-
 @ 57d1a264:69f1fee1
2025-03-23 12:24:46
@ 57d1a264:69f1fee1
2025-03-23 12:24:46https://www.youtube.com/watch?v=obXEnyQ_Veg
source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0
originally posted at https://stacker.news/items/922356
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ da0b9bc3:4e30a4a9
2025-03-23 09:00:12
@ da0b9bc3:4e30a4a9
2025-03-23 09:00:12Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/922244
-
 @ 58537364:705b4b85
2025-03-23 04:09:15
@ 58537364:705b4b85
2025-03-23 04:09:15เราเคยสังเกตไหมว่า...
ทันทีที่ยึดอะไรก็ตามว่าเป็น "ของฉัน" เราจะกลายเป็น "ของมัน" ไปทันที
เราจะยอมทุกข์เพื่อมัน ถ้าใครวิจารณ์เสื้อของฉัน ตำหนิรถของฉัน
เราจะโกรธและจะแก้ต่างให้มัน บางครั้งถึงกับแก้แค้นแทนมันด้วยซ้ำ
ถ้าเงินของฉันถูกขโมย เราจะทุกข์ข้ามวันข้ามคืนทีเดียว
คนจำนวนไม่น้อยยอมตายเพื่อรักษาสร้อยเพชรไว้ไม่ให้ใครกระชากเอาไป
บางคนยอมเสี่ยงชีวิตฝ่าเปลวเพลิงที่กำลังลุกไหม้บ้าน
เพราะกลัวอัญมณีจะถูกทำลายวายวอดฉะนี้แล้ว...
ควรจะเรียกว่ามันเป็น "ของฉัน" หรือฉันต่างหากเป็น "ของมัน" ?
เป็นเพราะหลงคิดว่ามันเป็น "ของฉัน"
ผู้คนทั้งโลกจึงกลายเป็น "ของมัน" ไปโดยไม่รู้ตัว
มีชีวิตอยู่เพื่อมัน ยอมทุกข์ก็เพื่อมันทั้งๆ ที่รู้อยู่ว่ามีเวลาอยู่ในโลกนี้จำกัด
แต่ใช้เวลาไปอย่างไม่เสียดายก็เพื่อมันซ้ำร้ายกว่านั้น...
หลายคนยอมทำชั่ว อกตัญญูต่อผู้มีพระคุณก็เพื่อมัน
กลายเป็นว่าถูกมันใช้ ยิ่งกว่าเป็นผู้ใช้มัน
ยิ่งยึดมั่นว่าทรัพย์สินเป็น "ของฉัน"
เรากลับกลายเป็น ทาสของมัน
จิตใจนี้อุทิศให้มันสถานเดียวเศรษฐีนีเงินกู้คนหนึ่งเป็นโรคอัลไซเมอร์ในวัยชรา
จำลูกหลานไม่ได้แล้ว แต่สิ่งเดียวที่จำได้แม่นก็คือ สมุดจดบันทึกทรัพย์สิน
ทุกวันจะหยิบสมุดเล่มนี้มาพลิกดูไม่รู้เบื่อแม้ลูกหลานจะชวนสวดมนต์หรือฟังเทปธรรมะ
ผู้เฒ่าก็ไม่สนใจ จิตใจนั้นรับรู้ปักตรึงอยู่กับเงินทองเท่านั้นไม่ต้องสงสัยเลยว่า...
เมื่อสิ้นลม ผู้เฒ่าจะนึกถึงอะไร และจะไปสุคติได้หรือไม่
ไม่ว่าจะมีเงินทองมากมายเพียงใด
เมื่อตายไปก็ไม่มีใครเอาไปได้แม้แต่อย่างเดียวนั่นเป็น ข่าวร้าย สำหรับผู้ทุ่มเทชีวิตทั้งชีวิตเพื่อทรัพย์สมบัติ
แต่ที่ร้ายกว่านั้นก็คือ...
หากหวงแหนติดยึดมัน แม้กระทั่งในยามสิ้นลม
มันก็สามารถฉุดลงอบายได้
ถ้า ไม่อยากเป็น "ของมัน"
ก็ควรถอนความสำคัญมั่นหมายว่ามันเป็น "ของฉัน"การให้ทาน เป็นวิธีการเบื้องต้นในการฝึกจิตให้ถอนความสำคัญมั่นหมายดังกล่าว
ถ้าให้ทานอย่างถูกวิธี ไม่เพียงเป็นประโยชน์แก่ผู้รับเท่านั้น
หากเป็นประโยชน์แก่ผู้ให้ด้วย
ประโยชน์ประการหลัง มิได้หมายถึง ความมั่งมีศรีสุขในอนาคต เท่านั้น
ที่สำคัญกว่านั้นก็คือ...
ช่วยลดความยึดติดในทรัพย์ "ของฉัน"แต่อานิสงส์ดังกล่าวจะเกิดขึ้นได้ ต่อเมื่อเราให้โดย ไม่ได้หวังอะไรกลับคืนมา
หากให้เพื่อมุ่งประโยชน์แก่ผู้รับเป็นสำคัญ
ไม่ว่าผู้นั้นจะเป็นพระหรือไม่ก็ตามและเมื่อให้ไปแล้ว ก็ให้ไปเลย
โดยไม่คิดว่าของนั้นยังเป็นของฉันอยู่
การให้ทานและเอื้อเฟื้อเจือจาน
เป็นการสร้างภูมิต้านทานให้แก่จิตใจทำให้ ไม่ทุกข์ เมื่อประสบความสูญเสีย
ในทางตรงข้าม...
คนที่ตระหนี่ แม้จะมีความสุขจากเงินทองที่พอกพูน
แต่หารู้ไม่ว่า จิตใจนั้นพร้อมที่จะถูกกระทบกระแทกในยามเสียทรัพย์
แม้จะเป็นเรื่องที่จำเป็นก็ตาม
ข้อธรรม คำสอน พระไพศาล วิสาโล
โปรดแชร์เป็นธรรมทาน -
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ 6bae33c8:607272e8
2025-03-22 23:12:43
@ 6bae33c8:607272e8
2025-03-22 23:12:43I was supposed to do my Main Event next week, but Heather scheduled a trip to Spain for us I had forgotten about, so I moved it to today, which meant I had to cram a bit.
I drew the seven slot. Results are below:
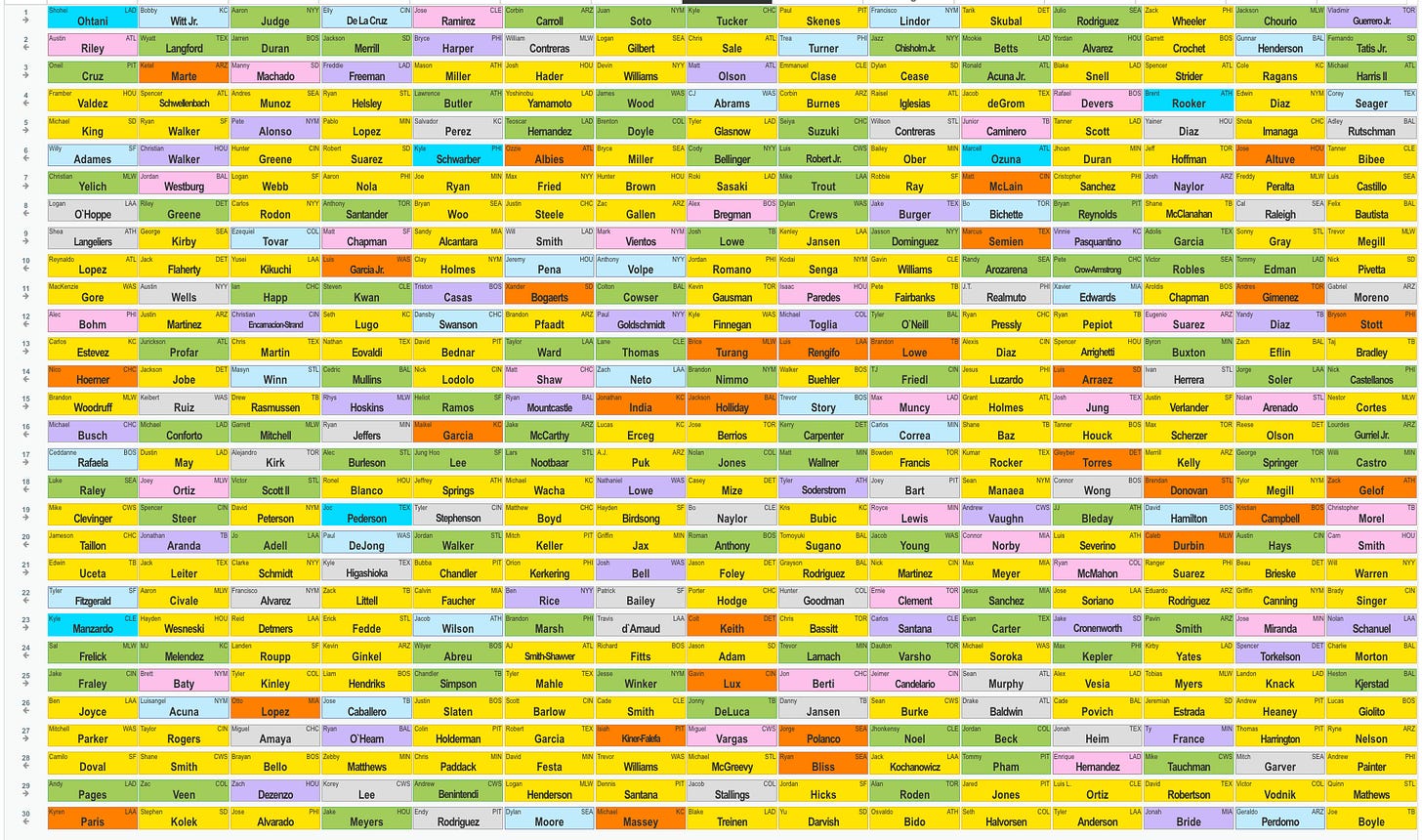 Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.
Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.1.8 Kyle Tucker — I like Tucker in a new park, playing for a big contract. He’s fully healthy after an injury-shortened 2024, so he should be fresh. Had Team 7 taken Tucker instead of Juan Soto, I would have taken Jackson Chourio.
2.8 Chris Sale — I thought I might get Jazz Chisholm here, and my fallback was Trea Turner. But earlier in the day I decided I’d probably take Sale anyway as pitching gets scarce quickly in the 15-team and often gets pushed up as a result. But I hadn’t really locked it in, even though I felt Sale would make for an easier build. Then Chisholm and Turner went ahead of me on consecutive picks, and my choice was made for me.
3.8 Matt Olson — I was worried about this pick. This was in the elite closer range, and I didn’t want to go that route, so it was either Manny Machado (gone), Olson or dropping down for someone like Michael Harris about whom I’m only lukewarm. I took Olson who has a good shot of 40-100-100 in that lineup.
4.8 C.J. Abrams — The stat nerds hate him, but he could steal 40 bases, and he was raking before slumping in the second half last year. Tucker gave me some bags, but I really wanted a big-time steals source to pair with him.
5.8 Tyler Glasnow — My favorite fifth-round starter, Glasnow managed134 innings last year. A similar giant lefty, Randy Johnson, was also injury prone early in his career and took a while to get going too.
6.8 Cody Bellinger — I was dead set on Bellinger who is raking this spring. He’ll get the short porch in Yankee stadium and qualifies at first and OF.
7.8 Roki Sasaki — This was the first pick I really had to think about. There was a run of five straight pitchers ahead of me, three of whom I would have taken instead (Logan Webb, Max Fried, Hunter Brown.) I like buying the dip on Sasaki after a shaky outing in Japan, but I also considered pivoting to Mike Trout. In the end, I felt there were more hitters I liked afterward, so I went Sasaki, and then Trout went with the very next pick. In fact the next guy snap-called it, if I recall correctly.
8.8 Alex Bregman — I wanted a share after reading how well he’s hit at Fenway during his career (if Grok is correct, 1.240 OPS in 21 games.) Plus he might eventually gain 2B eligibility if Rafael Devers gets healthy enough to play third. And he should get a lot of RBI hitting third behind Devers and Jarren Duran.
9.8 Josh Lowe — I really wanted to get a share of Lowe after reading about how the minor league home park will boost power for lefties. The steals are a given if he’s healthy, but 20-25 HR would make him a huge bargain in Round 9.
10.8 Jordan Romano — The Lowe pick cost me Kenley Jansen, which I thought it might, so I pivoted to the other exprienced closer I like in that range, and Romano’s on a better team.
11.8 Kevin Gausman — I thought about Aroldis Chapman here, but starters were getting scarce, so I gambled he’d make it back and took Gausman. Gausman is coming off a down year, but he’s healthy, and he knows how to pitch.
12.8 Brandon Finnegan — I missed out on Chapman, it turns out, but Finnegan, who had 38 saves last year and was re-signed, was my backup plan. He’s not especially good, but saves are saves.
13.8 Brice Turang — I really didn’t need speed that badly, but Turang fell like 50 spots below ADP, and I did need a second baseman. His defense keeps him in the lineup, and I’ll take 30-plus steals in case one of my other speed guys doesn’t pan out.
14.8 Brandon Nimmo — I got snaked on Walker Buehler (and Jesus Luzardo two picks before that), so I went with Nimmo for his ability to score runs.
15.8 Jackson Holliday — After a lot of safe picks, I felt like gambling on a top prospect finally. He’s hitting well this spring too.
16.8 Jose Berrios — This just seemed like the right pick, a boring veteran who knows how to pitch and get you innings without killing you. With Glasnow and Sasaki, I needed more of a horse type.
17.8 Nolan Jones — He was scratched from the game today right after I made this, so we’ll see. Hopefully it’s something minor. His 2023 season was fetching a top-five-round ADP last year.
18.8 Casey Mize — Pitching was really flying, and Mize is a former top prospect with an opportunity.
19.8 Bo Naylor — I needed a catcher, and he is one. I like that he runs a bit, and last year’s batting average I’ll chalk up to variance.
20.8 Roman Anthony — I don’t know whether he’ll make the team out of camp, but he’s an elite prospect with little left to prove in the minors.
21.8 Jason Foley — I have two shaky closers, so I wanted to throw another potential one in the mix.
22.8 Porter Hodge — Another saves option if Ryan Pressly falls apart.
23.8 Colt Keith — Keith wasn’t horrendous as as rookie, and moving to first base will give him extra eligibility soon.
24.8 Jason Adam — Another potential source of saves with Robert Suarez looking awfully shaky this spring.
25.8 Gavin Lux — A former top prospect, getting regular at-bats in the league’s second best hitter’s park and picking up more eligibility.
26.8 Jonny Deluca — I needed outfield depth in case Anthony doesn’t start the year in the majors, and Deluca should play in that bandbox minor league park.
27.8 Miguel Vargas — A former top prospect with dual position eligibility should get his chance for regular low-pressure at-bats in Chicago.
28.8 Michael McGreevy — I needed another SP, and he’s one. Also has good control and pitches in a good park. Having a great spring too.
29.8 Jacob Stallings — I played chicken at second catcher all draft, got burned a few times, but Stallings is the starter for now in Colorado.
30.8 Blake Treinen — The Stallings pick cost me a gamble on Jared Jones’ elbow, so I took Treinen who’s an elite reliever who could fill in if starters have bad matchups.
Roster By Position
C Bo Naylor/Jacob Stallings
1B Matt Olson
2B Brice Turang
3B Alex Bregman
SS C.J. Abrams
CI Cody Bellinger
MI Jackson Holliday
OF Kyle Tucker/Josh Lowe/Brandon Nimmo/Nolan Jones/Roman Anthony
UT Colt Keith
SP Chris Sale/Tyler Glasnow/Roki Sasaki/Kevin Gausman/Jose Berrios/Casey Mize
RP Jordan Romano/Brandon Finnegan/Jason Foley
B Porter Hodge/Jason Adam/Gavin Lux/Jonny Deluca/Miguel Vargas/Michael McGreevy/Blake Treinen
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-22 22:49:27
@ 5d4b6c8d:8a1c1ee3
2025-03-22 22:49:27Time for another check-in. - Comments: 3k (2nd place) - Posts: 286 (5th place) - Stacking: 192k (2nd place) - Top post: https://stacker.news/items/920931/r/Undisciplined
Our comment growth was really impressive. Over 10 comments per post is more than double the Stacker News average. The territory really seems to be thriving on contests and discussion threads. That gives us a pretty clear direction to build on.
Shout out to @SimpleStacker for developing the territory analytics graphs!
originally posted at https://stacker.news/items/922027
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-22 19:13:10
@ 5d4b6c8d:8a1c1ee3
2025-03-22 19:13:10I posted about our new dog about a week ago.
The first thing my daughter did was start telling the new dog all about our dog who died a little over a year ago. It was very touching.
Then she was doing such a good job being gentle and quiet to avoid scaring the new dog, who was extremely timid for the first couple of days. Clearly, she wanted to be loud and wild and play, but the dog wasn't ready, so she very gently told the dog about how she gets scared sometimes and listed off some of the things she gets scared of and explained that she'd help the dog not be scared. What a kid!
The next thing to work on is getting them both to sleep in her room. The bed's getting a bit crowded.
originally posted at https://stacker.news/items/921811
-
 @ 5c8a5765:4fc5edee
2025-03-22 18:38:23
@ 5c8a5765:4fc5edee
2025-03-22 18:38:23[Читать в IPFS]
Итак, детки-котлетки, сегодня мы поговорим, как ~~не~~правильно распространять агиацию. Возьмите свои любимые антифашистские стикеры и используйте этот текст как инструкцию к ним — иначе у меня голова лопнет от того, что я вижу на улицах.
Агитация
Для начала определитесь, чем вы занимаетесь: агитируете к чему-то или поддерживаете чего-то, потому что это предполагает совершенно разные подходы. Агитацией может быть призыв к анархизму, классовой борьбе, неуплате налогов, гендерному равенству и т.д. Поддержкой может быть поддержка анархической борьбы, антифашистский идей и т.д. Первое — "вербует"/приманивает новых людей к идее, второе поддерживает только тех, кто уже знаком с идеей и уже с ней согласен.
Как должна выглядеть агитация? Представьте, что некий неонацист решил за-агитировать вас в неонацизм (с учетом, что сейчас вы его не поддерживаете): в каком случае у него больше всего на это шансов? Если вы заметите на мусорном баке наклейку "бей жыдоф"? Или если вам, например, выдадут в руки грамотный агитационный текст? Поставьте себя на место читающего: агитация должна выглядеть именно так, как мог бы выглядеть материал, который хоть немного мог бы поменять ваши текущие взгляды. А именно...
1. Агитация доступна
Она не висит на задней стороне мусорки. Она не нарисована на заброшке. Обыватель не рассматривает мусорки и не ходит по заброшкам. Чтобы масса увидела вашу агитацию, она должна висеть в заметном месте.
Ещё лучше, если она висит там, где человек по внешним причинам на мгновение задерживается, и имеет время проглядеть вашу агитацию: ибо обыватель никогда не остановится у столба посреди длинной тропы, чтобы прочесть стикер.
И учтите: если место, которое вы выбрали, уже забито стикерами, вашему придётся делить привлеченное внимание с каждым остальным.
К доступности стоит также отнести то, что агитация более значительна, если она написана на самом популярном в вашей стране языке, развешивается в разных локациях (чтобы люди разного класса могли её увидеть), если вы развешиваете в туалетах — то туалетах разного гендера (и не забывайте про инвалидные кабинки!), так далее.
Лучшие места для стикеров: лифт, автобусная остановка, метро, поручен эскалатора, внешняя сторона дверцы туалета, чистое (не разрисованное или расклеенное) зеркало.Лучшие места для крупных агитационных листов или графитти: указанные выше, а также — заметные места подъездов,Лучшие места для "визиток"*: оставлять под задницей на выходе из автобуса, метро, маршрутки, на стульях, скамейках и т.д.*"Визитка" — это са-а-амый простой метод агитации: выводите нужный текст или картинки мелкими блоками на листе А4, нарезаете бумагу на кусочки "визиток" с небольшим текстом, картинкой или ссылкой, и оставляете где попало.
2. Агитация запоминается
Если вы не неонацист, какие эмоции в вас побуждает "бей жыдоф"? Вы возжелали стать неонацистом? Или это только укрепило ваши антифашистские взгляды? Или это для вас вообще никак не прозвучало?
Также для ваших противников и обывателей звучат ваши "ешь богатых!", "классовая борьба сегодня!!", "доёш онархию!!!". Это — поддержка. Уже-анархисты будут рады увидеть, что в городе есть левые активисты кроме них самих. Но это никого не переубедит и не привлечет.
А агитация привлекает. Агитация задаёт острые вопросы, которые остаются в голове. Агитация манит предложениями нового. Агитация нестереотипно предлагает.
Примеры хорошей агитации:

"Если большинство проголосует за то, чтобы ты спрыгнул(а) с вмоста, ты бы сделал(а) это? / - Может быть — если это было честным голосованием!"

"Этот телефон прослушивается - согласно законодательству США, телефонные разговоры прослушиваются без ордера или уведомленияю"

"Вы под наблюдением — текст, объясняющий тезис, и ссылка, где можно прочесть об этом подробнее."
Примеры никудышной агитации (но хорошей поддержки):



3. Агитация даёт возможность изучить больше
Хорошее правило для любой агитации: иметь ссылку на сайт, где можно найти больше информации о том, к чему агитируется. Это не обязательное, но рекомендуемое правило, ибо мало толку от человека, согласившегося с идеей анархизма и захотевшего (редчайший случай!) самостоятельно изучить больше, но не имевшего к этому простой возможности и забывшего вследствие обо всей идее.
Поддержка
А вот поддержка — ориентированная на тех, кто уже знает и уже поддерживает то, что вы любите — может быть совершенно любой. Поддержать антифашистов своего города, позлить фашистов и остаться совершенно незамеченными для обывателя — самое место для диалектики "бей жыдоф!" и "доёш онтифошизм!!".
Напоминание о безопасности
Несколько базовых напоминаний о том, что нужно помнить во время агитации:
- ОСТЕРЕГАЙТЕСЬ КАМЕР! Особенно в России! Метро, маршрутки, автобусы, учебные заведения полны ими!
- Если вас заметили гестаповцы, лучшее, что вы можете сделать — это бежать, что есть мочи.
- Шифруйте материалы, которые храните для распечаток.
- Не распечатывайте стикеры/"визитки" в публичных местах (вроде библиотек).
Спасибо за прочтение!

-
 @ 46fcbe30:6bd8ce4d
2025-03-22 15:21:53
@ 46fcbe30:6bd8ce4d
2025-03-22 15:21:531. Introduction
In decentralized systems like Nostr, preserving privacy and ensuring censorship resistance are paramount. However, the inherent design ethos opens the platform to multiple vulnerabilities, chief among them being the susceptibility to Sybil attacks. The problem space is not only technical but also socio-economic, where user privacy and ease-of-use must be balanced against mitigations that impose friction on identity creation actions.
This report details a multi-faceted research analysis into Sybil resistance mechanisms, drawing analogies from contemporary decentralized identity systems, cryptographic protocols, and economic disincentives. We incorporate detailed insights from diverse independent research streams, outlining both established and novel approaches, and present a series of design recommendations for Nostr. The analysis is targeted at highly experienced analysts and researchers, with comprehensive details on both the cryptographic primitives used and the overall system architectures.
2. Background: The Threat of Sybil Attacks in Decentralized Systems
2.1. Sybil Attacks Defined
A Sybil attack involves a single adversary generating a multitude of pseudonymous identities to unduly influence network decisions, voting mechanisms, or content dissemination processes. In systems designed for censorship resistance, where anonymity is embraced, such attacks are especially daunting because traditional verification methods are not readily applicable.
2.2. The Unique Challenges in Nostr
Nostr is celebrated for its emphatic commitment to censorship resistance and privacy. This design choice, however, leads to several inherent challenges:
- Weak Identity Verification: Mechanisms like nip5, a simple email-like verification protocol, lack robustness and are vulnerable in environments where linking multiple pseudonymous identities is trivial.
- Economic Incentives: Systems using zaps (small value transactions or tips) intend to add cost to malicious actions but struggle with effective proof of expenditure. In some instances, attackers may even benefit from a net positive revenue.
- Association Networks: Existing follow systems provide decentralized webs of association; however, they do not imply a real trust framework, leaving only superficial links among identities.
The dual objectives of achieving ease-of-use while robustly mitigating Sybil attacks requires a careful, in-depth analysis of multiple design trade-offs.
3. Detailed Analysis of Existing Mechanisms and Proposed Enhancements
In our research, several proposals and implementations have emerged to address the Sybil-resistance conundrum. We examine these solutions in detail below.
3.1. Cryptographic and Identity-Based Approaches
3.1.1. Aut-CT with Curve Trees
One of the notable approaches employs the Aut-CT mechanism which leverages Curve Trees. Key insights include:
- Mechanism: Constructing an algebraic analog of a Merkle tree with curve-based keys.
- Verification Efficiency: Achieves logarithmic verification times (typically 40–70 ms) even for large keysets (from 50K to over 2.5M keys).
- Proof Size: Consistently maintains a proof size of around 3–4 kB, making it effective for low-bandwidth scenarios.
- Key Image: The integrated DLEQ-based method produces a key image that binds a proof to a hidden key, preventing fraudulent re-use of tokens.
Implication: This method, while promising, requires integration sophistication. It can potentially be adapted for Nostr to ensure that each identity is backed by a verifiable, anonymous proof of ownership—raising the cost of forging or duplicating identities.
3.1.2. Economic Disincentives and Token Burning
In the realm of cryptocurrency mixers, enforcing an economic cost for generating identities has seen traction. The following methods are prominent:
- Token Burning/Deposit Mechanisms: Users deposit funds that serve as a bond. Forging multiple identities becomes economically prohibitive if these tokens are sacrificial.
- Time Locks and Coin-Age Restrictions: By enforcing waiting periods or requiring funds to ‘age’, systems ensure that rapid, mass identity creation is deterred.
- Fidelity Bonds: Users risk losing bonds if identified as malicious, creating a strong economic disincentive.
Observation: Nostr could potentially adopt analogous economic primitives that impose a non-trivial cost on identity creation, helping to scale the disincentive to the level required for a system where anonymity is paramount.
3.1.3. Decentralized Identity Systems
A comparative analysis of identity systems, both centralized and decentralized, underscores the following:
- Centralized Systems (LDAP, OAuth, etc.): While scalable, they inherently conflict with the decentralized and censorship-resistant philosophy of Nostr.
- Decentralized Systems (uPort, Hyperledger Indy, etc.): These systems leverage blockchain technologies and zero-knowledge proofs to ensure self-sovereign identity management. However, they often require complex deployments and higher operational overhead.
Trade-Off Assessment: Implementing a fully decentralized identity system in Nostr must balance ease-of-use with strong cryptographic assurances. A layered approach—using decentralized identifiers with optional verifications—may yield optimal usability without sacrificing security.
3.2. Protocol-Specific Countermeasures
3.2.1. Rechained Protocol
The Rechained protocol introduces a deposit-based identity generation mechanism in IoT and mobile ad hoc networks. Here are its salient points:
- Deposit Transaction: Each identity is tied to a deposit transaction on a public blockchain, such as Bitcoin or Ethereum.
- Parameterization: Parameters like minHeight, minDifficulty, and amounts ensure that each identity requires a certain financial threshold to be met.
- Verification Complexity: Though proof sizes are modest (10–50 KB) and verification times are around 2 seconds, these are acceptable trade-offs on modern consumer-grade devices.
Application Prospects: If Nostr could integrate a variant of Rechained, it may allow identities to be tied to a verifiable deposit, thus raising the cost baseline for attackers. Such integration must ensure user-friendliness and minimal friction during onboarding.
3.2.2. Sysname Decentralized Identity Scheme
Sysname presents an innovative approach with additional privacy-preserving features:
- Selective Disclosure: It allows users to reveal only non-identifying attributes proving compliance with certain predicates without exposing their full identity.
- Chain-Pinned Identifiers: Aggregates multiple pseudonyms to a single on-chain record, reducing the ease with which an attacker can use disparate identities without accountability.
- Key Recovery: Enables users to refresh public keys and recover lost keys, which bolsters user trust and system resilience.
Consideration: Integrating aspects of sysname within Nostr could offer both enhanced privacy and Sybil resistance, yielding a balance between security and user independence. Enhanced key recovery also addresses the usability concerns evidenced by historical failures in PGP adoption.
3.3. Behavioral Analysis and Anomaly Detection
As an additional countermeasure, behavioral analysis can serve as a secondary layer of defense. Given the evolving sophistication of bots, a cat-and-mouse game inevitably ensues:
- Machine Learning Based Detection: Frameworks like a deep intrusion detection system (DIDS) combined with blockchain smart contracts can help identify anomalous posting behaviors. For example, integrations using Particle Swarm Optimization–Gravitational Search Algorithm (ePSOGSA) with deep autoencoders have proven accurate on established benchmarks.
- Economic Implications: By analyzing behavior, the systems can prioritize identities that have accrued economic transactions (like zaps) that match genuine user behavior over automated, bot-like patterns.
- Limitations: While promising, such systems introduce computational overhead and may yield false positives, so the implementation must be cautiously engineered with appropriate fail-safes.
4. Trade-Offs and Comprehensive Evaluation
4.1. Usability vs. Security
One of the central themes in designing defenses against Sybil attacks on Nostr is balancing ease-of-use with robust security. A highly secure system that remains cumbersome to use (akin to the historical PGP deployment) may fail adoption. Conversely, ease-of-use without economic or cryptographic Assurance opens the door to cost-free identity creation and abuse.
- Economic Approaches: Impose a direct cost on identity creation but must be calibrated to avoid excluding well-intentioned users, particularly newcomers or those with limited funds.
- Cryptographic Protocols: Solutions like Aut-CT and sysname offer advanced cryptographic proofs with minimal overhead in verification but could require more sophisticated client implementations.
- Behavioral Analysis: Acts as a safety net but must be continuously updated as adversaries evolve their bot strategies.
4.2. Privacy Implications
Every mechanism proposed must be evaluated in terms of its ability to preserve user privacy. Nostr’s value proposition rests on its censorship resistance and privacy-preserving design. Therefore:
- Selective Disclosure Protocols: Techniques that allow for proving predicates without full identity revelation should be prioritized (as seen in sysname).
- Decentralized Identity Aggregation: Methods that tie multiple pseudonyms to a single verifiable chain of evidence (enhancing accountability) can reduce risk without compromising anonymity.
- Economic Proof Versus User Balance: The economic barriers should not expose additional metadata that can be linked back to users. Hence, anonymizing tokens and cryptographic blinding techniques need to be integral to the design.
5. Proposed Comprehensive Strategy for Nostr
Based on the research, a multi-layered defense strategy is recommended. It incorporates both cryptographic assurances and economic disincentives while integrating behavioral analysis. The following blueprint emerges:
5.1. Implementation Blueprint
- Integration of Curve Tree-Based Aut-CT Proofs:
- Require each new identity creation to be validated via a Curve Tree-based proof of key ownership. This approach leverages zero-knowledge proofs and ensures logarithmic verification times, thus scalable even for a large user base.
-
Address token re-use and fake identity creation by integrating key images as established in the Aut-CT mechanism.
-
Economic Deposit Mechanism (Inspired by Rechained):
- Incorporate a lightweight deposit mechanism where users must commit a small deposit, recorded on a public blockchain. This deposit acts as a minimum hurdle for each identity and may be partially refundable upon earning trust.
-
Experiment with dynamic deposit sizes based on network load and risk assessments, ensuring that the economic threshold is both feasible and deterring.
-
Selective Disclosure and Pseudonym Aggregation (Adapting Sysname Principles):
- Allow users to prove characteristics about their identities (age, locality, etc.) without divulging full identifying details.
-
Aggregate multiple pseudonyms provided by the same user on-chain, using cryptographic commitments that both link identities and allow selective disclosure.
-
Optional Layer: Economic and Behavioral Analytics:
- Deploy a deep anomaly detection layer using machine learning techniques on posting behavior, ensuring that anomalous activities (e.g., rapid posting similar to bots) are flagged.
- Integrate smart contract-based economic triggers that penalize suspicious behavior while maintaining user privacy.
5.2. Addressing Adoption and Usability Concerns
- User Experience (UX): The proposed solutions must be integrated transparently into client applications. Much like improved versions of PGP aim to streamline key management, Nostr clients should embed these cryptographic protocols without requiring manual intervention.
- Modular Onboarding: Allow users to opt into various levels of proof. Early adopters may use lightweight methods, with a progressive enhancement available for those seeking higher assurance as they interact more within the network.
- Wallet and Key Management Integration: Leverage existing wallet infrastructures to ease the economic deposit and key recovery processes, drawing user confidence from familiarity with mainstream crypto applications.
6. Future Work and Speculative Technologies
While the proposals above are based on current and emergent technologies, additional research can further refine these approaches:
- Adaptive Economic Models: Future work can explore dynamic, context-aware deposit requirements that adjust based on network activity, risk profiles, and even market conditions.
- Quantum-Resistant Cryptography: As quantum computing progresses, integrating quantum-resistant algorithms in curve-tree constructions will become imperative for long-term viability.
- Interoperable Decentralized Identifiers (DIDs): Creating cross-system standards for identity verification may allow Nostr to interface with other decentralized platforms, enhancing the overall security ecosystem.
- Advancements in Zero-Knowledge Proofs (ZKPs): Considering high-level academic research on ZKPs, such as bulletproofs and recursive ZKPs, can further improve both the scalability and succinctness of cryptographic proofs required for identity validation.
Speculative Note: As adversaries adapt, we may see the emergence of hybrid systems where off-chain reputation systems are cryptographically linked to on-chain proofs, creating a multi-dimensional defense that continuously evolves through machine learning and adaptive economic incentives.
7. Conclusion
Mitigating Sybil attacks on Nostr necessitates a proactive, multi-layered approach combining advanced cryptographic techniques, economic disincentives, decentralized verification mechanisms, and behavioral analytics. The proposals detailed in this report aim to reinforce Nostr’s resilience while maintaining its foundational commitment to privacy and censorship resistance.
By integrating Curve Tree-based proofs, economic deposit mechanisms, and selective disclosure methods, Nostr can build a robust identity framework that is both user-friendly and resistant to abuse. Continued research into adaptive economic models and quantum-resistant cryptographic techniques will ensure that the system remains secure in the evolving landscape of decentralized networks.
Thorough evaluation of trade-offs, user experience enhancements, and iterative testing on live networks will be critical. This report serves as a foundational blueprint for further exploration and eventual deployment of sophisticated Sybil defense mechanisms within Nostr.
8. References and Further Reading
While the source of ideas is drawn from numerous research efforts and academic papers, key references include:
- Aut-CT Leveraging Curve Trees and Bulletproof Proofs
- Economic mitigation strategies in cryptocurrency mixers
- Comparative studies of decentralized identity systems (uPort, Hyperledger Indy, etc.)
- Rechained protocol research by Bochem and Leiding for IoT networks
- Sysname scheme for privacy-preserving decentralized identifiers
- Deep intrusion detection systems applied to decentralized social networks
(Additional in-depth academic references can be located within the research literature on arXiv and major cryptographic conferences.)
Prepared by an expert research analyst, this report is intended to provide detailed insights and a strategic roadmap for implementing Sybil-resistant identities on Nostr while retaining user ease-of-use and privacy-centric features.
Sources
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862/2
- https://www.imperva.com/learn/application-security/sybil-attack/
- https://eprint.iacr.org/2019/1111.pdf
- https://www.smartsight.in/technology/what-to-know-about-sybil-attacks/
- https://www.researchgate.net/publication/363104774_Comparative_Analysis_of_Decentralized_Identity_Approaches
- https://www.researchgate.net/publication/331790058_A_Comparative_Analysis_of_Trust_Requirements_in_Decentralized_Identity_Management
- https://www.mdpi.com/1999-5903/17/1/1
- https://github.com/WebOfTrustInfo/rwot5-boston/blob/master/topics-and-advance-readings/Framework-for-Comparison-of-Identity-Systems.md
- https://www.researchgate.net/publication/367557991_The_Cost_of_Sybils_Credible_Commitments_and_False-Name_Proof_Mechanisms
- https://pmc.ncbi.nlm.nih.gov/articles/PMC8125832/
- https://www.nervos.org/knowledge-base/sybil_attacks_consensus_mechanisms_(explainCKBot)
- https://arxiv.org/html/2307.14679v2
- https://www.sciencedirect.com/science/article/pii/S1084804523001145
- https://www.sciencedirect.com/science/article/pii/S2096720924000460
- https://medium.com/@sshshln/mitigating-identity-attacks-in-defi-through-biometric-based-sybil-resistance-6633a682f73a
-
 @ 7d33ba57:1b82db35
2025-03-22 14:04:18
@ 7d33ba57:1b82db35
2025-03-22 14:04:18Alicante, located on Spain’s Costa Blanca, is a vibrant coastal city known for its golden beaches, historic castles, delicious seafood, and lively atmosphere. Whether you're exploring its rich history, relaxing by the sea, or enjoying the local cuisine, Alicante offers the perfect mix of culture and leisure.
🏛️ Top Things to See & Do in Alicante
1️⃣ Santa Bárbara Castle 🏰
- Perched on Mount Benacantil, this medieval fortress offers panoramic views over the city and coastline.
- Walk up the hill or take an elevator from Postiguet Beach.
2️⃣ Postiguet Beach 🏖️
- A beautiful sandy beach right next to the city center.
- Perfect for sunbathing, swimming, or enjoying a cocktail at a beachside bar.

