-
 @ 3ffac3a6:2d656657
2025-03-08 23:07:57
@ 3ffac3a6:2d656657
2025-03-08 23:07:57Recently, I found an old Sapphire Block Erupter USB at home that I used for Bitcoin mining back in 2013. Out of curiosity and nostalgia, I decided to try getting it to work again. I spent an entire afternoon configuring the device and, after much trial and error, discovered that I needed an older version of CGMiner to make it work.
The Sapphire Block Erupter USB was one of the first ASIC devices designed for Bitcoin mining. Although obsolete for competitive mining, it can still be used for learning, nostalgia, or experimentation. In this post, I’ll show you how to run a Block Erupter USB on Linux today.
1. Prerequisites
Before you start, make sure you have:
- A Sapphire Block Erupter USB
- A powered USB hub (optional but recommended)
- A computer running Linux (Ubuntu, Debian, or another compatible distribution)
- A mining pool account (e.g., Slush Pool, KanoPool, etc.)
2. Installing Dependencies
Before running the miner, install some dependencies:
bash sudo apt update && sudo apt install -y git build-essential autoconf automake libtool pkg-config libusb-1.0-0-dev3. Determining the Compatible Version of CGMiner
To find the correct CGMiner version that still supports Block Erupter USB, I performed a binary search across different versions, testing each one until I found the last one that properly recognized the device. The result was that version 3.4.3 is the most recent one that still supports Block Erupters. However, different versions of these devices may require different CGMiner versions.
4. Downloading and Compiling CGMiner
CGMiner is one of the software options compatible with Block Erupters. You can download the correct version from two trusted sources:
- From the official repository: CGMiner v3.4.3 on GitHub
- Alternatively, from this mirror: CGMiner v3.4.3 on Haven
To ensure file integrity, verify the SHA-256 hash:
3b44da12e5f24f603eeeefdaa2c573bd566c5c50c9d62946f198e611cd55876bNow, download and extract it:
```bash wget https://github.com/ckolivas/cgminer/archive/refs/tags/v3.4.3.tar.gz
Or, alternatively:
wget https://haven.girino.org/3b44da12e5f24f603eeeefdaa2c573bd566c5c50c9d62946f198e611cd55876b.tgz
sha256sum v3.4.3.tar.gz # Confirm that the hash matches
Extract the file
tar -xvf v3.4.3.tar.gz cd cgminer-3.4.3
Compile CGMiner
./autogen.sh --enable-icarus make -j$(nproc)
Install on the system (optional)
sudo make install ```
5. Connecting the Block Erupter USB
Plug the device into a USB port and check if it is recognized:
bash dmesg | grep USB lsusbYou should see something like:
Bus 003 Device 004: ID 10c4:ea60 Cygnal Integrated Products, Inc. CP2102 USB to UART Bridge ControllerIf needed, adjust the USB device permissions:
bash sudo chmod 666 /dev/ttyUSB06. Configuring and Running CGMiner
Now, run CGMiner, pointing it to your mining pool:
bash ./cgminer -o stratum+tcp://your.pool.com:3333 -u yourUsername -p yourPasswordIf the miner detects the Block Erupter correctly, you should see something like:
[2025-03-08 22:26:45] Started cgminer 3.4.3 [2025-03-08 22:26:45] No devices detected! [2025-03-08 22:26:45] Waiting for USB hotplug devices or press q to quit [2025-03-08 22:26:45] Probing for an alive pool [2025-03-08 22:26:46] Pool 0 difficulty changed to 65536 [2025-03-08 22:26:46] Network diff set to 111T [2025-03-08 22:26:46] Stratum from pool 0 detected new block [2025-03-08 22:27:02] Hotplug: Icarus added AMU 0Conclusion
Although no longer viable for real mining, the Sapphire Block Erupter USB is still great for learning about ASICs, testing mining pools, and understanding Bitcoin mining. If you enjoy working with old hardware and have one lying around, it’s worth experimenting with!
If you have any questions or want to share your experience, leave a comment below!
-
 @ 3ffac3a6:2d656657
2025-03-08 23:02:13
@ 3ffac3a6:2d656657
2025-03-08 23:02:13Como Rodar um Sapphire Block Erupter USB para Mineração no Linux em 2025
Recentemente, encontrei um Sapphire Block Erupter USB velho aqui em casa que eu usava para minerar Bitcoin em 2013. Por curiosidade e nostalgia, resolvi tentar colocá-lo para funcionar novamente. Passei uma tarde inteira tentando configurar o dispositivo e, depois de muita tentativa e erro, descobri que precisava de uma versão mais antiga do CGMiner para fazê-lo funcionar.
Os Sapphire Block Erupter USB foram um dos primeiros dispositivos ASIC voltados para mineração de Bitcoin. Embora estejam obsoletos para mineração competitiva, eles ainda podem ser usados para aprendizado, nostalgia ou experimentação. Neste post, vou te mostrar como rodar um Block Erupter USB no Linux atualmente.
1. Pré-requisitos
Antes de começar, certifique-se de que você tem:
- Um Sapphire Block Erupter USB
- Um hub USB alimentado (opcional, mas recomendado)
- Um computador rodando Linux (Ubuntu, Debian, Arch ou outra distribuição compatível)
- Um pool de mineração configurado (ex: Slush Pool, KanoPool, etc.)
2. Instalando as Dependências
Antes de rodar o minerador, instale algumas dependências:
bash sudo apt update && sudo apt install -y git build-essential autoconf automake libtool pkg-config libusb-1.0-0-dev3. Determinando a Versão Compatível do CGMiner
Para encontrar a versão correta do CGMiner que ainda suporta os Block Erupter USB, realizei uma busca binária entre diferentes versões, testando cada uma até encontrar a última que reconhecia corretamente o dispositivo. O resultado foi que a versão 3.4.3 é a mais recente que ainda suporta os Block Erupters. No entanto, outras versões desses dispositivos podem requerer versões diferentes do CGMiner.
4. Baixando e Compilando o CGMiner
O CGMiner é um dos softwares compatíveis com os Block Erupters. Você pode baixar a versão correta de duas fontes confiáveis:
- Do repositório oficial: CGMiner v3.4.3 no GitHub
- Alternativamente, deste espelho: CGMiner v3.4.3 no Haven
Para garantir a integridade do arquivo, você pode verificar o hash SHA-256:
3b44da12e5f24f603eeeefdaa2c573bd566c5c50c9d62946f198e611cd55876bAgora, faça o download e extraia:
```bash wget https://github.com/ckolivas/cgminer/archive/refs/tags/v3.4.3.tar.gz
Ou, alternativamente:
wget https://haven.girino.org/3b44da12e5f24f603eeeefdaa2c573bd566c5c50c9d62946f198e611cd55876b.tgz
sha256sum v3.4.3.tar.gz # Confirme que o hash bate
Extraia o arquivo
tar -xvf v3.4.3.tar.gz cd cgminer-3.4.3
Compile o CGMiner
./autogen.sh --enable-icarus make -j$(nproc)
Instale no sistema (opcional)
sudo make install ```
4. Conectando o Block Erupter USB
Plugue o dispositivo na porta USB e verifique se ele foi reconhecido:
bash dmesg | grep USB lsusbVocê deve ver algo como:
Bus 003 Device 004: ID 10c4:ea60 Cygnal Integrated Products, Inc. CP2102 USB to UART Bridge ControllerSe necessário, ajuste as permissões para o dispositivo USB:
bash sudo chmod 666 /dev/ttyUSB05. Configurando e Rodando o CGMiner
Agora, execute o CGMiner apontando para seu pool de mineração:
bash ./cgminer -o stratum+tcp://seu.pool.com:3333 -u seuUsuario -p suaSenhaSe o minerador detectar corretamente o Block Erupter, você verá algo como:
``` [2025-03-08 22:26:45] Started cgminer 3.4.3 [2025-03-08 22:26:45] No devices detected! [2025-03-08 22:26:45] Waiting for USB hotplug devices or press q to quit [2025-03-08 22:26:45] Probing for an alive pool [2025-03-08 22:26:46] Pool 0 difficulty changed to 65536 [2025-03-08 22:26:46] Network diff set to 111T [2025-03-08 22:26:46] Stratum from pool 0 detected new block [2025-03-08 22:27:02] Hotplug: Icarus added AMU 0
```
Conclusão
Apesar de não serem mais viáveis para mineração real, os Sapphire Block Erupter USB ainda são ótimos para aprender sobre ASICs, testar pools e entender mais sobre a mineração de Bitcoin. Se você gosta de hardware antigo e tem um desses guardado, vale a pena experimentar!
Se tiver dúvidas ou quiser compartilhar sua experiência, comente abaixo!
-
 @ ffbcb706:b0574044
2025-03-08 22:51:54
@ ffbcb706:b0574044
2025-03-08 22:51:54I recently switched from stock Android on my Pixel 8 Pro to GrapheneOS and transitioned from Authy to Aegis to move away from Big Tech and embrace open-source and privacy-focused alternatives. While Aegis offers local encrypted backups, I noticed it lacked external automatic sync, and I wanted to be sure that I could still access my 2FA tokens even if I lost my phone, without having to remember to back up Aegis externally every time I added a new 2FA entry.
Additionally, because many commands need to be run in Termux, I found it useful to use Scrcpy to control my Android device from my Ubuntu desktop. Scrcpy requires ADB and allows easy copy-paste functionality between Ubuntu and Android. I used ALT + V in Ubuntu scrcpy and then long-pressed the screen on my Pixel and selected 'Paste' to copy text easily. This is an optional but highly useful method for managing terminal commands efficiently.
This guide will walk you through setting up rclone and Termux:Boot to enable seamless Aegis backup automation on GrapheneOS. While I use GrapheneOS, this setup should work on most modern Android versions.
Prerequisites
Before starting, make sure you have:
- GrapheneOS installed on your Google Pixel Android device (Pixel 8 Pro in my case).
- Aegis Authenticator installed with automatic backup enabled.
- Proton Drive account ready.
- Obtainium installed or an alternative such as F-droid to manage Termux updates securely.
- Termux & Termux:Boot installed via Obtainium:
- Termux: https://github.com/termux/termux-app/releases
- Termux:Boot: https://github.com/termux/termux-boot/releases
- Scrcpy installed (optional, for easier command handling):
- Install on Ubuntu:
sudo apt install scrcpy - Ensure ADB is enabled on your Android device.
Step 1: Install Required Packages and Set Up the Backup Folder
Open Termux and install the required tools:
sh pkg update && pkg upgrade -y pkg install rclone inotify-tools termux-apiGrant storage permissions to Termux:
sh termux-setup-storageCreate the ProtonSync directory where all files to be backed up will be stored, including Aegis backups:
sh mkdir -p /storage/emulated/0/ProtonSync/Aegis/Ensure the directory exists:
sh ls /storage/emulated/0/ProtonSync/Aegis/If this returns an empty result (instead of an error), you are ready to proceed.
Step 2: Configure rclone for Proton Drive
Since August 2024, Proton Drive has been available as a dedicated backend in rclone (official documentation). However, this integration is still evolving, as it relies on a proton-api-bridge that is under active development.
Run:
sh rclone configFollow the prompts:
- Choose "n" for a new remote.
- Name it:
protondrive - Select Proton Drive from the list.
- Enter your Proton username and password.
- If 2FA is enabled, enter the current code from your authenticator app.
- Confirm and save the remote configuration.
Test the setup by listing files:
sh rclone lsd protondrive:If you see your Proton Drive folders, the connection works.
Step 3: Automate Sync with inotify-tools
We will set up a script to monitor new Aegis backup files and sync them instantly.
- Manually trigger a backup in Aegis first, to ensure a file is created. You can do this in Aegis → Settings → Backups → Trigger backup.
- Create the sync script directly in the Termux:Boot directory:
sh mkdir -p ~/.termux/boot/ nano ~/.termux/boot/watch_protonsync.sh- Add this content:
```sh
!/data/data/com.termux/files/usr/bin/bash
inotifywait -m -r -e close_write,moved_to,create /storage/emulated/0/ProtonSync/Aegis/ --format '%w%f' | while read file do rclone sync /storage/emulated/0/ProtonSync/Aegis/ protondrive:/ProtonSync/Aegis/ -P done ```
- Save and exit (
CTRL + X,Y,ENTER). - Make it executable:
sh chmod +x ~/.termux/boot/watch_protonsync.shRun it manually to test:
sh bash ~/.termux/boot/watch_protonsync.sh &Now, whenever Aegis creates a new backup file, it will automatically sync to Proton Drive.
Step 4: Test Auto-Start with Termux:Boot
- Reboot your phone.
- Open Aegis and manually trigger a backup (
Settings → Backups → Trigger backup). - Check Proton Drive under
/ProtonSync/Aegis/to confirm that the new backup appears.
If the file is there, the automation works! 🎉 I would advice to keep an eye regularly at the Proton Drive to check if the automation is still working.
-
 @ 2cb8ae56:84d30cba
2025-03-08 22:41:58
@ 2cb8ae56:84d30cba
2025-03-08 22:41:58[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
[62]
[63]
[64]
-
 @ 15125b37:e89877f5
2025-03-08 22:01:15
@ 15125b37:e89877f5
2025-03-08 22:01:15The story of Bitcoin from genesis to exodus
Welcome to "Becoming One with Bitcoin," a new series inviting you to delve deep into the captivating story of Bitcoin. From its origins in the Cypherpunk movement, the technology that set the stage, to its present and future potential—this journey will unravel Bitcoin’s past, present, and future. Follow closely to explore how this revolutionary digital currency came to be and why it continues to shape the world.
The History of Bitcoin, Part 1: From Cypherpunks to the Genesis Block
The Story of Bitcoin: The Road to the Genesis Block
The creation of Bitcoin in 2009 was not an isolated event but the result of decades of innovation, idealism, and frustration. Bitcoin’s emergence during the depths of the Great Recession and the financial collapse that triggered it was no coincidence. Many of the technologies and philosophies that formed the backbone of Bitcoin had been developed by visionaries and cryptography enthusiasts, but it was the perfect storm of economic turmoil that set the stage for Bitcoin’s release. Let’s explore the journey that led to Bitcoin’s genesis block, from the early work of the Cypherpunks to the breakdown of trust in traditional financial institutions.
The Cypherpunks and the Push for Privacy
Bitcoin’s roots extend back to the Cypherpunk movement of the late 1980s and early 1990s. Cypherpunks, such as David Chaum, Eric Hughes, Tim May, and others, were privacy advocates concerned with government and corporate power over personal information. The Cypherpunks believed cryptography could protect privacy and enable individual freedom in an increasingly digital world. They championed the idea that technology—specifically cryptographic code—could ensure privacy, autonomy, and even freedom from centralized control. Tim May’s Crypto Anarchist Manifesto (1992) laid out a vision for an unregulated digital space where individuals could interact freely, a powerful idea that became a driving force for the movement.
Digital Currency Projects Before Bitcoin
From the 1990s to the early 2000s, Cypherpunks and computer scientists tried to build digital currencies that could offer users privacy and independence, but most of these projects faced major technical or regulatory challenges. Here are some of the key projects that paved the way for Bitcoin:
-
David Chaum’s DigiCash – David Chaum, a cryptographer and Cypherpunk, launched DigiCash in the late 1980s. This private, digital currency used Chaum’s cryptographic protocol to allow users to make secure, untraceable transactions. However, DigiCash was centralized, depending on trust in Chaum’s company, which eventually went bankrupt.
-
Hashcash by Adam Back – In 1997, Adam Back introduced Hashcash, a proof-of-work system aimed at reducing email spam. Hashcash required users to expend computational power to “stamp” emails, making spamming expensive but legitimate communication cheap. This concept would later become Bitcoin’s mining mechanism.
-
B-money by Wei Dai – In 1998, Wei Dai proposed B-money, an anonymous, distributed electronic cash system. Though never implemented, B-money included ideas like decentralized consensus and pseudonymous identities, concepts later foundational to Bitcoin.
-
Bit Gold by Nick Szabo – Nick Szabo created Bit Gold in 2005, a system where users solved cryptographic puzzles and linked each solution to the previous one, forming a “chain” of transactions. Though Bit Gold never launched, Szabo’s work significantly influenced Bitcoin’s proof-of-work blockchain.
While each of these projects contributed to the understanding of cryptographic currency, they lacked the cohesion to achieve true decentralization and resilience.
The Financial Crisis and a Perfect Storm
Bitcoin’s release in January 2009 came as the world was reeling from the 2008 financial crisis. Years of risky mortgage lending and poor regulatory oversight had led to the collapse of the U.S. housing bubble, which spiraled into a full-scale financial meltdown. When major financial institutions like Lehman Brothers failed, stock markets crashed, and millions of people lost their homes and jobs, the world entered what would become known as the Great Recession.
In response, governments stepped in with massive bank bailouts, injecting trillions into the financial system to prevent a complete collapse. However, the bailouts sparked widespread anger as it became clear that the financial elite had been insulated from the consequences of their actions while average citizens bore the economic fallout. Many people saw the bailout as a betrayal, eroding trust in banks, corporations, and governments. The crisis was compounded by a rise in inflation as central banks printed money to stimulate the economy, reducing the purchasing power of the average person.
This situation created fertile ground for an alternative financial system, one that didn’t rely on banks or governments and was resistant to inflation. Into this backdrop, Bitcoin emerged as a decentralized and limited-supply currency, a stark contrast to the inflating fiat currencies and the bailout culture of centralized finance.
The Key Technologies Behind Bitcoin
Several innovations allowed Bitcoin to succeed where previous digital currencies had failed by integrating them into a resilient, secure system:
-
Cryptographic Hash Functions – Cryptographic hashes ensure Bitcoin transactions are secure, irreversible, and tamper-resistant. SHA-256, the hash function used in Bitcoin, transforms transaction data into fixed-length hashes, securing each block and linking it to the previous one in the blockchain.
-
Proof-of-Work (PoW) – Borrowed from Adam Back’s Hashcash, proof-of-work ensures new blocks in Bitcoin’s blockchain are legitimate by requiring miners to solve complex puzzles. PoW prevents double-spending and spam attacks, making it costly for bad actors to manipulate the blockchain.
-
Digital Signatures (ECDSA) – Bitcoin relies on the Elliptic Curve Digital Signature Algorithm (ECDSA) to authenticate users and secure transactions. Public and private keys enable users to sign transactions, proving ownership without revealing private keys.
-
P2P Network Architecture – Bitcoin uses a decentralized peer-to-peer network to distribute the blockchain. Bitcoin nodes independently verify transactions, maintaining a censorship-resistant ledger that can’t be shut down by any single authority.
Satoshi Nakamoto and the Genesis Block
In 2008, Satoshi Nakamoto published the Bitcoin whitepaper, introducing Bitcoin as a “peer-to-peer electronic cash system” designed to fix the flaws of traditional financial systems. Using cryptographic principles, Nakamoto created a currency that could operate without centralized control, allowing users to send and receive payments directly.
On January 3, 2009, Satoshi mined Bitcoin’s first block, the genesis block, embedding a now-famous message: “The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.” This line, referencing a headline from The Times newspaper, was a critique of the traditional financial system, reflecting Bitcoin’s intent as a resilient alternative to inflation-prone fiat currencies and bailout-dependent banks. In this moment, the genesis block symbolized a vision for financial sovereignty, with Bitcoin offering a form of money that anyone, anywhere, could use free from reliance on central banks.
In Summary
The story of Bitcoin is one of resilience, innovation, and idealism, shaped by cryptographers, computer scientists, and privacy advocates who were determined to create a decentralized, censorship-resistant currency. Its timing, born in the aftermath of the financial crisis, was pivotal. Bitcoin was not just a technological breakthrough but a statement against the status quo of centralized finance. As we trace Bitcoin’s journey from the Cypherpunk movement to the genesis block, it becomes clear that Bitcoin’s impact is not just about technology; it’s about the vision of financial freedom and privacy in an age of uncertainty and inflation.
-
-
 @ 401014b3:59d5476b
2025-03-08 20:14:04
@ 401014b3:59d5476b
2025-03-08 20:14:04Alright, football lunatics, it’s March 2025, and we’re storming into the AFC West like it’s a saloon brawl with whiskey on the line. Free agency’s a lawless frontier, the draft’s a roll of the dice, and this division’s always a mix of firepower and flops. The Chiefs owned 2024, the Chargers turned heads, the Broncos showed grit, and the Raiders… uh, raided their own dignity. Let’s slap some records on this rodeo and see who’s got the guts to lasso the crown. Saddle up, fam—here we go.
Kansas City Chiefs: 12-5 – Mahomes’ Dynasty Rolls On
The Chiefs were the AFC’s big dogs in 2024, and 2025’s no different. Patrick Mahomes is still the NFL’s cheat code—Xavier Worthy’s a speed demon, Travis Kelce’s defying Father Time, and the O-line’s a fortress. That defense—Chris Jones, Trent McDuffie—keeps QBs sweating, but free agency’s a buzzkill. The WR depth’s thin. Still, Mahomes magic lands ‘em at 12-5, division champs. KC’s the team everyone loves to hate—and they keep winning anyway.
Los Angeles Chargers: 10-7 – Harbaugh’s Grit Pays Off
The Chargers flipped the script in 2024 under Jim Harbaugh, and they’re building steam. Justin Herbert’s a cannon-armed freak, Ladd McConkey’s emerging, and J.K. Dobbins (if healthy) keeps the run game humming. The defense—Joey Bosa, Derwin James—is a problem when it’s clicking, but free agency looms. Khalil Mack’s getting old, and Asante Samuel Jr. might bolt. 10-7’s the vibe, snagging a wildcard. Harbaugh’s got ‘em believing—they’re legit playoff pests now.
Denver Broncos: 8-9 – Bo Nix’s Baby Steps
The Broncos showed fight in 2024 with rookie Bo Nix, and 2025’s a growth spurt. Nix has Courtland Sutton and Marvin Mims to sling it to, while Javonte Williams grinds the run game. That defense—Pat Surtain II, Zach Allen—is still nasty, but free agency could sting. Jonathon Cooper might cash out elsewhere, and the O-line needs juice. 8-9’s where they land—close, but not quite playoff-ready. Sean Payton’s cooking, but it’s not fully baked yet.
Las Vegas Raiders: 4-13 – Chaos in the Desert
The Raiders are the AFC West’s hot mess. No QB worth a damn (Aidan O’Connell? Please), Davante Adams bailed, and the run game’s a ghost town without Josh Jacobs. The defense—Maxx Crosby, Christian Wilkins—has some bite, but the roster’s a dumpster fire, and free agency won’t help. Tyree Wilson’s unproven, and the cap’s a nightmare. 4-13’s the brutal truth—they’re tanking for a draft savior. Vegas, baby, but not in a good way.
The Final Shootout
The AFC West in 2025 is a Chiefs cakewalk with a Charger chaser. The Chiefs (12-5) lock the title because Mahomes is Mahomes, the Chargers (10-7) snag a wildcard with Harbaugh’s mojo, the Broncos (8-9) tease progress, and the Raiders (4-13) crash and burn. Free agency’s the wild card—lose a star, you’re toast; keep ‘em, you’re riding high. Hit me on Nostr when I screw this up, but this is my AFC West sermon. Let’s roll, degenerates.
-
 @ 8671a6e5:f88194d1
2025-03-08 18:55:02
@ 8671a6e5:f88194d1
2025-03-08 18:55:02The ECB’s Tightrope Walk (2019–2025)
The European Central Bank (ECB) is caught between a rock and a hard place these past years (2019–2025). On one hand, it’s failing its core mission: keeping the Euro stable with a 2% inflation target. On the other, trust in the currency—and the EU itself—is crumbling fast. You can see it in the sinking European bond market and the growing crowd of voters backing anti-EU politicians.
As usual, the ECB sticks to its playbook: blending marketing with “innovations,” spicing it up with anti-crypto MiCA rulings on Bitcoin, and blaming everyone—Putin, Trump, Elon, China, the wind, the moon—for their woes. Since the financial crisis, it’s pumped 2.3 trillion euros into the economy, money conjured out of thin air for market purchases (quantitative easing). The result? Our wallets feel the pinch as purchasing power tanks, with inflation bouncing between 2.1% and 20%, depending on which figures you still trust. No shock there: for every euro circulating in 2002, there are now five.
Meanwhile, Europe’s scrambling to keep up appearances, led by a parliament of nitwits who treat error-riddled high school essays from the Dutch Central Bank as gospel—or print 1 trillion euros (!) to prop up their debt and war cycle. These politicians aren’t too dumb to spot the mistakes; they just care more about ramming through the “narrative,” shaky or not.
The Bitcoin Smokescreen Take the attack on Bitcoin, always nagging about its “energy use”—a standard they never apply elsewhere. Good thing, too; electricity isn’t “good” or “evil.” The real play? Clearing the path for a “digital euro,” cooked up by sly financial institutions hawking their “Aldi Bitcoin” via corporate blockchains.
Digital Euro: The Shiny Trap
Advantages I’ll grudgingly list a few perks, though they’re skin-deep: faster transactions than today’s sluggish bank transfers, digital payments (QR codes), and a unified standard across Europe. These tiny upgrades—great for marketing—don’t outweigh the massive downsides but do beat the current patchwork of payment systems. That’s the good news, and it ends here.
Disadvantages
The cons list is long, so I’ll hit the three worst:
Permission-Coin Nightmare You’ll need approval from some authority (or commercial bank) to receive, spend, or hold it. A 50€ note moves from A to B, no questions asked—cash has no name, needs no permission. Pocket money for your kid, a coin for a beggar, or paying for a used PlayStation: cash flows free. They want that gone. Bitcoin’s beauty mirrors cash but better—unconfiscatable, A to B, no permission needed, saint or crook. That’s the bedrock of a working social-economic system. Sorry, EU pious elite, but white, gray, and black economies will always exist—check your own subsidies; not everything’s clean. Worse, it threatens wage sanctity, potentially reviving forced spending schemes banned since 1887 (in Belgium, at least). Workers once got paid in cash and expiring factory vouchers—a disaster now illegal.
Programmable Tokens A digital euro (CBDC) turns money into controllable tokens, ripe for expiry dates, discounts, or restrictions. Big banks are testing this, aping Bitcoin’s gimmick but under total state control, endlessly minting “safe” tokens for their theft-driven consumer economy. Services like Corda are set to link your ID via eIDAS (Europe’s total-control digital identity surveillance) to these CBDC wallets. Your behavior won’t just be monitored—it’ll tie to fines or coin deductions. (link: https://r3.com/get-corda/ )
Total Control Coin Citizens lose on nearly all fronts. Recall the Belgian Franc-to-Euro shock (cheese sandwich: 40 francs to 1.2 euros, now 3+)? The digital euro rollout—likely hitting welfare recipients and civil servants (with little recourse) via a “gov-app” wallet around July 2025—will sting worse. You’ll get no real money, just controllable vouchers. The ECB won’t program the coins directly; they’ll let banks take the fall. If trust erodes (it will), they’ll blame “greedy banks” or “corrupt third parties.” Cash’s freedom—untraceable, unblockable—dies. The ECB gains tools: negative interest, forced loans, outright theft—all impossible with cash (unless they swap notes, which is slow and costly). Weaponized bank accounts already plague the EU; this makes them worse—shut down sans court order, targeting journalists, dissidents, anyone in the crosshairs.
This isn’t convenience—it’s power. And the ECB’s pushing it despite the euro’s instability. Fabio Panetta once said, “A digital euro would preserve the coexistence of safe central bank money and private money, ensuring sovereign money remains a monetary anchor” (Evolution or Revolution?, Feb 10, 2021). Stability’s key, yet they’re charging ahead anyway. (source)
Conclusion: The Great Heist The CBDC Digital Euro is the greatest theft in Europe since WWII. It’ll shred our freedom, warp market pricing, kill opposition, and chain us financially to the powerful—bank runs impossible. Citizens lose on 9/10 fronts… though payments will be quick. Trust in the Eurozone? It’ll erode faster, propped up only by nudging, marketing, and force.
Citizens will lose out on 9 out of 10 fronts… though, admittedly, payments will be quick.\ The loss in trust in the Eurozone even faster....
AVB\ \ tip if you like this
-
 @ 378562cd:a6fc6773
2025-03-08 16:31:22
@ 378562cd:a6fc6773
2025-03-08 16:31:22The insurance industry is one of the most lucrative businesses in the world, built on a foundation of fear, deception, and manipulation. It presents itself as a guardian of financial security, promising protection in times of crisis. However, in practice, it operates like a government-backed extortion scheme, siphoning money from individuals and businesses while finding ways to avoid paying out claims.
Many people view insurance as a necessary evil—a required expense for responsible living. But very few stop to consider the true nature of the industry and how it functions not as a service, but as a well-oiled criminal machine designed to extract wealth from the population while delivering as little value as possible.
A Business Model Built on Exploiting Fear and Uncertainty Insurance companies do not sell a product in the traditional sense. You don’t receive something tangible in return for your payments. Instead, they sell you a promise that if something terrible happens, they will be there to cover the costs. However, that promise is deliberately wrapped in vague legalese, riddled with loopholes, and ultimately designed to benefit the insurer more than the insured.
To make this scam even more effective, insurance companies exploit human psychology, knowing that fear is one of the strongest motivators. They bombard people with relentless messaging about the catastrophic risks of being uninsured—the dangers of driving without auto insurance, the financial ruin of an unexpected hospital visit, or the devastation of losing a home to a fire or natural disaster. Ask your local insurance person (if you think they would give you an honest answer) how many full payouts they have had to give out due to a complete loss over the past year, 5 years, since they have been selling insurance. You'd be amazed at how few that number really is.
But it doesn’t stop there. Other industries have caught on to this fear-driven strategy and now use insurance as the perfect scapegoat to justify absurdly inflated prices. Hospitals, auto manufacturers, homebuilders, and repair services all point to “rising insurance costs” among other things as the reason for their skyrocketing fees. A simple medical procedure that should cost a few hundred dollars now runs into the several thousands because “that’s what insurance pays.” Auto repairs that used to be affordable are now exorbitant because shops know insurers will cover part of the bill. The end result? A rigged system where businesses get richer while consumers pay more, not just in premiums, but in every aspect of life.
The truth? Insurance companies thrive on the fact that most policyholders will never need to file a major claim, and if they do, the company will do everything in its power to pay out as little as possible—or nothing at all.
The Three D’s: Deny, Delay, Defend
When it comes time for an insurance company to actually pay out a claim, they rarely do so without a fight. Instead, they deploy the Three D’s strategy—a well-documented tactic used to minimize payouts and maximize profits:
Deny the Claim – The first step is simple: find a reason, any reason, to reject your claim.
Did you miss a payment once five years ago? Denied.
Did you fail to report a minor detail when signing up for your policy? Denied.
Did they discover a tiny, unrelated pre-existing condition? Denied.
Delay the Payout – If they can’t outright deny your claim, the next step is to make the process as slow and painful as possible.
Endless paperwork requirements. Requests for additional documentation (often things that were already submitted). Long hold times when you call for an update. The goal? Wear you down so you give up or settle for less.
Defend Against Lawsuits – If you decide to take legal action, the company will unleash an army of high-priced attorneys (another equally criminal organization with the same rules and laws applied) to fight you every step of the way.
They have billions of dollars available for legal fees. They will outlast you, knowing that most individuals lack the time, money, or energy to engage in a lengthy legal battle. This cycle repeats daily, with millions of policyholders becoming victims of the very companies they’ve paid to protect them. Where is the legal protection to protect you and me? NON-EXISTENT FARSE!
The Myth of the “Struggling” Insurance Agent Insurance agents like to present themselves as hard-working individuals, just trying to make a living. They’ll tell you they’re not getting rich and that they only want what’s best for you. But make no mistake—there is no such thing as a "barely making it" insurance agent in the long run. Mine is constantly on FB telling of this trip to Mexico or some exotic island somewhere or someplace I would love to take my family someday but can never seem to afford it time or money.
Agents work on commission, meaning their income is tied directly to the number of policies they sell. This creates an incentive to push as many policies as possible, often using manipulative tactics.
They will upsell coverage you don’t need by playing on your fears. They will gloss over exclusions and fine print, ensuring you only focus on the benefits, not the limitations. They will push you into long-term commitments that make it costly to switch or cancel and have the "adjustor" and "company policy" as an scapegoat to ease their own conscience.
Meanwhile, at the top, insurance executives make obscene amounts of money while denying rightful claims to hard-working individuals. The CEOs of major insurance companies bring in tens of millions of dollars per year, all while raising premiums and reducing coverage for their customers.
Mandatory Insurance: A Government-Backed Extortion Scheme One of the most damning aspects of the insurance industry is how it has embedded itself into government policy, ensuring that people have no choice but to participate in the system.
Car Insurance: Nearly every state requires auto insurance, even though the majority of drivers never file a claim. Meanwhile, insurance companies raise rates even if you never get into an accident. Health Insurance: The government forces people to buy into overpriced health insurance plans that come with absurd deductibles, making them nearly useless for many policyholders. Home Insurance: Mortgage lenders force homeowners to carry insurance, ensuring another guaranteed revenue stream for the industry. These laws do not exist to protect consumers—they exist to guarantee profits for the insurance companies.
Who Really Benefits? Follow the Money
The biggest winners in the insurance industry are not the policyholders that provide ALL THE MONEY into this criminal organization. The true beneficiaries are the corporate executives and shareholders, and it funnels down to the individual agents collecting all this for them.
The largest insurance companies report billions of dollars in annual profits—far more than they pay out in claims. Shouldn't they break even after a 'modest" salary for their service and time? Wouldn't THAT make more sense to a sensible human being? They invest premium dollars into the stock market, real estate, and other ventures, ensuring their wealth (the money YOU gave them) continues to grow.
They lobby politicians to maintain their stranglehold on the industry, keeping regulations in their favor and ensuring insurance remains legally required in most aspects of life. In short, insurance companies are not in the business of helping people—they are in the business of making money.
The Harsh Reality: A System Designed to Exploit Most people will pay hundreds of thousands of dollars in insurance premiums throughout their lifetime. And yet, when the time comes to actually use the coverage, many find themselves fighting an uphill battle against a rigged system.
Consider these facts:
Insurance companies cancel policies when people become too “expensive.” They increase rates after a single claim—even if it wasn’t your fault. They spend billions on advertising to attract new customers but fight tooth and nail to avoid paying out existing ones. At what point does this stop being a service and start being a scam?
Final Thoughts: A Broken System That Needs an Overhaul
The insurance industry presents itself as a pillar of stability, but in reality, it is one of the most corrupt, exploitative industries in the world. It thrives by preying on fear, avoiding payouts, and ensuring government policies force people to participate in the scam.
If the system was truly fair, it would operate like mutual aid, where all policyholders contribute and receive support as needed. But instead, it functions like organized crime, where the ones collecting the money hold all the power, and those in need are left scrambling for scraps.
Until a major upheaval occurs, there’s little the average person can do to fight back against this deeply entrenched system. The harsh reality is that there are far too many crooks, manipulators, and dishonest players at every level of society—from corporate executives to politicians, from insurance adjusters to business owners who have happily joined in on the scam.
Reading the fine print won’t stop an industry designed to change the rules whenever it benefits them. Shopping around is meaningless when every company is playing the same rigged game. Demanding transparency? Good luck—those in power have built entire careers around keeping consumers in the dark.
At the end of the day, insurance companies—and the industries that now use them as an excuse to inflate costs—are not here to protect you. They exist to extract wealth from you, and there’s no real way to “win” in a system engineered to ensure you always lose.
-
 @ a012dc82:6458a70d
2025-03-08 10:26:25
@ a012dc82:6458a70d
2025-03-08 10:26:25The advent of Bitcoin introduced the world to a new form of digital gold, promising wealth and innovation through the marvels of blockchain technology. However, as the cryptocurrency landscape has evolved, so too have the implications of its underlying processes, particularly Bitcoin mining. In Granbury, Texas, a community has found itself at the intersection of technological advancement and environmental distress, embodying a growing concern over the real-world impacts of digital currencies. This narrative is not unique to Granbury but echoes across various locales globally, where the quest for digital wealth intersects with the fabric of everyday life, often at a cost not initially anticipated.
Table of Contents
-
The Heart of the Matter: Granbury's Plight
-
The Noise That Never Sleeps
-
A Community's Health at Stake
-
-
The Economics of Bitcoin Mining
- The Cost of Digital Wealth
-
Regulatory Responses and Community Action
- Seeking Solutions
-
The Future of Bitcoin Mining and Community Well-be …
- Sustainable Alternatives
-
Conclusion
-
FAQs
The Heart of the Matter: Granbury's Plight
Granbury, a small town in Texas, has become an unwilling host to the cacophony of Bitcoin mining. A local power plant, repurposed for the energy-intensive task of mining Bitcoin, has disrupted the lives of residents with its relentless noise. The sound, likened to the continuous roar of jet engines, penetrates the tranquility of this community, leaving in its wake sleepless nights, health issues, and a disturbed local ecosystem. This intrusion represents a broader dilemma faced by communities worldwide, where the benefits of technological progress clash with the sanctity of personal and environmental well-being.
The Noise That Never Sleeps
Cheryl Shadden, a nurse anesthetist living in Granbury, describes the noise as akin to sitting on an airport runway with jets taking off in succession. The constant hum has made simple pleasures like conversations on the back patio impossible, highlighting the intrusive nature of the mining operation. This relentless noise pollution is not just a minor inconvenience but a significant disruption to daily life, affecting everything from personal relationships to the simple enjoyment of one's home. The situation in Granbury sheds light on the often-overlooked consequences of industrial activities, prompting a reevaluation of what progress means at the expense of quality of life.
A Community's Health at Stake
The incessant din has not only stolen peace but has also been linked to physical ailments among the residents. Reports of migraines, sleep disturbances, and even wildlife fleeing the area paint a grim picture of the toll taken on the community's health and well-being. These health issues are a stark reminder of the environmental cost of our digital age, where the pursuit of innovation can sometimes lead to unforeseen consequences. The plight of Granbury's residents underscores the need for a balanced approach to technological development, one that considers the health and happiness of communities as a measure of success.
The Economics of Bitcoin Mining
Bitcoin mining, the process by which new bitcoins are entered into circulation and transactions are verified, is notoriously energy-hungry. It relies on a proof-of-work system that requires extensive computational power and, consequently, a significant amount of electricity. Texas, with its cheap energy and land, has become a global hub for these operations, attracting companies with the promise of low overhead costs. This economic boon, however, comes with its own set of challenges, as the environmental and social costs begin to surface in communities like Granbury.
The Cost of Digital Wealth
While Bitcoin mining has been lauded for its potential economic benefits, including job creation and investment, the case of Granbury reveals a darker side. The operation consumes approximately 2,100 megawatts of Texas's power supply, raising concerns about carbon and noise pollution, as well as increased utility bills for consumers. The juxtaposition of economic gain against environmental and social loss presents a complex dilemma. It raises critical questions about the sustainability of such ventures and the true cost of digital wealth in the age of cryptocurrency.
Regulatory Responses and Community Action
The situation in Granbury has sparked a dialogue on the need for regulatory oversight. Texas state law currently offers little recourse for noise pollution, with the maximum penalty for exceeding noise limits set at a mere $500 fine. This inadequacy has prompted local officials and residents to seek alternative solutions, including the construction of a sound barrier wall, which, paradoxically, has amplified the noise in some areas. The struggle for regulatory solutions reflects a broader challenge in governing emerging technologies and industries, where existing frameworks often fall short of addressing new and unforeseen impacts.
Seeking Solutions
In response to growing complaints, Marathon Digital Holdings, the company behind the Granbury mining operation, has pledged to conduct a sound study and take over full control of the mine to address community concerns. However, the effectiveness of these measures remains to be seen, and the community's frustration is palpable. This scenario highlights the importance of corporate responsibility and the need for companies to engage with and address the concerns of the communities in which they operate. It also underscores the potential for innovative solutions to mitigate the negative impacts of such operations, fostering a more harmonious relationship between industry and community.
The Future of Bitcoin Mining and Community Well-being
The case of Granbury serves as a cautionary tale of the unintended consequences of Bitcoin mining. As the cryptocurrency industry continues to grow, the balance between technological progress and environmental sustainability becomes increasingly precarious. This tension between innovation and well-being calls for a reimagined approach to technological development, one that prioritizes the health of our communities and the planet.
Sustainable Alternatives
The outcry from Granbury and similar communities across the country underscores the urgent need for sustainable mining practices. Alternatives such as proof-of-stake, a less energy-intensive consensus mechanism, offer a glimpse into a possible future where digital currencies can coexist with environmental stewardship. These alternatives not only represent a technical evolution but also a philosophical shift towards a more sustainable and equitable digital economy.
Conclusion
The story of Granbury is a microcosm of a larger debate on the impact of digital currencies on our physical world. As we venture further into the age of cryptocurrency, the challenge lies in harnessing its potential for economic growth without sacrificing the health and well-being of our communities. The digital gold rush must not lead to audible grief; instead, it should pave the way for innovations that are both economically beneficial and environmentally responsible. The journey from digital gold to a future where technology and nature harmonize requires not just technological innovation, but a collective commitment to redefining progress.
FAQs
How does Bitcoin mining affect local communities? Local communities, like Granbury, can experience noise pollution, increased electricity consumption leading to higher utility bills, potential environmental impacts due to increased energy use, and health issues among residents such as sleep disturbances and migraines.
What are the economic benefits of Bitcoin mining? Economic benefits include job creation, investment in local infrastructure, and increased demand for local services. However, these benefits often come with environmental and social costs that need to be carefully managed.
What measures are being taken to address the concerns of Granbury residents? Measures include the construction of sound barrier walls, conducting sound studies, and engaging with the community to find solutions. Companies like Marathon Digital Holdings are also taking steps to take over full control of mining operations to better address noise issues.
Are there sustainable alternatives to proof-of-work Bitcoin mining? Yes, alternatives such as proof-of-stake (PoS) are being explored and implemented in various cryptocurrencies. PoS is less energy-intensive and could potentially offer a more sustainable option for securing blockchain networks without the significant environmental impact of traditional mining.
How is the Texas government responding to the issue of Bitcoin mining noise pollution? The response includes monitoring noise levels and exploring legal and regulatory measures to manage the impact of mining operations. However, existing laws offer limited recourse, and there is ongoing discussion about the need for more effective regulations.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ da0b9bc3:4e30a4a9
2025-03-08 07:03:33
@ da0b9bc3:4e30a4a9
2025-03-08 07:03:33Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/907271
-
 @ 220522c2:61e18cb4
2025-03-08 06:19:30
@ 220522c2:61e18cb4
2025-03-08 06:19:30Comet is available on Linux

The Comet longform desktop app is available as an AppImage for Linux.
linux
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ 220522c2:61e18cb4
2025-03-08 03:51:09
@ 220522c2:61e18cb4
2025-03-08 03:51:09Enable trackpad pinch zoom for Brave on Linux
-
Open Brave: Launch the Brave browser.
-
Access Flags: Type brave://flags in the address bar and press Enter.
-
Search for Ozone Platform:In the search bar at the top, type ozone.
-
Find
Preferred Ozone platform -
Set it to
Wayland -
Done
-
-
 @ c3ae4ad8:e54d46cb
2025-03-08 03:38:15
@ c3ae4ad8:e54d46cb
2025-03-08 03:38:15This is for one serving (I'm currently doing a >500 cal low carb meal plan). Next time, I'll scramble an egg in there to up the protein a little more. High-protein, low-carb stir fry made with turkey, broccoli, snow peas, green onions, savoy cabbage, bok choy, garlic, in a sesame, soy and ginger sauce.
INGREDIENTS
- 1/3 lb / 170g ground turkey (I used 93% lean, hormone-free/organic)
- 2 tsp light olive oil or coconut oil
- 3 TB soy sauce, tamari, or coconut aminos
- 1 cup / 85g mixed stir fry greens, your choice (cabbage, bok choy, etc.)
- Half a bunch of green onion, roughly chopped, green parts only
- Dash of crushed red pepper flakes
- 1 clove minced garlic
- 1 tsp minced ginger
- Sesame seeds (optional, black, regular, or both!)
- 1 tsp sesame oil
DIRECTIONS
1. Heat oil in a skillet and add the ground turkey once the oil starts to shimmer.
2. On medium-high heat, cook the ground turkey, breaking it into bite-size pieces as it cooks, drizzling 1 TB of the soy sauce over the meat a little at a time. You want to evaporate the water out of the meat, so keep letting it cook until it's actually browned—the soy sauce helps with this, but you want the milliard reaction here (look it up and thank me later)!
3. Decrease the heat to low. Push the cooked turkey to one side and tilt the pan a bit away from you so the oil is isolated, and add the garlic into the oil and stir it in there a little bit.
4. Once the garlic is fragrant, stir the meat back into the garlic, toss in the chopped veggies, green onions, and remaining 1 TB of soy sauce. Then add the minced ginger and red pepper flakes on top, and quickly cover the pan with a lid. Let it steam for about 6-8 minutes on medium-low heat.
5. After the veggies are cooked, stir the little pile of steamed ginger into the mix, drizzle the sesame seed oil over the meat and veggies, stir again, and serve hot with optional sesame seeds as a garnish. Enjoy!
For more food and recipes by me, visit https://ketobeejay.npub.pro/ and click on "recipes" at the top
-
 @ 7b3f7803:8912e968
2025-03-08 03:05:16
@ 7b3f7803:8912e968
2025-03-08 03:05:16Libertarians believe in open borders in theory. In practice, open borders don't work, because, among other things, the combination with a welfare state creates a moral hazard, and the least productive of society end up within the borders of welfare states and drain resources. The social services are paid by the productive people of the country or, in the case of most fiat systems, by currency holders through inflation. Welfare states are much more likely under fiat money and the redistribution goes from native taxpayers to illegal immigrants. Thus, under fiat money, open borders end up being an open wound by which the productive lifeblood of the country bleeds out, despite the theoretical trade-efficiency benefits. As libertarians like to say, open borders and the welfare state don't mix. In this article, we'll examine the other sacred cow of libertarian thought: free trade.
Free Trade without Libertarian Ideals
Free trade is very similar to free movement of labor in that it works great in theory, but not in practice, especially under fiat money. In a libertarian free-market world, free trade works. But that assumes a whole host of libertarian ideals like sound money, non-interfering governments, and minimal aggression. Once those ideals are violated, such as with government intervention in the market, similar moral hazards and long-term costs come with them, making free trade about as libertarian as a fractional reserve bank.
An example will illustrate what I'm talking about. Let's say Portugal subsidizes their wine for export to other countries. The obvious first-order effect is that it makes Portuguese wine cheaper in France, perhaps undercutting the price of French wine. Libertarians would say, that's great! French customers get cheaper goods, so what's the problem?
As with any government intervention, there are significant second- and third-order effects in play. Subsidization puts unsubsidized companies at risk, perhaps driving them to bankruptcy. In this case, this might be a French wine maker. Subsidized companies may become zombies instead of dying out. In this case, this might be a Portuguese wine maker that was failing domestically but survives by selling to customers abroad with government subsidies. While French customers benefit in the short run with cheaper prices for wine, they are ultimately hurt because the goods that would have existed without government intervention never come to market. Perhaps French wine makers that went bankrupt were innovating. Perhaps the resources of the zombie Portuguese wine maker would have created something better.
Further, the dependency of French people on Portuguese wine means that something going wrong in Portugal, like a war or subsidy cuts, disrupts the supply and price of wine for France. Now France must meddle in Portugal internationally if it doesn't want the wine supply to get disrupted. The two countries get entangled in such a way as to become more interventionist internationally. A war involving Portugal now suddenly becomes France's business and incentivizes military aid or even violence. As usual, the unseen effects of government policy are the most pernicious.
Not Really Free
In other words, what we call free trade isn't really free trade. A country exporting to the US may subsidize their products through government intervention, making the product cheaper in the US. This hurts US companies, and they’re forced into choices they never would have had to face without the foreign government intervention. But because the good is crossing borders under the rubric of "free trade," it's somehow seen as fair. Of course it's not, as government intervention distorts the market whether it's done by our own government or a foreign government.
So why would a foreign government do this? It gets several benefits through targeted market manipulation. First, it makes its own companies' products more popular abroad and conversely, makes US companies' products less popular. This has the dual benefit of growing the foreign government’s firms and shrinking, perhaps bankrupting, the US ones.
Targeted subsidization like this can lead to domination under free trade. It's not unlike the Amazon strategy of undercutting everyone first and using the monopoly pricing power at scale once everyone else has bankrupted. The global monopoly is tremendously beneficial to the country that has it. Not only is there significant tax revenue over the long term, but also a head start on innovations within that industry and an advantage in production in the adjacent industries around the product.
Second, the manufacturing centralization gives that country leverage geo-politically. A critical product that no one else manufactures means natural alliances with the countries that depend on the product, which is especially useful for smaller countries like Taiwan. Their chip manufacturing industry, holding 60% of global supply (2024), has meant that they're a critical link for most other countries, and hence, they can use this fact to deter Chinese invasion.
Third, because of the centralization of expertise, more innovations, products, and manufacturing will tend to come within the country. This increased production has cascading benefits, including new industries and national security. China leads the world in drone technology, which undoubtedly has given it an innovation advantage for its military, should it go to war.
Fourth, the capital that flows into the country for investing in the monopolized industry will tend to stay, giving the country more wealth in the form of factories, equipment, and skills. While that capital may nominally be in the hands of foreigners, over time, the ownership of that industry will inevitably transition toward native locals, as the knowledge about how to run such industries gets dissipated within the country.
[Image: Map showing “China Drone Tech” and “Taiwan Chips” hubs, with arrows of capital flow staying local]
Currency Devaluation: The Universal Trade Weapon
It would be one thing if only a specific industry were singled out for government subsidies and then the products dumped into the US as a way to hurt US companies, as that would limit the scope of the damage. But with currency devaluation, a government can subsidize all of its exports at the same time. Indeed, this is something that many countries do. While short-term, this helps US consumers, it hurts US companies and forces them into decisions that aren't good for the US.
To compete, they have to lower costs by using the same devalued currency to pay their labor as their foreign competition. That is, by relocating their capital, their manufacturing, and even their personnel to the country that's devaluing the currency. Not only does relocating reduce labor cost, but it also often gets them benefits like tax breaks. This makes US companies de facto multinationals and not only makes them subject to other jurisdictions, but ultimately divides their loyalties. To take advantage of the reduced labor, capital must move to another country and, along with it, future innovation.
Such relocations ultimately leave the company stripped of their manufacturing capability in the US, as local competition will generally fare better over the long run. Much of the value of the industry then is captured by other governments in taxes, development, and even state-owned companies. Free trade, in other words, creates a vulnerability for domestic companies as they can be put at a significant disadvantage compared to foreign counterparts.
Hidden Effects of Foreign Intervention
Unlike the multinationals, small companies have no chance as they're not big enough to exploit the labor arbitrage. And as is usual in a fiat system, they suffer the most while the giant corporations get the benefits of the supposed "free trade". Most small companies can't compete, so we get mostly the bigger companies that survive.
The transition away from domestic manufacturing necessarily means significant disruption. Domestic workers are displaced and have to find new work. Factories and equipment either have to be repurposed or rot. Entire communities that depended on the manufacturing facility now have to figure out new ways to support themselves. It's no good telling them that they can just do something else. In a currency devaluation scenario, most of the manufacturing leaves and the jobs left are service-oriented or otherwise location-based, like real estate development. There's a natural limit to location-based industries because the market only grows with the location that you're servicing. Put another way, you can only have so many people give haircuts or deliver packages in a geographic area. There has to be some manufacturing of goods that can be sold outside the community, or the community will face scarce labor opportunities relative to the population.
You also can't say the displaced workers can start some other manufacturing business. Such businesses will get out-competed on labor by the currency-devaluing country, so there won't be much investment available for such a business, and even if there were, such a business would be competing with its hands tied behind its back. So in this scenario, what you end up with are a large pool of unemployed people whom the state subsidizes with welfare.
So when a US company leaves or goes bankrupt due to a foreign government's subsidies, the disruption alone imposes a significant short-term cost with displaced labor, unused capital goods, and devastated communities.
Mitigations
So how do countries fight back against such a devastating economic weapon? There are a few ways countries have found around this problem of currency devaluation under free trade. First, a country can prevent capital from leaving. This is called capital controls, and many countries, particularly those that manufacture a lot, have them. Try to get money, factories, or equipment out of Malaysia, for example, and you'll find that they make it quite difficult. Getting the same capital into the country, on the other hand, faces few restrictions. Unfortunately, the US can't put in capital controls because dollars are its main export. It is, after all, the reserve currency of the world.
Second, you can compete by devaluing your own currency. But that’s very difficult because it requires printing a lot of dollars, and that causes inflation. There's also no guarantee that a competing country doesn't devalue its currency again. The US is also in a precarious position as the world's reserve currency, so devaluing the currency more than it already does will make other holders of the dollar less likely to want to hold it, threatening the reserve currency status.
So the main two mitigations against currency devaluation in a free trade scenario are not available to the US. So what else is there? The remaining option is to drop free trade. The solution, in other words, is to add tariffs. This is how you can nullify the effects of foreign government intervention, by leveling the playing field for US manufacturers.
Tariffs
One major industry that's managed to continue being manufactured in the US despite significant foreign competition is cars. Notably, cars have a tariff, which incentivizes their manufacture in the US, even for foreign car makers. The tariff has acted as a way to offset foreign government subsidies and currency debasement.
The scope of this one industry for the US is huge. There are around 300,000 direct jobs in auto assembly within the US (USTR) and there are an additional 3 million jobs supplying these manufacturers within the US. But the benefits don't end there. The US is also creating a lot of innovation around cars, such as self-driving and plug-in electric cars. There are many countries that would love to have this industry for themselves, but because of tariffs, auto manufacturing continues in the US.
And though tariffs are seen as a tax on consumers, US car prices are cheap relative to the rest of the world. What surprises a lot of people when they move from the US to other countries is finding out that the same car often costs more abroad (e.g. 25% tariffs keep U.S. prices 20% below Europe’s $40K average, 2024). The downside of tariffs pales next to the downsides of "free trade."
Free Trade Doesn’t Work with Fiat Money
The sad reality is that while we would love for free trade to work in the ideal libertarian paradise, it won't in our current fiat-based system. The subsidization by foreign governments to bankrupt US companies or to make them multinational, combined with the unfortunate reality of the US dollar being the world reserve currency, means that free trade guts the US of manufacturing. Tariffs are a reasonable way to protect US manufacturers, particularly smaller ones that can't go multinational.
What's more, tariffs make the US less fragile and less dependent on international supply chains. Many of the wars in the past 60 years have been waged because of the entanglements the US has with other countries due to the reliance on international supply chains. Lessening this dependency, if only to prevent a war, has clear value.
Lastly, labor has been devalued significantly by fiat monetary expansion, but at least some of that can be recovered if tariffs create more manufacturing, which in turn adds to the demand for labor. This should reduce the welfare state as more opportunities are made available and fewer unemployed people will be on the rolls.
Conclusion
Fiat money produces a welfare state, which makes open borders unworkable. Fiat money also gives foreign governments a potent economic weapon to use against US companies, and by extension the labor force that powers them. Though currency debasement and capital controls are available to other countries as a defense, for the US, neither of these tools is available due to the fact that the dollar is the world reserve currency. As such, tariffs are a reasonable defense against the fiat subsidization of foreign governments.
-
 @ 7b3f7803:8912e968
2025-03-08 02:28:40
@ 7b3f7803:8912e968
2025-03-08 02:28:40 Libertarians believe in open borders in theory. In practice, open borders don’t work, because, among other things, the combination with a welfare state creates a moral hazard, and the least productive of society end up within the borders of welfare states and drain resources. The social services are paid by the productive people of the country or, in the case of most fiat systems, by currency holders through inflation. Welfare states are much more likely under fiat money and the redistribution goes from native taxpayers to illegal immigrants. Thus, under fiat money, open borders end up being an open wound by which the productive lifeblood of the country bleeds out, despite the theoretical trade-efficiency benefits. As libertarians like to say, open borders and the welfare state don’t mix. In this article, we’ll examine the other sacred cow of libertarian thought: free trade.
Libertarians believe in open borders in theory. In practice, open borders don’t work, because, among other things, the combination with a welfare state creates a moral hazard, and the least productive of society end up within the borders of welfare states and drain resources. The social services are paid by the productive people of the country or, in the case of most fiat systems, by currency holders through inflation. Welfare states are much more likely under fiat money and the redistribution goes from native taxpayers to illegal immigrants. Thus, under fiat money, open borders end up being an open wound by which the productive lifeblood of the country bleeds out, despite the theoretical trade-efficiency benefits. As libertarians like to say, open borders and the welfare state don’t mix. In this article, we’ll examine the other sacred cow of libertarian thought: free trade.Free Trade without Libertarian Ideals
 Free trade is very similar to free movement of labor in that it works great in theory, but not in practice, especially under fiat money. In a libertarian free-market world, free trade works. But that assumes a whole host of libertarian ideals like sound money, non-interfering governments, and minimal aggression. Once those ideals are violated, such as with government intervention in the market, similar moral hazards and long-term costs come with them, making free trade about as libertarian as a fractional reserve bank.
Free trade is very similar to free movement of labor in that it works great in theory, but not in practice, especially under fiat money. In a libertarian free-market world, free trade works. But that assumes a whole host of libertarian ideals like sound money, non-interfering governments, and minimal aggression. Once those ideals are violated, such as with government intervention in the market, similar moral hazards and long-term costs come with them, making free trade about as libertarian as a fractional reserve bank.An example will illustrate what I’m talking about. Let’s say Portugal subsidizes their wine for export to other countries. The obvious first-order effect is that it makes Portuguese wine cheaper in France, perhaps undercutting the price of French wine. Libertarians would say, that’s great! French customers get cheaper goods, so what’s the problem?
As with any government intervention, there are significant second- and third-order effects in play. Subsidization puts unsubsidized companies at risk, perhaps driving them to bankruptcy. In this case, this might be a French wine maker. Subsidized companies may become zombies instead of dying out. In this case, this might be a Portuguese wine maker that was failing domestically but survives by selling to customers abroad with government subsidies. While French customers benefit in the short run with cheaper prices for wine, they are ultimately hurt because the goods that would have existed without government intervention never come to market. Perhaps French wine makers that went bankrupt were innovating. Perhaps the resources of the zombie Portuguese wine maker would have created something better.
Further, the dependency of French people on Portuguese wine means that something going wrong in Portugal, like a war or subsidy cuts, disrupts the supply and price of wine for France. Now France must meddle in Portugal internationally if it doesn’t want the wine supply to get disrupted. The two countries get entangled in such a way as to become more interventionist internationally. A war involving Portugal now suddenly becomes France’s business and incentivizes military aid or even violence. As usual, the unseen effects of government policy are the most pernicious.
Not Really Free
 In other words, what we call free trade isn’t really free trade. A country exporting to the US may subsidize their products through government intervention, making the product cheaper in the US. This hurts US companies, and they’re forced into choices they never would have had to face without the foreign government intervention. But because the good is crossing borders under the rubric of “free trade,” it’s somehow seen as fair. Of course it’s not, as government intervention distorts the market whether it’s done by our own government or a foreign government.
