi:** "You shouldn't burden yourself with guilt, Mister T'yat. Anarak was bound to take that step sooner or later. What matters now is how you use your newfound role as an ambassador to the stars. Your actions will shape your planet's future in the galaxy."
*Bas smiles, clearly grateful for the support.*
**Bas T'yat:** "Thank you, Counselor. I'll do my best to live up to that responsibility."
*After a few more exchanges, the connection ends, and Bas T'yat's image fades from the viewscreen. Picard takes a deep breath and turns to face his bridge crew.*
**Picard:** [reflective] "We've witnessed two amazing displays of power today; one of the explosive variety, and the other of a free people's resolve. It's hard to imagine how their society works with no acceptance of authority, but today they've clearly displayed that they can accomplish amazing things working together even without any."
*Worf, still perplexed, shakes his head slightly.*
**Worf:** "I still don't understand how an entire planet could coordinate such a specific defense without any central leadership."
*Leaning casually against the console, Riker chuckles lightly.*
**Riker:** "It was in everyone's best interest, Worf. They just needed Bas's signal to know when the attack was imminent. The rest fell into place."
**Worf:** "And how they could hide that many warheads from our scans? Enriched Uranium is the easiest of all elements to scan for."
**Data:** "It appears that their stealth technology may be on par with our own."
*Picard, his expression thoughtful, gazes out at the stars beyond the viewscreen.*
**Picard:** "I'm placing a note in my log for Starfleet to leave this planet alone until they can't be ignored any longer. I believe it's for the best that we leave Anarak to chart its own course in the galaxy."
*He pauses, a faint smile tugging at the corner of his mouth.*
**Picard:** "I doubt we'll have trouble with them soon, at least, until they meet the Ferengi."
*The bridge crew shares a quick laugh and then a quiet moment of contemplation before returning to their stations. The camera pulls back, showing the Enterprise once again poised in the vastness of space, a symbol of hope and integrity amidst the complexities of a vast and unpredictable galaxy.
Fade to black.*
---
---
---
****This story is set in the Star Trek universe, created by Gene Roddenberry and owned by Paramount. I do not own any of the characters or settings from the Star Trek franchise, and this is purely a fan-made work for non-commercial purposes.****
-

@ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17
When I have stale bread, I often use it to make a bread salad.
The base is croutons of stale bread and then there are no limits to your imagination.
In this salad there was also
- Onions stewed in balsamic vinegar
- Spring onions (raw)
- Cherry tomatoes
- Eggplants and sweetcorn (fried, lukewarm)
- Pine nuts
- Finely sliced cheese
- Basil
https://image.nostr.build/ce0c7490f2adbd2aa4ccdfe80203a15dbb10686859a3256a0147d5f423478fd0.jpg
https://image.nostr.build/f930e0984ec9603b84c7a7868a97486140ee44590590102f7e460bfbfd3d70be.jpg
originally posted at https://stacker.news/items/672404
-

@ 469fa704:2b6cb760
2024-09-04 15:22:28
## Money Printing in general
First of all, we need to make a distinction between money creation by central banks and fractional-reserve banking. Usually, the term money printing or “printer goes brrrrrr” refers to the creation of new central bank money, which is primarily created by central banks through:
* **Open Market Operations**: Buying government securities, which injects money into the banking system by increasing bank reserves. This is often done electronically, not by physically printing money.
* **Quantitative Easing (QE)**: Purchasing assets to inject money directly into the economy, aiming to stimulate economic activity by increasing the money supply.
* **Setting Reserve Requirement**s: Although less about creating money, lowering reserve requirements can indirectly influence money creation by allowing banks to lend more, but as of recent policy changes, this has been set to zero in some systems, shifting focus to interest rates.
* **Interest on Reserves**: By adjusting the interest rate paid on reserves, central banks influence how much banks are willing to lend, thereby indirectly affecting money creation.
This is the first step of money creation, although printing money is usually connected to one of the aforementioned processes, the second step creates much more money through the expansion of credit.
## The Mechanics of Fractional-Reserve Banking
### The Concept
In fractional-reserve banking, banks accept deposits from customers and only keep a small fraction of these deposits in reserve, lending out the rest. This practice essentially creates new money because:
* **Deposits**: When you deposit money, say $1,000, into a bank, that money doesn't just sit there.
* **Reserves**: If the reserve requirement is 10%, the bank keeps $100 as reserves.
* **Loans**: The remaining $900 can be loaned out. Here's where money creation begins.
Note: Current reserve requirements of the FED ([Source](https://www.federalreserve.gov/monetarypolicy/reservereq.htm)) and the ECB ([Source](https://www.ecb.europa.eu/ecb-and-you/explainers/tell-me/html/minimum_reserve_req.en.html)) are set at 0% respectively 1%.
### Example Calculation of Money Creation
1. **Initial Deposit**: You deposit $1,000 into Bank A.
2. Bank A's Action:
* Keeps $10 (1%) as reserve.
* Loans out $990 to another customer.
3. **The $990 Loan**: This $990, when spent, might end up in Bank B as someone's deposit.
4. **Bank B's Action**:
* Keeps $9.9 (1% of $990) as reserve.
* Can loan out $980.1
5. **Continuation**: This process repeats, with each cycle creating new deposits from loans.
The **Deposit Multiplier** (m) can be calculated as:
* m = 1 divided by Reserve Ration = 1 / Reserve Ration
If the reserve ratio is 1%:
* m = 1 / 1% = 1 / 0.01 = 100
This means, theoretically, an initial deposit of $1,000 could expand to:
* $1,000 times 100 = $100,000
* However, in practice, this is tempered by factors like cash holdings, loan demand, and banks holding excess reserves.
### Historical and Economic Context
* **Evolution from Goldsmiths**: The system has its roots in the practices of goldsmiths who issued notes for gold deposits, which eventually circulated as money. This practice evolved into the modern banking system where notes (now digital entries) represent claims on money.
* **Regulation and Central Banking**: Over time, central banks like the Federal Reserve in the U.S. were established to regulate this process, provide stability, and act as lenders of last resort. The Fed's tools include setting reserve requirements, though this has become less relevant with the shift to a 0% reserve requirement.
### Criticisms and Alternatives
* **Risk of Bank Runs**: Critics argue that fractional-reserve banking makes the system vulnerable to bank runs, where too many depositors demand their money back at once, which the bank cannot cover since most of the money is loaned out.
* **Vollgeld Initiative and Full-Reserve Banking**: Movements like Switzerland's Vollgeld Initiative have proposed shifting to full-reserve banking, where banks must hold 100% of deposits in reserve, preventing them from creating money through lending. However, this would significantly alter how banks operate and make profits.
*** Modern Adjustments**: The move to a 0% reserve requirement in the U.S. reflects a shift towards using other monetary policy tools like interest rates on reserves to control money creation and economic stability.
### Real-World Implications
* **Money Supply Control**: While banks create money through loans, central banks like the Federal Reserve influence this through monetary policy, adjusting how much money banks can create.
* **Economic Stability**: The zero reserve requirement might seem to allow infinite money creation, but in reality, banks are constrained by capital requirements, risk assessments, and economic conditions.
## Conclusion
Fractional-reserve banking is a dynamic system that significantly influences economic growth by expanding the money supply through debt. While it allows for economic expansion, it also introduces risks of instability, which central banks attempt to mitigate through various policy tools. Understanding this system helps demystify how money flows and grows within an economy, showcasing both its capacity for economic stimulation and its inherent risks. As we move forward, debates continue on how best to balance these aspects to foster economic stability and growth.
In 2009, a new system called Bitcoin emerged that could redefine the rules for money creation.
-

@ 469fa704:2b6cb760
2024-09-04 12:07:53
## Unified Login Across Platforms
With Nostr, you use one login for all services, and your followers are seamlessly integrated. So you don't have start anew on every single platform. I think this is a real advantage of Nostr even for people not accustomed to Bitcoin or decentralization in general.
## Value for Value (V4V) Model
Embrace the V4V principle where value is exchanged directly between users. Meaning if you find something useful or anohter nostr user was able to help you then you can simply zap him or her some Sats.
## Blogging Platforms
* **Habla or Yakihonne**: Since joining Nostr 8 days ago, I've started blogging using Habla, which I found incredibly user-friendly. You can check out my articles directly on some clients like noStrudel, where they appear under my profile. Habla also serves as a great community explorer. Yakihonne, another comprehensive client with an integrated blog editor, caught my eye too, although it didn't sync all my Habla posts, possibly due to relay issues.
* **Highlighter.com**: Offers a sleek interface for reading articles. On noStrudel, articles are tucked away under the "More" menu.
## Presentations
* **Slidestr.net**: This tool transforms your notes into a slideshow, making revisiting old notes quite entertaining.
## Video Content
* **Flare.pub**: If you're looking for a YouTube-like experience, Flare.pub is the closest you'll get on Nostr. You can upload, watch videos, and curate playlists. Remember, since Nostr is fundamentally text-based, videos are hosted on traditional servers, but the interface remains decentralized. There's definitely room for more video content, so start creating!
## Live Streaming
* **Zapstream**: Offers a smooth streaming experience with a fee of 10 Sats per minute to cover server costs. You can watch streams on clients like Amethyst or noStrudel.
## Music and Podcasts
* **Wavlake and Tunestr**: Ideal for artists to share music or podcasts. Listeners can enjoy content freely or support creators via zaps, adhering to the V4V model.
## Lists and Grouping
* **Listr**: A tool for organizing everything from regional user groups to thematic notes or hashtags. You can also follow lists created by others in the Nostr community.
## Culinary Arts
* **zap.cooking**: A haven for aspiring or seasoned chefs, offering a plethora of recipes in a blog format. It's well-organized, allowing you to browse through different categories of recipes.
## Marketplaces
* **Plebian Market**: Reminiscent of eBay's early days, this marketplace allows easy buying and selling among users.
## Community Features
* Many clients like noStrudel, Habla, and Amethyst support community functionalities, enhancing user interaction within Nostr.
-

@ d830ee7b:4e61cd62
2024-09-04 07:29:41
Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล
ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน
แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด
ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ
## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks**
ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม
แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา..
เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่
ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin
ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน..
ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน
Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ
## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน**
ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core
Blockstream สนับสนุน "Small Blocks"
เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้
ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา
## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน**
ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB**
แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers
Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง
Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org
ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน
เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น..
## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว**
ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement"
ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว
ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash**
ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017
SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย
SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา..
อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit
ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"**
## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ**
ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้
Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้
Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว
เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด
นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย
## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright**
ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)**
การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔
ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash
กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts
Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer"
การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย
## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี**
หลังจากการ Hard Fork ของ Bitcoin Cash
Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value)
การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม
Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง
อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน
นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง
นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain
Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin
## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ**
ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ
ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง
สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป
# **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง**
## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล**
Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า
### **SegWit (Segregated Witness)**
เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network
### **Taproot**
เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป
Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ
## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่**
ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่
### **Bitcoin XT (2015)**
เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ
### **Bitcoin Classic (2016)**
เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน
### **Bitcoin Unlimited (2016)**
เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง
### **Bitcoin Cash (BCH) (2017)**
เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง
### **Bitcoin SV (BSV) (2018)**
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin
### **Bitcoin ABC (2020)**
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง
## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?**
หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists
Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"**
Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น..
### **การไม่ยอมเพิ่ม Blocksize Limit**
Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream
### **การเซ็นเซอร์ข้อมูล**
Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ
### **การต่อต้านนวัตกรรม**
Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น
### **การควบคุมโดยกลุ่มเล็กๆ**
Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin
Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto
## **บทสรุป:**
การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency
มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป
สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด
**"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่..
ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย..
เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง..
— Jakk Goodday
-

@ e0e92e54:d630dfaa
2024-09-04 04:13:19
_This is a copy of the email received from newsletter@Rumble.com_

# Free Speech Under Attack -- A Note from the CEO of Rumble
Dear Rumble Users,
I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble.
Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court.
World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them.
There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it.
Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people.
The people keep us alive and keep us going.
If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression.
We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil".
Sincerely,
Chris Pavlovski
Chairman and CEO of Rumble

444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA.
-

@ 96203d66:643a819c
2024-09-04 03:42:31
#[3]
#[4]
#[5]
#[6]
#[7]
#[8]
#[9]
#[10]
#[11]
#[12]
#[13]
#[14]
#[15]
#[16]
#[17]
#[18]
#[19]
#[20]
#[21]
#[22]
#[23]
#[24]
#[25]
#[26]
#[27]
#[28]
#[29]
#[30]
#[31]
-

@ 3b7fc823:e194354f
2024-09-04 01:33:21
Nyms, Personas, and Digital Identity
#GHOSTn
If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs.
Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see.
Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be.
Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes.
Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
-

@ 3b7fc823:e194354f
2024-09-04 00:26:48
Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
>
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled.
If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
>
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
>
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
>
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
>
>
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
>
Last point and most important:
Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-

@ 8cb60e21:5f2deaea
2024-09-03 22:26:25
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8cb60e21:5f2deaea
2024-09-03 22:26:25
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8cb60e21:5f2deaea
2024-09-03 21:58:26
# Lesson 3: Arrays, Objects, and Callbacks
### Arrays: Lists of Things
Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys:
```javascript
var catToys = ["mouse", "ball", "laser pointer"];
console.log(catToys[0]); // Prints "mouse"
```
### Objects: Grouping Related Information
Objects allow you to group related information together. They're like detailed profiles for each of your cat friends:
```javascript
var myCat = {
name: "Fluffy",
age: 3,
favoriteFood: "tuna"
};
console.log(myCat.name); // Prints "Fluffy"
```
### Callbacks: Doing Things Later
Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat:
```javascript
function feedCat(callback) {
console.log("Feeding the cat...");
setTimeout(function() {
console.log("Cat has finished eating!");
callback();
}, 2000);
}
feedCat(function() {
console.log("Time for a treat!");
});
```
This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat.
Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
-

@ 8cb60e21:5f2deaea
2024-09-03 21:58:26
# Lesson 2: Functions and Loops
### Functions: Your Own Commands
Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick:
```javascript
function meow(times) {
for (var i = 0; i < times; i++) {
console.log("Meow!");
}
}
meow(3); // This will print "Meow!" three times
```
### Built-in Functions
JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console:
```javascript
console.log("I'm a cat!");
```
### Loops: Repeating Tasks
Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds:
```javascript
for (var i = 0; i < 5; i++) {
console.log("Chasing tail, round " + (i + 1));
}
```
This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
-

@ 6bae33c8:607272e8
2024-09-03 10:47:55
I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track.
*(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)*
1. **Stefon Diggs leads the Texans in targets, catches and receiving yards**
Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year.
2. **CJ Stroud leads the NFL is passing yards**
This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2.
3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)**
Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens.
4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR**
Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020.
5. **The Giants will field a top-10 fantasy defense.**
I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers.
6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt**
I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua.
7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)**
Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time.
8. **Dalvin Cook will lead the Cowboys in rushing yards**
Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.)
9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.**
He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.)
10. **Dalton Kincaid (TE4) will lead all TE in catches**
I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2.
11. **Some of these predictions will be wrong**
No one’s perfect, but you never want to get shut out.
-

@ 469fa704:2b6cb760
2024-09-03 10:20:09
In traditional investment wisdom, diversification is the mantra chanted by financial advisors worldwide. It's the strategy to spread risk across various assets to mitigate losses. However, when it comes to Bitcoin, some argue this principle might not apply in the same way. Here's why:
## 1. Bitcoin's Unique Value Proposition
Bitcoin, often dubbed "digital gold," has several attributes that set it apart from other investments:
* **Finite Supply**: With a cap at 21 million coins, Bitcoin's scarcity is programmed into its code, mirroring the scarcity of gold but with even more certainty. This scarcity can drive value as demand increases over time, especially in an economic environment where fiat currencies are subject to inflation.
* **Decentralization**: Unlike stocks or real estate, Bitcoin isn't tied to any central authority or physical asset that can fail or be manipulated by a single entity. This decentralization reduces the risk of systemic failure that affects traditional markets.
* **Global Liquidity and Accessibility**: Bitcoin can be bought, sold, and transferred anywhere in the world, 24/7, with internet access. This global liquidity means Bitcoin can be more easily converted to other assets if needed, somewhat reducing the need for diversification.
## 2. The Risk-Reward Balance
* **Volatility as Opportunity**: While Bitcoin's volatility is often cited as a risk, for the informed investor, this volatility represents opportunities for significant gains. Those who understand Bitcoin's cycles might prefer to ride these waves rather than dilute potential gains through diversification into less volatile assets.
* **Long-term Appreciation**: Historical data suggests Bitcoin has provided substantial returns over the long term compared to most traditional investments. If one believes in Bitcoin's future as a dominant store of value, holding a diversified portfolio might mean missing out on Bitcoin's potential upside.
## 3. Bitcoin as a Diversifier
Ironically, Bitcoin itself serves as a diversification tool within traditional investment portfolios. Its price movements have shown low correlation with stocks, bonds, and even gold at times, suggesting that Bitcoin can diversify an investment portfolio on its own.
## 4. The Philosophical Shift
* **Trust in Code Over Corporations**: Investing heavily in Bitcoin might reflect a philosophical shift towards trusting mathematical algorithms over corporate governance or government policy. Here, diversification within the crypto space might seem less necessary if one views Bitcoin as the pinnacle of what cryptocurrency should be.
* **A Bet on a New Financial System**: Holding Bitcoin exclusively can be seen as a bet on a new financial paradigm where Bitcoin becomes the standard. In this vision, diversification into other assets might be counterproductive.
## 5. Potential Result
Upon reviewing the arguments and characteristics, one might conclude that Bitcoin is pursuing a dual trajectory. Firstly, its value increases partly because it remains a novel asset, not yet mainstream among the general populace. Secondly, Bitcoin is poised to absorb the value preservation function from other assets. This means that individuals who invest in stocks, bonds, real estate, commodities, etc., primarily for their value storage capabilities rather than their intrinsic utility (such as residing in a property), might transition to Bitcoin. This shift could consequently diminish the demand for these traditional assets and increase the value of Bitcoin respectively.
## 6. Caveats and Considerations
* **Not Without Risks**: This approach isn't without its perils. Bitcoin's future is not guaranteed, and regulatory, technological, or market shifts could impact its value negatively.
* **Liquidity Needs**: Individual financial situations might require liquidity or income generation that Bitcoin alone might not provide efficiently.
* **Emotional Discipline**: A Bitcoin-only strategy requires immense discipline and conviction, as the emotional toll of not diversifying can be high during market downturns.
## Conclusion
The argument for not diversifying if you hold Bitcoin hinges on its unique properties, the potential for high returns, and its role as a hedge against inflation and traditional financial systems. However, this strategy suits those with a high risk tolerance, a deep understanding of Finance, Economics and Investments, and a belief in Bitcoin's future dominance. For everyone else, while Bitcoin can be a significant part of a portfolio, traditional diversification might still offer peace of mind and stability. Remember, investment strategies should align with personal financial goals, risk tolerance, and market understanding. Always consider consulting with a financial advisor for personalized advice.
-

@ 161c8564:2d633b95
2024-09-02 20:24:34
Opinion about Freewallet Multi Crypto Wallet (iphone)
<!--HEADER END-->
FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it!
<!--FOOTER START-->
#WalletScrutiny #nostrOpinion
[Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
-

@ eed76ece:afa98124
2024-09-02 18:58:30
As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously.
Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online.
SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West.
Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway.
Examples
Customers in these regions I deal with primarily communicate with me in
Japan, Thailand using LINE and Tik Tok daily.
Most of the rest of the World communicate with me using WhatsApp.
Certain parts of Eastern Europe and Asia Telegram.
Interestingly my resellers in the USA primarily post on WhatsApp.
Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again".
"So I will always have free speech, the politicians told me so".
originally posted at https://stacker.news/items/670041
-

@ 56a6da9b:7f5a2243
2024-09-02 18:27:19
IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity.
originally posted at https://stacker.news/items/669994
-

@ 6bae33c8:607272e8
2024-09-02 18:09:19
I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot.
Here are the results:
([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream))
<img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png">
**1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount.
**2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead.
**3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there.
**4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target.
**5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone.
**6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year.
**7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position.
**8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR.
**9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.)
**10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.)
**11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks.
**12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build.
**13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job.
**14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert.
**15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old.
**16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down.
**17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too.
**18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie.
**19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.)
**20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence.
**Roster By Position**
**QB** Anthony Richardson
**RB** James Conner/Jaleel McLaughlin
**WR** Ja’Marr Chase/Drake London/DeVonta Smith
**TE** Dalton Kincaid
**FLEX** Stefon Diggs
**K** Younghoe Koo
**D** Giants
**Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
-

@ 3b7fc823:e194354f
2024-09-02 16:26:30
First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
>
1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program.
>
2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.
BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
>
3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works.
>
4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta.
>
5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.
>
BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
>
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-

@ 266815e0:6cd408a5
2024-09-02 15:27:16
After 7 months of work and procrastination I've decided to release another version of noStrudel
There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md)
And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker
```sh
docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0
```
## New Features
### Support for NIP-49 encrypted nsec
Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...)
There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps

### Blindspot feeds
There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing

### NIP-42 Relay authentication
The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings

### Wasm relay and event verification
The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view

The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting

### Thread tabs
Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note


### Wiki articles
Its not feature complete but you can now view and edit wiki articles in the app

### Finished the launchpad
The launchpad is now usable and shows the latest notifications, messages, streams, and tools

### Blossom uploads
The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings

And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`

### Task Manager
There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app

You can see what relays the app is currently connected to

And which relays are requesting NIP-42 authentication

## Bug fixes
- Fix null relay hints in DMs
- Fix users own events being hidden by muted words
- Fix random events showing up as DM messages
- Fix app prompting NIP-07 extension to unlock when app opens
- Remove corsproxy.io as default service for CORS proxy
-

@ 38d0888d:bd8e1246
2024-09-02 11:08:05
To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment.
A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding.
It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
-

@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53
There's a saying: Bitcoin is hope.
But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin.
For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right?
I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours?
She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw.
I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else.
So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero.
There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore.
We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent?
The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them.
Extreme situations, I know. But no one thinks it will happen to them—until it does.
So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why?
What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time.
Time with your kids. Time with your family. Time with yourself.
There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work.
But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here.
So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here.
I just need to get through the withdrawal phase.
originally posted at https://stacker.news/items/662939
-

@ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27
Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.

originally posted at https://stacker.news/items/669464
-

@ 79008e78:dfac9395
2024-09-02 06:17:23
ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer
----
ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer นั้นจะช่วยให้เราสามารถชำระเงินผ่านทางออนไลน์ได้โดยตรงจากฝ่ายหนึ่งไปยังอีกฝ่ายหนึ่งโดยไม่ต้องผ่านตัวกลางอย่างพวกสถาบันการเงิน โดยใช้ digital signature เป็นส่วนหนึ่งในการแก้ปัญหานี้ แต่มันจะไม่มีประโยชน์ใด ๆ เลยหากยังคงต้องอาศัยตัวกลางที่เชื่อถือได้มาแก้ปัญหา double spending เราขอเสนอวิธีแก้ปัญหา double spending โดยใช้เครือข่ายแบบ peer-to-peer ให้เครือข่ายคอยประทับเวลาธุรกรรมต่าง ๆ ในระบบและนำมาเรียงร้อยกันเป็นเส้นสายของ proof-of-work ที่ใช้ hash เพื่อสร้างธุรกรรมที่ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ต้องทำ proof-of-work ใหม่ โดยให้เส้นสายที่ยาวที่สุดนั้น ไม่เพียงแต่ทำหน้าที่เป็นลำดับของธุรกรรมที่เกิดขึ้นเท่านั้น แต่ยังเป็นสิ่งที่พิสูจน์ได้ว่ามาจากกำลังประมวลผล CPU ที่มากที่สุด และตราบใดที่ nodes ส่วนใหญ่ไม่ได้ร่วมมือกันโจมตีเครือข่ายและยังคงควบคุมกำลังประมวลผลส่วนใหญ่ในระบบไว้ พวกเขาก็จะสร้างเส้นสายที่ยาวที่สุดและสามารถเอาชนะผู้ประสงค์ร้ายที่จะโจมตีระบบได้ ตัวเครือข่ายเองไม่ได้ต้องมีโครงสร้างอะไรที่ซับซ้อน ข้อมูลต่าง ๆ ในเครือข่ายจะถูกกระจายส่งต่อโดยไม่ต้องสนใจว่าผู้รับจะได้รับหรือไม่ และ nodes ต่าง ๆ เองก็สามารถที่จะออกจากเครือข่ายและกลับเข้าร่วมใหม่ได้ตามที่ต้องการ โดยยอมรับเส้น proof-of-work ที่ยาวที่สุด เป็นหลักฐานของสิ่งที่เกิดขึ้นในขณะที่ node นั้น ๆ ไม่ได้อยู่ในเครือข่าย
1.บทนำ (Introduction)
-----
ไม่ว่าใครจะใคร่ซื้อใคร่ขายอะไรใด ๆ บนอินเตอร์เน็ตนั้น ก็จำเป็นต้องพึ่งพาสถาบันการเงินในฐานะของบุคคลที่สามเพื่อดำเนินการชำระเงินทางอิเล็กทรอนิกส์เสมอ ๆ ซึ่งถึงแม้ว่าระบบนี้มันจะทำงานได้ดีสำหรับธุรกรรมส่วนใหญ่ ๆ แต่ระบบก็ก็มีจุดอ่อนอยู่ที่ยังต้องอาศัยความไว้เนื้อเชื่อใจ (trust) ในระบบนี้การทำธุรกรรมที่ไม่สามารถย้อนกลับได้อย่างสมบูรณ์นั้นมันแทบจะเป็นไปไม่ได้เลย เนื่องจากสถาบันการเงินไม่สามารถหลีกเลี่ยงการเป็นตัวกลางในการไกล่เกลี่ยข้อพิพาทต่าง ๆ ที่อาจเกิดขึ้นได้ มิหนำซ้ำต้นทุนในการไกล่เกลี่ยยังทำให้ต้นทุนการทำธุรกรรมเพิ่มสูงขึ้น และเมื่อต้นทุนสูงขึ้นขนาดของธุรกรรมที่สามารถใช้งานได้จริงก็สูงขึ้นตามไปด้วย ธุรกรรมเล็ก ๆ น้อย ๆ ก็ไม่สามารถเกิดขึ้นได้ เมื่อมีความเป็นไปได้ที่ธุรกรรมจะเกิดการย้อนกลับ ความจำเป็นในการสร้างความไว้วางใจก็ยิ่งทวีคูณมากขึ้น ผู้ค้าก็จำเป็นต้องระมัดระวังลูกค้า ต้องเรียกร้องข้อมูลมากกว่าที่จำเป็น การฉ้อโกงกลายเป็นเรื่องที่หลีกเลี่ยงไม่ได้เพราะต้นทุนและความไม่แน่นอนในทำธุรกรรมเหล่านี้ แน่นอนว่าเราสามารถหลีกเลี่ยงมันได้โดยการใช้เงินสด แต่ก็ไม่มีกลไกใดที่ทำให้สามารถใช้เงินสดผ่านช่องทางการสื่อสาร (เอาให้เข้าใจง่ายก็อินเตอร์เน็ต)ได้ โดยไม่ต้องมีตัวกลาง ;-;
แปลว่าสิ่งที่จำเป็นสำหรับการแก้ไขปัญหานี้คือระบบการชำระเงินทางอิเล็กทรอนิกส์ ที่อยู่บนพื้นฐานของการพิสูจน์ด้วยการเข้ารหัสแทนที่จะเป็นความไว้วางใจ ซึ่งจะทำให้คู่สัญญาสองฝ่ายที่ยินยอมสามารถทำธุรกรรมร่วมกันได้โดยตรง โดยไม่จำเป็นต้องมีบุคคลที่สามมาคอยเป็นตัวกลาง ธุรกรรมที่ยากต่อการย้อนกลับจะช่วยปกป้องผู้ขายจากการฉ้อโกง และสามารถใช้กลไก escrow เพื่อปกป้องผู้ซื้อได้อีกด้วย ในเอกสารชุดนี้ เราขอเสนอวิธีแก้ปัญหาการใช้จ่ายซ้ำซ้อนโดยใช้เซิร์ฟเวอร์ timestamp กระจายศูนย์แบบ peer-to-peer เพื่อสร้างหลักฐานการคำนวณลำดับเวลาของธุรกรรม โดยระบบนี้จะปลอดภัยตราบใดที่กลุ่มของ node ที่ซื่อสัตย์ ยังคงมีกำลังประมวลผลที่มากกว่ากลุ่มที่ประสงค์ร้ายกับระบบ
2.ธุรกรรม (Transactions)
----
นิยามของเหรียญอิเล็กทรอนิกส์ในที่นี้ คือห่วงโซ่ที่คล้องเกี่ยวกันของ digital signature โดยที่เจ้าของเหรียญอิเล็กทรอนิกส์จะโอนเหรียญไปยังเจ้าของคนถัดไป ด้วยการลง digital signature บน hash ของธุรกรรมก่อนหน้ารวมถึงกุญแจสาธารณะของเจ้าของคนถัดไป และผนวกมันไว้ที่ส่วนท้ายของธุรกรรม และผู้รับเงินเองก็สามารถตรวจสอบลายเซ็นเพื่อยืนยันความเป็นเจ้าของได้
https://image.nostr.build/a467896797a9fb9f98c3c234f0adb4df2376f2c3d9a7cc9d8672d7a9f5aa9efa.png
แน่นอนว่าปัญหาก็คือผู้รับเงินไม่สามารถตรวจสอบได้ว่าเจ้าของคนใดคนหนึ่งก่อนหน้าเขาได้ใช้เหรียญดังกล่าวซ้ำซ้อนมากกว่าหนึ่งครั้งหรือไม่ และวิธีการแก้ไขปัญหานี้โดยทั่วไปก็คงเป็นการกำหนดตัวกลางที่มีความน่าเชื่อถือมาเป็นคนตรวจสอบทุกธุรกรรมเพื่อป้องกันการใช้จ่ายซ้ำซ้อน และหลังจากการทำธุรกรรมแต่ละครั้ง เหรียญจะต้องถูกส่งกลับไปยังตัวกลางเพื่อออกเหรียญใหม่ และจะมีเพียงเหรียญที่ออกจากตัวกลางโดยตรงเท่านั้นที่จะเชื่อถือได้ว่าจะไม่ถูกใช้จ่ายซ้ำซ้อน แต่ปัญหาก็คือ ชะตากรรมของระบบเงินทั้งหมดจะขึ้นอยู่กับตัวกลางตัวนี้ เพราะทุกธุรกรรมจำเป็นจะต้องผ่านพวกเขา ซึ่งก็ไม่ต่างอะไรกับธนาคาร
เราจึงต้องการวิธีการที่ทำให้ผู้รับเงินทราบได้ว่าเจ้าของคนก่อน ๆ ไม่ได้ลงนามในธุรกรรมใด ๆ มาก่อน เพื่อให้บรรลุวัตถุประสงค์นี้ เราจะทำการนับว่าธุรกรรมที่เกิดขึ้นก่อนเป็นธุรกรรมที่ถูกต้อง และจะไม่สนใจความพยายามใด ๆ ในการที่จะใช้เหรียญนั้น ๆ ซ้ำอีก และวิธีเดียวที่ทำแบบนี้ได้ คือการรับรู้ถึงธุรกรรมทั้งหมด เช่นเดียวกับโมเดลที่ได้กล่าวข้างต้น ที่ตัวกลางจะรับรู้ถึงธุรกรรมทั้งหมดและตัดสินว่าธุรกรรมใดมาก่อนมาหลัง เพื่อให้บรรลุเป้าหมายนี้โดยไม่ต้องมีบุคคลที่สามที่เชื่อถือได้ ธุรกรรมทั้งหมดจะต้องถูกประกาศต่อสาธารณะ [1] และเราต้องการระบบที่ผู้เข้าร่วมเห็นพ้องในประวัติธุรกรรมชุดเดียวกันตามลำดับที่ได้รับ ส่วนผู้รับเงินก็จำเป็นจะต้องมีหลักฐานว่า ในขณะที่ทำธุรกรรม "โหนด" ส่วนใหญ่ในระบบเห็นพ้องต้องกันว่าธุรกรรมนั้นได้รับเป็นลำดับแรก(ไม่มีธุรกรรมที่ใช้เหรียญพวกนี้มาก่อน)
3.ระบบบันทึกเวลา (Timestamp Server)
----
สำหรับแนวทางการแก้ปัญหาในครั้งนี้ เราจะใช้ประโยชน์จาก timestamp server ที่จะทำหน้าที่บันทึก hash ของบล๊อกที่ต้องการให้มีการบันทึกเวลา และจากนั้นจะทำการเผยแพร่ hash ดังกล่าว เหมือนกับหนังสือพิมพ์หรือโพสต์ใน Usenet [2-5] (ฟีลแบบทุกคนจะเห็นโพสต์นี้น้าา ประมาณนั้น) การบันทึกเวลานี้จะพิสูจน์ได้ว่าข้อมูลที่ถูก hash นั้นจะต้องมีอยู่จริงในเวลานั้นเพื่อให้ได้มาซึ่ง hash ดังกล่าว แต่ละการบันทึกเวลาจะรวมการบันทึกเวลาของหน้านี้ไว้ใน hash ของมันเพื่อสร้างเป็น chain โดยการบันทึกเวลาแต่ละครั้งจะยืนยันความถูกต้องของการบันทึกก่อนหน้าได้อีกด้วยด้วย
https://image.nostr.build/ddf92417c45dbb6e25da0af80a10d4cdbc3e725d047d65f54a3e3bfcf358c4d6.png
4.พรูฟ-ออฟ-เวิร์ค (Proof-of-Work)
----
ในการสร้าง Timestamp Server แบบกระจายศูนย์บนพื้นฐานแบบ peer to peer เราจำเป็นต้องใช้ระบบ Proof-of-Work (PoW) ที่คล้ายกับ Hashcash ของ Adam Back [6] แทนที่จะใช้วิธีการแบบเดิม ๆ อย่างการประกาศในหนังสือพิมพ์หรือ Usenet โดย PoW ใช้ในการตรวจสอบค่าที่มาจากกระบวนการ hash เช่น SHA-256 แล้ว ผลลัพธ์ที่ได้ (Hash) จะขึ้นต้นด้วยเลขศูนย์จำนวนหนึ่ง โดยที่ work (ประมาณว่าพลังประมวลผล) ที่ต้องใช้จะเพิ่มขึ้นแบบทวีคูณตามจำนวนเลขศูนย์ที่ต้องการ และสามารถตรวจสอบได้โดยการรัน Hash เพียงครั้งเดียว
ซึ่งสำหรับ timestamp network ของเรานั้น เราใช้ PoW โดยการเพิ่มค่า Nonce ในบล็อกไปเรื่อย ๆ จนกว่าจะพบค่าที่ทำให้ Hash ของบล็อกนั้นมีเลขศูนย์ตามที่กำหนด และเมื่อใช้กำลังประมวลผลของ CPU ไปกับการทำ PoW จนสำเร็จแล้ว บล็อกจะไม่สามารถเปลี่ยนแปลงได้ หากไม่มีการทำงานซ้ำใหม่ เนื่องจากบล็อกที่สร้างขึ้นภายหลังจะเชื่อมโยงกับบล็อกก่อนหน้า การเปลี่ยนแปลงบล็อกใด ๆ จะต้องทำ PoW ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด
https://image.nostr.build/c039ef4ca6833cb1ecee65ac5991df2406be9b7e490b86b3b19f94f267767182.png
นอกจากนี้ PoW ยังช่วยแก้ปัญหาของเสียงส่วนมากที่มาตัดสินใจในระบบนี้ เพราะหากเสียงข้างมากอ้างอิงจากหลักการหนึ่ง IP หนึ่งเสียง ใครก็ตามที่สามารถสร้าง IP ได้จำนวนมากก็จะสามารถควบคุมระบบได้ จึงใช้หลักการหนึ่ง CPU หนึ่งเสียงแทน การตัดสินใจของเสียงข้างมากจะแสดงด้วย Chain ที่ยาวที่สุด ซึ่งบ่งบอกถึงความพยายามในการคำนวณ (Proof-of-Work) ที่มากที่สุด หาก Node ที่ซื่อสัตย์ (Honest nodes) มีกำลังประมวลผลของ CPU ส่วนใหญ่อยู่ในการควบคุม Honest Chain ก็จะเติบโตเร็วที่สุดและแซงหน้า Chain อื่น ๆ ได้ ผู้โจมตีที่ต้องการแก้ไขบล็อกในอดีตจะต้องทำ Proof-of-Work ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด และต้องทำงานให้เร็วกว่า Honest Node ด้วย ซึ่งโอกาสที่ผู้โจมตีจะตามทันนั้นจะลดลงแบบทวีคูณเมื่อมีการเพิ่มบล็อกมากขึ้น
เพื่อชดเชยความเร็วของฮาร์ดแวร์ที่เพิ่มขึ้นและความสนใจในการรัน Node ที่ผันผวน ระดับความยากของ Proof-of-Work จะถูกกำหนดโดยค่าเฉลี่ย โดยตั้งเป้าไว้ที่จำนวนบล็อกเฉลี่ยต่อชั่วโมง หากสร้างบล็อกได้เร็วเกินไป ระดับความยากก็จะเพิ่มขึ้น
5.เครือข่าย (Network)
----
เครือข่ายนั้นมีการทำงาน ดังนี้
1. การประกาศธุรกรรมใหม่: ธุรกรรมใหม่จะถูกประกาศ (broadcast) ไปยังทุก node ในเครือข่าย
2. การรวบรวมธุรกรรม: แต่ละ node จะรวบรวมธุรกรรมใหม่ ๆ เหล่านี้ ไว้ในบล็อก
3. การค้นหา Proof-of-Work: แต่ละ node จะทำการคำนวณ เพื่อค้นหา Proof-of-Work ตามค่า difficulty สำหรับบล็อกนั้น ๆ
4. การประกาศบล็อก: เมื่อ node ใดค้นหา Proof-of-Work ได้แล้ว node นั้นจะทำการประกาศบล็อกไปยังทุก node ในเครือข่าย
5. การตรวจสอบและยอมรับบล็อก: node อื่น ๆ จะทำการตรวจสอบและยอมรับบล็อกนั้น เฉพาะเมื่อธุรกรรมทั้งหมดภายในบล็อกนั้นถูกต้องและยังไม่ถูกใช้มาก่อน
6. การสร้างบล็อกถัดไป: node ต่าง ๆ แสดงการยอมรับบล็อกโดยการเริ่มต้นสร้างบล็อกถัดไปใน chain ด้วย hash ของบล็อกที่ยอมรับ เป็น hash ก่อนหน้าในโครงสร้างของบล๊อกใหม่ที่กำลังสร้าง
node ต่าง ๆ จะถือว่า chain ที่ยาวที่สุดเป็น chain ที่ถูกต้องและจะทำงานเพื่อขยาย chain นั้นต่อไป หากมีสอง node ที่ได้ประกาศบล็อกเวอร์ชันที่แตกต่างกันในเวลาพร้อมกัน node บาง node อาจได้รับบล็อกหนึ่งก่อน อีกบล็อกหนึ่ง ในกรณีนี้ node เหล่านั้น จะทำงานบนบล็อกที่ได้รับก่อน แต่จะเก็บสำเนาของบล็อกอีกอันหนึ่งไว้ ในกรณีที่บล็อกนั้น กลายเป็นบล็อกที่อยู่ใน chain ที่ยาวกว่าปัญหาข้อโต้แย้งนี้ก็จะได้รับการแก้ไข เมื่อพบ Proof-of-Work อันถัดไปและ chain ใด chain หนึ่งยาวขึ้น node ที่กำลังทำงานอยู่บน chain ที่สั้นกว่าก็จะเปลี่ยนไปทำงานบน chain ที่ยาวกว่าแทน
การประกาศธุรกรรมใหม่ ไม่จำเป็นต้องไปถึงทุก node ในเครือข่าย ตราบใดที่พวกเขายังไปถึง node ส่วนใหญ่ในระบบได้ ธุรกรรมเหล่านั้นก็จะถูกบรรจุอยู่ในบล็อกในไม่ช้า นอกจากนี้การประกาศบล็อกยังไม่ต้องกังวลเรื่องจะมีบล๊อกที่สูญหาย เนื่องจากหากว่า node ไม่ได้รับบล็อกใด ๆ node ก็จะตระหนักได้ว่าพลาดบล็อกก่อนหน้าไปเมื่อได้รับบล๊อกใหม่มา และ node จะทำการร้องขอ block ที่ขาดไปจากเครือข่าย
6.แรงจูงใจ(Incentive)
----
โดยปกติแล้ว ธุรกรรมแรกของแต่ละบล๊อกนั้นจะเป็นธุรกรรมพิเศษที่จะขุดเหรียญที่สร้างขึ้นใหม่ซึ่งเป็นกรรมสิทธิ์ของผู้สร้างบล็อกนั้น ๆ ซึ่งจะเป็นการเพิ่มแรงจูงใจให้กับ node ต่าง ๆ ในการสนับสนุนเครือข่าย และเป็นวิธีการกระจายเหรียญให้หมุนเวียน เนื่องจากไม่มีหน่วยงานส่วนกลางที่ทำหน้าที่ในการออกเหรียญ การเพิ่มเหรียญใหม่ในปริมาณคงที่อย่างต่อเนื่องนั้นคล้ายคลึงกับการที่คนงานเหมืองทองคำใช้แรง และ เวลา เพื่อเพิ่มทองคำให้หมุนเวียน ในกรณีนี้ คือ เวลา กำลังประมวลผล และไฟฟ้าที่ถูกใช้ไป
นอกจากนี้แรงจูงใจจะมาจากค่าธรรมเนียมการทำธุรกรรม หากมูลค่าผลลัพธ์ของธุรกรรมน้อยกว่ามูลค่าที่ใส่เข้ามา ส่วนต่างนั้นก็คือค่าธรรมเนียมการทำธุรกรรมที่จะเพิ่มเข้าไปในมูลค่าแรงจูงใจของบล็อกที่มีธุรกรรมนั้น เมื่อเหรียญทั้งหมดในระบบมีจำนวนเท่ากับที่กำหนดไว้แล้ว แรงจูงใจหลักก็จะถูกเปลี่ยนมาเป็นค่าธรรมเนียมการทำธุรกรรม และปราศจากภาวะเงินเฟ้อโดยสิ้นเชิง
แรงจูงใจอาจช่วยกระตุ้นให้ node ต่าง ๆ ยังคงซื่อสัตย์ หากผู้โจมตีที่ละโมบสามารถรวบรวมกำลังประมวลผล ได้มากกว่า node ที่ซื่อสัตย์ทั้งหมด เขาจะต้องเลือกระหว่างการใช้มันเพื่อฉ้อโกงผู้อื่นโดยการใช้จ่ายซ้ำซ้อน หรือใช้มันเพื่อสร้างเหรียญใหม่ พวกเขาจะพบว่าการเล่นตามกฎ กฎที่เอื้อประโยชน์ให้กับเขาด้วยเหรียญใหม่มากกว่าคนอื่น ๆ รวมกันนั้นทำกำไรได้มากกว่าการบ่อนทำลายระบบและความถูกต้องของทรัพย์สินของเขาเอง
7.การจัดการพื้นที่ดิสก์(Reclaiming Disk Space)
----
เมื่อธุรกรรมถูกบรรจุลงในบล๊อกแล้ว สามารถกำจัดธุรกรรมที่ใช้ไปแล้วก่อนหน้านั้นออกได้เพื่อประหยัดพื้นที่ดิสก์ แต่การจะทำอย่างนี้ได้โดยไม่ให้เลข hash ของบล๊อกมีการเปลี่ยนแปลงนั้น ธุรกรรมจึงจำเป็นต้องถูก hash ในรูปแบบของ Merkle Tree [7][2][5] โดยมีแค่ root node ของ tree เท่านั้นที่จะรวมอยู่ใน hash ของบล๊อก นี่เป็นวิธีที่ทำให้สามารถบีบอัดข้อมูลในบล๊อกเก่า ๆ ได้โดยการตัดพวก hash ส่วนอื่น ๆ ของ tree ที่ไม่ใช่ root node ออก (ไม่จำเป็นต้องเก็บ hash ในชั้นอื่น ๆ ของ tree)
https://image.nostr.build/3ed95334891d91baca3f3f6f624a7ae22620be4ebfe0db5eb652cfce11255b9a.png
โดยในส่วน header ของบล็อกที่ไม่มีธุรกรรมจะมีขนาดประมาณ 80 ไบต์ หากเราสมมติว่าบล็อกถูกสร้างขึ้นทุก ๆ 10 นาที 80 ไบต์ * 6 * 24 * 365 = 4.2MB ต่อปี โดยที่ระบบคอมพิวเตอร์ทั่วไปที่วางขายในปี 2551 มี RAM 2GB และกฎของมัวร์ทำนายการเติบโตในปัจจุบันที่ 1.2GB ต่อปี การจัดเก็บข้อมูลไม่น่าจะเป็นปัญหาแม้ว่าส่วนหัวของบล็อกจะต้องถูกเก็บไว้ในหน่วยความจำก็ตาม
8.การตรวจสอบธุรกรรม (Simplified Payment Verification)
----
การที่จะยืนยันการชำระเงินโดยไม่จำเป็นต้องรัน full node ได้นั้น ผู้ใช้เพียงแค่เก็บสำเนาของส่วนหัวบล็อก (block header) ของสายบล็อก (chain) ที่ยาวที่สุด ซึ่งสามารถรับได้โดยการสอบถามจาก node อื่น ๆ ในเครือข่ายจนมั่นใจว่าได้รับสายที่ยาวที่สุด และรับ Merkle branch ที่เชื่อมโยงธุรกรรมกับบล็อกที่มีการประทับเวลา (Timestamp) อยู่ ถึงแม้ผู้ใช้จะไม่สามารถตรวจสอบธุรกรรมด้วยตัวเองได้ แต่การเชื่อมโยงธุรกรรมกับตำแหน่งในสายบล็อกจะทำให้เห็นว่า node ในเครือข่ายยอมรับแล้ว และบล็อกที่เพิ่มเข้ามาหลังจากนั้นเป็นการยืนยันเพิ่มเติมว่าเครือข่ายยอมรับธุรกรรมนี้แล้ว
https://i.imgur.com/VXtLpRF.png
การตรวจสอบดังกล่าวจะเชื่อถือได้ตราบใดที่ node ที่ซื่อสัตย์ยังคงควบคุมเครือข่าย แต่จะมีความเสี่ยงมากขึ้นหากเครือข่ายถูกโจมตีและถูกควบคุม ในขณะที่ node ในเครือข่ายสามารถตรวจสอบธุรกรรมได้ด้วยตัวเอง แต่วิธีการแบบง่ายนี้อาจถูกหลอกลวงโดยการใช้ธุรกรรมปลอมของผู้โจมตี ตราบใดที่ผู้โจมตียังคงสามารถควบคุมเครือข่ายได้ กลยุทธ์หนึ่งในการป้องกันปัญหานี้คือ การรับการแจ้งเตือนจาก node อื่น ๆ ในเครือข่ายเมื่อตรวจพบบล็อกที่ไม่ถูกต้อง ซึ่งจะแจ้งให้ซอฟต์แวร์ของผู้ใช้ดาวน์โหลดบล็อกแบบเต็มและธุรกรรมที่แจ้งเตือน เพื่อยืนยันความไม่สอดคล้องกัน ธุรกิจที่ได้รับการชำระเงินบ่อยครั้งอาจยังคงต้องการรัน node ของตนเอง เพื่อความปลอดภัยที่เป็นอิสระและการตรวจสอบที่รวดเร็วยิ่งขึ้น
9.การควบรวมและแบ่งย่อยมูลค่า(Combining and Splitting Value)
----
แม้ว่าการจัดการเหรียญหลาย ๆ เหรียญจะเป็นสิ่งที่สามารถทำได้ แต่การจัดการธุรกรรมแยกต่างหากสำหรับแต่ละเหรียญในการโอนก็คงเป็นเรื่องที่น่าปวดหัวอยู่ดี ฉะนั้นแล้วเพื่อให้สามารถแยกและรวมมูลค่ากันได้ ธุรกรรมจึงสามารถมี input และ output ได้หลายรายการ ซึ่งโดยปกติแล้วจะมี input เดียวจากธุรกรรมก่อนหน้าที่มีขนาดใหญ่กว่า หรือ input จำนวนเล็ก ๆ หลาย ๆ รายการ และ output ไม่เกินสองรายการ คือ รายการหนึ่งสำหรับการชำระเงิน และอีกหนึ่งรายการสำหรับการส่งเงินทอน หากมีกลับไปยังผู้ส่ง
https://image.nostr.build/9c6d3ce0e9f08c5b3fa3b82c2088ac6235603e5c0df3469060e6c9f74bce32fc.png
ควรสังเกตว่า fan-out (กระจายของธุรกรรม) ซึ่งเป็นกรณีที่ธุรกรรม ธุรกรรมหนึ่งนั้นขึ้นอยู่กับหลายธุรกรรม และธุรกรรมเหล่านั้นเองก็ขึ้นอยู่กับอีกหลายธุรกรรม แต่ไม่ใช่ปัญหาในที่นี้ เพราะไม่มีความจำเป็นในการดึงประวัติการทำธุรกรรมทั้งหมดออกมาเป็นสำเนา
10.ความเป็นส่วนตัว(Privacy)
----
ในรูปแบบธนาคารแบบดั้งเดิมนั้น ความเป็นส่วนตัวเกิดขึ้นได้ด้วยการจำกัดการเข้าถึงข้อมูล โดยให้เฉพาะผู้ที่เกี่ยวข้องและบุคคลที่สามที่ได้รับความไว้วางใจเท่านั้น แต่เนื่องจากในระบบนี้เรามีความจำเป็นในการประกาศธุรกรรมทั้งหมดต่อสาธารณะ ทำให้ไม่สามารถใช้วิธีนี้ได้ แต่ยังจำเป็นต้องคงความเป็นส่วนตัวไว้ โดยการแบ่งการไหลของข้อมูล ด้วยการไม่เปิดเผยตัวตนของเจ้าของ public key คนทั่วไปสามารถเห็นว่ามีคนกำลังส่งเงินจำนวนหนึ่งให้กับคนอื่น แต่จะไม่ทราบข้อมูลที่เชื่อมโยงธุรกรรมนั้นกับบุคคลใด ๆ ซึ่งคล้ายกับระดับข้อมูลที่เปิดเผยโดยตลาดหลักทรัพย์ ซึ่งมีการเปิดเผยเวลาและขนาดของการซื้อขายแต่ละครั้งต่อสาธารณะ แต่ไม่ได้ระบุว่าคู่สัญญาคือใคร
https://image.nostr.build/6ec3c84c7878dbd4558d2045518384daf5a341e86f4194cf367cc8426c2d72a7.png
เพื่อเสริมในเรื่องของความปลอดภัย ควรใช้ key pair ใหม่สำหรับการทำธุรกรรมในแต่ละครั้ง เพื่อป้องกันไม่ให้เชื่อมโยงกับเจ้าของคนเดียวกันได้ อย่างไรก็ตาม การเชื่อมโยงบางอย่างยังคงหลีกเลี่ยงไม่ได้ ในธุรกรรมที่มี input หลายรายการ ซึ่งจำเป็นต้องเปิดเผยว่า input เหล่านั้นเป็นของเจ้าของคนเดียวกัน ความเสี่ยงก็คือ หากมีการเปิดเผยตัวตนของเจ้าของคีย์ การเชื่อมโยงอาจเปิดเผยธุรกรรมอื่น ๆ ที่เป็นของเจ้าของรายเดียวกันได้
11.การคำนวณ(Calculations)
----
หากลองพิจารณาสถานการณ์ที่ผู้โจมตีพยายามสร้าง chain ปลอมให้เร็วกว่า chain จริง แม้ว่าจะทำได้สำเร็จ แต่มันก็ไม่สามารถทำให้ระบบเปิดรับการเปลี่ยนแปลงตามอำเภอใจได้อยู่ดี เช่น การสร้างมูลค่าจากอากาศธาตุ หรือการรับเงินที่ไม่เคยเป็นของผู้โจมตีมาก่อน Node ต่าง ๆ จะไม่ยอมรับธุรกรรมที่ไม่ถูกต้องเป็นการชำระเงิน และ Node ที่สุจริตก็จะไม่ยอมรับบล็อกที่มีธุรกรรมเหล่านั้นอย่างแน่นอน ผู้โจมตีทำได้เพียงพยายามเปลี่ยนแปลงธุรกรรมของตนเอง เพื่อนำเงินที่ใช้ไปแล้วกลับคืนมาเท่านั้น
การแข่งขันระหว่าง chain สุจริตกับ chain ของผู้โจมตี สามารถอธิบายได้ด้วยแบบจำลองการเดินสุ่มทวินาม (Binomial Random Walk) โดยเหตุการณ์ที่สำเร็จ หมายถึง chain ที่สุจริตถูกขยายออกไปอีกหนึ่งบล็อก เพิ่มความยาวนำหน้าไป +1 และเหตุการณ์ที่ล้มเหลว หมายถึง chain ของผู้โจมตีถูกขยายออกไปหนึ่งบล็อก ลดช่องว่างลง -1
ความน่าจะเป็นที่ผู้โจมตีจะไล่ตามทันจากช่องว่างที่กำหนด สามารถเปรียบเทียบด้วย Gambler's Ruin problem โดยสมมติว่านักพนันที่มีเครดิตไม่จำกัด เริ่มต้นด้วยการขาดทุน และเล่นพนันไปเรื่อย ๆ เพื่อให้ถึงจุดคุ้มทุน เราสามารถคำนวณความน่าจะเป็นที่เขาจะกลับมาถึงจุดคุ้มทุนได้ หรือความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน chain ที่สุจริตได้ ดังนี้ [8]:
p = ความน่าจะเป็นที่ Node ที่สุจริตจะพบบล็อกถัดไป
q = ความน่าจะเป็นที่ผู้โจมตีจะพบบล็อกถัดไป
qz = ความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน จากที่ตามหลังอยู่ z บล็อก
https://i.imgur.com/vePe255.png
จากสมมติฐานที่ว่า p > q ความน่าจะเป็นจะลดลงแบบเอกซ์โพเนนเชียล เมื่อจำนวนบล็อกที่ผู้โจมตีต้องไล่ตามทันเพิ่มขึ้น หากเขาไม่สามารถพุ่งขึ้นนำได้อย่างรวดเร็วตั้งแต่แรก โอกาสของเขาก็จะลดลงจนน้อยมาก ๆ เมื่อเขาตามหลังมากขึ้นเรื่อย ๆ
ทีนี้ลองพิจารณาว่า ผู้รับธุรกรรมใหม่ต้องรอเป็นเวลานานเท่าใด จึงจะแน่ใจได้ว่าผู้ส่งไม่สามารถเปลี่ยนแปลงธุรกรรมได้แล้ว เราสมมติว่าผู้ส่งเป็นผู้โจมตี ที่ต้องการให้ผู้รับเชื่อว่าเขาได้รับเงินไปแล้ว จากนั้นจึงเปลี่ยนให้เงินกลับเข้าหาตัวเองหลังจากเวลาผ่านไประยะหนึ่ง ผู้รับจะได้รับแจ้งเมื่อเกิดเหตุการณ์นี้ขึ้น แต่ผู้ส่งหวังว่ามันจะสายเกินไปแล้ว
ผู้รับจะสร้างคู่กุญแจใหม่ และให้กุญแจสาธารณะแก่ผู้ส่งไม่นานก่อนที่จะลงนาม ซึ่งจะป้องกันไม่ให้ผู้ส่งเตรียมบล็อกเชนปลอมไว้ล่วงหน้า โดยการทำงานอย่างต่อเนื่องจนกว่าเขาจะมีโอกาสได้บล็อกที่ยาวพอ จากนั้นจึงดำเนินธุรกรรมในทันที เมื่อส่งธุรกรรมแล้ว ผู้ส่งที่ไม่สุจริตจะเริ่มทำงานอย่างลับ ๆ บนบล็อกเชนคู่ขนาน ที่มีธุรกรรมในเวอร์ชันของเขาเองอยู่
ผู้รับจะรอจนกว่าธุรกรรมจะถูกเพิ่มลงในบล็อก และมีบล็อกที่ถูกเชื่อมต่อตามหลังมาอีก z บล็อก เขาไม่ทราบจำนวนความคืบหน้าที่แน่นอนที่ผู้โจมตีได้ทำไปแล้ว แต่สมมติว่าบล็อกที่สุจริตใช้เวลาเฉลี่ยต่อบล็อกตามที่คาดไว้ ความคืบหน้าที่อาจเกิดขึ้นได้ของผู้โจมตีจะเป็นการแจกแจงแบบปัวซง (Poisson distribution) ซึ่งมีค่าคาดหวังดังนี้:
https://i.imgur.com/mYsb48i.png
เพื่อให้ได้ความน่าจะเป็นที่ผู้โจมตียังคงสามารถไล่ทันได้ เราจะคูณความหนาแน่นของปัวซง สำหรับความคืบหน้าแต่ละระดับที่เขาสามารถทำได้ ด้วยความน่าจะเป็นที่เขาสามารถไล่ทันจากจุดนั้น:
https://i.imgur.com/jQGkQ8r.png
จัดเรียงใหม่เพื่อหลีกเลี่ยง infinite tail ของการแจกแจง
https://i.imgur.com/OOO6Gm9.png
แปลงมันให้เป็น C code
#include <math.h>
double AttackerSuccessProbability(double q, int z)
{
double p = 1.0 - q;
double lambda = z * (q / p);
double sum = 1.0;
int i, k;
for (k = 0; k <= z; k++)
{
double poisson = exp(-lambda);
for (i = 1; i <= k; i++)
poisson *= lambda / i;
sum -= poisson * (1 - pow(q / p, z - k));
}
return sum;
}
เมื่อรันผลลัพธ์บางส่วน เราจะเห็นว่าความน่าจะเป็นลดลงแบบเอกซ์โพเนนเชียลเมื่อ z เพิ่มขึ้น
q=0.1
z=0 P=1.0000000
z=1 P=0.2045873
z=2 P=0.0509779
z=3 P=0.0131722
z=4 P=0.0034552
z=5 P=0.0009137
z=6 P=0.0002428
z=7 P=0.0000647
z=8 P=0.0000173
z=9 P=0.0000046
z=10 P=0.0000012
q=0.3
z=0 P=1.0000000
z=5 P=0.1773523
z=10 P=0.0416605
z=15 P=0.0101008
z=20 P=0.0024804
z=25 P=0.0006132
z=30 P=0.0001522
z=35 P=0.0000379
z=40 P=0.0000095
z=45 P=0.0000024
z=50 P=0.0000006
การแก้หาค่า P ที่น้อยกว่า 0.1%...
P < 0.001
q=0.10 z=5
q=0.15 z=8
q=0.20 z=11
q=0.25 z=15
q=0.30 z=24
q=0.35 z=41
q=0.40 z=89
q=0.45 z=340
12.สรุป(Conclusion)
เราได้นำเสนอระบบธุรกรรมอิเล็กทรอนิกส์ที่ไม่ต้องพึ่งพาความไว้วางใจ เริ่มต้นจากกรอบแนวคิดของเหรียญที่สร้างจากลายเซ็นดิจิทัล ซึ่งช่วยควบคุมความเป็นเจ้าของได้อย่างดีแต่ก็ยังไม่สมบูรณ์ หากปราศจากวิธีการป้องกันการใช้จ่ายซ้ำซ้อน เพื่อแก้ปัญหานี้ เราจึงเสนอเครือข่ายแบบเพียร์ทูเพียร์ที่ใช้ proof-of-work ในการบันทึกประวัติธุรกรรมสาธารณะ ซึ่งจะกลายเป็นเรื่องยากอย่างมากสำหรับผู้โจมตีที่จะเปลี่ยนแปลง หาก node ที่ซื่อสัตย์ควบคุมพลังประมวลผล CPU ส่วนใหญ่ เครือข่ายนี้มีความแข็งแกร่งในความเรียบง่ายที่ไม่มีโครงสร้างใด ๆ ที่ซับซ้อน node ต่าง ๆ ทำงานพร้อมกันโดยประสานงานกันเพียงเล็กน้อย ไม่จำเป็นต้องระบุตัวตน เนื่องจากข้อความไม่ได้ถูกส่งไปยังสถานที่ใดสถานที่หนึ่งโดยเฉพาะ และเพียงแค่ต้องส่งมอบให้ถึงมือผู้รับอย่างดีที่สุด node สามารถออกจากและเข้าร่วมเครือข่ายได้ตามต้องการ โดยยอมรับ chain ที่มี proof-of-work มากที่สุดเป็นสิ่งที่เกิดขึ้นในขณะที่ไม่ได้เชื่อมต่อ พวกเขาโหวตด้วยพลังประมวลผล CPU แสดงการยอมรับบล็อกที่ถูกต้องโดยการทำงานเพื่อขยายบล็อก และปฏิเสธบล็อกที่ไม่ถูกต้องโดยการปฏิเสธที่จะทำงานกับบล็อกเหล่านั้น กฎและแรงจูงใจใด ๆ ที่จำเป็นสามารถบังคับใช้ได้ด้วยกลไกฉันทามตินี้
ไปอ่านต่อกันเองเด้ออ
---
[1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998.
[2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal
trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999.
[3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no
2, pages 99-111, 1991.
[4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping,"
In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993.
[5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference
on Computer and Communications Security, pages 28-35, April 1997.
[6] A. Back, "Hashcash - a denial of service counter-measure,"
http://www.hashcash.org/papers/hashcash.pdf, 2002.
[7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and
Privacy, IEEE Computer Society, pages 122-133, April 1980.
[8] W. Feller, "An introduction to probability theory and its applications," 1957.
-

@ 79008e78:dfac9395
2024-09-02 06:17:05
Nostr: โปรโตคอลทางเลือกใหม่สำหรับโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม
---
Nostr คือโปรโตคอลแบบเปิดที่เรียบง่าย ซึ่งช่วยให้สามารถสร้างโซเชียลมีเดียระดับโลกที่กระจายอำนาจและป้องกันการเซ็นเซอร์ได้
จากที่กล่าวข้างต้น เราสามารถพูดได้ว่า Nostr นั้นถูกออกแบบมาให้ใช้งานง่าย โดยมีเป้าหมายหลัก ๆ เพื่อสร้างเครือข่ายโซเชียลระดับโลกที่ปราศจากการเซ็นเซอร์ แล้วทำไมมันถึงทำอย่างนั้นได้? ในจุดนี้เราก็ต้องมาเจาะดูคุณสมบัติหลัก ๆ ของโปรโตคอลที่เรียกว่า Nostr กันก่อน:
**เรียบง่าย**
- โปรโตคอลนี้ใช้โครงสร้างข้อมูลแบบ Event Object ที่เรียบง่ายและยืดหยุ่น (ซึ่งส่งเป็น JSON ธรรมดา) และใช้การเข้ารหัสแบบ Elliptic-curve มาตรฐานสำหรับคีย์และลายเซ็น
- ช่องทางการสื่อสารที่รองรับเพียงอย่างเดียวคือการเชื่อมต่อ WebSockets จากไคลเอนต์ไปยังรีเลย์
- การออกแบบนี้ทำให้ง่ายต่อการพัฒนาไม่ว่าจะไคลเอนต์หรือรีเลย์ และยังช่วยส่งเสริมความหลากหลายของซอฟต์แวร์
**ยืดหยุ่น**
- เนื่องจาก Nostr ไม่ได้พึ่งพาเซิร์ฟเวอร์ที่เชื่อถือได้เพียงจำนวนหยิบมือ สำหรับการเคลื่อนย้ายหรือจัดเก็บข้อมูล แต่ใช้เซิร์ฟเวอร์จำนวนมหาศาลและกระจายตัวอยู่ทั่วโลก จึงมีความยืดหยุ่นสูง และมีการกระจายศูนย์อย่างแท้จริง
- โปรโตคอลนี้ถูกออกแบบมาโดยคำนึงถึงความเป็นไปได้ที่รีเลย์จะหายไป และอนุญาตให้ผู้ใช้เชื่อมต่อและเผยแพร่ข้อมูลไปยังรีเลย์จำนวนมากได้ตามต้องการ และยังสามารถเปลี่ยนแปลงได้ตลอดเวลาอีกด้วย
**ตรวจสอบได้**
- เนื่องจากบัญชี Nostr ใช้การเข้ารหัสแบบ PKE จึงง่ายต่อการตรวจสอบว่าข้อความถูกส่งมาจากผู้ใช้ที่ระบุจริงหรือไม่
เช่นเดียวกับ HTTP หรือ TCP-IP Nostr เป็นโปรโตคอลหรือมาตรฐานแบบเปิดที่ทุกคนสามารถนำไปสร้างต่อยอดได้ มันไม่ใช่แอปหรือบริการที่คุณจำเป็นต้องลงทะเบียน
แล้วทำไมเราถึงต้องการ Nostr?
---
ถึงในปัจจุบันโซเชียลมีเดียจะได้พัฒนามาเป็นช่องทางสำคัญในการไหลเวียนของข้อมูลทั่วโลก กลายเป็นช่องทางหลักในการติดต่อสื่อสาร แต่น่าเสียดายที่ระบบโซเชียลมีเดียในปัจจุบันของเรานั้นมีข้อบกพร่องมากมาย:
1. ใช้ความสนใจของคุณเพื่อขายโฆษณา
2. ใช้เทคนิคแปลกๆ เพื่อทำให้คุณเสพติด (อ้างอิงจากข้อ 1)
3. ตัดสินใจว่าจะแสดงเนื้อหาใดให้คุณเห็นโดยใช้อัลกอริทึมลับที่คุณไม่สามารถตรวจสอบหรือเปลี่ยนแปลงได้
4. ควบคุมอย่างเต็มที่ว่าใครสามารถเข้าร่วมและใครถูกเซ็นเซอร์
5. เต็มไปด้วยสแปมและบอท
ด้วยข้อจำกัดเหล่านี้ Nostr จึงเป็นทางเลือกที่น่าสนใจในการสร้างโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม
องค์ประกอบของโปรโตคอลที่ชื่อว่า Nostr
---
หลังจากได้ทำความรู้จัก Nostr กันไปแล้วเมื่อคราวก่อน คราวนี้เรามาเจาะดูองค์ประกอบของโปรโตคอลนี้กันดีกว่า
**Keys ระบบบัญชีผู้ใช้และรหัสผ่านสำหรับ Nostr**
- บัญชี Nostr แต่ละบัญชีจะใช้คู่กุญแจสาธารณะ/ส่วนตัว (Public/Private Key ) เปรียบเทียบง่าย ๆ คือ กุญแจสาธารณะของคุณคือชื่อผู้ใช้ และกุญแจส่วนตัวก็เป็นรหัสผ่าน แต่ว่า ก็มีข้อแตกต่างที่สำคัญอยู่ นั่นคือ กุญแจส่วนตัวของคุณนั้นจะไม่สามารถรีเซ็ตได้หากเกิดการสูญหายขึ้น คุณจะเสียบัญชีนั้นไปตลอดกาล
- โดยทั่วไปแล้ว กุญแจสาธารณะจะแสดงเป็นข้อความที่ขึ้นต้นด้วย npub1 และกุญแจส่วนตัวจะขึ้นต้นด้วย nsec1
- ทั้งนี้คุณควรที่จะตรวจสอบให้แน่ใจว่าคุณได้เก็บกุญแจส่วนตัวของคุณไว้ในที่ปลอดภัย เช่น โปรแกรมจัดการรหัสผ่านอย่างเช่น Bitwarden
**โปรโตคอลกับไคลเอนต์ ต่างกันอย่างไร?**
Nostr เองเป็นเพียงโปรโตคอล หมายความว่า Nostr นั้นเป็นเพียงกระบวนการที่ตกลงกันไว้สำหรับการส่งข้อความผ่านอินเทอร์เน็ต (เหมือนข้อกำหนด)
ซึ่งการที่คุณจะเข้าถึง Nostr (โปรโตคอล) นั้น ผู้ใช้ส่วนใหญ่จะใช้งานผ่านไคลเอนต์ ซึ่งตัวของไคลเอนต์นั้นอาจเป็นเว็บ แอปพลิเคชันเดสก์ท็อป หรือ แอปพลิเคชันมือถือ โดยไคลเอนต์สามารถดึงข้อมูลจากรีเลย์ และสร้างข้อมูลใหม่ และส่งข้อมูลนั้นไปยังรีเลย์เพื่อให้ผู้ใช้คนอื่น ๆ สามารถเรียกอ่าน ข้อมูลนั้น ๆ ได้ โดย "ข้อมูล" เพียงรูปแบบเดียวที่มีอยู่ใน Nostr คือสิ่งที่เราเรียกกันว่า event
**การพิสูจน์ความเป็นเจ้าของข้อมูลบน Nostr**
บน Nostr นั้นการพิสูจน์ตัวตนเป็นเรื่องที่ง่ายมากเนื่องจากทุก ๆ event ที่เกิดขึ้น **จำเป็น**ต้องมีลายเซ็นดิจิทัล (Digital Signature) โดยลายเซ็นนั้นจะช่วยให้มั่นใจได้ว่า ใครเป็นผู้สร้าง event นั้น ๆ ขึ้นมา โดยการพิสูจน์ทางคณิตศาสตร์
โดยในการสร้างลายเซ็นแต่ละครั้ง ไคลเอนต์จะจำเป็นต้องใช้กุญแจส่วนตัวของคุณ โดยทั่วไปแล้ว แอปพลิเคชันเจะมีที่ให้คุณใส่กุญแจส่วนตัวของคุณ เมื่อเปิดแอปพลิเคชันครั้งแรก พวกเขาสามารถคำนวณกุญแจสาธารณะของคุณได้จากกุญแจส่วนตัวเช่นกัน
ส่วนในกรณีที่คุณใช้งานผ่านเว็บแอป ผมไม่แนะนำให้ใส่กุญแจส่วนตัวลงไป แต่แนะนำให้ใช้ส่วนขยายของเบราว์เซอร์ ที่ใช้งานฟังก์ชันที่เกี่ยวข้องกับ Nostr ซึ่งอนุญาตให้เว็บไคลเอ็นต์ส่ง event ที่ยังไม่ถูกเซ็นมาให้ส่วนขยายและส่วนขยายจะทำหน้าที่เซ็น สำหรับวิธีนี้ เว็บไคลเอ็นต์ต่าง ๆ ไม่จำเป็นต้องรู้กุญแจส่วนตัวของคุณ แต่คุณก็ยังสามารถลงนามใน event ต่าง ๆ ได้ตามปกติ โดยส่วนขยายที่ได้รับความนิยมก็จะเป็น **Flamingo**, **Alby** และ **nos2x**
ไคลเอนต์ & รีเลย์
-----------
**ไคลเอนต์คืออะไร?**
หากจะอธิบายให้เห็นภาพอยากให้มองว่าไคลเอ็นต์ Nostr นั้นเป็นเหมือนกับแอปที่คุณใช้งานเพื่อเข้าถึง Twitter, Facebook, youtube เป็นต้น พวกมันคือ แอปพลิเคชัน, เว็บแอป ที่เชื่อมต่อคุณกับโลกของ Twitter, Facebook, youtube โดยตัวของไคลเอนต์ใน Nostr เองก็เปรียบเสมือนแอปต่าง ๆ ที่คุณใช้ดูหน้าฟีดนั่นเอง แต่ข้อดีของ Nostr ที่เหนือแอปพลิเคชันอื่น ๆ คือความเรียบง่ายและยืดหยุ่น ส่งผลให้ไคลเอ็นต์แต่ละตัวมีวิธีนำเสนอและใช้งานที่แตกต่างกันไป บางไคลเอ็นต์อาจออกแบบให้ใช้งานง่ายเหมือน Twitter บางตัวเน้นให้เห็นบทบาทสำคัญของรีเลย์ หรือโหนดที่กระจายข้อมูลอยู่ทั่วโลก บางตัวใช้ระบบอัลกอริทึมเพื่อให้แน่ใจว่าข้อมูลไม่ถูกปิดกั้น โดยไม่ทำให้ผู้ใช้งานรู้สึกยุ่งยาก
**เรียบง่ายและยืดหยุ่น?**
เนื่องจากการออกแบบของโปรโตคอลที่ทำการแยกข้อมูลของผู้ใช้ทั้งหมดออกจากไคลเอนต์ ทำให้ตัวของผู้ใช้งานเองนั้นมีอิสระเต็มที่ที่จะเลือกใช้ไคลเอนต์ต่าง ๆ เพื่อเข้าใช้งาน Nostr และแน่นอนว่า ผู้ใช้งานสามารถสลับหรือลงชื่อเข้าใช้ ไคลเอ็นต์ได้หลายตัวตามต้องการ ตราบใดที่ไคลเอ็นต์ทั้งหมดเชื่อมต่อกับชุดรีเลย์เดียวกัน คุณก็จะเห็นข้อมูลเดียวกันในทุก ๆ ไคลเอ็นต์
**ลงชื่อเข้าใช้ ไคลเอ็นต์หลาย ๆ ตัวแล้วจะกระทบต่อความปลอดภัยของแอคเคาร์ไหม?**
คำตอบของคำถามนี้นั้นขึ้นอยู่กับวิธีการที่คุณลงชื่อเข้าใช้ หากคุณลงชื่อเข้าใช้ด้วยกุญแจส่วนตัว ถึงแม้ว่าไคลเอ็นต์ส่วนใหญ่จะพยายามรักษาความปลอดภัยของกุญแจส่วนตัวอย่างดีที่สุด แต่ด้วยข้อจำกัดของซอฟต์แวร์ ย่อมมีความเสี่ยงที่จะเกิดช่องโหว่ การเจาะระบบ และข้อผิดพลาด ที่อาจทำให้กุญแจส่วนตัวของคุณรั่วไหลออกไปได้ ส่วนวิธีการป้องกันเกี่ยวกับเรื่องนี้คือการใช้ส่วนขยายของเว็บเบราว์เซอร์ เพราะการเข้าสู่ระบบในไคลเอนต์ต่าง ๆ ผ่านส่วนขยายนั้นจะใช้เพียงกุญแจสาธารณะในการเข้าสู่ระบบและทุกครั้งที่เราต้องการจะโพสต์หรือสร้าง event บน Nostr ไคลเอนต์จะทำการร่าง event นั้น ๆ และเว้นช่องของลายเซ็นเอาไว้จากนั้นเราจะต้องทำการเซ็นผ่านส่วนขยาย ด้วยวิธีนี้ทำให้กุญแจส่วนตัวของเราไม่หลุดออกไปไหนตลอดการใช้งาน
**รีเลย์คืออะไร?**
รีเลย์เปรียบเสมือนเซิร์ฟเวอร์ที่อยู่เบื้องหลังของ Nostr และทำหน้าที่รับ event ต่าง ๆ มาจากไคลเอนต์ Nostr และอาจจะจัดเก็บและกระจายข้อความเหล่านั้นไปยังไคลเอนต์อื่น ๆ ที่มีการเชื่อมต่ออยู่
เทคโนโลยีของรีเลย์นั้นเปลี่ยนแปลงอย่างรวดเร็ว ดังนั้นคาดว่าจะมีการเปลี่ยนแปลงอีกมากมายในอนาคต อย่างในปัจจุบันที่มีการนำเสนอ bostr หรือ รีเลย์ที่จะคอยส่ง event ของเราต่อให้กับรีเลย์อื่น ๆ ที่มีการเชื่อมต่อ เพื่อช่วยลดภาระของไคลเอนต์ในการรับส่งข้อมูลจากหลาย ๆ รีเลย์พร้อม ๆ กัน หรืออย่างการป้องกันสแปมด้วย POW หรือประเภทที่สามารถเก็บรูปหรือวิดีโอที่มีขนาดใหญ่ได้
แต่สิ่งหนึ่งที่ควรทราบก็คือ การที่ Nostr นั้นพยายามจะกระจายศูนย์และเหตุผลหลัก ๆ ที่สามารถทำแบบนั้นได้ก็ขึ้นอยู่กับรีเลย์ในการจัดเก็บและดึงข้อมูล ดังนั้น หากคุณรู้สึกว่าไคลเอนต์ Nostr ของคุณทำงานช้า ส่วนใหญ่ก็มักเกิดจากรีเลย์ที่คุณกำลังเชื่อมต่ออยู่ คุณอาจลองแก้ไขปัญญาโดยการเปลี่ยนหรือเพิ่มรีเลย์อีกสองสามรายการในไคลเอนต์ที่คุณใช้
**แล้วจะสามารถหารายการรีเลย์ได้จากไหน?**
การที่เราจะหารายการรีเลย์ที่เราควรเชื่อมต่อนั้น ๆ จริงแล้ว ๆ สามารถทำได้หลายวิธี แต่วิธีที่ผมแนะนำที่สุดจะเป็นการใช้ตามคนที่เราติดตามอยู่ เพราะจะเป็นวิธีที่เราสามารถเห็น event ต่าง ๆ ของคนที่เราติดตามได้ง่ายที่สุด และเช่นเดียวกัน เพื่อน ๆ หรือคนที่เราติดตามก็จะสามารถเห็น event ของเราได้เช่นกัน และสำหรับในประเทศไทย เรามีรีเลย์ที่คนไทยส่วนใหญ่นิยมใช้กันอยู่สองอัน นั้นคือ wss://relay.siamstr.com/ และ wss://relay.notoshi.win/ ถ้าหากว่าอยากเห็นคนไทยเยอะ ๆ บนหน้าไทม์ไลน์ ผมแนะนำเป็นอย่างยิ่งว่าควรเพิ่ม รายการรีเลย์เหล่านี้ลงไปในบัชญีหรือไคลเอนต์ต่าง ๆ ที่คุณใช้ด้วย
สำหรับอีกวิธีหนึ่งผมแนะนำให้เข้าไปในเว็บไซต์ nostr.watch เนื่องจากในเว็บไซต์นี้เป็นแหล่งข้อมูลที่ดีที่สุดสำหรับการค้นหาและประเมินความเร็วของรีเลย์ต่าง ๆ
**จะเกิดอะไรขึ้นถ้ารีเลย์ทั้งหมดที่ฉันเชื่อมต่ออยู่หยุดให้บริการ?**
สิ่งนี้เป็นสิ่งที่คุณต้องระวังมากที่สุดในการใช้งาน nostr เนื่องจากหากรีเลย์ทั้งหมดที่คุณเก็บข้อมูลไว้หยุดให้บริการทั้งหมดและคุณไม่มีการสำรองข้อมูล event ของคุณเก็บไว้เลย มันแปลว่าโพสต์ทั้งหมดของคุณ ผู้ติดตาม และรายการต่าง ๆ ที่คุณสรรค์สร้างไว้จะไม่สามารถกู้คืนได้ไปตลอดการ นี่จึงเป็นเหตุผลหลัก ๆ ที่ Nostr อนุญาตให้ผู้ใช้งานนั้นสามารถเชื่อมต่อกับรีเลย์ได้เป็นจำนวนมาก ก็เพื่อให้แน่ใจว่ามีข้อมูลสำรองเก็บไว้อยู่ที่ใดที่หนึ่งในระบบเสมอ แต่อย่างไรก็ตาม หากคุณต้องการที่จะมั่นใจได้ว่าข้อมูลต่าง ๆ ของคุณจะไม่ถูกเซ็นเซอร์ สิ่งที่คุณสามารถสามารถทำได้คือการใช้รีเลย์ส่วนตัวของคุณและกำหนดนโยบายต่าง ๆ ภายในรีเลย์ของคุณด้วยตัวคุณเอง
**แล้วฉันจะสามารถใช้รีเลย์ส่วนตัวได้อย่างไร?**
**อะแฮ่ม ๆ** ขอบอกไว้ก่อนว่ามันไม่คุ้มค่ากับความยุ่งยากสำหรับคนโดยทั่ว ๆ ไป ถึงในปัจจุบันจะมีเทคโนโลยีบางตัวที่เข้ามาช่วยให้มันทำได้ง่ายขึ้นแล้วก็ตาม
หากคุณต้องการที่จะสำรองข้อมูลนั้น การที่จะมีรีเลย์ส่วนตัวที่ออนไลน์ตลอดเวลาอาจเป็นเรื่องที่ไม่ได้จำเป็นขนาดนั้น เนื่องจากเราสามารถใช้งานบริการอย่าง https://nostrsync.live/ ในการดาวน์โหลดข้อมูลของเราจากรีเลย์ต่าง ๆ ได้ หรือการติดตั้งรีเลย์ส่วนตัวอย่าง nostr-relay-tray: https://github.com/CodyTseng/nostr-relay-tray ที่ช่วยให้เราสามารถมีรีเลย์ส่วนตัวที่ใช้สำหรับสำรองข้อมูลได้
Nostr Implementation Possibilities (NIPs)
NIP คืออะไร?
---
NIP มีไว้เพื่อส่งเสริมความสามารถในการทำงานของ Nostr และเป็นตัวคอยกำหนดให้ เหล่านักพัฒนาทำสิ่งต่าง ๆ ที่เหมือนกันในรูปแบบเดียวกัน เพราะมันคงไม่ใช่ความคิดที่ดีนัก หากนักพัฒนาแต่ละคนจะคิดค้นวิธีแก้ปัญหาทั่วไปของตัวเองและนำไปใช้ในแอปของตัวเองเท่านั้น และคงจะเป็นการดีกว่า ถ้าหากทุกคนใช้วิธีแก้ปัญหาที่เหมือนกัน นั่นคือเหตุผลที่ต้องมี NIP อยู่ในโปรโตคอลของ Nostr และในทำนองเดียวกัน แนวคิดใหม่อาจดูดีในแอปของนักพัฒนาบางราย แต่จะดูดียิ่งขึ้นอย่างแน่นอนหากแอปอื่น ๆ อีกมากมายใช้มาตรฐานเดียวกันและสามารถทำงานร่วมกันได้อย่างราบรื่น
**ทำไมมันถึงหน้าสนใจ?**
อย่าลืมว่า Nostr เป็นระบบแบบกระจายอำนาจและไม่ได้มีบริษัทหรือใครที่เป็นเจ้าของมัน อย่างเช่นโซเชียลมีเดียอื่น ๆ เช่น ทวิตเตอร์ อ่อไม่สิตอนนี้คงต้องเรียกมันว่า X สินะ ซึ่งหมายความว่าทิศทางของโพรโทคอล Nostr นั้นขึ้นอยู่กับพวกเราทุกคน! ไม่ว่าใคร ๆ ก็สามารถเสนอแนะและสนับสนุนการเปลี่ยนแปลงและให้ข้อเสนอแนะเกี่ยวกับแนวคิดที่ผู้อื่นเสนอ และการที่คุณเป็นส่วนหนึ่งของชุมชนนี้ ก็ทำให้คุณมีส่วนร่วมในทิศทางของ Nostr อีกด้วย
จากที่ส่งหากันได้แค่ข้อความ มาเป็นรูปภาพ มาเป็นวิดีโอ และมาเป็น”เงิน” นี่คือเส้นทางการเดินทางของโปรโตคอลนี้ในอดีต แล้วในอนาคตมันจะพัฒนาไปยังไงต่อก็ขึ้นอยู่กับเหล่าผู้ใช้งานและนักพัฒนาในอนาคต แล้วทำไมสิ่งนี้ถึงจะไม่น่าสนใจละ ?
Event
---
**Event คืออะไร?**
Event เป็น object เพียงประเภทเดียวที่มีอยู่บน Nostr โดยมีโครงสร้างประมาณนี้
```
{"id":"84d5d3dc9c388a702f39cad6360d41ebb804e809fb822f110ff8a14dfd35fc6c",
"pubkey":"66df60562d939ada8612436489945a4ecf1d62346b3d9478dea8a338f3203c64",
"created_at":1722315959,
"kind":1,
"tags":[["t","siamstr"]],
"content":"ไปสั่งกาแฟเมื่อกี้ พส เจ้าของร้านชมว่าเดี๋ยวนี้คล่องภาษาญี่ปุ่นแล้วนะ ไอเราก็ดีใจ พอเดินกลับถึงที่ทำงานละก็ตระหนักได้ว่า ตะกี้เราสั่ง “ไอซ์โคฮี โอเนไงชิมัส” “เทคเอาส์” “คาโดะเดสส” ไอบ้าไหนญี่ปุ่นก่อนอังกฤษทั้งนั้น 🤣🤣\n\n#siamstr",
"sig":"8f066a0099a5f580b605ebdb220179c4eca298947c38b855a0a8bf2783f28ddb537cb74a7f61d3ce8891189f719870efdf320ea4f895e03cdac44284c450c5c4"}
```
อย่าง Event ข้างต้นนี้มี kind เป็น 1 ซึ่งหมายถึง "ข้อความโน้ต" ซึ่งก็คือข้อความธรรมดา สั้น ๆ คล้ายกับที่ใช้กันใน Twitter เช่น บนฟีด การตอบกลับ และการโควท
**ประเภทของ Event (Event Kinds)**
หมายเลขของ kind แต่ละตัวมีความหมายแตกต่างกัน ตัวอย่างเช่น 0 หมายถึงอีเวนต์ "ข้อมูลเมตา" ใช้สำหรับให้รายละเอียดเกี่ยวกับผู้ใช้ เช่น ชื่อและรูปโปรไฟล์ รีเลย์ (Relays) สามารถจัดการกับ kind ที่แตกต่างกันได้ เช่น รีเลย์มักจะลบอีเวนต์ kind:0 เวอร์ชันเก่ากว่าออกไป และเก็บไว้เฉพาะเวอร์ชันล่าสุด ในขณะที่โดยทั่วไปจะเก็บอีเวนต์ kind:1 ไว้หลายรายการสำหรับแต่ละคีย์
โดยทั่วไปแล้ว คุณไม่จำเป็นต้องใช้ kind เกินกว่า 0 และ 1 ในการสร้างแอปพลิเคชันโซเชียลมีเดียบน Nostr แต่ kind อื่น ๆ ถูกคิดค้นขึ้นโดยไคลเอนต์ เพื่อมอบฟังก์ชันการทำงานอื่น ๆ ตามที่ระบุไว้ใน NIP บาง kind ไม่เกี่ยวข้องกับเครือข่าย และให้บริการตามความต้องการอื่น ๆ ของไคลเอนต์ที่เฉพาะเจาะจงกับฟังก์ชันการทำงานเหล่านั้น ซึ่งแนวคิดก็คือ สำหรับกรณีการใช้งานใหม่ ๆ แต่ละกรณี จะต้องมีการพิจารณาและเสนอซับโปรโตคอลเป็น NIP เพื่อให้สามารถทำงานร่วมกับไคลเอนต์ที่มีอยู่และในอนาคต ซึ่งอาจสนใจที่จะนำฟังก์ชันการทำงานนั้นไปใช้ ขณะเดียวกันก็มั่นใจได้ถึงความเข้ากันได้ย้อนหลัง และการรองรับสิ่งต่าง ๆ ที่มีอยู่และไม่ต้องการเปลี่ยนแปลง
**คุณสมบัติอื่น ๆ ของ Event**
created_at: เป็น Timestamp ของ UNIX ที่กำหนดโดยผู้สร้างอีเวนต์ โดยปกติจะเป็นเวลาที่สร้าง แม้ว่าจะไม่มีการตรวจสอบ แต่ก็ไม่ใช่ปัญหา
content: ขึ้นอยู่กับความหมายของ kind ในกรณีของ kind:1 จะเป็นเพียงสตริงข้อความธรรมดาที่คนอื่น ๆ อ่านได้
tags: ขึ้นอยู่กับ kind เช่นกัน แต่แท็กทั่วไปบางอย่างที่มักปรากฏใน event kind:1 และ kind อื่น ๆ คือ "p" ซึ่งใช้เพื่อกล่าวถึงกุญแจสาธารณะ และ "e" ใช้เพื่ออ้างถึง event อื่น
อยากมีส่วนร่วมในการพัฒนาของ Nostr ?
---
จริง ๆ แล้วใคร ๆ ก็สามารถเข้ามามีส่วนร่วมในการพัฒนา Nostr ได้ ไม่จำเป็นต้องเป็น dev หรือมีความรู้ด้านคอมพิวเตอร์ก็สามารถทำได้ ไม่ว่าจะเป็นการให้ feedback กับ dev ของ client ที่คุณใช้, การสร้างคอนเทนต์ต่าง ๆ บน Nostr การสร้างชุมชน รวมไปถึงการช่วย client ต่าง ๆ ในการทำ UI ให้เป็นภาษาท้องถิ่น และอื่น ๆ อีกมากมาย ใคร ๆ ก็สามารถช่วยได้ตามความสามารถที่แต่ละคนมี มันเลยทำให้ Nostr โครตน่าอยู่ :)
-