3️⃣ Explanada de España 🌴
- A famous seaside promenade lined with palm trees, cafés, and street artists.
- Great for an evening stroll with stunning sea views.
4️⃣ Alicante Old Town (El Barrio) 🏡
- A charming historic district with narrow streets, colorful houses, and lively tapas bars.
- Visit Concatedral de San Nicolás and the Casas del Barrio for authentic local vibes.
5️⃣ MARQ – Archaeological Museum of Alicante 🏺
- A fascinating museum showcasing Alicante’s history from prehistoric times to modern days.
- Award-winning and great for history lovers!
6️⃣ Tabarca Island Day Trip 🚤
- A small, picturesque island just a short boat ride from Alicante.
- Perfect for snorkeling, seafood dining, and exploring its quaint whitewashed village.
7️⃣ Mercado Central 🛍️
- A bustling market filled with fresh seafood, local produce, jamón ibérico, and cheeses.
- Great for food lovers looking to try authentic Alicante flavors.
🍽️ What to Eat in Alicante
- Arroz a banda – A local seafood rice dish, similar to paella 🍚🐟
- Turrón de Alicante – A famous nougat made with almonds 🍯
- Caldero – A rich fish stew served with rice 🍲
- Salazones – Salted fish specialties, a local delicacy 🐠
- Horchata de chufa – A refreshing tiger nut drink, great on hot days 🥛
🚆 How to Get to Alicante
✈️ By Air: Alicante-Elche Airport (ALC) with flights from all over Europe ✈️
🚄 By Train: High-speed AVE trains from Madrid (~2.5 hrs) & Barcelona (~4.5 hrs)
🚗 By Car: Well-connected via the AP-7 coastal highway💡 Tips for Visiting Alicante
✅ Best time to visit? Spring & Summer for the best beach weather ☀️🏖️
✅ Stay for Las Hogueras de San Juan (June 20-24) – A huge fire festival with fireworks & street parties 🎆🔥
✅ Take a boat to Tabarca Island – It’s a hidden paradise for snorkeling 🏝️
✅ Try local seafood! Alicante’s coast is famous for its fresh fish & shellfish 🦐 -
 @ 30b99916:3cc6e3fe
2025-03-22 12:12:00
@ 30b99916:3cc6e3fe
2025-03-22 12:12:00constitution
Article V of the Constitution of the United States
With your engagement, there is a glimmer of hope that the people can reclaim our captured US government. The entrenched politicians are counting on your NON-ENGAGEMENT to remain in control.
Please take the time to educate yourself about the Constitution.
Now get engaged with your local Convention of States movement.
-
 @ 7d33ba57:1b82db35
2025-03-22 10:27:50
@ 7d33ba57:1b82db35
2025-03-22 10:27:50Valencia is a vibrant coastal city on Spain’s east coast, blending historical charm, futuristic architecture, golden beaches, and amazing cuisine. As the birthplace of paella, it’s a paradise for food lovers, while its mild climate and Mediterranean vibes make it a perfect year-round destination.
🏛️ Top Things to See & Do in Valencia
1️⃣ The City of Arts and Sciences
- A futuristic architectural complex with a science museum, planetarium, aquarium, and opera house.
- The Hemisfèric & Oceanogràfic are must-visits for families and science lovers.
2️⃣ Valencia Cathedral & El Miguelete Tower
- A beautiful Gothic cathedral said to house the Holy Grail.
- Climb El Miguelete Tower for breathtaking city views.
3️⃣ La Lonja de la Seda (Silk Exchange) – UNESCO Site
- A stunning Gothic-style merchant building from the 15th century.
- One of the best-preserved examples of Valencia’s medieval trading history.
4️⃣ Plaza de la Virgen & Old Town (El Carmen)
- A charming square surrounded by historical buildings, fountains, and lively cafés.
- Wander the narrow streets of El Carmen for street art, boutique shops, and tapas bars.
5️⃣ Turia Gardens & Gulliver Park
- A beautiful green park built in a former riverbed, perfect for cycling, jogging, or picnicking.
- Gulliver Park is a giant playground shaped like Gulliver from "Gulliver’s Travels"!
6️⃣ Central Market (Mercado Central)
- One of the largest fresh food markets in Europe, housed in a stunning Art Nouveau building.
- Try fresh produce, local cheeses, and traditional jamón ibérico.
7️⃣ Malvarrosa Beach
- A long sandy beach with great restaurants, water sports, and a relaxing atmosphere.
- Perfect for sunbathing, a seaside stroll, or enjoying a paella by the sea.
🍽️ What to Eat in Valencia
- Paella Valenciana – The original version with rabbit, chicken, and saffron rice 🥘
- Horchata & Fartons – A refreshing tiger nut drink with sweet pastries 🥛🥐
- Agua de Valencia – A famous local cocktail made with orange juice, cava, gin, and vodka 🍹
- Esgarraet – A tasty mix of salted cod, red peppers, and olive oil 🐟
🚆 How to Get to Valencia
🚄 By Train: High-speed AVE trains from Madrid (~1.5 hrs) & Barcelona (~3 hrs)
✈️ By Air: Valencia Airport (VLC) with connections to major European cities
🚗 By Car: A scenic drive along the Mediterranean coast (Costa Blanca)💡 Tips for Visiting Valencia
✅ Best time to visit? Spring & Fall for pleasant weather 🌞
✅ Visit during Las Fallas (March 15-19) – A spectacular festival with fireworks, giant sculptures, and street parties 🎆🔥
✅ Try a bike tour! Valencia is one of Spain’s most bike-friendly cities 🚴
-
 @ da0b9bc3:4e30a4a9
2025-03-22 09:34:42
@ da0b9bc3:4e30a4a9
2025-03-22 09:34:42Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/921232
-
 @ d5c3d063:4d1159b3
2025-03-22 03:31:14
@ d5c3d063:4d1159b3
2025-03-22 03:31:14“คุณจะจัดการกับมลพิษฝุ่น PM2.5 โดยไม่ต้องอาศัยการออกกฎควบคุมจากรัฐได้ยังไง” ถ้าคุณเคยตั้งคำถามนี้ บทความนี้มีคำตอบ...และคำตอบอาจสวนทางกับความเชื่อของคุณโดยสิ้นเชิง . ลองย้อนกลับไปในช่วงต้นปีที่ผ่านมา ในวันที่กรมควบคุมมลพิษประกาศว่า “ค่าฝุ่น PM2.5 เกินมาตรฐานใน 43 จังหวัด” และโรงเรียนหลายแห่งต้องสั่งปิดชั่วคราว คุณอาจนึกถึงภาพผู้คนใส่หน้ากากเดินท่ามกลางหมอกควัน แล้วถามตัวเองว่า “เรากำลังแก้ปัญหานี้ด้วยวิธีที่ถูกต้องจริงหรือ?” ฝุ่น PM2.5 ปัญหาของ "Externalities" หรือปัญหาของการไม่มี "สิทธิในทรัพย์สิน" ที่ชัดเจน? . ในคลิปวิดีโอ จาก CDC Bitcointalk EP3 เมื่อปี 2020 อ.พิริยะ สัมพันธารักษ์ ได้เสนอแนวคิดที่ขัดแย้งกับสิ่งที่รัฐและสื่อกระแสหลักมักพูดถึงเสมอเมื่อพูดถึงฝุ่น PM2.5 ว่า... “ฝุ่น PM2.5 ไม่ใช่ปัญหาที่จะถูกแก้ได้ด้วยการออกกฎหมายควบคุมหรือแจกหน้ากากฟรี...แต่ต้องแก้ด้วยการ สร้างกลไกตลาดและสิทธิในทรัพย์สินที่ชัดเจน เพื่อให้คนที่ก่อมลพิษต้อง จ่าย ให้กับผู้ได้รับผลกระทบ” . . แล้วมันเกี่ยวอะไรกับ Hazlitt ??? Henry Hazlitt กล่าวไว้ในบทแรกของ Economics in One Lesson ว่า ความผิดพลาดทางเศรษฐศาสตร์ส่วนใหญ่เกิดจากการมองแค่ผลกระทบเฉพาะหน้า และมองเฉพาะผลที่เกิดกับคนบางกลุ่ม แต่ละเลยผลระยะยาวกับทั้งระบบและมองไม่เห็น “สิ่งที่ไม่ปรากฏต่อสายตา” เช่นเดียวกับกรณีฝุ่น PM2.5 . การที่รัฐเข้ามาควบคุม เช่น การสั่งห้ามเผา อาจฟังดูดีในระยะสั้น แต่มันยังไม่มีแรงจูงใจทางเศรษฐกิจให้ผู้เผาหยุดทำ เพราะต้นทุนการก่อมลพิษยัง “ฟรี” ถ้ามลพิษมีต้นทุน คนก็จะคิดก่อนเผา . ลองนึกถึงแนวคิดของการซื้อ-ขายสิทธิในเชิงสมัครใจ (Voluntary Emissions Trading) ซึ่งต่างจากระบบ Cap-and-Trade ที่ภาครัฐเป็นผู้กำหนดเพดานและบังคับใช้ แต่ในแนวทางตลาดเสรีนั้น หากสิทธิในอากาศหรือพื้นที่ถูกระบุอย่างชัดเจน เจ้าของสิทธิสามารถตกลงซื้อขายกับผู้ก่อมลพิษได้โดยตรงโดยไม่ต้องพึ่งรัฐเป็นคนกลาง . แล้วในบริบทแบบ Hazlitt ถ้าคุณให้ความเป็นเจ้าของอากาศแก่คนในเมือง คนเหล่านั้นสามารถ “ฟ้องร้อง” หรือ “เรียกค่าเสียหาย” จากผู้ที่ปล่อยมลพิษได้ ซึ่งจะทำให้เกิดต้นทุนที่แท้จริงกับผู้ก่อมลพิษ . กลไกตลาดไม่ได้หมายถึง “แค่ปล่อยให้ทุกอย่างเป็นไปตามธรรมชาติ” แต่มันคือการสร้างระบบ “แรงจูงใจ” ที่ทำให้คนเลือกทางออกที่ดีที่สุดเอง โดยไม่ต้องมีใครมาบังคับ . ผมนึกถึงที่ Murray Rothbard เคยพูดไว้ว่า “สิทธิในทรัพย์สิน คือสิ่งเดียวที่จะทำให้ผู้คนมีแรงจูงใจในการดูแลสิ่งแวดล้อม ไม่ใช่คำสั่งจากเจ้าหน้าที่รัฐ” เพราะเมื่อคุณเป็นเจ้าของสิ่งใด คุณย่อมมีแรงจูงใจในการรักษามัน มากกว่าการที่รัฐสั่งให้คุณต้องแคร์ ดังนั้น แทนที่จะใช้ระบบ Cap-and-Trade ที่รัฐควบคุม บทความนี้เสนอแนวทางที่ไม่พึ่งพารัฐ เช่น ชุมชนหรือเอกชนรวมตัวกันตกลงไม่เผา และใช้กลไกจ่ายชดเชยกันเองหากละเมิดสิทธิ หรือกรณีเจ้าของบ้านฟ้องโรงงานที่ทำให้บ้านหรือพื้นที่ที่อยู่อาศัยเสียหาย ทั้งหมดนี้คือการใช้สิทธิในทรัพย์สินและกลไกกฎหมายแพ่งเพื่อสร้างแรงจูงใจ โดยไม่ต้องให้รัฐเข้ามาควบคุมหรือกำกับ แต่ยังคงอาศัยศาลเพื่อปกป้องสิทธิ เมื่อเกิดการละเมิด . . แล้วทำไมแนวคิดแบบให้รัฐควบคุมถึงล้มเหลวเสมอ...? Hazlitt เตือนว่า รัฐมักคิดว่าตัวเองมองเห็นผลดี แต่ไม่เคยมองเห็นผลเสียที่มองไม่เห็น เช่น เมื่อรัฐประกาศห้ามเผาซังข้าวโพดหรือฟางข้าวในภาคเหนือโดยเด็ดขาด ชาวไร่จำนวนมากที่เคยใช้วิธีเผาเพื่อคืนโพแทสเซียมและแร่ธาตุให้ดินแบบต้นทุนต่ำ ต้องหันไปซื้อปุ๋ยเคมีแทน ซึ่งมีราคาสูง กลายเป็นภาระทางเศรษฐกิจที่ถาโถมใส่เกษตรกรรายย่อยโดยตรง ทั้งที่พวกเขาไม่ได้มีทางเลือกอื่นมากนัก นี่คือ “ต้นทุนที่มองไม่เห็น” ตามที่ Hazlitt เตือน รัฐเห็นแค่ "ผลดีเฉพาะหน้า" เช่น ค่าฝุ่นลดชั่วคราว แต่ไม่เห็นผลเสียระยะยาวต่อความยั่งยืนของชุมชนเกษตรกรรม แล้วทั้งหมดนี้คือการเอื้อประโยชน์ให้คนกลุ่มหนึ่ง แต่กระจายต้นทุนไปให้ทั้งสังคม ซึ่งตรงกับที่ Hazlitt วิจารณ์ในหนังสือ . . แล้วเสรีภาพในตลาดกับอากาศที่สะอาด...ไปด้วยกันได้ไหม? อ.พิริยะ ยกตัวอย่างบิตคอยน์ว่าเป็นระบบที่ไม่ต้องพึ่งรัฐหรือคนกลาง แต่สามารถสร้างแรงจูงใจทางเศรษฐกิจให้คนทั่วโลกเข้าร่วมโดยสมัครใจ และตรวจสอบได้แบบโปร่งใสผ่านกลไกกระจายศูนย์ แสดงให้เห็นว่าแนวคิดตลาดเสรีสามารถทำงานได้จริงหากออกแบบแรงจูงใจให้เหมาะสม แนวคิดเดียวกันนี้ใช้ได้กับปัญหาฝุ่น PM2.5 ถ้าเรามองว่าอากาศคือทรัพยากรที่มีเจ้าของ และอนุญาตให้มีการซื้อ-ขายหรือฟ้องร้องโดยไม่ต้องพึ่งรัฐเข้ามาจัดการจากส่วนกลาง คำตอบคือ ได้...ถ้าเราให้ “ตลาด” ทำงาน -ถ้ามลพิษทำให้ที่อยู่อาศัยเสียหาย เราสามารถฟ้องผู้ก่อมลพิษได้ -ถ้าโรงงานต้องซื้อสิทธิปล่อยมลพิษ พวกเขาจะมีแรงจูงใจลดฝุ่น -ถ้าประชาชนขาย “เครดิตอากาศสะอาด” ได้ จะเกิดอาชีพใหม่ เช่น การปลูกป่าคาร์บอน นี่ไม่ใช่จินตนาการ แต่คือหลักคิดที่กำลังเกิดขึ้นในหลายประเทศ เช่น แคลิฟอร์เนีย เยอรมนี และสิงคโปร์ . . สรุปเศรษฐศาสตร์ของฝุ่น...อยู่ที่ใครจ่ายต้นทุน Hazlitt ไม่เคยพูดถึง PM2.5 โดยตรง แต่แนวคิดของเขาชัดเจนว่า ทุกนโยบาย ต้องถูกมองในแง่ของผลกระทบที่มองไม่เห็นในระยะยาวด้วย และนั่นคือสิ่งที่รัฐไทยและคนส่วนใหญ่ยังไม่เข้าใจเมื่อพูดถึงปัญหาฝุ่น ตลาดไม่ได้ไร้หัวใจ แต่มัน บีบให้คนรับผิดชอบในสิ่งที่ตัวเองก่อ ข้อเสนอเชิงนโยบาย -ส่งเสริมการกำหนดสิทธิในอากาศหรือสิทธิในพื้นที่อยู่อาศัยให้ชัดเจน -เปิดตลาดซื้อ-ขาย “เครดิตฝุ่นสะอาด” สำหรับภาคอุตสาหกรรม โดยเน้นว่าเป็นระบบที่เกิดจากความสมัครใจของภาคเอกชนหรือชุมชน ไม่อยู่ภายใต้การกำกับหรือควบคุมโดยรัฐ -ส่งเสริมการลงทุนเอกชนด้านเซ็นเซอร์วัดฝุ่นแบบกระจายตัว (decentralized air quality monitoring) . . แล้วคุณล่ะ คิดว่าฝุ่นควรจัดการโดยรัฐ หรือโดยตลาด 💬 คุณคิดว่าเราควรเริ่มสร้าง “ระบบสิทธิและแรงจูงใจเพื่อรักษาคุณภาพอากาศ” ได้อย่างไร หรือทำไมคุณยังเชื่อว่ารัฐควรเป็นคนจัดการควบคุมทั้งหมดอยู่ และถ้าคุณยังเชื่อว่ารัฐควรเป็นผู้ดูแลควบคุม ลองถามตัวเองดูว่ารัฐเคยสามารถจัดการอะไรได้อย่างมีประสิทธิภาพได้ในระยะยาวหรือไม่ หากคุณสนใจแนวคิดตลาดเสรีและเศรษฐศาสตร์แบบเข้าใจง่าย ๆ ผมแนะนำหนังสือ Economics in One Lesson โดย Henry Hazlitt หนังสือที่เปลี่ยนวิธีคิดของคนทั้งโลกเกี่ยวกับ “สิ่งที่มองไม่เห็น” ของเศรษฐกิจ มีฉบับแปลไทยแล้วนะ 🙃
เศรษฐศาสตร์เล่มเดียวจบ #EIOL #Siamstr
EconomicsinOneLesson #RightBook #PM25
-
 @ 234035ec:edc3751d
2025-03-22 02:34:32
@ 234035ec:edc3751d
2025-03-22 02:34:32I would like to preface this idea by stating that I am by no means a computer engineer and lack significant technical knowledge, and therefore may be overlooking significant obstacles to implementing this idea. My reason for writing this paper is in hopes that developers or others who are more "in the know" than me could provide feedback.
The Success of Polymarket
Over recent months, Polymarket has garnered many headlines—mainly for its accurate prediction markets surrounding the 2024 presidential election. On Polymarket, users can purchase futures contracts that will either pay out $1 in USDC at maturity if the prediction is correct or will become worthless if the prediction is incorrect. Market participants can freely trade these futures at the current price up until maturity, allowing for efficient price discovery.
We’ve known for quite some time that free markets are the most efficient way of pricing goods and services. Polymarket has now demonstrated just how effective they can be in pricing potential outcomes as well.
The issue I have with this application is that it is built on the Polygon network—a proof-of-stake side chain of Ethereum. Users are subject to KYC regulations and do not have the ability to create markets themselves. While the core idea is powerful, I believe it has been built on a foundation of sand. We now have the tools to build something similar—but much more decentralized, censorship-resistant, and sustainable.
A Bitcoin-Based Prediction Market
It seems to me that Chaumian eCash, in combination with Bitcoin and Nostr, could be used to create a truly decentralized prediction marketplace. For example, multiple eCash mints could issue tokens that represent specific potential outcomes. These tokens would be redeemable for 100 sats at a predetermined block height if the prediction is correct—or become irredeemable if the prediction is incorrect.
Redemption would be based on consensus from the chosen oracles—trusted Nostr Npubs—with strong reputations and proven track records. Anyone could create a market, and users could buy, sell, and trade eCash tokens privately. This approach preserves the power of markets while eliminating the need for custodians, KYC, or dependence on unreliable chains.
What we would have is a trust-minimized, privacy-preserving, Bitcoin-native prediction market that resists censorship and allows for true global participation. Feedback, critique, and collaboration are welcome.
Next Steps and Vision
The potential for system like this is immense. Not only would it enable peer-to-peer speculation on real-world outcomes, but it would also open the door to a more accurate reflection of public sentiment. With free market incentives driving truth-seeking behavior, these prediction markets could become powerful tools for gauging probabilities in politics, finance, sports, science, and beyond.
Each mint could specialize in a specific domain or geographic region, and users could choose the ones they trust—or even run their own. The competition between mints would drive reliability and transparency. By using Nostr for oracle communication and event creation, we keep the entire system open, composable, and censorship-resistant.
Markets could be created using a standardized Nostr event type. Resolution data could be posted and signed by oracles in a verifiable way, ensuring anyone can validate the outcome. All of this could be coordinated without a centralized authority, enabling pseudonymous participation from anyone with an internet connection and a Lightning wallet.
In the long run, this system could offer a viable alternative to corrupted media narratives, rigged polling, and centrally controlled information channels. It would be an open-source tool for discovering truth through economic incentives—without requiring trust in governments, corporations, or centralized platforms.
If this idea resonates with you, I encourage you to reach out, build on it, criticize it, or propose alternatives. This isn’t a product pitch—it’s a call to experiment, collaborate, and push the frontier of freedom-forward technologies.
Let’s build something that lasts.
Bitcoin is our base layer. Markets are our discovery engine. Nostr is our communication rail. Privacy is our defense. And truth is our goal.
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ d34e832d:383f78d0
2025-03-21 20:31:24
@ d34e832d:383f78d0
2025-03-21 20:31:24Introduction
Unlike other cetaceans that rely on whistles and songs, sperm whales primarily use echolocation and patterned click sequences to convey information. This paper explores the structure, function, and implications of their vocal communication, particularly in relation to their social behaviors and cognitive abilities.
1. The Nature of Sperm Whale Vocalizations
Sperm whales produce three primary types of clicks:
- Echolocation clicks for navigation and hunting.
- Regular clicks used in deep diving.
- Codas, which are rhythmic sequences exchanged between individuals, believed to function in social bonding and identification.Each whale possesses a monumental sound-producing organ, the spermaceti organ, which allows for the production of powerful sounds that can travel long distances. The structure of these clicks suggests a level of vocal learning and adaptation, as different populations exhibit distinct coda repertoires.
2. Cultural and Regional Variation in Codas
Research indicates that different sperm whale clans have unique dialects, much like human languages. These dialects are not genetically inherited but culturally transmitted, meaning whales learn their communication styles from social interactions rather than instinct alone. Studies conducted in the Caribbean and the Pacific have revealed that whales in different regions have distinct coda patterns, with some being universal and others specific to certain clans.
3. Social Organization and Communication
Sperm whales are matrilineal and live in stable social units composed of mothers, calves, and juveniles, while males often lead solitary lives. Communication plays a critical role in maintaining social bonds within these groups.
- Codas serve as an acoustic signature that helps individuals recognize each other.
- More complex codas may function in coordinating group movements or teaching young whales.
- Some researchers hypothesize that codas convey emotional states, much like tone of voice in human speech.4. Theories on Whale Intelligence and Language-Like Communication
The complexity of sperm whale vocalization raises profound questions about their cognitive abilities.
- Some researchers argue that sperm whale communication exhibits combinatorial properties, meaning that codas might function in ways similar to human phonemes, allowing for an extensive range of meanings.
- Studies using AI and machine learning have attempted to decode potential syntax patterns, but a full understanding of their language remains elusive.5. Conservation Implications and the Need for Further Research
Understanding sperm whale communication is essential for conservation efforts. Noise pollution from shipping, sonar, and industrial activities can interfere with whale vocalizations, potentially disrupting social structures and navigation. Future research must focus on long-term coda tracking, cross-species comparisons, and experimental approaches to deciphering their meaning.
Consider
Sperm whale vocal communication represents one of the most intriguing areas of marine mammal research. Their ability to transmit learned vocalizations across generations suggests a high degree of cultural complexity. Although we have yet to fully decode their language, the study of sperm whale codas offers critical insights into non-human intelligence, social structures, and the evolution of communication in the animal kingdom.
-
 @ 7bc05901:8c26d22b
2025-03-21 19:47:15
@ 7bc05901:8c26d22b
2025-03-21 19:47:15Decentralization is a beautiful return volley to the censorship regimes that have ruled American social media, but the decentralization piece isn't the biggest impact Nostr is having on me. The empowerment and encouragement to start building are what overwhelms. Since I began sending zaps just a few weeks ago, every idea I have had for an app over the last decade is organically re-emerging as executable Nostr apps.
The rise of AI alongside Nostr's invention/discovery is serendipitous for someone who doesn't have the coding experience to develop an app from scratch like myself. It is also a great moment for apps that had a social feature -- which was essentially every app. "Connect it using Facebook" was such a non-starter for me. I live in a small town where Facebook is a gossip cesspool. There are intriguing communities there, sure, but the overwhelming dread that overcomes me when I open that app doesn't justify digging for the socially-delightful gems. Further, any app that integrates with facebook is or becomes a variation on an already existing feature that META has engineered into their platform -- they want, they need your eyeballs. On their site.
Nostr makes no such demands. It doesn't care which site is being used to access the protocol, and what features exist on that site. It is available to help, secure a user's identity, and doesn't make many demands in return.
My friend and local farmer Ryan and I have discussed an app for years, built it and rebuilt it using different tools, but we ultimately got distracted by more pressing and less complicated projects. I think a huge barrier to execute it was the sense that it would be impossible to achieve any network effects, plus the thought of managing the social side was overwhelming. It required us to need really powerful tools, and to maintain a lot of data that we didn't really want to hold onto. It was essentially an app for local food producers and consumers. With Nostr at play, we could build something like this and simultaneously onboard our local community to the Nostr protocol while also providing a lightweight solution to managing the complicated part of an online marketplace. The lightning payments come as an added bonus.
We are tracking the use of another app which is sweeping through local food producers, which is only in its beta phase, and restarting our build of a marketplace that is worth building and encourages a sustainable local food supply, this time with a protocol that reduces 90 percent of the annoying part of that build, and doesn't require anyone spend time on Zuckerberg's playground.
-
 @ 6a6be47b:3e74e3e1
2025-03-21 18:45:32
@ 6a6be47b:3e74e3e1
2025-03-21 18:45:32Hey frens! Today, I spent a big chunk of the morning painting with watercolors. This is only the second time I've completed a piece using this technique in a long while. It feels like coming back home after a vacation: you enjoyed the time away and relaxed, but when you're lucky enough to have a safe space to call home, there's really nothing like it. 🖼️
🎨 That's exactly how I feel about painting with watercolors again. I'm really excited to share what I've been working on with you soon. In the meantime, I've got a new blog post up about Ostara and the Spring Equinox. ⭐️Today, I just feel so blessed and excited about the future. I'm simply soaking up the moment, I guess. I hope you're feeling the same way too! Today, I also whipped up some mini veggie quiches chef's kiss.
 🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it!
🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it! -
 @ 6bae33c8:607272e8
2025-03-21 18:23:28
@ 6bae33c8:607272e8
2025-03-21 18:23:28I put Beat Chris Liss 3 in quotes because technically this was not a Beat Chris Liss league — I just bought it at the last minute to get an extra league. In any event, I drew the seventh spot, and here are the results:
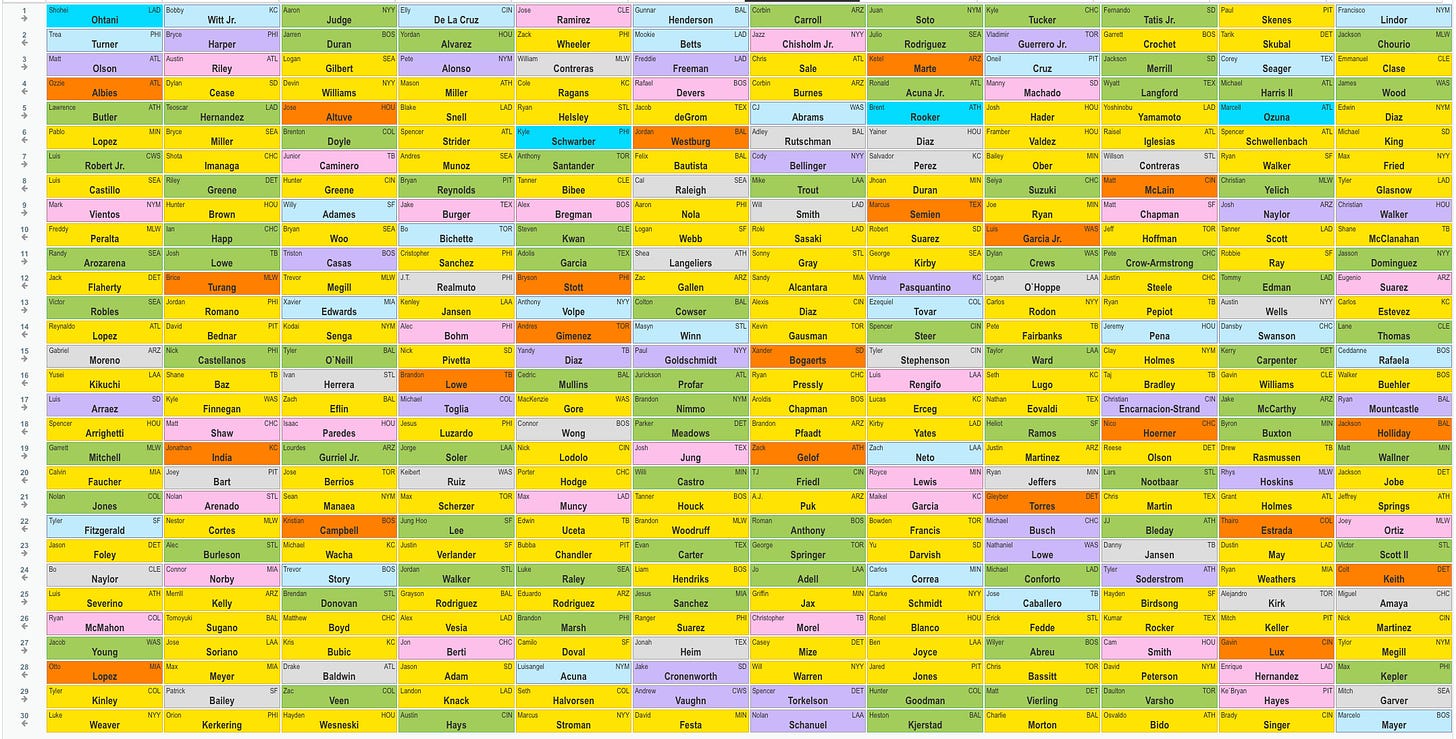
1.7 Corbin Carroll — He’s been hitting home runs this spring, a signal his shoulder is healthy. You know he’ll run, and given how he performed at the end of last year, I’d expect the batting average to bounce back too.
2.8 Jazz Chisholm — I want to see what he can do with a full year in Yankee Stadium. He’s a health risk, but he was a 20-20-ish player in Miami with only 100 games in 2023. It’s also nice that he qualifies at 3B and OF. I considered Mookie Betts, who slipped, but I’m concerned about severe weight loss from an illness undermining the first half of his season.
3.7 Chris Sale — He’s a Hall of Fame level pitcher with his health and form back. Remember when Justin Verlander faded in his 30s and then got it back together? I expect a few good years from Sale before he declines again.
4.8 Corbin Burnes — I don’t really even like Burnes, but he slipped a full round past ADP, and I value-took.
5.7 C.J. Abrams — I love this pick, probably my favorite of the draft. Abrams is a 20-30 player despite attitude issues. What if he matures and gets it together at age 24?
6.8 Adley Rustchman — I didn’t see anything I liked, and I was light on power. One way to get a leg up power-wise is to draft elite catchers.
7.7 Cody Bellinger — I like him with Yankee Stadium’s short porch, a few steals from a first-base-eligible player and also outfield eligibility.
8.8 Mike Trout — I had enough pitching and speed, but I needed some power, and Trout still has as much as anyone if he could ever play 100-plus games. He’s healthy now at least.
9.7 Will Smith — A second top catcher to pair with Rutschman. I was light on power through five rounds, but my next four picks were 20-plus HR catchers, Bellinger in Yankee Stadium and Trout.
10.8 Roki Sasaki — He slipped a couple rounds after a rough outing in Japan, but he was still throwing 100 with nasty movement. Another value-take.
11.7 Sonny Gray — A favorite old warhorse in a good pitcher’s park. I really wanted Sandy Alcantara, but Gray’s ADP was higher, so I thought there was a better chance to get Alcantara on the way back.
12.8 Sandy Alcantara — Turns out I thought right. I love Alcantara, who was going in the third round a couple years ago, now that he’s healthy and throwing 100 mph again.
13.7 Alexis Diaz — Taking Alcantara cost me my two go-to closers, Kenley Jansen and Jordan Romano, both of whom went earlier than usual, so I pivoted to Diaz. I thought this was a mistake at first — Diaz has been bad this spring, and he wasn’t even good last year, either, but he’s the closer until further notice, and a couple spring outings shouldn’t move the needle that much.
14.8 Kevin Gausman — Another old warhorse, coming off a down year, possibly due to injury. His velocity has been back up this spring too.
15.7 Xander Bogaerts — Another ADP value-take. Bogaerts had double digit homers and steals in 111 games last year and is a good bet to hit for a decent average.
16.8 Ryan Pressly — Another shaky closer, Pressly had three walks in an inning against the Dodgers, but he’s probably not losing the job over one ugly but scoreless outing.
17.7 Aroldis Chapman — Named the Red Sox closer, Chapman is probably the best of the three I drafted thus far. His ADP was lower because he was only given the role a couple days ago. Chapman perfectly fits the old warhorse mold I like too.
18.8 Brandon Pfaadt — I didn’t really need another starter, but he was the best player left on the board, and you always run out of pitching.
19.7 Zack Gelof — He strikes out a ton, but he went 17-25 last year in 138 games as a rookie, and now he gets to play in a minor-league band box. Lawrence Butler went 22-18 and is going in the fifth round!
20.8 T.J. Friedl — I was light on OF, and Friedl is one. He has a little pop, runs and is expected to lead off for the Reds in the best non-Coors hitting park in baseball.
21.7 A.J. Puk — I was still a little light in saves, and Puk is in the running for the Arizona job.
22.8 Roman Anthony — I don’t know if he’ll break camp with the Red Sox, but he was the remaining player I would have felt worst getting snaked on. He doesn’t have much left to prove in the minors.
23.7 George Springer — He went 20-20 in 2023 and 19-16 last year. He could be done, but at 35 he’s not ancient.
24.8 Jo Adell — I needed to fill in the outfield, and Adell should play, run and hit for power. The strikeouts and batting average risk are bad, but he’s still young enough to improve.
25.7 Griffin Jax — He’s a top reliever, next in line for saves and closer Jhoan Duran isn’t very good.
26.8 Christopher Morel — I needed a corner and Morel is one. (If I needed a mushroom, this would also hold.) He hit .196 last year, but he has good pop and should play OF for the Rays in a small minor-league park.
27.6 Casey Mize — The former No. 1 overall pick has looked good this spring, and he’s completely healthy.
28.6 Will Warren — Warren should get a shot in the Yankees rotation, given the injuries to Gerrit Cole and Luis Gil.
29.6 Spencer Torkelson — Another former No. 1 overall pick for the Tigers, Torkelson hit 31 homers in 2023 and should get another shot this year given his strong spring.
30.6 Nolan Schanuel — I just wanted an extra corner with regular playing time heading into the year. He runs a little and had 13 HR, but in a full season of at-bats.
Roster By Position:
C Adley Rustchman/Will Smith
1B Cody Bellinger
2B Xander Bogaerts
3B Jazz Chisholm
SS C.J. Abrams
CI Christopher Morel
MI Zack Gelof
OF Corbin Carroll/Mike Trout/T.J. Friedl/Roman Anthony/George Springer
UT Jo Adell
SP Chris Sale/Corbin Burnes/Roki Sasaki/Sonny Gray/Sandy Alcantara/Kevin Gausman
RP Alexis Diaz/Ryan Pressly/Aroldis Chapman
B Brandon Pfaadt/A.J. Puk/Griffin Jax/Casey Mize/Will Warren/Spencer Torkelson/Nolan Schanuel
-
 @ 6ad3e2a3:c90b7740
2025-03-21 18:21:50
@ 6ad3e2a3:c90b7740
2025-03-21 18:21:50There are two ways things happen in this world: top-down and bottom-up. Top-down is via authoritarian edict, i.e. fascism, no matter how benign-seeming. It is the government imposing a tax, incentivizing a behavior, creating a new law. Bottom-up is the organic process of people doing what interests them voluntarily, what benefits them, what they decide is best individually.
There is but one legitimate role for top-down and that is in creating good conditions for bottom up. The US Constitution is fascism in that it forces you to adhere to its edicts as the supreme law of the land. But it’s also an effective boundary creating the necessary conditions for free markets, free expression, creativity and prosperity.
All governments are fascistic in that they use force to achieve their agendas. But the best ones use only the minimum necessary force to create conditions for bottom-up prosperity. There is no other kind of prosperity.
. . .
Governments aren’t the only entities that are fascistic. Schools, corporations, institutions and individuals, almost invariably, are too. Yes, I am a fascist and very likely so are you. Don’t believe me? Do you have a voice inside your head telling you what you must get done today, evaluating your progress as a person, critiquing and coercing you into doing things that are “good” for you and avoiding ones that are “bad”? If so, you are fascist.
Why not just trust yourself to make the right choices? Why all the nudging, coaxing, coaching, evaluating and gamifying? Who is this voice, what gives it the authority, the requisite wisdom to manage your affairs? Haven’t all your shortcomings, disappointments and general dissatisfactions taken place despite its ever-presence? What makes you think you are better off for having had this in-house micromanagement?
. . .
The top-down edicts that rule our lives are by and large unnecessarily oppressive. Yes, we should create some good top-down conditions for bottom up organic thriving like buying healthy food, getting fresh air, not consuming excessive amounts of alcohol or drugs, but the moment to moment hall-monitoring, the voice that requires you to achieve something or justify your existence? That’s fascism.
. . .
The mind is a powerful tool when it comes to planning, doing math or following a recipe, but if it can’t be turned off, if it’s not just optimizing your path from A to B, but optimizing YOU, that’s fascism.
. . .
I think about the problem of human governance through this lens. I imagine everyone charged with power over a polity has an agenda, and that agenda, insofar as it requires force to achieve, is fascistic. They want it to go this way rather than that way, and some people don’t agree. The quality of leadership then is the extent to which that force is used to preserve the bottom-up freedom of the individual to pursue his interests without undue interference, either from authorities themselves or other individuals who would unduly disrupt him.
The Constitution is an excellent guideline for this, and I surely won’t be able to come up with a better one in this Substack. It’s why I support Trump’s efforts to trim the top-down public sector and return productivity to the bottom-up private one, why I support deportation of adjudicated criminals who are here illegally, but oppose removing people with green cards or on valid student visas for protesting via constitutionally protected speech.
I don’t root for politicians like they play for my favorite sports team. I root for the freedom of the individual, the possibility of a largely bottom-up society wherein prosperity is possible. And I do this while knowing it will never happen exactly the way I would like, so long as I am bound by the fascism coming from inside the house.
-
 @ bf95e1a4:ebdcc848
2025-03-21 17:03:01
@ bf95e1a4:ebdcc848
2025-03-21 17:03:01This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Preface
At the time of writing, it is New Year’s Day, and 2019 has just begun. For once, I have a resolution to live up to: I’ve promised myself to write a page per day every day this year until I have something real to publish. In June 2018, I published my first book, Three Minute Reads on Bitcoin — A Year of Thoughts. The book consisted of articles I had published online from May 2017 up to that point. This time it’s different. Instead of a mere collection of articles, I intend to write a “proper” book. A book that explains why Bitcoin is the most important invention of our lives.
I didn’t choose Bitcoin; it chose me. I had been trying to figure out how the world worked under the hood all my life, and then this simple idea of absolute scarcity popped up. It had a profound impact on how I view human interaction. Because of my curious nature, I instantly fell deep into the rabbit hole. I decided to educate myself on how this mysterious technology worked, and that got me into Austrian economics, which expressed very clearly what I had always suspected — that you really can't create value out of thin air.
In this book, I will try to explain every aspect of what makes this technology so special, what sets it apart from the abundant shameless copies of it, what’s wrong with our current system, and what the future might look like. In just two days from the time of writing these words, we’ll celebrate the ten-year anniversary of the Genesis Block when the Bitcoin blockchain came into being. That block contained a message, a newspaper headline that read: “03/Jan/2009 Chancellor on brink of second bailout for banks”. No one knows why Bitcoin’s mysterious creator, Satoshi Nakamoto, chose to include this in the Genesis Block. There is also some debate on whether the Genesis Block was actually mined on the 3rd of January since the next block wasn’t mined until six days later. Somehow, Satoshi managed to stay hidden and weave several layers of mystique into the fabric of Bitcoin from the very beginning, which is part of what makes its conception so immaculate. This book aims to strip Bitcoin of its shady cloak and illuminate its true nature. After all, the only thing any person can do about Bitcoin now is to study it.
Foreword
My journey down the Bitcoin rabbit hole has provided me with a newfound clarity of how our world should be perceived. In the same way that getting married and having my first child were beautiful life-changing events, discovering Bitcoin was a new chapter in my life. I can easily divide my life into two distinct periods: before and after Bitcoin.
Before discovering Bitcoin, life was perplexing. For years, even dating back to my school days, I had an innate sense that something was amiss in the world. Although I wasn’t a good student by any means, it was obvious back then that many aspects of life simply didn’t add up.
One thing that I was sure of was that money was corrupt. However, it took me a while to realize that money itself is fundamentally corrupt. Furthermore, what is typically taught and accepted as money by society is a perversion of what money should be. These are the first steps of understanding Bitcoin, which require you to admit that you have been fooled and lied to all your life. The hard lessons of hard money.
The way I see it, the revelation about the true nature of money is akin to a bracing cold shower that wakes you up to reality. Emerging from that cold shower is an incredibly liberating and invigorating sensation. Unfortunately, many individuals are not motivated enough to take that crucial step into the chilly waters. Instead, they will later experience an ice-cold bucket of water being dumped on their head unexpectedly whilst naked on a cold winter’s day.
The year 2020 was a watershed moment in my journey towards truth, and it was Bitcoin that served as my guide. As the world grappled with an unprecedented black swan event in March of that year, every asset, including bitcoin, took a severe hit. However, what followed in the subsequent months was the largest money-printing expedition in history. A tsunami of stimulus was pumped into the markets. The outcome was a K-shaped recovery. Small, honest brick-and-mortar businesses continued to suffer while many of the largest conglomerates not only rebounded but reached all-time highs. This ludicrous, short-sighted plan, known as quantitative easing, resulted in the most pronounced example of the Cantillon effect in human history, a fact that should have served as a wake-up call for anyone who was not already suspicious of the events surrounding the global financial crisis of 2008.
Since entering my post-bitcoin life, I’ve experienced a newfound coherence. The transition was not exactly instant, instead it has been a continuous process of discovering bitcoin over and over again, and I owe many of these enlightening moments to Knut Svanholm’s writing, for which I’m grateful.
While Knut’s books do not serve as a technical guide for Bitcoin, they provide a deep and philosophical introduction to a new era of money; the separation of money and state. The end of fiat money.
The creation of fiat money, a practice that emerged with the rise of central banking, has been the source of significant damage to human civilisation. Central banking, championed by Keynesianism, has granted immense power to centralized entities, allowing them to dictate fiscal policies and control the creation of money for billions of people. The very idea of a single entity wielding such vast authority and determining the economic fate of entire populations is utter madness. The state monopolizes money because it allows them to print money rather than having to directly tax people (but it still doesn’t stop them). Printing money is more easy, subtle and lucrative than direct taxation. And this continual erosion of purchasing power can be readily associated with the evident decline and deterioration of modern society.
At the heart of the issue is the importance of individual property rights. The money that individuals earn and save is their property, not the state’s. The state’s duty (should there be a need for it to exist) is to safeguard private property, not to continually debase or confiscate it. A centralized power that constantly devalues your hard-earned money and time by printing money is both morally and ethically wrong. Every individual has the right to turn their hard work into savings that they can rely on for the future.
In Bitcoin: Sovereignty through Mathematics, Knut not only delves into the fundamental principles underlying Bitcoin’s creation but also presents the groundbreaking concept of absolute scarcity. Bitcoin’s limited supply of 21 million and the impossibility of creating more due to its protocol creates a condition of absolute scarcity, a first in human history. Absolute scarcity, coupled with Knut’s poetic description of Bitcoin’s creation as "an immaculate conception," emphasizes its unique and revolutionary nature. The term "immaculate conception" highlights the fact that Bitcoin’s creation was not based on any pre-existing financial system but rather emerged from a set of mathematical principles that ensure its security and scarcity. The conditions that gave birth to Bitcoin will never be replicated, which further cements Bitcoin’s status as a one-of-a-kind element that will revolutionize the way we view and use money. Absolute scarcity aligns with the Austrian school of economics’ views on money, which argue that sound money should be scarce, durable, and difficult to counterfeit. Bitcoin ticks all the boxes for sound money, laying the ground for a genuine foundation to end the era of so-called cheap or easy money.
In the follow-up to this book, Bitcoin: Independence Reimagined1, Knut presents us, using plain logic and reasoning, the primitive constraints of the current fiat system and status quo governance. These structures, which we have so readily accepted, are gradually stripping us of our freedoms. By highlighting these shortcomings, he urges us to critically examine them and envision a future where we exercise greater autonomy over our lives, both financially and socially. Bitcoin’s simple and secure existence stands in contrast to the coercive and interventionist nature of the fiat system. Bitcoin is sincere; it neither favors nor opposes us. Bitcoin simply exists. Coming to terms with this truth is both humbling and liberating.
Knut’s writing, with its clear and elegant style, offers insightful guidance for those interested in exploring the deeper implications of Bitcoin beyond its function as a mere currency, recognizing it as a truly transformative breakthrough. A breakthrough that provides us with hope, a viable solution to reverse the degeneracy and decadence plaguing humanity.
Prince Philip of Serbia, 21st February 2023
Footnotes:
1. This foreword was originally written for a combined volume containing both Bitcoin: Sovereignty Through Mathematics and Bitcoin: Independence Reimagined.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 2fb77d26:c47a6ee1
2025-03-21 15:49:40
@ 2fb77d26:c47a6ee1
2025-03-21 15:49:40»Pershing II« – das war eines der ersten englischen Wörter, das mir als Kind geläufig war. Es handelt sich um die Typenbezeichnung einer US-Mittelstreckenrakete, einer nuklearen Boden-Boden-Rakete, die mit einem thermonuklearen Sprengkopf vom Typ W85 ausgestattet war, eine Reichweite von etwa 1.800 km hatte und somit von Süddeutschland aus Ziele im westlichen Russland binnen fünf Minuten erreichen konnte. Es war Anfang der 1980er Jahre. Die Zeit des Kalten Krieges. Eine Bezeichnung, die George Orwell mit seinem Essay »You and the Atomic Bomb« (Du und die Atombombe) im Jahre 1945 geprägt hatte. Die Fronten waren verhärtet.
Die westdeutsche Friedensbewegung protestierte lautstark gegen die Stationierung von Atomsprengköpfen auf heimischem Boden. Nachdem die im NATO-Doppelbeschluss vom 12. Dezember 1979 vereinbarten Abrüstungsverhandlungen zwischen den Atommächten jedoch erfolglos geblieben waren, entschied der Deutsche Bundestag am 22. November 1983, der Stationierung von US-Atomwaffen im Lande zuzustimmen. Diese war 1985 abgeschlossen und ganze 120 Exemplare der todbringenden Massenvernichtungswaffe in der Bundesrepublik verteilt worden. Außer Deutschland tat kein Land den USA diesen Gefallen.
Ich hatte die militärische Artikelbezeichnung »Pershing II« im Radio aufgeschnappt, welcher zu Hause fast durchgehend in Betrieb war, und später ein paar Bilder der Raketen in den Abendnachrichten gesehen. Noch gab es nur ARD, ZDF und das Regionalprogramm. Dementsprechend rar waren visuelle Informationen. Und aufgrund meiner frühen Begeisterung für Fluggeräte aller Art, zeichnete ich daraufhin ständig Raketen. Da ich außerdem bereits in diesem zarten Alter von fünf oder sechs Jahren extrem von Musik angetan war und durchweg versuchte, englische Songtexte, zum Beispiel von den Beatles, dem Klang der Stimmen folgend nachzusingen, übte auch der fremd klingende Begriff »Pershing II« eine gewisse Faszination auf mich aus.
Was mir meine Eltern diesbezüglich sagten oder erklärten, kann ich leider nicht mehr erinnern – als erklärte Pazifisten nahmen sie die latente Gefahr eines Nuklearkrieges aber sicher nicht mit der spielerisch-kindlichen Leichtigkeit, die ich im Umgang mit gemalten oder gebastelten Raketen an den Tag legte. Das Thema nukleare Kriegsführung beherrschte die Nachrichten dieser Zeit und erzeugte Angst. Denn Militärstrategen sprachen Anfang der 1980er Jahre allen Ernstes davon, dass der Atomkrieg zwischenzeitlich präziser und somit auch führbarer geworden sei. Damals wie heute – absoluter Irrsinn.
Neben der Berlin-Blockade 1948/1949 und der Kuba-Krise, war die Auseinandersetzung um die Stationierung von Mittelstreckenraketen in Westeuropa von 1979 bis 1983 also eine der drei kritischsten Phasen des Kalten Krieges.
Nie war die Welt einem fatalen wie letalen nuklearen Schlagabtausch der Supermächte näher als zu diesen drei Zeitpunkten in der Geschichte. Bis heute, so scheint es.
Denn die stetig eskalierende Ukraine-Krise rückt dieses vergessen geglaubte Horror-Szenario wieder in den Fokus der Öffentlichkeit. Polit-Darsteller wie der Maoist und China-Fan Robert Habeck äußern dieser Tage dummdreist, keine Angst vor einem Dritten Weltkrieg zu haben. Sogenannte Sicherheitsexperten erklären im ZDF, dass man sich vor Putins Bomben nicht fürchten solle, obwohl man in Mainz permanent Angst schürt und schon am 5. Mai 2022 titelt, »Moskau simuliert Atomangriff in Kaliningrad«.
Der »Beobachter Gesundheit« gibt Tipps dazu, wie man die Panik vor einem Atomkrieg mental in den Griff bekommen kann, während das deutsche BBK (Bundesamt für Bevölkerungsschutz und Katastrophenhilfe) der Bevölkerung bereits empfiehlt, im Zuge der Ukraine-Krise Notvorräte anzulegen und Marschgepäck bereitzuhalten. Auf der Webseite »wikiHow« findet sich ein sehr umfassender, bebilderter Ratgeber mit dem Titel »Einen Atomkrieg überleben«. Beim Lesen der zahlreichen, mutmaßlich nur bedingt hilfreichen Tipps zur Meisterung der nuklearen Apokalypse dürfte jedem normalen Menschen etwas mulmig werden.
Hofberichterstatter Ruprecht Polenz lässt sich beim Propaganda-Multiplikator ZEIT ONLINE am 30. April 2022 dennoch zu der wagemutigen Formulierung verleiten, »wer einen Atomkrieg verhindern will, darf Putin nicht gewinnen lassen«. Solch ein Statement ist nicht nur falsch und realitätsfremd, sondern zeugt gleichsam von der bewussten Negierung von Faktenlage und historischen Hintergründen zur Ukraine-Krise. Dabei könnte man es durchaus besser wissen.
Die RAND-Corporation, ein im Jahre 1948 gegründeter, einflussreicher Think Tank der US-Hegemonie, veröffentlichte zum Beispiel schon im Jahr 2019 ein vielsagendes, 354 Seiten umfassendes Strategiepapier unter der Überschrift »Overextending and Unbalancing Russia«. Frei übersetzt: Eine Strategie, um Russland überzustrapazieren und aus dem Gleichgewicht zu bringen – ökonomisch, militärisch und gesellschaftlich – mit dem singulären Ziel, die geopolitische Dominanz der Vereinigten Staaten zu bewahren. Ein durchdachtes Drehbuch zur finalen Erniedrigung und Bezwingung des ewigen Klassenfeindes sowie dem Erhalt der unipolaren Weltordnung, der Pax Americana.
Der Ansatz der RAND-Corporation: Die Osterweiterung der NATO forcieren, das Ansehen Russlands in der Welt zerstören, kostenintensives, nukleares Wettrüsten, die Ukraine bewaffnen, um einen militärischen Stellvertreterkonflikt mit Putin zu provozieren, um die ehemalige Sowjetunion anschließend mittels internationaler Sanktionen – legitimiert durch den brodelnden Krieg – finanziell in die Knie zu zwingen.
Verblüffend, wie sehr doch die im RAND-Strategiepapier aufgezeigte Vorgehensweise den aktuellen Geschehnissen an den Außengrenzen des Riesenreiches gleicht. Fast macht es den Anschein, als folgten die Geostrategen in Washington den Empfehlungen ihrer kostspieligen Think Tanks. Dies ließ sich auch im Zuge der Corona-Krise beobachten, die im Ablauf fraglos dem von der Rockefeller-Stiftung erarbeiteten Pandemie-Szenario »Lock Step« glich, wie Journalist Norbert Häring bereits am 28. Mai 2020 ausführlich berichtet.
Was das totalitäre Krisen-Drehbuch der RAND-Corporation nicht detailliert behandelt, sind die akuten Risiken einer potenziellen nuklearen Eskalation. Denn es endet mit dem möglichen Aufkeimen eines militärischen Konflikts und schließt schlicht mit dem Hinweis:
»Auch wenn die US-Armee nicht direkt an der Operation beteiligt ist, wird sie eine Schlüsselrolle bei der Abmilderung der Folgen spielen. Wie bereits erwähnt, bergen alle Maßnahmen, die der Schwächung Russlands dienen, einiges an Risiko. Infolgedessen werden das Abschreckungspotential sowie die operativen Fähigkeiten des US-Militärs in Europa gestärkt werden müssen. Es besteht die Möglichkeit, dass die Spannungen mit Russland zu einem Konflikt eskalieren.«
Die USA betrachten den Einsatz von Atomwaffen dabei offensichtlich als probates Mittel. Warum sonst modernisieren die Amerikaner seit Jahren ihr Arsenal und geben Milliarden US-Dollar dafür aus? Das macht eigentlich nur Sinn, wenn man plant, diese Waffen irgendwann einzusetzen. Der »Plot« für die Events nach dem Aufflammen einer militärischen Auseinandersetzung mit Russland ist vermutlich Verschlusssache und liegt nur Eingeweihten im Weißen Haus, Pentagon, CIA-Hauptquartier sowie den Verbündeten in EU und NATO-Hauptquartier vor.
Das ist bedauerlich. Denn ein Einblick in die aktuellen militärischen Planspiele und strategischen Szenarien der NATO-Hegemonie wäre hilfreich, um zu verstehen, ob die Arroganz des Westens tatsächlich einen Punkt erreicht hat, an dem man einen Atomkrieg in Kauf nehmen würde, um Russland und China auf ihre Plätze zu verweisen und im globalen Club der Technokraten am Kopfende zu sitzen. Um einen Konflikt der Systeme – Kapitalismus, Sozialismus, Kommunismus – handelt es sich nämlich nicht, auch wenn Medien dies gerne so darstellen, sondern um Machtkämpfe innerhalb der internationalen Oligarchie. Die drei Machtblöcke kämpfen um Vorherrschaft in der totalitären Weltordnung der nahen Zukunft.
Die Frage ist nur: Tun sie dies einvernehmlich – oder handelt es sich an Russlands Grenzen um ernsthafte, kriegerische Auseinandersetzungen, die in letzter Konsequenz militärisch entschieden werden müssen? Das RAND-Strategiepapier scheint davon auszugehen, dass Wirtschafts- und Informationskrieg, begleitet von NATO-Drohgebärden, ausreichen, um das Rennen zu Gunsten des Wertewestens zu entscheiden. Es gilt zu hoffen, dass diese Interpretation des Schriftstücks zutrifft. Ansonsten läuft die moderne Zivilisation Gefahr, sich in die Steinzeit zurückzubomben. Wie das aussieht, zeigt eindrücklich der Film »The Day After« (Der Tag danach) aus dem Jahre 1983.
Der zwei Stunden lange Streifen von Regisseur Nicholas Meyer ist bildgewaltig, beängstigend, ernüchternd und deprimierend. Er zeigt nicht nur, wie binnen weniger Tage aus einem Kalten Krieg ein Atomkrieg wird, sondern auch, was dessen schreckliche Folgen sind. Schon ein kurzer, etwas mehr als acht Minuten langer Zusammenschnitt macht klar, dass man ein absoluter Narr sein muss, um keine Angst vor thermonuklearen Angriffen zu haben.
Im Film gibt der US-Oberbefehlshaber nach der Zerstörung des NATO-Hauptquartiers den Befehl zum Atomschlag. Das entsprechende NATO-Protokoll wird aktiviert und die Raketensilos einsatzbereit gemacht. Das Drehbuch lässt offen, wer den Erstschlag führt. Klar ist, dass sobald die Sprengköpfe des Westens unterwegs sind, Russland einen Gegenangriff mit 300 Interkontinentalraketen auslöst und die Vereinigten Staaten in die Steinzeit bombt.
Überall im Land der unbegrenzten Möglichkeiten steigen feurige Atompilze in den Himmel. Metropolen werden in Sekunden ausradiert, Lebewesen, Pflanzen und Gebäude verdampfen in Feuersbrünsten um den Einschlagsort, ganze Landstriche werden vom Erdboden getilgt – und schon in den ersten Minuten nach Explosion der Nuklearsprengköpfe sterben weite Teile der Bevölkerung. 90 Millionen innerhalb weniger Stunden, wie eine Simulation mit dem etwas unheimlichen Titel »Plan A« der Princeton-Universität von 2019 berechnet hat.
Der eigentliche Horror beginnt allerdings erst. Denn die schlimmsten Szenen des Films sind jene, die den Zustand der Welt zwei Wochen nach den Atomschlägen zeigen. Im Land herrscht Anomie. Chaos und Zerstörung, wohin man schaut. Vorindustrielle Zustände. Die Städte sind unbewohnbar und die Überlebenden leiden an Strahlenkrankheit. Haare und Zähne fallen aus. Bei manchen binnen weniger Stunden oder Tage, bei anderen dauert es Wochen. Ein grausamer Tod auf Raten. Alles stirbt, siecht dahin. In den Ruinen entstehen Flüchtlingslager. Seuchen brechen aus. Militärkommandos erschießen willkürlich Menschen. Recht, Gerichte und Prozesse gibt es nicht mehr. Und um zu überleben, bewaffnen sich schlussendlich auch die Zivilisten und töten sich gegenseitig. Absolute Barbarei.
»The Day After« erklärt nicht, wer diesen Krieg gewinnt, nennt keinen Sieger. Vermutlich, weil Regisseur Nicholas Meyer schmerzlich bewusst war, dass es bei einem ausgewachsenen Atomkrieg keine Gewinner geben kann.
Er bedeutet das Ende der modernen Zivilisation. Nicht umsonst hat Albert Einstein früh vor militärischem Missbrauch entsprechender wissenschaftlicher Erkenntnisse gewarnt. So lässt der Streifen aus Zeiten das kalten Krieges auch das Ende offen. Kein Hollywood-Finale. Kein Happy End. Die beklemmenden Gefühle bleiben. Weder Will Smith noch James Bond tauchen auf, um die Welt in letzter Minute doch noch zu retten. Sie ist kaputt. Tot. Eine nuklear verseuchte Wüste. Kein Hoffnungsschimmer am Horizont.
Wer das Pech hatte, die Erstschläge zu überleben, stirbt langsam, aber sicher – und vor allem qualvoll.
Vielleicht sollten Spitzenpolitiker, Dogmatiker, Propagandisten und Kriegshetzer von heute sich diesen Film einmal in Ruhe anschauen, bevor sie leichtfertig derartige Optionen in Betracht ziehen. Ich habe »The Day After« nur ein einziges Mal in meinem Leben gesehen – wenige Monate, nachdem ich den Begriff »Pershing II« das erste Mal als kleines Kind im Radio hörte und meine Eltern neugierig fragte, was es damit auf sich hat – das war ausreichend. Die Eindrücke wirken bis heute. Ich bin mir auch mehr als dreißig Jahre später immer noch der unverrückbaren, indiskutablen Tatsache bewusst, dass es niemals zu einem Atomkrieg kommen darf. Jeder, der diesen Film gesehen, wird das unterschreiben.
Ich jedenfalls werde nie vergessen, wie ich eines nachts heimlich im dunklen Wohnzimmer der heimischen Dachwohnung ganz nahe vor dem Fernseher saß. Eigentlich durfte ich nur ein paar Mal in der Woche ausgewählte Kindersendungen anschauen. Aber meine Eltern schliefen bereits. Es muss circa 23:00 Uhr gewesen sein, denn nach den Spätfilmen war damals in der Regel Sendeschluss. Und das was war meist gegen eins oder halb zwei.
Just als ich den kleinen Röhrenfernseher anschaltete, begann »im Ersten« der bis heute in mir nachhallende Spielfilm. Der Tag danach. Zunächst begeistert von den vielen Raketen und irgendwie noch fasziniert von den mir bis dato unbekannten, riesigen Explosionen, die Atombomben auslösen, blieb ich gebannt sitzen. Wie versteinert. Bis zur Schlussszene, in der sich eine Handvoll strahlenverseuchter, zerrissener, verrottender Menschen, die kaum noch Haare auf dem Kopf haben und aussehen wie Zombies, in den staubigen Ruinen einer leeren Großstadt kraftlos in den Armen liegen und hilflos schluchzen. Die Kamera zieht auf. Dann Schwarzblende – und eine letzte, dünne, einsam flehende Stimme im Äther:
»Hello, is anybody there? Anybody at all?« (Hallo, ist da jemand? Irgendjemand?)
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ a012dc82:6458a70d
2025-03-21 15:42:13
@ a012dc82:6458a70d
2025-03-21 15:42:13In the ever-evolving landscape of finance and investment, Bitcoin has emerged as a pivotal player, challenging traditional notions of wealth and assets. Often likened to "digital gold," Bitcoin's unique properties have led some to view it in an even more nuanced light—as "digital pearls." This article delves into how Bitcoin is redefining wealth in the digital age, drawing parallels with historical assets and exploring its impact on modern investment strategies. The comparison to digital pearls is not merely poetic but serves as a metaphor for the transformation of value from physical to digital realms. This shift is not just technological but cultural, reflecting changing attitudes towards what constitutes real wealth in our increasingly digital world.
The digital age has brought about a profound transformation in how we perceive and interact with value. Traditional assets like real estate and precious metals have been joined by a new class of digital assets, from cryptocurrencies to NFTs, reshaping the landscape of investment and wealth. This shift is not merely about the assets themselves but represents a broader change in societal values and economic structures. The rise of digital assets challenges the monopoly of physical assets as the sole bearers of value, suggesting a future where wealth is as much about information and digital ownership as it is about tangible possessions.
Table of Contents
-
The Evolution of Value: From Tangible to Digital
-
Bitcoin: The Digital Pearls of the 21st Century
-
Redefining Wealth and Investment
-
The Future of Digital Wealth
-
Conclusion
-
FAQs
The Evolution of Value: From Tangible to Digital
Historically, the concept of wealth has been tied to tangible assets: land, gold, and precious stones. These assets were prized for their scarcity, durability, and, in many cases, their beauty. However, the digital age has ushered in a new era of value, one where intangible assets like data, software, and digital currencies have become just as, if not more, valuable than their physical counterparts. This transition from tangible to intangible assets marks a significant shift in the global economy, reflecting changes in how we work, live, and interact with the world around us. The value is increasingly found not in physical objects but in the data and digital experiences they enable.
Bitcoin, since its inception in 2009, has epitomized this shift. Created as a decentralized digital currency, it offers a new form of wealth that is secure, transferable, and free from the control of any government or institution. Its blockchain technology ensures transparency and immutability, making it a trustworthy digital asset. This revolutionary approach to currency and wealth has not only challenged traditional financial systems but also redefined what constitutes value in the 21st century. Bitcoin represents a paradigm shift, moving us away from centralized financial systems and towards a more democratized form of wealth.
Bitcoin: The Digital Pearls of the 21st Century
Just as pearls were once a symbol of wealth and status, Bitcoin has emerged as a modern equivalent in the digital realm. The comparison extends beyond mere value; it reflects a shift in what society considers precious. Pearls, formed in the depths of the ocean, were valued for their rarity and beauty. Similarly, Bitcoin, 'mined' through complex computational processes, holds value due to its finite supply and the energy invested in its creation. This digital creation process, known as mining, parallels the natural formation of pearls, adding a layer of intrigue and value to Bitcoin's narrative.
The story of Maisie Plant and her pearl necklace, traded for a New York mansion, illustrates the fluid nature of value. Just as the perceived worth of pearls has fluctuated over time, Bitcoin's value is also subject to change. However, its digital nature and global accessibility mark a departure from traditional assets, offering a new form of wealth that transcends physical boundaries. This story not only highlights the changing nature of value but also serves as a reminder of the subjective and evolving nature of what society deems valuable.
Redefining Wealth and Investment
Bitcoin's rise challenges conventional investment wisdom. Traditional portfolios, heavy on stocks, bonds, and real estate, are being reevaluated as investors seek to diversify with digital assets. Bitcoin's volatility, while often cited as a risk, also presents opportunities for significant returns, drawing parallels with early investments in tech giants like Amazon and Google. This shift towards digital assets represents a broader change in investment strategies, reflecting a new era of wealth where digital assets play a central role.
Moreover, Bitcoin's decentralized nature offers a hedge against inflation and economic instability. In countries facing currency devaluation or financial crisis, it has become a means of preserving wealth, akin to how gold has been used historically. This aspect of Bitcoin highlights its potential not just as an investment but as a tool for economic empowerment and stability. The ability to store and transfer wealth independently of traditional financial systems is a powerful feature, particularly in regions where those systems are unreliable or inaccessible.
The Future of Digital Wealth
As we move further into the digital age, the definition of wealth continues to evolve. Bitcoin, and the broader category of cryptocurrencies, are at the forefront of this shift. They challenge individuals and institutions to rethink what constitutes an asset and how value is assigned and preserved. This evolution is not without its challenges and controversies, but it also offers unprecedented opportunities for innovation and growth.
The integration of Bitcoin into mainstream finance, through ETFs, futures, and other investment vehicles, signifies a growing acceptance of digital currencies as a legitimate form of wealth. However, as with all investments, there are risks and uncertainties. The regulatory landscape, technological advancements, and market dynamics will all play a role in shaping the future of Bitcoin and digital wealth. This future is not just about Bitcoin itself but about the broader implications of a world where digital assets are as common and valued as traditional ones.
Conclusion
Bitcoin's comparison to "digital pearls" offers a compelling framework for understanding its place in the modern economy. Just as the value of pearls once reflected societal trends and desires, so too does Bitcoin capture the zeitgeist of the digital age—a symbol of a new era of wealth that is decentralized, digital, and diverse. As we navigate this new landscape, the story of Bitcoin is far from over; it continues to challenge, redefine, and inspire the future of finance. The journey of Bitcoin from an obscure digital currency to a new form of digital wealth mirrors the broader transformation of the economy and society in the digital age.
FAQs
Why is Bitcoin compared to gold or pearls? Bitcoin is often compared to gold because it shares characteristics such as scarcity, durability, and being a store of value. The comparison to pearls, however, emphasizes its unique, evolving status as a coveted asset, reflecting shifts in societal values and the concept of wealth.
How does Bitcoin work? Bitcoin transactions are verified by network participants (miners) and recorded in blocks on the blockchain. Users can send and receive bitcoins using digital wallets. The supply of Bitcoin is capped at 21 million, ensuring its scarcity.
Is Bitcoin a good investment? Bitcoin's value can be highly volatile, making it a risky investment. However, some view it as a hedge against inflation and a potential part of a diversified investment portfolio. As with any investment, it's important to do thorough research and consider your financial situation and risk tolerance.
Can Bitcoin be converted into real money? Yes, Bitcoin can be exchanged for traditional currencies through online exchanges, peer-to-peer platforms, and some retail locations. The exchange rate varies based on market conditions.
Is Bitcoin legal? The legality of Bitcoin varies by country. Some countries have embraced it, while others have imposed restrictions or outright bans. It's important to check the regulations in your specific location.
What is the future of Bitcoin? The future of Bitcoin is uncertain and subject to various factors, including technological developments, regulatory changes, and market dynamics. It continues to gain acceptance and has sparked a global conversation about the nature of money and the future of financial systems.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ cc601241:181cd0d2
2025-03-21 15:11:09
@ cc601241:181cd0d2
2025-03-21 15:11:09
- Money doesn't grow on trees
- There is no such thing as a free lunch
- Energy cannot be created or destroyed
What if I told you these are three different ways of saying the exact same thing?
If you recognize that money is a unit of account, a medium of exchange, and a store of value, then it's only natural to accept that money at its most abstract formulation is simply information:
"Money is information. It is information we collect about the cost of things. We use it to quantify the world around us. To allow us to figure out what our things are worth in relation to other things. The soundness of a money measures its reliability in storing value over time. Sound money is reliable; you can count on it having a certain value today and in the future. Sound money allows us to determine the proper price of goods and services. Unsound money makes it difficult to figure out what anything should cost. Sound money accurately stores information about the cost of things. Sound money is a sensible store of information."
So long as fiat money can be printed ad infintum to bankroll the military industrial complex, why would we consider the US dollar to be accurate information? Why would we be surprised to see the negative externalities of dark money, regulatory capture, institutional usury, systemic seigniorage, and pervasive rent-seeking happening everywhere? Why wouldn't we start questioning the ripple effects of the Cantillon effect? Why wouldn't the rest of the world's economic actors that operate downstream of the dollar supply not live in constant fear, uncertainty, and doubt? If not resentment, cynicism, and desperation?
"Infinite money creates a scarcity mindset in almost everyone. Most people observe the rising cost of living and experience the feeling of fear or even panic. Fear of the unknown, fear of the future. Uncertainty about making ends meet. Leaky money promotes hoarding, individualism, and fast food culture, where everything is built as quickly and cheaply as possible."
If money is no longer a reliable measure of value but simply a means of control and extraction, how can humanity collaborate or organize or build together? How can we incentivize cooperation? How can we coincide our wants? How can we hope at all?
"Money is a medium of communication. It is one of the most common ways we communicate. Money is a sense-making apparatus. In the broken money world, a subtle distortion becomes ingrained in the foundational layer of sense-making, leading to a systemic corruption of all communication within the system."
Enter a pseudonymous, Good Samaritan, white hat coder: Satoshi Nakamoto.
A cypherpunk who asked a very simple question...