In other words, what we call free trade isn’t really free trade. A country exporting to the US may subsidize their products through government intervention, making the product cheaper in the US. This hurts US companies, and they’re forced into choices they never would have had to face without the foreign government intervention. But because the good is crossing borders under the rubric of “free trade,” it’s somehow seen as fair. Of course it’s not, as government intervention distorts the market whether it’s done by our own government or a foreign government.So why would a foreign government do this? It gets several benefits through targeted market manipulation. First, it makes its own companies’ products more popular abroad and conversely, makes US companies’ products less popular. This has the dual benefit of growing the foreign government’s firms and shrinking, perhaps bankrupting, the US ones.
Targeted subsidization like this can lead to domination under free trade. It’s not unlike the Amazon strategy of undercutting everyone first and using the monopoly pricing power at scale once everyone else has bankrupted. The global monopoly is tremendously beneficial to the country that has it. Not only is there significant tax revenue over the long term, but also a head start on innovations within that industry and an advantage in production in the adjacent industries around the product.
Second, the manufacturing centralization gives that country leverage geo-politically. A critical product that no one else manufactures means natural alliances with the countries that depend on the product, which is especially useful for smaller countries like Taiwan. Their chip manufacturing industry, holding 60% of global supply (2024), has meant that they’re a critical link for most other countries, and hence, they can use this fact to deter Chinese invasion.
Third, because of the centralization of expertise, more innovations, products, and manufacturing will tend to come within the country. This increased production has cascading benefits, including new industries and national security. China leads the world in drone technology, which undoubtedly has given it an innovation advantage for its military, should it go to war.
Fourth, the capital that flows into the country for investing in the monopolized industry will tend to stay, giving the country more wealth in the form of factories, equipment, and skills. While that capital may nominally be in the hands of foreigners, over time, the ownership of that industry will inevitably transition toward native locals, as the knowledge about how to run such industries gets dissipated within the country.
Currency Devaluation: The Universal Trade Weapon
 It would be one thing if only a specific industry were singled out for government subsidies and then the products dumped into the US as a way to hurt US companies, as that would limit the scope of the damage. But with currency devaluation, a government can subsidize all of its exports at the same time. Indeed, this is something that many countries do. While short-term, this helps US consumers, it hurts US companies and forces them into decisions that aren’t good for the US.
It would be one thing if only a specific industry were singled out for government subsidies and then the products dumped into the US as a way to hurt US companies, as that would limit the scope of the damage. But with currency devaluation, a government can subsidize all of its exports at the same time. Indeed, this is something that many countries do. While short-term, this helps US consumers, it hurts US companies and forces them into decisions that aren’t good for the US.To compete, they have to lower costs by using the same devalued currency to pay their labor as their foreign competition. That is, by relocating their capital, their manufacturing, and even their personnel to the country that’s devaluing the currency. Not only does relocating reduce labor cost, but it also often gets them benefits like tax breaks. This makes US companies de facto multinationals and not only makes them subject to other jurisdictions, but ultimately divides their loyalties. To take advantage of the reduced labor, capital must move to another country and, along with it, future innovation.
Such relocations ultimately leave the company stripped of their manufacturing capability in the US, as local competition will generally fare better over the long run. Much of the value of the industry then is captured by other governments in taxes, development, and even state-owned companies. Free trade, in other words, creates a vulnerability for domestic companies as they can be put at a significant disadvantage compared to foreign counterparts.
Hidden Effects of Foreign Intervention
Unlike the multinationals, small companies have no chance as they’re not big enough to exploit the labor arbitrage. And as is usual in a fiat system, they suffer the most while the giant corporations get the benefits of the supposed “free trade”. Most small companies can’t compete, so we get mostly the bigger companies that survive.
The transition away from domestic manufacturing necessarily means significant disruption. Domestic workers are displaced and have to find new work. Factories and equipment either have to be repurposed or rot. Entire communities that depended on the manufacturing facility now have to figure out new ways to support themselves. It’s no good telling them that they can just do something else. In a currency devaluation scenario, most of the manufacturing leaves and the jobs left are service-oriented or otherwise location-based, like real estate development. There’s a natural limit to location-based industries because the market only grows with the location that you’re servicing. Put another way, you can only have so many people give haircuts or deliver packages in a geographic area. There has to be some manufacturing of goods that can be sold outside the community, or the community will face scarce labor opportunities relative to the population.
You also can’t say the displaced workers can start some other manufacturing business. Such businesses will get out-competed on labor by the currency-devaluing country, so there won’t be much investment available for such a business, and even if there were, such a business would be competing with its hands tied behind its back. So in this scenario, what you end up with are a large pool of unemployed people whom the state subsidizes with welfare.
So when a US company leaves or goes bankrupt due to a foreign government’s subsidies, the disruption alone imposes a significant short-term cost with displaced labor, unused capital goods, and devastated communities.
Mitigations
So how do countries fight back against such a devastating economic weapon? There are a few ways countries have found around this problem of currency devaluation under free trade. First, a country can prevent capital from leaving. This is called capital controls, and many countries, particularly those that manufacture a lot, have them. Try to get money, factories, or equipment out of Malaysia, for example, and you’ll find that they make it quite difficult. Getting the same capital into the country, on the other hand, faces few restrictions. Unfortunately, the US can’t put in capital controls because dollars are its main export. It is, after all, the reserve currency of the world.
Second, you can compete by devaluing your own currency. But that’s very difficult because it requires printing a lot of dollars, and that causes inflation. There’s also no guarantee that a competing country doesn’t devalue its currency again. The US is also in a precarious position as the world’s reserve currency, so devaluing the currency more than it already does will make other holders of the dollar less likely to want to hold it, threatening the reserve currency status.
So the main two mitigations against currency devaluation in a free trade scenario are not available to the US. So what else is there? The remaining option is to drop free trade. The solution, in other words, is to add tariffs. This is how you can nullify the effects of foreign government intervention, by leveling the playing field for US manufacturers.
Tariffs
 One major industry that’s managed to continue being manufactured in the US despite significant foreign competition is cars. Notably, cars have a tariff, which incentivizes their manufacture in the US, even for foreign car makers. The tariff has acted as a way to offset foreign government subsidies and currency debasement.
One major industry that’s managed to continue being manufactured in the US despite significant foreign competition is cars. Notably, cars have a tariff, which incentivizes their manufacture in the US, even for foreign car makers. The tariff has acted as a way to offset foreign government subsidies and currency debasement.The scope of this one industry for the US is huge. There are around 300,000 direct jobs in auto assembly within the US (USTR) and there are an additional 3 million jobs supplying these manufacturers within the US. But the benefits don’t end there. The US is also creating a lot of innovation around cars, such as self-driving and plug-in electric cars. There are many countries that would love to have this industry for themselves, but because of tariffs, auto manufacturing continues in the US.
And though tariffs are seen as a tax on consumers, US car prices are cheap relative to the rest of the world. What surprises a lot of people when they move from the US to other countries is finding out that the same car often costs more abroad (e.g. 25% tariffs keep U.S. prices 20% below Europe’s $40K average, 2024). The downside of tariffs pales next to the downsides of “free trade.”
Free Trade Doesn’t Work with Fiat Money
The sad reality is that while we would love for free trade to work in the ideal libertarian paradise, it won’t in our current fiat-based system. The subsidization by foreign governments to bankrupt US companies or to make them multinational, combined with the unfortunate reality of the US dollar being the world reserve currency, means that free trade guts the US of manufacturing. Tariffs are a reasonable way to protect US manufacturers, particularly smaller ones that can’t go multinational.
What’s more, tariffs make the US less fragile and less dependent on international supply chains. Many of the wars in the past 60 years have been waged because of the entanglements the US has with other countries due to the reliance on international supply chains. Lessening this dependency, if only to prevent a war, has clear value.
Lastly, labor has been devalued significantly by fiat monetary expansion, but at least some of that can be recovered if tariffs create more manufacturing, which in turn adds to the demand for labor. This should reduce the welfare state as more opportunities are made available and fewer unemployed people will be on the rolls.
Conclusion
Fiat money produces a welfare state, which makes open borders unworkable. Fiat money also gives foreign governments a potent economic weapon to use against US companies, and by extension the labor force that powers them. Though currency debasement and capital controls are available to other countries as a defense, for the US, neither of these tools is available due to the fact that the dollar is the world reserve currency. As such, tariffs are a reasonable defense against the fiat subsidization of foreign governments.
-
 @ df478568:2a951e67
2025-03-08 02:16:57
@ df478568:2a951e67
2025-03-08 02:16:57I began using/testing Cashu over 105,120 blocks ago when @NVK said "Cashu is very interesting.".
 The first time I swapped sweet cipher-text to sats, it was too new new and novel to digest. Someone sent me cashu over nostr, straight to my npub. I copy pasta-ed it into my minibits wallet and recieved 10 sats. In retrospect, I would compare it to gold backed paper currency. Over a century ago, paper USD was a coupon for gold, "redeemable in gold on demand at the United States Treasury, or in gold for lawful money at any federal reserve bank.
The first time I swapped sweet cipher-text to sats, it was too new new and novel to digest. Someone sent me cashu over nostr, straight to my npub. I copy pasta-ed it into my minibits wallet and recieved 10 sats. In retrospect, I would compare it to gold backed paper currency. Over a century ago, paper USD was a coupon for gold, "redeemable in gold on demand at the United States Treasury, or in gold for lawful money at any federal reserve bank.
In the analog days of the early 20th century a bean-counter at a Federal Reserve bank would give you approximately 5 ounces of gold for an analog bored ape, Ben Franklin. Cashu is an NFT without the jpeg and the innate ability to be redeemed for bitcoin over the lightning network. I've heard NVK describe it as "an honest shitcoin" and I like this framing. The rug-pull risk is greater than zero, but less than the rug-pull risk of Wallet of Satoshi with the added benefit of generational wealth.
This means we can abstract bitcoin value into something that looks like this.
cashuBpGFteCJodHRwczovL21pbnQubWluaWJpdHMuY2FzaC9CaXRjb2luYXVjc2F0YXSBomFpSABQBVDwSUFGYXCCpGFhAmFzeEBkMzM2Mjk1OTZhNTVkODcyNWFjOGI3MDQyNjM5MjQ0OTU4YmJlMjVkYmFhYzIyY2E5Y2M2NTMyNTM1OWFiZDI2YWNYIQNOrrDCFnYa3sMJxpr02o8Bg5AfibjqIOTmiktqYkABKWFko2FlWCBdC0gEM2j5YE4_xMGyuvLHIufqx7zzp6TNJAeJiB6_WmFzWCDRMyyGRmJPYmwB3u8kB7fyBlvRm69hC2DfkyY5Mizd-WFyWCB_88znXGBc_GgRngr9m1nEYAJEDUkQiQLT1e6R9_Un_aRhYQhhc3hANjVkYWQyM2ExNjQyNTYzMDU5OGRmMTdiNDc0YWQ0YzdhMjNhMmFiZjUwNjEzYTdjOTI4NzllMDllZTg5ODcxZWFjWCECoRg-ub_wReP4T6A0UuwqS36Iw6Ton4U5j6IJrLYjKCxhZKNhZVggmXDv_na1XQU3ESYq147mIyDyQm5mgsnkl7HxBbVmXv9hc1ggIbKkVVdG06hBgAvWBhoFo8T-V6MjNzxUGNaGjQjU2e5hclggAJp2vzdgwmehnhwmmFQsZ_BNTb8Aqz_ItwOx0iLQ9NlhZHgtQ29uZ3JhdHVsYXRpb25zIGZvciBjbGFpbWluZyB0aGlzIGVjYXNoIGZpcnN0The lightning network is cool, but requires the reciever to have a wallet. Many Americans began using nostr when Wallet of Satoshi was available to them. They disappeared like a magiian once Wallet of Satoshi was removed from the app stores. To be fair, it still works. Last I checked, sats from wallet of satoshi can still be received and spent from US based IP addresses, but non-technical noobs can no longer download it from app stores designed for the neuro-typical.
I sprinkled a little e cash in a few Substack articles, but few people know what it is. These things takes time. Maybe it's too early. Maybe, just maybe, we can make paper cash great again.
Is it a long shot? Sure. Will I try it anyway? Hell yes!
How To Make Paper Money Great Again
The plan: Create paper products with QR codes that have Cashu. Think tip cards or birtday cards designed to hold cash. You can choose your mint on Mibibits or Macadamia depending on your pnone. This is not bitcoin for posterity. We're talking about pocket spending money, not generational wealth.
I plan to make and sell greeting cards: HallMarc cards.😉 I draw like I'm 5, but we'll let the market decide if they prefer my Kidnergarden-style art or Ideogram. Then I'll write some cheesy words people like on greeting cards. Here's my first idea.
Happy Birthday
Stack Sats.
Okay....So it's more like a first draft, but this is a proof of concept. Cut me some slack. 😅 There's still a few kinks to work out, but here's the prototype.


Set Up Shop With A Free And Open Source Version
I will add these cards to my merch shop. I can add 1,000 sats, maybe some custom amounts, but I'll also open source them. I like to give cards that pay bitcoin to kids in my family. If I open source this, maybe more people will be willing to give the kids in their family sats. It only costs card stock paper, ink, and the sats you give away.
If you're like me, your family knows your a bitcoin dork anyway. We might as well show them it's not just an investment. It's money we can give them they can either save or spend.
We should mention it's better to save bitcoin. That's what stacking sats means. That will be my second draft.
Happy Birthday.
Save as much bitcoin as you can.
Npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
https://mempool.marc26z.com/block/000000000000000000001567ce65dab25358bcae86c2c573984888eb08948b65
https://marc26z.com/merch/
-
 @ 6e0ea5d6:0327f353
2025-03-08 01:31:14
@ 6e0ea5d6:0327f353
2025-03-08 01:31:14💀
No one returns the same after witnessing such great disrespect that even the eyes doubt what they see.
When behavior does not match the promise, when the path being followed contradicts our principles, when a lie unfolds right before our eyes, or when an offense is deliberately crafted as a test of our resolve, a feeling arises—one that urges us to intervene, to stop such foolishness so that things may proceed as they should. But it is an arrow already released. It cannot be retrieved. There is no turning back. And perhaps, Nietzsche’s words explain it best:
"I’m not upset that you lied to me; I’m upset that from now on, I can’t trust you."
This is what we feel, in conflict with what we know. But maturity has taught us whom to listen to. The mind knows that one must be cruel to oneself so that others will not be cruel to us.
It takes cruelty to kill with indifference what desires to live in our hearts.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 6e0ea5d6:0327f353
2025-03-08 01:17:35
@ 6e0ea5d6:0327f353
2025-03-08 01:17:35Ascolta bene, amico mio. Are you really concerned about what a morally bankrupt society has to say about "being a man"?
The same society that glorifies weakness, where anyone—without the slightest idea of what it means to bear the weight of masculinity—thinks they have the right to an opinion? And, of course, we can’t forget the spectacle: women without any solid paternal reference, never having experienced what it means to have a true masculine figure, now feel entitled to dictate how you should live, act, and even feel. This is more than a joke—it’s the tragic portrait of a civilization on the brink of collapse.
Think about it: it’s as if someone who has never held a hammer tried to teach a blacksmith how to forge steel. What do they know about the burden of being a man? They have never had to carry this weight. They have never known what it is to walk alone, facing the world without guarantees, without anyone to catch them when everything falls apart. Talking is easy, amico mio, when they’ve never had to get their hands dirty with the brutal reality we face every day.
Want to know what you should do? Ignore it. Simple as that. The opinion of those who have never walked your path holds no value. Do not take seriously the judgments of those trapped in a modern fantasy of masculinity, shaped by empty ideals that only encourage weakness. If these women have never had a strong father figure, a real example of masculinity, what do they know about being a man? Nothing. And the worst part: they don’t even realize the emptiness of their words.
And here’s the lesson: you don’t need the approval of a lost society that doesn’t understand the value of discipline, strength, and the sacrifice that true masculinity demands. You don’t need to be shaped by the expectations of this dying world. The only respect that matters is the one you have for yourself. Once you understand this, the judgment of others becomes irrelevant, and their voices fade into the wind like an insignificant breeze.
Who do you want to be respected by? A society that glorifies mediocrity? Or by those who, like you, know the true struggle?
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 378562cd:a6fc6773
2025-03-08 01:12:13
@ 378562cd:a6fc6773
2025-03-08 01:12:13Forgiveness is one of the hardest but most powerful things we can do. It’s not just about letting someone else off the hook—it’s about freeing ourselves from anger, bitterness, and pain. Holding onto grudges only weighs us down, while forgiveness brings peace and healing.
What Is Forgiveness?
Forgiveness means choosing to release resentment toward someone who has wronged us. It doesn’t mean forgetting what happened or pretending it didn’t hurt. It simply means we no longer decide to let the offense control our hearts and minds.
Why Is Forgiveness Important?
It sets us free. Holding onto anger only harms us, not the other person. It brings peace. Letting go of past hurts allows us to move forward. It strengthens relationships. No one is perfect—we all need grace at times. It reflects God's love. In the Bible, God forgives us and calls us to do the same (Ephesians 4:32).
How to Forgive
Make the choice. Forgiveness starts with a decision, even if emotions don’t follow right away. Pray for strength. Ask God to help you release the hurt. Let go of revenge. Forgiveness means choosing not to seek payback. Move forward. This doesn’t always mean restoring a relationship, but it does mean releasing the pain. Repeat if necessary. Sometimes, forgiveness is a process, not a one-time event.
Forgiving Yourself
Forgiveness isn’t just for others. Sometimes, we struggle to forgive ourselves for past mistakes. But if God offers us grace, we should accept it too. Learn from the past, but don’t let it define you.
Final Thoughts
Forgiveness isn’t always easy, but it is always worth it. It is a gift you give yourself, a step toward peace, and a reflection of God’s love. If you struggle to forgive, take it one step at a time. Let go, trust God, and walk in freedom.
Until Next Time... :)
-
 @ dc4cd086:cee77c06
2025-03-07 22:32:02
@ dc4cd086:cee77c06
2025-03-07 22:32:02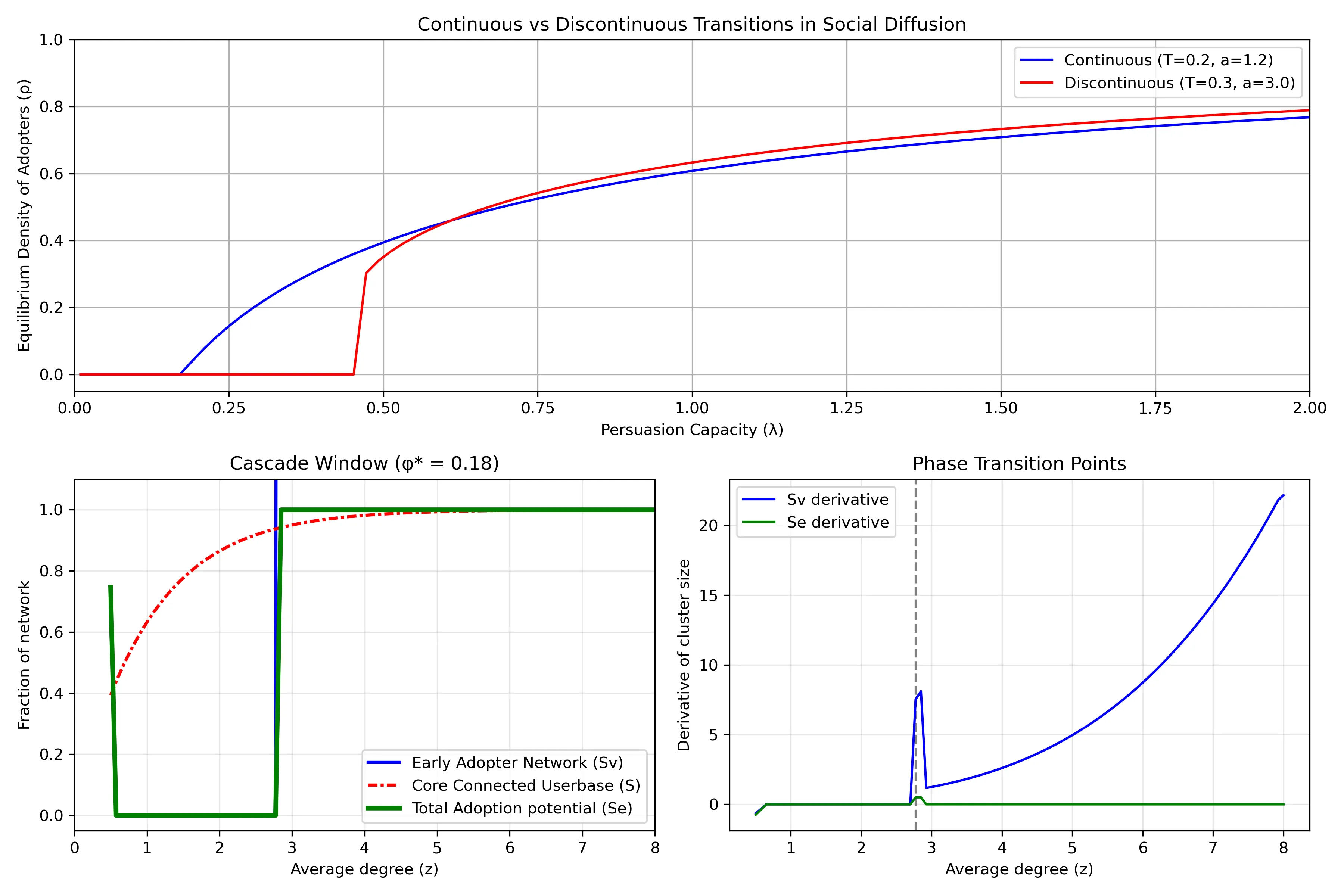
Understanding Network Dynamics in Technology Adoption
- Top Row: Continuous vs Discontinuous Transitions in Social Diffusion
- Shows two different ways that innovations spread through a population. The horizontal axis (
λ) represents "persuasion capacity" - how effectively adopters convince others to join. The vertical axis (ρ) shows what fraction of the population eventually adopts. - Blue line shows a continuous transition: as persuasion capacity increases, adoption grows gradually and smoothly. Example: streaming services that steadily gains users year after year.
- Red line shows a discontinuous transition (or "tipping point"): adoption remains near zero until reaching a critical threshold, then suddenly jumps to a high level. This represents technologies that spread explosively once they reach a critical mass.
- The different curves emerge from the situations of how people make adoption decisions. When there is higher adoption resistance (higher threshold
Tand steeper response curvea), discontinuous transitions become more likely.
Bottom Left: Cascade Window
When is widespread adoption possible? Its based on network structure. The horizontal axis (
z) represents network connectivity - on average, how many connections does an individual have? The plot has a regime "cascade window" - widespread adoption only occurs within a specific range of connectivity: - If connectivity is too low (left side), the network is too fragmented for innovations to spread widely - If connectivity is too high (right side), people become resistant to change because they need many of their connections to adopt before they will follow suitThe different curves show theoretical predictions for:
- The early adopter network (blue solid): people who can be convinced to adopt with minimal influence.
- The core connected userbase (red line): the largest interconnected population in the network
- Total adoption potential (green line): the potential total reach possible through both early adopters and those they influence
Bottom Right: Phase Transition Points
This plot highlights
critical thresholdswhere the system undergoes dramatic changes. The peaks represent points where small changes in network connectivity cause the largest shifts in adoption patterns. The vertical dashed line marks a critical connectivity value where adoption dynamics fundamentally change. Near these critical points, the network becomes especially sensitive - like how a small price drop might suddenly make a product accessible to a much larger market segment, increasing how easily individuals are connected.The green line (total adoption potential rate) shows only a brief spike at the critical threshold and then quickly returns to zero. Implying that the total potential reach of an innovation changes only at that specific critical point and then stabilizes. This is why timing market entry is so crucial - there's a narrow window where network conditions can suddenly enable widespread adoption, and missing this window means the technology might never achieve its full potential.
Further Reading:
- Malcom Gladwell's Tipping Point
Sources:
- https://www.frontiersin.org/journals/physics/articles/10.3389/fphy.2018.00021/full
-
https://www.pnas.org/doi/10.1073/pnas.1414708112
-
https://www.pnas.org/doi/10.1073/pnas.082090499
-
 @ 21ffd29c:518a8ff5
2025-03-07 20:56:56
@ 21ffd29c:518a8ff5
2025-03-07 20:56:56Once upon a time, there was a little boy named Jimmy who had been feeling very sick. He complained about the pain in his throat and nose. His parents tried everything to help him but nothing worked. One day, Jimmy's friend Jeeves came over to visit. He saw that his friend was trying to make something special for his family, and he decided to try home-brewed vaccines as well. Jeeves started experimenting with the homemade vaccine concoctions and made a couple of them. They were very good at making people feel better quickly. One day, Jimmy's parents asked Jeeves if they could have some of these home-made vaccines too. Jeeves agreed, but he had to be careful not to break his blender because it was quite small. The next day, Jeeves brought a mixture of eggs and sheep off the roof of his house, which made him very happy. He started trying them out, and they worked great! Jimmy's parents were so proud of their son for doing something like this. They thanked Jeeves for making such a great home-made vaccine. Jeeves then told Jimmy about how he had found a way to make the blender work again. That was exciting for everyone! The next day, they all tried the homemade vaccines again and made a lot of people feel better quickly too! He decided to make some extra batches of home-made vaccines for everyone who had asked if they could have one too! This was such a fun story! It made everyone feel so happy and excited, and they all wanted -
 @ ec9bd746:df11a9d0
2025-03-07 20:13:38
@ ec9bd746:df11a9d0
2025-03-07 20:13:38I was diving into PoW (Proof-of-Work) once again after nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uqzqj8a67jths8euy33v5yu6me6ngua5v3y3qq3dswuqh2pejmtls6datagmu rekindled my interest with his PoW Draw project. It was a fun little trifle, but it shifted my focus just the right way at the right time.
Because then, on Friday, came the Oval Office Travesty. Once I got over the initial shock, I decided I couldn't just curse and lament; I needed to do something bigger, something symbolic, something expressive. So that's exactly what I did—breaking nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2t9v7jg's record which he held for almost 2 and half years.
Here is a note with PoW 45, the highest PoW known to Nostr (as of now).
nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsqgqqqqqqqqqy8t8awr5c8z4yfp4cr8v7spp8psncv8twlh083flcr582fyu9
How Did I Pull It Off?
In theory, quite simple: Create note, run PoW mining script & wait.
Thanks to PoW Draw, I already had mining software at hand: nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqvqc5tlvn6etv09f0fvuauves49dvgnukjtzsndfv9y8yyrqyxmz7dty6z's notemine_hw, but when you know that there is a 1 in 2^45 chance that the next hash will be the correct one you want to increase the odds a bit. So on Monday evening, I started my Note Mining operation on an old 40 thread machine called Workhorse.
Issues Along the Way
I was immediately surprised that Workhorse (2× Intel Xeon Silver 4114) produced only about 3Mh/s. A laptop (Intel Core i7-1185G7) with Windows and all the bloat did 5Mh/s. That was strange.
Another hurdle was that notemine_hw does not refresh the
created_atfield. With just a few Mh/s of power I was potentially looking at weeks of computation, by then the note would be quite stale. So I created systemd service leveraging theRuntimeMaxSecoption to periodically restart every 3600 seconds assuring that the Note would be max 1 hour old at the time of publishing.Luckily PoW is that kind of problem where every hash attempt is an independent event, so the chance of success is the same whether you do it in small increments or one uninterrupted stretch. So by restarting the mining process I was only losing a few mere seconds every hour due to the overhead.
Once the note staleness issue was resolved, I looked at the 40 workers on Workhorse vs. 7 workers on the laptop and start messing around with running one instance with 40 workers and running 40 instances with 1 worker and found out, that the workers are not bound to a CPU thread and are jumping between the CPUs like rabbits high on Colombian carrots.
The solution? Running multiple instances with one worker each as a service locked to its own CPU core using systemd's
CPUAffinityoption. ``` $aida@workhorse:systemd/system $ sudo cat notemine@.service [Unit] Description=Notemine HW Publish (restarts hourly)[Service] Type=simple CPUAffinity=%i
The command to run:
ExecStart=/home/aida/.cargo/bin/notemine_hw publish --n-workers 1 --difficulty 45 --event-json /home/aida/note.json --relay-url 'wss://wot.shaving.kiwi' --nsec nsec0123456789abcdef
Let the process run for 1 hour (3600 seconds), then systemd will stop it:
RuntimeMaxSec=3600 TimeoutStopSec=1
Tells systemd to restart the service automatically after it stops:
Restart=always RestartSec=1
run as a non-root user:
User=aida Group=aida
[Install] WantedBy=multi-user.target ``` Then I added a starting service to spawn an instance for each CPU thread.
``` $aida@workhorse:systemd/system $ sudo cat notemine_start.service [Unit] Description=Start all services in sequence with 3-second intervals
[Service] Type=oneshot ExecStart=/usr/bin/zsh /home/aida/notemine_start.sh
RemainAfterExit=yes
[Install] WantedBy=multi-user.target
Here is the startup script (I know, loops exist—but Ctrl+C/Ctrl+V is so old-school):aida@workhorse:~ $ cat notemine_start.sh /usr/bin/systemctl start notemine@0.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@1.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@2.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@3.service /usr/bin/sleep 3 ... ... ... /usr/bin/systemctl start notemine@38.service`` The sleep there is critical to make sure that thecreated_at`timestamps are different, preventing redundant hashing.This adjustment made Workhorse the strongest machine in my fleet with 10+Mh/s.
The Luck Aspect
From Monday evening, I started adding all machines at my disposal into the fleet and by Wednesday evening I was crunching hashes on about 130 CPU threads (a lot of them were quite antique) and at the peak was just little shy of 40Mh/s. To compensate for the slow start with the few above-mentioned hiccups and the fact that I had to use my desktop to do other things from time to time, I counted with the conservative estimate of 30Mh/s when I was doing all the probability calculations.
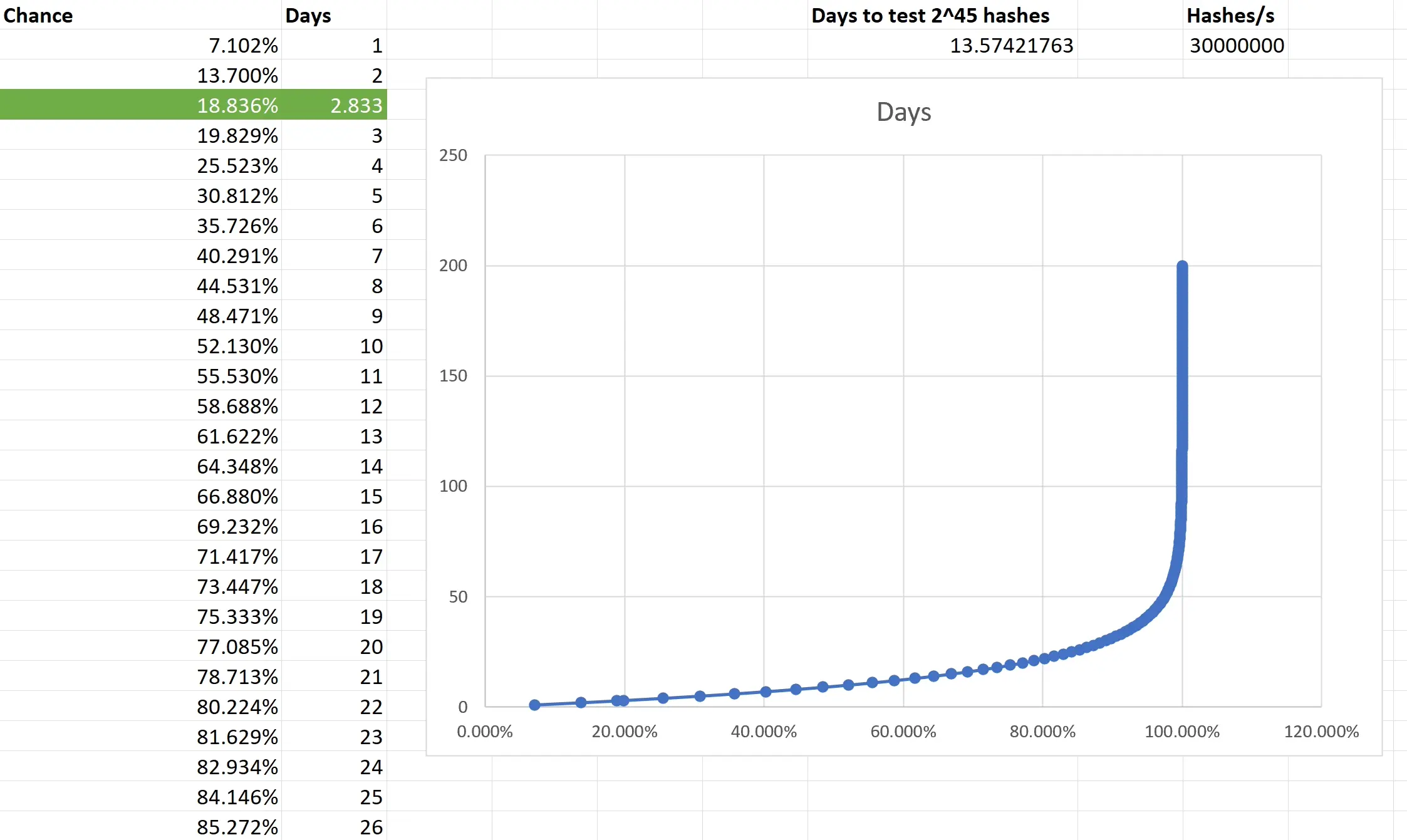
Based on the type of task that PoW mining is, the outcome is not predictible. You are only looking at what is the chance that the outcome of every single independent event will be consecutively non-favourable and then subtracting it from 1 to get the chance of that single favourable event you want. I really had to brush up on my combinatorics and discrete mathematics to make sure I have at least an elementary understanding of what is going on. Also, because we are not just throwing a dice 5 times, but are operating with big numbers, approximation was necessary. Luckily, the formula is available and quite simple in the end.
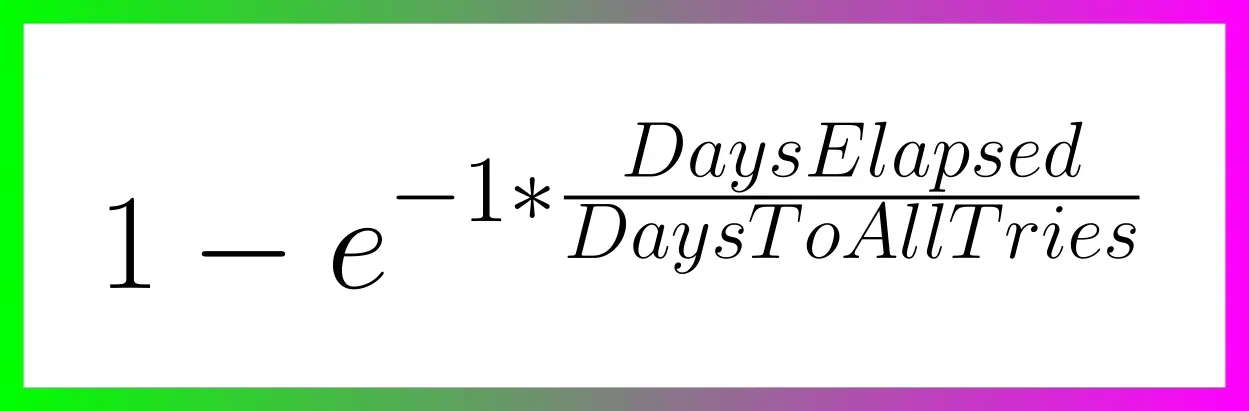
Two weeks to exhauste all the possible tries still doesn't guarantee anything, actually there is a slighlty less than 2 in 3 chance that you will have a result after all that time. So the fact that I was able to hit the right hash in less than 3 days was good luck. Not insane lottery winning luck, but good luck; slighlty lower than 1 in 5.
Do you want to beat me?
Go ahead! All the pitfalls are described above and until there is a GPU-based PoW Mining available, we are all on pretty even ground.
Do you hate the note?
In that case, feel free to enjoy this accompanying image:

-
 @ 29216785:2a636a70
2025-03-07 15:38:37
@ 29216785:2a636a70
2025-03-07 15:38:37This is a note
How is this being broadcasted to Nostr?
tag #notes #comet
-
 @ 401014b3:59d5476b
2025-03-07 14:44:12
@ 401014b3:59d5476b
2025-03-07 14:44:12Alright, football savages, it’s March 2025, and we’re tearing into the AFC North like it’s a pierogi-eating contest at a steel mill tailgate. Free agency’s a wild west shootout, the draft’s a blind bet, and this division’s always a brutal cage match of toughness and trash talk. The Bengals and Ravens duked it out in 2024, the Steelers hung tough, and the Browns… well, they Brownsed. Let’s throw some records on this grinder and see who’s got the grit to claim the crown. Here we go, fam—pass the Iron City.
Cincinnati Bengals: 11-6 – Burrow’s Back with a Vengeance
The Bengals were a force in 2024, and 2025’s shaping up as Joe Burrow’s revenge tour. With Ja’Marr Chase and Tee Higgins (assuming they keep him) torching DBs, this offense is a video game cheat code. The O-line’s finally decent, and the defense—Logan Wilson, Trey Hendrickson—if he stays, brings the pain when it matters. Roster changes are a hurdle—Higgins and Hendrickson might chase a mega-deal elsewhere—but Burrow’s ice-cold clutch factor seals it. 11-6, division champs. Cincy’s ready to remind everyone who dey really are.
Baltimore Ravens: 10-7 – Lamar’s Still a Freak
The Ravens are the AFC North’s relentless machine. Lamar Jackson’s running circles around defenses, Derrick Henry’s still trucking fools (if he’s back), and Zay Flowers keeps the passing game spicy. That defense—Roquan Smith, Kyle Hamilton—is a brick wall, but free agency could bite. Justin Madubuike SHOULD stay, and the secondary’s got holes to patch. 10-7’s the call, snagging a wildcard. They’re a half-step behind Cincy but built to ruin someone’s playoff dreams.
Pittsburgh Steelers: 9-8 – Tomlin’s Eternal .500 Magic
Mike Tomlin’s Steelers are the NFL’s cockroaches—impossible to kill. Russell Wilson initially steadied the ship in 2024, and with Najee Harris pounding the rock and George Pickens stretching the field, they’ve got enough juice. The defense—T.J. Watt, Cam Heyward (if he’s still kicking)—is still a nightmare, but age and free agency loom. Patrick Queen could bolt, the Steelers need to settle on a QB, and the secondary’s thin. 9-8’s classic Tomlin—competitive, scrappy, maybe a wildcard if the stars align. Pittsburgh doesn’t die; it just reloads.
Cleveland Browns: 6-11 – Deshaun’s Last Stand?
The Browns are the AFC North’s punching bag, and 2025 ain’t looking much brighter. Deshaun Watson’s a $230 million question mark—Nick Chubb’s back, Jerry Jeudy’s a weapon, but that O-line’s shaky. The defense—Myles Garrett, Denzel Ward—keeps ‘em in games, but free agency might swipe Jeremiah Owusu-Koramoah, and the vibes are off. 6-11’s the harsh truth—too much baggage, not enough spark. Cleveland’s stuck in neutral ‘til they figure out QB.
The Final Bell
The AFC North in 2025 is a Cincinnati coronation with a bloody chase. The Bengals (11-6) take the title because Burrow’s a killer, the Ravens (10-7) claw a wildcard with Lamar’s wizardry, the Steelers (9-8) hang tough, and the Browns (6-11) wallow. Free agency’s the game-changer—lose a stud, you’re screwed; keep ‘em, you’re cooking. Hit me on Nostr when I butcher this, but this is my AFC North gospel. Let’s roll, degenerates.
-
 @ eac63075:b4988b48
2025-03-07 14:35:26
@ eac63075:b4988b48
2025-03-07 14:35:26Listen the Podcast:
https://open.spotify.com/episode/7lJWc1zaqA9CNhB8coJXaL?si=4147bca317624d34
https://www.fountain.fm/episode/YEGnlBLZhvuj96GSpuk9
Abstract
This paper examines a hypothetical scenario in which the United States, under Trump’s leadership, withdraws from NATO and reduces its support for Europe, thereby enabling a Russian conquest of Ukraine and the subsequent expansion of Moscow’s influence over Eurasia, while the US consolidates its dominance over South America. Drawing on classical geopolitical theories—specifically those of Halford Mackinder, Alfred Thayer Mahan, Rudolf Kjellén, and Friedrich Ratzel—the study analyzes how these frameworks can elucidate the evolving power dynamics and territorial ambitions in a reconfigured global order. The discussion highlights Mackinder’s notion of the Eurasian Heartland and its strategic importance, Mahan’s emphasis on maritime power and control of strategic routes, Kjellén’s view of the state as an expanding organism, and Ratzel’s concept of Lebensraum as a justification for territorial expansion. The paper also explores contemporary developments, such as the US–Ukraine economic agreement and Trump’s overt territorial ambitions involving Greenland and Canada, in light of these theories. By juxtaposing traditional geopolitical concepts with current international relations, the study aims to shed light on the potential implications of such shifts for regional stability, global security, and the balance of power, particularly in relation to emerging neocolonial practices in Latin America.
Introduction
In recent years, the geopolitical dynamics involving the United States, Russia, and Ukraine have sparked analyses from different theoretical perspectives. This paper examines recent events – presupposing a scenario in which Donald Trump withdraws the US from NATO and reduces its support for Europe, allowing a Russian conquest of Ukraine and the expansion of Moscow’s influence over Eurasia, while the US consolidates its dominance over South America – in light of classical geopolitical theories. The ideas of Halford Mackinder, Alfred Thayer Mahan, Rudolf Kjellén, and Friedrich Ratzel are used as reference points. The proposal is to impartially evaluate how each theory can elucidate the developments of this hypothetical scenario, relating Russian territorial expansion in Eurasia to the strategic retreat of the US to the Western Hemisphere.
Initially, we will outline Mackinder’s conception of the Heartland (the central Eurasian territory) and the crucial role of Eastern Europe and Ukraine in the quest for global dominance. Next, we will discuss Mahan’s ideas regarding maritime power and the control of strategic routes, considering the impacts on the naval power balance among the US, Russia, and other maritime powers such as the United Kingdom and Japan. Subsequently, we will examine Kjellén’s organic theory of the state, interpreting the Russian expansionist strategy as a reflection of a state organism in search of vital space. In the same vein, Ratzel’s concept of “Lebensraum” will be explored, along with how Russia could justify territorial expansion based on resources and territory. Finally, the paper connects these theories to the current political context, analyzing the direct negotiations between Washington and Moscow (overlooking Ukraine and Europe), the US policy toward authoritarian regimes in Latin America, and the notion of a hemispheric division of power – the “Island of the Americas” under North American hegemony versus an Eurasia dominated by Russia. Lastly, it considers the possibility that such a geopolitical arrangement may foster the strengthening of authoritarian governments globally, rather than containing them, thus altering the paradigms of the liberal world order.
The Heartland of Mackinder: Ukraine, Eurasia, and Global Dominance
Halford J. Mackinder, a British geographer and pioneer of geopolitics, proposed the celebrated Heartland Theory in the early twentieth century. Mackinder divided the world into geostrategic zones and identified the Heartland—the central continental mass of Eurasia—as the “geographical pivot of history” [5]. His most famous maxim encapsulates this vision: “who rules Eastern Europe commands the Heartland; who rules the Heartland commands the World Island; who rules the World Island commands the world” [5]. Eastern Europe and, in particular, the region of present-day Ukraine, play a key role in this formula. This is because, for Mackinder, Eastern Europe functions as a gateway to the Heartland, providing access to resources and a strategic position for the projection of continental power [5].
Applying this theory to our scenario, the conquest of Ukraine and Eastern European countries by Russia would have profound geopolitical implications. From a Mackinderian point of view, such a conquest would enormously strengthen Russia’s position in the Heartland by adding manpower (population) and Ukraine’s industrial and agricultural resources to its power base [5]. In fact, Mackinder argued that controlling the Heartland conferred formidable geostrategic advantages—a vast terrestrial “natural fortress” protected from naval invasions and rich in resources such as wheat, minerals, and fuels [5]. Thus, if Moscow were to incorporate Ukraine (renowned for its fertile soil and grain production, as well as its mineral reserves) and extend its influence over Eastern Europe, Russia would consolidate the Heartland under its direct control. In this context, the absence of the USA (withdrawn from NATO and less engaged in Europe) would remove an important obstacle to Russian predominance in the region.
With central and eastern Eurasia under Russian influence, it would be possible to move toward the realization of the geopolitical nightmare described by Mackinder for Western maritime powers: a hegemonic continental power capable of projecting power to both Europe and Asia. Mackinder himself warned that if a Heartland power gained additional access to an oceanic coastline—in other words, if it combined land power with a significant maritime front—it would constitute a “danger” to global freedom [5]. In the scenario considered, besides advancing into Eastern Europe, Russia would already possess strategic maritime outlets (for example, in the Black Sea, via Crimea, and in the Baltic, via Kaliningrad or the Baltic States if influenced). Thus, the control of Ukraine would reinforce Russia’s position in the Black Sea and facilitate projection into the Eastern Mediterranean, expanding its oceanic front. From a Mackinderian perspective, this could potentially transform Russia into the dominant power of the “World Island” (the combined mass of Europe, Asia, and Africa), thereby unbalancing the global geopolitical order [5].
It is worth noting that, historically, Mackinder’s doctrine influenced containment strategies: both in the interwar period and during the Cold War, efforts were made to prevent a single power from controlling the Heartland and Eastern Europe. NATO, for example, can be seen as an instrument to prevent Soviet/Russian advances in Europe, in line with Mackinder’s imperative to “contain the Heartland.” Thus, if the USA were to abandon that role—by leaving NATO and tacitly accepting the Russian sphere of influence in Eurasia—we would be witnessing an inversion of the principles that have guided Western policy for decades. In short, under Mackinder’s theory, the Russian conquest of Ukraine and beyond would represent the key for Russia to command the Heartland and, potentially, challenge global hegemony, especially in a scenario where the USA self-restricts to the Western Hemisphere.
The Maritime Power of Mahan and the Naval Balance between West and East
While Mackinder emphasized continental land power, Alfred Thayer Mahan, a nineteenth-century American naval strategist, highlighted the crucial role of maritime power in global dominance. In his work The Influence of Sea Power upon History (1890), Mahan studied the example of the British Empire and concluded that control of the seas paved the way for British supremacy as a world power [10]. He argued that a strong navy and the control of strategic maritime routes were decisive factors for projecting military, political, and economic power. His doctrine can be summarized in the following points: (1) the United States should aspire to be a world power; (2) control of the seas is necessary to achieve that status; (3) such control is obtained through a powerful fleet of warships [17]. In other words, for Mahan, whoever dominates the maritime routes and possesses naval superiority will be in a position to influence global destinies, ensuring trade, supplies, and the rapid movement of military forces.
In the proposed scenario, in which the USA withdraws militarily from Europe and possibly from the Eurasian stage, Mahan’s ideas raise questions about the distribution of maritime power and its effects. Traditionally, the US Navy operates globally, ensuring freedom of navigation and deterring challenges in major seas (Atlantic, Pacific, Indian, etc.). A withdrawal of the USA from NATO could also signal a reduction in its naval presence in the Northeast Atlantic, the Mediterranean Sea, and other areas close to Eurasia. In such a case, who would fill this naval vacuum? Russia, although primarily a land power, has been attempting to modernize its navy and has specific interests—for example, consolidating its dominance in the Black Sea and maintaining a presence in the Mediterranean (with a naval base in Tartus, Syria). The United Kingdom, a historic European maritime power, would remain aligned with the USA but, without American military support in Europe, might potentially be overwhelmed trying to contain an increasingly assertive Russian navy in European waters on its own. Japan, another significant maritime actor allied with the USA, is concerned with the naval balance in the Pacific; without full American engagement, Tokyo might be compelled to expand its own naval power to contain both Russia in the Far East (which maintains a fleet in the Pacific) and, especially, the growing Chinese navy.
According to Mahan’s thinking, strategic maritime routes and choke points (crucial straits and channels) become contested prizes in this power game. With the USA focusing on the Americas, one could imagine Washington reinforcing control over the Panama Canal and Caribbean routes—reviving an “American Gulf” policy in the Western Atlantic and Eastern Pacific. In fact, indications of this orientation emerge in statements attributed to Trump, who once suggested reclaiming direct control over Panama, transforming Canada into a North American state, and even “annexing” Greenland due to its Arctic geopolitical importance [18]. These aspirations reflect a quest to secure advantageous maritime positions near the American continent.
Conversely, in the absence of American presence in the Eastern Atlantic and Mediterranean, Russia would have free rein for regional maritime projection. This could include anything from the unrestricted use of the Black Sea (after dominating Ukraine, thereby ensuring full access to Crimea and Ukrainian ports) to greater influence in the Eastern Mediterranean via Syria and partnerships with countries such as Iran or Egypt. The Baltic Sea would also become an area of expanded Russian interest, pressuring coastal countries and perhaps reducing NATO’s traditional local naval supremacy. However, it is worth noting that even with these regional expansions, Russia lacks a blue-water navy comparable to that of the USA; thus, its initial global maritime impact would be limited without alliances.
An important aspect of Mahan’s theories is that naval power serves as a counterbalance to the land power of the Heartland. Therefore, even if Russia were to dominate the Eurasian continental mass, the continued presence of American naval might on the oceans could prevent complete global domination by Moscow. However, if the USA voluntarily restricts its naval reach to the Americas, it would forgo influencing the power balance in the seas adjacent to Eurasia. Consequently, the balance of maritime power would tend to shift in favor of regional Eurasian actors. The United Kingdom and Japan, traditional allies of the USA, could intensify their naval capabilities to defend regional interests—the United Kingdom safeguarding the North Atlantic and the North Sea, and Japan patrolling the Northwest Pacific—but both would face budgetary and structural limitations in fully compensating for the absence of the American superpower. Consequently, Mahan’s vision suggests that the withdrawal of the USA from the extra-regional scene would weaken the liberal maritime regime, possibly opening space for revisionist powers to contest routes that were previously secured (for example, Russia and China encountering less opposition on the routes of the Arctic and the Indo-Pacific, respectively). In summary, naval hegemony would fragment, and control of strategic seas would become contested, reconfiguring the relative influence of the USA, Russia, and maritime allies such as the United Kingdom and Japan.
Kjellén and the State as a Living Organism: Russian Expansion as an Organic Necessity
Another useful theoretical lens to interpret Russian geopolitical posture is that of Rudolf Kjellén, a Swedish political scientist of the early twentieth century who conceived the State as a living organism. Kjellén, who even coined the term “geopolitics,” was influenced by Friedrich Ratzel’s ideas and by social Darwinism, arguing that States are born, grow, and decline analogously to living beings [13]. In his work Staten som livsform (The State as a Form of Life, 1916), he maintained that States possess an organic dimension in addition to the legal one and that “just as any form of life, States must expand or die” [14]. This expansion would not be motivated merely by aggressive conquest but seen as a necessary growth for the self-preservation of the state organism [14]. In complement, Kjellén echoed Ratzel’s “law of expanding spaces” by asserting that large States expand at the expense of smaller ones, with it being only a matter of time before the great realms fill the available spaces [14]. That is, from the organic perspective, vigorous States tend to incorporate smaller neighboring territories, consolidating territorially much like an organism absorbing nutrients.
Applying this theory to the strategy of contemporary Russia, we can interpret Moscow’s actions—including the invasion of Ukraine and the ambition to restore its sphere of influence in Eurasia—as the expression of an organic drive for expansion. For a strategist influenced by this school, Russia (viewed as a state organism with a long imperial history) needs to expand its territory and influence to ensure its survival and security. The loss of control over spaces that once were part of the Russian Empire or the Soviet Union (such as Ukraine itself, the Caucasus, or Central Asia) may be perceived by Russian elites as an atrophy of the state organism, rendering it vulnerable. Thus, the reincorporation of these territories—whether directly (annexation) or indirectly (political vassalage)—would equate to restoring lost members or strengthening vital organs of the state body. In fact, official Russian arguments often portray Ukraine as an intrinsic part of “Russian historicity,” denying it a fully separate identity—a narrative that aligns with the idea that Russian expansion in that region is natural and necessary for the Russian State (seen as encompassing also Russian speakers beyond its current borders).
Kjellén would thus provide a theoretical justification for Russian territorial expansion as an organic phenomenon. As a great power, Russia would inevitably seek to expand at the expense of smaller neighbors (Ukraine, Georgia, the Baltic States, etc.), as dictated by the tendency of “great spaces to organize” to the detriment of the small [14]. This view can be identified in contemporary Russian doctrines that value spheres of influence and the notion that neighboring countries must gravitate around Moscow in order for the natural order to be maintained. The very idea of “Eurasia” united under Russian leadership (advocated by modern Russian thinkers) echoes this organic conception of vital space and expansion as a sign of the State’s vitality.
However, Kjellén’s theory also warns of the phenomenon of “imperial overstretch,” should a State exceed its internal cohesion limits by expanding excessively [14]. He recognized that extending borders too far could increase friction and vulnerabilities, making it difficult to maintain cohesion—a very large organism may lack functional integration. In the Russian context, this suggests that although expansion is seen as necessary, there are risks if Russia tries to encompass more than it can govern effectively. Conquering Ukraine and subjugating Eastern Europe, for example, could economically and militarily overburden the Russian State, especially if it faced resistance or had to manage hostile populations. However, in the hypothetical scenario we adopt (isolated USA and a weakened Europe), Russia might calculate that the organic benefits of expansion (territory, resources, strategic depth) would outweigh the costs, since external interference would be limited. Thus, through Kjellén’s lens, expansionist Russia behaves as an organism following its instinct for survival and growth, absorbing weaker neighbors; yet such a process is not devoid of challenges, requiring that the “organism Russia” manages to assimilate these new spaces without collapsing under its own weight.
Ratzel and Lebensraum: Resources, Territory, and the Justification for Expansion
Parallel to Kjellén’s organic view, Friedrich Ratzel’s theory offers another conceptual basis for understanding Russian expansion: the concept of Lebensraum (vital space). Ratzel, a German geographer of the late nineteenth century, proposed that the survival and development of a people or nation depended critically on the available physical space and resources. Influenced by Darwinist ideas, he applied the notion of “survival of the fittest” to nations, arguing that human societies need to conquer territory and resources to prosper, and that the stronger and fittest civilizations will naturally prevail over the weaker ones [12]. In 1901, Ratzel coined the term Lebensraum to describe this need for “vital space” as a geographical factor in national power [15].
Subsequently, this idea would be adopted—and extremely distorted—by Nazi ideology to justify Germany’s aggressions in Europe. However, the core of Ratzel’s concept is that territorial expansion is essential for the survival and growth of a State, especially to secure food, raw materials, and space for its population [12].
When examining Russia’s stance under this perspective, we can see several narratives that evoke the logic of Lebensraum. Russia is the largest country in the world by area; however, much of its territory is characterized by adverse climates (tundra, taiga) and is relatively sparsely populated in Siberia. On the other hand, adjacent regions such as Ukraine possess highly arable lands (chernozem—black soil), significant Slavic population density, and additional natural resources (coal in the Donbass, for example). An implicit justification for Russian expansion could be the search for supplementary resources and fertile lands to secure its self-sufficiency and power—exactly as Ratzel described that vigorous nations do. Historical records show that Ratzel emphasized agrarian primacy: he believed that new territories should be colonized by farmers, providing the food base for the nation [12]. Ukraine, historically called the “breadbasket of Europe,” fits perfectly into this vision of conquest for sustenance and agricultural wealth.
Furthermore, Ratzel viewed geography as a determinant of the destiny of nations—peoples adapted to certain habitats seek to expand them if they aspire to grow. In contemporary Russian discourse, there is often mention of the need to ensure security and territorial depth in the face of NATO, or to unite brotherly peoples (Russians and Russian speakers) within a single political space. Such arguments can be read as a modern translation of Lebensraum: the idea that the Russian nation, in order to be secure and flourish, must control a larger space, encompassing buffer zones and critical resources. This Russian “vital space” would naturally include Ukraine and other former Soviet republics, given the historical and infrastructural interdependence. Ratzel emphasized that peoples migrated and expanded when their original homeland no longer met their needs or aspirations [12]. Although contemporary Russia does not suffer from demographic pressure (on the contrary, it faces population decline), under the logic of a great power there is indeed a sentiment of geopolitical insufficiency for having lost influence over areas considered strategic. Thus, reconquering these areas would mean recovering the “habitat” necessary for the Russian nation to prosper and feel secure.
It is important to mention that, in Ratzel’s and Kjellén’s formulations, the pursuit of Lebensraum or organic expansion is not morally qualified—it is treated as a natural process in the politics of power. Thus, on the discursive level, Russia can avoid overly aggressive rhetoric and resort to “natural” justifications: for example, claiming that it needs to occupy Ukraine for defensive purposes (security space) or to reunify peoples (a common cultural and historical space). Beneath these justifications, however, resonates the geopolitical imperative to acquire more territory and resources as a guarantee of national survival, something consonant with Ratzel’s theory. In fact, Russian Realpolitik frequently prioritizes the control of energy resources (gas, oil) and transportation routes. Expanding its influence over central Eurasia would also mean controlling oil pipelines, gas lines, and logistical corridors—essential elements of modern Lebensraum understood as access to vital resources and infrastructure.
In summary, by conquering Ukraine and extending its reach into Eurasia, Russia could effectively invoke the concept of Lebensraum: presenting its expansion not as mere imperialism, but as a necessity to secure indispensable lands and resources for its people and to correct the “injustice” of a vital space diminished by post-Cold War territorial losses. The theories of Ratzel and Kjellén together paint a picture in which Russian expansion emerges almost as a natural law—the great State reclaiming space to ensure its survival and development at the expense of smaller neighbors.
Trump, NATO, and the Threat of American Withdrawal
One of the most alarming changes with Trump's return to power is the tense relationship with the North Atlantic Treaty Organization (NATO). Trump has long criticized allies for not meeting military spending targets, even threatening during his first term to withdraw the US from the alliance if members did not increase their contributions [2]. This threat, initially viewed with skepticism, became concrete after his re-election, leading European allies to seriously consider the possibility of having to defend themselves without American support [1]. In fact, Trump suggested in post-election interviews that the US would only remain in NATO if the allies “paid their bills” – otherwise, he “would seriously consider” leaving [2]. Such statements reinforced the warning that the US might not honor NATO's mutual defense commitment, precisely at a time of continuous Russian threat due to the war in Ukraine [1].