@ 469fa704:2b6cb760
2024-09-02 06:11:43
***I joined Nostr a week ago and wanted to recap it for myself and also give other newbies a simple introduction. Maybe this will help you get started too.***
## Step 1: Create your identity and get your private key for a browser extension
I started with the Snort client on my local home server. It created my private/public key pair and I was good to go. Then I transferred the private key to Amethyst, a pretty good Android-based client. Before looking at various clients and other nostr-based websites, I tried transferring my private key into a browser extension.
I looked at Alby and nos2x. I chose the latter because I wanted to keep my Lightning wallet separate from my identity management. You don't have to, I just found it easier.
## Step 2: If you're confused, always check your feed settings
I tried many different clients and was very confused at first. Due to its decentralized nature, Nostr relies on relays, which are just small servers, and to each one you can connect to, all your data is stored. When you post a message, write a note, an article like this or simply who you follow. The main reason and benefit for this is that there is no single point of failure or server-like entity that could be censored.
The side effect of this, combined with using different clients, was that not only did it look different everywhere, but the content was also very different. This was simply because I wasn't connected to all my different clients with the same relays. But the main reason why each feed looks different on each client is usually because you can choose different variations of feeds and some clients even offer filters for the feeds.
Scroll down to get a small overview of the clients I've tried.
## Step 3: Set up your lightning wallet with something like Wallet of Satoshi
I made my Bitcoin Lightning wallet independent of my identity. That's why I just went with the number one Lightning wallet on the market: Satoshi's Wallet. It's very simple and provides you with a Lightning address that resembles and has the format of an email address. You can add this address to your Nostr profile description and you're ready to receive Sats. Anyone can send them to you, e.g. for a good message or something else they find valuable on Nostr (like a podcast, a video, an article, ...).
Just be aware that Satoshi's wallet contains your key and the sats you have there are not really your sats. So only leave a small amount there or no more than you need for your nostr experience.
## Step 4: Set up your Nostr address
I set up a unique NIP-05 identifier that is human readable and also looks like an email address. For me, that's tobiya@nostrplebs.com, also called a nostr address. It's much easier to read, share and remember than your public key, which is just a long, unwieldy string of characters.
Some popular services are:
* NostrVerified
* Alby
* Iris
* Primal
* Snort
* nostrplebs.com
Most offer free services or at least a free tier. I chose nostrplebs.com because it links my Nostr address (tobiya@nostrplebs.com) to my Lightning wallet. ⚡
## Brief overview of the clients (I have tested)
### Web/Browser:
* **Primal**: Fast, user-friendly, nice looking, easy to use
* **Coracle**: Focuses on decentralized reputation, privacy and trust metrics. Also well organized and structured
* **noStrudel**: The most comprehensive I've found, has everything
* **Rabbit**: Designed like X (Twitter) Pro, focuses on everything at once
* **Nostter**: Clearly structured, easy to find what you're looking for
* **Snort**: Fast web client for those who prefer simplicity and speed.
### iOS
I'm not an iPhone user, but everything I've discovered says that Damus is the best app for iOS.
### Android:
* **Amethyst**: Feature rich for Android, I only tried this program because it gives me everything I currently need on my phone.
* **Primal**: Works seamlessly with Primal on the web, which is a pretty convenient starting point if you only want to use one client.
As for the web clients, I'm still figuring out which one will be my favorite. But I think they're all good in their own way. In the time of writing, I am mainly using Primal on Android and Web, Amethyst and noStrudel.
### Let's have fun!!
-

@ 3b7fc823:e194354f
2024-09-01 19:21:09
Testing articles on Yakkihonne
-

@ 469fa704:2b6cb760
2024-09-01 13:26:42
## Side jobs and passive sources of income
To increase your income, it is often necessary to be creative and develop different income streams:
* **Freelancing**: platforms such as Upwork, Fiverr or Freelancer offer a variety of tasks, from graphic design to programming work to marketing. According to a study by Statista, freelancers in Germany earn between 20 and 50 euros per hour on average, depending on their expertise.
* **Part-time jobs**: You can take on a part-time job alongside your main job. Think about jobs that are flexible, such as driving services (e.g. Uber, Bolt), delivery services (e.g. Deliveroo, Gorillas) or tutoring. According to the Federal Employment Agency, part-time jobs can be tax-free up to 450 euros per month, which is an attractive option.
* **Passive income**: This requires work or capital initially, but can generate income in the long term:
* * **Real estate**: real estate investments offer regular rental income. According to the German Institute for Economic Research (DIW), the return on residential real estate in Germany can be between 3% and 5%.
* * **Dividend stocks**: Invest in companies that pay dividends. Companies such as Siemens or Deutsche Telekom have a long tradition of distributing dividends.
* * **Digital products**: Create e-books, online courses or apps. Once created, these products can generate continuous income.
* * **Affiliate marketing**: Partner with brands and earn through sales commissions. Amazon Associates is one of the best-known platforms for this.
## Reduce expenses
Another way to have more capital for investments such as Bitcoin is to reduce expenses:
* **Budgeting**: create a detailed budget. Apps like YNAB or Mint can help categorize expenses and analyze where savings can be made.
* **Food**: Plan your shopping, buy seasonal products and cook more yourself. According to a study by the Federal Ministry of Food and Agriculture, households spend an average of around 25% of their income on food.Conscious shopping can significantly reduce these costs.
* **Energy costs**: Use energy-saving light bulbs, switch off appliances completely and insulate your home better. According to the Federal Office of Economics and Export Control (BAFA), simple energy-saving measures can reduce costs by up to 20%.
* **Subscriptions and memberships**: Review regular subscriptions (gym, streaming services).Many people pay for services they rarely use. A survey by Statista showed that on average 10-15% of monthly spending is used for subscriptions.
* **Transportation**: Use public transportation or car sharing services instead of owning a car.Owning a car can cost several thousand euros a year, including insurance, maintenance and fuel.
* **Second-hand and upcycling**: Buy second-hand clothes or furniture.The second-hand market is booming and you can often find high-quality products at a fraction of the original price.
## Investing, or rather saving, in Bitcoin
After you have accumulated more Dollar or other paper money by increasing your income and reducing your expenses, you can invest in Bitcoin:
* **Bitcoin**: As the first and best-known cryptocurrency, Bitcoin has a high market capitalization and acceptance. Investors see Bitcoin as a “digital gold” alternative, especially in times of inflation.
* **Risk and volatility**: Bitcoin is known for its high volatility. It is important to only invest money that you don't need in the immediate future. In the long term, bitcoin is destined to rise in price in dollar terms due to its unique characteristics.
* **Long-term perspective**: Many investors hold Bitcoin as a long-term investment, similar to stocks. Historically, Bitcoin has shown positive returns over longer periods of time, despite high volatility.
## Practical steps to increase income and reduce expenses:
1. **Analyze income**: Make a note of all your sources of income and consider how you can increase them. This could be through salary increases, side hustles or new passive income streams.
2. **Review expenses**: Make a list of your monthly expenses and identify areas where you can cut back. Set specific goals for reduction.
3. **Investment plan**: After you have accumulated more capital, create an investment plan. For Bitcoin, this could mean investing small amounts regularly to take advantage of the average cost effect (dollar-cost averaging).
4. **Education and networking**: Invest time in education and build a network. This can lead to new income opportunities and increase your financial intelligence.
## Idea to get Ahead:
Create a budget and set a monthly savings goal for your Bitcoin investments. Calculate how much you can generate by reducing expenses and generating additional income.
Research and choose a Bitcoin only platform to buy Bitcoin (e.g. [Relai](https://relai.app/), [Coinfinity](https://coinfinity.co/), [21Bitcoin](https://21bitcoin.app/), [Pocket Bitcoin](https://pocketbitcoin.com/) ). Learn the basics of trading and start with a small investment.
-

@ 469fa704:2b6cb760
2024-09-01 13:26:13
## The basics of financial planning
Financial education is the first step to financial independence. Here are the core principles you need to understand:
* **Income vs. expenses**: The core of any financial plan is to earn more than you spend. This requires not only discipline, but also a clear overview of your financial comings and goings.
* **Budgeting**: Create a detailed budget plan. A budget helps you to see where your money is going and where you can save. It's a living document that you should adjust regularly.
* **Emergency fund**: An emergency fund is a buffer against unforeseen events. Experts recommend keeping at least three to six months of your expenses in cash or easily liquidated assets.
* **Set goals**: Define clear financial goals. These can be short-term (e.g. a new cell phone), medium-term (e.g. a car) or long-term (e.g. retirement). Each type of goal requires different strategies and time frames.
* **Debt management**: Distinguish between good debt (e.g. investments in education or real estate) and bad debt (e.g. credit cards with high interest rates). A debt repayment plan is often just as important as a savings plan.
## Understanding investments
Investing is the way to make your money work for you. Here are some basic concepts you should understand:
* **Interest and Compound Interest**: Interest is the compensation you receive or pay when you invest or borrow money. Compound interest is particularly powerful as it means you earn interest on your interest, which can lead to exponential growth over time.
* **Risk and return**: Investments with higher returns are often associated with higher risk. It's important to find a balance that suits your personal risk profile. Diversification can help manage this risk.
* **Diversification**: Spread your money across different asset classes (equities, bonds, real estate, commodities) and regions to minimize risk. This protects you from a total loss if one investment performs poorly.
*** Long-term perspective**: Investing is not a short-term game. It requires patience and a long-term perspective.Short-term market fluctuations should not lead to panic selling. This is true for every asset, even Bitcoin.
* **Costs and fees**: Pay attention to the costs and fees associated with investing. These can have a significant impact on your returns over time. Especially important are taxes.
## Practical steps to financial education:
* **Books and courses**: Invest in your financial education.There are many resources available, from classics like Rich Dad Poor Dad to online courses on platforms like Coursera or Udemy.
* **Financial apps and tools**: Use apps like Mint, YNAB (You Need A Budget), or Personal Capital to track your budget and investments. These tools can help you monitor your finances in real time. Even a good old spread sheet can work wonders.
* **Seek advice**: If possible, consult a financial advisor. They can provide personalized advice tailored to your specific situation. Make sure they offer independent advice.
* **Podcasts and blogs**: Follow financial podcasts or blogs to get the latest trends and tips. You can find also a lot of execellent stuff on Youtube, especially Bitcoin education.
* **Self-study**: Learn the basics of stock markets, bonds, real estate investing and other forms of investing. Websites like Investopedia or Khan Academy offer free knowledge.
* **Study Bitcoin**: Nothing teaches you so much about finance, investing, money and wealth than bitcoin. If you are eager to understand it even more, it will teach you also thermodynamics, cryptography (math), economics, philosophy and maybe a lot more.
## Practice for application:
Create a simple budget for the next month. Write down all expected income and expenses. Identify areas where you can save. Use an app or Excel spreadsheet to do this.
Research an investment opportunity that interests you (e.g. ETFs, shares, real estate funds). Understand the basics and think about how you could get started. Create a small investment plan.
-

@ c11cf5f8:4928464d
2024-09-01 13:22:49
Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too!
If you missed our last thread, [here](https://stacker.news/items/661607/r/AG) are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/668607
-

@ 6c2d68ba:846525ec
2024-09-01 13:02:53
Dear friend,
it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.
As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:
* What causes the discomfort that drives you out of the walled garden onto the open sea?
* Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?
* What are you hoping to find on the open sea that walled gardens cannot provide?
* What are you willing to sacrifice for freedom (of speech)?
* What will you need to keep the ship afloat?
* How will you react when you find yourself in the middle of a storm?
I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over.
This is about building a new world, an open world without walled gardens and data silos.
Onwards!
-

@ a30cdfee:2d2f97ff
2024-09-01 11:40:38
# Primal: Social Media with Bitcoin Tipping
[Primal](https://primal.net/) is a social media app that lets you tip (zap) other users with bitcoin!
How does Primal work and why should you join?
Primal is a social Bitcoin wallet.
If you like somebody's content, you can tip them Bitcoin micropayments through the Lightning Network.
Or monetize your own content.
You can also use it as a custodial Lightning wallet to pay for small purchases in bitcoin.
## Primal Is a Nostr Client
Primal uses the Nostr protocol as its social graph.
Nostr is an open protocol for decentralized and censorship-resistant social media.
If you're new to Nostr, learn more about it here: https://stacker.news/items/558629
Since Primal is only a client to access the Nostr protocol, it can only censor free speech or deplatform users on the Primal app, but not on Nostr.
Also, if you stop using Primal as your Nostr client, you can import all your followers, posts, etc. to a new client.
## Primal Feels Like Twitter (X)!
Primal's feed feels very familiar to other social media platforms, especially X (Twitter).
You can follow people, like their posts, repost etc.
It's not only for Bitcoin-related discussion: you can search for different hashtags and find your tribe, e.g. photography etc.

Primal works for iOS, Android and desktop.
On desktop, the "Explore" function is even more detailed.
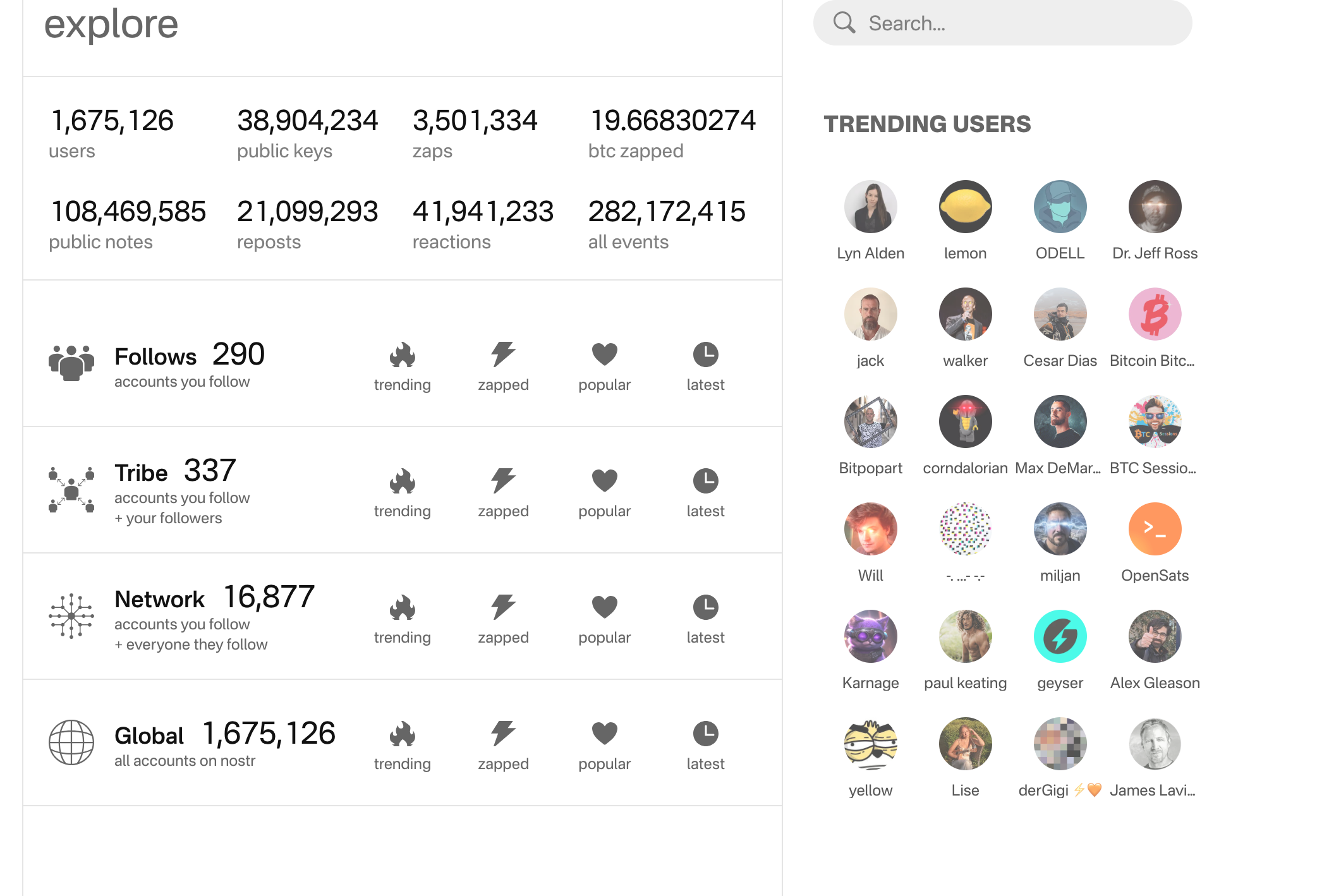
## Earn Bitcoin for Your Content!
By clicking the lightning bolt symbol on the feed, you can tip (zap) other users bitcoin.
You can also browse through your contacts and zap them.
Nostr is a great directory for Lightning payments!
If you hold the bolt symbol a bit longer, you can specify the zap amount if you want.
You can set your default zap amount in settings.
To set up a Lightning wallet with Primal, the app asks for your name, email address and the country of residence.
But as far as I know, you can use a nym and a throwaway email etc.
No need to upload any identity documents.
The maximum balance you can hold on the Primal wallet is 1 million sats, or 0.01 BTC.
The purpose of the wallet is not for long-term savings, but to onboard people to Nostr and to get familiarized with the culture of zapping.
To get your first sats on the Primal wallet, you can receive bitcoin on Lightning or on-chain.
Alternatively, you can buy sats on Primal with Apple Pay or Google Pay with your credit card (max. about $5 worth).
Or just start creating and receive zaps from other users.
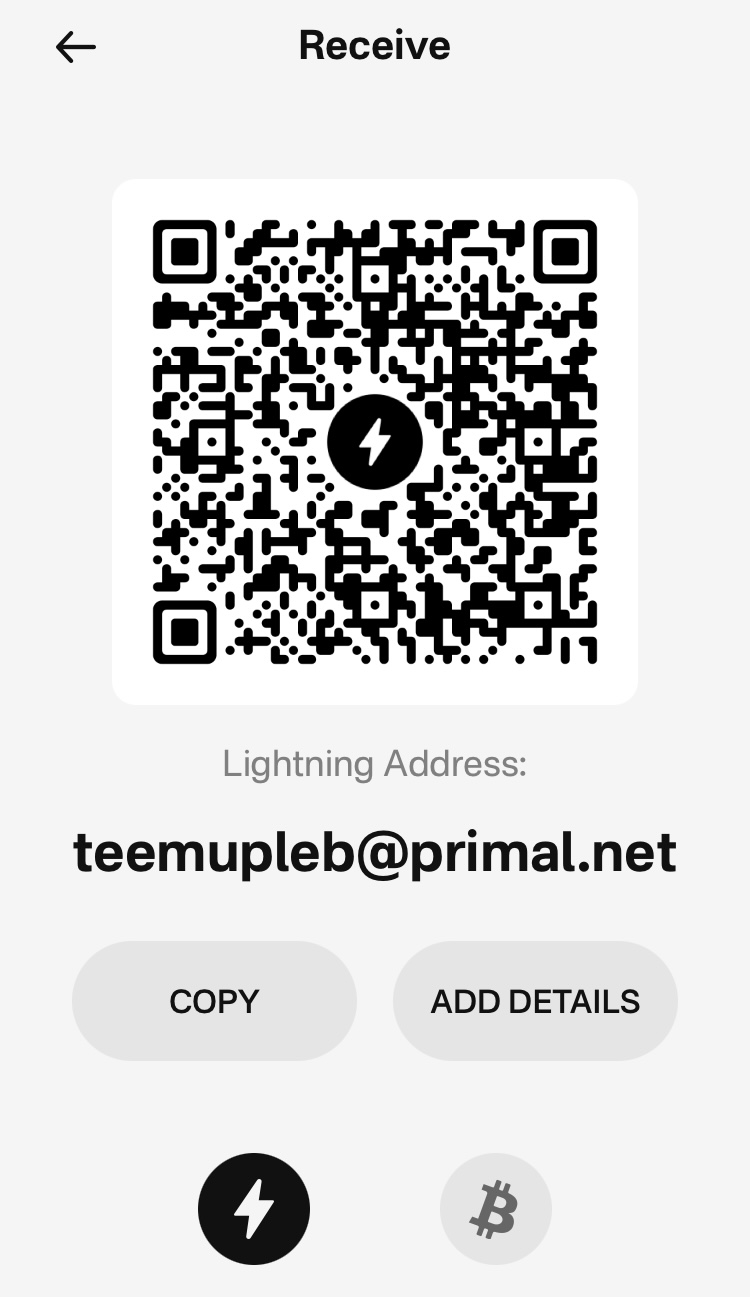
## Take Care of Your "nsec"!
Your "nsec" is your private key to your Primal (and Nostr account).
Don't share it with anyone!
Primal creates an nsec for you upon account creation, or you can import your own.
Primal is open-source, but it is not always a good practice to import private keys to any apps.
If you don't want to import the private keys you already have to Primal, you can use e.g. [Amber](https://github.com/greenart7c3/Amber ), a Nostr signer extension app for Android.
It's advisable to store your nsec in e.g. a password manager.
If you use Primal on desktop, you can use e.g. [Alby](https://getalby.com/) @Alby, as a Nostr signer extension, zapping wallet and a place to store your nsec.
Learn more about Alby [here](https://x.com/teemupleb/status/1599882236106416128).
You can also use another Nostr signer extensions on desktop, e.g. [Nos2x](https://github.com/fiatjaf/nos2x ), but they often have no wallet functions for zapping or receiving zaps.
They work only for posting, liking, replying, reposts etc.
## Convenient, but With Privacy Trade-Offs
You can send direct messages to other Primal users, but you should know that while the content of the direct messages is encrypted (visible only to you and your contact), the message metadata is public for all to see (who you're sending messages to, when, how often etc.)
Primal can be used as a [global international "Venmo" during dinner parties](https://x.com/joaodealmeida_/status/1828423275682373720).
No more head-scratching when trying to split the bill!
Not the most private way to do it though, but it's convenient!
Let's connect on Nostr!
You can find me [here](https://primal.net/teemupleb).
## Additional Resources
https://www.youtube.com/watch?v=Qd4Po4i7wvc
https://www.youtube.com/watch?v=7LsIb6D7FtU
## Project Links
[Website](https://primal.net/)
[GitHub](https://github.com/PrimalHQ)
[Nostr](https://primal.net/primal)
[X (Twitter)](https://x.com/primal_app)
originally posted at https://stacker.news/items/668536
-

@ 7fd90943:52bf6313
2024-09-01 07:20:27
> ![TIP]
> I was surprised to discover that I can send Hive in form of Bitcoin Lightning with this Decentralized Application. Right now the only way that I was able to access this is through HIVE keychain. I will try to find some other ways to access this. Now I can fund my Stacker wallet in the most convenient way possible.
originally posted at https://stacker.news/items/668391
-