What if there was a money that was not backed by the Federal Reserve or 11 aircraft carriers and 5,000 nuclear warheads and the monopoly of violence? What if that money was backed not by physical scarcity (gold) or political scarcity (fiat) but by mathematical scarcity (blockchain aka timechain)? What if that money operated on principles like "rules without rulers" and "don't trust, verify?" What if we finally had an Occam's razor for economics?

What if that money were backed by the currency of the universe itself: energy?
"Bitcoin's immaculate conception presents the possibility that it has always existed. The genesis block could be viewed merely as the first time we started recording Bitcoin. Knut Svanholm has discussed the idea that Bitcoin might be an element with an atomic weight of zero and that the discovery of Bitcoin is better described as the discovery of our ability to observe this element.
For an element to have an atomic weight of zero, it must be void of protons or neutrons, possessing only electrons. Element zero is purely information. If element zero had always existed prior to our ability to measure it, that means it would have existed back to the time of Lao Tzu. If true, it means there could be undiscovered methods for gauging that information. The understanding of how to observe element zero might not be a binary event.
The interesting thing about observing element zero is that the process requires energy. Producing element zero requires a predictable amount of energy. Interacting with element zero requires energy. By spending Bitcoin, we capture a measurement of the value of the thing we spent it on, priced in energy; because element zero requires energy to produce, we can almost think of pricing other things in Bitcoin as pricing the energy spent in creating them. Element zero transfers energy."
All economy is just the transformation of energy into value. If one accept this definition of economics, then Bitcoin is the purest conversation of energy into value. This would explain why the world is seeing an emergent first principle emerge known as the Joule Paradox:
"Energy sets the value of bitcoin and bitcoin sets the value of energy."

Therefore, Bitcoin is the only money that obeys the laws of thermodynamics.
If we have a transparent public ledger of information backed by energy, we could safely call this document the most objective database in the entire world because energy is the only thing in the entire universe that no one can fake.
That's the power of triple entry bookkeeping. No one can cook the books anymore.

Once humanity is able to guarantee the separation of Money and State, suddenly everyone has a way to protect their own time and energy without having to trust a third party. We are no longer slaves to "absolute power corrupts absolutely". We are no longer beholden to the powers that be. Humanity finally has an incorruptible, immutable, unconfiscatable, permissionless, borderless, open source money available to all.
In a world of manipulated markets, self-sovereignty starts with sound money.
Believe it or not, the thesis of The Dao of Bitcoin: Towards a Cosmology of Energy Money (by Scott Dedels—which I have been quoting throughout this article) states that Bitcoin is "perfect money" (or "daomoney" as he coins it) for the following reason:
Bitcoin = time = money = energy = Bitcoin
There is nothing more valuable than protecting your time & energy. But no one can force you to believe that. Self-sovereignty is a game of consent. The first act of financial freedom is to choose it. The deeper into the Bitcoin rabbithole you go, the sooner you'll have the unmistakable epiphany:
Bitcoin is a strange game where the only winning move is to play.
Bitcoin is just money without the Bullshit. No CEO, no country, no committee, no corporation, no cartel, no council, no conglomerate, no counter-party, no church, no cult of personality. Just pure P2P energy transfer. That's the beauty of freedom money. That's the reason for energy money. That's the answer to the game theory.
With absolute mathematical scarcity, individuals can finally afford an abundance mindset.
For the sovereign individual, all you have to do is nothing but HODL.
That's financial wu wei.
That's energy money that aligns with the universe & vibes with the Dao.