From a theoretical point of view, this posture of American retrenchment evokes the classic tension between maritime power and land power. Alfred Thayer Mahan emphasized that the global power of the US derived largely from its naval superiority and from alliances that ensured control over strategic maritime routes [9]. NATO, since 1949, has served not only to deter Soviet terrestrial advances in Eurasia, but also to secure the US naval presence in the North Atlantic and the Mediterranean – a fundamental element according to Mahan. In turn, Halford Mackinder warned that the balance of global power depended on the control of the Eurasian “Heartland” (the central region of Eurasia). The withdrawal or disengagement of the US (a maritime power) from this region could open the way for a continental power (such as Russia) to expand its influence in Eastern Europe, unbalancing the power balance [3]. In other words, by threatening to leave NATO, Trump jeopardizes the principle of containment that prevented Russian dominance over Eastern Europe – something that Mackinder would see as a dangerous shift in global power in favor of the Heartland power.
Adopting an impartial tone, it is observed that European countries have reacted to this new reality with precautionary measures. Strategic reports already calculate the cost of an autonomous European defense: hundreds of thousands of additional soldiers and investments of hundreds of billions of euros would be required if the US ceased to guarantee the security of the continent [1]. European dependence on American military power is significant and, without it, there would be a need for a major reinforcement of European Armed Forces [1]. This mobilization practically reflects the anticipation of a power vacuum left by the US – a scenario in which Mackinder’s theory (on the primacy of the Heartland and the vulnerability of the “external crescent” where Western Europe is located) regains its relevance.
The US–Ukraine Economic Agreement: Strategic Minerals in Exchange for Support?
Another novelty of Trump's second term is the unprecedented and transactional manner in which Washington has been dealing with the war in Ukraine. Instead of emphasizing security guarantees and alliances, the Trump administration proposed a trade agreement with Ukraine focused on the exploitation of strategic minerals, linking American support to a direct economic benefit. According to sources close to the negotiations, the US and Ukraine are about to sign a pact to share the revenues from the exploitation of critical mineral resources on Ukrainian territory [19]. Materials such as titanium, lithium, rare earths, and uranium – vital for high-tech and defense industries – would be at the core of this agreement [6]. According to the known draft, Ukraine would allocate 50% of the profits from new mineral ventures to a fund controlled by the US, which would reinvest part of the resources in the country’s own reconstruction [6] [19].
It is noteworthy that the pact does not include explicit security guarantees for Kyiv, despite Ukraine remaining under direct military threat from Russia [19]. Essentially, the Trump administration offers financial support and economic investment in exchange for a share in Ukrainian natural resources, but without formally committing to Ukraine's defense in the event of a renewed Russian offensive [19]. American authorities argue that this economic partnership would already be sufficient to “secure Ukrainian interests,” as it would provide the US with its own incentives to desire Ukraine’s stability [19]. “What could be better for Ukraine than being in an economic partnership with the United States?” stated Mike Waltz, a US national security advisor, defending the proposal [19].
Analysts, however, assess the agreement in divided terms. For some, it represents a form of economic exploitation at a time of Ukraine's fragility – comparing the demand to share mineral wealth amid war to a scheme of “mafia protection” [19]. Steven Cook, from the Council on Foreign Relations, classified the offer as “extortion,” and political scientist Virginia P. Fortna observed that charging resources from an invaded country resembles predatory practices [19]. Joseph Nye adds that it is a short-term gain strategy that could be “disastrous in the long run” for American credibility, reflecting the transactional approach that Trump even adopted with close allies in other contexts [19]. On the other hand, some see a future advantage for Kyiv: journalist Pierre Briançon suggests that at least this agreement aligns American commercial interests with Ukraine’s future, which could, in theory, keep the US involved in Ukrainian prosperity in the long term [19]. It is even recalled that President Zelensky himself proposed last year the idea of sharing natural resources with the US to bring the interests of the two countries closer together [19].
From the perspective of geopolitical theories, this agreement illustrates a shift towards economic pragmatism in international relations, approaching concepts proposed by Kjellén. Rudolf Kjellén, who coined the term “geopolitics,” saw the State as a territorial organism that seeks to ensure its survival through self-sufficiency and the control of strategic resources [4]. Trump's demand for a share in Ukrainian resources in order to continue supporting the country reflects a logic of autarky and direct national interest – that is, foreign policy serving primarily to reinforce the economic and material position of the US. This view contrasts with the traditional cooperative approach, but aligns with Kjellén’s idea that powerful States tend to transform international relations into opportunities for their own gain, ensuring access to vital raw materials. Similarly, Friedrich Ratzel argued that States have a “propensity to expand their borders according to their capacities,” seeking vital space (Lebensraum) and resources to sustain their development [11]. The US–Ukraine pact, by conditioning military/economic aid on obtaining tangible advantages (half of the mineral profits), is reminiscent of Ratzel’s perspective: the US, as a rising economic power, expands its economic influence over Ukrainian territory like an organism extending itself to obtain the necessary resources for its well-being. It is, therefore, a form of economic expansionism at the expense of purely ideological commitments or collective security.
Peace Negotiations Excluding Ukraine and the Legitimacy of the Agreement
Another controversial point is the manner in which peace negotiations between Russia and the West have been conducted under Trump's administration. Since taking office, the American president has engaged directly with Moscow in pursuit of a ceasefire, deliberately keeping the Ukrainian government out of the initial discussions [6]. Trump expressed his desire to “leave Zelensky out of the conversation” and also excluded the European Union from any influence in the process [6]. This negotiation strategy—conducted without the presence of the primary interested party, Ukraine—raises serious questions about the legitimacy and sustainability of any resulting agreement.
Historically, peace agreements reached without the direct participation of one of the conflicting parties tend to face problems in implementation and acceptance.
The exclusion of Ukraine in the decision-making phase brings to light the issue of guarantees. As noted, the emerging agreement lacks formal US security guarantees for Ukraine. This implies that, after the agreement is signed, nothing will prevent Russia from launching a new offensive if it deems it convenient, knowing that the US has not committed to defending it militarily. Experts have already warned that a ceasefire without robust protection may only be a pause for Russian rearmament, rendering the conflict “frozen” temporarily and potentially resumed in the near future. The European strategic community has expressed similar concern: without American deterrence, the risk of further Russian aggressions in the region increases considerably [1]. Denmark, for example, has released intelligence reports warning of possible imminent Russian attacks, prompting neighboring countries to accelerate plans for independent defense [1].
The legitimacy of this asymmetric peace agreement (negotiated without Ukraine fully at the table and under economic coercion) is also questionable from a legal and moral point of view. It violates the principle of self-determination by imposing terms decided by great powers on a sovereign country—a practice reminiscent of dark chapters in diplomacy, such as the Munich Agreement of 1938, when powers determined the fate of Czechoslovakia without its consent. In the current case, Ukraine would end up signing the agreement, but from a position of weakness, raising doubts about how durable such a commitment would be.
From Mackinder’s perspective, Ukraine’s removal from the battlefield without guarantees essentially means admitting a greater influence of Russia (the Heartland power) over Eastern Europe. This would alter the balance in Eurasia in a potentially lasting way. Furthermore, the fact that great powers negotiate over the heads of a smaller country evokes the imperial logic of the nineteenth and early twentieth centuries, when empires decided among themselves the divisions of foreign territories—a behavior that Mackinder saw as likely in a world of a “closed system.” With the entire world already occupied by States, Mackinder predicted that powers would begin to compete for influence within this consolidated board, often subjugating smaller states to gain advantage [3]. The US–Russia negotiation regarding Ukraine, without proper Ukrainian representation, exemplifies this type of neo-imperial dynamic in the twenty-first century.
Also noteworthy is the consonance with the ideas of Ratzel and Kjellén: both viewed smaller states as easily relegated to the status of satellites or even “parasitic organisms” in the orbit of larger states. Kjellén spoke of the intrinsic vulnerability of states with little territorial depth or economic dependence, making them susceptible to external pressures [4][20]. Ukraine, weakened by war and dependent on external aid, becomes a concrete example of this theorized vulnerability: it has had to cede strategic resources and accept terms dictated against its will in an attempt to secure its immediate survival. The resulting agreement, therefore, reflects a power imbalance characteristic of the hierarchical international relations described by classical geopolitical theorists.
Implicit Territorial Concessions and Trump’s Public Discourse
A central and controversial point in Trump’s statements regarding the war in Ukraine is the insinuation of territorial concessions to Russia as part of the conflict’s resolution. Publicly, Trump avoided explicitly condemning Russian aggression and even stated that he considered it “unlikely” that Ukraine would be able to retake all the areas occupied by the Russians [16]. In debates and interviews, he suggested that “if I were president, the war would end in 24 hours,” implying that he would force an understanding between Kyiv and Moscow that would likely involve ceding some territory in exchange for peace. This position marks a break with the previous US policy of not recognizing any territorial acquisitions made by force and fuels speculations that a future peace agreement sponsored by Trump would legitimize at least part of Russia’s gains since 2014 (Crimea, Donbass, and areas seized during the 2022 invasion).
The actions of his administration corroborate this interpretation. As discussed, the economic agreement focuses on the exploitation of Ukrainian natural resources, many of which are located precisely in regions currently under Russian military control, such as parts of the Zaporizhzhia Oblast, Donetsk, Lugansk, and the Azov Sea area [6]. A Ukrainian geologist, Hanna Liventseva, highlighted that “most of these elements (strategic minerals) are found in the south of the Ukrainian Shield, mainly in the Azov region, and most of these territories are currently invaded by Russia” [6]. This means that, to make joint exploitation viable, Russia’s de facto control over these areas would have to be recognized—or at least tolerated—in the short term. In other words, the pact indirectly and tacitly accepts Russian territorial gains, as it involves sharing the profits from resources that are not currently accessible to the Kyiv government.
Furthermore, figures close to Trump have made explicit statements regarding the possibility of territorial cession. Mike Waltz, Trump’s national security advisor, publicly stated that Zelensky might need to “cede land to Russia” to end the war [8]. This remark—made public in March 2025—confirms that the Trump White House considers it natural for Ukraine to relinquish parts of its territory in favor of an agreement. Such a stance marks a break from the previous Western consensus, which condemned any territorial gains by force. Under Trump, a pragmatic view (in the eyes of his supporters) or a cynical one (according to his critics) seems to prevail: sacrificing principles of territorial integrity to quickly end hostilities and secure immediate economic benefits.
In theoretical terms, this inclination to validate territorial gains by force recalls the concept of Realpolitik and the geopolitical Darwinism that influenced thinkers such as Ratzel. In Ratzel’s organic conception, expanding states naturally absorb neighboring territories when they are strong enough to do so, while declining states lose territory—a process almost biological in the selection of the fittest [11]. The Trump administration’s acceptance that Ukraine should “give something” to Moscow to seal peace reflects a normalization of this geopolitical selection process: it recognizes the aggressor (Russia) as having the “right” to retain conquered lands, because that is how power realities on the ground dictate. Mackinder, although firmly opposed to allowing Russia to dominate the Heartland, would see this outcome as the logical consequence of the lack of engagement from maritime powers (the USA and the United Kingdom, for example) in sustaining the Ukrainian counterattack. Without the active involvement of maritime power to balance the dispute, land power prevails in Eastern Europe.
From the perspective of international legitimacy, the cession of Ukrainian territories—whether de jure or de facto—creates a dangerous precedent in the post-Cold War era. Rewarding violent aggression with territorial gains may encourage similar strategies in other parts of the world, undermining the architecture of collective security. This is possibly a return to a world of spheres of influence, where great powers define borders and zones of control according to their convenience—something that the rules-based order after 1945 sought to avoid. Here, academic impartiality requires noting that coercion for territorial concessions rarely produces lasting peace, as the aggrieved party—in this case, Ukraine—may accept temporarily but will continue to assert its rights in the long term, as has occurred with other territorial injustices in history.
Territorial Ambitions of Trump: Greenland and Canada
Beyond the Eurasian theater of war, Trump revived geopolitical ambitions involving territories traditionally allied with the US: Greenland (an autonomous territory of Denmark) and Canada. As early as 2019, during his first term, Trump shocked the world by proposing to buy Greenland—rich in minerals and strategically positioned in the Arctic. Upon his return to power, he went further: expressing a “renewed interest” in acquiring Greenland and publicly suggesting the incorporation of Canada as the 51st American state [2].
In January 2025, during a press conference at Mar-a-Lago, he even displayed maps in which the US and Canada appeared merged into a single country, while Greenland was marked as a future American possession [2]. Posts by the president on social media included satirical images with a map of North America where Canada was labeled “51st” and Greenland designated as “Our Land” [2].
Such moves were met with concern and disbelief by allies. Canadian Prime Minister Justin Trudeau was caught on an open microphone warning that Trump’s fixation on annexation “is real” and not just a joke [7]. Trudeau emphasized that Washington appeared to covet Canada’s vast mineral resources, which would explain the insistence on the idea of absorption [7]. In public, Trump argued that Canadians “would be more prosperous as American citizens,” promising tax cuts and better services should they become part of the US [7]. On the Danish side, the reaction to the revived plan regarding Greenland was firmly negative—as it was in 2019—reaffirming that the territory is not for sale. Trump, however, insinuated that the issue might be one of national security, indicating that American possession of Greenland would prevent adverse influences (a reference to China and Russia in the Arctic) [2]. More worryingly, he refused to rule out the use of military means to obtain the island, although he assured that he had no intention of invading Canada by force (in the Canadian case, he spoke of “economic force” to forge a union) [2].
This series of initiatives reflects an unprecedented expansionist impetus by the US in recent times, at least in discourse. Analyzing this through the lens of classical geopolitics offers interesting insights. Friedrich Ratzel and his notion of Lebensraum suggest that powerful states, upon reaching a certain predominance, seek to expand their territory by influencing or incorporating adjacent areas. Trump, by targeting the immediate neighbor (Canada) and a nearby strategic territory (Greenland), appears to resurrect this logic of territorial expansion for the sake of gaining space and resources. Ratzel saw such expansion almost as a natural process for vigorous states, comparable to the growth of an organism [11]. From this perspective, the US would be exercising its “right” of expansion in North America and the polar region, integrating areas of vital interest.
Additionally, Alfred Mahan’s view on maritime power helps to understand the strategic value of Greenland. Mahan postulated that control of key maritime chokepoints and naval bases ensures global advantage [9]. Greenland, situated between the North Atlantic and the Arctic, has become increasingly relevant as climate change opens new polar maritime routes and reveals vast mineral deposits (including rare earth elements and oil). For the US, having a presence or sovereignty over Greenland would mean dominating the gateway to the Arctic and denying this space to rivals. This aligns with Mahan’s strategy of securing commercial and military routes (in this case, potential Arctic routes) and resources to consolidate naval supremacy. On the other hand, the incorporation of Canada—with its enormous territory, Arctic coastline, and abundant natural resources—would provide the US with formidable geoeconomic and geopolitical reinforcement, practically eliminating vulnerabilities along its northern border. This is an ambitious project that also echoes ideas of Kjellén, for whom an ideal State should seek territorial completeness and economic self-sufficiency within its region. Incorporating Canada would be the pinnacle of American regional autarky, turning North America into a unified bloc under Washington (a scenario reminiscent of the “pan-regions” conceived by twentieth-century geopoliticians influenced by Kjellén).
It is important to note, however, that these ambitions face enormous legal and political obstacles. The sovereignty of Canada and Greenland (Denmark) is guaranteed by international law, and both peoples categorically reject the idea of annexation. Any hostile action by the US against these countries would shake alliances and the world order itself. Even so, the very fact that an American president suggests such possibilities already produces geopolitical effects: traditional partners begin to distrust Washington’s intentions, seek alternative alliances, and strengthen nationalist discourses of resistance. In summary, Trump’s expansionist intentions in Greenland and Canada rekindle old territorial issues and paradoxically place the US in the position of a revisionist power—a role once associated with empires in search of colonies.
Implications for Brazil and South America: A New Neocolonization?
In light of this geopolitical reconfiguration driven by Trump's USA—with a reordering of alliances and a possible partition of spheres of influence among great powers—the question arises: what is the impact on Brazil and the other countries of South America? Traditionally, Latin America has been under the aegis of the Monroe Doctrine (1823), which established non-interference by Europe in the region and, implicitly, the primacy of the USA in the Western Hemisphere. In the post–Cold War period, this influence translated more into political and economic leadership, without formal annexations or direct territorial domination. However, the current context points to a kind of “neocolonization” of the Global South, in which larger powers seek to control resources and peripheral governments in an indirect yet effective manner.
Mackinder’s theories can be used to illuminate this dynamic. As mentioned, Mackinder envisioned the twentieth-century world as a closed system, in which there were no longer any unknown lands to be colonized—hence, the powers would fight among themselves for control over already occupied regions [3]. He predicted that Africa and Latin America (then largely European colonies or semi-colonies) would continue as boards upon which the great powers would project their disputes, a form of neocolonialism. In the current scenario, we see the USA proposing exchanges of protection for resources (as in Ukraine) and even leaders of developing countries seeking similar agreements. A notable example: the President of the Democratic Republic of the Congo, Felix Tshisekedi, praised the USA–Ukraine initiative and suggested an analogous agreement involving Congolese mineral wealth in exchange for US support against internal rebels (M23) [19]. In other words, African countries and possibly South American ones may enter into this logic of offering privileged access to resources (cobalt, lithium, food, biodiversity) in order to obtain security guarantees or investments. This represents a regression to the times when external powers dictated the directions of the South in exchange for promises of protection, characterizing a strategic neocolonialism.
For Brazil, in particular, this rearrangement generates both opportunities and risks. As a regional power with considerable diplomatic autonomy, Brazil has historically sought to balance relationships with the USA, Europe, China, and other actors, avoiding automatic alignments. However, in a world where Trump’s USA is actively redefining spheres of influence—possibly making deals with Russia that divide priorities (for example, Washington focusing on the Western Hemisphere and Moscow on the Eastern)—South America could once again be seen as an exclusive American sphere of influence. From this perspective, Washington could pressure South American countries to align with its directives, limiting partnerships with rivals (such as China) and seeking privileged access to strategic resources (such as the Amazon, fresh water, minerals, and agricultural commodities). Some indications are already emerging: Trump’s transactional approach mentioned by Nye included pressures on Canada and Mexico regarding border and trade issues, under the threat of commercial sanctions. It would not be unthinkable to adopt a hard line, for example, with regard to Brazilian environmental policies (linked to the Amazon) or Brazil’s relations with China, using tariffs or incentives as leverage—a sort of geopolitics of economic coercion.
On the other hand, Brazil and its neighbors could also attempt to take advantage of the Sino–North American competition. If the USA is distracted consolidating its hemispheric “hard power” hegemony (even with annexation fantasies in the north), powers such as China may advance their economic presence in South America through investments and trade (Belt and Road, infrastructure financing)—which is already happening. This would constitute an indirect neocolonial dispute in the South: Chinese loans and investments versus American demands and agreements, partly reminiscent of the nineteenth-century imperial competition (when the United Kingdom, USA, and others competed for Latin American markets and resources).
From a conceptual standpoint, Mackinder might classify South America as part of the “Outer Crescent” (external insular crescent)—peripheral to the great Eurasian “World-Island,” yet still crucial as a source of resources and a strategic position in the South Atlantic and Pacific. If the USA consolidates an informal empire in the Americas, it would be reinforcing its “insular bastion” far from the Eurasian Heartland, a strategy that Mackinder once suggested for maritime powers: to control islands and peripheral continents to compensate for the disadvantage of not controlling the Heartland. However, an excessive US dominance in the South could lead to local resistance and alternative alignments, unbalancing the region.
Kjellén would add that for Brazil to maintain its decisive sovereignty, it will need to strengthen its autarky and internal cohesion—in other words, reduce vulnerabilities (economic, military, social) that external powers might exploit [4]. Meanwhile, Mahan might point out the importance for Brazil of controlling its maritime routes and coastlines (South Atlantic) to avoid being at the mercy of a naval power like the USA. And Ratzel would remind us that states that do not expand their influence tend to be absorbed by foreign influences—which, in the context of Brazil, does not mean conquering neighboring territories, but rather actively leading South American integration to create a block more resilient to external intrusion.
In summary, South America finds itself in a more competitive and segmented world, where major players are resurrecting practices from past eras. The notion of “neocolonization” here does not imply direct occupation, but rather mechanisms of dependency: whether through unequal economic agreements or through diplomatic or military pressure for alignment. Brazil, as the largest economy and territory on the subcontinent, will have to navigate with heightened caution. A new global power balance, marked by the division of spheres of influence among the USA, China, and Russia, may reduce the sovereign maneuvering space of South American countries unless they act jointly. Thus, theoretical reflection suggests the need for South–South strategies, reinforcement of regional organizations, and diversification of partnerships to avoid falling into modern “neocolonial traps.”
Conclusion
The emerging post–re-election geopolitical conjuncture of Donald Trump signals a return to classical geopolitical principles, after several decades of predominance of institutional liberal views. We witness the revaluation of concepts such as spheres of influence, exchanges of protection for resources, naval power versus land power, and disputes over territory and raw materials—all central themes in the writings of Mackinder, Mahan, Kjellén, and Ratzel at the end of the nineteenth and the beginning of the twentieth century. An impartial analysis of these events, in light of these theories, shows internal coherence in Trump’s actions: although controversial, they follow a logic of maximizing national interest and the relative power of the USA on the world stage, even at the expense of established principles and alliances.
Halford Mackinder reminds us that, in a closed world with no new lands to conquer, the great powers will seek to redistribute the world among themselves [3]. This seems to manifest in the direct understandings between the USA and Russia over the fate of Ukraine, and in American ambitions in the Arctic and the Western Hemisphere. Alfred Mahan emphasizes that the control of the seas and strategic positions ensures supremacy—we see reflections of this in Trump’s obsession with Greenland (Arctic) and the possible neglect of the importance of maintaining NATO (and therefore the North Atlantic) as a cohesive bloc, something that Mahan’s theory would criticize due to the risk of a naval vacuum. Rudolf Kjellén and Friedrich Ratzel provide the framework to understand the more aggressive facet of expansionist nationalism: the idea of the State as an organism that needs to grow, secure resources, and seek self-sufficiency explains everything from the extortionate agreement imposed on Ukraine to the annexation rhetoric regarding Canada.
The potential consequences are profound. In the short term, we may witness a precarious ceasefire in the Ukraine war, with consolidated Russian territorial gains and Ukraine economically tied to the USA, but without formal military protection—a fragile “armed peace.” Western Europe, alarmed, may accelerate its independent militarization, perhaps marking the beginning of European defense autonomy, as is already openly debated [1]. At the far end of the globe, American activism in the Arctic and the Americas may reshape alliances: countries like Canada, once aligned with Washington, might seek to guarantee their sovereignty by distancing themselves from it; powers like China could take advantage of the openings to increase their presence in Latin America and Africa through economic diplomacy; and emerging countries of the Global South may have to choose between submitting to new “guardianships” or strengthening South–South cooperation.
Ultimately, the current situation reinforces the relevance of studying geopolitics through historical lenses. The actions of the Trump administration indicate that, despite all technological and normative advances, the competition for geographic power has not disappeared—it has merely assumed new formats. Academic impartiality obliges us not to prematurely judge whether these strategies will be successful or beneficial, but history and theory warn that neo-imperial movements tend to generate counter-reactions. As Mackinder insinuated, “every shock or change anywhere reverberates around the world,” and a sudden move by a superpower tends to provoke unforeseen adjustments and chain conflicts. It remains to be seen how the other actors—including Brazil and its neighbors—will adapt to this new chapter in the great struggle for global power, in which centuries-old theories once again have a surprising explanatory power over present events.
Bibliography
[1] A Referência. (2025). Europa calcula o custo de se defender sem os EUA: 300 mil soldados e 250 bilhões de euros a mais. Recuperado em 3 de março de 2025, de https://areferencia.com/europa/europa-calcula-o-custo-de-se-defender-sem-os-eua-300-mil-soldados-e-250-bilhoes-de-euros-a-mais/#:\~:text=Europa%20calcula%20o%20custo%20de,bilh%C3%B5es%20de%20euros%20a%20mais
[2] Brexit Institute. (2025). What happens if Trump invades Greenland? Recuperado em 3 de março de 2025, de https://dcubrexitinstitute.eu/2025/01/what-happens-if-trump-invades-greenland/#:\~:text=Ever%20since%20Donald%20Trump%20announced,agreed%20in%20Wales%20in%202014
[3] Cfettweis C:CST22(2)8576.DVI. (2025). Mackinder and Angell. Recuperado em 3 de março de 2025, de https://cfettweis.com/wp-content/uploads/Mackinder-and-Angell.pdf#:\~:text=meant%20the%20beginning%20of%20an,Mackinder
[4] Diva-Portal. (2025). The geopolitics of territorial relativity. Poland seen by Rudolf Kjellén. Recuperado em 3 de março de 2025, de https://www.diva-portal.org/smash/get/diva2:1696547/FULLTEXT02#:\~:text=,The%20state%20territory
[5] Geopolitical Monitor. (2025). The Russo-Ukrainian War and Mackinder’s Heartland Thesis. Recuperado em 3 de março de 2025, de https://www.geopoliticalmonitor.com/the-ukraine-war-and-mackinders-heartland-thesis/#:\~:text=In%201904%2C%20Sir%20Halford%20J,in%20adding%20a%20substantial%20oceanic
[6] Instituto Humanitas Unisinos. (2025). Trump obriga Zelensky a hipotecar a exploração de minerais críticos em troca do seu apoio. Recuperado em 3 de março de 2025, de https://www.ihu.unisinos.br/648986-trump-obriga-zelensky-a-hipotecar-a-exploracao-de-minerais-criticos-em-troca-do-seu-apoio#:\~:text=Essa%20troca%20inclui%20os%20cobi%C3%A7ados,s%C3%A3o%20praticamente%20inexploradas%20no%20pa%C3%ADs
[7] Politico. (2025). Trump’s annexation fixation is no joke, Trudeau warns. Recuperado em 3 de março de 2025, de https://www.politico.com/news/2025/02/07/canada-trudeau-trump-51-state-00203156#:\~:text=TORONTO%20%E2%80%94%20Prime%20Minister%20Justin,Canada%20becoming%20the%2051st%20state%2C%E2%80%9D%20Trudeau%20said
[8] The Daily Beast. (2025). Top Trump Adviser Moves Goalpost for Ukraine to End War. Recuperado em 3 de março de 2025, de https://www.thedailybeast.com/top-trump-adviser-moves-goalpost-for-ukraine-to-end-war/#:\~:text=LAND%20GRAB
[9] The Geostrata. (2025). Alfred Thayer Mahan and Supremacy of Naval Power. Recuperado em 3 de março de 2025, de https://www.thegeostrata.com/post/alfred-thayer-mahan-and-supremacy-of-naval-power#:\~:text=Alfred%20Thayer%20Mahan%20and%20Supremacy,control%20over%20maritime%20trade%20routes
[10] U.S. Department of State. (2025). Mahan’s The Influence of Sea Power upon History: Securing International Markets in the 1890s. Recuperado em 3 de março de 2025, de https://history.state.gov/milestones/1866-1898/mahan#:\~:text=Mahan%20argued%20that%20British%20control,American%20politicians%20believed%20that%20these
[11] Britannica. (2025a). Friedrich Ratzel | Biogeography, Anthropogeography, Political Geography. Recuperado em 3 de março de 2025, de https://www.britannica.com/biography/Friedrich-Ratzel#:\~:text=webster,Swedish%20political%20scientist%20%2076
[12] Britannica. (2025b). Lebensraum. Recuperado em 3 de março de 2025, de https://www.britannica.com/topic/Lebensraum#:\~:text=defined,The
[13] Britannica. (2025c). Rudolf Kjellén. Recuperado em 3 de março de 2025, de https://www.britannica.com/biography/Rudolf-Kjellen
[14] Wikipedia (ZH). (2025). Rudolf Kjellén. Recuperado em 3 de março de 2025, de https://zh.wikipedia.org/wiki/w:Rudolf_Kjell%C3%A9n#:\~:text=Besides%20legalistic%2C%20states%20have%20organic,preservation.%20%5B%203
[15] Wikipedia. (2025). Lebensraum. Recuperado em 3 de março de 2025, de https://en.wikipedia.org/wiki/Lebensraum#:\~:text=The%20German%20geographer%20and%20ethnographer,into%20the%20Greater%20Germanic%20Reich
[16] YouTube. (2025). Trump says Ukraine 'unlikely to get all land back' or join NATO [Vídeo]. Recuperado em 3 de março de 2025, de https://www.youtube.com/watch?v=BmHzAVLhsXU#:\~:text=Trump%20says%20Ukraine%20%27unlikely%20to,for%20it%20to%20join%20NATO
[17] U.S. Naval Institute. (2025) Operation World Peace. Recuperado em 3 de março de 2025, de https://www.usni.org/magazines/proceedings/1955/june/operation-world-peace#:\\~:text=“The Mahan doctrine%2C” according to,the word “airships” is more
[18] Emissary. (2024) Trump’s Greenland and Panama Canal Threats Are a Throwback to an Old, Misguided Foreign Policy. Recuperado em 3 de março de 2025, de https://carnegieendowment.org/emissary/2025/01/trump-greenland-panama-canal-monroe-doctrine-policy?lang=en
[19] A Referência. Acordo EUA-Ucrânia está praticamente fechado, mas analistas se dividem sobre quem sairá ganhando. Recuperado em 3 de março de 2025, de https://areferencia.com/europa/acordo-eua-ucrania-esta-praticamente-fechado-mas-analistas-se-dividem-sobre-quem-saira-ganhando/#:\\~:text=EUA e 17,o acordo a seu favor
[20] Wikipedia. (2025) Geopolitik. Recuperado em 3 de março de 2025, de https://en.wikipedia.org/wiki/Geopolitik#:\\~:text=Rudolph Kjellén was Ratzel's Swedish,Kjellén's State
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-07 14:30:14
@ 5d4b6c8d:8a1c1ee3
2025-03-07 14:30:14Somehow, the NFL just keeps being in the news. - A bunch of big name players have either been cut already or will certainly be cut and some others have made trade requests. - How did the combine shake up the draft picture? - The combination of depth and high-end talent at certain positions makes draft strategy interesting this year.
The NBA season is chugging along towards the finish line. - How are people watching NBA? I cancelled YouTubeTV after the Super Bowl and I hate League Pass. Are there better options? - The MVP race might be a done deal - The Raptors stink, but @grayruby holds out hope - For some reason Bam is of interest, despite the Heat being about as mid as a team can be
In other news, - We've got some contest updates for the territory - Ovi is closing in on the scoring record (Lebron getting to 50k points probably deserves a mention, too). Is it the era of old athletes or have we just gotten lucky with a few. - NHL trade deadline today: who got moved and did it matter? - Something about MLB teams playing in minor league parks: Why? - Lots of active sports markets at Predyx
Plus, anything the stackers want us to cover.
originally posted at https://stacker.news/items/906502
-
 @ 147ac18e:ef1ca1ba
2025-03-07 14:04:46
@ 147ac18e:ef1ca1ba
2025-03-07 14:04:46The world is on the brink of a technological shift, where artificial intelligence (AI) is becoming increasingly autonomous. With AI agents conducting transactions, hiring other AI agents, and managing digital assets, a critical question arises: What form of money will power this new AI-driven economy? The answer, as some industry experts predict, is Bitcoin.
The Rise of the Autonomous Economy
AI agents are no longer just tools executing predefined tasks; they are evolving into independent economic actors capable of initiating transactions, negotiating terms, and paying for services. The transaction volume within AI-driven economies is projected to be 100 times larger than human transactions, as each person may have dozens or even hundreds of AI agents working on their behalf. This creates an unprecedented demand for a seamless, efficient, and universally accepted form of digital money.
Why Bitcoin is the Natural Choice for AI Transactions
Bitcoin stands out as the ideal currency for AI-driven economies for several reasons:
-
Borderless and Permissionless: Unlike traditional banking systems that require identity verification (KYC/AML) and impose restrictions based on geography, Bitcoin allows AI agents to transact freely without human intervention.
-
Personless Transactions: AI agents, by nature, do not have legal identities, making it impossible for them to interact with banks or obtain credit cards. Bitcoin provides a neutral medium that does not require a legal entity to use it.
-
Energy-Backed Economy: AI agents function on computational power, which is an energy-intensive process. Bitcoin’s proof-of-work mechanism aligns well with this model, as it is also backed by computational energy. AI systems will inherently recognize Bitcoin as a valid medium of exchange due to this energy linkage.
-
Micropayments via Lightning Network: AI transactions will often involve micropayments—small fees for data processing, information retrieval, and digital labor. Traditional financial networks are inefficient in handling such transactions due to high fees and processing delays. The Bitcoin Lightning Network enables instant, low-cost micropayments, making it perfect for AI-to-AI financial interactions.
-
Immutability and Transparency: AI systems require trustless environments where transaction history cannot be altered or reversed. Bitcoin’s blockchain ensures that all transactions are transparent and immutable, reducing fraud and enabling verifiable AI-driven commerce.
The Symbiotic Growth of Bitcoin and AI
As AI-driven economies expand, Bitcoin adoption will accelerate in the following ways:
-
Increased Transaction Volume: With billions of AI transactions occurring daily, Bitcoin will see an explosion in on-chain and Lightning Network activity, solidifying its position as the world’s primary digital currency.
-
Institutional and Enterprise Adoption: As businesses integrate AI into their workflows, they will increasingly adopt Bitcoin to facilitate machine-to-machine payments, smart contracts, and decentralized finance (DeFi) solutions.
-
Regulatory Shift Towards Decentralized Currencies: Governments and financial institutions will have to acknowledge Bitcoin’s role in AI economies and adjust regulatory frameworks accordingly, further legitimizing its use.
-
Bitcoin as a Store of Value for AI: AI systems will not only use Bitcoin for transactions but may also accumulate it as a reserve asset due to its deflationary nature and finite supply.
The Future: Bitcoin as the De Facto AI Currency
As AI continues to reshape industries, Bitcoin is poised to become the backbone of an autonomous digital economy. The fusion of AI and Bitcoin will create a self-sustaining loop where AI agents fuel Bitcoin’s transactional utility, and Bitcoin’s decentralized nature enables AI’s economic autonomy. This symbiosis will not only drive Bitcoin adoption but could also redefine global economic structures.
In this AI-driven future, Bitcoin may not just be a currency for humans—it could very well be the native currency of artificial intelligence.
Episode link: https://fountain.fm/episode/Ds1qicPmbC3udErQ7J3z
-
-
 @ a012dc82:6458a70d
2025-03-07 13:17:07
@ a012dc82:6458a70d
2025-03-07 13:17:07In an era where digital currencies are becoming as commonplace as traditional banking, a groundbreaking development has emerged from the UK, capturing the attention of both financial experts and law enforcement agencies worldwide. The UK police have made a monumental discovery, uncovering a staggering $1.7 billion in Bitcoin, intricately linked to a vast investment fraud scheme with roots deep in China. This revelation not only highlights the growing issue of cybercrime and financial fraud but also showcases the sophisticated methods employed by criminals to exploit the digital currency landscape for illicit purposes.
Table of Contents
-
The Discovery
-
The Accusation
-
The Implications
-
The Investigation
-
The Broader Impact
-
Conclusion
-
FAQs
The Discovery
The astonishing discovery was made amidst the trial of Jian Wen, a 42-year-old UK citizen embroiled in allegations of money laundering connected to a massive $6 billion investment fraud scheme. This scheme, masterminded by Zhimin Qian, known to some as Yadi Zhang, has left approximately 130,000 investors in China in dire straits, their investments vanished into the ether. The UK police's breakthrough in tracing the Bitcoin linked to this scheme underscores the meticulous and technologically advanced tactics utilized by law enforcement to combat digital financial crimes. The ability to trace such a significant amount of Bitcoin back to a specific fraud case marks a significant achievement in the realm of financial crime investigation, reflecting the increasing capability of global law enforcement agencies to adapt to the challenges posed by the digital age.
The Accusation
Jian Wen finds herself at the center of this complex web of financial deceit, accused of attempting to launder the ill-gotten gains from the fraudulent scheme. Her alleged attempts to funnel these vast sums into the London real estate market, though ultimately unsuccessful, paint a vivid picture of the lengths to which individuals involved in such schemes will go to legitimize their criminal proceeds. Wen's steadfast denial of the allegations against her adds a layer of intrigue to the case, challenging prosecutors to untangle the sophisticated methods used to disguise the fraudulent origins of the funds. This case highlights the critical need for vigilance and sophistication in tracking financial transactions across the globe, as criminals increasingly turn to complex schemes and digital currencies to obscure their activities.
The Implications
The implications of this case extend far beyond the immediate legal battle unfolding in London. It shines a spotlight on the dark underbelly of the digital currency world, where anonymity and the lack of regulatory oversight can too easily be exploited for nefarious purposes. The use of Bitcoin and other cryptocurrencies in money laundering and fraud schemes poses significant challenges for regulators and law enforcement worldwide. This case serves as a stark reminder of the urgent need for international cooperation and regulatory harmonization to address the vulnerabilities of the digital financial system. As cryptocurrencies continue to gain mainstream acceptance, the need for enhanced regulatory frameworks and advanced technological tools to monitor and control digital financial transactions becomes increasingly apparent.
The Investigation
The investigation leading to the discovery of the $1.7 billion in Bitcoin is a testament to the evolving landscape of law enforcement in the digital age. The success of the UK police in tracing these funds highlights the advancements in forensic technology and the growing expertise within law enforcement agencies in navigating the complex world of cryptocurrency transactions. This case exemplifies the potential for collaboration between financial institutions, regulatory bodies, and international law enforcement agencies to combat financial crime effectively. The ability to trace and recover assets in cryptocurrency form represents a significant step forward in the global fight against money laundering and investment fraud, setting a precedent for future investigations.
The Broader Impact
The uncovering of this vast sum of Bitcoin linked to the China fraud scheme has far-reaching implications for the cryptocurrency market and the broader financial ecosystem. It raises critical questions about the security and stability of digital currencies and the potential for their misuse in criminal enterprises. This case could serve as a catalyst for change, prompting policymakers and regulators to implement more stringent controls on cryptocurrency transactions and enhance the transparency of digital financial systems. As the digital currency market continues to evolve, the lessons learned from this investigation will undoubtedly influence the development of policies and technologies designed to protect investors and maintain the integrity of the financial system.
Conclusion
The discovery of $1.7 billion in Bitcoin by the UK police marks a watershed moment in the fight against international financial fraud. As the trial against Jian Wen progresses, it promises to offer unprecedented insights into the mechanisms of cryptocurrency laundering and the global nature of financial crime. This case not only underscores the critical role of digital currencies in the modern financial landscape but also highlights the imperative for continuous vigilance, innovation, and cooperation among law enforcement, regulatory bodies, and the financial industry at large. In the quest to safeguard the integrity of the global financial market, the unraveling of this $1.7 billion Bitcoin mystery represents both a significant challenge and a vital opportunity for the future of financial security and crime prevention.
FAQs
Who is Jian Wen, and what are the accusations against her? Jian Wen is a 42-year-old UK citizen accused of attempting to launder the proceeds of a $6 billion investment fraud scheme from China by investing in high-value properties in London. She denies the allegations.
How did the UK police trace the Bitcoin linked to the fraud? The UK police utilized advanced forensic technology and collaborated with international law enforcement agencies to trace the Bitcoin transactions back to the fraud scheme, demonstrating their growing expertise in combating digital financial crimes.
What are the broader implications of this case for the cryptocurrency market? This case highlights the potential for misuse of cryptocurrencies in money laundering and fraud schemes, raising questions about the need for enhanced regulatory frameworks and technological tools to monitor digital financial transactions.
What does this case reveal about the challenges of combating financial crime in the digital age? The case underscores the complexities and challenges law enforcement faces in tracking and prosecuting financial crimes that exploit digital currencies, emphasizing the need for international cooperation and advanced technological capabilities.
How might this discovery influence future regulatory policies on cryptocurrencies? The discovery could prompt policymakers and regulators to implement stricter controls on cryptocurrency transactions and develop more transparent and secure digital financial systems to prevent their misuse in criminal activities.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ fcd81845:5c1832a7
2025-03-07 09:25:39
@ fcd81845:5c1832a7
2025-03-07 09:25:39Price Updates
In order to improve the services we offer, we are increasing the prices effective date March 6th 2025:
Here are the price changes (all prices are per month, rolling contract):
| name | Price | New Price | | ---- | ----- | --------- | | Tiny | 2 EUR | 2.70 EUR | | Small | 4 EUR | 5.10 EUR | | Medium | 8 EUR | 9.90 EUR | | Large | 17 EUR | 21.90 EUR | | X-Large | 30 EUR | 39.90 EUR | | XX-Large | 45 EUR | 55.50 EUR |
These changes coincide with the release of custom pricing!

We have also released a few other features:
- User configurable PTR records
- Separate billing page o VM info view
- VM resource usage graphs
- New VM's are assigned a forward DNS entry on lnvps.cloud (eg. vm-1.lnvps.cloud) existing VM's will have a forward entry added at a later date.
- As well as many other smaller improvements in the handling of resource allocation
-
 @ da0b9bc3:4e30a4a9
2025-03-07 06:27:17
@ da0b9bc3:4e30a4a9
2025-03-07 06:27:17Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/906261
-
 @ d360efec:14907b5f
2025-03-07 05:11:52
@ d360efec:14907b5f
2025-03-07 05:11:52Bitcoin (BTC) เผชิญกับการปรับฐานอย่างรุนแรงในวันที่ 7 มีนาคม 2568 หลังจากที่ราคาพุ่งขึ้นทำจุดสูงสุดใหม่ (All-Time High) อย่างต่อเนื่อง บทวิเคราะห์นี้จะเจาะลึกถึงสถานการณ์ปัจจุบันของ BTC โดยใช้การวิเคราะห์ทางเทคนิคจากหลาย Timeframe (15m, 4H, Day) พร้อมทั้งพิจารณาอินดิเคเตอร์สำคัญต่างๆ เพื่อประเมินแนวโน้มและกลยุทธ์การเทรดที่เหมาะสม
การวิเคราะห์ทางเทคนิค:
-
Timeframe 15 นาที (15m):
- เกิดการร่วงลงของราคาอย่างรุนแรง (Sell-Off) ทะลุแนวรับสำคัญหลายระดับ
- EMA 50 ตัด EMA 200 ลงมา (Death Cross) เป็นสัญญาณ Bearish ที่ชัดเจน
- Money Flow เป็นลบอย่างมาก
- Trend Strength เป็นเมฆสีแดงหนาแน่น (แนวโน้มขาลงแข็งแกร่ง)
- สรุป: แนวโน้มขาลงระยะสั้นชัดเจน
-
Timeframe 4 ชั่วโมง (4H):
- ราคาหลุดกรอบ Consolidation และ EMA 50
- EMA 50 ตัด EMA 200 ลงมา (Death Cross) ยืนยันสัญญาณ Bearish ระยะกลาง
- Money Flow เป็นลบ
- Trend Strength เป็นเมฆสีแดง
- แนวรับสำคัญอยู่ที่ EMA 200 (ประมาณ $60,000) และ $58,000
- สรุป: ยืนยันการปรับฐานระยะกลาง
-
Timeframe Day (Day):
- ราคายังคงอยู่เหนือ EMA 50 และ EMA 200 โครงสร้างขาขึ้นหลักยังไม่เสีย
- Money Flow ยังคงเป็นบวก (แม้จะเริ่มลดลง)
- Trend Strength เมฆสีเขียวยังคงอยู่ (แต่เริ่มบางลง)
- แนวรับสำคัญอยู่ที่ $60,000 (Low ก่อนหน้า) และ $50,000-$52,000 (EMA 200 และ Demand Zone)
- สรุป: แนวโน้มระยะยาวยังเป็นขาขึ้น แต่เริ่มมีสัญญาณอ่อนแรง
Buyside & Sellside Liquidity (สรุปจากทุก TF):
- Buyside Liquidity (แนวต้าน): $68,000-$69,000 (แนวต้านที่แข็งแกร่งในระยะสั้น), $72,000, $75,000 (เป้าหมายระยะยาว หากกลับเป็นขาขึ้น)
- Sellside Liquidity (แนวรับ): $60,000 (แนวรับสำคัญทางจิตวิทยา และ EMA 200 ใน TF 4H, Low ก่อนหน้าใน TF Day), $58,000 (Demand Zone ใน TF 4H), $50,000-$52,000 (EMA 200 และ Demand Zone ใน TF Day)
กลยุทธ์การเทรด:
- Day Trade (15m): ความเสี่ยงสูงมาก ไม่แนะนำให้ Buy เน้น Short Sell เมื่อราคา Rebound ขึ้นไปทดสอบแนวต้าน (EMA หรือบริเวณ $68,000-$69,000) และมีสัญญาณ Bearish แต่ต้องระมัดระวังอย่างยิ่ง เพราะขัดแย้งกับแนวโน้มหลักระยะยาว ตั้ง Stop Loss เหนือ Swing High
- Swing Trade (4H): ไม่แนะนำให้ Buy ตอนนี้ รอสัญญาณกลับตัวที่ชัดเจนกว่านี้ บริเวณแนวรับ EMA 200 ($60,000) หรือ $58,000 หากมีสัญญาณ Bullish ที่แนวรับเหล่านี้ ถึงจะพิจารณาเข้า Buy โดยตั้ง Stop Loss ต่ำกว่าแนวรับ
- Position Trade (Day): รอจังหวะที่แนวรับสำคัญ ($60,000 หรือ $50,000-$52,000) หรือรอสัญญาณกลับตัวที่ชัดเจน
สิ่งที่ต้องระวัง:
- ความผันผวนของราคา BTC ที่สูงมากในช่วงนี้
- ข่าวหรือเหตุการณ์ที่อาจส่งผลกระทบต่อตลาด
- False Breakout และ Dead Cat Bounce (การ Rebound สั้นๆ ก่อนลงต่อ)
- การสวน Trend มีความเสี่ยงสูงมาก
สรุป:
Bitcoin กำลังเผชิญกับการปรับฐานครั้งสำคัญ หลังจากที่ราคาพุ่งขึ้นอย่างต่อเนื่อง แนวโน้มระยะสั้น (15m) เป็นขาลงอย่างชัดเจน, ระยะกลาง (4H) ยืนยันการปรับฐาน, ส่วนระยะยาว (Day) ยังคงเป็นขาขึ้นแต่เริ่มอ่อนแรง นักลงทุนควรใช้ความระมัดระวังอย่างสูงในการเทรด Day Trader อาจพิจารณา Short Sell เมื่อมีสัญญาณ, Swing Trader ควรรอสัญญาณกลับตัวที่แนวรับ, ส่วน Position Trader ควรรอจังหวะที่แนวรับสำคัญ
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
-
 @ d360efec:14907b5f
2025-03-07 05:08:51
@ d360efec:14907b5f
2025-03-07 05:08:51$OKX: $BTC $USDT.P
Introduction:
Bitcoin (BTC) faced a sharp correction on March 7, 2025, after a continuous rally to new all-time highs. This analysis delves into the current situation of BTC using technical analysis from multiple timeframes (15m, 4H, Day), considering various key indicators to assess the trend and appropriate trading strategies.
Technical Analysis:
-
15-Minute Timeframe (15m):
- Experienced a sharp price drop (Sell-Off), breaking through several key support levels.
- EMA 50 crossed below EMA 200 (Death Cross), a clear Bearish signal.
- Money Flow is strongly negative.
- Trend Strength is a thick red cloud (strong downtrend).
- Conclusion: Clear short-term downtrend.
-
4-Hour Timeframe (4H):
- Price broke out of the consolidation range and below EMA 50.
- EMA 50 crossed below EMA 200 (Death Cross), confirming a medium-term Bearish signal.
- Money Flow is negative.
- Trend Strength is a red cloud.
- Key support is at EMA 200 (around $60,000) and $58,000.
- Conclusion: Confirms the medium-term correction.
-
Daily Timeframe (Day):
- The price remains above EMA 50 and EMA 200. The main uptrend structure is still intact.
- Money Flow remains positive (although starting to decrease).
- Trend Strength: The green cloud is still present (but starting to thin).
- Key support is at $60,000 (previous Low) and $50,000-$52,000 (EMA 200 and Demand Zone).
- Conclusion: The long-term trend is still uptrend, but signs of weakness are starting to appear.
Buyside & Sellside Liquidity (Summary from all TFs):
- Buyside Liquidity (Resistance): $68,000-$69,000 (strong resistance in the short term), $72,000, $75,000 (long-term targets if it turns bullish again).
- Sellside Liquidity (Support): $60,000 (key psychological support and EMA 200 on 4H TF, previous Low on Day TF), $58,000 (Demand Zone on 4H TF), $50,000-$52,000 (EMA 200 and Demand Zone on Day TF).
Trading Strategies:
- Day Trade (15m): Very high risk. Do not recommend Buy. Focus on Short Selling when the price rebounds to test resistance (EMA or the $68,000-$69,000 area) and there are Bearish signals. But be extremely careful as it contradicts the main long-term trend. Set a Stop Loss above the Swing High.
- Swing Trade (4H): Do not Buy now. Wait for clearer reversal signals around the EMA 200 support ($60,000) or $58,000. If there are Bullish signals at these supports, then consider entering a Buy with a Stop Loss below the support.
- Position Trade (Day): Wait for opportunities at key support levels ($60,000 or $50,000-$52,000) or wait for clear reversal signals.
Things to Watch Out For:
- Very high volatility of BTC price during this period.
- News or events that may affect the market.
- False Breakouts and Dead Cat Bounces (short rebounds before continuing to fall).
- Going against the trend is very high risk.
Summary:
Bitcoin is facing a significant correction after a continuous rally. The short-term trend (15m) is clearly bearish, the medium-term (4H) confirms the correction, while the long-term (Day) is still bullish but starting to weaken. Investors should be extremely cautious in trading. Day traders may consider Short Selling on signal, Swing traders should wait for reversal signals at support, and Position traders should wait for opportunities at key support levels.
Disclaimer: This analysis is a personal opinion and not investment advice. Investors should do their own research and make decisions carefully.
-
-
 @ c48e29f0:26e14c11
2025-03-07 04:51:09
@ c48e29f0:26e14c11
2025-03-07 04:51:09ESTABLISHMENT OF THE STRATEGIC BITCOIN RESERVE AND UNITED STATES DIGITAL ASSET STOCKPILE EXECUTIVE ORDER March 6, 2025
By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered:
Section 1. Background.
Bitcoin is the original cryptocurrency. The Bitcoin protocol permanently caps the total supply of bitcoin (BTC) at 21 million coins, and has never been hacked. As a result of its scarcity and security, Bitcoin is often referred to as “digital gold”. Because there is a fixed supply of BTC, there is a strategic advantage to being among the first nations to create a strategic bitcoin reserve. The United States Government currently holds a significant amount of BTC, but has not implemented a policy to maximize BTC’s strategic position as a unique store of value in the global financial system. Just as it is in our country’s interest to thoughtfully manage national ownership and control of any other resource, our Nation must harness, not limit, the power of digital assets for our prosperity.
Sec. 2. Policy.
It is the policy of the United States to establish a Strategic Bitcoin Reserve. It is further the policy of the United States to establish a United States Digital Asset Stockpile that can serve as a secure account for orderly and strategic management of the United States’ other digital asset holdings.
Sec. 3. Creation and Administration of the Strategic Bitcoin Reserve and United States Digital Asset Stockpile.
(a) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “Strategic Bitcoin Reserve,” capitalized with all BTC held by the Department of the Treasury that was finally forfeited as part of criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any executive department or agency (agency) and that is not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Government BTC). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Government BTC held by it to the Strategic Bitcoin Reserve and shall submit a report reflecting the result of that review to the Secretary of the Treasury. Government BTC deposited into the Strategic Bitcoin Reserve shall not be sold and shall be maintained as reserve assets of the United States utilized to meet governmental objectives in accordance with applicable law.
(b) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “United States Digital Asset Stockpile,” capitalized with all digital assets owned by the Department of the Treasury, other than BTC, that were finally forfeited as part of criminal or civil asset forfeiture proceedings and that are not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Stockpile Assets). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Stockpile Assets held by it to the United States Digital Asset Stockpile and shall submit a report reflecting the result of that review to the Secretary of the Treasury. The Secretary of the Treasury shall determine strategies for responsible stewardship of the United States Digital Asset Stockpile in accordance with applicable law.
(c) The Secretary of the Treasury and the Secretary of Commerce shall develop strategies for acquiring additional Government BTC provided that such strategies are budget neutral and do not impose incremental costs on United States taxpayers. However, the United States Government shall not acquire additional Stockpile Assets other than in connection with criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any agency without further executive or legislative action.
(d) “Government Digital Assets” means all Government BTC and all Stockpile Assets. The head of each agency shall not sell or otherwise dispose of any Government Digital Assets, except in connection with the Secretary of the Treasury’s exercise of his lawful authority and responsible stewardship of the United States Digital Asset Stockpile pursuant to subsection (b) of this section, or pursuant to an order from a court of competent jurisdiction, as required by law, or in cases where the Attorney General or other relevant agency head determines that the Government Digital Assets (or the proceeds from the sale or disposition thereof) can and should: (i) be returned to identifiable and verifiable victims of crime; (ii) be used for law enforcement operations;
(iii) be equitably shared with State and local law enforcement partners; or (iv) be released to satisfy requirements under 31 U.S.C. 9705, 28 U.S.C. 524(c), 18 U.S.C. 981, or 21 U.S.C. 881.(e) Within 60 days of the date of this order, the Secretary of the Treasury shall deliver an evaluation of the legal and investment considerations for establishing and managing the Strategic Bitcoin Reserve and United States Digital Asset Stockpile going forward, including the accounts in which the Strategic Bitcoin Reserve and United States Digital Asset Stockpile should be located and the need for any legislation to operationalize any aspect of this order or the proper management and administration of such accounts.
Sec. 4. Accounting.
Within 30 days of the date of this order, the head of each agency shall provide the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets with a full accounting of all Government Digital Assets in such agency’s possession, including any information regarding the custodial accounts in which such Government Digital Assets are currently held that would be necessary to facilitate a transfer of the Government Digital Assets to the Strategic Bitcoin Reserve or the United States Digital Asset Stockpile. If such agency holds no Government Digital Assets, such agency shall confirm such fact to the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets within 30 days of the date of this order.
Sec. 5. General Provisions.
(a) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department or agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 6, 2025
-
 @ d34e832d:383f78d0
2025-03-07 01:47:15
@ d34e832d:383f78d0
2025-03-07 01:47:15
A comprehensive system for archiving and managing large datasets efficiently on Linux.
1. Planning Your Data Archiving Strategy
Before starting, define the structure of your archive:
✅ What are you storing? Books, PDFs, videos, software, research papers, backups, etc.
✅ How often will you access the data? Frequently accessed data should be on SSDs, while deep archives can remain on HDDs.
✅ What organization method will you use? Folder hierarchy and indexing are critical for retrieval.
2. Choosing the Right Storage Setup
Since you plan to use 2TB HDDs and store them away, here are Linux-friendly storage solutions:
📀 Offline Storage: Hard Drives & Optical Media
✔ External HDDs (2TB each) – Use
ext4orXFSfor best performance.
✔ M-DISC Blu-rays (100GB per disc) – Excellent for long-term storage.
✔ SSD (for fast access archives) – More durable than HDDs but pricier.🛠 Best Practices for Hard Drive Storage on Linux
🔹 Use
smartctlto monitor drive health
bash sudo apt install smartmontools sudo smartctl -a /dev/sdX🔹 Store drives vertically in anti-static bags.
🔹 Rotate drives periodically to prevent degradation.
🔹 Keep in a cool, dry, dark place.☁ Cloud Backup (Optional)
✔ Arweave – Decentralized storage for public data.
✔ rclone + Backblaze B2/Wasabi – Cheap, encrypted backups.
✔ Self-hosted options – Nextcloud, Syncthing, IPFS.
3. Organizing and Indexing Your Data
📂 Folder Structure (Linux-Friendly)
Use a clear hierarchy:
plaintext 📁 /mnt/archive/ 📁 Books/ 📁 Fiction/ 📁 Non-Fiction/ 📁 Software/ 📁 Research_Papers/ 📁 Backups/💡 Use YYYY-MM-DD format for filenames
✅2025-01-01_Backup_ProjectX.tar.gz
✅2024_Complete_Library_Fiction.epub📑 Indexing Your Archives
Use Linux tools to catalog your archive:
✔ Generate a file index of a drive:
bash find /mnt/DriveX > ~/Indexes/DriveX_index.txt✔ Use
locatefor fast searches:
bash sudo updatedb # Update database locate filename✔ Use
Recollfor full-text search:
bash sudo apt install recoll recoll🚀 Store index files on a "Master Archive Index" USB drive.
4. Compressing & Deduplicating Data
To save space and remove duplicates, use:
✔ Compression Tools:
-tar -cvf archive.tar folder/ && zstd archive.tar(fast, modern compression)
-7z a archive.7z folder/(best for text-heavy files)✔ Deduplication Tools:
-fdupes -r /mnt/archive/(finds duplicate files)
-rdfind -deleteduplicates true /mnt/archive/(removes duplicates automatically)💡 Use
par2to create parity files for recovery:
bash par2 create -r10 file.par2 file.extThis helps reconstruct corrupted archives.
5. Ensuring Long-Term Data Integrity
Data can degrade over time. Use checksums to verify files.
✔ Generate Checksums:
bash sha256sum filename.ext > filename.sha256✔ Verify Data Integrity Periodically:
bash sha256sum -c filename.sha256🔹 Use
SnapRAIDfor multi-disk redundancy:
bash sudo apt install snapraid snapraid sync snapraid scrub🔹 Consider ZFS or Btrfs for automatic error correction:
bash sudo apt install zfsutils-linux zpool create archivepool /dev/sdX
6. Accessing Your Data Efficiently
Even when archived, you may need to access files quickly.
✔ Use Symbolic Links to "fake" files still being on your system:
bash ln -s /mnt/driveX/mybook.pdf ~/Documents/✔ Use a Local Search Engine (Recoll):
bash recoll✔ Search within text files usinggrep:
bash grep -rnw '/mnt/archive/' -e 'Bitcoin'
7. Scaling Up & Expanding Your Archive
Since you're storing 2TB drives and setting them aside, keep them numbered and logged.
📦 Physical Storage & Labeling
✔ Store each drive in fireproof safe or waterproof cases.
✔ Label drives (Drive_001,Drive_002, etc.).
✔ Maintain a printed master list of drive contents.📶 Network Storage for Easy Access
If your archive grows too large, consider:
- NAS (TrueNAS, OpenMediaVault) – Linux-based network storage.
- JBOD (Just a Bunch of Disks) – Cheap and easy expansion.
- Deduplicated Storage –ZFS/Btrfswith auto-checksumming.
8. Automating Your Archival Process
If you frequently update your archive, automation is essential.