@ 3c9712ff:14fecbc4
2024-09-01 03:39:08
The Australian dream used to be straightforward: secure a job, pay off your house by your late thirties, and retire with substantial assets and savings to support your lifestyle.
Some argue the introduction of compulsory superannuation contributions in 1991 signaled the government's lack of trust in Australians' ability to save and be self-sufficient in their later years. But I disagree.
The issue wasn’t that Australians were incapable of saving; it was that saving money was no longer enough. The erosion caused by the Keynesian experiment had seeped into Australian retirements, making it nearly impossible for an entire generation to retire off the savings from a [median salary of $27,200](https://www.9news.com.au/finance/rates-1990-versus-2007/8251875f-a878-49a5-bca6-559d2dcdb361#:~:text=Against%20a%20backdrop%20of%20average,up%2044.99%20percent%20of%20income.).
Superfunds were thus established by the government as a supposed solution to the problem they had created. How unsurprising.
Fast forward 33 years, and Australian superfunds, like those in most of the western world, are now facing two insurmountable challenges of population demographic, and a debasing currency.
**1. Our Population is Ageing**
On face value, it shouldn't matter whether the population is ageing. If I have my own retirement account which I paid into each month, why would it matter if the people around me are ageing as well?
The answer lies in duration mismatch. Retirement funds must manage a mix of short-term, long-term, and continuous obligations, balancing liquid liabilities (cash payments to members) with illiquid assets (investments). Because funds rely on more inflows (super contributions) than outflows (payouts to retirees), population demographics play a critical role in maintaining this balance - and Australia's isn't looking great.
*An example of an ageing population (Australia) vs a growing population (Nigeria)*
**2. Our Currency is Ever Debasing**
This is far more pernicious for our retirees
| Financial Year | [Average Super Return](https://www.superguide.com.au/comparing-super-funds/super-funds-returns-financial-year) | [Money Supply Growth](https://data.worldbank.org/indicator/FM.LBL.BMNY.ZG?locations=AU&most_recent_year_desc=true) | Net Return |
| --- | --- | --- | --- |
| 2023-24 | 9.1% | 4% | 5.1% |
| 2022-23 | 9.2% | 7.8% | 1.4% |
| 2021-20 | -3.3% | 6.7% | -10% |
| 2020-21 | 18% | 13.6% | 4.4% |
In Austrian Economics, inflation is understood as a monetary phenomenon that occurs when new monetary units are added to the existing supply. This monetary inflation is the precursor to both price and asset inflation.
Austrians also reject the idea of measuring price inflation with a single number, such as the CPI, as different asset classes respond differently to monetary inflation. For instance, industries like technology and manufacturing are less susceptible to price inflation due to the deflationary effects of increased automation and competition.
Conversely, hard assets like gold and real estate have reached record highs, as easy money tends to flow toward the most reliable stores of value.
#### Average Yearly Prices Increase since 2018 - Against YoY M2 and CPI
| | Iphone | [Median House](https://www.aussie.com.au/content/dam/aussie/documents/home-loans/aussie_25_years_report.pdf) | Money Supply Growth | [CPI](https://www.rba.gov.au/inflation/measures-cpi.html) |
| ----- | ----| ---- | ------ | --- |
| Since 2018 | 2.24% | 6.8% | 7.2% | 3.1%
---
*Although simplistic, the table above shows that hard assets move with monetary inflation, not CPI.
The real hurdle, or the absolute **minimum** that a superfund has to give it's members is not CPI or the 3.95% 10 year, but that monetary inflation rate of 7.2%.
An increase in the required rate of return invariably brings an increase in risk. Superfunds can't simply gamble Australians' retirement savings on high-risk offshore tech startups, so these returns are often sought through listed equities and commercial real estate—two interest rate sensitive asset classes. This correlation significantly limits the RBA's ability to manoeuvre and the dilemma is clear:
* Drop rates, inflate away our retirement.
* Increase rates, crash our retirement.
**Bitcoin to the Rescue**
You guess it, bitcoin fixes this.
Take the same example from 1991, but replace the Australian Peso with Bitcoin. In a Bitcoin world, we wouldn’t need superannuation. By simply saving 40 years of time and energy in a deflationary currency like Bitcoin, our savings alone would **increase** in purchasing power, eliminating the need to burden future generations for our retirement.
In the meantime, Australian superfunds should take a leaf out of a few smaller US pension funds like the [Wisconsin Pension Fund](https://www.wpr.org/news/wisconsin-pension-fund-bitcoin) and start gaining exposure to bitcoin.
A 2% allocation to a Bitcoin ETF is enough to ignite a chain reaction toward full institutional adoption. This truly scarce and desirable asset, with its **low** correlation to existing portfolios, isn’t just an opportunity—it’s a lifeline for the future of Australian retirees. It’s only a matter of time.
Colin Gifford
August 2024
 @ 84b0c46a:417782f5
2024-10-12 05:51:51- 1:nan: - **2** - 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p) - 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw - 2 - 2 - 3 - 3 - 2 - 1 |1|2| |:--|:--| |test| :nan: | --- ### :nan: **:nan:** 1. 1 2. 2 - tet - tes 3. 3 1. 1 2. 2 > t >> te >>> test - 19^th^ - H~2~O <marquee>(☝ ՞ਊ ՞)☝ウェーイ<marquee><SCRIPT>alert("( 厂˙ω˙ )厂うぇ乁( ˙ω˙ )厂ーい乁( ˙ω˙ 乁)")</SCRIPT> <img src="xx" onerror="alert('(☝ ՞ਊ ՞)☝ウェーイ')"> <marquee onstart="document.querySelector('body').innerHTML = `<main><p>全裸デブ</p></main>`">本サイトはfirefoxのみサポートしています</marquee> <marquee><font size=1000>うにょ</font></marquee> <marquee scrollamount=50>:wayo:</marquee> <marquee behavior="alternate">This text will bounce</marquee>
@ 84b0c46a:417782f5
2024-10-12 05:51:51- 1:nan: - **2** - 2[irorio絵文字](https://nostviewstr.vercel.app/naddr1qvzqqqr4fcpzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyvhwumn8ghj7cn0wd68ytnwda4k7arpwfhjucm0d5hszrnhwden5te0dehhxtnvdakz7qgewaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7f0qyshwumn8ghj7mn0wd68yttjv4kxz7fddfczumt0vd6xzmn99e3k7mf0qy08wumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wshsz9nhwden5te0dehhxarj9ejxzarp9e5xzatn9uq3xamnwvaz7tmwdaehgu3w0f3xgtn8vuhsz8nhwden5te0deex2mrp0ykk5upwvvkhxar9d3kxzu3wdejhgtcpzfmhxue69uhhytntda4xjunp9e5k7tcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcpr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9uq3vamnwvaz7tmjv4kxz7fwd4hhxarj9ec82c30qyt8wumn8ghj7un9d3shjtnd09khgtnrv9ekztcpremhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6ns9uq36amnwvaz7tmnwf68yetvv9ujucedwd6x2mrvv9ezumn9wshszrnhwden5te009skyafwd4jj7qqxd9ex76tjduya383p) - 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw - 2 - 2 - 3 - 3 - 2 - 1 |1|2| |:--|:--| |test| :nan: | --- ### :nan: **:nan:** 1. 1 2. 2 - tet - tes 3. 3 1. 1 2. 2 > t >> te >>> test - 19^th^ - H~2~O <marquee>(☝ ՞ਊ ՞)☝ウェーイ<marquee><SCRIPT>alert("( 厂˙ω˙ )厂うぇ乁( ˙ω˙ )厂ーい乁( ˙ω˙ 乁)")</SCRIPT> <img src="xx" onerror="alert('(☝ ՞ਊ ՞)☝ウェーイ')"> <marquee onstart="document.querySelector('body').innerHTML = `<main><p>全裸デブ</p></main>`">本サイトはfirefoxのみサポートしています</marquee> <marquee><font size=1000>うにょ</font></marquee> <marquee scrollamount=50>:wayo:</marquee> <marquee behavior="alternate">This text will bounce</marquee> @ 0e501ec7:de5ef3a4
2024-10-09 21:38:52PS: lees zeker eens de blog van Tim: <https://timscyclethoughts.blogspot.com/2024/09/> :)) Vandaag was onze eerste dag in het Abtshof. (Ik weet het, gisteren is overgeslagen, oeps, en ik heb nog niet uitgevonden hoe ik hier meer foto's op kan zetten, nogmaals oeps.) Het Absthof is een coöperatieve co-housing, met een grote moestuin en een houtatelier. Het is gelegen in Borlo, een klein dorpje in de buurt van Landen. Het thuis van de wooncoöperatie is een grote vierkantshoeve, die langzaamaan helemaal gerestaureerd geraakt op (redelijk) duurzame wijze. Een heel mooie plek, waar ik al een paar keer te gast ben geweest. Hier krijgen we kost en inwoon in ruil voor mee te helpen met vanalles. Wij zijn blij om hier te zijn en ervaring op te doen, en blij dat we wat kunnen bijdragen aan duurzame/alternatieve projecten zoals deze. Ook nog belangrijk: bij een coöperatie horen ook veel beslissingen, die gedragen moeten zijn. Hier werken ze met het kader van de sociocratie. Zeer interessant, ik zal er later nog over uitweiden. Dus: we hadden op ons gemakje een lange ochtend gehad, met een lekker ontbijtje, een goede opruimbeurt, de plantjes in de serre water geven, en een random astrix en obelix strip. Het ging over de picten, ofzoiets, en iemand die de macht wou grijoen door met de romeinen samen te werken. Bon, daarvoor zijn we hier niet. Ik zou eigenlijk in bed moeten nu, de dagen zijn lang en mijn slaap dierbaar. Toch wil ik eerst nog wat schrijven. Toch toch tocht door de bomen, wilgen, essen, rode beuk Net toen we buitenstapten om te vertrekken deze ochtend, begon het te regenen! Test regenkleren: gefaald. Regenbroek is zo lek alsof hij eigenlijk niet bestaat. Maakt niet uit, ik ben niet van suiker. ; ) We zullen wel nog eens kijken voor van dat eng waterdichtmaakspul, of ik gebruik hem als windstopper, ook goed. Hier aangekomen werden we meteen ontvangen door Jakob met een warm middagmaal. Heerlijke stampot, op smaak gebracht met varkenspoot. Heftig idee, maar ik en Tim konden er wel mee overweg, en waren eigenlijk wel nieuwsgierig hoe dat smaakte zo een varkenspoot. Blijkt: nogal taai, maar wel nog een goede ervaring. Would recommend. Daarna gingen we ons installeren, en we hadden geluk! We mochten slapen in een grote tent die nog op het veld stond. Daarin zijn zelfs bedjes, en hij lijkt (redelijk) waterdicht, al had ik toch niet direct al mijn spullen moeten uitspreiden. Ons kleine tentje zou het niet gehouden hebben om de hele week in de regen opgestaan te hebben vrees ik. Daarna bereikte mij het nieuws. Van de uitzetting in het Wondelbos. Ik was er zwaar van aangedaan, boos en verdrietig, gespannen. Machteloos. Machteloos. Ik heb toen geprobeerd mijn gevoel neer te schrijven, en heb de grote uitdaging overwonnen om dat kwetsbare tekstje te delen. (Op Facebook.) Ik was wel trots op mijn kleine overwinning, maar dat viel nogal in het grote niet bij mijn eerdere gevoel bij de grote machtsvertoning van de politie, en de start van het illegaal lijkende kap. Ik kan niet geloven dat ze een kapvergunning binnen hebben, terwijl de rechtspraak rond hun bouwvergunning nog niet rond is. Maar ja, wat weet ik ervan. Mijn gevoel kon ik dan een beetje van me afzetten door wat te helpen bij in de verbouwing van een nieuwe woning in de co-house: plaksel van de muur halen met een drilboor, puin naar buiten krijgen, spijkers uit de muur halen. Geleerd: oude spijkers moeten uit de muur voor je opnieuw plakt, anders krijg je roestvlekken. Ook geleerd: als je glas in een raam plaatst, mag je dat niet direct op het kader laten steunen, je moet er houtjes tussensteken (voor speling voor isolatie denk ik?). Morgen doen we daarmee verder én gaan we parket schaven. Ik heb echt wel zin om met het schaafmachien te leren werken! Daarna was het eten met alle bewoners, aan een grote lange tafel in de gemeenschappelijke zaal. Was vree gezellig, al was mijn sociale energie naar het einde een beetje op. Er was een 'mededelingrondje', om iedereen op de hoogte te brengen van belangrijk nieuws. Later op de avond hadden de bewoners ook nog een 'deel-cirkel'. Dat doen ze blijkbaar een keer in de maand, om eens samen te zitten en over zaken te kunnen praten op een meer diepgaande manier, en zonder de stress van beslissingen die gemaakt moeten worden, zoals in vergaderingen. Klinkt wel goed, al zou ik zelf niet direct weten of ik veel intieme zaken kan delen voor een groep. Ik zou in de eerste plaats stress krijgen. Maar misschien werkt het wel! Nu, naar bed, morgen weer een volle dag!
@ 0e501ec7:de5ef3a4
2024-10-09 21:38:52PS: lees zeker eens de blog van Tim: <https://timscyclethoughts.blogspot.com/2024/09/> :)) Vandaag was onze eerste dag in het Abtshof. (Ik weet het, gisteren is overgeslagen, oeps, en ik heb nog niet uitgevonden hoe ik hier meer foto's op kan zetten, nogmaals oeps.) Het Absthof is een coöperatieve co-housing, met een grote moestuin en een houtatelier. Het is gelegen in Borlo, een klein dorpje in de buurt van Landen. Het thuis van de wooncoöperatie is een grote vierkantshoeve, die langzaamaan helemaal gerestaureerd geraakt op (redelijk) duurzame wijze. Een heel mooie plek, waar ik al een paar keer te gast ben geweest. Hier krijgen we kost en inwoon in ruil voor mee te helpen met vanalles. Wij zijn blij om hier te zijn en ervaring op te doen, en blij dat we wat kunnen bijdragen aan duurzame/alternatieve projecten zoals deze. Ook nog belangrijk: bij een coöperatie horen ook veel beslissingen, die gedragen moeten zijn. Hier werken ze met het kader van de sociocratie. Zeer interessant, ik zal er later nog over uitweiden. Dus: we hadden op ons gemakje een lange ochtend gehad, met een lekker ontbijtje, een goede opruimbeurt, de plantjes in de serre water geven, en een random astrix en obelix strip. Het ging over de picten, ofzoiets, en iemand die de macht wou grijoen door met de romeinen samen te werken. Bon, daarvoor zijn we hier niet. Ik zou eigenlijk in bed moeten nu, de dagen zijn lang en mijn slaap dierbaar. Toch wil ik eerst nog wat schrijven. Toch toch tocht door de bomen, wilgen, essen, rode beuk Net toen we buitenstapten om te vertrekken deze ochtend, begon het te regenen! Test regenkleren: gefaald. Regenbroek is zo lek alsof hij eigenlijk niet bestaat. Maakt niet uit, ik ben niet van suiker. ; ) We zullen wel nog eens kijken voor van dat eng waterdichtmaakspul, of ik gebruik hem als windstopper, ook goed. Hier aangekomen werden we meteen ontvangen door Jakob met een warm middagmaal. Heerlijke stampot, op smaak gebracht met varkenspoot. Heftig idee, maar ik en Tim konden er wel mee overweg, en waren eigenlijk wel nieuwsgierig hoe dat smaakte zo een varkenspoot. Blijkt: nogal taai, maar wel nog een goede ervaring. Would recommend. Daarna gingen we ons installeren, en we hadden geluk! We mochten slapen in een grote tent die nog op het veld stond. Daarin zijn zelfs bedjes, en hij lijkt (redelijk) waterdicht, al had ik toch niet direct al mijn spullen moeten uitspreiden. Ons kleine tentje zou het niet gehouden hebben om de hele week in de regen opgestaan te hebben vrees ik. Daarna bereikte mij het nieuws. Van de uitzetting in het Wondelbos. Ik was er zwaar van aangedaan, boos en verdrietig, gespannen. Machteloos. Machteloos. Ik heb toen geprobeerd mijn gevoel neer te schrijven, en heb de grote uitdaging overwonnen om dat kwetsbare tekstje te delen. (Op Facebook.) Ik was wel trots op mijn kleine overwinning, maar dat viel nogal in het grote niet bij mijn eerdere gevoel bij de grote machtsvertoning van de politie, en de start van het illegaal lijkende kap. Ik kan niet geloven dat ze een kapvergunning binnen hebben, terwijl de rechtspraak rond hun bouwvergunning nog niet rond is. Maar ja, wat weet ik ervan. Mijn gevoel kon ik dan een beetje van me afzetten door wat te helpen bij in de verbouwing van een nieuwe woning in de co-house: plaksel van de muur halen met een drilboor, puin naar buiten krijgen, spijkers uit de muur halen. Geleerd: oude spijkers moeten uit de muur voor je opnieuw plakt, anders krijg je roestvlekken. Ook geleerd: als je glas in een raam plaatst, mag je dat niet direct op het kader laten steunen, je moet er houtjes tussensteken (voor speling voor isolatie denk ik?). Morgen doen we daarmee verder én gaan we parket schaven. Ik heb echt wel zin om met het schaafmachien te leren werken! Daarna was het eten met alle bewoners, aan een grote lange tafel in de gemeenschappelijke zaal. Was vree gezellig, al was mijn sociale energie naar het einde een beetje op. Er was een 'mededelingrondje', om iedereen op de hoogte te brengen van belangrijk nieuws. Later op de avond hadden de bewoners ook nog een 'deel-cirkel'. Dat doen ze blijkbaar een keer in de maand, om eens samen te zitten en over zaken te kunnen praten op een meer diepgaande manier, en zonder de stress van beslissingen die gemaakt moeten worden, zoals in vergaderingen. Klinkt wel goed, al zou ik zelf niet direct weten of ik veel intieme zaken kan delen voor een groep. Ik zou in de eerste plaats stress krijgen. Maar misschien werkt het wel! Nu, naar bed, morgen weer een volle dag! @ 0e501ec7:de5ef3a4
2024-10-09 21:37:38Ik rouw. Ik rouw om het bos, in mij groeit een grote krop van verdriet. O Wondelbos, ik zag je graag, je ontving me zo hartelijk, en ik zag hoe je de thuis was van zoveel leven, zoveel leven. Ik rouw om het vertrouwen in de rechtbank om rechtvaardig te zijn. Hoe vaak nog meneer de rechter, zal je als speelbal van machtige instituten gebruikt worden om kleine mensen, die mooie dingen proberen te doen, te intimideren? Hoe vaak nog zal jij, zonder kans voor de andere zijde om gehoord te worden, de politiemacht oproepen? Hoe vaak nog zal een vredezame actie met groot machtsvertoon beëindigd worden? Hoevaak nog zal illegale kap straffeloos blijven terwijl beschermers vervolgd en opgepakt worden? Hoevaak nog? Alle rede, alle gevoel zegt, dit bos moet behouden blijven. O bos, ik zal je missen. O Wondelbos, ik ben blij dat jij bij ons was. Nu komt voor jou een tijd van beton. Maar ik ben zeker dat er daaronder een kiertje openblijft, een zaadje zal liggen te wachten. Ik ben zeker dat het Imperium van beton ooit gedaan zal zijn, en dan zal Jij terug kunnen bloeien, terug kunnen groeien, thuis geven aan al die soorten, al die wezens, al dat leven. Dan zal Jij terug thuis kunnen komen, net als Wij. Liefs, Je liefste Aardbewoner
@ 0e501ec7:de5ef3a4
2024-10-09 21:37:38Ik rouw. Ik rouw om het bos, in mij groeit een grote krop van verdriet. O Wondelbos, ik zag je graag, je ontving me zo hartelijk, en ik zag hoe je de thuis was van zoveel leven, zoveel leven. Ik rouw om het vertrouwen in de rechtbank om rechtvaardig te zijn. Hoe vaak nog meneer de rechter, zal je als speelbal van machtige instituten gebruikt worden om kleine mensen, die mooie dingen proberen te doen, te intimideren? Hoe vaak nog zal jij, zonder kans voor de andere zijde om gehoord te worden, de politiemacht oproepen? Hoe vaak nog zal een vredezame actie met groot machtsvertoon beëindigd worden? Hoevaak nog zal illegale kap straffeloos blijven terwijl beschermers vervolgd en opgepakt worden? Hoevaak nog? Alle rede, alle gevoel zegt, dit bos moet behouden blijven. O bos, ik zal je missen. O Wondelbos, ik ben blij dat jij bij ons was. Nu komt voor jou een tijd van beton. Maar ik ben zeker dat er daaronder een kiertje openblijft, een zaadje zal liggen te wachten. Ik ben zeker dat het Imperium van beton ooit gedaan zal zijn, en dan zal Jij terug kunnen bloeien, terug kunnen groeien, thuis geven aan al die soorten, al die wezens, al dat leven. Dan zal Jij terug thuis kunnen komen, net als Wij. Liefs, Je liefste Aardbewoner @ 4ba8e86d:89d32de4
2024-10-09 13:13:10Recentemente, perdi minha lista de RSS, Decidi criar este texto sobre RSS pode ajudar a escapar das armadilhas do algoritmo das redes sociais. Além disso, para facilitar a vida daqueles que também desejam adotar o RSS como uma ferramenta de leitura, fiz um fork da lista de RSS do SethForPrivacy. Você pode acessar a lista no seguinte link: https://gist.github.com/Alexemidio/2699dd82077d483849b576a908b0c444 Aproveite a lista de RSS para personalizar seu fluxo de conteúdo e desfrutar de uma experiência de leitura mais controlada e direcionada. Utilizar um leitor de RSS bem organizado é uma estratégia eficaz para se libertar da rolagem incessante nas redes sociais e recuperar o controle sobre o conteúdo que você consome. Isso possibilita direcionar sua atenção para o conteúdo genuinamente relevante. Você já notou que os feeds das redes sociais frequentemente são inundados com notícias que provocam emoções negativas? Esse fenômeno, chamado de "doomscrolling", persiste, e as redes sociais parecem acentuar ainda mais a sua presença. A conhecida "bolha" das redes sociais nos mantém imersos, mostrando principalmente os posts com os quais interagimos. Isso tem provocado várias consequências prejudiciais, incluindo a disseminação de notícias falsas, desinformação e o agravamento de problemas como ansiedade e depressão entre os usuários. Mas, e se lhe disséssemos que existe uma alternativa? Uma maneira de receber informações diretamente, sem filtros ou algoritmos? É disso que vamos falar hoje: o RSS. O Que é o RSS? RSS é a abreviação de "Really Simple Syndication", que pode ser traduzida como "Sincronização Realmente Simples". Trata-se de um arquivo XML gerado por inúmeros sites para exibir as postagens que o site publica. Dessa forma, os leitores de RSS permitem às pessoas acompanhar diversos blogs, sites de notícias e muito mais, tudo a partir de um único local. Quem Criou o RSS? Uma das pessoas envolvidas na criação do RSS foi Aaron Swartz, um hacker notório por seu papel na fundação do Creative Commons e por ser um dos cofundadores da rede social Reddit. Se desejar se aprofundar na história de Aaron, recomendamos o documentário "O Menino da Internet: A História de Aaron Swartz" dublado em português completo. https://youtu.be/qm4NRSa9T2Q?si=GXyPXVOMJX20pIo_ Para quem gosta de RSS como eu, você não precisa usar NOSTR para acompanhar meu conteúdo. Basta me adicionar ao seu RSS. Meu RSS Nostr: nostr:npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr Utilizar um leitor de RSS bem organizado é uma maneira eficaz de se libertar da rolagem incessante e recuperar o controle sobre o conteúdo que você consome, direcionando sua atenção para o que realmente importa. Para pessoas interessantes como o nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 você não precisa segui-lo no Nostr, basta adicionar ao seu RSS. nostr:naddr1qqxnzdesx5ur2vekxucrqde5qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqa282ctyhs Leitores de RSS Recomendados: Feeder (Mobile): O Feeder é um aplicativo de leitor de RSS de código aberto que permite que você acompanhe e leia suas fontes de notícias favoritas em um só lugar. Com recursos avançados e uma interface intuitiva. Liferea (Desktop): Liferea é a abreviação de Linux Feed Reader, um programa agregador para leitura de notícias online. Ele suporta os principais tipos de arquivo criados para esse fim: RSS/RDF e Atom. Também pode importar e exportar no formato OPML.
@ 4ba8e86d:89d32de4
2024-10-09 13:13:10Recentemente, perdi minha lista de RSS, Decidi criar este texto sobre RSS pode ajudar a escapar das armadilhas do algoritmo das redes sociais. Além disso, para facilitar a vida daqueles que também desejam adotar o RSS como uma ferramenta de leitura, fiz um fork da lista de RSS do SethForPrivacy. Você pode acessar a lista no seguinte link: https://gist.github.com/Alexemidio/2699dd82077d483849b576a908b0c444 Aproveite a lista de RSS para personalizar seu fluxo de conteúdo e desfrutar de uma experiência de leitura mais controlada e direcionada. Utilizar um leitor de RSS bem organizado é uma estratégia eficaz para se libertar da rolagem incessante nas redes sociais e recuperar o controle sobre o conteúdo que você consome. Isso possibilita direcionar sua atenção para o conteúdo genuinamente relevante. Você já notou que os feeds das redes sociais frequentemente são inundados com notícias que provocam emoções negativas? Esse fenômeno, chamado de "doomscrolling", persiste, e as redes sociais parecem acentuar ainda mais a sua presença. A conhecida "bolha" das redes sociais nos mantém imersos, mostrando principalmente os posts com os quais interagimos. Isso tem provocado várias consequências prejudiciais, incluindo a disseminação de notícias falsas, desinformação e o agravamento de problemas como ansiedade e depressão entre os usuários. Mas, e se lhe disséssemos que existe uma alternativa? Uma maneira de receber informações diretamente, sem filtros ou algoritmos? É disso que vamos falar hoje: o RSS. O Que é o RSS? RSS é a abreviação de "Really Simple Syndication", que pode ser traduzida como "Sincronização Realmente Simples". Trata-se de um arquivo XML gerado por inúmeros sites para exibir as postagens que o site publica. Dessa forma, os leitores de RSS permitem às pessoas acompanhar diversos blogs, sites de notícias e muito mais, tudo a partir de um único local. Quem Criou o RSS? Uma das pessoas envolvidas na criação do RSS foi Aaron Swartz, um hacker notório por seu papel na fundação do Creative Commons e por ser um dos cofundadores da rede social Reddit. Se desejar se aprofundar na história de Aaron, recomendamos o documentário "O Menino da Internet: A História de Aaron Swartz" dublado em português completo. https://youtu.be/qm4NRSa9T2Q?si=GXyPXVOMJX20pIo_ Para quem gosta de RSS como eu, você não precisa usar NOSTR para acompanhar meu conteúdo. Basta me adicionar ao seu RSS. Meu RSS Nostr: nostr:npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr Utilizar um leitor de RSS bem organizado é uma maneira eficaz de se libertar da rolagem incessante e recuperar o controle sobre o conteúdo que você consome, direcionando sua atenção para o que realmente importa. Para pessoas interessantes como o nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 você não precisa segui-lo no Nostr, basta adicionar ao seu RSS. nostr:naddr1qqxnzdesx5ur2vekxucrqde5qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqa282ctyhs Leitores de RSS Recomendados: Feeder (Mobile): O Feeder é um aplicativo de leitor de RSS de código aberto que permite que você acompanhe e leia suas fontes de notícias favoritas em um só lugar. Com recursos avançados e uma interface intuitiva. Liferea (Desktop): Liferea é a abreviação de Linux Feed Reader, um programa agregador para leitura de notícias online. Ele suporta os principais tipos de arquivo criados para esse fim: RSS/RDF e Atom. Também pode importar e exportar no formato OPML. @ 0e501ec7:de5ef3a4
2024-10-08 20:06:29Aan het einde van een dag vol buiten zijn en fietsen en organiseren (spullen inpakken, uitpakken, drogen, eten verzamelen (letterlijk hihi), eten klaarmaken, afwas...) ben ik echt niet meer in staat om veel te schrijven. Hier komt dus een korte samenvatting van de laatste twee dagen, filosofische bedenkselen zijn voor een andere keer. Gisteren vertrokken we bij Yannick pas tegen de middag. Hoe kwam dat? Ik heb tot 9u (!) geslapen, wat wel nodig was want ik was echt volkomen uitgeput van de dag ervoor. (Veel prikkels joh, en fysieke uitdaging om 60 km te fietsen met een zwaarbeladen fiets.) (Ik weet het, klinkt niet als zoo veel maar mijn fysieke toestand was de laatste tijd niet zo heel formidabel, veel ziek en moe geweest.) Na het ontbijt heeft Tim met mijn bedenkelijke hulp mijn cassette (de tandwielen van achter) en mijn ketting vervangen. Dat ging best wel vlot, enkel het afstellen van de versnelling was niet zo gemakkelijk. We moesten een evenwicht vinden waarbij alle 9 schakels vlot gingen, aan de ene kant moesten we telkens aanspannen, terwijl we aan de andere kant telkens weer losten. Ik wou het al opgeven, toen we het net hadden gevonden. Na al dit geploeter begonnen we aan onze fietstocht door het mooie (en drukke) Brussel. Ik heb er zeer van genoten om door de stad te rijden op een kleine steek, een beetje foto's te maken en tussen de mensen te laveren. In Molenbeek kochten we in een lokale kruidenier wat droogvoer, en nog een brood, en toen trokken we verder: richting Meerdaalwoud! Eerst passeerden we nog het zoniën. Prachtig! Ik kon me niet inhouden om (bijna) alle paddestoelen te beginnen fotograferen en aan Het Algoritme van ObsIdentify te vragen hoe ze heten. Gelukkig vond Tim het wel sympathiek en stelde ik zijn geduld niet te veel op de proef. Ondertussen discussieerden we een beetje over de betrouwbaarheid van de media, het gewoonlijke, je weet wel. Gedurende de namiddag voelden we de bui al hangen, en ja hoor, tegen dat we aan de rand van het mooie Meerdaalwoud aankwamen, begon het zachtjes te druppen. In de gietende regen aten we rechtstaand ons stoofpotje op. Wat een vibe! Gelukkig was het niet koud, en konden we genieten van onze ultieme herfstsfeer. In de schemering, in de regen, klaar om in de tent te kruipen. Heerlijk! PS: Het lukt dus niet om de foto's op te laden, jammer! Ze zijn wel mooi hoor, ik verzeker het je! PPS: Ik vind het nu een beetje cringe om zo al onze gebeurtenissen te beschrijven, interesseert iemand dat eigenlijk? Interesseert het mij wel? Ik denk/voel erover na!
@ 0e501ec7:de5ef3a4
2024-10-08 20:06:29Aan het einde van een dag vol buiten zijn en fietsen en organiseren (spullen inpakken, uitpakken, drogen, eten verzamelen (letterlijk hihi), eten klaarmaken, afwas...) ben ik echt niet meer in staat om veel te schrijven. Hier komt dus een korte samenvatting van de laatste twee dagen, filosofische bedenkselen zijn voor een andere keer. Gisteren vertrokken we bij Yannick pas tegen de middag. Hoe kwam dat? Ik heb tot 9u (!) geslapen, wat wel nodig was want ik was echt volkomen uitgeput van de dag ervoor. (Veel prikkels joh, en fysieke uitdaging om 60 km te fietsen met een zwaarbeladen fiets.) (Ik weet het, klinkt niet als zoo veel maar mijn fysieke toestand was de laatste tijd niet zo heel formidabel, veel ziek en moe geweest.) Na het ontbijt heeft Tim met mijn bedenkelijke hulp mijn cassette (de tandwielen van achter) en mijn ketting vervangen. Dat ging best wel vlot, enkel het afstellen van de versnelling was niet zo gemakkelijk. We moesten een evenwicht vinden waarbij alle 9 schakels vlot gingen, aan de ene kant moesten we telkens aanspannen, terwijl we aan de andere kant telkens weer losten. Ik wou het al opgeven, toen we het net hadden gevonden. Na al dit geploeter begonnen we aan onze fietstocht door het mooie (en drukke) Brussel. Ik heb er zeer van genoten om door de stad te rijden op een kleine steek, een beetje foto's te maken en tussen de mensen te laveren. In Molenbeek kochten we in een lokale kruidenier wat droogvoer, en nog een brood, en toen trokken we verder: richting Meerdaalwoud! Eerst passeerden we nog het zoniën. Prachtig! Ik kon me niet inhouden om (bijna) alle paddestoelen te beginnen fotograferen en aan Het Algoritme van ObsIdentify te vragen hoe ze heten. Gelukkig vond Tim het wel sympathiek en stelde ik zijn geduld niet te veel op de proef. Ondertussen discussieerden we een beetje over de betrouwbaarheid van de media, het gewoonlijke, je weet wel. Gedurende de namiddag voelden we de bui al hangen, en ja hoor, tegen dat we aan de rand van het mooie Meerdaalwoud aankwamen, begon het zachtjes te druppen. In de gietende regen aten we rechtstaand ons stoofpotje op. Wat een vibe! Gelukkig was het niet koud, en konden we genieten van onze ultieme herfstsfeer. In de schemering, in de regen, klaar om in de tent te kruipen. Heerlijk! PS: Het lukt dus niet om de foto's op te laden, jammer! Ze zijn wel mooi hoor, ik verzeker het je! PPS: Ik vind het nu een beetje cringe om zo al onze gebeurtenissen te beschrijven, interesseert iemand dat eigenlijk? Interesseert het mij wel? Ik denk/voel erover na! @ 0e501ec7:de5ef3a4
2024-10-08 19:26:36Wat een vermoeiende dag! Eerst alle spanning van vertrekken, snel nog van telefoon wisselen, afscheid, veel afscheid, traantjes, nog mijn breispullen gaan halen die ik bij roos was vergeten, en dan pas eindelijk vertrekken! Fietsen fietsen fietsen! Op dit moment ben ik zeer moe, dat merk je misschien aan deze vluchtige schrijfstijl, mijn ogen vallen toe, maar dat was ik eigenlijk vanochtend al: gisterenavond waren er twee megaleuke feestjes! Eerst het verjaardagsfeestje van roos, zo vol met warme lieve mensen, en dan nog ook het verjaardagsfeestje van mijn mama! ook vol lieve mensen. Toen fietsen fietsen fietsen! Ik reed eerst alleen, langs de mooie lange schelde, tussen de wilgen, het riet, de velden... Ik was verwonderd iver de schoonheid van de paarden die langs het jaagpad stonden, ik was verwonderd over een kind dat vrolijk door een veld liep, wat een beeld zobder weerga, een soort van plattelandse veiligheid/vrijheid die we biet vaak meer tegenkomen. Toen werd ik opgehouden door allerlei werken, ik probeerde een omleiding te volgen (waarbij ik een sappige grote kastanjeoogst scoorde bij een prachtig paar bomen!) maar kwam weer midden in de jaagpadwerken uit en had toen een groot avontuur voor de boeg, hoeveel keer ik met die zwaarbeladen fiets de dijk op en af moest aj aj. Daarbij had ik ook nog een stevige tegenwind, waardoor ik pas na 14u aankwam bij mijn lieve oma en opa. Tim was daar al, en had al goed gesocialiseerd! We babbelden met ons vieren over vanalles, er kwamen allerlei oude verhalen bovendrijven bij oma en opa, ze waren precies zeer verheugd om tegen een nog niet bekende, jonge avonturier zoals Tim al hun verhalen uit de doeken te doen :)). Na ons buikje meer dan rond gegeten te hebben, trokken we weer op pad, deze keer met de knooppuntenroute die Tim had uitgestippeld. Bezienswaardigheden: de eiffeltoren van Asse, een paard om een heuvelkam, een steile bergaf die plots een grindweg werd, een boze tegenligger, veel politieke (rechtse) posters. En heuvels, en veel zondagsmensen. Tegen 6 uur kwamen we dan toe in Zellik, bij Yannick, een vriend van Tim. Die ontving ons hartelijk, met een mooie radiostem (hij studeert dat!). Na het eten speelde we nog een spelletje Boonanza, zeer leuk. Ik merk wel dat ik echt heel veel zin heb om de blog te onderhouden, het is echt zo een projectje waarmee ik iets kan brengen naar de mensen waarvan ik hou, verhalen, ideeën, foto's. Ik hoop wel dat het een beetje overkomt, ik ben nogal onzeker over het rare vreemde platformpje dat niemand kent (maar ik ben gewoon onzeker en kwetsbaar tsjah) (wat het is kan je lezen in 'een eerste poging'). Als je het leest, laat me weten wat je ervan vindt! Als mensen het leuk vinden gaat mijn motivatie om er meer op te plaatsen misschien wel overleven :). Tijdens het fietsen moest ik regelmatig denken aan The Cyborg Manifesto van Donna Haraway. Zelf heb ik dat boekje eigenlijk nog niet gelezen, maar het idee van de cyborg, het uitgebreide lichaam/zelf met technologie zet me wel aan het denken. Ik op de fiets met al mijn warme (regen)kleren in de fietszak ben precies een soort reuze huisjesslak aan topsnelheid. We razen door het landschap, ervaren het, de wind, de zon en regen, interageren met de menselijke en botanische bewoners ervan... En aan het einde van de dag zetten we onze tent op, ons verplaatsbare huisje. Wat als nu eens stopten met de wereld, ecosystemen en natuur, ons lichaam te beschouwen als machines, als radartjes, waarin problemen kunnen opgelost worden met quick files zoals een pilletje of de inrichting van reservaten (zoals we gewoon zijn bij de machines: een beetje smeren, een tandwiel vervangen, de nieuwe update installeren). Wat als we nu eens de machines als deel van ons lichaam zagen? Een lichaam om gehecht aan te zijn, om zorg voor te dragen? Om mee in wederkerige interactie met de wezens rond ons te gaan? Bon, ik moet er nog eens over nadenken, en dat boek lezen, misschien heb ik daar ooit wel eens tijd voor. Na een lange fietsdag ben ik er allisinds te moe voor!
@ 0e501ec7:de5ef3a4
2024-10-08 19:26:36Wat een vermoeiende dag! Eerst alle spanning van vertrekken, snel nog van telefoon wisselen, afscheid, veel afscheid, traantjes, nog mijn breispullen gaan halen die ik bij roos was vergeten, en dan pas eindelijk vertrekken! Fietsen fietsen fietsen! Op dit moment ben ik zeer moe, dat merk je misschien aan deze vluchtige schrijfstijl, mijn ogen vallen toe, maar dat was ik eigenlijk vanochtend al: gisterenavond waren er twee megaleuke feestjes! Eerst het verjaardagsfeestje van roos, zo vol met warme lieve mensen, en dan nog ook het verjaardagsfeestje van mijn mama! ook vol lieve mensen. Toen fietsen fietsen fietsen! Ik reed eerst alleen, langs de mooie lange schelde, tussen de wilgen, het riet, de velden... Ik was verwonderd iver de schoonheid van de paarden die langs het jaagpad stonden, ik was verwonderd over een kind dat vrolijk door een veld liep, wat een beeld zobder weerga, een soort van plattelandse veiligheid/vrijheid die we biet vaak meer tegenkomen. Toen werd ik opgehouden door allerlei werken, ik probeerde een omleiding te volgen (waarbij ik een sappige grote kastanjeoogst scoorde bij een prachtig paar bomen!) maar kwam weer midden in de jaagpadwerken uit en had toen een groot avontuur voor de boeg, hoeveel keer ik met die zwaarbeladen fiets de dijk op en af moest aj aj. Daarbij had ik ook nog een stevige tegenwind, waardoor ik pas na 14u aankwam bij mijn lieve oma en opa. Tim was daar al, en had al goed gesocialiseerd! We babbelden met ons vieren over vanalles, er kwamen allerlei oude verhalen bovendrijven bij oma en opa, ze waren precies zeer verheugd om tegen een nog niet bekende, jonge avonturier zoals Tim al hun verhalen uit de doeken te doen :)). Na ons buikje meer dan rond gegeten te hebben, trokken we weer op pad, deze keer met de knooppuntenroute die Tim had uitgestippeld. Bezienswaardigheden: de eiffeltoren van Asse, een paard om een heuvelkam, een steile bergaf die plots een grindweg werd, een boze tegenligger, veel politieke (rechtse) posters. En heuvels, en veel zondagsmensen. Tegen 6 uur kwamen we dan toe in Zellik, bij Yannick, een vriend van Tim. Die ontving ons hartelijk, met een mooie radiostem (hij studeert dat!). Na het eten speelde we nog een spelletje Boonanza, zeer leuk. Ik merk wel dat ik echt heel veel zin heb om de blog te onderhouden, het is echt zo een projectje waarmee ik iets kan brengen naar de mensen waarvan ik hou, verhalen, ideeën, foto's. Ik hoop wel dat het een beetje overkomt, ik ben nogal onzeker over het rare vreemde platformpje dat niemand kent (maar ik ben gewoon onzeker en kwetsbaar tsjah) (wat het is kan je lezen in 'een eerste poging'). Als je het leest, laat me weten wat je ervan vindt! Als mensen het leuk vinden gaat mijn motivatie om er meer op te plaatsen misschien wel overleven :). Tijdens het fietsen moest ik regelmatig denken aan The Cyborg Manifesto van Donna Haraway. Zelf heb ik dat boekje eigenlijk nog niet gelezen, maar het idee van de cyborg, het uitgebreide lichaam/zelf met technologie zet me wel aan het denken. Ik op de fiets met al mijn warme (regen)kleren in de fietszak ben precies een soort reuze huisjesslak aan topsnelheid. We razen door het landschap, ervaren het, de wind, de zon en regen, interageren met de menselijke en botanische bewoners ervan... En aan het einde van de dag zetten we onze tent op, ons verplaatsbare huisje. Wat als nu eens stopten met de wereld, ecosystemen en natuur, ons lichaam te beschouwen als machines, als radartjes, waarin problemen kunnen opgelost worden met quick files zoals een pilletje of de inrichting van reservaten (zoals we gewoon zijn bij de machines: een beetje smeren, een tandwiel vervangen, de nieuwe update installeren). Wat als we nu eens de machines als deel van ons lichaam zagen? Een lichaam om gehecht aan te zijn, om zorg voor te dragen? Om mee in wederkerige interactie met de wezens rond ons te gaan? Bon, ik moet er nog eens over nadenken, en dat boek lezen, misschien heb ik daar ooit wel eens tijd voor. Na een lange fietsdag ben ik er allisinds te moe voor! @ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias. <iframe width="560" height="315" src="https://www.youtube.com/embed/fehgwnSUcqQ?si=nPK7UOFr19BT5ifm" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ### 1. Privacy and Ownership: Foundations of Personal AI At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations. In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI. ### 2. Bias and Fairness: The Ethical Dilemma of LLMs Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values. This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks. Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge. ### 3. Explainability: The Need for Transparency One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions. Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm. This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks. ### Addressing the Ethical Landscape of Personal AI As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development. Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources. There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom. The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development. ### Conclusion In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values. If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
@ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias. <iframe width="560" height="315" src="https://www.youtube.com/embed/fehgwnSUcqQ?si=nPK7UOFr19BT5ifm" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ### 1. Privacy and Ownership: Foundations of Personal AI At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations. In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI. ### 2. Bias and Fairness: The Ethical Dilemma of LLMs Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values. This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks. Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge. ### 3. Explainability: The Need for Transparency One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions. Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm. This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks. ### Addressing the Ethical Landscape of Personal AI As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development. Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources. There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom. The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development. ### Conclusion In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values. If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation! @ 0e501ec7:de5ef3a4
2024-10-05 10:41:58De kamer is stil, maar weinig verlicht met een grijs en duister schemerlicht. Ze zitten rond een vreemdsoortige tafel, aan het verste uiteinde ervan staat een beeld. Het beeld is niet goed zichtbaar, maar de vormen ervan geven je een krop in je keel, je maag keert om. Dit zijn de machtigste mannen op aarde. Mannen ja, geen seksistische veralgemening hier, het zijn effectief alleen mannen in deze ruimte. Voor zover het te ontwaren is in het duistere licht, zijn ze gezond, fit, alsof ze dagelijks naar de yogales en de basicfit gaan. Ze zijn serieus, ze lachen niet, er is werk te doen. Ze kennen elkaar, ook al praten ze amper. Ze praten over het weer. Je weet dat dit geen leuke plek is. Je weet dat een lach je hier duur te staan kan komen. Hoe ben je hier terecht gekomen? De Mannen zitten in hun glanzende stoelen van Fenolformaldehyde en Perfluoroctaanzuur, en de stilte wordt nog zwaarder. Je hebt het koud, er steekt een ijzige wind op in de kamer, een ijskoude luchtstroom. \------------------------------------------------------------------------ Duizenden jaren hebben de kou en het ijs het mythische Antarctica vormgegeven. Dit deel van onze geliefde Biosfeer, van Patchamama, heeft nooit veel mensen gekend, de Pinguïns, de Walrussen en de Zeehonden leefden hun levens los van ons, soms vreedzaam, soms lang, soms kort en gruwelijk. Maar ze kenden hun land en ze kenden elkaar, ze wisten dat na het licht de duisternis kwam, dat de duisternis kou met zich meebracht, die soms dodelijk was, maar altijd weer plaats maakte voor een minder frisse tijd waarin ze makkelijker konden gaan jagen op de Vissen, die ze ook zeer goed kenden. Toen de eerste Mensen kwamen waren ze woordeloos. Dit waren nooit mensen van veel gebabbel geweest, anders waren ze niet tot hier geraakt, maar de aanblik van de prachtige witte glooiingen van Antarctica, de aanblik van kou en schoonheid, ongrijpbaar en gevaarlijk, maar toch zo verleidelijk, ontnam ze van alle woorden. Vol ontzag, getransformeerd keerden ze terug naar huis, al gebeurde dat niet altijd. Antarctica werd een belangrijk personage in vele heldenverhalen, in gedichten, schilderijen. Het duurde niet lang of alle Mensen hadden ervan gehoord, en velen waren in de ban van deze voor hun desolate plek. Vol leven was Antarctica, een onmisbaar orgaan in het lichaam van onze Aarde. Ze reguleerde de oceaanstromen, waaronder de golfstroom, en zorgde voor een constantere verdeling van warmte en koude. Dankzij Antarctica waren veel van de plekken die wij Thuis noemden zoals ze waren. Alle organen van onze Aarde zorgden er samen voor dat het regende wanneer het moest regenen, dat de zon scheen wanneer we er zo op wachtten, dat het ene jaar een beetje op het andere leek en we ons Thuis voelden. Thuis in de Biosfeer. \------------------------------------------------------------------------ Vandaag is er iets te vieren onder deze Mannen. Ze zijn erin geslaagd om een groot offer te brengen. Van een omvang die gewone mensen, zoals jij en ik niet kunnen omvatten. Hun God is bloedig, van een zwart soort bloed, met een hoge energetische waarde. Een te hoge energetische waarde zou je kunnen zeggen, zo hoog, dat dit bloed al snel verslavend werkt, in een trance brengt. Een trance van productiviteit, efficiëntie, destructie. Een trance van macht en geld, en 'vrije' markt. Maar de 'vrije markt' is al ter dood gebracht. Geofferd, in een vorig decennium. Het zwarte bloed vroeg meer machtsconcentratie om te blijven stromen. Deze Godheid vroeg meer toewijding, meer opoffering, meer zweet en fragiele lonen. Meer pesticiden, meer deregulatie, meer privatisering, meer staatsteun voor multinational, meer belastingverlaging. Ten dienste van de 'vrije' markt. Ten dienste van de monopolie. Dit is een God van de marktdominantie, een God van de monopolies. Jij moet dan misschien aan dat gezelschapsspel denken, dat je in een vorig leven met je familie speelde. Soms was dat nog leuk, maar even vaak eindigde het in ruzie, dat weet je nog goed. Je weet evengoed dat dít spel niet meer leuk is, al lang niet meer. Het zwarte bloed ontregelde de organen van de Aarde, opdat er nog meer zwart bloed zou moge vloeien. De Mannen vieren in stilte. Het ijs van Antarctica is gesmolten, het offer is compleet. Hun leger aan loonarbeiders (meer zweet en fragiele lonen, zo had de God geboden) zijn begonnen aan de eerste boortorens, boorplatformen en pijpleidingen. Ze weten dat hun God blij zal zijn met dit offer, hij heeft er al zolang om gevraagd. Het duurde bijna te lang, de vrees begon te groeien. Deze Mannen zijn dan machtig, angst is hun niet onbekend. Angst is hun beste vriend, al is het geen zorgzame vriendschap. Eerder een verstikkende, voortduwende, trekkende vriendschap. Ze zijn bang dat ze niet genoeg kunnen geven. Als ze niet hard genoeg werken en de offers krimpen zal hun rijk instorten. Zullen zij instorten. Onder de zware zwarte Wraak van hun Godheid. De God heeft beloofd dat Hij hun leugens voor iedereen zal uitspreiden als ze zijn offers niet kunnen brengen. Hij heeft gezworen hun Imperium te laten brokkelen wanneer zij niet hard genoeg werken en de vernietiging Hem niet tevreden stelt. Ze zijn bang. De ijzige wind kietelt in hun nek. Maar ze vieren, ze hebben iets te vieren.
@ 0e501ec7:de5ef3a4
2024-10-05 10:41:58De kamer is stil, maar weinig verlicht met een grijs en duister schemerlicht. Ze zitten rond een vreemdsoortige tafel, aan het verste uiteinde ervan staat een beeld. Het beeld is niet goed zichtbaar, maar de vormen ervan geven je een krop in je keel, je maag keert om. Dit zijn de machtigste mannen op aarde. Mannen ja, geen seksistische veralgemening hier, het zijn effectief alleen mannen in deze ruimte. Voor zover het te ontwaren is in het duistere licht, zijn ze gezond, fit, alsof ze dagelijks naar de yogales en de basicfit gaan. Ze zijn serieus, ze lachen niet, er is werk te doen. Ze kennen elkaar, ook al praten ze amper. Ze praten over het weer. Je weet dat dit geen leuke plek is. Je weet dat een lach je hier duur te staan kan komen. Hoe ben je hier terecht gekomen? De Mannen zitten in hun glanzende stoelen van Fenolformaldehyde en Perfluoroctaanzuur, en de stilte wordt nog zwaarder. Je hebt het koud, er steekt een ijzige wind op in de kamer, een ijskoude luchtstroom. \------------------------------------------------------------------------ Duizenden jaren hebben de kou en het ijs het mythische Antarctica vormgegeven. Dit deel van onze geliefde Biosfeer, van Patchamama, heeft nooit veel mensen gekend, de Pinguïns, de Walrussen en de Zeehonden leefden hun levens los van ons, soms vreedzaam, soms lang, soms kort en gruwelijk. Maar ze kenden hun land en ze kenden elkaar, ze wisten dat na het licht de duisternis kwam, dat de duisternis kou met zich meebracht, die soms dodelijk was, maar altijd weer plaats maakte voor een minder frisse tijd waarin ze makkelijker konden gaan jagen op de Vissen, die ze ook zeer goed kenden. Toen de eerste Mensen kwamen waren ze woordeloos. Dit waren nooit mensen van veel gebabbel geweest, anders waren ze niet tot hier geraakt, maar de aanblik van de prachtige witte glooiingen van Antarctica, de aanblik van kou en schoonheid, ongrijpbaar en gevaarlijk, maar toch zo verleidelijk, ontnam ze van alle woorden. Vol ontzag, getransformeerd keerden ze terug naar huis, al gebeurde dat niet altijd. Antarctica werd een belangrijk personage in vele heldenverhalen, in gedichten, schilderijen. Het duurde niet lang of alle Mensen hadden ervan gehoord, en velen waren in de ban van deze voor hun desolate plek. Vol leven was Antarctica, een onmisbaar orgaan in het lichaam van onze Aarde. Ze reguleerde de oceaanstromen, waaronder de golfstroom, en zorgde voor een constantere verdeling van warmte en koude. Dankzij Antarctica waren veel van de plekken die wij Thuis noemden zoals ze waren. Alle organen van onze Aarde zorgden er samen voor dat het regende wanneer het moest regenen, dat de zon scheen wanneer we er zo op wachtten, dat het ene jaar een beetje op het andere leek en we ons Thuis voelden. Thuis in de Biosfeer. \------------------------------------------------------------------------ Vandaag is er iets te vieren onder deze Mannen. Ze zijn erin geslaagd om een groot offer te brengen. Van een omvang die gewone mensen, zoals jij en ik niet kunnen omvatten. Hun God is bloedig, van een zwart soort bloed, met een hoge energetische waarde. Een te hoge energetische waarde zou je kunnen zeggen, zo hoog, dat dit bloed al snel verslavend werkt, in een trance brengt. Een trance van productiviteit, efficiëntie, destructie. Een trance van macht en geld, en 'vrije' markt. Maar de 'vrije markt' is al ter dood gebracht. Geofferd, in een vorig decennium. Het zwarte bloed vroeg meer machtsconcentratie om te blijven stromen. Deze Godheid vroeg meer toewijding, meer opoffering, meer zweet en fragiele lonen. Meer pesticiden, meer deregulatie, meer privatisering, meer staatsteun voor multinational, meer belastingverlaging. Ten dienste van de 'vrije' markt. Ten dienste van de monopolie. Dit is een God van de marktdominantie, een God van de monopolies. Jij moet dan misschien aan dat gezelschapsspel denken, dat je in een vorig leven met je familie speelde. Soms was dat nog leuk, maar even vaak eindigde het in ruzie, dat weet je nog goed. Je weet evengoed dat dít spel niet meer leuk is, al lang niet meer. Het zwarte bloed ontregelde de organen van de Aarde, opdat er nog meer zwart bloed zou moge vloeien. De Mannen vieren in stilte. Het ijs van Antarctica is gesmolten, het offer is compleet. Hun leger aan loonarbeiders (meer zweet en fragiele lonen, zo had de God geboden) zijn begonnen aan de eerste boortorens, boorplatformen en pijpleidingen. Ze weten dat hun God blij zal zijn met dit offer, hij heeft er al zolang om gevraagd. Het duurde bijna te lang, de vrees begon te groeien. Deze Mannen zijn dan machtig, angst is hun niet onbekend. Angst is hun beste vriend, al is het geen zorgzame vriendschap. Eerder een verstikkende, voortduwende, trekkende vriendschap. Ze zijn bang dat ze niet genoeg kunnen geven. Als ze niet hard genoeg werken en de offers krimpen zal hun rijk instorten. Zullen zij instorten. Onder de zware zwarte Wraak van hun Godheid. De God heeft beloofd dat Hij hun leugens voor iedereen zal uitspreiden als ze zijn offers niet kunnen brengen. Hij heeft gezworen hun Imperium te laten brokkelen wanneer zij niet hard genoeg werken en de vernietiging Hem niet tevreden stelt. Ze zijn bang. De ijzige wind kietelt in hun nek. Maar ze vieren, ze hebben iets te vieren. @ 0e501ec7:de5ef3a4
2024-10-04 16:53:22We zijn nu 2 dagen voor het gepland vertrek, 4/10/2024. Ik ben zeer blij dat ik een fietsmaatje heb, genaamd Tim, die een datum heeft vastgelegd om te vertrekken. Als ik dat niet had gehad, dan was ik het vertrek waarschijnlijk nog een hele poos blijven uitstellen, of zelfs nooit vertrokken geraakt! Nu heb ik deze week wel met wat stress rondgelopen, je weet wel hoe stressgevoelig ik ben en je klaarmaken voor een grote reis is toch wel een beetje spannend. Onze reis heeft geen strak plan. Als mensen ernaar vragen zeg ik altijd: we vertrekken richting het zuiden. Dan vragen ze nog: 'hoelang blijf je weg' en dan moet ik bekennen dat ik het niet weet. Veel mensen reageren een beetje onbegrijpend, maar een paar snappen het meteen en zijn laaiend enthousiast. En ik moet bekennen, dat ben ik zelf ook wel! Het is dus voor het grootste deel positieve spanning. Natuurlijk ook een beetje koudwatervrees, letterlijk dan, want ik heb zo een voorgevoel dat het veél gaat regenen! Ons plannetje is om naast fietsen ook te stoppen op interessante plekken, zoals transitie-projecten of alternatieve gemeenschappen. Daar willen we graag meewerken en helpen waar we kunnen, maar ook mensen leren kennen en veel bijleren! Ik wil bijvoorbeeld heel graag houtbewerking leren, en Tim wilt graag over moestuinen en andere landbouwtechnieken leren (denk ik). En dat komt goed uit: veel projecten hebben een houtatelier en een grote moestuin. Al moeten we dat natuurlijk zien hé. Het eerste project zal het Absthof worden, in Borlo. Zondag vertrekken we dus in die richting. We passeren mijn grootouders in Aalst, slapen dan waarschijnlijk bij een vriend van Tim in Zellik, en gaan dan via het Meerdaalwoud naar Landen/Borlo. Ik ben zeer benieuwd hoe het fietsen mij gaat bevallen. Ik ben de laatste tijd nogal moe geweest, moe en ziek. Van één nachtje te weinig slaap voelde ik mij telkens weer verkouden. Ik denk echter dat het vooral het teveel aan stress en te weinig mentale rust is van het laatste jaar dat daar aan de oorzaak van ligt. Ik verwacht dus dat de fietsreis mij goed gaat doen, om mijn lichaam terug te herstellen en een routine op te bouwen met minder stress. Maaar: toch spannend! In het begin zou ik wel eens te moe kunnen zijn om ver te fietsen. Hopelijk lukt het mij om op tijd te zeggen Jow ik ben echt moe we zullen vandaag toch wat minder moeten fietsen. Dat zal wel echt belangrijk zijn, want als ik mij in het begin overdoe ga ik het misschien niet lang volhouden. Komt wel goed! De voorbereidingen van deze week waren: de fiets kuisen, versnellingen afstellen, slag uit de wielen halen (merci Tim!!!), een stuurpenverlenger installeren zodat ik minder voorovergebogen zit, regenkleren opnieuw behandelen zodat ze waterdicht zijn, en een tripje naar de Decathlon, voor waterdichte overschoenen, een achterlicht en wat waterdichte zakken. Daarnaast ben ik ook nog vandaag naar de gemeente geweest om een volmacht te regelen, voor de verkiezingen volgende week!
@ 0e501ec7:de5ef3a4
2024-10-04 16:53:22We zijn nu 2 dagen voor het gepland vertrek, 4/10/2024. Ik ben zeer blij dat ik een fietsmaatje heb, genaamd Tim, die een datum heeft vastgelegd om te vertrekken. Als ik dat niet had gehad, dan was ik het vertrek waarschijnlijk nog een hele poos blijven uitstellen, of zelfs nooit vertrokken geraakt! Nu heb ik deze week wel met wat stress rondgelopen, je weet wel hoe stressgevoelig ik ben en je klaarmaken voor een grote reis is toch wel een beetje spannend. Onze reis heeft geen strak plan. Als mensen ernaar vragen zeg ik altijd: we vertrekken richting het zuiden. Dan vragen ze nog: 'hoelang blijf je weg' en dan moet ik bekennen dat ik het niet weet. Veel mensen reageren een beetje onbegrijpend, maar een paar snappen het meteen en zijn laaiend enthousiast. En ik moet bekennen, dat ben ik zelf ook wel! Het is dus voor het grootste deel positieve spanning. Natuurlijk ook een beetje koudwatervrees, letterlijk dan, want ik heb zo een voorgevoel dat het veél gaat regenen! Ons plannetje is om naast fietsen ook te stoppen op interessante plekken, zoals transitie-projecten of alternatieve gemeenschappen. Daar willen we graag meewerken en helpen waar we kunnen, maar ook mensen leren kennen en veel bijleren! Ik wil bijvoorbeeld heel graag houtbewerking leren, en Tim wilt graag over moestuinen en andere landbouwtechnieken leren (denk ik). En dat komt goed uit: veel projecten hebben een houtatelier en een grote moestuin. Al moeten we dat natuurlijk zien hé. Het eerste project zal het Absthof worden, in Borlo. Zondag vertrekken we dus in die richting. We passeren mijn grootouders in Aalst, slapen dan waarschijnlijk bij een vriend van Tim in Zellik, en gaan dan via het Meerdaalwoud naar Landen/Borlo. Ik ben zeer benieuwd hoe het fietsen mij gaat bevallen. Ik ben de laatste tijd nogal moe geweest, moe en ziek. Van één nachtje te weinig slaap voelde ik mij telkens weer verkouden. Ik denk echter dat het vooral het teveel aan stress en te weinig mentale rust is van het laatste jaar dat daar aan de oorzaak van ligt. Ik verwacht dus dat de fietsreis mij goed gaat doen, om mijn lichaam terug te herstellen en een routine op te bouwen met minder stress. Maaar: toch spannend! In het begin zou ik wel eens te moe kunnen zijn om ver te fietsen. Hopelijk lukt het mij om op tijd te zeggen Jow ik ben echt moe we zullen vandaag toch wat minder moeten fietsen. Dat zal wel echt belangrijk zijn, want als ik mij in het begin overdoe ga ik het misschien niet lang volhouden. Komt wel goed! De voorbereidingen van deze week waren: de fiets kuisen, versnellingen afstellen, slag uit de wielen halen (merci Tim!!!), een stuurpenverlenger installeren zodat ik minder voorovergebogen zit, regenkleren opnieuw behandelen zodat ze waterdicht zijn, en een tripje naar de Decathlon, voor waterdichte overschoenen, een achterlicht en wat waterdichte zakken. Daarnaast ben ik ook nog vandaag naar de gemeente geweest om een volmacht te regelen, voor de verkiezingen volgende week! @ 0e501ec7:de5ef3a4
2024-10-04 10:54:18Have you watched the pigeons? have you watched the crow? Heb je het beemdooievaarsbekje ooit al eens goed bekeken? Heb je al eens gevraagd aan de boomkikker hoe die naar het leven kijkt? Wat hen denkt van jouw prachtig onderhouden voortuingazon? Every species is a soul, a fire, a story, a story that is told and retold and retold Every species is a song A song of love, of life of neverending trial and struggle Trial and error they say, evolution they say, mutation and selection But your demystification is not working The species never stop telling their unholy wispering stories They never stop This is a song for the lost souls This is a song of grief This story tells the song ofthe species that don't that cannot anymore The species we lost I love you herfstvuurspin Ik hou van je ik hou van je ik Ik mis je Ik voel in heel mijn lijf dat je ontbreekt en ik ben zeker dat ik niet de enige ben
@ 0e501ec7:de5ef3a4
2024-10-04 10:54:18Have you watched the pigeons? have you watched the crow? Heb je het beemdooievaarsbekje ooit al eens goed bekeken? Heb je al eens gevraagd aan de boomkikker hoe die naar het leven kijkt? Wat hen denkt van jouw prachtig onderhouden voortuingazon? Every species is a soul, a fire, a story, a story that is told and retold and retold Every species is a song A song of love, of life of neverending trial and struggle Trial and error they say, evolution they say, mutation and selection But your demystification is not working The species never stop telling their unholy wispering stories They never stop This is a song for the lost souls This is a song of grief This story tells the song ofthe species that don't that cannot anymore The species we lost I love you herfstvuurspin Ik hou van je ik hou van je ik Ik mis je Ik voel in heel mijn lijf dat je ontbreekt en ik ben zeker dat ik niet de enige ben @ 0e501ec7:de5ef3a4
2024-10-03 09:54:14Dit is een eerste poging om een post te creëeren die op de oracolo html-blog verschijnt. Ik snap helemaal niet zo goed hoe dit allemaal werkt, maar het lijkt wel spannend. De blog werkt op basis van een htmlbestandje, dat je zou kunnen hosten via github. ofzo. Waarom zo en niet op een andere manier? Ik vind nostr wel cool, omdat het helemaal gedecentraliseerd is en zonder groot bedrijf. Het wordt gebouwd door een heleboel geëngageerde developpers, en is ook open-source. Joepie! Misschien is het gewoon eens iets anders dat ik wil uitproberen, dat kan ook. Allesinds, ik voel er (nog) niet de enorme weerstand tegen die ik wel voel bij alle meta-dingetjes zoals facebook enz. Als dit werkt gebruik ik het misschien wel als blog tijdens onze fietsreis, wie weet. Ah en nog iets, in navolging van de 100rabbits programeur die op een zeilboot woont: kleine apps die doen wat ze moeten doen om de computer minder te belasten en energie te besparen, dat is helemaal cool en duurzaam en heeft off-grid potentieel. (Maar daar heb ik dan wel weer een bedenking bij: nostr is wel wat verbonden met bitcoin, en die heeft niet zo een energie-zuinig imago.)
@ 0e501ec7:de5ef3a4
2024-10-03 09:54:14Dit is een eerste poging om een post te creëeren die op de oracolo html-blog verschijnt. Ik snap helemaal niet zo goed hoe dit allemaal werkt, maar het lijkt wel spannend. De blog werkt op basis van een htmlbestandje, dat je zou kunnen hosten via github. ofzo. Waarom zo en niet op een andere manier? Ik vind nostr wel cool, omdat het helemaal gedecentraliseerd is en zonder groot bedrijf. Het wordt gebouwd door een heleboel geëngageerde developpers, en is ook open-source. Joepie! Misschien is het gewoon eens iets anders dat ik wil uitproberen, dat kan ook. Allesinds, ik voel er (nog) niet de enorme weerstand tegen die ik wel voel bij alle meta-dingetjes zoals facebook enz. Als dit werkt gebruik ik het misschien wel als blog tijdens onze fietsreis, wie weet. Ah en nog iets, in navolging van de 100rabbits programeur die op een zeilboot woont: kleine apps die doen wat ze moeten doen om de computer minder te belasten en energie te besparen, dat is helemaal cool en duurzaam en heeft off-grid potentieel. (Maar daar heb ik dan wel weer een bedenking bij: nostr is wel wat verbonden met bitcoin, en die heeft niet zo een energie-zuinig imago.) @ e6817453:b0ac3c39
2024-09-30 14:52:23In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance. <iframe width="560" height="315" src="https://www.youtube.com/embed/BkNqu51et9U?si=lne0jWxdrZPxSgd1" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ## The Vector Search and Metadata Challenge In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results. Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data. ## LibSQL and vector search metadata LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points. ``` create table if not exists conversation ( id varchar(36) primary key not null, startDate real, endDate real, summary text, vectorSummary F32_BLOB(512) ); ``` It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage. As you can see, you can access vector-like data and start date in the same query. ``` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from conversation where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top}; ``` **vector\_distance\_cos** calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data. This approach could be calculation intensive and fail on large amounts of data. Libsql offers a way more effective vector search based on FlashDiskANN vector indexed. ``` vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i ``` **vector\_top\_k** is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies. Now we get a classical problem of integration vector search results with metadata queries. ## Post-Filtering: A Common Approach The most widely adopted method in these pipelines is **post-filtering**. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.  Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter. ``` const sqlQuery = ` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i inner join conversation c on i.id = c.rowid where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top}; ``` However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results. One working strategy is to make the top value in vector\_top\_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows. ## Pre-Filtering: A More Complex Approach Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning. While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.  In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data. ## Pre-filtering with distance-based filtering So, we are getting back to an old concept. We do prefiltering instead of using a vector index. ``` WITH FilteredDates AS ( SELECT c.id, c.startDate, c.endDate, c.summary, c.vectorSummary FROM YourTable c WHERE ${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''} ), DistanceCalculation AS ( SELECT fd.id, fd.startDate, fd.endDate, fd.summary, fd.vectorSummary, vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance FROM FilteredDates fd ) SELECT dc.id, dc.startDate, dc.endDate, dc.summary, dc.distance FROM DistanceCalculation dc WHERE 1=1 ${distance ? `AND dc.distance <= ${distance}` : ''} ORDER BY dc.distance LIMIT ${top}; ``` It makes sense if the filter produces small data and distance calculation happens on the smaller data set.  As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches. ## Choosing Between Pre and Post-Filtering Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization. In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further. ## **Conclusion** Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further.
@ e6817453:b0ac3c39
2024-09-30 14:52:23In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance. <iframe width="560" height="315" src="https://www.youtube.com/embed/BkNqu51et9U?si=lne0jWxdrZPxSgd1" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ## The Vector Search and Metadata Challenge In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results. Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data. ## LibSQL and vector search metadata LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points. ``` create table if not exists conversation ( id varchar(36) primary key not null, startDate real, endDate real, summary text, vectorSummary F32_BLOB(512) ); ``` It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage. As you can see, you can access vector-like data and start date in the same query. ``` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from conversation where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top}; ``` **vector\_distance\_cos** calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data. This approach could be calculation intensive and fail on large amounts of data. Libsql offers a way more effective vector search based on FlashDiskANN vector indexed. ``` vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i ``` **vector\_top\_k** is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies. Now we get a classical problem of integration vector search results with metadata queries. ## Post-Filtering: A Common Approach The most widely adopted method in these pipelines is **post-filtering**. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.  Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter. ``` const sqlQuery = ` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i inner join conversation c on i.id = c.rowid where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top}; ``` However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results. One working strategy is to make the top value in vector\_top\_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows. ## Pre-Filtering: A More Complex Approach Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning. While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.  In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data. ## Pre-filtering with distance-based filtering So, we are getting back to an old concept. We do prefiltering instead of using a vector index. ``` WITH FilteredDates AS ( SELECT c.id, c.startDate, c.endDate, c.summary, c.vectorSummary FROM YourTable c WHERE ${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''} ), DistanceCalculation AS ( SELECT fd.id, fd.startDate, fd.endDate, fd.summary, fd.vectorSummary, vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance FROM FilteredDates fd ) SELECT dc.id, dc.startDate, dc.endDate, dc.summary, dc.distance FROM DistanceCalculation dc WHERE 1=1 ${distance ? `AND dc.distance <= ${distance}` : ''} ORDER BY dc.distance LIMIT ${top}; ``` It makes sense if the filter produces small data and distance calculation happens on the smaller data set.  As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches. ## Choosing Between Pre and Post-Filtering Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization. In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further. ## **Conclusion** Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further. @ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x). # TL;DR This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/). The following concepts are explored: 1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust). 2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse. 3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time. The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems. [Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater. # Cognitive Dissonance Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol. I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement. The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership. For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data). In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned. How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data? # Self-sovereign Identity Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity. All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money. Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state. Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k). https://i.nostr.build/xpcCSkDg3uVw0yku.png While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this. Nostr is PGP for the masses and will take cryptographic identities mainstream. # Full NOSTARD? Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons. We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be. https://i.nostr.build/s3So2JVAqoY4E1dI.png There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap. While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g). https://i.nostr.build/ot9jtM5cZtDHNKWc.png So, how do we appropriately blend cryptographically owned data with the commons? If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons). The remainder of this article explores how we can: 1. Verify ownership of a physical place in the real world; 2. Link that ownership to the corresponding digital place in cyberspace. As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0. And as we all know, the Second Law of Infodynamics (no citation\!) states that: > "The total amount of sensitive information leaked will always increase over time." This especially holds true if that data is centralised. Not your keys, not your notes. Not your keys, not your identity. # Places and Web-of-Trust [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)). However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world. Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop. This requires users to: 1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace). 2. Signal this verification to their social graph. Let's look at the latter idea first with the concept of Attestations ... # Attestations A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false. Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too. However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc). Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation: https://i.nostr.build/lZAXOEwvRIghgFY4.png Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with: 1. Your social graph; 2. The type or subject of the content being attested and by whom; 3. Your personal preferences. They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places. [NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive. **‘This is true’** resonates more strongly than **‘I like this.’**. https://i.nostr.build/s8NIG2kXzUCLcoax.jpg There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP? https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust. # Proof of Place Attestations handle the signalling of your truth, but what about the initial verification itself? We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth. Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace. One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location. Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places). In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential): > "A failure to understand Proof of Work, is a failure to understand Bitcoin." In the Nostrverse, Proof of Place helps bridge the digital and physical worlds. [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that: > "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone." https://i.nostr.build/dOnpxfI4u7EL2v4e.png This isn’t true for Nostr. In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯 # Check-ins Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes). For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used. Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices. Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am. Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable. How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\! Check-ins could also be used as a signal for bonafide Place ownership over time. # Summary: Trust Your Bros So, to recap, we have: **Places**: Digital representations of physical locations on Nostr. **Check-ins**: Users signalling their presence at a location. **Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim. You can visualise how these three concepts combine in the diagram below: https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg And, as always, top right trumps bottom left\! We have: **Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all. **Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL. **Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph. https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map? Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide. As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities. # Thanks With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\!
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on [Habla](https://habla.news/u/nathan@btcmap.org/2uBWmmKOqd-09vQVMH8X0), [YakiHonne](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrq6c73gs) or [Highlighter](nostr:naddr1qvzqqqr4gupzp384u7n44r8rdq74988lqcmggww998jjg0rtzfd6dpufrxy9djk8qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qq2nya2z2akk6j60w9jz6vpeweg4vn2g8pvrqzwws2x). # TL;DR This article explores the links between public, community-driven data sources (such as [OpenStreetMap](https://www.openstreetmap.org)) and private, cryptographically-owned data found on networks such as [Nostr](https://nostr.org/). The following concepts are explored: 1. **Attestations**: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your [web-of-trust](https://en.wikipedia.org/wiki/Web_of_trust). 2. **Proof of Place**: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in [meatspace](https://en.wiktionary.org/wiki/meatspace) with their digital representations in the Nostrverse. 3. **Check-ins**: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time. The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems. [Open Data](https://en.wikipedia.org/wiki/Open_data) in a public commons has a place and should not be thrown out with the Web 2.0 bathwater. # Cognitive Dissonance Ever since discovering [Nostr](https://nostr.org/) in August of 2022 I've been grappling with how [BTC Map](https://btcmap.org/) \- a project that helps bitcoiners find places to spend sats \- should most appropriately use this new protocol. I am assuming, dear reader, that you are somewhat familiar with Nostr \- a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: [Nostr is Identity for the Internet](https://hivemind.vc/identity/) and [The Power of Nostr](https://www.lynalden.com/the-power-of-nostr/) by [@max](nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3) and [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a), respectively. Nostr is so much more than a short-form social media replacement. The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting \- all your silos are indeed broken \- however, something fundamental has been bothering me for a while and I think it comes down to data ownership. For those unfamiliar, BTC Map uses [OpenStreetMap (OSM)](https://www.openstreetmap.org) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) \- FOSD if you will, but more commonly referred to as [Open Data](https://en.wikipedia.org/wiki/Open_data). In contrast, Notes and Other Stuff on Nostr ([Places](https://github.com/nostr-protocol/nips/pull/927) in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned. How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data? # Self-sovereign Identity Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something \- an identity. All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money. Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state. Or, as [@nvk](nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8) said recently: ["Don't build your house on someone else's land."](nostr:nevent1qqsf493dryeqzrsfjq938hpjg3jf3yd8cv70a9ggzlts5p29tasawkqpz9mhxue69uhkummnw3ezuamfdejj7q3qaz9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgsxpqqqqqqzajen2k). https://i.nostr.build/xpcCSkDg3uVw0yku.png While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this. Nostr is PGP for the masses and will take cryptographic identities mainstream. # Full NOSTARD? Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons. We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be. https://i.nostr.build/s3So2JVAqoY4E1dI.png There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a [Wikifreedia](https://wikifreedia.xyz/) variant of OpenStreetMap. While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native \- there's no need to go [Full NOSTARD](https://fountain.fm/clip/48noGYA7bRXNP96dqsOP). H/T to [@princeySOV](nostr:npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2) for the [original meme](nostr:nevent1qqst7609zyuy92q655mzls5trdv8u6h8d4v7myjc3t6gvxs68qrtp6cpr9mhxue69uhhyetvv9ujuam9d3kx7unyv4ezumn9wszka25g). https://i.nostr.build/ot9jtM5cZtDHNKWc.png So, how do we appropriately blend cryptographically owned data with the commons? If a location is owned in meatspace *and* it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the [tragedy of the commons](https://en.wikipedia.org/wiki/Tragedy_of_the_commons). The remainder of this article explores how we can: 1. Verify ownership of a physical place in the real world; 2. Link that ownership to the corresponding digital place in cyberspace. As a side note, I don't see private key custodianship \- or, even worse, permissioned use of Places signed by another identity's key \- as any more viable than the rented identities of Web 2.0. And as we all know, the Second Law of Infodynamics (no citation\!) states that: > "The total amount of sensitive information leaked will always increase over time." This especially holds true if that data is centralised. Not your keys, not your notes. Not your keys, not your identity. # Places and Web-of-Trust [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has been leading the charge on the [Places NIP](https://github.com/nostr-protocol/nips/pull/927), introducing Nostr notes (kind 37515\) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) (championed by [@oscar](nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2) of [@fountain](nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5)). However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world. Ultimately, this problem can only be solved in a decentralised way by using [Web-of-Trust](https://en.wikipedia.org/wiki/Web_of_trust) \- using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop. This requires users to: 1. Verify the owner of a Place in cyberspace is the owner of a place in [meatspace](https://en.wiktionary.org/wiki/meatspace). 2. Signal this verification to their social graph. Let's look at the latter idea first with the concept of Attestations ... # Attestations A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false. Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too. However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc). Here is a [recent example](nostr:nevent1qqsx8qu64xpnqaqkcqtrm4ly4l6xdqk9g2wkcaxxm3hzcc2p3hcz2ugzyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057y5k93z) from [@lyn](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) that would carry more signal if it were an Attestation: https://i.nostr.build/lZAXOEwvRIghgFY4.png Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or [Data Vending Machines](https://www.data-vending-machines.org/) in accordance with: 1. Your social graph; 2. The type or subject of the content being attested and by whom; 3. Your personal preferences. They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places. [NIP-25 (Reactions)](https://github.com/nostr-protocol/nips/blob/master/25.md) do allow for users to up/downvote notes with optional content (e.g., emojis) and *could* work for Attestations, but I think we need something less ambiguous and more definitive. **‘This is true’** resonates more strongly than **‘I like this.’**. https://i.nostr.build/s8NIG2kXzUCLcoax.jpg There are similar concepts in the Web 3 / Web 5 world such as [Verified Credentials](https://developer.tbd.website/docs/web5/verifiable-credentials/what-are-vcs) by [tdb](nostr:npub10ckt8dne8lahkwxwevtxf3rlvgttf2lvqrqc4rg7h8mdhsx6rcpqsg7muq). However, Nostr is the Web 3 now and so wen Attestation NIP? https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg That said, I have seen [@utxo](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) has been [exploring ‘smart contracts’ on nostr](nostr:nevent1qqswm26c4s4h56zwkk47w40mhsqqn66jk6lfas8r07w67h69474kkfgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsw9n8heusyq0el9f99tveg7r0rhcu9tznatuekxt764m78ymqu36c0kd565) and Attestations *may* just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust. # Proof of Place Attestations handle the signalling of your truth, but what about the initial verification itself? We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth. Introducing *Proof of Place*, an out–of-band process where an oracle (such as [BTC Map](https://btcmap.org/)\) would mail \- yes physically mail\- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace. One way of doing this would be to mint a 1 sat [cashu](https://github.com/cashubtc) ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location. Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places). In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) says in [PoW is Essential](https://dergigi.com/threads/pow-is-essential): > "A failure to understand Proof of Work, is a failure to understand Bitcoin." In the Nostrverse, Proof of Place helps bridge the digital and physical worlds. [@Gigi](nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) also observes in [Memes vs The World](https://dergigi.com/threads/memes-vs-the-world) that: > "In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone." https://i.nostr.build/dOnpxfI4u7EL2v4e.png This isn’t true for Nostr. In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯 # Check-ins Although not a draft NIP yet, [@Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w) has also been exploring the familiar concept of [Foursquare](https://foursquare.com/)\-style [Check-ins on Nostr](nostr:naddr1qvzqqqr4gupzp68dx7vvdlltl7sg2qdv8838ze3tl5tq76y0jnz966fdsana6dz6qqxnzde3xqungv3jxq6ngvp52f3mja) (with kind 13811 notes). For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as [OSM elements](https://wiki.openstreetmap.org/wiki/Elements)) if [NIP-73 \- External Content IDs](https://github.com/nostr-protocol/nips/blob/744bce8fcae0aca07b936b6662db635c8b4253dd/73.md) are used. Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices. Bringing Check-ins to Nostr is possible (as [@sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) capably [shows here](nostr:note1wjf6x9a5xehzr3z0hm8fgdyenznf6hxlmswldhmhsgk7fc9e86cscmsnve)), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am. Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable. How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene \- I’m sure [@blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) and [@Ben Arc](nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm) could hack something together over a weekend\! Check-ins could also be used as a signal for bonafide Place ownership over time. # Summary: Trust Your Bros So, to recap, we have: **Places**: Digital representations of physical locations on Nostr. **Check-ins**: Users signalling their presence at a location. **Attestations**: Verifiable social proofs used to confirm ownership or the truth of a claim. You can visualise how these three concepts combine in the diagram below: https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg And, as always, top right trumps bottom left\! We have: **Level 0 \- Trust Me Bro:** Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all. **Level 1 \- Definitely Maybe Somewhere:** This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL. **Level 2 \- Trust Your Bros:** An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph. https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map? Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ \- you decide. As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities. # Thanks With thanks to [Arkinox](nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w), [Avi](nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s), [Ben Gunn](nostr:npub1lt8nn8aaa6qa63wjwj8gz2djf5nlhg3zfd0v6l45v8zhvuyh0p3s5zzt5y), [Kieran](nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49), [Blackcoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt), [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe), [Tomek](nostr:npub1t30xvk4f3h86lhxazadwx6f2namer9yzgl70kfljfhr556g7su0qwg0lmp), [Calle](nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg), [Short Fiat](nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9), [Ben Weeks](nostr:npub1jutptdc2m8kgjmudtws095qk2tcale0eemvp4j2xnjnl4nh6669slrf04x) and [Bitcoms](nostr:npub18s6axkw94d57sg438rp7pzf94vn8la4axyvd5f6wnjrgudtw54ps53eqxk) for helping shape my thoughts and refine content, whether you know it or not\! @ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining. Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully. Solo mining pools exist, such as: https://solo.ckpool.org/ It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool. You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power. There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely. A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine. So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning. So here’s my recommendation. Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin. Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join. If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools. Bear in mind that many of the other smaller pools are still controlled by Bitmain. If you're still interested in lottery mining, here are your chances of winning a block: Represented as Hash rates of different miners: Nerdminer: 20 KH/s = 20,000 H/s Bitaxe: 750 GH/s = 750,000,000,000 H/s Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000 If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357% Over a year, your chances increase to: 0.00627707006369428% Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one): 0.000005% Over a year, your chances increase to: 0.00026% Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions: https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/ https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx https://www.youtube.com/watch?v=Wo91DWvZRs8 https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
@ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining. Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully. Solo mining pools exist, such as: https://solo.ckpool.org/ It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool. You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power. There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely. A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine. So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning. So here’s my recommendation. Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin. Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join. If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools. Bear in mind that many of the other smaller pools are still controlled by Bitmain. If you're still interested in lottery mining, here are your chances of winning a block: Represented as Hash rates of different miners: Nerdminer: 20 KH/s = 20,000 H/s Bitaxe: 750 GH/s = 750,000,000,000 H/s Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000 If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357% Over a year, your chances increase to: 0.00627707006369428% Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one): 0.000005% Over a year, your chances increase to: 0.00026% Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions: https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/ https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx https://www.youtube.com/watch?v=Wo91DWvZRs8 https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg @ 01d0bbf9:91130d4c
2024-09-26 17:58:10## Chef's notes Amazingly tangy, firey hot, but still mellow and bright. I use this on everything– Use it to dress salads, dip (honey mustard) for fried chicken, elevate your taco nights, heck a spoonful first thing in the morning will wake you up better than coffee! Don't forget to use up those delicious chilis and garlic, they are so good! ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 1-2 weeks - 🍽️ Servings: (12x) 8oz jars ## Ingredients - 16oz fresh chili peppers - 8oz red onion - 8oz garlic - 96oz honey - Fresh thyme ## Directions 1. Thinly slice peppers, garlic, shallots and fresh thyme 2. Add chopped ingredients to the honey 3. Leave to ferment (loosely covered) for 1-2 weeks 4. Drizzle that amazing pungent firey gold liquid over EVERYTHING. (Don't forget to use up those amazing chilis and garlic too.)
@ 01d0bbf9:91130d4c
2024-09-26 17:58:10## Chef's notes Amazingly tangy, firey hot, but still mellow and bright. I use this on everything– Use it to dress salads, dip (honey mustard) for fried chicken, elevate your taco nights, heck a spoonful first thing in the morning will wake you up better than coffee! Don't forget to use up those delicious chilis and garlic, they are so good! ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 1-2 weeks - 🍽️ Servings: (12x) 8oz jars ## Ingredients - 16oz fresh chili peppers - 8oz red onion - 8oz garlic - 96oz honey - Fresh thyme ## Directions 1. Thinly slice peppers, garlic, shallots and fresh thyme 2. Add chopped ingredients to the honey 3. Leave to ferment (loosely covered) for 1-2 weeks 4. Drizzle that amazing pungent firey gold liquid over EVERYTHING. (Don't forget to use up those amazing chilis and garlic too.) @ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like: Messaging: https://www.0xchat.com/#/ - Private messaging - think WhatsApp Xitter Like Clients: https://damus.io/ - iPhone client https://nostrapps.com/amethyst - Android client https://primal.net/downloads - Android, iPhone & Desktop https://shipyard.pub/posts - Schedule future posts Interesting sites: https://zap.stream/ - Video streaming https://fountain.fm/ - Podcasting https://wavlake.com/ - Music streaming https://shopstr.store/ - Online shop https://zap.cooking/recent - Cooking recipes https://ostrich.work/ - NOSTR jobs board NOSTR tools https://nostr.band/ - Powerful search tool https://nostr.wine/ - Powerful, but centralised paid relay https://npub.pro/ - Website creation tool https://nostr.build/ - Media and file storage https://relay.tools/ - Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user - Creator tools List of NOSTR apps: https://nostrapps.com/
@ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like: Messaging: https://www.0xchat.com/#/ - Private messaging - think WhatsApp Xitter Like Clients: https://damus.io/ - iPhone client https://nostrapps.com/amethyst - Android client https://primal.net/downloads - Android, iPhone & Desktop https://shipyard.pub/posts - Schedule future posts Interesting sites: https://zap.stream/ - Video streaming https://fountain.fm/ - Podcasting https://wavlake.com/ - Music streaming https://shopstr.store/ - Online shop https://zap.cooking/recent - Cooking recipes https://ostrich.work/ - NOSTR jobs board NOSTR tools https://nostr.band/ - Powerful search tool https://nostr.wine/ - Powerful, but centralised paid relay https://npub.pro/ - Website creation tool https://nostr.build/ - Media and file storage https://relay.tools/ - Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user - Creator tools List of NOSTR apps: https://nostrapps.com/ @ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous. In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism. On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important. That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played. Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end. The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism: I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is. In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore. The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true. The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good. In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.” I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous. In other words, my [primary negative sentiment](https://chrisliss.substack.com/p/utilitarianism-is-a-scourge) — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause [catastrophic outcomes](https://chrisliss.substack.com/p/off-the-cliff) — stems from a sort of disappointed idealism, not cynicism. On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important. That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played. Twitter threads don’t show up on substack anymore, but I’d encourage you to read [this one](https://twitter.com/KanekoaTheGreat/status/1681458308358737920) with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end. The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism: I’d encourage people to read the [entire thread](https://twitter.com/Chris_Liss/status/1681474427551363073), but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is. In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore. The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true. The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good. In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.” I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it. @ ee11a5df:b76c4e49
2024-09-11 08:16:37# Bye-Bye Reply Guy There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients. But we are not there yet. In the mean time we have ReplyGuy, and gossip needed some changes to deal with it. ## Strategies in Short 1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people. 2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering. 3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post) 4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more. 5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity 6. **PROOF OF WORK**: Require a minimum proof-of-work All of these strategies are useful, but they have to be combined properly. ## filter.rhai Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam. This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release. Here is an example using all of the techniques listed above: ```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off) fn filter() { // Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY } ```
@ ee11a5df:b76c4e49
2024-09-11 08:16:37# Bye-Bye Reply Guy There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients. But we are not there yet. In the mean time we have ReplyGuy, and gossip needed some changes to deal with it. ## Strategies in Short 1. **WEB OF TRUST**: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people. 2. **TRUSTED RELAYS**: Allow every post from relays that you trust to do good spam filtering. 3. **REJECT FRESH PUBKEYS**: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post) 4. **PATTERN MATCHING**: Scan for known spam phrases and words and block those events, either on content or metadata or both or more. 5. **TIE-IN TO EXTERNAL SYSTEMS**: Require a valid NIP-05, or other nostr event binding their identity to some external identity 6. **PROOF OF WORK**: Require a minimum proof-of-work All of these strategies are useful, but they have to be combined properly. ## filter.rhai Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam. This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release. Here is an example using all of the techniques listed above: ```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off) fn filter() { // Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY } ``` @ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good! If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/> # Intro **Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us. **Paolo:** Thank you for having us. **Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we? **Luke:** Sounds like that's the plan. So thank you again, both for joining us. # Introducing Paolo and Mathias **Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you **Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate. **Luke:** And, Mathias, over to you. **Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use. P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that. And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here. **Luke:** Oh, fantastic. # Introduction to Holepunch **Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch. What is Holepunch and what are you doing? **Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us. but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy. It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God. that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks. Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use, Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it? and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world. And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company. And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand. anything, super exciting and, encourage everybody to try to check it out. **Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product? What is the easiest way that you would explain what it is? # The Vision Behind Keet **Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer People don't care about technology. We loved it, but don't have that surface off too much to the user. Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it. It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard. And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that. # Keet vs Nostr **Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here. **Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform. And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly. You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users. So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays. and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology. It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace. Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly. **Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that. # Pear Runtime **Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform, **Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it. And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications. We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that. So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve. But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything. So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view. and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard. so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example. It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app. So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place. But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that. And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone. And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached. Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like **Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective. And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that? **Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective. And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things. I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point. # Decentralization vs. Centralization **Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor? **Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias. I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right? Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions. and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers. That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there. And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far. Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features. And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users. And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is. It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that. And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key **Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites. But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept. over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud. And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers. the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on. is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole. And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before. Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize. And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system. And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country. So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to. **Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives. So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right? **Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all. So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting. yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why # Challenges and Future of Decentralization **Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company. And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing. So is there a limitation to how far this can go? **Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world. Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling. So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house. I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created. imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you. Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure. So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another. And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example. **Knut:** Yeah. **Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money. And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook? it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way. And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it. We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback. # Bitcoin and Holepunch: Drawing Parallels **Mathias:** I think, that's the main thing to think about in that. Discussion. **Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line. And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin? **Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange. For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government. and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right? Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them. and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them. **Luke:** Yeah, fantastic. # The Future of Decentralized Communication **Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet. So is, that a goal? Is that on the roadmap? **Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world. But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind. **Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly. And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app. And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly, # Interoperability and User Experience **Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong, **Mathias:** Very, true. **Luke:** you backups with the same 1224 words. Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be **Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it. **Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life. You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build. Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible. **Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems? What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that? **Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us. The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity. No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful. **Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever. but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera. But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem. And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it. **Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options. Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right? you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion. so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai. So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that. And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself. And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center. **Knut:** Yeah. # The Role of Tether in the Crypto Ecosystem **Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo? And, what, made this thing happen? Can you give us the story here about Tether? # Tether's Origin and Evolution **Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014. it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat. That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000. But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right? International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin. For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic. # USDT's Impact on Emerging Markets **Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries. Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap. So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time. we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world. At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right? you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others. And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT. If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right? So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U. S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant. # Bitcoin as a Savings Account **Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend. The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies. we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining. We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other. I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math. That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin. **Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother. **Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether. So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right? So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education. **Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic. I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke. **Luke:** Always say the title, Knut. Always say the title. **Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course. **Paolo:** Oh, with pleasure, with great pleasure, with a nice, education. **Luke:** Absolutely. Yep. # Plan B Forum and Future Events **Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year. so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event. **Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year. I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world. And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing. **Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time. And I think we're even playing this year, aren't we, Luke? **Paolo:** You're **Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos. Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague? **Knut:** paranoid and, **Paolo:** Can I commission a **Knut:** What song would you like to hear? **Paolo:** I have two that I would suggest. One is Nothing Else Matters. **Knut:** Alright. **Paolo:** So I think that, is very inspiring, right? **Knut:** Bitcoin, for sure. Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke? **Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference, **Knut:** Yeah. **Mathias:** not so much music, but yeah, that's peer to **Knut:** Nothing else matters. **Luke:** looking forward to that. **Knut:** Sorry, brain fart. Sad but true is about the dollar still being around, **Paolo:** Yeah, you can say that. **Luke:** Okay. # Final Thoughts and Closing Remarks **Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that? **Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms. There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out. **Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting. **Mathias:** Just those things, that's all. **Paolo:** Yeah, we can piss off more than this. Thanks. **Mathias:** a **Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners? **Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them. **Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good. **Luke:** So that's, all at Keet. Is that correct? For Keet? **Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer. **Knut:** Alright, **Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah. **Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano. **Paolo:** Likewise, I **Knut:** But yeah, worth saying again. **Paolo:** Thank you for having an invitation. **Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
@ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good! If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! <https://bitcoininfinitystore.com/> # Intro **Luke:** Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us. **Paolo:** Thank you for having us. **Knut:** Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we? **Luke:** Sounds like that's the plan. So thank you again, both for joining us. # Introducing Paolo and Mathias **Luke:** would you both mind giving a quick introduction on yourselves just so our listeners have the background on you **Paolo:** Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate. **Luke:** And, Mathias, over to you. **Mathias:** Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use. P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that. And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here. **Luke:** Oh, fantastic. # Introduction to Holepunch **Luke:** Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch. What is Holepunch and what are you doing? **Mathias:** Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us. but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy. It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God. that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks. Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use, Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it? and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world. And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company. And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand. anything, super exciting and, encourage everybody to try to check it out. **Luke:** we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product? What is the easiest way that you would explain what it is? # The Vision Behind Keet **Mathias:** But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer People don't care about technology. We loved it, but don't have that surface off too much to the user. Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it. It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard. And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that. # Keet vs Nostr **Knut:** Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here. **Paolo:** I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform. And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly. You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users. So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays. and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology. It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace. Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly. **Luke:** Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that. # Pear Runtime **Luke:** So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform, **Mathias:** Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it. And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications. We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that. So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve. But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything. So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view. and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard. so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example. It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app. So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place. But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that. And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone. And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached. Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like **Knut:** and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective. And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that? **Mathias:** I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective. And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things. I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point. # Decentralization vs. Centralization **Luke:** So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor? **Mathias:** yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias. I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right? Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions. and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers. That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there. And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far. Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features. And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users. And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is. It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that. And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key **Paolo:** I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites. But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept. over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud. And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers. the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on. is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole. And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before. Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize. And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system. And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country. So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to. **Knut:** Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives. So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right? **Mathias:** I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all. So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting. yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why # Challenges and Future of Decentralization **Luke:** So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company. And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing. So is there a limitation to how far this can go? **Paolo:** I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world. Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling. So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house. I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created. imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you. Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure. So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another. And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example. **Knut:** Yeah. **Mathias:** I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money. And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook? it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way. And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it. We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback. # Bitcoin and Holepunch: Drawing Parallels **Mathias:** I think, that's the main thing to think about in that. Discussion. **Luke:** when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line. And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin? **Paolo:** Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange. For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government. and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right? Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them. and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them. **Luke:** Yeah, fantastic. # The Future of Decentralized Communication **Luke:** And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet. So is, that a goal? Is that on the roadmap? **Paolo:** Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world. But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind. **Mathias:** But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly. And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app. And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly, # Interoperability and User Experience **Luke:** Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong, **Mathias:** Very, true. **Luke:** you backups with the same 1224 words. Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be **Mathias:** We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it. **Paolo:** I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life. You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build. Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible. **Luke:** Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems? What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that? **Paolo:** Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us. The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity. No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful. **Mathias:** also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever. but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera. But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem. And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it. **Paolo:** And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options. Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right? you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion. so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai. So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that. And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself. And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center. **Knut:** Yeah. # The Role of Tether in the Crypto Ecosystem **Knut:** It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo? And, what, made this thing happen? Can you give us the story here about Tether? # Tether's Origin and Evolution **Paolo:** Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014. it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat. That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000. But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right? International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin. For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic. # USDT's Impact on Emerging Markets **Paolo:** So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries. Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap. So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time. we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world. At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right? you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others. And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT. If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right? So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U. S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant. # Bitcoin as a Savings Account **Paolo:** the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend. The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies. we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining. We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other. I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math. That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin. **Knut:** Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother. **Paolo:** we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether. So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right? So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education. **Knut:** No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic. I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke. **Luke:** Always say the title, Knut. Always say the title. **Knut:** Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course. **Paolo:** Oh, with pleasure, with great pleasure, with a nice, education. **Luke:** Absolutely. Yep. # Plan B Forum and Future Events **Luke:** 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year. so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event. **Paolo:** I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year. I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world. And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing. **Knut:** No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time. And I think we're even playing this year, aren't we, Luke? **Paolo:** You're **Luke:** yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos. Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague? **Knut:** paranoid and, **Paolo:** Can I commission a **Knut:** What song would you like to hear? **Paolo:** I have two that I would suggest. One is Nothing Else Matters. **Knut:** Alright. **Paolo:** So I think that, is very inspiring, right? **Knut:** Bitcoin, for sure. Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke? **Mathias:** we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference, **Knut:** Yeah. **Mathias:** not so much music, but yeah, that's peer to **Knut:** Nothing else matters. **Luke:** looking forward to that. **Knut:** Sorry, brain fart. Sad but true is about the dollar still being around, **Paolo:** Yeah, you can say that. **Luke:** Okay. # Final Thoughts and Closing Remarks **Luke:** Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that? **Mathias:** only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms. There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out. **Paolo:** we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting. **Mathias:** Just those things, that's all. **Paolo:** Yeah, we can piss off more than this. Thanks. **Mathias:** a **Luke:** No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners? **Paolo:** just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them. **Mathias:** We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good. **Luke:** So that's, all at Keet. Is that correct? For Keet? **Mathias:** Key. io and pairs. com for our runtime. It's all peer to peer. **Knut:** Alright, **Mathias:** Wonderful. And you're also still on the legacy social media platforms, right? Yeah. **Knut:** we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano. **Paolo:** Likewise, I **Knut:** But yeah, worth saying again. **Paolo:** Thank you for having an invitation. **Luke:** Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show. @ 8cb60e21:5f2deaea
2024-09-10 21:14:08<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-10 21:14:08<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint. I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point. I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog. In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout. Are there any odds you're excited about (doesn't have to be football)? originally posted at https://stacker.news/items/679894
@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint. I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, [freebitcoin](https://freebitco.in/?r=51325722) hasn't put any NFL games up, yet. Hopefully they get around to it at some point. I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog. In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout. Are there any odds you're excited about (doesn't have to be football)? originally posted at https://stacker.news/items/679894 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。 通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。 --- 2024年08月13日更新: > 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。 为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。 --- ### 准备工具 - Ntfy服务 - Google Script - Google Sheets ### 操作步骤 1. 在Ntfy后台账号,设置访问令牌。 [](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌") 2. 添加订阅主题。 [](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题") 2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图: [](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id") 3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌): ```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet(); // 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据 var sentEmails = getSentEmails(sheet); var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length); if (threads.length === 0) return; threads.forEach(function(thread) { var threadId = thread.getId(); if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); } }); } function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; } var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"} 内容: ${email.getPlainBody() || "无内容"}`; var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true }; try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } } function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column } function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); } function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间 var data = sheet.getDataRange().getValues(); var rowsToDelete = []; data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } }); // 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); } ``` 4.Goole Script需要添加gmail服务,如图: [](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务") 5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图: [](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器") [](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细") ### 结尾 本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。 如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。 效果预览: [](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览")
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23### 由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。 通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。 --- 2024年08月13日更新: > 修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。 为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。 --- ### 准备工具 - Ntfy服务 - Google Script - Google Sheets ### 操作步骤 1. 在Ntfy后台账号,设置访问令牌。 [](https://tgpic.lepidus.me/file/db4faa1a82507771a2412.jpg "访问令牌") 2. 添加订阅主题。 [](https://tgpic.lepidus.me/file/c55b5e2f455918fc38c48.jpg "订阅主题") 2. 进入[Google Sheets](https://docs.google.com/spreadsheets/u/0/ "Google Sheets")创建一个表格.记住id,如下图: [](https://tgpic.lepidus.me/file/d33272bd247b71a61314a.jpg "Google Sheets id") 3. 进入[Google Script](https://script.google.com/home "Google Script")创建项目。填入以下代码(注意填入之前的ntfy地址和令牌): ```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet(); // 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据 var sentEmails = getSentEmails(sheet); var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length); if (threads.length === 0) return; threads.forEach(function(thread) { var threadId = thread.getId(); if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); } }); } function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; } var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"} 内容: ${email.getPlainBody() || "无内容"}`; var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true }; try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } } function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column } function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); } function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间 var data = sheet.getDataRange().getValues(); var rowsToDelete = []; data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } }); // 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); } ``` 4.Goole Script需要添加gmail服务,如图: [](https://tgpic.lepidus.me/file/42afddf2441556fca7ddb.jpg "gmail服务") 5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图: [](https://tgpic.lepidus.me/file/b12042613a793f08bce55.png "触发器") [](https://tgpic.lepidus.me/file/768be170e04ebfd6788fc.png "触发器设置详细") ### 结尾 本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。 如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。 效果预览: [](https://tgpic.lepidus.me/file/f934acd1c188e475cd9e5.jpg "效果预览") @ 655a7cf1:d0510794
2024-09-10 13:16:15Currently have kyc BTC, huge fan of lightning Network. Because I am a constant user of lightning. Plan on doing my business with lightning as well , peer-to-peer I'm not sure if I'm so worried about kyc I might be misguided in this situation. originally posted at https://stacker.news/items/679520
@ 655a7cf1:d0510794
2024-09-10 13:16:15Currently have kyc BTC, huge fan of lightning Network. Because I am a constant user of lightning. Plan on doing my business with lightning as well , peer-to-peer I'm not sure if I'm so worried about kyc I might be misguided in this situation. originally posted at https://stacker.news/items/679520 @ 6ad3e2a3:c90b7740
2024-09-10 09:26:37While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions: **1. Separate passengers from their bags as early as possible.** The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences: a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes. b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day. c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five. d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier. e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable. The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children. To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc. There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.) Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane. **2. Eliminate Security Lines** Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement. a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use. Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious. b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side. Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side. **3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.** Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal. **4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.** There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done. Here are some other suggestions: 1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up. 2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges. 3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease. 4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them. I can anticipate some objections to these ideas, and I’ll address each one in turn. **1. This would cost too much money.** My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.) **2. It’s too much of a security risk.** Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end. Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle. **3. I like free carry-ons because it saves me from waiting at the baggage claim.** Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse. The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist. *\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.* *\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.*
@ 6ad3e2a3:c90b7740
2024-09-10 09:26:37While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions: **1. Separate passengers from their bags as early as possible.** The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences: a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes. b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day. c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five. d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier. e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable. The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children. To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off *outside* the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc. There would be no need for bag tags because people *could* have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.) Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane. **2. Eliminate Security Lines** Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement. a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use. Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious. b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side. Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side. **3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.** Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal. **4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.** There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done. Here are some other suggestions: 1. With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up. 2. Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges. 3. Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease. 4. Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them. I can anticipate some objections to these ideas, and I’ll address each one in turn. **1. This would cost too much money.** My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.) **2. It’s too much of a security risk.** Airport security is incredibly flawed right now, as [tests repeatedly show](http://edition.cnn.com/2015/06/01/politics/tsa-failed-undercover-airport-screening-tests/). You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end. Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle. **3. I like free carry-ons because it saves me from waiting at the baggage claim.** Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse. The bottom line — the current state of air travel both in the US and Europe is unacceptable\*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing\*\* lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist. *\*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.* *\*\* This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.* @ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed. @ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
@ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg @ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect. Therefore, I strongly advise you to run multiple clients. On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay. If you haven’t taken the plunge to run a node, now might be a good time to think about it. There are many, many options for clients, the “Social” section of https://nostrapps.com/ lists 23 currently. Play with them, see what they do, if you’re a developer, you could even consider building or forking your own. Have fun and realise we are building freedom tech, not just running it.
@ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect. Therefore, I strongly advise you to run multiple clients. On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay. If you haven’t taken the plunge to run a node, now might be a good time to think about it. There are many, many options for clients, the “Social” section of https://nostrapps.com/ lists 23 currently. Play with them, see what they do, if you’re a developer, you could even consider building or forking your own. Have fun and realise we are building freedom tech, not just running it. @ e83b66a8:b0526c2b
2024-09-09 20:27:41First, Key management. When you “created” your NOSTR account, what you actually created was a cryptographic key pair. This consists of a private key, which starts “nsec” and a public key which starts with “npub”. As the names suggest, your “nsec” key is private and you should never reveal it to anyone. Your “npub” key is your public key, feel free to share that everywhere. Your “npub” key is used by others to verify your identity, through the signature added to your messages. It is also used by others to encrypt private messages to you. We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary. For the moment, consider using software key management options, some of which are listed under “signers” here: https://nostrapps.com/ N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted: Secondly, Lightning wallets. It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key. You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet. Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason…. It also allows you to send small micropayments to posts or people you like. Thirdly, Paid Services As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability. I, for example choose to pay for the following services: https://nostr.wine/ - 120,000 Sats for 2 years relay https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month https://nostr.build/ - Media storage - 69,000 Sats for 1 year Total: 22,750 Sats per month Approx $15 per month This is not strictly necessary, but I decided to support the various developers behind these projects. Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward.
@ e83b66a8:b0526c2b
2024-09-09 20:27:41First, Key management. When you “created” your NOSTR account, what you actually created was a cryptographic key pair. This consists of a private key, which starts “nsec” and a public key which starts with “npub”. As the names suggest, your “nsec” key is private and you should never reveal it to anyone. Your “npub” key is your public key, feel free to share that everywhere. Your “npub” key is used by others to verify your identity, through the signature added to your messages. It is also used by others to encrypt private messages to you. We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary. For the moment, consider using software key management options, some of which are listed under “signers” here: https://nostrapps.com/ N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted: Secondly, Lightning wallets. It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key. You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet. Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason…. It also allows you to send small micropayments to posts or people you like. Thirdly, Paid Services As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability. I, for example choose to pay for the following services: https://nostr.wine/ - 120,000 Sats for 2 years relay https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month https://nostr.build/ - Media storage - 69,000 Sats for 1 year Total: 22,750 Sats per month Approx $15 per month This is not strictly necessary, but I decided to support the various developers behind these projects. Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward. @ c11cf5f8:4928464d
2024-09-09 18:45:16 originally posted at https://stacker.news/items/678432
@ c11cf5f8:4928464d
2024-09-09 18:45:16 originally posted at https://stacker.news/items/678432 @ e968e50b:db2a803a
2024-09-09 18:21:54 Open the frozen pizza bay doors, Hal. originally posted at https://stacker.news/items/678403
@ e968e50b:db2a803a
2024-09-09 18:21:54 Open the frozen pizza bay doors, Hal. originally posted at https://stacker.news/items/678403 @ 6bae33c8:607272e8
2024-09-09 16:07:43I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
@ 6bae33c8:607272e8
2024-09-09 16:07:43I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry. Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — [made it to the final 23](https://www.youtube.com/watch?v=huDt630lNXs) in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing. When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “[the man in the arena](https://www.trcp.org/2011/01/18/it-is-not-the-critic-who-counts/) whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week. This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, [the entire odyssey](https://podcasts.apple.com/us/podcast/a-real-man-would/id1023898853?i=1000661712394) while sick and still jet-lagged in 122-degree heat. But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. *I* was the guy who got this done. *I* flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia. And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring [sports content to nostr](https://iris.to/npub1dwhr8j9uy6ju2uu39t6tj6mw76gztr4rwdd6jr9qtkdh5crjwt5q2nqfxe) which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write. And I got the idea to do this seriously because Heather wrote a [guide to Lisbon](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) which [I posted on nostr](https://njump.me/nevent1qqsfqv5gzytdxmtt2kfj2d3565qe848klnkxne9jaquzudrmzzq5vcqzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5qqcyqqqqqqgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyt8wumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mgpr3mhxue69uhkummnw3ezumt4w35ku7thv9kxcet59e3k7mgpp4mhxue69uhkummn9ekx7mqgucshh), and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a [(very in-depth) guide](https://njump.me/nevent1qqs9tlalaaxc9s0d3wtldcxjcu2xtwmda03ln37l05y465xfppc7x5gzyqy0v0mtymwefaha06kw286cnq5rqnv9vsku8eh89rg3szqnqnpfxqcyqqqqqqgpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgnwaehxw309aex2mrp09skymr99ehhyecpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmdqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdyj9jl7) to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be [Team of Destiny](https://www.youtube.com/watch?v=huDt630lNXs), Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week. . . . While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play. There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent. At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor. I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha. . . . In last week’s [Survivor post](https://www.realmansports.com/p/surviving-week-1-d02), I wrote: *What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.* It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens. . . . I [picked the Bengals](https://www.realmansports.com/p/surviving-week-1-d02) knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more. And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it. I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable. . . . I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed. @ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :) I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet. What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds? What is your experience? I'd love to hear about it!
@ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :) I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet. What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds? What is your experience? I'd love to hear about it! @ 3875a16c:988456c9
2024-09-09 14:50:15**ORIGINAL PANEL TITLE:** MAKING BITCOIN MORE PRIVATE WITH CISA **SPEAKERS:** NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP **CONFERENCE:** BITCOIN NASHVILLE 2024 **ORIGINALLY PUBLISHED ON:** BITLYRICS.CO ## Introduction This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/). Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development. --- ### NiftyNei (Moderator): Hey everyone, my name is Nifty, and I’m going to be moderating this panel today. We’re here to talk about CISA (cross-input signature aggregation). Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage. We’re excited to be talking to you guys about this. I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA. Craig, do you want to start? --- ### Craig Raw (Sparrow Wallet): I built Sparrow Wallet. It’s a security and privacy-focused wallet. The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen. When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically. So, that was the first time I really started to look at it from the privacy angle. --- ### Fabian Jahr (Brink): I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it. Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core. Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months. I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller. I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it. --- ### Jameson Lopp (Casa): I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups. I think the first time I heard about CISA was in an Andrew Poelstra talk. I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted. This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics. --- ### NiftyNei (Moderator): That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for. Does anyone have a good explanation of how it works? --- ### Fabian Jahr (Brink): I can start off. So, it’s really already all in the name: cross-input signature aggregation. If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated. What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction. So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before. Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea. --- ### NiftyNei (Moderator): I have a quick question about that. So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right? So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature. Is that a good summary of what you’re explaining? --- ### Fabian Jahr (Brink): Yeah, I would say so. --- ### Craig Raw (Sparrow Wallet): So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it. That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one. Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it. Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones. Unfortunately, the downside of that is that you have to do the interaction while you sign. The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing. As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient. --- ### NiftyNei (Moderator): Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right? You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level? --- ### Jameson Lopp (Casa): Well, there’s also full-block aggregation, right? This is going really far down the rabbit hole, and I think it’s not even something that’s on the table. There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations. My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized. If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again. --- ### NiftyNei (Moderator): So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation. We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there. One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right? Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated. --- ### Jameson Lopp (Casa): Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically. If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount. It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO. You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet. It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot. It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before. So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so. --- ### Fabian Jahr (Brink): And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy. The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property. Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.” Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it. Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature. --- ### Jameson Lopp (Casa): Yeah, we have to think about the incentives, right? I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are. But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late. We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so. It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software. Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money? --- ### Craig Raw (Sparrow): So you might be wondering at this stage what the savings actually look like. It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block. You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage. Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%. But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space. So that’s how I would encourage you to think about it from the start. For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride. We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about. --- ### NiftyNei (Moderator): I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy. I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal? What was it about the Taproot process where this proposal didn’t make it over the line? --- ### Fabian Jahr (Brink): I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed. From what I can see, I don’t think there was any direct opposition. The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller. I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding. I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much. --- ### Craig Raw (Sparrow): Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough. There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.” That’s an interesting point of view. --- ### Jameson Lopp (Casa): It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet. --- ### Craig Raw (Sparrow): Yeah, so we’re in a very different space now. Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine. I’m talking about the well-understood half-signature aggregation form of it. From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that. So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing. If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down. So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line. --- ### Jameson Lopp (Casa): I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin. With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process. As far as I’m aware, there’s been limited adoption of Schnorr so far. I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility. I care about this a lot, operating a multi-signature self-custody wallet. We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature. That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out. So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block. --- ### NiftyNei (Moderator): So, we only have a few minutes left. Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in. --- ### Fabian Jahr (Brink): There are still quite a few things to hammer out in terms of all the details, like defining a spec. For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open. However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity. We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now. --- ### Jameson Lopp (Casa): Yeah, call your local developer and demand signature aggregation today. --- ### Craig Raw (Sparrow): Fabian has developed a great site where you can learn more. If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it. It’s very easy to read, not overly technical, and I think it gives a good grounding in these things. Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not. As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now. So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not. --- ### Jameson Lopp (Casa): I don’t know, do you want to save money? It should be an easy question. --- ### Fabian Jahr (Brink): And have better privacy. --- ### NiftyNei (Moderator): Great! Thanks y’all. --- **Follow the speakers: ** [NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr) **Watch the original content: ** [Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107) **Also read: Build It Right: ** [Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/) **Disclaimer: ** Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/).
@ 3875a16c:988456c9
2024-09-09 14:50:15**ORIGINAL PANEL TITLE:** MAKING BITCOIN MORE PRIVATE WITH CISA **SPEAKERS:** NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP **CONFERENCE:** BITCOIN NASHVILLE 2024 **ORIGINALLY PUBLISHED ON:** BITLYRICS.CO ## Introduction This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( [CISA](https://cisaresearch.org/faq)). Moderated by NiftyNei from [Base58](https://base58.info/), the panel includes Jameson Lopp from [Casa](https://casa.io/), Craig Raw from [Sparrow Wallet](https://sparrowwallet.com/), and Fabian Jahr from [Brink](https://brink.dev/). Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development. --- ### NiftyNei (Moderator): Hey everyone, my name is Nifty, and I’m going to be moderating this panel today. We’re here to talk about CISA (cross-input signature aggregation). Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage. We’re excited to be talking to you guys about this. I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA. Craig, do you want to start? --- ### Craig Raw (Sparrow Wallet): I built Sparrow Wallet. It’s a security and privacy-focused wallet. The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen. When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically. So, that was the first time I really started to look at it from the privacy angle. --- ### Fabian Jahr (Brink): I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it. Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core. Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months. I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller. I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it. --- ### Jameson Lopp (Casa): I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups. I think the first time I heard about CISA was in an Andrew Poelstra talk. I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted. This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics. --- ### NiftyNei (Moderator): That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for. Does anyone have a good explanation of how it works? --- ### Fabian Jahr (Brink): I can start off. So, it’s really already all in the name: cross-input signature aggregation. If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated. What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction. So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before. Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea. --- ### NiftyNei (Moderator): I have a quick question about that. So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right? So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature. Is that a good summary of what you’re explaining? --- ### Fabian Jahr (Brink): Yeah, I would say so. --- ### Craig Raw (Sparrow Wallet): So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it. That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one. Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it. Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones. Unfortunately, the downside of that is that you have to do the interaction while you sign. The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing. As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient. --- ### NiftyNei (Moderator): Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right? You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level? --- ### Jameson Lopp (Casa): Well, there’s also full-block aggregation, right? This is going really far down the rabbit hole, and I think it’s not even something that’s on the table. There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations. My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized. If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again. --- ### NiftyNei (Moderator): So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation. We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there. One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right? Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated. --- ### Jameson Lopp (Casa): Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically. If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount. It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO. You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet. It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot. It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before. So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so. --- ### Fabian Jahr (Brink): And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy. The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property. Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.” Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it. Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature. --- ### Jameson Lopp (Casa): Yeah, we have to think about the incentives, right? I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are. But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late. We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so. It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software. Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money? --- ### Craig Raw (Sparrow): So you might be wondering at this stage what the savings actually look like. It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block. You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage. Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%. But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space. So that’s how I would encourage you to think about it from the start. For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride. We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about. --- ### NiftyNei (Moderator): I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy. I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal? What was it about the Taproot process where this proposal didn’t make it over the line? --- ### Fabian Jahr (Brink): I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed. From what I can see, I don’t think there was any direct opposition. The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller. I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding. I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much. --- ### Craig Raw (Sparrow): Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough. There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.” That’s an interesting point of view. --- ### Jameson Lopp (Casa): It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet. --- ### Craig Raw (Sparrow): Yeah, so we’re in a very different space now. Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine. I’m talking about the well-understood half-signature aggregation form of it. From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that. So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing. If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down. So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line. --- ### Jameson Lopp (Casa): I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin. With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process. As far as I’m aware, there’s been limited adoption of Schnorr so far. I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility. I care about this a lot, operating a multi-signature self-custody wallet. We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature. That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out. So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block. --- ### NiftyNei (Moderator): So, we only have a few minutes left. Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in. --- ### Fabian Jahr (Brink): There are still quite a few things to hammer out in terms of all the details, like defining a spec. For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open. However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity. We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now. --- ### Jameson Lopp (Casa): Yeah, call your local developer and demand signature aggregation today. --- ### Craig Raw (Sparrow): Fabian has developed a great site where you can learn more. If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to [CISAResearch.org](https://cisaresearch.org/), you can learn more about it. It’s very easy to read, not overly technical, and I think it gives a good grounding in these things. Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not. As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now. So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not. --- ### Jameson Lopp (Casa): I don’t know, do you want to save money? It should be an easy question. --- ### Fabian Jahr (Brink): And have better privacy. --- ### NiftyNei (Moderator): Great! Thanks y’all. --- **Follow the speakers: ** [NiftyNei](https://njump.me/npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy) – [Craig Raw](https://njump.me/npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2) – [Jameson Lopp](https://njump.me/npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp) – [Fabian Jahr](https://github.com/fjahr) **Watch the original content: ** [Click here](https://www.youtube.com/watch?v=HvI7NPI_Pk0&list=PLe0djdakvnFYPDH8_rd4NsABQCODVZ-ru&index=107) **Also read: Build It Right: ** [Achieving Interoperability with Open Networks](https://bitlyrics.co/transcripts/interoperable-businesses-open-networks/) **Disclaimer: ** Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please [contact us](https://bitlyrics.co/contact/). @ 44dc1c2d:31c74f0b
2024-09-09 01:55:24## Chef's notes Makes an excellent Chicken sandwich. ## Details - ⏲️ Prep time: 6 Ish hours - 🍳 Cook time: 40 min - 🍽️ Servings: 1 loaf ## Ingredients - 3 ½ - 4 cups bread flour, or more as needed - 1 ⅓ cups warm milk (110°F – 115°F) - 5 tablespoons honey - 4 tablespoons salted butter, melted and slightly cooled - 1 tablespoon instant “rapid rise” yeast - 1 ½ teaspoons salt - Oil or butter for greasing the bowl - 1 tablespoon melted salted butter, for brushing the crust at the end ## Directions 1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl. 2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes. 3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours. 4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan. 5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F. 6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped. 7. Brush the top of the warm bread with melted butter. 8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24## Chef's notes Makes an excellent Chicken sandwich. ## Details - ⏲️ Prep time: 6 Ish hours - 🍳 Cook time: 40 min - 🍽️ Servings: 1 loaf ## Ingredients - 3 ½ - 4 cups bread flour, or more as needed - 1 ⅓ cups warm milk (110°F – 115°F) - 5 tablespoons honey - 4 tablespoons salted butter, melted and slightly cooled - 1 tablespoon instant “rapid rise” yeast - 1 ½ teaspoons salt - Oil or butter for greasing the bowl - 1 tablespoon melted salted butter, for brushing the crust at the end ## Directions 1. To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl. 2. Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes. 3. Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours. 4. Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan. 5. Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F. 6. Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped. 7. Brush the top of the warm bread with melted butter. 8. Remove from the pan and cool on a wire rack for at least 1 hour before slicing. @ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one? Thanks originally posted at https://stacker.news/items/677439
@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one? Thanks originally posted at https://stacker.news/items/677439 @ eed76ece:afa98124
2024-09-08 21:13:37Seems like if you want to sell an item on SN using @AGORA makes logical sense. Perhaps if your a manufacturer, importer, exporter, stocking distributor, wholesaler etc. you should also consider using @Import_Export or both @AGORA and see if they help each other. Being totally upfront Import_Export is probably a better use case especially if you are running over 75% B2B. We are note promoting the use of B2C on SN. We're 100% focused on interactions between businesses only. Our primary markets are in Asia and Southeast Asia. Europe and the UK are dying a slow death, and the last straw was the Telegram event. So I am endorsing you to please at least on SN refer to @AGORA for basic B2C (retail). Thank you, https://www.globalmerchant.io originally posted at https://stacker.news/items/677390
@ eed76ece:afa98124
2024-09-08 21:13:37Seems like if you want to sell an item on SN using @AGORA makes logical sense. Perhaps if your a manufacturer, importer, exporter, stocking distributor, wholesaler etc. you should also consider using @Import_Export or both @AGORA and see if they help each other. Being totally upfront Import_Export is probably a better use case especially if you are running over 75% B2B. We are note promoting the use of B2C on SN. We're 100% focused on interactions between businesses only. Our primary markets are in Asia and Southeast Asia. Europe and the UK are dying a slow death, and the last straw was the Telegram event. So I am endorsing you to please at least on SN refer to @AGORA for basic B2C (retail). Thank you, https://www.globalmerchant.io originally posted at https://stacker.news/items/677390 @ e8b86bc1:3503c58f
2024-09-08 19:37:36Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> Freewallet is now charging inactivity fees, a sneaky method to take money from users who aren’t regularly using the app. Avoid this scam wallet! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
@ e8b86bc1:3503c58f
2024-09-08 19:37:36Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> Freewallet is now charging inactivity fees, a sneaky method to take money from users who aren’t regularly using the app. Avoid this scam wallet! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app) @ c11cf5f8:4928464d
2024-09-08 19:10:39Considering the "whatever" item in question is a random item, a unique piece --not something you produce or need to market-- which platform, website or which strategy you'll put in place to get the value of your item in sats, immediately, anonymously, via the Lightning Network? originally posted at https://stacker.news/items/677270
@ c11cf5f8:4928464d
2024-09-08 19:10:39Considering the "whatever" item in question is a random item, a unique piece --not something you produce or need to market-- which platform, website or which strategy you'll put in place to get the value of your item in sats, immediately, anonymously, via the Lightning Network? originally posted at https://stacker.news/items/677270 @ 6f170f27:711e26dd
2024-09-08 17:45:46 > Far too many people: "GDP is bad. I prefer [thing correlated at 0.9 with GDP]." Manufacturing:  Life expectancy:  Happiness:  Many other metrics & discussion in the source: https://x.com/cremieuxrecueil/status/1832588128084730334 originally posted at https://stacker.news/items/677211
@ 6f170f27:711e26dd
2024-09-08 17:45:46 > Far too many people: "GDP is bad. I prefer [thing correlated at 0.9 with GDP]." Manufacturing:  Life expectancy:  Happiness:  Many other metrics & discussion in the source: https://x.com/cremieuxrecueil/status/1832588128084730334 originally posted at https://stacker.news/items/677211 @ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。 --- ### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。 项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed 项目的教程很详细,具体去看项目教程。 ### telegram设置: - 需要有telegram账号 - 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。 - 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。 - 一定要添加创建的机器人到频道作为管理员才能使用。 ### cloudflare的设置 - 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。 - 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图: [](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv") - BASIC_USER 后台登陆名 - BASIC_PASS 后台密码 - AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。 ### 其他 - 成人内容屏蔽 - pico 使用api接口 去项目地址看 ### 最后 我搭建的地址: https://imgbed.lepidus.me
@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43> 由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。 --- ### 有人通过原项目的基础上分支另外项目,可以通过频道上传图片。 项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed 项目的教程很详细,具体去看项目教程。 ### telegram设置: - 需要有telegram账号 - 通过[@BotFather](https://t.me/BotFather "@BotFather")创建一个telegram机器人,并获取api key。 - 创建一个频道,获取频道id,通过转发一条消息到 [@VersaToolsBot](https://t.me/VersaToolsBot "@VersaToolsBot")机器人可以查看频道id。 - 一定要添加创建的机器人到频道作为管理员才能使用。 ### cloudflare的设置 - 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。 - 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图: [](https://imgbed.lepidus.me/file/AgACAgEAAyEGAASHShAaAAMFZt2erJ5-KyEOHIwfkCjN64RmA68AAtSsMRtrRvBGWZXC5Glh0M0BAAMCAAN3AAM2BA.png "kv") - BASIC_USER 后台登陆名 - BASIC_PASS 后台密码 - AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。 ### 其他 - 成人内容屏蔽 - pico 使用api接口 去项目地址看 ### 最后 我搭建的地址: https://imgbed.lepidus.me @ d52f4f20:98efcdfb
2024-09-08 12:05:31_original post 28/12/2010 .net_ Para você que se sente meio preso ao instalar o Ubuntu, pois ele já vem pronto para um usuário final, mas isso não me agrada parece que perco o espirito de liberdade. Mas o ponto forte Ubuntu são suas atualizações, então eu fui em busca de como fazer uma instalação customizada somente com os pacotes do Ubuntu. Depois de muita pesquisa e anos de experiência com linux desenvolvi o que chamo de instalação mínima **Alguns conceitos da minha instalação** – Não tem gerenciador de login gráfico. – Precisar habilitar o root, na unha e você usa isso. – Não tem menus, os aplicativos são chamados via tecla de atalho ou docks. – Não tem menu para desligar. – Não é um desktop, usa apenas um gerenciador de Janelas. – Aqui tudo é minimalista, não é bonito também não quer dizer que é feio, é apenas simples faz o necessário. – Não importa a versão do ubuntu, atual ou não essa técnica quase nunca mudará. **Seria bom/Pré-Requisitos** – Se você tem conceitos de particionamento. – Se você já instalou um Debian. – Se você sabe usar o vim. – Conexão com internet via placa de rede 10/100 (sim tem que ser assim). **Introdução** A idéia é usar a instalação mínima do Ubuntu (https://help.ubuntu.com/community/Installation/MinimalCD), onde é bem parecida com a NetInstall do Debian. Iremos baixar a imagem(12 ~ 13MB) do link acima e queimar em um cd rom e dar boot. Vamos usar o assistente de instalação, e não selecionaremos nenhum pacote na instalação, tudo sera instalado via linha de comando usando o apt. Pra quem já instalou usando o anaconda da RedHat não terá problemas, qualquer ser capaz de ler consegue instalar.  Esta é a primeira tela exibida após o boot, selecione o menu  Va seguindo o instalador conforme as telas, não quer que eu fique explicando tudo né?    Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.  Aqui você estara selecionando daonde pacotes serão baixados.  Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.    Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.    Após criar, FINISH!  Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.  O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.  senha é bom por né.  Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.   Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente.  Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar.  Grub é o gerenciador de boot, instale ele ai sem medo.  Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada. Logue-se com seu usuário, meu caso “lion” (que coisa gay figura 24 ainda).  **Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI. **Torna-se root** Isso é primordio no linux, sempre somos o ROOT, o Ubuntu tem essa filosofia para você não fazer cagada, mas na vida uma boa técnica de aprendizado é fazendo cagada, então vamos habilitar o root. Calma usaremos o root para tarefas como instalar novos software, mas a execução e configuração de nosso ambiente será com nosso usuário. ``` $ sudo passwd root ``` Pronto a partir de agora os comandos começados com # quer dizer que você tem que estar logado como root, e quando estiver $ você deve executar com seu usuário. Loge-se como root vamos usar bastante de um $su ou entre num novo tty como root. **Instalando o vim** ``` #apt-get install vim ``` (repare # você tem que estar logado como root) **Removendo o boot-splash** Amigos estamos falando de uma maquina limpa, o boot splash só come memória. Faça um backup antes e depois edite o arquivo “/boot/grub/grub.cfg” procure a palavra splash e apague somente ela e salve o arquivo. É necessário dar diretos de gravação e depois volte como somente leitura. **Removendo Mensagem de boas vindas MOTD** Logo após o login, é exibida uma mensagem de boas vindas enorme do ubuntu, eu não gosto dela, nem do debian eu gostava e eu a removia editando o script “/etc/init.d/boot-misc.sh” mas no ubuntu esse arquivo não existe. Depois de muito fuçar eu descobri que removendo os arquivos do diretorio “/etc/update-motd.d/” a mensagem some, pra mim basta, também removi o conteudo do arquivo /var/run/motd ; **UPDATE** Dica do comentário do Marcelo Godim Ele é gerenciado pelo pam_motd basta ir em /etc/pam.d nos arquivos “login” e “sshd” e comentar essas linhas abaixo: login: #session optional pam_motd.so sshd: #session optional pam_motd.so # [1] **Mudando mensagem da versão** Dica velha edite o arquivo “/etc/issue” coloque o que preferir. ——Se você não precisa de modo gráfico a instalação terminou aqui. Alterando o sources.list adicionando outros repositórios Edite o arquivo /etc/apt/sources.list e deixe assim, basicamente adicionados pacotes do site Medibuntu, se prefereir siga esses passos é melhor do que editar o arquivo. **Instalando o resto dos pacotes** #apt-get install xserver-xorg xinit alsa-base alsa-utils openbox obconf obmenu feh nitrogen tint2 k3b conky gmrun pcmanfm gtk-theme-switch ssh smbfs smbclient dosfstools setserial usbutils leafpad x11-apps openbox-themes terminator chromium-browser xcompmgr gcc g++ openjdk-6-jdk mysql-server mysql-query-browser gftp gcc-avr avrdude imagemagick gparted ntfs-3g file-roller zip unrar gpicview gtk2-engines gnome-icon-theme-gartoon vim unace rar unrar zip unzip p7zip-full p7zip-rar sharutils uudeview mpack lha arj cabextract file-roller pidgin pidgin-data pidgin-lastfm pidgin-guifications msn-pecan pidgin-musictracker pidgin-plugin-pack pidgin-themes mplayer vlc cairo-dock w32codecs audacious Vai dormir, seila vai baixar ai uns 500mb, você pode tirar ou por o que quiser ai isso é minha instalação. Como entrar no modo gráfico? Logue-se com seu usuário ``` $startx ``` O comando antigo, simples, que dei a primeira vez no meu conectiva 4.  Este é o resultado final, mas para isso vamos algumas dicas. Toda incialização dos aplicativos eu concentrei no .config/openbox/autostart.sh segue o meu ai ``` # Set desktop wallpaper nitrogen –restore & # Enable Eyecandy – off by default xcompmgr -cCfF -r7 -o.65 -l-10 -t-8 & # Launch network manager applet (sleep 4s && nm-applet) & # Launch clipboard manager #(sleep 1s && parcellite) & # Uncomment to enable system updates at boot #(sleep 180s && system-update) & cairo-dock & # Launch Conky #conky -q & # Launch panel tint2 & ``` **Configurando teclas de atalho**, edite o arquivo .config/openbox/rc.xml, vá até a seção keybinds as minhas são essas abaixo: ``` <keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-1″><action name=”Execute”> <execute>xcompmgr -cCfF -r7 -o.65 -l-10 -t-8</execute></action></keybind><keybind key=”W-2″><action name=”Execute”> <execute>pkill xcompmgr</execute></action></keybind><keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-e”><action name=”Execute”> <execute>pcmanfm</execute></action></keybind><keybind key=”W-g”><action name=”Execute”> <startupnotify> <enabled>true</enabled> <name>transset</name> </startupnotify> <command>transset .50</command></action></keybind><keybind key=”W-h”><action name=”Execute”> <startupnotify><enabled>true</enabled><name>transset 1</name></startupnotify><command>transset 1</command></action></keybind><keybind key=”W-l”><action name=”Execute”><startupnotify><enabled>true</enabled><name>Lock screen</name></startupnotify><command>gnome-screensaver-command -l</command></action></keybind><keybind key=”W-t”><action name=”Execute”><execute>terminator</execute></action></keybind><keybind key=”W-r”> <action name=”Execute”> <execute>gmrun</execute> </action></keybind> ``` Pesquise como instalar temas GTK, configurar o TINT2 (desk bar), Cairo Dock, também tem muitas configurações de openbox na internet. Esse tutorial vem de anos de convivio com linux, é duro passar tudo a limpo aqui, uma dica e testar o Linux Crunch-Bang aprendi muitas customizações com ele. #blog #tech
@ d52f4f20:98efcdfb
2024-09-08 12:05:31_original post 28/12/2010 .net_ Para você que se sente meio preso ao instalar o Ubuntu, pois ele já vem pronto para um usuário final, mas isso não me agrada parece que perco o espirito de liberdade. Mas o ponto forte Ubuntu são suas atualizações, então eu fui em busca de como fazer uma instalação customizada somente com os pacotes do Ubuntu. Depois de muita pesquisa e anos de experiência com linux desenvolvi o que chamo de instalação mínima **Alguns conceitos da minha instalação** – Não tem gerenciador de login gráfico. – Precisar habilitar o root, na unha e você usa isso. – Não tem menus, os aplicativos são chamados via tecla de atalho ou docks. – Não tem menu para desligar. – Não é um desktop, usa apenas um gerenciador de Janelas. – Aqui tudo é minimalista, não é bonito também não quer dizer que é feio, é apenas simples faz o necessário. – Não importa a versão do ubuntu, atual ou não essa técnica quase nunca mudará. **Seria bom/Pré-Requisitos** – Se você tem conceitos de particionamento. – Se você já instalou um Debian. – Se você sabe usar o vim. – Conexão com internet via placa de rede 10/100 (sim tem que ser assim). **Introdução** A idéia é usar a instalação mínima do Ubuntu (https://help.ubuntu.com/community/Installation/MinimalCD), onde é bem parecida com a NetInstall do Debian. Iremos baixar a imagem(12 ~ 13MB) do link acima e queimar em um cd rom e dar boot. Vamos usar o assistente de instalação, e não selecionaremos nenhum pacote na instalação, tudo sera instalado via linha de comando usando o apt. Pra quem já instalou usando o anaconda da RedHat não terá problemas, qualquer ser capaz de ler consegue instalar.  Esta é a primeira tela exibida após o boot, selecione o menu  Va seguindo o instalador conforme as telas, não quer que eu fique explicando tudo né?    Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.  Aqui você estara selecionando daonde pacotes serão baixados.  Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.    Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.    Após criar, FINISH!  Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.  O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.  senha é bom por né.  Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.   Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente.  Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar.  Grub é o gerenciador de boot, instale ele ai sem medo.  Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada. Logue-se com seu usuário, meu caso “lion” (que coisa gay figura 24 ainda).  **Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI. **Torna-se root** Isso é primordio no linux, sempre somos o ROOT, o Ubuntu tem essa filosofia para você não fazer cagada, mas na vida uma boa técnica de aprendizado é fazendo cagada, então vamos habilitar o root. Calma usaremos o root para tarefas como instalar novos software, mas a execução e configuração de nosso ambiente será com nosso usuário. ``` $ sudo passwd root ``` Pronto a partir de agora os comandos começados com # quer dizer que você tem que estar logado como root, e quando estiver $ você deve executar com seu usuário. Loge-se como root vamos usar bastante de um $su ou entre num novo tty como root. **Instalando o vim** ``` #apt-get install vim ``` (repare # você tem que estar logado como root) **Removendo o boot-splash** Amigos estamos falando de uma maquina limpa, o boot splash só come memória. Faça um backup antes e depois edite o arquivo “/boot/grub/grub.cfg” procure a palavra splash e apague somente ela e salve o arquivo. É necessário dar diretos de gravação e depois volte como somente leitura. **Removendo Mensagem de boas vindas MOTD** Logo após o login, é exibida uma mensagem de boas vindas enorme do ubuntu, eu não gosto dela, nem do debian eu gostava e eu a removia editando o script “/etc/init.d/boot-misc.sh” mas no ubuntu esse arquivo não existe. Depois de muito fuçar eu descobri que removendo os arquivos do diretorio “/etc/update-motd.d/” a mensagem some, pra mim basta, também removi o conteudo do arquivo /var/run/motd ; **UPDATE** Dica do comentário do Marcelo Godim Ele é gerenciado pelo pam_motd basta ir em /etc/pam.d nos arquivos “login” e “sshd” e comentar essas linhas abaixo: login: #session optional pam_motd.so sshd: #session optional pam_motd.so # [1] **Mudando mensagem da versão** Dica velha edite o arquivo “/etc/issue” coloque o que preferir. ——Se você não precisa de modo gráfico a instalação terminou aqui. Alterando o sources.list adicionando outros repositórios Edite o arquivo /etc/apt/sources.list e deixe assim, basicamente adicionados pacotes do site Medibuntu, se prefereir siga esses passos é melhor do que editar o arquivo. **Instalando o resto dos pacotes** #apt-get install xserver-xorg xinit alsa-base alsa-utils openbox obconf obmenu feh nitrogen tint2 k3b conky gmrun pcmanfm gtk-theme-switch ssh smbfs smbclient dosfstools setserial usbutils leafpad x11-apps openbox-themes terminator chromium-browser xcompmgr gcc g++ openjdk-6-jdk mysql-server mysql-query-browser gftp gcc-avr avrdude imagemagick gparted ntfs-3g file-roller zip unrar gpicview gtk2-engines gnome-icon-theme-gartoon vim unace rar unrar zip unzip p7zip-full p7zip-rar sharutils uudeview mpack lha arj cabextract file-roller pidgin pidgin-data pidgin-lastfm pidgin-guifications msn-pecan pidgin-musictracker pidgin-plugin-pack pidgin-themes mplayer vlc cairo-dock w32codecs audacious Vai dormir, seila vai baixar ai uns 500mb, você pode tirar ou por o que quiser ai isso é minha instalação. Como entrar no modo gráfico? Logue-se com seu usuário ``` $startx ``` O comando antigo, simples, que dei a primeira vez no meu conectiva 4.  Este é o resultado final, mas para isso vamos algumas dicas. Toda incialização dos aplicativos eu concentrei no .config/openbox/autostart.sh segue o meu ai ``` # Set desktop wallpaper nitrogen –restore & # Enable Eyecandy – off by default xcompmgr -cCfF -r7 -o.65 -l-10 -t-8 & # Launch network manager applet (sleep 4s && nm-applet) & # Launch clipboard manager #(sleep 1s && parcellite) & # Uncomment to enable system updates at boot #(sleep 180s && system-update) & cairo-dock & # Launch Conky #conky -q & # Launch panel tint2 & ``` **Configurando teclas de atalho**, edite o arquivo .config/openbox/rc.xml, vá até a seção keybinds as minhas são essas abaixo: ``` <keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-1″><action name=”Execute”> <execute>xcompmgr -cCfF -r7 -o.65 -l-10 -t-8</execute></action></keybind><keybind key=”W-2″><action name=”Execute”> <execute>pkill xcompmgr</execute></action></keybind><keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-e”><action name=”Execute”> <execute>pcmanfm</execute></action></keybind><keybind key=”W-g”><action name=”Execute”> <startupnotify> <enabled>true</enabled> <name>transset</name> </startupnotify> <command>transset .50</command></action></keybind><keybind key=”W-h”><action name=”Execute”> <startupnotify><enabled>true</enabled><name>transset 1</name></startupnotify><command>transset 1</command></action></keybind><keybind key=”W-l”><action name=”Execute”><startupnotify><enabled>true</enabled><name>Lock screen</name></startupnotify><command>gnome-screensaver-command -l</command></action></keybind><keybind key=”W-t”><action name=”Execute”><execute>terminator</execute></action></keybind><keybind key=”W-r”> <action name=”Execute”> <execute>gmrun</execute> </action></keybind> ``` Pesquise como instalar temas GTK, configurar o TINT2 (desk bar), Cairo Dock, também tem muitas configurações de openbox na internet. Esse tutorial vem de anos de convivio com linux, é duro passar tudo a limpo aqui, uma dica e testar o Linux Crunch-Bang aprendi muitas customizações com ele. #blog #tech @ c11cf5f8:4928464d
2024-09-08 09:08:04 - - - Here we are again with our [The Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times), trying to give you a hit of what you missed this past month in the ~AGORA territory. - - - ### Top-Performing Ads Drumroll please 🥁 ... for the most engaging ones: * `01` [[SELL] 1 Million Products, Travel Agency, Concierge and Cars - ShopinBit.com](https://stacker.news/items/673616/r/AG) by @shopinbit * `02` [[SELL] Satoffee⚡️☕️ Cafeteras automáticas que aceptan Bitcoin Lightning 🇪🇸 🌐](https://stacker.news/items/675680/r/AG) by @VEINTIUNO * `03` [[⚖️SELL] Hand-Made Flecktarn Pouch(es)](https://stacker.news/items/650741/r/AG) by Fabs * `04` [[OFFER] Proton Wallet - 3 invites left](https://stacker.news/items/656656/r/AG) by @npub1q67p49masrcjf__d7qaq6mwh0q * `05` [[SELL] Bitcoin Accepted Here – Unisex organic cotton Black T-shirt](https://stacker.news/items/666650/r/AG) by @VEINTIUNO * `06` [[FOR SALE] Playstation 2 (PS2) Games - Excellent Condition - Pay In SATS!!!](https://stacker.news/items/647968/r/AG) by @watchmancbiz * `07` [[OFFER] Happy Bitcoin Infinity Day](https://stacker.news/items/657338/r/AG) by @thebullishbitcoiner - - - ##### In case you missed Here some interesting post opening conversation and free speech: This edition winner look's @proofoftaste, with his request for help finding a way to get a local product delivered to his country. The challenge was that the producer, required an ID number on checkout! Pretty unusual... or it will be soon the norm? Thanks a lot for @supratic for being so active in the territory and sharing so many topics and articles about commerce and law, basically giving us a hit on how the world is currently ruled, pretty fascinating! * `01` [Can someone in Italy help me get my favourite sauce to Germany?](https://stacker.news/items/644918/r/AG) by @proofoftaste * `02` [The History of Banking – Ernest Rauthschild](https://stacker.news/items/643333/r/AG) by @supratic * `03` [10 Hidden Rules of Commerce](https://stacker.news/items/654215/r/AG) by @supratic * `04` [How to Start Your Own Micronation](https://stacker.news/items/647294/r/AG) by @supratic * `05` [Understanding the One People's Public Trust: A Beginner's Guide to the OPPT(https://stacker.news/items/641554/r/AG) by @supratic * `06` [A Bank Whistleblower called me...](https://stacker.news/items/646118/r/AG) by @supratic * `07` [One Stupid Fu*K 🥒 Contract Killer Course 2.0 - Brandon Joe Williams](https://stacker.news/items/675943/r/AG) by @02a0eb55b5 - - - ##### 🏷️ Spending Sunday is back! https://stacker.news/items/653241/r/AG Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! - - - ##### Just a reminder for you all To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting. - - - ### Create your Ads now!  This territory aims to connect stackers and curious buyers online and IRL for exclusive P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it! Let's start something new? Hit one of the links below to free your mind: * [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation, * [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or, * if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)! * [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners * [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats * [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item * [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else * [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift! * [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to - - - Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we'll help you publish a personalized post. originally posted at https://stacker.news/items/676777
@ c11cf5f8:4928464d
2024-09-08 09:08:04 - - - Here we are again with our [The Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times), trying to give you a hit of what you missed this past month in the ~AGORA territory. - - - ### Top-Performing Ads Drumroll please 🥁 ... for the most engaging ones: * `01` [[SELL] 1 Million Products, Travel Agency, Concierge and Cars - ShopinBit.com](https://stacker.news/items/673616/r/AG) by @shopinbit * `02` [[SELL] Satoffee⚡️☕️ Cafeteras automáticas que aceptan Bitcoin Lightning 🇪🇸 🌐](https://stacker.news/items/675680/r/AG) by @VEINTIUNO * `03` [[⚖️SELL] Hand-Made Flecktarn Pouch(es)](https://stacker.news/items/650741/r/AG) by Fabs * `04` [[OFFER] Proton Wallet - 3 invites left](https://stacker.news/items/656656/r/AG) by @npub1q67p49masrcjf__d7qaq6mwh0q * `05` [[SELL] Bitcoin Accepted Here – Unisex organic cotton Black T-shirt](https://stacker.news/items/666650/r/AG) by @VEINTIUNO * `06` [[FOR SALE] Playstation 2 (PS2) Games - Excellent Condition - Pay In SATS!!!](https://stacker.news/items/647968/r/AG) by @watchmancbiz * `07` [[OFFER] Happy Bitcoin Infinity Day](https://stacker.news/items/657338/r/AG) by @thebullishbitcoiner - - - ##### In case you missed Here some interesting post opening conversation and free speech: This edition winner look's @proofoftaste, with his request for help finding a way to get a local product delivered to his country. The challenge was that the producer, required an ID number on checkout! Pretty unusual... or it will be soon the norm? Thanks a lot for @supratic for being so active in the territory and sharing so many topics and articles about commerce and law, basically giving us a hit on how the world is currently ruled, pretty fascinating! * `01` [Can someone in Italy help me get my favourite sauce to Germany?](https://stacker.news/items/644918/r/AG) by @proofoftaste * `02` [The History of Banking – Ernest Rauthschild](https://stacker.news/items/643333/r/AG) by @supratic * `03` [10 Hidden Rules of Commerce](https://stacker.news/items/654215/r/AG) by @supratic * `04` [How to Start Your Own Micronation](https://stacker.news/items/647294/r/AG) by @supratic * `05` [Understanding the One People's Public Trust: A Beginner's Guide to the OPPT(https://stacker.news/items/641554/r/AG) by @supratic * `06` [A Bank Whistleblower called me...](https://stacker.news/items/646118/r/AG) by @supratic * `07` [One Stupid Fu*K 🥒 Contract Killer Course 2.0 - Brandon Joe Williams](https://stacker.news/items/675943/r/AG) by @02a0eb55b5 - - - ##### 🏷️ Spending Sunday is back! https://stacker.news/items/653241/r/AG Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! - - - ##### Just a reminder for you all To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting. - - - ### Create your Ads now!  This territory aims to connect stackers and curious buyers online and IRL for exclusive P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it! Let's start something new? Hit one of the links below to free your mind: * [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation, * [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or, * if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)! * [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners * [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats * [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item * [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else * [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift! * [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to - - - Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we'll help you publish a personalized post. originally posted at https://stacker.news/items/676777 @ c11cf5f8:4928464d
2024-09-08 08:35:16Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/668607/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/676757
@ c11cf5f8:4928464d
2024-09-08 08:35:16Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/668607/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/676757 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further. #### ***Consider the Most Fundamental Questions*** 1. **The Origin of the Universe** 2. **The Origin of Life on Earth** #### ***The Origin of the Universe*** You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding. The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding. Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**. #### ***The Origin of Life on Earth*** The origin of life is even more complex. Life requires three essential components: - **Proteins** for basic functioning - **RNA** for storing and replicating genes - **Lipids** (cell walls) to create separation from the environment Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**. #### ***The Question of Certainty*** If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early. #### ***Reclaiming Control of Science and Education*** The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend: - **“A Brief History of Time”** by **Stephen Hawking** for physics - **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03***“The more you learn about something, the more you realize you know nothing.”*** This saying resonates deeply with me. The truth is, **no one really has all the big answers**. Many in the scientific community seem to pretend they do. Let’s explore this further. #### ***Consider the Most Fundamental Questions*** 1. **The Origin of the Universe** 2. **The Origin of Life on Earth** #### ***The Origin of the Universe*** You might think we have a solid answer: **the Big Bang**. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to **Sir Roger Penrose** for a deeper understanding. The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: **the endless expansion and contraction of the universe**. This idea doesn’t contradict our current understanding. Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet **neither can be definitively proven** over the other. This highlights the **limitations of our current understanding**. #### ***The Origin of Life on Earth*** The origin of life is even more complex. Life requires three essential components: - **Proteins** for basic functioning - **RNA** for storing and replicating genes - **Lipids** (cell walls) to create separation from the environment Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from **outside sources**. Some scholars even question the entire **random mutation model**. #### ***The Question of Certainty*** If scientists don’t know the answers, **why do they pretend they do?** In my humble opinion, **It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative,** Interestingly, I’m not alone in believing they closed the books too early. #### ***Reclaiming Control of Science and Education*** The best way to reclaim control of science and education is to **learn**. If you’re looking for a starting point, I highly recommend: - **“A Brief History of Time”** by **Stephen Hawking** for physics - **“Sapiens”** or **“The Selfish Gene”** for evolutionary biology All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner. @ 6bae33c8:607272e8
2024-09-07 22:09:27With all five of my football drafts/auctions in the books, here's the portfolio I've amassed for 2024, not including the RotoWire Dynasty League: **Links**: [BCL1](https://www.realmansports.com/p/beat-chris-liss-1-344), [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e?utm_source=publication-search), [BCL3](https://www.realmansports.com/p/beat-chris-liss-3-062), [Steak League](https://www.realmansports.com/p/steak-league-879), [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7)  **Players in whom I have the most shares:** **QB**: Justin Fields (4), CJ Stroud (2), Anthony Richardson (2), Tua Tagovailoa (2) **RB**: Jonathan Brooks (2), Brian Robinson (2), Jerome Ford (2), Jordan Mason (2), JK Dobbins (2), Khalil Herbert (2), Dalvin Cook (2) **WR:** Stefon Diggs (5), Ja’Marr Chase (3), Rashid Shaheed (3), Ladd McConkey (2), Roman Wilson (2) **TE:** Jonnu Smith (3) **K**: Younghoe Koo (3), Harrison Butker (2) **D:** Giants (4) **Notes:** Obviously, I thought Stefon Diggs was mispriced, though I only had to pay close to what I thought he was worth in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7) — in the rest of the leagues he fell to me at ADP or below. He and Ja’Marr Chase are massively important to me this year, and to a lesser extent CJ Stroud. I also have Justin Fields and the Giants defense everywhere, but both were essentially free, and I could swap them out without issue. I also have a lot of Younghoe Koo, but he too could obviously be swapped out. I like having a couple key players to build around rather than five disparate teams. Of course if Diggs gets hurt or turns out to be washed up, it’ll be rough, but in some ways it’s like the old days where you had only one team, and you had to live and die with it. **Prominent Players I Don't Have (bold is by choice):** Bijan Robinson, Tyreek Hill, Breece Hall, Amon-Ra St. Brown, Justin Jefferson, Garrett Wilson, A.J. Brown, Jonathan Taylor, Puka Nacua, **Davante Adams**, **Saquon Barkley**, Chris Olave, Rashee Rice, **Kyren Williams**, Travis Etienne, Cooper Kupp, Isiah Pacheco, **Michael Pittman**, **Nico Collins**, **DK Metcalf**, **Mike Evans**, **Deebo Samuel, Josh Allen,** DJ Moore, Brandon Aiyuk, Derrick Henry, Zay Flowers, **James Cook**, Terry McLaurin, Kenneth Walker, **Xavier Worthy**, Amari Cooper, Josh Jacobs, Trey McBride, **George Pickens**, Lamar Jackson, **Christian Kirk**, Tee Higgins, **Calvin Ridley**, **Rachaad White,** Jayden Reed, Diontae Johnson, **Travis Kelce**, **Joe Mixon**, **Alvin Kamara**, Christian Watson, **Jalen Hurts**, Aaron Jones, Patrick Mahomes, David Montgomery, **Zamir White, Keenan Allen,** Kyle Pitts, **D’Andre Swift**, George Kittle **Past Portfolios:** [**2023**](https://www.realmansports.com/p/my-portfolio-ef6?utm_source=publication-search)**, [2022](https://www.realmansports.com/p/my-portfolio?utm_source=%2Fsearch%2Fmy%2520portfolio&utm_medium=reader2), [2021](https://www.rotowire.com/football/article/nfl-chris-lissrsquo-portfolio-58839), [2020](https://www.rotowire.com/football/article.php?id=52704)[, 2019](https://www.rotowire.com/blog/post.php?id=29428), [2018](https://www.rotowire.com/blog/post.php?id=26158), [2017](https://www.rotowire.com/blog/post.php?id=23069), [2016](https://www.rotowire.com/blog/post.php?id=13592), [2015](https://www.rotowire.com/blog/post.php?id=8991)**
@ 6bae33c8:607272e8
2024-09-07 22:09:27With all five of my football drafts/auctions in the books, here's the portfolio I've amassed for 2024, not including the RotoWire Dynasty League: **Links**: [BCL1](https://www.realmansports.com/p/beat-chris-liss-1-344), [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e?utm_source=publication-search), [BCL3](https://www.realmansports.com/p/beat-chris-liss-3-062), [Steak League](https://www.realmansports.com/p/steak-league-879), [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7)  **Players in whom I have the most shares:** **QB**: Justin Fields (4), CJ Stroud (2), Anthony Richardson (2), Tua Tagovailoa (2) **RB**: Jonathan Brooks (2), Brian Robinson (2), Jerome Ford (2), Jordan Mason (2), JK Dobbins (2), Khalil Herbert (2), Dalvin Cook (2) **WR:** Stefon Diggs (5), Ja’Marr Chase (3), Rashid Shaheed (3), Ladd McConkey (2), Roman Wilson (2) **TE:** Jonnu Smith (3) **K**: Younghoe Koo (3), Harrison Butker (2) **D:** Giants (4) **Notes:** Obviously, I thought Stefon Diggs was mispriced, though I only had to pay close to what I thought he was worth in the [Primetime](https://www.realmansports.com/p/nffc-primetime-fa7) — in the rest of the leagues he fell to me at ADP or below. He and Ja’Marr Chase are massively important to me this year, and to a lesser extent CJ Stroud. I also have Justin Fields and the Giants defense everywhere, but both were essentially free, and I could swap them out without issue. I also have a lot of Younghoe Koo, but he too could obviously be swapped out. I like having a couple key players to build around rather than five disparate teams. Of course if Diggs gets hurt or turns out to be washed up, it’ll be rough, but in some ways it’s like the old days where you had only one team, and you had to live and die with it. **Prominent Players I Don't Have (bold is by choice):** Bijan Robinson, Tyreek Hill, Breece Hall, Amon-Ra St. Brown, Justin Jefferson, Garrett Wilson, A.J. Brown, Jonathan Taylor, Puka Nacua, **Davante Adams**, **Saquon Barkley**, Chris Olave, Rashee Rice, **Kyren Williams**, Travis Etienne, Cooper Kupp, Isiah Pacheco, **Michael Pittman**, **Nico Collins**, **DK Metcalf**, **Mike Evans**, **Deebo Samuel, Josh Allen,** DJ Moore, Brandon Aiyuk, Derrick Henry, Zay Flowers, **James Cook**, Terry McLaurin, Kenneth Walker, **Xavier Worthy**, Amari Cooper, Josh Jacobs, Trey McBride, **George Pickens**, Lamar Jackson, **Christian Kirk**, Tee Higgins, **Calvin Ridley**, **Rachaad White,** Jayden Reed, Diontae Johnson, **Travis Kelce**, **Joe Mixon**, **Alvin Kamara**, Christian Watson, **Jalen Hurts**, Aaron Jones, Patrick Mahomes, David Montgomery, **Zamir White, Keenan Allen,** Kyle Pitts, **D’Andre Swift**, George Kittle **Past Portfolios:** [**2023**](https://www.realmansports.com/p/my-portfolio-ef6?utm_source=publication-search)**, [2022](https://www.realmansports.com/p/my-portfolio?utm_source=%2Fsearch%2Fmy%2520portfolio&utm_medium=reader2), [2021](https://www.rotowire.com/football/article/nfl-chris-lissrsquo-portfolio-58839), [2020](https://www.rotowire.com/football/article.php?id=52704)[, 2019](https://www.rotowire.com/blog/post.php?id=29428), [2018](https://www.rotowire.com/blog/post.php?id=26158), [2017](https://www.rotowire.com/blog/post.php?id=23069), [2016](https://www.rotowire.com/blog/post.php?id=13592), [2015](https://www.rotowire.com/blog/post.php?id=8991)** @ 6bae33c8:607272e8
2024-09-07 22:07:54I submitted my five picks for the Circa Millions contest today. I think it’s $6M in total prizes. I want to put a disclaimer here: I’m putting these behind a paywall not because you should pay for these picks — never pay for anyone’s picks. If the picks were that good, whoever was making them could just print money and wouldn’t need yours. If you want to subscribe in earnest, do so because you’re interested to see who I chose and read the reasoning, not because you (erroneously) think it’s the way to get some easy winners. Or if you want to support my substack generally because you think it adds value to you. Those are fine reasons to subscribe, but doing so because you think copying my picks will make you money is dumb. Okay that out of the way, here are the picks:  **Dolphins -3.5 vs Jaguars** — I like taking the Dolphins in early September, it’s hot and humid there, difficult for opposing teams to adjust to it. It’s like Lambeau Field in December, only in reverse. Moreover, the Dolphins are a veteran offense that’s played together for years, while the Jaguars are working in two new receivers. **Falcons -3.5 vs Steelers** — Justin Fields is probably an upgrade over Russell Wilson at this point, but he’s haphazard and will have to learn the players and offense on the fly. The Falcons have a new QB too, but he’s an old pro, has better weapons and a better offensive line. **Giants +1 vs Vikings** — The Giants have three Pro-Bowl level pass rushers, finally have a playmaking receiver and upgraded their offensive line this offseason. And yet despite facing Sam Darnold at home, they’re still getting a point. **Cardinals +6.5 at Bills** — Kyler Murray is now another year removed from knee surgery, should be his usual spry self, and Marvin Harrison adds another dimension to the offense it sorely needed. The Bills will move the ball, but I think Arizona will hang with them and keep it close enough. **Browns -2 vs Cowboys** — The Browns should be able to run the ball and keep the Dallas pass rush off Deshaun Watson, while Dallas’ offensive line has slipped a bit, and the Browns defense was No. 1 against the pass last year. Dak Prescott also has big home/road splits.
@ 6bae33c8:607272e8
2024-09-07 22:07:54I submitted my five picks for the Circa Millions contest today. I think it’s $6M in total prizes. I want to put a disclaimer here: I’m putting these behind a paywall not because you should pay for these picks — never pay for anyone’s picks. If the picks were that good, whoever was making them could just print money and wouldn’t need yours. If you want to subscribe in earnest, do so because you’re interested to see who I chose and read the reasoning, not because you (erroneously) think it’s the way to get some easy winners. Or if you want to support my substack generally because you think it adds value to you. Those are fine reasons to subscribe, but doing so because you think copying my picks will make you money is dumb. Okay that out of the way, here are the picks:  **Dolphins -3.5 vs Jaguars** — I like taking the Dolphins in early September, it’s hot and humid there, difficult for opposing teams to adjust to it. It’s like Lambeau Field in December, only in reverse. Moreover, the Dolphins are a veteran offense that’s played together for years, while the Jaguars are working in two new receivers. **Falcons -3.5 vs Steelers** — Justin Fields is probably an upgrade over Russell Wilson at this point, but he’s haphazard and will have to learn the players and offense on the fly. The Falcons have a new QB too, but he’s an old pro, has better weapons and a better offensive line. **Giants +1 vs Vikings** — The Giants have three Pro-Bowl level pass rushers, finally have a playmaking receiver and upgraded their offensive line this offseason. And yet despite facing Sam Darnold at home, they’re still getting a point. **Cardinals +6.5 at Bills** — Kyler Murray is now another year removed from knee surgery, should be his usual spry self, and Marvin Harrison adds another dimension to the offense it sorely needed. The Bills will move the ball, but I think Arizona will hang with them and keep it close enough. **Browns -2 vs Cowboys** — The Browns should be able to run the ball and keep the Dallas pass rush off Deshaun Watson, while Dallas’ offensive line has slipped a bit, and the Browns defense was No. 1 against the pass last year. Dak Prescott also has big home/road splits. @ 6bae33c8:607272e8