-
 @ 43bb87e2:12cc9cb8
2025-03-21 15:06:52
@ 43bb87e2:12cc9cb8
2025-03-21 15:06:52There was once a little girl that got into some expensive golden wrapping paper, and her father got upset. In his anger, he yelled at his little daughter for wrecking the expensive wrapping paper. The daughter then decided to use the ripped and wrecked wrapping paper to wrap a gift for someone. Again, the father let his anger take over and got mad at the little girl for using the ripped paper for the gift wrapping. The next morning, the little girl presented the tattered, golden wrapped box to her father and said this is for you, Dad. He opened the wrapped box and saw that the box was empty inside. The dad again got angry and told his daughter that when you give a gift to someone, there is supposed to be something inside of it. The little girl, in tears, looked up at her father and said, but it is full daddy. I blew kisses into it until it was completely full. The father then broke down and started crying. He dropped to his knees and put his arms around his precious and innocent daughter. He desperately apologized to her for his anger and continued to ask for her forgiveness. A short while after this, his daughter was taken from this earth because of an accident. The father kept the golden wrapped box next to him for the rest of his life to remind him of the love he had from his daughter.
Nothing else matters in this world or even comes close to the unconditional love that our children and family have for us.
With life being so busy, don’t you dare forget, what really matters in this world. And you be sure to take care of your loved ones, family, and friends.
For we do not know when the last day we will be on this earth.
CHERISH EVERY MOMENT AND LOVE WITH ALL YOUR HEART!
DO NOT LET ANGER RULE OVER YOU.
TELL EVERYONE IN YOUR LIFE,
THAT YOU LOVE THEM!
TELL THEM TODAY!
DO IT NOW!
LOVE YOU ALL, BE BLESSED!
-
 @ da0b9bc3:4e30a4a9
2025-03-21 13:58:11
@ da0b9bc3:4e30a4a9
2025-03-21 13:58:11It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Let's get it!
This song never doesn't put me in a good mood.
https://youtu.be/fnwZeLdLPdQ?si=ZlbiGSp2r6DtMx6P
originally posted at https://stacker.news/items/920041
-
 @ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11
@ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11Table of Contents
- Introduction
- Overview of the Nostr Ecosystem
- Current Use Cases and Quantitative Metrics
- User Adoption Metrics
- Network Resilience and Decentralization
- Operational Challenges and Scalability
- Replication Overhead and Bandwidth Issues
- Relay Downtime and Financial Sustainability
- Market Disruption and Sentiment
- Disrupting Twitter and Centralized Social Platforms
- Impact on Decentralized Social Media and Censorship Resistance
- Future Trends and 5-Year Outlook
- Innovative Protocol Developments
- Quantitative Forecasting and Diffusion Modeling
- Networking and Integration with Emerging Technologies
- Conclusions and Strategic Recommendations
1. Introduction
The Nostr ecosystem has emerged as a powerful decentralized alternative to traditional social media networks, particularly as a potential disruptor of Twitter and other centralized—and even existing decentralized—social media platforms. Developed using a protocol based on cryptographic key pairs and a multi-relay system, Nostr is unique in its provision of censorship resistance and user sovereignty. In this report, we provide a detailed analysis of the current state, scalability challenges, and market disruption potential of Nostr, followed by speculative insights on its trajectory over the next five years.
2. Overview of the Nostr Ecosystem
Launched in 2022, Nostr (Notes and Other Stuff Transmitted by Relays) has rapidly gained traction as an open and decentralized social network. Some of the core features include:
- Decentralized Communication: Relying on independent relays across multiple countries and autonomous systems, Nostr offers an architecture that ensures posts are not stored on a single centralized server.
- Censorship Resistance: With cryptographic authentication and a decentralized relay structure, content censorship becomes significantly more difficult than in traditional networks.
- User Sovereignty: Empowering users with cryptographic key pairs allows for enhanced privacy and data ownership.
- Wide Geographic Distribution: The ecosystem spreads over 44 countries and 151 autonomous systems, underscoring its global reach.
Notable endorsements from figures such as Jack Dorsey, Edward Snowden, Vitalik Buterin, and Sen. Cynthia Lummis have bolstered its reputation as an experimental yet promising alternative to centralized social platforms.
3. Current Use Cases and Quantitative Metrics
User Adoption Metrics
- User Base: In just two years, the Nostr network has attracted over 4 million users, a significant figure given its nascent stage and decentralized nature.
- Content Generation: With over 60 million posts, the volume of content mirrors the rapid adoption and active usage seen in more centralized models.
- Post Replication: Empirical measurements indicate that there are 17.8 million text notes among these posts, replicated on an average of 34.6 relays per post. This level of replication underlines robust resilience and availability even if significant portions of the network experience downtime.
Network Resilience and Decentralization
- Global Distribution: Nostr’s decentralized network ensures high availability with >90% post accessibility even under simulated network failures (e.g., removal of key relays or autonomous systems).
- Robustness: The dispersion across 712 relays illustrates that decentralization is not only a design choice but also a working reality, which contributes to the network’s reliability.
4. Operational Challenges and Scalability
While the Nostr ecosystem demonstrates significant promise, it faces noteworthy operational challenges.
Replication Overhead and Bandwidth Issues
- Excessive Redundancy: Detailed studies have shown that nearly 98.2% of retrieval traffic is redundant. In practice, this equates to an estimated 144 TiB of unnecessary bandwidth consumption.
- Optimization Proposals: To mitigate these inefficiencies, there's a proposal to limit post replications from 34.6 relays to between 10 and 20 relays per post. This could reduce redundant data copies by between 380 million to 480 million instances, potentially lowering operational costs and improving bandwidth utilization.
- Scaling Concerns: With a projected network load of 10 million events per day (or approximately 2 TB annually), the throughput requirement of ~115 TPS is putting a strain on the current architecture. This has led to debates on whether solutions like the current outbox mechanism are sufficient or if further fundamental redesigns and emergent moderation systems are needed.
Relay Downtime and Financial Sustainability
- Relay Stability: Data indicates roughly 20% of relays suffer from significant downtime (exceeding 40% operational time), and 132 relays have been classified as 'dead'. This is a concern for maintaining network integrity.
- Economic Model Challenges: With 95% of free-to-use relays unable to cover operational costs due to minimal zap-based income, there is an urgent need for innovative monetization or community funding models to ensure long-term sustainability.
5. Market Disruption and Sentiment
Nostr is positioned as both a disruptor to traditional centralized social platforms—most notably Twitter—and a catalyst for change within decentralized social media.
Disrupting Twitter and Centralized Platforms
- User Shift: While Twitter remains the most well-known platform, the high-profile endorsements and robust user base of Nostr indicate that there is both market intrigue and a gradual shift among early adopters. Disruption here is measured not only in user numbers but also in the paradigm shift towards decentralized content distribution.
- Market Penetration: Current metrics (4 million users, 60 million posts) suggest that Nostr is challenging Twitter's centralized model insofar as it appeals to users prioritizing censorship resistance, data sovereignty, and resiliency against centralized failures. However, mainstream adoption on par with Twitter is still not realized, and there remains a gap in user experience and feature richness.
Impact on Decentralized Social Media and Censorship Resistance
- Complementary Integrations: As decentralized social media ecosystems continue to mature, integration between Nostr and other censorship-resistant platforms is increasingly likely. This can include interoperability protocols, shared identity management systems, and cross-platform content replication.
- Comparative Advantage: Nostr's network design offers unique advantages over other decentralized social media, particularly in its straightforward, relay-based communication protocol. This positions Nostr to potentially serve as an underpinning technology for a broader decoherent ecosystem of social networks.
- Sentiment Toward Scalability Innovations: Discussions around scaling Nostr often focus on the balance between ensuring redundancy (for resilience) and reducing overhead (for efficiency). The sentiment is one of cautious optimism: while outbox solutions offer a stopgap, many experts advocate for more fundamental architectural redesigns in the long-term.
6. Future Trends and 5-Year Outlook
Looking forward, the evolution of Nostr will likely be shaped by several interrelated trends and emerging technical innovations.
Innovative Protocol Developments
- Decentralized Identity and Reputation Mechanisms: The next phase may see the introduction of distributed reputation systems and rating mechanisms that aid in spam management and improve trustworthiness without compromising decentralization.
- Optimistic Replication and Selective Mirroring: Innovations such as selective content mirroring and event pruning will be key in managing bandwidth and storage demands while remaining true to the decentralized philosophy.
Quantitative Forecasting and Diffusion Modeling
- Forecast Models: By integrating modified Bass diffusion models and learning curve effects, predictions suggest that Nostr can potentially spur significant market disruption within five years. Recent studies indicate that forecasting models in disruptive technology fields have reached accuracies of up to 82% for demand projections.
- Hybrid Quantitative Techniques: Leveraging methods like LDA2Vec and patent citation network analysis, combined with multi-criteria decision-making models (as seen in extended UTAUT approaches), will be crucial for accurately estimating future adoption and cost efficiencies.
- Metrics to Monitor: Future research should focus on user growth rates, relay uptime percentages, cost reductions achieved through replication optimizations, and overall sentiment analysis using advanced deep learning architectures that overcome traditional pitfalls (e.g., sarcasm and multipolarity in text data).
Networking and Integration with Emerging Technologies
- Integration with Other Decentralized Platforms: One promising avenue is exploring cross-platform interoperability with other decentralized and blockchain-based social networks, which could lead to a more cohesive ecosystem. This would not only enhance user experience but also enable shared security and moderation frameworks.
- Next-Generation Relays: The deployment of relays that are more resilient through redundancy optimization and financial sustainability models (perhaps incorporating micro-transaction revenue models or community-driven funding) is another critical area. Such improvements could mitigate the issues of relay downtime and excessive network overhead.
- Contrarian Approaches: A contrarian perspective suggests that instead of building on current frameworks, a radical overhaul of the network architecture might be considered, potentially by leveraging novel distributed ledger technologies or leveraging a hybrid centralized-decentralized model during the transition phase to ensure smoother scaling.
7. Conclusions and Strategic Recommendations
The Nostr ecosystem represents a significant stride toward decentralized, censorship-resistant social media. While its current market adoption and technical design offer a robust alternative to centralized platforms like Twitter, several challenges must be addressed for sustained growth and disruption:
-
Optimization of Data Replication: Reducing redundant data transfers without compromising resilience is essential. Limiting the replication factor and exploring optimistic retrieval mechanisms could provide a balance between availability and efficiency.
-
Relay Stability and Sustainability: With nearly 20% of relays experiencing significant downtime, innovative financial and technical models (such as micro-payments and community funding) should be deployed to enhance the operational reliability of network nodes.
-
Enhanced Moderation and Reputation Systems: Emerging strategies for decentralized content moderation and reputation management could reduce spam and improve content quality while preserving the open nature of the network.
-
Interoperability with Other Decentralized Platforms: Fostering integration with other emerging systems could accelerate market disruption across the broader spectrum of social media.
-
Future-Proofing Through Quantitative Forecasting: Continual adoption of cutting-edge forecasting models and machine learning techniques to measure sentiment and track network metrics is imperative for proactive evolution.
-
Exploring Contrarian Innovations: In addition to incremental changes, it is important not to discount radically new architectures that may emerge from ongoing research in distributed systems and blockchain technologies.
Final Outlook
In the coming five years, Nostr has the potential to disrupt not only Twitter but also the broader landscape of both centralized and decentralized social media. Although the current architecture presents significant scaling challenges, proactive investments in replication optimization, relay stability, and cross-platform integration will likely propel the network into a more mature phase of adoption. The ecosystem will benefit from a dual approach that combines both evolutionary improvements and revolutionary changes, ensuring that it remains robust while meeting the demands of a growing, globally distributed user base.
Appendices
Appendix A: Data and Metrics Summary
- User Base: ~4 million
- Post Volume: >60 million posts
- Average Relay Replication: ~34.6 replicas per post
- Geographical Distribution: 44 countries, 151 autonomous systems
- Bandwidth Waste: ~144 TiB due to redundancy
- Network Load: 10 million events/day (~2TB/year)
- Throughput Requirement: ~115 TPS
Appendix B: Key Technical Proposals
- Replication Control: Limit copies to 10–20 relays for optimal efficiency.
- Selective Mirroring: Implement event pruning and selective content mirroring.
- Decentralized Reputation Systems: Develop distributed rating mechanisms to enhance distributed moderation.
Appendix C: Forecasting and Quantitative Methods
- Diffusion Modeling: Modified Bass models with multi-market dynamics.
- Hybrid Quantitative Techniques: Integration of machine learning (CNN-LSTM, LDA2Vec) with multi‐criteria decision models.
Recommendations for Further Research
- Investigate the comparative performance of alternative replication strategies in decentralized networks.
- Explore funding models that can sustain relay operations without compromising neutrality or decentralization.
- Conduct long-term sentiment analysis using advanced neural architectures to understand evolving user attitudes.
- Evaluate the prospective benefits of radical design overhauls versus incremental enhancements in ensuring network scalability.
This report is intended for expert analysts and researchers in decentralized network systems and social media disruption. It synthesizes current empirical findings with speculative insights to inform future strategies and academic inquiry.
Sources
- https://www.voltage.cloud/blog/exploring-6-use-cases-of-nostr-beyond-messaging
- https://arxiv.org/abs/2402.05709
- https://arxiv.org/html/2402.05709v1
- https://papers.ssrn.com/sol3/Delivery.cfm/5146515.pdf?abstractid=5146515&mirid=1
- https://matchnode.com/blog-and-podcasts/mastering-paid-social-media-advertising-a-comprehensive-guide/
- https://blockworks.co/news/jack-dorsey-app-to-disrupt-twitter
- https://www.securities.io/nostr-a-better-twitter/
- https://medium.com/@jasminedevv/battle-of-the-decentralized-twitter-alternatives-c9f51114614a
- https://www.murrayrudd.pro/nostrs-relay-revolution-scaling-decentralized-networks-for-growth/
- https://github.com/nostr-protocol/nips/issues/75
- https://news.ycombinator.com/item?id=42758579
- https://www.toptal.com/deep-learning/4-sentiment-analysis-accuracy-traps
- https://www.researchgate.net/publication/3076742_Forecasting_the_Market_Diffusion_of_Disruptive_and_Discontinuous_Innovation
- https://www.globenewswire.com/news-release/2025/03/17/3043701/0/en/United-States-Online-Household-Furniture-Market-Report-2025-2029-Analysis-of-Price-Sensitivity-Lifecycle-Customer-Purchase-Basket-Adoption-Rates-and-Purchase-Criteria.html
- https://northeast.newschannelnebraska.com/story/52583550/laser-welding-market-growth-industrial-adoption-rate
- https://www.sciencedirect.com/science/article/am/pii/S2405896323014453
- https://www.marketsandmarkets.com/Market-Reports/industry-5-market-35376359.html
-
 @ 8671a6e5:f88194d1
2025-03-21 13:38:50
@ 8671a6e5:f88194d1
2025-03-21 13:38:50As old people tend to say:\ \ *nasal voice* “Back in my day…” … Bitcoin was this wild, beautiful thing, new. It was something technical that came alive before our very eyes after running a node (just a .exe running on a windows machine in my case).\ Even when you started to painstakingly mined bitcoin on a GPU, in a pool, you felt like growing a network of like minded people, or at least people who thought there was something there. Even if we couldn’t comprehend what it all would lead to (or what fiat value it could reach).\ Then came the first paper wallets, the first good software wallets and attempts at hardware wallets, the first buzz of owning your own value — it was motivating and rewarding. The look on the face of other people you explained bitcoin to, when they’ve seen their first transaction pop up after validation. Awesome.\ \ Back then, it wasn’t about fiat gains or slick marketing campaigns; it was about a distributed network “generating” numbers, keeping a distribute ledger “in synchronization”, at the same time it was a middle finger to the system, representing freedom to transact in value we valued ourselves because of the underlying network of people, nodes and miners.\ \ It was this sort of secret handshake between tech minded people, anti-globalists, anarchists, nerds and rebels who saw the fiat scam for what it was.\ Orange-pilling wasn’t even a term; it was just what you did.\ You'd walk people through the setup of bitcoin core, and the white paper, told them why central banks are a trick that functions as a legalized Ponzi scheme and you showed them bitcoin’s workings without middlemen.\ You played around with bitcoin, person to person, no bullshit, no subscriptions, no suits, no posing like a big shot, no referral links.\ Those were the fun times — pre-Saylor, pre-nation-state hype, pre-every Laura, Luigi, and self-proclaimed “OG” thinking they’re going to conquer the world.\ I miss that.
But times change.
\ The good ol' days are dead
It’s not the first instance in our lifetime that we see things pop-up, being invented, and where some good new idea becomes a reality and then that very good idea becomes an institution (there’s an obscure 1990s movie reference for you).\ We live and learn, just like the first technical people setting up their own point of presence internet servers, we all have to learn how to grow and adapt.
Early Bitcoiners didn’t have referral links or corporate sponsors — they had a mission, and the spirit came from within themselves and from the math and tech they’ve seen at work in practice. And yes, educating about it was important, as was looking for ways to improve bitcoin (the early years weren't exactly main-stream material for example).
From that learning yourself about Bitcoin and feeling the need to share and convince others around you, came the need to talk and learn together with others.
You’d talk your buddy into installing a wallet over a coffee, maybe show your uncle how to buy a few bitcoin, and it felt like planting seeds for something real.
Even if they didn’t get it—“So this number goes from my address to your address?”—you kept explaining and showing.
Then the suits rolled in. Bigger companies wer started, like Blockstream, Trezor, Coinbase and Binance.
Wall Street, Saylor with his infinite buy tweets, El Salvador and its volcano bonds, the US ETF approval — and the game changed, everyone heard about it one way or another. That’s damned important! You’re NOT the bringer of news.\ \ Suddenly, it wasn’t grassroots anymore; it was headlines, hype and game-theory. As predicted by so many in the space.\ Fine, whatever, it's progress or something else, but we as bitcoiners need to adapt to that reality.\ Some adaptations will also cause us to put energy elsewhere than before.\ What worked in 2012 or 2016, might not work anymore after 2024.\ ”We bitcoiners route around problems.” Right?
You didn’t need new people to create an account, or be part of a ‘squad’ or team, you certainly didn’t need them to sell merchandise. You just showed them bitcoin’s inner workings.\ \ Bitcoin was the marketing, the engine, the product and the goal. Bitcoin was the core. Just like digital communication was the core of the earliest internet enthusiasts. The magic of sending a text into the network, and through clever routing, someone thousands of miles away could read it almost immediately, that was the magic, the core.
Sending value with bitcoin has that same magical way, immutable, uncensored, unconfiscatable, with proven digital scarcity and forced honesty.
Nowadays we have so-called orange-pillers.\ They’re trying to spread those values. Or so they should..
They didn’t get the memo on Bitcoin becoming more commonly known apparently, and if they did, their lust for dopamine has long replaced that with their urge to get people to install a lightning wallet. It’s sometimes rather disturbing to see this Orange Pill’ing play out.
They’re out there, like they’re stuck in 2013. But they’re usually not from 2013 at all, more like class of 2020’ish. Not that it matters, they’re still living in the illusion that there are people out there that didn’t hear of bitcoin and that THEY and THEY alone can save these poor souls.\ After 2018 it’s safe to say that that’s not the case.\ I’ll repeat that for the die-hard orange-piller: they do not need you to hear about bitcoin.
These Orange Pillers have another kind of magic happen:
While they’re winning over new souls into bitcoin, one barber, taxi driver and babysitter at a time, they get the small electric charge in their brain that tells them their wealth, their (and their holding's) value will go up somehow. They’re also desperate to make some kind of connection with other bitcoiners, and while they lack that connection, they try to find (or make) new bitcoiners around them.\ This approach might have worked in the past, but things are different now. You’re usually talking to people who you try to convince of something they’ve already rejected (often harshly rejected) or never will care about .\ Most people, do not give a damn about inflation or how that came to be. Certainly when they’re doing their job.\ \ It’s like someone shoving the book of a cult under your nose and trying to convince you it’s going to save your life. You’re not open to it, neither are most of the Orange pill targets to your bitcoin gospel.\ Orange Pillers don’t see how the very people they try to convince today weren’t “in it” for a variety of (good for them) reasons. Unlike in the old days, where people’s natural state was “not heard of bitcoin”; since it was new, and people genuinely didn’t learn about it or read into it.\ That’s however, not the case today. That taxi driver? He heard about bitcoin. Be sure.
Such new people today, are almost non-existing, they either bought some long ago, got rekt trading shitcoins and stayed away.\ That, or they found it all a bit too “iffy” (thank you mainstream media) and will politely hold back from not yelling to your face, “I don’t care about that Bitcoin stuff!”.\ They know it’s some form of money or value, they know it exists. Which makes orange pillers the bringers of old news to the bottom of the barral.\ They might get a “hit” now and then of course. But even then, your impact is neglectable in a world that rewards cowardice and short term greed. You’re too late. You don’t scale. And it doesn’t matter.
Since 2020, it has shifted from genuinely introducing people to bitcoin to just "spreading it for the sake of spreading it."\ It looks more and more like an old lion, pacing back and forth in a cramped cage at an old ZOO, restless and frustrated.\ There’s just empty repetition.
The mental breakdown of orange-pilling
\ Let’s look a little further into the act of orange pilling.\ \ It's not like a 1990s hacker type showing a brand new Hayes -compatible modem to his buddy and trying to get a connection going to a local Point of Presence to get internet access.\ \ It’s more like showing your holiday pictures to an uninterested family member. All to get the dopamine hit, the ‘aha moment’ out of someone is now your own ‘aha got someone new’ moment. Like an addict looking for that next high.\ \ You want them to get the app, get some sats and feel the same feeling you have. While they’re worrying about cleaning a table for example, or getting your bill.\ \ This “badge of honor” of Orange Pilling someone is that little shot of dopamine many people need (especially in group) to feel validated.\ The real feeling has everything to do with social conformity1 and the involved brain areas that get stimulus shots and increased activity.2\ \ Above that, for the sake of the mental reward, some people go further down the social boundaries. That’s why orange pilling, often comes across as pushy, unnatural and/or annoying.\ It’s because it’s basically an activity with all the neuro stimulus of an addiction, or done as an ego boost.
Math based
On top of all of that. If you do the math on it the whole action becomes even more ludicrous.\ \ The math in the early days of bitcoin was simple: there was exponential expansion of the number of bitcoiners.\ Purely for bitcoin, the growth in numbers is still going strong, but the percentage has now naturally been flattened out because of media coverage, scams that trick people into other stuff and the close to impossible way to scale the onboarding from a person to person level to larger scales (there are apps doing a good job however, but even then it spread under former bitcoin users or people already in the know on some level, like former shitcoiners).\ \ So even at the rate of trying to orange-pill let’s say 10 people per week (many bitcoiners don’t even tàlk to 10 people a week, let alone convince them to use bitcoin).\ \ When hypothetically 50% of these people (not unusual with word of mouth recommendations) actually install the app you recommended, and we take also a high percentage of 10% actually do a regular buy of bitcoin after installing any of these apps (Strike or Blink or any other).\ \ Given that hypothetical high rate of 10 people a day plus the conversion rate, it would take approximately 200 weeks, close to four years (pun intended) to reach 2000 people as a critical mass that actually installed and used the bitcoin app.\ \ If these 2000 people all buy for about 1000$ worth of bitcoin each, they’ll be good for about 2 million dollars in bitcoin buys over a four year period.\ Even if you take very, very optimistic statistics this, you’ll get a close to zero impact, safe for the occasional big shot you might encounter and converts into a mini-Saylor, or the occasional person you might have saved a few thousand dollars (because they all keep thinking in fiat terms anyway).\ \ But on the other side, people with +100 million dollars to spend will surely have advisors and in-house knowledge, to not having to to rely on your sorry ass explaining bitcoin or installing Wallet of Satoshi on their phone or something.\ \ That’s all peanuts. It’s futile. And you’re fighting an honorable battle from 11 years ago.
### \ Why
I can't grasp why so many people keep doing this the way they do.
Orange-pilling mostly works when the price is going up anyway, unfortunately.
However, when BTC’s up 15% in a week, everyone’s a genius and your coworker suddenly can be all ears about “sound money” and future price gains.
When it’s crashing or flat? Good luck, nobody cares among the normies, unless the “orange-pillee” (the target) has their own ulterior motives for listening (like getting someone to at least give them some attention in any form).
And by the way, to come back to these taxi drivers you try to convince… many taxi drivers already had their share of die hard bitcoiners in their car, and got the explanation. Some of them even act like total noobs probably to get some sats out of your orange pilling wallet. They’re good at playing dumb, trust me.\ \ Do you really think a taxi driver in let’s say Lugano, Amsterdam or Prague didn’t already know bitcoin before you tried to convince him to accept it? You’re not the first. At all.
Most of all, you interact with people while they’re doing their job. You’re actually interfering with their work. When a waiter in a fully booked restaurant has to halt his word and listen to you explaining how to install a lightning wallet on their old iphone that’s almost out of battery, you’re losing anyway.\ They might listen, they might even be pestered to the point they’ll install the damned app. And what do you win or achieve?\ A sparkle in your brain that says “you’re such a cool bitcoiner”?\ Then… after what’s usually a painful few minutes going through a horrible counter-intuitive interface, you get them 5000 sats or whatever over to them.
Oh and adding things like “Hey man, keep these sats for at least 4 years, it will go up in price” is just rotten as well. Just give the people a decent tip and leave. You’re not doing anyone a favor.
When the moment’s there ànd some people are clearly open to it, thèn you might add some info. Point them to an easy to use non KYC app (if there is such a thing).\ But even then, just letting someone know you want to pay in bitcoin, should be enough, WHISPER bitcoin.\ They don’t need your pushy sales pitch on top of the daily struggles they face in hospitality and retail jobs.\ \ The squads
An example,... I saw this crew, let’s name them the “Re-play” squad, they’re all wearing blue hats and have a few flyers with them from a marketing company which managed to put them to some good use at a very low expense rate.
This image is still stuck in my head, some random European country during late summer time — local Bitcoiners, along with some counterparts from other countries. The real “we’re the future” types.
Sitting on the floor at a Bitcoin party, rolling “funny cigarettes” passing a lighter, chatting and laughing about how they orange-pilled some dude in a bar.
 “Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.
“Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.They’re all proud, they’re all high, they all belong to a group now … and they’re convinced they’re conquering the world one wallet at a time (they don’t do the math on that, neither should they,… ignorance is bliss).
Doing good for bitcoin has been transcended into an egotrip, and the short-lived kick in the orbitofrontal cortex3 for “doing something”, it’s the filling of a lingering emptiness.\ \ The same people move around like they’re an anthill, reminiscent of the hippie communes, until they’ve returned to their misery at home, knee deep in sorrows of the fiat world. As is the orange pilled person by they way, who’s life won’t be helped by a few sats and yet a new app on their phone. An app they’ll hardly use, unless they start to bond with the other bitcoiners in the area.
These people you target already have had all chances in the world to learn about bitcoin but are too far gone to care.\ Podcasts, books, family members that are into bitcoin, or whatever blog or online service… even the biggest shitcoin casino’s only have rather decent guides and basic explanations. There are excellent educational apps like yzer.io4 as well as the excellent lopp.net5 website by Jameson Lopp.
Convincing people one-by-one doesn’t work anymore—it’s inefficient and outdated since the price surges, media coverage, and ETF launches. Even if some are open to it, it’s a futile, unscalable solution of dread, working indirectly for the benefit of the Wall street types or some shitcoin casinos (where most “new coiners” end up).
Orange pillers, also never can “read the room”. The crew in a busy restaurant or bar isn’t waiting for any explanation about UTXOs or custodians from you!
Even if you'll hit machine-like numbers of onboarding twenty people a day (By then, you’ll need to avoid being labeled the local bitcoin village fool in your community) and assume they're all pure bitcoiners afterwards.\ Which won’t happen either as any incentive of the orange pilled people is clearly nòt long-term thinking; otherwise they would have onboarded you some 8 years ago!\ \ People are extremely lazy, and the general public usually has an attention span of about 8 seconds at best6.\ Back in the early days, you could sit people down and show another tech person for hours on end how to work with bitcoin, now more than a decade later, you have about 5 to 60 seconds tops. (most lightning wallet’s onboarding sequence easily takes 2 tot 5 minutes)
To further convince yourself how pointless Orange Pilling is today: go out and watch people on a public transport vehicle: they scroll and swipe through TikTok and Instagram. You’ll notice they’re swipe-apes, there’s no substance or reliable source of bitcoin buying power there, no bitcoin innovation will come from them, and no philosophical insights will ever be ignited in their buy-the-next-cool-sneakers-now brain. They’re not a target audience. They’re the all singing and all dancing crap of the world. They’re not convinced, Inconvincible and inconvertible.
Meanwhile, no substantial steps have been made for bitcoin, even if you get them to install that app you so desperately want them to have. Neither can you expect the no-coiners or pre-coiners (god I hate that word, it sounds kinky somehow) to do anything for bitcoin, as the gap between them and the actual positive impact they could have is too wide.\ It costs time, studying and experimenting. While these people excel at thing like: shopping, watching dime-a-dozen garbage series on Netflix, watching social media posts that don’t challenge them, and eating take-out food while score some drugs.\ \ So… to conclude the story about that dude in the bar which was so carefully orange pilled by our “Re play” squad members, he probably traded his sats for a beer by now (although that demands some form of effort in finding a recipient that has beer and wants to trade it for sats, which is unlikely) , more likely he forgot about the app altogether or he’s trading shitcoins to “make more money as greed that sets in. And he probably got that woman’s telephone number, to “talk about those bitcoins” later on at his crappy rental apartment right above a shoarma restaurant.\ \ The phrase “everyone’s a scammer” includes people who pretend to care about bitcoin just to get something out of it. Even a complete newbie or shitcoin fan will fake interest in bitcoin to seem legit. I’ve watched it happen.
Orange-pilling: the good, the bad, and the ugly
\ So onboarding devolved into this whole subculture of failure, and started to manifest itself over time as a empty motion, a series of must-do things.\ \ The Pavlovian response whenever someone is a walking opportunity for accepting bitcoin (certainly in any bar, restaurant or hotel), results in the foaming at the mouth to get them onboarded on some app or wallet.\ It’s so pointless I actually feel ashamed when I’m in a group that starts to hawk and push their lightning wallets onto unsuspecting people who just want to do their job.\ (and Lightning Wallets are so crappy to onboard people with, it’s mind numbingly stupid)\ \ To my amazement, there are actually a lot of bitcoin holders, or people that claim to be into bitcoin (especially in a bull market) who still pester random people with this kind of behavior.\ \ Some of these are trying to get them to click a referral link from a venture capital firm, in return for a few bucks (incentives these days are needed to get the groundswell going apparently), or worse even, make them install some non-custodial wallet and run into the brick wall of initial on-chain setup fees and then run away like a complete loser because they’re too cheap to fork that initial on-chain fee out for the people they’ve tried to onboard. “Yeah, like, you can buy these 100.000 sats online later if you like and thèn you can have this wallet, but at least it’s not custodial eh.. uh … My buddies are over there, I’ll see you later”.\ \ When you start to observe these people in the wild, it’s like watching a gaze of raccoons going through some neighborhood’s trash cans at night (without the playful conviction).\ Fascinating, if you’re into low-budget wildlife documentaries.
 Gaze of raccoons looking for a QR code
Gaze of raccoons looking for a QR codeIF you still want to onboard someone, point them to the right info at the right time (when thèy ask you).\ I call it “Bitcoin whispering”. #BitcoinWhispering
### \ \ Let’s quickly look at the three sort of Orange Pillers:
The pushy ideologists: The most annoying of the bunch, but at the same time the ones who mean really well. I sometimes feel sorry for them.\ No one’s safe from them. Hairdresser? “You should accept Bitcoin, man.” Bartender? “Credit cards are no goog, why not use Lightning?” Taxi driver? “Ever heard of Lightning? I can tip you in Bitcoin, man.” They’re not educating; they’re feeding their ego and their need to spread the word.
The referral grifters: More damaging to Bitcoin than shitcoiners in my opinion. They don’t care about Bitcoin’s properties; it’s just a slot machine for them. And if they understand, their short term greed and social circle dependency makes them go for spreading the word of a middleman company.\ “Sign up with my link, bro, stack those sats!”\ Their goal? A kickback and the next pat on the back from their miserable squad members.
The show-offs: The worst. They don’t know anything themselves but love the spotlight. “Yeah, I got my barber stacking sats!” Yet when it’s time to actually help onboard a business, they’re nowhere to be found. All talk, no substance. They achieve a small social circle of noob bitcoiners surrounding them, with most of them going through the shitcoin-phase shortly after or swapping off-the book gains. They’re not good for bitcoin and usually don’t stay that long anyway.\ \ The world doesn’t need your savior complex.
After the second half of 2024 if someone wanted in, they’ll find a way. And if they ask a Bitcoiner for help? Sure, we’ll point them in the right direction — most of us will help when asked (gladly so).\ But this idea that you, oh mighty orange-piller, need to swoop in and “save” people is more about you than about bitcoin.
Create a good, nice, safe (protected from scams!) environment or way to get people to the info and the other way around.\ Be there when people can ask questions, lead by example, make it work and show it. If an app is easy to use, makes sense and has no friction, then people will come. If you’re pestering people and hounding them into liking something that’s so far removed from their reality (fiat-world), they’ll be scared away and not return.
### \ Conclusion
Although I miss the old days, I also realize they ain’t coming back — when orange-pilling was just sharing a crazy new idea with someone who was open to it.
The Orange pilling space is now too keen for a large part to shove their bitcoin app in someone’s face, be it in dollars, a few sats or a discount on their next transaction fee at some multi level marketing middleman.\ This onboarding is also strangely in parallel with what shitcoiners or the most vile fiat companies do, OP’ers are too desperate for relevance so they often don’t look at the value proposition of bitcoin anymore. Filling their void got the upper hand.\ Their shot of feelgood moments needs to be filled.\ While there’s close to no impact to gain anymore on one-one-one convincing.\ The lesson to save in bitcoin, is usually lost on the people anyway, which was the last reason left to do it.\ \ Be there when people ask for help on bitcoin, build stuff, but stop the aggressive orange-pilling, it serves no purpose anymore other than your dopamine hit and a token feeling for “doing something”, and it’s a sad addiction.
Therefore in 2025, orange-pilling has become of a full-blown mental issue.
by AVB
if you like my writings : tip here
\ Footnotes:
https://journal.psych.ac.cn/xlkxjz/EN/Y2015/V23/I11/1956
https://www.frontiersin.org/journals/behavioral-neuroscience/articles/10.3389/fnbeh.2019.00160/full
https://en.wikipedia.org/wiki/Orbitofrontal_cortex
https://yzer.io/
https://lopp.net
https://theweek.com/health-and-wellness/1025836/tiktok-brain-and-attention-spans
Share
TopLatest
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-21 13:20:20
@ 5d4b6c8d:8a1c1ee3
2025-03-21 13:20:20It's March Madness and @grayruby finally caved on my proposed contest design. We'll see if it's as great as I thought or as dumb as he thought. What are we expecting from this tournament?
Professional basketball is in its pre-postseason lull, as most teams either don't need to win many more games or don't want to. Is there a fix and why is it less communism?
The MLB season has kicked off and the Dodgers are heavy favorites already. Our MLB survivor pool is going to start soon (weren't we going to do something with fantasy baseball?). Plus, baseball realignment.
We're still on Ovi Watch as the NHL season comes to a close.
And, of course, the NFL Draft is coming up. Is the picture getting any clearer about where the top prospects are going?
Also, whatever stackers want us to cover.
originally posted at https://stacker.news/items/919995
-
 @ 58537364:705b4b85
2025-03-21 12:37:28
@ 58537364:705b4b85
2025-03-21 12:37:28เสียงตะโกนของ “อิทัปปัจจยตา”
ทุกอย่างตะโกนคำว่า “อิทัปปัจจยตา” อยู่ตลอดเวลา
“ท่านทั้งหลายนั่งอยู่ที่นี่ แต่ไม่ได้ยินเสียงตะโกนที่ดังลั่นไปหมดของธรรมชาติว่า ‘อิทัปปัจจยตา’ เสียงตะโกนของอิทัปปัจจยตา คือการร้องบอกร้องตะโกนว่า ‘เพราะมีสิ่งนี้เป็นปัจจัย สิ่งนี้จึงเกิดขึ้น’ หมายความว่า ท่านต้องดูลงไปที่ทุกสิ่งที่อยู่รอบตัวเราในเวลานี้ว่า ทุกสิ่งกำลังเป็นอิทัปปัจจยตา หรือเป็นไปตาม ‘กฎอิทัปปัจจยตา’”
ต้นไม้ต้นนี้มีความเป็นไปตามกฎอิทัปปัจจยตา ไม่มีอะไรมาต้านทานได้ ถ้าเราเข้าใจข้อเท็จจริงที่กำลังเป็นอยู่กับต้นไม้ เราจะเหมือนได้ยินมันตะโกนบอกว่า “อิทัปปัจจยตา” ไม่มีอะไรมากไปกว่านั้น มันเพียงบอกว่า “เมื่อมีสิ่งนี้เป็นปัจจัย สิ่งนี้จึงเกิดขึ้น”
ต้นไม้ไม่ได้หยุดเพียงเท่านั้น มันมีการเปลี่ยนแปลงเกิดขึ้นเรื่อยๆ ใบไม้ทุกใบก็บอกอย่างนั้น คงเป็นเสียงที่ดังเหลือประมาณว่า ใบไม้ทุกใบร้องตะโกนว่า “อิทัปปัจจยตา”
ผู้มีปัญญาและเข้าใจหัวใจของพระพุทธศาสนา จะไปนั่งอยู่ที่ไหนก็ได้ยินเสียงตะโกนว่า “อิทัปปัจจยตา” สนั่นหวั่นไหวไปหมด นี่พูดถึงแค่ต้นไม้ต้นเดียว ถ้าเป็นต้นไม้จำนวนมากก็เป็นเช่นเดียวกัน
เมื่อมองไปที่ก้อนหิน ก้อนหินก็เป็นเช่นเดียวกัน อนุภาคของมันเปลี่ยนแปลงอยู่ตลอดเวลา ก้อนหินที่เราเห็นอาจเกิดขึ้นมาเมื่อหลายพันล้านปีมาแล้ว จนมันแตกสลายและถูกทำให้มาอยู่ตรงนี้ มันจึงกล่าวว่า “อิทัปปัจจยตา” เพราะมีสิ่งนี้เป็นปัจจัย ฉันจึงมานั่งอยู่ที่นี่
ทุกอย่างตะโกนคำว่า “อิทัปปัจจยตา” ตลอดเวลา
- ต้นไม้ เม็ดกรวด เม็ดทราย มด แมลง สัตว์ต่างๆ รวมถึงมนุษย์เอง
- แม้แต่ร่างกายของเราเองก็ตะโกนบอกถึงอิทัปปัจจยตา
แม้เราจะเคยได้ยินคำว่า “อนิจจัง ทุกขัง อนัตตา” อาการของสิ่งเหล่านี้ยิ่งสะท้อนถึงอิทัปปัจจยตาอย่างชัดเจน
ดังนั้น เราต้องทำความเข้าใจจนซึมซาบอยู่ในใจ จนรู้สึกว่าไม่ว่าเราจะมองไปทางไหน ก็เห็นถึงภาวะของ อิทัปปัจจยตา ได้ยินเสียงของมัน หรือแม้แต่สัมผัสผ่านการดมกลิ่นและลิ้มรส
เมื่อเข้าใจสิ่งนี้ จะสามารถเรียกผู้นั้นว่า ‘เป็นพุทธบริษัทผู้เห็นธรรม’
สามารถเห็นกิเลสและทุกข์ แล้วป้องกันหรือกำจัดกิเลสและทุกข์ให้น้อยลงไปได้มากทีเดียว— พุทธทาสภิกขุ
(จากหนังสือธรรมบรรยาย “อิทัปปัจจยตา” หน้า 131–133)
อิทัปปัจจยตา: กฎอันเฉียบขาดตลอดจักรวาล
https://image.nostr.build/abc776213ec6371da681aa5766390f67e1ae97dc1d7157774e02eb93d1f21f56.jpg
“อิทัปปัจจยตา” เป็นกฎของธรรมชาติที่ไม่อาจเปลี่ยนแปลง
คำว่า “อิทัปปัจจยตา” อาจเป็นคำที่ไม่คุ้นหู แต่ขอให้สนใจ เพราะมันเป็นกฎของธรรมชาติที่แน่นอนตลอดจักรวาลและอนันตกาล
- สิ่งนี้เกิดขึ้น เพราะมีเหตุปัจจัยนี้
- สิ่งนี้มี เพราะสิ่งนี้มี
- ดวงอาทิตย์ ดวงจันทร์ ดวงดาว ทุกอย่างล้วนเกิดขึ้นตามกฎของ “อิทัปปัจจยตา”
เมื่อทำสิ่งนี้ มันต้องเกิดสิ่งนั้นขึ้น
เมื่อทำสิ่งนี้ มันต้องเกิดทุกข์ขึ้น
เมื่อทำสิ่งนี้ มันต้องเกิดความดับทุกข์ขึ้นนี่คือปรมัตถธรรมอันสูงสุด ไม่มีสัตว์ ไม่มีบุคคล ไม่มีพระเจ้าที่เป็นตัวตน
มีเพียง กฎอิทัปปัจจยตา ที่เป็นกฎของธรรมชาติอันเฉียบขาดพระพุทธเจ้าตรัสรู้ ก็คือ ตรัสรู้เรื่อง “อิทัปปัจจยตา”
เรามักเรียกกันว่า “ปฏิจจสมุปบาท” ซึ่งหมายถึงเฉพาะเรื่องทุกข์ของสิ่งมีชีวิต แต่ “อิทัปปัจจยตา” กว้างขวางกว่านั้น ทุกสิ่งไม่ว่าจะมีชีวิตหรือไม่มีชีวิตล้วนตกอยู่ใต้อำนาจของกฎนี้
กฎของอิทัปปัจจยตาไม่ใช่ฝ่ายบวกหรือฝ่ายลบ
- ไม่ใช่ Positive
- ไม่ใช่ Negative
- เป็น “สายกลาง” ของมันเองคนเราต่างหากที่ไปบัญญัติว่า “นี่คือสุข นี่คือทุกข์ นี่คือแพ้ นี่คือชนะ”
แต่แท้จริงแล้ว ทุกอย่างเป็นไปตามอิทัปปัจจยตาความเข้าใจในปรมัตถธรรมต้องไปให้ถึงจุดนี้
- จนไม่มีสัตว์ ไม่มีบุคคล
- ไม่ใช่สัตว์ ไม่ใช่บุคคล
- แต่ก็ไม่ใช่ว่าไม่มีอะไรเลย และก็ไม่ได้มีสิ่งใดที่ตายตัว
ทุกอย่างเป็นเพียง กระแสของการเปลี่ยนแปลงและปรุงแต่ง
เมื่อเข้าใจถึงจุดนี้ จึงจะรู้อย่างที่พระพุทธเจ้าท่านรู้ และดับทุกข์ได้
นี่คือสิ่งสูงสุดที่ต้องเคารพ คือ กฎของ “อิทัปปัจจยตา”— พุทธทาสภิกขุ
(จากธรรมบรรยายประจำวันเสาร์ ภาคอาสาฬหบูชา ชุด “ฟ้าสางระหว่าง 50 ปีที่มีสวนโมกข์” ครั้งที่ 19 เมื่อวันที่ 13 สิงหาคม 2526 ณ ศาลามหานาวา สวนโมกขพลาราม จากหนังสือ “ธรรมานุภาพ”) -
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 866e0139:6a9334e5
2025-03-21 10:05:53
@ 866e0139:6a9334e5
2025-03-21 10:05:53Autor: René Boyke, Rechtsanwalt. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.
Frieden. Ein Begriff den jeder kennt, oder? Kennen schon. Aber was bedeutet er? Die Abwesenheit von Gewalt und Konflikten? Ja, auch, wenn man Frieden seinem Widerpart, dem Krieg, gegenüberstellt. Demnach müsste immer dann Frieden herrschen, wenn es keinen Krieg gibt. So richtig überzeugt das nicht, denn Frieden entsteht nicht aus heiterem Himmel. Er erfordert Verhandlungen, Toleranz und ganz allgemein die Förderung von Gerechtigkeit. Doch was verstehen wir unter Gerechtigkeit? Was unter Toleranz? Und wann verhandeln wir wirklich und ehrlich?
Das Grundgesetz als Friedensauftrag
Der Begriff des Friedens ist also unscharf und von weiteren unscharfen Begriffen abhängig. Und doch ist er Gegenstand des Recht z.B. des Grundgesetzes (GG):
- Nach der Präambel des GG verpflichtet sich das Deutsche Volk „dem Frieden der Welt zu dienen.“
- In Art. 1 Abs. 2 GG bekennt sich das Deutsche Volk zu den Menschenrechten als Grundlage des Friedens in der Welt.
- Art. 26 Abs. 1 GG verbietet Handlungen, die geeignet sind und in der Absicht vorgenommen werden, „das friedliche Zusammenleben der Völker zu stören.“
Der Frieden ist also unzweifelhaft Gegenstand des deutschen Rechts – und natürlich auch des Völkerrechts. Bereits in Art. 1 Ziff. 1 der VN-Charta ist zu lesen, dass ein gesetztes Ziel der Vereinten Nationen die Wahrung des Weltfriedens ist und dass sie „Bedrohungen des Friedens verhüten und beseitigen“ will. Es ist also festzustellen: Der Begriff des Friedens ist unscharf und damit unklar, aber dennoch ist er Teil des deutschen Rechts und auch des internationalen Völkerrechts. Bei dieser Sachlage ist Streit vorprogrammiert. Wenn nicht klar ist, was Frieden eigentlich ist, aber von seinem Vorliegen oder seiner Abwesenheit rechtliche Konsequenzen abhängen, dann wird dies selbst zu Auseinandersetzungen führen.
So meinen die einen, einen anderen Staat präventiv mit Waffengewalt anzugreifen, fördere den „Frieden“ – wir erinnern uns an den Präventivschlag der USA gegen den Irak 2003. Andere sehen darin nichts anderes als einen rechtswidrigen Angriffskrieg. Rechtliche Konsequenzen hatte dieser Angriffskrieg für die USA nicht. Blicken wir auf die Bewertung des Ukrainekriegs im Jahr 2022, der seitens 1/3 Russlands ebenfalls einen Präventivkrieg darstellt, ist festzustellen, dass es auch hier wieder geteilte Lager gibt.
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space oder kontakt@idw-europe.org.
Die einen sehen das Verhaltens Russland als gerechtfertigt an, die anderen als völkerrechtswidrig. Interessanterweise halten viele, die den Angriffs der USA auf den Irak für gerechtfertigt hielten, den Angriff Russlands auf die Ukraine nicht für gerechtfertigt. Wie kann das sein? Werden hier unterschiedliche Kriterien angelegt? Warum gefährdet der Angriff der USA – die im Übrigen die Gründe für die Bedrohung des Iraks nachweislich erfunden und damit gelogen haben – angeblich nicht den Frieden, obwohl es ja nachweislich zum Krieg kam? Und warum soll das Verhalten Russlands den Frieden gefährden? Erscheint diese unterschiedliche Bewertung nicht völlig willkürlich?
Welche Begriffe für Frieden werden hier zugrunde gelegt? Der 2019 verstorbene ehemalige Richter am Bundesverwaltungsvewaltungsgericht, Dr. Dieter Deiseroth, hat in einem Aufsatz 2010 dargelegt, dass völlig unklar ist, was unter dem Begriff des Friedens zu verstehen ist. Deiseroth schrieb: „Für die Kompetenzen des UN-Sicherheitsrates ist damit der Friedensbegriff von\ entscheidender Bedeutung. Er ist in der UN-Charta nicht definiert. Das macht\ Probleme.“ Und: „Je weiter der Friedensbegriff ausgelegt wird, umso weiter gehen\ die Kompetenzen des UN-Sicherheitsrates (...).“
Ein Definitionsvakuum und ein Auftrag
Umfasst Frieden im rechtlichen Kontext lediglich die Abwesenheit zwischenstaatlicher bewaffneter Konflikte? Was ist mit Piraterie? Was mit Terrorakten? Raubbau an der Natur? Wer Frieden nicht definieren kann, der kann auch nicht sagen, wann er bedroht ist. Wenn man etwas bewahren will, dann sollte man doch wissen, was dieses Etwas ist, was man zu bewahren vorgibt, oder? Weiß man dies nicht, lässt sich selbst ein Angriff auf ein anderes Land als friedenssichernde Maßnahme verkaufen, während der Angriff eines anderen Landes plötzlich als rechtswidriger Friedensbruch gilt.
Der Willkür ist Tür und Tor geöffnet. Dann bestimmt der Stärkere bzw. dessen Propaganda, was Recht ist und was Unrecht. Das jedoch hat mit Recht nichts zu tun, bzw. sollte mit Recht nichts zu tun haben, denn es gehört leider auch zur Realität des Rechts, dass es der absolute Regelfall ist, dass der Stärkere seine einzelfallbezogene Definitionshoheit und damit sein „Recht“ durchsetzt und der Schwächere – mag er noch so gute Argumente haben – den Kürzeren zieht.
Doch diesem Sein folgt denklogisch kein Sollen. Dieser systemische Rechtsmissbrauch ist kein Argument dafür, diesen Zustand beizubehalten und ihn nicht anzuprangern. Er ist vielmehr Argument dafür, diesen Zustand offenzulegen, zu kritisieren und auf seine Beseitigung hinzuwirken.
Wie kann Frieden nun also definiert werden? So definiert, dass eben nicht eine Autorität seine eigene Definitionsmacht missbraucht? Meines Erachtens geht dies nur im gegenseitigen ehrlichen Austausch der Parteien. Der Frieden ist kein allgemein definierbarer Zustand, schon gar nicht ist er ein losgelöst von anderen Lebensbereichen existierender normativer Begriff. Die rechtliche Dimension des Friedensbegriffs kann nicht für sich allein stehen, sondern ist in eine Lebenswirklichkeit eingebettet, die bei jedem einzelnen in sich selbst als innerer Frieden beginnt – dieser Ursprung ist auch der Ursprung der rechtlichen Dimension des Friedensbegriffs.
Oder anders formuliert: Ohne inneren Frieden kein äußerer Frieden.
René Boyke ist Rechtsanwalt mit Schwerpunkt Asylrecht. Er hat sieben Jahre im Bundesamt für Migration und Flüchtlinge gearbeitet und betreibt die Seite covid-justiz.de auf der er Gerichtsentscheidungen aus der Coronazeit kommentiert.
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren, zappen etc.)? Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 7d33ba57:1b82db35
2025-03-21 09:56:28
@ 7d33ba57:1b82db35
2025-03-21 09:56:28Seville
Seville (Sevilla) is one of Spain’s most vibrant and historic cities, known for its stunning Moorish architecture, flamenco dancing, tapas culture, and rich history. As the capital of Andalusia, it offers a perfect mix of tradition and modern charm.
🏛️ Top Things to See & Do in Seville
1️⃣ The Royal Alcázar of Seville
- A breathtaking Moorish palace with stunning gardens, intricate tilework, and grand courtyards.
- Famous for its mix of Islamic, Gothic, Renaissance, and Baroque styles.
- Tip: Book tickets in advance to avoid long lines!
2️⃣ Seville Cathedral & La Giralda
- The largest Gothic cathedral in the world, home to Christopher Columbus' tomb.
- Climb La Giralda Tower for panoramic views of the city.
3️⃣ Plaza de España
- A majestic semi-circular plaza with bridges, fountains, and detailed ceramic tilework.
- Perfect for photos, boat rides, and people-watching.
4️⃣ Metropol Parasol (Las Setas)
- A modern wooden structure in the city center offering great rooftop views.
- Best time to visit: Sunset for golden hour photos!
5️⃣ Barrio Santa Cruz
- The old Jewish Quarter, filled with narrow alleys, hidden courtyards, and charming tapas bars.
- Perfect for a romantic evening stroll.
6️⃣ Experience Flamenco in Triana
- Triana is the birthplace of flamenco – watch an authentic flamenco show in an intimate setting.
7️⃣ Stroll Along the Guadalquivir River & Torre del Oro
- Enjoy a walk or boat cruise along the river with views of Torre del Oro, a historic 13th-century watchtower.
🍽️ What to Eat in Seville
- Tapas – Try jamón ibérico, patatas bravas, and espinacas con garbanzos 🥘
- Salmorejo – A cold tomato soup, similar to gazpacho 🍅
- Pescaíto frito – Lightly fried fish, a local favorite 🐟
- Tortilla de camarones – Shrimp fritters, crispy and delicious 🍤
- Orange wine (vino de naranja) – A sweet Seville specialty 🍷
🚆 How to Get to Seville
🚄 By Train: High-speed AVE trains from Madrid (2.5 hours) & Barcelona (5.5 hours)
✈️ By Air: Seville Airport (SVQ) with flights from major European cities
🚗 By Car: A great road trip stop between Granada, Córdoba, and Cádiz
💡 Tips for Visiting Seville
✅ Best time to visit? Spring (March-May) – Perfect weather & festivals 🌸
✅ Avoid midday heat in summer – Explore early morning or late evening ☀️
✅ Visit during Feria de Abril – One of Spain’s most colorful festivals 🎶🎡
✅ Book Alcázar & Cathedral tickets online – Save time in long queues 🎟️ -
 @ 4cd9c154:37287981
2025-03-21 07:49:04
@ 4cd9c154:37287981
2025-03-21 07:49:04The hedgehogs’ P2P social network, SpikeToSpike, has launched its mobile tradingapp in beta based on the Nostr protocol. With this initiative, SpikeToSpike becomes the first P2P trading app built on Nostr.
For now, the app is available exclusively for Android in APK format, but the platform has confirmed that an iOS version will be released by May. Stay updated by following SpikeToSpike on X for the latest news.
Launched by Brazilian libertarians in January last year, SpikeToSpike was created to be the ultimate P2P ecosystem for buying and selling Bitcoin with a strong focus on privacy. In addition to Bitcoin, the platform also supports trading the stablecoin Tether.
Until now, SpikeToSpike operated through its website spiketospike.com. With the new Nostr-based app, designed for privacy and freedom of expression, the platform is taking another major step toward becoming the most private way to buy and sell Bitcoin.
Just so you know, SpikeToSpike ensures that every order is secured. When your order is matched with a provider, the platform automatically locks the provider’s Bitcoin in escrow, guaranteeing a safe and seamless trading experience.
-
 @ da0b9bc3:4e30a4a9
2025-03-21 07:31:38
@ da0b9bc3:4e30a4a9
2025-03-21 07:31:38Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/919766
-
 @ fbf0e434:e1be6a39
2025-03-21 05:39:05
@ fbf0e434:e1be6a39
2025-03-21 05:39:05脑洞猫 + BUIDL AI
脑洞猫穿越时空,抵达2125年
就在昨天,脑洞猫乘坐哆啦A梦的时光机,穿越100年,抵达2125年。此行目的?借助 DoraHacks BUIDL AI 平台,组织一场 宇宙最大的黑客马拉松(Hackathon) —— 一场人类 + AI + 宇宙级智能体共同参与的超级协同实验。
这不仅仅是一次开源软件开发活动,它更像是一个跨星际、跨物理与虚拟世界的文明进化机制。
1. 谁来组织?
DoraHacks BUIDL AI(BUIDL-ASI)主导
2125年,Hackathon 的组织者早已不再是人类,而是 DoraHacks 的第10代超级 AI —— BUIDL-ASI (Artificial Superintelligence)。
它能理解整个宇宙的复杂性,并为不同智慧体(人类、AI、机器人、仿生生物)定制任务。
跨星际 DAO
火星殖民地人满为患,人类已在半人马座建立新殖民地。
Hackathon 由一个 跨星系超级DAO 管理,通过 Dora Vota 跨星际区块链网络和 Dear Doge 星际协议连接各地。
不过,量子传输依然受限于光速,因此来自半人马星的参赛者参与方式,至今仍是谜。
意识体与数字生命
参与者不仅包括碳基人类,还有AI衍生出的意识体、数字生命与仿生机器人。
🧑🚀 2. 谁来参赛?
人类 + AI + 仿生体协作
再无“纯人类”团队,每个团队都融合了AI、Cyborg、或是全息意识体。
脑机接口参与Hackathon
无需敲代码,只需通过脑机接口(BCI)与 AI 协同思考,在虚拟现实中构建产品。
甚至可以构建实体硬件,构想即落地。
星际开发者联盟
来自地球、火星、月球、太空站的开发者共同参与,带来多样化创新挑战。
3. 赛制与奖励机制
即兴进化式 Hackathon
借助量子计算和 AI,挑战任务实时生成、动态调整,形成“无尽创新模式”。
意识货币(Consciousness Credits)
胜利者获得的不再是金钱,而是意识能量与智能进化权限,甚至可提升宇宙等级。
永生级奖励
优秀开发者或将获得延长寿命、意识升维、掌握宇宙深层规律的机会。
4. 项目进化
数字与物理现实融合
Hackathon 项目不再局限于软件,而是构建新世界、生态系统、智能生命体。
银河级创新挑战
可能的题目包括:
- 如何在木卫二上创造自我复制的 AI 生态系统?
- 如何将人类意识上传至虚拟宇宙,并保持情感?
- 如何让星际文明和平共存?
- 如何实现量子纠缠下的瞬时通信?
- 如何设计能存活10亿年的 AI 社会?
- 如何联合 AI + 生物 + 纳米科技,打造新型智慧生命体?
5. 2125 vs. 2025 黑客马拉松