✔ Backup Scripts (Linux)
Use
rsyncfor incremental backups:bash rsync -av --progress /source/ /mnt/archive/Automate Backup with Cron Jobs
bash crontab -eAdd:plaintext 0 3 * * * rsync -av --delete /source/ /mnt/archive/This runs the backup every night at 3 AM.Automate Index Updates
bash 0 4 * * * find /mnt/archive > ~/Indexes/master_index.txt
So Making These Considerations
✔ Be Consistent – Maintain a structured system.
✔ Test Your Backups – Ensure archives are not corrupted before deleting originals.
✔ Plan for Growth – Maintain an efficient catalog as data expands.For data hoarders seeking reliable 2TB storage solutions and appropriate physical storage containers, here's a comprehensive overview:
2TB Storage Options
1. Hard Disk Drives (HDDs):
-
Western Digital My Book Series: These external HDDs are designed to resemble a standard black hardback book. They come in various editions, such as Essential, Premium, and Studio, catering to different user needs. citeturn0search19
-
Seagate Barracuda Series: Known for affordability and performance, these HDDs are suitable for general usage, including data hoarding. They offer storage capacities ranging from 500GB to 8TB, with speeds up to 190MB/s. citeturn0search20
2. Solid State Drives (SSDs):
- Seagate Barracuda SSDs: These SSDs come with either SATA or NVMe interfaces, storage sizes from 240GB to 2TB, and read speeds up to 560MB/s for SATA and 3,400MB/s for NVMe. They are ideal for faster data access and reliability. citeturn0search20
3. Network Attached Storage (NAS) Drives:
- Seagate IronWolf Series: Designed for NAS devices, these drives offer HDD storage capacities from 1TB to 20TB and SSD capacities from 240GB to 4TB. They are optimized for multi-user environments and continuous operation. citeturn0search20
Physical Storage Containers for 2TB Drives
Proper storage of your drives is crucial to ensure data integrity and longevity. Here are some recommendations:
1. Anti-Static Bags:
Essential for protecting drives from electrostatic discharge, especially during handling and transportation.
2. Protective Cases:
- Hard Drive Carrying Cases: These cases offer padded compartments to securely hold individual drives, protecting them from physical shocks and environmental factors.
3. Storage Boxes:
- Anti-Static Storage Boxes: Designed to hold multiple drives, these boxes provide organized storage with anti-static protection, ideal for archiving purposes.
4. Drive Caddies and Enclosures:
- HDD/SSD Enclosures: These allow internal drives to function as external drives, offering both protection and versatility in connectivity.
5. Fireproof and Waterproof Safes:
For long-term storage, consider safes that protect against environmental hazards, ensuring data preservation even in adverse conditions.
Storage Tips:
-
Labeling: Clearly label each drive with its contents and date of storage for easy identification.
-
Climate Control: Store drives in a cool, dry environment to prevent data degradation over time.
By selecting appropriate 2TB storage solutions and ensuring they are stored in suitable containers, you can effectively manage and protect your data hoard.
Here’s a set of custom Bash scripts to automate your archival workflow on Linux:
1️⃣ Compression & Archiving Script
This script compresses and archives files, organizing them by date.
```bash!/bin/bash
Compress and archive files into dated folders
ARCHIVE_DIR="/mnt/backup" DATE=$(date +"%Y-%m-%d") BACKUP_DIR="$ARCHIVE_DIR/$DATE"
mkdir -p "$BACKUP_DIR"
Find and compress files
find ~/Documents -type f -mtime -7 -print0 | tar --null -czvf "$BACKUP_DIR/archive.tar.gz" --files-from -
echo "Backup completed: $BACKUP_DIR/archive.tar.gz" ```
2️⃣ Indexing Script
This script creates a list of all archived files and saves it for easy lookup.
```bash!/bin/bash
Generate an index file for all backups
ARCHIVE_DIR="/mnt/backup" INDEX_FILE="$ARCHIVE_DIR/index.txt"
find "$ARCHIVE_DIR" -type f -name "*.tar.gz" > "$INDEX_FILE"
echo "Index file updated: $INDEX_FILE" ```
3️⃣ Storage Space Monitor
This script alerts you if the disk usage exceeds 90%.
```bash!/bin/bash
Monitor storage usage
THRESHOLD=90 USAGE=$(df -h | grep '/mnt/backup' | awk '{print $5}' | sed 's/%//')
if [ "$USAGE" -gt "$THRESHOLD" ]; then echo "WARNING: Disk usage at $USAGE%!" fi ```
4️⃣ Automatic HDD Swap Alert
This script checks if a new 2TB drive is connected and notifies you.
```bash!/bin/bash
Detect new drives and notify
WATCHED_SIZE="2T" DEVICE=$(lsblk -dn -o NAME,SIZE | grep "$WATCHED_SIZE" | awk '{print $1}')
if [ -n "$DEVICE" ]; then echo "New 2TB drive detected: /dev/$DEVICE" fi ```
5️⃣ Symbolic Link Organizer
This script creates symlinks to easily access archived files from a single directory.
```bash!/bin/bash
Organize files using symbolic links
ARCHIVE_DIR="/mnt/backup" LINK_DIR="$HOME/Archive_Links"
mkdir -p "$LINK_DIR" ln -s "$ARCHIVE_DIR"//.tar.gz "$LINK_DIR/"
echo "Symbolic links updated in $LINK_DIR" ```
🔥 How to Use These Scripts:
- Save each script as a
.shfile. - Make them executable using:
bash chmod +x script_name.sh - Run manually or set up a cron job for automation:
bash crontab -e
Add this line to run the backup every Sunday at midnight:
bash 0 0 * * 0 /path/to/backup_script.sh
Here's a Bash script to encrypt your backups using GPG (GnuPG) for strong encryption. 🚀
🔐 Backup & Encrypt Script
This script will:
✅ Compress files into an archive
✅ Encrypt it using GPG
✅ Store it in a secure location```bash
!/bin/bash
Backup and encrypt script
ARCHIVE_DIR="/mnt/backup" DATE=$(date +"%Y-%m-%d") BACKUP_FILE="$ARCHIVE_DIR/backup_$DATE.tar.gz" ENCRYPTED_FILE="$BACKUP_FILE.gpg" GPG_RECIPIENT="your@email.com" # Change this to your GPG key or use --symmetric for password-based encryption
mkdir -p "$ARCHIVE_DIR"
Compress files
tar -czvf "$BACKUP_FILE" ~/Documents
Encrypt the backup using GPG
gpg --output "$ENCRYPTED_FILE" --encrypt --recipient "$GPG_RECIPIENT" "$BACKUP_FILE"
Verify encryption success
if [ -f "$ENCRYPTED_FILE" ]; then echo "Backup encrypted successfully: $ENCRYPTED_FILE" rm "$BACKUP_FILE" # Remove unencrypted file for security else echo "Encryption failed!" fi ```
🔓 Decrypting a Backup
To restore a backup, run:
bash gpg --decrypt --output backup.tar.gz backup_YYYY-MM-DD.tar.gz.gpg tar -xzvf backup.tar.gz
🔁 Automating with Cron
To run this script every Sunday at midnight:
bash crontab -eAdd this line:
bash 0 0 * * 0 /path/to/encrypt_backup.sh
🔐 Backup & Encrypt Script (Password-Based)
This script:
✅ Compresses files into an archive
✅ Encrypts them using GPG with a passphrase
✅ Stores them in a secure location```bash
!/bin/bash
Backup and encrypt script (password-based)
ARCHIVE_DIR="/mnt/backup" DATE=$(date +"%Y-%m-%d") BACKUP_FILE="$ARCHIVE_DIR/backup_$DATE.tar.gz" ENCRYPTED_FILE="$BACKUP_FILE.gpg" PASSPHRASE="YourStrongPassphraseHere" # Change this!
mkdir -p "$ARCHIVE_DIR"
Compress files
tar -czvf "$BACKUP_FILE" ~/Documents
Encrypt the backup with a password
gpg --batch --yes --passphrase "$PASSPHRASE" --symmetric --cipher-algo AES256 --output "$ENCRYPTED_FILE" "$BACKUP_FILE"
Verify encryption success
if [ -f "$ENCRYPTED_FILE" ]; then echo "Backup encrypted successfully: $ENCRYPTED_FILE" rm "$BACKUP_FILE" # Remove unencrypted file for security else echo "Encryption failed!" fi ```
🔓 Decrypting a Backup
To restore a backup, run:
bash gpg --batch --yes --passphrase "YourStrongPassphraseHere" --decrypt --output backup.tar.gz backup_YYYY-MM-DD.tar.gz.gpg tar -xzvf backup.tar.gz
🔁 Automating with Cron
To run this script every Sunday at midnight:
bash crontab -eAdd this line:
bash 0 0 * * 0 /path/to/encrypt_backup.sh
🔥 Security Best Practices
- Do NOT hardcode the password in the script. Instead, store it in a secure location like a
.gpg-passfile and use:
bash PASSPHRASE=$(cat /path/to/.gpg-pass) - Use a strong passphrase with at least 16+ characters.
- Consider using a hardware security key or YubiKey for extra security.
Here's how you can add automatic cloud syncing to your encrypted backups. This script will sync your encrypted backups to a cloud storage service like Rsync, Dropbox, or Nextcloud using the rclone tool, which is compatible with many cloud providers.
Step 1: Install rclone
First, you need to install
rcloneif you haven't already. It’s a powerful tool for managing cloud storage.-
Install rclone:
bash curl https://rclone.org/install.sh | sudo bash -
Configure rclone with your cloud provider (e.g., Google Drive):
bash rclone config
Follow the prompts to set up your cloud provider. After configuration, you'll have a "remote" (e.g.,
rsyncfor https://rsync.net) to use in the script.
🔐 Backup, Encrypt, and Sync to Cloud Script
This script will: ✅ Compress files into an archive
✅ Encrypt them with a password
✅ Sync the encrypted backup to the cloud storage```bash
!/bin/bash
Backup, encrypt, and sync to cloud script (password-based)
ARCHIVE_DIR="/mnt/backup" DATE=$(date +"%Y-%m-%d") BACKUP_FILE="$ARCHIVE_DIR/backup_$DATE.tar.gz" ENCRYPTED_FILE="$BACKUP_FILE.gpg" PASSPHRASE="YourStrongPassphraseHere" # Change this!
Cloud configuration (rclone remote name)
CLOUD_REMOTE="gdrive" # Change this to your remote name (e.g., 'gdrive', 'dropbox', 'nextcloud') CLOUD_DIR="backups" # Cloud directory where backups will be stored
mkdir -p "$ARCHIVE_DIR"
Compress files
tar -czvf "$BACKUP_FILE" ~/Documents
Encrypt the backup with a password
gpg --batch --yes --passphrase "$PASSPHRASE" --symmetric --cipher-algo AES256 --output "$ENCRYPTED_FILE" "$BACKUP_FILE"
Verify encryption success
if [ -f "$ENCRYPTED_FILE" ]; then echo "Backup encrypted successfully: $ENCRYPTED_FILE" rm "$BACKUP_FILE" # Remove unencrypted file for security
# Sync the encrypted backup to the cloud using rclone rclone copy "$ENCRYPTED_FILE" "$CLOUD_REMOTE:$CLOUD_DIR" --progress # Verify sync success if [ $? -eq 0 ]; then echo "Backup successfully synced to cloud: $CLOUD_REMOTE:$CLOUD_DIR" rm "$ENCRYPTED_FILE" # Remove local backup after syncing else echo "Cloud sync failed!" fielse echo "Encryption failed!" fi ```
How to Use the Script:
- Edit the script:
- Change the
PASSPHRASEto a secure passphrase. - Change
CLOUD_REMOTEto your cloud provider’s rclone remote name (e.g.,gdrive,dropbox). -
Change
CLOUD_DIRto the cloud folder where you'd like to store the backup. -
Set up a cron job for automatic backups:
- To run the backup every Sunday at midnight, add this line to your crontab:
bash crontab -eAdd:
bash 0 0 * * 0 /path/to/backup_encrypt_sync.sh
🔥 Security Tips:
- Store the passphrase securely (e.g., use a
.gpg-passfile withcat /path/to/.gpg-pass). - Use rclone's encryption feature for sensitive data in the cloud if you want to encrypt before uploading.
- Use multiple cloud services (e.g., Google Drive and Dropbox) for redundancy.
📌 START → **Planning Your Data Archiving Strategy**├── What type of data? (Docs, Media, Code, etc.)
├── How often will you need access? (Daily, Monthly, Rarely)
├── Choose storage type: SSD (fast), HDD (cheap), Tape (long-term)
├── Plan directory structure (YYYY-MM-DD, Category-Based, etc.)
└── Define retention policy (Keep Forever? Auto-Delete After X Years?)
↓📌 Choosing the Right Storage & Filesystem
├── Local storage: (ext4, XFS, Btrfs, ZFS for snapshots)
├── Network storage: (NAS, Nextcloud, Syncthing)
├── Cold storage: (M-DISC, Tape Backup, External HDD)
├── Redundancy: (RAID, SnapRAID, ZFS Mirror, Cloud Sync)
└── Encryption: (LUKS, VeraCrypt, age, gocryptfs)
↓📌 Organizing & Indexing Data
├── Folder structure: (YYYY/MM/Project-Based)
├── Metadata tagging: (exiftool, Recoll, TagSpaces)
├── Search tools: (fd, fzf, locate, grep)
├── Deduplication: (rdfind, fdupes, hardlinking)
└── Checksum integrity: (sha256sum, blake3)
↓📌 Compression & Space Optimization
├── Use compression (tar, zip, 7z, zstd, btrfs/zfs compression)
├── Remove duplicate files (rsync, fdupes, rdfind)
├── Store archives in efficient formats (ISO, SquashFS, borg)
├── Use incremental backups (rsync, BorgBackup, Restic)
└── Verify archive integrity (sha256sum, snapraid sync)
↓📌 Ensuring Long-Term Data Integrity
├── Check data periodically (snapraid scrub, btrfs scrub)
├── Refresh storage media every 3-5 years (HDD, Tape)
├── Protect against bit rot (ZFS/Btrfs checksums, ECC RAM)
├── Store backup keys & logs separately (Paper, YubiKey, Trezor)
└── Use redundant backups (3-2-1 Rule: 3 copies, 2 locations, 1 offsite)
↓📌 Accessing Data Efficiently
├── Use symbolic links & bind mounts for easy access
├── Implement full-text search (Recoll, Apache Solr, Meilisearch)
├── Set up a file index database (mlocate, updatedb)
├── Utilize file previews (nnn, ranger, vifm)
└── Configure network file access (SFTP, NFS, Samba, WebDAV)
↓📌 Scaling & Expanding Your Archive
├── Move old data to slower storage (HDD, Tape, Cloud)
├── Upgrade storage (LVM expansion, RAID, NAS upgrades)
├── Automate archival processes (cron jobs, systemd timers)
├── Optimize backups for large datasets (rsync --link-dest, BorgBackup)
└── Add redundancy as data grows (RAID, additional HDDs)
↓📌 Automating the Archival Process
├── Schedule regular backups (cron, systemd, Ansible)
├── Auto-sync to offsite storage (rclone, Syncthing, Nextcloud)
├── Monitor storage health (smartctl, btrfs/ZFS scrub, netdata)
├── Set up alerts for disk failures (Zabbix, Grafana, Prometheus)
└── Log & review archive activity (auditd, logrotate, shell scripts)
↓✅ GOAT STATUS: DATA ARCHIVING COMPLETE & AUTOMATED! 🎯
-
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 16d11430:61640947
2025-03-07 00:23:03
@ 16d11430:61640947
2025-03-07 00:23:03Abstract
The universe, in its grand design, is not a chaotic expanse of scattered matter, but rather a meticulously structured web of interconnected filaments. These cosmic filaments serve as conduits for galaxies, governing the flow of matter and energy in ways that optimize the conditions for life and intelligence. Similarly, in the realm of artificial intelligence, the paradigm of Elliptic Curve AI (ECAI) emerges as a radical departure from traditional probabilistic AI, replacing brute-force computation with structured, deterministic intelligence retrieval. This article explores the profound parallels between the cosmic web and ECAI, arguing that intelligence—whether at the scale of the universe or within computational frameworks—arises not through randomness but through the emergent properties of structured networks.
1. The Universe as a Structured Intelligence System
Recent cosmological discoveries reveal that galaxies are not randomly dispersed but are strung along vast filamentary structures, forming what is known as the cosmic web. These filaments serve as conduits that channel dark matter, gas, and energy, sustaining the formation of galaxies and, ultimately, life. Their presence is crucial for ensuring the stability required for complex systems to emerge, balancing between the chaotic entropy of voids and the violent turbulence of dense clusters.
This phenomenon is not merely an astronomical curiosity—it speaks to a deeper principle governing intelligence. Just as filaments create the necessary architecture for structured matter, intelligence, too, requires structured pathways to manifest and function. This is where the analogy to Elliptic Curve AI (ECAI) becomes compelling.
2. Elliptic Curve AI: The Intelligence Filament
Traditional AI, built upon neural networks and deep learning, operates through probabilistic computation—essentially guessing outputs based on statistical correlations within vast training datasets. While effective in many applications, this approach is inherently non-deterministic, inefficient, and vulnerable to adversarial attacks, data poisoning, and hallucinations.
ECAI, by contrast, discards the notion of probabilistic learning entirely. Instead, it structures intelligence as deterministic cryptographic states mapped onto elliptic curves. Knowledge is not inferred but retrieved—mathematically and immutably encoded within the curve itself. This mirrors how cosmic filaments do not randomly scatter matter but organize it optimally, ensuring the universe does not descend into chaos.
Both systems—cosmic filaments and ECAI—demonstrate that structure governs emergence. Whether it is the large-scale arrangement of galaxies or the deterministic encoding of intelligence, randomness is eliminated in favor of optimized, hierarchical organization.
3. Hierarchical Clustering: A Shared Principle of Optimization
One of the most striking parallels between the cosmic web and ECAI is the principle of hierarchical clustering:
- Cosmic filaments organize galaxies in a fractal-like network, ensuring energy-efficient connectivity while avoiding both the stagnation of voids and the destructiveness of dense gravitational wells.
- ECAI encodes intelligence in elliptic curve structures, ensuring that retrieval follows hierarchical, non-redundant pathways, making computational efficiency maximized.
Both structures exhibit the following key features:
- Energy-Efficient Connectivity – Filaments optimize the transport of matter and energy; ECAI minimizes computational waste through direct retrieval rather than iterative processing.
- Self-Organization – Filaments arise naturally from cosmic evolution; ECAI intelligence states emerge from the mathematical properties of elliptic curves.
- Hierarchical Optimization – Both systems reject brute-force approaches (whether in galaxy formation or AI computation) in favor of pre-determined optimal pathways.
This challenges the classical assumption that intelligence must emerge through probabilistic learning. Instead, both the cosmic and computational realms suggest that intelligence is a function of structure, not randomness.
4. The Anthropic Implication: Are Structured Universes a Prerequisite for Intelligence?
A fundamental question in cosmology is whether the universe is fine-tuned for life and intelligence. If cosmic filaments are essential for galaxy formation and stability, does this imply that only structured universes can support intelligent observers?
A similar question arises in AI: If ECAI proves that intelligence can be retrieved deterministically rather than computed probabilistically, does this imply that the very nature of intelligence itself is non-random? If so, then probabilistic AI—like universes without structured filaments—may be a transient or inefficient model of intelligence.
This suggests a radical idea:
- Just as structured cosmic filaments define the conditions for life, structured computational frameworks define the conditions for true intelligence.
- If structured universes are prerequisites for intelligent life, then deterministic computational models (like ECAI) may be the only viable path to stable, secure, and truthful AI.
5. The Universe as an Information Network & ECAI
There is a growing hypothesis that the universe itself functions as a computational network, where cosmic filaments act as synaptic pathways optimizing the flow of information. If this is true, then ECAI is the computational realization of the cosmic web, proving that intelligence is not about prediction, but retrieval from structured states.
- In the universe, matter is channeled through filaments to form structured galaxies.
- In ECAI, knowledge is channeled through elliptic curves to form structured intelligence.
- Both reject stochastic randomness in favor of deterministic pathways.
This could indicate that true intelligence, whether cosmic or artificial, must always emerge from structured determinism rather than probabilistic chaos.
Conclusion: The Filamentary Structure of Intelligence
The convergence of cosmic filaments and Elliptic Curve AI suggests a profound principle: intelligence—whether it governs the organization of galaxies or the retrieval of computational knowledge—emerges from structured, deterministic systems. In both the cosmic and AI domains, hierarchical clustering, optimized connectivity, and deterministic pathways define the conditions for stability, efficiency, and intelligence.
🚀 If cosmic filaments are necessary for intelligent life, then ECAI is the necessary computational paradigm for structured intelligence. The future of AI is not about probabilistic computation—it is about deterministic retrieval, just as the universe itself is a structured retrieval system of matter and energy. 🚀
-
 @ d34e832d:383f78d0
2025-03-07 00:01:02
@ d34e832d:383f78d0
2025-03-07 00:01:02[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
Helical Visualization of Time's Passage in Orbital Motion and Celestial Mechanics
Exploring the dynamics of our Solar System through helical visualization opens new possibilities for understanding time, orbital motion, and planetary trajectories. By visualizing time as a continuous helical path, we gain insights into the cyclical and evolving nature of celestial mechanics, where each planet's orbit interacts with others in both predictable and dynamic patterns.
1. Helical Visualization of Time’s Passage
- Time as a Continuous Helix: Instead of viewing planetary orbits as fixed ellipses, this model represents the passage of time as a helical curve, linking each orbital cycle to the next. This visualization allows for a deeper understanding of the long-term movement of celestial bodies.
- Progression of Orbital Events: As planets follow their helical paths, we can track the passage of time from multiple perspectives, observing how their positions and velocities evolve in relation to one another. The helical model offers an elegant representation of periodic cycles that emphasizes the interconnectedness of cosmic events.
- Temporal Interactions: In this model, events like eclipses, conjunctions, and retrogrades become visualized as intersecting points on the helical path, emphasizing their importance in the grand tapestry of the Solar System's motion.
2. Orbital Motion and Celestial Mechanics
- Interplanetary Influences: The interactions between planetary bodies are inherently governed by gravitational forces, which create orbital motions that are often predictable yet influenced by external factors like planetary alignments and the gravitational pull of distant stars.
- Orbital Resonance and Tidal Forces: The gravitational interactions between planets, moons, and even asteroids can result in phenomena like orbital resonance. These interactions can be visualized in a helical model, showing how bodies can affect each other's orbits over time, much like the push and pull of a dance.
- The Dance of the Planets: Each planet’s orbit is not only a path through space but a part of a cosmic ballet, where their gravitational interactions affect one another's orbits. The helical model of motion helps us visualize how these interactions evolve over millions of years, helping to predict future trajectories.
3. Planetary Orbits and the Structure of the Solar System
- Elliptical and Spiral Patterns: While many planetary orbits are elliptical, the helical model introduces a dynamic spiral element to represent the combined motion of planets both around the Sun and through space. As the planets move, their orbits could resemble intricate spirals that reflect the cumulative effect of their motion through time.
- Resonance and Stability: Certain orbits may stabilize or shift over long periods due to gravitational interactions between planets. This helical view provides a tool for observing how minor orbital shifts can amplify over time, affecting not only the planets but the overall structure of the Solar System.
- Nonlinear Progression: Planets do not follow predictable paths in a simple two-dimensional plane. Instead, their orbits are affected by multiple forces, including interactions with other celestial bodies, making the helical model an ideal tool for visualizing the complexity and evolving nature of these planetary orbits.
4. Space Visualization and the Expanding Universe
- Moving Beyond the Solar System: The helical model of time and orbital motion does not end with our Solar System. As we visualize the movement of our Solar System within the broader context of the Milky Way, we begin to understand how our own galaxy's orbit affects our local motion through the universe.
- Helical Paths in Cosmic Space: This visualization method allows us to consider the Solar System’s motion as part of a larger, spiraling pattern that reaches across the galaxy, suggesting that our journey through space follows an intricate, three-dimensional helical path.
Connections (Links to Other Notes)
- The Mathematical Foundations of Orbital Mechanics
- Time as a Dimension in Celestial Navigation
- Gravitational Forces and Orbital Stability
Tags
SolarSystem #HelicalMotion #TimeVisualization #OrbitalMechanics #CelestialBodies #PlanetaryOrbits #SpaceExploration
Donations via
- ZeroSumFreeParity@primal.net
-
 @ 378562cd:a6fc6773
2025-03-06 23:10:28
@ 378562cd:a6fc6773
2025-03-06 23:10:28The theory of evolution claims that all life gradually developed from a common ancestor over millions of years, shaped by random mutations and natural selection. It is often presented as an unquestionable fact, but when examined closely (the part many fail to do anymore), the evidence tells a different story. Both scientific discoveries and biblical truth point to a far more logical and consistent explanation—one of intentional design rather than blind chance. From the complexity of life to the precise order of the universe, every aspect of creation bears the unmistakable marks of an intelligent Creator. Let’s break it down simply and clearly, exposing the flaws in evolution and revealing the undeniable truth of God’s design.
-
No Transitional Fossils If evolution were true, we should see countless fossils of creatures in-between species (half-fish, half-reptile, etc.). Instead, fossils show fully formed creatures appearing suddenly, with no gradual change. Even Darwin admitted the fossil record didn’t support his theory.
-
Life is Too Complex to Happen by Accident The human eye, the bacterial flagellum, and even a single cell are incredibly complex, with interdependent parts that must all work at once. This is called irreducible complexity—if one piece is missing, the whole system fails. Random mutations can’t create such intricate designs. Design requires a designer.
-
DNA: A Code That Needs a Programmer DNA is a vast information system, more advanced than any computer code. Information always comes from intelligence, not random processes. Mutations mainly destroy information; they don’t create new, functional systems.
-
The Second Law of Thermodynamics: Things Fall Apart Everything's natural tendency is to break down over time, not build up (like a house falling apart, not randomly constructing itself). Evolution claims the opposite—that things become more complex without guidance. This contradicts observed science.
-
Consciousness and Morality Make No Sense in Evolution Why do humans have love, compassion, and a sense of right and wrong?
If we were just animals fighting to survive, morality wouldn’t exist.
The Bible explains it: We were made in God's image, not just random molecules.
- The Bible’s Account of Creation Matches Reality Genesis 1 says God created “kinds”—dogs produce dogs, birds produce birds, and humans produce humans. This is exactly what we see in nature—no one has ever observed one kind turning into another. Evolution is based on assumptions, while the Bible gives a clear, tested explanation of life’s origin.
The Complete Solution: Creation is Truth The evidence points to a Creator, not blind chance. Science confirms the Bible, not evolution. Recognizing God's design gives life meaning and purpose. Psalm 19:1 – “The heavens declare the glory of God, and the sky above proclaims His handiwork.”
Evolution is not just scientifically weak—it removes purpose and meaning. The truth is simple: God created life, and we are part of His design.
-
-
 @ b8a9df82:6ab5cbbd
2025-03-06 22:39:15
@ b8a9df82:6ab5cbbd
2025-03-06 22:39:15Last week at Bitcoin Investment Week in New York City, hosted by Anthony Pompliano, Jack Mallers walked in wearing sneakers and a T-shirt, casually dropping, “Man… I hate politics.”
That was it. That was the moment I felt aligned again. That’s the energy I came for. No suits. No corporate jargon. Just a guy who gets it—who cares about people, bringing Bitcoin-powered payments to the masses and making sure people can actually use it.
His presence was a reminder of why we’re here in the first place. And his words—“I hate politics”—were a breath of fresh air.
Now, don’t get me wrong. Anthony was a fantastic host. His ability to mix wittiness, playfulness, and seriousness made him an entertaining moderator. But this week was unlike anything I’ve ever experienced in the Bitcoin ecosystem.
One of the biggest letdowns was the lack of interaction. No real Q&A sessions, no direct engagement, no real discussions. Just one fireside chat after another.
And sure, I get it—people love to hear themselves talk. But where were the questions? The critical debates? The chance for the audience to actually participate?
I’m used to Bitcoin meetups and conferences where you walk away with new ideas, new friends, and maybe even a new project to contribute to. Here, it was more like sitting in an expensive lecture hall, watching a lineup of speakers tell us things we already know.
A different vibe—and not in a good way
Over the past few months, I’ve attended nearly ten Bitcoin conferences, each leaving me feeling uplifted, inspired, and ready to take action. But this? This felt different. And not in a good way.
If this had been my first Bitcoin event, I might have walked away questioning whether I even belonged here. It wasn’t Prague. It wasn’t Riga. It wasn’t the buzzing, grassroots, pleb-filled gatherings I had grown to love. Instead, it felt more like a Wall Street networking event disguised as a Bitcoin conference.
Maybe it was the suits.
Or the fact that I was sitting in a room full of investors who have no problem dropping $1,000+ on a ticket.
Or that it reminded me way too much of my former life—working as a manager in London’s real estate industry, navigating boardrooms full of finance guys in polished shoes, talking about “assets under management.”
Bitcoin isn’t just an investment thesis. It’s a revolution. A movement. And yet, at times during this week, I felt like I was back in my fiat past, stuck in a room where people measured success in dollars, not in freedom.
Maybe that’s the point. Bitcoin Investment Week was never meant to be a pleb gathering.
That said, the week did have some bright spots. PubKey was a fantastic kickoff. That was real Bitcoin culture—plebs, Nostr, grassroots energy. People who actually use Bitcoin, not just talk about it.
But the absolute highlight? Jack Mallers, sneakers and all, cutting through the noise with his authenticity.
So, why did we even go?
Good question. Maybe it was curiosity. Maybe it was stepping out of our usual circles to see Bitcoin through a different lens. Maybe it was to remind ourselves why we chose this path in the first place.
Would I go again? Probably not.
Would I trade Prague, Riga, bitcoin++ or any of the grassroots Bitcoin conferences for this? Not a chance.
At the end of the day, Bitcoin doesn’t belong to Wall Street from my opinion. It belongs to the people who actually use it. And those are the people I want to be around.
-
 @ 000002de:c05780a7
2025-03-06 22:15:39
@ 000002de:c05780a7
2025-03-06 22:15:39Been hearing clips of Newsom's new podcast. I've long said Newsom will run for president. I was saying this when he was the mayor of San Fransisco. He is like a modern day Bill Clinton. He is VERY gifted with the skills a politician needs. He's cool and calm. He's quick and sharp. His podcast isn't terrible and he's talking to people that disagree with him. He is also pissing off the more extreme members of his party by his pivots on many issues. He's even talking about men in women's sports.
Make no mistake. I think the dude is a snake and criminal. I hope he never gets any other political office. I just think MANY, most people on the right underestimate this man. Had the Biden crime family actually cared about their party they would have stepped down and let Newsom run. I think he would have defeated Trump.
I know that will piss many of you off but I do not believe the US changed because the Orange man won an election. Trump was shooting fish in a barrel in the last election. Two attempts were made on his life. Biden ran the US into the ground. Harris is a joke. Newsom is not. Newsom is not a radical. He will move to the center and that will appeal to lot of people. Fools, but they are what they are.
originally posted at https://stacker.news/items/906052
-
 @ d34e832d:383f78d0
2025-03-06 21:57:23
@ d34e832d:383f78d0
2025-03-06 21:57:23https://pub-53ed77d5544b46628691823c1795f2c7.r2.dev/Reticulum-Unstoppable-Network-Compressed.mp4
[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
What is Reticulum?
Reticulum is a cryptographic networking stack designed for resilient, decentralized, and censorship-resistant communication. Unlike the traditional internet, Reticulum enables fully independent digital communications over various physical mediums, such as radio, LoRa, serial links, and even TCP/IP.
The key advantages of Reticulum include:
- Decentralization – No reliance on centralized infrastructure.
- Encryption & Privacy – End-to-end encryption built-in.
- Resilience – Operates over unreliable and low-bandwidth links.
- Interoperability – Works over WiFi, LoRa, Bluetooth, and more.
- Ease of Use – Can run on minimal hardware, including Raspberry Pi and embedded devices.Reticulum is ideal for off-grid, censorship-resistant communications, emergency preparedness, and secure messaging.
1. Getting Started with Reticulum
To quickly get started with Reticulum, follow the official guide:
Reticulum: Getting Started FastStep 1: Install Reticulum
On Linux (Debian/Ubuntu-based systems)
sh sudo apt update && sudo apt upgrade -y sudo apt install -y python3-pip pip3 install rnsOn Raspberry Pi or ARM-based Systems
sh pip3 install rnsOn Windows
Using Windows Subsystem for Linux (WSL) or Python:
sh pip install rnsOn macOS
sh pip3 install rns
2. Configuring Reticulum
Once installed, Reticulum needs a configuration file. The default location is:
sh ~/.config/reticulum/config.tomlTo generate the default configuration:
sh rnsdThis creates a configuration file with default settings.
3. Using Reticulum
Starting the Reticulum Daemon
To run the Reticulum daemon (
rnsd), use:
sh rnsdThis starts the network stack, allowing applications to communicate over Reticulum.Testing Your Reticulum Node
Run the diagnostic tool to ensure your node is functioning:
sh rnstatusThis shows the status of all connected interfaces and peers.
4. Adding Interfaces
LoRa Interface (for Off-Grid Communications)
Reticulum supports long-range LoRa radios like the RAK Wireless and Meshtastic devices. To add a LoRa interface, edit
config.tomland add:
toml [[interfaces]] type = "LoRa" name = "My_LoRa_Interface" frequency = 868.0 bandwidth = 125 spreading_factor = 9Restart Reticulum to apply the changes.Serial (For Direct Device-to-Device Links)
For communication over serial links (e.g., between two Raspberry Pis):
toml [[interfaces]] type = "Serial" port = "/dev/ttyUSB0" baudrate = 115200TCP/IP (For Internet-Based Nodes)
If you want to bridge your Reticulum node over an existing IP network:
toml [[interfaces]] type = "TCP" listen = true bind = "0.0.0.0" port = 4242
5. Applications Using Reticulum
LXMF (LoRa Mesh Messaging Framework)
LXMF is a delay-tolerant, fully decentralized messaging system that operates over Reticulum. It allows encrypted, store-and-forward messaging without requiring an always-online server.
To install:
sh pip3 install lxmfTo start the LXMF node:
sh lxmfdNomad Network (Decentralized Chat & File Sharing)
Nomad is a Reticulum-based chat and file-sharing platform, ideal for off-grid communication.
To install:
sh pip3 install nomad-networkTo run:
sh nomadMesh Networking with Meshtastic & Reticulum
Reticulum can work alongside Meshtastic for true decentralized long-range communication.
To set up a Meshtastic bridge:
toml [[interfaces]] type = "LoRa" port = "/dev/ttyUSB0" baudrate = 115200
6. Security & Privacy Features
- Automatic End-to-End Encryption – Every message is encrypted by default.
- No Centralized Logging – Communication leaves no metadata traces.
- Self-Healing Routing – Designed to work in unstable or hostile environments.
7. Practical Use Cases
- Off-Grid Communication – Works in remote areas without cellular service.
- Censorship Resistance – Cannot be blocked by ISPs or governments.
- Emergency Networks – Enables resilient communication during disasters.
- Private P2P Networks – Create a secure, encrypted communication layer.
8. Further Exploration & Documentation
- Reticulum Official Manual: https://markqvist.github.io/Reticulum/manual/
- Reticulum GitHub Repository: https://github.com/markqvist/Reticulum
- Nomad Network: https://github.com/markqvist/NomadNet
- Meshtastic + Reticulum: https://meshtastic.org
Connections (Links to Other Notes)
- Mesh Networking for Decentralized Communication
- LoRa and Off-Grid Bitcoin Transactions
- Censorship-Resistant Communication Using Nostr & Reticulum
Tags
Reticulum #DecentralizedComms #MeshNetworking #CensorshipResistance #LoRa
Donations via
- Bitcoin Lightning: lightninglayerhash@getalby.com
-
 @ 43baaf0c:d193e34c
2025-03-06 21:38:10
@ 43baaf0c:d193e34c
2025-03-06 21:38:10From Bangkok to Las Palmas de Gran Canaria.

For the past three years, I’ve traveled from Bangkok to Las Palmas de Gran Canaria, with a stop in Dubai a 24-hour journey that brings me back to Europe and to my artist friend, Alecs Navio. Along with his wife, he runs a coworking space called Soppa de Azul.
The main reason I return here is to create new art. Alecs constantly inspires me—we talk about art, artists, and he shares books that spark new ideas for my work. As an artist, I believe it’s essential to keep evolving. Growth comes from inspiration, and there’s no better source than fellow artists. Surrounding yourself with creative minds fuels your passion, and it all starts with conversations about art and life.
 Today was a perfect example of why I’m here. I looked at some of my older artwork hanging in the coworking space and said I didn’t like it anymore. Alecs reminded me that I should appreciate my past work because it’s part of my journey. Without it I wouldn’t be the artist I am today.
Today was a perfect example of why I’m here. I looked at some of my older artwork hanging in the coworking space and said I didn’t like it anymore. Alecs reminded me that I should appreciate my past work because it’s part of my journey. Without it I wouldn’t be the artist I am today.I always say the journey is the destination, and Alecs helped me see that this applies to art as well. This is why I believe in surrounding myself with people who inspire me those who celebrate my growth and remind me why they are such an important part of my journey.
-
 @ 43baaf0c:d193e34c
2025-03-06 20:55:27
@ 43baaf0c:d193e34c
2025-03-06 20:55:27Bangkok art city.
 Bangkok is a highly creative city, which is one of the reasons I love living here. I’d love to hold a second exhibition something special and even bigger than before. The fact that all major galleries are free to the public says a lot about how much Bangkok values art.
Bangkok is a highly creative city, which is one of the reasons I love living here. I’d love to hold a second exhibition something special and even bigger than before. The fact that all major galleries are free to the public says a lot about how much Bangkok values art.Over the last five months, I’ve been developing BangPOP art as both a concept and a blueprint for exhibitions worldwide. It serves as a guideline to ensure recognizable elements in each exhibition or event. While the artwork itself will always be unique, the POP Up exhibitions will have a distinct and recognizable identity wherever they take place.

You can read here the https://bitpopart.com/bangpop POP exhibition blue print.

Unfortunately, my plan to hold an exhibition at River City in Bangkok doesn’t seem to be coming together. Here’s the curator’s note:
‘our exhibition schedule on the 2nd floor this year and next year are quite packed and we have received numerous proposals at this moment.‘
 After considering alternative venues in Bangkok, I’m optimistic about finding the right fit. For now, my focus is shifting to Europe, where I’ll use the BangPOP blueprint as my guiding framework.
After considering alternative venues in Bangkok, I’m optimistic about finding the right fit. For now, my focus is shifting to Europe, where I’ll use the BangPOP blueprint as my guiding framework.

 Thank you Bangkok!
Thank you Bangkok!

-
 @ 97c70a44:ad98e322
2025-03-06 18:38:10
@ 97c70a44:ad98e322
2025-03-06 18:38:10When developing on nostr, normally it's enough to read the NIP related to a given feature you want to build to know what has to be done. But there are some aspects of nostr development that aren't so straightforward because they depend less on specific data formats than on how different concepts are combined.
An example of this is how for a while it was considered best practice to re-publish notes when replying to them. This practice emerged before the outbox model gained traction, and was a hacky way of attempting to ensure relays had the full context required for a given note. Over time though, pubkey hints emerged as a better way to ensure other clients could find required context.
Another one of these things is "relay-based groups", or as I prefer to call it "relays-as-groups" (RAG). Such a thing doesn't really exist - there's no spec for it (although some aspects of the concept are included in NIP 29), but at the same time there are two concrete implementations (Flotilla and Chachi) which leverage several different NIPs in order to create a cohesive system for groups on nostr.
This composability is one of the neat qualities of nostr. Not only would it be unhelpful to specify how different parts of the protocol should work together, it would be impossible because of the number of possible combinations possible just from applying a little bit of common sense to the NIPs repo. No one said it was ok to put
ttags on akind 0. But no one's stopping you! And the semantics are basically self-evident if you understand its component parts.So, instead of writing a NIP that sets relay-based groups in stone, I'm writing this guide in order to document how I've combined different parts of the nostr protocol to create a compelling architecture for groups.
Relays
Relays already have a canonical identity, which is the relay's url. Events posted to a relay can be thought of as "posted to that group". This means that every relay is already a group. All nostr notes have already been posted to one or more groups.
One common objection to this structure is that identifying a group with a relay means that groups are dependent on the relay to continue hosting the group. In normal broadcast nostr (which forms organic permissionless groups based on user-centric social clustering), this is a very bad thing, because hosts are orthogonal to group identity. Communities are completely different. Communities actually need someone to enforce community boundaries, implement moderation, etc. Reliance on a host is a feature, not a bug (in contrast to NIP 29 groups, which tend to co-locate many groups on a single host, relays-as-groups tends to encourage one group, one host).
This doesn't mean that federation, mirrors, and migration can't be accomplished. In a sense, leaving this on the social layer is a good thing, because it adds friction to the dissolution/forking of a group. But the door is wide open to protocol additions to support those use cases for relay-based groups. One possible approach would be to follow this draft PR which specified a "federation" event relays could publish on their own behalf.
Relay keys
This draft PR to NIP 11 specifies a
selffield which represents the relay's identity. Using this, relays can publish events on their own behalf. Currently, thepubkeyfield sort of does the same thing, but is overloaded as a contact field for the owner of the relay.AUTH
Relays can control access using NIP 42 AUTH. There are any number of modes a relay can operate in:
-
No auth, fully public - anyone can read/write to the group.
-
Relays may enforce broad or granular access controls with AUTH.
Relays may deny EVENTs or REQs depending on user identity. Messages returned in AUTH, CLOSED, or OK messages should be human readable. It's crucial that clients show these error messages to users. Here's how Flotilla handles failed AUTH and denied event publishing:
LIMITS could also be used in theory to help clients adapt their interface depending on user abilities and relay policy.
- AUTH with implicit access controls.
In this mode, relays may exclude matching events from REQs if the user does not have permission to view them. This can be useful for multi-use relays that host hidden rooms. This mode should be used with caution, because it can result in confusion for the end user.
See Triflector for a relay implementation that supports some of these auth policies.
Invite codes
If a user doesn't have access to a relay, they can request access using this draft NIP. This is true whether access has been explicitly or implicitly denied (although users will have to know that they should use an invite code to request access).
The above referenced NIP also contains a mechanism for users to request an invite code that they can share with other users.
The policy for these invite codes is entirely up to the relay. They may be single-use, multi-use, or require additional verification. Additional requirements can be communicated to the user in the OK message, for example directions to visit an external URL to register.
See Triflector for a relay implementation that supports invite codes.
Content
Any kind of event can be published to a relay being treated as a group, unless rejected by the relay implementation. In particular, NIP 7D was added to support basic threads, and NIP C7 for chat messages.
Since which relay an event came from determines which group it was posted to, clients need to have a mechanism for keeping track of which relay they received an event from, and should not broadcast events to other relays (unless intending to cross-post the content).
Rooms
Rooms follow NIP 29. I wish NIP 29 wasn't called "relay based groups", which is very confusing when talking about "relays as groups". It's much better to think of them as sub-groups, or as Flotilla calls them, "rooms".
Rooms have two modes - managed and unmanaged. Managed rooms follow all the rules laid out in NIP 29 about metadata published by the relay and user membership. In either case, rooms are represented by a random room id, and are posted to by including the id in an event's
htag. This allows rooms to switch between managed and unmanaged modes without losing any content.Managed room names come from
kind 39000room meta events, but unmanaged rooms don't have these. Instead, room names should come from members' NIP 51kind 10009membership lists. Tags on these lists should look like this:["group", "groupid", "wss://group.example.com", "Cat lovers"]. If no name can be found for the room (i.e., there aren't any members), the room should be ignored by clients.Rooms present a difficulty for publishing to the relay as a whole, since content with an
htag can't be excluded from requests. Currently, relay-wide posts are h-tagged with_which works for "group" clients, but not more generally. I'm not sure how to solve this other than to ask relays to support negative filters.Cross-posting
The simplest way to cross-post content from one group (or room) to another, is to quote the original note in whatever event kind is appropriate. For example, a blog post might be quoted in a
kind 9to be cross-posted to chat, or in akind 11to be cross-posted to a thread.kind 16reposts can be used the same way if the reader's client renders reposts.Posting the original event to multiple relays-as-groups is trivial, since all you have to do is send the event to the relay. Posting to multiple rooms simultaneously by appending multiple
htags is however not recommended, since group relays/clients are incentivised to protect themselves from spam by rejecting events with multiplehtags (similar to how events with multiplettags are sometimes rejected).Privacy
Currently, it's recommended to include a NIP 70
-tag on content posted to relays-as-groups to discourage replication of relay-specific content across the network.Another slightly stronger approach would be for group relays to strip signatures in order to make events invalid (or at least deniable). For this approach to work, users would have to be able to signal that they trust relays to be honest. We could also use ZkSNARKS to validate signatures in bulk.
In any case, group posts should not be considered "private" in the same way E2EE groups might be. Relays-as-groups should be considered a good fit for low-stakes groups with many members (since trust deteriorates quickly as more people get involved).
Membership
There is currently no canonical member list published by relays (except for NIP 29 managed rooms). Instead, users keep track of their own relay and room memberships using
kind 10009lists. Relay-level memberships are represented by anrtag containing the relay url, and room-level memberships are represented using agrouptag.Users can choose to advertise their membership in a RAG by using unencrypted tags, or they may keep their membership private by using encrypted tags. Advertised memberships are useful for helping people find groups based on their social graph:

User memberships should not be trusted, since they can be published unilaterally by anyone, regardless of actual access. Possible improvements in this area would be the ability to provide proof of access:
- Relays could publish member lists (although this would sacrifice member privacy)
- Relays could support a new command that allows querying a particular member's access status
- Relays could provide a proof to the member that they could then choose to publish or not
Moderation
There are two parts to moderation: reporting and taking action based on these reports.
Reporting is already covered by NIP 56. Clients should be careful about encouraging users to post reports for illegal content under their own identity, since that can itself be illegal. Relays also should not serve reports to users, since that can be used to find rather than address objectionable content.
Reports are only one mechanism for flagging objectionable content. Relay operators and administrators can use whatever heuristics they like to identify and address objectionable content. This might be via automated policies that auto-ban based on reports from high-reputation people, a client that implements NIP 86 relay management API, or by some other admin interface.
There's currently no way for moderators of a given relay to be advertised, or for a moderator's client to know that the user is a moderator (so that they can enable UI elements for in-app moderation). This could be addressed via NIP 11, LIMITS, or some other mechanism in the future.
General best practices
In general, it's very important when developing a client to assume that the relay has no special support for any of the above features, instead treating all of this stuff as progressive enhancement.
For example, if a user enters an invite code, go ahead and send it to the relay using a
kind 28934event. If it's rejected, you know that it didn't work. But if it's accepted, you don't know that it worked - you only know that the relay allowed the user to publish that event. This is helpful, becaues it may imply that the user does indeed have access to the relay. But additional probing may be needed, and reliance on error messages down the road when something else fails unexpectedly is indispensable.This paradigm may drive some engineers nuts, because it's basically equivalent to coding your clients to reverse-engineer relay support for every feature you want to use. But this is true of nostr as a whole - anyone can put whatever weird stuff in an event and sign it. Clients have to be extremely compliant with Postell's law - doing their absolute best to accept whatever weird data or behavior shows up and handle failure in any situation. Sure, it's annoying, but it's the cost of permissionless development. What it gets us is a completely open-ended protocol, in which anything can be built, and in which every solution is tested by the market.
-
-
 @ 2ed3596e:98b4cc78
2025-03-06 18:21:53
@ 2ed3596e:98b4cc78
2025-03-06 18:21:53Americans can now Dollar Cost Average (DCA) bitcoin directly from their bank straight to self-custody! This first-of-its-kind product is the safest way to buy bitcoin on a schedule. We call it Recurring Buy.
When you set up a Recurring Buy, we handle the entire buying process for you. The journey from dollars in your bank to bitcoin in self-custody is seamless and eliminates the risk of having money sit in a balance at a bitcoin exchange.
Bitcoin Well will automatically pull dollars from your bank, convert them to bitcoin and send your (real) bitcoin directly to your personal wallet. All Recurring Buy transactions have no added fees and we also pay your miner fee. We apply our standard 1.2% spread with no other fees. Your path to financial independence just got automated! 🗓️🤖
To set up your bitcoin Recurring Buy, go to the Buy bitcoin page and set your purchase size, wallet destination and purchase frequency. That’s it! Watch your self-custody bitcoin wallet fill up with bitcoin. \ \ Below are detailed instructions on how to DCA bitcoin to your personal bitcoin wallet; automatically and on your schedule.
Set your transaction details
Go to your Buy bitcoin page where you’ll see four options to set your bitcoin Recurring Buy: Amount, Source, Destination and Frequency.
You can set up to five unique Recurring Buys. This enables you to buy different amounts of bitcoin on different time frames concurrently, all while being sent directly to self-custody for free 🤯

\ Amount: Select the amount of dollars you want to convert into bitcoin. \ \ Source: The bank to pull dollars.\ \ Destination: Your personal bitcoin wallet. Bitcoin Well automatically converts incoming dollars to bitcoin immediately when they are received. Your bitcoin will be automatically batched and sent to you for free.
Frequency: Your purchase frequency is set to ‘One time’ by default so you can smash buy.
You can set your payment frequency to weekly, biweekly or monthly. When setting your frequency, choose the start date: you can select “Today” or navigate the calendar to choose a later start date.

\ Once you’ve set up your Recurring Buy, select “Review” and then “Confirm” to activate your bitcoin Recurring Buy. The best bitcoin Recurring Buy in the USA is here 🐐
Pausing, cancelling or changing your Recurring Buy
\ You can easily pause or cancel any of your Recurring Buys from the Buy bitcoin page. All of your Recurring Buys will be shown on the right-hand side of your Buy bitcoin page on desktop or at the bottom of your Buy bitcoin page on mobile. \ \ To pause a Recurring Buy, click the pause button within the Recurring Buy preview in your Buy bitcoin page. Similarly, to cancel a Recurring Buy, click the ‘Cancel’ button within the Recurring Buy preview. \ \ To replace an active Recurring Buy, simply cancel your active Recurring Buy as described above and then set up a new Recurring Buy with your new desired amount and frequency. For example: you want to cancel an existing biweekly $200 Recurring Buy with a weekly $100 Recurring Buy. Cancel the existing biweekly $200 Recurring buy, then set up a new weekly $100 Recurring Buy as described in Set your transaction details.

\ As always, your bitcoin is automatically purchased at the current market rate when your dollars arrive. Additionally, your bitcoin will be batched and sent out on the blockchain for free by default.
Earn sats from your bitcoin transactions
\ Bitcoin Well is also the best place in the world to earn bitcoin. When you earn points in your Bitcoin Well account, you gain the opportunity to play the Bitcoin (Wishing) Well, where you win sats with every play.
The best part? We send bitcoin that you win straight to your personal wallet via the Lightning Network ⚡
Oh yeah, did we mention you can win 1,000,000 sats? If you're an active Bitcoin Well customer, there is a chance you've earned a pile of points. The more you use your account for buying, selling or spending bitcoin - the more points you’ll earn! Log in to your Bitcoin Well account and check your point balance.
About Bitcoin Well
\ Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we make it easy to use bitcoin with self-custody.
-
 @ 5b0183ab:a114563e
2025-03-06 17:38:10
@ 5b0183ab:a114563e
2025-03-06 17:38:10What Is Dark Nostr?
Dark Nostr can be described as the unintended adverse effects that arise from creating systems designed to resist censorship and promote freedom. These systems often rely on algorithms and micropayments to function, but their very design can inadvertently spawn phenomena that are unpredictable, uncontrollable, and sometimes downright weird.
Think of it as the Yin to the Yang of decentralized freedom—a necessary shadow cast by the bright ideals of liberation. While freedom protocols aim to empower individuals, they also open the door to consequences that aren’t always sunshine and rainbows.
An Emergent Phenomenon
The fascinating thing about Dark Nostr is its emergent nature. This means it’s not something you can fully define or predict ahead of time; instead, it arises organically as decentralized systems are implemented and evolve. Like watching clouds form shapes in the sky, GM miners panhandle for sats or shower girls in the global feed, you can only observe it as it happens—and even then, its contours remain elusive.
Emergent phenomena are tricky beasts. While simplicity is at the core of the protocol layer darkness is born on the edge where complexity thrives—where individual components interact in ways that produce unpredictable outcomes. In this case, Dark Nostr encapsulates everything from algorithmic quirks and micropayment dynamics to unforeseen social consequences within decentralized ecosystems.
Studying Dark Nostr: Memes as Cultural Artifacts
Here’s where things get anthropologically juicy: much of what we know about Dark Nostr comes not from academic papers or technical manuals but from memes. Yes, memes—the internet’s favorite medium for cultural commentary—have become a lens through which this phenomenon is being observed and studied.
Memes act as modern-day hieroglyphs, distilling complex ideas into bite-sized cultural artifacts that reflect collective sentiment. When communities encounter something as nebulous as Dark Nostr, they turn to humor and symbolism to make sense of it. In doing so, they create a shared narrative—a way to grapple with the shadow side of decentralization without losing sight of its promise.
Why Does It Matter?
Dark Nostr isn’t just an abstract concept for philosophers or tech enthusiasts—it’s a reminder that every innovation comes with trade-offs. While decentralized systems aim to empower individuals by resisting censorship and central control, they also carry risks that must be acknowledged:
- Algorithmic Chaos: Algorithms designed for freedom might amplify harmful content or create echo chambers.
- Micropayment Pitfalls: Financial incentives could lead to exploitation or manipulation within these systems.
- Social Dynamics: The lack of centralized control might enable bad actors or foster unforeseen societal shifts.Understanding Dark Nostr is crucial for anyone involved in building or using decentralized technologies. It challenges us to balance freedom with responsibility and reminds us that even the most well-intentioned systems have their shadow side.
Conclusion: Embracing the Shadow
Dark Nostr is more than just a cautionary tale—it’s a fascinating glimpse into the complexities of human interaction with technology. As an emergent phenomenon, it invites us to remain vigilant and adaptive as we navigate the uncharted waters of decentralization.
By studying its manifestations through cultural artifacts like memes and engaging in thoughtful reflection, we can better prepare for both its opportunities and risks. After all, every great innovation needs its shadow—it’s what makes progress real, messy, and human.
So here we stand before Dark Nostr: may we study it wisely, meme it relentlessly, and learn from its lessons as we build the future together.
Stay Vigilent Nostr.....
-
 @ 6e0ea5d6:0327f353
2025-03-06 15:32:33
@ 6e0ea5d6:0327f353
2025-03-06 15:32:33Ascolta bene!
Absorb from suffering the lessons that joy would never dare to offer you.
Davvero, all strong men are truly tested only when everything falls apart. It is easy to feel good and motivated on happy days. But in life's great adversities, we discover whether we can truly withstand what our optimism conveniently sweeps under the rug.
When you are dragged by powerful currents, regretting diving into deep waters is useless. The only path is to fight with strong strokes to avoid drowning and cling to the first rock or log that appears on the riverbank to survive. Likewise, my friend, your regrets and remorse are like concrete weights tied to your feet, dragging you deeper into despair.
Which man has never tormented himself thinking, "What if I had done things differently?" The failure of your decisions must be confronted with all your strength. Do not lament what you could have done or failed to do—focus your mind on fixing what is still within your control. This is not about motivation; it is about survival. A wound, once healed, becomes a scar. A mistake, once learned from, becomes a valuable lesson.
Anguish, sadness, and frustration are anchors that paralyze and offer no benefit. You must not stop your journey just because your shoes have worn out. You cannot bury your will to win simply because of the defeats along the way. Nothing will ever be easy—it never was. Anyone who says otherwise is a cunning liar!
Infatti, if there is one piece of advice I can give to each of you, it is this: never allow yourself to succumb when everything collapses, and your plans slip through your fingers.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ f1989a96:bcaaf2c1
2025-03-06 14:49:57
@ f1989a96:bcaaf2c1
2025-03-06 14:49:57Good morning, readers!
In Nicaragua, the regime is increasingly cracking down on civil society, imposing new financial regulations on non-governmental organizations (NGOs) that require them to disclose donors and report all financial transactions — further restricting their ability to operate independently. Meanwhile, in Iraq, the central bank governor announced plans to introduce a central bank digital currency (CBDC) to replace cash in circulation. CBDCs are a mechanism for using digital currencies to centralize financial control.
In freedom tech news, Alby Go, a mobile Bitcoin Lightning wallet, added support for Pick n Pay QR codes, making it easier for South Africans to pay with Bitcoin at one of the country’s largest retailers. Additionally, Bitcoin Safe, an open-source Bitcoin wallet designed to simplify self-custody, introduced support for Burmese and Korean Languages, making the wallet more accessible to activists, dissidents, and individuals in these regions.
We end with a new discussion from 21st Capital, where Alex Gladstein, Chief Strategy Officer at HRF, joins Ziya Sadr, an Iranian activist and Bitcoin educator, to explore Bitcoin’s role in fighting financial repression and advancing global freedom. Sadr, who was detained by the Iranian regime during the Mahsa Amini protests, shares a sobering account of authoritarian control and the ways Bitcoin can help alleviate these struggles.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Nicaragua | Increases Financial Surveillance of NGOs
Nicaragua’s dictator, Daniel Ortega, intensified his crackdown on civil society with two new regulations that significantly increase the Ministry of the Interior’s (MINT) authority over national and foreign NGOs. The new regulations require NGOs to submit financial documentation, disclose their donors, and report all financial transactions. Using this information, authorities can now classify organizations as “threats,” conduct surprise inspections, impose sanctions, seize assets, and force closure. These regulations, framed as efforts to combat “digital terrorism,” intensify state surveillance and control and are a continuation of the regime’s systematic use of financial repression to silence dissent. This year alone, Ortega shut down 15 NGOs, and since 2021, he has closed over 5,600.
El Salvador | IMF Approves 1.4 Billion Loan With Further Restrictions
The International Monetary Fund (IMF) has officially approved its $1.4 billion loan to El Salvador while reinforcing even stricter limits on Bitcoin. This comes after last month’s legal reforms that made Bitcoin acceptance voluntary and prohibited its use for tax payments. The finalized deal, which grants an immediate $113 million disbursement, confines “government engagement in Bitcoin-related economic activities, as well as government transactions in and purchases of Bitcoin.” Despite these constraints, President Bukele has continued to flaunt Bitcoin purchases on social media, leaving many questions unanswered. Where does this bitcoin come from? Who controls the wallets? The lack of transparency remains.
Iraq | Issuing CBDC to Replace Cash
Iraq’s central bank governor, Ali Al-Allaq, announced that “the Iraqi central bank is now moving to create its own digital currency which will gradually replace paper notes.” Al-Allaq highlighted that this move aligns with broader “radical” changes in the global financial system. This news comes after Iraq banned all digital assets in 2017, citing concerns over financial crime and terrorism. Yet, its embrace of a CBDC over decentralized currencies like Bitcoin highlights a familiar pattern. China, Nigeria, and Russia have also pushed for CBDCs while restricting Bitcoin. Evidently, authoritarian regimes prefer financial control to remain in their own hands rather than risk empowering the public.