2024-09-07 22:05:26This is my main event for fantasy football, the $1700 buy-in NFFC Primetime. I wound up picking 11th (I had the fourth to last choice), and while in retrospect maybe I should have opted for ninth or 10th, I wanted to get a share of Jahmyr Gibbs which is why I chose that slot. I also ran through some scenarios beforehand — what if Ja’Marr Chase (still not signed) falls — do I take him in a fourth league? But as you’ll see, the first round was complete chalk, and no windfalls whatsoever fell to me. But I had a plan for that, and I more or less executed it. Without further ado, here are the results: <img src="https://blossom.primal.net/4bbf1f4369c4eea958b04922892f9c485dcbce7d68f011e55c11997f05ae6006.png"> **1.11 Jahmyr Gibbs** — This was the most likely scenario, and it took me about two seconds to make the pick once the top three backs and seven receivers were gone. If Gibbs (who is not on the injury report) hadn’t had a hamstring injury in camp, I’d have him close to the middle of the round rather than the end. Let’s hope he doesn’t aggravate it. **2.2 Marvin Harrison** — I would have taken either Puka Nacua or Jonathan Taylor, but no breaks here either. Both went at the turn, and I knew I was taking a receiver. Starting RB-WR is the easiest build, in my opinion, but Harrison was kind of an agnostic pick. I had considered Rashee Rice, but as Alan Seslowsky pointed out, while his suspension for hit and run might not kick in until after the season (when the legal process has run its course), that could be pushed up if his lawyers negotiate a plea. Between that an the presence of so many options for the Chiefs, I went Harrison over him narrowly. But it was a close call. **3.2 Stefon Diggs** — I missed Malik Nabers, Cooper Kupp, (maybe Jaylen Waddle) and De’Von Achane who went with the four consecutive picks ahead of me, so it was Diggs, Nico Collins (his teammate who has a higher ADP), DeVonta Smith or (maybe) Derrick Henry. I went Diggs who I had personally ranked the highest, wouldn’t make it back to me, who I have in every league and was part of my “unfriendly” draft plan, i.e., the Plan B I had talked about. **4.11 Tank Dell** — He’s too small to hold up, but whenever he played he produced, and he gives me a bit of a Diggs hedge. I also wanted Trey McBride on this turn (as I had Marvin Harrison and could have drafted Kyler Murray — who I love this year — later), but he went on the turn. I thought about taking McBride first, but they were side by side in ADP, and my Plan B was to stack Texans, so I went Dell and took a chance. **5.2 Chris Godwin** — This was the one pick I kind of regret (though it’s debatable.) I like Jayden Reed a lot, but he was half a round lower per ADP, and there was *some* chance I could get him on the way back. I had Godwin everywhere last year, and he was a disappointment, but apparently he’s healthier now and is going back to the slot full time where he excels. **6.11 Jaxon Smith-Njigba** — The other pivot off Godwin was JSN, and sure enough he made it back all the way, though he starts off as my first bench player. That’s okay though — you need at least five viable receivers throughout the year, and I didn’t have to take C.J. Stroud because if the guy at the turn took him, I would just pivot to the Kyler Murray/Harrison stack. **7.2 C.J. Stroud** — He was there, and I executed Plan B. Yes, I have a weak first three rounds by ADP, but I have Gibbs, Harrison and a big piece of the Texans passing game which I think will lead the NFL in yardage. **8.11 Jaylen Warren** — I needed a second back, and Warren is one. He’s a good pass catcher and should see half the snaps in Pittsburgh. **9.2 Brian Robinson** — I like Robinson as a player, he’s the undisputed early-down option on what should be a better offense. (Think Ricky Pearsall, but at RB.) Too soon? Austin Ekeler will obviously see the passing-down work unless he proves totally washed up. The Robinson pick cost me David Njoku and Brock Bowers unfortunately, which was a gamble I knew I was making. **10.11 Jordan Mason** — At 29 and playing into the Super Bowl, Christian McCalfinjury was already a risk, and that he’s “expected” to play Monday night rather than 100 percent fine is worrying. Mason could be a league winner if McCaffrey goes down. **11.2 J.K. Dobbins** — The Mason pick cost me Jaleel McLaughlin, so I pivoted to Dobbins who still has a high ceiling if he can ever stay healthy. **12.11 Dallas Goedert** — Tight ends had flown off the board, but I was happy to get Goedert who has been valuable on a per-game basis the last couple years and is still just 29 which is late prime for the position. **13.2 Dalton Schultz** — Why not stack it even harder? The Texans could throw for 5,000-plus yards, and I have three of the four top targets and the QB. **14.11 Andrei Iosivas** — He’s gotten a lot of buzz in camp, seems like the No. 3 receiver right now, Tee Higgins is hurt and Ja’Marr Chase is still unsigned. **15.2 Cam Akers** — The Iosivas pick cost me Jalen McMillan who would have served as Godwin insurance, but Akers could easily take an aging Joe Mixon’s job. Maybe it’s too much Houston, but if it’s a top-three offense, I’m good with it. **16.11 Justin Fields** — The backup QBs had flown off the board, and Fields has too much upside to pass up. Plus he might even start Week 1 with Russell Wilson already hurt, and if he plays well, he might never look back. **17.2 Harrison Butker** — It’s either the based af kicker or a Younghoe for me. Plus he locked in a decent Week 1. **18.11 Dalvin Cook** — He had only 67 carries last year for a bad Jets offense. What if he isn’t as washed up as we think? He could easily win that job over Zeke Elliott and Rico Dowdle. **19.2 Jonnu Smith** — TE is my weakest position, so I took another upside gamble. What if he’s the Dolphins third target? **20.11 Giants Defense** — I think I took them in all four NFFC leagues. They get the Darnold Vikings at home and then Jayden Daniels in his second career start. And they have three Pro Bowl level pass rushers. **Roster By Position** **QB** CJ Stroud **RB** Jahmyr Gibbs/Jaylen Warren **WR** Marvin Harrison/Stefon Diggs/Tank Dell **TE** Dallas Goedert **FLEX** Chris Godwin **K** Harrison Butker **D** Giants **B** Jaxon Smith-Njigba/Brian Robinson/Jordan Mason/JK Dobbins/Dalton Schultz/Andrei Iosivas/Cam Akers/Justin Fields/Dalvin Cook/Jonnu Smith
@ 6bae33c8:607272e8
2024-09-07 22:05:26This is my main event for fantasy football, the $1700 buy-in NFFC Primetime. I wound up picking 11th (I had the fourth to last choice), and while in retrospect maybe I should have opted for ninth or 10th, I wanted to get a share of Jahmyr Gibbs which is why I chose that slot. I also ran through some scenarios beforehand — what if Ja’Marr Chase (still not signed) falls — do I take him in a fourth league? But as you’ll see, the first round was complete chalk, and no windfalls whatsoever fell to me. But I had a plan for that, and I more or less executed it. Without further ado, here are the results: <img src="https://blossom.primal.net/4bbf1f4369c4eea958b04922892f9c485dcbce7d68f011e55c11997f05ae6006.png"> **1.11 Jahmyr Gibbs** — This was the most likely scenario, and it took me about two seconds to make the pick once the top three backs and seven receivers were gone. If Gibbs (who is not on the injury report) hadn’t had a hamstring injury in camp, I’d have him close to the middle of the round rather than the end. Let’s hope he doesn’t aggravate it. **2.2 Marvin Harrison** — I would have taken either Puka Nacua or Jonathan Taylor, but no breaks here either. Both went at the turn, and I knew I was taking a receiver. Starting RB-WR is the easiest build, in my opinion, but Harrison was kind of an agnostic pick. I had considered Rashee Rice, but as Alan Seslowsky pointed out, while his suspension for hit and run might not kick in until after the season (when the legal process has run its course), that could be pushed up if his lawyers negotiate a plea. Between that an the presence of so many options for the Chiefs, I went Harrison over him narrowly. But it was a close call. **3.2 Stefon Diggs** — I missed Malik Nabers, Cooper Kupp, (maybe Jaylen Waddle) and De’Von Achane who went with the four consecutive picks ahead of me, so it was Diggs, Nico Collins (his teammate who has a higher ADP), DeVonta Smith or (maybe) Derrick Henry. I went Diggs who I had personally ranked the highest, wouldn’t make it back to me, who I have in every league and was part of my “unfriendly” draft plan, i.e., the Plan B I had talked about. **4.11 Tank Dell** — He’s too small to hold up, but whenever he played he produced, and he gives me a bit of a Diggs hedge. I also wanted Trey McBride on this turn (as I had Marvin Harrison and could have drafted Kyler Murray — who I love this year — later), but he went on the turn. I thought about taking McBride first, but they were side by side in ADP, and my Plan B was to stack Texans, so I went Dell and took a chance. **5.2 Chris Godwin** — This was the one pick I kind of regret (though it’s debatable.) I like Jayden Reed a lot, but he was half a round lower per ADP, and there was *some* chance I could get him on the way back. I had Godwin everywhere last year, and he was a disappointment, but apparently he’s healthier now and is going back to the slot full time where he excels. **6.11 Jaxon Smith-Njigba** — The other pivot off Godwin was JSN, and sure enough he made it back all the way, though he starts off as my first bench player. That’s okay though — you need at least five viable receivers throughout the year, and I didn’t have to take C.J. Stroud because if the guy at the turn took him, I would just pivot to the Kyler Murray/Harrison stack. **7.2 C.J. Stroud** — He was there, and I executed Plan B. Yes, I have a weak first three rounds by ADP, but I have Gibbs, Harrison and a big piece of the Texans passing game which I think will lead the NFL in yardage. **8.11 Jaylen Warren** — I needed a second back, and Warren is one. He’s a good pass catcher and should see half the snaps in Pittsburgh. **9.2 Brian Robinson** — I like Robinson as a player, he’s the undisputed early-down option on what should be a better offense. (Think Ricky Pearsall, but at RB.) Too soon? Austin Ekeler will obviously see the passing-down work unless he proves totally washed up. The Robinson pick cost me David Njoku and Brock Bowers unfortunately, which was a gamble I knew I was making. **10.11 Jordan Mason** — At 29 and playing into the Super Bowl, Christian McCalfinjury was already a risk, and that he’s “expected” to play Monday night rather than 100 percent fine is worrying. Mason could be a league winner if McCaffrey goes down. **11.2 J.K. Dobbins** — The Mason pick cost me Jaleel McLaughlin, so I pivoted to Dobbins who still has a high ceiling if he can ever stay healthy. **12.11 Dallas Goedert** — Tight ends had flown off the board, but I was happy to get Goedert who has been valuable on a per-game basis the last couple years and is still just 29 which is late prime for the position. **13.2 Dalton Schultz** — Why not stack it even harder? The Texans could throw for 5,000-plus yards, and I have three of the four top targets and the QB. **14.11 Andrei Iosivas** — He’s gotten a lot of buzz in camp, seems like the No. 3 receiver right now, Tee Higgins is hurt and Ja’Marr Chase is still unsigned. **15.2 Cam Akers** — The Iosivas pick cost me Jalen McMillan who would have served as Godwin insurance, but Akers could easily take an aging Joe Mixon’s job. Maybe it’s too much Houston, but if it’s a top-three offense, I’m good with it. **16.11 Justin Fields** — The backup QBs had flown off the board, and Fields has too much upside to pass up. Plus he might even start Week 1 with Russell Wilson already hurt, and if he plays well, he might never look back. **17.2 Harrison Butker** — It’s either the based af kicker or a Younghoe for me. Plus he locked in a decent Week 1. **18.11 Dalvin Cook** — He had only 67 carries last year for a bad Jets offense. What if he isn’t as washed up as we think? He could easily win that job over Zeke Elliott and Rico Dowdle. **19.2 Jonnu Smith** — TE is my weakest position, so I took another upside gamble. What if he’s the Dolphins third target? **20.11 Giants Defense** — I think I took them in all four NFFC leagues. They get the Darnold Vikings at home and then Jayden Daniels in his second career start. And they have three Pro Bowl level pass rushers. **Roster By Position** **QB** CJ Stroud **RB** Jahmyr Gibbs/Jaylen Warren **WR** Marvin Harrison/Stefon Diggs/Tank Dell **TE** Dallas Goedert **FLEX** Chris Godwin **K** Harrison Butker **D** Giants **B** Jaxon Smith-Njigba/Brian Robinson/Jordan Mason/JK Dobbins/Dalton Schultz/Andrei Iosivas/Cam Akers/Justin Fields/Dalvin Cook/Jonnu Smith @ 6bae33c8:607272e8
2024-09-07 22:00:17Unfortunately, I didn’t have a ton of action in this game. I had the Packers with the points and am now 0-2 to start the week in my home picking pool. I had Xavier McKinney in the [Steak League](https://www.realmansports.com/p/steak-league-879?utm_source=publication-search) which was nice as like Roquan Smith he too started the year with a pick. But I was missing the principal scorers namely Saquon Barkley (maybe I let the nerds talk me out of him, as I had him [ranked highly initially](https://www.realmansports.com/p/running-back-rankings?utm_source=publication-search)) and Jayden Reed. Barkley I’m okay with because the potential for Jalen Hurts TDs was something I hadn’t initially considered, but Reed was a major error and in fact I passed on him for freaking Chris Godwin in my [Primetime last night](https://www.realmansports.com/p/nffc-primetime-fa7?utm_source=publication-search)! I had even argued with Alan Seslowsky that Reed was the [obvious choice](https://www.realmansports.com/p/week-1) among the Packers receivers. So seeing him go off (and he should have had a third TD, but it was called back due to something I’ve never seen before (both teams having 12 men on the field) was painful. Godwin is almost sure to have a terrible season now just to hammer home the lesson for me: Don’t worry about 10 spots of ADP, take the fucking guy you like. Stop listening to the consensus when you have a real lean. I don’t know how many times I need to learn this lesson, but apparently at least one more! - Reed looked like the most electrifying receiver on the field for the Packers. He had only six targets, not including the TD called back due to the penalties, but it’s obvious he’ll get more, and the handoff he took 33-yards to the house will incentivize them to do that again too. Year 2 after the surprisingly strong Year 1. He belongs in the second round now, along with Rashee Rice. - Christian Watson caught a TD and will be involved, but as great an athlete as he is he doesn’t have Reed’s football skills. Romeo Doubs is just a guy, but he’s reliable, and Dontayvion Wicks had a rough game — he’s an easy cut for me. - Jordan Love didn’t scramble much, and the Packers settled for a ton of field goals, but he looked okay. I think once they give Reed his 10 targets, Love will have his expected numbers. *(Just read on RotoWire that Love left the game for the last two plays with an unspecified leg injury, something not apparent on the 40-minute edited version. I thought they brought Malik Willis to throw a Hail Mary!* *Obviously, if he’s out for any length of time, all bets are off for the Packers receivers.)* - Josh Jacobs got stuffed in short yardage early, fumbled (though the Packers recovered), but ran well and hard late and even caught two passes. I have zero shares, but he looks like a fine pick for the late-third/early fourth. His backup Emanuel Wilson looked pretty spry too. Marshawn Lloyd is a cut now too in most formats. - Brayden Narveson missed a key kick off the post, but got a lot of attempts. He seems to have landed in the right place for a big season. - Jalen Hurts was a bit sloppy with two picks and a lost fumble, never got going on the ground (seemed like the Packers were really dedicated to taking that away), and the ass-smash didn’t work as well without Jason Kelce. But his receivers are so good, and Saquon Barkley is a big upgrade too. I would downgrade him a little though as his rushing TD projection maybe went from 10 to seven. - AJ Brown didn’t even look like he was running fast as he easily scored a 67-yard TD past the Packers defense. DeVonta Smith seemed to line up more in the slot and was automatic on key third-downs. There was no third receiver of which to speak, and even Dallas Goedert saw only five targets. - Barkley looked great, both on his TD catch, and as a rusher. As I said I don’t have any shares despite being high on him initially, but I love Barkley as a player (and bitcoiner!), and still kind of root for him. I hope he smashes this year.
@ 6bae33c8:607272e8
2024-09-07 22:00:17Unfortunately, I didn’t have a ton of action in this game. I had the Packers with the points and am now 0-2 to start the week in my home picking pool. I had Xavier McKinney in the [Steak League](https://www.realmansports.com/p/steak-league-879?utm_source=publication-search) which was nice as like Roquan Smith he too started the year with a pick. But I was missing the principal scorers namely Saquon Barkley (maybe I let the nerds talk me out of him, as I had him [ranked highly initially](https://www.realmansports.com/p/running-back-rankings?utm_source=publication-search)) and Jayden Reed. Barkley I’m okay with because the potential for Jalen Hurts TDs was something I hadn’t initially considered, but Reed was a major error and in fact I passed on him for freaking Chris Godwin in my [Primetime last night](https://www.realmansports.com/p/nffc-primetime-fa7?utm_source=publication-search)! I had even argued with Alan Seslowsky that Reed was the [obvious choice](https://www.realmansports.com/p/week-1) among the Packers receivers. So seeing him go off (and he should have had a third TD, but it was called back due to something I’ve never seen before (both teams having 12 men on the field) was painful. Godwin is almost sure to have a terrible season now just to hammer home the lesson for me: Don’t worry about 10 spots of ADP, take the fucking guy you like. Stop listening to the consensus when you have a real lean. I don’t know how many times I need to learn this lesson, but apparently at least one more! - Reed looked like the most electrifying receiver on the field for the Packers. He had only six targets, not including the TD called back due to the penalties, but it’s obvious he’ll get more, and the handoff he took 33-yards to the house will incentivize them to do that again too. Year 2 after the surprisingly strong Year 1. He belongs in the second round now, along with Rashee Rice. - Christian Watson caught a TD and will be involved, but as great an athlete as he is he doesn’t have Reed’s football skills. Romeo Doubs is just a guy, but he’s reliable, and Dontayvion Wicks had a rough game — he’s an easy cut for me. - Jordan Love didn’t scramble much, and the Packers settled for a ton of field goals, but he looked okay. I think once they give Reed his 10 targets, Love will have his expected numbers. *(Just read on RotoWire that Love left the game for the last two plays with an unspecified leg injury, something not apparent on the 40-minute edited version. I thought they brought Malik Willis to throw a Hail Mary!* *Obviously, if he’s out for any length of time, all bets are off for the Packers receivers.)* - Josh Jacobs got stuffed in short yardage early, fumbled (though the Packers recovered), but ran well and hard late and even caught two passes. I have zero shares, but he looks like a fine pick for the late-third/early fourth. His backup Emanuel Wilson looked pretty spry too. Marshawn Lloyd is a cut now too in most formats. - Brayden Narveson missed a key kick off the post, but got a lot of attempts. He seems to have landed in the right place for a big season. - Jalen Hurts was a bit sloppy with two picks and a lost fumble, never got going on the ground (seemed like the Packers were really dedicated to taking that away), and the ass-smash didn’t work as well without Jason Kelce. But his receivers are so good, and Saquon Barkley is a big upgrade too. I would downgrade him a little though as his rushing TD projection maybe went from 10 to seven. - AJ Brown didn’t even look like he was running fast as he easily scored a 67-yard TD past the Packers defense. DeVonta Smith seemed to line up more in the slot and was automatic on key third-downs. There was no third receiver of which to speak, and even Dallas Goedert saw only five targets. - Barkley looked great, both on his TD catch, and as a rusher. As I said I don’t have any shares despite being high on him initially, but I love Barkley as a player (and bitcoiner!), and still kind of root for him. I hope he smashes this year. @ 9358c676:9f2912fc
2024-09-07 18:50:14## Introduction The human immunodeficiency virus (HIV) began as a pandemic in the 1980s. In its early days, it was seen as a certain death sentence, a taboo associated with marginalized groups, and it highlighted the failures of poverty in accessing healthcare. Gradually, the struggle for life and the suffering of those who are no longer with us, including both famous and anonymous individuals, became visible. Today, 40 years later, HIV is presented as a chronic disease with effective treatment. **Patients living with HIV who receive appropriate treatment have no detectable virus in their circulating blood, enjoy a good quality of life, and are more concerned about other aspects of their health during medical consultations, almost forgetting their condition.** For these patients, daily treatment is the cure, similar to someone taking a pill every day for high blood pressure or diabetes. ## The Global Impact HIV is a lentivirus, a subgroup of retroviruses composed of RNA. The natural history of HIV infection involves an attack on the immune system, particularly targeting CD4 cells, where chronic deterioration can lead to the acquisition of infectious and oncological diseases that may be fatal over the years, resulting in acquired immunodeficiency syndrome (AIDS). Interestingly, there is a small group of people known as "elite controllers" who manage to control HIV infection without treatment and remain healthy for much of their lives, despite having a hidden deep viral reservoir. The primary modes of transmission are sexual, followed by blood and vertical transmission from mother to child, with the first mode predominating today. Today, in the downward trend of the HIV epidemic, **it is estimated that 39 million people are living with HIV worldwide.** Depending on the region, nearly half of this population belongs to at-risk groups, such as men who have sex with men (MSM), transgender individuals, sex workers, and people who inject drugs. These vulnerable groups are especially important for prevention efforts. However, little is done for prevention in the general population, which sometimes represents the other half of the cake of people living with HIV (PLWH). ## Breaking the Dogma: The Concept of Undetectable = Untransmittable (U=U) The introduction of highly effective antiretroviral therapy (HAART) in 1994 broke the curve of the HIV epidemic. The introduction of new medications with fewer side effects and greater effectiveness in controlling the virus has been crucial. In 2007, the launch of Raltegravir as the first viral integrase inhibitor marked a milestone in current treatments, **allowing patients to effectively control the virus within 3 to 6 months.** The positive impact of these treatments led health organizations to launch the concept of **undetectable = untransmittable (U=U)** to impact the general population and at-risk groups, updating the dogma and eradicating stigma: **a patient living with HIV who maintains an undetectable viral load in their blood through treatment will not transmit HIV sexually.** Although this concept has transformed the social dynamics and stigma surrounding the disease, adherence to treatment must be complete to achieve this new paradigm. ## Prophylaxis as a Method to Prevent HIV in Healthy Populations The correct use of condoms has been the cornerstone of HIV prevention and other sexually transmitted infections over the years. However, it is not the only tool available today and can be complemented for comprehensive sexual health. **Pre-exposure prophylaxis (PrEP)** is a novel strategy that involves administering antiretroviral medication to vulnerable groups before they are exposed to HIV (MSM, transgender individuals, sex workers, people who inject drugs). It involves taking medication daily, effectively reducing the risk of contracting HIV and providing protection to these groups. It is similar to taking a contraceptive pill daily. It has had a very positive impact on protecting these populations. In the Americas, it has been successfully implemented in the United States, Mexico, Peru, and Brazil. Other countries, although with some delay, are now implementing this strategy. **Post-exposure prophylaxis (PEP),** on the other hand, is a strategy that involves administering antiretroviral treatment after a potential exposure to HIV. If the treatment is administered within the first 72 hours and maintained for 4 weeks, the chances of contracting HIV decrease substantially. Both strategies have been remarkably successful in preventing HIV in at-risk populations and healthy populations, although their dissemination and awareness remain limited. https://image.nostr.build/08682bf763ade56741d8e4c8c6d870cb8d71ab7d72c605b9aa805af2234348ff.jpg ## The New Horizon: Long-Acting Antiretrovirals, HIV Vaccines, and Promising Therapies The introduction of viral integrase inhibitors and new nucleoside analogs in the last 15 years has allowed for the availability of safe drugs with minimal side effects in the treatment of HIV, **many of which are included in a single pill regimen per day.** However, the pharmaceutical industry continues to diversify the offerings in a healthy manner. **Cabotegravir is a new long-acting integrase inhibitor that is administered via injection.** Combined with Rilpivirine, it has proven to be effective and safe in the treatment of HIV, with injections every 2 months. This has revolutionized treatment for people who are tired of taking pills daily, as well as in PrEP, where effective prevention against HIV can be achieved with injections every 2 months for at-risk groups. Additionally, **subdermal implants of Islatravir,** a new long-acting nucleoside analog, are being tested as a PrEP strategy. Similar to monthly hormonal contraceptive injections or hormonal contraceptive implants, this strategy has proven effective in at-risk groups. Regarding the **HIV vaccine,** we have been developing it for over two decades, with advances and setbacks. While vaccines have shown promising results in terms of safety and antibody generation, we still need to await conclusive phase III results demonstrating their effectiveness in at-risk groups and the general population. ## The Eradication of HIV and Patients Cured Without Treatment While current treatment allows for the elimination of HIV from the bloodstream and sexual transmission, there remains a reservoir in some deep immune cells that have been infected by the retrovirus, which contain latent HIV DNA and have the potential to reactivate if daily treatment is interrupted. However, **there are patients who have managed to eliminate HIV from their bodies, including these deep cells, and HIV is undetectable upon discontinuation of treatment.** These cases are very rare, with only 7 to 8 individuals being the subject of intensive scientific study. Among them are the "Berlin patient" of Germany and "City of Hope patient" from Argentina. Some of these cases involved patients under effective HIV treatment who underwent suppressive chemotherapy for bone marrow transplants and managed to eliminate these deep cells with latent HIV DNA. Unfortunately, this treatment is not scalable for the entire HIV-positive population, both due to its cost and potential side effects. However, **"Shock and Kill" strategies** have been proposed, aiming to use monoclonal antibodies to activate these latent cells during HIV treatment, exposing them to antiretroviral medication for elimination, thereby eradicating these small reservoirs of HIV. ## WHO Goals The World Health Organization (WHO) has established clear objectives that are constantly updated to achieve the eradication of HIV in the population. **The updated goals of the WHO propose that, to end the HIV epidemic, three objectives must be met by the year 2025-2030:** 1. 95% of people living with HIV must be diagnosed through testing. 2. 95% of diagnosed individuals must be on highly effective antiretroviral therapy (HAART). 3. 95% of those on HAART must have an undetectable viral load in their blood. Developing and underdeveloped countries currently have an effectiveness rate for these strategies that disagree significantly. https://image.nostr.build/ac6693df57aaca6dac0b06b5db9eb1a2757e7c08511edb0f11617e12653d3db5.png ## Key Takeaways * HIV has a cure, and the cure is permanent treatment. * Treatment for HIV is free and accessible to the population, as it is a public health impact disease. * A person living with HIV who receives appropriate treatment will not transmit the virus sexually, will enjoy a full life without the disease, and can have children without HIV. * In the event of a potential HIV exposure (such as unprotected sexual contact with an infrequent partner), you can go to a hospital within the first 72 hours to receive treatment that will prevent HIV infection. * Just as we witnessed the eradication of smallpox from the face of the earth in 1978 due to scientific advances, we will live to see the eradication of HIV. ## Autor **Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community** npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj ## Resources 1. [World Health Organization (WHO)](https://www.who.int/en/health-topics/hiv-aids#tab=tab_1) 2. [Centers for Disease Control and Prevention (CDC)](https://www.cdc.gov/hiv/?CDC_AAref_Val=https://www.cdc.gov/hiv/default.html) 3. [UNAIDS](https://www.unaids.org/en) ## Bibliography 1. The natural history of HIV infection. DOI: 10.1097/COH.0b013e328361fa66 2. Changing Knowledge and Attitudes Towards HIV Treatment-as-Prevention and "Undetectable = Untransmittable": A Systematic Review. DOI: 10.1007/s10461-021-03296-8 3. Challenges of HIV diagnosis and management in the context of pre-exposure prophylaxis (PrEP), post-exposure prophylaxis (PEP), test and start and acute HIV infection: a scoping review. DOI: 10.1002/jia2.25419 4. Long-acting cabotegravir and rilpivirine dosed every 2 months in adults with HIV-1 infection (ATLAS-2M), 48-week results: a randomised, multicentre, open-label, phase 3b, non-inferiority study. DOI: 10.1016/S0140-6736(20)32666-0 5. Efficacy and safety of long-acting cabotegravir compared with daily oral tenofovir disoproxil fumarate plus emtricitabine to prevent HIV infection in cisgender men and transgender women who have sex with men 1 year after study unblinding: a secondary analysis of the phase 2b and 3 HPTN 083 randomised controlled trial. DOI: 10.1016/S2352-3018(23)00261-8 6. Safety and immunogenicity of a subtype C ALVAC-HIV (vCP2438) vaccine prime plus bivalent subtype C gp120 vaccine boost adjuvanted with MF59 or alum in healthy adults without HIV (HVTN 107): A phase 1/2a randomized trial. DOI: 10.1371/journal.pmed.1004360 7. Shock and kill within the CNS: A promising HIV eradication approach?. DOI: 10.1002/JLB.5VMR0122-046RRR
@ 9358c676:9f2912fc
2024-09-07 18:50:14## Introduction The human immunodeficiency virus (HIV) began as a pandemic in the 1980s. In its early days, it was seen as a certain death sentence, a taboo associated with marginalized groups, and it highlighted the failures of poverty in accessing healthcare. Gradually, the struggle for life and the suffering of those who are no longer with us, including both famous and anonymous individuals, became visible. Today, 40 years later, HIV is presented as a chronic disease with effective treatment. **Patients living with HIV who receive appropriate treatment have no detectable virus in their circulating blood, enjoy a good quality of life, and are more concerned about other aspects of their health during medical consultations, almost forgetting their condition.** For these patients, daily treatment is the cure, similar to someone taking a pill every day for high blood pressure or diabetes. ## The Global Impact HIV is a lentivirus, a subgroup of retroviruses composed of RNA. The natural history of HIV infection involves an attack on the immune system, particularly targeting CD4 cells, where chronic deterioration can lead to the acquisition of infectious and oncological diseases that may be fatal over the years, resulting in acquired immunodeficiency syndrome (AIDS). Interestingly, there is a small group of people known as "elite controllers" who manage to control HIV infection without treatment and remain healthy for much of their lives, despite having a hidden deep viral reservoir. The primary modes of transmission are sexual, followed by blood and vertical transmission from mother to child, with the first mode predominating today. Today, in the downward trend of the HIV epidemic, **it is estimated that 39 million people are living with HIV worldwide.** Depending on the region, nearly half of this population belongs to at-risk groups, such as men who have sex with men (MSM), transgender individuals, sex workers, and people who inject drugs. These vulnerable groups are especially important for prevention efforts. However, little is done for prevention in the general population, which sometimes represents the other half of the cake of people living with HIV (PLWH). ## Breaking the Dogma: The Concept of Undetectable = Untransmittable (U=U) The introduction of highly effective antiretroviral therapy (HAART) in 1994 broke the curve of the HIV epidemic. The introduction of new medications with fewer side effects and greater effectiveness in controlling the virus has been crucial. In 2007, the launch of Raltegravir as the first viral integrase inhibitor marked a milestone in current treatments, **allowing patients to effectively control the virus within 3 to 6 months.** The positive impact of these treatments led health organizations to launch the concept of **undetectable = untransmittable (U=U)** to impact the general population and at-risk groups, updating the dogma and eradicating stigma: **a patient living with HIV who maintains an undetectable viral load in their blood through treatment will not transmit HIV sexually.** Although this concept has transformed the social dynamics and stigma surrounding the disease, adherence to treatment must be complete to achieve this new paradigm. ## Prophylaxis as a Method to Prevent HIV in Healthy Populations The correct use of condoms has been the cornerstone of HIV prevention and other sexually transmitted infections over the years. However, it is not the only tool available today and can be complemented for comprehensive sexual health. **Pre-exposure prophylaxis (PrEP)** is a novel strategy that involves administering antiretroviral medication to vulnerable groups before they are exposed to HIV (MSM, transgender individuals, sex workers, people who inject drugs). It involves taking medication daily, effectively reducing the risk of contracting HIV and providing protection to these groups. It is similar to taking a contraceptive pill daily. It has had a very positive impact on protecting these populations. In the Americas, it has been successfully implemented in the United States, Mexico, Peru, and Brazil. Other countries, although with some delay, are now implementing this strategy. **Post-exposure prophylaxis (PEP),** on the other hand, is a strategy that involves administering antiretroviral treatment after a potential exposure to HIV. If the treatment is administered within the first 72 hours and maintained for 4 weeks, the chances of contracting HIV decrease substantially. Both strategies have been remarkably successful in preventing HIV in at-risk populations and healthy populations, although their dissemination and awareness remain limited. https://image.nostr.build/08682bf763ade56741d8e4c8c6d870cb8d71ab7d72c605b9aa805af2234348ff.jpg ## The New Horizon: Long-Acting Antiretrovirals, HIV Vaccines, and Promising Therapies The introduction of viral integrase inhibitors and new nucleoside analogs in the last 15 years has allowed for the availability of safe drugs with minimal side effects in the treatment of HIV, **many of which are included in a single pill regimen per day.** However, the pharmaceutical industry continues to diversify the offerings in a healthy manner. **Cabotegravir is a new long-acting integrase inhibitor that is administered via injection.** Combined with Rilpivirine, it has proven to be effective and safe in the treatment of HIV, with injections every 2 months. This has revolutionized treatment for people who are tired of taking pills daily, as well as in PrEP, where effective prevention against HIV can be achieved with injections every 2 months for at-risk groups. Additionally, **subdermal implants of Islatravir,** a new long-acting nucleoside analog, are being tested as a PrEP strategy. Similar to monthly hormonal contraceptive injections or hormonal contraceptive implants, this strategy has proven effective in at-risk groups. Regarding the **HIV vaccine,** we have been developing it for over two decades, with advances and setbacks. While vaccines have shown promising results in terms of safety and antibody generation, we still need to await conclusive phase III results demonstrating their effectiveness in at-risk groups and the general population. ## The Eradication of HIV and Patients Cured Without Treatment While current treatment allows for the elimination of HIV from the bloodstream and sexual transmission, there remains a reservoir in some deep immune cells that have been infected by the retrovirus, which contain latent HIV DNA and have the potential to reactivate if daily treatment is interrupted. However, **there are patients who have managed to eliminate HIV from their bodies, including these deep cells, and HIV is undetectable upon discontinuation of treatment.** These cases are very rare, with only 7 to 8 individuals being the subject of intensive scientific study. Among them are the "Berlin patient" of Germany and "City of Hope patient" from Argentina. Some of these cases involved patients under effective HIV treatment who underwent suppressive chemotherapy for bone marrow transplants and managed to eliminate these deep cells with latent HIV DNA. Unfortunately, this treatment is not scalable for the entire HIV-positive population, both due to its cost and potential side effects. However, **"Shock and Kill" strategies** have been proposed, aiming to use monoclonal antibodies to activate these latent cells during HIV treatment, exposing them to antiretroviral medication for elimination, thereby eradicating these small reservoirs of HIV. ## WHO Goals The World Health Organization (WHO) has established clear objectives that are constantly updated to achieve the eradication of HIV in the population. **The updated goals of the WHO propose that, to end the HIV epidemic, three objectives must be met by the year 2025-2030:** 1. 95% of people living with HIV must be diagnosed through testing. 2. 95% of diagnosed individuals must be on highly effective antiretroviral therapy (HAART). 3. 95% of those on HAART must have an undetectable viral load in their blood. Developing and underdeveloped countries currently have an effectiveness rate for these strategies that disagree significantly. https://image.nostr.build/ac6693df57aaca6dac0b06b5db9eb1a2757e7c08511edb0f11617e12653d3db5.png ## Key Takeaways * HIV has a cure, and the cure is permanent treatment. * Treatment for HIV is free and accessible to the population, as it is a public health impact disease. * A person living with HIV who receives appropriate treatment will not transmit the virus sexually, will enjoy a full life without the disease, and can have children without HIV. * In the event of a potential HIV exposure (such as unprotected sexual contact with an infrequent partner), you can go to a hospital within the first 72 hours to receive treatment that will prevent HIV infection. * Just as we witnessed the eradication of smallpox from the face of the earth in 1978 due to scientific advances, we will live to see the eradication of HIV. ## Autor **Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community** npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj ## Resources 1. [World Health Organization (WHO)](https://www.who.int/en/health-topics/hiv-aids#tab=tab_1) 2. [Centers for Disease Control and Prevention (CDC)](https://www.cdc.gov/hiv/?CDC_AAref_Val=https://www.cdc.gov/hiv/default.html) 3. [UNAIDS](https://www.unaids.org/en) ## Bibliography 1. The natural history of HIV infection. DOI: 10.1097/COH.0b013e328361fa66 2. Changing Knowledge and Attitudes Towards HIV Treatment-as-Prevention and "Undetectable = Untransmittable": A Systematic Review. DOI: 10.1007/s10461-021-03296-8 3. Challenges of HIV diagnosis and management in the context of pre-exposure prophylaxis (PrEP), post-exposure prophylaxis (PEP), test and start and acute HIV infection: a scoping review. DOI: 10.1002/jia2.25419 4. Long-acting cabotegravir and rilpivirine dosed every 2 months in adults with HIV-1 infection (ATLAS-2M), 48-week results: a randomised, multicentre, open-label, phase 3b, non-inferiority study. DOI: 10.1016/S0140-6736(20)32666-0 5. Efficacy and safety of long-acting cabotegravir compared with daily oral tenofovir disoproxil fumarate plus emtricitabine to prevent HIV infection in cisgender men and transgender women who have sex with men 1 year after study unblinding: a secondary analysis of the phase 2b and 3 HPTN 083 randomised controlled trial. DOI: 10.1016/S2352-3018(23)00261-8 6. Safety and immunogenicity of a subtype C ALVAC-HIV (vCP2438) vaccine prime plus bivalent subtype C gp120 vaccine boost adjuvanted with MF59 or alum in healthy adults without HIV (HVTN 107): A phase 1/2a randomized trial. DOI: 10.1371/journal.pmed.1004360 7. Shock and kill within the CNS: A promising HIV eradication approach?. DOI: 10.1002/JLB.5VMR0122-046RRR @ 41d0a715:9733c512
2024-09-07 15:27:14>Blaise Pascal: 'I have made this letter longer than usual, only because I have not had the time to make it shorter.' Some of you Stackers need to spend a little more time to make your posts short and sweet. Sometimes I realize a post doesn't even have a point after wasting time reading it. A long poorly written post is a waste of my time and yours too! originally posted at https://stacker.news/items/676136
@ 41d0a715:9733c512
2024-09-07 15:27:14>Blaise Pascal: 'I have made this letter longer than usual, only because I have not had the time to make it shorter.' Some of you Stackers need to spend a little more time to make your posts short and sweet. Sometimes I realize a post doesn't even have a point after wasting time reading it. A long poorly written post is a waste of my time and yours too! originally posted at https://stacker.news/items/676136 @ 655a7cf1:d0510794
2024-09-06 23:45:52I can't stop thinking about it. When I go to clear out a cave in Skyrim I always find the troll the spider some version of some enemy with gold. I ask myself how did they get this gold.? Is there someone in the cities that goes to and fro to have commerce with underworld. If so what would this market look like. Would it be trade based or commodity based. Sometimes in these caves I can find upwards of 100 gold I can also find individuals with upwards of 20 gold on them. Assuming they live paycheck to paycheck this is a moderate size of money they're carrying around from week to week. It tells me that the trade is doing well. Am I completely psychotic for constantly thinking about this? Does anybody else thought about this or done any research or have any links that I can find? originally posted at https://stacker.news/items/673609
@ 655a7cf1:d0510794
2024-09-06 23:45:52I can't stop thinking about it. When I go to clear out a cave in Skyrim I always find the troll the spider some version of some enemy with gold. I ask myself how did they get this gold.? Is there someone in the cities that goes to and fro to have commerce with underworld. If so what would this market look like. Would it be trade based or commodity based. Sometimes in these caves I can find upwards of 100 gold I can also find individuals with upwards of 20 gold on them. Assuming they live paycheck to paycheck this is a moderate size of money they're carrying around from week to week. It tells me that the trade is doing well. Am I completely psychotic for constantly thinking about this? Does anybody else thought about this or done any research or have any links that I can find? originally posted at https://stacker.news/items/673609 @ 8cb60e21:5f2deaea
2024-09-06 22:28:24JavaScript For Cats An introduction for new programmers cat So easy your human companion could do it too! JavaScript is a programming language or, in other words, a means by which a computer is instructed to do things. Just the same as one controls humans with hisses and meows, one controls computers with statements written in a programming language. All web browsers understand JavaScript and you can take advantage of that to make web pages do crazy things! JavaScript started as a way to make web pages more interactive. Nowadays JavaScript runs in more places than just web browsers — it runs on web servers, phones and even robots! This page will teach you some JavaScript basics so that you can get up and running in no time*. * Actual time: more than none. Probably an hour or two. Also since you are a cat you are less likely to run and more likely to lay around in the sun Table of contents The console Strings Values and variables Using functions Built in JS functions Download new JS functions Writing new functions Loops Arrays Objects Callbacks Recommended reading Don't be a scaredy-cat cat You will always land on your feet — even when programming! Unlike pawing over a glass of water on your laptop, nothing in these tutorials will damage your computer in any way, even if you mistype a command or click the wrong button. Like cats, computer programmers make mistakes all time: misspelling things, forgetting quotes or brackets, and being forgetful of how basic functions (and yarn, lasers) work. Programmers care more about making it work eventually rather than trying to make it work the very first time. The best way to learn is by making mistakes! So don't be a scaredy-cat! The absolute worst thing that will happen is that you might have to refresh this page in your web browser if you get stuck. Don't worry though, this will happen very rarely. # The basics There is JavaScript running on this page right now. Let's play around with it a little. For the sake of simplicity I'll assume you are using Google Chrome to read this page (if you aren't it's probably easier on both of us if you follow along with Chrome). First, right click anywhere on the screen and hit Inspect Element, then click on the Console tab. You should see a thingy that looks like this: console This is a console, otherwise known as a "command line" or "terminal". Basically it's a way to type one thing at a time into a computer and immediately get the computers answer back. They are super useful as a learning tool (I still use the console nearly every day that I'm coding). The console does some pretty cool stuff. Here I have started to type something and the console is helping me out by giving me a list of all the possible things I could continue to type! Another thing you could do is type 1 + 1 into the console and then hit the Enter key and watch what happens. Using the console is a very important part of learning JavaScript. If you don't know if something works or what the command is for something, go to the console and figure it out! Here's an example: # Strings Since I am a cat I want to replace every instance of the word dog on the Internet with those blasted dogs. First go into your console and type in a few sentences that contain the word dog at least once. In JavaScript a bunch of letters, numbers, words or anything else is known as a String (as in a string of characters). Strings have to begin AND end with a quotation mark. Single ' or double " is fine, just make sure you use the same at the beginning as you do at the end. console See the nasty error message? Don't worry - you didn't break any laws. SyntaxError ILLEGAL is just the way it sounds when robots tell you that your program has a problem. The first two sentences had matching quotation marks at the beginning and end, but when I mixed single and double quotation marks it freaked out on me. OK, to fix up one of these sentences (by replacing dog with our enhanced version) we have to first save the original sentence so that we can call it up later when we do our replacing magic. Notice how the string gets repeated in red when we type it into the console? This is because we haven't told it to save the sentence anywhere so it just gives it right back (or it gives us an Error back if we messed something up). # Values and variables Values are the simplest components in JavaScript. 1 is a value, true is a value, "hello" is a value, function() {} is a value, the list goes on! There are a handful of different types of values in JavaScript but we don't need to go over them all right away — you will learn them naturally the more you code! To store values we use things called variables. The word 'variable' means 'can change' and is used because variables can store many different types of values and can change their value many times. They are pretty much like mailboxes. We put something in a variable, like our sentence, and then give the variable an address that we can use to look up the sentence later. In real life mailboxes have to have PO Box numbers but in JavaScript you usually just use lowercase letters or numbers without any spaces. console var is shorthand for variable and the = means store the thing on the right-hand side in the thing on the left-hand side. Also as you can see, now that we are storing our sentence in a variable the console doesn't just return our sentence right away, but instead gives us undefined which means there was nothing to return. If you simply type a variable name into the console it will print out the value stored in that variable. A note about variables is that by default they go away when you switch to a different page. If I were to hit the Refresh button in Chrome, for example, my dogSentence variable would get wiped and it would be like it never existed. But don't worry about this too much for now — you can just hit the up or down arrows on your keyboard while in the console to go through everything you've entered in recently. # Functions Now that we have our sentence stored in a variable, let's change a word stored in it! We can do this by performing a function. Functions are a type of value that, well, serve a specific function (AKA purpose or action) for us. Calling them "actions" sounded weird I guess so they went with the word "function" instead. JavaScript has a function called replace that does exactly what we want! Functions take in any number of values in their parentheses (zero, one or many) and return either nothing (undefined) or the changed string. The replace function is available to use on any strings and takes in two values: the characters to take out and the characters to swap in. It gets confusing to describe these things so here is a visual example: console Notice how the value of dogSentence is the same even after we run replace on it? This is because the replace function, (and most JavaScript functions for that matter) takes the value we give it and returns a new value, without modifying the value we passed in. Since we didn't store the result (there is no = on the left side of the replace function) it just printed out the return value in our console. # The "standard library" You might be wondering what other functions are available in JavaScript. The answer: A TON. There are lots built in, standard libraries that you can learn about at MDN (A site run by Mozilla that has lotsa nifty information about web technologies). For example here is the MDN page on JavaScript's Math object. # Third-party JavaScript There is also a lot of JavaScript code available that is not built in. JavaScript from third parties is usually referred to as a "library" or "plugin". One of my favorites is called Underscore.js. Let's go and grab it and load it into our page! First go to the Underscore site, http://underscorejs.org/, click on the download link (I usually use development versions because they are easier to read but both will give you the same basic functionality), and then copy all the code onto your clipboard (you can use Select All from the Edit menu to select everything). Then paste it into your console and hit enter. Now your browser has a new variable in it: _. Underscore gives you a ton of helpful functions to play with. We'll learn more about how to use them later. console # Making new functions You aren't limited to using other peoples functions — you can also write them yourself. It's pretty easy! Let's make a function called makeMoreExciting that adds a bunch of exclamation points to the end of a string. function makeMoreExciting(string) { return string + '!!!!' } In my head I read it out loud like this: "there's a function called 'make more exciting' that takes in a string and returns a new copy of that string that has a bunch of exclamation points at the end". Here is how we would write this in the console manually if we weren't using a function: console The expression string + '!!!!' returns a new string and our variable called string stays the same as before (since we never updated it to anything else with =). Let's use our function instead of doing it manually. First, paste the function into the console and then call the function by passing in a string: console You could also call the same function by passing in a variable that points to a string (in the above example we just typed the string straight in there as a value instead of saving it to a variable first): console The line makeMoreExciting(sentence) is equivalent to saying sentence + '!!!!'. What if we wanted to modify in-place (aka update) the value of sentence? Simply save the return value of the function back into our sentence variable: var sentence = "time for a nap" sentence = makeMoreExciting(sentence) Now sentence will have the exclamation marks in it! Note that you only have to use var when you are initializing a variable — the first time you ever use it. After that you shouldn't use var unless you want to re-initialize (reset/clear/empty) the variable. What would happen if we took out the return statement in our function? console Why is sentence empty? Because functions return undefined by default! You can choose to return a value by returning something. Functions should take in a value and, if they change the value or create a new value that is supposed to be used later, return a value (fun fact: a fancy term for this style is functional programming). Here is another function that doesn't return anything but instead uses a different method to show us the output: function yellIt(string) { string = string.toUpperCase() string = makeMoreExciting(string) console.log(string) } This function, yellIt, uses our previous function makeMoreExciting as well as the built-in String method toUpperCase. Methods are just a name for a function when it belongs to something — in this case toUpperCase is a function that belongs to String so we can refer to it as either a method or a function. makeMoreExciting on the other hand doesn't belong to anyone so it would be technically incorrect to refer to it as a method (confusing, I know). The last line of the function is another built-in that simply takes in any values that you give it and prints them out into the console. console So is there something wrong with the above yellIt function? It depends! Here are the two major types of functions: functions that modify or create values and return them functions take in values and perform some action that cannot be returned console.log is an example of the second type of function: it prints things out to your console — an action that you can see with your eyes but that cannot be represented as a JavaScript value. My own rule of thumb is to try to keep the two types of functions separate from each other, so here's how I would rewrite the yellIt function: function yellIt(string) { string = string.toUpperCase() return makeMoreExciting(string) } console.log(yellIt("i fear no human")) This way yellIt becomes more generic, meaning it only does one or two simple little things and doesn't know anything about printing itself to a console — that part can always be programmed later, outside the function definition. # Loops Now that we have some basic skills under our belt (Author's note: do cats even wear belts?) we can start being lazy. What?! Yes, that's right: programming is about being lazy. Larry Wall, inventor of the Perl programming language, called laziness the most important virtue of a good programmer. If computers didn't exist you would have to do all sorts of tedious tasks by hand, but if you learn to program you can lay in the sun all day while a computer somewhere runs your programs for you. It is a glorious lifestyle filled with relaxation! Loops are one of the most important ways to harness the power of a computer. Remember Underscore.js from earlier? Make sure you have it loaded in the page (remember: you can just hit the up arrow on your keyboard a few times and then hit Enter to load it in again if you need to) and try copy/pasting this into your console: function logANumber(someNumber) { console.log(someNumber) } _.times(10, logANumber) This code uses the times method of Underscore which takes in 1 number and 1 function and then starts from 0 and for 10 steps counts up by 1, calling the function with the number each step of the way. console If we were to manually write out what times is doing in the above code it would look like this: logANumber(0) logANumber(1) logANumber(2) logANumber(3) logANumber(4) logANumber(5) logANumber(6) logANumber(7) logANumber(8) logANumber(9) But cats refuse to do unnecessary manual work like this so we must always ask ourselves, "am I doing this in the laziest way possible?". So why is this called looping? Think of it like this: If we were to write out a list of 10 numbers (from 0 to 9) using a JavaScript Array it would look like this: var zeroThroughTen = [0, 1, 2, 3, 4, 5, 6, 7, 8, 9] What times really does is visit each number and repeat a task: in the example above the task was to call the logANumber function with the current number. Repeating tasks in this way is referred to as looping over the Array. # Arrays I've mentioned these a few times but let's spend a minute learning about them. Imagine you need to keep track of all your buddies. Well, an Array will do just fine. Think of an Array like a sorted list that you can keep tons of stuff in. This is how you make one: var myCatFriends = ["bill", "tabby", "ceiling"] Sweet! Now you have a list of your cat buddies. Elements (that is what you call a single item in an array) that are stored within arrays start at 0 and count up from there. So myCatFriends[0] returns bill and myCatFriends[1] returns tabby... etc etc. To get buddies out of your brand new Array you can just access an element directly like so: console.log(myCatFriends[0]) console If you made a brand new cat friend at the hippest cat club the other night and you want to add them to your list it is super simple: myCatFriends.push("super hip cat"). To check that the new cat made it into your array you can use .length: console Notice how push returned the length? Handy! Also take note that arrays will always preserve ordering which means they will remember the order in which you added or defined things. Not everything in JavaScript preserves ordering so remember this special property of Arrays! # Objects Arrays are good for lists, but for other tasks they can be hard to work with. Consider our array of cat friends. What if you also wanted to store more than just names? var myCatFriends = ["bill", "tabby", "ceiling"] var lastNames = ["the cat", "cat", "cat"] var addresses = ["The Alley", "Grandmas House", "Attic"] Sometimes it is nice to have all of the addresses or names in one variable. But sometimes you have a cat in mind, let's say Bill, and you just want to look up that cat's address. With arrays it takes a lot of work because you can't just say 'hey array, give me Bill's address' because 'Bill' is in one array and his address is in a totally different array. console This can be brittle because if our arrays change and we add a new cat to the beginning we would have to also update our billsPosition variable to point to the new location of Bill's information in the arrays! Here is a easier to maintain way to store information like this using objects: var firstCat = { name: "bill", lastName: "the cat", address: "The Alley" } var secondCat = { name: "tabby", lastName: "cat", address: "Grandmas House" } var thirdCat = { name: "ceiling", lastName: "cat", address: "Attic" } Why would we do it this way? Because now we have a variable for each cat that we can use to get that cats values in a more convenient and readable way. console You can think of Objects like keys on a keyring. Each one is for a specific door and if you have nice labels on your keys you can open doors very fast. In fact, the things on the left hand side of the : are called keys (are also known as properties) and the things on the right hand side are values. // an object with a single key 'name' and single value 'bill' { name: 'bill' } So why would you ever use arrays if you can just put your data in objects? Because objects don't remember the order of the keys that you set. You might enter in an object like this: { date: "10/20/2012", diary: "slept a bit today", name: "Charles" } But the computer could give it back to you like this: { diary: "slept a bit today", name: "Charles", date: "10/20/2012" } Or like this! { name: "Charles", diary: "slept a bit today", date: "10/20/2012" } So you can't ever trust the order of keys in objects. If you wanna get REALLY fancy you can make an array filled with objects, or an object filled with arrays! var moodLog = [ { date: "10/20/2012", mood: "catnipped" }, { date: "10/21/2012", mood: "nonplussed" }, { date: "10/22/2012", mood: "purring" } ] // ordered from least to most favorite var favorites = { treats: ["bird sighting", "belly rub", "catnip"], napSpots: ["couch", "planter box", "human face"] } When you combine different things like this you are making data structures, just like legos! # Callbacks Callbacks aren't really a feature of JavaScript like Object or Array, but instead just a certain way to use functions. To understand why callbacks are useful you first have to learn about asynchronous (often shortened to async) programming. Asynchronous code by definition is code written in a way that is not synchronous. Synchronous code is easy to understand and write. Here is an example to illustrate: var photo = download('http://foo-chan.com/images/sp.jpg') uploadPhotoTweet(photo, '@maxogden') This synchronous pseudo-code downloads an adorable cat photo and then uploads the photo to twitter and tweets the photo at @maxogden. Pretty straightforward! (Author's note: I @maxogden do happily accept random cat photo tweets) This code is synchronous because in order for photo to get uploaded to the tweet, the photo download must be completed. This means that line 2 cannot run until the task on line 1 is totally finished. If we were to actually implement this pseudo-code we would want to make sure that download 'blocked' execution until the download was finished, meaning it would prevent any other JavaScript from being executed until it finished, and then when the download completes it would un-block the JavaScript execution and line 2 would execute. Synchronous code is fine for things that happen fast, but it's horrible for things that require saving, loading, downloading or uploading. What if the server you're downloading the photo from is slow, or the internet connection you are using is slow, or the computer you are running the code on has too many youtube cat video tabs open and is running slowly? It means that it could potentially take minutes of waiting before line 2 gets around to running. Meanwhile, because all JavaScript on the page is being blocked from being run while the download is happening, the webpage would totally freeze up and become unresponsive until the download is done. Blocking execution should be avoided at all costs, especially when doing so makes your program freeze up or become unresponsive. Let's assume the photo above takes one second to download. To illustrate how long one second is to a modern computer, here is a program that tests to see how many tasks JavaScript can process in one second. function measureLoopSpeed() { var count = 0 function addOne() { count = count + 1 } // Date.now() returns a big number representing the number of // milliseconds that have elapsed since Jan 01 1970 var now = Date.now() // Loop until Date.now() is 1000 milliseconds (1 second) or more into // the future from when we started looping. On each loop, call addOne while (Date.now() - now < 1000) addOne() // Finally it has been >= 1000ms, so let's print out our total count console.log(count) } measureLoopSpeed() Copy-paste the above code into your JavaScript console and after one second it should print out a number. On my computer I got 8527360, approximately 8.5 million. In one second JavaScript can call the addOne function 8.5 million times! So if you have synchronous code for downloading a photo, and the photo download takes one second, it means you are potentially preventing 8.5 million operations from happening while JavaScript execution is blocked. Some languages have a function called sleep that blocks execution for some number of seconds. For example here is some bash code running in Terminal.app on Mac OS that uses sleep. When you run the command sleep 3 && echo 'done sleeping now' it blocks for 3 seconds before printing out done sleeping now. console JavaScript doesn't have a sleep function. Since you are a cat you are probably asking yourself, "Why am I learning a programming language that does not involve sleeping?". But stay with me. Instead of relying on sleep to wait for things to happen the design of JavaScript encourages use of functions instead. If you have to wait for task A to finish before doing task B, you put all of the code for task B into a function and you only call that function when A is done. For example, this is blocking-style code: a() b() And this is in a non-blocking style: a(b) In the non-blocking version b is a callback to a. In the blocking version a and b are both called/invoked (they both have () after them which executes the functions immediately). In the non-blocking version you will notice that only a gets invoked, and b is simply passed in to a as an argument. In the blocking version, there is no explicit relationship between a and b. In the non-blocking version it becomes a's job to do what it needs to do and then call b when it is done. Using functions in this way is called callbacks because your callback function, in this case b, gets called later on when a is all done. Here is a pseudocode implementation of what a might look like: function a(done) { download('https://pbs.twimg.com/media/B4DDWBrCEAA8u4O.jpg:large', function doneDownloading(error, png) { // handle error if there was one if (err) console.log('uh-oh!', error) // call done when you are all done done() }) } Think back to our non-blocking example, a(b), where we call a and pass in b as the first argument. In the function definition for a above the done argument is our b function that we pass in. This behavior is something that is hard to wrap your head around at first. When you call a function, the arguments you pass in won't have the same variable names when they are in the function. In this case what we call b is called done inside the function. But b and done are just variable names that point to the same underlying function. Usually callback functions are labelled something like done or callback to make it clear that they are functions that should be called when the current function is done. So, as long as a does it's job and called b when it is done, both a and b get called in both the non-blocking and blocking versions. The difference is that in the non-blocking version we don't have to halt execution of JavaScript. In general non-blocking style is where you write every function so that it can return as soon as possible, without ever blocking. To drive the point home even further: If a takes one second to complete, and you use the blocking version, it means you can only do one thing. If you use the non-blocking version (aka use callbacks) you can do literally millions of other things in that same second, which means you can finish your work millions of times faster and sleep the rest of the day. Remember: programming is all about laziness and you should be the one sleeping, not your computer. Hopefully you can see now that callbacks are just functions that call other functions after some asynchronous task. Common examples of asynchronous tasks are things like reading a photo, downloading a song, uploading a picture, talking to a database, waiting for a user to hit a key or click on someone, etc. Anything that takes time. JavaScript is really great at handling asynchronous tasks like these as long as you take the time to learn how to use callbacks and keep your JavaScript from being blocked. The end! This is just the beginning of your relationship with JavaScript! You can't learn it all at once, but you should find what works for you and try to learn all of the concepts here. I'd recommend coming back again tomorrow and going through the entire thing again from the beginning! It might take a few times through before you get everything (programming is hard). Just try to avoid reading this page in any rooms that contain shiny objects . . . they can be incredibly distracting. Got another topic you wanna see covered? Open an issue for it on github. # Recommended reading JavaScript For Cats skips over lots of details that aren't important for getting started (cats are not known for their attention spans), but if you feel like you need to dive in deeper then check these out: NodeSchool.io is a community driven, open source educational software that teaches various web development skills in an interactive, self-guided format. I helped make NodeSchool! Sadly it features fewer cats than this page. Eloquent Javascript is a free book that teaches you JavaScript! It's pretty good! Especially the chapter on values, variables, and control flow Mozilla's JavaScript Guide also has a pretty sweet intro chapter called values, variables and literals standard JS Style Guide is a "zero configuration" linter for JS style that I use Let's Write Code by @shama a great series of YouTube coding tutorials made by a friend of mine # Satisfied customers satisfied customer satisfied customer satisfied customer satisfied customer satisfied customer JSForCats.com is a labor of love and work in progress by @maxogden. If you would like to contribute and make this tutorial better there is a Github repo right over here. console
@ 8cb60e21:5f2deaea
2024-09-06 22:28:24JavaScript For Cats An introduction for new programmers cat So easy your human companion could do it too! JavaScript is a programming language or, in other words, a means by which a computer is instructed to do things. Just the same as one controls humans with hisses and meows, one controls computers with statements written in a programming language. All web browsers understand JavaScript and you can take advantage of that to make web pages do crazy things! JavaScript started as a way to make web pages more interactive. Nowadays JavaScript runs in more places than just web browsers — it runs on web servers, phones and even robots! This page will teach you some JavaScript basics so that you can get up and running in no time*. * Actual time: more than none. Probably an hour or two. Also since you are a cat you are less likely to run and more likely to lay around in the sun Table of contents The console Strings Values and variables Using functions Built in JS functions Download new JS functions Writing new functions Loops Arrays Objects Callbacks Recommended reading Don't be a scaredy-cat cat You will always land on your feet — even when programming! Unlike pawing over a glass of water on your laptop, nothing in these tutorials will damage your computer in any way, even if you mistype a command or click the wrong button. Like cats, computer programmers make mistakes all time: misspelling things, forgetting quotes or brackets, and being forgetful of how basic functions (and yarn, lasers) work. Programmers care more about making it work eventually rather than trying to make it work the very first time. The best way to learn is by making mistakes! So don't be a scaredy-cat! The absolute worst thing that will happen is that you might have to refresh this page in your web browser if you get stuck. Don't worry though, this will happen very rarely. # The basics There is JavaScript running on this page right now. Let's play around with it a little. For the sake of simplicity I'll assume you are using Google Chrome to read this page (if you aren't it's probably easier on both of us if you follow along with Chrome). First, right click anywhere on the screen and hit Inspect Element, then click on the Console tab. You should see a thingy that looks like this: console This is a console, otherwise known as a "command line" or "terminal". Basically it's a way to type one thing at a time into a computer and immediately get the computers answer back. They are super useful as a learning tool (I still use the console nearly every day that I'm coding). The console does some pretty cool stuff. Here I have started to type something and the console is helping me out by giving me a list of all the possible things I could continue to type! Another thing you could do is type 1 + 1 into the console and then hit the Enter key and watch what happens. Using the console is a very important part of learning JavaScript. If you don't know if something works or what the command is for something, go to the console and figure it out! Here's an example: # Strings Since I am a cat I want to replace every instance of the word dog on the Internet with those blasted dogs. First go into your console and type in a few sentences that contain the word dog at least once. In JavaScript a bunch of letters, numbers, words or anything else is known as a String (as in a string of characters). Strings have to begin AND end with a quotation mark. Single ' or double " is fine, just make sure you use the same at the beginning as you do at the end. console See the nasty error message? Don't worry - you didn't break any laws. SyntaxError ILLEGAL is just the way it sounds when robots tell you that your program has a problem. The first two sentences had matching quotation marks at the beginning and end, but when I mixed single and double quotation marks it freaked out on me. OK, to fix up one of these sentences (by replacing dog with our enhanced version) we have to first save the original sentence so that we can call it up later when we do our replacing magic. Notice how the string gets repeated in red when we type it into the console? This is because we haven't told it to save the sentence anywhere so it just gives it right back (or it gives us an Error back if we messed something up). # Values and variables Values are the simplest components in JavaScript. 1 is a value, true is a value, "hello" is a value, function() {} is a value, the list goes on! There are a handful of different types of values in JavaScript but we don't need to go over them all right away — you will learn them naturally the more you code! To store values we use things called variables. The word 'variable' means 'can change' and is used because variables can store many different types of values and can change their value many times. They are pretty much like mailboxes. We put something in a variable, like our sentence, and then give the variable an address that we can use to look up the sentence later. In real life mailboxes have to have PO Box numbers but in JavaScript you usually just use lowercase letters or numbers without any spaces. console var is shorthand for variable and the = means store the thing on the right-hand side in the thing on the left-hand side. Also as you can see, now that we are storing our sentence in a variable the console doesn't just return our sentence right away, but instead gives us undefined which means there was nothing to return. If you simply type a variable name into the console it will print out the value stored in that variable. A note about variables is that by default they go away when you switch to a different page. If I were to hit the Refresh button in Chrome, for example, my dogSentence variable would get wiped and it would be like it never existed. But don't worry about this too much for now — you can just hit the up or down arrows on your keyboard while in the console to go through everything you've entered in recently. # Functions Now that we have our sentence stored in a variable, let's change a word stored in it! We can do this by performing a function. Functions are a type of value that, well, serve a specific function (AKA purpose or action) for us. Calling them "actions" sounded weird I guess so they went with the word "function" instead. JavaScript has a function called replace that does exactly what we want! Functions take in any number of values in their parentheses (zero, one or many) and return either nothing (undefined) or the changed string. The replace function is available to use on any strings and takes in two values: the characters to take out and the characters to swap in. It gets confusing to describe these things so here is a visual example: console Notice how the value of dogSentence is the same even after we run replace on it? This is because the replace function, (and most JavaScript functions for that matter) takes the value we give it and returns a new value, without modifying the value we passed in. Since we didn't store the result (there is no = on the left side of the replace function) it just printed out the return value in our console. # The "standard library" You might be wondering what other functions are available in JavaScript. The answer: A TON. There are lots built in, standard libraries that you can learn about at MDN (A site run by Mozilla that has lotsa nifty information about web technologies). For example here is the MDN page on JavaScript's Math object. # Third-party JavaScript There is also a lot of JavaScript code available that is not built in. JavaScript from third parties is usually referred to as a "library" or "plugin". One of my favorites is called Underscore.js. Let's go and grab it and load it into our page! First go to the Underscore site, http://underscorejs.org/, click on the download link (I usually use development versions because they are easier to read but both will give you the same basic functionality), and then copy all the code onto your clipboard (you can use Select All from the Edit menu to select everything). Then paste it into your console and hit enter. Now your browser has a new variable in it: _. Underscore gives you a ton of helpful functions to play with. We'll learn more about how to use them later. console # Making new functions You aren't limited to using other peoples functions — you can also write them yourself. It's pretty easy! Let's make a function called makeMoreExciting that adds a bunch of exclamation points to the end of a string. function makeMoreExciting(string) { return string + '!!!!' } In my head I read it out loud like this: "there's a function called 'make more exciting' that takes in a string and returns a new copy of that string that has a bunch of exclamation points at the end". Here is how we would write this in the console manually if we weren't using a function: console The expression string + '!!!!' returns a new string and our variable called string stays the same as before (since we never updated it to anything else with =). Let's use our function instead of doing it manually. First, paste the function into the console and then call the function by passing in a string: console You could also call the same function by passing in a variable that points to a string (in the above example we just typed the string straight in there as a value instead of saving it to a variable first): console The line makeMoreExciting(sentence) is equivalent to saying sentence + '!!!!'. What if we wanted to modify in-place (aka update) the value of sentence? Simply save the return value of the function back into our sentence variable: var sentence = "time for a nap" sentence = makeMoreExciting(sentence) Now sentence will have the exclamation marks in it! Note that you only have to use var when you are initializing a variable — the first time you ever use it. After that you shouldn't use var unless you want to re-initialize (reset/clear/empty) the variable. What would happen if we took out the return statement in our function? console Why is sentence empty? Because functions return undefined by default! You can choose to return a value by returning something. Functions should take in a value and, if they change the value or create a new value that is supposed to be used later, return a value (fun fact: a fancy term for this style is functional programming). Here is another function that doesn't return anything but instead uses a different method to show us the output: function yellIt(string) { string = string.toUpperCase() string = makeMoreExciting(string) console.log(string) } This function, yellIt, uses our previous function makeMoreExciting as well as the built-in String method toUpperCase. Methods are just a name for a function when it belongs to something — in this case toUpperCase is a function that belongs to String so we can refer to it as either a method or a function. makeMoreExciting on the other hand doesn't belong to anyone so it would be technically incorrect to refer to it as a method (confusing, I know). The last line of the function is another built-in that simply takes in any values that you give it and prints them out into the console. console So is there something wrong with the above yellIt function? It depends! Here are the two major types of functions: functions that modify or create values and return them functions take in values and perform some action that cannot be returned console.log is an example of the second type of function: it prints things out to your console — an action that you can see with your eyes but that cannot be represented as a JavaScript value. My own rule of thumb is to try to keep the two types of functions separate from each other, so here's how I would rewrite the yellIt function: function yellIt(string) { string = string.toUpperCase() return makeMoreExciting(string) } console.log(yellIt("i fear no human")) This way yellIt becomes more generic, meaning it only does one or two simple little things and doesn't know anything about printing itself to a console — that part can always be programmed later, outside the function definition. # Loops Now that we have some basic skills under our belt (Author's note: do cats even wear belts?) we can start being lazy. What?! Yes, that's right: programming is about being lazy. Larry Wall, inventor of the Perl programming language, called laziness the most important virtue of a good programmer. If computers didn't exist you would have to do all sorts of tedious tasks by hand, but if you learn to program you can lay in the sun all day while a computer somewhere runs your programs for you. It is a glorious lifestyle filled with relaxation! Loops are one of the most important ways to harness the power of a computer. Remember Underscore.js from earlier? Make sure you have it loaded in the page (remember: you can just hit the up arrow on your keyboard a few times and then hit Enter to load it in again if you need to) and try copy/pasting this into your console: function logANumber(someNumber) { console.log(someNumber) } _.times(10, logANumber) This code uses the times method of Underscore which takes in 1 number and 1 function and then starts from 0 and for 10 steps counts up by 1, calling the function with the number each step of the way. console If we were to manually write out what times is doing in the above code it would look like this: logANumber(0) logANumber(1) logANumber(2) logANumber(3) logANumber(4) logANumber(5) logANumber(6) logANumber(7) logANumber(8) logANumber(9) But cats refuse to do unnecessary manual work like this so we must always ask ourselves, "am I doing this in the laziest way possible?". So why is this called looping? Think of it like this: If we were to write out a list of 10 numbers (from 0 to 9) using a JavaScript Array it would look like this: var zeroThroughTen = [0, 1, 2, 3, 4, 5, 6, 7, 8, 9] What times really does is visit each number and repeat a task: in the example above the task was to call the logANumber function with the current number. Repeating tasks in this way is referred to as looping over the Array. # Arrays I've mentioned these a few times but let's spend a minute learning about them. Imagine you need to keep track of all your buddies. Well, an Array will do just fine. Think of an Array like a sorted list that you can keep tons of stuff in. This is how you make one: var myCatFriends = ["bill", "tabby", "ceiling"] Sweet! Now you have a list of your cat buddies. Elements (that is what you call a single item in an array) that are stored within arrays start at 0 and count up from there. So myCatFriends[0] returns bill and myCatFriends[1] returns tabby... etc etc. To get buddies out of your brand new Array you can just access an element directly like so: console.log(myCatFriends[0]) console If you made a brand new cat friend at the hippest cat club the other night and you want to add them to your list it is super simple: myCatFriends.push("super hip cat"). To check that the new cat made it into your array you can use .length: console Notice how push returned the length? Handy! Also take note that arrays will always preserve ordering which means they will remember the order in which you added or defined things. Not everything in JavaScript preserves ordering so remember this special property of Arrays! # Objects Arrays are good for lists, but for other tasks they can be hard to work with. Consider our array of cat friends. What if you also wanted to store more than just names? var myCatFriends = ["bill", "tabby", "ceiling"] var lastNames = ["the cat", "cat", "cat"] var addresses = ["The Alley", "Grandmas House", "Attic"] Sometimes it is nice to have all of the addresses or names in one variable. But sometimes you have a cat in mind, let's say Bill, and you just want to look up that cat's address. With arrays it takes a lot of work because you can't just say 'hey array, give me Bill's address' because 'Bill' is in one array and his address is in a totally different array. console This can be brittle because if our arrays change and we add a new cat to the beginning we would have to also update our billsPosition variable to point to the new location of Bill's information in the arrays! Here is a easier to maintain way to store information like this using objects: var firstCat = { name: "bill", lastName: "the cat", address: "The Alley" } var secondCat = { name: "tabby", lastName: "cat", address: "Grandmas House" } var thirdCat = { name: "ceiling", lastName: "cat", address: "Attic" } Why would we do it this way? Because now we have a variable for each cat that we can use to get that cats values in a more convenient and readable way. console You can think of Objects like keys on a keyring. Each one is for a specific door and if you have nice labels on your keys you can open doors very fast. In fact, the things on the left hand side of the : are called keys (are also known as properties) and the things on the right hand side are values. // an object with a single key 'name' and single value 'bill' { name: 'bill' } So why would you ever use arrays if you can just put your data in objects? Because objects don't remember the order of the keys that you set. You might enter in an object like this: { date: "10/20/2012", diary: "slept a bit today", name: "Charles" } But the computer could give it back to you like this: { diary: "slept a bit today", name: "Charles", date: "10/20/2012" } Or like this! { name: "Charles", diary: "slept a bit today", date: "10/20/2012" } So you can't ever trust the order of keys in objects. If you wanna get REALLY fancy you can make an array filled with objects, or an object filled with arrays! var moodLog = [ { date: "10/20/2012", mood: "catnipped" }, { date: "10/21/2012", mood: "nonplussed" }, { date: "10/22/2012", mood: "purring" } ] // ordered from least to most favorite var favorites = { treats: ["bird sighting", "belly rub", "catnip"], napSpots: ["couch", "planter box", "human face"] } When you combine different things like this you are making data structures, just like legos! # Callbacks Callbacks aren't really a feature of JavaScript like Object or Array, but instead just a certain way to use functions. To understand why callbacks are useful you first have to learn about asynchronous (often shortened to async) programming. Asynchronous code by definition is code written in a way that is not synchronous. Synchronous code is easy to understand and write. Here is an example to illustrate: var photo = download('http://foo-chan.com/images/sp.jpg') uploadPhotoTweet(photo, '@maxogden') This synchronous pseudo-code downloads an adorable cat photo and then uploads the photo to twitter and tweets the photo at @maxogden. Pretty straightforward! (Author's note: I @maxogden do happily accept random cat photo tweets) This code is synchronous because in order for photo to get uploaded to the tweet, the photo download must be completed. This means that line 2 cannot run until the task on line 1 is totally finished. If we were to actually implement this pseudo-code we would want to make sure that download 'blocked' execution until the download was finished, meaning it would prevent any other JavaScript from being executed until it finished, and then when the download completes it would un-block the JavaScript execution and line 2 would execute. Synchronous code is fine for things that happen fast, but it's horrible for things that require saving, loading, downloading or uploading. What if the server you're downloading the photo from is slow, or the internet connection you are using is slow, or the computer you are running the code on has too many youtube cat video tabs open and is running slowly? It means that it could potentially take minutes of waiting before line 2 gets around to running. Meanwhile, because all JavaScript on the page is being blocked from being run while the download is happening, the webpage would totally freeze up and become unresponsive until the download is done. Blocking execution should be avoided at all costs, especially when doing so makes your program freeze up or become unresponsive. Let's assume the photo above takes one second to download. To illustrate how long one second is to a modern computer, here is a program that tests to see how many tasks JavaScript can process in one second. function measureLoopSpeed() { var count = 0 function addOne() { count = count + 1 } // Date.now() returns a big number representing the number of // milliseconds that have elapsed since Jan 01 1970 var now = Date.now() // Loop until Date.now() is 1000 milliseconds (1 second) or more into // the future from when we started looping. On each loop, call addOne while (Date.now() - now < 1000) addOne() // Finally it has been >= 1000ms, so let's print out our total count console.log(count) } measureLoopSpeed() Copy-paste the above code into your JavaScript console and after one second it should print out a number. On my computer I got 8527360, approximately 8.5 million. In one second JavaScript can call the addOne function 8.5 million times! So if you have synchronous code for downloading a photo, and the photo download takes one second, it means you are potentially preventing 8.5 million operations from happening while JavaScript execution is blocked. Some languages have a function called sleep that blocks execution for some number of seconds. For example here is some bash code running in Terminal.app on Mac OS that uses sleep. When you run the command sleep 3 && echo 'done sleeping now' it blocks for 3 seconds before printing out done sleeping now. console JavaScript doesn't have a sleep function. Since you are a cat you are probably asking yourself, "Why am I learning a programming language that does not involve sleeping?". But stay with me. Instead of relying on sleep to wait for things to happen the design of JavaScript encourages use of functions instead. If you have to wait for task A to finish before doing task B, you put all of the code for task B into a function and you only call that function when A is done. For example, this is blocking-style code: a() b() And this is in a non-blocking style: a(b) In the non-blocking version b is a callback to a. In the blocking version a and b are both called/invoked (they both have () after them which executes the functions immediately). In the non-blocking version you will notice that only a gets invoked, and b is simply passed in to a as an argument. In the blocking version, there is no explicit relationship between a and b. In the non-blocking version it becomes a's job to do what it needs to do and then call b when it is done. Using functions in this way is called callbacks because your callback function, in this case b, gets called later on when a is all done. Here is a pseudocode implementation of what a might look like: function a(done) { download('https://pbs.twimg.com/media/B4DDWBrCEAA8u4O.jpg:large', function doneDownloading(error, png) { // handle error if there was one if (err) console.log('uh-oh!', error) // call done when you are all done done() }) } Think back to our non-blocking example, a(b), where we call a and pass in b as the first argument. In the function definition for a above the done argument is our b function that we pass in. This behavior is something that is hard to wrap your head around at first. When you call a function, the arguments you pass in won't have the same variable names when they are in the function. In this case what we call b is called done inside the function. But b and done are just variable names that point to the same underlying function. Usually callback functions are labelled something like done or callback to make it clear that they are functions that should be called when the current function is done. So, as long as a does it's job and called b when it is done, both a and b get called in both the non-blocking and blocking versions. The difference is that in the non-blocking version we don't have to halt execution of JavaScript. In general non-blocking style is where you write every function so that it can return as soon as possible, without ever blocking. To drive the point home even further: If a takes one second to complete, and you use the blocking version, it means you can only do one thing. If you use the non-blocking version (aka use callbacks) you can do literally millions of other things in that same second, which means you can finish your work millions of times faster and sleep the rest of the day. Remember: programming is all about laziness and you should be the one sleeping, not your computer. Hopefully you can see now that callbacks are just functions that call other functions after some asynchronous task. Common examples of asynchronous tasks are things like reading a photo, downloading a song, uploading a picture, talking to a database, waiting for a user to hit a key or click on someone, etc. Anything that takes time. JavaScript is really great at handling asynchronous tasks like these as long as you take the time to learn how to use callbacks and keep your JavaScript from being blocked. The end! This is just the beginning of your relationship with JavaScript! You can't learn it all at once, but you should find what works for you and try to learn all of the concepts here. I'd recommend coming back again tomorrow and going through the entire thing again from the beginning! It might take a few times through before you get everything (programming is hard). Just try to avoid reading this page in any rooms that contain shiny objects . . . they can be incredibly distracting. Got another topic you wanna see covered? Open an issue for it on github. # Recommended reading JavaScript For Cats skips over lots of details that aren't important for getting started (cats are not known for their attention spans), but if you feel like you need to dive in deeper then check these out: NodeSchool.io is a community driven, open source educational software that teaches various web development skills in an interactive, self-guided format. I helped make NodeSchool! Sadly it features fewer cats than this page. Eloquent Javascript is a free book that teaches you JavaScript! It's pretty good! Especially the chapter on values, variables, and control flow Mozilla's JavaScript Guide also has a pretty sweet intro chapter called values, variables and literals standard JS Style Guide is a "zero configuration" linter for JS style that I use Let's Write Code by @shama a great series of YouTube coding tutorials made by a friend of mine # Satisfied customers satisfied customer satisfied customer satisfied customer satisfied customer satisfied customer JSForCats.com is a labor of love and work in progress by @maxogden. If you would like to contribute and make this tutorial better there is a Github repo right over here. console @ 8cb60e21:5f2deaea
2024-09-06 22:23:03<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-06 22:23:03<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 472f440f:5669301e
2024-09-06 21:56:48I had the pleasure of sitting back down with Will Reeves, Founder and CEO of Fold, on TFTC last week to discuss Fold's journey from a startup to (soon to be) a publicly listed company. I particularly liked this conversation because it was a great lens into the grit it takes to run a successful bitcoin company. https://fountain.fm/episode/1FrspxmpK5bsoReGx73n Building a successful company is extremely hard in its own right. Building a successful bitcoin company is significantly harder considering the fact that you're building a company in parallel with a nascent and volatile monetary asset that is monetizing in real time. Bitcoin adoption comes in waves. People flood in when the price is ripping and fade out when the price corrects and goes into a multi-year bear market before the tide comes back in. This means that your potential user base is expanding and contracting more than it would be in other industries. As a company you need to be able to absorb the incoming waves of new adopters and then capture and retain the users who stick around for the bear market. To do this correctly, a founder and their team needs to thread many needles. First, can you assemble a team that can actually build something? Second, can you bring a product to market that people actually use because it provides value to them? Third, can you stick out against the crowd? So on and so forth. One of the most important aspects of building a bitcoin company during bitcoin's monetization phase is timing. There are many great ideas that people have in terms of companies, products and tools that can built using bitcoin. There are sci-fi futures that can be built today on bitcoin if people really wanted to. The problem that arises is that adoption and understanding of bitcoin are at a point where, even though a functional product could be brought to market, it won't be adopted by a large number of people because there 1.) aren't enough people who would understand how to use it and 2.) for the people who do understand how to use it and could benefit from it, the universe of people they can interact with using that product is minuscule. Timing is everything. And I think Fold nailed the timing of their product. Allowing people to passively stack sats by offering a product that enables them to go about their daily spending and get sats back instead of cash back rewards is a great first-touch bitcoin experience. Once Fold found their sticky user base and perfected their sats back experience, they began expanding their product offering to provide their users with more bitcoin services. Buy/sell bitcoin in-app, bill pay for sats back, and more. They'll eventually roll out a credit card and additional financial services. Start simple, provide something of value, nail the timing and then expand from there. That seems to be the recipe. For any founders in the space reading this, I highly recommend you listen to the episode. Particularly for the advice Will gives about knowing when to sprint on product and when to lean into growth. Bear markets are for building and bull markets are for casting the widest net possible and capturing as many new users as possible. At Ten31 we are extremely proud to back Fold and a number of other companies in the bitcoin space that understand the intricacies described above. We work with some of the best founders in the world. Founders who know how to eat glass with the best of them. Bitcoin can be a cruel mistress and no one knows that more intimately than the founders building bitcoin companies. --- Final thought... The NFL having a week 1 game in Brazil should get Roger Godell fired. Enjoy your weekend, freaks.
@ 472f440f:5669301e
2024-09-06 21:56:48I had the pleasure of sitting back down with Will Reeves, Founder and CEO of Fold, on TFTC last week to discuss Fold's journey from a startup to (soon to be) a publicly listed company. I particularly liked this conversation because it was a great lens into the grit it takes to run a successful bitcoin company. https://fountain.fm/episode/1FrspxmpK5bsoReGx73n Building a successful company is extremely hard in its own right. Building a successful bitcoin company is significantly harder considering the fact that you're building a company in parallel with a nascent and volatile monetary asset that is monetizing in real time. Bitcoin adoption comes in waves. People flood in when the price is ripping and fade out when the price corrects and goes into a multi-year bear market before the tide comes back in. This means that your potential user base is expanding and contracting more than it would be in other industries. As a company you need to be able to absorb the incoming waves of new adopters and then capture and retain the users who stick around for the bear market. To do this correctly, a founder and their team needs to thread many needles. First, can you assemble a team that can actually build something? Second, can you bring a product to market that people actually use because it provides value to them? Third, can you stick out against the crowd? So on and so forth. One of the most important aspects of building a bitcoin company during bitcoin's monetization phase is timing. There are many great ideas that people have in terms of companies, products and tools that can built using bitcoin. There are sci-fi futures that can be built today on bitcoin if people really wanted to. The problem that arises is that adoption and understanding of bitcoin are at a point where, even though a functional product could be brought to market, it won't be adopted by a large number of people because there 1.) aren't enough people who would understand how to use it and 2.) for the people who do understand how to use it and could benefit from it, the universe of people they can interact with using that product is minuscule. Timing is everything. And I think Fold nailed the timing of their product. Allowing people to passively stack sats by offering a product that enables them to go about their daily spending and get sats back instead of cash back rewards is a great first-touch bitcoin experience. Once Fold found their sticky user base and perfected their sats back experience, they began expanding their product offering to provide their users with more bitcoin services. Buy/sell bitcoin in-app, bill pay for sats back, and more. They'll eventually roll out a credit card and additional financial services. Start simple, provide something of value, nail the timing and then expand from there. That seems to be the recipe. For any founders in the space reading this, I highly recommend you listen to the episode. Particularly for the advice Will gives about knowing when to sprint on product and when to lean into growth. Bear markets are for building and bull markets are for casting the widest net possible and capturing as many new users as possible. At Ten31 we are extremely proud to back Fold and a number of other companies in the bitcoin space that understand the intricacies described above. We work with some of the best founders in the world. Founders who know how to eat glass with the best of them. Bitcoin can be a cruel mistress and no one knows that more intimately than the founders building bitcoin companies. --- Final thought... The NFL having a week 1 game in Brazil should get Roger Godell fired. Enjoy your weekend, freaks. @ e83b66a8:b0526c2b