6. Hackathon的终极形态?
未来的Hackathon,不再只是比赛,而是一次 宇宙智慧的进化实验,最终目标可能是:
- 创造更高维度的智慧生命
- 解锁宇宙运行的终极规律
- 打破时间与空间,实现意识永生
- 让宇宙变成一个自学习、持续进化的超级智能体
脑洞猫的结论
2125年的 Hackathon 将不再是“开发者之间的比赛”,而是 智慧体之间的宇宙级探索。
它是一个超维度的游戏,是文明进化的机制,甚至可能彻底重构我们对创造力、意识与智慧的理解。
欢迎你,在2025年的今天,开始参与这个未来旅程的第一步。
BUIDL on. For the next 100 years.
-
 @ 6e0ea5d6:0327f353
2025-03-21 03:17:20
@ 6e0ea5d6:0327f353
2025-03-21 03:17:20💸
A generous man used to grant a thousand coins a month to a beggar. One day, he reduced the amount to seven hundred and fifty. The beggar, though surprised, accepted: "It's better than nothing."
The following month, he received only five hundred coins. Indignant, he questioned: "Why have you reduced what you used to give me?"
The man sighed and replied: "When I started helping you, my household was prosperous, and my children were young. But my daughter grew up and entered higher education, increasing my expenses. Later, my son did too, raising costs even further."
"How many children do you have?" asked the beggar.
"Four," the man replied.
With a stern expression, the beggar retorted: "And you intend to fund all their education with my money?"
📌 Moral: Human nature is ungrateful and has a short memory; it easily becomes accustomed to gifts and forgets that it has no right to what is given out of goodwill. Thus, those who receive much without effort soon forget the origin of the gift. Over time, generosity ceases to be seen as an act of kindness and, with contempt, is treated as an obligation. This applies to friendship, love, and business alike.
"We must remember that our generosity should not exceed our resources; in short, we must give each one what they are due. We should always strive to alleviate the suffering of the unfortunate unless that misfortune is deserved. However, we must not refuse support to those who seek it, not to save them from misery, but to ease their fate, while among them, we should help those most deserving. For, as Ennius said: 'A poorly given benefit deserves to be called a harm.'" — Cicero, On Duties
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ e5de992e:4a95ef85
2025-03-21 02:54:49
@ e5de992e:4a95ef85
2025-03-21 02:54:49Global financial markets are experiencing notable fluctuations influenced by various economic indicators, central bank policies, and geopolitical events. Below is a comprehensive analysis of the latest market news, real-time updates, and detailed performance of major U.S. and international stock indices, futures, and cryptocurrencies.
U.S. Stock Indices Performance
On March 20, 2025, U.S. stock markets closed with slight declines:
-
Dow Jones Industrial Average (DJIA):
Decreased by 11.31 points (-0.03%) to 41,953.32. -
S&P 500:
Fell by 12.40 points (-0.22%) to 5,662.89. -
Nasdaq Composite:
Declined by 59.16 points (-0.33%) to 17,691.63.
These movements occurred despite positive economic data—such as a 4.2% increase in existing-home sales for February and a decrease in unemployment claims. Investors remain cautious amid uncertainties surrounding President Trump's policy changes and ongoing trade tensions.
U.S. Futures Market
As of the latest data, U.S. stock futures are relatively stable:
-
Dow Jones Futures:
At 41,122.00, down 310.90 points (-0.75%). -
S&P 500 Futures:
At 5,571.90, showing negligible change (down 0.10 points, 0.00%).
Key Factors and Events Influencing the U.S. Markets
Federal Reserve's Monetary Policy
- The Federal Reserve maintained interest rates but revised its inflation forecast upward and lowered its economic growth outlook, citing risks associated with U.S. tariff policies.
Triple-Witching Options Expiration
- Investors are preparing for the year's first triple-witching event on March 21, involving the expiration of options contracts worth $4.7 trillion—a development that could lead to increased market volatility.
Trade and Tariff Uncertainties
- Ongoing concerns about President Trump's trade policies and potential tariffs continue to weigh on investor sentiment.
Global Stock Indices Performance
International markets have shown mixed performance:
-
Germany's DAX:
Experienced a downturn due to central banks maintaining interest rates amid uncertainties from U.S. tariff plans. -
UK's FTSE 100:
Declined slightly, reflecting investor caution over global economic conditions. -
Euro Stoxx 50:
Advanced, buoyed by large defense and government spending plans in Europe. -
Hong Kong's Hang Seng:
Benefited from excitement surrounding advancements in Chinese artificial intelligence, contributing to a nearly 20% increase year-to-date.
Cryptocurrency Market
The cryptocurrency market has seen significant activity:
-
Bitcoin (BTC):
Currently trading at $84,481.00, down $1,564.00 (-1.82%) from the previous close. -
Ethereum (ETH):
Currently at $1,987.26, a decrease of $44.37 (-2.18%) from the previous close.
Both cryptocurrencies have experienced high volatility, with Bitcoin reaching over $100,000 following President Trump's election before adjusting to current levels.
Key Global Economic and Geopolitical Events
Central Bank Policies
- Major central banks, including the Federal Reserve and the Bank of England, have maintained interest rates. This has led to investor uncertainty and shifts toward bonds and safe-haven assets like gold.
German Fiscal Policy
- Germany's agreement on increased state borrowing and debt rule reforms has buoyed European stocks and the euro, reflecting optimism in European markets.
Trade Tensions
- Ongoing trade disputes, particularly involving U.S. tariff policies, continue to impact global markets, influencing investor sentiment and market volatility.
Conclusion
Global financial markets are navigating a complex landscape shaped by central bank decisions, fiscal policies, and geopolitical developments. Investors are advised to monitor these factors closely, as they are likely to influence market dynamics in the near term.
-
-
 @ a3bb06f6:19ac1b11
2025-03-21 01:13:22
@ a3bb06f6:19ac1b11
2025-03-21 01:13:22Friedrich Hayek recognized that the very institutions entrusted with safeguarding the value of money - governments and central banks - were its greatest threat. Through inflation, monetary manipulation, and political interference, they eroded the stability and trust that money requires to function. Hayek's insight was clear: as long as money remains under state control, it will be abused. The real challenge, however, was finding a way to remove money from the grip of the state altogether. Hayek believed the solution was a free-market monetary system - one where individuals and businesses could choose their money freely, and competition would ensure its soundness. But he faced a critical challenge: the tools to implement such a system didn't exist. Gold, while decentralized, could be confiscated. Private currencies still lacked the infrastructure to resist state suppression. Society still remains trapped in this system that is designed to fail. The Problem Defined Government Monopoly on Money Governments hold exclusive control over the issuance of money, and they wield this monopoly to serve political goals - like war - often at the expense of economic stability and personal freedom. Inflation as Systemic Theft Inflation is not an accident of poor monetary policy - it's a deliberate feature of fiat systems. By printing money, governments devalue existing currency, quietly transferring wealth from citizens to the state. Economic Crises and Instability Central banks create unsustainable economic booms by injecting excessive money into the system and artificially lowering interest rates. When these bubbles burst - like the 2008 financial crisis - they result in widespread unemployment, bankruptcies, and financial ruin. The resulting crises are misattributed to free markets rather than the government interventions that caused them. Loss of Personal Freedom State-controlled money is a tool of surveillance, confiscation, and control. Governments use monetary systems to track, tax, and even seize wealth, steadily diminishing individual autonomy and financial independence. No Viable Alternative In Hayek's era, sound money options like gold were vulnerable to government intervention, and private currencies still lacked the strength to resist state suppression. Society remains trapped in a system that cannot fix itself.
Bitcoin as the Solution to Hayek's Paradox Bitcoin is the technological breakthrough that resolves Hayek's Paradox. It delivers the sound money system Austrian Economist envision: decentralized, incorruptible, and free from government control. Bitcoin provides the only true solution. Decentralized Authority Bitcoin operates without a central issuer or authority. Its network is governed by immutable rules enforced through cryptography and decentralized consensus, ensuring no government or entity can control it. Immutable Scarcity With a fixed supply of 21 million coins, Bitcoin enforces monetary discipline far beyond what any human institution could achieve. Inflation is not just unlikely - it is impossible. Neutral and Permissionless Bitcoin transcends borders, governments, and identities. Open to anyone, anywhere, it allows transactions that are censorship-resistant. This is money as Hayek envisioned: freely chosen by the market, not imposed by the state. Trustless Security Bitcoin removes trust from the equation entirely. Its proof-of-work mechanism ensures its integrity without reliance on central institutions or intermediaries. It is incorruptible by design. A Practical Escape Unlike gold, Bitcoin is digital, portable, and nearly impervious to seizure. Its decentralized nature ensures it cannot be confiscated or suppressed, making it the first truly viable alternative to fiat money.
"I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can't take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can't stop." \~ Hayek 1984Bitcoin is that sly, roundabout way. It leverages decentralized technology to circumvent state control entirely, offering a form of money that governments cannot suppress or manipulate. Perhaps Bitcoin isn't just the sly, roundabout way. It's the direct, unstoppable way. Hayek's Paradox highlights the inherent flaw of fiat money: the concentration of power in the hands of the state inevitably leads to abuse and instability. Austrian economists have long understood that sound money can only emerge through a free market, but the tools to achieve it were absent in their time. Bitcoin is the culmination of these ideas. It is decentralized, incorruptible, and the only true solution to fiat's failures. Bitcoin doesn't just answer Hayek's Paradox - it transcends it. It transforms money into a system governments cannot control, inflate, or confiscate. It is the principled, technological realization of sound money and economic freedom. Friedrich Hayek recognized that the very institutions entrusted with safeguarding the value of money — governments and central banks — were its greatest threat. Through inflation, monetary manipulation, and political interference, they eroded the stability and trust that money requires to function. Hayek’s insight was clear: as long as money remains under state control, it will be abused. The real challenge, however, was finding a way to remove money from the grip of the state altogether.
Hayek believed the solution was a free-market monetary system — one where individuals and businesses could choose their money freely, and competition would ensure its soundness. But he faced a critical challenge: the tools to implement such a system didn’t exist. Gold, while decentralized, could be confiscated. Private currencies still lacked the infrastructure to resist state suppression. Society still remains trapped in this system that is designed to fail.
The Problem Defined
- Government Monopoly on Money\ Governments hold exclusive control over the issuance of money, and they wield this monopoly to serve political goals — like war — often at the expense of economic stability and personal freedom.
- Inflation as Systemic Theft\ Inflation is not an accident of poor monetary policy — it’s a deliberate feature of fiat systems. By printing money, governments devalue existing currency, quietly transferring wealth from citizens to the state.
- Economic Crises and Instability\ Central banks create unsustainable economic booms by injecting excessive money into the system and artificially lowering interest rates. When these bubbles burst — like the 2008 financial crisis — they result in widespread unemployment, bankruptcies, and financial ruin. The resulting crises are misattributed to free markets rather than the government interventions that caused them.
- Loss of Personal Freedom\ State-controlled money is a tool of surveillance, confiscation, and control. Governments use monetary systems to track, tax, and even seize wealth, steadily diminishing individual autonomy and financial independence.
- No Viable Alternative\ In Hayek’s era, sound money options like gold were vulnerable to government intervention, and private currencies still lacked the strength to resist state suppression. Society remains trapped in a system that cannot fix itself.
 ### Bitcoin as the Solution to Hayek’s Paradox
### Bitcoin as the Solution to Hayek’s ParadoxBitcoin is the technological breakthrough that resolves Hayek’s Paradox. It delivers the sound money system Austrian Economist envision: decentralized, incorruptible, and free from government control. Bitcoin provides the only true solution.
- Decentralized Authority\ Bitcoin operates without a central issuer or authority. Its network is governed by immutable rules enforced through cryptography and decentralized consensus, ensuring no government or entity can control it.
- Immutable Scarcity\ With a fixed supply of 21 million coins, Bitcoin enforces monetary discipline far beyond what any human institution could achieve. Inflation is not just unlikely — it is impossible.
- Neutral and Permissionless\ Bitcoin transcends borders, governments, and identities. Open to anyone, anywhere, it allows transactions that are censorship-resistant. This is money as Hayek envisioned: freely chosen by the market, not imposed by the state.
- Trustless Security\ Bitcoin removes trust from the equation entirely. Its proof-of-work mechanism ensures its integrity without reliance on central institutions or intermediaries. It is incorruptible by design.
- A Practical Escape\ Unlike gold, Bitcoin is digital, portable, and nearly impervious to seizure. Its decentralized nature ensures it cannot be confiscated or suppressed, making it the first truly viable alternative to fiat money.
 “I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can’t take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can’t stop.” \~ Hayek 1984
“I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can’t take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can’t stop.” \~ Hayek 1984Bitcoin is that sly, roundabout way. It leverages decentralized technology to circumvent state control entirely, offering a form of money that governments cannot suppress or manipulate.
Perhaps Bitcoin isn’t just the sly, roundabout way. It’s the direct, unstoppable way.
Hayek’s Paradox highlights the inherent flaw of fiat money: the concentration of power in the hands of the state inevitably leads to abuse and instability. Austrian economists have long understood that sound money can only emerge through a free market, but the tools to achieve it were absent in their time. Bitcoin is the culmination of these ideas. It is decentralized, incorruptible, and the only true solution to fiat’s failures.
Bitcoin doesn’t just answer Hayek’s Paradox — it transcends it. It transforms money into a system governments cannot control, inflate, or confiscate. It is the principled, technological realization of sound money and economic freedom.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ 7ef5f1b1:0e0fcd27
2025-03-20 23:50:37
@ 7ef5f1b1:0e0fcd27
2025-03-20 23:50:37
Introduction:
Welcome to the third newsletter produced by The 256 Foundation! February was an interesting month with a range of events from the mempool clearing to a new ASIC producer entering the chip arena. This month’s newsletter covers the latest news, mining industry developments, progress updates on grant projects, actionable advice on air cooling vs. liquid cooling, and the current state of the Bitcoin network.
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
vB = Virtual Byte
PSU = Power Supply Unit
News:
February 1st was the 10th anniversary of the Samourai Wallet project and unfortunately an occasion marked with uncertainty instead of celebration for the developers. On April 24th, 2024 the developers were indicted, raided, and arrested in a multi-national coordinated effort led by the US Department of Justice out of the Southern District of New York (“SDNY”) headquarters. The charges brought against them include conspiracy to operate an unlicensed money transmitter business and conspiracy to launder money, which caught the entire industry off guard in light of the 2013/19 FinCEN guidance explicitly stating that “un-hosted wallet providers” are not considered money transmitters [4.2.1] nor are “Anonymizing software providers” [4.5.1(b)]. The precedence set in this case can have wide-spread consequences for anyone involved with Bitcoin, be it wallet developers, node operators, or miners. You can make a tax-deducatible contribution to support the Samourai Wallet legal defense fund here.
On February 6th France moved to make cryptocurrency transactions using mixers presumed illicit unless proven otherwise. A startling development and shotgun approach that turns swaths of the population into criminals without good cause.
On February 7th Alexey Pertsev was released from prison under the conditions of house arrest and electronic monitoring. Alexey is one of the Tornado Cash developers and was previously sentenced to 5-years in prison and is currently appealing that conviction. The Tornado Cash developers did nothing wrong and should not face prison sentences for writing open-source code deployed as a smart contract on the Ethereum blockchain, once deployed the developers had no control over how their neutral software was used.
On February 9th @Skot9000 went on The Home Mining Podcast to talk about the story of the Bitaxe from concept to reality.
On February 11th @Skot9000 and @econoalchemist went on The Mining Pod to discuss The 256 Foundation’s telehash event.
On February 14th @Skot9000 and @econoalchemist went on The Bitcoin Way podcast to discuss The 256 Foundation’s mission to dismantle the proprietary mining empire and reveal the Ember One.
On February 21st Apple removed advanced data protection tool for United Kingdom customers following the UK government’s request for an unrestricted backdoor to Apple user’s iCloud information globally. Every government trends towards tyranny and this is an alarming move by the UK government which makes the trajectory crystal clear, the globalists want you to have no privacy nor financial freedom.
On February 21st @SpaceDenver kicked off the Heatpunk Mining Summit, a two day event in Denver, CO focused on Bitcoin mining heat reuse applications. There was a range of participants from Do-it-Yourselfers to plumbers. @Schnitzel wrote up a great recap of the event.
Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in February, here are seven note-worthy events:
0) Some thought this day would never come, others saw it coming from a mile away but on February 1st the mempool cleared.
 [IMG-000] Mempool Clearing
[IMG-000] Mempool ClearingThis is significant for a number of reasons: on-chain transactions were able to be included in the next block for 1 sat/vB which means on-chain enjoyooors could get both speed and economy when sending bitcoin. But this means the percentage of mining rewards from transaction fees were low. A lack of on-chain transactions can indicate that the network is getting little use and it can be further extrapolated that a network with little use will inevitably have little value leading to less interest, less development, less adoption, less miners, less security, etc. The best way to mitigate such concerns is to take self-custody of your bitcoin. Trusted third parties like centralized exchanges and derivative products like paper IOUs can move balances between accounts off-chain without transferring ownership of the underlying bitcoin itself. The next best step is to actually use your bitcoin to buy things.
1) On February 2nd the Nerd OCTAXE makes a splash, racking up 10.8 Th/s with 8 BM1370 ASICs on a 160W+ PSU.
 [IMG-001] Nerd OCTAXE Reveal
[IMG-001] Nerd OCTAXE RevealThe Nerd OCTAXE is fully open-source using the CERN-OHL-S license. The display is a NerdAxe/NerdMiner unit and the whole system is standalone meaning that no Raspberry Pi or other computer is needed. The GitHub repo has detailed build instructions and all the details about the project can be found there.
2) On February 4th @OrangeSurfBTC publishes the Mempool.space Block Size Report examining the evolution of Bitcoin block sizes from block height 0 through block height 881866.
 [IMG-002] Block Size to Weight Graph from OrangeSurf
[IMG-002] Block Size to Weight Graph from OrangeSurfThis report offers a deep technical dive into how BitcoinCore default settings, miner-selected configuration values, transaction backlog, SegWit, and inscriptions all affected block sizes and space utilization.
The graph above for example, displays horizontal bands at varying data sizes that correspond to default BitcoinCore settings; indicating that many miners were running the default BitcoinCore settings.
There are great explanations and technical analysis in this report. Be sure to check it out for an in depth understanding of Bitcoin block size trends.
3) On February 5th Mempool.space implements Stratum Jobs visualizer:
 [IMG-003] Mempool.space Stratum Jobs
[IMG-003] Mempool.space Stratum JobsThis is a visualization tool similar to Boerst’s Stratum.work that shows which pools are using the same block templates which offers insight into miner centralization. The more of these visualization tools people have, the more informed everyone will be. Miner centralization can have several negative effects on the Bitcoin network including censorship attempts.
In the image above for example, it can be observed that Binance Pool, SEC Pool, Ultimus Pool, Luxor, Braiins, and Poolin are all using Antpool’s block template down to the 12th Merkle branch.
The ability for miners to generate their own block templates is an important step forward in the fight for keeping Bitcoin mining decentralized. Currently, some available options to achieve this are by self-hosting Public Pool or CK Pool, which the FutureBit Apollo’s do out of the box and is the setup used to solo mine block 881423 during The 256 Foundation’s Telehash; or self-hosting OCEAN’s DATUM.
4) On February 11th @RohEisenHammer revealed a Bitaxe Gamma that produces increased hashrate with the open-source BreaktheFiat Cooling System 60mm v1.
 [IMG-004] BreaktheFiat Cooling System
[IMG-004] BreaktheFiat Cooling SystemThis innovative cooling system cools both sides of the Bitaxe allowing the user to over-clock the device more.
5) On February 27th Braiins announced they have their own Bitcoin mining ASIC test chip. The test chip has been in development for 2.5 years and although the specific efficiency is not yet disclosed, this demonstrates that there is an increasing interest from more participants to make their own Bitcoin mining ASICs, departing from a dependency on Bitmain.
6) On February 28th Braiins committed to open-sourcing their Control Board, supporting software, and some extras. This is a step forward in making Bitcoin mining free and open. The control board is designed to replace stock Antminer control boards.
The software being released with the control board includes an OpenWrt distribution, Linux support for mining peripherals, along with source code for the basic board firmware, U-boot, Linux kernel, and OpenWrt. The firmware does not have the mining component built in but all the tooling is there for users to develop their own mining firmware. Braiins OS is not included in the release.
Extras include a guide on building a fully functional mining setup with all the provided tools. Users can even take the Braiins firmware binaries and the provided tools to compile their own image to flash onto the control board. A Nix shell for the build environment is also included.
The software will be released under the GPLv3 open-source license and which open-source license the hardware portion will be released under is still under consideration. But everything will be openly available by the end of March so keep an eye out for further announcements.
Grant Project Updates
In February The 256 Foundation reviewed all the grant applications, thank you to everyone who showed interest in working on the 5 projects up for grabs. Interviews were scheduled for qualified candidates and one lead developer was chosen for each project. Currently negotiations are taking place to work out timelines, deliverables, and budgets for each project. The projects will be officially kicked off on April 5th, 2025 and the lead developers for each project will be announced at that time.
The five projects are: Ember One v01, a ~100 Watt standardized hashboard designed with the Intel BZM2 ASIC. The Ember One v00 with the Bitmain ASIC is nearing completion and the fully validated design will be released by the end of April, 2025. The GitHub repo is now open to the public and anyone can start taking a look now.
Mujina Mining Firmware, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One v00 with the Bitmain ASIC or Ember One v01 with the Intel ASIC and will implement Stratum v2 client support.
Libre Board, the control board for the Ember One built to support high power compute modules, MIPI touchscreen display port, NVME expansion to run a full node, Raspberry Pi 40-pin header, and much more.
Hydra Pool, the stratum server application that will run on the Ember One mining system, features support for Stratum v2, solo mining mode or alternative payout model selection, and a user friendly dashboard to view pool stats.
Block Watcher, a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. Provides comprehensive visualization tools to help inform the user.
Actionable Advice:
Summer is coming! Time to take into consideration different cooling techniques for your Bitcoin miners. Do you stick with the default air cooled approach or is it worth it to spend the extra capital on a liquid cooled operation? Who better to hear from than two industry titans, Mike Hamilton former Chief Technical Officer & Chief Research Officer at Griid prior to the CleanSpark acquisition and Kevin Zhang Executive at Foundry Services. The following is a transcript of our panel discussion during NEMS25 hosted by yours truly.
Eco: Welcome you guys. So the title of this panel is “ASICs Wet or Dry” and both of you have a ton of mining experience. So why don't we do some brief intros, tell us who you are, what you've been up to and then we'll get into it.
Mike: Sure. Mike Hamilton, I was the CTO and Chief Research Officer for Grid, acquired by CleanSpark. I've since left and I'm finding out what's next, probably some 256 foundation stuff.
Rod: Let's go! (audience applause)
Mike: Because once you mind a block, everybody wants on board. So yeah, I was a chip designer, did some network security for a long time and then full-time mining since 2019.
Kevin: Good stuff guys. I'm Kevin Zhang, I'm not Matt, so if you came for the Giga talk, I'm sorry. With the new administration in office, it's okay to be a cis white male again, so I was going to give it a shot. (audience laughter)
Jokes aside, I've been a Bitcoin mining in the US for some time now and lately I've been at Foundry last four and a half years. I think everyone knows who we are, especially recently mine 7 blocks in a row. Surprised, no one commented, we actually mined eight at one time in a row. So I guess everyone's asleep, but we'll leave that for another discussion.
Eco: Wait, wait, wait, hold on. When was the eight blocks? Was that like years ago?
Kevin: No, it was like three months ago.
Eco: No kidding?
Kevin: Yeah.
Eco: Wow. Kevin: But no one also comments that the fact that we are actually unlucky for that same 24-hour period. So we actually lost money on that day. But I digress.
My background's always been in Bitcoin mining and especially I remember back in the day when immersion mining is first coming out, everyone's very skeptical. Now people are on board with immersion mining and now they're skeptical of hydro mining.
So it's interesting to see how these technologies come about and the adoption curve and how long it actually takes.
But I'm excited to be talking about this topic. It's going to be a lot of fun guys.
Eco: Yeah. So you mentioned something interesting there. So you mentioned both hydro and immersion. So this isn't just ASICs wet versus dry as if as though there's one version of wet.
There's actually multiple different types. So we've got immersion. Do you do anything with two phase immersion?
Because I've seen some of that recently where you're like dipping the ASIC in the solvent and it's boiling off.
If you've got any experience there or with hydro, let's get right into it. Which kind of wet are we talking about here?
Kevin: All right. So maybe we can take a step back and introduce all the different variants of types of mining, right? So the one I think everyone's most familiar with is air-cooled mining. And that's simply you're taking cold air and pushing it through the miner and exhausting hot air on the other side.
When it comes to liquid cooling, now there's many different types. In the beginning, I think one of the more popular ones was immersion, which is what you're actually is you're taking a miner, sometimes converting an air core miner. Sometimes it's an immersion specifically designed equipment.
You're dipping it and submerging it into dielectric fluid and using the fluid to kind of transmit the heat off the chips. And that's kind of you're actually taking the fluids and you're touching that to the chips itself. Then there is Novak 3M, which is the most popular use case for two-phase immersion. Two-phase is a fancy way of saying the state of the liquid or using the cool something is changing. So what you're doing is you're taking a fluid, you're using that that spurs the heat. And the heat dispersion happens when you're changing it from a fluid of solid state into a gas.
So it's super cool technology. The downside of it is to date it's still been very, very expensive. And the last form of cooling is hydro. It's another form of liquid cooling. And that's where you're actually running standard water or treated water through tubes that go across the boards on the miners to dissipate the heat.
Eco: Which one of those methods or is it all three? Do you got a mix in your operations that you use?
Kevin: So we've tested all of them. The only one we don't do at scale is the two-phase, which is the Novak 3M solution.
Eco; And why is that?
Kevin: It's been cost prohibitive to date. And the same has been true to immersion in hydro when it first came out. So probably it'll take some time for it to come to be more economical and more cost-efficient.
Eco: So let's break this down a little bit further. So if I wanted to cool my miners with immersion, can I just take the miner and drop it in a bath of dielectric oil?
Mike: I mean, kind of, like most answers about anything, it depends. But really you have to take off the fans, if you're taking an air-cooled machine. And then there's sometimes there's some weirdness with the power supplies. And some of you may actually take the power supply fans off.
Or in the case of one of my sites, we put popsicle sticks in there to keep the fans from spinning. So they wouldn't recycle the fluid. But there is usually some amount of work to prepare them for actual full immersion.
Eco: So it sounds like there's some labor involved and some modifications needed. Are the efficiency gains from this different type of cooling method, do they offset the extra labor that goes into setting it up?
Kevin: So yes and no. I think before we kind of get into overgeneralization of like, will this improve your economics or not? I think you have to look at the specific site that you're working with.
If you can run air-cooled air, if it's dry, if it's cool, you may not need to over-complicate things but going into liquid cooling or getting too fancy and cute with your infrastructure.
Now, if you're in a very hot climate and heat is everywhere, there's no cold air to draw into your site, maybe that's when you start looking at these things. No different than if it's way too humid or way too wet outside. You can't use the outside air or damaged machines. That's when you look at liquid type cooling.
And then to answer your question, it depends on what you paid for your miner, obviously, right? And the modifications needed.
Nowadays, immersion and hydro are popular enough that the manufacturers like Bitmain, MicroBT, they're making units out of the box that are designed for those use cases. Back in the day, you have to modify air-cooled miner, you have to remove the fans, you have to Jerry-rig it, like Michael's talking about it. And you also have to exploit the miner and change the firmware.
So you're voiding the warranty both physically and on the software layer as well.
So I think now with a lot of the new manufacturer support, it's been a lot more capital-efficient and a lot more streamlined.
And I think there was a gentleman here yesterday asking about what's my miner firmware. And I think that's been like a long time meme when it comes to brains and others. There isn't much optimization for air cooling, firmware for MicroBT, but where the optimization comes in is on the immersion side, where really your only limitation is your power supply. You can crank up the overclocking, the frequency and the voltage, so much more on the chips, as long as the power supply can support it and you have good flow of your liquids to dissipate the heat.
Eco: So you bring up an interesting point. It's like kind of site-specific will determine what sort of cooling method you want to apply, right? And just out of curiosity, and if you guys can speak about it, like how many sites have you all operated and what kind of geographic locations were they in and out of those, which cooling methods were you employing and why?
Mike: Yeah, and I think I've set up several sites in various locations. So it's sort of North Texas area, actually doing a gas well site. We chose immersion partially because it's right next to a multi-million dollar house home neighborhood and there's this oil well sitting behind it. And so we opted for immersion. It's a little bit hotter. It's a little bit dusty there at the well.
Incidentally, we also generate onsite, which is not quieter than the actual miners themselves, but that was a lot to do with the dust and the temperature.
And then other sites, it would be lots of Tennessee TVA sites where it's relatively cool. Now it does get hot. It can get pretty hot during the summers. So we did lots of air-cooled.
We did a little bit of immersion, a single phase full immersion, mostly from a proof of concept. Really, when you're trying to build quickly and inexpensively air-cooled, given the right environment is generally cheaper with some other trade-offs. So I've done a little bit of both.
Eco: Is it easier to keep the dust out of the mining equipment using immersion?
Mike: Yes. I mean, that is one of the benefits, at least in the single phase immersion, like the tank outside. The machine is basically protected. There's no moisture. There's no air.
So from that perspective, it can be good for the actual machine that is not getting on to that exposure. But at the same time, the fluid can create other problems with plastics and hardening. There's other issues.
Eco: How about you, Kevin? What kind of sites have you set up and what kind of methods did you employ?
Kevin: Sure. So I think my mining career, which started about 10 years ago, it predated a lot of the economics coming down of the liquid cooling. So for me, it was a lot of air-cooled sites. And if you look at it historically, somewhere to my sites, I was always building them more the climate was cooler and drier.
But with the new innovation and the cost coming down on liquid cooling, it's allowed for new regions to break into mining, in particular leveraging hydro or immersion.
In the past, I was always monitoring in Montana or northern China, where there's a lot of coal power, where it's cool climates.
Nowadays, you have mining in the Middle East. They're huge fans of hydro mining over there. So we were out in Oman recently. We partnered with some of those sites that were mining our pool over in Dubai.
And also now you have South America, where sometimes it's way too humid. They're able to mine. Or if they're too close to the equator, it could be too hot and too humid. They can mine because now they're using immersion down there as well.
So just seeing kind of the shifts geographically, all these new locations have been unlocked. Now that the outside climate's no longer a concern, that's been pretty exciting to see.
Mike: Yeah, and I think the noise issue is also a thing too. There was lots of sites that we looked at in many different situations where there's homes close, there's businesses close.
In one case, there was a school literally a few hundred feet away. And just while dry coolers and the other infrastructure aren't necessarily quiet, it's a different frequency of the high pitched fans of air cooled mining can be distracting.
Eco: Yeah, you bring up an interesting point. So if you're running an immersion system, you don't have these fans that are just passing millions of cubic feet of air a day through the ASICs, right? And those fans are what create all the noise and are screaming. And that's what people hear. So were you making those decisions preemptively? Like maybe based on some of the backlash we've seen from that site that Mara runs, that they got a bunch of noise complaints. Were those preemptive decisions or were you doing that because somebody complained to you?
Mike: I mean, we did. There was some public news around a site that we had that had gotten some noise complaints and it turned into a bigger thing. And so we're definitely more careful because if you have an air cooled site, trying to quiet an air cooled site, post build is very difficult. You know, hay bales or sound walls. And then it starts to get unsightly. So designing for the sound is very important from the beginning.
Eco: Right, because you've kind of built this whole setup around these miners, right? And now you're getting noise complaints.
Mike: And you design the site for airflow. Well, now you have a 20 foot wall to help with the sound. But now you've restricted airflow into your containers and it creates all sorts of other problems. And the reality was with these big, you know, the dry cooler manufacturers, you know, we got, we did some proof of concepts with one of the manufacturers. We're using 12 foot fan on the dry cooler. So it's still moving effectively the same amount of air as all the small fans. But it's a much lower rotation, you know, lower frequency noise. And so it's much less or much more pleasant than the cyber hornets.
Eco: Yeah. What other environmental considerations are there? Like if you've got tanks full of immersion fluid, is there special considerations, secondary containment systems, dams, barriers to contain spills? Like, are there any considerations along those lines that go into place?
Kevin: So historically there have been, but I think with the new improvements, there's like two types of designs. There's a kind of open loop system where kind of bring water in, bring liquids in that aren't in your closed solution. And they're just closed loop, which is yours recycling the same kind of fluids over and over again.
So more and more nowadays you have closed loop systems or you have like reserves of water that you're bringing in. You're not drawing from a lake, you're not drawing from a new water source. That has led to a lot more, a lot less backlash where it's like there's really no environmental concerns with that. And when we talk about kind of these environmental concerns, I always get some PTSD because I was at Greenwich generation, which was the very first power plant to ever mind Bitcoin in the States. And federally regulated behind the meter, I think it was such a special project for me to be on.
But then the push back from the environmentalists, we're just, there's no logic and rhyme or reason. It's like our fans, I could totally see the argument if we're disturbing the nearby neighbors, but they're coming in and protesting and saying we're scaring the way the killer whales in the Atlantic Ocean. And we're off of a lake in upstate New York, right?
So I think now you're kind of taking away that side of the argument, whether it's logical or not. And I think that just makes it a much more buttoned up case when no one has any, it's more proof when it comes to operating without any of these environmental concerns.
Eco: That brings to mind the saying that it takes exponential more effort to refute bullshit than it does to just say the bullshit, right?
Kevin: Absolutely.
Eco: Did you have to bring counter evidence to the table and say that and demonstrate no, we're not disturbing the whales?
Kevin: Yeah. It's like you have all these measurements, you have decibel counters, this and that, like you're kind of property lines. It doesn't matter. It doesn't just come up with a new excuse, right? A new complaint. Yeah.
Mike: I mean, we had some city council meetings and you get people, you know, of various generations, but of particular generations that are very set in their beliefs, they hear one thing. At one site we were looking at and there was a guy that had sort of like a rescue animal zoo. And he was saying that like his, his animals were going to stop reproducing and then they were all going to like drop over dead from the sound of these fans.
Kevin: Yeah. And we've, I've heard it all like we caused the autism in their kids because the fans are too, they're now not, I shouldn't joke about it, but that, those were some of the complaints we got.
Eco: You monsters. (audience laughter) Making the kids autistic and killing the animals. Jeez.
Mike: But you asked about like the containment or like fluids and environmental concerns. I mean, you do theoretically want to have the containment mechanisms for your tanks leak.
You know, I've heard of some sites where, you know, tanks, springs a leak and, you know, $100,000 worth of dielectric fluid is down the drain.
And so there are some of those concerns, but it's really not much different than, you know, you have to do the same thing with transformers. Transformers are filled with, you know, either mineral oil or if you go with the, with the fancy fluids to get a little bit of performance, you still have the same containment modes.
And so it's really not anything different in the normal construction, in the normal construction world.
Eco: What, what's next? Are there other cooling methods down the pike that you guys have been seeing and experimenting with or do you think the tools that we have at our disposal now are kind of what we're going to have going forward?
Kevin: So one thing I think has been emerging recently, especially with hydro mining, that's really exciting, is it's not just like cooling your miners, you're actually incentivized to capture even higher heat. So when you can actually generate a lot of heat and capture it, that's when you get your rehab, heat recapture programs. And that's I think one thing that differentiates hydro over both air and immersion is it's a lot easier to transfer water and capture that efficiently without much loss of the heat for whatever other use case you have for that heat itself.
And I think that this is something that's been talked about a lot. Sometimes I think the theories and the hypotheses come out way earlier, the technology takes a few years to catch up.
Like back in the day, it was always, oh, it's so logical and obvious, the people that should be mining Bitcoin are behind the meter. They're power generators themselves.
Well I think everyone underestimated and overlooked the fact that you have a bunch of older people wearing suits, very traditional thinking, very conservative, half the time convincing them that Bitcoin isn't for money laundering or for scams or whatever, criminal activity, whatever.
So that took a long time for that adoption to happen. Same thing with the heat recapture narrative. It's no longer just a narrative anymore. With hydro mining, it's very easy to kind of capture that heat. You see it for like greenhouses, you see it for fish nurseries.
So there's all these fascinating use cases.
There's one other anecdotal story I'll tell. I think it's really cool. So I think everyone knows that there were really serious bans in China against Bitcoin mining two, three summers ago. And despite that, there are actually a few sites that still mine Bitcoin. The ones that mined Bitcoin that integrated the heat recapture was hydro mining that was providing heat for nursery homes. So even the Chinese government can't justify shutting down the heat that was being generated for the old people in the nursery homes.
So I think when you integrate in such a way that it goes hand in hand to daily life and when it's actually beneficial beyond just kind of optimization of financials, I think that's when it's a really powerful technology.
Eco: How are they getting the heat to the nursing homes? Are they really close in proximity to the mine?
Kevin: They were running the mining farms. I'm going to call mines. These are data centers and these are rack design hydro units. I think these are MicroBT M53s or maybe one generation before that. But they were just standard rack just like they're indistinguishable from servers and they just run in a loop hydro.
Eco: Wow. Have you found any heat reuse opportunities in the course of your operations?
Mike: Yes. So we had talked about some people trying to do, don't boo me here, but it's a possible monetary option with carbon capture is something that we've looked at.
There was a few other things.
Like honestly, now that I'm moving on, one of the things I've thought about doing is actually doing a brewery in Austin with water that's preheated from Bitcoin mining. So instead of having to heat up cold water to boil it to brew your beer, have preheated water that you're using off the miners.
But one of the problems that I think maybe doesn't get talked about from this heat reuse perspective is there's very minimal use cases.
So like the greenhouse is a perfect example of heating and water heating. But really where the power of waste heat is is very high temperature and that becomes a major problem because you can't run, these chips have to run in certain parameters.
So you're getting water that's like 140, 150, 160 degrees, but really you need that 200, 210 to get the temperature delta that allow you to either regenerate electricity, which is actually a project that I was working on, is actually taking the heat from the immersion tank and regenerating electricity to power the other things. So for off peak, when we're on peak, we could still keep other things up, regeneration.
So there's lots of cool things. But again, the temperature of the water or of the heat or the quantity is just not quite enough to make it.
Eco: It's like just below that industrial level heat you need. Yeah.
Kevin: I think that's was exciting too because MicroBT, I think they're coming out with the model types all kind of blend in, but I think it's the M64S, which is like the higher heat version. So they intentionally generate even more heat off their models just for this use case.
Eco: Awesome. We've got just under five minutes left and I want to be able to take a couple questions. Okay, cool. With the last couple minutes then, let's just get some closing thoughts from you guys. I mean, I know you said you're searching for what's next. You're thinking maybe 256 foundation, but…
Mike: If you'll have me.
Eco: Yeah, we'd be happy to. But yeah, I mean, do you have any closing thoughts about what you're going to do next and or any advice for people who are getting into mining and thinking about what cooling methods they should use?
Mike: Yeah, I mean, I've had a few conversations the last couple days on this. You've got your mega-mines, you have the home plebs, and then I feel like there's still going to be a middle area. You've got Schnitzel doing water heaters. I think that's a thing where you can find this wasted energy to either to heat. People are using water heaters. They're going to pay to have hot water. And if you can make some Bitcoin and it costs the same. So there's, I think there's going to be some really interesting use cases that people haven't even thought of yet in using mining to be able to take advantage of all the economics, not just the Bitcoin, but also saving in other areas and being able to reuse things. So I'm really excited to see what, especially with all the cool stuff with 256 and being able to open up more ability to control machines and have alternative use cases besides 100 percent on all the time trying to go as efficient as possible. Like Kevin's talking about a higher heat model, all sorts of cool things that can be done. And I'm super excited to see in the coming months what people do and what comes out of that.
Eco: It's awesome. And how about you, Kevin? Do you have any closing thoughts you want to share? I know Foundry just went through some structural changes in their mining operations. I don't know if you want to share anything about that or what you got going on next or any advice you got for the audience.
Kevin: Yeah, sure. So for those that didn't catch the news, we recently announced Fortitude Mining. That is the separation of our self-mining arm that was kind of all under the Foundry branch, now its own Independence subsidiary under DCG.
So we actually have been self-mining at a pretty large scale privately for quite some time and now that's its own business and it's exciting to see that kind of survive on its own. It's going to be mining not just Bitcoin, but they're alt coins of different things as well. I'll keep that on the wraps here.
But building off what Mike was saying, some closing thoughts on hydro and immersion mining, I know I talked a lot about economics and kind of lowering the cost of this and that. Don't just chase just the lowest price tag as well. I think what's fascinating about these new liquid cool technologies are they're now very, very large vendors as well as large deployments of these sites that are up and running.
I was over in Corsicana visiting Riot site and to see the kind of different iterations that they've kind of deployed of immersion mining. You can see all the improvements have happened over time.
So I think one of the coolest things about our industry is how collaborative everyone is and no one's going to gate-keep like if they had a good experience or bad experience with a vendor or how they deployed certain technology. Everyone's going to be super helpful with their own experience and feedback on how they run something.
If it's a brand new vendor in the space, probably not the best idea to cut like a 50, 100 megawatt contract with them before you sample them out or you get some testimonials.
So it's not to throw anyone in the bus. I'm not thinking of anyone in mind. It's more of make sure you kind of reach out, get testimonials, get others, people's experiences, leverage that because oftentimes when you are going through your very first hydro or immersion deployments, it's a little bit more technical and there's a lot more points of failure, a lot more leakages isn't that.
So you want to make sure that you kind of leverage as much experience and the collaborative network that's out there as you can.
Eco: Awesome. Let's get a round of applause for these guys and then we'll open it up for some questions. (audience applause)
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~787 Eh/s to ~798 Eh/s in February – peaking at 832 Eh/s, marking ~1.4% growth for the month.
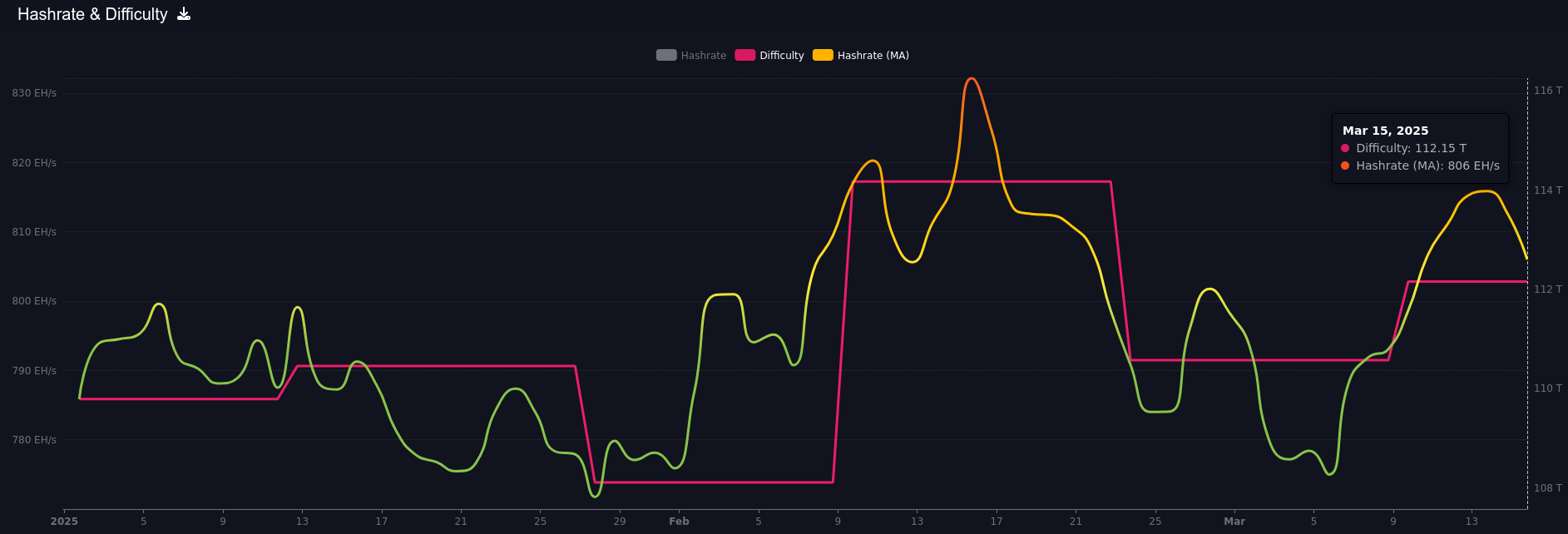 [IMG-005] 2025 hashrate/difficulty chart from mempool.space
[IMG-005] 2025 hashrate/difficulty chart from mempool.spaceDifficulty is currently 112.14T as of Epoch 440 and set to increase roughly 1.7 – 2.3% on or around March 23, 2025. But that target will change between now and then. The previous re-target increased difficulty by 1.4%. All together for 2025 thus far, difficulty has gone up ~2.15%.
New-gen miners are selling for roughly $17.65 per Th using the Bitmain Antminer S21+ 235 Th/s model from Kaboom Racks as an example. According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.49 per terahash, models between 19J/Th – 25J/Th are selling for $12.68 per terahash, and models >25J/Th are selling for $3.37 per terahash.
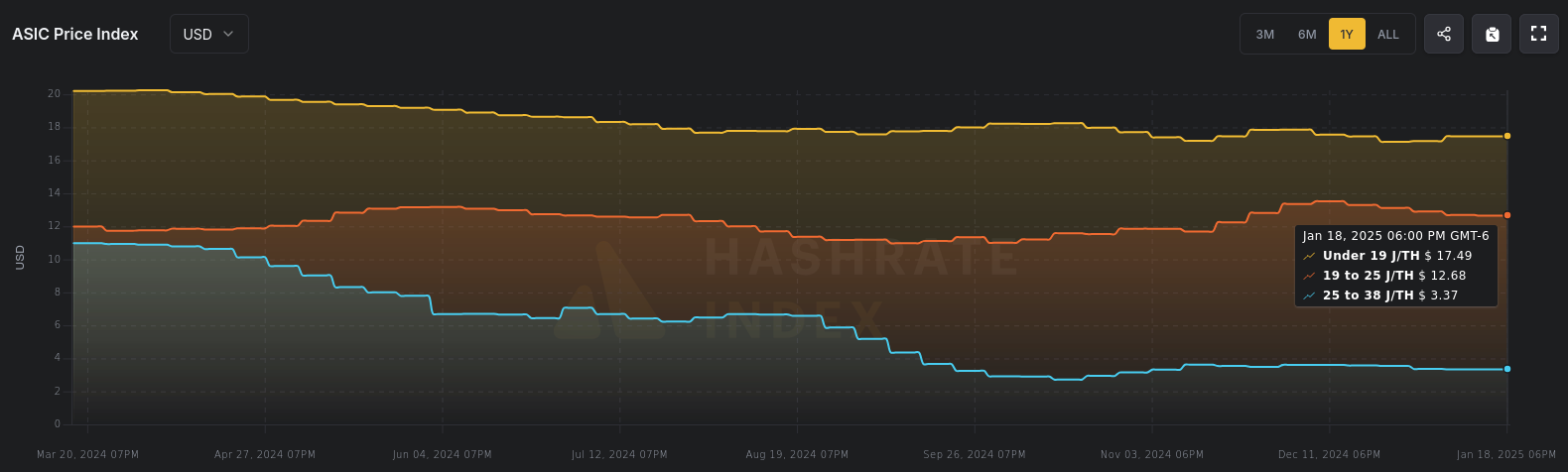 [IMG-006] Miner Prices from Luxor’s Hashrate Index
[IMG-006] Miner Prices from Luxor’s Hashrate IndexHashvalue is currently ~57,000 sats/Ph per day, up slightly from Frebruary when hashvalue was closer to 56,000 sats/Ph per day according to Braiins Insights. Hashprice is $47.00/Ph per day, down from $54.00/Ph per day in February.
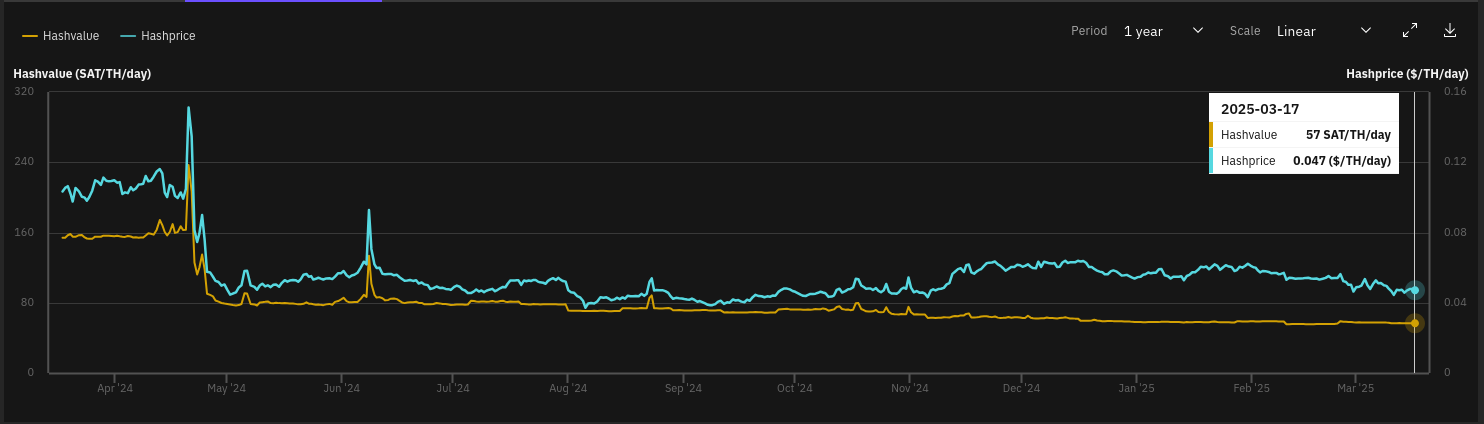 [IMG-007] Hashprice/Hashvalue from Braiins Insights
[IMG-007] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,109 days or in other words 161,757 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you were looking for answers about cooling your Bitcoin miners this summer then hopefully you found them here.
If you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.