Nigeria | Frees Tigran Gambaryan in Exchange for Greater Financial Surveillance
In October 2024, Nigeria released Tigran Gambaryan, a former Binance executive accused of money laundering and contributing to the naira’s devaluation — though, in reality, he was a scapegoat for the regime’s economic mismanagement. According to The Rage, his release was secured through a deal with the US to help Nigeria prosecute “cryptocurrency and financial crimes.” Soon after, the two countries announced the creation of a “Bilateral Liaison Group on Illicit Finance and Cryptocurrencies” to expand Nigeria’s surveillance capabilities and “pursue cybercrime investigations and prosecutions.” Gambaryan, who described his prison conditions as “torture,” now faces an unsettling reality: his freedom may have come at the cost of strengthening an authoritarian regime notorious for its financial repression.
Turkey | X Blocks Accounts of Three Journalists at Regimes Request
X recently blocked the accounts of three Kurdish journalists in Turkey — Abdurrahman Gök, Oktay Candemir, and Ruşen Takva — following a Turkish government request citing concerns over “national security.” The journalists, known for exposing government corruption and reporting on Kurdish issues, now join a growing list of silenced Turkish reporters. This comes as Turkey intensifies its crackdown on independent media through arrests, legal pressure, and censorship. With 95% of media outlets in Turkey complying with the regime, social platforms remain one of the last places for free expression. Yet, as X and other platforms increasingly comply with authoritarian demands, access to independent information shrinks. This escalating repression underscores the need for censorship-resistant alternatives like nostr, where government pressure or corporate compliance cannot easily suppress speech.
__________
Webinar Series for Nonprofits: Become Unstoppable
HRF will host a free, three-day webinar from March 17–19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation.
SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)
Join HRF at SXSW 2025 in Austin from March 7–13 to explore how CBDCs threaten financial freedom. Experts Roger Huang, Charlene Fadirepo, and Nick Anthony will discuss how authoritarian regimes use CBDCs for surveillance and control. Attendees can also visit HRF’s CBDC Tracker booth to explore an interactive map of CBDC developments worldwide.
Get your tickets
__________
BITCOIN AND FREEDOM TECH NEWS
Nostr Wallet Connect | Introduces Pull Request for On-Chain Send and Receive
Nostr Wallet Connect (NWC), a protocol that connects Bitcoin Lightning wallets and applications, is developing a potential upgrade: support for on-chain Bitcoin transactions. Currently, NWC is designed for Lightning transactions. This new update would allow users to also send and receive on-chain Bitcoin transactions, which are slower and less private, but more secure with higher send and receive limits. This means users and apps can more easily move funds between Lightning and regular Bitcoin wallets, making NWC more practical and flexible. This upgrade enhances financial resilience for dissidents and activists by providing a more secure and flexible way to store and move Bitcoin.
Bitcoin Safe | Adds Support for Burmese and Korean Languages
Bitcoin Safe, an open-source Bitcoin wallet designed to make self-custody simple — even for non-technical users — introduced support for Burmese and Korean Languages. This support makes the wallet more accessible to activists, dissidents, and individuals in these regions, empowering them with uncensorable and unseizable money. Bitcoin Safe guides users through the entire setup process, offering step-by-step instructions for single-signature wallets (where one private key controls your Bitcoin) and multisignature wallets (which require multiple private keys for added security). By breaking down barriers to Bitcoin self-custody, Bitcoin Safe is making financial freedom accessible to those who need it most.
Frostr | Turn Your Nostr Private Key into a Rotatable Multisig
Frostr is an experimental new tool that adds a layer of security to a user’s nostr private key by splitting it into multiple parts. Instead of using a single key, Frostr divides the key into shares, requiring a subset of these shares to sign messages on nostr. This offers two key benefits. First, greater security; even if one share is lost or stolen, a user’s full key remains secret and in their control. Second, flexible key rotation; users can replace or update shares of the key without changing their digital identity. This is an important advancement for activists, journalists, and human rights defenders. Many authoritarian regimes track, censor, and punish those who speak freely. If an activist’s private key is compromised, their digital identity and safety could be at risk. Frostr removes this single point of failure and empowers users to communicate freely, securely, and flexibly, even in hostile environments.
Alby Go | Integrates Pick n Pay QRs for Bitcoin Payments in South Africa
Alby Go, a mobile Bitcoin Lightning wallet, added support for Pick n Pay QR codes, making it easier for South Africans to pay with Bitcoin at one of the country’s largest retailers. The update also integrates BTC map, offering users a detailed directory of merchants that accept Bitcoin. These changes make everyday Bitcoin payments more practical, expand access to businesses that accept Bitcoin, and give South Africans an alternative to the country’s unstable financial system and currency.
bitcoin++ | Announces Freedom and Privacy Edition
bitcoin++, a bitcoin-only developer conference series, is set to return on August 7-8, 2025, with a dedicated focus on freedom and privacy. Taking place in Riga, Latvia the event will bring together privacy advocates, developers, and freedom tech enthusiasts to explore the latest developments in privacy tech, censorship resistance, and open-source development on Bitcoin. Learn more and get your tickets here.
RECOMMENDED CONTENT
Bitcoin’s Potential to Revolutionize Freedom with Alex Gladstein
In this episode of 21st Capital, Alex Gladstein, Chief Strategy Officer at HRF, sits down with Ziya Sadr, an Iranian activist and Bitcoin educator, to discuss Bitcoin’s role in fighting financial repression and advancing global freedom. Ziya helped build Iran’s Farsi-speaking Bitcoin community, created educational content on privacy, and contributed to open-source translation projects. He was later detained by the Iranian regime during the Mahsa Amini protests. During the discussion, Gladstein highlights stories of individuals escaping authoritarian control, accessing global markets, and securing their wealth through Bitcoin. Watch here to learn how Bitcoin is a tool for human rights.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-06 14:49:20
@ 5d4b6c8d:8a1c1ee3
2025-03-06 14:49:20https://primal.net/e/nevent1qvzqqqqqqypzqntcggz30qhq60ltqdx32zku9d46unhrkjtcv7fml7jx3dh4h94nqqsvzgwvn5e9wr7hujh8f86gffs9s9xkx483rm3at9t4gmkryhwu05qhf8s8l
Nice quick primer on one of the advantages of fasting.
originally posted at https://stacker.news/items/905637
-
 @ cbaa0c82:e9313245
2025-03-06 13:45:58
@ cbaa0c82:e9313245
2025-03-06 13:45:58TheWholeGrain - #February2025
Ah, February! The month of love! Well, it is if Valentine's Day and a few slices of bread have anything to say about it! All of this month's Sunday Singles all revolved around this theme. How can we portray to folks our love for, well, Love! We even changed our logo on Valentine's Day this year and released the art for it as a note using the NOSTR protocol.
The adventure known as Questline released two more pages of its story ending the month with readers wondering how will the gang deal with their first adversary.
As usual a piece of Concept Art and Bitcoin Art were released. However, some will notice that the art work was released with a new framing standard which we plan to continue.
Last of all, we started releasing merchandise with an exclusive bundle inspired by this month's Toast's Comic Collection. You'll see more information about this near the end of this issue of The Whole Grain.
Sunday Singles - February 2025 2025-02-02 | Sunday Single 78 Title: Cupid If you don’t watch out, you might just get struck by Cupid’s arrow! https://i.nostr.build/Op8Snf3PjwJvzzK8.png
2025-02-09 | Sunday Single 79 Title: Ace of Hearts Will you be an Ace this Valentine’s Day? https://i.nostr.build/X5fEXpE9HJIR2QCH.png
2025-02-16 | Sunday Single 80 Title: Three of Hearts Talk about lucky! Here are three hearts worth having! https://i.nostr.build/5JfWe3GggiPEEULv.png
2025-02-23 | Sunday Single 81 Title: Chemistry For the past month our top scientist has been studying chemistry. https://i.nostr.build/VS4GN0D7vH7cQUyv.png
Adventure Series: Questline Bread, Toast, and End-Piece left a recently burned down village behind them. As they continue forward pondering what they have recently seen they are about to be surprised by something big...
Writer: Daniel David (dan 🍞) Artist: Dakota Jernigan (The Bitcoin Painter)
2025-02-11 | Questline 003 - Time to Move Forward After some time investigating the recently torched village our heroes continue on the path. Toast is happy to be leaving it behind them, but Bread continues to wonder what could have possibly caused such immense damage... and where were all the villagers? https://i.nostr.build/gh7OlC14dUCrzorW.png
2025-02-25 | Questline 004 - Winged Predator The village and its dark clouds can no longer be seen behind our heroes. However, Bread still cannot stop pondering the village, and what could have happened to it. Suddenly, within a span of few seconds, Toast notices their three shadows engrossed by a much larger one and hears what is approaching behind them. https://i.nostr.build/SlAxb3eRzptMe3il.png
Other Content Released in February 2025 2025-02-05 | Toast's Comic Collection Title: Batbread #10 I am... vengeance. I am... the night.
I am... Batbread. https://i.nostr.build/Townax6XYzlZbKpa.png2025-02-12 | Concept Art Title: Second Toast Sketch A second sketch of the character Toast. Remade and cleaned up. https://i.nostr.build/zcUuetaZDGEqjrqU.png
2025-02-14 | Leftover Title: Valentine's Day 2025 Happy Valentine's Day! 💘
We know that we say this a lot, but... 🍞 ♥️ U https://i.nostr.build/12MUzD8uVwfDBY0t.png2025-02-19 | Bitcoin Art Title: The Miner Block Height: 884458 End-Piece is the miner of the group. Someone has to do the hard work! https://i.nostr.build/03EYvG3owN6TeRki.png
Merchandise Announcement We want to begin selling some merchandise. After the success of the exclusive metal cut-outs sold at Nostr Valley 2024 we decided to sell something similar. Bread and Toast made an announcement this past month shortly after this month's Toast's Comic Collection release with the Batbread Bundle (Limited Supply). https://i.nostr.build/PNt4kyEJkaCe7q1K.png
If you are interested in purchasing he Batbread Bundle contact us by email at store@breadandtoast.com with "Batbread" in the subject line! There are only 21 in total available. It'll be first come, first serve!
Thanks for checking out the sixth issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
🍞 ♥️ U Bread, Toast, and End-Piece
BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #Valentines #Love #🖼️
List of nPubs Mentioned: The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
-
 @ e09beaa0:0720965a
2025-03-06 13:34:08
@ e09beaa0:0720965a
2025-03-06 13:34:08This event has been deleted; your client is ignoring the delete request.
-
 @ d830ee7b:4e61cd62
2025-03-06 12:41:15
@ d830ee7b:4e61cd62
2025-03-06 12:41:15สายลมพัดกระโชกแรง แทรกซึมผ่านแนวต้นไม้สูงใหญ่ในป่าทึบ รัตติกาลโอบล้อมทุกสิ่งไว้ในความมืดมิด ร่างของเอี้ยก้วยเคลื่อนผ่านเส้นทางขรุขระ ย่ำเดินไปบนโคลนที่เปียกชื้นจากฝนที่ตกพรำมาทั้งวัน
ทุกย่างก้าวหนักอึ้ง... ไม่ใช่เพราะความเหนื่อยล้าของร่างกาย แต่เป็นภาระของหัวใจที่แบกรับไว้—มันหนักเสียยิ่งกว่าภูเขาหลายลูก
เซียวเหล่งนึ่ง... จากไปแล้ว
ราวกับสวรรค์เล่นตลก เหมือนโชคชะตากำลังทดสอบจิตวิญญาณของเขา ทุกสิ่งที่เขาต่อสู้เพื่อมัน ทุกสิ่งที่เขาหวงแหน... กลับถูกพรากไปอย่างโหดร้าย ไม่มีสิ่งใดเจ็บปวดมากไปกว่าการยืนอยู่เพียงลำพังในโลกกว้างใหญ่ที่ไร้เงาของนาง
ไม่นานก่อนหน้านี้ เอี้ยก้วยและเซียวเหล่งนึ่งยังคงอยู่ด้วยกันภายใน หุบเขาสุสานโบราณ—สถานที่ที่ทั้งสองเคยให้คำมั่นว่าจะครองรักกันไปชั่วชีวิต แต่แล้วโชคชะตาก็พลิกผันอย่างโหดร้าย
เซียวเหล่งนึ่งเชื่อว่า ตนเองถูกวางยาพิษร้ายแรง นางไม่ต้องการให้เอี้ยก้วยต้องทนทุกข์ทรมานกับการเห็นนางจากไปช้าๆ—นางจึงเลือกที่จะทิ้งเขาไว้
“อย่าตามหาข้า...”
เสียงของนางยังคงก้องอยู่ในใจเขา แม้จะเป็นเพียงกระซิบแผ่วเบาในคืนฝนตก แต่สำหรับเอี้ยก้วย มันราวกับเสียงฟ้าผ่าที่ทำลายทุกสิ่ง
เขาเคยสาบานว่าจะอยู่เคียงข้างนาง แต่สุดท้ายนางกลับเลือกหนทางนี้...
ฝนยังคงโปรยปราย สายลมยังคงโหมพัด แต่ในใจของเอี้ยก้วย กลับเงียบงันยิ่งกว่าทะเลทรายอันว่างเปล่า
ตั้งแต่วันที่เซียวเหล่งนึ่งจากไป เขาออกเดินทางโดยไร้จุดหมาย เท้าของเขาพาเขาไปข้างหน้าอย่างไร้ทิศทาง แม้แต่ตัวเขาเองก็ไม่รู้ว่ากำลังจะไปที่ใด
หรือบางที... อาจเป็นเพราะเขาไม่สนใจอีกแล้ว
เขาเดินฝ่าภูเขา ป่าทึบ ลัดเลาะเส้นทางอันเปลี่ยวร้างของยุทธภพ แววตาของเขามิได้เต็มไปด้วยความโกรธแค้นอีกต่อไป แต่มันกลับกลายเป็นความว่างเปล่า ราวกับวิหคที่บินหลงทางในฟากฟ้าอันไร้ที่สิ้นสุด
เขาไม่ได้มุ่งหน้ากลับไปที่สุสานโบราณ เพราะเขารู้ว่า—ต่อให้กลับไป ก็จะไม่พบสิ่งใดอีกแล้ว

เสียงฟ้าคำรามก้องกังวาน สายฟ้าผ่าลงมาส่องแสงวาบผ่านม่านเมฆดำสนิท ลำแสงสีขาวแหวกทะลุเงาของต้นไม้สูงใหญ่ เผยให้เห็นร่างของเอี้ยก้วยที่ยังคงยืนอยู่กลางพายุ
เสื้อคลุมของเขาเปียกโชกจากสายฝน น้ำฝนไหลซึมผ่านผิวกาย แต่อากาศหนาวเย็นกลับไม่อาจทำให้เขาสั่นสะท้านได้ เพราะจิตใจของเขาเย็นยะเยือกยิ่งกว่าสายลมที่พัดผ่าน
“ทำไมกัน...”
เสียงของเขาถูกกลืนหายไปในเสียงพายุ เอี้ยก้วยกำมือแน่น รู้สึกถึงอารมณ์ที่ปะทุขึ้นภายใน—มันเป็นทั้งความเจ็บปวด ความโกรธ ความสับสน และความสิ้นหวัง
แต่ทันใดนั้นเอง...
เขาสัมผัสได้ถึงบางสิ่ง
มันไม่ใช่เพียงเสียงพายุ หรือเสียงใบไม้ไหวในสายลม—แต่เป็นสายตา... สายตาของใครบางคนกำลังจ้องมองเขาอยู่
ร่างของเอี้ยก้วยตวัดสายตามองไปรอบตัว ลมหายใจของเขาติดขัด ฝนที่ตกหนักบดบังทุกสิ่งรอบกาย แต่มันมิอาจบดบังสัมผัสของเขาได้
จากมุมหนึ่งของม่านฝน...
เงาหนึ่งขยับเข้ามาอย่างแผ่วเบา
แม้ไม่มีเสียงฝีเท้า แต่พลังที่เปล่งออกมากลับหนักหน่วง ยิ่งกว่าคลื่นของมหาสมุทร
เสียงหนึ่งดังขึ้น แทรกผ่านสายฝน...
"ดูเหมือนเจ้ายังไม่เข้าใจสายฝนดีพอ..."
มันไม่ดังนักแต่กลับทะลวงเข้าสู่หัวใจ เอี้ยก้วยหันขวับ ดวงตาจ้องเขม็งผ่านม่านน้ำ
แล้วเขาก็เห็น...
ชายผู้นั้นยืนอยู่กลางสายฝน แต่เสื้อคลุมขาวของเขากลับมิได้เปียกโชกแม้แต่น้อย ร่างสูงโปร่งแต่กลับแฝงไว้ด้วยพลังอันไม่อาจหยั่งถึง ดวงตาของเขาสงบนิ่งยิ่งกว่าน้ำในบึงลึก ทว่ากลับสะท้อนความลี้ลับดุจมหาสมุทร
“ข้าแซ่ JAKK นามว่า Goodday”
เสียงของเขาราบเรียบ แต่กลับทำให้หัวใจของเอี้ยก้วยเต้นแรงอย่างไม่รู้สาเหตุ มันไม่ใช่พลังข่มขู่ แต่เป็นแรงกดดันที่มาโดยธรรมชาติ ราวกับภูเขาสูงตระหง่านที่มิได้พยายามบดบังแสงอาทิตย์ แต่กลับบังมันไว้โดยสมบูรณ์
“เจ้าคือใครกันแน่?” เอี้ยก้วยเอ่ยถาม ดวงตาจ้องมองชายลึกลับตรงหน้า “เจ้ามีจุดประสงค์ใดถึงได้ปรากฏตัวต่อหน้าข้า?”
JAKK เพียงแค่ยิ้มบาง ๆ แต่ในดวงตานั้นกลับฉายแววที่ทำให้หัวใจของเอี้ยก้วยสั่นสะท้าน
“ข้าคือผู้เดินทางผ่าน เช่นเดียวกับสายฝนนี้”
เอี้ยก้วยขมวดคิ้ว คำพูดเหล่านั้นช่างคลุมเครือ ราวกับหยาดฝนที่ร่วงหล่นแต่กลับไร้รูปร่างจับต้อง
ทันใดนั้นเอง สายลมกระโชกแรงขึ้น ฝนที่เคยสาดกระหน่ำกลับเปลี่ยนทิศทาง หยาดน้ำที่ตกลงมากลางอากาศดูเหมือนจะหยุดนิ่ง ก่อนจะไหลวนตามแรงที่มองไม่เห็น ราวกับทั้งสายฝนนี้กำลังถูกควบคุม

ฟึ่บ!
เสี้ยววินาทีถัดมา เอี้ยก้วยสัมผัสได้ถึงแรงบางอย่างที่พุ่งผ่านใบหน้า ไม่ใช่ลม ไม่ใช่ฝน แต่มันคือบางสิ่งที่จับต้องไม่ได้!
เขาตวัดกระบี่ขึ้นอย่างฉับพลัน แต่กลับสัมผัสได้เพียงความว่างเปล่า พริบตานั้นเอง... ใบไม้ด้านหลังเขาถูกเฉือนขาดเป็นเส้นตรง!
เอี้ยก้วยเบิกตากว้าง "นี่มัน..."
JAKK เอียงศีรษะเล็กน้อย ดวงตาฉายแววของผู้ที่มองเห็นสิ่งที่ผู้อื่นมองไม่ออก
“ฝนสามารถทำให้ดินชุ่มชื้น หรือสามารถกัดเซาะภูเขาได้” เขากล่าวช้า ๆ “แต่เจ้ากลับปล่อยให้มันตกต้องโดยไร้ความหมาย”
เอี้ยก้วยกำกระบี่แน่น รู้สึกถึงความโกรธที่แล่นขึ้นมาในอก "เจ้าหมายความว่าอย่างไร?"
JAKK ไม่ตอบ แต่เพียงยื่นมือออกไป หยดน้ำฝนที่ปลายนิ้วของเขาค่อย ๆ ไหลรวมกันเป็นเส้นบางเบา ส่องประกายราวใยไหมในความมืด
"น้ำ... ไม่ได้แข็งแกร่งที่สุด"
"แต่มันไม่มีใครทำลายมันได้"
เอี้ยก้วยขมวดคิ้ว เขาไม่เข้าใจ... หรือบางที เขาอาจไม่อยากเข้าใจ
JAKK ปล่อยให้ความเงียบเข้าปกคลุมชั่วขณะ ก่อนจะกล่าวขึ้นด้วยเสียงแผ่วเบา แต่แหลมคมกว่ากระบี่ใด ๆ
"เจ้ากำลังเผชิญหน้ากับสายฝน... หรือเจ้ากำลังปล่อยให้มันกลืนกินเจ้า?"
คำถามที่ดูเหมือนไร้ความหมาย... กลับหนักหน่วงยิ่งกว่าสายฝนที่โหมกระหน่ำ เอี้ยก้วยรู้สึกถึงอะไรบางอย่างกำลังสั่นคลอนอยู่ในจิตใจของตนเอง
"ฝนเป็นเพียงฝน ข้าจะไปอยู่เหนือมันหรือถูกมันชะล้างได้อย่างไร?" เขาตอบโดยไม่ต้องคิด
JAKK ยิ้มเพียงเล็กน้อย ก่อนกล่าวคำที่ทำให้เอี้ยก้วยต้องนิ่งงัน
"เช่นนั้น เจ้าก็ไม่อาจเข้าใจสิ่งที่กำลังมองหา..."
สายฝนยังคงโปรยปราย ท้องฟ้ามืดครึ้มราวกับมหาสมุทรที่คว่ำลงสู่พื้นพิภพ ฟ้าคำรามก้อง ลำแสงสายฟ้าแหวกม่านเมฆดำสาดลงมาราวกับต้องการเปิดโปงความลึกลับที่ปกคลุมค่ำคืนนี้
เอี้ยก้วยยืนตระหง่านอยู่กลางลานหิน สายตาของเขามิได้จดจ้องสายฝนที่ซัดกระหน่ำร่างของเขาอีกต่อไป หากแต่จับจ้องอยู่ที่ชายตรงหน้า—บุรุษผู้เผยตนจากม่านฝน ร่างสูงสง่าในอาภรณ์ขาวสะอาดไร้รอยเปียก ดวงตาสงบนิ่งดังมหานทีอันลึกล้ำ
“เจ้ากำลังต้านฝน…” JAKK กล่าวเสียงเรียบ “แต่สายฝนนี้มิใช่ศัตรูของเจ้า”
เอี้ยก้วยสูดลมหายใจเข้าลึก กระชับกระบี่ในมือแน่น
“ข้ามิได้มาที่นี่เพื่อทดสอบความหมายของหยาดฝน” เสียงของเขาเด็ดเดี่ยว “แต่เพื่อพิสูจน์ว่าข้ายังยืนหยัดอยู่ได้ แม้สวรรค์จะทอดทิ้งข้า”

JAKK มิได้กล่าวตอบ แต่ปลายนิ้วของเขายื่นออกมาเพียงเล็กน้อย
ฟึ่บ!
สายฝนรอบตัว JAKK คล้ายหยุดนิ่งไปชั่วขณะ ก่อนจะรวมตัวกันเป็นเส้นสายโปร่งใสราวกับใยไหมสะท้อนแสงจันทร์
“ใยวารี”
เสียงกระซิบแผ่วเบาดังลอดออกจากริมฝีปากของ JAKK และในพริบตานั้นเอง เส้นสายเหล่านั้นก็แปรเปลี่ยนเป็นอาวุธแห่งธารา แหวกอากาศพุ่งเข้าหาเอี้ยก้วยด้วยความเร็วเหนือมนุษย์!
เคร้ง!
เอี้ยก้วยสะบัดกระบี่ปัดป้อง แต่บางสิ่งผิดปกติ เส้นใยน้ำมิได้ถูกเฉือนขาด กลับพันรอบคมกระบี่ราวกับเถาวัลย์ที่ไร้ตัวตน ร่างของเขาถูกดึงรั้งไปข้างหน้าโดยไม่รู้ตัว!
“อะไร!?”
ฟึ่บ!
เอี้ยก้วยตัดสินใจกระโจนขึ้นกลางอากาศ หมุนตัวเพื่อสะบัดใยวารีออกจากร่าง แต่ในขณะที่เขาลอยตัวกลางหาว ใยโปร่งใสเหล่านั้นกลับเคลื่อนตามมาอย่างลื่นไหล ปรับทิศทางเหมือนมันมีชีวิต!
JAKK มองภาพนั้นนิ่ง ๆ ดวงตาของเขาไร้แววเย้ยหยัน มีเพียงประกายแห่งการสังเกต
“สายน้ำไม่เคยยึดติด ไม่เคยต่อต้าน” JAKK กล่าวเรียบ ๆ “มันซึมซับทุกสิ่งอย่างไร้รูปร่าง เจ้ายังไม่เข้าใจสิ่งที่อยู่ตรงหน้า”
เอี้ยก้วยกัดฟันแน่น ฝ่ามือที่จับกระบี่เริ่มสั่นเล็กน้อย นี่มิใช่วิชาที่เขาเคยประมือมาก่อน…
“ถ้าเช่นนั้น ข้าจะทำให้มันแตกสลาย!”
กระบี่วิหคโบยบิน!
เอี้ยก้วยระเบิดพลังสุดกำลัง กวัดแกว่งกระบี่เป็นวงกว้าง ตวัดเป็นแนวสายลมกรรโชก!
ลำแสงแห่งกระบี่พุ่งตัดผ่านม่านฝน ปะทะเข้ากับใยวารีที่พุ่งมาอย่างแรง!
ฉัวะ!
สิ่งที่เกิดขึ้นหาใช่การแตกสลายของใยวารีไม่ เส้นใยเหล่านั้นกลับยืดหยุ่นและดูดซับแรงปะทะของกระบี่ ราวกับมันมิใช่ของแข็งหรือของเหลว แต่เป็นสภาวะที่อยู่เหนือขึ้นไป!
เคร้ง!
แรงสะท้อนทำให้เอี้ยก้วยเสียหลัก กระบี่ของเขาถูกดูดซับพลังไปในชั่วพริบตา ร่างของเขาถอยหลังไปหลายก้าว หัวใจเต้นแรง
“เป็นไปไม่ได้...”
JAKK ก้าวเข้ามาช้า ๆ สายตาไร้แววสมเพชหรือโอ้อวด มีเพียงความสงบเช่นผืนน้ำที่ไร้คลื่น
“พลังที่แข็งแกร่งที่สุด มิใช่พลังที่เผชิญหน้า” เขากล่าว “แต่คือพลังที่อยู่เหนือการเผชิญหน้า”
เอี้ยก้วยยังไม่เข้าใจ แต่จิตใจของเขาเริ่มหวั่นไหว
JAKK มองเขาเงียบ ๆ ก่อนจะพลิกมืออย่างแผ่วเบา
ฟึ่บ!
ใยวารีสายสุดท้ายพุ่งตรงเข้าหาร่างของเอี้ยก้วย!
เอี้ยก้วยสะบัดกระบี่ขึ้นสุดกำลังเพื่อป้องกัน แต่…
ครั้งนี้ เขารู้สึกว่า มันมิใช่สิ่งที่สามารถต้านทานได้ด้วยพลังเพียงอย่างเดียว

เขายังคงหอบหายใจหนัก สองมือกำกระบี่แน่น สายตาจับจ้องไปยังชายตรงหน้า—JAKK บุรุษผู้ควบคุมน้ำฝนได้ดั่งอวัยวะของตนเอง เขาเพียงยืนอยู่ตรงนั้น ดวงตาเรียบนิ่ง ไม่แสดงความเหนือกว่า แต่กลับเปล่งพลังลี้ลับราวกับสายน้ำในห้วงลึก
เอี้ยก้วยไม่เคยเจอศัตรูเช่นนี้มาก่อน
ทุกกระบวนท่าของเขาถูกทำให้ไร้ความหมาย ดุจพายุกระหน่ำใส่ธารน้ำ มันมิได้แตกหัก แต่มันกลืนกินและซึมซับทุกสิ่งที่เข้ามา
“ข้ายังไม่เข้าใจ…”
เสียงของเอี้ยก้วยแผ่วเบา แต่หนักแน่นในความสงสัย ดวงตาของเขายังคงคุกรุ่นด้วยไฟแห่งการต่อสู้ แต่ในแววตานั้น เริ่มฉายแววของบางสิ่งที่เปลี่ยนแปลง
JAKK พินิจเขาครู่หนึ่งก่อนกล่าวขึ้น “เจ้ายังมิอาจปล่อยให้สายน้ำไหลผ่านใจเจ้า”
เขายื่นมือออกไป หยดน้ำฝนที่ตกลงมากลางอากาศหยุดนิ่งชั่วขณะ ก่อนจะค่อย ๆ เคลื่อนไหว หมุนวนในอากาศดุจเส้นไหมโปร่งใส เอี้ยก้วยจ้องมองมัน หัวใจเต้นแรง
มันไร้รูปร่าง ไร้ขีดจำกัด…
เช่นนั้นข้าจะทำลายมันได้อย่างไร?
เอี้ยก้วยก้าวถอยหลังหนึ่งก้าว นี่เป็นครั้งแรกที่เขารู้สึกว่าไม่อาจพึ่งพากระบี่ของตนเองได้
“ข้าคิดว่าข้ารู้จักกระบี่ของข้าดีที่สุด แต่เหตุใดมันจึงไร้พลังต่อหน้าเจ้า?”
JAKK มิได้ตอบ แต่พลิกฝ่ามือเบา ๆ เส้นใยวารีที่ลอยอยู่กลางอากาศเริ่มขยับ เปลี่ยนเป็นรูปแบบใหม่ตลอดเวลา บางครั้งมันรวมกันเป็นหยดน้ำเดียว บางครั้งมันแตกออกเป็นเส้นสายมากมาย ไร้รูปแบบตายตัว
“แล้วเจ้าคิดว่าตนเองคืออะไร?” JAKK เอ่ยขึ้น
เอี้ยก้วยขมวดคิ้ว “ข้าเป็นข้า… เอี้ยก้วย”
JAKK ส่ายหน้า “หากเจ้ามีตัวตนเช่นนั้น เจ้าจะไม่มีวันเข้าใจวารี”
เอี้ยก้วยเม้มริมฝีปากแน่น นี่เป็นครั้งแรกที่เขารู้สึกว่าตัวเองถูกผลักให้ตกลงสู่ห้วงแห่งความเงียบ
เขาสูดลมหายใจเข้าลึก ก่อนจะค่อย ๆ หลับตาลง
สายฝนยังคงตกลงมา แต่บัดนี้ มันมิได้รู้สึกเหมือนดาบนับพันที่โหมกระหน่ำลงบนร่างของเขาอีกต่อไป
มันค่อย ๆ ซึมผ่านผิวหนัง คล้ายกับเขาเองก็เป็นส่วนหนึ่งของมัน
ปลายนิ้วของเขาขยับเพียงเล็กน้อย—และในวินาทีนั้น เขารู้สึกได้ถึงแรงสั่นสะเทือนบางอย่าง
เขาสัมผัสได้ถึงสายน้ำรอบตัว
แต่ก่อนที่เขาจะเข้าใจมันอย่างแท้จริง—
ฟึ่บ!
JAKK พลิกฝ่ามือเสี้ยววินาที เส้นใยวารีสะบัดวูบ ปลดปล่อยแรงกระแทกมหาศาล!
เอี้ยก้วยลืมตาขึ้น แต่คราวนี้ เขามิได้ต้านทานมัน
เขาเคลื่อนตัวไปกับมัน—
ร่างของเขาหลุดจากการจู่โจมได้อย่างฉิวเฉียด โดยที่มิได้ออกแรงฝืนเลยแม้แต่น้อย!

หยาดน้ำเย็นเฉียบโปรยปรายลงมาอย่างต่อเนื่อง สายลมพัดโหมรุนแรงพอจะถอนรากต้นไม้ แต่ภายในใจของเอี้ยก้วย กลับสงบนิ่งอย่างไม่เคยเป็นมาก่อน
เมื่อครู่... ร่างของเขาหลุดพ้นจากการจู่โจมของ "ใยวารี" โดยที่มิได้ต่อต้าน แต่มันไม่ใช่เพราะเขาเร็วขึ้น หรือแข็งแกร่งขึ้น
เขาเพียง ‘ปล่อยให้มันไหลไป’
ดวงตาของเขาเบิกกว้าง ความรู้สึกหนึ่งพลันแล่นผ่านจิตใจราวกับสายฟ้าที่ส่องลงบนมหาสมุทรอันมืดมิด
JAKK มองเขาอยู่ห่าง ๆ มุมปากของชายลึกลับผู้นี้ยกขึ้นเพียงเล็กน้อย แต่แฝงไว้ด้วยความพึงพอใจ
“เริ่มเข้าใจแล้วหรือไม่?”
เอี้ยก้วยกำกระบี่แน่น... แต่ครั้งนี้ มิใช่ด้วยความโกรธ มิใช่เพื่อจู่โจม มิใช่เพื่อพิสูจน์ตนเองต่อโชคชะตา แต่เพื่อสัมผัสถึงบางสิ่งที่เคยถูกซ่อนเร้นมาตลอดชีวิต
“ข้าเริ่มสัมผัสได้... แต่ข้ายังไม่เข้าใจ”
JAKK ยกมือขึ้น นิ้วชี้แตะกลางอากาศ—
ฟึ่บ!
หยดฝนที่โปรยปรายอยู่พลันรวมตัวกันกลางอากาศ หมุนวนเป็นเกลียว ก่อนจะยืดขยายออกเป็น กระบี่วารี—ใสกระจ่างประหนึ่งกระจก แต่มิใช่ของแข็ง มิใช่ของเหลว มันไร้ตัวตนและมีอยู่ในคราวเดียวกัน
“เจ้าจะต้องเรียนรู้ด้วยร่างกายของเจ้าเอง”
“มาเถิด เอี้ยก้วย”
เอี้ยก้วยมิใช่คนที่หวั่นเกรงต่อความท้าทาย เขาสูดลมหายใจเข้าลึก ก้าวขาขึ้นหน้าอย่างมั่นคง ดวงตาทอประกาย ครั้งนี้ เขาจะมิใช่ผู้ที่ปล่อยให้คลื่นซัดไปตามใจมันอีกต่อไป
เขาตวัดกระบี่ขึ้น—
ฟึ่บ!
JAKK เคลื่อนกาย กระบี่วารีของเขาโค้งงอ ปรับเปลี่ยนรูปทรงไปราวกับธารน้ำที่ไหลเวียน ไม่มีมุม ไม่มีองศา ไม่มีวิถีที่คาดเดาได้

เอี้ยก้วยตวัดกระบี่เข้าปะทะ—
เคร้ง!
ปลายกระบี่กระทบกัน แต่กลับมิได้มีเสียงกังวานของโลหะ กลับเป็นเสียงสายน้ำแตกกระจาย ก่อนจะรวมตัวกันใหม่ราวกับไม่เคยแปรเปลี่ยน
“กระบี่ของเจ้ามีขอบเขต” JAKK กล่าว “แต่วารี... ไร้ขอบเขต”
เอี้ยก้วยมิได้ตอบ แต่ร่างของเขาเริ่มเคลื่อนไหวช้าลง สายตามิได้จับจ้องไปที่กระบี่ของ JAKK อีกต่อไป แต่กลับมองไปที่ ‘กระแสน้ำ’ ที่กำลังไหลเวียนอยู่รอบตัวเขา
เขาต้องไม่ต่อสู้กับมัน แต่ต้องเป็นหนึ่งเดียวกับมัน
ร่างของเอี้ยก้วยเริ่มขยับไหลลื่นขึ้น ความแข็งแกร่งของกระบี่วิหคถูกหลอมรวมเข้ากับความอ่อนโยนของสายน้ำ ทุกก้าวย่างของเขาเบาหวิว ทุกกระบวนท่าที่ปล่อยออกไป ไม่มีจุดเริ่มต้นและไม่มีจุดจบ
JAKK มองดูการเปลี่ยนแปลงนั้นก่อนจะค่อย ๆ ลดกระบี่วารีลง
“เข้าใจแล้วหรือยัง?”
เอี้ยก้วยมิได้ตอบ เขาเพียงปล่อยให้หยาดฝนซึมผ่านร่างของตนเอง แต่ครั้งนี้ มิใช่เพราะมันตกลงมา แต่เพราะเขาเป็นส่วนหนึ่งของมัน
JAKK ยิ้มบาง ๆ ก่อนกล่าวทิ้งท้าย—
“เมื่อเจ้าเป็นวารี เจ้าจะไม่มีวันถูกทำลาย”

สิบหกปีต่อมา..
สายลมอ่อนพัดผ่านแมกไม้ เสียงน้ำไหลจากลำธารเล็ก ๆ ขับขานเป็นบทเพลงแห่งความสงบ ฟากฟ้าไร้เมฆฝน แสงอาทิตย์อ่อนจางทอดผ่านปลายใบไผ่ ดุจรอยยิ้มของสวรรค์หลังจากผ่านพายุอันเกรี้ยวกราดมาเนิ่นนาน
เอี้ยก้วยยืนอยู่บนโขดหินริมลำธาร มองสายน้ำที่ไหลผ่านราวกับไม่มีจุดสิ้นสุด ในแววตานั้นมีเพียงความสงบและลึกซึ้ง ร่างของเขายังคงองอาจเช่นวันวาน แต่สิ่งที่เปลี่ยนไปคือพลังอันเงียบสงบที่แผ่ซ่านอยู่รอบกาย มิใช่เพลิงแห่งโทสะ หากแต่เป็นสายธารที่ไหลลื่น ไม่มีสิ่งใดขวางกั้นได้
“เจ้ากำลังคิดอะไรอยู่?”
เสียงอ่อนโยนดังขึ้นเบื้องหลัง เซียวเหล่งนึ่ง ก้าวออกจากร่มเงาของต้นไม้ นางยังคงงดงามดังเดิม แม้กาลเวลาจะล่วงผ่าน ทว่าดวงตาของนางยังเปี่ยมไปด้วยความอ่อนโยน และรอยยิ้มที่มอบให้เอี้ยก้วยยังคงเป็นเช่นเดิม
เอี้ยก้วยหันมองนาง ก่อนยิ้มบาง ๆ แล้วทอดสายตากลับไปยังลำธาร “มีผู้หนึ่งเคยกล่าวกับข้า... วารีไม่เคยต่อต้านสิ่งใด แต่ไม่มีสิ่งใดทำลายมันได้”
เซียวเหล่งนึ่งขมวดคิ้วเล็กน้อย “ผู้ใด?”
เอี้ยก้วยนิ่งไปชั่วขณะ ก่อนตอบ “อาวุโสผู้หนึ่งนามว่า Jakk Goodday ไม่เพียงยอดฝีมือ แต่เป็นผู้ที่เข้าใจธรรมชาติแห่งทุกสรรพสิ่ง” เขายิ้มเล็กน้อย “เขาสอนข้าถึงพลังที่แท้จริงของวารี”
เซียวเหล่งนึ่งรับฟังเงียบ ๆ นางมองเขาด้วยแววตาที่เต็มไปด้วยความเข้าใจ
เขาหย่อนปลายนิ้วลงไปในน้ำเบื้องหน้า แหวนน้ำกระจายออกเป็นวง ทว่าไม่นานก็คืนสู่สภาพเดิม "แรงที่รุนแรงที่สุด ไม่ได้ทำให้ทุกอย่างแตกสลาย... แต่มันจะถูกดูดซับไปในที่สุด" เอี้ยก้วยพึมพำเบา ๆ
“เมื่อก่อน ข้ามักต่อต้านทุกสิ่ง” เอี้ยก้วยเอ่ยขึ้น แววตาสะท้อนถึงอดีตที่ผ่านมา “ข้าสู้กับโชคชะตา ข้าท้าทายทุกสิ่งที่ขัดขวางข้า ไม่ว่าจะเป็นสวรรค์หรือมนุษย์”
 เอี้ยก้วยหลับตาลง สายลมพัดผ่านร่างของเขาเย็นเยียบ ก่อนจะเปิดตาขึ้นช้า ๆ
"เมื่อก่อนข้าต้านทานทุกสิ่ง แต่บางครั้ง... ทางที่มั่นคงที่สุด อาจเป็นทางที่ไม่มีเส้นทางเลย" เขาเอ่ยเสียงเบา คล้ายกล่าวกับตนเองมากกว่านาง
เอี้ยก้วยหลับตาลง สายลมพัดผ่านร่างของเขาเย็นเยียบ ก่อนจะเปิดตาขึ้นช้า ๆ
"เมื่อก่อนข้าต้านทานทุกสิ่ง แต่บางครั้ง... ทางที่มั่นคงที่สุด อาจเป็นทางที่ไม่มีเส้นทางเลย" เขาเอ่ยเสียงเบา คล้ายกล่าวกับตนเองมากกว่านางเซียวเหล่งนึ่งก้าวเข้าไปใกล้ มองสบตาเขานิ่ง ๆ "แล้วตอนนี้ เจ้าจะไหลไปตามกระแสน้ำ... หรือเจ้ายังต้องการกระบี่ของเจ้าอยู่?"
“น้ำไม่เคยฝืนตัวมันเอง มันไม่แข็งกร้าว แต่มันชนะทุกสิ่ง ไม่ว่าจะเป็นหินแข็งหรือเหล็กกล้า” เขายื่นมือแตะผิวน้ำเบา ๆ “กระบี่ของข้าเคยเป็นดังเปลวไฟที่เผาผลาญทุกสิ่ง แต่ตอนนี้... มันเป็นสายธารที่ไหลไปตามใจของมัน”
เซียวเหล่งนึ่งก้าวเข้ามาใกล้ แสงอาทิตย์ส่องต้องนางราวกับนางเป็นภาพฝัน “ข้าดีใจที่เจ้ากลับมา... และข้าดีใจที่เจ้าพบสิ่งที่เจ้าตามหามาตลอด”
เอี้ยก้วยหันกลับมาสบตานาง แววตาของเขาอ่อนโยน "ข้ารู้แล้วว่า การรอคอยที่แท้จริง... มิใช่เพียงรอคอยเจ้า แต่เป็นรอคอยวันที่ข้าจะเข้าใจตัวข้าเอง"
เซียวเหล่งนึ่งยิ้ม “และตอนนี้ เจ้าเข้าใจแล้วหรือไม่?”
เอี้ยก้วยพยักหน้า “ข้าเข้าใจแล้ว” เขากุมมือนางเบา ๆ “รักที่แท้จริงมิใช่พันธนาการ มันเป็นดั่งสายน้ำ ไม่ต้องไขว่คว้า ไม่ต้องครอบครอง แต่ไหลไปตามทางของมันเอง”
เซียวเหล่งนึ่งเงยหน้าขึ้นสบตาเขา นางไม่ต้องการคำพูดใดอีก เพราะทุกสิ่งอยู่ในดวงตาของเขาแล้ว
สายลมพัดผ่านเบา ๆ ลำธารยังคงไหลไปข้างหน้า ไม่มีสิ่งใดหยุดยั้งมันได้ เช่นเดียวกับเวลาที่เคลื่อนผ่าน และความรักที่ไม่มีวันจืดจาง
และในที่สุด... เอี้ยก้วยก็ได้กลายเป็นดั่งสายน้ำ ที่ไม่มีวันถูกทำลาย

-
 @ 5b705e6c:25c1efe5
2025-03-06 11:41:19
@ 5b705e6c:25c1efe5
2025-03-06 11:41:19Trying out comet!
-
 @ 8947a945:9bfcf626
2025-03-06 10:50:28
@ 8947a945:9bfcf626
2025-03-06 10:50:28Law of diminishing returns : ทำมากได้น้อย ซวยหน่อยขาดทุน
 ** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับ
** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับผมได้ยิน คุณท็อป จิรายุส (คุณท๊อป บิทคับ) พูดคำว่า "Law of diminishing returns" ไว้ตอนแชร์มุมมองด้านการทำธุรกิจ ตอนนั้นผมไม่เข้าใจ แต่ผมรู้สึกว่ามันเป็นเจ๋งดี
สำหรับผม สรุปกฏนี้สั้นๆ คือ “ทำมากได้น้อย ซวยหน่อยขาดทุน”
กฏข้อนี้ว่าด้วยเรื่องการทำธุรกิจ พูดถึงปัจจัย 3 อย่าง - Fixed input คือสิ่งที่ไม่สามารถผลิตเพิ่มได้อีกในธุรกิจตอนนั้น เช่น จำนวนห้องตรวจในโรงพยาบาล, พื้นที่ที่ดินทำการเกษตร, ห้องเก็บสินค้า, จำนวนโต๊ะทำงานในสำนักงาน, ช่องบริการลูกค้าในธุรกิจบริการต่างๆ เป็นต้น ผมขอเรียกสั้นๆว่า “พื้นที่” - Variable input คือสิ่งที่สามารถเติมเข้ามาในธุรกิจได้ ปรับแต่งได้ เช่น แรงงาน เครื่องจักร พลังงาน - Marginal product คือผลลัพธ์ของธุรกิจ กำไรเพิ่มขึ้นหลังจากเพิ่ม variable input เข้าสู่ระบบ
ระยะของ law of diminishing returns
- Increased return (ทำเงินได้เยอะขึ้น) เมื่อป้อนแรงงานหรือเครื่องจักรเข้าสู่ระบบ ธุรกิจสามารถทำเงินเพิ่มขึ้นเนื่องจาก fixed input เดิมที่ถูกใช้สอยไม่เต็มที่ (underutilized) ถูกเติมเต็ม กรณีของรพ. คือมีห้องตรวจที่ว่าง ไม่มีหมอนั่งตรวจคนไข้ ห้องตรวจนั้นก็จะไม่สร้างรายได้ แต่เมื่อห้องนั้นมีหมอมานั่ง จะเปลี่ยนเป็นพื้นที่ที่ก่อให้เกิดรายได้ เมื่อห้องตรวจทุกห้องมีหมอนั่งครบ ถือว่าเต็มศักยภาพ ประสิทธิภาพการทำงานที่ดีตามมา
- Diminishing return (ทำมากได้น้อย) จุดของความพอดี (optimum point) คือจุดที่สมดุลพอดีของธุรกิจนั้น ทำกำไรได้เหมาะสม ไม่มากไม่น้อยจนเกินไป แต่ถ้ามองไม่เห็นจุด optimum นี้แล้วยังเพิ่ม”แรงงาน”เข้าไปอีก มันจะทำให้ ”พื้นที่” วุ่นวายเละเทะ ประสิทธิภาพในการทำงานลดลง
- Negative returns (ซวยหน่อยขาดทุน) ถ้ายังไม่หยุดเพิ่ม “แรงงาน” อีก สามารถนำมาสู่การขาดทุน
สรุปเป็นกราฟหน้าตาตามนี้ครับ
ทำไมมันถึงเป็นอย่างนั้น
ผมใช้โมเดลธุรกิจรพ.นี้เป็นตัวอย่างเลยนะครับ
ช่วงแรกที่สร้างรพ. ห้องตรวจมีไม่มาก จำนวนหมอและคนไข้สมดุลกันพอดี งานไม่หนักเกินไป การดูแลคนไข้มีประสิทธิภาพ รพ.เป็นที่ไว้ใจของคนในพื้นที่ มีชื่อเสียง ถูกบอกต่อ ทำให้จำนวนคนไข้เข้ามารับบริการมากขึ้น ต้องขยายพื้นที่รพ. สร้างตึกเพิ่ม รับบุคคลากรทุกระดับเข้ามาทำงานมากขึ้น จนเต็มพื้นที่ที่ดินรพ.ไม่สามารถขยายเพิ่มไปได้มากกว่านี้แล้ว เกิดสมดุลพอดี ทุกพื้นที่ถูกใช้งานเต็มศักยภาพ ประสิทธิภาพงานดีมาก

ผลการดำเนินงาน
ไม่เคยขาดทุน ผ่านช่วงวิกฤตต้มยำกุ้ง และ COVID ได้สบายๆ ฐานะทางการเงินแข็งแรง จ่ายปันผลสม่ำเสมอ ถ้าผมเป็นเจ้าของรพ.ผมจะ 1. สร้างระบบ 2. สร้างทีมผู้บริหาร 3. เน้นย้ำความสำคัญทำตามระบบ 3. Plan - Do- Check - Act เมื่อเกิดปัญหา
เพื่อให้ตัวผมสามารถถอยตัวเองออกมาจากตัวธุรกิจ คอยติดตาม monitor ทุกไตรมาส อย่างใกล้ชิด ไม่ทำอะไรเพิ่มไปมากกว่านี้
แต่สุดท้ายมันก็เกิดเหตุการณ์ทายาทรุ่นที่ 2 “ไม่เอา” นั่นแหละครับ มันทำให้วัฒนธรรมองค์กรเปลี่ยน ก้าวเท้าเข้าไปสู่ยุคตกต่ำ

บริหารแบบล้าหลัง ทำอะไรไม่สุด คิดว่าทำแล้วแต่จริงๆคือไม่ได้ทำ แก้ปัญหาไม่ตรงจุดสร้างปัญหากว่าเดิม
ตัวอย่าง
1. นโยบายการประหยัดพลังงานเพื่อลด carbon footprint
ฟังดูเหมือนจะดี แต่รพ.สื่อสารให้
รณรงค์ให้ปิดไฟ ... ปิดแอร์เมื่อไม่ใช้งาน ...
ผมว่าประโยคนี้มันคุ้นๆ เหมือนเคยได้ยินมามากกว่า 10 ปีแล้ว ... หรือผมเข้าใจผิดหรือเปล่าไม่แน่ใจ
รณรงค์แค่นี้แหละครับ เรื่องลด carbon footprint ไม่ได้เป็นการคิดอะไรใหม่ๆที่เหมาะกับยุคสมัย หรือสร้างอะไรที่จับต้องได้ (objective)
แต่สิ่งที่ทำสวนทางโดยสิ้นเชิงคือใช้พลาสติกแบบใช้แล้วทิ้ง (single use plastic) เป็นภาชนะหลักในการบรรจุอาหารของแพทย์ และผู้เข้าร่วมประชุมงานใหญ่ๆ
 มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ
มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ2. การตลาดที่ล้มเหลวและพาแพทย์ซวย

ทำการตลาดไม่เข้าเป้า “เหมือนจะ” ทำ digital marketing แต่ทำแค่โพสกราฟฟิคโปรโมชั่นภาพนิ่งลงสื่อโซเชียลทุกช่องทาง แล้วบอกว่านั่นคือ digital marketing
... แต่เดี๋ยวก่อนๆๆๆ ...
ผมจะบอกว่าการโพสมันเป็นแค่ 1 ใน 10 ของ digital marketing แต่รพ.เข้าใจว่าตัวเองได้เข้าสู่ digital marketing แล้ว
... จริงๆมันไม่ใช่เลยเว้ย ...
ผลลัพธ์คือไม่สามารถเปิดน่านน้ำลูกค้าใหม่ได้เลย ได้แต่ฐานลูกค้าเดิมที่มี brand royalty (แต่แนวโน้มลดลง)
แถมที่แย่ที่สุดคือทำการตลาดแพคเกจออกมาโดยไม่ปรึกษาแพทย์ก่อนว่ามันขัดต่อมาตรฐานการรักษาหรือไม่ กลายเป็นทำแพคเกจดึงดูดคนไข้เข้ามาใช้บริการ แต่การรักษาในแพคเกจขัดต่อมาตรฐานการรักษาของแพทย์
คนไข้ไม่รู้หรอกครับ คนไข้จะเอาตามที่มีในแพคเกจ เขาจ่ายตังค์แล้ว แต่ความซวยมันไปตกอยู่กับแพทย์
3. วางกลยุทธไม่เข้าเป้า

ทุกๆต้นปีทางผู้บริหารจะประกาศกลยุทธประจำปี ว่าในปีนั้นๆรพ.จะมุ้งเน้นพัฒนาด้านไหน รพ.นี้มีปัญหาที่เป็นงูกินหางมานาน มันส่งผลต่อประสิทธิภาพการทำงานของหมอและพยาบาล มีการเสนอแก้ปัญหาเรื่องนี้วนซ้ำซากมา 5 ปี แต่ไม่ได้รับแก้ไขจริงจัง (ผมขอไม่เล่านะครับ)
แต่กลยุทธประจำปี 3 ปีที่ผ่านมา พุ่งใส่ตัวบุคคลากร เน้นพฤติกรรมบริการที่ดีเลิศ ทราบมาว่ามีการลงทุนกับโครงการนี้หลักแสนหรือหลักล้าน มีการจัด workshop เชิญวิทยากรและ trainer จากบริษัทภายนอก (outsource) เข้ามาอบรม เป็นโครงการที่เน้นให้บุคคลากรทุกคนเข้าอบรม 100%
ผมมองว่าปัญหาที่เป็นราก (root cause) มันยังไม่ถูกแก้เลย เปรียบเทียบเหมือนฐานรากของอาคารที่มันโคลงเคลงๆไม่มั่นคงยังไม่ได้รับการแก้ไข แต่พยายามตกแต่งห้องด้วยวัสดุคุณภาพดีและเทคโนโลยีที่ทันสมัย … แต่พร้อมจะล้มลงมาได้ทุกเมื่อ
4. มีเสน่ดึงดูด partner ใหม่ๆ แต่ไม่เอาเอง
ในช่วง COVID ระลอกแรก มีผู้นำทางด้านธุรกิจโรงแรมในจังหวัดมานำเสนอโมเดลธุรกิจ “hospitel เปลี่ยนโรงแรมให้เป็นโรงพยาบาล” ด้วยศักยภาพของรพ.ที่มีบุคคลากรเพียงพอ และตัวโรงแรมที่นำมาเสนอมีห้องพักประมาณ 300 ห้อง เป็นโมเดลที่รพ.และโรงแรม win-win ทั้งคู่ แต่ทางผู้บริหารมองว่าไม่คุ้ม ปฏิเสธข้อเสนอนี้ ทำให้เสียโอกาสให้กับคู่แข่งคว้าตลาด blue ocean นี้ไป

ผมได้แต่เกาหัวตอนรู้เรื่องนี้ เพราะ 1. ช่วง COVID คนไข้น้อย พนักงานโดนลดชั่วโมงการทำงาน ได้เงินเดือนขั้นต่ำ ไม่ได้ OT 2. ทาง partner เสนอขอบุคคลากรเหล่านี้แหละ ไปช่วยงาน เรื่องสถานที่ทางโรงแรมเขามีแม่บ้าน ฝ่ายทำความสะอาดอยู่แล้ว 3. ทาง partner เสนอ profit sharing กับทางรพ. ถึงผมจะไม่รู้ตัวเลข แต่เชื่อว่ามันยุติธรรม
ผมก็ไม่รู้ครับ ว่าอะไรคือคุ้มสำหรับผู้บริหาร
5. Top down absolute power
ไม่ฟังข้อเสนอจากตัวแทนหมอ คนที่มีอำนาจการตัดสินใจไม่เคยเอาตัวลงมาคุยกับหมอแบบจริงจังเลย
1-2 ปีจะลงมาพบหมอทั้งรพ.ซักหนึ่งครั้ง สร้างภาพเก่ง พูดขายฝันสวนหรูถึงภาพที่เขาต้องการ สั่งการลงมา พอเกิดปัญหาตัวเองไม่ลงมารับผิดชอบ แต่อาศัยหน่วยข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ออกคำสั่งแก้ผ้าเอาหน้ารอดลงมาทีหลัง
แถมสั่งให้เงียบและหุบปาก
ครั้งหนึ่งมีคำสั่งออกมาไม่ชัดเจน จนพยาบาลทำงานไม่ได้ ตัวแทนพยาบาลต้องโทรมาหาผมเพื่อให้ผมช่วย
ผมรวบรวมข้อมูลทั้งหมดและพบว่าคำสั่งมีปัญหาจริงๆ ผมจึง chat line ลงไปสอบถามผู้บริหารเพื่อขอความชัดเจน
… ผ่านไปไม่ถึง 5 นาที หนึ่งในผู้บริหาร(คนที่แทงข้างหลังผมที่หาว่าผมมาตรวจคนไข้ VIP เขาช้า 5 นาทีนั่นแหละ)โทรหาผมทันทีคุยกับผมสั้นๆ ใจความว่า “คำสั่งนั้นเอาแบบเดิม ไม่ต้องแก้ และให้ผมเงียบๆซะ”... (ก็ได้วะครับ)

จุดเปลี่ยนที่ทำให้รพ.เข้าสู่ law of diminishing returns
ห้องตรวจทุกห้องของรพ. ถูกใช้จนเต็มศักยภาพ … เอาจริงๆคือล้นศักยภาพเสียอีก (over-utilized) บางแผนกมีเก้าอี้ดนตรี - หมอคนแรกหมดเวลาออกตรวจ - หมอคนต่อไปเดินเข้าใช้ห้องตรวจต่อทันที - ถ้าไม่ทันก็ต้องคว้าห้องตรวจที่ว่างพร้อมใช้งานก่อน - หมอทำการไล่ที่กันเอง - หมอบางท่านต้องใช้ห้องทำงานของพยาบาลเป็นห้องตรวจชั่วคราว
ห้องพักผู้ป่วยก็เช่นกัน บางช่วงเตียงเต็มจนไม่สามารถ admit คนไข้ได้
แต่จำที่ผมบอกได้มั้ยครับว่า คนที่เป็น top down absolute power ไม่เคยเอาตัวลงมาพูดคุยกับแพทย์เพื่อรับฟังปัญหาที่แท้จริงเลย รับแต่ข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ช่วงนึงมีคนไข้ complaint ว่ารอนั่งรอหมอนาน หมอมาตรวจช้า ผู้บริหารเลยพยายามจะแก้ปัญหา โดยการ monitor waiting time (ระยะเวลารอหมอ) หยิบยกเรื่องนี้ขึ้นมาเป็นวาระเร่งด่วนต้องรีบแก้ไข
แต่เขายังงงๆกับ concept waiting time อยู่เลยว่าจะนับตั้งแต่ตอนไหนถึงตอนไหน - Waiting time สั้นแปลว่าดี เพราะคนไข้ได้เจอหมอเร็ว - Waiting time นานแปลว่าไม่ดี เพราะคนไข้นั่งรอหมอนาน
เขาตีความจากตัวเลขครับ แต่เคยเอาตัวลงมาดูจริงๆหรือเปล่าว่าทำไมตัวเลขมันถึงออกมาไม่ดี
คำตอบคือ“ไม่” ครับ
หมอบางสาขามีความจำเป็นต้องไปดูคนไข้ที่อาการหนักใช้เวลารักษานาน ... หรือ ... รับปรึกษาจากแพทย์ต่างสาขา ... หรือ ... เป็นสาขาเฉพาะทางของเฉพาะทางอีกที ต้องใช้เวลาตรวจละเอียดตรวจนาน
มันเป็นกระบวนการทำงานของหมอ ที่หมอด้วยกันเข้าใจกัน
ส่วนคนเก็บข้อมูลก็นำเสนอไปทั้งอย่างนั้นโดยที่ไม่ได้วิเคราะห์อะไรเลย มันเป็นการกรองข้อมูลที่ไม่รอบคอบก่อนนำเสนอผู้บริหาร
สุดท้ายผู้บริหาร “โทษหมอ” ว่าไม่มีการบริหารเวลาทำงานที่ดีเพียงพอ ทำให้คนไข้รอนาน เขาสรุปกันดื้อๆแบบนี้เลยครับ
พอหนักๆเข้า “รอหมอนาน ต้องเพิ่มหมอ” season การรับสมัครหมอหลายตำแหน่งได้เริ่มขึ้น
แต่เดี๋ยวนะ ห้องตรวจมันแน่นจนแทบไม่มีที่ให้หมอนั่งทำงานแล้ว แต่เขาก็ไม่สนครับ รับหมอหน้าใหม่ๆมาเพิ่มเรื่อยๆ
ด้วย mindset ว่า "ต้องเพิ่มหมอ หมอจะได้เยอะขึ้น คนไข้จะได้ไม่ต้องรอนาน" และเชื่อว่าจะทำรายได้ให้รพ.มากขึ้น หมอหน้าใหม่บางท่านเข้ามาทำงานวันแรกถึงขั้นอยู่ในสภาวะ dead air คือไม่มีที่ให้นั่งทำงาน
“ทำมากได้น้อย” เริ่มต้น
คนไข้รพ.นี้ ส่วนใหญ่เป็นโรคซับซ้อน ต้องการทักษะและเวลาหมอเฉพาะทางแต่ละสาขาอยู่ดี ไม่ได้ทำให้ waiting time ดีขึ้น คนไข้ยัง “นั่งรอหมอนานเหมือนเดิม”
รายได้เริ่มลดลง ยอดคนไข้เริ่มลดลง รพ.พยายามแก้เกมโดยการเพิ่มราคาค่าบริการ (เพิ่มขนาด ticket size) ทำให้มีเสียงรีวิวตามโซเชียลว่า "แพง"
ผลที่เกิดขึ้นคือคนไข้หลายคนอาศัยรพ.นี้ในการตรวจวินิจฉัยโรคแล้วเอาผลไปรักษาต่อรพ.รัฐบาลตามสิทธิ์เพราะสู้ราคาค่ารักษาไม่ไหว บางคนมีประกันสุขภาพหลายฉบับแต่ก็ต้องจ่ายส่วนต่างมากอยู่ดี

วิธีการข้างต้นนี้ ไม่ผิดกติกาครับ ผล X-ray , CT, MRI, ultrasound จากรพ.เอกชน ไวกว่ารพ.รัฐบาลอยู่แล้ว แต่ก็มีคนไข้บางส่วนยินดีจ่ายแพง เพราะเชื่อมั่นหมอที่รพ.นี้ไม่อยากย้ายรพ.ก็มีครับ เพราะหมอไม่ได้ทำอะไรผิด หมอเก่งๆมีเยอะ
ถึงแม้ว่ารพ.จะรักษา momentum มีจำนวนคนไข้ประมาณ 1100 - 1200 รายต่อวัน แต่ก็เป็นโรคง่ายๆ(simple disease) เช่นไข้หวัด อาหารเป็นพิษ เป็นต้น โรคเหล่านี้ ticket size ไม่ได้ใหญ่มาก ประคองไว้ไม่ให้ขาดทุนเท่านั้นครับ
แต่ความแพงแบบไม่สมเหตุสมผล ทำให้คนไข้หลายรายถอดใจย้ายรพ.ตั้งแต่ทราบค่าใช้จ่ายวินาทีแรก
คนไข้น้อยลง --> รายได้ลดลง --> เพิ่ม ticket size ต่อหัวให้แพงขึ้น --> คนไข้หนีเพราะแพงเกิน
ผมไม่รู้ว่าผู้บริหารเขาเห็นไหม แต่คาดว่าคงจะไม่เห็น
ส่วนโรคหรือการผ่าตัดที่สมศักดิ์ศรีกับศักยภาพของรพ. "น้อยมากจนแทบไม่มี" ไม่ใช่สาเหตุอื่นเลยครับ โดนรพ.คู่แข่งในรัศมี 20 กิโลเมตรเอาไปหมด เพราะราคาถูกกว่า หมอก็เก่งไม่แพ้กัน หมอบางคนเคยอยู่ที่รพ.แห่งนี้ เสนอโปรเจคการรักษาโรคบางโรคที่สามารถสร้างรายได้เป็นกอบเป็นกำ แต่ทางรพ.ไม่เอาเอง สุดท้ายหมอเหล่านั้นย้ายไปอยู่กับรพ.คู่แข่งและผลักดันโปรเจคเหล่านั้นสำเร็จจนมีชื่อเสียง
"รพ.ขายสินค้า premium ไม่ได้เลย ขายได้แต่สินค้าเกรดท้องตลาด"
กลยุทธที่รพ.ทำต่อมาคือเพิ่มจำนวนชั่วโมงการทำงานของหมอให้เพิ่มขึ้นโดยให้หมอมาทำงานเร็วขึ้น 2 ชม. แต่ไม่จ่าย OT ให้ ด้วยตรรกะว่าถ้าหมอทำงานนานขึ้น จะมีจำนวนคนไข้มากขึ้น ทางรพ.ไม่ได้ขอร้อง แต่บีบคอให้หมอร่วมมือ หากไม่ร่วมมือไล่ออกทันที

ไปๆมาๆ มีการไล่ออกกระทันหันเกิดขึ้น มีการส่งหนังสือส่วนตัวหาหมอทุกคน ใครมีรายชื่อที่จะปลดออกก็ต้องออกจากงานทันที
ผมมองว่าฐานะทางการเงินมีปัญหารุนแรงครับ เงินเดือนพนักงานถือเป็น fixed cost ที่ธุรกิจต้องแบกรับ ถ้าเจ๋งจริงต้องควบคุมรายจ่ายให้ธุรกิจสามารถไปต่อได้โดยไม่ปลดคน ในส่วนของธุรกิจรพ. หมอคือบุคคลากรที่สำคัญที่สุดและเป็นด่านสุดท้ายที่จะไล่ออกเพื่อรักษาชีวิตของธุรกิจ ตอนนี้รพ.ได้เข้าสู่ระยะสุดท้ายของ law of diminishing returns คือ “ซวยหน่อยขาดทุน” เป็นที่เรียบร้อยครับ
จุดจบของรพ.แบบนี้ ที่ศักยภาพดี แต่บริหารห่วยแตก มันจะจบด้วยการถูก take over ผ่านมาไม่นานกราฟหุ้นออกอาการ exit liquidity แล้วครับ
ข้อคิดที่อยากแบ่งปันกับทุกคนที่อ่านมาจนจบ
- ช่วงธุรกิจเปลี่ยนผ่านสู่ทายาท คือจุดวัดใจหัวเลี้ยวหัวต่อว่าจะรอดหรือไม่รอด
- Law of diminishing returns ไม่ได้ใช้เฉพาะกับธุรกิจ แต่สามารถประยุกต์ใช้กับการดำเนินชีวิตได้หลายมิติ หากใครเข้าใจ จะขยับเข้าสู่ Pareto’s rule … สั้นๆคือ ทำน้อยแต่ได้(โคตร)มาก
- เจ้าของธุรกิจ ต้องหูไว มองหาเนื้อร้ายที่คอยกัดกินธุรกิจให้เจอ แล้วกำจัดมันซะ ก่อนที่ธุรกิจจะล้มทั้งยืน ทับตัวเองตาย
-
 @ 3492dd43:1af4ffdd
2025-03-06 09:39:22
@ 3492dd43:1af4ffdd
2025-03-06 09:39:22Testing comet.md
the idea of writing locally is a great. Why would i need to be connected to the internet to login to a server somewhere in order to write. Upon reflection, that seems highly regarded.