2024-09-06 19:16:04The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud. Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data. There is a different way. NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol. The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms. Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid. Secondly as a user, you don’t have an account, you have a private key which is used to secure your data. Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key. Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays. All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it. Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key. Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content. Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions. Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant. As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models. The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not. NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment. From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed. While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops. If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here: https://primal.net/downloads It will create a private key for you and setup a Bitcoin wallet. Once you have done this you can visit me here: nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already. NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here: nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Or you can see his account like this: https://primal.net/jack Edward Snowden is also on the platform and you can find him here: https://primal.net/Snowden NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation. Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/ Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus or Amethyst for Android: https://nostrapps.com/amethyst The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it. Some of the more interesting projects right now are: https://www.0xchat.com/#/ – Private messaging – think WhatsApp https://zap.stream/ – Video streaming https://fountain.fm/ – Podcasting https://wavlake.com/ – Music streaming https://shopstr.store/ – Online shop https://npub.pro/ – Website creation tool https://nostr.build/ – Media and file storage https://relay.tools/ – Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user – Creator tools Remember, the same keys you created for Primal can be used across the whole ecosystem. If you want to see some of the other apps that have been built on the NOSTR protocol visit: https://nostrapps.com/
@ e83b66a8:b0526c2b
2024-09-06 19:16:04The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud. Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data. There is a different way. NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol. The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms. Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid. Secondly as a user, you don’t have an account, you have a private key which is used to secure your data. Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key. Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays. All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it. Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key. Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content. Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions. Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant. As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models. The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not. NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment. From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed. While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops. If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here: https://primal.net/downloads It will create a private key for you and setup a Bitcoin wallet. Once you have done this you can visit me here: nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already. NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here: nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Or you can see his account like this: https://primal.net/jack Edward Snowden is also on the platform and you can find him here: https://primal.net/Snowden NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation. Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/ Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus or Amethyst for Android: https://nostrapps.com/amethyst The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it. Some of the more interesting projects right now are: https://www.0xchat.com/#/ – Private messaging – think WhatsApp https://zap.stream/ – Video streaming https://fountain.fm/ – Podcasting https://wavlake.com/ – Music streaming https://shopstr.store/ – Online shop https://npub.pro/ – Website creation tool https://nostr.build/ – Media and file storage https://relay.tools/ – Build and curate your own relay https://creatr.nostr.wine/subscriptions/new-user – Creator tools Remember, the same keys you created for Primal can be used across the whole ecosystem. If you want to see some of the other apps that have been built on the NOSTR protocol visit: https://nostrapps.com/ @ ffd375eb:4529ed08
2024-09-06 15:39:31## Chef's notes Watch the video 🇫🇷: https://youtu.be/cYl4Lb0vbyc ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 3 months - 🍽️ Servings: Many ## Ingredients - 1 fennel bulb - 1 large onion - 3 garlic cloves - 1/2 tsp salt per fennel bulb - 1 tbsp turmeric powder per fennel bulb - 1 tbsp oil per fennel bulb - 1 tsp black pepper per fennel bulb - 1 tbsp honey per fennel bulb ## Directions 1. Thinly slice the fennel bulb, onion, and garlic using a mandoline slicer. 2. In a bowl, mix the sliced fennel, onion, garlic, and salt. Let sit for a bit to allow the salt to act on the ingredients. 3. In a separate bowl, mix the turmeric, oil, black pepper, and honey to make a sauce. 4. Combine the fennel, onion, garlic mixture with the turmeric sauce and mix well.
@ ffd375eb:4529ed08
2024-09-06 15:39:31## Chef's notes Watch the video 🇫🇷: https://youtu.be/cYl4Lb0vbyc ## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 3 months - 🍽️ Servings: Many ## Ingredients - 1 fennel bulb - 1 large onion - 3 garlic cloves - 1/2 tsp salt per fennel bulb - 1 tbsp turmeric powder per fennel bulb - 1 tbsp oil per fennel bulb - 1 tsp black pepper per fennel bulb - 1 tbsp honey per fennel bulb ## Directions 1. Thinly slice the fennel bulb, onion, and garlic using a mandoline slicer. 2. In a bowl, mix the sliced fennel, onion, garlic, and salt. Let sit for a bit to allow the salt to act on the ingredients. 3. In a separate bowl, mix the turmeric, oil, black pepper, and honey to make a sauce. 4. Combine the fennel, onion, garlic mixture with the turmeric sauce and mix well. @ 3bf0c63f:aefa459d
2024-09-06 12:49:46# Nostr: a quick introduction, attempt #2 Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else. Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services. (Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation). More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46# Nostr: a quick introduction, attempt #2 Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else. Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services. (Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation). More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between _clients_ (i.e. the program that runs on a user computer) and _relays_ (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback". @ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes. In any event, it was an okay game, not great, but there were some interesting takeaways. - Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff. - Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask. - Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.) - Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more. - Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot. - Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown. - Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though. - Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game. - Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role. - After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG. - You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night.
@ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I *thought* I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes. In any event, it was an okay game, not great, but there were some interesting takeaways. - Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff. - Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask. - Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.) - Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more. - Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot. - Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown. - Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though. - Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game. - Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role. - After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG. - You have to love [Steak League IDP Roquan Smith](https://www.realmansports.com/p/steak-league-879) getting a pick for you opening night. @ c7eadcf0:7821e562
2024-09-06 00:10:23Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck. Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis. Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin. This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite? Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out.
@ c7eadcf0:7821e562
2024-09-06 00:10:23Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck. Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis. Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin. This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite? Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out. @ 472f440f:5669301e
2024-09-05 22:25:15[https://x.com/parkeralewis/status/1831746160781938947]() Here's a startling chart from an American staple, Walgreens. The convenience store and pharmacy chain has seen its stock price plummet by more than 67% this year and by more than 90% from its all time high, which was reached in 2015. The combination of the COVID lock downs and the lax laws around theft that followed were materially detrimental to Walgreens business. The crux of their problem at the moment, however, is a double whammy of those disruptions in their business coupled with the "higher for longer" interest rate policy from the Fed over the last couple of years. As Tuur points out in the tweet above, Walgreens has $34B in debt, which means they definitely have significant interest rate payments they need to make on a monthly basis. Tuur also points out that Walgreens has very little cash compared to their debt obligations. Let's take a look at their balance sheet as of May of this year. ![https://www.tftc.io/content/images/2024/09/Screenshot-2024-09-05-at-3.59.46-PM.png]() Less than $1B in cash for $34B debt with $67.56B in total liabilities. Even worse, their cash balance was drained by more than 27% over the course of the year between May 2023 and May 2024. As you may notice their total assets fell by more than 15% over the same period. This is because Walgreens understands the dire financial straits it finds itself in and has begun shutting down thousands of their locations across the country. ![https://www.tftc.io/content/images/2024/09/Screenshot-2024-09-05-at-4.49.58-PM.png]() The recent efforts of Walgreens to sell off their assets to raise cash to pay down their debts seem to be completely ineffective as their cash balance is falling faster than their total assets, which is falling 7x faster than their total liabilities. These numbers are most definitely going to get worse as cascading sell pressure in commercial real estate markets (which is the bucket that Walgreens locations fall into) drive down the value of their assets. Leaving them with less cash to pay down their debts as time goes on. To make matters worse, it puts the institutions that lent money to Walgreens in a terrible position. How many commercial and investment banks has Walgreens tapped to fund their operations with expensive debt? How exposed to Walgreens is any individual lender? Could a default on some or all of their loans catch these financial institutions off sides? If it isn't Walgreens that pushes them off sides, how many more bad borrowers would it take to push them off sides? As our good friend Parker Lewis points out, the only way the hemorrhaging can be stopped is if the Federal Reserve and Federal Government step in with bail outs in the form of massive liquidity injections via quantitative easing and other emergency measures. On top of this, the Fed and the Federal Government find themselves in a classic catch-22. If they let Walgreens fall into bankruptcy it could set off a domino effect that could exacerbate inflation. Riteaid, a similar retail convenience store and pharmacy chain, filed for bankruptcy last October and is still wading its way through that process. Part of that process has been shuttering many of their storefronts. One has to imagine that since Walgreens and Riteaid are having these problems, some of their other competitors must be feeling the pain as well. If enough of these convenience stores, which tens of millions of Americans depend on for everyday goods, find themselves in a position where they have to shut down their stores it could lead to a supply crunch. People will obviously not be able to get their goods from Riteaid or Walgreens and will flee to alternatives, exacerbating the stress on their supplies, which will drive prices higher. This is a catch-22 because the only way to avoid this mad dash for consumer goods in the midst of a convenience store Armageddon is to re-introduce ZIRP and flood the market with freshly printed dollars, which will drive prices up as well. Talk about a rock and a hard place. You better get yourself some bitcoin. --- Final thought... Zach Bryan radio crushes.
@ 472f440f:5669301e
2024-09-05 22:25:15[https://x.com/parkeralewis/status/1831746160781938947]() Here's a startling chart from an American staple, Walgreens. The convenience store and pharmacy chain has seen its stock price plummet by more than 67% this year and by more than 90% from its all time high, which was reached in 2015. The combination of the COVID lock downs and the lax laws around theft that followed were materially detrimental to Walgreens business. The crux of their problem at the moment, however, is a double whammy of those disruptions in their business coupled with the "higher for longer" interest rate policy from the Fed over the last couple of years. As Tuur points out in the tweet above, Walgreens has $34B in debt, which means they definitely have significant interest rate payments they need to make on a monthly basis. Tuur also points out that Walgreens has very little cash compared to their debt obligations. Let's take a look at their balance sheet as of May of this year. ![https://www.tftc.io/content/images/2024/09/Screenshot-2024-09-05-at-3.59.46-PM.png]() Less than $1B in cash for $34B debt with $67.56B in total liabilities. Even worse, their cash balance was drained by more than 27% over the course of the year between May 2023 and May 2024. As you may notice their total assets fell by more than 15% over the same period. This is because Walgreens understands the dire financial straits it finds itself in and has begun shutting down thousands of their locations across the country. ![https://www.tftc.io/content/images/2024/09/Screenshot-2024-09-05-at-4.49.58-PM.png]() The recent efforts of Walgreens to sell off their assets to raise cash to pay down their debts seem to be completely ineffective as their cash balance is falling faster than their total assets, which is falling 7x faster than their total liabilities. These numbers are most definitely going to get worse as cascading sell pressure in commercial real estate markets (which is the bucket that Walgreens locations fall into) drive down the value of their assets. Leaving them with less cash to pay down their debts as time goes on. To make matters worse, it puts the institutions that lent money to Walgreens in a terrible position. How many commercial and investment banks has Walgreens tapped to fund their operations with expensive debt? How exposed to Walgreens is any individual lender? Could a default on some or all of their loans catch these financial institutions off sides? If it isn't Walgreens that pushes them off sides, how many more bad borrowers would it take to push them off sides? As our good friend Parker Lewis points out, the only way the hemorrhaging can be stopped is if the Federal Reserve and Federal Government step in with bail outs in the form of massive liquidity injections via quantitative easing and other emergency measures. On top of this, the Fed and the Federal Government find themselves in a classic catch-22. If they let Walgreens fall into bankruptcy it could set off a domino effect that could exacerbate inflation. Riteaid, a similar retail convenience store and pharmacy chain, filed for bankruptcy last October and is still wading its way through that process. Part of that process has been shuttering many of their storefronts. One has to imagine that since Walgreens and Riteaid are having these problems, some of their other competitors must be feeling the pain as well. If enough of these convenience stores, which tens of millions of Americans depend on for everyday goods, find themselves in a position where they have to shut down their stores it could lead to a supply crunch. People will obviously not be able to get their goods from Riteaid or Walgreens and will flee to alternatives, exacerbating the stress on their supplies, which will drive prices higher. This is a catch-22 because the only way to avoid this mad dash for consumer goods in the midst of a convenience store Armageddon is to re-introduce ZIRP and flood the market with freshly printed dollars, which will drive prices up as well. Talk about a rock and a hard place. You better get yourself some bitcoin. --- Final thought... Zach Bryan radio crushes. @ acc925af:db9fb0bb
2024-09-05 20:26:50While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good **Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:** # Prerequisites: 1. Twitter Developer Account 2. Nostr Wallet with NWC support (e.g., Alby, Nostrify) 3. Twitter API credentials (API key, API secret key, Access token, Access token secret) 4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library) ### Step 1: Set up Twitter API credentials > Create a Twitter Developer account and obtain API credentials > Install Tweepy using pip: pip install tweepy ### Step 2: Connect Nostr Wallet using NWC > Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify) > Set up the wallet and obtain the NWC credentials (e.g., public key, private key) ### Step 3: Create a Python script > Import Tweepy and nostr-client libraries > Authenticate with Twitter API using Tweepy > Connect to Nostr Wallet using NWC credentials > Define a function to send 21 satoshis for every like > Use Tweepy to stream likes and trigger the payment function `Python` script: ``` import tweepy from nostr_client import Client # Twitter API credentials twitter_api_key = "YOUR_API_KEY" twitter_api_secret_key = "YOUR_API_SECRET_KEY" twitter_access_token = "YOUR_ACCESS_TOKEN" twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET" # Nostr Wallet NWC credentials nwc_public_key = "YOUR_NWC_PUBLIC_KEY" nwc_private_key = "YOUR_NWC_PRIVATE_KEY" # Set up Tweepy auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key) auth.set_access_token(twitter_access_token, twitter_access_token_secret) api = tweepy.API(auth) # Set up Nostr Client nwc_client = Client() nwc_client.connect(nwc_public_key, nwc_private_key) # Define payment function def send_satoshis(): # Create a new Nostr event with 21 satoshis event = nwc_client.create_event(21) # Send the event to the Nostr network nwc_client.send_event(event) # Stream likes and trigger payment function class LikeStream(tweepy.StreamListener): def on_like(self, like): send_satoshis() stream = tweepy.Stream(auth, LikeStream()) stream.filter(track=["likes"]) ``` ##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._ originally posted at https://stacker.news/items/673795
@ acc925af:db9fb0bb
2024-09-05 20:26:50While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good **Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:** # Prerequisites: 1. Twitter Developer Account 2. Nostr Wallet with NWC support (e.g., Alby, Nostrify) 3. Twitter API credentials (API key, API secret key, Access token, Access token secret) 4. Python script with Tweepy (Twitter API library) and nostr-client (Nostr library) ### Step 1: Set up Twitter API credentials > Create a Twitter Developer account and obtain API credentials > Install Tweepy using pip: pip install tweepy ### Step 2: Connect Nostr Wallet using NWC > Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify) > Set up the wallet and obtain the NWC credentials (e.g., public key, private key) ### Step 3: Create a Python script > Import Tweepy and nostr-client libraries > Authenticate with Twitter API using Tweepy > Connect to Nostr Wallet using NWC credentials > Define a function to send 21 satoshis for every like > Use Tweepy to stream likes and trigger the payment function `Python` script: ``` import tweepy from nostr_client import Client # Twitter API credentials twitter_api_key = "YOUR_API_KEY" twitter_api_secret_key = "YOUR_API_SECRET_KEY" twitter_access_token = "YOUR_ACCESS_TOKEN" twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET" # Nostr Wallet NWC credentials nwc_public_key = "YOUR_NWC_PUBLIC_KEY" nwc_private_key = "YOUR_NWC_PRIVATE_KEY" # Set up Tweepy auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key) auth.set_access_token(twitter_access_token, twitter_access_token_secret) api = tweepy.API(auth) # Set up Nostr Client nwc_client = Client() nwc_client.connect(nwc_public_key, nwc_private_key) # Define payment function def send_satoshis(): # Create a new Nostr event with 21 satoshis event = nwc_client.create_event(21) # Send the event to the Nostr network nwc_client.send_event(event) # Stream likes and trigger payment function class LikeStream(tweepy.StreamListener): def on_like(self, like): send_satoshis() stream = tweepy.Stream(auth, LikeStream()) stream.filter(track=["likes"]) ``` ##### _Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended._ originally posted at https://stacker.news/items/673795 @ e968e50b:db2a803a
2024-09-05 19:33:33ATTENTION PARENTS! I have revamped my LNBITS [bitcoin piggy bank](http://bitcoinpiggybank.vercel.app) so you don't need to deploy it yourself. Check it out at http://bitcoinpiggybank.vercel.app. All you need now is a LNBITS wallet. I've deployed a website that you can just log into with that and nothing else. I'm thinking about actually renting out my own domain for this one if people find it useful. https://www.youtube.com/watch?v=X-MNqJiLCM4 Teach your kids about sound money while they're actually stacking sats and using a fun interface. originally posted at https://stacker.news/items/673739
@ e968e50b:db2a803a
2024-09-05 19:33:33ATTENTION PARENTS! I have revamped my LNBITS [bitcoin piggy bank](http://bitcoinpiggybank.vercel.app) so you don't need to deploy it yourself. Check it out at http://bitcoinpiggybank.vercel.app. All you need now is a LNBITS wallet. I've deployed a website that you can just log into with that and nothing else. I'm thinking about actually renting out my own domain for this one if people find it useful. https://www.youtube.com/watch?v=X-MNqJiLCM4 Teach your kids about sound money while they're actually stacking sats and using a fun interface. originally posted at https://stacker.news/items/673739 @ 469fa704:2b6cb760
2024-09-05 15:06:49## The Evolution of Web 3.0: Bitcoin's Role in Decentralizing the Internet ### Introduction to Web 3.0 Web 3.0, often referred to as the decentralized web, represents the next phase in the evolution of the internet. Unlike its predecessors, Web 3.0 aims to redistribute control from centralized entities back to individual users through technologies like blockchain, cryptocurrencies, and decentralized applications (dApps). This shift promises a more democratic internet where users control their data, identity, and digital destiny. ## The Bitcoin Protocol: A Foundation for Web 3.0 ### Bitcoin's Influence on Decentralization Bitcoin, introduced in 2008, can be seen as a precursor to Web 3.0 due to its decentralized nature. The Bitcoin protocol introduced the world to blockchain technology, a decentralized ledger that records all transactions across a network of computers. This technology underpins Web 3.0's ethos by: * **Promoting Decentralization**: Bitcoin's network operates without a central authority, showcasing how internet services could run on similar principles, reducing the power of centralized tech giants. * **Enhancing Security and Privacy**: Through cryptographic means, Bitcoin ensures that transactions are secure and pseudonymus, a feature integral to Web 3.0's vision of user-controlled data. ### Scalability and Functionality Challenges However, Bitcoin's protocol wasn't designed on the base layer with the complex applications of Web 3.0 in mind. Its primary function as a digital currency means: * **Scalability Issues**: Bitcoin's blockchain has limitations in transaction speed and volume, which might not suffice for a fully realized Web 3.0 environment where millions of micro-transactions could occur seamlessly. * **Limited Smart Contract Capabilities**: Bitcoin's scripting language isn't as versatile as platforms like Ethereum, which are designed to support a broader range of decentralized applications. ### Expanding Bitcoin's Role with Layer 2 Solutions To bridge these gaps, developers are working on Layer 2 solutions like the Lightning Network for faster transactions, and projects like Stacks aim to bring smart contract functionality directly to Bitcoin. These innovations suggest that while Bitcoin might not be the sole backbone of Web 3.0 yet, it can significantly contribute to its infrastructure. In the long term, the question is whether we need more than one network, I mean, we don't have multiple Internets today. The market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that. ## Web 3.0 Beyond Bitcoin ### A Broader Blockchain Ecosystem At the moment Web 3.0 encompasses by far more than just Bitcoin. It includes: * **Ethereum and Smart Contracts**: Ethereum's introduction of smart contracts has been pivotal, allowing for decentralized applications that can interact in complex ways, far beyond simple transactions. * **Other Blockchains**: Platforms like Solana, Sui, and Near are gaining traction for their high throughput and lower costs, addressing some of Bitcoin's limitations on the base layer. ## The Cultural and Economic Shift The move towards Web 3.0 isn't just technological but cultural. There's a growing sentiment, reflected in posts on platforms like X, that users are ready for a change where they own their digital presence. Here's some background based on general knowledge and trends up to 2024: ### Cultural Shift: * **Distrust in Centralized Institutions**: There's been a growing distrust in traditional centralized institutions like banks, governments, and large corporations. This distrust stems from various scandals, data breaches, privacy concerns, and perceived inefficiencies or corruption. Posts on platforms like X or even more on Nostr reflect this sentiment, where users often discuss the diminishing trust in these institutions. * **Rise of Individual Empowerment**: Culturally, there's a move towards empowerment of the individual, facilitated by technology. Social media, blockchain, and other decentralized technologies give individuals tools to bypass traditional gatekeepers in finance, media, and more. This shift champions the idea that individuals should have more control over their data, finances, and digital identity. * **Identity and Community**: Decentralization also touches on identity politics and community governance. There's a trend towards localism or regionalism where communities seek more control over their governance, which can be seen in movements for local autonomy or even secessionist sentiments in various parts of the world. * **Cultural Movements**: Movements like the maker culture, DIY (Do It Yourself), open-source software, and even the gig economy reflect a cultural shift towards decentralization where individuals or small groups can produce, create, or work independently of large entities. ### Economic Shift: * **Decentralized Finance (DeFi)**: DeFi represents one of the most tangible shifts, aiming to recreate and potentially improve financial systems outside of traditional banking. This includes lending, borrowing, and earning interest in a trustless, permissionless environment, primarily using blockchain technology. * **Cryptocurrencies and Tokenization**: The rise of cryptocurrencies like Bitcoin and Ethereum symbolizes a move away from centralized monetary systems. Tokenization of assets, from art (NFTs - Non-Fungible Tokens) to real estate, embodies this shift, allowing for fractional ownership and reducing the barriers to investment. * **Globalization vs. Localism**: While globalization has interconnected economies, there's a counter-trend where economic decentralization supports local economies. This can be seen in the push for local currencies, community-supported agriculture, or local energy production like solar microgrids. * **Work and Employment**: The gig economy, remote work, and digital nomadism are part of this economic shift. Platforms enabling freelance work decentralize employment, moving away from traditional office environments and 9-to-5 jobs. ### General Observations: * **Technology as an Enabler**: Blockchain, the internet, and advancements in communication technology are pivotal in this shift. They provide the infrastructure necessary for decentralization to occur at scale. * **Political Implications**: Economically, this shift maybe challenges existing power structures, potentially leading to regulatory battles as seen with cryptocurrencies. Culturally, it might lead to a redefinition of nationalism, community, and individual rights in the digital age. * **Challenges**: Despite its promise, decentralization faces hurdles like scalability issues, regulatory pushback, the digital divide, and the potential for new forms of centralization (e.g., large crypto exchanges becoming new central authorities). ## Conclusion: Bitcoin's Place in Web 3.0 Bitcoin's protocol ignited the spark for a decentralized internet, but Web 3.0 is evolving into a multifaceted ecosystem where Bitcoin might play a crucial, though not yet exclusive, role. The integration of Bitcoin with newer technologies and platforms could see it becoming a fundamental layer in the Web 3.0 stack, particularly in areas of value transfer and as a store of value within decentralized finance (DeFi). As we progress, the synergy between Bitcoin's proven security and stability, combined with the innovation of other blockchain technologies, might just be the blend needed for Web 3.0 to achieve mainstream adoption, ensuring the internet becomes more open, secure, and user-centric. *As stated before, the market will probably decide in favor of the strongest and most secure network, and **Bitcoin** is by far that.*
@ 469fa704:2b6cb760
2024-09-05 15:06:49## The Evolution of Web 3.0: Bitcoin's Role in Decentralizing the Internet ### Introduction to Web 3.0 Web 3.0, often referred to as the decentralized web, represents the next phase in the evolution of the internet. Unlike its predecessors, Web 3.0 aims to redistribute control from centralized entities back to individual users through technologies like blockchain, cryptocurrencies, and decentralized applications (dApps). This shift promises a more democratic internet where users control their data, identity, and digital destiny. ## The Bitcoin Protocol: A Foundation for Web 3.0 ### Bitcoin's Influence on Decentralization Bitcoin, introduced in 2008, can be seen as a precursor to Web 3.0 due to its decentralized nature. The Bitcoin protocol introduced the world to blockchain technology, a decentralized ledger that records all transactions across a network of computers. This technology underpins Web 3.0's ethos by: * **Promoting Decentralization**: Bitcoin's network operates without a central authority, showcasing how internet services could run on similar principles, reducing the power of centralized tech giants. * **Enhancing Security and Privacy**: Through cryptographic means, Bitcoin ensures that transactions are secure and pseudonymus, a feature integral to Web 3.0's vision of user-controlled data. ### Scalability and Functionality Challenges However, Bitcoin's protocol wasn't designed on the base layer with the complex applications of Web 3.0 in mind. Its primary function as a digital currency means: * **Scalability Issues**: Bitcoin's blockchain has limitations in transaction speed and volume, which might not suffice for a fully realized Web 3.0 environment where millions of micro-transactions could occur seamlessly. * **Limited Smart Contract Capabilities**: Bitcoin's scripting language isn't as versatile as platforms like Ethereum, which are designed to support a broader range of decentralized applications. ### Expanding Bitcoin's Role with Layer 2 Solutions To bridge these gaps, developers are working on Layer 2 solutions like the Lightning Network for faster transactions, and projects like Stacks aim to bring smart contract functionality directly to Bitcoin. These innovations suggest that while Bitcoin might not be the sole backbone of Web 3.0 yet, it can significantly contribute to its infrastructure. In the long term, the question is whether we need more than one network, I mean, we don't have multiple Internets today. The market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that. ## Web 3.0 Beyond Bitcoin ### A Broader Blockchain Ecosystem At the moment Web 3.0 encompasses by far more than just Bitcoin. It includes: * **Ethereum and Smart Contracts**: Ethereum's introduction of smart contracts has been pivotal, allowing for decentralized applications that can interact in complex ways, far beyond simple transactions. * **Other Blockchains**: Platforms like Solana, Sui, and Near are gaining traction for their high throughput and lower costs, addressing some of Bitcoin's limitations on the base layer. ## The Cultural and Economic Shift The move towards Web 3.0 isn't just technological but cultural. There's a growing sentiment, reflected in posts on platforms like X, that users are ready for a change where they own their digital presence. Here's some background based on general knowledge and trends up to 2024: ### Cultural Shift: * **Distrust in Centralized Institutions**: There's been a growing distrust in traditional centralized institutions like banks, governments, and large corporations. This distrust stems from various scandals, data breaches, privacy concerns, and perceived inefficiencies or corruption. Posts on platforms like X or even more on Nostr reflect this sentiment, where users often discuss the diminishing trust in these institutions. * **Rise of Individual Empowerment**: Culturally, there's a move towards empowerment of the individual, facilitated by technology. Social media, blockchain, and other decentralized technologies give individuals tools to bypass traditional gatekeepers in finance, media, and more. This shift champions the idea that individuals should have more control over their data, finances, and digital identity. * **Identity and Community**: Decentralization also touches on identity politics and community governance. There's a trend towards localism or regionalism where communities seek more control over their governance, which can be seen in movements for local autonomy or even secessionist sentiments in various parts of the world. * **Cultural Movements**: Movements like the maker culture, DIY (Do It Yourself), open-source software, and even the gig economy reflect a cultural shift towards decentralization where individuals or small groups can produce, create, or work independently of large entities. ### Economic Shift: * **Decentralized Finance (DeFi)**: DeFi represents one of the most tangible shifts, aiming to recreate and potentially improve financial systems outside of traditional banking. This includes lending, borrowing, and earning interest in a trustless, permissionless environment, primarily using blockchain technology. * **Cryptocurrencies and Tokenization**: The rise of cryptocurrencies like Bitcoin and Ethereum symbolizes a move away from centralized monetary systems. Tokenization of assets, from art (NFTs - Non-Fungible Tokens) to real estate, embodies this shift, allowing for fractional ownership and reducing the barriers to investment. * **Globalization vs. Localism**: While globalization has interconnected economies, there's a counter-trend where economic decentralization supports local economies. This can be seen in the push for local currencies, community-supported agriculture, or local energy production like solar microgrids. * **Work and Employment**: The gig economy, remote work, and digital nomadism are part of this economic shift. Platforms enabling freelance work decentralize employment, moving away from traditional office environments and 9-to-5 jobs. ### General Observations: * **Technology as an Enabler**: Blockchain, the internet, and advancements in communication technology are pivotal in this shift. They provide the infrastructure necessary for decentralization to occur at scale. * **Political Implications**: Economically, this shift maybe challenges existing power structures, potentially leading to regulatory battles as seen with cryptocurrencies. Culturally, it might lead to a redefinition of nationalism, community, and individual rights in the digital age. * **Challenges**: Despite its promise, decentralization faces hurdles like scalability issues, regulatory pushback, the digital divide, and the potential for new forms of centralization (e.g., large crypto exchanges becoming new central authorities). ## Conclusion: Bitcoin's Place in Web 3.0 Bitcoin's protocol ignited the spark for a decentralized internet, but Web 3.0 is evolving into a multifaceted ecosystem where Bitcoin might play a crucial, though not yet exclusive, role. The integration of Bitcoin with newer technologies and platforms could see it becoming a fundamental layer in the Web 3.0 stack, particularly in areas of value transfer and as a store of value within decentralized finance (DeFi). As we progress, the synergy between Bitcoin's proven security and stability, combined with the innovation of other blockchain technologies, might just be the blend needed for Web 3.0 to achieve mainstream adoption, ensuring the internet becomes more open, secure, and user-centric. *As stated before, the market will probably decide in favor of the strongest and most secure network, and **Bitcoin** is by far that.* @ 9977c3ad:43a20d63
2024-09-05 11:21:09## Details - 🍽️ Servings: 2 ## Ingredients - 1 cup Jasmine rice - 1 Tbsp. lavender flowers, crushed with mortar and pestle - 1/4 cup apple cider vinegar - 2 Tbsp. fine cane sugar - 2 Tbsp. honey - 1 sprig rosemary - 1/4 tsp angostura bitters - 1/2 cup blackberries - 1/2 cup blueberries - 4 cups trimmed and quartered shiitake mushrooms - 1 tsp fresh coriander crushed - 1/4 tsp fresh cumin ground - 1/2 tsp red pepper flakes - 3 sprigs of thyme - 2 Tbsp. olive oil - 1 tsp soy sauce - 1 cup creamy coconut milk ## Directions 1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes. 2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside. 3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
@ 9977c3ad:43a20d63
2024-09-05 11:21:09## Details - 🍽️ Servings: 2 ## Ingredients - 1 cup Jasmine rice - 1 Tbsp. lavender flowers, crushed with mortar and pestle - 1/4 cup apple cider vinegar - 2 Tbsp. fine cane sugar - 2 Tbsp. honey - 1 sprig rosemary - 1/4 tsp angostura bitters - 1/2 cup blackberries - 1/2 cup blueberries - 4 cups trimmed and quartered shiitake mushrooms - 1 tsp fresh coriander crushed - 1/4 tsp fresh cumin ground - 1/2 tsp red pepper flakes - 3 sprigs of thyme - 2 Tbsp. olive oil - 1 tsp soy sauce - 1 cup creamy coconut milk ## Directions 1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes. 2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside. 3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens. @ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam. However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash. Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin. BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now. https://strike.me/blog/bolt12-offers/ As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented. Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology". The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack. This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential. Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust. Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin. --- Final thought... Vibes are high.
@ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam. However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash. Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin. BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now. https://strike.me/blog/bolt12-offers/ As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented. Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology". The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack. This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential. Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust. Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin. --- Final thought... Vibes are high. @ 572aa884:e266a569
2024-09-04 19:46:40# STAR TREK TNG: INCOMPATIBLE IDEALS *by Luke Parker* --- **Premise**: *This screenplay is for an episode of Star Trek: The Next Generation, set near the end of Season 7. It imagines a first contact encounter between Picard’s Enterprise and a fully Anarcho-Capitalist planet with no government nor belief in authority.* --- **Scene 1: Bridge** --- *Exterior views of the Starship Enterprise give way to Captain Jean-Luc Picard standing at his command station on the bridge, his gaze steady and contemplative as he records his log.* **Picard:** (voiceover) "Captain's log, Stardate 48881.4. We were on our way to Deep Space 9 to provide support for the upcoming Bajoran elections when we received an audio-only distress call from a person on the planet Anarak, just outside of Cardassian space. The planet has yet to be contacted by the Federation, and in fact very little is known about it other than how it has a highly unusual social structure; one that appears to function without any form of central government or hierarchical leadership. It is a society that, despite its relatively high level of technological sophistication, has yet to achieve warp capability. The message is urgently requesting help from any peaceful civilization in range to defend his people against Cardassian invaders. It is difficult to imagine even the Cardassians violating the Prime Directive in such a manner. We are changing course to investigate." *Picard finishes his log entry and looks up, his expression thoughtful. The rest of the bridge crew is attentive with the memory of the Cardassain conquest of Bajor fresh in their minds.* **Data:** [turning from his console to face Picard] "Captain, Starfleet's lone anthropological record on Anarak indicates that it has a relatively large population and is advanced in various scientific fields. However, there are no reports of warp capability nor a leadership structure for us to contact there. Their society’s structure might challenge our usual protocols for contact." **Riker:** [with a hint of curiosity] "An advanced society with no central government? That's a first." **Picard:** [nodding] "Indeed, Number One. The distress call came from an individual named Bas T'yat, who identifies himself only as an entrepreneur. Our intelligence suggests that Anarak's society is structured in a way that is not only hostile to hierarchies but completely devoid of any form of leadership or authority. They seem to operate on a principle of total autonomy. This would seem to indicate an absence of a planetary defense system." **Troi:** [thoughtful, with concern] "Without a central authority, how do they respond to any external threats? A society like this could be quite vulnerable to more aggressive powers, like the Cardassians." **Picard:** [grimly] "It seems that may already be the case. The distress signal implied that a hostile force, likely Cardassian, has targeted them. Without a unified defense, they could be easy prey." **Worf:** [sternly] "If the Cardassians are involved, Captain, they will not hesitate to exploit such a weakness. We must be prepared for hostilities." **Data:** [analyzing the implications] "However, the lack of formal governance could complicate any assistance we offer. Without a government to negotiate with, we may face challenges in determining how to intervene appropriately." **Picard:** [resolute, yet cautious] "We will treat Anarak as we would any other planet sending a distress call, regardless of their social structure. However, we must tread carefully. If we arrive to find Cardassians engaged in hostile acts, we may be forced to intervene. But in Federation space, our priority remains the protection of life and the maintenance of Federation principles." *The bridge crew exchanges looks of determination, each officer understanding the complexities of the mission ahead.* **Picard:** [decisive, raising his voice slightly] "Set course for Anarak. Engage at warp seven." **Data:** [acknowledging] "Course plotted, Captain. Engaging warp seven." *The familiar hum of the warp engines intensifies as the stars on the viewscreen stretch into streaks of light, and the Enterprise leaps into warp, speeding towards the strange planet and the potential conflict awaiting them.* --- **Scene 2: Bridge** --- *The Enterprise emerges from warp above the planet Anarak, the planet’s blue-green surface appearing deceptively peaceful below.* **Worf:** [at tactical, scanning the area] "Captain, no alien vessels are currently in the vicinity, only artificial satellites. However, I'm detecting signs of recent battle on the planet's surface." **Picard:** [moving closer to Worf's station] "Specify, Lieutenant." **Worf:** [analyzing the data] "There is minor damage to infrastructure in multiple locations, consistent with Cardassian disruptor fire. Several structures show signs of targeted attacks, but the damage is localized and not extensive." **Data:** [at the science station] "Captain, I'm detecting several warp signatures leading to and from the planet. However, one of these signatures does not match any known Cardassian engine profile and is not in our warp signature database." **Riker:** [concerned, looking to Picard] "An unknown vessel in the area right around the time of a Cardassian attack? This could complicate matters." **Troi:** [sensing the tension, her voice calm but alert] "Whoever they are, they may not have the best intentions. The people of Anarak could be more vulnerable than we initially thought." *Picard ponders this information, his expression thoughtful yet wary. The bridge crew continues their scans, tension mounting as they try to make sense of the situation.* **Worf:** [interrupting the silence] "Captain, we are being hailed from the surface." **Picard:** [decisive, nodding] "On screen." *The viewscreen flickers to life, revealing the image of a middle-aged man with a rugged, practical look. He exudes an air of cautious relief, though his eyes betray a deep-seated wariness.* **Bas T'yat:** "Alien vessel, thank you for coming so quickly. My name is Bas T'yat, and I’m an entrepreneur and concerned family man. Please, can you tell me, are you an ally of the Cardassians?" **Picard:** [calm and reassuring] "Mr. T'yat, I am Captain Jean-Luc Picard of the Federation starship Enterprise. I assure you, the Federation is not aligned with the Cardassians, although we have dealt with them before, and are aware of their transgressions." **Bas T'yat:** [sighs in relief] "Thank goodness. We desperately need your help. An alien ship identifying itself as Cardassian has been harassing us for weeks. I fear they'll return soon, and we have little defense against their matter transportation technology. I'm a successful inventor and businessman, Captain. I have resources and tech that could be of value to your Federation, and I'm prepared to trade anything you want in order to help protect my people." **Picard:** [curious, leaning slightly forward] "Tell me more about these attacks. What exactly have the Cardassians done?" **Bas T'yat:** [his tone shifting to one of frustration mixed with guilt] "It started about a month ago. One of our companies, my own company, in fact, launched a new type of vessel that can travel faster than light using a warp field, the first one we've ever built. Within an hour of it's maiden voyage the Cardassians showed up. At first, they demanded to know who was in charge of the planet. They didn't like the answer they got: We are a free people and no one commands us." **Riker:** [sharing a knowing glance with Picard] "A society without centralized leadership would be difficult for the Cardassians to understand or even tolerate." **Bas T'yat:** [nodding] "That was my conclusion. They treated us like a lawless frontier, moving in to take whatever they wanted. They attacked our resource stockpiles, dematerialising and I assume stealing whatever they could before we even knew what was happening. Our ground-based defense missiles successfully took out their two smaller fighter crafts that came down into our sirspace, but we have no defense against their transporter technology. Their last visit was just a raid from orbit. They just grabbed what they could without even entering the atmosphere and left within minutes." **Picard:** [thoughtful, with a hint of concern] "I see. There are widely-agreed-upon rules against this type of behavior, I assure you. However, since the Federation has never made contact with your people before now, we are unfamiliar with the proper etiquette for such a first encounter. How do you suggest we proceed safely for an official meeting?" *Bas pauses, visibly perplexed by the concept of "official" procedures, his expression almost amused.* **Bas T'yat:** [with a chuckle] "Official meeting? Captain, just come on down and park your craft outside my coordinates. My wife will make us all some refreshments." **Picard:** [with a slight smile, yet maintaining formality] "We appreciate the hospitality, Mr. T'yat, but we prefer to beam down if that's acceptable to you. We can be there in a few minutes." **Bas T'yat:** [nervous but agreeable] "Beam down? Uh, sure, that's fine. I was wondering if that technology worked on people. Love to see it in action." **Picard:** [nodding respectfully] "Understood. I'll be down with a small team to meet you outside your building shortly. Picard out." *The screen goes dark as the connection ends, leaving the bridge crew to process the encounter.* **Riker:** [with a wry smile] "Drinks with the locals; sounds like fun." **Troi:** [softly, but with insight] "He's nervous, but also hopeful. I'm sensing some hurt pride in him, too, Captain. This is likely the first time his people have ever had to reach out to anyone off-world for help. His pride may cloud his ability to fully grasp the dangers they’re facing." **Picard:** [serious, standing up to address the crew] "On top of being an official first contact, the Cardassians have made this a very delicate situation. We must be prepared for anything. Counselor Troi, Data, and La Forge, you're with me. Number one, you have the bridge." *The crew nods in understanding as the away team heads to the turbolift. The tension in the air is palpable as they ready themselves for what may be a challenging first contact and a possible hostile encounter with the Cardassians.* --- **Scene 3: Bas T’yat’s Front Lawn** --- *The team materializes on the surface of Anarak, just outside of a large, elegant house set in a lush, rural landscape. The area is a blend of modern luxury and natural beauty, though signs of recent damage are evident. Smoke still rises from a nearby hangar, the aftermath of the Cardassian attack clear in the smoldering ruins. As the team takes in their surroundings, a group of locals approaches. At the forefront is Bas T'yat, flanked by a few colleagues. He's a middle-aged man with a commanding presence, dressed in practical yet fine clothing. His stride is confident, and his eyes sharp with the determination of a man used to getting what he wants. Bas’s face lights up with a mixture of curiosity and enthusiasm as he sees the away team.* **Bas T'yat:** [warmly, holding his palms upwards and then extending one hand towards Picard in a greeting] "Captain Picard! Welcome to Anarak! I'm Bas T'yat. It is my honor to meet you." **Picard:** [imitating the hand motion, with a polite smile] "The honor is ours, Mr. T'yat. Thank you for your hospitality. May our two peoples forever live in harmony." *Bas gestures to the smoldering hangar in the distance, his tone tinged with frustration.* **Bas T'yat:** [with a sigh] "That would be wonderful. I do wish the circumstances for your visit were better. [clenching his fists] That's my hangar over there, or what's left of it, anyway. The Cardassians destroyed it and the spacecraft I designed and built there. It was our first warp vessel, one that the whole world cheered on at launch just last month. We were going to colonize the asteroids with it." **Geordi:** [To Picard, gesturing towards the wreckage] "If I may, Captain?" **Picard:** "Certainly." [To Bas T'yat] "This is my head engineer, Commander Geordi La Forge." **Geordi:** [stepping forward] "Mr. T'yat, if it's alright with you, I'd like to examine the wreckage. I might be able to determine if anything is salvageable." **Bas T'yat:** [nodding, gesturing to a colleague] "Of course. Lar Kinn here is our chief pilot. He made the historic first flight and he'll take you to the hangar and help with anything you need." *Geordi and Lar Kinn head towards the hangar, with Geordi hoping to confirm if this was the source of the warp signature detected in orbit. Meanwhile, Bas leads Picard, Troi, and Data toward his house. As they walk, Bas impatiently answers a few questions about his planet, his voice tinged with annoyance and concern.* **Data:** “Mr. T’yat, if I may, I notice that your neighborhood’s infrastructure is well taken care of. If Anarak has no central authority of any kind, who is responsible for keeping the roads and infrastructure?” **Bas T'yat:** ”Well, as a rule of thumb, if it’s on my land, I am. If it’s not on my land, then someone else is, but I may have to pay them to use it. They look so nice because we all get better insurance rates for keeping them that way.” **Data:** “Curious. And who initiates larger projects like mass transportation and research?” **Bas T'yat:** [slightly annoyed] “They are all risky endeavors taken by entrepreneurs like myself. Sometimes profits take decades to appear, but like with my new warp engine, I’m sure they’ll make me a huge fortune one day.” [turning to ensure Picard can hear him] "Anyway, I fear the Cardassians aren't done with us. They've stopped even trying to make demands of us, which makes me think they're planning something bigger. Perhaps a larger assault. We've been able to fend them off so far, but I have no clue how to defend against those transporter devices." **Picard:** [impressed] "It is remarkable that your society, with no planetary defense force, was able to repel Cardassian military forces, even if only temporarily. Cardassian ships are known for their significant weapons and shields." **Bas T'yat:** [with a hint of pride] "The people of Anarak are no strangers to defending themselves. We have numerous private protection agencies, each with advanced missile fortifications and other kinds of defenses to protect every inch of this planet. But these were designed to fend off terrorists or rival companies, not an alien invader." *They reach the entrance to Bas's home. He pauses before entering, turning to Picard with a serious expression.* **Bas T'yat:** [earnestly] "Captain, I'm prepared to trade for whatever defensive technology you can provide, especially something to counter the Cardassian's transporter technology. I am confident that our ground defenses can take out their shuttlecraft, but we're helpless against their ability to beam in and out at will." *Picard pauses, his face reflecting the weight of his decision before he speaks.* **Picard:** [in his most diplomatic tone] "Mr. T'yat, the Federation is committed to helping those in need, and we don't tolerate bullies. However, there are restrictions on the technology we can share, particularly weaponry. Also, the Federation's assistance often depends on whether a planet is on the path to becoming a member. We must ensure that our values align. In this case, a diplomatic approach might bring a far more lasting peace than simply escalating an arms race." *Bas considers this, his optimism tinged with caution. The group moves into a large room with lots of seating where a warm drink much like tea is offered. Picard partakes graciously.* **Bas T'yat:** [thoughtfully] "I see. Federation membership is... a complicated idea. I'm sure many heads of companies like myself would welcome it, but for the whole planet to become a singular member of any larger federation is hard to imagine. Our society values individual freedom above all else, and I'm not sure how compatible everyone here is with the Federation's ideals." **Data:** "The benefits of Federation membership are considerable. Could not your people one day vote on the issue to see if a majority wants to join after taking ample time to research membership?" **Bas T'yat:** [skeptically] "Voting is something that hasn't been done here for tens of thousands of years. We consider it to be archaic, a form of slavery of the minority. Honestly, I'm surprised your culture still practices it." **Picard:** [nodding, a little embarrassed] "I see. Rest assured that we try to only vote on things that have every participant's full consent. You'll find that this is very common among the races you meet as your people start to explore the stars. But until then, know that the Federation's primary concern is the safety of everyone in Federation space, including your people." *While inside Bas's home, Data discreetly connects to an open network connection, accessing Anarak's version of the internet called the Openlink. His eyes flicker left to right at an inhuman speed as he analyzes the planet's defenses and infrastructure.* **Data:** [quietly, to Picard as he processes the data] "Captain, while there are many advanced technologies in the hands of individuals and companies, I find no evidence of any kind of unified military infrastructure. The defense efforts are completely decentralized, which will surely prove problematic in the event of a full-scale Cardassian invasion." **Picard:** [grimly] "Given the Cardassians' history, we must prepare for the worst." *Just then, Geordi returns from the hangar, his expression a mix of curiosity and concern.* **Geordi:** "Captain, I've confirmed that Bas's ship was the source of the warp signature we detected. Unfortunately, the wreckage isn't salvageable. It could be a long time before Anarak returns to the stars." **Bas T'yat:** [with a determined grin] "I wouldn't say that. My first flight was widely publicized. Lar Kinn and I are celebrities now. Hundreds of other companies are likely working on similar technology already. Some of us refer to it as 'the great space race,' with the goal of creating the first off-world colony, and my company is currently in the lead." **Picard:** [with a slight smile, impressed by the resilience] "It seems the people of Anarak are not to be counted out yet. Your intrepid spirit will serve you well as Anarakans start exploring the Galaxy." **Troi:** [warmly] "Your optimism is admirable, Mr. T'yat. But remember, resilience is strongest when combined with caution." **Bas T'yat:** [nodding, appreciatively] "Wise words, Miss Troi. Hopefully with your help we'll be ready for whatever comes next." **Picard:** [ready to leave] "This tea is delicious, thank you for your hospitality. Next I'll need to talk to my superiors at Starfleet headquarters before we can proceed any further. I'll be sure and pass your concerns and needs on to them and then we'll contact you again later today." *The away team prepares to depart, with Bas expressing his thanks once more. As they beam back to the Enterprise, each member reflects on the unique challenges of Anarak.* --- **Scene 4: Picard’s ready room** --- *Minutes later, Captain Picard sits alone in his ready room, the vast starscape of space visible through the window behind him. His posture is straight, and the weight of the decision before him is clear in his eyes. He taps a command into his desk console, and the screen flickers to life with the familiar stern face of Vice Admiral Alynna Nechayev. Her image on the screen is as imposing as ever.* **Picard:** [calmly, but with underlying urgency] "Admiral, I've just concluded a preliminary contact with a representative of Anarak, just a few light years this side of Cardassian space. The situation is more complex than anticipated. The planet is under threat from the Cardassians; specifically Gul Bankar, who's been making increasingly aggressive moves from orbit. Meanwhile, the society on Anarak is... unconventional. They have no central government, no formal leadership nor military structure. The entire planet operates under a decentralized, anarchic, commerce-based system." **Nechayev:** [eyes narrowing] "Anarchists? No structure? That's not exactly an encouraging environment for a first contact, Jean-Luc. **Picard:** “Admiral, they’ve managed to develop warp technology without either a government or military. It’s a remarkable feat, but one that leaves them vulnerable.” **Nechayev:** “Are you certain there’s no one in authority at all? Not even an ambassador?" **Picard:** [nodding] "Precisely. Their social structure wouldn’t allow it. Our first contact has been with an individual and his family, one Bas T'yat; a wealthy businessman and the inventor of their first warp-capable ship. He's requesting assistance to defend against further Cardassian attacks, but without a central authority, assisting one individual could have unpredictable consequences." **Nechayev:** [questioning sharply] "Hmm. And what of the Cardassians? Is there any evidence of their involvement?" **Picard:** [gravely] "Plenty. The Cardassians have already raided the planet, seizing valuable resources. Their ship left orbit shortly before our arrival, but the threat of their return looms large. Bas T'yat is convinced they'll come back with a larger force." *Nechayev pauses, her expression hardening as she considers the situation.* **Nechayev:** [warningly] "Starfleet cannot afford to be drawn into deeper hostilities with the Cardassian Union, Jean-Luc. Especially not over a non-member world. You must tread carefully. A diplomatic solution is paramount, and under no circumstances should you provide this Bas T'yat with advanced defensive technology. The Prime Directive is clear; we don't interfere with the internal affairs of non-member worlds, and besides, you haven't even made proper first contact with the planet, only with one family." **Picard:** [measured, but firm] "Admiral, with respect, Anarak is far more advanced than many worlds we've encountered. Their technological capabilities, while decentralized, are impressive. Now that they are getting their space legs it won't be long before Anarakans are showing up in ports across the quadrant. And if the Cardassians establish a foothold here, it could destabilize the entire region." *Nechayev's face softens slightly, recognizing the gravity of the situation. She sighs, her resolve shifting as she weighs the options.* **Nechayev:** [reluctantly] "Alright, Jean-Luc. I don’t like this, but I trust your judgement. You may share transport inhibitor technology. Only enough to help them counter the Cardassians' beaming technology, but nothing more. And remember, this Bas T'yat doesn't speak for his whole planet. Try to treat his family like you would if you found them alone in a spaceship." **Picard:** "Understood, Admiral. I'll proceed with caution." **Nechayev:** [more sternly] "Just don't start another war, Jean-Luc." *The screen goes dark. Picard leans back in his chair, the weight of the decision pressing on him. He stands, smoothing his uniform, and exits the ready room onto the bridge.* --- **Scene 5: Bridge** --- *On the bridge, the atmosphere is tense as the crew processes the situation. Picard steps up to his command chair, addressing the senior officers who have gathered.* **Picard:** [seriously] "Admiral Nechayev has authorized us to share transport inhibitor technology with Anarak to help them defend against further Cardassian raids. But we must be mindful of the ethical implications of our actions." **Dr. Crusher:**: [concerned] "Captain, I'm worried about the consequences of becoming involved in this situation. If we assist Anarak, it could escalate into a larger conflict--one that could draw the Federation into another war with the Cardassians." **Worf:** [gruffly, with resolve] "But allowing the Cardassians to plunder a defenseless society is equally unacceptable, Doctor. We have a responsibility to protect the vulnerable." **Picard:** [thoughtfully, considering both viewpoints] "I'm inclined to agree with Worf on this one, Beverly. We must work fast to deploy the inhibitors wherever we can, but that does bring up another problem. The Prime Directive prevents us from interfering in the internal affairs of non-member worlds. And giving one individual on Anarak access to advanced technology could upset the delicate balance of their society. What if Bas T'yat's company gains a monopoly on defense technology? It could shift the power dynamics on the entire planet." **Troi:** [insightfully, her voice calm] "Captain, I sense that Bas T'yat is deeply worried about his planet's future. He feels a strong sense of responsibility and guilt for the attacks... I don't think that he had any way to know that their warp signature would act as a beacon to those seeking resources. They didn't even know other life forms existed until the Cardassians arrived. It's clear that Anarakans weren't prepared for the reality of interstellar contact." **Picard:** [resolved] "I agree, Counselor. We're dealing with a society that is both advanced and vulnerable. A dangerous combination. We must proceed carefully." *Picard considers this, his brow furrowed in thought. Finally, he makes a decision.* **Picard:** [decisively] "We must proceed, however. I'll invite Bas T'yat to the Enterprise to discuss the situation further. We will ensure that any assistance we provide doesn't destabilize their society, or escalate the conflict." *Picard hails Bas T'yat from his command station.* **Picard:** [calmly] "Mr. T'yat, I'd like to invite you aboard the Enterprise to discuss our options in person." *The main screen fills with T'yat's face again.* **Bas T'yat:** [with a hint of hesitation] "Thank you, Captain, I accept. But I'd prefer to take my own craft... Still not quite comfortable with the transporter technology, if you'll understand. I'll bring my wife, L'anna, and my pilot, Lar Kinn." **Picard:** [diplomatic, nodding slightly] "Understood. We'll be ready to receive you in the shuttlebay.” --- **Scene 6: Main Shuttlebay** --- *In the Enterprise's shuttlebay, the crew prepares to greet their visitors. The doors slide open, and a sleek, streamlined skysled enters the bay, guided by Lar Kinn at the controls. The craft settles gently onto the deck, and the hatch opens. Bas T'yat steps out, accompanied by his wife, L'anna, and Lar Kinn, who looks around the shuttlebay with wide-eyed curiosity. Picard, Troi, and Data are there to meet them, offering warm greetings as the Anarakans take in the impressive sight of the Enterprise's interior.* **Picard:** [welcoming, with a gesture towards the ship] "Welcome aboard the Enterprise, Mr. and Mrs. T'yat. I trust your journey was smooth?" **Bas T'yat:** [grinning, clearly impressed] "Very much so, Captain. Your ship is... well, it's more than I imagined. Thank you for having us." *Troi steps forward, offering a kind smile.* **Troi:** [invitingly] "If you'd like, I can give you a tour of the ship. We're quite proud of our vessel, and I think you'll find it fascinating." *L'anna's eyes widen with excitement, and she nods eagerly. Bas exchanges a look with Lar Kinn, just catching up to the group. He seems just as eager to explore as the others, and nods excitedly to Troi.* **Bas T'yat:** [appreciatively] "We'd be honored. Lead the way, Counselor." **Lar Kinn:** So can all these shuttles go faster than light? *With that, the group sets off on a tour of the Enterprise, the Anarakans marveling at the advanced technology and seamless design of the Federation starship. As they walk, Troi can't help but notice the mix of awe and determination in Bas T'yat an inventor and leader who knows that his world's future may very well depend on the choices made in the hours to come.* --- **Scene 7: Bridge** --- *The scene opens as Counselor Troi leads Bas T'yat, L'anna, and Lar Kinn onto the bridge of the Enterprise. The visitor's awe is palpable as they take in the grandeur of the ship's command center. Picard, standing near the captain's chair, barely has a moment to welcome them when a sudden alert draws everyone's attention.* **Data:** [at his station, voice urgent] "Captain, I'm detecting the return of the Cardassian battle cruiser. It is registered as the Kolarak. It just popped out from behind the home star and is entering orbit around Anarak." **Riker:** "Yellow alert. On screen." *Picard immediately straightens, his expression shifting from welcoming to resolute. The tension on the bridge heightens as the viewscreen flickers to life, displaying the imposing sight of the Kolarak. The Cardassian vessel looms in space, its dark hull bristling with weaponry.* **Picard:** [calmly, but with authority] "Mr. Worf, open a channel to the Kolarak." *The screen quickly reveals the stern visage of a Cardassian Gul in his command chair. His eyes narrow as he takes in the sight of the bridge crew and the unfamiliar faces of Bas and his companions.* **Picard:** [with measured politeness] "I am Captain Jean-Luc Picard of the Federation starship Enterprise. With whom am I speaking?" **Gul Bankar:** [with a sneer, his voice dripping with condescension] "You may address me as Gul Bankar." **Picard:** "Gul Bankar, there have been reports of your vessel causing harm and stealing resources from the planet below. With me is Bas T'yat, the owner of the warp-capable vessel that it appears your forces destroyed on the surface. We request an explanation for these hostilities." **Gul Bankar:** "Captain Picard, your presence here is an unwelcome interference. This planet, and its inhabitants, are under Cardassian protection. You will withdraw immediately, leaving Anarak to our care." *Picard's gaze hardens, but his tone remains calm and firm.* **Picard:** [skeptically] "Cardassian protection? Anarak lies within Federation territory. We received a distress call and are here to provide assistance." *Bankar's expression darkens, his eyes flashing with anger.* **Gul Bankar:** [coldly] "The Federation's meddling in this region is all too well documented, Picard, but Anarak is too close to Cardassian space for your interference to be tolerated. I find your so-called assistance nothing more than another prelude to annexation." *Bas, standing beside Troi, listens intently, his face reflecting a mixture of concern and frustration. Picard, sensing the rising tension, steps closer to the viewscreen.* **Picard:** [with resolve] "The Federation respects the sovereignty of all worlds. We are only here because of your aggressive actions, not to claim this planet. We have long worked to maintain peace in this sector, and I would hate to see that peace jeopardized by your reckless actions here." **Gul Bankar:** [sarcastically] "Peace? The Federation's control of Terok Nor and the Bajoran wormhole is hardly a gesture of peace. It was a clear power grab, one that we will not allow to extend to Anarak." *Picard's eyes narrow, his voice taking on a steely edge.* **Picard:** [firmly] "Gul Bankar, a conflict between the Federation and the Cardassian Union would serve no one's interests, especially not over a planet that is so new to the neighborhood. I suggest you contact your superiors before taking any further aggressive actions." *There's a tense silence as Bankar considers Picard's words, his eyes flicking to Bas and then back to Picard. Finally, he lowers his head in a slight nod, though his expression remains hostile.* **Gul Bankar:** [grudgingly] "Very well, Captain. I will contact Central Command. But understand this; Anarak will not fall under Federation control, and I will ensure that Cardassia's interests are protected. I will contact you again in 4 hours." *The transmission abruptly cuts off, leaving the bridge in a heavy silence. The Kolarak remains on the viewscreen, hovering ominously in space, nose to nose with the Enterprise now. Picard exhales, turning to face his crew.* **Picard:** [calmly, but with an undertone of urgency] "Maintain our position and yellow alert, Mr. Worf, and monitor the Kolarak for any signs of hostile activity." *Worf gives a curt nod, his eyes never leaving the tactical display.* **Worf:** [with determination] "Aye, Captain. Shields at maximum, weapons ready." *Picard then turns to Bas, who is visibly shaken but trying to maintain his composure.* **Picard:** [reassuringly] "Mr. T'yat, I understand this is a difficult situation and you don't yet know who to trust, but I assure you that we aim to keep the peace in this sector and will do everything in our power to ensure your planet's safety. We ask nothing in return from the Anarakan people. However, it is crucial that we handle this matter diplomatically." *Bas nods, though his expression is one of deep concern.* **Bas T'yat:** [uneasily] "I appreciate that, Captain, and don't worry, nothing that Gul Bankar says will make me trust his offer of "protection" after he destroyed my ship and stole resources from all over the planet. But I do worry that he’s using this time to call for reinforcements." *Picard places a reassuring hand on Bas's shoulder, his voice steady.* **Picard:** [confidently] "If he attacks, we'll face that challenge together, Mr. T'yat. You are free to return to the surface at any time but for now, I think it best that we consider how fast we could deploy our transporter inhibitor technology on your planet." **Bas T'yat:** [enthusiastically] "You mean you're willing to sell us devices that can stop them from beaming up our resources?" **Picard:** "Or beaming their troops down. And we wouldn't sell it to you, it is our gift. The Federation doesn't sell it's assistance to those in need." *The visitors faces all brighten in unison with relief.* **L'anna:** "I don't know how we could ever thank you enough, Captain. This means everything to our people." **Picard:** "Don't thank us yet, there is still the issue of deploying enough of them in time. If they're going to attack in 4 hours you'd need them set up near all the most valuable targets at the very least. They'll need a steady supply of energy, too." *Bas furls his lips in concerned thought.* **Data:** "Captain, I've analyzed all of the planet's most valuable resource depots that our scanners can detect and I see 168 unique locations that we should set up transport inhibitors. There may, of course, be other targets too that they would want." **Riker:** [apprehensively] "That's way too many for us to replicate in time, much less visit each location to install within the next 4 hours." **Picard:** "We need a way to speed up that deployment, at least to enough sites that will show Gul Bankar that things have changed... And hopefully without him detecting our movements." **Bas T'yat:** "If I may captain, I think I know a better way to deploy them if I can just make a detailed scan of one and save it to our printer file format... We don't have your transporter technology, but our device printers are able to scan and quickly reproduce any technological device that we can identify the components of." **Riker:** "And how will that help distribute them to everyone in time?" **Bas T'yat:** "Simple, every business and household has one of these printers. I can upload the scanned file to our Openlink and tell all of Anarak in one broadcast about the imminent threat and how to protect themselves from it with one of these inhibitors. They'll pop out thousands of them in time." **Picard:** "That sounds very promising, Mr. T’yat. But I want your assurance that your company will not hold any sort of monopoly on this technology or otherwise profit from it; In lieu of a government, the Federation requires that this gift be made to your whole planet at once." **Bas T'yat:** [after some hesitation] "Alright, Captain. You have my promise. Giving up some profits is the least I can do to make up for attracting the Cardassians to Anarak." *Picard looks visibly relieved, giving a curt nod to Bas.* **Picard:** "Data, take our guests to engineering and grab whomever you may need to assist you with making this happen in time. Remember, you’ll also need to show the Anarakans how to use these devices." **Data:** "Aye sir." [To the visitors] "If you'll follow me please, we'll be able to work on this in engineering." *Data, Bas, Lar Kinn, and L'anna walk briskly to the turbolift. The scene closes with Picard returning to his command chair, the bridge crew resuming their stations as the standoff between the Enterprise and the Kolarak continues. The two ships remain locked in silence, nose to nose, as the 4-hour countdown begins.* --- **Scene 8: Main Engineering** --- *The scene opens in Main Engineering, where Geordi La Forge, Data, and Ensign Sam Lavelle are putting the final touches on the scan for their transport inhibitor device. Bas T'yat and Lar Kinn stand nearby, observing the process with keen interest. The atmosphere is tense, underscored by the ticking clock counting down the hours until Gul Bankar's deadline.* **Geordi:** [focused as he works] "All right, that should do it. The scan of this transport inhibitor is ready, and the data's been formatted for your printers." *He hands a datapad to Bas, who takes it with a mix of curiosity and nervousness.* **Geordi:** [reassuringly] "You'll be able to upload the complete plans from this device, including an adapter for your power source. Once it's on your network, anyone with Openlink access will be able to build and deploy these inhibitors in a matter of minutes. It's up to you, however, to convince them to do that." **Bas T'yat:** [relieved] "Thank you, Commander. I'm sure many will manage it in time, but I just hope it's enough." **Lavelle:** [chiming in, pointing to the datapad] "Also I've included a detailed instruction set too. It explains how to set the units up and operate them." *Bas nods his thanks, flipping through the instructions as Lar Kinn looks over his shoulder.* **Data:** [ever precise, offering a suggestion] "Mr. T'yat, given the standoff outside, it may be prudent to avoid the use of the transporter. The Kolarak is likely monitoring our actions closely. Sending the plans with you aboard the skysled would appear less provocative." *Bas looks visibly relieved at the suggestion, nodding in agreement.* **Bas T'yat:** [grateful] "Thank you, we'd prefer not having our atoms scattered throughout the atmosphere today anyway." **Geordi:** [nodding, humorously] "No problem. We'll make sure the skysled is ready to go." *Data gestures toward the exit of Engineering, indicating it's time to depart.* **Data:** [calmly, but with urgency] "We should make our way to the shuttlebay. There's less than two hours remaining before the Gul's deadline. It's imperative that as many Anarakans as possible receive these plans in time." *Bas and Lar Kinn exchange a look, their expressions set with determination as they follow Data out of Engineering. The camera follows the group as they walk briskly through the corridors of the Enterprise.* **L'anna:** "You'll be sure to tell the Captain and Councilor Troi that we said goodbye?" **Data:** "Of course. And let me say that I find your culture truly intriguing, and hope we get the chance to visit again in the future, no matter if Anarak chooses Federation membership or otherwise." **Bas T'yat:** "You'd be our welcome guest anytime, Mr. Data. I think you'd most enjoy seeing the progress my people have made with robotics and artificial intelligence. My company produces one of the best-selling android assistants on the market." **Data:** "Fascinating. I look forward to it. Here we are." *As they reach the shuttlebay, the large bay doors slide open, revealing the sleek skysled waiting for them. The ship is prepped and ready for launch, its engines humming with quiet power.* **Data:** [pausing as their ship's door opens] "We wish you a safe journey, Mr. T'yat, L'anna, Mr. Kinn." **Bas T'yat:** [nodding, with resolve] "We'll make sure everyone gets these plans. Thank you, Commander Data." *Lar Kinn gives Data a respectful nod before they step onto the skysled. Data watches as they take their positions inside the cockpit. Data then taps his communicator, his voice steady.* **Data:** "Data to the Bridge, our visitors are ready to depart." *The camera cuts to the exterior of the Enterprise, where the massive shuttlebay doors slide open. The skysled, with its sleek design and glowing engines, slowly backs out of the bay, the vastness of space stretching out behind it. As the skysled turns on its main engines, the camera shifts to an interior cabin view, showing Bas and Lar Kinn exchanging a final, determined nod before the vessel speeds downwards towards Anarak.* --- **Scene 9: Bridge** --- *The scene opens 30 minutes later. The tension on the Enterprise bridge is palpable as the Openlink broadcasts Bas's message and the transport inhibitor plans worldwide. The crew watches anxiously as the first inhibitors are swiftly deployed across Anarak. Suddenly, the ship's sensors beep urgently. Worf glances at his console, eyes narrowing.* **Worf:** [alarmed] "Captain, seven additional Cardassian battle cruisers have exited warp and joined Gul Bankar's ship. They're forming up and preparing to engage." **Riker:** "Red alert, forward shields to maximum." *Picard's expression hardens as the Kolarak hails them. Gul Bankar's visage appears on the viewscreen, eyes burning with fury.* **Gul Bankar:** [accusatory] "We've detected the inhibitor plans on their planet-wide network, Picard. You've broken our gentleman's agreement by sharing advanced technology with a primitive civilization. So much for Starfleet ideals! You're no match for us now. Try and stop us at your own peril." *With that, Bankar cuts off communications. Picard stands, frustration etched into his features as the fleet of eight warships begins its descent toward Anarak.* **Data:** [urgently] "Captain, the Cardassian ships are gaining speed and appear to be initiating an attack run on the planet's largest population center. Tens of millions of civilian lives are at risk, more than usual because the defensive turrets are spread out among the greater population. It is not uncommon for them to be placed on rooftops and around housing here." *The crew's tension escalates as the gravity of the situation sinks in. Picard, feeling the weight of command, turns to his officers.* **Picard:** [steady but intense] "Ideas?" **Worf:** "Captain, we could attempt to disable their weapons and transporters, focusing on minimizing their capacity to attack." **Riker:** [shaking his head] "Even so, we're outmatched. Enterprise won't survive against eight battle cruisers." **Troi:** [calm but urgent] "We just need to buy time. To give the Anarakans a chance to fully deploy their defense net. But any kind of engagement from us still risks re-igniting a war with the Cardassians." *Data, ever analytical, speaks up with a grim tone.* **Data:** "Captain, I've run millions of battle scenarios. None result in the Enterprise surviving while saving more than a few dozen lives on the surface. Our current position is untenable." *As the Cardassian warships break through the planet's stratosphere, Ensign Lavelle, stationed at comms, suddenly speaks up.* **Lavelle:** [urgently] "Captain, Bas T'yat has just sent out another message across the planet, warning of the incoming Cardassian fleet." *Picard opens his mouth and lifts his index finger to respond, but he's cut off by a sudden, blinding array of light erupting from the planet's surface, filling up the viewscreen. The bridge crew shields their eyes as the screen fills with thousands of pinpricks of light; an overwhelming launch of nuclear-armed missiles aimed directly at the Cardassian fleet.* **Worf:** [stunned] "Captain, these are nuclear-fission warheads, each with a 10-megaton yield. I've never seen a civilization with this many dirty weapons in active deployment." *The bridge falls silent as the sheer scale of the Anarakan response becomes clear. The entire hemisphere of Anarak has mobilized, proving their incredible capacity for defense, despite the lack of a centralized government.* **Data:** "Fascinating. It could be that no central authority is needed for coordination when the threat is dire. These people all appear to be responding individually with their own weapons." *The first few dozen warheads impact the Cardassian shields, which manage to absorb their blasts. But the onslaught is unrelenting. Hundreds, then thousands of warheads detonate in rapid succession, creating a cataclysmic, sustained explosion. The Cardassian ships, though formidable, are utterly overwhelmed. The viewscreen shows an apocalyptic display; a temporary star forms in Anarak's upper atmosphere, engulfing the entire Cardassian flotilla in an unprecedented, blinding flash.* **Picard:** "Helm, back off our position." *The bridge crew watches in stunned silence as the massive explosion slowly dissipates, leaving nothing but a red afterglow and the eerie silence of space. Power has gone out across the hemisphere on the planet below, but not a single molecule of the Cardassian ships remain. Picard and his crew are left in awe, mingled with a deep sense of disappointment. The enormity of what they've witnessed sinks in; a civilization so welcoming, yet still capable of such destructive power... Sso fundamentally different from the Federation's ideals. Troi closes her eyes tightly and winces, blocking out the pain of all those Cardassian deaths. Picard stands, staring out at the aftermath, the weight of the moment heavy on his shoulders.* **Picard:** [quietly, with a great sense of loss] "Such utter destruction..." *The camera pulls back, showing the Enterprise as a small silhouette against the reddish glow below.* --- **Scene 10: Bridge** --- *The scene opens minutes later with the Enterprise bridge crew still processing the aftermath of the overwhelming display of destructive power. The mood is somber as the reality of what they've witnessed lingers. Suddenly, Bas T'yat's face appears on the viewscreen, his expression a mixture of relief and satisfaction.* **Bas T'yat:** [earnestly] "Captain Picard, I wanted to thank you and your crew for everything. It seems our future is secure now, thanks to the defense network and your assistance. We're eager to move forward and hope the Federation will allow us to engage in commerce with your worlds and other peaceful civilizations." *Picard stands, his gaze steady, though his tone reflects the weight of what has transpired. He pauses for a moment, as if searching for the right words, the bridge falling into a brief, tense silence.* **Picard:** [measured, but firm] "Mister T'yat, I must be candid. While the Enterprise is pleased to have assisted in safeguarding your world, the events of today have left us with grave concerns. The way Anarak handled the Cardassians… particularly the use of nuclear warheads, demonstrates a fundamental difference in values between our societies. We cannot endorse methods that pose such a grave risk to all life, even in defence. The Federation could not, in good conscience, approve your planet for membership given these circumstances." *Bas's expression shifts to one of slight disappointment, but he remains composed.* **Bas T'yat:** "I understand, Captain. We've always been a world that does things our own way. Federation membership would have been a tough sell to my people anyway. But what about trade? Surely we can still establish commerce with Federation worlds?" *Picard nods, his tone softening slightly.* **Picard:** "Trade remains an option. We won't turn away peaceful commerce between Anarak and Federation planets. However, I must stress that the use of nuclear weapons is fundamentally at odds with Federation ethics. While I recognize their role in your planet's defense, I hope that over time, your people will explore more sophisticated and less destructive means of protection." *Bas nods again, understanding the implications of Picard's words.* **Bas T'yat:** "It's clear that today's events were... extreme. The fallout, the EMP blackouts, the atmospheric damage; we've already seen unacceptable cost. I'll do my best to guide my people toward more advanced defenses, and away from reliance on such careless weapons. It will be my penance for leading the Cardassians here." *Troi senses his guilt once again and takes a deep breath. Clearly still shaken by the loss of life, she steadies herself before offering a supportive smile.* **Troi:** "You shouldn't burden yourself with guilt, Mister T'yat. Anarak was bound to take that step sooner or later. What matters now is how you use your newfound role as an ambassador to the stars. Your actions will shape your planet's future in the galaxy." *Bas smiles, clearly grateful for the support.* **Bas T'yat:** "Thank you, Counselor. I'll do my best to live up to that responsibility." *After a few more exchanges, the connection ends, and Bas T'yat's image fades from the viewscreen. Picard takes a deep breath and turns to face his bridge crew.* **Picard:** [reflective] "We've witnessed two amazing displays of power today; one of the explosive variety, and the other of a free people's resolve. It's hard to imagine how their society works with no acceptance of authority, but today they've clearly displayed that they can accomplish amazing things working together even without any." *Worf, still perplexed, shakes his head slightly.* **Worf:** "I still don't understand how an entire planet could coordinate such a specific defense without any central leadership." *Leaning casually against the console, Riker chuckles lightly.* **Riker:** "It was in everyone's best interest, Worf. They just needed Bas's signal to know when the attack was imminent. The rest fell into place." **Worf:** "And how they could hide that many warheads from our scans? Enriched Uranium is the easiest of all elements to scan for." **Data:** "It appears that their stealth technology may be on par with our own." *Picard, his expression thoughtful, gazes out at the stars beyond the viewscreen.* **Picard:** "I'm placing a note in my log for Starfleet to leave this planet alone until they can't be ignored any longer. I believe it's for the best that we leave Anarak to chart its own course in the galaxy." *He pauses, a faint smile tugging at the corner of his mouth.* **Picard:** "I doubt we'll have trouble with them soon, at least, until they meet the Ferengi." *The bridge crew shares a quick laugh and then a quiet moment of contemplation before returning to their stations. The camera pulls back, showing the Enterprise once again poised in the vastness of space, a symbol of hope and integrity amidst the complexities of a vast and unpredictable galaxy. Fade to black.* --- --- --- ****This story is set in the Star Trek universe, created by Gene Roddenberry and owned by Paramount. I do not own any of the characters or settings from the Star Trek franchise, and this is purely a fan-made work for non-commercial purposes.****
@ 572aa884:e266a569