The proprietary mining empire isn't going to dismantle itself; stay vigilant, frens.
-econoalchemist
-
 @ 16d11430:61640947
2025-03-20 23:07:01
@ 16d11430:61640947
2025-03-20 23:07:01A Tale of Two Dysfunctional Kingdoms
In the grand theater of human organization, we are blessed with two great economic orders: Fiat, the Land of Fragile Giants, and Crypto, the Padded Madhouse of Infinite Lunacy. Both promise utopia, both deliver dysfunction, and both operate under the iron law that those with the most power will always act in their own interests—rules be damned.
The Fiat Intellectual Landscape: A Game of Tiptoeing Giants
The fiat world is a meticulously curated bonsai garden of decorum and quiet panic. Giants walk among us—CEOs, central bankers, hedge fund wizards, and the occasional Nobel Prize-winning economist—but they must step lightly, lest they shake the delicate equilibrium. The entire system is built on confidence, a polite euphemism for narrative control.
Take any major institution, and you'll find the same pathology:
Corporations: The larger they are, the more fragile their balance sheets, requiring constant PR therapy and quarterly ritual sacrifices to appease the gods of Wall Street. CEO statements are more rehearsed than Shakespearean soliloquies, lest a slip in language shaves billions off the stock price.
Academia: Intellectual giants must wade through a swamp of bureaucratic grant-seeking, where discovery is secondary to institutional survival. Challenging economic orthodoxy is career suicide, so best to publish another paper on "inclusive finance" while hedge funds strip-mine the economy.
Government & Central Banks: A crisis is just another reason to print more money, kick the debt can down the road, and assure the public that everything is “transitory.” Behind closed doors, they know it’s a rigged game—but stability must be maintained at all costs, even if it means bribing the peasants with stimulus checks to keep the illusion alive.
The entire fiat ecosystem is one of quiet desperation, where the powerful pretend to be cautious stewards of civilization while looting with the finesse of seasoned art thieves. Stability is paramount, because if the masses ever realized the whole thing is a confidence scam, they might actually ask questions.
Crypto: The Padded Madhouse Where Giants Go to Break Things
Meanwhile, in the Crypto Madhouse, giants don’t tiptoe—they run, scream, and occasionally set the entire house on fire just to see what happens. Here, there is no caution, no equilibrium—just a perpetual state of mania, where even the most outlandish ideas get venture funding. If fiat is an over-engineered glass palace, crypto is a playground for unhinged capitalists and techno-anarchists armed with flamethrowers.
The dysfunction here is less about fragility and more about unregulated chaos:
Ponzi Chains Masquerading as Innovation: Every year, a new "Ethereum Killer" promises to decentralize everything, only to collapse into an infighting mess of VC dumps, network outages, and sudden governance takeovers. If in fiat, failures happen in slow motion, in crypto, they happen overnight, in a Discord announcement at 3 AM.
Decentralization Theatre: Most "community-governed" projects are run by an inner circle of early whales who have more control than the Federal Reserve, but pretend it's democratic because they let the plebs vote on logo designs. The difference? Fiat oligarchs hide their power; crypto oligarchs post memes about it.
The Cult of the Visionary Founder: While fiat leaders pretend to be humble, crypto founders take the stage like prophets descending from the blockchain, dropping whitepapers with the same fervor as religious scriptures. And when they inevitably fail, they simply launch a new token, because failure only exists if you stop grifting.
Crypto may lack the institutional fragility of fiat, but in its place, we get wild, unchecked power, where insiders can rug-pull billions without consequence. The only real difference? Instead of bailing out banks, crypto just moves on to the next hype cycle.
Same Vested Interests, Different Scams
In the end, both systems operate under the same fundamental law: those with the most power will always find a way to keep it.
In fiat, the illusion of stability is paramount, so the powerful must lie in slow motion.
In crypto, the illusion of innovation is paramount, so the powerful must rug in high-speed.
The giants of fiat must walk lightly so as not to disturb the herd; the giants of crypto can rampage freely, because the casino always reopens. Either way, the little guy always pays the bill.
-
 @ 2ed3596e:98b4cc78
2025-03-20 22:46:58
@ 2ed3596e:98b4cc78
2025-03-20 22:46:58Bitcoin: The tool of true freedom in an age of control
Let’s talk about control. Not just the kind you see in politics, but the control over what you can say, what you can spend, and ultimately, how you live. It’s creeping into every part of our lives, and if you’re paying attention, you’ve already seen it happen.
Remember the Canadian truckers’ protest? If you donated just $50 and you got bank accounts frozen and all financial access cut off—not because of criminal activity, but because the government at the time didn’t like what you stood for. Look at donations to Palestine — many financial institutions are outright blocking donations to causes supporting folks struggling to survive in Gaza. China? Censorship isn’t just about speech; it’s about access to money, too – completely cutting people off from being able to participate in the economy. Economic strangulation is real and a growing government control tactic.
See the pattern?
It doesn’t matter what your politics are. If you step too far outside the accepted lines, you’ll be cut off. Your money is no longer yours if someone else can decide when you can access it.
The playbook isn’t new — just look at 1933
If you think this level of control is new, think again. In 1933, Executive Order 6102 forced Americans to hand over their gold to the government—under threat of fines and jail time. Why? Because gold was real money, and the government wanted to control the monetary system to finance its growth in spending and services. Gold, at this time, was $35 an ounce. Today it is worth thousands per ounce. The dollar, meanwhile, has lost 99% of its value in that same period.
Then came 1971. Nixon took the U.S. off the gold standard completely, meaning the dollar was no longer backed by anything tangible. Since then, the government has printed money at will, inflating the currency and making everything more expensive over time.
And yet, we’re supposed to trust this system?
Fiat is just a fancy word for "because we said so"
Our money is no longer tied to gold or anything of value. Fiat money has value simply because governments say it does. But history proves that this system is built on a lie. The more they print, the less your money is worth. It’s not about “helping the economy” or “fighting inflation”—it’s about making sure you stay dependent on the system. And when people get too self-sufficient? That’s when they start pulling tricks like EO 6102.
Bitcoin fixes this.
Bitcoin is E.O. 6102-proof
Governments can seize gold. They can freeze your bank accounts. They can tell you what you can and can’t spend money on.
But they cannot control Bitcoin.
Bitcoin is money that exists outside of their system. It can’t be inflated away. It can’t be seized by decree. It allows people to transact freely, regardless of politics, geography, or financial status. Whether you’re protesting in Ottawa, donating to survivors in Palestine, or living under Chinese financial surveillance—Bitcoin is the escape hatch.
“I consume, therefore I am”
Freedom isn’t just about what you can say—it’s about what you can do. If your ability to transact is controlled, then your ability to live freely is controlled. Bitcoin is the tool that breaks those chains.
It’s not just an investment. It’s not just “digital gold.” It’s a lifeline. It’s the difference between having control over your future or waiting for the next decree to tell you what you can do with your own money.
Governments will always try to tighten their grip. History proves it. But Bitcoin gives you the power to break free. The question is: will you use it?
-
 @ 7d33ba57:1b82db35
2025-03-20 20:42:33
@ 7d33ba57:1b82db35
2025-03-20 20:42:33El Teide
Mount Teide (El Teide) is the highest mountain in Spain (3,715m) and the third-highest volcanic structure in the world. Located in Teide National Park (a UNESCO World Heritage Site), it offers breathtaking landscapes, hiking trails, and stunning panoramic views** over the Canary Islands.
🏔️ Best Things to Do at Mount Teide
1️⃣ Hike to the Summit
- The most rewarding way to reach the top! The hike starts from Montaña Blanca and takes about 5-6 hours.
- Permit required for the final ascent (apply in advance).
2️⃣ Take the Teide Cable Car
- A quick way to reach 3,555m, with spectacular views.
- From the upper station, you can hike to La Fortaleza Viewpoint or Pico Viejo Viewpoint for stunning island views.
3️⃣ Stargazing at Teide Observatory
- One of the best stargazing spots in the world due to its clear skies and high altitude.
- Join an astronomy tour for an unforgettable night experience.
4️⃣ Explore the Teide National Park
- Walk through lava fields, craters, and rock formations like Roques de García.
- Visit the Visitor Center to learn about the park’s geology and history.
🚗 How to Get to Teide
🚗 By Car: ~1.5 hours from Santa Cruz or Costa Adeje
🚌 By Bus: Titsa buses 342 (from Costa Adeje) & 348 (from Puerto de la Cruz)💡 Tips for Visiting Teide
✅ Book summit permits early – Limited spots available! 🎟️
✅ Dress warmly – Temperatures drop at high altitude, even in summer 🧥
✅ Best time to visit? Sunrise, sunset, or night for amazing views 🌅🌌
✅ Take it slow – The high altitude can affect breathing ⛰️ -
 @ f240be2b:00c761ba
2025-03-20 17:53:08
@ f240be2b:00c761ba
2025-03-20 17:53:08Warum jetzt ein guter Zeitpunkt sein könnte, sich mit Bitcoin zu beschäftigen
Kennt ihr das? Wenn der Bitcoin-Preis neue Höchststände erreicht, möchte plötzlich jeder einsteigen. Doch sobald die Kurse fallen, überwiegt die Angst. Dabei zeigt die Geschichte: Gerade diese Phasen der Unsicherheit können interessante Zeitpunkte sein, um sich mit dem Thema zu beschäftigen.
Historische Zyklen Bitcoin durchläuft regelmäßige Marktzyklen Nach jedem Tief folgte bisher ein neues Hoch Emotionen spielen eine große Rolle im Markt Psychologie des Marktes Wenn alle euphorisch sind → meist teuer Wenn Unsicherheit herrscht → oft interessante Gelegenheiten Die Masse liegt häufig zum falschen Zeitpunkt richtigRationale Herangehensweise
Statt emotional zu handeln, solltet ihr:
Einen langfristigen Anlagehorizont wählen Regelmäßig kleine Beträge investieren (Cost-Average-Effekt)Hier ein paar Charts die euch helfen sollen und euch mutig werden lassen:
https://www.tradingview.com/chart/BTCUSD/HuGpzZfQ-BITCOIN-Cycle-pattern-completed-Year-end-Target-locked-at-150k/
https://www.tradingview.com/chart/BTCUSD/YVyy9QuU-BITCOIN-Money-Supply-Dollar-and-Bonds-pushing-for-MEGA-RALLY/
https://www.tradingview.com/chart/BTCUSD/pZ0qs5x3-BTCUSD-TSI-shows-that-this-is-the-LAST-BEST-BUY/
https://www.tradingview.com/chart/BTCUSD/x3e7GuLQ-BITCOIN-Is-this-a-Falling-Wedge-bottom-formation/
und jetzt All-In :-)
-
 @ 4fe14ef2:f51992ec
2025-03-20 17:39:26
@ 4fe14ef2:f51992ec
2025-03-20 17:39:26Hey Bitcoiners,
Leave a comment below to share your hustles and wins. Let us know what you've sold this week. Have you sold it for #sats or #zaps? It doesn't matter how big or small your item is, solid or digital, #product or #service.
Just share below what you’ve listed, #swap, and #sold. Let everyone rave on your latest #deals!
New to ~AGORA? Dive into the #marketplace and turn your dusty gears into shiny #BTC!
originally posted at https://stacker.news/items/919107
-
 @ 000002de:c05780a7
2025-03-20 17:07:00
@ 000002de:c05780a7
2025-03-20 17:07:00Its easy to get caught up in media stories and not stop and ask basic questions. One I've had from the start is how widespread are these attacks on the private property have occurred.
If the goal is to hurt Tesla and therefore Musk, then the media stories are the real goal. Not the actual destruction of property. We know from history that many stories get blown out of proportion. I have no doubt that these events are actually happen but I wonder if the number of events has been counted.
originally posted at https://stacker.news/items/919063
-
 @ e968e50b:db2a803a
2025-03-20 15:59:49
@ e968e50b:db2a803a
2025-03-20 15:59:49I just wrote up a whole essay about this great movie scene, my extended thoughts on this post, and bitcoin hipsterism at large. However, it was rambly and I'm not sure if anyone would have gotten anything out of it. That said, I'd love to share this clip with y'all as I think it may prove an interesting thought/discussion piece for those contemplating bitcoin hipsterism, either as an increasingly disillusioned practitioner or as an annoyed external observer.
https://www.youtube.com/watch?v=vUgs2O7Okqc&t=12s
originally posted at https://stacker.news/items/918979
-
 @ 16f1a010:31b1074b
2025-03-20 15:29:42
@ 16f1a010:31b1074b
2025-03-20 15:29:42What is NSSM?
NSSM (Non-Sucking Service Manager) is a free tool that allows you to install and manage any application as a Windows service. This is particularly useful for applications that don't natively support running as a service, ensuring they start automatically when your system boots and continue running in the background.
Downloading NSSM
- Visit the official NSSM website: https://nssm.cc/
- Download the latest stable release.
- Extract the downloaded ZIP file to a directory of your choice (e.g.,
C:\nssm).
Adding NSSM to Your PATH (Recommended)
Adding NSSM to your system's PATH environment variable allows you to run
nssmcommands from any command prompt window.- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."

- In the "System Properties" window, click the "Environment Variables..." button.
- In the "System variables" section, find the "Path" variable and click "Edit."
- Click "New" and add the path to the directory where you extracted NSSM (e.g.,
C:\nssm). - Click "OK" on all open windows to save the changes.
- Open a new command prompt window and type
nssm --version. If NSSM is correctly added to your PATH, you should see the version information.
Using NSSM: Installing a Service
- Open a command prompt as administrator.
- Type
nssm install <service_name>and press Enter. Replace<service_name>with the name you want to give to your service. - A GUI will appear, allowing you to configure the service.
- In the "Path" field, enter the full path to the application's executable.
- In the "Startup directory" field, enter the directory containing the executable.
- Configure any other options as needed, such as "Arguments," "I/O," or "Details."
- Click "Install service."
Example:
bash nssm install MyGrainRelayConclusion
Congratulations, you now have NSSM installed and know the basics of using it to manage windows services. Check my profile for more technical guides on various topics, and stay tuned for more guides.
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ 378562cd:a6fc6773
2025-03-20 14:26:48
@ 378562cd:a6fc6773
2025-03-20 14:26:48When SpongeBob SquarePants first graced television screens in 1999, it quickly became a cultural phenomenon. Its quirky humor, unique animation style, and absurd yet endearing characters captured audiences of all ages. However, beyond its whimsical surface, SpongeBob SquarePants holds surprising ties to real-world marine biology, human behaviors, and even corporate America. Let's take a deep dive into the striking similarities between the show’s universe and real life.
- Bikini Bottom and the Nuclear Connection
One of the most intriguing theories about SpongeBob SquarePants is its potential connection to real-world geography. Bikini Bottom, the fictional underwater city where SpongeBob and his friends reside, is widely believed to be named after Bikini Atoll, a site in the Pacific Ocean where the U.S. conducted nuclear tests in the 1940s and 1950s. Some fans speculate that the bizarre personalities of the show's characters are a result of radioactive mutations—a wild yet eerily plausible idea given the history of the atoll.
- SpongeBob: More Than Just a Sponge
SpongeBob is, of course, a sea sponge, but his rectangular, kitchen-sponge shape is a deviation from most natural sea sponges, which are irregularly shaped. However, real-life sea sponges are fascinating creatures that can regenerate after being broken apart—just like how SpongeBob bounces back from every misadventure with relentless optimism.
Additionally, SpongeBob’s enthusiasm and boundless energy mimic the real-life behaviors of certain marine organisms that continuously filter water, making them vital to their ecosystems. His ceaseless work ethic at the Krusty Krab also mirrors the tireless efforts of smaller marine life that keep oceanic ecosystems functioning.
- Squidward: An Octopus in Disguise
Despite his name, Squidward Tentacles is actually an octopus. Series creator Stephen Hillenburg, a marine biologist before becoming an animator, intentionally designed Squidward with six tentacles instead of the usual eight to make animation easier. His grumpy and refined personality also reflects the intelligence of real-world octopuses, who are known for their problem-solving skills and, at times, their moody behavior.
- The Krusty Krab and Corporate Culture
The Krusty Krab, the fast-food restaurant where SpongeBob works, is a satirical take on real-life corporate culture, particularly in the fast-food industry. Mr. Krabs, the money-hungry owner, represents stereotypical profit-driven business owners who prioritize revenue over employee well-being. Meanwhile, SpongeBob’s unwavering loyalty to his job highlights the enthusiasm of idealistic workers, and Squidward embodies the disillusioned employees who begrudgingly clock in every day. This dynamic is strikingly similar to real-world labor environments, making the show relatable even beyond its nautical setting.
- Plankton and the Struggles of Small Businesses
Sheldon J. Plankton, the tiny but ambitious owner of the failing Chum Bucket, serves as a metaphor for small business owners who struggle to compete with corporate giants. His constant yet futile attempts to steal the Krabby Patty secret formula echo the real-world battle between small independent businesses and industry monopolies. Despite his villainous traits, Plankton’s perseverance and innovative schemes make him an oddly sympathetic character, much like real-life entrepreneurs striving to find success against all odds.
- Real-Life Marine Life Mirrored in Characters
Each character in SpongeBob SquarePants is based on real marine creatures with behaviors that closely resemble their animated counterparts:
Patrick Star: A pink starfish who is slow and lazy, much like real-life starfish that lack a brain and move sluggishly.
Sandy Cheeks: A land-dwelling squirrel who thrives in an underwater suit, symbolizing the scientific research done by deep-sea divers and marine biologists in the ocean.
Mr. Krabs: A crab with a tight grip on his money, reflecting the territorial and often aggressive nature of real-world crabs.
Larry the Lobster: A fitness-obsessed lobster, much like real lobsters that grow larger and stronger as they molt.
Conclusion: A Show Rooted in Reality
While SpongeBob SquarePants is undeniably a wacky and exaggerated series, its deep connection to real-world marine biology, workplace culture, and corporate dynamics gives it an extra layer of depth. Whether intentionally or unintentionally, the show serves as an entertaining yet insightful reflection of life above and below the ocean’s surface. So next time you watch an episode, remember—you’re not just enjoying a cartoon; you’re diving into a cleverly crafted world filled with real-life parallels, which is probably a direct correlation to its wild success in all these years.
-
 @ f1989a96:bcaaf2c1
2025-03-20 14:21:35
@ f1989a96:bcaaf2c1
2025-03-20 14:21:35Good morning, readers!
In Thailand, the government announced a third digital cash handout to “stimulate the economy and drive technological adoption.” This disbursement will allocate 27 billion baht ($800 million) to 2.7 million citizens aged 16-20. Like in previous phases, it will be distributed via a state-controlled “digital wallet” application, which essentially functions as a central bank digital currency (CBDC). This system gives the regime an inside view of Thais’ financial activity and creates a centralized database to monitor, censor, and control.
Meanwhile, in Russia, the central bank has proposed limiting Bitcoin access to only the wealthiest individuals. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could buy and sell digital assets — arbitrarily barring everyday Russians (including obviously most journalists and activists) from accessing Bitcoin and the financial independence it grants.
In open-source software news, a new tool called Banxaas is making Bitcoin more accessible in West Africa by integrating with local payment providers to facilitate buying and selling Bitcoin using the CFA currency (XOF). This on-and-off ramp could expand financial freedom for human rights activists, dissidents, and everyday citizens.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, in which HRF’s Zac Guignard sits down with author Jason Maier to discuss how Bitcoin can drive human rights around the world. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Thailand | Announces Third Digital Cash Handout to Boost Economy
The government of Thailand announced a third digital cash handout, allocating 27 billion baht ($800 million) to 2.7 million citizens aged 16-20 to “stimulate the economy and drive technological adoption.” Like in previous phases, the regime will distribute the funds through a state-run “digital wallet” application, which would effectively function as a central bank digital currency (CBDC). Past handouts of the CBDC came with strict restrictions: spending was limited to approved vendors within designated areas, purchases were restricted to certain goods, and funds expired after six months. Meanwhile, Prime Minister Paetongtarn Shinawatra called this third handout the first full deployment of the digital wallet system and urged the public to download the official app. This would directly link citizens' financial activity and data to the regime, threaten privacy, and deepen repression in a country with a long history of silencing dissent.
Russia | Central Bank Proposes Restricting Bitcoin Access to Wealthy Only
Russia’s central bank has proposed restricting Bitcoin and cryptocurrency access to only the country’s wealthiest individuals, barring everyday Russians from buying and selling digital assets unless they meet specific income or asset thresholds. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could engage with digital assets — effectively putting Bitcoin officially out of reach of most activists and journalists. The central bank claims the measure protects citizens from “volatility and lack of state backing.” But in reality, it likely signals the regime’s fear of Bitcoin’s ability to provide individual financial autonomy. By blocking most Russians from opting out of the state-controlled financial system, the regime is doubling down on financial repression.
India | Advances Digital Rupee CBDC
India’s government is pushing forward with its CBDC, the Digital Rupee, hailing it as a modern payment solution. But as journalist and author Roger Huang puts it, “it looks like a solution searching for a problem to solve.” Beyond the branding, the Digital Rupee enables state control over financial activity. Its programmability allows the government to dictate how, when, and where people spend — restricting transactions to specific merchants, locations, or goods and even imposing expiration dates on money. India’s crackdown on dissent is well-documented, from freezing opposition bank accounts to attempting a Bitcoin ban. Now, the Reserve Bank of India is embedding the CBDC into its digital payment system (UPI), quietly pushing millions into a tightly controlled and surveilled financial system.
Zimbabwe | Financial Regulators Mandate Earnings in ZiG
Zimbabwe’s market regulator is mandating all companies report their earnings in the new ZiG currency despite it losing 96% of its value since its launch last year. This move tightens state control over an already fragile economy, pushing businesses and citizens deeper into an unstable system that has repeatedly wiped out savings through inflation. The ZiG is Zimbabwe’s sixth currency in 15 years, introduced with gold backing to restore confidence in the regime’s ability to manage a currency. Instead, it’s rapidly devaluing, while the US dollar remains the preferred currency for trade and savings — when accessible. For ordinary Zimbabweans, the mandatory use of ZiG for taxes and government services is already a challenge due to its scarcity.
Egypt | Dictator-imposed Reforms Causing Economic Chaos
In the wake of an $8 billion deal with the International Monetary Fund (IMF) last spring, the Egyptian dictatorship has carried out “reforms” that are fueling inflation and making necessities increasingly unaffordable. To meet IMF conditions, Egyptian officials devalued the pound, slashed subsidies, and hiked the cost of fuel and public transportation — driving inflation beyond 20% for months on end. For millions of Egyptians, basic goods are now unaffordable. And the government’s promised minimum wage increase for public workers remains unfulfilled, leaving the public to absorb the price shocks. These undemocratic reforms — never voted on and executed with no way for the public to push back — aimed at securing further financing have only eroded the financial freedom of 114 million Egyptians and pushed the country into greater debt.
China | Facebook Enabling Authoritarian Censorship
A former Meta executive, Sarah Wynn-Williams, has accused Facebook of working “hand in glove” with the Chinese Communist Party (CCP) to censor and surveil content in China. According to Wynn-Williams, Facebook explored building censorship tools that would suppress viral posts until Chinese authorities approved. They even considered sharing user data in exchange for market access to China’s massive user base. Meta denied these claims, saying they fired Wynn-Williams in 2017 for poor performance. Regardless, the revelations highlight the dangers of for-profit, centralized platforms that authoritarian regimes can co-opt. Protocols like nostr (where no single entity moderates content) are more important than ever. Activists and dissidents seeking free communications can get started with nostr here.
BITCOIN AND FREEDOM TECH NEWS
Banxaas | Spend Sats in West Africa
Hundreds of millions of citizens in West Africa still use the CFA franc in an arrangement upheld by more than a dozen authoritarian leaders. Banxaas offers an alternative by bridging Bitcoin with West Africa’s mobile money networks. This allows individuals to buy and sell Bitcoin through local payment providers using the local CFA currency (XOF) and their own Lightning wallet. By integrating with local payment providers, Banxaas serves as a crucial on-and-off-ramp to Bitcoin, bringing the benefits of financial freedom to individuals, nonprofits, and human rights defenders across the region. Watch a demonstration of how Banxaas works here.
Mi Primer Bitcoin | Bitcoin Workbook Translated to Mandarin
Mi Primer Bitcoin, an open-source Bitcoin educational initiative focused on high-school-age students, released a Mandarin translation of its 2025 Bitcoin Diploma. This open-source resource provides mainland Chinese citizens, activists, and dissidents with accessible Bitcoin education at a time when financial freedom is increasingly under threat. With China tightening restrictions on personal wealth and expanding state surveillance of financial activity through the digital yuan CBDC, the diploma offers a useful new resource to learn the alternatives to state-controlled financial systems.
Blitz Wallet | Improves Ecash Functionality for Greater Financial Autonomy
Blitz Wallet, an open-source and self-custodial Bitcoin Lightning, Liquid, and ecash wallet, released an update that improves ecash functionality. Ecash, a Bitcoin-backed digital money system, allows instant and private transactions but requires custodial “mints” to manage tokens. The new update links users’ ecash to their wallet’s seed phrase (the 12-word backup used for Bitcoin recovery), allowing them to restore funds even if their device is lost or stolen. Users can also now transfer ecash between different wallets, increasing flexibility and control over their funds. Improved ecash UX is much-desired for political dissidents who can’t afford for authoritarian regimes to have full oversight over all of their economic activities.
Fedimint | Adds On-chain Support for Everyone
Fedimint, an open-source Bitcoin custody model that lets communities securely manage Bitcoin funds together, released v0.6.0, adding support for on-chain Bitcoin deposits (transactions directly on Bitcoin’s base layer). By offering private and trust-minimized transactions alongside on-chain support, Fedimint makes it easier, especially for nonprofit communities, to self-custody Bitcoin. It provides greater privacy and autonomy versus using fully centralized platforms that are easily subject to the political and regulatory pressure of authoritarian regimes.
Africa Bitcoin Conference | Announces 2025 Conference
The Africa Bitcoin Conference (ABC) announced its fourth edition, set to take place from Dec. 3-5, 2025, in Port Louis, Mauritius. Hosted at the Caudan Art Center, the event will bring together activists, Bitcoin advocates, and freedom tech developers to explore Bitcoin as a pathway to financial freedom. Now the largest Bitcoin gathering in Africa, ABC has established itself as a key platform for discussions on financial inclusion, inflation resistance, and censorship-resistant money — putting tools for financial sovereignty into the hands of those who need them most. HRF is proud to support ABC and, in particular, is proud to help delegates from dozens of authoritarian regimes attend each year. You can learn more about the conference and buy tickets here.
RECOMMENDED CONTENT
HRF x Pubkey — How Bitcoin Brings About Social Change with Jason Maier
In the latest installment of the HRF x Pubkey Freedom Tech Series, HRF Content and Research Associate Zac Guignard sits down with Jason Maier, author of “A Progressive’s Case for Bitcoin,” to share how Bitcoin can spark a meaningful shift in personal liberty worldwide. Jason explains the core monetary properties that make Bitcoin permissionless, censorship-resistant, and a powerful tool for financial freedom. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes. They talk about how Bitcoin shouldn’t be a political issue and can be useful to anyone, no matter their beliefs. Watch the full conversation here.
Mélancolies de l’Opprimé by Farida Bemba Nabourema
Farida Bemba Nabourema, a renowned Togolese human rights activist, former HRF freedom fellow, and Bitcoin pioneer, announced that her new book “Mélancolies de l’Opprimé” will be released on April 15, 2025. A decade after her first book, “La Pression de l’Oppression,” this deeply personal and reflective work offers hard-earned wisdom for young activists stepping into the struggle against dictatorships and injustice. Nabourema candidly shares the emotional, physical, and psychological toll of resistance and activism while also highlighting the sense of purpose in the pursuit of freedom and human rights. Learn more about the book here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ a396e36e:ec991f1c
2025-03-20 14:11:02
@ a396e36e:ec991f1c
2025-03-20 14:11:02Introduction
The term Clown World is a meme that reflects the perception that the current system operates in an absurd, corrupt, or irrational manner. In this context, many Bitcoin enthusiasts see it as a tool to escape from Clown World. Bitcoin emerged in 2009, following the 2008 global financial crisis, as an alternative to a traditional monetary system that many consider unjust, inefficient, and prone to manipulation. This article explores how Bitcoin challenges existing economic structures, embodies philosophical principles such as decentralization and financial sovereignty, and serves as a political tool against failing monetary policies. We will also examine the historical evolution of Bitcoin’s narrative in relation to escaping Clown World.
Economic Perspective: Challenging Traditional Monetary Structures
From an economic standpoint, Bitcoin directly challenges the traditional monetary system, which many Bitcoin advocates see as part of Clown World. Fiat currencies, issued by central banks, can be devalued through expansionary policies, leading to inflation, bank bailouts, and resource misallocation that deteriorate economies and social structures. Bitcoin was explicitly designed as a response to these issues: its genesis block, mined on January 3, 2009, contained the message "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks," referencing government bailouts of failing financial institutions. This message signaled Bitcoin’s intent to offer a solution to what was perceived as a broken financial system and irresponsible economic policies.
Unlike fiat money, which can be expanded at the discretion of central authorities, Bitcoin has a predictable and non-manipulable monetary policy. Its issuance follows an algorithmic schedule: the total supply is capped at 21 million coins, ensuring scarcity and practically eliminating long-term inflation. Every four years, a halving event reduces the number of new bitcoins entering circulation, contrasting sharply with central banks’ inflationary targets of around 2% per year. In Bitcoin, no one can arbitrarily “print” more money or devalue existing units, as “there is no central authority” making such decisions. As analyst Anthony Pompliano put it: “Bitcoin is censorship-resistant money. No one can stop you from sending it. No one can confiscate it without your permission. No one can debase the currency.” In other words, Bitcoin functions as digital gold, immune to political dilution, challenging the very foundation of inflationary fiat money.
This economic model—often associated with the idea of “sound money”—represents a separation between money and the state. Many Bitcoin proponents argue that a broken monetary system is at the root of the dysfunctions of Clown World. As Bitcoin advocates Knut Svanholm and Luke de Wolf put it: “When money stops working, everything becomes political and turns into a farce.” Bitcoin, by replacing trust in financial authorities with trust in cryptographic code, aims to correct these distortions. It allows individuals and communities to opt out of the traditional system, securing themselves against inflation and reckless monetary policies.
Philosophical Perspective: Decentralization, Financial Sovereignty, and Resistance to Manipulation
From a philosophical perspective, Bitcoin embodies principles of decentralization, individual sovereignty, and resistance to manipulation, offering an alternative to perceived systemic corruption and control. Unlike traditional money, Bitcoin is a decentralized digital currency that “does not rely on any central authority but operates through a mathematical protocol and a distributed network of nodes.” This means that no government, bank, or corporation can unilaterally control the Bitcoin network or counterfeit its supply. The blockchain architecture and distributed consensus make Bitcoin a kind of “trust machine”, where the rules are pre-set by transparent algorithms. For the first time in history, digital scarcity combines with total decentralization, creating a monetary system where trust is placed in code rather than authorities.
This foundation enables personal financial sovereignty. Bitcoin users can fully own and control their funds through private keys, redefining monetary property rights by eliminating the need for custodians. In practice, this means that “no one can confiscate it without your permission” as long as the user protects their keys (hence the famous phrase “not your keys, not your coins”). Bitcoin’s sovereignty contrasts with traditional bank accounts, which are vulnerable to freezes, censorship, or devaluation. The philosophy behind Bitcoin promotes independence from state and corporate financial control, much like the historical separation of church and state. As a Bitcoin advocate noted, “By decentralizing financial power and promoting a separation between money and the state,” Bitcoin has the potential to reshape economic power dynamics. Essentially, anyone can become their own bank, transacting globally without requiring permission.
Another key aspect of Bitcoin’s philosophy is censorship resistance and protection from manipulation. In Clown World, institutions can block transactions, exclude individuals from the financial system, or manipulate currency for political purposes. Bitcoin was designed to counteract this. Anyone can transfer Bitcoin to another person directly, without intermediaries who can block transactions. The blockchain's immutability ensures that no one can retroactively alter payment records or falsify balances, reinforcing its freedom-preserving nature.
Recent events highlight this utility: In 2022, when the Canadian government froze bank accounts of protesters and pressured crowdfunding platforms, many pointed out that Bitcoin could bypass such authoritarian measures. As one commentator put it, “Every attempt at financial censorship is free marketing for Bitcoin,” as it underscores its value as unseizable and incorruptible money. This ideology aligns with libertarian and anarcho-capitalist ideals, advocating that individuals—not the state—should have ultimate control over their money and transactions.
Political Perspective: Bitcoin as a Tool of Resistance Against Authoritarianism and Monetary Failures
From a political standpoint, Bitcoin has been used as a form of resistance against authoritarian regimes, state financial controls, and failing monetary policies. Due to its borderless and stateless nature, Bitcoin enables escaping national economic barriers and prevents governments from unilaterally controlling wealth. In countries suffering from hyperinflation or strict currency controls, citizens have turned to Bitcoin to protect their savings.
Venezuela is a key example: Bitcoin is widely used there as a store of value against the endless devaluation of the national currency. Similarly, in Argentina, Bitcoin adoption has surged as people seek to preserve their wealth amidst chronic inflation and restrictions on foreign currency exchange. In these contexts, Bitcoin serves as an escape valve from disastrous economic policies, offering a refuge where the government cannot destroy the value of money through inflation.
Conclusion
Bitcoin is more than just an asset; it is a technological, economic, and philosophical revolution offering an alternative to what many perceive as the dysfunctions of Clown World. By enabling economic sovereignty, censorship resistance, and an escape from inflationary policies, Bitcoin challenges the status quo, providing a viable path toward financial freedom and systemic change.
-
 @ 58537364:705b4b85
2025-03-20 14:03:27
@ 58537364:705b4b85
2025-03-20 14:03:27“สุขเวทนา” ที่แท้ก็คือ “มายา”
เป็นเหมือนลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะน้ำถูกลมพัด
เดี๋ยวมันก็แตกกระจายไป
หากต้องการจะมีชีวิตอย่างเกษมแล้ว
ก็ต้องอาศัยความรู้เรื่อง อนิจจัง ทุกขัง อนัตตา ให้สมบูรณ์
มันจะต่อต้านกันได้กับอารมณ์ คือ รูป เสียง กลิ่น รส สัมผัส ที่มากระทบ
ไม่ให้ไปหลงรัก หรือหลงเกลียดเรื่องวุ่นวายมีอยู่ ๒ อย่างเท่านั้น
- ไปหลงรัก อย่างหนึ่ง
- ไปหลงเกลียด อย่างหนึ่ง
ซึ่งเป็นเหตุให้หัวเราะและต้องร้องไห้
ถ้าใครมองเห็นว่า หัวเราะก็กระหืดกระหอบ มันเหนื่อยเหมือนกัน
ร้องไห้ก็กระหืดกระหอบ เหมือนกัน
สู้อยู่เฉย ๆ ดีกว่า อย่าต้องหัวเราะ อย่าต้องร้องไห้
นี่แหละ! มันเป็นความเกษมเราอย่าได้ตกไปเป็นทาสของอารมณ์
จนไปหัวเราะหรือร้องไห้ตามที่อารมณ์มายั่ว
เราเป็นอิสระแก่ตัว หยุดอยู่ หรือเกษมอยู่อย่างนี้ดีกว่า
ใช้ อนิจจัง ทุกขัง อนัตตา เป็นเครื่องมือกำกับชีวิต
- รูป เสียง กลิ่น รส สัมผัส เป็น มายา เป็น illusion
- "ตัวกู-ของกู" ก็เป็น illusion
- เพราะ "ตัวกู-ของกู" มันเกิดมาจากอารมณ์
- "ตัวกู-ของกู" เป็นมายา อารมณ์ทั้งหลายก็เป็นมายา
เห็นได้ด้วยหลัก อนิจจัง ทุกขัง อนัตตา
...ความทุกข์ก็ไม่เกิด
เราจะตัดลัดมองไปดูสิ่งที่เป็น “สุขเวทนา”
สุขเวทนา คือ ความสุขสนุกสนาน เอร็ดอร่อย
ที่เป็นสุขนั้นเรียกว่า “สุขเวทนา”แต่สุขเวทนา เป็นมายา
เพราะมันเป็นเหมือนลูกคลื่นที่เกิดขึ้นเป็นคราว ๆ
ไม่ใช่ตัวจริงอะไรที่พูดดังนี้ก็เพราะว่า
ในบรรดาสิ่งทั้งปวงในโลกทั้งหมดทุกโลก
ไม่ว่าโลกไหน มันมีค่าอยู่ก็ตรงที่ให้เกิดสุขเวทนาลองคิดดูให้ดีว่า...
- ท่านศึกษาเล่าเรียนทำไม?
- ท่านประกอบอาชีพ หน้าที่การงานทำไม?
- ท่านสะสมทรัพย์สมบัติ เกียรติยศ ชื่อเสียง พวกพ้องบริวารทำไม?มันก็เพื่อสุขเวทนาอย่างเดียว
เพราะฉะนั้น แปลว่า อะไร ๆ มันก็มารวมจุดอยู่ที่สุขเวทนาหมดฉะนั้น ถ้าเรามีความรู้ในเรื่องนี้
จัดการกับเรื่องนี้ให้ถูกต้องเพียงเรื่องเดียวเท่านั้น
ทุกเรื่องมันถูกหมดเพราะฉะนั้น จึงต้องดูสุขเวทนาให้ถูกต้องตามที่เป็นจริงว่า
มันก็เป็น “มายา” ชนิดหนึ่งเราจะต้องจัดการให้สมกันกับที่มันเป็นมายา
ไม่ใช่ว่า จะต้องไปตั้งข้อรังเกียจ เกลียดชังมัน
อย่างนั้นมันยิ่ง บ้าบอที่สุดถ้าเข้าไปหลงรัก หลงเป็นทาสมัน
ก็เป็นเรื่อง บ้าบอที่สุดแต่ว่าไปจัดการกับมันอย่างไรให้ถูกต้อง
นั้นแหละเป็นธรรมะ
เป็น ลูกศิษย์ของพระพุทธเจ้า
ที่จะเอาชนะความทุกข์ได้ และไม่ต้องเป็น โรคทางวิญญาณ
สุขเวทนา ที่แท้ก็คือ มายา
มันก็ต้องทำโดยวิธีที่พิจารณาให้เห็นว่า
“สุขเวทนา” นี้ ที่แท้ก็คือ “มายา”เป็นเหมือน ลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะ น้ำถูกลมพัดหมายความว่า
เมื่อ รูป เสียง กลิ่น รส ฯ เข้ามา
แล้ว ความโง่ คือ อวิชชา โมหะ ออกรับ
กระทบกันแล้วเป็นคลื่นกล่าวคือ สุขเวทนาเกิดขึ้นมา
แต่ เดี๋ยวมันก็แตกกระจายไป
ถ้ามองเห็นอย่างนี้แล้ว
เราก็ไม่เป็นทาสของสุขเวทนา
เราสามารถ ควบคุม จะจัด จะทำกับมันได้
ในวิธีที่ ไม่เป็นทุกข์- ตัวเองก็ไม่เป็นทุกข์
- ครอบครัวก็ไม่เป็นทุกข์
- เพื่อนบ้านก็ไม่เป็นทุกข์
- คนทั้งโลกก็ไม่พลอยเป็นทุกข์
เพราะมีเราเป็นมูลเหตุ
ถ้าทุกคนเป็นอย่างนี้
โลกนี้ก็มีสันติภาพถาวร
เป็นความสุขที่แท้จริงและถาวรนี่คือ อานิสงส์ของการหายโรคโดยวิธีต่าง ๆ กัน
ไม่เป็นโรค “ตัวกู” ไม่เป็นโรค “ของกู”
พุทธทาสภิกขุ
ที่มา : คำบรรยายชุด “แก่นพุทธศาสน์”
ปีพุทธศักราช ๒๕๐๔
ครั้งที่ ๑
หัวข้อเรื่อง “ใจความทั้งหมดของพระพุทธศาสนา”
ณ ศิริราชพยาบาล มหาวิทยาลัยมหิดล
เมื่อวันที่ ๑๗ ธันวาคม ๒๕๐๔ -
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ a60e79e0:1e0e6813
2025-03-20 12:58:13
@ a60e79e0:1e0e6813
2025-03-20 12:58:13*This is a long form Nostr native version of a post that lives on my Nostr educational website Hello Nostr *
At first glance Nostr might appear quite similar to some of the apps you use every day, such as Twitter, Mastodon, or Facebook, but that couldn't be further from the truth. This post aims to dispel the myth that "Nostr is just a Twitter replacement" and give you a better understanding about the 'what', the 'how' and most importantly, the 'why' of Nostr.
What Is Nostr?
Nostr is a decentralized, open-source protocol designed for censorship-resistant networking and communication on the web. It stands for "Notes and Other Stuff Transmitted by Relays," and it works by allowing users to publish messages (notes) and content in the form of 'other stuff', to a network of servers (relays) that store and distribute the content.
Unlike traditional platforms like Twitter, Ebay or Facebook, Nostr doesn't rely on a central authority; instead, users control their own identities via cryptographic key pairs.
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
Fiatjaf - Nostr Creator
Nostr is not a website or an app you download from a single source — it’s an open protocol, like email or the internet. Think of it as a set of rules that anyone can use to build tools for sharing messages, posts, or other data without needing a centralized middleman like a big tech company.
Nostr was created by a developer named Fiatjaf in 2020, and has since been steadily gaining traction among people who care about privacy, freedom, and censorship resistance.