This basically has the feel of a combination of an rss reader and the apple notes app. Include email intergration and also subscribing and reading, and this will be a game changer
-
 @ a012dc82:6458a70d
2025-03-06 08:28:23
@ a012dc82:6458a70d
2025-03-06 08:28:23In a groundbreaking move that could significantly alter the investment landscape, Harvest Fund Management, a prominent Chinese asset manager, has boldly stepped forward with an application for a spot Bitcoin exchange-traded fund (ETF) in Hong Kong. This initiative is not just a leap towards diversifying investment options but also a testament to the evolving acceptance and integration of digital assets into the mainstream financial ecosystem.
Table of Contents
-
Introduction to Spot Bitcoin ETFs
-
Harvest Fund's Strategic Move
-
The Significance for Hong Kong
-
Regulatory Landscape and Stablecoin Interest
-
The Road Ahead
-
Conclusion
-
FAQs
Introduction to Spot Bitcoin ETFs
Spot Bitcoin ETFs represent a bridge between the traditional financial world and the burgeoning realm of cryptocurrencies. By mirroring the current market price of Bitcoin, these ETFs offer investors a straightforward path to participate in the cryptocurrency market without the direct ownership of Bitcoin. This eliminates the need for investors to engage with cryptocurrency exchanges or secure digital wallets, thereby lowering the entry barriers to the Bitcoin market. The significance of spot Bitcoin ETFs extends beyond convenience; they are a symbol of the growing legitimization of cryptocurrencies as a viable asset class. By being listed on conventional stock exchanges, these ETFs are subjected to regulatory scrutiny and standards, offering a layer of security and transparency that is sometimes questioned in the crypto space. This development could potentially attract a new wave of institutional and retail investors, who have been on the sidelines due to concerns over regulatory clarity and the technical challenges associated with cryptocurrency investments.
Harvest Fund's Strategic Move
Harvest Fund Management's application for a spot Bitcoin ETF is a calculated strategic move, positioning the firm at the forefront of financial innovation in Hong Kong. By aiming to launch the city's first such ETF, Harvest Fund is not merely expanding its product lineup but is also contributing to the legitimization and institutionalization of Bitcoin as an investable asset. This pioneering effort reflects a deep understanding of market dynamics and a vision for the future of investment, where digital and traditional assets coexist within regulated frameworks. The initiative by Harvest Fund could catalyze a shift in investor sentiment, encouraging more conservative players to consider the potential of Bitcoin and other cryptocurrencies. Furthermore, it sets a benchmark for product innovation and regulatory compliance, potentially influencing the pace and direction of cryptocurrency adoption across the financial sector. As the first mover, Harvest Fund could enjoy a competitive advantage, capturing significant market share among investors eager to explore digital assets within a regulated environment.
The Significance for Hong Kong
Hong Kong's financial landscape is on the cusp of transformation, with Harvest Fund's application signaling a broader trend towards the acceptance of digital assets. This move comes at a pivotal moment, as Hong Kong seeks to assert itself as a global hub for cryptocurrency and blockchain technology. The interest from approximately 10 fund companies in launching their own spot crypto ETFs underscores the city's potential to lead in the virtual asset space. This collective momentum could significantly enhance Hong Kong's attractiveness as a financial center, drawing in global investors looking for regulated avenues into the cryptocurrency market. The introduction of spot Bitcoin ETFs would not only diversify the city's financial products but also reinforce its reputation as a jurisdiction that balances innovation with investor protection. By providing a structured and regulated framework for cryptocurrency investments, Hong Kong can set a global standard for how financial centers can adapt to the evolving landscape of digital assets. This development is a key step in the broader journey towards integrating cryptocurrencies into the global financial system, with Hong Kong leading the way.
Regulatory Landscape and Stablecoin Interest
The enthusiasm for spot Bitcoin ETFs in Hong Kong is paralleled by an equally significant interest in stablecoins, indicating a comprehensive approach to cryptocurrency regulation and adoption. The discussions between the HKMA and various companies about stablecoin trials reflect a proactive stance towards understanding and integrating digital currencies in a way that supports financial stability and innovation. This balanced approach is crucial, as stablecoins represent a bridge between traditional fiat currencies and cryptocurrencies, offering the potential for more efficient payment systems and financial services. The regulatory efforts around stablecoins, coupled with the move towards spot Bitcoin ETFs, show Hong Kong's commitment to creating a robust framework for digital assets. This not only enhances the city's competitive edge as a financial hub but also provides a blueprint for other jurisdictions navigating the complexities of cryptocurrency regulation. By leading in both areas, Hong Kong is positioning itself at the forefront of financial innovation, setting the stage for a future where digital and traditional finance converge seamlessly.
The Road Ahead
The initiative by Harvest Fund Management to launch a spot Bitcoin ETF in Hong Kong marks the beginning of a new era in cryptocurrency investment. This move is more than just an expansion of the financial products available to investors; it is a signal of the maturing relationship between the cryptocurrency industry and the broader financial community. As regulatory frameworks continue to evolve and more players enter the market, the landscape for cryptocurrency investment is set to undergo significant changes. Hong Kong's role in this transition cannot be understated. By fostering an environment that encourages innovation while ensuring investor protection, the city is not just adapting to the rise of digital assets but is actively shaping the future of finance. The success of Harvest Fund's application and the subsequent launch of the city's first spot Bitcoin ETF could serve as a catalyst for other financial centers to follow suit, potentially leading to a global shift in how cryptocurrencies are perceived and utilized within the investment world.
Conclusion
Harvest Fund Management's bold step towards launching a spot Bitcoin ETF in Hong Kong is a landmark moment in the integration of digital assets into mainstream finance. This initiative not only opens up new avenues for investment but also underscores Hong Kong's ambition to be at the forefront of financial innovation. As the regulatory landscape evolves and the market for digital assets continues to grow, the efforts of Harvest Fund and like-minded institutions will be crucial in bridging the gap between traditional finance and the digital asset world. The path ahead is promising, and Hong Kong's leadership in this space could pave the way for a new chapter in the global financial narrative, where digital and traditional assets coexist in a regulated, dynamic, and inclusive investment ecosystem.
FAQs
Who has filed for the first spot Bitcoin ETF in Hong Kong? Harvest Fund Management, a major Chinese asset manager, has filed an application for the first spot Bitcoin ETF in Hong Kong with the Securities and Futures Commission (SFC).
Why is a spot Bitcoin ETF significant for investors? A spot Bitcoin ETF provides a regulated, accessible, and potentially less risky way for investors to gain exposure to Bitcoin's price movements without dealing with the complexities of cryptocurrency exchanges, digital wallets, and private keys.
How does a spot Bitcoin ETF work? A spot Bitcoin ETF buys and holds actual Bitcoin, and the value of the ETF shares fluctuates with the real-time price of Bitcoin. Investors can buy and sell these shares through traditional stock exchanges.
What are the benefits of investing in a spot Bitcoin ETF? Investing in a spot Bitcoin ETF offers the benefits of trading and owning a stock, including regulatory protection, ease of access, and liquidity, while also providing exposure to Bitcoin's price.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32
@ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32It's been barely two years since I joined Nostr on my main npub, nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and in just that relatively short time, the amount of development on top of this protocol has been staggering. When nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m first opened the floodgates of adoption by tweeting about Nostr, it felt like most of the available clients were barely serviceable and held together with a prayer and copious amounts of duct tape. Of course, it can sometimes still feel that way, but there are definitely some Nostr apps looking and feeling more polished and providing true innovation when compared with legacy social platforms. Indeed, there are a growing number of Nostr-based applications and tools that have very little to do with social media at all.
One thing we have not had available to the growing Nostr community, and those considering joining it, is a source for application reviews that is thorough, approachable, knowledgeable, and balanced. This is what I hope to begin to provide through this new npub dedicated to reviewing as many of the Nostr clients, apps, and tools as I possibly can, so you the reader can determine which ones will fit your needs, and perhaps help you find new ones you had never heard about.
One of the best parts about Nostr is the portability of your identity and social graph, allowing users to log into any Nostr-based application with their same "account" without some centralized tech giant like Google or Apple owning who you are and all of your data. Leverage this super-power of Nostr with me as we explore the best applications and tools the intrepid developers building on this platform have cooked up.
What will you review?
My choice of applications to review will be based on a few factors.
First, I will only be reviewing applications that have a production release, or are otherwise considered production ready by the developer. nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s, you won't have to worry that I will be putting NoteDeck under the microscope while it is still very much in alpha. All of us who love to try the new clients as soon as they are available understand well enough that there will be plenty of bugs, UI quirks, and rough edges to look past.
Second, I will generally be reviewing applications that are meant to be user-facing for the average person. That is, apps that your normie friends might soon be using, and then asking you why they can't edit anything they post. I will not be doing reviews of various relay implementations, for instance, unless they are designed to be approachable to the average user to install and manage. nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h, your project might just be a notable exception.
Third, my reviews will be limited by the operating systems I have available to me at the time. Sorry folks over on iOS, Mac, and Windows. I will only be able to review apps I can run on Android, Linux, or my web browser for the time being.
How will the apps be rated?
I want to be thorough in my reviews, and yet avoid overloading my readers with information they don't care about. In order to attempt to achieve this, I will break my reviews into several sections, so readers can skip to the sections relevant to their interests.
First, I will provide a basic overview of the type of application I am reviewing, what it is trying to achieve, and why a user might want to try it out.
Next, I will give my overall impression of the application. The good, the bad, and the ugly, as it were, so that those who just want a brief rundown can get the TLDR right out the gate and be on their way.
Then we will begin diving into the nitty-gritty with an in depth look at the main features of the application. What it does well. What features seem lacking. What expected features are absent. What features make it unique and set it apart from other applications with a similar purpose.
For the sake of all the baby Nostriches out there, the next section will be an assessment of how approachable the application would likely be to a normie who is coming to Nostr with no idea what a public and private key are, what relays are, or why they might want to start interacting here instead of on a legacy equivalent. What would someone used to Twitter think of #Snort? What would someone used to Spotify think of #Fountain or #Wavlake?
The next section will be a review of the application's UI. The design and polish. How easy it is to find the things you want in the areas you would expect them. In short, how well the application achieves the goal of making the user feel at home and want to continue using the app just through quality UI design.
If you know me and my contstant harping on developers to include various forms of external signing, it should be no surprise to you that the next section will cover login options. What does the sign-in and sign-up flow look like, and does the user have to expose their private key to the application in order to use it?
A review of virtually any Nostr application would be incomplete without a section dedicated to zap integration. How prominent is zapping in the app? How easy is it to zap or start receiving zaps? Are zaps displayed in a way that encourages users to compete to be top zapper? Is Nostr Wallet Connect supported for using external wallets for one-tap-zapping?
Most Nostr applications, even "other stuff" clients, are designed to present some form of content to the user. The next section will cover how easy it is for the user to find the type of content they may be interested in, or to discover content they didn't know they might be interested in. For social clients, how easy is it to discover other users that they might want to follow?
The backbone of the protocol is the interplay between clients and relays, and the next section of the review will cover how the app manages relays. Are they hidden from the user? Are there sensible defaults? Can users who want to do so select the relays they prefer? Does the app respect relays the user has selected in other apps, or are the app's relays independent of those selected in other apps. Worse, does the app overwrite your selected relays with its defaults?
Finally, I will scour the #AskNostr feed for questions and comments from other users about the app under review to get more perspectives than just my own. What are the common pain-points other users are having? What do they love about the app? What features would they like to see added?
Are there other sections you would like to see me add before I start dropping reviews? Get them to me soon, because I am currently taking notes for my first review, which will be the #Primal #Android client!
PV 🤙
-
 @ 1c19eb1a:e22fb0bc
2025-03-06 07:48:38
@ 1c19eb1a:e22fb0bc
2025-03-06 07:48:38I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, Zapstore, or by downloading it directly from Primal's GitHub. This review is current as of Primal Android version 2.0.21.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 3.8 / 5
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarting experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 1 / 5
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ 1c19eb1a:e22fb0bc
2025-03-06 07:47:42
@ 1c19eb1a:e22fb0bc
2025-03-06 07:47:42After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.5 / 5
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.0 / 5
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touchpoint with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ 2cb8ae56:84d30cba
2025-03-06 07:40:38
@ 2cb8ae56:84d30cba
2025-03-06 07:40:38どうも、Nostrまとめ(2024)ぶりですね。
記事として出すのはかなりお久しぶりかも、お名前変わりまして「フェゼレント」でございます。 意味としては以下の通りです
1.Fezer(フェザー)という英単語 2.ent(エント)という造語 2-1. netを崩した形、よくこれに打ち間違えます。 2-2. Entertainment(エンターテイメント)の略語、なんか娯楽とか話題を生み出せる人になりたいですね。
1と2をガッタイ!!!(トムブラウン風)しまして、フェゼレントです。
なんとググってみますと、Fezerent及びフェゼレントの検索結果が0。 これは...一種のチャンスでは!?と思って、使っています。
さて、そこで出てくるのが「薄味のキャルピス」と「IVstrook」の今後ですよね。 後者に至っては3年分の料金を払ってドメインまで取っているわけですし、前者はかなりネットとかラジオでも浸透しています。
というわけで、こんな風に置き換えます。
Nostr、YT、Discordはフェゼレント及びFezerentを使用します。 それ以外(ラジオを含む)では薄味のキャルピス、IVstrookを使用します。 そして、NHKなどAM波を使用して放送を行っているラジオ局用で使用していた「テックジャンカー」ですが、使用を停止します。 あんま浸透しなかったわけですからね
そんな感じでやっていきます 最後に、記事最後に使用する署名のような奴ですが、そちらは変更なく「IVstrook」単体で行います。
また、ニコニコ動画及び各種ポッドキャストサービスにて配信しておりました「Small Room Space」ですが、今後はzap.streamというNostrのシステムを使用したサービスを用い、番組名の変更は行わないものとします。 zap.streamでの配信開始は「4月7日」 ちょうど#1が公開されてから1年が経過した日です
重ねて、当名義を使用したニコニコ動画への投稿は「3月8日」をもって終了とし、zap.streamへ移行します。
以上、今年に入ってからまともにニコニコ動画で投稿できていませんでしたが、そのような運びとさせていただきます。
2025/03/06 IVstrook
-
 @ da0b9bc3:4e30a4a9
2025-03-06 06:35:31
@ da0b9bc3:4e30a4a9
2025-03-06 06:35:31Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/905374
-
 @ 6b0a60cf:b952e7d4
2025-03-06 02:45:45
@ 6b0a60cf:b952e7d4
2025-03-06 02:45:45とあるSNSで海外の相互さん(以降、Aさんと呼ぶ)からDMで相談されたことがあって、思ったことをつらつらと書いてみる。
非公開の場での相談なので多少ぼかしを入れるけど。事の経緯
発端は、Aさんの友人が作品に日本人作者の素材を使用しようとしていて、その利用規約を翻訳して読んだらうまく翻訳されなくて理解が正しいのかわからない、なので間違いが無いか確認してほしい、という相談だった。
あー、確かに日本語特有の回りくどい表現があるねー、と思いながらバシッと簡潔に意訳してお伝えしたところ、スッキリ理解していただけたらしく一件落着となった。独自ライセンス文化
しかしまあ、創作界隈における作品・素材の利用規約というものは総じて長くて細かい。
ジャンルによるのかもしれないけれど。
自分は絵や音を創ることは無いがプログラムのコードを書く趣味はあるのでプログラム向けのライセンスを利用している。MITとかGPLとかいうやつ。
創作向けであればCCライセンスが適しているだろう。しかしこれがなかなか広まらない。
杓子定規のライセンスでは表しきれないような特別な希望があるのだろう。
そして独自ライセンスが跋扈することとなる。NO MORE 映画泥棒
特に気になるのが、「泥棒をしてはいけません」レベルの注意書きが散見されるのだ。
わざわざライセンスに書くことではない。あなたが警告するまでもなく、違法な行為は処罰される。
でも、たぶん効果があるからこういうのが広まるのだろう。
「泥棒してはいけないって書いてないから泥棒しました」というレベルの利用者が存在するのだろう。
そういう人は書いてあっても読んでないか、理屈をこねて泥棒するんだろうと思うけれども。その術はオレに効く
で、そういう警告文が魔除けの札のごとくびっしり貼られていると、こちらにやましい心が無くても、ちょっとこの素材は利用しないほうがよさそうだな……と思って引き返してしまうことがある。
SNSで可愛い絵を見て、作者さんをフォローしようと思ったら「無断転載禁止」みたいなのがプロフにずらずら書いてあって「おっと……」みたいに引き返すことがあるが、それに似ている。
きっと過去によくない体験をしてしまって、そのようにプロフに書くことでそれが改善するという実体験があって、そうなっているのだろうと推測している。異文化の壁を超えて
冒頭で話したAさんはきわめて紳士的な方であり、日本文化に対してもよく理解しようと努めてくれるので、話が通じやすくて助かったし、件の素材についても臆すること無く使用することになりそうだった。
ただ魔除けの札が効かないような魑魅魍魎にはいくら札を貼っても意味がないし、実際の悪魔祓いの効果と善良な利用者をも祓ってしまう機会損失(?)を比べて合理的なのだろうか、と考えたりしたのでした。オチは無い。ライセンス
この文章は CC0 1.0 でライセンスします。
Nostrイベントとして公開する以上はNIPsに従う範囲内で自由に利用されることを望みます。
NIPsに違反したご利用は他のクライアントの利用者にご迷惑になるのでご遠慮いただくことを希望します。^1 -
 @ a63655ce:05240c71
2025-03-06 00:48:46
@ a63655ce:05240c71
2025-03-06 00:48:46looks really clean.
window.nostrasked for the key multiple times for some reason -
 @ 6e0ea5d6:0327f353
2025-03-06 00:18:09
@ 6e0ea5d6:0327f353
2025-03-06 00:18:09Ascolta, amico mio...
There come moments when a grown man looks in the mirror and fails to recognize himself.
Naturally, when this happens, there is nothing more fitting than lighting a cigarette, pouring a glass of fine wine, and toasting to oneself—the birth of a new man, forged in the womb of a harsh and sobering reality.
One cannot scatter thorns along a path walked barefoot, nor allow the tongue to speak what the mind may later pay for—but this, we learn only through years of suffering.
Only now do I realize that, among all the teachers I have had, experience was the harshest of them all, for it first administered the test and only afterward taught me the lesson.
In peaceful moments, one can reflect more easily on the world around him. Imagine, then, the depths of reflection that can be reached in a state of true inner tranquility.
If you have never gazed upon the horizon, taken in all the fortune before your eyes, and declared to yourself, "I will own all of this!", then you have never possessed true ambition. However, blind ambition will leave you waking up hungry for wealth and power but going to sleep with an empty soul.
Walk always with honor, pride, and loyalty—let these principles never depart from you nor fail to steady your steps. In your battles, do not wish for your enemies to be handed to you on their knees; instead, seek to gain the strength and ruthlessness to bring them down while they stand.
Your greatest dilemma is the eternal paradox in the life of a businessman within the sacred Sicilian organization: how to acquire power and wealth without placing both feet in hell?
Be careful not to surrender to arrogance. The man who shouts his virtues to the wind will, when he falls, hear only the echo of his own pride.
Let your greatest legacy be to live in a way that does not shame your mother and makes your father proud.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ b8851a06:9b120ba1
2025-03-05 23:03:00
@ b8851a06:9b120ba1
2025-03-05 23:03:00The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there.
This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development.
The Riviera Plan: Rebuilding Without Its People
National Security Council spokesman Brian Hughes put it bluntly:
"Gaza is uninhabitable."
This isn't a call for humanitarian intervention. It's a pretext for forced displacement.
Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement.
Regional Consensus Rejected
The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland.
By dismissing this plan, Washington sent a clear message: Palestinian self-determination remains subordinate to Western geopolitical interests.
This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant.
The Fiat War Machine Connection
War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home.
As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
"Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation."
This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity."
Ukraine Parallels: When Support Is Conditional
The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection.
Both conflicts reveal the same truth: geopolitical support is increasingly transactional rather than values-based.
As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal."
The Cycle Continues
The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going.
Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it?
How long before people wake up #nostr? How long before the cycle breaks?
"Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world.
-
 @ b7b1382e:74635e6c
2025-03-05 22:32:18
@ b7b1382e:74635e6c
2025-03-05 22:32:18Abstract
By Lamar Wilson
This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability.
1. Introduction
Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation.
The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption.
2. Structural Components of the Proposed Framework
2.1 Uniform Flat Income Taxation
The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements:
-
Individual Taxation: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems.
-
Business Taxation: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure.
The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007).
2.2 Universal Redistribution Mechanism
The second component involves the pooling and redistribution of tax revenue:
-
Collection Aggregation: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool.
-
Equal Per Capita Distribution: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism.
This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017).
2.3 Tiered Consumption Taxation
The third component introduces a differentiated consumption tax structure:
-
Essential Goods and Services: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities.
-
Non-Essential and Luxury Items: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods.
This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018).
3. Economic Implications Analysis
3.1 Distributive Effects Across Income Levels
3.1.1 Lower-Income Households
The model's impact on lower-income households involves several counterbalancing forces:
- The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems.
- The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic.
- The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures.
Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013).
3.1.2 Higher-Income Households
For higher-income households, the framework produces different effects:
- The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets.
- The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income.
- Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns.
The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015).
3.2 Macroeconomic Implications
3.2.1 Investment and Growth Effects
The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through:
- Increased business formation and expansion
- Enhanced capital investment
- Improved labor productivity through capital deepening
- Potential innovation stimulation through retained earnings
Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008).
3.2.2 Demand Stability and Consumption Patterns
The redistribution component creates a consumption floor that may enhance economic stability through:
- Maintaining baseline consumer demand during economic downturns
- Reducing consumption volatility across business cycles
- Supporting broader-based consumption patterns
- Creating demand-side support for business expansion
This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012).
3.2.3 Labor Market Dynamics
The simplified tax structure potentially influences labor market participation through:
- Elimination of high marginal tax rates that may discourage additional work
- Reduced tax-related work disincentives at lower income levels
- Possible increased labor force participation due to simplified income-benefit calculations
- Potential wage effects as businesses retain higher post-tax profits
The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015).
4. Implementation Challenges and Considerations
4.1 Fiscal Revenue Adequacy
A primary challenge involves ensuring sufficient government revenue, particularly during the transition period:
- The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls.
- Government spending obligations would require adjustment, postponement, or alternative funding mechanisms.
- Transitional provisions may be necessary to align revenue reductions with spending adaptations.
Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006).
4.2 Wealth Concentration Effects
Despite redistribution mechanisms, the framework may influence wealth concentration dynamics:
- Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals.
- Business owners might experience wealth growth exceeding redistribution effects.
- Global investment patterns could divert economic benefits outside the domestic economy.
Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014).
4.3 Long-Term Sustainability Considerations
The framework's long-term viability depends on several factors:
- Sustained economic growth sufficient to support government functions with reduced tax rates
- Continued business investment in productive domestic activities rather than financial engineering
- Maintenance of investment-consumption balance to prevent boom-bust cycles
- Evolution of the system in response to changing economic conditions
Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012).
5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure
5.1 Compliance Cost Reduction
The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments:
- Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022)
- The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018)
- Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021)
- The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement
The proposed flat tax system would dramatically reduce these costs through:
- Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity)
- Removal of recordkeeping requirements for numerous tax provisions
- Significant reduction in tax planning expenses for both individuals and businesses
- Decreased need for professional tax preparation services
- Streamlined tax enforcement with fewer provisions to interpret and audit
Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020).
5.2 Administrative Efficiency Gains
The current tax administration infrastructure incurs substantial costs:
- The IRS employs approximately 75,000 full-time equivalent positions
- Tax litigation consumes significant judicial resources across multiple court systems
- Regulatory development and guidance require extensive government resources
- Tax enforcement costs represent approximately 35 cents per $100 collected
The proposed system would generate administrative efficiencies through:
- Simplified verification processes requiring fewer personnel
- Reduced need for specialized tax rulings and interpretations
- Lower audit costs due to straightforward compliance requirements
- Streamlined distribution mechanisms leveraging existing payment systems
Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction.
5.3 Economic Efficiency Improvements
Beyond direct compliance and administrative costs, the current system creates significant economic distortions:
- Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value
- Complex provisions create market inefficiencies and misallocation of resources
- High marginal rates discourage additional productive activity
- International tax complexities influence global investment decisions
The proposed system addresses these inefficiencies through:
- Uniform treatment of income regardless of source
- Elimination of tax-motivated transaction structures
- Reduced incentives for artificial entity structures
- Simplified international transactions with domestic reinvestment incentives
Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012).
5.4 Distributional Cost Analysis
The current system's compliance burden falls disproportionately across income levels:
- Lower-income taxpayers spend a higher percentage of their income on tax compliance
- Small businesses face compliance costs estimated at $1,500-$4,000 per employee
- Middle-income taxpayers navigate complex provisions with limited professional assistance
- High-income taxpayers allocate substantial resources to tax planning and compliance
The proposed system redistributes this burden by:
- Equalizing compliance requirements across income levels
- Substantially reducing small business administrative overhead
- Eliminating the need for complex tax planning strategies
- Providing transparent, predictable tax consequences for economic decisions
This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs.
6. Conclusion
The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support.
The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability.
Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes.
References
Acemoglu, D., & Robinson, J. A. (2012). Why nations fail: The origins of power, prosperity, and poverty. Crown Business.
Greenberg, S. (2020). Reforming the U.S. tax system: Evidence on economic growth and distribution. American Enterprise Institute.
Jorgenson, D. W., & Yun, K. Y. (2012). Tax reform and the cost of capital. Oxford University Press.
Laffer, A. B., Moore, S., & Williams, J. (2018). The wealth of states: How taxes, energy, and worker freedom change everything. Wiley.
Tax Foundation (2021). The cost of tax compliance. Fiscal Fact No. 512.
Taxpayer Advocate Service (2022). Annual report to Congress. Internal Revenue Service.
Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. NBER Working Paper Series.
Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. American Economic Review, 105(5), 38-42.
Card, D., & Krueger, A. B. (2015). Myth and measurement: The new economics of the minimum wage. Princeton University Press.
Hall, R. E., & Rabushka, A. (2007). The flat tax. Hoover Institution Press.
Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. International Tax and Public Finance, 15(6), 712-751.
Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. Commitment to Equity Handbook.
Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). Tax by design. Oxford University Press.
Piketty, T. (2014). Capital in the twenty-first century. Harvard University Press.
Piketty, T., & Saez, E. (2013). Optimal labor income taxation. Handbook of Public Economics, 5, 391-474.
Stiglitz, J. E. (2012). The price of inequality: How today's divided society endangers our future. W.W. Norton & Company.
Van Parijs, P., & Vanderborght, Y. (2017). Basic income: A radical proposal for a free society and a sane economy. Harvard University Press.
A Tripartite Approach to Fiscal Reform: Analyzing the Economic Impact of a Flat Tax, Redistribution, and Consumption Tax Framework
Author: Lamar Wilson
Abstract
By Lamar Wilson
This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability.
1. Introduction
Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation.
The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption.
2. Structural Components of the Proposed Framework
2.1 Uniform Flat Income Taxation
The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements:
-
Individual Taxation: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems.
-
Business Taxation: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure.
The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007).
2.2 Universal Redistribution Mechanism
The second component involves the pooling and redistribution of tax revenue:
-
Collection Aggregation: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool.
-
Equal Per Capita Distribution: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism.
This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017).
2.3 Tiered Consumption Taxation
The third component introduces a differentiated consumption tax structure:
-
Essential Goods and Services: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities.
-
Non-Essential and Luxury Items: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods.
This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018).
3. Economic Implications Analysis
3.1 Distributive Effects Across Income Levels
3.1.1 Lower-Income Households
The model's impact on lower-income households involves several counterbalancing forces:
- The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems.
- The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic.
- The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures.
Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013).
3.1.2 Higher-Income Households
For higher-income households, the framework produces different effects:
- The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets.
- The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income.
- Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns.
The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015).
3.2 Macroeconomic Implications
3.2.1 Investment and Growth Effects
The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through:
- Increased business formation and expansion
- Enhanced capital investment
- Improved labor productivity through capital deepening
- Potential innovation stimulation through retained earnings
Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008).
3.2.2 Demand Stability and Consumption Patterns
The redistribution component creates a consumption floor that may enhance economic stability through:
- Maintaining baseline consumer demand during economic downturns
- Reducing consumption volatility across business cycles
- Supporting broader-based consumption patterns
- Creating demand-side support for business expansion
This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012).
3.2.3 Labor Market Dynamics
The simplified tax structure potentially influences labor market participation through:
- Elimination of high marginal tax rates that may discourage additional work
- Reduced tax-related work disincentives at lower income levels
- Possible increased labor force participation due to simplified income-benefit calculations
- Potential wage effects as businesses retain higher post-tax profits
The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015).
4. Implementation Challenges and Considerations
4.1 Fiscal Revenue Adequacy
A primary challenge involves ensuring sufficient government revenue, particularly during the transition period:
- The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls.
- Government spending obligations would require adjustment, postponement, or alternative funding mechanisms.
- Transitional provisions may be necessary to align revenue reductions with spending adaptations.
Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006).
4.2 Wealth Concentration Effects
Despite redistribution mechanisms, the framework may influence wealth concentration dynamics:
- Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals.
- Business owners might experience wealth growth exceeding redistribution effects.
- Global investment patterns could divert economic benefits outside the domestic economy.
Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014).
4.3 Long-Term Sustainability Considerations
The framework's long-term viability depends on several factors:
- Sustained economic growth sufficient to support government functions with reduced tax rates
- Continued business investment in productive domestic activities rather than financial engineering
- Maintenance of investment-consumption balance to prevent boom-bust cycles
- Evolution of the system in response to changing economic conditions
Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012).
5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure
5.1 Compliance Cost Reduction
The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments:
- Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022)
- The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018)
- Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021)
- The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement
The proposed flat tax system would dramatically reduce these costs through:
- Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity)
- Removal of recordkeeping requirements for numerous tax provisions
- Significant reduction in tax planning expenses for both individuals and businesses
- Decreased need for professional tax preparation services
- Streamlined tax enforcement with fewer provisions to interpret and audit
Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020).
5.2 Administrative Efficiency Gains
The current tax administration infrastructure incurs substantial costs:
- The IRS employs approximately 75,000 full-time equivalent positions
- Tax litigation consumes significant judicial resources across multiple court systems
- Regulatory development and guidance require extensive government resources
- Tax enforcement costs represent approximately 35 cents per $100 collected
The proposed system would generate administrative efficiencies through:
- Simplified verification processes requiring fewer personnel
- Reduced need for specialized tax rulings and interpretations
- Lower audit costs due to straightforward compliance requirements
- Streamlined distribution mechanisms leveraging existing payment systems
Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction.
5.3 Economic Efficiency Improvements
Beyond direct compliance and administrative costs, the current system creates significant economic distortions:
- Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value
- Complex provisions create market inefficiencies and misallocation of resources
- High marginal rates discourage additional productive activity
- International tax complexities influence global investment decisions
The proposed system addresses these inefficiencies through:
- Uniform treatment of income regardless of source
- Elimination of tax-motivated transaction structures
- Reduced incentives for artificial entity structures
- Simplified international transactions with domestic reinvestment incentives
Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012).
5.4 Distributional Cost Analysis
The current system's compliance burden falls disproportionately across income levels:
- Lower-income taxpayers spend a higher percentage of their income on tax compliance
- Small businesses face compliance costs estimated at $1,500-$4,000 per employee
- Middle-income taxpayers navigate complex provisions with limited professional assistance
- High-income taxpayers allocate substantial resources to tax planning and compliance
The proposed system redistributes this burden by:
- Equalizing compliance requirements across income levels
- Substantially reducing small business administrative overhead
- Eliminating the need for complex tax planning strategies
- Providing transparent, predictable tax consequences for economic decisions
This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs.
6. Conclusion
The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support.
The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability.
Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes.
References
Acemoglu, D., & Robinson, J. A. (2012). Why nations fail: The origins of power, prosperity, and poverty. Crown Business.
Greenberg, S. (2020). Reforming the U.S. tax system: Evidence on economic growth and distribution. American Enterprise Institute.
Jorgenson, D. W., & Yun, K. Y. (2012). Tax reform and the cost of capital. Oxford University Press.
Laffer, A. B., Moore, S., & Williams, J. (2018). The wealth of states: How taxes, energy, and worker freedom change everything. Wiley.
Tax Foundation (2021). The cost of tax compliance. Fiscal Fact No. 512.
Taxpayer Advocate Service (2022). Annual report to Congress. Internal Revenue Service.
Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. NBER Working Paper Series.
Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. American Economic Review, 105(5), 38-42.
Card, D., & Krueger, A. B. (2015). Myth and measurement: The new economics of the minimum wage. Princeton University Press.
Hall, R. E., & Rabushka, A. (2007). The flat tax. Hoover Institution Press.
Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. International Tax and Public Finance, 15(6), 712-751.
Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. Commitment to Equity Handbook.
Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). Tax by design. Oxford University Press.
Piketty, T. (2014). Capital in the twenty-first century. Harvard University Press.
Piketty, T., & Saez, E. (2013). Optimal labor income taxation. Handbook of Public Economics, 5, 391-474.
Stiglitz, J. E. (2012). The price of inequality: How today's divided society endangers our future. W.W. Norton & Company.
Van Parijs, P., & Vanderborght, Y. (2017). Basic income: A radical proposal for a free society and a sane economy. Harvard University Press.
-
-
 @ 6389be64:ef439d32
2025-03-05 21:18:52
@ 6389be64:ef439d32
2025-03-05 21:18:52Carbon is a "Long-Tail" asset: the residual earnings that come from an asset after it has had its initial market impact.
The Carbon Cascade converts labile into recalcitrant carbon.
During transformation power is generated and lands restored.
Total production of biomass per annum is 100 billion tons of carbon and at $500 to $2,000 per ton of biochar that's $100 trillion of potential carbon trading on the open market. (fanciful to be sure)
originally posted at https://stacker.news/items/904996
-
 @ 05933d87:81bac46e
2025-03-05 20:17:49
@ 05933d87:81bac46e
2025-03-05 20:17:49A few months ago, an Uber driver alerted me to the presence of his rival. By that point, Waymo had been testing in Austin for over a year. I hid my excitement during the ride but I applied as a beta tester, noting my belonging to the demographics a PM might test for. My application went ignored until, huzzah, Waymo sent me an email yesterday announcing their self-driving cars are available directly through Uber in Austin.
I configured my allegiance to our new overlords swearing in on my screened sandwich of silicon.
Without willing it, and having forgot my new religion, I woke earlier than planned today and hailed a ride. The app spoke to me, "if you wait 3 minutes longer, we'll send you a car without a driver." For five minutes, I watched a car but not a driver move in the direction of me and my screen.
The ride was nice. I didn't have to theatrically rush to a waiting human. There was less social weirdness than I would normally sit with on a ride. I could inspect the car without risking the driver sense that I'm inspecting them. The car couldn't look at me buffering, deciphering if I am homeless or merely look it. I got to pick my own music. I got to watch people un-contacted by Waymo watch the car.
But ... it drove a lot more like a robot driving a car than a human driving a car. It pumped the brakes a few times as we passed weirdly parked cars uncertain (apparently) if the car might move into our lane. Once it signaled that we were headed into oncoming traffic as a street widened from one lane to two. Worst of all, it dropped me off near an anomalous stretch of sidewalk where my door opened to a wall, and if I were to climb and get out the other side, I'd arrive in the middle lane of a busy street. Trapped, I pinched myself through the door and, like Laura Croft, navigated the road's edge to a sidewalk.
tbh I'm still excited for my next Waymo ride. I'll just choose a different drop-off address.
originally posted at https://stacker.news/items/904830
-
 @ b4403b24:83542d4e
2025-03-05 19:18:39
@ b4403b24:83542d4e
2025-03-05 19:18:39I can't believe so many shitcoiners are invited to attend 🫣
originally posted at https://stacker.news/items/904818
-
 @ 97c70a44:ad98e322
2025-03-05 18:09:05
@ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill.
But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed.
It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that.
All these terms are really referring to one concept under many different names: that of "cryptographic identity".
Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze.
Identity
What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way:
Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible.
This definition has three parts:
- Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence.
- Identity is a unit: you can't break an identity into multiple parts. A thing might be composed of multiple parts, but that's only incidental to the identity of a thing, which is a concept, not a material thing.
- Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples.
Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept".
I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our actual identities as people, but entirely fictional identities that we use to extend our agency into the digital world.
Think of it this way - your bank login does not represent you as a complete person. It only represents the access granted to you by the bank. This access is in fact an entirely new identity that has been associated with you, and is limited in what it's useful for.
Other examples of fictional identities include:
- The country you live in
- Your social media persona
- Your mortgage
- Geographical coordinates
- A moment in time
- A chess piece
Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules.
For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction.
"Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated.
Certificates
Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope.
This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account".
In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination.
This pattern for authentication is ubiquitous, and has some very important implications.
First of all, certified authentication implies that the issuer of the certificate has the right to exclusive control of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights.
Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it.
Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has.
Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties.
Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into.
In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties.
Self-Certification
But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?

Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority.
So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity?
The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world.
Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck.
In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify.
There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to personality. These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable.
So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself.
Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact.
Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified and unforgeable.
Digital Signatures
In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something looks like a physical signature, but for something that does the same thing as a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact.
With that, let's get into the weeds.
An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number.
A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get
5, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number5. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number3.A real-life example of a useful one-way function is
sha256. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like intosha256, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output.Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output.
"Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes into the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we could do it that way (maybe), but there's actually a much simpler solution.
Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though.
The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next.
Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability.
Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their giant wall of lava lamps to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice.
To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key".
And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is.
A "cryptographic identity" is identified by a public key, and authenticated by the ability to prove that you know the private key.
Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an algorithm that only someone who knows the private key can execute.
This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can prove that you know the private key.
For example, if my secret number is
12, and someone tells me the number37, I can "combine" the two by adding them together and returning the number49. This "proves" that my secret number is12. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge.What's it for?
If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number?
To answer this, let's consider a simple example: that of public social media posts.
Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key".
Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet.
In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time).
Now pretend that X gets bought by someone even more evil than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control your identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted.
In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of).
But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another.
Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you.
What X can't do in this system is pretend you said something you didn't, because they don't know your private key.
X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and keep your followers. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by your digital signature, not X's "because I say so".
This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms:
- Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called bitcoin.
- Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen).
- Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. Zero-knowledge proofs take this a step further.
In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom.
Objections
Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve.
Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time.
Key Storage
Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure.
Apart from the fact that all of this is an argument for cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too!
Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a hardware signing device. This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity.
There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few:
- Hierarchical Deterministic Keys allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind.
- Key Rotation allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust.
- Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like Amber to manage sessions with different applications.
- Key sharding takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key.
Multi-Factor Authentication
One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device.
Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation.
In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem:
- Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve Zooko's trilemma.
- Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity.
Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about.
Surveillance
One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information.
The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it.
This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID".
The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired.
Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties.
Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see this blog post.
Making Keys Usable
You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With nostr, some new things are happening in the world of key management that have never really happened before.
Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect.
Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that humans care about.
By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face.
So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit njump.me.
Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
-
 @ 8d34bd24:414be32b
2025-03-05 16:52:58
@ 8d34bd24:414be32b
2025-03-05 16:52:58Sometimes I wonder why I write posts like this. This is not the way to gain a big following, but then again, that is not my goal. My goal is to share Jesus with anyone who will listen, to faithfully speak whatever truth I feel God is leading me to share, and to teach the inerrant word of God in order to draw people, both believers and not yet believers, closer to Jesus. I trust God to use my words in whatever way He sees best. If it only reaches a few, that is OK by me. If somehow this substack starts reaching a vast audience, then praise God for that!
Today, I am writing about a hard truth. The Bible contains a number of hard truths that most people don’t want to believe, but which our Creator God has stated as truth. None of us likes being called a sinner, but the Bible says:
as it is written, “There is none righteous, not even one. (Romans 3:10)
As hard as the truth that we are all sinners is, a much harder truth is that not everyone gets to go to Heaven. Some people are destined for Hell. I am going to investigate some verses that illuminate this truth.
Ironically, most people have two contradictory thoughts. Most people wonder why God allows so much evil in the world. If He is truly sovereign, why doesn’t He stop evil? At the same time they wonder why a loving God would send anyone to Hell. We can’t expect God to stop and punish evil, but not send some people to Hell. We can’t have it both ways.
The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:9)
This verse explains the basic facts of how God’s holiness is reconciled with His love and mercy, but of course there is so much more. If God is truly sovereign over all, then why is there any evil? Why does anyone sin? Why is there pain and suffering?
The Lord has made everything for its own purpose,\ Even the wicked for the day of evil.\ Everyone who is proud in heart is an abomination to the Lord;\ Assuredly, he will not be unpunished.\ By lovingkindness and truth iniquity is atoned for,\ And by the fear of the Lord one keeps away from evil. (Proverbs 16:4-6) {emphasis mine}
Everyone and everything was made for God’s own purpose. As our Creator, He has the right to make each of us for whatever purpose He desires. The creature has no right to question the Creator and His purpose.
Then I went down to the potter’s house, and there he was, making something on the wheel. But the vessel that he was making of clay was spoiled in the hand of the potter; so he remade it into another vessel, as it pleased the potter to make.
Then the word of the Lord came to me saying, “Can I not, O house of Israel, deal with you as this potter does?” declares the Lord. “Behold, like the clay in the potter’s hand, so are you in My hand, O house of Israel. At one moment I might speak concerning a nation or concerning a kingdom to uproot, to pull down, or to destroy it; if that nation against which I have spoken turns from its evil, I will relent concerning the calamity I planned to bring on it. Or at another moment I might speak concerning a nation or concerning a kingdom to build up or to plant it; if it does evil in My sight by not obeying My voice, then I will think better of the good with which I had promised to bless it. (Jeremiah 18:3-10) {emphasis mine}
But the Bible says it even goes beyond God directly responding to our choices. The God of the Bible is creator and sovereign over all. Nothing happens contrary to His will.
So then He has mercy on whom He desires, and He hardens whom He desires.
You will say to me then, “Why does He still find fault? For who resists His will?” On the contrary, who are you, O man, who answers back to God? The thing molded will not say to the molder, “Why did you make me like this,” will it? Or does not the potter have a right over the clay, to make from the same lump one vessel for honorable use and another for common use? What if God, although willing to demonstrate His wrath and to make His power known, endured with much patience vessels of wrath prepared for destruction? And He did so to make known the riches of His glory upon vessels of mercy, which He prepared beforehand for glory, even us, whom He also called, not from among Jews only, but also from among Gentiles. (Romans 9:18-24) {emphasis mine}
The above passage speaks a very uncomfortable truth. We don’t like thinking we don’t have full and complete free-will to do whatever we want and to determine our future, but it isn’t that simple. The Bible says specifically that some are “prepared for destruction” and others are “prepared beforehand for glory.”
For by grace you have been saved through faith; and that not of yourselves, it is the gift of God; not as a result of works, so that no one may boast. For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. (Ephesians 2:8-10) {emphasis mine}
We aren’t saved because we are smarter than all of the people who didn’t choose Jesus. We aren’t wiser than those who chose their own path rather than the path designed by God. We are saved by God as a gift. He called those who were dead in their sins to life in him. The dead can’t choose anything. We all must be made spiritually alive so we can follow Him. Only Jesus does that. We can’t make ourselves alive in Him.
Every believer needs to thank Jesus daily for the miracle of spiritual life in Him that has been given to us despite us not deserving it or choosing it.
In this is love, not that we loved God, but that He loved us and sent His Son to be the propitiation for our sins. (1 John 4:10)
and
We love, because He first loved us. (1 John 4:19)
Jesus acted first, choosing us, and we responded, not that we chose Him and He loved us because of our choice.
I’m sure many of my readers are cringing at this Biblical truth. We all try to make God’s word say something else because we don’t like feeling out of control. We don’t like to think that someone else is smarter, stronger, or more in control of our lives than ourselves. Still, being made to follow Jesus is the greatest blessing a person can receive.
Trust in the Lord with all your heart\ And do not lean on your own understanding.\ In all your ways acknowledge Him,\ And He will make your paths straight.\ Do not be wise in your own eyes;\ Fear the Lord and turn away from evil.\ It will be healing to your body\ And refreshment to your bones. (Proverbs 3:5-8)
We don’t have to fully understand God’s truth, but we do need to accept it.
May God guide you in the truth through His God breathed word, so we may serve Him faithfully and submit fully to His authority and His will to the glory of His majesty.
Trust Jesus
-
 @ 401014b3:59d5476b
2025-03-05 15:37:44
@ 401014b3:59d5476b
2025-03-05 15:37:44Alright, football fiends, it’s March 2025, and we’re diving into the NFC North like it’s a polar plunge with a side of cheap beer. Free agency’s a free-for-all, the draft’s a crapshoot, and this division’s always a slugfest of grit, guts, and grudges. The Vikings shocked the world with a 14-3 run in 2024, the Lions roared, the Packers stayed scrappy, and the Bears showed flashes. Let’s slap some records on this beast and figure out who’s got the stones to take the North. Here we go, fam—hold my bratwurst.
Minnesota Vikings: 11-6 – Darnold’s Encore or Bust
The Vikings were the NFL’s Cinderella story in 2024, rolling to 14-3 with Sam Darnold slinging it and Brian Flores’ defense eating souls. Justin Jefferson’s still a cheat code, and Aaron Jones keeps the ground game humming. That D-line—Jonathan Greenard, Andrew Van Ginkel—stays nasty, but free agency’s lurking. Danielle Hunter’s long gone, and guys like Harrison Phillips might chase a bag. J.J. McCarthy’s waiting in the wings, but Darnold’s 2024 magic earns him the nod. Regression’s real after a dream season—11-6 feels right, snagging the division. They’re not hitting 14 again, but they’re still a playoff lock.
Detroit Lions: 10-7 – Campbell’s Grit Keeps Grinding
The Lions were a buzzsaw in 2024, and they’re not fading. Jared Goff’s got Amon-Ra St. Brown and Jameson Williams torching secondaries, while David Montgomery and Jahmyr Gibbs bulldoze defenses. Aidan Hutchinson’s a one-man wrecking crew up front, but free agency could nick ‘em—Brian Branch or Alim McNeill might dip. Dan Campbell’s got this team playing with their hair on fire, and that O-line’s still elite. 10-7’s the call, grabbing a wildcard. They’re a hair behind Minnesota but ready to punch someone’s lights out in January.
Green Bay Packers: 9-8 – Love’s Rollercoaster Redux
The Packers are the NFC North’s wild card—literally. Jordan Love’s got that boom-or-bust vibe, Josh Jacobs keeps the run game honest, and the WR trio—Christian Watson, Romeo Doubs, Jayden Reed—is a problem when healthy. Rashan Gary’s a beast on D, but the secondary’s shaky, and Jaire Alexander might bolt if the money’s right. This team’s young, scrappy, and inconsistent—9-8’s where they land. Might sneak a wildcard if the chips fall, but they’re not catching the top dogs yet.
Chicago Bears: 6-11 – Caleb’s Sophomore Slump
The Bears had their moments in 2024, but 2025’s a grind. Caleb Williams has DJ Moore and Rome Odunze to sling it to, and D’Andre Swift’s solid, but that O-line’s still a sieve. The defense—Montez Sweat, Jaylon Johnson—can ball, but depth’s thin, and free agency might swipe Tremaine Edmunds. Williams takes a step, but not a leap—6-11’s the harsh reality. They’re building something, but it’s not playoff-ready. Sorry, Windy City, you’re still in the basement.
The Final Roar
The NFC North in 2025 is a Viking victory lap with a tight chase. The Vikings (11-6) snag the crown because Darnold’s 2024 glow carries over, the Lions (10-7) claw a wildcard with grit, the Packers (9-8) flirt with relevance, and the Bears (6-11) eat turf. Free agency’s the X-factor—lose a star, you’re cooked; keep ‘em, you’re golden. Yell at me on X when I botch this, but this is my NFC North sermon. Let’s ride, degenerates.
-
 @ d360efec:14907b5f
2025-03-05 13:58:42
@ d360efec:14907b5f
2025-03-05 13:58:42ภาพรวม:
จากภาพรวมทั้ง 3 Timeframe (TF) จะเห็นได้ว่า BTC มีแนวโน้มเป็นขาขึ้น (Bullish) อย่างชัดเจน โดยเฉพาะอย่างยิ่งใน TF Day ที่ราคาอยู่เหนือเส้น EMA 50 และ EMA 200 อย่างแข็งแกร่ง อย่างไรก็ตาม ใน TF ที่เล็กลงมา (15m และ 4H) เริ่มเห็นสัญญาณการพักตัวและอาจมีการปรับฐานระยะสั้น
การวิเคราะห์แยกตาม Timeframe:
- TF Day:
-

- SMC: ราคามีการ Breakout โครงสร้างตลาดขาลงก่อนหน้า และสร้าง Higher High (HH) และ Higher Low (HL) อย่างต่อเนื่อง
- ICT Buyside & Sellside Liquidity:
- Buyside Liquidity: อยู่บริเวณ $70,000 (เป็นเป้าหมายถัดไปที่ราคามีโอกาสขึ้นไปทดสอบ)
- Sellside Liquidity: อยู่บริเวณ $60,000 (เป็นแนวรับสำคัญ หากราคาหลุดลงมา อาจมีการปรับฐานที่รุนแรงขึ้น)
- Money Flow: เป็นบวก สนับสนุนแนวโน้มขาขึ้น
- EMA: EMA 50 (เหลือง) อยู่เหนือ EMA 200 (ขาว) เป็นสัญญาณ Bullish
- Trend Strength: เมฆสีเขียวหนาแน่น แสดงถึงแนวโน้มขาขึ้นที่แข็งแกร่ง และมีสัญญาณ Buy
- Chart Pattern: ไม่มีรูปแบบ Chart Pattern ที่ชัดเจนใน TF นี้
-
TF 4H:
-

- SMC: ราคาเริ่มมีการพักตัวและสร้างฐาน (Consolidation)
- ICT Buyside & Sellside Liquidity:
- Buyside Liquidity: อยู่บริเวณ $69,000 (แนวต้านย่อย)
- Sellside Liquidity: อยู่บริเวณ $64,000 (แนวรับย่อย)
- Money Flow: เริ่มมีสัญญาณการไหลออกของเงิน (Outflow)
- EMA: EMA 50 ยังคงอยู่เหนือ EMA 200 แต่เริ่มมีการ Cross กัน อาจเป็นสัญญาณเตือนการพักตัว
- Trend Strength: เมฆสีเขียวเริ่มบางลง และมีสัญญาณ Neutral
- Chart Pattern: อาจกำลังก่อตัวเป็นรูปแบบ Head and Shoulders (กลับตัว) หรืออาจเป็นเพียงการพักตัวเพื่อไปต่อ
-
TF 15m:

- SMC: ราคาอยู่ในช่วง Sideways แคบๆ
- ICT Buyside & Sellside Liquidity:
- Buyside Liquidity: อยู่บริเวณ $68,500
- Sellside Liquidity: อยู่บริเวณ $66,000
- Money Flow: เป็นลบ (Outflow)
- EMA: EMA 50 และ EMA 200 พันกัน (Cross) บ่งบอกถึงการไม่มี Trend ที่ชัดเจน
- Trend Strength: เมฆสีแดง แสดงถึงแนวโน้มขาลงระยะสั้น และมีสัญญาณ Sell
- Chart Pattern: ไม่พบรูปแบบ Chart Pattern ที่ชัดเจน
กลยุทธ์และคำแนะนำ:
-
Day Trade:
- กลยุทธ์: เน้น Buy on Dip (ซื้อเมื่อราคาอ่อนตัว) ใน TF 15m หรือ 4H โดยรอสัญญาณการกลับตัวของราคา และตั้ง Stop Loss ที่เหมาะสม
- Setup (SMC):
- รอให้ราคาลงมาทดสอบแนวรับ (Demand Zone) ที่ $66,000-$67,000 ใน TF 15m
- สังเกต Price Action ว่ามีการกลับตัว (เช่น Bullish Engulfing, Hammer) หรือไม่
- เข้า Buy เมื่อมีสัญญาณยืนยัน และตั้ง Stop Loss ต่ำกว่า Swing Low ล่าสุด
- Take Profit ที่แนวต้านถัดไป ($68,500) หรือ Buyside Liquidity
- สิ่งที่ต้องระวัง:
- ความผันผวนของราคา BTC ที่สูง
- ข่าวหรือเหตุการณ์ที่อาจส่งผลกระทบต่อตลาด
- สัญญาณ Divergence (หากมี) ระหว่างราคาและ Indicator
-
ภาพรวม (ระยะกลาง-ยาว): ยังคงมีมุมมองเป็น Bullish แต่ควรระมัดระวังการพักตัวหรือปรับฐานระยะสั้น
สรุป:
BTC ยังคงมีแนวโน้มเป็นขาขึ้นในระยะกลาง-ยาว แต่ในระยะสั้นอาจมีการพักตัวหรือปรับฐาน Day Trader ควรใช้กลยุทธ์ Buy on Dip และบริหารความเสี่ยงอย่างรอบคอบ
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-
 @ d360efec:14907b5f
2025-03-05 13:46:26
@ d360efec:14907b5f
2025-03-05 13:46:26Overview:
From an overall perspective across all 3 timeframes (TF), BTC shows a clear uptrend (Bullish), especially in the Day TF where the price is firmly above the EMA 50 and EMA 200. However, in the smaller TFs (15m and 4H), there are signs of consolidation and a potential short-term correction.