2024-09-04 19:46:40# STAR TREK TNG: INCOMPATIBLE IDEALS *by Luke Parker* --- **Premise**: *This screenplay is for an episode of Star Trek: The Next Generation, set near the end of Season 7. It imagines a first contact encounter between Picard’s Enterprise and a fully Anarcho-Capitalist planet with no government nor belief in authority.* --- **Scene 1: Bridge** --- *Exterior views of the Starship Enterprise give way to Captain Jean-Luc Picard standing at his command station on the bridge, his gaze steady and contemplative as he records his log.* **Picard:** (voiceover) "Captain's log, Stardate 48881.4. We were on our way to Deep Space 9 to provide support for the upcoming Bajoran elections when we received an audio-only distress call from a person on the planet Anarak, just outside of Cardassian space. The planet has yet to be contacted by the Federation, and in fact very little is known about it other than how it has a highly unusual social structure; one that appears to function without any form of central government or hierarchical leadership. It is a society that, despite its relatively high level of technological sophistication, has yet to achieve warp capability. The message is urgently requesting help from any peaceful civilization in range to defend his people against Cardassian invaders. It is difficult to imagine even the Cardassians violating the Prime Directive in such a manner. We are changing course to investigate." *Picard finishes his log entry and looks up, his expression thoughtful. The rest of the bridge crew is attentive with the memory of the Cardassain conquest of Bajor fresh in their minds.* **Data:** [turning from his console to face Picard] "Captain, Starfleet's lone anthropological record on Anarak indicates that it has a relatively large population and is advanced in various scientific fields. However, there are no reports of warp capability nor a leadership structure for us to contact there. Their society’s structure might challenge our usual protocols for contact." **Riker:** [with a hint of curiosity] "An advanced society with no central government? That's a first." **Picard:** [nodding] "Indeed, Number One. The distress call came from an individual named Bas T'yat, who identifies himself only as an entrepreneur. Our intelligence suggests that Anarak's society is structured in a way that is not only hostile to hierarchies but completely devoid of any form of leadership or authority. They seem to operate on a principle of total autonomy. This would seem to indicate an absence of a planetary defense system." **Troi:** [thoughtful, with concern] "Without a central authority, how do they respond to any external threats? A society like this could be quite vulnerable to more aggressive powers, like the Cardassians." **Picard:** [grimly] "It seems that may already be the case. The distress signal implied that a hostile force, likely Cardassian, has targeted them. Without a unified defense, they could be easy prey." **Worf:** [sternly] "If the Cardassians are involved, Captain, they will not hesitate to exploit such a weakness. We must be prepared for hostilities." **Data:** [analyzing the implications] "However, the lack of formal governance could complicate any assistance we offer. Without a government to negotiate with, we may face challenges in determining how to intervene appropriately." **Picard:** [resolute, yet cautious] "We will treat Anarak as we would any other planet sending a distress call, regardless of their social structure. However, we must tread carefully. If we arrive to find Cardassians engaged in hostile acts, we may be forced to intervene. But in Federation space, our priority remains the protection of life and the maintenance of Federation principles." *The bridge crew exchanges looks of determination, each officer understanding the complexities of the mission ahead.* **Picard:** [decisive, raising his voice slightly] "Set course for Anarak. Engage at warp seven." **Data:** [acknowledging] "Course plotted, Captain. Engaging warp seven." *The familiar hum of the warp engines intensifies as the stars on the viewscreen stretch into streaks of light, and the Enterprise leaps into warp, speeding towards the strange planet and the potential conflict awaiting them.* --- **Scene 2: Bridge** --- *The Enterprise emerges from warp above the planet Anarak, the planet’s blue-green surface appearing deceptively peaceful below.* **Worf:** [at tactical, scanning the area] "Captain, no alien vessels are currently in the vicinity, only artificial satellites. However, I'm detecting signs of recent battle on the planet's surface." **Picard:** [moving closer to Worf's station] "Specify, Lieutenant." **Worf:** [analyzing the data] "There is minor damage to infrastructure in multiple locations, consistent with Cardassian disruptor fire. Several structures show signs of targeted attacks, but the damage is localized and not extensive." **Data:** [at the science station] "Captain, I'm detecting several warp signatures leading to and from the planet. However, one of these signatures does not match any known Cardassian engine profile and is not in our warp signature database." **Riker:** [concerned, looking to Picard] "An unknown vessel in the area right around the time of a Cardassian attack? This could complicate matters." **Troi:** [sensing the tension, her voice calm but alert] "Whoever they are, they may not have the best intentions. The people of Anarak could be more vulnerable than we initially thought." *Picard ponders this information, his expression thoughtful yet wary. The bridge crew continues their scans, tension mounting as they try to make sense of the situation.* **Worf:** [interrupting the silence] "Captain, we are being hailed from the surface." **Picard:** [decisive, nodding] "On screen." *The viewscreen flickers to life, revealing the image of a middle-aged man with a rugged, practical look. He exudes an air of cautious relief, though his eyes betray a deep-seated wariness.* **Bas T'yat:** "Alien vessel, thank you for coming so quickly. My name is Bas T'yat, and I’m an entrepreneur and concerned family man. Please, can you tell me, are you an ally of the Cardassians?" **Picard:** [calm and reassuring] "Mr. T'yat, I am Captain Jean-Luc Picard of the Federation starship Enterprise. I assure you, the Federation is not aligned with the Cardassians, although we have dealt with them before, and are aware of their transgressions." **Bas T'yat:** [sighs in relief] "Thank goodness. We desperately need your help. An alien ship identifying itself as Cardassian has been harassing us for weeks. I fear they'll return soon, and we have little defense against their matter transportation technology. I'm a successful inventor and businessman, Captain. I have resources and tech that could be of value to your Federation, and I'm prepared to trade anything you want in order to help protect my people." **Picard:** [curious, leaning slightly forward] "Tell me more about these attacks. What exactly have the Cardassians done?" **Bas T'yat:** [his tone shifting to one of frustration mixed with guilt] "It started about a month ago. One of our companies, my own company, in fact, launched a new type of vessel that can travel faster than light using a warp field, the first one we've ever built. Within an hour of it's maiden voyage the Cardassians showed up. At first, they demanded to know who was in charge of the planet. They didn't like the answer they got: We are a free people and no one commands us." **Riker:** [sharing a knowing glance with Picard] "A society without centralized leadership would be difficult for the Cardassians to understand or even tolerate." **Bas T'yat:** [nodding] "That was my conclusion. They treated us like a lawless frontier, moving in to take whatever they wanted. They attacked our resource stockpiles, dematerialising and I assume stealing whatever they could before we even knew what was happening. Our ground-based defense missiles successfully took out their two smaller fighter crafts that came down into our sirspace, but we have no defense against their transporter technology. Their last visit was just a raid from orbit. They just grabbed what they could without even entering the atmosphere and left within minutes." **Picard:** [thoughtful, with a hint of concern] "I see. There are widely-agreed-upon rules against this type of behavior, I assure you. However, since the Federation has never made contact with your people before now, we are unfamiliar with the proper etiquette for such a first encounter. How do you suggest we proceed safely for an official meeting?" *Bas pauses, visibly perplexed by the concept of "official" procedures, his expression almost amused.* **Bas T'yat:** [with a chuckle] "Official meeting? Captain, just come on down and park your craft outside my coordinates. My wife will make us all some refreshments." **Picard:** [with a slight smile, yet maintaining formality] "We appreciate the hospitality, Mr. T'yat, but we prefer to beam down if that's acceptable to you. We can be there in a few minutes." **Bas T'yat:** [nervous but agreeable] "Beam down? Uh, sure, that's fine. I was wondering if that technology worked on people. Love to see it in action." **Picard:** [nodding respectfully] "Understood. I'll be down with a small team to meet you outside your building shortly. Picard out." *The screen goes dark as the connection ends, leaving the bridge crew to process the encounter.* **Riker:** [with a wry smile] "Drinks with the locals; sounds like fun." **Troi:** [softly, but with insight] "He's nervous, but also hopeful. I'm sensing some hurt pride in him, too, Captain. This is likely the first time his people have ever had to reach out to anyone off-world for help. His pride may cloud his ability to fully grasp the dangers they’re facing." **Picard:** [serious, standing up to address the crew] "On top of being an official first contact, the Cardassians have made this a very delicate situation. We must be prepared for anything. Counselor Troi, Data, and La Forge, you're with me. Number one, you have the bridge." *The crew nods in understanding as the away team heads to the turbolift. The tension in the air is palpable as they ready themselves for what may be a challenging first contact and a possible hostile encounter with the Cardassians.* --- **Scene 3: Bas T’yat’s Front Lawn** --- *The team materializes on the surface of Anarak, just outside of a large, elegant house set in a lush, rural landscape. The area is a blend of modern luxury and natural beauty, though signs of recent damage are evident. Smoke still rises from a nearby hangar, the aftermath of the Cardassian attack clear in the smoldering ruins. As the team takes in their surroundings, a group of locals approaches. At the forefront is Bas T'yat, flanked by a few colleagues. He's a middle-aged man with a commanding presence, dressed in practical yet fine clothing. His stride is confident, and his eyes sharp with the determination of a man used to getting what he wants. Bas’s face lights up with a mixture of curiosity and enthusiasm as he sees the away team.* **Bas T'yat:** [warmly, holding his palms upwards and then extending one hand towards Picard in a greeting] "Captain Picard! Welcome to Anarak! I'm Bas T'yat. It is my honor to meet you." **Picard:** [imitating the hand motion, with a polite smile] "The honor is ours, Mr. T'yat. Thank you for your hospitality. May our two peoples forever live in harmony." *Bas gestures to the smoldering hangar in the distance, his tone tinged with frustration.* **Bas T'yat:** [with a sigh] "That would be wonderful. I do wish the circumstances for your visit were better. [clenching his fists] That's my hangar over there, or what's left of it, anyway. The Cardassians destroyed it and the spacecraft I designed and built there. It was our first warp vessel, one that the whole world cheered on at launch just last month. We were going to colonize the asteroids with it." **Geordi:** [To Picard, gesturing towards the wreckage] "If I may, Captain?" **Picard:** "Certainly." [To Bas T'yat] "This is my head engineer, Commander Geordi La Forge." **Geordi:** [stepping forward] "Mr. T'yat, if it's alright with you, I'd like to examine the wreckage. I might be able to determine if anything is salvageable." **Bas T'yat:** [nodding, gesturing to a colleague] "Of course. Lar Kinn here is our chief pilot. He made the historic first flight and he'll take you to the hangar and help with anything you need." *Geordi and Lar Kinn head towards the hangar, with Geordi hoping to confirm if this was the source of the warp signature detected in orbit. Meanwhile, Bas leads Picard, Troi, and Data toward his house. As they walk, Bas impatiently answers a few questions about his planet, his voice tinged with annoyance and concern.* **Data:** “Mr. T’yat, if I may, I notice that your neighborhood’s infrastructure is well taken care of. If Anarak has no central authority of any kind, who is responsible for keeping the roads and infrastructure?” **Bas T'yat:** ”Well, as a rule of thumb, if it’s on my land, I am. If it’s not on my land, then someone else is, but I may have to pay them to use it. They look so nice because we all get better insurance rates for keeping them that way.” **Data:** “Curious. And who initiates larger projects like mass transportation and research?” **Bas T'yat:** [slightly annoyed] “They are all risky endeavors taken by entrepreneurs like myself. Sometimes profits take decades to appear, but like with my new warp engine, I’m sure they’ll make me a huge fortune one day.” [turning to ensure Picard can hear him] "Anyway, I fear the Cardassians aren't done with us. They've stopped even trying to make demands of us, which makes me think they're planning something bigger. Perhaps a larger assault. We've been able to fend them off so far, but I have no clue how to defend against those transporter devices." **Picard:** [impressed] "It is remarkable that your society, with no planetary defense force, was able to repel Cardassian military forces, even if only temporarily. Cardassian ships are known for their significant weapons and shields." **Bas T'yat:** [with a hint of pride] "The people of Anarak are no strangers to defending themselves. We have numerous private protection agencies, each with advanced missile fortifications and other kinds of defenses to protect every inch of this planet. But these were designed to fend off terrorists or rival companies, not an alien invader." *They reach the entrance to Bas's home. He pauses before entering, turning to Picard with a serious expression.* **Bas T'yat:** [earnestly] "Captain, I'm prepared to trade for whatever defensive technology you can provide, especially something to counter the Cardassian's transporter technology. I am confident that our ground defenses can take out their shuttlecraft, but we're helpless against their ability to beam in and out at will." *Picard pauses, his face reflecting the weight of his decision before he speaks.* **Picard:** [in his most diplomatic tone] "Mr. T'yat, the Federation is committed to helping those in need, and we don't tolerate bullies. However, there are restrictions on the technology we can share, particularly weaponry. Also, the Federation's assistance often depends on whether a planet is on the path to becoming a member. We must ensure that our values align. In this case, a diplomatic approach might bring a far more lasting peace than simply escalating an arms race." *Bas considers this, his optimism tinged with caution. The group moves into a large room with lots of seating where a warm drink much like tea is offered. Picard partakes graciously.* **Bas T'yat:** [thoughtfully] "I see. Federation membership is... a complicated idea. I'm sure many heads of companies like myself would welcome it, but for the whole planet to become a singular member of any larger federation is hard to imagine. Our society values individual freedom above all else, and I'm not sure how compatible everyone here is with the Federation's ideals." **Data:** "The benefits of Federation membership are considerable. Could not your people one day vote on the issue to see if a majority wants to join after taking ample time to research membership?" **Bas T'yat:** [skeptically] "Voting is something that hasn't been done here for tens of thousands of years. We consider it to be archaic, a form of slavery of the minority. Honestly, I'm surprised your culture still practices it." **Picard:** [nodding, a little embarrassed] "I see. Rest assured that we try to only vote on things that have every participant's full consent. You'll find that this is very common among the races you meet as your people start to explore the stars. But until then, know that the Federation's primary concern is the safety of everyone in Federation space, including your people." *While inside Bas's home, Data discreetly connects to an open network connection, accessing Anarak's version of the internet called the Openlink. His eyes flicker left to right at an inhuman speed as he analyzes the planet's defenses and infrastructure.* **Data:** [quietly, to Picard as he processes the data] "Captain, while there are many advanced technologies in the hands of individuals and companies, I find no evidence of any kind of unified military infrastructure. The defense efforts are completely decentralized, which will surely prove problematic in the event of a full-scale Cardassian invasion." **Picard:** [grimly] "Given the Cardassians' history, we must prepare for the worst." *Just then, Geordi returns from the hangar, his expression a mix of curiosity and concern.* **Geordi:** "Captain, I've confirmed that Bas's ship was the source of the warp signature we detected. Unfortunately, the wreckage isn't salvageable. It could be a long time before Anarak returns to the stars." **Bas T'yat:** [with a determined grin] "I wouldn't say that. My first flight was widely publicized. Lar Kinn and I are celebrities now. Hundreds of other companies are likely working on similar technology already. Some of us refer to it as 'the great space race,' with the goal of creating the first off-world colony, and my company is currently in the lead." **Picard:** [with a slight smile, impressed by the resilience] "It seems the people of Anarak are not to be counted out yet. Your intrepid spirit will serve you well as Anarakans start exploring the Galaxy." **Troi:** [warmly] "Your optimism is admirable, Mr. T'yat. But remember, resilience is strongest when combined with caution." **Bas T'yat:** [nodding, appreciatively] "Wise words, Miss Troi. Hopefully with your help we'll be ready for whatever comes next." **Picard:** [ready to leave] "This tea is delicious, thank you for your hospitality. Next I'll need to talk to my superiors at Starfleet headquarters before we can proceed any further. I'll be sure and pass your concerns and needs on to them and then we'll contact you again later today." *The away team prepares to depart, with Bas expressing his thanks once more. As they beam back to the Enterprise, each member reflects on the unique challenges of Anarak.* --- **Scene 4: Picard’s ready room** --- *Minutes later, Captain Picard sits alone in his ready room, the vast starscape of space visible through the window behind him. His posture is straight, and the weight of the decision before him is clear in his eyes. He taps a command into his desk console, and the screen flickers to life with the familiar stern face of Vice Admiral Alynna Nechayev. Her image on the screen is as imposing as ever.* **Picard:** [calmly, but with underlying urgency] "Admiral, I've just concluded a preliminary contact with a representative of Anarak, just a few light years this side of Cardassian space. The situation is more complex than anticipated. The planet is under threat from the Cardassians; specifically Gul Bankar, who's been making increasingly aggressive moves from orbit. Meanwhile, the society on Anarak is... unconventional. They have no central government, no formal leadership nor military structure. The entire planet operates under a decentralized, anarchic, commerce-based system." **Nechayev:** [eyes narrowing] "Anarchists? No structure? That's not exactly an encouraging environment for a first contact, Jean-Luc. **Picard:** “Admiral, they’ve managed to develop warp technology without either a government or military. It’s a remarkable feat, but one that leaves them vulnerable.” **Nechayev:** “Are you certain there’s no one in authority at all? Not even an ambassador?" **Picard:** [nodding] "Precisely. Their social structure wouldn’t allow it. Our first contact has been with an individual and his family, one Bas T'yat; a wealthy businessman and the inventor of their first warp-capable ship. He's requesting assistance to defend against further Cardassian attacks, but without a central authority, assisting one individual could have unpredictable consequences." **Nechayev:** [questioning sharply] "Hmm. And what of the Cardassians? Is there any evidence of their involvement?" **Picard:** [gravely] "Plenty. The Cardassians have already raided the planet, seizing valuable resources. Their ship left orbit shortly before our arrival, but the threat of their return looms large. Bas T'yat is convinced they'll come back with a larger force." *Nechayev pauses, her expression hardening as she considers the situation.* **Nechayev:** [warningly] "Starfleet cannot afford to be drawn into deeper hostilities with the Cardassian Union, Jean-Luc. Especially not over a non-member world. You must tread carefully. A diplomatic solution is paramount, and under no circumstances should you provide this Bas T'yat with advanced defensive technology. The Prime Directive is clear; we don't interfere with the internal affairs of non-member worlds, and besides, you haven't even made proper first contact with the planet, only with one family." **Picard:** [measured, but firm] "Admiral, with respect, Anarak is far more advanced than many worlds we've encountered. Their technological capabilities, while decentralized, are impressive. Now that they are getting their space legs it won't be long before Anarakans are showing up in ports across the quadrant. And if the Cardassians establish a foothold here, it could destabilize the entire region." *Nechayev's face softens slightly, recognizing the gravity of the situation. She sighs, her resolve shifting as she weighs the options.* **Nechayev:** [reluctantly] "Alright, Jean-Luc. I don’t like this, but I trust your judgement. You may share transport inhibitor technology. Only enough to help them counter the Cardassians' beaming technology, but nothing more. And remember, this Bas T'yat doesn't speak for his whole planet. Try to treat his family like you would if you found them alone in a spaceship." **Picard:** "Understood, Admiral. I'll proceed with caution." **Nechayev:** [more sternly] "Just don't start another war, Jean-Luc." *The screen goes dark. Picard leans back in his chair, the weight of the decision pressing on him. He stands, smoothing his uniform, and exits the ready room onto the bridge.* --- **Scene 5: Bridge** --- *On the bridge, the atmosphere is tense as the crew processes the situation. Picard steps up to his command chair, addressing the senior officers who have gathered.* **Picard:** [seriously] "Admiral Nechayev has authorized us to share transport inhibitor technology with Anarak to help them defend against further Cardassian raids. But we must be mindful of the ethical implications of our actions." **Dr. Crusher:**: [concerned] "Captain, I'm worried about the consequences of becoming involved in this situation. If we assist Anarak, it could escalate into a larger conflict--one that could draw the Federation into another war with the Cardassians." **Worf:** [gruffly, with resolve] "But allowing the Cardassians to plunder a defenseless society is equally unacceptable, Doctor. We have a responsibility to protect the vulnerable." **Picard:** [thoughtfully, considering both viewpoints] "I'm inclined to agree with Worf on this one, Beverly. We must work fast to deploy the inhibitors wherever we can, but that does bring up another problem. The Prime Directive prevents us from interfering in the internal affairs of non-member worlds. And giving one individual on Anarak access to advanced technology could upset the delicate balance of their society. What if Bas T'yat's company gains a monopoly on defense technology? It could shift the power dynamics on the entire planet." **Troi:** [insightfully, her voice calm] "Captain, I sense that Bas T'yat is deeply worried about his planet's future. He feels a strong sense of responsibility and guilt for the attacks... I don't think that he had any way to know that their warp signature would act as a beacon to those seeking resources. They didn't even know other life forms existed until the Cardassians arrived. It's clear that Anarakans weren't prepared for the reality of interstellar contact." **Picard:** [resolved] "I agree, Counselor. We're dealing with a society that is both advanced and vulnerable. A dangerous combination. We must proceed carefully." *Picard considers this, his brow furrowed in thought. Finally, he makes a decision.* **Picard:** [decisively] "We must proceed, however. I'll invite Bas T'yat to the Enterprise to discuss the situation further. We will ensure that any assistance we provide doesn't destabilize their society, or escalate the conflict." *Picard hails Bas T'yat from his command station.* **Picard:** [calmly] "Mr. T'yat, I'd like to invite you aboard the Enterprise to discuss our options in person." *The main screen fills with T'yat's face again.* **Bas T'yat:** [with a hint of hesitation] "Thank you, Captain, I accept. But I'd prefer to take my own craft... Still not quite comfortable with the transporter technology, if you'll understand. I'll bring my wife, L'anna, and my pilot, Lar Kinn." **Picard:** [diplomatic, nodding slightly] "Understood. We'll be ready to receive you in the shuttlebay.” --- **Scene 6: Main Shuttlebay** --- *In the Enterprise's shuttlebay, the crew prepares to greet their visitors. The doors slide open, and a sleek, streamlined skysled enters the bay, guided by Lar Kinn at the controls. The craft settles gently onto the deck, and the hatch opens. Bas T'yat steps out, accompanied by his wife, L'anna, and Lar Kinn, who looks around the shuttlebay with wide-eyed curiosity. Picard, Troi, and Data are there to meet them, offering warm greetings as the Anarakans take in the impressive sight of the Enterprise's interior.* **Picard:** [welcoming, with a gesture towards the ship] "Welcome aboard the Enterprise, Mr. and Mrs. T'yat. I trust your journey was smooth?" **Bas T'yat:** [grinning, clearly impressed] "Very much so, Captain. Your ship is... well, it's more than I imagined. Thank you for having us." *Troi steps forward, offering a kind smile.* **Troi:** [invitingly] "If you'd like, I can give you a tour of the ship. We're quite proud of our vessel, and I think you'll find it fascinating." *L'anna's eyes widen with excitement, and she nods eagerly. Bas exchanges a look with Lar Kinn, just catching up to the group. He seems just as eager to explore as the others, and nods excitedly to Troi.* **Bas T'yat:** [appreciatively] "We'd be honored. Lead the way, Counselor." **Lar Kinn:** So can all these shuttles go faster than light? *With that, the group sets off on a tour of the Enterprise, the Anarakans marveling at the advanced technology and seamless design of the Federation starship. As they walk, Troi can't help but notice the mix of awe and determination in Bas T'yat an inventor and leader who knows that his world's future may very well depend on the choices made in the hours to come.* --- **Scene 7: Bridge** --- *The scene opens as Counselor Troi leads Bas T'yat, L'anna, and Lar Kinn onto the bridge of the Enterprise. The visitor's awe is palpable as they take in the grandeur of the ship's command center. Picard, standing near the captain's chair, barely has a moment to welcome them when a sudden alert draws everyone's attention.* **Data:** [at his station, voice urgent] "Captain, I'm detecting the return of the Cardassian battle cruiser. It is registered as the Kolarak. It just popped out from behind the home star and is entering orbit around Anarak." **Riker:** "Yellow alert. On screen." *Picard immediately straightens, his expression shifting from welcoming to resolute. The tension on the bridge heightens as the viewscreen flickers to life, displaying the imposing sight of the Kolarak. The Cardassian vessel looms in space, its dark hull bristling with weaponry.* **Picard:** [calmly, but with authority] "Mr. Worf, open a channel to the Kolarak." *The screen quickly reveals the stern visage of a Cardassian Gul in his command chair. His eyes narrow as he takes in the sight of the bridge crew and the unfamiliar faces of Bas and his companions.* **Picard:** [with measured politeness] "I am Captain Jean-Luc Picard of the Federation starship Enterprise. With whom am I speaking?" **Gul Bankar:** [with a sneer, his voice dripping with condescension] "You may address me as Gul Bankar." **Picard:** "Gul Bankar, there have been reports of your vessel causing harm and stealing resources from the planet below. With me is Bas T'yat, the owner of the warp-capable vessel that it appears your forces destroyed on the surface. We request an explanation for these hostilities." **Gul Bankar:** "Captain Picard, your presence here is an unwelcome interference. This planet, and its inhabitants, are under Cardassian protection. You will withdraw immediately, leaving Anarak to our care." *Picard's gaze hardens, but his tone remains calm and firm.* **Picard:** [skeptically] "Cardassian protection? Anarak lies within Federation territory. We received a distress call and are here to provide assistance." *Bankar's expression darkens, his eyes flashing with anger.* **Gul Bankar:** [coldly] "The Federation's meddling in this region is all too well documented, Picard, but Anarak is too close to Cardassian space for your interference to be tolerated. I find your so-called assistance nothing more than another prelude to annexation." *Bas, standing beside Troi, listens intently, his face reflecting a mixture of concern and frustration. Picard, sensing the rising tension, steps closer to the viewscreen.* **Picard:** [with resolve] "The Federation respects the sovereignty of all worlds. We are only here because of your aggressive actions, not to claim this planet. We have long worked to maintain peace in this sector, and I would hate to see that peace jeopardized by your reckless actions here." **Gul Bankar:** [sarcastically] "Peace? The Federation's control of Terok Nor and the Bajoran wormhole is hardly a gesture of peace. It was a clear power grab, one that we will not allow to extend to Anarak." *Picard's eyes narrow, his voice taking on a steely edge.* **Picard:** [firmly] "Gul Bankar, a conflict between the Federation and the Cardassian Union would serve no one's interests, especially not over a planet that is so new to the neighborhood. I suggest you contact your superiors before taking any further aggressive actions." *There's a tense silence as Bankar considers Picard's words, his eyes flicking to Bas and then back to Picard. Finally, he lowers his head in a slight nod, though his expression remains hostile.* **Gul Bankar:** [grudgingly] "Very well, Captain. I will contact Central Command. But understand this; Anarak will not fall under Federation control, and I will ensure that Cardassia's interests are protected. I will contact you again in 4 hours." *The transmission abruptly cuts off, leaving the bridge in a heavy silence. The Kolarak remains on the viewscreen, hovering ominously in space, nose to nose with the Enterprise now. Picard exhales, turning to face his crew.* **Picard:** [calmly, but with an undertone of urgency] "Maintain our position and yellow alert, Mr. Worf, and monitor the Kolarak for any signs of hostile activity." *Worf gives a curt nod, his eyes never leaving the tactical display.* **Worf:** [with determination] "Aye, Captain. Shields at maximum, weapons ready." *Picard then turns to Bas, who is visibly shaken but trying to maintain his composure.* **Picard:** [reassuringly] "Mr. T'yat, I understand this is a difficult situation and you don't yet know who to trust, but I assure you that we aim to keep the peace in this sector and will do everything in our power to ensure your planet's safety. We ask nothing in return from the Anarakan people. However, it is crucial that we handle this matter diplomatically." *Bas nods, though his expression is one of deep concern.* **Bas T'yat:** [uneasily] "I appreciate that, Captain, and don't worry, nothing that Gul Bankar says will make me trust his offer of "protection" after he destroyed my ship and stole resources from all over the planet. But I do worry that he’s using this time to call for reinforcements." *Picard places a reassuring hand on Bas's shoulder, his voice steady.* **Picard:** [confidently] "If he attacks, we'll face that challenge together, Mr. T'yat. You are free to return to the surface at any time but for now, I think it best that we consider how fast we could deploy our transporter inhibitor technology on your planet." **Bas T'yat:** [enthusiastically] "You mean you're willing to sell us devices that can stop them from beaming up our resources?" **Picard:** "Or beaming their troops down. And we wouldn't sell it to you, it is our gift. The Federation doesn't sell it's assistance to those in need." *The visitors faces all brighten in unison with relief.* **L'anna:** "I don't know how we could ever thank you enough, Captain. This means everything to our people." **Picard:** "Don't thank us yet, there is still the issue of deploying enough of them in time. If they're going to attack in 4 hours you'd need them set up near all the most valuable targets at the very least. They'll need a steady supply of energy, too." *Bas furls his lips in concerned thought.* **Data:** "Captain, I've analyzed all of the planet's most valuable resource depots that our scanners can detect and I see 168 unique locations that we should set up transport inhibitors. There may, of course, be other targets too that they would want." **Riker:** [apprehensively] "That's way too many for us to replicate in time, much less visit each location to install within the next 4 hours." **Picard:** "We need a way to speed up that deployment, at least to enough sites that will show Gul Bankar that things have changed... And hopefully without him detecting our movements." **Bas T'yat:** "If I may captain, I think I know a better way to deploy them if I can just make a detailed scan of one and save it to our printer file format... We don't have your transporter technology, but our device printers are able to scan and quickly reproduce any technological device that we can identify the components of." **Riker:** "And how will that help distribute them to everyone in time?" **Bas T'yat:** "Simple, every business and household has one of these printers. I can upload the scanned file to our Openlink and tell all of Anarak in one broadcast about the imminent threat and how to protect themselves from it with one of these inhibitors. They'll pop out thousands of them in time." **Picard:** "That sounds very promising, Mr. T’yat. But I want your assurance that your company will not hold any sort of monopoly on this technology or otherwise profit from it; In lieu of a government, the Federation requires that this gift be made to your whole planet at once." **Bas T'yat:** [after some hesitation] "Alright, Captain. You have my promise. Giving up some profits is the least I can do to make up for attracting the Cardassians to Anarak." *Picard looks visibly relieved, giving a curt nod to Bas.* **Picard:** "Data, take our guests to engineering and grab whomever you may need to assist you with making this happen in time. Remember, you’ll also need to show the Anarakans how to use these devices." **Data:** "Aye sir." [To the visitors] "If you'll follow me please, we'll be able to work on this in engineering." *Data, Bas, Lar Kinn, and L'anna walk briskly to the turbolift. The scene closes with Picard returning to his command chair, the bridge crew resuming their stations as the standoff between the Enterprise and the Kolarak continues. The two ships remain locked in silence, nose to nose, as the 4-hour countdown begins.* --- **Scene 8: Main Engineering** --- *The scene opens in Main Engineering, where Geordi La Forge, Data, and Ensign Sam Lavelle are putting the final touches on the scan for their transport inhibitor device. Bas T'yat and Lar Kinn stand nearby, observing the process with keen interest. The atmosphere is tense, underscored by the ticking clock counting down the hours until Gul Bankar's deadline.* **Geordi:** [focused as he works] "All right, that should do it. The scan of this transport inhibitor is ready, and the data's been formatted for your printers." *He hands a datapad to Bas, who takes it with a mix of curiosity and nervousness.* **Geordi:** [reassuringly] "You'll be able to upload the complete plans from this device, including an adapter for your power source. Once it's on your network, anyone with Openlink access will be able to build and deploy these inhibitors in a matter of minutes. It's up to you, however, to convince them to do that." **Bas T'yat:** [relieved] "Thank you, Commander. I'm sure many will manage it in time, but I just hope it's enough." **Lavelle:** [chiming in, pointing to the datapad] "Also I've included a detailed instruction set too. It explains how to set the units up and operate them." *Bas nods his thanks, flipping through the instructions as Lar Kinn looks over his shoulder.* **Data:** [ever precise, offering a suggestion] "Mr. T'yat, given the standoff outside, it may be prudent to avoid the use of the transporter. The Kolarak is likely monitoring our actions closely. Sending the plans with you aboard the skysled would appear less provocative." *Bas looks visibly relieved at the suggestion, nodding in agreement.* **Bas T'yat:** [grateful] "Thank you, we'd prefer not having our atoms scattered throughout the atmosphere today anyway." **Geordi:** [nodding, humorously] "No problem. We'll make sure the skysled is ready to go." *Data gestures toward the exit of Engineering, indicating it's time to depart.* **Data:** [calmly, but with urgency] "We should make our way to the shuttlebay. There's less than two hours remaining before the Gul's deadline. It's imperative that as many Anarakans as possible receive these plans in time." *Bas and Lar Kinn exchange a look, their expressions set with determination as they follow Data out of Engineering. The camera follows the group as they walk briskly through the corridors of the Enterprise.* **L'anna:** "You'll be sure to tell the Captain and Councilor Troi that we said goodbye?" **Data:** "Of course. And let me say that I find your culture truly intriguing, and hope we get the chance to visit again in the future, no matter if Anarak chooses Federation membership or otherwise." **Bas T'yat:** "You'd be our welcome guest anytime, Mr. Data. I think you'd most enjoy seeing the progress my people have made with robotics and artificial intelligence. My company produces one of the best-selling android assistants on the market." **Data:** "Fascinating. I look forward to it. Here we are." *As they reach the shuttlebay, the large bay doors slide open, revealing the sleek skysled waiting for them. The ship is prepped and ready for launch, its engines humming with quiet power.* **Data:** [pausing as their ship's door opens] "We wish you a safe journey, Mr. T'yat, L'anna, Mr. Kinn." **Bas T'yat:** [nodding, with resolve] "We'll make sure everyone gets these plans. Thank you, Commander Data." *Lar Kinn gives Data a respectful nod before they step onto the skysled. Data watches as they take their positions inside the cockpit. Data then taps his communicator, his voice steady.* **Data:** "Data to the Bridge, our visitors are ready to depart." *The camera cuts to the exterior of the Enterprise, where the massive shuttlebay doors slide open. The skysled, with its sleek design and glowing engines, slowly backs out of the bay, the vastness of space stretching out behind it. As the skysled turns on its main engines, the camera shifts to an interior cabin view, showing Bas and Lar Kinn exchanging a final, determined nod before the vessel speeds downwards towards Anarak.* --- **Scene 9: Bridge** --- *The scene opens 30 minutes later. The tension on the Enterprise bridge is palpable as the Openlink broadcasts Bas's message and the transport inhibitor plans worldwide. The crew watches anxiously as the first inhibitors are swiftly deployed across Anarak. Suddenly, the ship's sensors beep urgently. Worf glances at his console, eyes narrowing.* **Worf:** [alarmed] "Captain, seven additional Cardassian battle cruisers have exited warp and joined Gul Bankar's ship. They're forming up and preparing to engage." **Riker:** "Red alert, forward shields to maximum." *Picard's expression hardens as the Kolarak hails them. Gul Bankar's visage appears on the viewscreen, eyes burning with fury.* **Gul Bankar:** [accusatory] "We've detected the inhibitor plans on their planet-wide network, Picard. You've broken our gentleman's agreement by sharing advanced technology with a primitive civilization. So much for Starfleet ideals! You're no match for us now. Try and stop us at your own peril." *With that, Bankar cuts off communications. Picard stands, frustration etched into his features as the fleet of eight warships begins its descent toward Anarak.* **Data:** [urgently] "Captain, the Cardassian ships are gaining speed and appear to be initiating an attack run on the planet's largest population center. Tens of millions of civilian lives are at risk, more than usual because the defensive turrets are spread out among the greater population. It is not uncommon for them to be placed on rooftops and around housing here." *The crew's tension escalates as the gravity of the situation sinks in. Picard, feeling the weight of command, turns to his officers.* **Picard:** [steady but intense] "Ideas?" **Worf:** "Captain, we could attempt to disable their weapons and transporters, focusing on minimizing their capacity to attack." **Riker:** [shaking his head] "Even so, we're outmatched. Enterprise won't survive against eight battle cruisers." **Troi:** [calm but urgent] "We just need to buy time. To give the Anarakans a chance to fully deploy their defense net. But any kind of engagement from us still risks re-igniting a war with the Cardassians." *Data, ever analytical, speaks up with a grim tone.* **Data:** "Captain, I've run millions of battle scenarios. None result in the Enterprise surviving while saving more than a few dozen lives on the surface. Our current position is untenable." *As the Cardassian warships break through the planet's stratosphere, Ensign Lavelle, stationed at comms, suddenly speaks up.* **Lavelle:** [urgently] "Captain, Bas T'yat has just sent out another message across the planet, warning of the incoming Cardassian fleet." *Picard opens his mouth and lifts his index finger to respond, but he's cut off by a sudden, blinding array of light erupting from the planet's surface, filling up the viewscreen. The bridge crew shields their eyes as the screen fills with thousands of pinpricks of light; an overwhelming launch of nuclear-armed missiles aimed directly at the Cardassian fleet.* **Worf:** [stunned] "Captain, these are nuclear-fission warheads, each with a 10-megaton yield. I've never seen a civilization with this many dirty weapons in active deployment." *The bridge falls silent as the sheer scale of the Anarakan response becomes clear. The entire hemisphere of Anarak has mobilized, proving their incredible capacity for defense, despite the lack of a centralized government.* **Data:** "Fascinating. It could be that no central authority is needed for coordination when the threat is dire. These people all appear to be responding individually with their own weapons." *The first few dozen warheads impact the Cardassian shields, which manage to absorb their blasts. But the onslaught is unrelenting. Hundreds, then thousands of warheads detonate in rapid succession, creating a cataclysmic, sustained explosion. The Cardassian ships, though formidable, are utterly overwhelmed. The viewscreen shows an apocalyptic display; a temporary star forms in Anarak's upper atmosphere, engulfing the entire Cardassian flotilla in an unprecedented, blinding flash.* **Picard:** "Helm, back off our position." *The bridge crew watches in stunned silence as the massive explosion slowly dissipates, leaving nothing but a red afterglow and the eerie silence of space. Power has gone out across the hemisphere on the planet below, but not a single molecule of the Cardassian ships remain. Picard and his crew are left in awe, mingled with a deep sense of disappointment. The enormity of what they've witnessed sinks in; a civilization so welcoming, yet still capable of such destructive power... Sso fundamentally different from the Federation's ideals. Troi closes her eyes tightly and winces, blocking out the pain of all those Cardassian deaths. Picard stands, staring out at the aftermath, the weight of the moment heavy on his shoulders.* **Picard:** [quietly, with a great sense of loss] "Such utter destruction..." *The camera pulls back, showing the Enterprise as a small silhouette against the reddish glow below.* --- **Scene 10: Bridge** --- *The scene opens minutes later with the Enterprise bridge crew still processing the aftermath of the overwhelming display of destructive power. The mood is somber as the reality of what they've witnessed lingers. Suddenly, Bas T'yat's face appears on the viewscreen, his expression a mixture of relief and satisfaction.* **Bas T'yat:** [earnestly] "Captain Picard, I wanted to thank you and your crew for everything. It seems our future is secure now, thanks to the defense network and your assistance. We're eager to move forward and hope the Federation will allow us to engage in commerce with your worlds and other peaceful civilizations." *Picard stands, his gaze steady, though his tone reflects the weight of what has transpired. He pauses for a moment, as if searching for the right words, the bridge falling into a brief, tense silence.* **Picard:** [measured, but firm] "Mister T'yat, I must be candid. While the Enterprise is pleased to have assisted in safeguarding your world, the events of today have left us with grave concerns. The way Anarak handled the Cardassians… particularly the use of nuclear warheads, demonstrates a fundamental difference in values between our societies. We cannot endorse methods that pose such a grave risk to all life, even in defence. The Federation could not, in good conscience, approve your planet for membership given these circumstances." *Bas's expression shifts to one of slight disappointment, but he remains composed.* **Bas T'yat:** "I understand, Captain. We've always been a world that does things our own way. Federation membership would have been a tough sell to my people anyway. But what about trade? Surely we can still establish commerce with Federation worlds?" *Picard nods, his tone softening slightly.* **Picard:** "Trade remains an option. We won't turn away peaceful commerce between Anarak and Federation planets. However, I must stress that the use of nuclear weapons is fundamentally at odds with Federation ethics. While I recognize their role in your planet's defense, I hope that over time, your people will explore more sophisticated and less destructive means of protection." *Bas nods again, understanding the implications of Picard's words.* **Bas T'yat:** "It's clear that today's events were... extreme. The fallout, the EMP blackouts, the atmospheric damage; we've already seen unacceptable cost. I'll do my best to guide my people toward more advanced defenses, and away from reliance on such careless weapons. It will be my penance for leading the Cardassians here." *Troi senses his guilt once again and takes a deep breath. Clearly still shaken by the loss of life, she steadies herself before offering a supportive smile.* **Troi:** "You shouldn't burden yourself with guilt, Mister T'yat. Anarak was bound to take that step sooner or later. What matters now is how you use your newfound role as an ambassador to the stars. Your actions will shape your planet's future in the galaxy." *Bas smiles, clearly grateful for the support.* **Bas T'yat:** "Thank you, Counselor. I'll do my best to live up to that responsibility." *After a few more exchanges, the connection ends, and Bas T'yat's image fades from the viewscreen. Picard takes a deep breath and turns to face his bridge crew.* **Picard:** [reflective] "We've witnessed two amazing displays of power today; one of the explosive variety, and the other of a free people's resolve. It's hard to imagine how their society works with no acceptance of authority, but today they've clearly displayed that they can accomplish amazing things working together even without any." *Worf, still perplexed, shakes his head slightly.* **Worf:** "I still don't understand how an entire planet could coordinate such a specific defense without any central leadership." *Leaning casually against the console, Riker chuckles lightly.* **Riker:** "It was in everyone's best interest, Worf. They just needed Bas's signal to know when the attack was imminent. The rest fell into place." **Worf:** "And how they could hide that many warheads from our scans? Enriched Uranium is the easiest of all elements to scan for." **Data:** "It appears that their stealth technology may be on par with our own." *Picard, his expression thoughtful, gazes out at the stars beyond the viewscreen.* **Picard:** "I'm placing a note in my log for Starfleet to leave this planet alone until they can't be ignored any longer. I believe it's for the best that we leave Anarak to chart its own course in the galaxy." *He pauses, a faint smile tugging at the corner of his mouth.* **Picard:** "I doubt we'll have trouble with them soon, at least, until they meet the Ferengi." *The bridge crew shares a quick laugh and then a quiet moment of contemplation before returning to their stations. The camera pulls back, showing the Enterprise once again poised in the vastness of space, a symbol of hope and integrity amidst the complexities of a vast and unpredictable galaxy. Fade to black.* --- --- --- ****This story is set in the Star Trek universe, created by Gene Roddenberry and owned by Paramount. I do not own any of the characters or settings from the Star Trek franchise, and this is purely a fan-made work for non-commercial purposes.**** @ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17When I have stale bread, I often use it to make a bread salad. The base is croutons of stale bread and then there are no limits to your imagination. In this salad there was also - Onions stewed in balsamic vinegar - Spring onions (raw) - Cherry tomatoes - Eggplants and sweetcorn (fried, lukewarm) - Pine nuts - Finely sliced cheese - Basil https://image.nostr.build/ce0c7490f2adbd2aa4ccdfe80203a15dbb10686859a3256a0147d5f423478fd0.jpg https://image.nostr.build/f930e0984ec9603b84c7a7868a97486140ee44590590102f7e460bfbfd3d70be.jpg originally posted at https://stacker.news/items/672404
@ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17When I have stale bread, I often use it to make a bread salad. The base is croutons of stale bread and then there are no limits to your imagination. In this salad there was also - Onions stewed in balsamic vinegar - Spring onions (raw) - Cherry tomatoes - Eggplants and sweetcorn (fried, lukewarm) - Pine nuts - Finely sliced cheese - Basil https://image.nostr.build/ce0c7490f2adbd2aa4ccdfe80203a15dbb10686859a3256a0147d5f423478fd0.jpg https://image.nostr.build/f930e0984ec9603b84c7a7868a97486140ee44590590102f7e460bfbfd3d70be.jpg originally posted at https://stacker.news/items/672404 @ 469fa704:2b6cb760
2024-09-04 15:22:28## Money Printing in general First of all, we need to make a distinction between money creation by central banks and fractional-reserve banking. Usually, the term money printing or “printer goes brrrrrr” refers to the creation of new central bank money, which is primarily created by central banks through: * **Open Market Operations**: Buying government securities, which injects money into the banking system by increasing bank reserves. This is often done electronically, not by physically printing money. * **Quantitative Easing (QE)**: Purchasing assets to inject money directly into the economy, aiming to stimulate economic activity by increasing the money supply. * **Setting Reserve Requirement**s: Although less about creating money, lowering reserve requirements can indirectly influence money creation by allowing banks to lend more, but as of recent policy changes, this has been set to zero in some systems, shifting focus to interest rates. * **Interest on Reserves**: By adjusting the interest rate paid on reserves, central banks influence how much banks are willing to lend, thereby indirectly affecting money creation. This is the first step of money creation, although printing money is usually connected to one of the aforementioned processes, the second step creates much more money through the expansion of credit. ## The Mechanics of Fractional-Reserve Banking ### The Concept In fractional-reserve banking, banks accept deposits from customers and only keep a small fraction of these deposits in reserve, lending out the rest. This practice essentially creates new money because: * **Deposits**: When you deposit money, say $1,000, into a bank, that money doesn't just sit there. * **Reserves**: If the reserve requirement is 10%, the bank keeps $100 as reserves. * **Loans**: The remaining $900 can be loaned out. Here's where money creation begins. Note: Current reserve requirements of the FED ([Source](https://www.federalreserve.gov/monetarypolicy/reservereq.htm)) and the ECB ([Source](https://www.ecb.europa.eu/ecb-and-you/explainers/tell-me/html/minimum_reserve_req.en.html)) are set at 0% respectively 1%. ### Example Calculation of Money Creation 1. **Initial Deposit**: You deposit $1,000 into Bank A. 2. Bank A's Action: * Keeps $10 (1%) as reserve. * Loans out $990 to another customer. 3. **The $990 Loan**: This $990, when spent, might end up in Bank B as someone's deposit. 4. **Bank B's Action**: * Keeps $9.9 (1% of $990) as reserve. * Can loan out $980.1 5. **Continuation**: This process repeats, with each cycle creating new deposits from loans. The **Deposit Multiplier** (m) can be calculated as: * m = 1 divided by Reserve Ration = 1 / Reserve Ration If the reserve ratio is 1%: * m = 1 / 1% = 1 / 0.01 = 100 This means, theoretically, an initial deposit of $1,000 could expand to: * $1,000 times 100 = $100,000 * However, in practice, this is tempered by factors like cash holdings, loan demand, and banks holding excess reserves. ### Historical and Economic Context * **Evolution from Goldsmiths**: The system has its roots in the practices of goldsmiths who issued notes for gold deposits, which eventually circulated as money. This practice evolved into the modern banking system where notes (now digital entries) represent claims on money. * **Regulation and Central Banking**: Over time, central banks like the Federal Reserve in the U.S. were established to regulate this process, provide stability, and act as lenders of last resort. The Fed's tools include setting reserve requirements, though this has become less relevant with the shift to a 0% reserve requirement. ### Criticisms and Alternatives * **Risk of Bank Runs**: Critics argue that fractional-reserve banking makes the system vulnerable to bank runs, where too many depositors demand their money back at once, which the bank cannot cover since most of the money is loaned out. * **Vollgeld Initiative and Full-Reserve Banking**: Movements like Switzerland's Vollgeld Initiative have proposed shifting to full-reserve banking, where banks must hold 100% of deposits in reserve, preventing them from creating money through lending. However, this would significantly alter how banks operate and make profits. *** Modern Adjustments**: The move to a 0% reserve requirement in the U.S. reflects a shift towards using other monetary policy tools like interest rates on reserves to control money creation and economic stability. ### Real-World Implications * **Money Supply Control**: While banks create money through loans, central banks like the Federal Reserve influence this through monetary policy, adjusting how much money banks can create. * **Economic Stability**: The zero reserve requirement might seem to allow infinite money creation, but in reality, banks are constrained by capital requirements, risk assessments, and economic conditions. ## Conclusion Fractional-reserve banking is a dynamic system that significantly influences economic growth by expanding the money supply through debt. While it allows for economic expansion, it also introduces risks of instability, which central banks attempt to mitigate through various policy tools. Understanding this system helps demystify how money flows and grows within an economy, showcasing both its capacity for economic stimulation and its inherent risks. As we move forward, debates continue on how best to balance these aspects to foster economic stability and growth. In 2009, a new system called Bitcoin emerged that could redefine the rules for money creation.
@ 469fa704:2b6cb760
2024-09-04 15:22:28## Money Printing in general First of all, we need to make a distinction between money creation by central banks and fractional-reserve banking. Usually, the term money printing or “printer goes brrrrrr” refers to the creation of new central bank money, which is primarily created by central banks through: * **Open Market Operations**: Buying government securities, which injects money into the banking system by increasing bank reserves. This is often done electronically, not by physically printing money. * **Quantitative Easing (QE)**: Purchasing assets to inject money directly into the economy, aiming to stimulate economic activity by increasing the money supply. * **Setting Reserve Requirement**s: Although less about creating money, lowering reserve requirements can indirectly influence money creation by allowing banks to lend more, but as of recent policy changes, this has been set to zero in some systems, shifting focus to interest rates. * **Interest on Reserves**: By adjusting the interest rate paid on reserves, central banks influence how much banks are willing to lend, thereby indirectly affecting money creation. This is the first step of money creation, although printing money is usually connected to one of the aforementioned processes, the second step creates much more money through the expansion of credit. ## The Mechanics of Fractional-Reserve Banking ### The Concept In fractional-reserve banking, banks accept deposits from customers and only keep a small fraction of these deposits in reserve, lending out the rest. This practice essentially creates new money because: * **Deposits**: When you deposit money, say $1,000, into a bank, that money doesn't just sit there. * **Reserves**: If the reserve requirement is 10%, the bank keeps $100 as reserves. * **Loans**: The remaining $900 can be loaned out. Here's where money creation begins. Note: Current reserve requirements of the FED ([Source](https://www.federalreserve.gov/monetarypolicy/reservereq.htm)) and the ECB ([Source](https://www.ecb.europa.eu/ecb-and-you/explainers/tell-me/html/minimum_reserve_req.en.html)) are set at 0% respectively 1%. ### Example Calculation of Money Creation 1. **Initial Deposit**: You deposit $1,000 into Bank A. 2. Bank A's Action: * Keeps $10 (1%) as reserve. * Loans out $990 to another customer. 3. **The $990 Loan**: This $990, when spent, might end up in Bank B as someone's deposit. 4. **Bank B's Action**: * Keeps $9.9 (1% of $990) as reserve. * Can loan out $980.1 5. **Continuation**: This process repeats, with each cycle creating new deposits from loans. The **Deposit Multiplier** (m) can be calculated as: * m = 1 divided by Reserve Ration = 1 / Reserve Ration If the reserve ratio is 1%: * m = 1 / 1% = 1 / 0.01 = 100 This means, theoretically, an initial deposit of $1,000 could expand to: * $1,000 times 100 = $100,000 * However, in practice, this is tempered by factors like cash holdings, loan demand, and banks holding excess reserves. ### Historical and Economic Context * **Evolution from Goldsmiths**: The system has its roots in the practices of goldsmiths who issued notes for gold deposits, which eventually circulated as money. This practice evolved into the modern banking system where notes (now digital entries) represent claims on money. * **Regulation and Central Banking**: Over time, central banks like the Federal Reserve in the U.S. were established to regulate this process, provide stability, and act as lenders of last resort. The Fed's tools include setting reserve requirements, though this has become less relevant with the shift to a 0% reserve requirement. ### Criticisms and Alternatives * **Risk of Bank Runs**: Critics argue that fractional-reserve banking makes the system vulnerable to bank runs, where too many depositors demand their money back at once, which the bank cannot cover since most of the money is loaned out. * **Vollgeld Initiative and Full-Reserve Banking**: Movements like Switzerland's Vollgeld Initiative have proposed shifting to full-reserve banking, where banks must hold 100% of deposits in reserve, preventing them from creating money through lending. However, this would significantly alter how banks operate and make profits. *** Modern Adjustments**: The move to a 0% reserve requirement in the U.S. reflects a shift towards using other monetary policy tools like interest rates on reserves to control money creation and economic stability. ### Real-World Implications * **Money Supply Control**: While banks create money through loans, central banks like the Federal Reserve influence this through monetary policy, adjusting how much money banks can create. * **Economic Stability**: The zero reserve requirement might seem to allow infinite money creation, but in reality, banks are constrained by capital requirements, risk assessments, and economic conditions. ## Conclusion Fractional-reserve banking is a dynamic system that significantly influences economic growth by expanding the money supply through debt. While it allows for economic expansion, it also introduces risks of instability, which central banks attempt to mitigate through various policy tools. Understanding this system helps demystify how money flows and grows within an economy, showcasing both its capacity for economic stimulation and its inherent risks. As we move forward, debates continue on how best to balance these aspects to foster economic stability and growth. In 2009, a new system called Bitcoin emerged that could redefine the rules for money creation. @ 469fa704:2b6cb760
2024-09-04 12:07:53## Unified Login Across Platforms With Nostr, you use one login for all services, and your followers are seamlessly integrated. So you don't have start anew on every single platform. I think this is a real advantage of Nostr even for people not accustomed to Bitcoin or decentralization in general. ## Value for Value (V4V) Model Embrace the V4V principle where value is exchanged directly between users. Meaning if you find something useful or anohter nostr user was able to help you then you can simply zap him or her some Sats. ## Blogging Platforms * **Habla or Yakihonne**: Since joining Nostr 8 days ago, I've started blogging using Habla, which I found incredibly user-friendly. You can check out my articles directly on some clients like noStrudel, where they appear under my profile. Habla also serves as a great community explorer. Yakihonne, another comprehensive client with an integrated blog editor, caught my eye too, although it didn't sync all my Habla posts, possibly due to relay issues. * **Highlighter.com**: Offers a sleek interface for reading articles. On noStrudel, articles are tucked away under the "More" menu. ## Presentations * **Slidestr.net**: This tool transforms your notes into a slideshow, making revisiting old notes quite entertaining. ## Video Content * **Flare.pub**: If you're looking for a YouTube-like experience, Flare.pub is the closest you'll get on Nostr. You can upload, watch videos, and curate playlists. Remember, since Nostr is fundamentally text-based, videos are hosted on traditional servers, but the interface remains decentralized. There's definitely room for more video content, so start creating! ## Live Streaming * **Zapstream**: Offers a smooth streaming experience with a fee of 10 Sats per minute to cover server costs. You can watch streams on clients like Amethyst or noStrudel. ## Music and Podcasts * **Wavlake and Tunestr**: Ideal for artists to share music or podcasts. Listeners can enjoy content freely or support creators via zaps, adhering to the V4V model. ## Lists and Grouping * **Listr**: A tool for organizing everything from regional user groups to thematic notes or hashtags. You can also follow lists created by others in the Nostr community. ## Culinary Arts * **zap.cooking**: A haven for aspiring or seasoned chefs, offering a plethora of recipes in a blog format. It's well-organized, allowing you to browse through different categories of recipes. ## Marketplaces * **Plebian Market**: Reminiscent of eBay's early days, this marketplace allows easy buying and selling among users. ## Community Features * Many clients like noStrudel, Habla, and Amethyst support community functionalities, enhancing user interaction within Nostr.
@ 469fa704:2b6cb760
2024-09-04 12:07:53## Unified Login Across Platforms With Nostr, you use one login for all services, and your followers are seamlessly integrated. So you don't have start anew on every single platform. I think this is a real advantage of Nostr even for people not accustomed to Bitcoin or decentralization in general. ## Value for Value (V4V) Model Embrace the V4V principle where value is exchanged directly between users. Meaning if you find something useful or anohter nostr user was able to help you then you can simply zap him or her some Sats. ## Blogging Platforms * **Habla or Yakihonne**: Since joining Nostr 8 days ago, I've started blogging using Habla, which I found incredibly user-friendly. You can check out my articles directly on some clients like noStrudel, where they appear under my profile. Habla also serves as a great community explorer. Yakihonne, another comprehensive client with an integrated blog editor, caught my eye too, although it didn't sync all my Habla posts, possibly due to relay issues. * **Highlighter.com**: Offers a sleek interface for reading articles. On noStrudel, articles are tucked away under the "More" menu. ## Presentations * **Slidestr.net**: This tool transforms your notes into a slideshow, making revisiting old notes quite entertaining. ## Video Content * **Flare.pub**: If you're looking for a YouTube-like experience, Flare.pub is the closest you'll get on Nostr. You can upload, watch videos, and curate playlists. Remember, since Nostr is fundamentally text-based, videos are hosted on traditional servers, but the interface remains decentralized. There's definitely room for more video content, so start creating! ## Live Streaming * **Zapstream**: Offers a smooth streaming experience with a fee of 10 Sats per minute to cover server costs. You can watch streams on clients like Amethyst or noStrudel. ## Music and Podcasts * **Wavlake and Tunestr**: Ideal for artists to share music or podcasts. Listeners can enjoy content freely or support creators via zaps, adhering to the V4V model. ## Lists and Grouping * **Listr**: A tool for organizing everything from regional user groups to thematic notes or hashtags. You can also follow lists created by others in the Nostr community. ## Culinary Arts * **zap.cooking**: A haven for aspiring or seasoned chefs, offering a plethora of recipes in a blog format. It's well-organized, allowing you to browse through different categories of recipes. ## Marketplaces * **Plebian Market**: Reminiscent of eBay's early days, this marketplace allows easy buying and selling among users. ## Community Features * Many clients like noStrudel, Habla, and Amethyst support community functionalities, enhancing user interaction within Nostr. @ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ ## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks** ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา.. เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่ ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน.. ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ ## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน** ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core Blockstream สนับสนุน "Small Blocks" เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้ ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา ## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน** ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB** แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น.. ## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว** ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement" ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ ## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash** ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017 SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา.. อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"** ## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ** ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้ Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้ Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย ## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright** ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)** การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔 ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer" การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย ## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี** หลังจากการ Hard Fork ของ Bitcoin Cash Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value) การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin ## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ** ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป # **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง** ## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล** Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า ### **SegWit (Segregated Witness)** เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network ### **Taproot** เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ ## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่** ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่ ### **Bitcoin XT (2015)** เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ ### **Bitcoin Classic (2016)** เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน ### **Bitcoin Unlimited (2016)** เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง ### **Bitcoin Cash (BCH) (2017)** เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง ### **Bitcoin SV (BSV) (2018)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin ### **Bitcoin ABC (2020)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง ## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?** หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"** Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น.. ### **การไม่ยอมเพิ่ม Blocksize Limit** Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream ### **การเซ็นเซอร์ข้อมูล** Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ ### **การต่อต้านนวัตกรรม** Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น ### **การควบคุมโดยกลุ่มเล็กๆ** Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto ## **บทสรุป:** การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด **"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่.. ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย.. เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง.. — Jakk Goodday
@ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ ## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks** ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา.. เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่ ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน.. ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ ## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน** ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core Blockstream สนับสนุน "Small Blocks" เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้ ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา ## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน** ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB** แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น.. ## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว** ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement" ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ ## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash** ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017 SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา.. อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"** ## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ** ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้ Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้ Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย ## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright** ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)** การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔 ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer" การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย ## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี** หลังจากการ Hard Fork ของ Bitcoin Cash Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value) การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin ## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ** ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป # **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง** ## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล** Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า ### **SegWit (Segregated Witness)** เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network ### **Taproot** เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ ## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่** ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่ ### **Bitcoin XT (2015)** เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ ### **Bitcoin Classic (2016)** เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน ### **Bitcoin Unlimited (2016)** เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง ### **Bitcoin Cash (BCH) (2017)** เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง ### **Bitcoin SV (BSV) (2018)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin ### **Bitcoin ABC (2020)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง ## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?** หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"** Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น.. ### **การไม่ยอมเพิ่ม Blocksize Limit** Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream ### **การเซ็นเซอร์ข้อมูล** Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ ### **การต่อต้านนวัตกรรม** Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น ### **การควบคุมโดยกลุ่มเล็กๆ** Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto ## **บทสรุป:** การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด **"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่.. ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย.. เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง.. — Jakk Goodday @ e0e92e54:d630dfaa
2024-09-04 04:13:19_This is a copy of the email received from newsletter@Rumble.com_  # Free Speech Under Attack -- A Note from the CEO of Rumble Dear Rumble Users, I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble. Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court. World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them. There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it. Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people. The people keep us alive and keep us going. If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression. We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil". Sincerely, Chris Pavlovski Chairman and CEO of Rumble  444 Gulf of Mexico Dr. Longboat Key, FL 34228, USA.
@ e0e92e54:d630dfaa
2024-09-04 04:13:19_This is a copy of the email received from newsletter@Rumble.com_  # Free Speech Under Attack -- A Note from the CEO of Rumble Dear Rumble Users, I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble. Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court. World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them. There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it. Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people. The people keep us alive and keep us going. If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression. We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil". Sincerely, Chris Pavlovski Chairman and CEO of Rumble  444 Gulf of Mexico Dr. Longboat Key, FL 34228, USA. @ 96203d66:643a819c
2024-09-04 03:42:31#[3] #[4] #[5] #[6] #[7] #[8] #[9] #[10] #[11] #[12] #[13] #[14] #[15] #[16] #[17] #[18] #[19] #[20] #[21] #[22] #[23] #[24] #[25] #[26] #[27] #[28] #[29] #[30] #[31]
@ 96203d66:643a819c
2024-09-04 03:42:31#[3] #[4] #[5] #[6] #[7] #[8] #[9] #[10] #[11] #[12] #[13] #[14] #[15] #[16] #[17] #[18] #[19] #[20] #[21] #[22] #[23] #[24] #[25] #[26] #[27] #[28] #[29] #[30] #[31] @ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity #GHOSTn If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs. Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see. Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be. Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes. Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
@ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity #GHOSTn If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs. Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see. Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be. Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes. Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do. @ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn. So what is encryption? It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with. > BEGINNER LEVEL - Encrypt your phone and computer. People walk around with their whole lives on their phone. Protect it. -phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password. After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive. -Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts. -Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault". -Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution. Awesome sauce. You have achieved minimum status. > ADVANCED LEVEL - Encrypt individual files. You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you. What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted. I will share with you one of my favorite small programs: Picocrypt. Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away. Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own. > EXPERT LEVEL - Encrypt containers and hidden containers. What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful. Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives. Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container. This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that. These features allow you to do all sorts of interesting things only limited by your need and imagination. What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun. > NEMO - Failsafe Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot. Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone. > > Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc > Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn. So what is encryption? It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with. > BEGINNER LEVEL - Encrypt your phone and computer. People walk around with their whole lives on their phone. Protect it. -phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password. After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive. -Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts. -Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault". -Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution. Awesome sauce. You have achieved minimum status. > ADVANCED LEVEL - Encrypt individual files. You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you. What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted. I will share with you one of my favorite small programs: Picocrypt. Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away. Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own. > EXPERT LEVEL - Encrypt containers and hidden containers. What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful. Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives. Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container. This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that. These features allow you to do all sorts of interesting things only limited by your need and imagination. What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun. > NEMO - Failsafe Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot. Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone. > > Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc > Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is. @ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 3: Arrays, Objects, and Callbacks ### Arrays: Lists of Things Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys: ```javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse" ``` ### Objects: Grouping Related Information Objects allow you to group related information together. They're like detailed profiles for each of your cat friends: ```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" }; console.log(myCat.name); // Prints "Fluffy" ``` ### Callbacks: Doing Things Later Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat: ```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); } feedCat(function() { console.log("Time for a treat!"); }); ``` This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat. Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 3: Arrays, Objects, and Callbacks ### Arrays: Lists of Things Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys: ```javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse" ``` ### Objects: Grouping Related Information Objects allow you to group related information together. They're like detailed profiles for each of your cat friends: ```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" }; console.log(myCat.name); // Prints "Fluffy" ``` ### Callbacks: Doing Things Later Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat: ```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); } feedCat(function() { console.log("Time for a treat!"); }); ``` This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat. Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat! @ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 2: Functions and Loops ### Functions: Your Own Commands Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick: ```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } } meow(3); // This will print "Meow!" three times ``` ### Built-in Functions JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console: ```javascript console.log("I'm a cat!"); ``` ### Loops: Repeating Tasks Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds: ```javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); } ``` This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 2: Functions and Loops ### Functions: Your Own Commands Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick: ```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } } meow(3); // This will print "Meow!" three times ``` ### Built-in Functions JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console: ```javascript console.log("I'm a cat!"); ``` ### Loops: Repeating Tasks Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds: ```javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); } ``` This will print "Chasing tail, round X" five times, where X goes from 1 to 5. @ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track. *(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)* 1. **Stefon Diggs leads the Texans in targets, catches and receiving yards** Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year. 2. **CJ Stroud leads the NFL is passing yards** This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2. 3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)** Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens. 4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR** Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020. 5. **The Giants will field a top-10 fantasy defense.** I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers. 6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt** I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua. 7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)** Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time. 8. **Dalvin Cook will lead the Cowboys in rushing yards** Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.) 9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.** He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.) 10. **Dalton Kincaid (TE4) will lead all TE in catches** I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. 11. **Some of these predictions will be wrong** No one’s perfect, but you never want to get shut out.
@ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track. *(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)* 1. **Stefon Diggs leads the Texans in targets, catches and receiving yards** Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year. 2. **CJ Stroud leads the NFL is passing yards** This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2. 3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)** Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens. 4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR** Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020. 5. **The Giants will field a top-10 fantasy defense.** I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers. 6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt** I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua. 7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)** Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time. 8. **Dalvin Cook will lead the Cowboys in rushing yards** Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.) 9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.** He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.) 10. **Dalton Kincaid (TE4) will lead all TE in catches** I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. 11. **Some of these predictions will be wrong** No one’s perfect, but you never want to get shut out. @ 469fa704:2b6cb760
2024-09-03 10:20:09In traditional investment wisdom, diversification is the mantra chanted by financial advisors worldwide. It's the strategy to spread risk across various assets to mitigate losses. However, when it comes to Bitcoin, some argue this principle might not apply in the same way. Here's why: ## 1. Bitcoin's Unique Value Proposition Bitcoin, often dubbed "digital gold," has several attributes that set it apart from other investments: * **Finite Supply**: With a cap at 21 million coins, Bitcoin's scarcity is programmed into its code, mirroring the scarcity of gold but with even more certainty. This scarcity can drive value as demand increases over time, especially in an economic environment where fiat currencies are subject to inflation. * **Decentralization**: Unlike stocks or real estate, Bitcoin isn't tied to any central authority or physical asset that can fail or be manipulated by a single entity. This decentralization reduces the risk of systemic failure that affects traditional markets. * **Global Liquidity and Accessibility**: Bitcoin can be bought, sold, and transferred anywhere in the world, 24/7, with internet access. This global liquidity means Bitcoin can be more easily converted to other assets if needed, somewhat reducing the need for diversification. ## 2. The Risk-Reward Balance * **Volatility as Opportunity**: While Bitcoin's volatility is often cited as a risk, for the informed investor, this volatility represents opportunities for significant gains. Those who understand Bitcoin's cycles might prefer to ride these waves rather than dilute potential gains through diversification into less volatile assets. * **Long-term Appreciation**: Historical data suggests Bitcoin has provided substantial returns over the long term compared to most traditional investments. If one believes in Bitcoin's future as a dominant store of value, holding a diversified portfolio might mean missing out on Bitcoin's potential upside. ## 3. Bitcoin as a Diversifier Ironically, Bitcoin itself serves as a diversification tool within traditional investment portfolios. Its price movements have shown low correlation with stocks, bonds, and even gold at times, suggesting that Bitcoin can diversify an investment portfolio on its own. ## 4. The Philosophical Shift * **Trust in Code Over Corporations**: Investing heavily in Bitcoin might reflect a philosophical shift towards trusting mathematical algorithms over corporate governance or government policy. Here, diversification within the crypto space might seem less necessary if one views Bitcoin as the pinnacle of what cryptocurrency should be. * **A Bet on a New Financial System**: Holding Bitcoin exclusively can be seen as a bet on a new financial paradigm where Bitcoin becomes the standard. In this vision, diversification into other assets might be counterproductive. ## 5. Potential Result Upon reviewing the arguments and characteristics, one might conclude that Bitcoin is pursuing a dual trajectory. Firstly, its value increases partly because it remains a novel asset, not yet mainstream among the general populace. Secondly, Bitcoin is poised to absorb the value preservation function from other assets. This means that individuals who invest in stocks, bonds, real estate, commodities, etc., primarily for their value storage capabilities rather than their intrinsic utility (such as residing in a property), might transition to Bitcoin. This shift could consequently diminish the demand for these traditional assets and increase the value of Bitcoin respectively. ## 6. Caveats and Considerations * **Not Without Risks**: This approach isn't without its perils. Bitcoin's future is not guaranteed, and regulatory, technological, or market shifts could impact its value negatively. * **Liquidity Needs**: Individual financial situations might require liquidity or income generation that Bitcoin alone might not provide efficiently. * **Emotional Discipline**: A Bitcoin-only strategy requires immense discipline and conviction, as the emotional toll of not diversifying can be high during market downturns. ## Conclusion The argument for not diversifying if you hold Bitcoin hinges on its unique properties, the potential for high returns, and its role as a hedge against inflation and traditional financial systems. However, this strategy suits those with a high risk tolerance, a deep understanding of Finance, Economics and Investments, and a belief in Bitcoin's future dominance. For everyone else, while Bitcoin can be a significant part of a portfolio, traditional diversification might still offer peace of mind and stability. Remember, investment strategies should align with personal financial goals, risk tolerance, and market understanding. Always consider consulting with a financial advisor for personalized advice.
@ 469fa704:2b6cb760
2024-09-03 10:20:09In traditional investment wisdom, diversification is the mantra chanted by financial advisors worldwide. It's the strategy to spread risk across various assets to mitigate losses. However, when it comes to Bitcoin, some argue this principle might not apply in the same way. Here's why: ## 1. Bitcoin's Unique Value Proposition Bitcoin, often dubbed "digital gold," has several attributes that set it apart from other investments: * **Finite Supply**: With a cap at 21 million coins, Bitcoin's scarcity is programmed into its code, mirroring the scarcity of gold but with even more certainty. This scarcity can drive value as demand increases over time, especially in an economic environment where fiat currencies are subject to inflation. * **Decentralization**: Unlike stocks or real estate, Bitcoin isn't tied to any central authority or physical asset that can fail or be manipulated by a single entity. This decentralization reduces the risk of systemic failure that affects traditional markets. * **Global Liquidity and Accessibility**: Bitcoin can be bought, sold, and transferred anywhere in the world, 24/7, with internet access. This global liquidity means Bitcoin can be more easily converted to other assets if needed, somewhat reducing the need for diversification. ## 2. The Risk-Reward Balance * **Volatility as Opportunity**: While Bitcoin's volatility is often cited as a risk, for the informed investor, this volatility represents opportunities for significant gains. Those who understand Bitcoin's cycles might prefer to ride these waves rather than dilute potential gains through diversification into less volatile assets. * **Long-term Appreciation**: Historical data suggests Bitcoin has provided substantial returns over the long term compared to most traditional investments. If one believes in Bitcoin's future as a dominant store of value, holding a diversified portfolio might mean missing out on Bitcoin's potential upside. ## 3. Bitcoin as a Diversifier Ironically, Bitcoin itself serves as a diversification tool within traditional investment portfolios. Its price movements have shown low correlation with stocks, bonds, and even gold at times, suggesting that Bitcoin can diversify an investment portfolio on its own. ## 4. The Philosophical Shift * **Trust in Code Over Corporations**: Investing heavily in Bitcoin might reflect a philosophical shift towards trusting mathematical algorithms over corporate governance or government policy. Here, diversification within the crypto space might seem less necessary if one views Bitcoin as the pinnacle of what cryptocurrency should be. * **A Bet on a New Financial System**: Holding Bitcoin exclusively can be seen as a bet on a new financial paradigm where Bitcoin becomes the standard. In this vision, diversification into other assets might be counterproductive. ## 5. Potential Result Upon reviewing the arguments and characteristics, one might conclude that Bitcoin is pursuing a dual trajectory. Firstly, its value increases partly because it remains a novel asset, not yet mainstream among the general populace. Secondly, Bitcoin is poised to absorb the value preservation function from other assets. This means that individuals who invest in stocks, bonds, real estate, commodities, etc., primarily for their value storage capabilities rather than their intrinsic utility (such as residing in a property), might transition to Bitcoin. This shift could consequently diminish the demand for these traditional assets and increase the value of Bitcoin respectively. ## 6. Caveats and Considerations * **Not Without Risks**: This approach isn't without its perils. Bitcoin's future is not guaranteed, and regulatory, technological, or market shifts could impact its value negatively. * **Liquidity Needs**: Individual financial situations might require liquidity or income generation that Bitcoin alone might not provide efficiently. * **Emotional Discipline**: A Bitcoin-only strategy requires immense discipline and conviction, as the emotional toll of not diversifying can be high during market downturns. ## Conclusion The argument for not diversifying if you hold Bitcoin hinges on its unique properties, the potential for high returns, and its role as a hedge against inflation and traditional financial systems. However, this strategy suits those with a high risk tolerance, a deep understanding of Finance, Economics and Investments, and a belief in Bitcoin's future dominance. For everyone else, while Bitcoin can be a significant part of a portfolio, traditional diversification might still offer peace of mind and stability. Remember, investment strategies should align with personal financial goals, risk tolerance, and market understanding. Always consider consulting with a financial advisor for personalized advice. @ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
@ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app) @ eed76ece:afa98124
2024-09-02 18:58:30As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously. Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online. SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West. Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway. Examples Customers in these regions I deal with primarily communicate with me in Japan, Thailand using LINE and Tik Tok daily. Most of the rest of the World communicate with me using WhatsApp. Certain parts of Eastern Europe and Asia Telegram. Interestingly my resellers in the USA primarily post on WhatsApp. Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again". "So I will always have free speech, the politicians told me so". originally posted at https://stacker.news/items/670041
@ eed76ece:afa98124
2024-09-02 18:58:30As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously. Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online. SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West. Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway. Examples Customers in these regions I deal with primarily communicate with me in Japan, Thailand using LINE and Tik Tok daily. Most of the rest of the World communicate with me using WhatsApp. Certain parts of Eastern Europe and Asia Telegram. Interestingly my resellers in the USA primarily post on WhatsApp. Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again". "So I will always have free speech, the politicians told me so". originally posted at https://stacker.news/items/670041 @ 56a6da9b:7f5a2243
2024-09-02 18:27:19IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity. originally posted at https://stacker.news/items/669994
@ 56a6da9b:7f5a2243
2024-09-02 18:27:19IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity. originally posted at https://stacker.news/items/669994 @ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot. Here are the results: ([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream)) <img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png"> **1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount. **2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead. **3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there. **4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target. **5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone. **6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year. **7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position. **8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR. **9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.) **10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.) **11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks. **12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build. **13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job. **14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert. **15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old. **16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down. **17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too. **18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie. **19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.) **20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence. **Roster By Position** **QB** Anthony Richardson **RB** James Conner/Jaleel McLaughlin **WR** Ja’Marr Chase/Drake London/DeVonta Smith **TE** Dalton Kincaid **FLEX** Stefon Diggs **K** Younghoe Koo **D** Giants **Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
@ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot. Here are the results: ([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream)) <img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png"> **1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount. **2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead. **3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there. **4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target. **5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone. **6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year. **7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position. **8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR. **9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.) **10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.) **11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks. **12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build. **13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job. **14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert. **15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old. **16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down. **17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too. **18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie. **19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.) **20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence. **Roster By Position** **QB** Anthony Richardson **RB** James Conner/Jaleel McLaughlin **WR** Ja’Marr Chase/Drake London/DeVonta Smith **TE** Dalton Kincaid **FLEX** Stefon Diggs **K** Younghoe Koo **D** Giants **Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston @ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy. You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start. Don't worry, here are some absolute beginner first steps that will make a big difference. > 1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. > 2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data. BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS. > 3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. > 4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. > 5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice. > BONUS TIP: Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population. > OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security. What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone. The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure? There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
@ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy. You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start. Don't worry, here are some absolute beginner first steps that will make a big difference. > 1. No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. > 2. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data. BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS. > 3. Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. > 4. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. > 5. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice. > BONUS TIP: Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population. > OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security. What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone. The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure? There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later. @ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md) And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker ```sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0 ``` ## New Features ### Support for NIP-49 encrypted nsec Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...) There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps  ### Blindspot feeds There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing  ### NIP-42 Relay authentication The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings  ### Wasm relay and event verification The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view  The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting  ### Thread tabs Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note   ### Wiki articles Its not feature complete but you can now view and edit wiki articles in the app  ### Finished the launchpad The launchpad is now usable and shows the latest notifications, messages, streams, and tools  ### Blossom uploads The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings  And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`  ### Task Manager There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app  You can see what relays the app is currently connected to  And which relays are requesting NIP-42 authentication  ## Bug fixes - Fix null relay hints in DMs - Fix users own events being hidden by muted words - Fix random events showing up as DM messages - Fix app prompting NIP-07 extension to unlock when app opens - Remove corsproxy.io as default service for CORS proxy
@ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md) And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker ```sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0 ``` ## New Features ### Support for NIP-49 encrypted nsec Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...) There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps  ### Blindspot feeds There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing  ### NIP-42 Relay authentication The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings  ### Wasm relay and event verification The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view  The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting  ### Thread tabs Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note   ### Wiki articles Its not feature complete but you can now view and edit wiki articles in the app  ### Finished the launchpad The launchpad is now usable and shows the latest notifications, messages, streams, and tools  ### Blossom uploads The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings  And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`  ### Task Manager There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app  You can see what relays the app is currently connected to  And which relays are requesting NIP-42 authentication  ## Bug fixes - Fix null relay hints in DMs - Fix users own events being hidden by muted words - Fix random events showing up as DM messages - Fix app prompting NIP-07 extension to unlock when app opens - Remove corsproxy.io as default service for CORS proxy @ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment. A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding. It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
@ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment. A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding. It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment. @ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope. But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin. For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right? I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours? She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw. I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else. So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore. We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent? The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them. Extreme situations, I know. But no one thinks it will happen to them—until it does. So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why? What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time. Time with your kids. Time with your family. Time with yourself. There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work. But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here. So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here. I just need to get through the withdrawal phase. originally posted at https://stacker.news/items/662939
@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope. But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin. For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right? I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours? She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw. I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else. So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore. We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent? The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them. Extreme situations, I know. But no one thinks it will happen to them—until it does. So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why? What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time. Time with your kids. Time with your family. Time with yourself. There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work. But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here. So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here. I just need to get through the withdrawal phase. originally posted at https://stacker.news/items/662939 @ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.  originally posted at https://stacker.news/items/669464
@ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.  originally posted at https://stacker.news/items/669464 @ 79008e78:dfac9395