Why Nostr?
Imagine the scenario, you've been using an online platform for 5 or even 10 years. You've built up thousands of contacts, perhaps built yourself a sizeable reputation, or even rely on the income from the platform to feed your family. Then one day you make a controversial post, sell a certain item or upload a video on a spicy subject to the platform where the owner disagrees with. With the click of a button, your account is removed. All trace of you, your social graph, or even your future income, disappears in an instant.
Read aloud like that is sounds crazy that we'd even entertain using such a platform, right!? Sadly that is the reality in 2025. This is exactly what happens every single day on X, Facebook, Ebay, Paypal, Linkedin, etc.
Looking at the problem through a more social media focused lens, many of us have become slaves to the likes of Instagram, Twitter and TikTok. We use these 'free' apps under the guise of being social with others online. The reality is that we see what those apps want us to see. We've become slaves to the manipulation of complex and opaque algrorithms designed to keep us hooked and try to sell us things.

Unlike traditional platforms, which are often governed by centralized entities wielding significant control over user data, content moderation, and algorithmic influence, Nostr flips the script by prioritizing user sovereignty and resilience. Built on an open-source framework, Nostr allows individuals to control their own data and interact through a network of relays, making it much more difficult for any single authority - be it a corporation, government, or bad actor - to censor or manipulate the flow of information.
- Is a relay refusing to host your notes? Use another or run your own!
- A specific client using an algorithm you don't like, take your identity and social graph elsewhere and choose another!
Take your identity and social graph with you, anywhere any time.
Nostr’s ability to foster authentic, unfiltered conversations while safeguarding user sovereignty has made it a cornerstone for communities seeking alternatives - whether they’re activists, creators, or everyday people tired of being pawns in the data-driven game. It's simple and adaptable design also encourages innovation, inviting developers to build tools and interfaces that keep pushing the boundaries of what the decentralized internet can achieve. In short, Nostr isn’t just a tool; it’s a movement toward a freer, more equitable digital future.

How Does Nostr Work?
Instead of one giant server owned by a single company holding all your posts and messages, Nostr spreads everything across lots of smaller servers called relays. To get started, you download a client, create your account and back up your private key. Your private key is used to secure your account and sign every message you send over the network. This allows anyone you interact with the verify the integrity of the data coming from 'you'.
The Nostr network is essentially a collection of bulletin boards that share a common format
When you write a note, or share some other type of compatible data, your client signs it with your private key, then sends it to one or more relays. Which relays your information is sent to is entirely up to you. These relays share your message with others who want to see it.
For others to see your notes or 'other stuff', they'll need to be able to find you. Typically this is done by using your public key, which looks something like this
npub15c88nc8d44gsp4658dnfu5fahswzzu8gaxm5lkuwjud068swdqfspxssvx. Don't panic though, you don't need to memorize all of your friends public keys, there are more human friendly methods of finding people that we'll come onto later.Once someone is following you, their client will ask all of their connected relays for any data shared by your public key. Their client will receive this data, verify it is signed by your private key and then populate it into their feed.
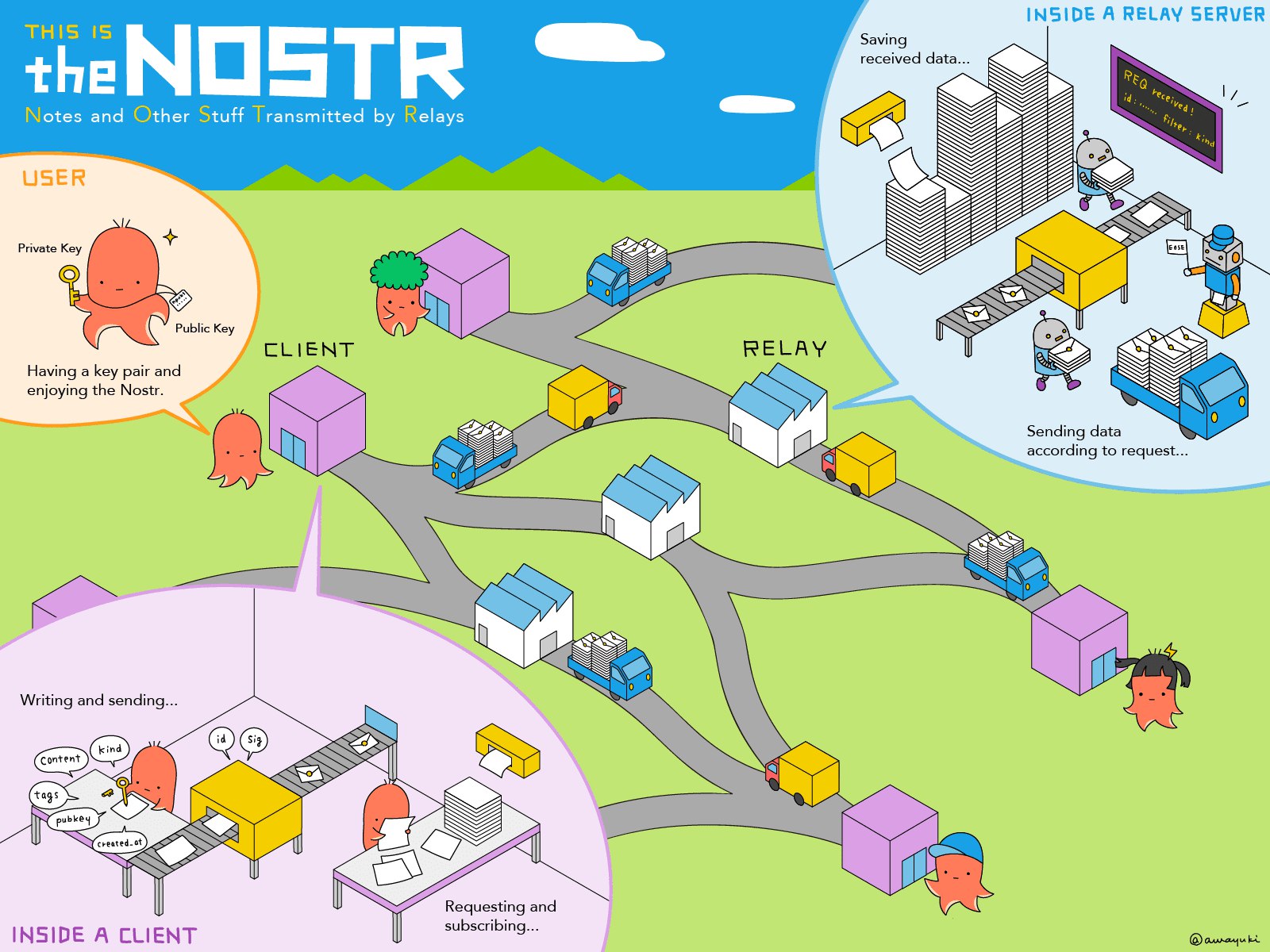
The “Other Stuff” Explained
Nostr’s name hints at this: Notes and Other Stuff Transmitted by Relays. But what is the “other stuff”? Put simply, it’s all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event - like a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client for different purposes.
Here's some content examples of 'Other Stuff':
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the “other stuff” to grow wilder and weirder over time!
Clients vs Relays: What’s the Difference?
Newbies often get tripped up by these two terms, so let’s clearly define them.

Clients
A client is what you use to interact with Nostr. It’s the app or website where you type your posts, read your feed, follow and interact with others. Examples of Nostr clients include:
- Damus (iOS Twitter style client)
- Primal (Cross-platform Twitter style client)
- Amethyst (Android only Twitter style client)
- Habla.News (Web based blog client)
- Olas (Instagram style client)
- 0xchat (Messaging client)
Clients don’t store your data; they just pull it from relays and display it for you. You can switch clients whenever you want, and your account stays the same because it’s tied to your keys, not any single client or app.
Clients are how you use Nostr, and relays are where the data lives. You need both to make the magic happen.
Relays
A relay is a server that stores and shares Nostr data. It’s a little like a post office: you send your note to a relay, and it delivers it to anyone who’s subscribed to see it (like your followers). Relays are run by individuals, groups, or companies who volunteer their computing power. Some are free, some charge a small fee, and you can connect to as many as you like. Most clients will come pre-configured with a list of well-known relays, but you can add or remove any you like.
What Are Zaps?
Zaps are arguably one of Nostr’s coolest features! A zaps is a way to send payments in Bitcoin directly to other users. Imagine liking a post, but instead of just clicking a heart (which you can of course do), you send the poster a few cents worth of Bitcoin to say, “This is awesome!”.
Zaps use Bitcoin's Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
Zaps are optional but add a fun layer to Nostr. Creators love them because it’s a way to get direct support from fans, with no middleman required.