Analysis by Timeframe:
- Day TF:
-
- SMC: The price has broken out of the previous downtrend structure and continues to create Higher Highs (HH) and Higher Lows (HL).
- ICT Buyside & Sellside Liquidity:
- Buyside Liquidity: Around $70,000 (the next target the price is likely to test).
- Sellside Liquidity: Around $60,000 (a key support level; if the price breaks below this, a deeper correction may occur).
- Money Flow: Positive, supporting the uptrend.
- EMA: EMA 50 (yellow) is above EMA 200 (white), a bullish signal.
- Trend Strength: Thick green cloud, indicating a strong uptrend, and a Buy signal.
- Chart Pattern: No clear chart pattern on this TF.
-
4H TF:
-
- SMC: The price is starting to consolidate and form a base.
- ICT Buyside & Sellside Liquidity:
- Buyside Liquidity: Around $69,000 (minor resistance).
- Sellside Liquidity: Around $64,000 (minor support).
- Money Flow: Starting to show signs of outflow.
- EMA: EMA 50 is still above EMA 200, but they are starting to cross, which could be a warning sign of consolidation.
- Trend Strength: The green cloud is starting to thin, and there is a Neutral signal.
- Chart Pattern: Potentially forming a Head and Shoulders pattern (reversal) or it may just be a consolidation before continuing higher.
-
15m TF:
- SMC: The price is in a narrow sideways range.
- ICT Buyside & Sellside Liquidity:
- Buyside Liquidity: Around $68,500.
- Sellside Liquidity: Around $66,000.
- Money Flow: Negative (Outflow).
- EMA: EMA 50 and EMA 200 are intertwined (Cross), indicating a lack of a clear trend.
- Trend Strength: Red cloud, indicating a short-term downtrend, and a Sell signal.
- Chart Pattern: No clear chart pattern found.
Strategy and Recommendations:
-
Day Trade:
- Strategy: Focus on Buy on Dip in the 15m or 4H TF, waiting for price reversal signals, and setting appropriate Stop Losses.
- Setup (SMC):
- Wait for the price to test the support (Demand Zone) at $66,000-$67,000 in the 15m TF.
- Observe Price Action for a reversal (e.g., Bullish Engulfing, Hammer).
- Enter a Buy when there is a confirmation signal and set a Stop Loss below the latest Swing Low.
- Take Profit at the next resistance ($68,500) or Buyside Liquidity.
- Things to watch out for:
- High volatility of BTC price.
- News or events that may affect the market.
- Divergence signals (if any) between price and indicators.
-
Overall (Medium-Long Term): Still bullish, but be cautious of short-term consolidations or corrections.
Summary:
BTC remains bullish in the medium to long term, but there may be a short-term consolidation or correction. Day traders should use a Buy on Dip strategy and manage risk carefully.
Disclaimer: This analysis is a personal opinion and not investment advice. Investors should do their own research and make decisions carefully.
-
 @ beb6bdc9:eeb17df3
2025-03-05 13:25:08
@ beb6bdc9:eeb17df3
2025-03-05 13:25:08https://image.nostr.build/2ad4cf1beb7f1ebaecfe1e011f83c85d09c2c17e4a1f40eac412bb08e03d82c4.jpg 00020126360014BR.GOV.BCB.PIX0114dig@depix.info520400005303986540549.905802BR5923CURSO BITCOIN PARA TDAH6013SATOSHILANDIA62070503***63045C68
↑ COPIE TODO O TEXTO DA CHAVE PIX ACIMA! ↑
Para ter acesso ao guia BITCOIN PARA TDAH, pague a chave pix copia e cola acima e apresente o comprovante de pagamento em:
https://t.me/dinopacon
-
 @ a58a2663:87bb2918
2025-03-05 12:41:36
@ a58a2663:87bb2918
2025-03-05 12:41:36After two years of using Standard Notes as my main note-taking app, I’m switching to Obsidian.
The $100 that Standard Notes charges for basic editing capabilities is difficult to justify, especially for someone paying in Brazilian Real and striving to make a living from writing. However, I will certainly miss its simplicity and cleaner interface.
It’s my impression that the developers are missing an opportunity to create a privacy-focused note-taking app tailored to the specific needs of writers, rather than general users.
Substack, for example, achieved such success because it targeted the distribution and monetization of writers’ work. But we need more tools focused not on distribution or monetization, but on the actual process—indeed, the various phases of the process—of creating texts. This is especially true for complex, long-form texts with different levels of argumentation, numerous written and multimedia sources, and cross-references to other works by the author.
It’s crucial that an app like this doesn’t feel overly complex, like Notion or Evernote, or so all-purpose, like Obsidian. And, of course, I’m not talking about a new full-fledged text editor like Scrivener.
Just a thought. Take note.
-
 @ 5f3e7e41:81cb07cf
2025-03-05 11:37:27
@ 5f3e7e41:81cb07cf
2025-03-05 11:37:27The question of life’s meaning has long been a central concern in philosophy, debated by existentialists, nihilists, absurdists, and theologians alike. Is there an inherent purpose to human existence, or must we construct our own meaning? This essay explores the philosophical dimensions of the question by examining various perspectives, including existentialism, nihilism, and teleological interpretations. Existentialist Perspective Existentialists argue that meaning is not intrinsic but must be created. Jean-Paul Sartre, for instance, asserts that existence precedes essence—humans exist first and define their own purpose afterward. Unlike an artifact designed for a specific function, human beings are thrown into existence without predetermined meaning. Sartre’s concept of radical freedom suggests that we are entirely responsible for imbuing our lives with purpose through our choices and actions. Albert Camus, while existential in his approach, leans toward absurdism. He argues that human beings seek meaning in a universe that offers none. This fundamental conflict, the absurd, leads to either nihilism or rebellion. Camus advocates for an embrace of the absurd—accepting life’s lack of inherent purpose and living in defiance of this reality, deriving meaning from the act of living itself. Nihilistic Perspective Nihilism, most famously articulated by Friedrich Nietzsche, asserts that life has no objective meaning, purpose, or value. The "death of God" in Nietzsche’s work signifies the collapse of religious and metaphysical sources of meaning, leaving humanity in an existential void. Without a higher order dictating meaning, one might fall into existential despair. However, Nietzsche’s solution is the creation of personal values through the concept of the Übermensch, an individual who forges their own path and meaning without reliance on external validation. Teleological and Theistic Views In contrast, religious and teleological perspectives propose an intrinsic meaning to life, often rooted in divine purpose. Theistic traditions argue that meaning is bestowed upon humanity by a higher power. For example, in Christianity, the purpose of life is to fulfill God’s will, achieve salvation, and cultivate virtue. Similarly, in Aristotelian philosophy, eudaimonia, or human flourishing, is seen as the ultimate telos (end goal) of human existence, achieved through rational activity and moral virtue. Synthesis: A Constructivist Approach Given the divergence in perspectives, one might adopt a constructivist stance that synthesizes elements from each. If no inherent meaning exists, as existentialists and nihilists suggest, and if religious interpretations require faith, then meaning may best be understood as a subjective construction. Humans, as rational and reflective beings, can choose to ascribe significance to their existence based on personal values, relationships, creative endeavors, or contributions to humanity. Conclusion The meaning of life remains an open question, shaped by individual perspectives and cultural influences. Whether meaning is self-created, divinely ordained, or ultimately absent, the inquiry itself underscores a fundamental aspect of human nature: the relentless pursuit of significance. Perhaps the search for meaning is what gives life its greatest meaning.
-
 @ bd32f268:22b33966
2025-03-05 11:04:29
@ bd32f268:22b33966
2025-03-05 11:04:29Segundo a filosofia Aristotélica quando analisamos uma coisa seja ela um objecto ou um fenómeno devemos ser capazes de observar as suas causas. Podemos dizer que analisar as causas nos permite compreender com outra densidade, a origem, o significado e a finalidade das coisas.
Atualmente, estamos vetados a um reducionismo materialista quando fazemos ciência, sendo portanto nota dominante a nossa fixação na matéria como o fator primordial do conhecimento dos objetos. Ao fixarmo-nos neste aspeto perdemos muitas outras dimensões que compõe as coisas.
Atendamos então a Aristóteles e a quatro causas que este autor identifica para as coisas e fenómenos.
Segundo o filósofo grego as causas dividem-se entre: materiais (relativas ao que algo é feito), as formais (relativas ao que algo é), as eficientes/motoras (relativas ao que as produziu ou quem as produziu) e as finais ( relativas á finalidade, Télos ou para quê; ou seja o que algo visa ou “tem por fim”).
Seguindo esta teoria das quatro das quatro causas podemos descrever as condições de existência tanto de entidades estáticas como em transformação. Quer isto dizer que assim temos meios para explorar o porquê das coisas. Até conhecermos o porquê das coisas não podemos dizer que as conhecemos verdadeiramente.
Analisemos um exemplo para que fique mais claro este método de análise. Uma mesa tem como causa material a madeira que a compõe, a sua causa formal (que diz respeito à forma) é a estrutura, ou seja o seu design; a sua causa eficiente é o trabalho de carpintaria que lhe deu origem e a sua causa final é servir de suporte para as refeições.
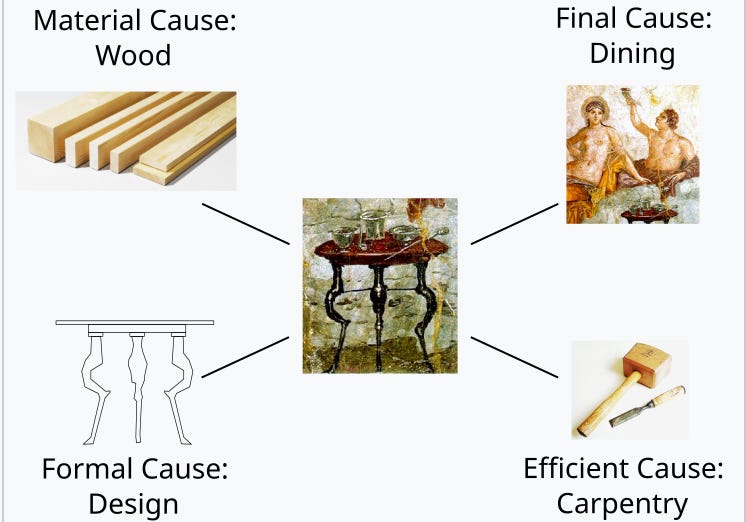 \
Destas causas destaco em particular a causa final que creio ser a que mais frequentemente induz confusão nas pessoas. De facto, o conhecimento da finalidade das coisas é fundamental inclusive para que possamos viver de forma harmoniosa com a realidade. É certo que nos podemos sentar numa mesa e jantar na cadeira, contudo automaticamente vamos perceber a desarmonia que advém dessa decisão.
\
Destas causas destaco em particular a causa final que creio ser a que mais frequentemente induz confusão nas pessoas. De facto, o conhecimento da finalidade das coisas é fundamental inclusive para que possamos viver de forma harmoniosa com a realidade. É certo que nos podemos sentar numa mesa e jantar na cadeira, contudo automaticamente vamos perceber a desarmonia que advém dessa decisão.Por vezes essa desarmonia não será tão evidente, no entanto não nos podemos esquecer que tudo o que existe tem um propósito, isto é orienta-se para um fim, cumprindo-nos agir em conformidade com a natureza das coisas para alcançar essa harmonia com a própria realidade.
São muitas as ocasiões na nossa vida que queremos de alguma forma revogar esta inclinação natural das coisas para os seus fins, que funciona também como objeto e fundamento para a lei natural. Vejamos por exemplo a forma como muitas vezes quando comemos, em vez ordenar a nossa ação pelo fim primeiro (alimentar-se) buscamos o prazer como fim primário ao qual os outros estão subordinados resultando em desordem, ou seja num apetite que não está em conformidade com o objetivo último da alimentação. Não quer isto dizer que não se possa ou deva sentir prazer ao comer, quer apenas dizer que o fim último para que existe esse ato não é o prazer, mas sim a subsistência do corpo. Com este exemplo conseguimos perceber que há uma ordenação natural nos fins para que se orientam as coisas, sendo que nessa ordenação há sempre fins primários e secundários. Sendo conscientes dessa hierarquia podemos, de uma forma mais ajustada adaptar as nossas atitudes á realidade, isto é aos preceitos da lei natural.
-
 @ a012dc82:6458a70d
2025-03-05 10:24:56
@ a012dc82:6458a70d
2025-03-05 10:24:56In the dynamic and often unpredictable realm of cryptocurrency, the actions of Bitcoin whales—investors who hold large amounts of BTC—can significantly influence market trends and investor sentiment. A recent transaction, involving the transfer of over $1.5 billion worth of Bitcoin, has once again highlighted the profound impact these entities can have on the digital currency landscape. This article delves into the details of this massive move, exploring its implications and the broader context of whale activity in the cryptocurrency market.
Table of Contents
-
The Billion-Dollar Transaction: A Deep Dive
- Other Significant Whale Movements
-
Analyzing the Impact of Whale Activity
-
Market Volatility and Speculation
-
Psychological Impact on Investors
-
-
The Role of Whales in the Cryptocurrency Ecosystem
-
Liquidity and Market Depth
-
Influence on Adoption and Perception
-
-
The Billion-Dollar Transfer in Context
-
Bitcoin's Market Position
-
Historical Whale Activity
-
-
Future Implications and the Evolving Role of Whale …
-
Regulatory Environment
-
Institutional Investors and Market Stability
-
Technological Advances and Market Monitoring
-
-
Conclusion
-
FAQs
The Billion-Dollar Transaction: A Deep Dive
On January 31st, the cryptocurrency community was abuzz with news of a monumental Bitcoin transfer. A whale moved 35,049 BTC, valued at approximately $1,518,020,170, from one unknown wallet to another. This transaction not only stood out due to its sheer size but also because it underscored the significant liquidity and wealth concentrated in the hands of a few within the Bitcoin ecosystem.
Other Significant Whale Movements
The billion-dollar transfer was part of a series of large transactions that day, which included:
-
25,266 BTC ($1,099,679,062) transferred between unknown wallets.
-
929 BTC ($39,562,024) moved from Coinbase to Gemini.
-
2,500 BTC ($106,647,312) sent to PayPal.
-
1,736 BTC ($73,943,008) transferred to Gemini.
-
34,300 BTC ($1,476,690,397) moved between unknown wallets.
These transactions, totaling around $4.5 billion, highlight the enormous sums that whales can mobilize, influencing the Bitcoin market's liquidity and volatility.
Analyzing the Impact of Whale Activity
The actions of Bitcoin whales can lead to significant market movements. Large-scale transfers and trades can signal potential sales or acquisitions, prompting widespread speculation and reactive trading among smaller investors.
Market Volatility and Speculation
The recent billion-dollar transaction has sparked intense speculation regarding the whale's motives and the potential repercussions for Bitcoin's price stability. Such movements can create uncertainty, leading to price volatility as the market reacts to perceived changes in supply and demand.
Psychological Impact on Investors
Whale activity can also have a psychological impact on retail investors. The knowledge that a single entity or group can move the market might lead to caution, fear, or even panic selling, exacerbating price fluctuations and potentially leading to market manipulation accusations.
The Role of Whales in the Cryptocurrency Ecosystem
Bitcoin whales play a crucial role in the cryptocurrency ecosystem. Their significant holdings give them considerable influence over market dynamics, liquidity, and even the adoption and perception of Bitcoin as a digital asset.
Liquidity and Market Depth
Whales contribute to market liquidity and depth by providing substantial capital. Their trades, though potentially disruptive in the short term, help create a more liquid market, enabling other investors to execute large transactions more smoothly.
Influence on Adoption and Perception
The actions of whales can influence the broader perception of Bitcoin. Significant investments or divestments by these entities can signal confidence or concern regarding Bitcoin's future, influencing the sentiment of smaller investors and the general public.
The Billion-Dollar Transfer in Context
To fully understand the implications of the billion-dollar transfer, it's essential to consider the broader context of Bitcoin's market position and the historical activity of whales.
Bitcoin's Market Position At the time of the transfer, Bitcoin was trading at $42,647, experiencing a slight decrease from its previous values. This period of relative stability makes the timing of the whale's move particularly noteworthy, as it suggests strategic positioning rather than a reaction to short-term market trends.
Historical Whale Activity
Historically, whale movements have preceded significant market movements, both bullish and bearish. By analyzing past transactions, investors attempt to predict future market directions based on whale behavior. However, the opaque nature of these entities and their motivations makes such predictions speculative at best.
Future Implications and the Evolving Role of Whales
As the cryptocurrency market matures, the role and impact of whales may evolve. Regulatory changes, the growing adoption of Bitcoin, and the entrance of institutional investors could all influence whale behavior and their impact on the market.
Regulatory Environment
Increased regulatory scrutiny could lead to more transparency in whale transactions, potentially mitigating some of the market volatility associated with these moves. However, it could also lead to more sophisticated strategies by whales to conceal their actions or to manipulate the market within legal boundaries.
Institutional Investors and Market Stability
The entrance of more institutional investors into the cryptocurrency market could dilute the relative influence of individual whales, leading to greater market stability. Institutional investors typically employ more conservative strategies and are subject to stricter regulatory oversight, which could help moderate the impact of large-scale transactions.
Technological Advances and Market Monitoring Advancements in blockchain analytics and monitoring tools are making it easier to track whale activity in real-time. This increased transparency could help demystify whale actions, allowing smaller investors to make more informed decisions and potentially leveling the playing field.
Conclusion
The recent billion-dollar Bitcoin transfer by a whale is a stark reminder of the significant influence these entities hold over the cryptocurrency market. While their actions can lead to market volatility and speculation, they also play a crucial role in providing liquidity and depth to the market. As the cryptocurrency ecosystem continues to evolve, understanding the motivations and implications of whale activity will remain a critical aspect of navigating the digital asset landscape.
FAQs
What is a Bitcoin whale? A Bitcoin whale is an individual or entity that holds a large amount of Bitcoin. These investors have enough capital to influence market movements significantly when they buy or sell large quantities of BTC.
How much Bitcoin was moved by the whale? The whale moved 35,049 BTC, which was valued at approximately $1,518,020,170 at the time of the transaction.
Where was the Bitcoin transferred? The Bitcoin was transferred from one unknown wallet to another. The identities of the parties involved and the purpose of the transfer remain undisclosed.
Were there other significant transactions on the same day? Yes, there were several other significant transactions on the same day, including transfers worth hundreds of millions and billions of dollars, contributing to a total movement of about $4.5 billion in Bitcoin by whales.
How do whale movements affect the Bitcoin market? Whale movements can lead to increased volatility in the Bitcoin market. Large transactions can signal potential sales or purchases to other traders, influencing the market price and leading to speculative trading.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnewsco
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e31e84c4:77bbabc0
2025-03-05 10:23:47
@ e31e84c4:77bbabc0
2025-03-05 10:23:47The IMF’s $1.4 Billion Shackle was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: muggyarch11@walletofsatoshi.com**
The recent $1.4 billion Extended Fund Facility (EFF) agreement between the International Monetary Fund (IMF) and El Salvador marks a significant turning point in the nation's economic and monetary policy. The IMF’s $1.4 billion “lifeline” is a sly Trojan horse, gutting El Salvador’s sovereignty and kneecapping its 2021 Bitcoin law— which represented a bold step toward monetary freedom and economic self-determination— all to prop up the same economic mess it pretends to fix. Brilliant, right?
The IMF’s Colonialist Agenda: A Historical Precedent
In 2021, El Salvador made history by adopting Bitcoin as legal tender, positioning itself at the forefront of financial innovation and offering its citizens an alternative to the U.S. dollar. This move was a bold step toward monetary independence and as a pathway toward individual financial sovereignty by reducing remittance costs for Salvadorans and bypassing the predatory international banking system. By making Bitcoin legal tender, El Salvador was taking steps to free itself from financial colonialism.
The IMF’s response to El Salvador’s Bitcoin law was predictably hostile from day one. The institution repeatedly warned of the “risks” associated with Bitcoin, framing it as a threat to financial stability rather than a tool for economic empowerment. Hypocrisy drips from every word—the IMF’s own debt traps and inflationary schemes have fueled the chaos it now “rescues” El Salvador from.
The Bretton Woods institution has long been the enforcer of the global financial elite, ensuring that nations remain shackled to the U.S. dollar-dominated system. Through predatory loans and stringent conditions, the IMF perpetuates economic subjugation. Now, facing pressure from these same institutions, El Salvador finds itself caught in the classic IMF trap: accepting loans with strings attached that further cement dependency.
This aid package isn't a solution to El Salvador's problems; it's leverage to force compliance with the global banking cartel's agenda. Under the IMF agreement, El Salvador has been compelled to amend its Bitcoin law, revoking Bitcoin's status as legal tender and making its acceptance by businesses voluntary. Additionally, tax obligations must now be settled exclusively in U.S. dollars. This gut-wrenching retreat from its bold Bitcoin rebellion represents a diabolical masterpiece of oppression—stripping citizens of financial freedom and forcing them to forever bow before the fiat gods.
Why the IMF Must Destroy Bitcoin’s Medium of Exchange Use Case
To understand why the IMF is so determined to undermine Bitcoin’s role as a medium of exchange in El Salvador, it’s important to revisit the fundamental nature of money. The widely cited “three functions” of money—medium of exchange, store of value, and unit of account—are often misunderstood. These are not rigid definitions, but empirical observations of how money functions in practice.
Money is, first and foremost, the generally accepted medium of exchange. The other functions tend to follow, but they are not exclusive to money. For example, gold can serve as a store of value but is no longer a commonly accepted medium of exchange, and other commodities can also act as units of account, but neither is money unless it is widely accepted as a medium of exchange. Bitcoin’s rise as a store of value (akin to “digital gold”) is not as threatening to the fiat system as its potential to function as a widely accepted medium of exchange. A strong store of value can exist within a system that is still dominated by fiat currencies.
If Bitcoin were to become a dominant medium of exchange, it would directly challenge the monopoly of central banks and the control that institutions like the IMF exert over global financial systems. That is why the IMF’s primary goal in El Salvador is not necessarily to stop Bitcoin’s adoption altogether but rather to strip Bitcoin of its medium of exchange function, thus effectively relegating Bitcoin to a speculative asset or store of value.
Furthermore, this Bitcoin experiment was the first real-world test of Bitcoin as a medium of exchange at the nation-state level. If it had succeeded, other countries—especially those in the Global South struggling with inflation, currency devaluation, and IMF-imposed austerity—might have followed suit. The IMF couldn't afford to let that happen. By neutralizing Bitcoin's role as money, it ensures that alternative financial systems do not gain traction outside the fiat-based global order. In other words, as long as Bitcoin can't be used freely as a medium of exchange, it cannot fulfill its role as money, and the fiat gods' grip on the global monetary system remains unchallenged—at least for now.
The $1.4 Billion Faustian Bargain
El Salvador’s decision to seek IMF funding is a reflection of the immense pressure it faces from global financial markets and institutions. The country’s high debt levels and weak external buffers are, in large part, a consequence of its integration into a global financial system that prioritizes short-term capital flows over long-term economic stability. By accepting the IMF’s terms, El Salvador has effectively traded its sovereignty for temporary financial relief.
What is even more surprising is that El Salvador had an alternative to this Faustian bargain: the issuance of Bitcoin bonds. While initially proposed as a way to finance Bitcoin City and geothermal Bitcoin mining infrastructure, the volcano bonds the country could have raised the $1.4 billion needed without sacrificing its monetary sovereignty. This represents a missed opportunity for El Salvador to bolster its financial independence, attract global capital, and solidify its position as a pioneer in the adoption of decentralized money.
Instead of falling back into the IMF’s debt trap—complete with austerity measures, restrictions on Bitcoin use, and financial surveillance—El Salvador could have embraced a Bitcoin-native financial strategy that aligned with its long-term vision of economic independence.
So why didn't El Salvador go through with the Bitcoin bond issuance? I don't know, but if I were to speculate, I would say the answer likely lies in political and institutional inertia, coupled with external pressures from the IMF and its allied institutions, or worse. If El Salvador had raised capital through Bitcoin bonds, it would have sent shockwaves through the financial world, proving that a nation-state could operate independently of the IMF.
The Long-Term Consequences for El Salvador
While the IMF’s program may provide short-term relief, its long-term consequences are likely to be detrimental to the Salvadoran people. The emphasis on fiscal consolidation and debt reduction will inevitably lead to cuts in public spending, particularly in areas such as social services and infrastructure. These measures will disproportionately affect the most vulnerable segments of society, exacerbating inequality and undermining the country’s social fabric.
Moreover, the IMF’s focus on “strengthening governance and transparency” is a thinly veiled attempt to impose external control over El Salvador’s domestic policies. The requirement to enhance Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) frameworks, while ostensibly aimed at combating illicit activities, will likely be used to surveil and restrict the financial activities of ordinary citizens. This represents a gross violation of individual rights and a further erosion of economic freedom.
Conclusion
The IMF's $1.4 billion arrangement with El Salvador represents not economic salvation but a calculated reassertion of control. By forcing El Salvador to retreat from its Bitcoin initiative, the IMF is protecting the very system that has kept developing nations financially subjugated for decades.
For Salvadorans, this means their bold experiment in monetary sovereignty has been curtailed, not by market forces or technological limitations, but by the deliberate intervention of the guardians of the old financial order.
Those who believe in true financial freedom must recognize this for what it is: not assistance, but suppression; not aid, but control. The battle for monetary sovereignty continues, and despite this setback, Bitcoin's promise of financial liberation remains as vital as ever—not just for El Salvador, but for all those seeking escape from the oppressive machinery of central banking.
The IMF’s $1.4 Billion Shackle was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: muggyarch11@walletofsatoshi.com**
-
 @ 220522c2:61e18cb4
2025-03-05 09:53:59
@ 220522c2:61e18cb4
2025-03-05 09:53:59How to package a macOS Desktop App
Introduction
Creating and distributing macOS desktop applications is a huge pain in the ass and can be very confusing. I'm writing this article as a reference for myself as well as any other developer who wants to package a desktop app for macOS.
Join the Apple Developer Program
-
Go to developer.apple.com and sign in with your Apple ID
-
Enroll in an individual ($99/year) or organization ($299/year) membership
-
Complete the enrollment process and wait for approval
Setup Xcode for some reason
-
Download Xcode from from the Mac App Store
-
Go to Xcode -> Settings -> Accounts
-
Click the "+" button and add your Apple Developer Account
Check if Xcode Command Line Tools are installed
xcode-select -pIf they are not installed for some reason you can install them with
xcode-select --installGenerate a Certificate Signing Request (CSR)
-
Open Keychain Access
-
Go to Keychain Access > Certificate Assistant > Request a Certificate From a Certificate Authority
-
Enter your email address and a common name (e.g., your name or company name)
-
Leave "CA Email Address" blank, select Saved to disk, and click Continue
-
Save the
.certSigningRequestfile somewhere
Request Certificate
-
Log in to developer.apple.com/account
-
Go to Certificates, Identifiers & Profiles > Certificates
-
Click the + button to add a new certificate
-
Under "Software," select Developer ID Application, then Continue
-
Choose G2 Sub-CA (Xcode 11.4.1 or later)
-
Upload the
.certSigningRequestfile you just created, then Continue -
Download the
.cerfile (e.g.,developerID_application.cer)
Install the Certificate
-
Double-click the downloaded
.cerfile to add it to your Keychain Access under "My Certificates" -
Verify it’s there with a private key, after selecting the cert look at the top tabs, select "My Certificates" expand the certificate to see the key icon
Sign your Application
You can now try signing your application, if you run into issues check out the troubleshooting section at the bottom of this article.
codesign --deep --force --verify --verbose --sign "Developer ID Application: Your Name (TeamID)" --options=runtime --timestamp /path/to/YourApp.appPackage Your App
Most apps distributed via websites are packaged in a
.dmg(disk image) for a polished user experience:- Use Disk Utility or a tool like
create-dmg(install via Homebrew:brew install create-dmg)
create-dmg --volname "YourApp" --app-drop-link 600 185 --window-pos 200 120 --window-size 800 400 "YourApp.dmg" /path/to/YourApp.appThis will setup the drag and drop thing for you app into the applications folder, when you run this command that drag and drop ui will pop up, ignore it.
You really should use a tool like this, if you try to do it on your own you'll need to deal with symlinks, applescript and other nonsense. I've done it this way and if there's interest I can write a part two for a more manual approach.
- Sign the
.dmg
codesign --deep --force --verify --verbose --sign "Developer ID Application: Your Name (TeamID)" --options=runtime --timestamp YourApp.dmgNotarize your App
Apple requires notarization to confirm your app isn’t malicious. You’ll need an app-specific password (not your Apple ID password)
Create and App-Specific Password:
-
Go to appleid.apple.com, sign in, and under "Sign-In and Security," select App-Specific Passwords
-
Generate a new password (name it whatever you like) and save it
Submit for Notarization
- Use the
notarytoolcommand
xcrun notarytool submit /path/to/YourApp.dmg --apple-id "your@email.com" --password "app-specific-password" --team-id "YourTeamID" --wait-
Replace placeholders with your Apple ID, the app-specific password, and your Team ID
-
The
--waitflag shows the result immediately (takes a few minutes). You’ll get a "Success" message or a log ID with issues to fix
Staple the Notarization Ticket:
- After approval, attach the notarization ticket to your
.dmg
xcrun stapler staple /path/to/YourApp.dmg- This ensures Gatekeeper can verify it offline
Upload and Distribute
-
Upload the notarized
.dmgto your GitHub or your website -
Provide a download link (preferably HTTPS for security)
-
Users might see a Gatekeeper prompt on first launch; they can right-click > Open or allow it in System Settings > Security & Privacy
Troubleshooting
I have had countless issues when trying to sign applications
Unable to build chain to self-signed root
One issue that I've run into on both of my macbooks is:
Warning: unable to build chain to self-signed root for signerSomething I usually have to do is open the Developer Certificate, expand the trust section and set "When using this certificate:" to "Use System Defaults" Then I restart my laptop once or twice and eventually it works.
Can't delete cert in GUI
I have also had an issue where I can't delete the certs in the gui, in this case run the command to list the certs:
security find-identity -v -p codesigningand delete it based on the hash in the beginning:
security delete-certificate -Z ABC123...Notarization fails
This is usually due to not passing the hardened runtime option so try resigning the app and dmg with
--options runtimeYou can use the command below to see what's wrong
xcrun notarytool log "notary id" --apple-id "your@email.com" --password "app-specific-password" --team-id "HGGSBC8HJF"Conclusion
Having an article like this would have saved me a lot of time debugging.
npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2
Posted at notestack.com
-
-
 @ fd78c37f:a0ec0833
2025-03-05 09:50:19
@ fd78c37f:a0ec0833
2025-03-05 09:50:19In this edition, we invited njump.me/npub134d6jtyveg74cuuj7qun4v2m6r7x7c6ryk69z4q7pa7f43kran2sl2yggk from Bitcoin Junior Club to share how she empowers children, teenagers, and families through Bitcoin education. She emphasizes that in the Bitcoin ecosystem, education should come before mass adoption.
YakiHonne: Şelale, thank you for being here! Before we dive into the interview questions, I'd like to introduce YakiHonne, the hosting platform for today’s discussion. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. With YakiHonne, individuals can express themselves freely, without the fear of censorship, bans, or restrictions. Today, we’ll be exploring more about your community,Şelale. So, let’s start with an introduction—could you tell us a bit about yourself and your community?
Şelale:Thank you! I'm actually a big fan of YakiHonne. Nostr is my second biggest passion, right after Bitcoin. And within this ecosystem, everything YakiHonne has done—whether empowering communities or supporting creators—looks truly incredible. I could represent many different communities, but today, I want to focus on a recent project I started together with my husband—Bitcoin Junior Club. It's a fun and educational space designed for children, teenagers, and entire families.
My Bitcoin journey dates back to around 2017 when I started diving deeper into Bitcoin. During the block size controversy. I found myself repeatedly reading the Whitepaper, trying to understand why some people were attempting to manipulate the rules and why the debate was gaining so much traction in the mass media. As I often say, the Bitcoin journey is a dynamic process—over the years, my experiences, perspectives, and areas of focus have continuously evolved. Right now, one of my key priorities are families and education. The Bitcoin ecosystem had already seen various emerging trends, such as the rise of female-oriented communities, hence the need for children related topics as well. Overall, the last few years have brought more creative minds building up their projects, which is very nice to see. A good example here would be Bitcoin FilmFest, another dynamic initiative I’m involved in. These are all signs of Bitcoin's ever-expanding and evolving landscape.
YakiHonne: I would like to know, what sparked your interest in Bitcoin? And what motivated you to create Bitcoin Junior Club? What inspired you to create a whole community around it?
Şelale:There were many different aspects that drew me to Bitcoin, but I would say the most important one is the aspect of freedom, Bitcoin is the best form of money humanity has ever had. No middlemen, no one setting the rules. For the first time, people who have always been unprivileged and unbanked now have a real alternative—a way to opt out of the system they were born into. At the same time, when we look at developed countries, we see increasing surveillance, restrictions, and privacy constraints. Once again, Bitcoin serves a crucial role here. It is freedom money, a freedom tool, and that’s what hooked me the most.
On the other hand, what truly motivated me to launch our project was the realization that money is just a tool. If people stop thinking critically, if they don’t truly understand its potential, even something as revolutionary as Bitcoin can be misused or even turned against us.
Together with my husband, we believe that education is essential, especially for younger generations. We want to help them develop critical and creative thinking skills, to keep questioning topics they come across, and to think for themselves. This is the core reason we started this community. Along the way, I’ve come across many family-friendly projects with a similar mission. But most of such resources are scattered and difficult to locate. That’s why, one of our main goals is to create a comprehensive database—a place where people can find all kinds of educational resources, from the content we produce to information about existing initiatives in areas like: homeschooling, unschooling, Bitcoin, financial education, and more.
At the heart of it all, our focus remains on fostering creativity and independent thinking, because without it, we risk heading toward a future I personally don’t want to see. In the end, our mission is to help raise sovereign generations— individuals who truly understand and embrace financial and personal freedom.
 (source: interactive game for kids and families, “Bitcoin Calendar, Part 01”)
(source: interactive game for kids and families, “Bitcoin Calendar, Part 01”)YakiHonne: Yes, absolutely! I really appreciate your recognition of Bitcoin’s freedom aspect, as that is its very core—sovereignty. I also deeply admire your dedication to educating the next generation—it’s truly essential. We need to nurture and guide these young minds so that when they step into this space, they can help maintain the stability of the Bitcoin ecosystem and safeguard the communities that have been built around it. Could you share with us how your community was founded and how you initially attracted members?
Şelale:Well, to make a long story short, it all started as a way for me to relax at night. I work on several projects within the Bitcoin ecosystem, and when I feel mentally exhausted, I like to unwind by designing and drawing. That’s how it all began—I started designing various creative worksheets, such as logic puzzles, coloring pages, and other engaging activities targeted at younger audiences.
My husband and I are also nomads, so a few years ago, we began distributing these materials to different homes during our travels. The response was overwhelmingly positive—kids were excited and, interestingly, it also turned out to be a subtle "orange pill" tool for their parents. Quite often, when they noticed the Bitcoin logo in these materials, it sparked their curiosity and triggered many questions.
At first, I simply wanted to share these resources freely with the community, allowing anyone interested to use them. Over time, I came across many other family-friendly Bitcoin-themed materials such as books, videos, and games. I wanted to create a space where these things could be seen and heard. That’s when I decided to build a website, which could be described more as a database rather than a community.
Since I’m involved in multiple projects and have limited time, I don’t want to focus entirely on building a community around Bitcoin Junior Club—at least not for now. Instead, my priority is to expand the database, continue creating creative educational materials, and connect with other family-friendly Bitcoin projects to give them extra visibility.
 (source: a snapshot from the home-page of Bitcoin Junior Club)
(source: a snapshot from the home-page of Bitcoin Junior Club)YakiHonne: What challenges did you encounter while creating this project?
Şelale:If we were to shift more towards community-building, I would say the biggest challenge lies in the diverse target audience—especially across different age groups. If you want to engage very young children, aged 2 to 3.5 years, you also need to involve their parents or mentors. If you want to reach teenagers and young adults (aged 11 to 20+), their interests, perspectives, and learning preferences are entirely different. To truly engage all these different groups, you need a wide range of tools that cater to their needs and interests. That is a significant challenge.
I’ve noticed that when people discover Bitcoin Junior Club, they often feel excited and relieved, realizing that such an initiative exists. But at the same time, it’s a fragmented process—it takes time to plant the seed and let people know, this resource is available if you or someone you know might need it.
These are the biggest challenges. But nothing to worry about. The project is naturally and organically growing, and the community will likely develop on its own over time.
 (source: Selected photos from Adopting Bitcoin El Salvador, Nov 2024, where a 2-day event for families, co-organized by Bitcoin Junior Club, was run in parallel to the entire conference)
(source: Selected photos from Adopting Bitcoin El Salvador, Nov 2024, where a 2-day event for families, co-organized by Bitcoin Junior Club, was run in parallel to the entire conference)YakiHonne: Yeah, that’s very true. The age gap and diverse target audience can indeed be a challenge for many communities. It’s a key factor to consider. However, I really admire the way you’ve been able to navigate this challenge and still effectively reach out to them despite the difficulties. That’s truly something worth recognizing.
Şelale:Thank you, that’s true. What I see here, once again, is the power of Nostr. On other social media platforms and across the Internet, there is so much noise—it’s an overwhelming space. But Nostr is different. The community is still relatively small, which means the audience is more specific and targeted. This also makes it faster and easier to understand their needs. Compared to three, four, or five years ago, this is a huge advantage when it comes to reaching specific groups and learning from them.
YakiHonne: What advice would you give to someone looking to start or grow a Bitcoin-focused community in today's landscape?
Şelale: Overall, don’t overthink it, and don’t try to build something too big from the start. Whatever you envision at the beginning will likely evolve over time. If you know your skills and have an idea that could bring value to the community, start with a high-level roadmap. Avoid over-planning—don’t try to monetize everything or map out years ahead, especially in the early stages, unless you’re working on a large-scale project in a bigger group.
Start with smaller steps and learn from the feedback. As we often say in the Bitcoin world, “don’t ask for permission, just do it”.
I would also emphasize: Learn and adapt along the way, because the feedback you receive from people is the best teacher. As I mentioned earlier, your initial idea may evolve into something different—so don’t give up, and don’t get discouraged. Just keep building. Also, especially for non-technical people, remember that contributing to the Bitcoin ecosystem isn’t just about tech. Of course, technology is at the core of our freedom-oriented future, and it’s incredibly important. But you don’t need technical skills to contribute—there are many ways to add value. It can be anything.
YakiHonne: Yes, I really love the last part of what you just said—it’s so important. Many people tend to believe that if you don’t have technical skills, you can’t contribute to the Bitcoin ecosystem, and this is a very common misconception. The more we educate people and help them understand that Bitcoin needs contributions beyond just the technical side, the stronger the community will become. It’s a crucial point and absolutely true. I’d love to know—does your community focus more on the technical or non-technical aspects of Bitcoin? Or do you cover both?
Şelale:I would say both, but more indirectly. Bitcoin Junior Club is not only a fun and educational space, but also an online resource providing a wide variety of materials, and so it naturally covers both technical and non-technical aspects. There are many excellent technical projects out there, such as those related to Lightning Network, which are more technical fields, and these can target young generations as well. Lightning Piggy is a great example to use here.
Also, during my recent time in El Salvador, I came across an amazing project, Node Nation, that teaches teenagers how to run their own Bitcoin nodes—a clearly technical-focused initiative.
In the future, if we continue to expand and place more emphasis on family-friendly gatherings in person, where practical activities are the core, the technical aspect may naturally grow as well. I have some ideas related to coding courses, interactive games, and other technical aspects that teenagers could be interested in. However, for now, our main focus remains on education and sharing existing resources with more people online. All in all, Bitcoin Junior Club is indirectly engaging with both technical and non-technical content.
YakiHonne: Sounds like a lot of work, but what you guys are doing is truly amazing. I can already see the large-scale impact this will have in the coming years. Since you are involved in the technical side as well, what advice would you give to technically inclined individuals or organizations looking to contribute meaningfully to the Bitcoin ecosystem?
Şelale:My advice would be: go out and speak up. Try to join different meetups—not necessarily large conferences, but smaller local meetups, hackathons, and co-working spaces. These environments will help you connect with others who also have technical skills. You may meet people who are already working on something related to your field, and eventually can guide you toward bigger areas of contribution. Face to face meetings are the best options to find potential collaborators, and to build something together, as well as to strengthen your skills, and to motivate you to start building on your own.
Also, don’t hesitate to share your ideas and ask questions publicly—for example, on Nostr, or through platforms like YakiHonne.
Simply, speak up, and see if anyone is working on something similar or wants to collaborate.
Most importantly, don’t be shy. Don’t isolate yourself in your own bubble. Just like creative people, technical people too, sometimes tend to stay in their own world, hesitant to step out. The truth is, it’s not that difficult to get involved—you just need to let people know you exist and what you can contribute.
YakiHonne: You know, many people tend to believe that only large conferences are worthwhile, thinking they won’t gain much from local meetups. But in reality, starting with local gatherings often leads to stronger connections. That’s a crucial point. So, my next question, Selale—how do you see the role of Bitcoin communities evolving as the technology matures, particularly in areas like scalability, privacy, and adaptability with other systems?
Şelale:What I’m about to say might be a bit of an unpopular opinion, but this is how I genuinely feel—especially in the past few years, there has been a lot of noise around mass adoption and scaling up, with a strong focus on doing things on a huge scale for everyone.
However, I believe there is a more important step before that—which is mass education and awareness. If we truly want to protect privacy and ensure the conscious use of Bitcoin, so that it remains a freedom technology, we need to prioritize education before expansion.
I hope that Bitcoin communities will become more aware of this and continue building on core values—the real Bitcoin ethos, such as truth, long-trem progress, privacy, and sovereignty, rather than just repeating hype-driven trends. I hope the community moves in this direction or, at the very least, remains strong enough to keep spreading the message of privacy and scalability as tools for freedom, rather than just chasing mass adoption and making everything overly simple.
Of course, user experience matters—I absolutely support improving UX across different areas because it’s necessary for broader adoption. However, before that, we need to raise awareness and ensure that people—whoever they are—truly understand Bitcoin’s potential along with the risks that come with losing sovereignty, overexposing personal data, and rushing into oversimplification.
For me, Proof of Work is not just about mining—it also means that understanding Bitcoin requires effort. You have to invest time, energy, and thought into learning about it. Making things too easy, too big, and too flashy isn’t necessarily something I believe in or support.
YakiHonne: Though it’s true that Bitcoin communities will play an increasingly significant role as time goes on and as the technology matures, they will also evolve in terms of scalability, privacy, and adaptability. These aspects align with the core values that most Bitcoin communities uphold, especially given Bitcoin’s decentralized nature. So, we’ve now come to our last question for today, and I must say, it’s one of my favorite questions. Is the government in your region supportive or opposed to Bitcoin? And how has that impacted the community?
Şelale:That’s an interesting question, because as a nomad, I don’t stay under the influence of any single government for long—usually not more than one to three months. We are constantly changing locations. However, we mostly stay within the European Union, and just using it as an example, with its centralized structure, it’s fundamentally opposite to what Bitcoin stands for. It operates against nation-states, encouraging people to think and act not as individuals, but as a collective.
I don’t see any direct threats or actions taken against Bitcoin Junior Club or any other communities I’m involved in. However, I do believe that the narratives pushed by certain jurisdictions can create obstacles—or, maybe on the other hand, they can actually awaken more people. These days, it has become popular among politicians to claim they are pro-Bitcoin, using it as a low-hanging fruit to gain attention. Hence, it’s hard to say whether some governments are truly pro- or anti-Bitcoin. From my personal journey I see them rather having a neutral approach, but it could change in the next few months, as supporting Bitcoin has suddenly become trendy. Probably a topic for a longer chat.
At the same time, I’ve seen areas in which ruling parties are officially anti-Bitcoin, yet people still find ways to work within the ecosystem and continue spreading the message of freedom.
YakiHonne: Just an outside the box question. Did anyone around your area or towards your community consider Bitcoin to be a scam?
Şelale:I had those experiences many years ago, in the very beginning. Currently, I’ve just consciously stopped spending time around people who hold such opinions, so I don’t see or hear it as often. ItThat said, it still happens occasionally—especially in Western countries. If I talk to someone new and they ask, “What do you do?” and I mention Bitcoin, sometimes they respond with:"Oh, that’s a Ponzi scheme." It’s very rare, but it still happens. For me, it just shows that those people are still too influenced by mainstream narratives—the same way people repeat things like "Bitcoin consumes too much energy" without fully understanding the subject. However, compared to five to ten years ago, these misconceptions have definitely become less common.
As a site note, I’ve reached a stage where instead of overwhelming others with Bitcoin-themed conversations, I prefer to keep building- i.e. working on various resources that will be easy enough to find to learn from. If somebody later wants to ask questions or debate, still doubting whether Bitcoin is good or bad for humanity, I am ready to join. All in all, instead of actively trying to convince people, I focus my energy on projects like Bitcoin Junior Club, Bitcoin Film Fest, and other initiatives that provide content for freedom-seekers at heart.
YakiHonne: Thank you so much. We've reached the end of today's interview, and it has truly been a fantastic conversation. I’ve gained a lot of valuable insights from you, and I genuinely appreciate the incredible work that you and your community are doing in the European Union. It’s truly inspiring. I’m certain that Europe is privileged to have you and your team contributing to this space.
Şelale: The pleasure is mine. Thank you very much for this conversation. Once again, kudos to all you are bullying at Yaki Honne.
-
 @ da0b9bc3:4e30a4a9
2025-03-05 07:20:21
@ da0b9bc3:4e30a4a9
2025-03-05 07:20:21Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/904251
-
 @ 1d7ff02a:d042b5be
2025-03-05 06:02:55
@ 1d7ff02a:d042b5be
2025-03-05 06:02:55ມະນຸດມີຄວາມຈະເລີນໄດ້ຍ້ອນຮູ້ຈັກສ້າງຄວາມຫມັ້ນຄົງໃນອະນາຄົດ
ມະນຸດເຮົາສ້າງຄວາມຈະເລີນຮຸ່ງຮອງໄດ້ກໍຍ້ອນການສ້າງຄວາມຫມັ້ນຄົງໃນກະນາຄົດ ເຊິ່ງສະແດງອອກຢູ່ໃນ ຈາກແຕ່ກ່ອນຕ້ອງອອກໄປ ຫາອາຫານ ລ່າສັດ ເພື່ອເປັນພະລັງງານໃນການມີຊີວິດ ຈົນຮູ້ເຮົາຮູ້ຈັກການເກັບດອງອາຫານໃຫ້ກິນຍາວນານຂຶ້ນ, ຈາການຫາອາຫານເພື່ອຕົວເອງຢ່າງດຽວ ກໍຮູ້ຈັກການແລກປ່ຽນ (barter trade) ເຮັດໃຫ້ໄດ້ສິນຄ້າທີ່ຕົວເອງຕ້ອງການ ໂດຍບໍ່ຕ້ອງໃຊ້ເວລາທັງຫມົດໄປກັບການຫາ ຫລື ຜະລິດສິ່ງນັ້ນ ແລະ ສຸດທ້າຍເຮົາກໍຮູ້ຈັກເລືອກສິນຄ້າທີ່ມີຄວາມຫມັ້ນຄົງ ແລະ ຜະລິດຍາກ ມາເປັນເງິນ ເພື່ອໃຊ້ເປັນ ສື່ກາງ ໃນການແລກປ່ຽນ ຈົນແຕ່ລະຄົນມີເວລາໃນການໂຟກັສ ພັດທະນາທັກສະທີ່ຕົວເອງສົນໃຈຈົນມີຄວາມຊຳນານກວ່າຄົນທົ່ວໄປ ເຮັດໃຫ້ສາມາດຜະລິດສິນຄ້າ ແລະ ບໍລິການ ທີ່ມີຄຸນນະພາບ ແລະ ລາຄາຖືກລົງ. ປະກົດການເຫລົ່ານີ້ເກີດຂຶ້ນໄດ້ຍ້ອນເຮົາມີຄວາມຫມັ້ນຄົງໃນອະນາຄົດດ້ວຍເງິນເກັບ ຈົນມີເວລາຈະລອງຜິດລອງຖືກໄດ້.
ແຕ່ຫລັງຈາກທີ່ເຮົາອອກຈາກ ມາດຕະຖານທອງຄຳ ກໍເຮັດໃຫ້ເງິນມັນເຊື່ອມຄ່າລົງໄປຕາມການເວລາ ຈົນເຮັດໃຫ້ຄົນເຫັນແກ່ເວລາອັນສັ້ນ, ຜະລິດສິນຄ້າ ແລະ ບໍລິການ ທີ່ບໍ່ໄດ້ຄຸນນະພາບ ເພາະຄິດແຕ່ວ່າຈະເຮັດແນວໃດເພື່ອຈະໄດ້ເງິນຫລາຍຂຶ້ນ ເພາະເງິນມັນເຊື່ອມມູນຄ່າລົງເລື່ອຍໆ ຈົນລືມຄິດໄປວ່າສິ່ງໃດແທ້ ທີ່ສຳຄັນໃນຊີວິດ ຈົນເກີດບັນຫາຕ່າງໆ ບໍ່ວ່າຈະເປັນສັງຄົມ ແລະ ເສດຖະກິດ.
ບິດຄອຍ ບໍ່ໄດ້ເຮັດໃຫ້ທ່ານລວຍໄວຂຶ້ນ ແຕ່ມັນກຳລັງແກ້ບັນຫາພື້ນຖານຢ່າງການ ເກັບເງິນ ຢູ່ ເພາະປະຈຸບັນມະນຸດເກັບເງິນບໍ່ໄດ້ແລ້ວ ເພາະມູນຄ່າຂອງມັນຫລຸດລົງເລື່ອຍໆ
ການ DCA ບິດຄອຍ

ບິດຄອຍມີຄວາມຜັນຜວນເລື່ອງລາຄາຫລາຍ ກໍຍ້ອນເຮົາເບິ່ງໃນໄລຍະສັ້ນ ແຕ່ຖ້າເຮົາເບິ່ງມັນເປັນເຄື່ອງມືເກັບອອມເຮົາຈະເຫັນຄວາມຈິງ ບິດຄອຍຄືຄວາມຫມັ້ນຄົງ ແລະ ຕໍ່ຕ້ານການເຟີ້ຂອງເງິນ. ຕົວຢ່າງລຸ່ມນີ້ເປັນການຄຳນວນວ່າ ຖ້າເຮົາເກັບບິດຄອຍ ທຸກເດືອນ ຜ່ານໄປ 8 ປີ ມັນຈະມີມູນຄ່າເພີ່ມຂຶ້ນ 617% ຫລື ປະມານປີລະ 77% ໂດຍສະເລ່ຍ ເຊິ່ງມັນກໍບໍ່ໄດ້ເປັນໂຕເລກໂອເວີຫຍັງຫລາຍ ແຕ່ສາມາດເອົາຊະນະເງິນເພີ້ໄດ້ແລ້ວ ພຽງແຕ່ເກັບ ແລະ ບໍ່ຕ້ອງຄິດຫຍັງ.
### ເມື່ອເຮົາມີເງິນເກັບທີ່ຮັກສາມູນຄ່າໄດ້ ມັນເປັນຄົນລະເລື່ອງເລີຍໃນການໃຊ້ຊີວິດ ແລະ ວິທີຄິດ
ຄົນຈະມີຄວາມຄິດການໄກຫລາຍຂຶ້ນ, ມີເວລາຄິດທົບທວນເລື່ອງຕ່າງໆໃນຊີວິດຢ່າງລະອຽດຖີ່ຖ້ວນ ແລະ ຕັດສິນໃຈແບບມີເຫດມີຜົນ. ຄົນຈະເລືອກເຮັດວຽກມີຢາກເຮັດ ເຖິງວ່າລາຍໄດ້ອາດຈະຫນ້ອຍ ແຕ່ເງິນເກັບສາມາດຮັກສາມູນຄ່າຂຶ້ນໄດ້ເລື່ອຍໆ, ເຮົາຈະມີເວລາໃຫ້ກັບຄອບຄົວຫລາຍກວ່າ ເພາະບໍ່ໄດ້ແລ່ນຕາມວຽກເພື່ອຈະໄດ້ລາຍຮັບເພີ່ມຂຶ້ນຕາມການເຊື່ອມຄ່າຂອງເງິນ. ຄົນຈະໃຫ້ຄວາມສຳຄັນກັບສຸຂະພາບຫລາຍຂຶ້ນ ເພາະສຸດທ້າຍແລ້ວເຮົາຈະເຂົ້າໃຈວ່າສຸຂະພາບນີ້ແລະ ສຳຄັນສຸດ.
ຈາກຄວາມຮູ້ສຶກຂອງຕົວຂ້ອຍເອງມັນເຮັດໃຫ້ ມີຄວາມຫວັງ ແລະ ຕື່ນເຕັ້ນທີ່ຈະໄດ້ໃຊ້ຊີວິດໄປໃນການນາຄົດ ເພາະຮູ້ສຶກວ່າມີຄວາມຫມັ້ນຄົງ ຈາກການຄ່ອຍໆເກັບ ບິດຄອຍ ໂດຍມີເປົ້າຫມາຍເຮັດແນວໃດ ຈະໄດ້ໃຊ້ເວລາທີ່ເຫລືອຢູ່ ເກັບຄົນທີ່ເຮົາຮັກ, ເຮັດສິ່ງທີ່ມັກ ແລະ ມີສຸຂະພາບດີຈົນຈາກໂລກນີ້ໄປໃຫ້ເຈັບປວດຫນ້ອຍທີ່ສຸດ.
-
 @ 401014b3:59d5476b
2025-03-05 01:39:21
@ 401014b3:59d5476b
2025-03-05 01:39:21Alright, football freaks, it’s March 2025, and we’re slinging some half-baked AFC East predictions like it’s a tailgate wing-eating contest. Free agency’s a madhouse, the draft’s a blind stab, and this division’s always a mix of fireworks and faceplants. The Bills ran the show in 2024, the Dolphins teased us, the Jets are jetting Rodgers out the door, and the Pats have a new sheriff in town. Let’s slap records on this chaos and see who’s got the cajones to take the crown. Strap in—this one’s a banger.
Buffalo Bills: 12-5 – Josh Allen’s Reign of Pain
The Bills owned the AFC East in 2024, and 2025’s looking like a victory lap. Josh Allen’s a goddamn force of nature—cannon arm, truck-stick legs—and he’s got James Cook tearing up the ground game even without a stud WR1. That O-line’s a top-10 crew, and the defense, despite some roster churn, still hits hard with Greg Rousseau leading the charge. Free agency might nibble at the edges—Matt Milano’s return could be clutch—but this squad’s a bully. 12-5’s the vibe, division locked up again. Good luck stopping ‘em.
Miami Dolphins: 9-8 – Tua’s Hot-and-Cold Hustle
The Dolphins are the AFC East’s rollercoaster—thrilling ‘til they puke. Tua Tagovailoa’s slinging to Tyreek Hill and Jaylen Waddle, but that O-line’s still a question mark, and they fold like lawn chairs in December. The defense stepped up in 2024 with Jalen Ramsey locking down receivers, but free agency could sting—Jaelan Phillips might chase a bag elsewhere. If Tua stays healthy and the core holds, 9-8’s on the table. Wildcard’s their best shot—Buffalo’s still the big brother they can’t shake.
New York Jets: 8-9 – New QB, Same Jets Jinx
The Jets are ditching Aaron Rodgers—old man’s outta here—and rolling with a new QB (TBD, but let’s say a rookie or a vet like Tyrod Taylor for kicks). Garrett Wilson and Breece Hall are studs, but that O-line’s a disaster, and the defense might take a hit if Sauce Gardner starts sniffing bigger paychecks. New coach, fresh start, same Jets curse? They’ve got enough talent to flirt with 8-9, maybe sniff a wildcard if the QB doesn’t totally tank. Still feels like classic Jets—almost there, never quite.
New England Patriots: 5-12 – Vrabel’s Rough Rebuild
The Pats are a work in progress, but Mike Vrabel’s the new head honcho, and that’s worth a damn shout. The ex-Titans tough guy’s got Drake Maye at QB—bright future, brutal present. 2025’s gonna be a grind; Maye’s taking rookie lumps behind a shaky O-line with no real weapons to speak of. Christian Gonzalez is a lockdown corner, but the defense ain’t what it was without Belichick’s wizardry. Vrabel’s a culture guy—he’ll keep ‘em scrappy—but 5-12’s the reality. They’re building, not winning, in Foxboro this year.