2024-09-02 06:17:23ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer ---- ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer นั้นจะช่วยให้เราสามารถชำระเงินผ่านทางออนไลน์ได้โดยตรงจากฝ่ายหนึ่งไปยังอีกฝ่ายหนึ่งโดยไม่ต้องผ่านตัวกลางอย่างพวกสถาบันการเงิน โดยใช้ digital signature เป็นส่วนหนึ่งในการแก้ปัญหานี้ แต่มันจะไม่มีประโยชน์ใด ๆ เลยหากยังคงต้องอาศัยตัวกลางที่เชื่อถือได้มาแก้ปัญหา double spending เราขอเสนอวิธีแก้ปัญหา double spending โดยใช้เครือข่ายแบบ peer-to-peer ให้เครือข่ายคอยประทับเวลาธุรกรรมต่าง ๆ ในระบบและนำมาเรียงร้อยกันเป็นเส้นสายของ proof-of-work ที่ใช้ hash เพื่อสร้างธุรกรรมที่ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ต้องทำ proof-of-work ใหม่ โดยให้เส้นสายที่ยาวที่สุดนั้น ไม่เพียงแต่ทำหน้าที่เป็นลำดับของธุรกรรมที่เกิดขึ้นเท่านั้น แต่ยังเป็นสิ่งที่พิสูจน์ได้ว่ามาจากกำลังประมวลผล CPU ที่มากที่สุด และตราบใดที่ nodes ส่วนใหญ่ไม่ได้ร่วมมือกันโจมตีเครือข่ายและยังคงควบคุมกำลังประมวลผลส่วนใหญ่ในระบบไว้ พวกเขาก็จะสร้างเส้นสายที่ยาวที่สุดและสามารถเอาชนะผู้ประสงค์ร้ายที่จะโจมตีระบบได้ ตัวเครือข่ายเองไม่ได้ต้องมีโครงสร้างอะไรที่ซับซ้อน ข้อมูลต่าง ๆ ในเครือข่ายจะถูกกระจายส่งต่อโดยไม่ต้องสนใจว่าผู้รับจะได้รับหรือไม่ และ nodes ต่าง ๆ เองก็สามารถที่จะออกจากเครือข่ายและกลับเข้าร่วมใหม่ได้ตามที่ต้องการ โดยยอมรับเส้น proof-of-work ที่ยาวที่สุด เป็นหลักฐานของสิ่งที่เกิดขึ้นในขณะที่ node นั้น ๆ ไม่ได้อยู่ในเครือข่าย 1.บทนำ (Introduction) ----- ไม่ว่าใครจะใคร่ซื้อใคร่ขายอะไรใด ๆ บนอินเตอร์เน็ตนั้น ก็จำเป็นต้องพึ่งพาสถาบันการเงินในฐานะของบุคคลที่สามเพื่อดำเนินการชำระเงินทางอิเล็กทรอนิกส์เสมอ ๆ ซึ่งถึงแม้ว่าระบบนี้มันจะทำงานได้ดีสำหรับธุรกรรมส่วนใหญ่ ๆ แต่ระบบก็ก็มีจุดอ่อนอยู่ที่ยังต้องอาศัยความไว้เนื้อเชื่อใจ (trust) ในระบบนี้การทำธุรกรรมที่ไม่สามารถย้อนกลับได้อย่างสมบูรณ์นั้นมันแทบจะเป็นไปไม่ได้เลย เนื่องจากสถาบันการเงินไม่สามารถหลีกเลี่ยงการเป็นตัวกลางในการไกล่เกลี่ยข้อพิพาทต่าง ๆ ที่อาจเกิดขึ้นได้ มิหนำซ้ำต้นทุนในการไกล่เกลี่ยยังทำให้ต้นทุนการทำธุรกรรมเพิ่มสูงขึ้น และเมื่อต้นทุนสูงขึ้นขนาดของธุรกรรมที่สามารถใช้งานได้จริงก็สูงขึ้นตามไปด้วย ธุรกรรมเล็ก ๆ น้อย ๆ ก็ไม่สามารถเกิดขึ้นได้ เมื่อมีความเป็นไปได้ที่ธุรกรรมจะเกิดการย้อนกลับ ความจำเป็นในการสร้างความไว้วางใจก็ยิ่งทวีคูณมากขึ้น ผู้ค้าก็จำเป็นต้องระมัดระวังลูกค้า ต้องเรียกร้องข้อมูลมากกว่าที่จำเป็น การฉ้อโกงกลายเป็นเรื่องที่หลีกเลี่ยงไม่ได้เพราะต้นทุนและความไม่แน่นอนในทำธุรกรรมเหล่านี้ แน่นอนว่าเราสามารถหลีกเลี่ยงมันได้โดยการใช้เงินสด แต่ก็ไม่มีกลไกใดที่ทำให้สามารถใช้เงินสดผ่านช่องทางการสื่อสาร (เอาให้เข้าใจง่ายก็อินเตอร์เน็ต)ได้ โดยไม่ต้องมีตัวกลาง ;-; แปลว่าสิ่งที่จำเป็นสำหรับการแก้ไขปัญหานี้คือระบบการชำระเงินทางอิเล็กทรอนิกส์ ที่อยู่บนพื้นฐานของการพิสูจน์ด้วยการเข้ารหัสแทนที่จะเป็นความไว้วางใจ ซึ่งจะทำให้คู่สัญญาสองฝ่ายที่ยินยอมสามารถทำธุรกรรมร่วมกันได้โดยตรง โดยไม่จำเป็นต้องมีบุคคลที่สามมาคอยเป็นตัวกลาง ธุรกรรมที่ยากต่อการย้อนกลับจะช่วยปกป้องผู้ขายจากการฉ้อโกง และสามารถใช้กลไก escrow เพื่อปกป้องผู้ซื้อได้อีกด้วย ในเอกสารชุดนี้ เราขอเสนอวิธีแก้ปัญหาการใช้จ่ายซ้ำซ้อนโดยใช้เซิร์ฟเวอร์ timestamp กระจายศูนย์แบบ peer-to-peer เพื่อสร้างหลักฐานการคำนวณลำดับเวลาของธุรกรรม โดยระบบนี้จะปลอดภัยตราบใดที่กลุ่มของ node ที่ซื่อสัตย์ ยังคงมีกำลังประมวลผลที่มากกว่ากลุ่มที่ประสงค์ร้ายกับระบบ 2.ธุรกรรม (Transactions) ---- นิยามของเหรียญอิเล็กทรอนิกส์ในที่นี้ คือห่วงโซ่ที่คล้องเกี่ยวกันของ digital signature โดยที่เจ้าของเหรียญอิเล็กทรอนิกส์จะโอนเหรียญไปยังเจ้าของคนถัดไป ด้วยการลง digital signature บน hash ของธุรกรรมก่อนหน้ารวมถึงกุญแจสาธารณะของเจ้าของคนถัดไป และผนวกมันไว้ที่ส่วนท้ายของธุรกรรม และผู้รับเงินเองก็สามารถตรวจสอบลายเซ็นเพื่อยืนยันความเป็นเจ้าของได้ https://image.nostr.build/a467896797a9fb9f98c3c234f0adb4df2376f2c3d9a7cc9d8672d7a9f5aa9efa.png แน่นอนว่าปัญหาก็คือผู้รับเงินไม่สามารถตรวจสอบได้ว่าเจ้าของคนใดคนหนึ่งก่อนหน้าเขาได้ใช้เหรียญดังกล่าวซ้ำซ้อนมากกว่าหนึ่งครั้งหรือไม่ และวิธีการแก้ไขปัญหานี้โดยทั่วไปก็คงเป็นการกำหนดตัวกลางที่มีความน่าเชื่อถือมาเป็นคนตรวจสอบทุกธุรกรรมเพื่อป้องกันการใช้จ่ายซ้ำซ้อน และหลังจากการทำธุรกรรมแต่ละครั้ง เหรียญจะต้องถูกส่งกลับไปยังตัวกลางเพื่อออกเหรียญใหม่ และจะมีเพียงเหรียญที่ออกจากตัวกลางโดยตรงเท่านั้นที่จะเชื่อถือได้ว่าจะไม่ถูกใช้จ่ายซ้ำซ้อน แต่ปัญหาก็คือ ชะตากรรมของระบบเงินทั้งหมดจะขึ้นอยู่กับตัวกลางตัวนี้ เพราะทุกธุรกรรมจำเป็นจะต้องผ่านพวกเขา ซึ่งก็ไม่ต่างอะไรกับธนาคาร เราจึงต้องการวิธีการที่ทำให้ผู้รับเงินทราบได้ว่าเจ้าของคนก่อน ๆ ไม่ได้ลงนามในธุรกรรมใด ๆ มาก่อน เพื่อให้บรรลุวัตถุประสงค์นี้ เราจะทำการนับว่าธุรกรรมที่เกิดขึ้นก่อนเป็นธุรกรรมที่ถูกต้อง และจะไม่สนใจความพยายามใด ๆ ในการที่จะใช้เหรียญนั้น ๆ ซ้ำอีก และวิธีเดียวที่ทำแบบนี้ได้ คือการรับรู้ถึงธุรกรรมทั้งหมด เช่นเดียวกับโมเดลที่ได้กล่าวข้างต้น ที่ตัวกลางจะรับรู้ถึงธุรกรรมทั้งหมดและตัดสินว่าธุรกรรมใดมาก่อนมาหลัง เพื่อให้บรรลุเป้าหมายนี้โดยไม่ต้องมีบุคคลที่สามที่เชื่อถือได้ ธุรกรรมทั้งหมดจะต้องถูกประกาศต่อสาธารณะ [1] และเราต้องการระบบที่ผู้เข้าร่วมเห็นพ้องในประวัติธุรกรรมชุดเดียวกันตามลำดับที่ได้รับ ส่วนผู้รับเงินก็จำเป็นจะต้องมีหลักฐานว่า ในขณะที่ทำธุรกรรม "โหนด" ส่วนใหญ่ในระบบเห็นพ้องต้องกันว่าธุรกรรมนั้นได้รับเป็นลำดับแรก(ไม่มีธุรกรรมที่ใช้เหรียญพวกนี้มาก่อน) 3.ระบบบันทึกเวลา (Timestamp Server) ---- สำหรับแนวทางการแก้ปัญหาในครั้งนี้ เราจะใช้ประโยชน์จาก timestamp server ที่จะทำหน้าที่บันทึก hash ของบล๊อกที่ต้องการให้มีการบันทึกเวลา และจากนั้นจะทำการเผยแพร่ hash ดังกล่าว เหมือนกับหนังสือพิมพ์หรือโพสต์ใน Usenet [2-5] (ฟีลแบบทุกคนจะเห็นโพสต์นี้น้าา ประมาณนั้น) การบันทึกเวลานี้จะพิสูจน์ได้ว่าข้อมูลที่ถูก hash นั้นจะต้องมีอยู่จริงในเวลานั้นเพื่อให้ได้มาซึ่ง hash ดังกล่าว แต่ละการบันทึกเวลาจะรวมการบันทึกเวลาของหน้านี้ไว้ใน hash ของมันเพื่อสร้างเป็น chain โดยการบันทึกเวลาแต่ละครั้งจะยืนยันความถูกต้องของการบันทึกก่อนหน้าได้อีกด้วยด้วย https://image.nostr.build/ddf92417c45dbb6e25da0af80a10d4cdbc3e725d047d65f54a3e3bfcf358c4d6.png 4.พรูฟ-ออฟ-เวิร์ค (Proof-of-Work) ---- ในการสร้าง Timestamp Server แบบกระจายศูนย์บนพื้นฐานแบบ peer to peer เราจำเป็นต้องใช้ระบบ Proof-of-Work (PoW) ที่คล้ายกับ Hashcash ของ Adam Back [6] แทนที่จะใช้วิธีการแบบเดิม ๆ อย่างการประกาศในหนังสือพิมพ์หรือ Usenet โดย PoW ใช้ในการตรวจสอบค่าที่มาจากกระบวนการ hash เช่น SHA-256 แล้ว ผลลัพธ์ที่ได้ (Hash) จะขึ้นต้นด้วยเลขศูนย์จำนวนหนึ่ง โดยที่ work (ประมาณว่าพลังประมวลผล) ที่ต้องใช้จะเพิ่มขึ้นแบบทวีคูณตามจำนวนเลขศูนย์ที่ต้องการ และสามารถตรวจสอบได้โดยการรัน Hash เพียงครั้งเดียว ซึ่งสำหรับ timestamp network ของเรานั้น เราใช้ PoW โดยการเพิ่มค่า Nonce ในบล็อกไปเรื่อย ๆ จนกว่าจะพบค่าที่ทำให้ Hash ของบล็อกนั้นมีเลขศูนย์ตามที่กำหนด และเมื่อใช้กำลังประมวลผลของ CPU ไปกับการทำ PoW จนสำเร็จแล้ว บล็อกจะไม่สามารถเปลี่ยนแปลงได้ หากไม่มีการทำงานซ้ำใหม่ เนื่องจากบล็อกที่สร้างขึ้นภายหลังจะเชื่อมโยงกับบล็อกก่อนหน้า การเปลี่ยนแปลงบล็อกใด ๆ จะต้องทำ PoW ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด https://image.nostr.build/c039ef4ca6833cb1ecee65ac5991df2406be9b7e490b86b3b19f94f267767182.png นอกจากนี้ PoW ยังช่วยแก้ปัญหาของเสียงส่วนมากที่มาตัดสินใจในระบบนี้ เพราะหากเสียงข้างมากอ้างอิงจากหลักการหนึ่ง IP หนึ่งเสียง ใครก็ตามที่สามารถสร้าง IP ได้จำนวนมากก็จะสามารถควบคุมระบบได้ จึงใช้หลักการหนึ่ง CPU หนึ่งเสียงแทน การตัดสินใจของเสียงข้างมากจะแสดงด้วย Chain ที่ยาวที่สุด ซึ่งบ่งบอกถึงความพยายามในการคำนวณ (Proof-of-Work) ที่มากที่สุด หาก Node ที่ซื่อสัตย์ (Honest nodes) มีกำลังประมวลผลของ CPU ส่วนใหญ่อยู่ในการควบคุม Honest Chain ก็จะเติบโตเร็วที่สุดและแซงหน้า Chain อื่น ๆ ได้ ผู้โจมตีที่ต้องการแก้ไขบล็อกในอดีตจะต้องทำ Proof-of-Work ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด และต้องทำงานให้เร็วกว่า Honest Node ด้วย ซึ่งโอกาสที่ผู้โจมตีจะตามทันนั้นจะลดลงแบบทวีคูณเมื่อมีการเพิ่มบล็อกมากขึ้น เพื่อชดเชยความเร็วของฮาร์ดแวร์ที่เพิ่มขึ้นและความสนใจในการรัน Node ที่ผันผวน ระดับความยากของ Proof-of-Work จะถูกกำหนดโดยค่าเฉลี่ย โดยตั้งเป้าไว้ที่จำนวนบล็อกเฉลี่ยต่อชั่วโมง หากสร้างบล็อกได้เร็วเกินไป ระดับความยากก็จะเพิ่มขึ้น 5.เครือข่าย (Network) ---- เครือข่ายนั้นมีการทำงาน ดังนี้ 1. การประกาศธุรกรรมใหม่: ธุรกรรมใหม่จะถูกประกาศ (broadcast) ไปยังทุก node ในเครือข่าย 2. การรวบรวมธุรกรรม: แต่ละ node จะรวบรวมธุรกรรมใหม่ ๆ เหล่านี้ ไว้ในบล็อก 3. การค้นหา Proof-of-Work: แต่ละ node จะทำการคำนวณ เพื่อค้นหา Proof-of-Work ตามค่า difficulty สำหรับบล็อกนั้น ๆ 4. การประกาศบล็อก: เมื่อ node ใดค้นหา Proof-of-Work ได้แล้ว node นั้นจะทำการประกาศบล็อกไปยังทุก node ในเครือข่าย 5. การตรวจสอบและยอมรับบล็อก: node อื่น ๆ จะทำการตรวจสอบและยอมรับบล็อกนั้น เฉพาะเมื่อธุรกรรมทั้งหมดภายในบล็อกนั้นถูกต้องและยังไม่ถูกใช้มาก่อน 6. การสร้างบล็อกถัดไป: node ต่าง ๆ แสดงการยอมรับบล็อกโดยการเริ่มต้นสร้างบล็อกถัดไปใน chain ด้วย hash ของบล็อกที่ยอมรับ เป็น hash ก่อนหน้าในโครงสร้างของบล๊อกใหม่ที่กำลังสร้าง node ต่าง ๆ จะถือว่า chain ที่ยาวที่สุดเป็น chain ที่ถูกต้องและจะทำงานเพื่อขยาย chain นั้นต่อไป หากมีสอง node ที่ได้ประกาศบล็อกเวอร์ชันที่แตกต่างกันในเวลาพร้อมกัน node บาง node อาจได้รับบล็อกหนึ่งก่อน อีกบล็อกหนึ่ง ในกรณีนี้ node เหล่านั้น จะทำงานบนบล็อกที่ได้รับก่อน แต่จะเก็บสำเนาของบล็อกอีกอันหนึ่งไว้ ในกรณีที่บล็อกนั้น กลายเป็นบล็อกที่อยู่ใน chain ที่ยาวกว่าปัญหาข้อโต้แย้งนี้ก็จะได้รับการแก้ไข เมื่อพบ Proof-of-Work อันถัดไปและ chain ใด chain หนึ่งยาวขึ้น node ที่กำลังทำงานอยู่บน chain ที่สั้นกว่าก็จะเปลี่ยนไปทำงานบน chain ที่ยาวกว่าแทน การประกาศธุรกรรมใหม่ ไม่จำเป็นต้องไปถึงทุก node ในเครือข่าย ตราบใดที่พวกเขายังไปถึง node ส่วนใหญ่ในระบบได้ ธุรกรรมเหล่านั้นก็จะถูกบรรจุอยู่ในบล็อกในไม่ช้า นอกจากนี้การประกาศบล็อกยังไม่ต้องกังวลเรื่องจะมีบล๊อกที่สูญหาย เนื่องจากหากว่า node ไม่ได้รับบล็อกใด ๆ node ก็จะตระหนักได้ว่าพลาดบล็อกก่อนหน้าไปเมื่อได้รับบล๊อกใหม่มา และ node จะทำการร้องขอ block ที่ขาดไปจากเครือข่าย 6.แรงจูงใจ(Incentive) ---- โดยปกติแล้ว ธุรกรรมแรกของแต่ละบล๊อกนั้นจะเป็นธุรกรรมพิเศษที่จะขุดเหรียญที่สร้างขึ้นใหม่ซึ่งเป็นกรรมสิทธิ์ของผู้สร้างบล็อกนั้น ๆ ซึ่งจะเป็นการเพิ่มแรงจูงใจให้กับ node ต่าง ๆ ในการสนับสนุนเครือข่าย และเป็นวิธีการกระจายเหรียญให้หมุนเวียน เนื่องจากไม่มีหน่วยงานส่วนกลางที่ทำหน้าที่ในการออกเหรียญ การเพิ่มเหรียญใหม่ในปริมาณคงที่อย่างต่อเนื่องนั้นคล้ายคลึงกับการที่คนงานเหมืองทองคำใช้แรง และ เวลา เพื่อเพิ่มทองคำให้หมุนเวียน ในกรณีนี้ คือ เวลา กำลังประมวลผล และไฟฟ้าที่ถูกใช้ไป นอกจากนี้แรงจูงใจจะมาจากค่าธรรมเนียมการทำธุรกรรม หากมูลค่าผลลัพธ์ของธุรกรรมน้อยกว่ามูลค่าที่ใส่เข้ามา ส่วนต่างนั้นก็คือค่าธรรมเนียมการทำธุรกรรมที่จะเพิ่มเข้าไปในมูลค่าแรงจูงใจของบล็อกที่มีธุรกรรมนั้น เมื่อเหรียญทั้งหมดในระบบมีจำนวนเท่ากับที่กำหนดไว้แล้ว แรงจูงใจหลักก็จะถูกเปลี่ยนมาเป็นค่าธรรมเนียมการทำธุรกรรม และปราศจากภาวะเงินเฟ้อโดยสิ้นเชิง แรงจูงใจอาจช่วยกระตุ้นให้ node ต่าง ๆ ยังคงซื่อสัตย์ หากผู้โจมตีที่ละโมบสามารถรวบรวมกำลังประมวลผล ได้มากกว่า node ที่ซื่อสัตย์ทั้งหมด เขาจะต้องเลือกระหว่างการใช้มันเพื่อฉ้อโกงผู้อื่นโดยการใช้จ่ายซ้ำซ้อน หรือใช้มันเพื่อสร้างเหรียญใหม่ พวกเขาจะพบว่าการเล่นตามกฎ กฎที่เอื้อประโยชน์ให้กับเขาด้วยเหรียญใหม่มากกว่าคนอื่น ๆ รวมกันนั้นทำกำไรได้มากกว่าการบ่อนทำลายระบบและความถูกต้องของทรัพย์สินของเขาเอง 7.การจัดการพื้นที่ดิสก์(Reclaiming Disk Space) ---- เมื่อธุรกรรมถูกบรรจุลงในบล๊อกแล้ว สามารถกำจัดธุรกรรมที่ใช้ไปแล้วก่อนหน้านั้นออกได้เพื่อประหยัดพื้นที่ดิสก์ แต่การจะทำอย่างนี้ได้โดยไม่ให้เลข hash ของบล๊อกมีการเปลี่ยนแปลงนั้น ธุรกรรมจึงจำเป็นต้องถูก hash ในรูปแบบของ Merkle Tree [7][2][5] โดยมีแค่ root node ของ tree เท่านั้นที่จะรวมอยู่ใน hash ของบล๊อก นี่เป็นวิธีที่ทำให้สามารถบีบอัดข้อมูลในบล๊อกเก่า ๆ ได้โดยการตัดพวก hash ส่วนอื่น ๆ ของ tree ที่ไม่ใช่ root node ออก (ไม่จำเป็นต้องเก็บ hash ในชั้นอื่น ๆ ของ tree) https://image.nostr.build/3ed95334891d91baca3f3f6f624a7ae22620be4ebfe0db5eb652cfce11255b9a.png โดยในส่วน header ของบล็อกที่ไม่มีธุรกรรมจะมีขนาดประมาณ 80 ไบต์ หากเราสมมติว่าบล็อกถูกสร้างขึ้นทุก ๆ 10 นาที 80 ไบต์ * 6 * 24 * 365 = 4.2MB ต่อปี โดยที่ระบบคอมพิวเตอร์ทั่วไปที่วางขายในปี 2551 มี RAM 2GB และกฎของมัวร์ทำนายการเติบโตในปัจจุบันที่ 1.2GB ต่อปี การจัดเก็บข้อมูลไม่น่าจะเป็นปัญหาแม้ว่าส่วนหัวของบล็อกจะต้องถูกเก็บไว้ในหน่วยความจำก็ตาม 8.การตรวจสอบธุรกรรม (Simplified Payment Verification) ---- การที่จะยืนยันการชำระเงินโดยไม่จำเป็นต้องรัน full node ได้นั้น ผู้ใช้เพียงแค่เก็บสำเนาของส่วนหัวบล็อก (block header) ของสายบล็อก (chain) ที่ยาวที่สุด ซึ่งสามารถรับได้โดยการสอบถามจาก node อื่น ๆ ในเครือข่ายจนมั่นใจว่าได้รับสายที่ยาวที่สุด และรับ Merkle branch ที่เชื่อมโยงธุรกรรมกับบล็อกที่มีการประทับเวลา (Timestamp) อยู่ ถึงแม้ผู้ใช้จะไม่สามารถตรวจสอบธุรกรรมด้วยตัวเองได้ แต่การเชื่อมโยงธุรกรรมกับตำแหน่งในสายบล็อกจะทำให้เห็นว่า node ในเครือข่ายยอมรับแล้ว และบล็อกที่เพิ่มเข้ามาหลังจากนั้นเป็นการยืนยันเพิ่มเติมว่าเครือข่ายยอมรับธุรกรรมนี้แล้ว https://i.imgur.com/VXtLpRF.png การตรวจสอบดังกล่าวจะเชื่อถือได้ตราบใดที่ node ที่ซื่อสัตย์ยังคงควบคุมเครือข่าย แต่จะมีความเสี่ยงมากขึ้นหากเครือข่ายถูกโจมตีและถูกควบคุม ในขณะที่ node ในเครือข่ายสามารถตรวจสอบธุรกรรมได้ด้วยตัวเอง แต่วิธีการแบบง่ายนี้อาจถูกหลอกลวงโดยการใช้ธุรกรรมปลอมของผู้โจมตี ตราบใดที่ผู้โจมตียังคงสามารถควบคุมเครือข่ายได้ กลยุทธ์หนึ่งในการป้องกันปัญหานี้คือ การรับการแจ้งเตือนจาก node อื่น ๆ ในเครือข่ายเมื่อตรวจพบบล็อกที่ไม่ถูกต้อง ซึ่งจะแจ้งให้ซอฟต์แวร์ของผู้ใช้ดาวน์โหลดบล็อกแบบเต็มและธุรกรรมที่แจ้งเตือน เพื่อยืนยันความไม่สอดคล้องกัน ธุรกิจที่ได้รับการชำระเงินบ่อยครั้งอาจยังคงต้องการรัน node ของตนเอง เพื่อความปลอดภัยที่เป็นอิสระและการตรวจสอบที่รวดเร็วยิ่งขึ้น 9.การควบรวมและแบ่งย่อยมูลค่า(Combining and Splitting Value) ---- แม้ว่าการจัดการเหรียญหลาย ๆ เหรียญจะเป็นสิ่งที่สามารถทำได้ แต่การจัดการธุรกรรมแยกต่างหากสำหรับแต่ละเหรียญในการโอนก็คงเป็นเรื่องที่น่าปวดหัวอยู่ดี ฉะนั้นแล้วเพื่อให้สามารถแยกและรวมมูลค่ากันได้ ธุรกรรมจึงสามารถมี input และ output ได้หลายรายการ ซึ่งโดยปกติแล้วจะมี input เดียวจากธุรกรรมก่อนหน้าที่มีขนาดใหญ่กว่า หรือ input จำนวนเล็ก ๆ หลาย ๆ รายการ และ output ไม่เกินสองรายการ คือ รายการหนึ่งสำหรับการชำระเงิน และอีกหนึ่งรายการสำหรับการส่งเงินทอน หากมีกลับไปยังผู้ส่ง https://image.nostr.build/9c6d3ce0e9f08c5b3fa3b82c2088ac6235603e5c0df3469060e6c9f74bce32fc.png ควรสังเกตว่า fan-out (กระจายของธุรกรรม) ซึ่งเป็นกรณีที่ธุรกรรม ธุรกรรมหนึ่งนั้นขึ้นอยู่กับหลายธุรกรรม และธุรกรรมเหล่านั้นเองก็ขึ้นอยู่กับอีกหลายธุรกรรม แต่ไม่ใช่ปัญหาในที่นี้ เพราะไม่มีความจำเป็นในการดึงประวัติการทำธุรกรรมทั้งหมดออกมาเป็นสำเนา 10.ความเป็นส่วนตัว(Privacy) ---- ในรูปแบบธนาคารแบบดั้งเดิมนั้น ความเป็นส่วนตัวเกิดขึ้นได้ด้วยการจำกัดการเข้าถึงข้อมูล โดยให้เฉพาะผู้ที่เกี่ยวข้องและบุคคลที่สามที่ได้รับความไว้วางใจเท่านั้น แต่เนื่องจากในระบบนี้เรามีความจำเป็นในการประกาศธุรกรรมทั้งหมดต่อสาธารณะ ทำให้ไม่สามารถใช้วิธีนี้ได้ แต่ยังจำเป็นต้องคงความเป็นส่วนตัวไว้ โดยการแบ่งการไหลของข้อมูล ด้วยการไม่เปิดเผยตัวตนของเจ้าของ public key คนทั่วไปสามารถเห็นว่ามีคนกำลังส่งเงินจำนวนหนึ่งให้กับคนอื่น แต่จะไม่ทราบข้อมูลที่เชื่อมโยงธุรกรรมนั้นกับบุคคลใด ๆ ซึ่งคล้ายกับระดับข้อมูลที่เปิดเผยโดยตลาดหลักทรัพย์ ซึ่งมีการเปิดเผยเวลาและขนาดของการซื้อขายแต่ละครั้งต่อสาธารณะ แต่ไม่ได้ระบุว่าคู่สัญญาคือใคร https://image.nostr.build/6ec3c84c7878dbd4558d2045518384daf5a341e86f4194cf367cc8426c2d72a7.png เพื่อเสริมในเรื่องของความปลอดภัย ควรใช้ key pair ใหม่สำหรับการทำธุรกรรมในแต่ละครั้ง เพื่อป้องกันไม่ให้เชื่อมโยงกับเจ้าของคนเดียวกันได้ อย่างไรก็ตาม การเชื่อมโยงบางอย่างยังคงหลีกเลี่ยงไม่ได้ ในธุรกรรมที่มี input หลายรายการ ซึ่งจำเป็นต้องเปิดเผยว่า input เหล่านั้นเป็นของเจ้าของคนเดียวกัน ความเสี่ยงก็คือ หากมีการเปิดเผยตัวตนของเจ้าของคีย์ การเชื่อมโยงอาจเปิดเผยธุรกรรมอื่น ๆ ที่เป็นของเจ้าของรายเดียวกันได้ 11.การคำนวณ(Calculations) ---- หากลองพิจารณาสถานการณ์ที่ผู้โจมตีพยายามสร้าง chain ปลอมให้เร็วกว่า chain จริง แม้ว่าจะทำได้สำเร็จ แต่มันก็ไม่สามารถทำให้ระบบเปิดรับการเปลี่ยนแปลงตามอำเภอใจได้อยู่ดี เช่น การสร้างมูลค่าจากอากาศธาตุ หรือการรับเงินที่ไม่เคยเป็นของผู้โจมตีมาก่อน Node ต่าง ๆ จะไม่ยอมรับธุรกรรมที่ไม่ถูกต้องเป็นการชำระเงิน และ Node ที่สุจริตก็จะไม่ยอมรับบล็อกที่มีธุรกรรมเหล่านั้นอย่างแน่นอน ผู้โจมตีทำได้เพียงพยายามเปลี่ยนแปลงธุรกรรมของตนเอง เพื่อนำเงินที่ใช้ไปแล้วกลับคืนมาเท่านั้น การแข่งขันระหว่าง chain สุจริตกับ chain ของผู้โจมตี สามารถอธิบายได้ด้วยแบบจำลองการเดินสุ่มทวินาม (Binomial Random Walk) โดยเหตุการณ์ที่สำเร็จ หมายถึง chain ที่สุจริตถูกขยายออกไปอีกหนึ่งบล็อก เพิ่มความยาวนำหน้าไป +1 และเหตุการณ์ที่ล้มเหลว หมายถึง chain ของผู้โจมตีถูกขยายออกไปหนึ่งบล็อก ลดช่องว่างลง -1 ความน่าจะเป็นที่ผู้โจมตีจะไล่ตามทันจากช่องว่างที่กำหนด สามารถเปรียบเทียบด้วย Gambler's Ruin problem โดยสมมติว่านักพนันที่มีเครดิตไม่จำกัด เริ่มต้นด้วยการขาดทุน และเล่นพนันไปเรื่อย ๆ เพื่อให้ถึงจุดคุ้มทุน เราสามารถคำนวณความน่าจะเป็นที่เขาจะกลับมาถึงจุดคุ้มทุนได้ หรือความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน chain ที่สุจริตได้ ดังนี้ [8]: p = ความน่าจะเป็นที่ Node ที่สุจริตจะพบบล็อกถัดไป q = ความน่าจะเป็นที่ผู้โจมตีจะพบบล็อกถัดไป qz = ความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน จากที่ตามหลังอยู่ z บล็อก https://i.imgur.com/vePe255.png จากสมมติฐานที่ว่า p > q ความน่าจะเป็นจะลดลงแบบเอกซ์โพเนนเชียล เมื่อจำนวนบล็อกที่ผู้โจมตีต้องไล่ตามทันเพิ่มขึ้น หากเขาไม่สามารถพุ่งขึ้นนำได้อย่างรวดเร็วตั้งแต่แรก โอกาสของเขาก็จะลดลงจนน้อยมาก ๆ เมื่อเขาตามหลังมากขึ้นเรื่อย ๆ ทีนี้ลองพิจารณาว่า ผู้รับธุรกรรมใหม่ต้องรอเป็นเวลานานเท่าใด จึงจะแน่ใจได้ว่าผู้ส่งไม่สามารถเปลี่ยนแปลงธุรกรรมได้แล้ว เราสมมติว่าผู้ส่งเป็นผู้โจมตี ที่ต้องการให้ผู้รับเชื่อว่าเขาได้รับเงินไปแล้ว จากนั้นจึงเปลี่ยนให้เงินกลับเข้าหาตัวเองหลังจากเวลาผ่านไประยะหนึ่ง ผู้รับจะได้รับแจ้งเมื่อเกิดเหตุการณ์นี้ขึ้น แต่ผู้ส่งหวังว่ามันจะสายเกินไปแล้ว ผู้รับจะสร้างคู่กุญแจใหม่ และให้กุญแจสาธารณะแก่ผู้ส่งไม่นานก่อนที่จะลงนาม ซึ่งจะป้องกันไม่ให้ผู้ส่งเตรียมบล็อกเชนปลอมไว้ล่วงหน้า โดยการทำงานอย่างต่อเนื่องจนกว่าเขาจะมีโอกาสได้บล็อกที่ยาวพอ จากนั้นจึงดำเนินธุรกรรมในทันที เมื่อส่งธุรกรรมแล้ว ผู้ส่งที่ไม่สุจริตจะเริ่มทำงานอย่างลับ ๆ บนบล็อกเชนคู่ขนาน ที่มีธุรกรรมในเวอร์ชันของเขาเองอยู่ ผู้รับจะรอจนกว่าธุรกรรมจะถูกเพิ่มลงในบล็อก และมีบล็อกที่ถูกเชื่อมต่อตามหลังมาอีก z บล็อก เขาไม่ทราบจำนวนความคืบหน้าที่แน่นอนที่ผู้โจมตีได้ทำไปแล้ว แต่สมมติว่าบล็อกที่สุจริตใช้เวลาเฉลี่ยต่อบล็อกตามที่คาดไว้ ความคืบหน้าที่อาจเกิดขึ้นได้ของผู้โจมตีจะเป็นการแจกแจงแบบปัวซง (Poisson distribution) ซึ่งมีค่าคาดหวังดังนี้: https://i.imgur.com/mYsb48i.png เพื่อให้ได้ความน่าจะเป็นที่ผู้โจมตียังคงสามารถไล่ทันได้ เราจะคูณความหนาแน่นของปัวซง สำหรับความคืบหน้าแต่ละระดับที่เขาสามารถทำได้ ด้วยความน่าจะเป็นที่เขาสามารถไล่ทันจากจุดนั้น: https://i.imgur.com/jQGkQ8r.png จัดเรียงใหม่เพื่อหลีกเลี่ยง infinite tail ของการแจกแจง https://i.imgur.com/OOO6Gm9.png แปลงมันให้เป็น C code #include <math.h> double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; } เมื่อรันผลลัพธ์บางส่วน เราจะเห็นว่าความน่าจะเป็นลดลงแบบเอกซ์โพเนนเชียลเมื่อ z เพิ่มขึ้น q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012 q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006 การแก้หาค่า P ที่น้อยกว่า 0.1%... P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340 12.สรุป(Conclusion) เราได้นำเสนอระบบธุรกรรมอิเล็กทรอนิกส์ที่ไม่ต้องพึ่งพาความไว้วางใจ เริ่มต้นจากกรอบแนวคิดของเหรียญที่สร้างจากลายเซ็นดิจิทัล ซึ่งช่วยควบคุมความเป็นเจ้าของได้อย่างดีแต่ก็ยังไม่สมบูรณ์ หากปราศจากวิธีการป้องกันการใช้จ่ายซ้ำซ้อน เพื่อแก้ปัญหานี้ เราจึงเสนอเครือข่ายแบบเพียร์ทูเพียร์ที่ใช้ proof-of-work ในการบันทึกประวัติธุรกรรมสาธารณะ ซึ่งจะกลายเป็นเรื่องยากอย่างมากสำหรับผู้โจมตีที่จะเปลี่ยนแปลง หาก node ที่ซื่อสัตย์ควบคุมพลังประมวลผล CPU ส่วนใหญ่ เครือข่ายนี้มีความแข็งแกร่งในความเรียบง่ายที่ไม่มีโครงสร้างใด ๆ ที่ซับซ้อน node ต่าง ๆ ทำงานพร้อมกันโดยประสานงานกันเพียงเล็กน้อย ไม่จำเป็นต้องระบุตัวตน เนื่องจากข้อความไม่ได้ถูกส่งไปยังสถานที่ใดสถานที่หนึ่งโดยเฉพาะ และเพียงแค่ต้องส่งมอบให้ถึงมือผู้รับอย่างดีที่สุด node สามารถออกจากและเข้าร่วมเครือข่ายได้ตามต้องการ โดยยอมรับ chain ที่มี proof-of-work มากที่สุดเป็นสิ่งที่เกิดขึ้นในขณะที่ไม่ได้เชื่อมต่อ พวกเขาโหวตด้วยพลังประมวลผล CPU แสดงการยอมรับบล็อกที่ถูกต้องโดยการทำงานเพื่อขยายบล็อก และปฏิเสธบล็อกที่ไม่ถูกต้องโดยการปฏิเสธที่จะทำงานกับบล็อกเหล่านั้น กฎและแรงจูงใจใด ๆ ที่จำเป็นสามารถบังคับใช้ได้ด้วยกลไกฉันทามตินี้ ไปอ่านต่อกันเองเด้ออ --- [1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [6] A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [8] W. Feller, "An introduction to probability theory and its applications," 1957.
@ 79008e78:dfac9395
2024-09-02 06:17:23ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer ---- ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer นั้นจะช่วยให้เราสามารถชำระเงินผ่านทางออนไลน์ได้โดยตรงจากฝ่ายหนึ่งไปยังอีกฝ่ายหนึ่งโดยไม่ต้องผ่านตัวกลางอย่างพวกสถาบันการเงิน โดยใช้ digital signature เป็นส่วนหนึ่งในการแก้ปัญหานี้ แต่มันจะไม่มีประโยชน์ใด ๆ เลยหากยังคงต้องอาศัยตัวกลางที่เชื่อถือได้มาแก้ปัญหา double spending เราขอเสนอวิธีแก้ปัญหา double spending โดยใช้เครือข่ายแบบ peer-to-peer ให้เครือข่ายคอยประทับเวลาธุรกรรมต่าง ๆ ในระบบและนำมาเรียงร้อยกันเป็นเส้นสายของ proof-of-work ที่ใช้ hash เพื่อสร้างธุรกรรมที่ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ต้องทำ proof-of-work ใหม่ โดยให้เส้นสายที่ยาวที่สุดนั้น ไม่เพียงแต่ทำหน้าที่เป็นลำดับของธุรกรรมที่เกิดขึ้นเท่านั้น แต่ยังเป็นสิ่งที่พิสูจน์ได้ว่ามาจากกำลังประมวลผล CPU ที่มากที่สุด และตราบใดที่ nodes ส่วนใหญ่ไม่ได้ร่วมมือกันโจมตีเครือข่ายและยังคงควบคุมกำลังประมวลผลส่วนใหญ่ในระบบไว้ พวกเขาก็จะสร้างเส้นสายที่ยาวที่สุดและสามารถเอาชนะผู้ประสงค์ร้ายที่จะโจมตีระบบได้ ตัวเครือข่ายเองไม่ได้ต้องมีโครงสร้างอะไรที่ซับซ้อน ข้อมูลต่าง ๆ ในเครือข่ายจะถูกกระจายส่งต่อโดยไม่ต้องสนใจว่าผู้รับจะได้รับหรือไม่ และ nodes ต่าง ๆ เองก็สามารถที่จะออกจากเครือข่ายและกลับเข้าร่วมใหม่ได้ตามที่ต้องการ โดยยอมรับเส้น proof-of-work ที่ยาวที่สุด เป็นหลักฐานของสิ่งที่เกิดขึ้นในขณะที่ node นั้น ๆ ไม่ได้อยู่ในเครือข่าย 1.บทนำ (Introduction) ----- ไม่ว่าใครจะใคร่ซื้อใคร่ขายอะไรใด ๆ บนอินเตอร์เน็ตนั้น ก็จำเป็นต้องพึ่งพาสถาบันการเงินในฐานะของบุคคลที่สามเพื่อดำเนินการชำระเงินทางอิเล็กทรอนิกส์เสมอ ๆ ซึ่งถึงแม้ว่าระบบนี้มันจะทำงานได้ดีสำหรับธุรกรรมส่วนใหญ่ ๆ แต่ระบบก็ก็มีจุดอ่อนอยู่ที่ยังต้องอาศัยความไว้เนื้อเชื่อใจ (trust) ในระบบนี้การทำธุรกรรมที่ไม่สามารถย้อนกลับได้อย่างสมบูรณ์นั้นมันแทบจะเป็นไปไม่ได้เลย เนื่องจากสถาบันการเงินไม่สามารถหลีกเลี่ยงการเป็นตัวกลางในการไกล่เกลี่ยข้อพิพาทต่าง ๆ ที่อาจเกิดขึ้นได้ มิหนำซ้ำต้นทุนในการไกล่เกลี่ยยังทำให้ต้นทุนการทำธุรกรรมเพิ่มสูงขึ้น และเมื่อต้นทุนสูงขึ้นขนาดของธุรกรรมที่สามารถใช้งานได้จริงก็สูงขึ้นตามไปด้วย ธุรกรรมเล็ก ๆ น้อย ๆ ก็ไม่สามารถเกิดขึ้นได้ เมื่อมีความเป็นไปได้ที่ธุรกรรมจะเกิดการย้อนกลับ ความจำเป็นในการสร้างความไว้วางใจก็ยิ่งทวีคูณมากขึ้น ผู้ค้าก็จำเป็นต้องระมัดระวังลูกค้า ต้องเรียกร้องข้อมูลมากกว่าที่จำเป็น การฉ้อโกงกลายเป็นเรื่องที่หลีกเลี่ยงไม่ได้เพราะต้นทุนและความไม่แน่นอนในทำธุรกรรมเหล่านี้ แน่นอนว่าเราสามารถหลีกเลี่ยงมันได้โดยการใช้เงินสด แต่ก็ไม่มีกลไกใดที่ทำให้สามารถใช้เงินสดผ่านช่องทางการสื่อสาร (เอาให้เข้าใจง่ายก็อินเตอร์เน็ต)ได้ โดยไม่ต้องมีตัวกลาง ;-; แปลว่าสิ่งที่จำเป็นสำหรับการแก้ไขปัญหานี้คือระบบการชำระเงินทางอิเล็กทรอนิกส์ ที่อยู่บนพื้นฐานของการพิสูจน์ด้วยการเข้ารหัสแทนที่จะเป็นความไว้วางใจ ซึ่งจะทำให้คู่สัญญาสองฝ่ายที่ยินยอมสามารถทำธุรกรรมร่วมกันได้โดยตรง โดยไม่จำเป็นต้องมีบุคคลที่สามมาคอยเป็นตัวกลาง ธุรกรรมที่ยากต่อการย้อนกลับจะช่วยปกป้องผู้ขายจากการฉ้อโกง และสามารถใช้กลไก escrow เพื่อปกป้องผู้ซื้อได้อีกด้วย ในเอกสารชุดนี้ เราขอเสนอวิธีแก้ปัญหาการใช้จ่ายซ้ำซ้อนโดยใช้เซิร์ฟเวอร์ timestamp กระจายศูนย์แบบ peer-to-peer เพื่อสร้างหลักฐานการคำนวณลำดับเวลาของธุรกรรม โดยระบบนี้จะปลอดภัยตราบใดที่กลุ่มของ node ที่ซื่อสัตย์ ยังคงมีกำลังประมวลผลที่มากกว่ากลุ่มที่ประสงค์ร้ายกับระบบ 2.ธุรกรรม (Transactions) ---- นิยามของเหรียญอิเล็กทรอนิกส์ในที่นี้ คือห่วงโซ่ที่คล้องเกี่ยวกันของ digital signature โดยที่เจ้าของเหรียญอิเล็กทรอนิกส์จะโอนเหรียญไปยังเจ้าของคนถัดไป ด้วยการลง digital signature บน hash ของธุรกรรมก่อนหน้ารวมถึงกุญแจสาธารณะของเจ้าของคนถัดไป และผนวกมันไว้ที่ส่วนท้ายของธุรกรรม และผู้รับเงินเองก็สามารถตรวจสอบลายเซ็นเพื่อยืนยันความเป็นเจ้าของได้ https://image.nostr.build/a467896797a9fb9f98c3c234f0adb4df2376f2c3d9a7cc9d8672d7a9f5aa9efa.png แน่นอนว่าปัญหาก็คือผู้รับเงินไม่สามารถตรวจสอบได้ว่าเจ้าของคนใดคนหนึ่งก่อนหน้าเขาได้ใช้เหรียญดังกล่าวซ้ำซ้อนมากกว่าหนึ่งครั้งหรือไม่ และวิธีการแก้ไขปัญหานี้โดยทั่วไปก็คงเป็นการกำหนดตัวกลางที่มีความน่าเชื่อถือมาเป็นคนตรวจสอบทุกธุรกรรมเพื่อป้องกันการใช้จ่ายซ้ำซ้อน และหลังจากการทำธุรกรรมแต่ละครั้ง เหรียญจะต้องถูกส่งกลับไปยังตัวกลางเพื่อออกเหรียญใหม่ และจะมีเพียงเหรียญที่ออกจากตัวกลางโดยตรงเท่านั้นที่จะเชื่อถือได้ว่าจะไม่ถูกใช้จ่ายซ้ำซ้อน แต่ปัญหาก็คือ ชะตากรรมของระบบเงินทั้งหมดจะขึ้นอยู่กับตัวกลางตัวนี้ เพราะทุกธุรกรรมจำเป็นจะต้องผ่านพวกเขา ซึ่งก็ไม่ต่างอะไรกับธนาคาร เราจึงต้องการวิธีการที่ทำให้ผู้รับเงินทราบได้ว่าเจ้าของคนก่อน ๆ ไม่ได้ลงนามในธุรกรรมใด ๆ มาก่อน เพื่อให้บรรลุวัตถุประสงค์นี้ เราจะทำการนับว่าธุรกรรมที่เกิดขึ้นก่อนเป็นธุรกรรมที่ถูกต้อง และจะไม่สนใจความพยายามใด ๆ ในการที่จะใช้เหรียญนั้น ๆ ซ้ำอีก และวิธีเดียวที่ทำแบบนี้ได้ คือการรับรู้ถึงธุรกรรมทั้งหมด เช่นเดียวกับโมเดลที่ได้กล่าวข้างต้น ที่ตัวกลางจะรับรู้ถึงธุรกรรมทั้งหมดและตัดสินว่าธุรกรรมใดมาก่อนมาหลัง เพื่อให้บรรลุเป้าหมายนี้โดยไม่ต้องมีบุคคลที่สามที่เชื่อถือได้ ธุรกรรมทั้งหมดจะต้องถูกประกาศต่อสาธารณะ [1] และเราต้องการระบบที่ผู้เข้าร่วมเห็นพ้องในประวัติธุรกรรมชุดเดียวกันตามลำดับที่ได้รับ ส่วนผู้รับเงินก็จำเป็นจะต้องมีหลักฐานว่า ในขณะที่ทำธุรกรรม "โหนด" ส่วนใหญ่ในระบบเห็นพ้องต้องกันว่าธุรกรรมนั้นได้รับเป็นลำดับแรก(ไม่มีธุรกรรมที่ใช้เหรียญพวกนี้มาก่อน) 3.ระบบบันทึกเวลา (Timestamp Server) ---- สำหรับแนวทางการแก้ปัญหาในครั้งนี้ เราจะใช้ประโยชน์จาก timestamp server ที่จะทำหน้าที่บันทึก hash ของบล๊อกที่ต้องการให้มีการบันทึกเวลา และจากนั้นจะทำการเผยแพร่ hash ดังกล่าว เหมือนกับหนังสือพิมพ์หรือโพสต์ใน Usenet [2-5] (ฟีลแบบทุกคนจะเห็นโพสต์นี้น้าา ประมาณนั้น) การบันทึกเวลานี้จะพิสูจน์ได้ว่าข้อมูลที่ถูก hash นั้นจะต้องมีอยู่จริงในเวลานั้นเพื่อให้ได้มาซึ่ง hash ดังกล่าว แต่ละการบันทึกเวลาจะรวมการบันทึกเวลาของหน้านี้ไว้ใน hash ของมันเพื่อสร้างเป็น chain โดยการบันทึกเวลาแต่ละครั้งจะยืนยันความถูกต้องของการบันทึกก่อนหน้าได้อีกด้วยด้วย https://image.nostr.build/ddf92417c45dbb6e25da0af80a10d4cdbc3e725d047d65f54a3e3bfcf358c4d6.png 4.พรูฟ-ออฟ-เวิร์ค (Proof-of-Work) ---- ในการสร้าง Timestamp Server แบบกระจายศูนย์บนพื้นฐานแบบ peer to peer เราจำเป็นต้องใช้ระบบ Proof-of-Work (PoW) ที่คล้ายกับ Hashcash ของ Adam Back [6] แทนที่จะใช้วิธีการแบบเดิม ๆ อย่างการประกาศในหนังสือพิมพ์หรือ Usenet โดย PoW ใช้ในการตรวจสอบค่าที่มาจากกระบวนการ hash เช่น SHA-256 แล้ว ผลลัพธ์ที่ได้ (Hash) จะขึ้นต้นด้วยเลขศูนย์จำนวนหนึ่ง โดยที่ work (ประมาณว่าพลังประมวลผล) ที่ต้องใช้จะเพิ่มขึ้นแบบทวีคูณตามจำนวนเลขศูนย์ที่ต้องการ และสามารถตรวจสอบได้โดยการรัน Hash เพียงครั้งเดียว ซึ่งสำหรับ timestamp network ของเรานั้น เราใช้ PoW โดยการเพิ่มค่า Nonce ในบล็อกไปเรื่อย ๆ จนกว่าจะพบค่าที่ทำให้ Hash ของบล็อกนั้นมีเลขศูนย์ตามที่กำหนด และเมื่อใช้กำลังประมวลผลของ CPU ไปกับการทำ PoW จนสำเร็จแล้ว บล็อกจะไม่สามารถเปลี่ยนแปลงได้ หากไม่มีการทำงานซ้ำใหม่ เนื่องจากบล็อกที่สร้างขึ้นภายหลังจะเชื่อมโยงกับบล็อกก่อนหน้า การเปลี่ยนแปลงบล็อกใด ๆ จะต้องทำ PoW ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด https://image.nostr.build/c039ef4ca6833cb1ecee65ac5991df2406be9b7e490b86b3b19f94f267767182.png นอกจากนี้ PoW ยังช่วยแก้ปัญหาของเสียงส่วนมากที่มาตัดสินใจในระบบนี้ เพราะหากเสียงข้างมากอ้างอิงจากหลักการหนึ่ง IP หนึ่งเสียง ใครก็ตามที่สามารถสร้าง IP ได้จำนวนมากก็จะสามารถควบคุมระบบได้ จึงใช้หลักการหนึ่ง CPU หนึ่งเสียงแทน การตัดสินใจของเสียงข้างมากจะแสดงด้วย Chain ที่ยาวที่สุด ซึ่งบ่งบอกถึงความพยายามในการคำนวณ (Proof-of-Work) ที่มากที่สุด หาก Node ที่ซื่อสัตย์ (Honest nodes) มีกำลังประมวลผลของ CPU ส่วนใหญ่อยู่ในการควบคุม Honest Chain ก็จะเติบโตเร็วที่สุดและแซงหน้า Chain อื่น ๆ ได้ ผู้โจมตีที่ต้องการแก้ไขบล็อกในอดีตจะต้องทำ Proof-of-Work ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด และต้องทำงานให้เร็วกว่า Honest Node ด้วย ซึ่งโอกาสที่ผู้โจมตีจะตามทันนั้นจะลดลงแบบทวีคูณเมื่อมีการเพิ่มบล็อกมากขึ้น เพื่อชดเชยความเร็วของฮาร์ดแวร์ที่เพิ่มขึ้นและความสนใจในการรัน Node ที่ผันผวน ระดับความยากของ Proof-of-Work จะถูกกำหนดโดยค่าเฉลี่ย โดยตั้งเป้าไว้ที่จำนวนบล็อกเฉลี่ยต่อชั่วโมง หากสร้างบล็อกได้เร็วเกินไป ระดับความยากก็จะเพิ่มขึ้น 5.เครือข่าย (Network) ---- เครือข่ายนั้นมีการทำงาน ดังนี้ 1. การประกาศธุรกรรมใหม่: ธุรกรรมใหม่จะถูกประกาศ (broadcast) ไปยังทุก node ในเครือข่าย 2. การรวบรวมธุรกรรม: แต่ละ node จะรวบรวมธุรกรรมใหม่ ๆ เหล่านี้ ไว้ในบล็อก 3. การค้นหา Proof-of-Work: แต่ละ node จะทำการคำนวณ เพื่อค้นหา Proof-of-Work ตามค่า difficulty สำหรับบล็อกนั้น ๆ 4. การประกาศบล็อก: เมื่อ node ใดค้นหา Proof-of-Work ได้แล้ว node นั้นจะทำการประกาศบล็อกไปยังทุก node ในเครือข่าย 5. การตรวจสอบและยอมรับบล็อก: node อื่น ๆ จะทำการตรวจสอบและยอมรับบล็อกนั้น เฉพาะเมื่อธุรกรรมทั้งหมดภายในบล็อกนั้นถูกต้องและยังไม่ถูกใช้มาก่อน 6. การสร้างบล็อกถัดไป: node ต่าง ๆ แสดงการยอมรับบล็อกโดยการเริ่มต้นสร้างบล็อกถัดไปใน chain ด้วย hash ของบล็อกที่ยอมรับ เป็น hash ก่อนหน้าในโครงสร้างของบล๊อกใหม่ที่กำลังสร้าง node ต่าง ๆ จะถือว่า chain ที่ยาวที่สุดเป็น chain ที่ถูกต้องและจะทำงานเพื่อขยาย chain นั้นต่อไป หากมีสอง node ที่ได้ประกาศบล็อกเวอร์ชันที่แตกต่างกันในเวลาพร้อมกัน node บาง node อาจได้รับบล็อกหนึ่งก่อน อีกบล็อกหนึ่ง ในกรณีนี้ node เหล่านั้น จะทำงานบนบล็อกที่ได้รับก่อน แต่จะเก็บสำเนาของบล็อกอีกอันหนึ่งไว้ ในกรณีที่บล็อกนั้น กลายเป็นบล็อกที่อยู่ใน chain ที่ยาวกว่าปัญหาข้อโต้แย้งนี้ก็จะได้รับการแก้ไข เมื่อพบ Proof-of-Work อันถัดไปและ chain ใด chain หนึ่งยาวขึ้น node ที่กำลังทำงานอยู่บน chain ที่สั้นกว่าก็จะเปลี่ยนไปทำงานบน chain ที่ยาวกว่าแทน การประกาศธุรกรรมใหม่ ไม่จำเป็นต้องไปถึงทุก node ในเครือข่าย ตราบใดที่พวกเขายังไปถึง node ส่วนใหญ่ในระบบได้ ธุรกรรมเหล่านั้นก็จะถูกบรรจุอยู่ในบล็อกในไม่ช้า นอกจากนี้การประกาศบล็อกยังไม่ต้องกังวลเรื่องจะมีบล๊อกที่สูญหาย เนื่องจากหากว่า node ไม่ได้รับบล็อกใด ๆ node ก็จะตระหนักได้ว่าพลาดบล็อกก่อนหน้าไปเมื่อได้รับบล๊อกใหม่มา และ node จะทำการร้องขอ block ที่ขาดไปจากเครือข่าย 6.แรงจูงใจ(Incentive) ---- โดยปกติแล้ว ธุรกรรมแรกของแต่ละบล๊อกนั้นจะเป็นธุรกรรมพิเศษที่จะขุดเหรียญที่สร้างขึ้นใหม่ซึ่งเป็นกรรมสิทธิ์ของผู้สร้างบล็อกนั้น ๆ ซึ่งจะเป็นการเพิ่มแรงจูงใจให้กับ node ต่าง ๆ ในการสนับสนุนเครือข่าย และเป็นวิธีการกระจายเหรียญให้หมุนเวียน เนื่องจากไม่มีหน่วยงานส่วนกลางที่ทำหน้าที่ในการออกเหรียญ การเพิ่มเหรียญใหม่ในปริมาณคงที่อย่างต่อเนื่องนั้นคล้ายคลึงกับการที่คนงานเหมืองทองคำใช้แรง และ เวลา เพื่อเพิ่มทองคำให้หมุนเวียน ในกรณีนี้ คือ เวลา กำลังประมวลผล และไฟฟ้าที่ถูกใช้ไป นอกจากนี้แรงจูงใจจะมาจากค่าธรรมเนียมการทำธุรกรรม หากมูลค่าผลลัพธ์ของธุรกรรมน้อยกว่ามูลค่าที่ใส่เข้ามา ส่วนต่างนั้นก็คือค่าธรรมเนียมการทำธุรกรรมที่จะเพิ่มเข้าไปในมูลค่าแรงจูงใจของบล็อกที่มีธุรกรรมนั้น เมื่อเหรียญทั้งหมดในระบบมีจำนวนเท่ากับที่กำหนดไว้แล้ว แรงจูงใจหลักก็จะถูกเปลี่ยนมาเป็นค่าธรรมเนียมการทำธุรกรรม และปราศจากภาวะเงินเฟ้อโดยสิ้นเชิง แรงจูงใจอาจช่วยกระตุ้นให้ node ต่าง ๆ ยังคงซื่อสัตย์ หากผู้โจมตีที่ละโมบสามารถรวบรวมกำลังประมวลผล ได้มากกว่า node ที่ซื่อสัตย์ทั้งหมด เขาจะต้องเลือกระหว่างการใช้มันเพื่อฉ้อโกงผู้อื่นโดยการใช้จ่ายซ้ำซ้อน หรือใช้มันเพื่อสร้างเหรียญใหม่ พวกเขาจะพบว่าการเล่นตามกฎ กฎที่เอื้อประโยชน์ให้กับเขาด้วยเหรียญใหม่มากกว่าคนอื่น ๆ รวมกันนั้นทำกำไรได้มากกว่าการบ่อนทำลายระบบและความถูกต้องของทรัพย์สินของเขาเอง 7.การจัดการพื้นที่ดิสก์(Reclaiming Disk Space) ---- เมื่อธุรกรรมถูกบรรจุลงในบล๊อกแล้ว สามารถกำจัดธุรกรรมที่ใช้ไปแล้วก่อนหน้านั้นออกได้เพื่อประหยัดพื้นที่ดิสก์ แต่การจะทำอย่างนี้ได้โดยไม่ให้เลข hash ของบล๊อกมีการเปลี่ยนแปลงนั้น ธุรกรรมจึงจำเป็นต้องถูก hash ในรูปแบบของ Merkle Tree [7][2][5] โดยมีแค่ root node ของ tree เท่านั้นที่จะรวมอยู่ใน hash ของบล๊อก นี่เป็นวิธีที่ทำให้สามารถบีบอัดข้อมูลในบล๊อกเก่า ๆ ได้โดยการตัดพวก hash ส่วนอื่น ๆ ของ tree ที่ไม่ใช่ root node ออก (ไม่จำเป็นต้องเก็บ hash ในชั้นอื่น ๆ ของ tree) https://image.nostr.build/3ed95334891d91baca3f3f6f624a7ae22620be4ebfe0db5eb652cfce11255b9a.png โดยในส่วน header ของบล็อกที่ไม่มีธุรกรรมจะมีขนาดประมาณ 80 ไบต์ หากเราสมมติว่าบล็อกถูกสร้างขึ้นทุก ๆ 10 นาที 80 ไบต์ * 6 * 24 * 365 = 4.2MB ต่อปี โดยที่ระบบคอมพิวเตอร์ทั่วไปที่วางขายในปี 2551 มี RAM 2GB และกฎของมัวร์ทำนายการเติบโตในปัจจุบันที่ 1.2GB ต่อปี การจัดเก็บข้อมูลไม่น่าจะเป็นปัญหาแม้ว่าส่วนหัวของบล็อกจะต้องถูกเก็บไว้ในหน่วยความจำก็ตาม 8.การตรวจสอบธุรกรรม (Simplified Payment Verification) ---- การที่จะยืนยันการชำระเงินโดยไม่จำเป็นต้องรัน full node ได้นั้น ผู้ใช้เพียงแค่เก็บสำเนาของส่วนหัวบล็อก (block header) ของสายบล็อก (chain) ที่ยาวที่สุด ซึ่งสามารถรับได้โดยการสอบถามจาก node อื่น ๆ ในเครือข่ายจนมั่นใจว่าได้รับสายที่ยาวที่สุด และรับ Merkle branch ที่เชื่อมโยงธุรกรรมกับบล็อกที่มีการประทับเวลา (Timestamp) อยู่ ถึงแม้ผู้ใช้จะไม่สามารถตรวจสอบธุรกรรมด้วยตัวเองได้ แต่การเชื่อมโยงธุรกรรมกับตำแหน่งในสายบล็อกจะทำให้เห็นว่า node ในเครือข่ายยอมรับแล้ว และบล็อกที่เพิ่มเข้ามาหลังจากนั้นเป็นการยืนยันเพิ่มเติมว่าเครือข่ายยอมรับธุรกรรมนี้แล้ว https://i.imgur.com/VXtLpRF.png การตรวจสอบดังกล่าวจะเชื่อถือได้ตราบใดที่ node ที่ซื่อสัตย์ยังคงควบคุมเครือข่าย แต่จะมีความเสี่ยงมากขึ้นหากเครือข่ายถูกโจมตีและถูกควบคุม ในขณะที่ node ในเครือข่ายสามารถตรวจสอบธุรกรรมได้ด้วยตัวเอง แต่วิธีการแบบง่ายนี้อาจถูกหลอกลวงโดยการใช้ธุรกรรมปลอมของผู้โจมตี ตราบใดที่ผู้โจมตียังคงสามารถควบคุมเครือข่ายได้ กลยุทธ์หนึ่งในการป้องกันปัญหานี้คือ การรับการแจ้งเตือนจาก node อื่น ๆ ในเครือข่ายเมื่อตรวจพบบล็อกที่ไม่ถูกต้อง ซึ่งจะแจ้งให้ซอฟต์แวร์ของผู้ใช้ดาวน์โหลดบล็อกแบบเต็มและธุรกรรมที่แจ้งเตือน เพื่อยืนยันความไม่สอดคล้องกัน ธุรกิจที่ได้รับการชำระเงินบ่อยครั้งอาจยังคงต้องการรัน node ของตนเอง เพื่อความปลอดภัยที่เป็นอิสระและการตรวจสอบที่รวดเร็วยิ่งขึ้น 9.การควบรวมและแบ่งย่อยมูลค่า(Combining and Splitting Value) ---- แม้ว่าการจัดการเหรียญหลาย ๆ เหรียญจะเป็นสิ่งที่สามารถทำได้ แต่การจัดการธุรกรรมแยกต่างหากสำหรับแต่ละเหรียญในการโอนก็คงเป็นเรื่องที่น่าปวดหัวอยู่ดี ฉะนั้นแล้วเพื่อให้สามารถแยกและรวมมูลค่ากันได้ ธุรกรรมจึงสามารถมี input และ output ได้หลายรายการ ซึ่งโดยปกติแล้วจะมี input เดียวจากธุรกรรมก่อนหน้าที่มีขนาดใหญ่กว่า หรือ input จำนวนเล็ก ๆ หลาย ๆ รายการ และ output ไม่เกินสองรายการ คือ รายการหนึ่งสำหรับการชำระเงิน และอีกหนึ่งรายการสำหรับการส่งเงินทอน หากมีกลับไปยังผู้ส่ง https://image.nostr.build/9c6d3ce0e9f08c5b3fa3b82c2088ac6235603e5c0df3469060e6c9f74bce32fc.png ควรสังเกตว่า fan-out (กระจายของธุรกรรม) ซึ่งเป็นกรณีที่ธุรกรรม ธุรกรรมหนึ่งนั้นขึ้นอยู่กับหลายธุรกรรม และธุรกรรมเหล่านั้นเองก็ขึ้นอยู่กับอีกหลายธุรกรรม แต่ไม่ใช่ปัญหาในที่นี้ เพราะไม่มีความจำเป็นในการดึงประวัติการทำธุรกรรมทั้งหมดออกมาเป็นสำเนา 10.ความเป็นส่วนตัว(Privacy) ---- ในรูปแบบธนาคารแบบดั้งเดิมนั้น ความเป็นส่วนตัวเกิดขึ้นได้ด้วยการจำกัดการเข้าถึงข้อมูล โดยให้เฉพาะผู้ที่เกี่ยวข้องและบุคคลที่สามที่ได้รับความไว้วางใจเท่านั้น แต่เนื่องจากในระบบนี้เรามีความจำเป็นในการประกาศธุรกรรมทั้งหมดต่อสาธารณะ ทำให้ไม่สามารถใช้วิธีนี้ได้ แต่ยังจำเป็นต้องคงความเป็นส่วนตัวไว้ โดยการแบ่งการไหลของข้อมูล ด้วยการไม่เปิดเผยตัวตนของเจ้าของ public key คนทั่วไปสามารถเห็นว่ามีคนกำลังส่งเงินจำนวนหนึ่งให้กับคนอื่น แต่จะไม่ทราบข้อมูลที่เชื่อมโยงธุรกรรมนั้นกับบุคคลใด ๆ ซึ่งคล้ายกับระดับข้อมูลที่เปิดเผยโดยตลาดหลักทรัพย์ ซึ่งมีการเปิดเผยเวลาและขนาดของการซื้อขายแต่ละครั้งต่อสาธารณะ แต่ไม่ได้ระบุว่าคู่สัญญาคือใคร https://image.nostr.build/6ec3c84c7878dbd4558d2045518384daf5a341e86f4194cf367cc8426c2d72a7.png เพื่อเสริมในเรื่องของความปลอดภัย ควรใช้ key pair ใหม่สำหรับการทำธุรกรรมในแต่ละครั้ง เพื่อป้องกันไม่ให้เชื่อมโยงกับเจ้าของคนเดียวกันได้ อย่างไรก็ตาม การเชื่อมโยงบางอย่างยังคงหลีกเลี่ยงไม่ได้ ในธุรกรรมที่มี input หลายรายการ ซึ่งจำเป็นต้องเปิดเผยว่า input เหล่านั้นเป็นของเจ้าของคนเดียวกัน ความเสี่ยงก็คือ หากมีการเปิดเผยตัวตนของเจ้าของคีย์ การเชื่อมโยงอาจเปิดเผยธุรกรรมอื่น ๆ ที่เป็นของเจ้าของรายเดียวกันได้ 11.การคำนวณ(Calculations) ---- หากลองพิจารณาสถานการณ์ที่ผู้โจมตีพยายามสร้าง chain ปลอมให้เร็วกว่า chain จริง แม้ว่าจะทำได้สำเร็จ แต่มันก็ไม่สามารถทำให้ระบบเปิดรับการเปลี่ยนแปลงตามอำเภอใจได้อยู่ดี เช่น การสร้างมูลค่าจากอากาศธาตุ หรือการรับเงินที่ไม่เคยเป็นของผู้โจมตีมาก่อน Node ต่าง ๆ จะไม่ยอมรับธุรกรรมที่ไม่ถูกต้องเป็นการชำระเงิน และ Node ที่สุจริตก็จะไม่ยอมรับบล็อกที่มีธุรกรรมเหล่านั้นอย่างแน่นอน ผู้โจมตีทำได้เพียงพยายามเปลี่ยนแปลงธุรกรรมของตนเอง เพื่อนำเงินที่ใช้ไปแล้วกลับคืนมาเท่านั้น การแข่งขันระหว่าง chain สุจริตกับ chain ของผู้โจมตี สามารถอธิบายได้ด้วยแบบจำลองการเดินสุ่มทวินาม (Binomial Random Walk) โดยเหตุการณ์ที่สำเร็จ หมายถึง chain ที่สุจริตถูกขยายออกไปอีกหนึ่งบล็อก เพิ่มความยาวนำหน้าไป +1 และเหตุการณ์ที่ล้มเหลว หมายถึง chain ของผู้โจมตีถูกขยายออกไปหนึ่งบล็อก ลดช่องว่างลง -1 ความน่าจะเป็นที่ผู้โจมตีจะไล่ตามทันจากช่องว่างที่กำหนด สามารถเปรียบเทียบด้วย Gambler's Ruin problem โดยสมมติว่านักพนันที่มีเครดิตไม่จำกัด เริ่มต้นด้วยการขาดทุน และเล่นพนันไปเรื่อย ๆ เพื่อให้ถึงจุดคุ้มทุน เราสามารถคำนวณความน่าจะเป็นที่เขาจะกลับมาถึงจุดคุ้มทุนได้ หรือความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน chain ที่สุจริตได้ ดังนี้ [8]: p = ความน่าจะเป็นที่ Node ที่สุจริตจะพบบล็อกถัดไป q = ความน่าจะเป็นที่ผู้โจมตีจะพบบล็อกถัดไป qz = ความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน จากที่ตามหลังอยู่ z บล็อก https://i.imgur.com/vePe255.png จากสมมติฐานที่ว่า p > q ความน่าจะเป็นจะลดลงแบบเอกซ์โพเนนเชียล เมื่อจำนวนบล็อกที่ผู้โจมตีต้องไล่ตามทันเพิ่มขึ้น หากเขาไม่สามารถพุ่งขึ้นนำได้อย่างรวดเร็วตั้งแต่แรก โอกาสของเขาก็จะลดลงจนน้อยมาก ๆ เมื่อเขาตามหลังมากขึ้นเรื่อย ๆ ทีนี้ลองพิจารณาว่า ผู้รับธุรกรรมใหม่ต้องรอเป็นเวลานานเท่าใด จึงจะแน่ใจได้ว่าผู้ส่งไม่สามารถเปลี่ยนแปลงธุรกรรมได้แล้ว เราสมมติว่าผู้ส่งเป็นผู้โจมตี ที่ต้องการให้ผู้รับเชื่อว่าเขาได้รับเงินไปแล้ว จากนั้นจึงเปลี่ยนให้เงินกลับเข้าหาตัวเองหลังจากเวลาผ่านไประยะหนึ่ง ผู้รับจะได้รับแจ้งเมื่อเกิดเหตุการณ์นี้ขึ้น แต่ผู้ส่งหวังว่ามันจะสายเกินไปแล้ว ผู้รับจะสร้างคู่กุญแจใหม่ และให้กุญแจสาธารณะแก่ผู้ส่งไม่นานก่อนที่จะลงนาม ซึ่งจะป้องกันไม่ให้ผู้ส่งเตรียมบล็อกเชนปลอมไว้ล่วงหน้า โดยการทำงานอย่างต่อเนื่องจนกว่าเขาจะมีโอกาสได้บล็อกที่ยาวพอ จากนั้นจึงดำเนินธุรกรรมในทันที เมื่อส่งธุรกรรมแล้ว ผู้ส่งที่ไม่สุจริตจะเริ่มทำงานอย่างลับ ๆ บนบล็อกเชนคู่ขนาน ที่มีธุรกรรมในเวอร์ชันของเขาเองอยู่ ผู้รับจะรอจนกว่าธุรกรรมจะถูกเพิ่มลงในบล็อก และมีบล็อกที่ถูกเชื่อมต่อตามหลังมาอีก z บล็อก เขาไม่ทราบจำนวนความคืบหน้าที่แน่นอนที่ผู้โจมตีได้ทำไปแล้ว แต่สมมติว่าบล็อกที่สุจริตใช้เวลาเฉลี่ยต่อบล็อกตามที่คาดไว้ ความคืบหน้าที่อาจเกิดขึ้นได้ของผู้โจมตีจะเป็นการแจกแจงแบบปัวซง (Poisson distribution) ซึ่งมีค่าคาดหวังดังนี้: https://i.imgur.com/mYsb48i.png เพื่อให้ได้ความน่าจะเป็นที่ผู้โจมตียังคงสามารถไล่ทันได้ เราจะคูณความหนาแน่นของปัวซง สำหรับความคืบหน้าแต่ละระดับที่เขาสามารถทำได้ ด้วยความน่าจะเป็นที่เขาสามารถไล่ทันจากจุดนั้น: https://i.imgur.com/jQGkQ8r.png จัดเรียงใหม่เพื่อหลีกเลี่ยง infinite tail ของการแจกแจง https://i.imgur.com/OOO6Gm9.png แปลงมันให้เป็น C code #include <math.h> double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; } เมื่อรันผลลัพธ์บางส่วน เราจะเห็นว่าความน่าจะเป็นลดลงแบบเอกซ์โพเนนเชียลเมื่อ z เพิ่มขึ้น q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012 q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006 การแก้หาค่า P ที่น้อยกว่า 0.1%... P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340 12.สรุป(Conclusion) เราได้นำเสนอระบบธุรกรรมอิเล็กทรอนิกส์ที่ไม่ต้องพึ่งพาความไว้วางใจ เริ่มต้นจากกรอบแนวคิดของเหรียญที่สร้างจากลายเซ็นดิจิทัล ซึ่งช่วยควบคุมความเป็นเจ้าของได้อย่างดีแต่ก็ยังไม่สมบูรณ์ หากปราศจากวิธีการป้องกันการใช้จ่ายซ้ำซ้อน เพื่อแก้ปัญหานี้ เราจึงเสนอเครือข่ายแบบเพียร์ทูเพียร์ที่ใช้ proof-of-work ในการบันทึกประวัติธุรกรรมสาธารณะ ซึ่งจะกลายเป็นเรื่องยากอย่างมากสำหรับผู้โจมตีที่จะเปลี่ยนแปลง หาก node ที่ซื่อสัตย์ควบคุมพลังประมวลผล CPU ส่วนใหญ่ เครือข่ายนี้มีความแข็งแกร่งในความเรียบง่ายที่ไม่มีโครงสร้างใด ๆ ที่ซับซ้อน node ต่าง ๆ ทำงานพร้อมกันโดยประสานงานกันเพียงเล็กน้อย ไม่จำเป็นต้องระบุตัวตน เนื่องจากข้อความไม่ได้ถูกส่งไปยังสถานที่ใดสถานที่หนึ่งโดยเฉพาะ และเพียงแค่ต้องส่งมอบให้ถึงมือผู้รับอย่างดีที่สุด node สามารถออกจากและเข้าร่วมเครือข่ายได้ตามต้องการ โดยยอมรับ chain ที่มี proof-of-work มากที่สุดเป็นสิ่งที่เกิดขึ้นในขณะที่ไม่ได้เชื่อมต่อ พวกเขาโหวตด้วยพลังประมวลผล CPU แสดงการยอมรับบล็อกที่ถูกต้องโดยการทำงานเพื่อขยายบล็อก และปฏิเสธบล็อกที่ไม่ถูกต้องโดยการปฏิเสธที่จะทำงานกับบล็อกเหล่านั้น กฎและแรงจูงใจใด ๆ ที่จำเป็นสามารถบังคับใช้ได้ด้วยกลไกฉันทามตินี้ ไปอ่านต่อกันเองเด้ออ --- [1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [6] A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [8] W. Feller, "An introduction to probability theory and its applications," 1957. @ 79008e78:dfac9395
2024-09-02 06:17:05Nostr: โปรโตคอลทางเลือกใหม่สำหรับโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม --- Nostr คือโปรโตคอลแบบเปิดที่เรียบง่าย ซึ่งช่วยให้สามารถสร้างโซเชียลมีเดียระดับโลกที่กระจายอำนาจและป้องกันการเซ็นเซอร์ได้ จากที่กล่าวข้างต้น เราสามารถพูดได้ว่า Nostr นั้นถูกออกแบบมาให้ใช้งานง่าย โดยมีเป้าหมายหลัก ๆ เพื่อสร้างเครือข่ายโซเชียลระดับโลกที่ปราศจากการเซ็นเซอร์ แล้วทำไมมันถึงทำอย่างนั้นได้? ในจุดนี้เราก็ต้องมาเจาะดูคุณสมบัติหลัก ๆ ของโปรโตคอลที่เรียกว่า Nostr กันก่อน: **เรียบง่าย** - โปรโตคอลนี้ใช้โครงสร้างข้อมูลแบบ Event Object ที่เรียบง่ายและยืดหยุ่น (ซึ่งส่งเป็น JSON ธรรมดา) และใช้การเข้ารหัสแบบ Elliptic-curve มาตรฐานสำหรับคีย์และลายเซ็น - ช่องทางการสื่อสารที่รองรับเพียงอย่างเดียวคือการเชื่อมต่อ WebSockets จากไคลเอนต์ไปยังรีเลย์ - การออกแบบนี้ทำให้ง่ายต่อการพัฒนาไม่ว่าจะไคลเอนต์หรือรีเลย์ และยังช่วยส่งเสริมความหลากหลายของซอฟต์แวร์ **ยืดหยุ่น** - เนื่องจาก Nostr ไม่ได้พึ่งพาเซิร์ฟเวอร์ที่เชื่อถือได้เพียงจำนวนหยิบมือ สำหรับการเคลื่อนย้ายหรือจัดเก็บข้อมูล แต่ใช้เซิร์ฟเวอร์จำนวนมหาศาลและกระจายตัวอยู่ทั่วโลก จึงมีความยืดหยุ่นสูง และมีการกระจายศูนย์อย่างแท้จริง - โปรโตคอลนี้ถูกออกแบบมาโดยคำนึงถึงความเป็นไปได้ที่รีเลย์จะหายไป และอนุญาตให้ผู้ใช้เชื่อมต่อและเผยแพร่ข้อมูลไปยังรีเลย์จำนวนมากได้ตามต้องการ และยังสามารถเปลี่ยนแปลงได้ตลอดเวลาอีกด้วย **ตรวจสอบได้** - เนื่องจากบัญชี Nostr ใช้การเข้ารหัสแบบ PKE จึงง่ายต่อการตรวจสอบว่าข้อความถูกส่งมาจากผู้ใช้ที่ระบุจริงหรือไม่ เช่นเดียวกับ HTTP หรือ TCP-IP Nostr เป็นโปรโตคอลหรือมาตรฐานแบบเปิดที่ทุกคนสามารถนำไปสร้างต่อยอดได้ มันไม่ใช่แอปหรือบริการที่คุณจำเป็นต้องลงทะเบียน แล้วทำไมเราถึงต้องการ Nostr? --- ถึงในปัจจุบันโซเชียลมีเดียจะได้พัฒนามาเป็นช่องทางสำคัญในการไหลเวียนของข้อมูลทั่วโลก กลายเป็นช่องทางหลักในการติดต่อสื่อสาร แต่น่าเสียดายที่ระบบโซเชียลมีเดียในปัจจุบันของเรานั้นมีข้อบกพร่องมากมาย: 1. ใช้ความสนใจของคุณเพื่อขายโฆษณา 2. ใช้เทคนิคแปลกๆ เพื่อทำให้คุณเสพติด (อ้างอิงจากข้อ 1) 3. ตัดสินใจว่าจะแสดงเนื้อหาใดให้คุณเห็นโดยใช้อัลกอริทึมลับที่คุณไม่สามารถตรวจสอบหรือเปลี่ยนแปลงได้ 4. ควบคุมอย่างเต็มที่ว่าใครสามารถเข้าร่วมและใครถูกเซ็นเซอร์ 5. เต็มไปด้วยสแปมและบอท ด้วยข้อจำกัดเหล่านี้ Nostr จึงเป็นทางเลือกที่น่าสนใจในการสร้างโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม องค์ประกอบของโปรโตคอลที่ชื่อว่า Nostr --- หลังจากได้ทำความรู้จัก Nostr กันไปแล้วเมื่อคราวก่อน คราวนี้เรามาเจาะดูองค์ประกอบของโปรโตคอลนี้กันดีกว่า **Keys ระบบบัญชีผู้ใช้และรหัสผ่านสำหรับ Nostr** - บัญชี Nostr แต่ละบัญชีจะใช้คู่กุญแจสาธารณะ/ส่วนตัว (Public/Private Key ) เปรียบเทียบง่าย ๆ คือ กุญแจสาธารณะของคุณคือชื่อผู้ใช้ และกุญแจส่วนตัวก็เป็นรหัสผ่าน แต่ว่า ก็มีข้อแตกต่างที่สำคัญอยู่ นั่นคือ กุญแจส่วนตัวของคุณนั้นจะไม่สามารถรีเซ็ตได้หากเกิดการสูญหายขึ้น คุณจะเสียบัญชีนั้นไปตลอดกาล - โดยทั่วไปแล้ว กุญแจสาธารณะจะแสดงเป็นข้อความที่ขึ้นต้นด้วย npub1 และกุญแจส่วนตัวจะขึ้นต้นด้วย nsec1 - ทั้งนี้คุณควรที่จะตรวจสอบให้แน่ใจว่าคุณได้เก็บกุญแจส่วนตัวของคุณไว้ในที่ปลอดภัย เช่น โปรแกรมจัดการรหัสผ่านอย่างเช่น Bitwarden **โปรโตคอลกับไคลเอนต์ ต่างกันอย่างไร?** Nostr เองเป็นเพียงโปรโตคอล หมายความว่า Nostr นั้นเป็นเพียงกระบวนการที่ตกลงกันไว้สำหรับการส่งข้อความผ่านอินเทอร์เน็ต (เหมือนข้อกำหนด) ซึ่งการที่คุณจะเข้าถึง Nostr (โปรโตคอล) นั้น ผู้ใช้ส่วนใหญ่จะใช้งานผ่านไคลเอนต์ ซึ่งตัวของไคลเอนต์นั้นอาจเป็นเว็บ แอปพลิเคชันเดสก์ท็อป หรือ แอปพลิเคชันมือถือ โดยไคลเอนต์สามารถดึงข้อมูลจากรีเลย์ และสร้างข้อมูลใหม่ และส่งข้อมูลนั้นไปยังรีเลย์เพื่อให้ผู้ใช้คนอื่น ๆ สามารถเรียกอ่าน ข้อมูลนั้น ๆ ได้ โดย "ข้อมูล" เพียงรูปแบบเดียวที่มีอยู่ใน Nostr คือสิ่งที่เราเรียกกันว่า event **การพิสูจน์ความเป็นเจ้าของข้อมูลบน Nostr** บน Nostr นั้นการพิสูจน์ตัวตนเป็นเรื่องที่ง่ายมากเนื่องจากทุก ๆ event ที่เกิดขึ้น **จำเป็น**ต้องมีลายเซ็นดิจิทัล (Digital Signature) โดยลายเซ็นนั้นจะช่วยให้มั่นใจได้ว่า ใครเป็นผู้สร้าง event นั้น ๆ ขึ้นมา โดยการพิสูจน์ทางคณิตศาสตร์ โดยในการสร้างลายเซ็นแต่ละครั้ง ไคลเอนต์จะจำเป็นต้องใช้กุญแจส่วนตัวของคุณ โดยทั่วไปแล้ว แอปพลิเคชันเจะมีที่ให้คุณใส่กุญแจส่วนตัวของคุณ เมื่อเปิดแอปพลิเคชันครั้งแรก พวกเขาสามารถคำนวณกุญแจสาธารณะของคุณได้จากกุญแจส่วนตัวเช่นกัน ส่วนในกรณีที่คุณใช้งานผ่านเว็บแอป ผมไม่แนะนำให้ใส่กุญแจส่วนตัวลงไป แต่แนะนำให้ใช้ส่วนขยายของเบราว์เซอร์ ที่ใช้งานฟังก์ชันที่เกี่ยวข้องกับ Nostr ซึ่งอนุญาตให้เว็บไคลเอ็นต์ส่ง event ที่ยังไม่ถูกเซ็นมาให้ส่วนขยายและส่วนขยายจะทำหน้าที่เซ็น สำหรับวิธีนี้ เว็บไคลเอ็นต์ต่าง ๆ ไม่จำเป็นต้องรู้กุญแจส่วนตัวของคุณ แต่คุณก็ยังสามารถลงนามใน event ต่าง ๆ ได้ตามปกติ โดยส่วนขยายที่ได้รับความนิยมก็จะเป็น **Flamingo**, **Alby** และ **nos2x** ไคลเอนต์ & รีเลย์ ----------- **ไคลเอนต์คืออะไร?** หากจะอธิบายให้เห็นภาพอยากให้มองว่าไคลเอ็นต์ Nostr นั้นเป็นเหมือนกับแอปที่คุณใช้งานเพื่อเข้าถึง Twitter, Facebook, youtube เป็นต้น พวกมันคือ แอปพลิเคชัน, เว็บแอป ที่เชื่อมต่อคุณกับโลกของ Twitter, Facebook, youtube โดยตัวของไคลเอนต์ใน Nostr เองก็เปรียบเสมือนแอปต่าง ๆ ที่คุณใช้ดูหน้าฟีดนั่นเอง แต่ข้อดีของ Nostr ที่เหนือแอปพลิเคชันอื่น ๆ คือความเรียบง่ายและยืดหยุ่น ส่งผลให้ไคลเอ็นต์แต่ละตัวมีวิธีนำเสนอและใช้งานที่แตกต่างกันไป บางไคลเอ็นต์อาจออกแบบให้ใช้งานง่ายเหมือน Twitter บางตัวเน้นให้เห็นบทบาทสำคัญของรีเลย์ หรือโหนดที่กระจายข้อมูลอยู่ทั่วโลก บางตัวใช้ระบบอัลกอริทึมเพื่อให้แน่ใจว่าข้อมูลไม่ถูกปิดกั้น โดยไม่ทำให้ผู้ใช้งานรู้สึกยุ่งยาก **เรียบง่ายและยืดหยุ่น?** เนื่องจากการออกแบบของโปรโตคอลที่ทำการแยกข้อมูลของผู้ใช้ทั้งหมดออกจากไคลเอนต์ ทำให้ตัวของผู้ใช้งานเองนั้นมีอิสระเต็มที่ที่จะเลือกใช้ไคลเอนต์ต่าง ๆ เพื่อเข้าใช้งาน Nostr และแน่นอนว่า ผู้ใช้งานสามารถสลับหรือลงชื่อเข้าใช้ ไคลเอ็นต์ได้หลายตัวตามต้องการ ตราบใดที่ไคลเอ็นต์ทั้งหมดเชื่อมต่อกับชุดรีเลย์เดียวกัน คุณก็จะเห็นข้อมูลเดียวกันในทุก ๆ ไคลเอ็นต์ **ลงชื่อเข้าใช้ ไคลเอ็นต์หลาย ๆ ตัวแล้วจะกระทบต่อความปลอดภัยของแอคเคาร์ไหม?** คำตอบของคำถามนี้นั้นขึ้นอยู่กับวิธีการที่คุณลงชื่อเข้าใช้ หากคุณลงชื่อเข้าใช้ด้วยกุญแจส่วนตัว ถึงแม้ว่าไคลเอ็นต์ส่วนใหญ่จะพยายามรักษาความปลอดภัยของกุญแจส่วนตัวอย่างดีที่สุด แต่ด้วยข้อจำกัดของซอฟต์แวร์ ย่อมมีความเสี่ยงที่จะเกิดช่องโหว่ การเจาะระบบ และข้อผิดพลาด ที่อาจทำให้กุญแจส่วนตัวของคุณรั่วไหลออกไปได้ ส่วนวิธีการป้องกันเกี่ยวกับเรื่องนี้คือการใช้ส่วนขยายของเว็บเบราว์เซอร์ เพราะการเข้าสู่ระบบในไคลเอนต์ต่าง ๆ ผ่านส่วนขยายนั้นจะใช้เพียงกุญแจสาธารณะในการเข้าสู่ระบบและทุกครั้งที่เราต้องการจะโพสต์หรือสร้าง event บน Nostr ไคลเอนต์จะทำการร่าง event นั้น ๆ และเว้นช่องของลายเซ็นเอาไว้จากนั้นเราจะต้องทำการเซ็นผ่านส่วนขยาย ด้วยวิธีนี้ทำให้กุญแจส่วนตัวของเราไม่หลุดออกไปไหนตลอดการใช้งาน **รีเลย์คืออะไร?** รีเลย์เปรียบเสมือนเซิร์ฟเวอร์ที่อยู่เบื้องหลังของ Nostr และทำหน้าที่รับ event ต่าง ๆ มาจากไคลเอนต์ Nostr และอาจจะจัดเก็บและกระจายข้อความเหล่านั้นไปยังไคลเอนต์อื่น ๆ ที่มีการเชื่อมต่ออยู่ เทคโนโลยีของรีเลย์นั้นเปลี่ยนแปลงอย่างรวดเร็ว ดังนั้นคาดว่าจะมีการเปลี่ยนแปลงอีกมากมายในอนาคต อย่างในปัจจุบันที่มีการนำเสนอ bostr หรือ รีเลย์ที่จะคอยส่ง event ของเราต่อให้กับรีเลย์อื่น ๆ ที่มีการเชื่อมต่อ เพื่อช่วยลดภาระของไคลเอนต์ในการรับส่งข้อมูลจากหลาย ๆ รีเลย์พร้อม ๆ กัน หรืออย่างการป้องกันสแปมด้วย POW หรือประเภทที่สามารถเก็บรูปหรือวิดีโอที่มีขนาดใหญ่ได้ แต่สิ่งหนึ่งที่ควรทราบก็คือ การที่ Nostr นั้นพยายามจะกระจายศูนย์และเหตุผลหลัก ๆ ที่สามารถทำแบบนั้นได้ก็ขึ้นอยู่กับรีเลย์ในการจัดเก็บและดึงข้อมูล ดังนั้น หากคุณรู้สึกว่าไคลเอนต์ Nostr ของคุณทำงานช้า ส่วนใหญ่ก็มักเกิดจากรีเลย์ที่คุณกำลังเชื่อมต่ออยู่ คุณอาจลองแก้ไขปัญญาโดยการเปลี่ยนหรือเพิ่มรีเลย์อีกสองสามรายการในไคลเอนต์ที่คุณใช้ **แล้วจะสามารถหารายการรีเลย์ได้จากไหน?** การที่เราจะหารายการรีเลย์ที่เราควรเชื่อมต่อนั้น ๆ จริงแล้ว ๆ สามารถทำได้หลายวิธี แต่วิธีที่ผมแนะนำที่สุดจะเป็นการใช้ตามคนที่เราติดตามอยู่ เพราะจะเป็นวิธีที่เราสามารถเห็น event ต่าง ๆ ของคนที่เราติดตามได้ง่ายที่สุด และเช่นเดียวกัน เพื่อน ๆ หรือคนที่เราติดตามก็จะสามารถเห็น event ของเราได้เช่นกัน และสำหรับในประเทศไทย เรามีรีเลย์ที่คนไทยส่วนใหญ่นิยมใช้กันอยู่สองอัน นั้นคือ wss://relay.siamstr.com/ และ wss://relay.notoshi.win/ ถ้าหากว่าอยากเห็นคนไทยเยอะ ๆ บนหน้าไทม์ไลน์ ผมแนะนำเป็นอย่างยิ่งว่าควรเพิ่ม รายการรีเลย์เหล่านี้ลงไปในบัชญีหรือไคลเอนต์ต่าง ๆ ที่คุณใช้ด้วย สำหรับอีกวิธีหนึ่งผมแนะนำให้เข้าไปในเว็บไซต์ nostr.watch เนื่องจากในเว็บไซต์นี้เป็นแหล่งข้อมูลที่ดีที่สุดสำหรับการค้นหาและประเมินความเร็วของรีเลย์ต่าง ๆ **จะเกิดอะไรขึ้นถ้ารีเลย์ทั้งหมดที่ฉันเชื่อมต่ออยู่หยุดให้บริการ?** สิ่งนี้เป็นสิ่งที่คุณต้องระวังมากที่สุดในการใช้งาน nostr เนื่องจากหากรีเลย์ทั้งหมดที่คุณเก็บข้อมูลไว้หยุดให้บริการทั้งหมดและคุณไม่มีการสำรองข้อมูล event ของคุณเก็บไว้เลย มันแปลว่าโพสต์ทั้งหมดของคุณ ผู้ติดตาม และรายการต่าง ๆ ที่คุณสรรค์สร้างไว้จะไม่สามารถกู้คืนได้ไปตลอดการ นี่จึงเป็นเหตุผลหลัก ๆ ที่ Nostr อนุญาตให้ผู้ใช้งานนั้นสามารถเชื่อมต่อกับรีเลย์ได้เป็นจำนวนมาก ก็เพื่อให้แน่ใจว่ามีข้อมูลสำรองเก็บไว้อยู่ที่ใดที่หนึ่งในระบบเสมอ แต่อย่างไรก็ตาม หากคุณต้องการที่จะมั่นใจได้ว่าข้อมูลต่าง ๆ ของคุณจะไม่ถูกเซ็นเซอร์ สิ่งที่คุณสามารถสามารถทำได้คือการใช้รีเลย์ส่วนตัวของคุณและกำหนดนโยบายต่าง ๆ ภายในรีเลย์ของคุณด้วยตัวคุณเอง **แล้วฉันจะสามารถใช้รีเลย์ส่วนตัวได้อย่างไร?** **อะแฮ่ม ๆ** ขอบอกไว้ก่อนว่ามันไม่คุ้มค่ากับความยุ่งยากสำหรับคนโดยทั่ว ๆ ไป ถึงในปัจจุบันจะมีเทคโนโลยีบางตัวที่เข้ามาช่วยให้มันทำได้ง่ายขึ้นแล้วก็ตาม หากคุณต้องการที่จะสำรองข้อมูลนั้น การที่จะมีรีเลย์ส่วนตัวที่ออนไลน์ตลอดเวลาอาจเป็นเรื่องที่ไม่ได้จำเป็นขนาดนั้น เนื่องจากเราสามารถใช้งานบริการอย่าง https://nostrsync.live/ ในการดาวน์โหลดข้อมูลของเราจากรีเลย์ต่าง ๆ ได้ หรือการติดตั้งรีเลย์ส่วนตัวอย่าง nostr-relay-tray: https://github.com/CodyTseng/nostr-relay-tray ที่ช่วยให้เราสามารถมีรีเลย์ส่วนตัวที่ใช้สำหรับสำรองข้อมูลได้ Nostr Implementation Possibilities (NIPs) NIP คืออะไร? --- NIP มีไว้เพื่อส่งเสริมความสามารถในการทำงานของ Nostr และเป็นตัวคอยกำหนดให้ เหล่านักพัฒนาทำสิ่งต่าง ๆ ที่เหมือนกันในรูปแบบเดียวกัน เพราะมันคงไม่ใช่ความคิดที่ดีนัก หากนักพัฒนาแต่ละคนจะคิดค้นวิธีแก้ปัญหาทั่วไปของตัวเองและนำไปใช้ในแอปของตัวเองเท่านั้น และคงจะเป็นการดีกว่า ถ้าหากทุกคนใช้วิธีแก้ปัญหาที่เหมือนกัน นั่นคือเหตุผลที่ต้องมี NIP อยู่ในโปรโตคอลของ Nostr และในทำนองเดียวกัน แนวคิดใหม่อาจดูดีในแอปของนักพัฒนาบางราย แต่จะดูดียิ่งขึ้นอย่างแน่นอนหากแอปอื่น ๆ อีกมากมายใช้มาตรฐานเดียวกันและสามารถทำงานร่วมกันได้อย่างราบรื่น **ทำไมมันถึงหน้าสนใจ?** อย่าลืมว่า Nostr เป็นระบบแบบกระจายอำนาจและไม่ได้มีบริษัทหรือใครที่เป็นเจ้าของมัน อย่างเช่นโซเชียลมีเดียอื่น ๆ เช่น ทวิตเตอร์ อ่อไม่สิตอนนี้คงต้องเรียกมันว่า X สินะ ซึ่งหมายความว่าทิศทางของโพรโทคอล Nostr นั้นขึ้นอยู่กับพวกเราทุกคน! ไม่ว่าใคร ๆ ก็สามารถเสนอแนะและสนับสนุนการเปลี่ยนแปลงและให้ข้อเสนอแนะเกี่ยวกับแนวคิดที่ผู้อื่นเสนอ และการที่คุณเป็นส่วนหนึ่งของชุมชนนี้ ก็ทำให้คุณมีส่วนร่วมในทิศทางของ Nostr อีกด้วย จากที่ส่งหากันได้แค่ข้อความ มาเป็นรูปภาพ มาเป็นวิดีโอ และมาเป็น”เงิน” นี่คือเส้นทางการเดินทางของโปรโตคอลนี้ในอดีต แล้วในอนาคตมันจะพัฒนาไปยังไงต่อก็ขึ้นอยู่กับเหล่าผู้ใช้งานและนักพัฒนาในอนาคต แล้วทำไมสิ่งนี้ถึงจะไม่น่าสนใจละ ? Event --- **Event คืออะไร?** Event เป็น object เพียงประเภทเดียวที่มีอยู่บน Nostr โดยมีโครงสร้างประมาณนี้ ``` {"id":"84d5d3dc9c388a702f39cad6360d41ebb804e809fb822f110ff8a14dfd35fc6c", "pubkey":"66df60562d939ada8612436489945a4ecf1d62346b3d9478dea8a338f3203c64", "created_at":1722315959, "kind":1, "tags":[["t","siamstr"]], "content":"ไปสั่งกาแฟเมื่อกี้ พส เจ้าของร้านชมว่าเดี๋ยวนี้คล่องภาษาญี่ปุ่นแล้วนะ ไอเราก็ดีใจ พอเดินกลับถึงที่ทำงานละก็ตระหนักได้ว่า ตะกี้เราสั่ง “ไอซ์โคฮี โอเนไงชิมัส” “เทคเอาส์” “คาโดะเดสส” ไอบ้าไหนญี่ปุ่นก่อนอังกฤษทั้งนั้น 🤣🤣\n\n#siamstr", "sig":"8f066a0099a5f580b605ebdb220179c4eca298947c38b855a0a8bf2783f28ddb537cb74a7f61d3ce8891189f719870efdf320ea4f895e03cdac44284c450c5c4"} ``` อย่าง Event ข้างต้นนี้มี kind เป็น 1 ซึ่งหมายถึง "ข้อความโน้ต" ซึ่งก็คือข้อความธรรมดา สั้น ๆ คล้ายกับที่ใช้กันใน Twitter เช่น บนฟีด การตอบกลับ และการโควท **ประเภทของ Event (Event Kinds)** หมายเลขของ kind แต่ละตัวมีความหมายแตกต่างกัน ตัวอย่างเช่น 0 หมายถึงอีเวนต์ "ข้อมูลเมตา" ใช้สำหรับให้รายละเอียดเกี่ยวกับผู้ใช้ เช่น ชื่อและรูปโปรไฟล์ รีเลย์ (Relays) สามารถจัดการกับ kind ที่แตกต่างกันได้ เช่น รีเลย์มักจะลบอีเวนต์ kind:0 เวอร์ชันเก่ากว่าออกไป และเก็บไว้เฉพาะเวอร์ชันล่าสุด ในขณะที่โดยทั่วไปจะเก็บอีเวนต์ kind:1 ไว้หลายรายการสำหรับแต่ละคีย์ โดยทั่วไปแล้ว คุณไม่จำเป็นต้องใช้ kind เกินกว่า 0 และ 1 ในการสร้างแอปพลิเคชันโซเชียลมีเดียบน Nostr แต่ kind อื่น ๆ ถูกคิดค้นขึ้นโดยไคลเอนต์ เพื่อมอบฟังก์ชันการทำงานอื่น ๆ ตามที่ระบุไว้ใน NIP บาง kind ไม่เกี่ยวข้องกับเครือข่าย และให้บริการตามความต้องการอื่น ๆ ของไคลเอนต์ที่เฉพาะเจาะจงกับฟังก์ชันการทำงานเหล่านั้น ซึ่งแนวคิดก็คือ สำหรับกรณีการใช้งานใหม่ ๆ แต่ละกรณี จะต้องมีการพิจารณาและเสนอซับโปรโตคอลเป็น NIP เพื่อให้สามารถทำงานร่วมกับไคลเอนต์ที่มีอยู่และในอนาคต ซึ่งอาจสนใจที่จะนำฟังก์ชันการทำงานนั้นไปใช้ ขณะเดียวกันก็มั่นใจได้ถึงความเข้ากันได้ย้อนหลัง และการรองรับสิ่งต่าง ๆ ที่มีอยู่และไม่ต้องการเปลี่ยนแปลง **คุณสมบัติอื่น ๆ ของ Event** created_at: เป็น Timestamp ของ UNIX ที่กำหนดโดยผู้สร้างอีเวนต์ โดยปกติจะเป็นเวลาที่สร้าง แม้ว่าจะไม่มีการตรวจสอบ แต่ก็ไม่ใช่ปัญหา content: ขึ้นอยู่กับความหมายของ kind ในกรณีของ kind:1 จะเป็นเพียงสตริงข้อความธรรมดาที่คนอื่น ๆ อ่านได้ tags: ขึ้นอยู่กับ kind เช่นกัน แต่แท็กทั่วไปบางอย่างที่มักปรากฏใน event kind:1 และ kind อื่น ๆ คือ "p" ซึ่งใช้เพื่อกล่าวถึงกุญแจสาธารณะ และ "e" ใช้เพื่ออ้างถึง event อื่น อยากมีส่วนร่วมในการพัฒนาของ Nostr ? --- จริง ๆ แล้วใคร ๆ ก็สามารถเข้ามามีส่วนร่วมในการพัฒนา Nostr ได้ ไม่จำเป็นต้องเป็น dev หรือมีความรู้ด้านคอมพิวเตอร์ก็สามารถทำได้ ไม่ว่าจะเป็นการให้ feedback กับ dev ของ client ที่คุณใช้, การสร้างคอนเทนต์ต่าง ๆ บน Nostr การสร้างชุมชน รวมไปถึงการช่วย client ต่าง ๆ ในการทำ UI ให้เป็นภาษาท้องถิ่น และอื่น ๆ อีกมากมาย ใคร ๆ ก็สามารถช่วยได้ตามความสามารถที่แต่ละคนมี มันเลยทำให้ Nostr โครตน่าอยู่ :)
@ 79008e78:dfac9395
2024-09-02 06:17:05Nostr: โปรโตคอลทางเลือกใหม่สำหรับโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม --- Nostr คือโปรโตคอลแบบเปิดที่เรียบง่าย ซึ่งช่วยให้สามารถสร้างโซเชียลมีเดียระดับโลกที่กระจายอำนาจและป้องกันการเซ็นเซอร์ได้ จากที่กล่าวข้างต้น เราสามารถพูดได้ว่า Nostr นั้นถูกออกแบบมาให้ใช้งานง่าย โดยมีเป้าหมายหลัก ๆ เพื่อสร้างเครือข่ายโซเชียลระดับโลกที่ปราศจากการเซ็นเซอร์ แล้วทำไมมันถึงทำอย่างนั้นได้? ในจุดนี้เราก็ต้องมาเจาะดูคุณสมบัติหลัก ๆ ของโปรโตคอลที่เรียกว่า Nostr กันก่อน: **เรียบง่าย** - โปรโตคอลนี้ใช้โครงสร้างข้อมูลแบบ Event Object ที่เรียบง่ายและยืดหยุ่น (ซึ่งส่งเป็น JSON ธรรมดา) และใช้การเข้ารหัสแบบ Elliptic-curve มาตรฐานสำหรับคีย์และลายเซ็น - ช่องทางการสื่อสารที่รองรับเพียงอย่างเดียวคือการเชื่อมต่อ WebSockets จากไคลเอนต์ไปยังรีเลย์ - การออกแบบนี้ทำให้ง่ายต่อการพัฒนาไม่ว่าจะไคลเอนต์หรือรีเลย์ และยังช่วยส่งเสริมความหลากหลายของซอฟต์แวร์ **ยืดหยุ่น** - เนื่องจาก Nostr ไม่ได้พึ่งพาเซิร์ฟเวอร์ที่เชื่อถือได้เพียงจำนวนหยิบมือ สำหรับการเคลื่อนย้ายหรือจัดเก็บข้อมูล แต่ใช้เซิร์ฟเวอร์จำนวนมหาศาลและกระจายตัวอยู่ทั่วโลก จึงมีความยืดหยุ่นสูง และมีการกระจายศูนย์อย่างแท้จริง - โปรโตคอลนี้ถูกออกแบบมาโดยคำนึงถึงความเป็นไปได้ที่รีเลย์จะหายไป และอนุญาตให้ผู้ใช้เชื่อมต่อและเผยแพร่ข้อมูลไปยังรีเลย์จำนวนมากได้ตามต้องการ และยังสามารถเปลี่ยนแปลงได้ตลอดเวลาอีกด้วย **ตรวจสอบได้** - เนื่องจากบัญชี Nostr ใช้การเข้ารหัสแบบ PKE จึงง่ายต่อการตรวจสอบว่าข้อความถูกส่งมาจากผู้ใช้ที่ระบุจริงหรือไม่ เช่นเดียวกับ HTTP หรือ TCP-IP Nostr เป็นโปรโตคอลหรือมาตรฐานแบบเปิดที่ทุกคนสามารถนำไปสร้างต่อยอดได้ มันไม่ใช่แอปหรือบริการที่คุณจำเป็นต้องลงทะเบียน แล้วทำไมเราถึงต้องการ Nostr? --- ถึงในปัจจุบันโซเชียลมีเดียจะได้พัฒนามาเป็นช่องทางสำคัญในการไหลเวียนของข้อมูลทั่วโลก กลายเป็นช่องทางหลักในการติดต่อสื่อสาร แต่น่าเสียดายที่ระบบโซเชียลมีเดียในปัจจุบันของเรานั้นมีข้อบกพร่องมากมาย: 1. ใช้ความสนใจของคุณเพื่อขายโฆษณา 2. ใช้เทคนิคแปลกๆ เพื่อทำให้คุณเสพติด (อ้างอิงจากข้อ 1) 3. ตัดสินใจว่าจะแสดงเนื้อหาใดให้คุณเห็นโดยใช้อัลกอริทึมลับที่คุณไม่สามารถตรวจสอบหรือเปลี่ยนแปลงได้ 4. ควบคุมอย่างเต็มที่ว่าใครสามารถเข้าร่วมและใครถูกเซ็นเซอร์ 5. เต็มไปด้วยสแปมและบอท ด้วยข้อจำกัดเหล่านี้ Nostr จึงเป็นทางเลือกที่น่าสนใจในการสร้างโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม องค์ประกอบของโปรโตคอลที่ชื่อว่า Nostr --- หลังจากได้ทำความรู้จัก Nostr กันไปแล้วเมื่อคราวก่อน คราวนี้เรามาเจาะดูองค์ประกอบของโปรโตคอลนี้กันดีกว่า **Keys ระบบบัญชีผู้ใช้และรหัสผ่านสำหรับ Nostr** - บัญชี Nostr แต่ละบัญชีจะใช้คู่กุญแจสาธารณะ/ส่วนตัว (Public/Private Key ) เปรียบเทียบง่าย ๆ คือ กุญแจสาธารณะของคุณคือชื่อผู้ใช้ และกุญแจส่วนตัวก็เป็นรหัสผ่าน แต่ว่า ก็มีข้อแตกต่างที่สำคัญอยู่ นั่นคือ กุญแจส่วนตัวของคุณนั้นจะไม่สามารถรีเซ็ตได้หากเกิดการสูญหายขึ้น คุณจะเสียบัญชีนั้นไปตลอดกาล - โดยทั่วไปแล้ว กุญแจสาธารณะจะแสดงเป็นข้อความที่ขึ้นต้นด้วย npub1 และกุญแจส่วนตัวจะขึ้นต้นด้วย nsec1 - ทั้งนี้คุณควรที่จะตรวจสอบให้แน่ใจว่าคุณได้เก็บกุญแจส่วนตัวของคุณไว้ในที่ปลอดภัย เช่น โปรแกรมจัดการรหัสผ่านอย่างเช่น Bitwarden **โปรโตคอลกับไคลเอนต์ ต่างกันอย่างไร?** Nostr เองเป็นเพียงโปรโตคอล หมายความว่า Nostr นั้นเป็นเพียงกระบวนการที่ตกลงกันไว้สำหรับการส่งข้อความผ่านอินเทอร์เน็ต (เหมือนข้อกำหนด) ซึ่งการที่คุณจะเข้าถึง Nostr (โปรโตคอล) นั้น ผู้ใช้ส่วนใหญ่จะใช้งานผ่านไคลเอนต์ ซึ่งตัวของไคลเอนต์นั้นอาจเป็นเว็บ แอปพลิเคชันเดสก์ท็อป หรือ แอปพลิเคชันมือถือ โดยไคลเอนต์สามารถดึงข้อมูลจากรีเลย์ และสร้างข้อมูลใหม่ และส่งข้อมูลนั้นไปยังรีเลย์เพื่อให้ผู้ใช้คนอื่น ๆ สามารถเรียกอ่าน ข้อมูลนั้น ๆ ได้ โดย "ข้อมูล" เพียงรูปแบบเดียวที่มีอยู่ใน Nostr คือสิ่งที่เราเรียกกันว่า event **การพิสูจน์ความเป็นเจ้าของข้อมูลบน Nostr** บน Nostr นั้นการพิสูจน์ตัวตนเป็นเรื่องที่ง่ายมากเนื่องจากทุก ๆ event ที่เกิดขึ้น **จำเป็น**ต้องมีลายเซ็นดิจิทัล (Digital Signature) โดยลายเซ็นนั้นจะช่วยให้มั่นใจได้ว่า ใครเป็นผู้สร้าง event นั้น ๆ ขึ้นมา โดยการพิสูจน์ทางคณิตศาสตร์ โดยในการสร้างลายเซ็นแต่ละครั้ง ไคลเอนต์จะจำเป็นต้องใช้กุญแจส่วนตัวของคุณ โดยทั่วไปแล้ว แอปพลิเคชันเจะมีที่ให้คุณใส่กุญแจส่วนตัวของคุณ เมื่อเปิดแอปพลิเคชันครั้งแรก พวกเขาสามารถคำนวณกุญแจสาธารณะของคุณได้จากกุญแจส่วนตัวเช่นกัน ส่วนในกรณีที่คุณใช้งานผ่านเว็บแอป ผมไม่แนะนำให้ใส่กุญแจส่วนตัวลงไป แต่แนะนำให้ใช้ส่วนขยายของเบราว์เซอร์ ที่ใช้งานฟังก์ชันที่เกี่ยวข้องกับ Nostr ซึ่งอนุญาตให้เว็บไคลเอ็นต์ส่ง event ที่ยังไม่ถูกเซ็นมาให้ส่วนขยายและส่วนขยายจะทำหน้าที่เซ็น สำหรับวิธีนี้ เว็บไคลเอ็นต์ต่าง ๆ ไม่จำเป็นต้องรู้กุญแจส่วนตัวของคุณ แต่คุณก็ยังสามารถลงนามใน event ต่าง ๆ ได้ตามปกติ โดยส่วนขยายที่ได้รับความนิยมก็จะเป็น **Flamingo**, **Alby** และ **nos2x** ไคลเอนต์ & รีเลย์ ----------- **ไคลเอนต์คืออะไร?** หากจะอธิบายให้เห็นภาพอยากให้มองว่าไคลเอ็นต์ Nostr นั้นเป็นเหมือนกับแอปที่คุณใช้งานเพื่อเข้าถึง Twitter, Facebook, youtube เป็นต้น พวกมันคือ แอปพลิเคชัน, เว็บแอป ที่เชื่อมต่อคุณกับโลกของ Twitter, Facebook, youtube โดยตัวของไคลเอนต์ใน Nostr เองก็เปรียบเสมือนแอปต่าง ๆ ที่คุณใช้ดูหน้าฟีดนั่นเอง แต่ข้อดีของ Nostr ที่เหนือแอปพลิเคชันอื่น ๆ คือความเรียบง่ายและยืดหยุ่น ส่งผลให้ไคลเอ็นต์แต่ละตัวมีวิธีนำเสนอและใช้งานที่แตกต่างกันไป บางไคลเอ็นต์อาจออกแบบให้ใช้งานง่ายเหมือน Twitter บางตัวเน้นให้เห็นบทบาทสำคัญของรีเลย์ หรือโหนดที่กระจายข้อมูลอยู่ทั่วโลก บางตัวใช้ระบบอัลกอริทึมเพื่อให้แน่ใจว่าข้อมูลไม่ถูกปิดกั้น โดยไม่ทำให้ผู้ใช้งานรู้สึกยุ่งยาก **เรียบง่ายและยืดหยุ่น?** เนื่องจากการออกแบบของโปรโตคอลที่ทำการแยกข้อมูลของผู้ใช้ทั้งหมดออกจากไคลเอนต์ ทำให้ตัวของผู้ใช้งานเองนั้นมีอิสระเต็มที่ที่จะเลือกใช้ไคลเอนต์ต่าง ๆ เพื่อเข้าใช้งาน Nostr และแน่นอนว่า ผู้ใช้งานสามารถสลับหรือลงชื่อเข้าใช้ ไคลเอ็นต์ได้หลายตัวตามต้องการ ตราบใดที่ไคลเอ็นต์ทั้งหมดเชื่อมต่อกับชุดรีเลย์เดียวกัน คุณก็จะเห็นข้อมูลเดียวกันในทุก ๆ ไคลเอ็นต์ **ลงชื่อเข้าใช้ ไคลเอ็นต์หลาย ๆ ตัวแล้วจะกระทบต่อความปลอดภัยของแอคเคาร์ไหม?** คำตอบของคำถามนี้นั้นขึ้นอยู่กับวิธีการที่คุณลงชื่อเข้าใช้ หากคุณลงชื่อเข้าใช้ด้วยกุญแจส่วนตัว ถึงแม้ว่าไคลเอ็นต์ส่วนใหญ่จะพยายามรักษาความปลอดภัยของกุญแจส่วนตัวอย่างดีที่สุด แต่ด้วยข้อจำกัดของซอฟต์แวร์ ย่อมมีความเสี่ยงที่จะเกิดช่องโหว่ การเจาะระบบ และข้อผิดพลาด ที่อาจทำให้กุญแจส่วนตัวของคุณรั่วไหลออกไปได้ ส่วนวิธีการป้องกันเกี่ยวกับเรื่องนี้คือการใช้ส่วนขยายของเว็บเบราว์เซอร์ เพราะการเข้าสู่ระบบในไคลเอนต์ต่าง ๆ ผ่านส่วนขยายนั้นจะใช้เพียงกุญแจสาธารณะในการเข้าสู่ระบบและทุกครั้งที่เราต้องการจะโพสต์หรือสร้าง event บน Nostr ไคลเอนต์จะทำการร่าง event นั้น ๆ และเว้นช่องของลายเซ็นเอาไว้จากนั้นเราจะต้องทำการเซ็นผ่านส่วนขยาย ด้วยวิธีนี้ทำให้กุญแจส่วนตัวของเราไม่หลุดออกไปไหนตลอดการใช้งาน **รีเลย์คืออะไร?** รีเลย์เปรียบเสมือนเซิร์ฟเวอร์ที่อยู่เบื้องหลังของ Nostr และทำหน้าที่รับ event ต่าง ๆ มาจากไคลเอนต์ Nostr และอาจจะจัดเก็บและกระจายข้อความเหล่านั้นไปยังไคลเอนต์อื่น ๆ ที่มีการเชื่อมต่ออยู่ เทคโนโลยีของรีเลย์นั้นเปลี่ยนแปลงอย่างรวดเร็ว ดังนั้นคาดว่าจะมีการเปลี่ยนแปลงอีกมากมายในอนาคต อย่างในปัจจุบันที่มีการนำเสนอ bostr หรือ รีเลย์ที่จะคอยส่ง event ของเราต่อให้กับรีเลย์อื่น ๆ ที่มีการเชื่อมต่อ เพื่อช่วยลดภาระของไคลเอนต์ในการรับส่งข้อมูลจากหลาย ๆ รีเลย์พร้อม ๆ กัน หรืออย่างการป้องกันสแปมด้วย POW หรือประเภทที่สามารถเก็บรูปหรือวิดีโอที่มีขนาดใหญ่ได้ แต่สิ่งหนึ่งที่ควรทราบก็คือ การที่ Nostr นั้นพยายามจะกระจายศูนย์และเหตุผลหลัก ๆ ที่สามารถทำแบบนั้นได้ก็ขึ้นอยู่กับรีเลย์ในการจัดเก็บและดึงข้อมูล ดังนั้น หากคุณรู้สึกว่าไคลเอนต์ Nostr ของคุณทำงานช้า ส่วนใหญ่ก็มักเกิดจากรีเลย์ที่คุณกำลังเชื่อมต่ออยู่ คุณอาจลองแก้ไขปัญญาโดยการเปลี่ยนหรือเพิ่มรีเลย์อีกสองสามรายการในไคลเอนต์ที่คุณใช้ **แล้วจะสามารถหารายการรีเลย์ได้จากไหน?** การที่เราจะหารายการรีเลย์ที่เราควรเชื่อมต่อนั้น ๆ จริงแล้ว ๆ สามารถทำได้หลายวิธี แต่วิธีที่ผมแนะนำที่สุดจะเป็นการใช้ตามคนที่เราติดตามอยู่ เพราะจะเป็นวิธีที่เราสามารถเห็น event ต่าง ๆ ของคนที่เราติดตามได้ง่ายที่สุด และเช่นเดียวกัน เพื่อน ๆ หรือคนที่เราติดตามก็จะสามารถเห็น event ของเราได้เช่นกัน และสำหรับในประเทศไทย เรามีรีเลย์ที่คนไทยส่วนใหญ่นิยมใช้กันอยู่สองอัน นั้นคือ wss://relay.siamstr.com/ และ wss://relay.notoshi.win/ ถ้าหากว่าอยากเห็นคนไทยเยอะ ๆ บนหน้าไทม์ไลน์ ผมแนะนำเป็นอย่างยิ่งว่าควรเพิ่ม รายการรีเลย์เหล่านี้ลงไปในบัชญีหรือไคลเอนต์ต่าง ๆ ที่คุณใช้ด้วย สำหรับอีกวิธีหนึ่งผมแนะนำให้เข้าไปในเว็บไซต์ nostr.watch เนื่องจากในเว็บไซต์นี้เป็นแหล่งข้อมูลที่ดีที่สุดสำหรับการค้นหาและประเมินความเร็วของรีเลย์ต่าง ๆ **จะเกิดอะไรขึ้นถ้ารีเลย์ทั้งหมดที่ฉันเชื่อมต่ออยู่หยุดให้บริการ?** สิ่งนี้เป็นสิ่งที่คุณต้องระวังมากที่สุดในการใช้งาน nostr เนื่องจากหากรีเลย์ทั้งหมดที่คุณเก็บข้อมูลไว้หยุดให้บริการทั้งหมดและคุณไม่มีการสำรองข้อมูล event ของคุณเก็บไว้เลย มันแปลว่าโพสต์ทั้งหมดของคุณ ผู้ติดตาม และรายการต่าง ๆ ที่คุณสรรค์สร้างไว้จะไม่สามารถกู้คืนได้ไปตลอดการ นี่จึงเป็นเหตุผลหลัก ๆ ที่ Nostr อนุญาตให้ผู้ใช้งานนั้นสามารถเชื่อมต่อกับรีเลย์ได้เป็นจำนวนมาก ก็เพื่อให้แน่ใจว่ามีข้อมูลสำรองเก็บไว้อยู่ที่ใดที่หนึ่งในระบบเสมอ แต่อย่างไรก็ตาม หากคุณต้องการที่จะมั่นใจได้ว่าข้อมูลต่าง ๆ ของคุณจะไม่ถูกเซ็นเซอร์ สิ่งที่คุณสามารถสามารถทำได้คือการใช้รีเลย์ส่วนตัวของคุณและกำหนดนโยบายต่าง ๆ ภายในรีเลย์ของคุณด้วยตัวคุณเอง **แล้วฉันจะสามารถใช้รีเลย์ส่วนตัวได้อย่างไร?** **อะแฮ่ม ๆ** ขอบอกไว้ก่อนว่ามันไม่คุ้มค่ากับความยุ่งยากสำหรับคนโดยทั่ว ๆ ไป ถึงในปัจจุบันจะมีเทคโนโลยีบางตัวที่เข้ามาช่วยให้มันทำได้ง่ายขึ้นแล้วก็ตาม หากคุณต้องการที่จะสำรองข้อมูลนั้น การที่จะมีรีเลย์ส่วนตัวที่ออนไลน์ตลอดเวลาอาจเป็นเรื่องที่ไม่ได้จำเป็นขนาดนั้น เนื่องจากเราสามารถใช้งานบริการอย่าง https://nostrsync.live/ ในการดาวน์โหลดข้อมูลของเราจากรีเลย์ต่าง ๆ ได้ หรือการติดตั้งรีเลย์ส่วนตัวอย่าง nostr-relay-tray: https://github.com/CodyTseng/nostr-relay-tray ที่ช่วยให้เราสามารถมีรีเลย์ส่วนตัวที่ใช้สำหรับสำรองข้อมูลได้ Nostr Implementation Possibilities (NIPs) NIP คืออะไร? --- NIP มีไว้เพื่อส่งเสริมความสามารถในการทำงานของ Nostr และเป็นตัวคอยกำหนดให้ เหล่านักพัฒนาทำสิ่งต่าง ๆ ที่เหมือนกันในรูปแบบเดียวกัน เพราะมันคงไม่ใช่ความคิดที่ดีนัก หากนักพัฒนาแต่ละคนจะคิดค้นวิธีแก้ปัญหาทั่วไปของตัวเองและนำไปใช้ในแอปของตัวเองเท่านั้น และคงจะเป็นการดีกว่า ถ้าหากทุกคนใช้วิธีแก้ปัญหาที่เหมือนกัน นั่นคือเหตุผลที่ต้องมี NIP อยู่ในโปรโตคอลของ Nostr และในทำนองเดียวกัน แนวคิดใหม่อาจดูดีในแอปของนักพัฒนาบางราย แต่จะดูดียิ่งขึ้นอย่างแน่นอนหากแอปอื่น ๆ อีกมากมายใช้มาตรฐานเดียวกันและสามารถทำงานร่วมกันได้อย่างราบรื่น **ทำไมมันถึงหน้าสนใจ?** อย่าลืมว่า Nostr เป็นระบบแบบกระจายอำนาจและไม่ได้มีบริษัทหรือใครที่เป็นเจ้าของมัน อย่างเช่นโซเชียลมีเดียอื่น ๆ เช่น ทวิตเตอร์ อ่อไม่สิตอนนี้คงต้องเรียกมันว่า X สินะ ซึ่งหมายความว่าทิศทางของโพรโทคอล Nostr นั้นขึ้นอยู่กับพวกเราทุกคน! ไม่ว่าใคร ๆ ก็สามารถเสนอแนะและสนับสนุนการเปลี่ยนแปลงและให้ข้อเสนอแนะเกี่ยวกับแนวคิดที่ผู้อื่นเสนอ และการที่คุณเป็นส่วนหนึ่งของชุมชนนี้ ก็ทำให้คุณมีส่วนร่วมในทิศทางของ Nostr อีกด้วย จากที่ส่งหากันได้แค่ข้อความ มาเป็นรูปภาพ มาเป็นวิดีโอ และมาเป็น”เงิน” นี่คือเส้นทางการเดินทางของโปรโตคอลนี้ในอดีต แล้วในอนาคตมันจะพัฒนาไปยังไงต่อก็ขึ้นอยู่กับเหล่าผู้ใช้งานและนักพัฒนาในอนาคต แล้วทำไมสิ่งนี้ถึงจะไม่น่าสนใจละ ? Event --- **Event คืออะไร?** Event เป็น object เพียงประเภทเดียวที่มีอยู่บน Nostr โดยมีโครงสร้างประมาณนี้ ``` {"id":"84d5d3dc9c388a702f39cad6360d41ebb804e809fb822f110ff8a14dfd35fc6c", "pubkey":"66df60562d939ada8612436489945a4ecf1d62346b3d9478dea8a338f3203c64", "created_at":1722315959, "kind":1, "tags":[["t","siamstr"]], "content":"ไปสั่งกาแฟเมื่อกี้ พส เจ้าของร้านชมว่าเดี๋ยวนี้คล่องภาษาญี่ปุ่นแล้วนะ ไอเราก็ดีใจ พอเดินกลับถึงที่ทำงานละก็ตระหนักได้ว่า ตะกี้เราสั่ง “ไอซ์โคฮี โอเนไงชิมัส” “เทคเอาส์” “คาโดะเดสส” ไอบ้าไหนญี่ปุ่นก่อนอังกฤษทั้งนั้น 🤣🤣\n\n#siamstr", "sig":"8f066a0099a5f580b605ebdb220179c4eca298947c38b855a0a8bf2783f28ddb537cb74a7f61d3ce8891189f719870efdf320ea4f895e03cdac44284c450c5c4"} ``` อย่าง Event ข้างต้นนี้มี kind เป็น 1 ซึ่งหมายถึง "ข้อความโน้ต" ซึ่งก็คือข้อความธรรมดา สั้น ๆ คล้ายกับที่ใช้กันใน Twitter เช่น บนฟีด การตอบกลับ และการโควท **ประเภทของ Event (Event Kinds)** หมายเลขของ kind แต่ละตัวมีความหมายแตกต่างกัน ตัวอย่างเช่น 0 หมายถึงอีเวนต์ "ข้อมูลเมตา" ใช้สำหรับให้รายละเอียดเกี่ยวกับผู้ใช้ เช่น ชื่อและรูปโปรไฟล์ รีเลย์ (Relays) สามารถจัดการกับ kind ที่แตกต่างกันได้ เช่น รีเลย์มักจะลบอีเวนต์ kind:0 เวอร์ชันเก่ากว่าออกไป และเก็บไว้เฉพาะเวอร์ชันล่าสุด ในขณะที่โดยทั่วไปจะเก็บอีเวนต์ kind:1 ไว้หลายรายการสำหรับแต่ละคีย์ โดยทั่วไปแล้ว คุณไม่จำเป็นต้องใช้ kind เกินกว่า 0 และ 1 ในการสร้างแอปพลิเคชันโซเชียลมีเดียบน Nostr แต่ kind อื่น ๆ ถูกคิดค้นขึ้นโดยไคลเอนต์ เพื่อมอบฟังก์ชันการทำงานอื่น ๆ ตามที่ระบุไว้ใน NIP บาง kind ไม่เกี่ยวข้องกับเครือข่าย และให้บริการตามความต้องการอื่น ๆ ของไคลเอนต์ที่เฉพาะเจาะจงกับฟังก์ชันการทำงานเหล่านั้น ซึ่งแนวคิดก็คือ สำหรับกรณีการใช้งานใหม่ ๆ แต่ละกรณี จะต้องมีการพิจารณาและเสนอซับโปรโตคอลเป็น NIP เพื่อให้สามารถทำงานร่วมกับไคลเอนต์ที่มีอยู่และในอนาคต ซึ่งอาจสนใจที่จะนำฟังก์ชันการทำงานนั้นไปใช้ ขณะเดียวกันก็มั่นใจได้ถึงความเข้ากันได้ย้อนหลัง และการรองรับสิ่งต่าง ๆ ที่มีอยู่และไม่ต้องการเปลี่ยนแปลง **คุณสมบัติอื่น ๆ ของ Event** created_at: เป็น Timestamp ของ UNIX ที่กำหนดโดยผู้สร้างอีเวนต์ โดยปกติจะเป็นเวลาที่สร้าง แม้ว่าจะไม่มีการตรวจสอบ แต่ก็ไม่ใช่ปัญหา content: ขึ้นอยู่กับความหมายของ kind ในกรณีของ kind:1 จะเป็นเพียงสตริงข้อความธรรมดาที่คนอื่น ๆ อ่านได้ tags: ขึ้นอยู่กับ kind เช่นกัน แต่แท็กทั่วไปบางอย่างที่มักปรากฏใน event kind:1 และ kind อื่น ๆ คือ "p" ซึ่งใช้เพื่อกล่าวถึงกุญแจสาธารณะ และ "e" ใช้เพื่ออ้างถึง event อื่น อยากมีส่วนร่วมในการพัฒนาของ Nostr ? --- จริง ๆ แล้วใคร ๆ ก็สามารถเข้ามามีส่วนร่วมในการพัฒนา Nostr ได้ ไม่จำเป็นต้องเป็น dev หรือมีความรู้ด้านคอมพิวเตอร์ก็สามารถทำได้ ไม่ว่าจะเป็นการให้ feedback กับ dev ของ client ที่คุณใช้, การสร้างคอนเทนต์ต่าง ๆ บน Nostr การสร้างชุมชน รวมไปถึงการช่วย client ต่าง ๆ ในการทำ UI ให้เป็นภาษาท้องถิ่น และอื่น ๆ อีกมากมาย ใคร ๆ ก็สามารถช่วยได้ตามความสามารถที่แต่ละคนมี มันเลยทำให้ Nostr โครตน่าอยู่ :) @ 469fa704:2b6cb760
2024-09-02 06:11:43***I joined Nostr a week ago and wanted to recap it for myself and also give other newbies a simple introduction. Maybe this will help you get started too.*** ## Step 1: Create your identity and get your private key for a browser extension I started with the Snort client on my local home server. It created my private/public key pair and I was good to go. Then I transferred the private key to Amethyst, a pretty good Android-based client. Before looking at various clients and other nostr-based websites, I tried transferring my private key into a browser extension. I looked at Alby and nos2x. I chose the latter because I wanted to keep my Lightning wallet separate from my identity management. You don't have to, I just found it easier. ## Step 2: If you're confused, always check your feed settings I tried many different clients and was very confused at first. Due to its decentralized nature, Nostr relies on relays, which are just small servers, and to each one you can connect to, all your data is stored. When you post a message, write a note, an article like this or simply who you follow. The main reason and benefit for this is that there is no single point of failure or server-like entity that could be censored. The side effect of this, combined with using different clients, was that not only did it look different everywhere, but the content was also very different. This was simply because I wasn't connected to all my different clients with the same relays. But the main reason why each feed looks different on each client is usually because you can choose different variations of feeds and some clients even offer filters for the feeds. Scroll down to get a small overview of the clients I've tried. ## Step 3: Set up your lightning wallet with something like Wallet of Satoshi I made my Bitcoin Lightning wallet independent of my identity. That's why I just went with the number one Lightning wallet on the market: Satoshi's Wallet. It's very simple and provides you with a Lightning address that resembles and has the format of an email address. You can add this address to your Nostr profile description and you're ready to receive Sats. Anyone can send them to you, e.g. for a good message or something else they find valuable on Nostr (like a podcast, a video, an article, ...). Just be aware that Satoshi's wallet contains your key and the sats you have there are not really your sats. So only leave a small amount there or no more than you need for your nostr experience. ## Step 4: Set up your Nostr address I set up a unique NIP-05 identifier that is human readable and also looks like an email address. For me, that's tobiya@nostrplebs.com, also called a nostr address. It's much easier to read, share and remember than your public key, which is just a long, unwieldy string of characters. Some popular services are: * NostrVerified * Alby * Iris * Primal * Snort * nostrplebs.com Most offer free services or at least a free tier. I chose nostrplebs.com because it links my Nostr address (tobiya@nostrplebs.com) to my Lightning wallet. ⚡ ## Brief overview of the clients (I have tested) ### Web/Browser: * **Primal**: Fast, user-friendly, nice looking, easy to use * **Coracle**: Focuses on decentralized reputation, privacy and trust metrics. Also well organized and structured * **noStrudel**: The most comprehensive I've found, has everything * **Rabbit**: Designed like X (Twitter) Pro, focuses on everything at once * **Nostter**: Clearly structured, easy to find what you're looking for * **Snort**: Fast web client for those who prefer simplicity and speed. ### iOS I'm not an iPhone user, but everything I've discovered says that Damus is the best app for iOS. ### Android: * **Amethyst**: Feature rich for Android, I only tried this program because it gives me everything I currently need on my phone. * **Primal**: Works seamlessly with Primal on the web, which is a pretty convenient starting point if you only want to use one client. As for the web clients, I'm still figuring out which one will be my favorite. But I think they're all good in their own way. In the time of writing, I am mainly using Primal on Android and Web, Amethyst and noStrudel. ### Let's have fun!!
@ 469fa704:2b6cb760
2024-09-02 06:11:43***I joined Nostr a week ago and wanted to recap it for myself and also give other newbies a simple introduction. Maybe this will help you get started too.*** ## Step 1: Create your identity and get your private key for a browser extension I started with the Snort client on my local home server. It created my private/public key pair and I was good to go. Then I transferred the private key to Amethyst, a pretty good Android-based client. Before looking at various clients and other nostr-based websites, I tried transferring my private key into a browser extension. I looked at Alby and nos2x. I chose the latter because I wanted to keep my Lightning wallet separate from my identity management. You don't have to, I just found it easier. ## Step 2: If you're confused, always check your feed settings I tried many different clients and was very confused at first. Due to its decentralized nature, Nostr relies on relays, which are just small servers, and to each one you can connect to, all your data is stored. When you post a message, write a note, an article like this or simply who you follow. The main reason and benefit for this is that there is no single point of failure or server-like entity that could be censored. The side effect of this, combined with using different clients, was that not only did it look different everywhere, but the content was also very different. This was simply because I wasn't connected to all my different clients with the same relays. But the main reason why each feed looks different on each client is usually because you can choose different variations of feeds and some clients even offer filters for the feeds. Scroll down to get a small overview of the clients I've tried. ## Step 3: Set up your lightning wallet with something like Wallet of Satoshi I made my Bitcoin Lightning wallet independent of my identity. That's why I just went with the number one Lightning wallet on the market: Satoshi's Wallet. It's very simple and provides you with a Lightning address that resembles and has the format of an email address. You can add this address to your Nostr profile description and you're ready to receive Sats. Anyone can send them to you, e.g. for a good message or something else they find valuable on Nostr (like a podcast, a video, an article, ...). Just be aware that Satoshi's wallet contains your key and the sats you have there are not really your sats. So only leave a small amount there or no more than you need for your nostr experience. ## Step 4: Set up your Nostr address I set up a unique NIP-05 identifier that is human readable and also looks like an email address. For me, that's tobiya@nostrplebs.com, also called a nostr address. It's much easier to read, share and remember than your public key, which is just a long, unwieldy string of characters. Some popular services are: * NostrVerified * Alby * Iris * Primal * Snort * nostrplebs.com Most offer free services or at least a free tier. I chose nostrplebs.com because it links my Nostr address (tobiya@nostrplebs.com) to my Lightning wallet. ⚡ ## Brief overview of the clients (I have tested) ### Web/Browser: * **Primal**: Fast, user-friendly, nice looking, easy to use * **Coracle**: Focuses on decentralized reputation, privacy and trust metrics. Also well organized and structured * **noStrudel**: The most comprehensive I've found, has everything * **Rabbit**: Designed like X (Twitter) Pro, focuses on everything at once * **Nostter**: Clearly structured, easy to find what you're looking for * **Snort**: Fast web client for those who prefer simplicity and speed. ### iOS I'm not an iPhone user, but everything I've discovered says that Damus is the best app for iOS. ### Android: * **Amethyst**: Feature rich for Android, I only tried this program because it gives me everything I currently need on my phone. * **Primal**: Works seamlessly with Primal on the web, which is a pretty convenient starting point if you only want to use one client. As for the web clients, I'm still figuring out which one will be my favorite. But I think they're all good in their own way. In the time of writing, I am mainly using Primal on Android and Web, Amethyst and noStrudel. ### Let's have fun!! @ 3b7fc823:e194354f
2024-09-01 19:21:09Testing articles on Yakkihonne
@ 3b7fc823:e194354f
2024-09-01 19:21:09Testing articles on Yakkihonne @ 469fa704:2b6cb760
2024-09-01 13:26:42## Side jobs and passive sources of income To increase your income, it is often necessary to be creative and develop different income streams: * **Freelancing**: platforms such as Upwork, Fiverr or Freelancer offer a variety of tasks, from graphic design to programming work to marketing. According to a study by Statista, freelancers in Germany earn between 20 and 50 euros per hour on average, depending on their expertise. * **Part-time jobs**: You can take on a part-time job alongside your main job. Think about jobs that are flexible, such as driving services (e.g. Uber, Bolt), delivery services (e.g. Deliveroo, Gorillas) or tutoring. According to the Federal Employment Agency, part-time jobs can be tax-free up to 450 euros per month, which is an attractive option. * **Passive income**: This requires work or capital initially, but can generate income in the long term: * * **Real estate**: real estate investments offer regular rental income. According to the German Institute for Economic Research (DIW), the return on residential real estate in Germany can be between 3% and 5%. * * **Dividend stocks**: Invest in companies that pay dividends. Companies such as Siemens or Deutsche Telekom have a long tradition of distributing dividends. * * **Digital products**: Create e-books, online courses or apps. Once created, these products can generate continuous income. * * **Affiliate marketing**: Partner with brands and earn through sales commissions. Amazon Associates is one of the best-known platforms for this. ## Reduce expenses Another way to have more capital for investments such as Bitcoin is to reduce expenses: * **Budgeting**: create a detailed budget. Apps like YNAB or Mint can help categorize expenses and analyze where savings can be made. * **Food**: Plan your shopping, buy seasonal products and cook more yourself. According to a study by the Federal Ministry of Food and Agriculture, households spend an average of around 25% of their income on food.Conscious shopping can significantly reduce these costs. * **Energy costs**: Use energy-saving light bulbs, switch off appliances completely and insulate your home better. According to the Federal Office of Economics and Export Control (BAFA), simple energy-saving measures can reduce costs by up to 20%. * **Subscriptions and memberships**: Review regular subscriptions (gym, streaming services).Many people pay for services they rarely use. A survey by Statista showed that on average 10-15% of monthly spending is used for subscriptions. * **Transportation**: Use public transportation or car sharing services instead of owning a car.Owning a car can cost several thousand euros a year, including insurance, maintenance and fuel. * **Second-hand and upcycling**: Buy second-hand clothes or furniture.The second-hand market is booming and you can often find high-quality products at a fraction of the original price. ## Investing, or rather saving, in Bitcoin After you have accumulated more Dollar or other paper money by increasing your income and reducing your expenses, you can invest in Bitcoin: * **Bitcoin**: As the first and best-known cryptocurrency, Bitcoin has a high market capitalization and acceptance. Investors see Bitcoin as a “digital gold” alternative, especially in times of inflation. * **Risk and volatility**: Bitcoin is known for its high volatility. It is important to only invest money that you don't need in the immediate future. In the long term, bitcoin is destined to rise in price in dollar terms due to its unique characteristics. * **Long-term perspective**: Many investors hold Bitcoin as a long-term investment, similar to stocks. Historically, Bitcoin has shown positive returns over longer periods of time, despite high volatility. ## Practical steps to increase income and reduce expenses: 1. **Analyze income**: Make a note of all your sources of income and consider how you can increase them. This could be through salary increases, side hustles or new passive income streams. 2. **Review expenses**: Make a list of your monthly expenses and identify areas where you can cut back. Set specific goals for reduction. 3. **Investment plan**: After you have accumulated more capital, create an investment plan. For Bitcoin, this could mean investing small amounts regularly to take advantage of the average cost effect (dollar-cost averaging). 4. **Education and networking**: Invest time in education and build a network. This can lead to new income opportunities and increase your financial intelligence. ## Idea to get Ahead: Create a budget and set a monthly savings goal for your Bitcoin investments. Calculate how much you can generate by reducing expenses and generating additional income. Research and choose a Bitcoin only platform to buy Bitcoin (e.g. [Relai](https://relai.app/), [Coinfinity](https://coinfinity.co/), [21Bitcoin](https://21bitcoin.app/), [Pocket Bitcoin](https://pocketbitcoin.com/) ). Learn the basics of trading and start with a small investment.
@ 469fa704:2b6cb760
2024-09-01 13:26:42## Side jobs and passive sources of income To increase your income, it is often necessary to be creative and develop different income streams: * **Freelancing**: platforms such as Upwork, Fiverr or Freelancer offer a variety of tasks, from graphic design to programming work to marketing. According to a study by Statista, freelancers in Germany earn between 20 and 50 euros per hour on average, depending on their expertise. * **Part-time jobs**: You can take on a part-time job alongside your main job. Think about jobs that are flexible, such as driving services (e.g. Uber, Bolt), delivery services (e.g. Deliveroo, Gorillas) or tutoring. According to the Federal Employment Agency, part-time jobs can be tax-free up to 450 euros per month, which is an attractive option. * **Passive income**: This requires work or capital initially, but can generate income in the long term: * * **Real estate**: real estate investments offer regular rental income. According to the German Institute for Economic Research (DIW), the return on residential real estate in Germany can be between 3% and 5%. * * **Dividend stocks**: Invest in companies that pay dividends. Companies such as Siemens or Deutsche Telekom have a long tradition of distributing dividends. * * **Digital products**: Create e-books, online courses or apps. Once created, these products can generate continuous income. * * **Affiliate marketing**: Partner with brands and earn through sales commissions. Amazon Associates is one of the best-known platforms for this. ## Reduce expenses Another way to have more capital for investments such as Bitcoin is to reduce expenses: * **Budgeting**: create a detailed budget. Apps like YNAB or Mint can help categorize expenses and analyze where savings can be made. * **Food**: Plan your shopping, buy seasonal products and cook more yourself. According to a study by the Federal Ministry of Food and Agriculture, households spend an average of around 25% of their income on food.Conscious shopping can significantly reduce these costs. * **Energy costs**: Use energy-saving light bulbs, switch off appliances completely and insulate your home better. According to the Federal Office of Economics and Export Control (BAFA), simple energy-saving measures can reduce costs by up to 20%. * **Subscriptions and memberships**: Review regular subscriptions (gym, streaming services).Many people pay for services they rarely use. A survey by Statista showed that on average 10-15% of monthly spending is used for subscriptions. * **Transportation**: Use public transportation or car sharing services instead of owning a car.Owning a car can cost several thousand euros a year, including insurance, maintenance and fuel. * **Second-hand and upcycling**: Buy second-hand clothes or furniture.The second-hand market is booming and you can often find high-quality products at a fraction of the original price. ## Investing, or rather saving, in Bitcoin After you have accumulated more Dollar or other paper money by increasing your income and reducing your expenses, you can invest in Bitcoin: * **Bitcoin**: As the first and best-known cryptocurrency, Bitcoin has a high market capitalization and acceptance. Investors see Bitcoin as a “digital gold” alternative, especially in times of inflation. * **Risk and volatility**: Bitcoin is known for its high volatility. It is important to only invest money that you don't need in the immediate future. In the long term, bitcoin is destined to rise in price in dollar terms due to its unique characteristics. * **Long-term perspective**: Many investors hold Bitcoin as a long-term investment, similar to stocks. Historically, Bitcoin has shown positive returns over longer periods of time, despite high volatility. ## Practical steps to increase income and reduce expenses: 1. **Analyze income**: Make a note of all your sources of income and consider how you can increase them. This could be through salary increases, side hustles or new passive income streams. 2. **Review expenses**: Make a list of your monthly expenses and identify areas where you can cut back. Set specific goals for reduction. 3. **Investment plan**: After you have accumulated more capital, create an investment plan. For Bitcoin, this could mean investing small amounts regularly to take advantage of the average cost effect (dollar-cost averaging). 4. **Education and networking**: Invest time in education and build a network. This can lead to new income opportunities and increase your financial intelligence. ## Idea to get Ahead: Create a budget and set a monthly savings goal for your Bitcoin investments. Calculate how much you can generate by reducing expenses and generating additional income. Research and choose a Bitcoin only platform to buy Bitcoin (e.g. [Relai](https://relai.app/), [Coinfinity](https://coinfinity.co/), [21Bitcoin](https://21bitcoin.app/), [Pocket Bitcoin](https://pocketbitcoin.com/) ). Learn the basics of trading and start with a small investment. @ 469fa704:2b6cb760
2024-09-01 13:26:13## The basics of financial planning Financial education is the first step to financial independence. Here are the core principles you need to understand: * **Income vs. expenses**: The core of any financial plan is to earn more than you spend. This requires not only discipline, but also a clear overview of your financial comings and goings. * **Budgeting**: Create a detailed budget plan. A budget helps you to see where your money is going and where you can save. It's a living document that you should adjust regularly. * **Emergency fund**: An emergency fund is a buffer against unforeseen events. Experts recommend keeping at least three to six months of your expenses in cash or easily liquidated assets. * **Set goals**: Define clear financial goals. These can be short-term (e.g. a new cell phone), medium-term (e.g. a car) or long-term (e.g. retirement). Each type of goal requires different strategies and time frames. * **Debt management**: Distinguish between good debt (e.g. investments in education or real estate) and bad debt (e.g. credit cards with high interest rates). A debt repayment plan is often just as important as a savings plan. ## Understanding investments Investing is the way to make your money work for you. Here are some basic concepts you should understand: * **Interest and Compound Interest**: Interest is the compensation you receive or pay when you invest or borrow money. Compound interest is particularly powerful as it means you earn interest on your interest, which can lead to exponential growth over time. * **Risk and return**: Investments with higher returns are often associated with higher risk. It's important to find a balance that suits your personal risk profile. Diversification can help manage this risk. * **Diversification**: Spread your money across different asset classes (equities, bonds, real estate, commodities) and regions to minimize risk. This protects you from a total loss if one investment performs poorly. *** Long-term perspective**: Investing is not a short-term game. It requires patience and a long-term perspective.Short-term market fluctuations should not lead to panic selling. This is true for every asset, even Bitcoin. * **Costs and fees**: Pay attention to the costs and fees associated with investing. These can have a significant impact on your returns over time. Especially important are taxes. ## Practical steps to financial education: * **Books and courses**: Invest in your financial education.There are many resources available, from classics like Rich Dad Poor Dad to online courses on platforms like Coursera or Udemy. * **Financial apps and tools**: Use apps like Mint, YNAB (You Need A Budget), or Personal Capital to track your budget and investments. These tools can help you monitor your finances in real time. Even a good old spread sheet can work wonders. * **Seek advice**: If possible, consult a financial advisor. They can provide personalized advice tailored to your specific situation. Make sure they offer independent advice. * **Podcasts and blogs**: Follow financial podcasts or blogs to get the latest trends and tips. You can find also a lot of execellent stuff on Youtube, especially Bitcoin education. * **Self-study**: Learn the basics of stock markets, bonds, real estate investing and other forms of investing. Websites like Investopedia or Khan Academy offer free knowledge. * **Study Bitcoin**: Nothing teaches you so much about finance, investing, money and wealth than bitcoin. If you are eager to understand it even more, it will teach you also thermodynamics, cryptography (math), economics, philosophy and maybe a lot more. ## Practice for application: Create a simple budget for the next month. Write down all expected income and expenses. Identify areas where you can save. Use an app or Excel spreadsheet to do this. Research an investment opportunity that interests you (e.g. ETFs, shares, real estate funds). Understand the basics and think about how you could get started. Create a small investment plan.
@ 469fa704:2b6cb760
2024-09-01 13:26:13## The basics of financial planning Financial education is the first step to financial independence. Here are the core principles you need to understand: * **Income vs. expenses**: The core of any financial plan is to earn more than you spend. This requires not only discipline, but also a clear overview of your financial comings and goings. * **Budgeting**: Create a detailed budget plan. A budget helps you to see where your money is going and where you can save. It's a living document that you should adjust regularly. * **Emergency fund**: An emergency fund is a buffer against unforeseen events. Experts recommend keeping at least three to six months of your expenses in cash or easily liquidated assets. * **Set goals**: Define clear financial goals. These can be short-term (e.g. a new cell phone), medium-term (e.g. a car) or long-term (e.g. retirement). Each type of goal requires different strategies and time frames. * **Debt management**: Distinguish between good debt (e.g. investments in education or real estate) and bad debt (e.g. credit cards with high interest rates). A debt repayment plan is often just as important as a savings plan. ## Understanding investments Investing is the way to make your money work for you. Here are some basic concepts you should understand: * **Interest and Compound Interest**: Interest is the compensation you receive or pay when you invest or borrow money. Compound interest is particularly powerful as it means you earn interest on your interest, which can lead to exponential growth over time. * **Risk and return**: Investments with higher returns are often associated with higher risk. It's important to find a balance that suits your personal risk profile. Diversification can help manage this risk. * **Diversification**: Spread your money across different asset classes (equities, bonds, real estate, commodities) and regions to minimize risk. This protects you from a total loss if one investment performs poorly. *** Long-term perspective**: Investing is not a short-term game. It requires patience and a long-term perspective.Short-term market fluctuations should not lead to panic selling. This is true for every asset, even Bitcoin. * **Costs and fees**: Pay attention to the costs and fees associated with investing. These can have a significant impact on your returns over time. Especially important are taxes. ## Practical steps to financial education: * **Books and courses**: Invest in your financial education.There are many resources available, from classics like Rich Dad Poor Dad to online courses on platforms like Coursera or Udemy. * **Financial apps and tools**: Use apps like Mint, YNAB (You Need A Budget), or Personal Capital to track your budget and investments. These tools can help you monitor your finances in real time. Even a good old spread sheet can work wonders. * **Seek advice**: If possible, consult a financial advisor. They can provide personalized advice tailored to your specific situation. Make sure they offer independent advice. * **Podcasts and blogs**: Follow financial podcasts or blogs to get the latest trends and tips. You can find also a lot of execellent stuff on Youtube, especially Bitcoin education. * **Self-study**: Learn the basics of stock markets, bonds, real estate investing and other forms of investing. Websites like Investopedia or Khan Academy offer free knowledge. * **Study Bitcoin**: Nothing teaches you so much about finance, investing, money and wealth than bitcoin. If you are eager to understand it even more, it will teach you also thermodynamics, cryptography (math), economics, philosophy and maybe a lot more. ## Practice for application: Create a simple budget for the next month. Write down all expected income and expenses. Identify areas where you can save. Use an app or Excel spreadsheet to do this. Research an investment opportunity that interests you (e.g. ETFs, shares, real estate funds). Understand the basics and think about how you could get started. Create a small investment plan. @ c11cf5f8:4928464d
2024-09-01 13:22:49Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too! If you missed our last thread, [here](https://stacker.news/items/661607/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/668607
@ c11cf5f8:4928464d
2024-09-01 13:22:49Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too! If you missed our last thread, [here](https://stacker.news/items/661607/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/668607 @ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend, it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart. As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you: * What causes the discomfort that drives you out of the walled garden onto the open sea? * Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall? * What are you hoping to find on the open sea that walled gardens cannot provide? * What are you willing to sacrifice for freedom (of speech)? * What will you need to keep the ship afloat? * How will you react when you find yourself in the middle of a storm? I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over. This is about building a new world, an open world without walled gardens and data silos. Onwards!
@ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend, it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart. As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you: * What causes the discomfort that drives you out of the walled garden onto the open sea? * Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall? * What are you hoping to find on the open sea that walled gardens cannot provide? * What are you willing to sacrifice for freedom (of speech)? * What will you need to keep the ship afloat? * How will you react when you find yourself in the middle of a storm? I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over. This is about building a new world, an open world without walled gardens and data silos. Onwards! @ a30cdfee:2d2f97ff
2024-09-01 11:40:38# Primal: Social Media with Bitcoin Tipping [Primal](https://primal.net/) is a social media app that lets you tip (zap) other users with bitcoin! How does Primal work and why should you join?  Primal is a social Bitcoin wallet. If you like somebody's content, you can tip them Bitcoin micropayments through the Lightning Network. Or monetize your own content. You can also use it as a custodial Lightning wallet to pay for small purchases in bitcoin. ## Primal Is a Nostr Client Primal uses the Nostr protocol as its social graph. Nostr is an open protocol for decentralized and censorship-resistant social media. If you're new to Nostr, learn more about it here: https://stacker.news/items/558629 Since Primal is only a client to access the Nostr protocol, it can only censor free speech or deplatform users on the Primal app, but not on Nostr. Also, if you stop using Primal as your Nostr client, you can import all your followers, posts, etc. to a new client. ## Primal Feels Like Twitter (X)! Primal's feed feels very familiar to other social media platforms, especially X (Twitter). You can follow people, like their posts, repost etc. It's not only for Bitcoin-related discussion: you can search for different hashtags and find your tribe, e.g. photography etc.  Primal works for iOS, Android and desktop. On desktop, the "Explore" function is even more detailed.  ## Earn Bitcoin for Your Content! By clicking the lightning bolt symbol on the feed, you can tip (zap) other users bitcoin. You can also browse through your contacts and zap them. Nostr is a great directory for Lightning payments!  If you hold the bolt symbol a bit longer, you can specify the zap amount if you want.  You can set your default zap amount in settings.  To set up a Lightning wallet with Primal, the app asks for your name, email address and the country of residence. But as far as I know, you can use a nym and a throwaway email etc. No need to upload any identity documents. The maximum balance you can hold on the Primal wallet is 1 million sats, or 0.01 BTC. The purpose of the wallet is not for long-term savings, but to onboard people to Nostr and to get familiarized with the culture of zapping. To get your first sats on the Primal wallet, you can receive bitcoin on Lightning or on-chain. Alternatively, you can buy sats on Primal with Apple Pay or Google Pay with your credit card (max. about $5 worth). Or just start creating and receive zaps from other users.  ## Take Care of Your "nsec"! Your "nsec" is your private key to your Primal (and Nostr account). Don't share it with anyone! Primal creates an nsec for you upon account creation, or you can import your own.  Primal is open-source, but it is not always a good practice to import private keys to any apps. If you don't want to import the private keys you already have to Primal, you can use e.g. [Amber](https://github.com/greenart7c3/Amber ), a Nostr signer extension app for Android. It's advisable to store your nsec in e.g. a password manager. If you use Primal on desktop, you can use e.g. [Alby](https://getalby.com/) @Alby, as a Nostr signer extension, zapping wallet and a place to store your nsec. Learn more about Alby [here](https://x.com/teemupleb/status/1599882236106416128). You can also use another Nostr signer extensions on desktop, e.g. [Nos2x](https://github.com/fiatjaf/nos2x ), but they often have no wallet functions for zapping or receiving zaps. They work only for posting, liking, replying, reposts etc. ## Convenient, but With Privacy Trade-Offs You can send direct messages to other Primal users, but you should know that while the content of the direct messages is encrypted (visible only to you and your contact), the message metadata is public for all to see (who you're sending messages to, when, how often etc.) Primal can be used as a [global international "Venmo" during dinner parties](https://x.com/joaodealmeida_/status/1828423275682373720). No more head-scratching when trying to split the bill! Not the most private way to do it though, but it's convenient!  Let's connect on Nostr! You can find me [here](https://primal.net/teemupleb). ## Additional Resources https://www.youtube.com/watch?v=Qd4Po4i7wvc https://www.youtube.com/watch?v=7LsIb6D7FtU ## Project Links [Website](https://primal.net/) [GitHub](https://github.com/PrimalHQ) [Nostr](https://primal.net/primal) [X (Twitter)](https://x.com/primal_app) originally posted at https://stacker.news/items/668536
@ a30cdfee:2d2f97ff
2024-09-01 11:40:38# Primal: Social Media with Bitcoin Tipping [Primal](https://primal.net/) is a social media app that lets you tip (zap) other users with bitcoin! How does Primal work and why should you join?  Primal is a social Bitcoin wallet. If you like somebody's content, you can tip them Bitcoin micropayments through the Lightning Network. Or monetize your own content. You can also use it as a custodial Lightning wallet to pay for small purchases in bitcoin. ## Primal Is a Nostr Client Primal uses the Nostr protocol as its social graph. Nostr is an open protocol for decentralized and censorship-resistant social media. If you're new to Nostr, learn more about it here: https://stacker.news/items/558629 Since Primal is only a client to access the Nostr protocol, it can only censor free speech or deplatform users on the Primal app, but not on Nostr. Also, if you stop using Primal as your Nostr client, you can import all your followers, posts, etc. to a new client. ## Primal Feels Like Twitter (X)! Primal's feed feels very familiar to other social media platforms, especially X (Twitter). You can follow people, like their posts, repost etc. It's not only for Bitcoin-related discussion: you can search for different hashtags and find your tribe, e.g. photography etc.  Primal works for iOS, Android and desktop. On desktop, the "Explore" function is even more detailed.  ## Earn Bitcoin for Your Content! By clicking the lightning bolt symbol on the feed, you can tip (zap) other users bitcoin. You can also browse through your contacts and zap them. Nostr is a great directory for Lightning payments!  If you hold the bolt symbol a bit longer, you can specify the zap amount if you want.  You can set your default zap amount in settings.  To set up a Lightning wallet with Primal, the app asks for your name, email address and the country of residence. But as far as I know, you can use a nym and a throwaway email etc. No need to upload any identity documents. The maximum balance you can hold on the Primal wallet is 1 million sats, or 0.01 BTC. The purpose of the wallet is not for long-term savings, but to onboard people to Nostr and to get familiarized with the culture of zapping. To get your first sats on the Primal wallet, you can receive bitcoin on Lightning or on-chain. Alternatively, you can buy sats on Primal with Apple Pay or Google Pay with your credit card (max. about $5 worth). Or just start creating and receive zaps from other users.  ## Take Care of Your "nsec"! Your "nsec" is your private key to your Primal (and Nostr account). Don't share it with anyone! Primal creates an nsec for you upon account creation, or you can import your own.  Primal is open-source, but it is not always a good practice to import private keys to any apps. If you don't want to import the private keys you already have to Primal, you can use e.g. [Amber](https://github.com/greenart7c3/Amber ), a Nostr signer extension app for Android. It's advisable to store your nsec in e.g. a password manager. If you use Primal on desktop, you can use e.g. [Alby](https://getalby.com/) @Alby, as a Nostr signer extension, zapping wallet and a place to store your nsec. Learn more about Alby [here](https://x.com/teemupleb/status/1599882236106416128). You can also use another Nostr signer extensions on desktop, e.g. [Nos2x](https://github.com/fiatjaf/nos2x ), but they often have no wallet functions for zapping or receiving zaps. They work only for posting, liking, replying, reposts etc. ## Convenient, but With Privacy Trade-Offs You can send direct messages to other Primal users, but you should know that while the content of the direct messages is encrypted (visible only to you and your contact), the message metadata is public for all to see (who you're sending messages to, when, how often etc.) Primal can be used as a [global international "Venmo" during dinner parties](https://x.com/joaodealmeida_/status/1828423275682373720). No more head-scratching when trying to split the bill! Not the most private way to do it though, but it's convenient!  Let's connect on Nostr! You can find me [here](https://primal.net/teemupleb). ## Additional Resources https://www.youtube.com/watch?v=Qd4Po4i7wvc https://www.youtube.com/watch?v=7LsIb6D7FtU ## Project Links [Website](https://primal.net/) [GitHub](https://github.com/PrimalHQ) [Nostr](https://primal.net/primal) [X (Twitter)](https://x.com/primal_app) originally posted at https://stacker.news/items/668536 @ 7fd90943:52bf6313
2024-09-01 07:20:27> ![TIP] > I was surprised to discover that I can send Hive in form of Bitcoin Lightning with this Decentralized Application. Right now the only way that I was able to access this is through HIVE keychain. I will try to find some other ways to access this. Now I can fund my Stacker wallet in the most convenient way possible.  originally posted at https://stacker.news/items/668391
@ 7fd90943:52bf6313
2024-09-01 07:20:27> ![TIP] > I was surprised to discover that I can send Hive in form of Bitcoin Lightning with this Decentralized Application. Right now the only way that I was able to access this is through HIVE keychain. I will try to find some other ways to access this. Now I can fund my Stacker wallet in the most convenient way possible.  originally posted at https://stacker.news/items/668391 @ 3c9712ff:14fecbc4
2024-09-01 03:39:08The Australian dream used to be straightforward: secure a job, pay off your house by your late thirties, and retire with substantial assets and savings to support your lifestyle. Some argue the introduction of compulsory superannuation contributions in 1991 signaled the government's lack of trust in Australians' ability to save and be self-sufficient in their later years. But I disagree. The issue wasn’t that Australians were incapable of saving; it was that saving money was no longer enough. The erosion caused by the Keynesian experiment had seeped into Australian retirements, making it nearly impossible for an entire generation to retire off the savings from a [median salary of $27,200](https://www.9news.com.au/finance/rates-1990-versus-2007/8251875f-a878-49a5-bca6-559d2dcdb361#:~:text=Against%20a%20backdrop%20of%20average,up%2044.99%20percent%20of%20income.). Superfunds were thus established by the government as a supposed solution to the problem they had created. How unsurprising. Fast forward 33 years, and Australian superfunds, like those in most of the western world, are now facing two insurmountable challenges of population demographic, and a debasing currency. **1. Our Population is Ageing** On face value, it shouldn't matter whether the population is ageing. If I have my own retirement account which I paid into each month, why would it matter if the people around me are ageing as well? The answer lies in duration mismatch. Retirement funds must manage a mix of short-term, long-term, and continuous obligations, balancing liquid liabilities (cash payments to members) with illiquid assets (investments). Because funds rely on more inflows (super contributions) than outflows (payouts to retirees), population demographics play a critical role in maintaining this balance - and Australia's isn't looking great.   *An example of an ageing population (Australia) vs a growing population (Nigeria)* **2. Our Currency is Ever Debasing** This is far more pernicious for our retirees | Financial Year | [Average Super Return](https://www.superguide.com.au/comparing-super-funds/super-funds-returns-financial-year) | [Money Supply Growth](https://data.worldbank.org/indicator/FM.LBL.BMNY.ZG?locations=AU&most_recent_year_desc=true) | Net Return | | --- | --- | --- | --- | | 2023-24 | 9.1% | 4% | 5.1% | | 2022-23 | 9.2% | 7.8% | 1.4% | | 2021-20 | -3.3% | 6.7% | -10% | | 2020-21 | 18% | 13.6% | 4.4% | In Austrian Economics, inflation is understood as a monetary phenomenon that occurs when new monetary units are added to the existing supply. This monetary inflation is the precursor to both price and asset inflation. Austrians also reject the idea of measuring price inflation with a single number, such as the CPI, as different asset classes respond differently to monetary inflation. For instance, industries like technology and manufacturing are less susceptible to price inflation due to the deflationary effects of increased automation and competition. Conversely, hard assets like gold and real estate have reached record highs, as easy money tends to flow toward the most reliable stores of value. #### Average Yearly Prices Increase since 2018 - Against YoY M2 and CPI | | Iphone | [Median House](https://www.aussie.com.au/content/dam/aussie/documents/home-loans/aussie_25_years_report.pdf) | Money Supply Growth | [CPI](https://www.rba.gov.au/inflation/measures-cpi.html) | | ----- | ----| ---- | ------ | --- | | Since 2018 | 2.24% | 6.8% | 7.2% | 3.1% --- *Although simplistic, the table above shows that hard assets move with monetary inflation, not CPI. The real hurdle, or the absolute **minimum** that a superfund has to give it's members is not CPI or the 3.95% 10 year, but that monetary inflation rate of 7.2%. An increase in the required rate of return invariably brings an increase in risk. Superfunds can't simply gamble Australians' retirement savings on high-risk offshore tech startups, so these returns are often sought through listed equities and commercial real estate—two interest rate sensitive asset classes. This correlation significantly limits the RBA's ability to manoeuvre and the dilemma is clear: * Drop rates, inflate away our retirement. * Increase rates, crash our retirement. **Bitcoin to the Rescue** You guess it, bitcoin fixes this. Take the same example from 1991, but replace the Australian Peso with Bitcoin. In a Bitcoin world, we wouldn’t need superannuation. By simply saving 40 years of time and energy in a deflationary currency like Bitcoin, our savings alone would **increase** in purchasing power, eliminating the need to burden future generations for our retirement. In the meantime, Australian superfunds should take a leaf out of a few smaller US pension funds like the [Wisconsin Pension Fund](https://www.wpr.org/news/wisconsin-pension-fund-bitcoin) and start gaining exposure to bitcoin. A 2% allocation to a Bitcoin ETF is enough to ignite a chain reaction toward full institutional adoption. This truly scarce and desirable asset, with its **low** correlation to existing portfolios, isn’t just an opportunity—it’s a lifeline for the future of Australian retirees. It’s only a matter of time. Colin Gifford August 2024
@ 3c9712ff:14fecbc4
2024-09-01 03:39:08The Australian dream used to be straightforward: secure a job, pay off your house by your late thirties, and retire with substantial assets and savings to support your lifestyle. Some argue the introduction of compulsory superannuation contributions in 1991 signaled the government's lack of trust in Australians' ability to save and be self-sufficient in their later years. But I disagree. The issue wasn’t that Australians were incapable of saving; it was that saving money was no longer enough. The erosion caused by the Keynesian experiment had seeped into Australian retirements, making it nearly impossible for an entire generation to retire off the savings from a [median salary of $27,200](https://www.9news.com.au/finance/rates-1990-versus-2007/8251875f-a878-49a5-bca6-559d2dcdb361#:~:text=Against%20a%20backdrop%20of%20average,up%2044.99%20percent%20of%20income.). Superfunds were thus established by the government as a supposed solution to the problem they had created. How unsurprising. Fast forward 33 years, and Australian superfunds, like those in most of the western world, are now facing two insurmountable challenges of population demographic, and a debasing currency. **1. Our Population is Ageing** On face value, it shouldn't matter whether the population is ageing. If I have my own retirement account which I paid into each month, why would it matter if the people around me are ageing as well? The answer lies in duration mismatch. Retirement funds must manage a mix of short-term, long-term, and continuous obligations, balancing liquid liabilities (cash payments to members) with illiquid assets (investments). Because funds rely on more inflows (super contributions) than outflows (payouts to retirees), population demographics play a critical role in maintaining this balance - and Australia's isn't looking great.   *An example of an ageing population (Australia) vs a growing population (Nigeria)* **2. Our Currency is Ever Debasing** This is far more pernicious for our retirees | Financial Year | [Average Super Return](https://www.superguide.com.au/comparing-super-funds/super-funds-returns-financial-year) | [Money Supply Growth](https://data.worldbank.org/indicator/FM.LBL.BMNY.ZG?locations=AU&most_recent_year_desc=true) | Net Return | | --- | --- | --- | --- | | 2023-24 | 9.1% | 4% | 5.1% | | 2022-23 | 9.2% | 7.8% | 1.4% | | 2021-20 | -3.3% | 6.7% | -10% | | 2020-21 | 18% | 13.6% | 4.4% | In Austrian Economics, inflation is understood as a monetary phenomenon that occurs when new monetary units are added to the existing supply. This monetary inflation is the precursor to both price and asset inflation. Austrians also reject the idea of measuring price inflation with a single number, such as the CPI, as different asset classes respond differently to monetary inflation. For instance, industries like technology and manufacturing are less susceptible to price inflation due to the deflationary effects of increased automation and competition. Conversely, hard assets like gold and real estate have reached record highs, as easy money tends to flow toward the most reliable stores of value. #### Average Yearly Prices Increase since 2018 - Against YoY M2 and CPI | | Iphone | [Median House](https://www.aussie.com.au/content/dam/aussie/documents/home-loans/aussie_25_years_report.pdf) | Money Supply Growth | [CPI](https://www.rba.gov.au/inflation/measures-cpi.html) | | ----- | ----| ---- | ------ | --- | | Since 2018 | 2.24% | 6.8% | 7.2% | 3.1% --- *Although simplistic, the table above shows that hard assets move with monetary inflation, not CPI. The real hurdle, or the absolute **minimum** that a superfund has to give it's members is not CPI or the 3.95% 10 year, but that monetary inflation rate of 7.2%. An increase in the required rate of return invariably brings an increase in risk. Superfunds can't simply gamble Australians' retirement savings on high-risk offshore tech startups, so these returns are often sought through listed equities and commercial real estate—two interest rate sensitive asset classes. This correlation significantly limits the RBA's ability to manoeuvre and the dilemma is clear: * Drop rates, inflate away our retirement. * Increase rates, crash our retirement. **Bitcoin to the Rescue** You guess it, bitcoin fixes this. Take the same example from 1991, but replace the Australian Peso with Bitcoin. In a Bitcoin world, we wouldn’t need superannuation. By simply saving 40 years of time and energy in a deflationary currency like Bitcoin, our savings alone would **increase** in purchasing power, eliminating the need to burden future generations for our retirement. In the meantime, Australian superfunds should take a leaf out of a few smaller US pension funds like the [Wisconsin Pension Fund](https://www.wpr.org/news/wisconsin-pension-fund-bitcoin) and start gaining exposure to bitcoin. A 2% allocation to a Bitcoin ETF is enough to ignite a chain reaction toward full institutional adoption. This truly scarce and desirable asset, with its **low** correlation to existing portfolios, isn’t just an opportunity—it’s a lifeline for the future of Australian retirees. It’s only a matter of time. Colin Gifford August 2024