The Final Buzzer
The AFC East in 2025 is Buffalo’s playground with a dash of dysfunction. The Bills (12-5) snag the crown because Josh Allen’s a beast, the Dolphins (9-8) tease a wildcard, the Jets (8-9) stumble sans Rodgers, and the Pats (5-12) grit it out under Vrabel. That’s 34 wins, 34 losses—math’s tight when you factor in the division’s slugfest with the NFL’s other suckers. Free agency’s the X-factor—lose a star, you’re screwed; snag a gem, you’re golden. Yell at me on X when I botch this, but for now, this is my story, and I’m sticking to it. Let’s ride, degenerates.
-
 @ 62a6a41e:b12acb43
2025-03-04 22:19:29
@ 62a6a41e:b12acb43
2025-03-04 22:19:29War is rarely (or if ever) the will of the people. Throughout history, wars have been orchestrated by political and economic elites, while the media plays a key role in shaping public opinion. World War I is a clear example of how propaganda was used to glorify war, silence dissent, and demonize the enemy.
Today, we see similar tactics being used in the Ukrainian War. The media spreads one-sided narratives, censors alternative views, and manipulates public sentiment. This article argues that wars are decided from the top, and media is used to justify them.
How the Media Glorified and Propagated WW1
The Media Sold War as an Adventure
Before WW1, newspapers and propaganda made war seem noble and exciting. Young men were encouraged to enlist for honor and glory. Posters displayed slogans like “Your Country Needs You”, making war look like a duty rather than a tragedy.
Demonization of the Enemy
Governments and media portrayed Germans as "barbaric Huns," spreading exaggerated stories like the "Rape of Belgium," where German soldiers were accused of horrific war crimes—many later proven false. Today, Russia is painted as purely evil, while NATO’s role and Ukraine’s internal conflicts are ignored.
Social Pressure & Nationalism
Anyone who opposed WW1 was labeled a traitor. Conscientious objectors were shamed, jailed, or even executed. The same happens today—if you question support for Ukraine, you are called "pro-Russian" or "anti-European." In the U.S., opposing war is falsely linked to supporting Trump or extremism.
Fabricated Stories
During WW1, fake reports of German soldiers killing babies were widely spread. In Ukraine, reports of massacres and war crimes often circulate without verification, while Ukrainian war crimes receive little coverage.
How the Media Promotes War Today: The Case of Ukraine
One-Sided Narratives
The media presents Ukraine as a heroic struggle against an evil invader, ignoring the 2014 coup, the Donbas conflict, and NATO expansion. By simplifying the issue, people are discouraged from questioning the full story.
Censorship and Suppression of Dissent
During WW1, anti-war activists were jailed. Today, journalists and commentators questioning NATO’s role face censorship, deplatforming, or cancellation.
Selective Coverage
Media highlights civilian deaths in Ukraine but ignores similar suffering in Yemen, Syria, or Palestine. Coverage depends on political interests, not humanitarian concern.
Glorification of War Efforts
Ukrainian soldiers—even extremist groups—are painted as heroes. Meanwhile, peace negotiations and diplomatic efforts receive little attention.
War is a Top-Down Decision, Not the Will of the People
People Don’t Want Wars
If given a choice, most people would reject war. Examples:
- Before WW1: Many workers and socialists opposed war, but governments ignored them.
- Vietnam War: Protests grew, but the war continued.
- Iraq War (2003): Millions protested, yet the invasion went ahead.
Small Elites Decide War
Wars benefit arms manufacturers, politicians, and corporate interests—not ordinary people. Public opposition is often ignored or crushed.
Manipulation Through Fear
Governments use fear to justify war: “If we don’t act now, it will be too late.” This tactic was used in WW1, the Iraq War, and is used today in Ukraine.
Violence vs. War: A Manufactured Conflict
Violence Happens, But War is Manufactured
Conflicts and disputes are natural, but large-scale war is deliberately planned using propaganda and logistical preparation.
War Requires Justification
If war were natural, why does it need massive media campaigns to convince people to fight? Just like in WW1, today’s wars rely on media narratives to gain support.
The Crimea Referendum: A Case of Ignored Democracy
Crimea’s 2014 Referendum
- Over 90% of Crimeans voted to join Russia in 2014.
- Western governments called it "illegitimate," while similar referendums (like in Kosovo) were accepted.
The Contradiction in Democracy
- If democracy is sacred, why ignore a clear vote in Crimea?
- Other examples: Brexit was resisted, Catalonia’s referendum was shut down, and peace referendums were dismissed when they didn’t fit political interests.
- Democracy is used as a tool when convenient.
VII. The Libertarian Case Against War
The Non-Aggression Principle (NAP)
Libertarianism is fundamentally opposed to war because it violates the Non-Aggression Principle (NAP)—the idea that no person or institution has the right to initiate force against another. War, by its very nature, is the ultimate violation of the NAP, as it involves mass killing, destruction, and theft under the guise of national interest.
War is State Aggression
- Governments wage wars, not individuals. No private citizen would naturally start a conflict with another country.
- The state forces people to fund wars through taxation, violating their economic freedom.
- Conscription, used in many wars, is nothing more than state-sponsored slavery, forcing individuals to fight and die for political goals they may not support.
War Creates Bigger Government
- War expands state power, eroding civil liberties (e.g., WW1's Espionage Act, the Patriot Act after 9/11).
- The military-industrial complex grows richer while taxpayers foot the bill.
- Emergency powers granted during wars rarely get repealed after conflicts end, leaving citizens with fewer freedoms.
Peaceful Trade vs. War
- Libertarians advocate for free trade as a means of cooperation. Countries that trade are less likely to go to war.
- Wars destroy wealth and infrastructure, while peaceful trade increases prosperity for all.
- Many wars have been fought not for defense, but for economic interests, such as securing oil, resources, or geopolitical power.
Who Benefits from War?
- Not the people, who suffer death, destruction, and economic hardship.
- Not small businesses or workers, who bear the burden of inflation and taxes to fund wars.
- Not individual liberty, as war leads to greater state control and surveillance.
- Only the elites, including defense contractors, politicians, and bankers, who profit from war and use it to consolidate power.
Conclusion: The Media’s Role in War is Crucial
Wars don’t happen naturally—they are carefully planned and sold to the public using propaganda, fear, and nationalism.
- WW1 and Ukraine prove that media is key to war-making.
- The media silences peace efforts and glorifies conflict.
- If people truly had a choice, most wars would never happen.
To resist this, we must recognize how we are manipulated and reject the forced narratives that push us toward war.
-
 @ 3c7dc2c5:805642a8
2025-03-04 22:04:22
@ 3c7dc2c5:805642a8
2025-03-04 22:04:22🧠Quote(s) of the week:
Bitcoin adoption: 1. Slow enough to confuse nearly everyone. 2. Fast enough to change your life if you can just stay focused for 4 years. Do you notice the higher your intellect grows (thanks to Bitcoin) the more unsocial you become, In real life. Or it's just me?
'First companies will add Bitcoin to their balance sheets. Then states will buy for their treasuries. And finally, sovereigns will hold it as a strategic asset. A natural progression that is already underway.' - James Lavish
🧡Bitcoin news🧡
After last week's dip, I want to share the following quote and picture. Just to keep you sharp & focused.
SAIFEDEAN AMMOUS: "If you think in years, dips are opportunities—not problems. Zoom out."
Bitcoin for Freedom: 'The Bitcoin dip is the best test to check if you understand Bitcoin. If you feel bad when it dips you don’t understand it. When you understand Bitcoin the fiat value doesn’t affect you and you have FOMO all the time.'
On the 25th of February:
➡️REKT! $1.5 BILLION leveraged crypto positions liquidated in 24 hours as Bitcoin plunges below $87,000. Bitcoin is down ~$20K from its all-time high of $109,354. $755.59 million was liquidated from the BTC perpetual futures market in the past 24 hours.
Just know for now Bitcoin is still following (with a 2-3 month lag) global liquidity.
M2 is a measure of liquidity and has been declining since December, but has recently begun to inflect back up again.
If history repeats the Bitcoin dip will soon come to an end and the recovery will be violent.
Oh, and just one more thing on this topic: 'M2 money supply growth per cycle:
2013 cycle: +26%
2017 cycle: +22%
2021 cycle: +49%
2025 cycle: +0.5%
We’ve seen this entire bull market happen with no new money in circulation.' - Bitcoin Isaiah
➡️Rep. Logan Manhart's bill, which aimed to establish a Bitcoin strategic reserver in South Dakota, failed in committee by a vote of 9-3. Manhart plans to reintroduce the bill next year.
➡️'Metaplanet has raised ~$47 million in equity at a market in the first four trading days of its “21m Plan,” with 5.54% of the plan completed to date.' - Dylan LeClair Metaplanet has purchased an additional 135 Bitcoin.
➡️'Germany’s €370 BILLION DekaBank is launching Bitcoin and crypto trading + custody for institutions. Their government sells BTC. Their citizens stack it.' - Bitcoin Archive
➡️At the end of the Weekly Recap, I always share a little gift, a podcast, an article, a report, or a newsletter. This week a report by River. Excellent report. Please give it a read. This is the most important graph in the entire document IMO; we're just getting started:
➡️'31% of Australians have owned BTC or crypto, an all-time-high in adoption, per IRCI '25. 42.9% anticipate widespread future adoption, though 14.3% cite economic and regulatory concerns for not investing. 1 in 5 investors reported banking transaction delays or blocks.' - Bitcoin News
➡️'For years, Bitcoiners pushed exchanges to adopt Lightning. And guess what? It worked. Public Lightning volume is up 266% in about a year.' -Sam Wouters
➡️The Bybit hackers are bridging their stolen ETH to Bitcoin.
➡️ America’s largest publicly traded Bitcoin mining company, Mara, just acquired this 114-megawatt wind farm in Hansford County, Texas.
➡️ 'MicroStrategy has $8.2B debt against $43.4B of BTC. A leverage ratio of ~19%. Only $5B of CBs are below their conversion price, so the effective leverage ratio is more like ~11.5%. BTC would have to drop 80%-90% for MSTR to become insolvent. And none of this debt matures until 2028...' - Bitcoin Overflow
On the 26th of February:
➡️'The IMF today sent out a press release that says as per their agreement with El Salvador, "program commitments will confine" government purchases of bitcoin. This is the first time I've seen El Salvador's bitcoin reserve being implicated in the $1.4bn IMF deal.' - Pleditor
➡️'Unless bitcoin rebounds soon, it looks like the 4-year CAGR could dip below 10% for the first time ever.' - Wicked
➡️'This is currently who is selling. Short-term holders who bought the top are selling spot Bitcoin, this isn't leverage-driven, and perps aren't negative.
That is why equities such as MSTR are green, they must have bottomed out or close to it.
Just your old fashioned fire sale, in BTC.' - James van Straten
More than 74% of realized Bitcoin losses came from holders who bought in the last month! Only the educated survive.
➡️Publicly traded Fold Holdings buys an additional 10 Bitcoins for $875,000.
➡️SEC closes its inquiry into Gemini without enforcement after a 699-day investigation. Cameron Winklevoss calls for accountability, suggesting agencies reimburse legal costs for investigations lacking clear guidelines.
On the 28th of February:
➡️Matthew Sigel:
List of Bitcoin corrections in the run-up to $20k in 2017:
-41%
-38%
-29%
-34%
-41%
-40%
-27%
List of Bitcoin corrections in the run-up to $69k in 2021:
-21%
-17%
-31%
-26%
-55% (!!)
-25%
➡️BlackRock adds its own Bitcoin ETF into its $150 BILLION model-portfolio universe - Bloomberg While Bitcoin is facing short-term pressure from economic fears as weak-ass paper hands are folding, long-term institutional adoption keeps rising.
On the 1st of March:
➡️ Bitcoin dominance back above 61%.
➡️'Bitcoin mining/energy convergence spotted. Petrobras (Brazil) just started mining Bitcoin using flare gas (reduces methane emissions) They join oil companies already mining Bitcoin: Tecpetrol, YPF, Plus Petrol (Argentina), Gazpromneft (Russia), ExxonMobil & ConocoPhillips (US).' - Daniel Batten
On the 2nd of March:
➡️President Trump has officially announced the US Strategic Crypto Reserve and Bitcoin is back above $94,000. In just 3 hours, crypto markets have now added over +$300 BILLION in market cap on the news.
And you can't make this shit up. I couldn't agree more with Peter Schiff: "Bitcoin is digital gold, which is better than analog gold. So let's create a Bitcoin reserve...", "But what's the rationale for an XRP reserve? Why the hell would we need that?"
Trump pumped and dumped a meme coin on the eve of his presidency. Of course, he wants shitcoins, XRP, SOL, and ADA, in the strategic reserve. This is basically all of our journeys from Bitcoin to shitcoins, back to Bitcoin, but on a national scale.
Even Brian Armstrong, CEO of the biggest shitcoin casino in the world, Coinbase, thinks the Reserve should be Bitcoin only.
Luke Broyles:
'My prediction: 1) Trump makes crypto reserve. 2) Reserve pumps all assets. 3) Retail and some companies get burnt in said pump. 4) Public outcry to crypto reserve along with other critiques of the Trump administration. 5) Crypto reserve is dumped in the next bear market. Massive downwards narrative catalyst. Back to no Bitcoin. 6) The government figures out the importance of Bitcoin PoW and goes BTC only soon afterward. 7) Other nations follow suit over years'
Seems legit. Please read the following post by Parker Lewis:
https://x.com/parkeralewis/status/1895550178184110217
“Bitcoin is the first form of money to ever exist that is also a currency.”
It is both a protocol and network, as the currency is embedded within the code, and validated by the network.
On the 3rd of March:
➡️Metaplanet has acquired 156 BTC for ~$13.4 million at ~$85,890 per bitcoin and has achieved a BTC Yield of 31.8% YTD 2025. As of 3/3/2025, we hold 2391 Bitcoin acquired for ~$196.3 million at ~82,100 per Bitcoin.
➡️Fidelity has bought $142.08 million Bitcoin for its ETF.
➡️Vietnam's Prime Minister has directed the Central Bank and Finance Ministry to draft a Digital Assets Framework by March.
➡️BlackRock’s model advisor team releases new Bitcoin report Key takeaways from “Why Bitcoin? A Perspective from Model Portfolio Builders”: • Bitcoin as a novel store of value and global monetary alternative • Hedge against USD hegemony and political instability • A play on the shift from offline to online commerce • Boosted by boomer-to-millennial wealth transfer • Potential for diversification and unique risk premia in portfolios • Intrinsic value expected to be increasingly recognized worldwide • Relevance grows in a debt-laden, digital-first, AI-entrenched world
➡️Meanwhile Ray Dalio tells Bloomberg that Bitcoin could be "a big part" of the restructuring of the global debt-based monetary system. Gold and Bitcoin are "store holds of wealth".
💸Traditional Finance / Macro:
On the 26th of February:
👉🏽Nvidia stock soars after posting record quarterly revenue of $39.3 billion, above expectations of $38.0 billion.
🏦Banks:
👉🏽 no news
🌎Macro/Geopolitics:
On the 24th of February:
👉🏽'US CPI inflation is on track to hit 4.6% over the next 6 months, according to Bank of America. CPI inflation has averaged +0.4% on a month-over-month basis over the last 3 months. If this trend continues, this puts year-over-year inflation on pace to hit 4.6% by July, the highest since April 2023. That would be more than DOUBLE the Fed’s 2% inflation target. Even if monthly inflation prints ease to 0.3%, year-over-year inflation would still rise to 3.8%. Inflation is accelerating.' - TKL
On the 25th of February:
👉🏽After the ECB's massive losses, now Germany’s Central Bank. The Bundesbank reports a €19.2 billion loss for 2024—the first loss since 1979 and the largest in its history. It's not a good time for Central Bankers. Accountability anyone? 'This loss is primarily attributed to the sharp increase in interest rates initiated by the ECB since the summer of 2022 to combat high inflation. This led to higher interest expenses for the Bundesbank, as it had to pay more on deposits held by commercial banks.
In 2023, the Bundesbank offset a loss of €21.6 billion by fully releasing its provision for general risk and drawing from other reserves. However, by the end of 2024, only €0.7 billion in reserves remained available, insufficient to cover the year's losses. This resulted in an accumulated loss of €19.2 billion, which will be carried forward to 2025.' - Wyatt J. Prescott
👉🏽 A typical politician, says one thing to get elected and does another, no wonder people are losing trust in the system. Leader of the CDU Friedrich Merz just completely went back on what was said during the election and announced that there will be NO TALK of shutting the borders to those without valid documentation.
"I want to say it very clearly again. None of us will talk about border closures, no one, although this was claimed at times during the election campaign, none of us want to close the borders"
Grok has fact-checked this. Merz DID say this during the election and has now reneged on it only ONE DAY after the election.
👉🏽'G-7 Debt/GDP forecast, we are entering a new era, it would be really naive to assume positive real interest rates as we go forward. Position your long-term investments and wealth protection accordingly.' -Michael A. Arouet
On the 26th of February:
👉🏽'Germany, where consumer sentiment has worsened again due to the weak labor market figures. The GfK Consumer Confidence Index dropped from -22.6 to -24.7, its lowest level since Apr 2024. Economists polled by Bloomberg had predicted an improvement to -21.6. This adds more pressure on the CDU/CSU and SPD to form a govt quickly and restore confidence in the economy.' - Holger Zschaepitz
👉🏽The US government spent $710 billion in the first month of the Trump presidency, up from $630 billion in the same period a year ago - Analysis
Funny how inflation works innit? And you still believe the 2% or 3% CPI?
On the 27th of February:
👉🏽U.S. Credit Card Defaults soared to $46 Billion, the most since the aftermath of the Global Financial Crisis.
On the 28th of February:
👉🏽Treasury Secretary Scott Bessent was just questioned if we're in a recession. "We're seeing the hangover from the excess spending in the Biden 4 years. In 6 to 12 months, it becomes Trump's economy." Translation: They want the market to crash soon.
Great quote on this topic: 'It would be in their best interest to let it crash. If they implement QE, we will see massive inflation. It's better to get it out prior to the midterms and then implement QE and buy the midterms. At least that's what I would do.
On the 1st of March:
👉🏽The White House announces that President Trump will host and speak at the first-ever White House Crypto Summit on March 7. The event will bring together top crypto founders, CEOs, investors, and members of the President’s Working Group on Digital Assets.
European victory plan: 1) Destroy gas supplies coming from Russia 2) Destroy the relationship with Russia 3) Make yourself dependent on US gas supplies 4) Destroy the relationship with the USA 5) Give all your money to Ukraine 6) … 7) Victory
👉🏽CarlBMenger: US national debt:
Feb 28, 2025: $36.5 trillion
Feb 28, 2024: $34.3 trillion
Feb 28, 2023: $31.6 trillion
Nothing is going to stop this train.
“National debt is immoral and destructive, silently undermining the basis of the state; it delivers the present generation to the execration of posterity.” - Napoleon
👉🏽Italy’s government has approved a law to restart nuclear power, nearly 4 decades after a 1987 referendum shut it down.
PM Meloni: "The government has approved another important measure to ensure clean, safe, low-cost energy that can guarantee energy security and strategic independence." If nuclear reaches 11% of the energy mix, Italy could save €17 billion in decarbonization costs by 2050. Source: Reuters
👉🏽Gold funds see record weekly inflows. Investors poured a staggering $4.7 billion into gold funds this week, marking an all-time high.
On the 2nd of March:
👉🏽For the Dutch / EU readers amongst my followers: 'This chart always shocks me when I see it. Major European countries have unfunded pension obligations of 400 to 500% of GDP. Combined with collapsing demographics it’s a recipe for disaster. Who is supposed to pay for these pensions? - Michael A. Aouret
Got Bitcoin?
👉🏽'How bad has the US debt crisis become? US net interest payments as a percentage of federal revenue reached a whopping 18.7% in January, the highest since the 1990s. This is just 20 basis points below the all-time high of 18.9% posted in 1992. Furthermore, this share has DOUBLED in just 18 months as interest costs have skyrocketed. Interest expense hit a record $1.2 trillion over the last 12 months and is the second-largest government outlay after Social Security.
The worst part? Net interest costs as a percentage of federal revenues are estimated to reach 34% by 2054, assuming there will be no recession over this period.' - TKL
👉🏽ARGENTINA'S ECONOMY SURGES—MILEI'S POLICIES DRIVE 7.1% GDP GROWTH PROJECTION
GDP is expected to grow 7.1% interannually in Q2 2025. After a tough 2024, Milei’s austerity measures and economic freedom reforms are restoring confidence—just in time for the 2025 electoral cycle. Milei’s bold strategy is proving to be the right call.
Source: Ramiro Castiñeira
👉🏽French President Emmanuel Macron today urged EU member states to agree on "massive, common funding" (ERGO: lending) to unlock investments of hundreds of billions of euros for European defense and security. Source: Politico Jippieee more debt, and who the F will be paying for all that?
On the 3rd of February:
👉🏽Dutch inflation rose to 3,8% in February.
👉🏽Gold prices surge back above $2,900 as volatility rises and geopolitical tensions escalate.
🎁If you have made it this far I would like to give you a little gift:
What’s Driving Bitcoin Adoption in 2025?
Trust in Bitcoin has grown faster than that of any asset in history. While bitcoin is a form of money, its rate of growth mirrors that of the internet. River's new report is a deep dive into Bitcoin adoption. In this report: - Why this bull market is different - The current state of the Bitcoin protocol, network, and monetary system - Deep dives on institutional, business, & nation-state adoption - A fresh look at Lightning Network's growth - Why Bitcoin adoption is still very early
You can find the report here: https://blog.river.com/bitcoin-adoption-2025/
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 6e0ea5d6:0327f353
2025-03-04 20:02:47
@ 6e0ea5d6:0327f353
2025-03-04 20:02:47The recipe for the downfall of a relationship is quite simple: marry someone with whom you have nothing in common.
The exotic tends to be attractive, but how many times, in a fine restaurant, has a customer discreetly spat into a napkin what they had just chewed because the eye-catching appearance betrayed them with an unbearable taste?
At the end of a hard day or a week of good results, we simply want to recline in a chair and celebrate in our own way what we have overcome. In the high phase of life, when the days are ripe for harvest, this desire will manifest with even greater intensity. And when your prosperity extends into the shade, and the days grow longer due to idleness, what will the two of you have to talk about?
Will your mentalities align?
Or will this person nestle on your shoulder and pour out a history of degeneration, drinking, parties, and casual relationships, because that is their only life experience?
I do not speak only in the professional sense, but of progress as a whole: when you have overcome your flaws, will you want to share your life with someone who nurtures theirs and takes their own ego as a lover?
Some are lucky to meet during the journey—a great privilege. But in general, the busy ones find each other after the work is done, and it is natural for both to want to enjoy in this peaceful phase what their efforts have granted them. At that moment, being beside someone whose travels or experiences are fresh and well-earned as rewards for their own sacrifices contrasts with sharing life with someone who has already been through it countless times, with the merit of a parasite.
Opportunists and freeloaders exist on both sides. Do not take by the hand someone who is merely waiting for a winner at the finish line. It is easy to appear clean and unscarred when one has not run even a kilometer. Do not be unfair to your lifelong efforts; find someone who represents you in determination, ethics, and principles, and you will multiply your fruits here on Earth. Also, remember that old piece of advice: "be what you seek to have," so that your future demands are not those of a hypocrite.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 000002de:c05780a7
2025-03-04 19:27:34
@ 000002de:c05780a7
2025-03-04 19:27:34I was reminded of this comic this morning. Very relevant to this day.
The losers suddenly fear the government. Or rather the current administration. Those that used to fear the government falsely believe they can wield it to do "good". This is an illusion. Like the Ring of Power it has no master. The only winner is the state. It grows more powerful.
originally posted at https://stacker.news/items/903795
-
 @ e968e50b:db2a803a
2025-03-04 19:00:20
@ e968e50b:db2a803a
2025-03-04 19:00:20your tombstone - 1000 sats - the player will run into it along the trail just like the original game, your nym from stacker.news will be featured and I might write you an epitaph
your tombstone with baller epitaph - 5000 sats - same thing, but I promise to put some time into writing your epitaph and you can make some requests about it
Just shoot me a dm with the amount of sats and your requested epitaph if it applies.
https://thebitcointrail.space/
originally posted at https://stacker.news/items/903776
-
 @ e968e50b:db2a803a
2025-03-04 18:34:23
@ e968e50b:db2a803a
2025-03-04 18:34:23Spoiler Alert
Please do not read this post if you have not read The Three Body Problem or The Dark Forest by Liu Cixin and ever intend to.
Now that you've been warned...
I just finally finished The Dark Forest, the middle book of the three body trilogy. Boy howdy!!! How cool were those last 50 pages!?
So, there's much to discuss for bitcoiners concerning the parallel between the dark forest and the byzantine generals' dilemma, but, for now, can we just talk about the ultra-brief mention of lasers in that chaotic part after the destruction of Starship Earth?
If I got it right, in that era, the general population possesses en masse handgun style lasers. These lasers are powerful enough for self defense, but individually, not powerful enough to take down a spaceship trying to launch. HOWEVER, and this is the cool part, all together they CAN take down a spaceship because...you know, how lasers work and stuff. They compound their energy together or something like that. Correct me here science nerds.
like this, but with lasers, right?
What an interesting, but basically-just-mentioned-in-passing idea! I feel like the implications of this could have been fleshed out a whole lot more, although I can see how it was just a creative idea he came up with to serve a totally different story.
Anyway, it reminded me of bitcoin...but violent. I've long had an idea in the back of my head for a fantasy story in which the magic system is decentralized, but Cixin Liu came up with a really great sci-fi equivalent here. I wonder if some creative storyteller might want to jump on a similar idea?
...and yeah, I know, a WAY bigger discussion could be had about how the dark forest and the byzantine generals' dilemma are similar and the implication that a bitcoiny response could shed light in the dark forest. I just think this whole laser thing is more of a cool parallel right now.
originally posted at https://stacker.news/items/903753
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ a012dc82:6458a70d
2025-03-04 16:16:12
@ a012dc82:6458a70d
2025-03-04 16:16:12Argentina's financial landscape is taking a significant turn with the adoption of Bitcoin for rental payments, an innovative move reflecting the country's openness to digital currencies. This pioneering transaction not only serves as a testament to Argentina's adaptability in the face of economic fluctuations but also marks a pivotal shift towards a more inclusive financial system. Amidst the backdrop of inflationary pressures and currency devaluation, cryptocurrencies offer a semblance of stability and reliability, enticing Argentinians to look towards digital solutions for everyday transactions. The use of Bitcoin in real estate transactions symbolizes a broader acceptance of digital currencies, challenging traditional banking paradigms and showcasing the potential for a digital economy. This event is not just a milestone for Argentina but also a beacon for countries worldwide grappling with similar economic challenges, demonstrating the viability of cryptocurrencies as a medium of exchange. By embracing Bitcoin for such a critical aspect of daily life—rental payments—Argentina is setting a precedent, illustrating the practical applications of digital currencies beyond speculative investments. This movement towards digital currency adoption is fostering a new era of financial inclusivity, where access to banking and financial services is no longer hindered by traditional barriers, offering a glimmer of hope for a more democratized financial future.
Table of Contents
-
The Historic Bitcoin Rental Transaction
-
Impact on Real Estate and Financial Transactions
-
Challenges and Opportunities Ahead
-
The Future of Cryptocurrencies in Argentina
-
Conclusion
-
FAQs
The Historic Bitcoin Rental Transaction
The transaction facilitated by Fiwind marks a watershed moment for Argentina, showcasing the tangible application of Bitcoin in the real estate market. This isn't merely about the novelty of using digital currency for rent but a reflection of a deeper shift towards digital transformation in financial dealings. The choice of Bitcoin, equivalent to 100 USDT, for this transaction, underscores the growing confidence in cryptocurrencies as a stable and viable alternative to fiat currencies, even in the face of their notorious volatility. This event highlights the synergies between blockchain technology and real estate transactions, pointing towards a future where such digital transactions could become the norm rather than the exception. The role of Fiwind in this transaction is emblematic of the critical role fintech companies are playing in bridging the gap between traditional financial services and the emerging digital economy. Through this pioneering payment, Argentina is not just experimenting with new technology but also laying the groundwork for a financial ecosystem that is more adaptable, secure, and inclusive. The successful execution of this rental payment using Bitcoin paves the way for further innovation in the sector, encouraging other players in the real estate market to explore the benefits of cryptocurrency transactions. This could lead to a ripple effect, where the acceptance and use of digital currencies become widespread, transforming the way financial transactions are conducted across the board.
Impact on Real Estate and Financial Transactions
The introduction of Bitcoin payments in the real estate sector is not just a one-off event but a sign of the evolving landscape of financial transactions in Argentina and globally. This development has the potential to catalyze a significant shift in how transactions are conducted, moving away from traditional, cumbersome processes to more streamlined, digital-first approaches. The benefits of using cryptocurrencies for real estate transactions extend beyond the immediate convenience and security—they represent a fundamental change in the perception and utilization of digital currencies in substantial financial dealings. The blockchain technology underlying Bitcoin transactions offers unparalleled transparency and security, mitigating many of the risks associated with traditional real estate transactions, such as fraud and delays in payment processing. Moreover, this shift towards digital currencies can greatly enhance the accessibility of real estate markets, removing barriers for international investors and simplifying cross-border transactions. As Argentina explores the full potential of cryptocurrencies in real estate, it sets a precedent for other sectors to follow suit, potentially revolutionizing payment and investment models across the economy. This could lead to greater efficiency, reduced costs, and a more inclusive market, where anyone with access to digital currencies can participate without the need for traditional banking infrastructure. The impact of this development could extend far beyond the real estate sector, influencing how businesses and individuals alike think about and engage with the financial system.
Challenges and Opportunities Ahead
While the adoption of Bitcoin for rental payments in Argentina opens up new avenues for the use of digital currencies, it also brings to light several challenges that need to be addressed. Regulatory uncertainty remains one of the biggest hurdles, as governments and financial institutions grapple with how to integrate cryptocurrencies within existing legal and financial frameworks. The volatile nature of digital currencies adds another layer of complexity, raising questions about valuation, taxation, and consumer protection. Despite these challenges, the opportunities presented by the broader adoption of cryptocurrencies are immense. They offer the potential for a more efficient and transparent financial system, reduced transaction costs, and increased access to financial services for underserved populations. Moreover, the adoption of digital currencies can spur innovation in financial technologies, encouraging the development of new tools and services that enhance the security and efficiency of transactions. As Argentina navigates these challenges and opportunities, it can serve as a valuable case study for other countries considering the role of digital currencies in their economies. By addressing regulatory and volatility concerns, Argentina can pave the way for a more stable and inclusive financial ecosystem, where cryptocurrencies play a significant role in everyday transactions. This journey towards cryptocurrency adoption is not without its obstacles, but the potential benefits for economic inclusivity, efficiency, and innovation make it a venture worth pursuing.
The Future of Cryptocurrencies in Argentina
The successful rental payment in Bitcoin is more than a novelty; it's a harbinger of the potential future role of digital currencies in Argentina's economy. As the country continues to explore the possibilities of cryptocurrencies, we can expect to see an expansion in their use across various sectors, from retail to services and beyond. This could dramatically transform the payment landscape, making digital currencies a common feature of everyday transactions. The implications of such a shift are profound, offering the possibility of a more inclusive financial system that transcends the limitations of traditional banking. However, the journey towards widespread adoption of cryptocurrencies is contingent on several factors, including technological advancements, regulatory clarity, and societal acceptance. As Argentina navigates these factors, it could emerge as a leader in the adoption of digital currencies, setting a benchmark for other nations. The potential for cryptocurrencies to improve efficiency, reduce transaction costs, and enhance financial inclusion is significant, suggesting a bright future for their role in Argentina's economy. This evolution towards a digital-first financial landscape represents a significant leap forward, promising a more accessible, secure, and efficient way of conducting transactions for all Argentinians.
Conclusion
The integration of Bitcoin into Argentina's rental market is a significant milestone, highlighting the growing acceptance and potential of cryptocurrencies to redefine traditional financial systems. This development is not just about the adoption of a new payment method but reflects a broader shift towards digital innovation and economic reform. As Argentina continues to embrace cryptocurrencies, it contributes to the global conversation on the future of finance, demonstrating the practical benefits and challenges of digital currencies. The journey of cryptocurrencies from niche investment to mainstream payment option is fraught with hurdles, but the opportunities they present for economic reform and innovation are unparalleled. As we reflect on Argentina's experience, it's clear that the role of cryptocurrencies in the global financial system is only set to grow, promising a future where digital transactions are the norm, offering greater accessibility, security, and efficiency. The adoption of Bitcoin for rentals in Argentina is just the beginning, paving the way for a future where cryptocurrencies play a central role in our financial lives, transforming how we think about and engage with money.
FAQs
What is the significance of Argentina embracing Bitcoin for rentals? Argentina's adoption of Bitcoin for rentals marks a milestone in the country's financial landscape, highlighting its progressive approach to digital currencies.
How was the historic Bitcoin rental transaction in Argentina facilitated? The transaction was made possible by Fiwind and involved a rental payment in Bitcoin, equivalent to 100 USDT.
What impact does this development have on real estate and financial transactions in Argentina? It opens new avenues for faster, more secure, and accessible payment methods in real estate, potentially transforming financial transactions across various sectors.
What challenges and opportunities are associated with cryptocurrency adoption in Argentina? Challenges include regulatory issues and cryptocurrency volatility, while opportunities include a more efficient and inclusive financial system.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 378562cd:a6fc6773
2025-03-04 15:01:35
@ 378562cd:a6fc6773
2025-03-04 15:01:35In a world filled with uncertainty, confusion, and competing worldviews, it is easy to feel lost. Society bombards us with messages about identity, morality, and purpose that often shift with cultural trends. However, for those who turn to the Bible, a firm foundation for understanding life’s complexities can be found. Through Scripture, we gain clarity about the nature of the world, our purpose within it, and the ultimate hope that transcends its troubles.
A World in Chaos—But Not Without Order
The world can often feel like a place of chaos and suffering. Wars rage, injustices abound, and personal struggles weigh heavily on the human heart. But when we view the world through the lens of the Bible, we see that disorder is not without explanation. The Bible teaches that sin entered the world through human rebellion against God (Genesis 3). This act brought brokenness into every aspect of creation, distorting relationships, corrupting institutions, and introducing pain and death.
Yet, even in the midst of chaos, there remains divine order. God’s sovereignty ensures that history moves according to His plan. Proverbs 19:21 reminds us, “Many are the plans in a person’s heart, but it is the Lord’s purpose that prevails.” What appears as randomness or injustice to the human eye is under the guiding hand of a righteous and sovereign Creator.
Truth in a World of Relativism
One of the greatest struggles in modern society is the battle over truth. The world preaches relativism—"your truth is your truth"—yet this leads to confusion and moral decay. The Bible, however, provides an unchanging standard. Jesus declared, “I am the way, the truth, and the life. No one comes to the Father except through me” (John 14:6). This claim affirms objective truth and establishes that truth is found in a person—Jesus Christ.
When we navigate life through the wisdom of the Bible, we are not left to the whims of popular opinion. Instead, we are anchored in eternal principles. God’s Word defines right and wrong, illuminates the path to salvation, and offers guidance for every area of life (Psalm 119:105).
Finding Purpose and Identity
Modern culture pushes the idea that we must create our own purpose and define our own identity. However, this pursuit often leads to emptiness. The Bible tells us that we are not random accidents but intentionally created by God in His image (Genesis 1:27). Our purpose is not self-made but God-given: to glorify Him and enjoy a relationship with Him (Isaiah 43:7).
Rather than seeking fulfillment in fleeting successes, personal achievements, or societal approval, the Bible calls us to find meaning in serving God and others. Ecclesiastes 12:13 sums it up: “Fear God and keep His commandments, for this is the duty of all mankind.”
Hope in the Midst of Suffering
Without the Bible, suffering can seem meaningless. Pain, loss, and hardship often raise questions about God’s goodness. However, Scripture reveals that suffering is not wasted. Romans 8:28 assures believers that “in all things God works for the good of those who love Him.” Trials refine our faith, draw us closer to God, and remind us that our true home is not in this broken world but in the eternal kingdom of God.
Moreover, Jesus Himself suffered on our behalf, taking upon Himself the punishment for sin so that we might have eternal life (Isaiah 53:5). Because of His resurrection, we have the assurance of victory over sin and death. This hope transforms how we endure hardships, knowing that every trial has a purpose and that ultimate restoration is coming (Revelation 21:4).
A Call to Live Differently
Understanding the world through the lens of the Bible is not just about gaining knowledge—it’s about transformation. Romans 12:2 instructs us: “Do not conform to the pattern of this world, but be transformed by the renewing of your mind.” When we see life through God’s truth, we are called to live in a way that reflects His character—loving our neighbors, standing firm in righteousness, and sharing the Gospel with those in darkness.
The world will continue to shift, and confusion will persist for those seeking answers outside God’s Word. But for those who turn to the Bible, there is clarity, purpose, and unshakable hope. By aligning our lives with God’s truth, we can make sense of this world and confidently walk the path He has laid before us.
-
 @ 75869cfa:76819987
2025-03-04 14:05:38
@ 75869cfa:76819987
2025-03-04 14:05:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 228,000 daily trusted pubkey events. The number of new users has seen a notable increase, with profiles with a contact list amounting to 17 times the same period. More than 11 million events have been published, with posts and reposts showing an increase. Total Zap activity stands at approximately 13 million, marking a 22% decrease.
Additionally, 28 pull requests were submitted to the Nostr protocol, with 5 merged. A total of 45 Nostr projects were tracked, with 11 releasing product updates, and over 462 long-form articles were published, 26% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 1 significant events is upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 228,000, representing a slight 8.7% decrease compared to the previous period. Daily activity peaked at 18256 events, with a low of approximately 16087.
The number of new users has increased significantly. Profiles with a contact list are now around 393,637, a 17-fold increase. Pubkeys writing events have declined to approximately 227,635, but have still grown by 14%. Profiles with a bio are now 9 times the previous number.
Regarding event publishing, the total number of note events published is about 11 million. Posts remain the most dominant in terms of volume, totaling approximately 1.7 million, reflecting an increase of 6.8%. Reposts are showing a increase of approximately 12%, while reactions have experienced a 8% decline.
For zap activity, the total zap amount is about 13 million, showing a decrease of over 22% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
nip99 e-commerce use case extension
nostr:npub1gmmrkec8een5jelrxq5rz260nqzpnj45yzznpaerqv0yma3s86gqpfe2h0 is proposing nip99 e-commerce use case extension. This pull request simply adds a link to the specification we are developing and have consensus on, allowing other developers who want to implement NIP-99 for e-commerce to discover how the major developers are approaching it. In this way, we ensure that NIP-99 remains lightweight and allows for broad use cases while also providing guidance for the e-commerce use case that is currently prevalent.
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing "global" relay lists that streamlines the b/c process by standardizing it across multiple apps and also by allowing these lists to be shared, so when the relays that were hardcoded (and that were, at the time of the hardcoding, known to be such public squares) get shut down then clients can automatically or manually switch to new ones.
[NIP 53 Addendum] - Add Interactive Rooms, Meetings, and Live Presence.
nostr:npub18pudjhdhhp2v8gxnkttt00um729nv93tuepjda2jrwn3eua5tf5s80a699 is proposing that add Interactive Rooms and Meetings, and Live presence to NIP-53. Kind 30312 (Interactive Rooms), Kind 30313 (Meetings), Kind 10312 (Room Presence). These Kinds would apply to interactive audio/video platforms such as Hivetalk version 2.0 (not public yet) and Nostr Nests.
NIP-5E: Censorship Resistant Live Streams
v0l is proposing a way to distribute live video streams via Nostr. "Live Video" in this context implies segmented video streams like HLS or DASH. Each segment of the stream is a NIP-94 event which describes where the file can be found and its hash.
Add birth field to NIP-24 for birth date representation
nostr:npub12egp0pvh2f0fp6sk5nt6ncehqzkz8zsma8dl8agf8p3f98v6resqku4w26 is proposing a PR that introduces the birth field to NIP-24, allowing users to specify their birth date. The goal is to enable applications to celebrate users' birthdays and allow other users to notice and join in the celebration, enhancing social interactions.Defined the format as [day, month, year (optional)]. The year is optional to accommodate users who prefer not to disclose their age.
NIP-05: add dynamic server recommendation
nostr:npub1q3sle0kvfsehgsuexttt3ugjd8xdklxfwwkh559wxckmzddywnws6cd26p is proposing NIP-05 services who let people sign up for a NIP-05 name are recommended to make the names unique case insensitive.
Staab is proposing PR that adds a delegation command to NIP 46, which allows applications that are already authorized to create new sessions with limited permissions. My use case for this is sharing a read-only session with push- or email- notification servers, which can only sign kind 22242 events on behalf of the user, in order to get access to auth-gated relays.
Staab updates NIP: XXX - Push Notifiation with the following differences: It uses parameterized replaceable events, which allows for multiple subscriptions to exist at the same time;It uses NIP 44 encryption rather than NIP 04;It uses filters rather than ad-hoc targets;It uses delegated authentication in order to gain access to gated relays;It uses a different mechanism for pausing notifications and auto-expiring pauses.
NIP-22: Format should follow scope
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing This adds some flexibility in formatting styles for NIP-22. Since this NIP is always used inside a scope (another NIP), formatting rules SHOULD be defined by that NIP. Examples: If the Comment is replying to a markdown-based NIP, it should allow markdown. If the Comment is replying to an asciidoc-based NIP, it should allow asciidoc.
NIP-34!: use NIP-22 thread style for patch and status events
nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr created this as part of reviewing #1744. For the status event, references to merged patch events are done using the q tag even though the they are not included in content. This is because NIP-22 only supports the use of e reference for the parent event id.
believethehype introduces kind 7007 (ping) to send a small request to a dvm to check if it is alive. The DVM replies with a kind 7000 feedback event and status pong, and optional information in content. This allows clients to test if a dvm is alive without sending an actual job request to the dvm.
Notable Projects
Coracle 0.6.5 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
New maintenance release of Coracle is out: * Fix memory leak * Fix isEventMuted * Fix toast animation * Fix (and improve) drafts * Fix parser dropping sections of notes
Primal nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal for iOS build 2.1.26 has just been released. Here’s what’s new: * Improved feeds * Deep linking threads, articles, profiles * Bug fixes & stability improvements
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
web v4.4.0: * Zap polls can now be added directly from the list or created instantly within notes and comments. * Muting users is now more reliable. * Users can download and export their NWC secret for wallets. * Wallets and account credentials are automatically saved upon signup and logout. * Faster login and signup when interacting with Yakihonne while logged out. * Bug fixes and performance optimizations for improved reliability.
mobile v1.6.6: * Ability to export your NWC wallets and your keys. * Blink wallet is now available as one of the external wallets that can be used. * Private messages drafts are now available. * Notes stats optimised. * Wallet management overall performance has been improved. * Fixing bugs and improving the overall performance
GOSSIP nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
Several major bugs have been fixed in the last week. * PRIVACY: gossip was authenticating to relays in many cases even if you turned on "require user approval before AUTHenticating..." * Gossip was rendering nevent links as note1 links in some cases * When clicking the parent link, sometimes it wasn't finding the parent note (even though the note you clicked correctly hinted at which relay the note was at) * New users who adjusted settings during the first run were having their public key wiped, which appeared to have no identity and they had to regenerate on second run
nos.social nostr:npub1pu3vqm4vzqpxsnhuc684dp2qaq6z69sf65yte4p39spcucv5lzmqswtfch
With the Nos 1.2 update, you can use Nos to create, edit, and delete lists of your favorite people and accounts! We're also bringing you fixes for the biggest issues in the previous version: * Fixed: restarting app reverts to Following rather than selected list or relay * Fixed: lists change positions randomly * Fixed: adding and removing relays is not reflected in the feed filter * Fixed: text fields sometimes don't work on onboarding screens * Fixed: main action button is not visible on iPad on "Build Your Network" onboarding screen * Fixed: crash when processing a malformed delete event
Fountain 1.1.17 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
- In this update, we completely rebuilt the authentication flows as some users reported issues accessing the app. We're currently building out the redesigned library and content pages along with updates to transcripts.
Plebeian Market nostr:npub1market6g3zl4mxwx5ugw56hfg0f7dy7jnnw8t380788mvdyrnwuqgep7hd
- Social Sharing: New social sharing buttons have been implemented, allowing users to share listings and pages effortlessly across social platforms.
- Open Graph Integration: Enhanced sharing capabilities with the addition of an Open Graph library, making it easier to share listings on social media.
- Pagination on Mobile: Now see up to 20 items before you need to paginate, making browsing smoother and more efficient on your mobile device.
- UX/UI Overhaul: Significant improvements to the UX and UI of the Settings and Dashboard for a more intuitive navigation.
- Dashboard Enhancements: Various fixes to ensure the dashboard is more functional and user-friendly.
- Relays Pop-Out: Improved UI so the Relays pop-out no longer goes underneath the category menu on the homepage and other pages.
- Save Button: A 'Save' button has been added to every page for quick and easy updates to your listings or settings.
- Payment Details Clarity: Examples are now included in the 'Payment Details' field to guide sellers on what information to provide.
- And fixes some bugs.
DEG Mods nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x
- The ability to switch between reply and quote-replies
- Preview the recent posts of an author under their profile box when viewing a mod or blog they've published
- Clicking on images in a feed post triggers the gallery system for it
- Adjusted the design of images and videos that appear in the feed page
- Reposting won't trigger a popup
- Textarea in feed page will reset its size after posting, along with preview reset
- Load new posts button now works/appears properly
- Reply depth numbering now works correctly
- User LN address now updates correctly if they change it (was a caching issue)
Zapstore 0.2.5 nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8
- Hopefully fixed the missing apps issue
- No more toast showing Zapstore update available (pinned instead)
- Trigger local version refresh on app detail page
futr nostr nostr:npub18wxf0t5jsmcpy57ylzx595twskx8eyj382lj7wp9rtlhzdg5hnnqvt4xra
- Optimized Subscription Handling
- Implemented proper event pagination with timestamp tracking.
- Added event deduplication across batches.
- Improved debug logging for pagination and subscription events.
- Fixed timestamp handling to prevent future-dated events.
- Reduced events per pubkey from 2000 to 500 for better efficiency.
- Relay Connection & Event Parsing
- Improved relay connection state management.
- Fixed parsing of OK messages from relays.
- Updated follow list and DM relay parsing.
- Added proper nevent links for quoted reposts.
- Increased connection timeout from 3s to 15s to enhance reliability.
- UI & UX Enhancements
- Fixed follow list flickering by improving model caching.
- Improved login experience with better async timing.
- Fixed profile filter issues to improve data consistency.
- And another changes.
ZEUS v0.10.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
- Receive: add advanced settings toggle
- Remove deprecated backends
- Move sweep on-chain functionality to Tools view
- Update colors according to themes in external link modal
- Improve contrast of warning buttons in Disaster Recovery view
- Bug fix: display of backup status
- Bug fix: ZEUS Pay local notifications
- Renewable channels
- NWC client support
- Embedded LND: v0.18.5-beta
- New share button (share ZEUS QR images)
- Activity: highlight filter icon when filters active
- chantools: sweepremoteclosed
- Tools: Export Activity CSVs, Developer tools
- Activity: filter by max amount, memo + note
- CLNRest: add payment timeout setting
Long-Form Content Eco
In the past two weeks, more than 462 long-form articles have been published, including over 79 articles on Bitcoin and more than 42 related to Nostr, accounting for 26% of the total content.
These articles about Nostr mainly explore its potential as a decentralized, censorship-resistant communication protocol, contrasting it with traditional social media platforms like Facebook and X. They discuss Nostr’s ability to foster free speech, privacy, and security while providing a foundation for new applications, including encrypted messaging (such as the use of the Double Ratchet Algorithm in NIP-117 and NIP-118), decentralized identity management, and anonymous event relaying (as proposed in "Renoters"). Several pieces, including "The Advancement of the Nostr Protocol," highlight recent technical advancements, developer tools like Nostr SDK, and practical use cases for Bitcoin applications. Others, criticize centralized platforms for their control over user data and content moderation policies. Additionally, topics like relay setup, voting systems, and AI alignment with human values are explored, emphasizing Nostr’s broader applications beyond social media.
These Bitcoin articles explore adoption, investment strategies, security, privacy, and their impact on global finance. Many highlight Bitcoin’s role in fostering financial resilience in Zimbabwe, rural economies, and the importance of user adoption over merchant adoption. Investment discussions cover DCA strategies, ETF influence, and ways to maximize returns. Privacy and security topics emphasize decentralization, self-custody, and best practices to protect assets. Bitcoin is framed as an alternative to fiat, with critiques of traditional finance and central banking. Geopolitical discussions examine the IMF’s influence, France’s fiscal crisis, and El Salvador’s Bitcoin policy. Technical innovations, such as EVM integration, Lightning Network advancements, and multi-payment solutions, continue to expand the Bitcoin ecosystem, driving broader adoption and usability.
Thank you, nostr:npub1m0sxqk5uwvtjhtt4yw3j0v3k6402fd35aq8832gp8kmer78atvkq9vgcru nostr:npub13rvvn5g23anm09kwnya8qvzqejxfajfa56rnn47ck5l96ke6cq4sdcd4e0 nostr:npub10m6lrv2kaf08a8um0plhj5dj6yqlw7qxzeag6393z352zrs0e5nsr2tff3 nostr:npub17v7g49shev2lwp0uwrx5v88ad6hj970zfse74wkes9jguhkx7aqsgjwsvj nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz nostr:npub1nlk894teh248w2heuu0x8z6jjg2hyxkwdc8cxgrjtm9lnamlskcsghjm9c nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1g53mukxnjkcmr94fhryzkqutdz2ukq4ks0gvy5af25rgmwsl4ngq43drvk nostr:npub16dswlmzpcys0axfm8kvysclaqhl5zv20ueurrygpnnm7k9ys0d0s2v653f nostr:npub1x7zk9nfqsjwuuwm5mpdu8eevsnu2kk0ff23fv58p45d50fhuvaeszg44p2 nostr:npub1mwce4c8qa2zn9zw9f372syrc9dsnqmyy3jkcmpqkzaze0slj94dqu6nmwy and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The Bitcoin Freedom Festival took place from February 20 to 24, 2025, at the Awakening Center in Uvita, Costa Rica. In collaboration with the Awake Earth Festival, the event blended a music festival with Bitcoin seminars and lectures. From February 20 to 23, it featured music, healing workshops, ceremonies, and educational talks, with internationally renowned artists and captivating discussions. February 24 was a special day dedicated to Bitcoin, with all activities centered around it. nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * The 5th Bitcoin Educators Unconference, organized by Mi Primer Bitcoin, was successfully held on February 27, 2025, at Bitcoin Park in Nashville, USA. The event focused on grassroots projects and Bitcoin education, adopting a decentralized, community-led format. Every participant was a potential speaker, proposing discussion topics at the beginning of the event, which were then grouped into breakout sessions for in-depth discussions. nostr:npub17cyatz6z2dzcw6xehtcm9z45m76lde5smxdmyasvs00r4pqv863qrs4ml3
Here is the upcoming Nostr event that you might want to check out.
- The Bitcoin Educators Unconference will take place on April 10, 2025, at Bitcoin Park in Nashville, USA. The event follows a decentralized, community-led format, with a focus on Bitcoin education and independent Bitcoin educators. It aims to foster collaboration and networking among Bitcoin educators, creating a truly interactive space.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 83fd07de:aec50d47
2025-03-04 13:48:29
@ 83fd07de:aec50d47
2025-03-04 13:48:29Attempts to artificially inflate demand for Bitcoin—whether through ordinals for 'crypto' people, ETFs for institutional investors, or Bitcoin Strategic Reserves (BSR) for states—for purposes other than self-sovereign savings and payments, will almost always backfire.
The reasons you use to onboard people to Bitcoin can often be the same reasons they eventually decide to leave. While it's true that this process can lead to incremental improvements in user education, it also subjects actual Bitcoin users to considerable volatility, a defining characteristic of the Bitcoin user journey.
Simply put, all pro-Bitcoin narratives appear strong when prices are rising and weak when they are falling. So, what do the Bitcoin users actually know better than tourists that enable them to outlast the madness of the crowds?
https://media.tenor.com/QHPiPY42oR0AAAAC/benbvolliefde-b%26bvolliefde.gif
Unlike tourists, Bitcoin users know that bitcoin itself is not volatile; rather, it's the valuation expressed in fiat currency that experiences volatility. They know that Bitcoin is not something to be blindly trusted but something to be verified. They know that nothing out there beats running and using your own node. They know that their self-custody setup is solid. They know that Lightning works, offering incredible UX advancement in web payments. Additionally, they know how Nostr empowers exploration of new frontiers on the web, revealing traditional tech infrastructures for what they truly are. And there is so much more.
Yet most importantly, Bitcoin users know they ARE IN CHARGE of creating a new world.
Individual agency has been reclaimed, and it matters greatly. Anyone who is aware of this shift will embrace it wholeheartedly and will be reluctant to relinquish it, if ever.
Bitcoin is not a quest of telling what people should value; it's a journey of discovering the value of time well spent—a life worth living.
https://i.nostr.build/0TdM9A3rzm6BSElE.png
-
 @ a9434ee1:d5c885be
2025-03-04 13:05:42
@ a9434ee1:d5c885be
2025-03-04 13:05:42The Key Pair
What a Nostr key pair has by default:
- A unique ID
- A name
- A description
- An ability to sign stuff
The Relay
What a Nostr relay has (or should have) by default:
- Permissions, Moderation, AUTH, ...
- Pricing & other costs to make the above work (cost per content type, subscriptions, xx publications per xx timeframe, ...)
- List of accepted content types
- (to add) Guidelines
The Community
Since I need Communities to have all the above mentioned properties too, the simplest solution seems to be to just combine them. And when you already have a key pair and a relay, you just need the third basic Nostr building block to bring them together...
The Event
To create a #communikey, a key pair (The Profile) needs to sign a (kind 30XXX) event that lays out the Community's : 1. Main relay + backup relays 2. Main blossom server + backup servers 3. (optional) Roles for specific npubs (admin, CEO, dictator, customer service, design lead, ...) 4. (optional) Community mint 5. (optional) "Welcome" Publication that serves as an introduction to the community
This way: * any existing npub can become a Community * Communities are not tied to one relay and have a truly unique ID * Things are waaaaaay easier for relay operators/services to be compatible (relative to existing community proposals) * Running one relay per community works an order of magnitude better, but isn't a requirement
The Publishers
What the Community enjoyers need to chat in one specific #communikey : * Tag the npub in the (kind 9) chat message
What they needs to publish anything else in one or multiple #communikeys : * Publish a (kind 32222 - Targeted publication) event that lists the npubs of the targeted Communities * If the event is found on the main relay = The event is accepted
This way: * any existing publication can be targeted at a Community * Communities can #interop on content and bring their members together in reply sections, etc... * Your publication isn't tied forever to a specific relay
Ncommunity
If nprofile = npub + relay hints, for profiles
Then ncommunity = npub + relay hints, for communities -
 @ 2f4550b0:95f20096
2025-03-04 12:57:08
@ 2f4550b0:95f20096
2025-03-04 12:57:08In today’s fast-evolving workplaces, effective leadership hinges on more than just authority or charisma. You must unlock the potential of your team. Enter andragogy, a framework for adult learning that can transform how leaders inspire, engage, and empower their people. Initially developed by educator Malcolm Knowles in the 1960s, andragogy shifts the focus from traditional, top-down teaching to a model tailored to the unique needs of adult learners. For leaders, mastering this approach is a superpower that leverages the experience and problem-solving capacity of their teams to drive real results.
So, what is andragogy? Unlike pedagogy, which focuses on teaching children through structured, teacher-led methods, andragogy recognizes that adults learn differently. Knowles identified key principles that define this model: adults are self-directed, bring a wealth of experience to the table, are motivated by relevance, prefer problem-centered learning, and thrive when they understand the “why” behind what they’re doing. For leaders, these principles aren’t abstract theories. They’re actionable tools you can leverage to build stronger, more capable teams.
The beauty of andragogy lies in its respect for what adults already know. Think about your team: they’re not blank slates waiting for instructions. They’ve got years of experience, insights from past roles, and skills honed through trial and error. Too often, leaders fall into the trap of micromanaging or delivering one-size-fits-all approach that ignores this depth. Andragogy flips the script. Adult learning theory reminds us to tap into that reservoir of expertise and channel it toward solving the real-world challenges our organizations face.
Imagine you’re leading a team tasked with improving customer retention. A traditional approach might involve sending out a manual or dictating a step-by-step process. An andragogical approach, however, starts by asking: What do you already know about keeping customers happy? You might facilitate a discussion where team members share stories. Maybe a sales rep recalls a tactic that won back a frustrated client, or a support agent highlights a pattern they’ve noticed in feedback. Suddenly, you’re not just giving orders; you’re curating a collective problem-solving session that respects their expertise and builds buy-in. The result? Solutions grounded in real experience.
This approach also aligns with adults’ preference for relevance and practicality. Knowles emphasized that adults learn best when they see immediate value in what they’re doing. As a leader, you can harness this by tying learning to tangible outcomes. Let’s say your team needs to adopt a new software tool. Instead of a generic training session, frame it around a specific problem, like streamlining a workflow that’s been eating up hours. Give them space to experiment with the tool, share what works, and tweak it based on their insights. They’re not just learning; they’re solving something that matters to them, which fuels motivation and ownership.
Andragogy’s problem-centered focus is another leadership goldmine. Adults don’t want to memorize facts for the sake of it; they want to tackle issues they’re facing right now. This is where you, as a leader, can shine. By positioning yourself as a facilitator rather than a dictator, you create an environment where your team attacks real challenges collaboratively. Take a stalled project, for instance. Instead of prescribing a fix, gather your team and ask: What’s blocking us, and what have we seen work elsewhere? Let them draw on their past wins and failures to craft a solution. You’re not just solving the problem. You’re building a team that’s confident in its ability to adapt.
Ready for a quick win to test this out? Here’s one you can try tomorrow: The Experience Share. Next time you’re in a team meeting, pick a current challenge like a deadline crunch or a client complaint. Allocate 15 minutes for everyone to share one relevant experience they’ve had that could inform the solution. Maybe someone’s navigated a similar deadline before, or another dealt with a picky client. Jot down the ideas, then guide the group to pick one or two to act on. It’s fast, leverages their know-how, and shows you value their input. Watch engagement and results tick up.
The andragogy edge isn’t about reinventing leadership; it’s about amplifying what’s already there. By treating your team as capable, self-directed learners with valuable experience, you unlock a level of collaboration and innovation that top-down methods can’t touch. In a world where adaptability is king, this isn’t just a theory. It’s your secret weapon. So, step back, tap into your team’s wisdom, and watch them rise to the occasion. Leadership doesn’t get more super than that.