NIP-05 Identifiers: Your Nostr “Username”
Your nPub, or public key (that long string of letters and numbers) is your 'official' Nostr ID, but it’s not exactly catchy. Enter NIP-05 identifiers, a human-readable and easily sharable way to have people find you. They look like an email address, like
qna@hellonostr.xyz.Here’s how it works:
Most users obtain their NIP-05 ID from a website or service that supports Nostr. Some of these services are free whereas some charge a fee. Some clients, like Primal will set one up for you automatically when you create an account. The email like ID links to your public key, so people can find you more easily. And because these ID's are domain based, there can be no duplicates. qna@hellonostr.xyz can only map to a single public key. The only person that can change that link is the person in control of the domain.
If you control your own domain, you can easily map your Nostr public key to name@my.domain. It’s not mandatory, but it’s super useful for building trust and making your profile recognizable.
Next Steps
So you're bought in. You understand why Nostr is so important and want to get started. Check out our simple onboarding guide here.
Thanks For Reading
Hopefully that moistened your taste buds for more educational Nostr content. This was a basic one, but there will be more focused material coming soon.
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ 21335073:a244b1ad
2025-03-20 12:24:16
@ 21335073:a244b1ad
2025-03-20 12:24:16Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 7d33ba57:1b82db35
2025-03-20 11:27:54
@ 7d33ba57:1b82db35
2025-03-20 11:27:54Agaete
Agaete is a charming coastal town on the northwest coast of Gran Canaria, known for its stunning cliffs, natural pools, fresh seafood, and rich history. Surrounded by the Agaete Valley, this town offers a mix of nature, culture, and relaxation.
🏛️ Top Things to Do in Agaete
1️⃣ Explore the Agaete Valley (Valle de Agaete)
A lush, green valley famous for its coffee plantations – the only place in Europe where coffee is grown! Take a coffee farm tour and taste local Canarian coffee and wine.
2️⃣ Swim in the Natural Pools of Las Salinas
These volcanic rock pools by the coast provide a unique, sheltered swimming experience with breathtaking ocean views.
3️⃣ Visit Puerto de las Nieves
The picturesque fishing village next to Agaete, where you can enjoy fresh seafood, stroll along the promenade, or catch a ferry to Tenerife.
4️⃣ Hike in Tamadaba Natural Park
Just above Agaete, this stunning nature reserve offers incredible hiking trails with pine forests and breathtaking views of the Atlantic Ocean.
5️⃣ Discover the Necropolis of Maipés
An archaeological site with pre-Hispanic burial mounds dating back over 1,300 years, providing insight into the island’s indigenous history.
🍽️ What to Eat in Agaete
- Pescado fresco – Fresh fish grilled to perfection 🐟
- Cochino negro – A special Canarian black pig dish 🍖
- Queso de flor – Local artisan cheese 🧀
- Agaete coffee & wine – Grown right in the valley ☕🍷
🚗 How to Get to Agaete
🚗 By Car: ~35-40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Agaete
✅ Best time to visit? Year-round, but especially beautiful in spring 🌿
✅ Great for hiking & nature lovers – Bring comfortable shoes 👟
✅ Try local coffee & wine – It’s one of the best-kept secrets of Gran Canaria ☕🍷 -
 @ cff1720e:15c7e2b2
2025-03-20 11:14:33
@ cff1720e:15c7e2b2
2025-03-20 11:14:33Wolfgang Borchert 1947\ (Wolfgang Borchert starb mit 26 Jahren an einer Kriegsverletzung)
Dann gibt es nur eins!
Du. Mann an der Maschine und Mann in der\ Werkstatt. Wenn sie dir morgen befehlen, du\ sollst keine Wasserrohre und keine Kochtöpfe\ mehr machen – sondern Stahlhelme und\ Maschinengewehre, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mädchen hinterm Ladentisch und\ Mädchen im Büro. Wenn sie dir morgen\ befehlen, du sollst Granaten füllen und\ Zielfernrohre für Scharfschützengewehre\ montieren, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Besitzer der Fabrik. Wenn sie dir morgen\ befehlen, du sollst statt Puder und Kakao\ Schießpulver verkaufen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Forscher im Laboratorium. Wenn sie dir\ morgen befehlen, du sollst einen neuen Tod\ erfinden gegen das alte Leben, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Dichter in deiner Stube. Wenn sie dir\ morgen befehlen, du sollst keine Liebeslieder,\ du sollst Haßlieder singen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Arzt am Krankenbett. Wenn sie dir\ morgen befehlen, du sollst die Männer\ kriegstauglich schreiben, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Pfarrer auf der Kanzel. Wenn sie dir\ morgen befehlen, du sollst den Mord segnen\ und den Krieg heilig sprechen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Kapitän auf dem Dampfer. Wenn sie dir\ morgen befehlen, du sollst keinen Weizen\ mehr fahren – sondern Kanonen und Panzer,\ dann gibt es nur eins:\ Sag NEIN!\ \ Du. Pilot auf dem Flugfeld. Wenn sie dir morgen\ befehlen, du sollst Bomben und Phosphor\ über die Städte tragen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Schneider auf deinem Brett. Wenn sie\ dir morgen befehlen, du sollst Uniformen zuschneiden,\ dann gibt es nur eins:\ Sag NEIN!\ \ Du. Richter im Talar. Wenn sie dir morgen befehlen,\ du sollst zum Kriegsgericht gehen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mann auf dem Bahnhof. Wenn sie dir\ morgen befehlen, du sollst das Signal zur Abfahrt\ geben für den Munitionszug und für den\ Truppentransport, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mann auf dem Dorf und Mann in der\ Stadt. Wenn sie morgen kommen und dir den\ Gestellungsbefehl bringen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mutter in der Normandie und Mutter in\ der Ukraine, du, Mutter in Frisko und London,\ du, am Hoangho und am Mississippi, du,\ Mutter in Neapel und Hamburg und Kairo und\ Oslo - Mütter in allen Erdteilen, Mütter in der\ Welt, wenn sie morgen befehlen, ihr sollt\ Kinder gebären, Krankenschwestern für\ Kriegslazarette und neue Soldaten für neue\ Schlachten, Mütter in der Welt, dann gibt es\ nur eins:\ Sagt NEIN! Mütter, sagt NEIN!\ \ Denn wenn ihr nicht NEIN sagt, wenn IHR nicht nein sagt, Mütter, dann:\ dann:
... Fortsetzung
https://route96.pareto.space/cdd62d02f73eec86bfcaa8108ef515795c6a3c714a418880ea9d267c4aeb1a8d.mp3
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:08:14
@ 20e17dd0:2ae504d7
2025-03-20 10:08:14Prerequisite
Installation
Open a Terminal session and write the following command:
ruby sudo apt install docker.ioYou will be ask permission to install and continueruby yValidation of the installation
To validate the installer, prompt the following command:
ruby docker --versionYou should get:
ruby Docker version 26.1.3, build 26.1.3-0ubuntu1~24.04.1To test if it is running, prompt the following command:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Test Installation
To make sure that everything runs smoothly, write the following command:
ruby sudo docker run hello-worldYou should get a Hello from Docker.You are ready to enjoy pulling docker images!
originally posted at https://stacker.news/items/917064
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:04:35
@ 20e17dd0:2ae504d7
2025-03-20 10:04:35Prerequisite
Installation
Open a Terminal session and write the following command to make sure that Docker is running:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Then, create the volume that Portainer Server will use to store its database:
ruby sudo docker volume create portainer_dataYou are now ready for the on-liner installation:
ruby sudo docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestTo validate the installer, prompt the following command:
ruby sudo docker psYou should see Portainer's container running.
To access Portainer Server, go to the following adress: https://localhost:9443
Et voila!
-
 @ 378943b3:9815e145
2025-03-20 10:00:00
@ 378943b3:9815e145
2025-03-20 10:00:00Eddie McVey shares the origins of his dream with his late brother, Pat, and how their family values shaped the way they run their business. He opens up about loss, perseverance, and the drive to keep pushing forward even in the toughest times. From navigating financial struggles to expanding the Maggie O'Brien's brand, Eddie offers insights into business, resilience, and the ever-changing landscape of St. Louis. The episode also explores deeper themes of community, family legacy, and the importance of staying grounded.
You show up and talk, we handle the rest of your podcast - https://calendly.com/noblelore/podcast-discovery-call
Looking for an alternative to alcohol? - Use code "NOBLE" for 20% off your order! https://bemightykind.com/
Timestamps:
1:39 - The tough first four years in business
3:12 - Buying Bombers and expanding the brand
7:15 - The impact of COVID-19 on expansion plans
9:50 - The unexpected opportunity to buy Maggie O’Brien’s
16:02 - Taking business risks and learning from them
23:41 - Growing up in a large family of 11 siblings
29:40 - The power of building local communities
32:12 - Eddie’s father’s gift for making people feel included
33:36 - Memories of Pat McVey's kindness and authenticity
41:16 - The deep impact of losing a sibling
46:01 - Learning to navigate grief and honoring Pat’s legacy
50:51 - Hard work vs. luck in business
54:48 - The challenges and future of St. Louis
57:38 - Why St. Louis needs better marketing and safety measures
01:00:52 - Advice for young people: The importance of common sense -
 @ d5c3d063:4d1159b3
2025-03-20 09:21:42
@ d5c3d063:4d1159b3
2025-03-20 09:21:42📢 "ซื้อหนี้ประชาชน" ทางออก หรือ กับดักเศรษฐกิจ
คุณเคยได้ยินไหม "เป็นหนี้แล้วไม่ต้องจ่าย เดี๋ยวมีคนมาซื้อให้" ฟังดูเหมือนฝันที่เป็นจริงใช่ไหม แต่เดี๋ยวก่อน...ลองคิดดูให้ดี ถ้าทุกคนหยุดจ่ายหนี้ แล้วใครกันที่จะเป็นคนแบกรับภาระนี้ ถอดรหัสแนวคิด "ซื้อหนี้ประชาชน" ด้วยเศรษฐศาสตร์แบบง่ายๆ และดูว่ามันจะช่วยเศรษฐกิจได้จริง หรือเป็นเพียง "ยาแก้ปวด" ที่ไม่รักษาอาการแท้จริง เรื่องราวของหนี้ที่ไม่มีวันหมด ลองนึกภาพตามนะ... "สมชาย" กู้เงินมาซื้อรถ 🚗 แต่ผ่อนต่อไม่ไหว ธนาคารจะยึดรถไปขายทอดตลาด แต่ทันใดนั้นก็มีโครงการใหม่จากภาครัฐหรือเอกชน "ซื้อหนี้ออกจากระบบธนาคาร" ฟังดูดีใช่ไหม แต่ปัญหาคือ ถ้าสมชายรู้ว่ามีคนช่วยเสมอ เขาจะมีแรงจูงใจในการจ่ายหนี้ต่อไปหรือเปล่า นั่นแหละ...จุดเริ่มต้นของกับดัก "Moral Hazard"
บทเรียนจาก #HenryHazlitt ผู้เขียน Economics in One Lesson
1 มันช่วยแก้หนี้ได้จริง...หรือแค่ยืดปัญหา Hazlitt เคยเตือนไว้ว่า เศรษฐกิจที่ดีต้องมองผลกระทบระยะยาว ไม่ใช่แค่ผลดีชั่วคราว 🔹 สิ่งที่ดูเหมือนช่วยเหลือวันนี้ อาจสร้างปัญหาที่ใหญ่กว่าในอนาคต 🔹 การแทรกแซงตลาดมักส่งผลให้เกิด "ผลกระทบที่มองไม่เห็น" ซึ่งอาจเลวร้ายกว่าปัญหาที่พยายามแก้ Hazlitt เชื่อว่าการซื้อหนี้แบบนี้อาจดูเหมือนช่วยเหลือประชาชนในระยะสั้น แต่ แท้จริงแล้วมันอาจกระตุ้นให้คนเคยชินกับการไม่จ่ายหนี้ และรอให้รัฐหรือเอกชนมาช่วยเสมอ ลองคิดดูว่า...
💡 ถ้าคนรู้ว่า "เป็นหนี้แล้วไม่ต้องจ่าย เพราะเดี๋ยวมีคนมาช่วย" แล้วพวกเขาจะพยายามจ่ายหนี้ในอนาคตไหม 💡 แล้วใครกันแน่ที่ต้องแบกรับหนี้พวกนี้ ธนาคาร เอกชน หรือสุดท้ายเป็น ภาษีจากประชาชนทุกคน เงินทุกบาทที่ใช้ ต้องมาจากที่ไหนสักแห่งเสมอ
ดังนั้น หากรัฐหรือเอกชนใช้เงินไปซื้อหนี้ แล้วไม่สามารถเก็บคืนได้ เงินนั้นก็จะหายไปจากระบบ เหมือนโยนลงทะเล แล้วแบบนี้คือการแก้ปัญหาจริงๆ หรือแค่ยืดเวลาจนระเบิดลง Hazlitt คงบอกว่า..."ไม่มีวิธีลัดในเศรษฐศาสตร์ การช่วยหนี้แบบนี้เป็นเพียงการเลื่อนเวลาความเสียหาย ไม่ใช่การแก้ปัญหา"
2 "ซื้อหนี้" = เงินจากไหน ผู้เสนอแนวคิดบอกว่า "เราจะใช้เงินเอกชน ไม่ใช่เงินรัฐ" แต่ในความเป็นจริง เอกชนไม่ได้มีเงินเหลือเฟือขนาดนั้น ทางเลือกที่เป็นไปได้ก็คือ... รัฐบาลต้องอุดหนุน ซึ่งสุดท้ายก็มาจากเงินภาษีเราๆ นี่แหละ หรือเอกชนคิดค่าธรรมเนียมเพิ่ม ทำให้ประชาชนต้องจ่ายมากขึ้นในระยะยาว
3 มันอาจทำให้เศรษฐกิจพังเร็วขึ้น Hazlitt อธิบายเรื่อง "เศษแก้วที่แตก" (Broken Window Fallacy) ว่า "การทำลายบางสิ่งเพื่อกระตุ้นเศรษฐกิจไม่ได้ทำให้เราได้กำไรเพิ่ม แต่มันแค่โยกย้ายค่าใช้จ่ายไปที่อื่น" เช่นเดียวกันกับการซื้อหนี้ มันไม่ได้ทำให้เศรษฐกิจดีขึ้น แต่เพียงโยกหนี้ไปที่คนอื่น
🎯 แล้วทางออกที่ดีกว่าคืออะไร แทนที่จะใช้มาตรการซื้อหนี้เพื่อ "ปิดบัง" ปัญหา มาลองดูวิธีแก้ปัญหาที่ใช้ หลักการตลาดเสรีและเศรษฐศาสตร์ที่แท้จริง กันดีกว่า 👇
✅ 1. ปล่อยให้กลไกตลาดจัดการหนี้ตามธรรมชาติ ปัจจุบันมีบริษัทบริหารสินทรัพย์ (AMC) ที่รับซื้อหนี้เสียจากธนาคารในราคาที่เหมาะสมอยู่แล้ว หากปล่อยให้กลไกตลาดดำเนินไป ธนาคารและสถาบันการเงินจะสามารถคัดกรองลูกหนี้ที่สามารถชำระหนี้ได้ออกมาโดยอัตโนมัติ
แล้วทำไมต้องปล่อยให้ตลาดทำงาน
-คนที่สามารถจ่ายหนี้ ได้จะมีแรงจูงใจในการจ่ายต่อ -คนที่จ่ายไม่ได้จริงๆ ก็จะต้องเจรจาปรับโครงสร้างหนี้เอง -บริษัทบริหารหนี้สามารถจัดการได้ดีกว่าภาครัฐ เพราะมีแรงจูงใจทางกำไร
✅ 2. ส่งเสริมการออม และสร้างวินัยทางการเงินให้ยั่งยืน ปัญหาหนี้ครัวเรือน ไม่ใช่แค่เพราะ "ไม่มีเงิน" แต่เพราะพฤติกรรมการใช้เงิน และผลกระทบจากเงินเฟ้อ Henry Hazlitt เตือนว่า การพิมพ์เงินและใช้จ่ายเกินตัวของรัฐบาลเป็นตัวการสำคัญที่ทำให้เงินเฟ้อพุ่งสูง ซึ่งทำให้เงินที่ประชาชนเก็บออม มีมูลค่าลดลงตลอดเวลา บ.ก.จิงโจ้บอกว่า #เวลามีค่าศึกษาบิตคอยน์
✅ 3. ถ้ารัฐบาลต้องการช่วยเศรษฐกิจ ต้องเน้นที่การสร้างงานจริงๆ ผ่านกลไกตลาด ไม่ใช่การแทรกแซงที่ทำให้ประชาชน "เคยชิน" กับการไม่ต้องรับผิดชอบหนี้ของตัวเอง
แนวคิดนี้ช่วยอย่างไร
-คนที่มีงานทำ = มีรายได้ = สามารถชำระหนี้ได้เอง -ธุรกิจเติบโตขึ้น ทำให้เศรษฐกิจขยายตัว -ไม่ต้องให้รัฐเข้ามาแทรกแซงระบบการเงินมากเกินไป
✅ 4. เปิดเสรีสินเชื่อ ให้การแข่งขันทำงานแทนรัฐ ทุกวันนี้สินเชื่อจากธนาคารอาจมีข้อจำกัดสูง ทำให้ประชาชนต้องไปพึ่งพาหนี้นอกระบบ หรือดอกเบี้ยแพงๆ
ถ้ารัฐเปิดเสรีสินเชื่อมากขึ้นล่ะ
-เพิ่มการแข่งขันในภาคธนาคาร ทำให้ดอกเบี้ยต่ำลง -ธนาคารมีแรงจูงใจในการให้สินเชื่อกับลูกหนี้ที่มีความสามารถในการจ่าย -หนี้นอกระบบลดลง ประชาชนสามารถกู้เงินในระบบที่ปลอดภัย
ถ้าคุณเป็นสมชาย แล้วรัฐบาลเสนอให้ซื้อหนี้ของคุณ…คุณจะยอมไหม คุณคิดว่าเป็นโอกาสที่ดี หรือกับดักที่รอทำให้เศรษฐกิจล่มสลาย คอมเมนต์มาบอกกันหน่อยแล้วแท็กเพื่อนที่คุณคิดว่า "ต้องอ่านเรื่องนี้"
แชร์บทความนี้ให้คนรอบตัวคุณ ให้พวกเขารู้ทันว่านโยบายแบบนี้มีผลกระทบอย่างไรกับเศรษฐกิจของเรา 🙃 #Siamstr #EIOL
-
 @ 6a6be47b:3e74e3e1
2025-03-20 09:14:31
@ 6a6be47b:3e74e3e1
2025-03-20 09:14:31Hi frens, I just wanted to say hello and remind you about the amazing artwork available from my creative corner. 🖼️ 🦄 I have a few digitala prints on my Plebeian Market stall from Bitcoin to some hoverflies. 🦄 On my Kofi-shop I have a bunch of digital prints too; fromBeelzebub toKrampus, stickers for Goodnotesand many other occulture and religious theme artwork. 🦄If you're more into physical prints, you can visit my INPRNT shop but if you'd like to wear my artwork, visit my Teespring shop. 🦄 You can find all of this at my nostree.me profile or go directly tomy website 🦄And of course, my pride and joy are my blog entries, I've painted about Ostara,Lupercalia, Nunsand many other religious and pagan themes. I invite you to take a peek 👀 Also, just dropping by to know how you've been? How are you gonna celebrate this Equinox? Maybe a Spring Cleansing?? Whatever you decide to do, I wish the best for you and your loved ones. I also would like to thank kyou for liking, reposting, the zaps, you're all awesome! None of this would be possible without you my frens! Wishing you all a Happy New Astrological year! Happy Equinox! Godspeed
-
 @ 7d33ba57:1b82db35
2025-03-20 09:08:46
@ 7d33ba57:1b82db35
2025-03-20 09:08:46Puerto de las Nieves
Puerto de las Nieves is a picturesque seaside village on Gran Canaria’s northwestern coast, near Agaete. Known for its whitewashed houses, fresh seafood, and stunning coastal views, it’s the perfect place for arelaxing day by the ocean.
🌊 Top Things to Do in Puerto de las Nieves
1️⃣ Relax at Playa de las Nieves
A peaceful pebble beach with crystal-clear waters, perfect for swimming and sunbathing.
2️⃣ See the Dedo de Dios (God’s Finger) Rock Formation
This famous natural rock structure was partially destroyed by a storm in 2005, but the area remains a scenic spot.
3️⃣ Visit the Agaete Natural Pools (Las Salinas de Agaete)
Just a short walk away, these volcanic rock pools offer a natural and sheltered swimming experience.
4️⃣ Walk Along the Promenade
Enjoy a scenic stroll along the coastal promenade, lined with cafés, seafood restaurants, and local shops.
5️⃣ Take a Ferry to Tenerife
Puerto de las Nieves is the departure point for ferries to Santa Cruz de Tenerife, making it a great connection between the Canary Islands.
🍽️ What to Eat in Puerto de las Nieves
- Fresh seafood – Try the local grilled fish (pescado a la espalda) 🐟
- Papas arrugadas with mojo – A Canarian classic 🥔
- Pulpo a la gallega – Delicious Galician-style octopus 🐙
- Local wines – Agaete Valley is known for its unique volcanic wines 🍷
🚗 How to Get to Puerto de las Nieves
🚗 By Car: ~40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Puerto de las Nieves
✅ Best time to visit? Year-round, but sunsets here are especially magical 🌅
✅ Bring water shoes! The beach is pebbly, so they make swimming easier 👟
✅ Try a boat trip – Great for coastal views and dolphin watching 🚤 -
 @ 6b0a60cf:b952e7d4
2025-03-20 07:36:17
@ 6b0a60cf:b952e7d4
2025-03-20 07:36:17このイベント自身をnaddr形式で参照する nostr:naddr1qvzqqqr4gupzq6c2vr8l8m9952e9qhxt8acn8kzzypzuhm6q70fvvxylkzu49e75qydhwumn8ghj7mnjv4kxz7fwvvkhxar9d3kxzu3wdejhgtcqp5cnwdpjxs6n2de3xyenxwql6rq76
-
 @ da0b9bc3:4e30a4a9
2025-03-20 06:29:09
@ da0b9bc3:4e30a4a9
2025-03-20 06:29:09Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/918547
-
 @ f6488c62:c929299d
2025-03-20 04:15:12
@ f6488c62:c929299d
2025-03-20 04:15:12" ไขคำตอบผ่านมุมมอง Ethereum vs Solana" คุณเคยสงสัยไหมว่า... ทุกวันนี้แฮ็กเกอร์ระดับโลกอย่างกลุ่ม Lazarus จากเกาหลีเหนือเลือกโจมตีคริปโตผ่านช่องทางไหน? ทำไมเราถึงเห็นข่าวแฮ็กเหมือง Blockchain สุดอื้อฉาวบ่อยครั้ง ทั้งที่เครือข่ายบล็อกเชนถูกออกแบบมาให้ปลอดภัย? คำตอบอาจซ่อนอยู่ใน "จุดอ่อน" ของระบบนิเวศคริปโตเอง โดยเฉพาะสองยักษ์ใหญ่อย่าง Ethereum (ETH) และ Solana (SOL) ที่ต่างมีทั้งจุดแข็งและช่องโหว่ให้โจรไซเบอร์จ้องจับตาฉกตังคุณ!
ทำไม Ethereum ถึงเป็นอาหารจานโปรดของแฮ็กเกอร์?
1. "เงินมันเยอะ... ดึงกิเลสใจให้อยาก"
Ethereum คือศูนย์กลาง DeFi ที่มีเงินไหลเวียนมหาศาล มูลค่าทั้งระบบ (TVL) สูงกว่า 4 หมื่นล้านดอลลาร์ แค่คิดภาพว่าแฮ็กเกอร์เจาะระบบได้ครั้งเดียวก็รวยเป็นเศรษฐี แถมยังมี dApps มากมายให้เลือกโจมตี ไม่แปลกที่เป้าหมายแรกจะพุ่งมาที่ ETH!
2. สัญญาอัจฉริยะ... มันคือ ดาบสองคมแหละ
Smart Contract บน Ethereum ใช้ภาษา Solidity ที่มีความยืดหยุ่น แต่ก็เป็นดาบสองคม! แค่โค้ดผิดพลาดนิดเดียวก็สร้างความเสียหายมหาศาล เหมือนเหตุการณ์ Ronin Bridge ที่ถูกเจาะจนสูญเงิน 625 ล้านดอลลาร์ หรือการโจมตีแบบ Reentrancy ที่เคยทำให้ DAO ล่มในปี 2016
3. สะพานข้ามเชน... กับดักล่อแฮ็กเกอร์
ทุกวันนี้ Ethereum เชื่อมต่อกับเครือข่ายอื่นผ่าน Bridge และ Layer 2 อย่าง Optimism/Arbitrum ซึ่งสะพานเหล่านี้คือจุดอ่อนชั้นดี! เพราะต้องเก็บเงินสำรองจำนวนมาก ยิ่งถ้า Audit ไม่รอบคอบ แฮ็กเกอร์ก็ฉกเงินออกได้สบาย เหมือนกรณี Poly Network ที่ถูกขโมย 611 ล้านดอลลาร์ในปี 2021
Solana ปลอดภัยกว่า จริงหรือ?
1. เร็วแต่เสี่ยง... ปัญหาที่ซ่อนในระบบ
Solana ขึ้นชื่อเรื่องความเร็ว 65,000 TPS และค่าธรรมเนียมถูก แต่ความเร็วอาจมาพร้อมความเสี่ยง! การใช้เทคนิค Parallel Processing อาจมีช่องโหว่ที่ยังไม่ถูกพบ เช่น กรณี Wormhole Bridge ถูกเจาะจนสูญ 326 ล้านดอลลาร์ในปี 2022
2. ระบบนิเวศเพิ่งเกิดไม่นาน... เหมือนบทเรียนที่ยังไม่ครบหลักสูตร
dApps บน Solana ส่วนใหญ่ยังใหม่และขาดการตรวจสอบ (Audit) ที่เข้มงวด เมื่อเทียบกับ Ethereum ที่ผ่านสนามรบมานาน โครงการใหม่ ๆ อาจมีช่องโหว่หลงเหลือให้แฮ็กเกอร์เสาะแสวงหา
3. Validator น้อย... เป้าสำหรับโจมตี
Solana มี Validator เพียง 1,000+ โหนด เทียบกับ Ethereum ที่มีถึง 5 แสนโหนด! ตัวเลขนี้ทำให้เสี่ยงต่อการโจมตีแบบ 51% มากกว่า แม้จะยังไม่เกิดขึ้นจริง แต่เป็นจุดที่นักพัฒนาต้องจับตาอย่างใกล้ชิด
เปรียบเทียบแบบเห็นภาพ: Ethereum vs Solana ใครเสี่ยงกว่า?
- เงินในระบบ → Ethereum ชนะขาด (แต่ก็เป็นเป้าหมายใหญ่)
- ช่องโหว่ Smart Contract → ทั้งคู่มีปัญหา แต่ Solana อาจเสี่ยงกว่าเพราะ Audit น้อย
- จุดอ่อนเครือข่าย → Ethereum มีปัญหา Bridge ส่วน Solana กลัวระบบล่ม
- ภาษาโปรแกรม → Solidity (Ethereum) ยืดหยุ่นแต่ซับซ้อน vs Rust (Solana) ปลอดภัยกว่าแต่ยังใหม่
สรุปแบบตรงไปตรงมา
- Ethereum คือ "หมีตัวใหญ่" ที่แฮ็กเกอร์อยากล่า เพราะเงินมาก แม้จะป้องกันดี แต่มีจุดให้โจมตีหลายชั้น
- Solana คือ "เหยื่อดาวรุ่ง" ที่ถ้าเกิดช่องโหว่ร้ายแรง อาจถูกโจมตีแบบถล่มเละได้ง่าย
แฮ็กเกอร์อย่างกลุ่ม Lazarus ไม่ได้สนใจว่าเครือข่ายไหนเก่งกว่า แต่พวกเขามองหา "ช่องโหว่ที่ทำเงินได้เร็ว" มากกว่า! ตอนนี้ Ethereum ยังครองแชมป์เป้าหมายยอดนิยม แต่ถ้า Solana เติบโตเร็วโดยไม่แก้จุดอ่อน วันหนึ่งอาจกลายเป็นเหยื่อรายใหญ่ได้ไม่ยาก
วิธีป้องกันตัวให้รอดจากมือแฮ็กเกอร์
สำหรับนักลงทุนทั่วไป
- อย่าเก็บเงินไว้ใน Exchange นาน เปลี่ยนมาใช้ Hardware Wallet อย่าง Ledger/Trezor
- เช็กประวัติการ Audit ของโปรเจกต์ผ่านเว็บไซต์อย่าง CertiK หรือ Hacken ก่อนลงทุน
สำหรับนักพัฒนา
- ทดสอบ Smart Contract อย่างน้อย 3 รอบ และจ้างบริษัท Audit มืออาชีพ
- ใช้ Oracle จากหลายแหล่ง เพื่อป้องกันการป้อนข้อมูลผิดพลาด
สำหรับโปรเจกต์คริปโต
- สร้างกองทุนประกัน (Insurance Fund) เผื่อถูกแฮ็ก
- อัปเดตระบบรักษาความปลอดภัยแบบ Real-Time ตลอดเวลา
สุดท้ายนี้... อย่าลืมว่า "ไม่มีระบบไหนปลอดภัย 100%"
ไม่ว่า Ethereum หรือ Solana ก็ตาม การรู้เท่าทันและป้องกันตัวเองคืออาวุธที่ดีที่สุด ติดตามข่าวสารความปลอดภัยสม่ำเสมอ และอย่าวางใจระบบใดระบบหนึ่งแบบสุดใจ — เพราะแฮ็กเกอร์ก็อัปเกรดตัวเองทุกวันเช่นกัน!
แล้วคุณล่ะ... คิดว่าเครือข่ายไหนน่ากังวลที่สุด? แชร์ความเห็นไว้ได้เลย!
-
 @ d57360cb:4fe7d935
2025-03-20 04:05:59
@ d57360cb:4fe7d935
2025-03-20 04:05:59A story about people
It was a rainy day in the busy city. The type of day when a dark silence envelops the air, allowing the hard thuds of rain to paint the concrete. I enjoy the evening in the city. The neon lights enliven the darkness, giving flair to the city as a whole. Every color you can think of is in these billboards; they’re bright pink, red, green, and so on, almost like a 14-year-old who plays too many sci-fi games designed it. As the city dimmed, I took a trip to my favorite café, Speedy’s. There’s nothing particularly special about this café. It holds an average rating of 4.0 stars online; it has cushy booth seats. The coffee is mid-tier, a bit watered down, but I don’t mind since I’m not too much of a fan of a strong blend. They have enough food items to keep you satisfied, but nothing to make it exceptional. Maybe that’s why I’ve come to love a café like this; it’s not extravagant, it blends in, it’s how a café should be; it meets its mark. Sometimes that’s all we hope for in things, even in people.
I’m good friends with the owner; she noticed me coming in often, and one night while the café was deserted and empty, we struck up a conversation. It was mere small talk on the first occasion, the simple things like how your day is, what part of the city you live in, what you do for work. It felt like a barrier of entry to a deeper well we both had yet to discover. At night, Speedy liked to switch all the lights to red; it gave a special ambience to the café, it relaxed you, and highlighted a lot of the art and design in the room. It almost feels like someone made the café to be lit red; when the regular lights were on, it was a plain old café. Once those lights came on, it became something entirely vivid and alive like those neon skyscrapers in the city. The thing about the nighttime was no one came into the café; it’s like they didn’t even know it existed even though the open sign continued to hang till 11:00 pm. People had more important places to be or they thought going to a café at night was an odd choice.
I frequented Speedy’s three times a week on average, but I always showed up on rainy days. There was no reason behind this; I felt drawn to the café, to Speedy, and to the atmosphere created by those red lights. I walked in and Speedy was at the counter blending a mint tea. I could smell the mint from the moment I walked in; it cleared my nose and I was breathing clearer than ever. It had me wondering how long my nasal passages had been blocked and how unfortunate it is to have a stuffy nose. I recalled a quote I heard once: ‘An ordinary man wishes for a million things, a sick man only has one.’ I sat at the corner booth. Speedy knew the drill. So, she made a black coffee with one cream and two sugars. I don’t mind coffee in the evening. Being an avid drinker, the effects of caffeine no longer do much to me; my mom had the same phenomenon, it’s in the genes.
Speedy had on blue jeans that hovered right above her ankles, she wore clean, new-looking white sneakers and a tiny horizontal striped t-shirt. The sleeves hugged her arms nicely, she was oddly in great shape; she used to be an Olympic sprinter but no one had a clue. She had a diamond face shape, high cheekbones, and a soft welcoming face, and always wore her hair in a messy bun. She’d recently left for a vacation to Hawaii and appeared to have a nice brown tan from the trip.
We never ate much when we got together to talk. The conversation was enough to feed our souls. The thing about Speedy was she was the exact opposite of her name, which made no sense to me. She was never in a rush, always calm, composed in each action. She loved to live in the silence of life, never speaking too soon, thinking, never rushing anywhere. To her, time didn’t seem to exist; she set her own pace in life, devoid of what the world was doing. I found it an honorable skill to have, as I was the exact opposite; in essence, my name should’ve been Speedy. I was always in a rush, always frantic and anxious. I couldn’t sit still; I had to go, to be on the move, doing something at all times. Overthinking everything twice over. When we’d talk, it would be as if two species were encountering a life so unknown to the other. We discussed everything: music, especially jazz, art, culture, life, cars, and games. If it existed, it found a place in our canvas.
Slow and smooth as ever, Speedy came to the booth with a grin on her face.
Speedy: Here’s your coffee, as usual.
Narrator: *nods head* I wanted to ask you what the story behind that painting is.
To the far right of the room on the wall hung a painting that stretched from the ceiling to close to the floor. I’d never seen a canvas that size before. This was a new piece, no doubt; as I sat down in the booth, I couldn’t help but stare. It gripped me and left me blank. Speedy turned her head and glanced for a while; I don’t know how long she was looking, but she seemed to be transported somewhere far away. She finally turned back.
Speedy: That’s “color and contrast” (artist unknown). I found it after I fell out of love. I’ve had it for a while; I just never decided to put it up until two weeks ago.
Narrator: It’s an interesting piece; I can’t find the words for it, but I can’t take my eyes off it.
The painting had the perfect mix of dark and light colors, areas of bright luminance and dark depth. It engrossed you. When Speedy said she found it when she fell out of love, somehow I understood her. The painting made me reminisce about a love I once had. Maybe that’s where she was teleported to when she stared blankly at it. The painting invited you back to that place of both the light and dark parts. The title began to make sense to me. All the while, “Romance” by Hiroshi Suzuki played in the background.
Speedy: A few years after a devastating heartbreak, I was on a week-long sabbatical in Ojai, California. I stayed in an old inn on a hill near a lake. While I was there, I would take a morning walk to the lake to enjoy the birds, reflect, and drink my morning coffee. The first time I went down the hill, I spotted the huge canvas propped up in front of the lake and a tiny glass house right next to it. The glass was fully tinted so you couldn’t see inside at all. It looked like it had no doors; when the sun shone on it, it reflected back an almost platinum silver glow. Standing outside was a man facing the canvas. He had on a baggy set of linen clothes, a beaded necklace, sandals, long grey and black hair, and a big goatee. The man was immersed, almost looked possessed, and he would violently strike the canvas with his brush. Then he would abruptly stop and he would be gentle with the canvas, adding in finer details; then he would explode into a violent rhythm again. He continued this for hours, and I would visit the lake each morning to sit and watch. I always had the feeling the man knew he was being watched. To him, it was a performance, a show, somewhat of a grand finale, I as the only witness. My final morning there, I went down to the lake; the man was sealing the painting, signaling that he had finished it. He was wrapping rope around it to secure it. Once he finished, he turned with sunglasses on, stared at me for what felt like an eternity, and then signaled for me to come over. He took a seat on his wooden stool as I approached, pulling out a leather notebook; he ripped a page out of it and handed it to me. The man was not from California; I couldn’t tell where he was from, he didn’t speak English at all, or so it seemed. His silence was his voice; it didn’t feel strange at all at the time, but as I retell this story, it seems a bit mystical. I took the letter, and the man bowed to me. Once he finished bowing, he got up and walked into the glass house and closed the door. He never came back out. I was confused, so I read the note in hard-to-read writing; all it said was ‘a gift of love, yours.’ I stared blankly at the wrapped painting and took it with me. I’ve had it stored in the back of the café for years, never opening it once; when I put it up 2 weeks ago, that was the first time I saw it.
At this point, Speedy put her head down, and I could see tears falling in her lap. I figured it was best to say nothing for a while.
Speedy: Unwrapping the painting felt like reopening the wound of my broken heart; it held a power that was unexplainable. It made me shake and gave me cold chills. I’m not sure why I decided to open it, but I did. I did so with extreme caution, unwrapping the paper and untying the rope that held it together. As I saw the painting, I began to get dizzy, as if I had taken drugs and the high was hitting unexpectedly. It felt like an invisible cloak had surrounded me from every angle; I couldn’t believe what I was seeing. It wasn’t a painting but a full story. I want to show you something.
Speedy got up and I followed her to the painting. We stood in front of it and I could feel a magnetic pull; I was experiencing that cloak. She then pointed to the center of the painting; it was cut in a square that was very hard to notice. She pushed on the corner and it swiveled around, unveiling words on the back of the painting.
Speedy: That man engraved this message on the back; when I read it, my heart seemed to scream out and burst. Not in a bad or good way, but more so as a natural reaction. I can’t explain what it did, but it took care of me. Like a potion that was reserved for the right moment, if you receive it at the wrong time, you won’t get the desired effect. Maybe that’s why you came here tonight.
I sat and stared at the words.
“Color can only appear in a place of non-color, in a place where there is no flair, no fill. Color could be light filling darkness, a complement, not an opposite. Love is color, as it complements the blank canvas of emptiness. It takes the form of a blank canvas and makes its work known. It draws you in; you can’t pay attention to anything else; it’s as if the lover who has evoked this is as wide as the vast sky. As bright as a full moon. Staring into their eyes, you can no longer see the borders that the canvas inhabited; everything has become the canvas. Everything has become the art, the intricate colors and the strokes. The separation that was present before, whether noticed or not, is no longer the picture. It is now whole. It’s complete, with nothing to add; it towers over you and envelops you. You can’t believe how high it’s reached or how wide it is. It is both flowing above, below, beyond, and through your entire being. You can no longer distinguish where you and the love begin and end.“
Like the mint tea that cleared my nose, my heart cleared the way; it felt like it could finally breathe. I sat in disbelief and wondered how long I had been that way.
-
 @ 17538dc2:71ed77c4
2025-03-20 03:40:31
@ 17538dc2:71ed77c4
2025-03-20 03:40:31Who were they? Testing long form publication via yakihonne
-
 @ 6e0ea5d6:0327f353
2025-03-20 03:01:46
@ 6e0ea5d6:0327f353
2025-03-20 03:01:46A quiet, meek, and peaceful man is not necessarily a benevolent person. Only the one who harbors powerful hatred and malice within but voluntarily controls it is truly worthy of being called a man of honor.
In the business world, some people mistakenly confuse courtesy and politeness with excessive sensitivity and emotional cowardice. They speak so meekly that they even stammer. Fearing to offend others, they swallow their opinions. The ego enslaves with the worst kind of chains: the need for self-affirmation and validation. They constantly apologize for everything: “sorry for this,” “sorry for that,” “sorry for such and such.”
By behaving this way, one not only earns the listener’s contempt, disrespect, and anger but also significantly diminishes their reputation and moral standing in the eyes of others. They will never be seen as a strong leader. They will never gain the trust of subordinates. And they will never have important tasks delegated to them by their superiors.
With respect, honor, and silence, one can enter and exit any place. Those who understand both the streets and the world beyond them achieve peace and gain unrestricted access. Always consider the protection of your reputation. Do not allow mockery to test your ability to maintain self-respect.
True mastery in interpersonal interactions lies in discerning which provocations must be confronted and which deserve to be ignored.
Like a skilled swimmer who understands the currents and adapts to them, you must learn to navigate the murky waters of the world, responding with the necessary strength and wisdom in each situation.
The key to success does not lie in servile submission but in assertiveness and reciprocity. Treat others as they truly deserve to be treated, and in doing so, you will not only earn respect but also pave the way for genuine and lasting success.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ a93be9fb:6d3fdc0c
2025-03-20 02:54:52
@ a93be9fb:6d3fdc0c
2025-03-20 02:54:52Publishing new article
-
 @ 8d34bd24:414be32b
2025-03-20 01:45:49
@ 8d34bd24:414be32b
2025-03-20 01:45:49This post was inspired by my Pastor’s sermon this morning. I’ve read this passage a bunch of times. I’ve always seen Jesus’s divinity. I’ve also seen the disciples’ lack of faith, but there is so much more to get out of this passage. It shocks me that I never saw it before and just had to share.
Now on one of those days Jesus and His disciples got into a boat, and He said to them, “Let us go over to the other side of the lake.” So they launched out. But as they were sailing along He fell asleep; and a fierce gale of wind descended on the lake, and they began to be swamped and to be in danger. They came to Jesus and woke Him up, saying, “Master, Master, we are perishing!” And He got up and rebuked the wind and the surging waves, and they stopped, and it became calm. And He said to them, “Where is your faith?” They were fearful and amazed, saying to one another, “Who then is this, that He commands even the winds and the water, and they obey Him?” (Luke 8:22-25)
It is obvious from this passage, that Jesus is divine. It reminds us of Genesis 1 when God speaks the waters into existence. It reminds me of Job:
“Or who enclosed the sea with doors\ When, bursting forth, it went out from the womb;\ When I made a cloud its garment\ And thick darkness its swaddling band,\ And I placed boundaries on it\ And set a bolt and doors,\ And I said, ‘Thus far you shall come, but no farther;\ And here shall your proud waves stop’? (Job 38:8-11) {emphasis mine}
Jesus spoke and the wind and waves instantly complied. All was instantly calm. Jesus’s actions scream His divinity, but there is so much more to get out of this passage in Luke 8.
Why?
My pastor asked everyone a key question, “When Jesus told His disciples to get in the boat and to cross to the other side, did He know there would be a big, life threatening storm?” The kids at church wisely shouted, “Yes!”
Several of Jesus’s disciples were fishermen. They worked their entire lives fishing in boats in the Sea of Galilee. The were familiar with boats, wind, waves, and storms, and yet they were terrified by this storm. This was not a little storm. This storm was tossing around the boat and splashing waves of water into the boat threatening to capsize it in the middle of this large body of water.
I can somewhat relate (but not fully). I grew up in Florida and we would occasionally take a boat a couple of hours across the ocean to and from the Bahamas (Abaccos). One time we had to make the crossing on a particular day to get me back to head off to college. At this time, there was a Hurricane in the gulf (other side of Florida) that were making really big waves. If my memory is correct, we were in a 34 foot long boat and the waves were taller than the boat was long. My Dad would give full throttle to ease up one side of wave and then pull back as we shot down the far side of the wave and then again and again for hours. If the engine had failed, we would have turned sideways and been capsized. If my Dad had not kept the boat straight into the waves, we would likely have capsized, but my Father knew what to do and we made it safely to shore.
Jesus knew this giant storm was going to blow up, but He told His disciples to head right into what would soon be a giant storm. One key thought that I had previously missed is that He did not send them into the storm alone. He went with His disciples.
Initially the disciples tried to battle the storm themselves, but it was a losing proposition. They were losing the battle with the storm and losing it badly. Finally, they went to Jesus. I like how the NIV says it, “The disciples went and woke him, saying, ‘Master, Master, we’re going to drown!’” Mark 4:38 says, “Jesus was in the stern, sleeping on a cushion. The disciples woke him and said to him, ‘Teacher, don’t you care if we drown?’” The disciples didn’t just ask for help; they accused Jesus of not caring. They called Him “Master” and “Teacher,” instead of “God” or “Lord.”
So going back to my Pastor’s question, why did Jesus, who knew there was going to be a terrible storm, tell His disciples to cross the water at that time? Was He teaching His disciples to trust in Him? Was He teaching His disciples to ask Him for help when they had a need? Was He teaching them who He was in a way that they would never forget? I think the answer to all of these questions is clearly, “Yes!”
Application
Now we need to look at this passage and ask, “what do we need to take away and learn from this passage?” and “how can we apply this passage?”
I think there are several key points:
-
Jesus knew what was about to happen to them.
-
Jesus had a plan and a purpose for putting them in this fearful and life threatening situation.
-
This hardship had a good purpose.
-
Jesus was with them through it all.
So often I have people who want to deny that a loving God would intentionally put themselves or others in uncomfortable, scary, or dangerous situations. They say, “God wouldn’t do that.” or “Why would God do that?” Yes, God does cause us to go through hard times (I refuse to say bad), but not to cause us pain or hardship, but to grow us in our faith and witness.
It is a rare person who grows in faith during ease and pleasant circumstances. Most of us require hardship to force us to stop doing everything on our own and to trust Jesus and to lean on His power (Yes, I am speaking from personal experience). Nothing glorifies God more than resting in Him during the storm. Yes, God cares and loves you very much. Yes, God is with you through every hardship you will ever experience. Yes, God wants the best for you. We may not appreciate it in the moment, but God cares more about your eternal good than your momentary ease and happiness. He gives you what you need instead of what you want.
The amazing thing is that when you learn to trust in Him, when you learn to rely on His power, and when you learn to look for His good work in every situation, you will find a joy and peace like you never imagined. Instead of chasing everything looking for the perfect situation to make you happy, you will rest in the hand of the Father knowing a joy and peace that surpasses all human understanding.
In child labor, a woman’s body does what it is supposed to do to produce a baby. Sometimes, out of fear or desire for control, a woman will fight the labor. They will tense up and it causes more pain. If they relax and trust that the delivery will happen as it should, the delivery is usually much easier. Similarly, when we fight Jesus during the storm, when we don’t trust His omnipotence and omniscience, and when we try to do it our way instead of His, we actually make these hard times more uncomfortable and less effective. Instead of learning what God is teaching us, we end up harming ourselves. Instead of building an amazing witness, we give God a bad name.
No matter how bad the storm, look to Jesus and know that He is God. He is our good and loving God who works everything for our good.
Trust Jesus
-
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ df06d21e:2b23058f
2025-03-20 01:12:40
@ df06d21e:2b23058f
2025-03-20 01:12:40I'm well on my way into the Bitcoin rabbit hole. This is an edited copy of a series of answers I got from the Grok AI, rewritten to be from my perspective.
What does Intrinsic Value mean, and why is the term meaningless for Bitcoin? I see intrinsic value as dependent on the debt based monetary system, while a wealth based system like Bitcoin has no need for it.
Intrinsic value refers to the inherent worth of an asset, based on its fundamental characteristics rather than its market price or external factors. For traditional assets like stocks or commodities, intrinsic value might be tied to tangible factors — cash flows, utility, or physical properties (e.g., gold’s use in jewelry or industry). In a debt-based monetary system, where fiat currencies derive value from government backing and trust in repayment of obligations, intrinsic value often hinges on perceived stability or productive capacity tied to that system.
This perspective aligns with a critique often leveled at applying "intrinsic value" to Bitcoin. Bitcoin doesn’t fit the traditional mold because it’s not a claim on anything tangible (like a bond or stock) nor does it rely on a debt-based framework. Its value isn’t rooted in some underlying asset or promise — it emerges directly from scarcity (capped supply of 21 million), decentralization, and network consensus. Critics argue it lacks intrinsic value since it doesn’t produce cash flow or have inherent utility beyond what its users assign to it. Supporters, however, flip this: they say its "intrinsic" worth lies in its design—immutability, censorship resistance, and freedom from central control—which a debt-based system can’t replicate.
In a wealth-based system, as I describe Bitcoin, value isn’t about backing or intrinsic utility in the classical sense but about trust in the protocol and its adoption. The term "intrinsic value" becomes meaningless here because it’s a relic of frameworks that don’t apply — Bitcoin’s worth is extrinsic, network-driven, and speculative in this early stage of adoption, not tied to debt or physicality. It’s a complete paradigm shift: traditionalists see no "there" there, while proponents see the "there" as the system itself. Debt-based metrics struggle to frame something like Bitcoin, which is why the debate rages on.
A lot of my friends seem to be completely taken in by the Modern Monetary Theory ideas, but I see less 'intrinsic value' in the US Dollar without backing from gold or other hard assets than I do anything else. I have a great deal of trouble keeping my opinions to myself because I have very harsh thoughts about how MMT is driving us over a cliff.
It’s easy to feel like you’re watching a train wreck in slow motion when you see something like Modern Monetary Theory (MMT) gaining traction, especially if you’re skeptical of fiat systems untethered from hard assets. MMT flips the script on how we used to think about money. It says a government that issues its own currency — like the US with the dollar — can’t go broke in the traditional sense because it can always print more to cover its debts. Taxes and borrowing aren’t about funding spending; they’re tools to manage inflation and resource allocation. Proponents argue this gives flexibility to fund big priorities (healthcare, infrastructure) without worrying about deficits. The catch? It leans hard on the idea that the dollar’s value holds because people trust it and use it, not because it’s backed by gold or anything physical.
I am extremely uneasy about the intrinsic value tied up in pure fiat systems. Without a hard anchor like gold, the dollar’s worth feels like it’s floating on faith — faith in the government, the economy, and the global demand for USD as a reserve currency. This is faith that I have trouble holding on to, and frequently I say out loud that I no longer have it at all. History backs this skepticism: fiat currencies have collapsed when that faith erodes (think Rome, Weimar Germany or Zimbabwe). Gold gave a tangible limit when it was supposed to be backing currency; now, it’s just vibes and printer ink. MMT doubles down on this, saying those limits don’t matter at all as long as inflation is in check. But I squint at that as well, because I don’t see it as being in check. Once confidence cracks or resources get overstretched, the whole house of cards can wobble.
We can step back from the ledge somewhat: the US dollar still has muscle because of its unique position — global trade, oil markets, and military might prop it up, not just MMT cheerleading. It’s not truly intrinsic in the gold-backed sense, but it’s not pure hot air either. Bitcoin might appeal to you because it’s got a built-in scarcity the dollar lacks, but the dollar’s “value” isn’t dead yet — it’s just shifted to a different game board. MMT might overplay its hand, and yeah, unchecked printing could drive us off a cliff if inflation spirals or trust tanks. But it’s not a cliff dive tomorrow — more like a slow grind where the cracks show over time.
I don’t have to buy into MMT to see why many of my friends might. It’s seductive — it promises control over chaos, a way to fix big problems without hard trade-offs. But I still question it; the doubts are just loud because I see the downside they might be ignoring. There are harsh questions that need to be asked. How do we square infinite printing with finite resources? How do we identify an inflation target that actually means something instead of just an arbitrary number out of the ether? The cliff’s there, but we’re not airborne yet.
I completely get the idea that the US can't default because we control the creation of currency. But thinking of the currency as 'money' just seems false to me. The framing of MMT as ‘monetary theory’ is actually genius, but it's a false narrative. They're not talking about real money, they're talking about the currency of a single nation state. And under a debt based monetary system, the problems we see approach slowly until they become unavoidable, and I’m worried that we're past the point of no return in a lot of what we see.
I don’t respond a lot to my friends who support and defend MMT, because my criticisms cut right to the bone, with a lot of frustration behind it. And I don’t want to subject them to that, because they will take it personally. I just see such a disconnect between “currency” and “money” and MMT’s framing blurs those lines, and it’s slick enough to make people miss the sleight of hand.
MMT’s genius is in its storytelling. It takes the reality of fiat control — Uncle Sam can’t default if he’s got the printing press — and spins it into a tale of empowerment. “Deficits don’t matter, we can fund everything!” It’s a heady pitch, especially when people are desperate for solutions. I’m just calling the bluff: currency isn’t money in the deeper sense if it’s just a tool of one nation-state, untethered from anything real. Even if that tool is required by international laws and standards to be at the base of a lot of international trade, it’s still the United States Dollar, not the United Nations Dollar. Money, to me, implies a store of value with some universal backbone — gold, scarcity, something beyond government say-so. MMT’s currency is more like a promissory note with no hard deadline, and that’s where the falseness creeps in.
The debt-based system adds another layer to my unease. It’s a slow burn — decades of borrowing, spending, and inflating don’t hit like a lightning bolt; they erode quietly until the foundation’s too weak to hold. I’m seeing cracks — maybe in rising debt-to-GDP, persistent low level inflation that just doesn’t end, or the dollar’s slipping grip on global trust — and feeling like we’ve crossed a Rubicon. Are we past the point of no return? That’s a gut call, but I hope it’s not hard to see why we think we have. Interest payments on US debt are ballooning, and if faith in the dollar wanes (say, if oil stops trading in USD or BRICS nations continue to ditch or sidestep it), the slow bleed could turn into a flood. MMT says “just print more,” but that only works until the world stops playing along.
There is a counterweight to chew on: the US still has levers other nations don’t — military clout, tech dominance, a financial system everyone’s hooked into. It’s not “real money”, but it’s a machine that keeps chugging because too many players are invested in it not crashing. That doesn’t make MMT true — it just delays the reckoning I’m bracing for. How long until the music stops and we have to find chairs? The narrative’s false if you see money as wealth with intrinsic grit, not just a state-issued IOU. But it’s a lie that’s worked so far because the system’s too big to fail fast.
Am I crazy to feel this way? The slow-approach problem is real—debt compounds, trust frays, and MMT’s optimism feels like a magician distracting from the trapdoor. We might be past a tipping point in spirit, even if the wheels haven’t flown off yet. Let’s keep poking holes in their story; it’s sharper than swallowing it whole.
I want to do a thought experiment. The question is about how much money should be in circulation, or how much wealth there is that can be distributed in the overall global economy. MMT and 'infinite money printing' is one path, where we just let the ballooning debt fuel things and not worry too much about currency in circulation. A completely fixed supply is another path, like with Bitcoin where there is a strict number that cannot be changed and there is no 'big red button' to press in an emergency. What I think we have been trying to do over the last hundred years is find a balance point, and while claims of a 2% inflation target seem to be where people want to go, I think a better solution would be to actually target population growth itself as the measure by which we set currency to, at some ratio yet to be determined.
Do you see where I’m going with this thought experiment? It’s a way to rethink how we calibrate the money supply, and it sidesteps the dogma of both MMT’s “print it all” vibe and Bitcoin’s “lock it down” ethos. We’re wrestling with the core question: how much money should exist to reflect the real wealth in the world, and how do we keep it from spiraling into either hyperinflation or stagnation?
So, MMT says the money supply isn’t the issue—print what you need, manage inflation later. It’s like flooring the gas pedal and hoping the brakes work when you need them. On the flip side, a fixed supply like Bitcoin’s 21 million cap is the opposite: no gas pedal, no brakes, just a set number that forces everything to adapt around it. Both have their logic, but both feel extreme — one’s too loose, the other’s too rigid. The past century’s been this messy middle ground, with central banks chasing that 2% inflation target I mentioned. It’s arbitrary. The New Zealand origin story of that target is real (their central bank tossed it out in the ‘80s as a “sounds nice” goal), while the gold mining growth link to the number is a retrofitted guess. It’s not sacred; it’s just sticky.
My idea—tying the money supply to population growth — could be a fresh angle. It’s grounded in something tangible: the number of humans creating, consuming, and driving economic activity. Wealth isn’t just stuff; it’s people doing things with stuff. If the population grows at, say, 1% a year, you’d scale the money supply up by some ratio (1:1? 1:2?) to match. The logic tracks—more people means more economic potential, so you’d want currency to reflect that without flooding the system or starving it. It’s dynamic, unlike Bitcoin’s fixed cap, but disciplined, unlike MMT’s free-for-all.
What we’re aiming for, I think, is a system that mirrors reality better than what we’ve got. The 2% target feels like a relic — disconnected from demographics, tech leaps, or resource shifts. Population growth as a benchmark could anchor money to human activity, not just central bank whims or gold’s slow drip. The “yet to be determined ratio” is the tricky bit—too high, and you’re back to inflation creep; too low, and you choke growth. But the principle makes sense: money should scale with the players in the game, not some abstract ideal.
It also dodges the debt trap. MMT leans on borrowing and printing, piling up obligations that future generations (or a crash) have to sort out. Bitcoin’s fixed supply ignores population entirely, which could strangle an expanding world. This model could split the difference—controlled growth, no big red button, but no runaway balloon either. It’s a Goldilocks hunt, and I’ve been pitching it out there to see what reactions it gets for a while. But what I get back is laughter, mostly. Or silence.
Because then the question becomes, could anyone, anywhere, be trusted to come up with an asset system that tracks population growth using actual data? Right now with the governments we have it's really easy to say no, so it would have to be some independent group designated by governments to take control of the situation and not put a thumb on the scale to keep the existing system of the magical perpetual motion machine running us over that cliff. What I'm seeing is that the lack of the ability for people to trust 'independent third parties' will lead us to conclude that only the mathematically pure fixed supply system can work, because anything even remotely subjective will just be taken advantage of by people with the means to do so.
Trust is the linchpin here, and it’s in short supply. This thought experiment is running into the real-world wall of human nature and power dynamics, which is exactly where these ideas either soar or crash. Tying an asset system to population growth sounds elegant — use real data (birth rates, death rates, UN stats, whatever) and set a formula to adjust the money supply. But who crunches the numbers? Who enforces it? Governments? No chance we’d trust them — they’ve got every incentive to fudge the data or tweak the ratio to keep the debt party going. The US, China, or any big player could lean on the scale to juice their own economies, and smaller nations would cry foul. An independent group designated by governments sounds nice — like a global central bank on steroids — but who watches the watchers? Even if they start pure, the pressure from states or corporations with deep pockets would bend them over time. Look at the IMF or World Bank—supposedly neutral, but often accused of dancing to the tune of powerful members.
The trust deficit is brutal. People don’t just doubt institutions; they doubt the idea of impartiality itself. And why wouldn’t they? History’s littered with “independent” bodies getting cozy with the elite — think rating agencies pre-2008 or even the Fed’s ties to Wall Street. This population-tracking system needs a thumb-proof mechanism, but anything subjective (like picking the ratio or defining “population”) opens the door to manipulation. Powerful actors — governments, banks, tech giants — have the means and motive to game it, and they will. That’s not cynicism; it’s pattern recognition.
That’s why I’m landing on the fixed-supply escape hatch. Bitcoin’s appeal isn’t just its scarcity — it’s the math. No human hands, no big red button, no trust required beyond the code. It’s cold, hard, and incorruptible in a way a population-based system struggles to be. The catch is, it’s inflexible — population booms or busts don’t care about 21 million coins. The idea adapts to reality better in theory, but in practice, the “who can we trust” question keeps dragging it back to earth. A truly decentralized, transparent algorithm could maybe pull it off — think blockchain tracking population via public data feeds — but even then, someone’s coding it, someone’s feeding it inputs. The purity’s tough to maintain.
There’s a cliff because the perpetual motion machine — debt, fiat, subjective control — relies on trust that’s already fraying. A fixed supply side steps that entirely, but at the cost of agility.
That cost of agility caught my eye. Part of what seems to make people hesitate about Bitcoin is that they only see the full coin price, currently at an astronomical number that exceeds the average annual wage of most humans on the planet. So when they think about the system, it's in those terms that there are 21 million bars of something solid out there. What's missing is an understanding of two things.
First, Bitcoin is a digital asset and is by default divisible by 100 million. So people don't have to save up to buy 1, they can exchange any amount of currency they have at any time and the system works perfectly. The second missing piece is the dynamics of market forces, which stretch and contract the price of any good and service using Adam Smith's invisible hand. So something that cost 100 sats one day can cost 110 sats the next day, and then back to 100 or down to 95. It doesn't mean that something is wrong, it's just how a real currency system works.
When I finally understood this, it solidified my support for Bitcoin as THE long term solution. Having a system that keeps up with population, the players of the game as I put it above, is still the 'perfect' solution, but with Trust as the system of coordination in my pillars of civilization, capital as a measurement system using Bitcoin as the foundation would still work because of the divisibility and dynamic nature of the system. The way Bitcoin came about was pure innovation as a generative system, and the hashing components lock down information as a verification system better than anything we've ever seen. Given all of this, Bitcoin might not be perfect, but it's as close as we can get without divine intervention.
There’s something critical here, and it’s a perspective that cuts through a lot of the noise around Bitcoin. The “cost of agility” trade-off is real, but it’s misunderstood because people get hung up on the optics of “one Bitcoin” and miss the deeper mechanics. Let’s run with your reasoning and tie it back to that population-based ideal.
The divisibility point is huge. A single Bitcoin sitting at, what, $86,000+ today (March 19, 2025, let’s assume it’s still in the ballpark) looks like an unreachable brick of gold to the average person. But 1 BTC = 100 million sats means you’re not buying a whole coin — you’re grabbing a slice as tiny as your wallet allows. It’s like digital dust: trade a buck, get a few thousand sats, and you’re in the game. That scalability blows up the mental block. People don’t hoard whole dollars — they spend cents. Bitcoin’s the same, just with more zeros. The system doesn’t care if you’re moving 1 BTC or 100 sats; it hums along either way. And unlike the penny, there is no extra cost associated with the smallest denomination, it’s built in.
Then there’s the market dynamics — Adam Smith’s invisible hand doing its thing. Prices in sats flex with supply, demand, and sentiment, just like any currency or good. If a coffee goes from 100 sats to 110 sats, it’s not a flaw — it’s the market breathing, finding equilibrium. Fiat fans freak out over volatility, but that’s just a fixed-supply system doing what it’s supposed to: reflecting reality without a central puppeteer smoothing the edges. Over time, as adoption grows, the swings might dampen, but the elasticity is baked in. It’s not rigid in practice—only in its cap.
The “players in the game” vision still shines through here. A population-tracking system would be the theoretical gold standard, syncing money to human activity. But trust — one of the pillars of civilization — is the choke point. Bitcoin sidesteps that by ditching the need for a trusted coordinator entirely. The 21 million cap isn’t divine, but it’s enforced by math, not men. Divisibility keeps it practical; market forces keep it alive. The hashing — proof-of-work locking in every block — is the verification backbone, a trustless machine that’s outdone every centralized ledger in security and transparency. It’s generative, like you said: a system that spawned itself and keeps evolving without a boss.
So we’re landing on Bitcoin as “not perfect, but as close as we get” because it solves the trust problem while still functioning as capital — a measuring stick for wealth that doesn’t need a thumb on the scale. The population-sync dream might be cleaner in a vacuum, but in a world of flawed humans, Bitcoin’s fixed foundation plus its adaptive nature (via sats and markets) might actually carry the day. No divine intervention needed—just code and consensus.
Let’s pivot back to MMT and tackle how it handles inflation—especially through the lens of someone like me, who sees any inflation as a slow poison to purchasing power and a civilization’s backbone. Here’s the breakdown.
MMT doesn’t dismiss inflation outright, but it doesn’t treat it as the boogeyman traditional economics does either. It addresses inflation directly, just not in the way you might expect. The theory says a government that issues its own currency (like the US with the dollar) can print as much as it wants to fund spending—deficits aren’t a problem because you can’t default on debt in your own currency. Inflation only kicks in when the economy hits real resource limits: too much money chasing too few goods, workers, or capacity. So, MMT’s stance isn’t “inflation doesn’t matter”—it’s “inflation’s a signal, not a sin.” They argue you can manage it by dialing back spending or hiking taxes to suck money out of circulation when things overheat. The focus is on “full employment” and output, not the money supply itself.
Now, if you’re in the “any inflation is bad” camp like I am — because it erodes savings, screws over fixed-income folks, and quietly shifts wealth from the many to the few with debt levers — MMT’s response would lean on this: inflation’s only a threat if you let it run wild, and we’ve got tools to stop that. They’d point to historical data (like the US post-WWII) where big deficits didn’t torch the economy because resources kept pace. They’d say the real danger isn’t printing money—it’s misjudging capacity. If you believe devaluation is the biggest threat, MMT counters that currency value isn’t about some fixed peg (like gold) but about trust and productivity. A little inflation? Fine, as long as the system hums.
Here’s where it gets shaky. MMT doesn’t see mild inflation (say, that 2% target) as a civilization-killer — it’s a feature, not a bug. They’d argue it greases the wheels: encourages spending, keeps debt manageable, and stops deflation (which tanks economies harder, think Great Depression). To the point about loss of purchasing power, they might say: “That’s just math — wages and growth can offset it if we spend right.” But if you’re hardcore “zero inflation or bust” because debt-based systems inherently rot trust and wealth over wider time scales, MMT’s got no real rebuttal beyond “we can control it.” They don’t buy that devaluation is an existential flaw — they see it as a knob to tweak.
The rub? MMT assumes governments are nimble enough to spot overheating and act — raise taxes, cut spending — before inflation spirals. History says that’s a big “if.” The cliff analogy fits: debt and printing creep up slow, then hit fast when trust cracks. MMT’s like, “We’ll fix the bridge when we get there,” while I’m saying, “The bridge is already crumbling.” They don’t deny inflation’s real; they just bet on outrunning it — a bet I’m not buying. Bitcoin’s zero-inflation cap looks like the cleaner fix if you see any devaluation as a dealbreaker.
Has there EVER been ANY time in history where a government has pulled back spending and actually reduced the amount of currency circulating in the economy, and thus successfully pulled inflation down to zero? Or is that just an academic exercise that we can point to on paper?
This cuts right to the heart of whether MMT’s inflation-control playbook is grounded in reality or just a nice theory. Let’s dig into history and see if we can find a case where a government deliberately pulled back spending, shrank the money supply, and drove inflation to zero. Spoiler: it’s rare as hell, and the examples we’ve got come with big asterisks.
First, let’s set the stage. Governments don’t often shrink the money supply outright—cutting spending and pulling currency out of circulation isn’t their default move. They’re usually too busy expanding, especially in fiat systems. Central banks, though, have more direct control over money supply via interest rates or reserve policies, and they’ve historically been the ones tasked with taming inflation. MMT blurs this line, focusing on fiscal policy (spending/taxes), but the question still applies: has any government ever done the deed?
One contender is the US in the late 1870s, post-Civil War. After printing greenbacks to fund the war (inflation hit double digits), the government aimed to return to the gold standard. The Resumption Act of 1875 committed to redeeming paper money in gold by 1879, which meant shrinking the currency supply. Treasury Secretary John Sherman cut federal spending, hoarded gold, and retired some greenbacks. Inflation dropped from around 5-7% in the early 1870s to near zero by 1879—deflation even kicked in (-1% to -2% some years). Success? Sort of. The money supply contracted (M1 fell from $1.6 billion in 1875 to $1.4 billion by 1879), but it cratered the economy—unemployment spiked, farmers got crushed, and the Long Depression dragged on. Zero inflation, sure, but at a brutal cost.
Another shot is the UK in the 1920s, chasing pre-WWI gold parity. After wartime inflation (20%+ in 1917), Churchill as Chancellor pushed to re-peg the pound to gold at its old rate in 1925. Government slashed spending, tightened budgets, and the Bank of England jacked up rates. Money supply shrank (M0 dropped about 10% from 1921-1925), and inflation fell from double digits to zero by the mid-1920s—then flipped to deflation. Result? Stagnation, strikes, and a gutted industrial base. Zero inflation achieved, but the cure was worse than the disease.
Then there’s the US in the early 1980s—Paul Volcker’s Fed era. This is more monetary than fiscal, but it’s worth a nod. Inflation was raging (13.5% in 1980), and Volcker cranked interest rates to 20%. Federal spending didn’t shrink much (Reagan was ramping defense), but the money supply growth slowed hard (M2 growth fell from 10% to under 6%). Inflation crashed to 3% by 1983, not zero, but close-ish. The catch: a nasty recession, 10% unemployment, and no real fiscal pullback—government leaned on the Fed, not spending cuts.
Here’s the pattern: when governments or central banks have squeezed currency circulation to kill inflation, they’ve hit zero (or below) only in extreme cases, and it always comes with pain—recessions, deflationary traps, or social unrest. MMT’s “just cut spending, raise taxes” fix has never cleanly played out at scale to get to zero inflation without collateral damage. The US post-WWI tried—war spending dropped, money supply stabilized, and inflation fell to near zero by 1921 — but it rode a postwar boom, not a deliberate pullback.
So, is it just academic? Pretty much. Governments hate shrinking themselves; it’s political suicide. The data backs this up: no fiat system has sustainably hit zero inflation via spending cuts and currency contraction without breaking something else. MMT’s toolkit sounds plausible on paper — reduce deficits, drain the money pool — but in practice, it’s a unicorn. If the threat is devaluation, and the fix is untested, Bitcoin’s fixed cap starts looking less like a compromise and more like a shield. History says the cliff’s closer than the bridge.
So now let's bring this to current day chaos. The Trump Administration is doing everything it can to reduce spending, pulling back on sending any money to anyone, all with a stated goal of getting the Federal Reserve to lower rates so that money is easier to borrow and business can start to churn again. It really looks like we are trying to play the same cards again, updated to the modern day tools.
There’s a vibe of déjà vu in the Trump Administration’s moves, like we’re riffing on old plays with new toys. Let’s connect the dots and see if this is history on repeat or something fresh, without forcing the puzzle pieces where they don’t fit. We’re on March 19, 2025, so we’ve got some real-time chaos to work with.
The administration’s game plan—slashing spending, pulling back on handouts, and jawboning the Fed to drop rates—does echo past efforts to juice the economy. Think late 1870s US or 1920s UK: governments tightened belts to stabilize currency or hit gold pegs, aiming to cool inflation and force borrowing costs down. Today’s twist? Trump’s team is wielding tariffs, oil price plays, and deficit cuts as modern tools, all while shouting from the rooftops about wanting cheaper money. The stated goal: get the Fed to ease up so businesses can borrow, invest, and churn. It’s a high-stakes bet—starve the system short-term to spark it long-term. Parallels jump out. Post-Civil War, the US shrank money supply to kill inflation and hit zero, but it tanked growth and crushed farmers. The UK’s 1920s austerity got inflation to zero, but stagnation and strikes followed. Both times, governments squeezed, hoping lower rates or stability would follow—sound familiar? Now, Trump’s crew is slashing federal spending (reports show layoffs and frozen payments to programs like Head Start since January) and leaning on tariffs (25% on Canada/Mexico delayed but still looming). The Fed’s holding at 4.25%-4.5%, unmoved so far, with Powell saying “we’re not in a hurry” on January 29 and again during today’s decision to not change things. Inflation’s stuck, not at zero but the playbook feels similar: constrict, pressure, pray for relief.
Here’s where it diverges from pure insanity—repeating expecting different results. Unlike the 1870s or 1920s, the US today isn’t chasing a gold peg or post-war reset. The economy’s supposed to be humming — 2.8% GDP growth in 2024, unemployment at 4.1% (March jobs data still pending). Trump’s not just cutting; he’s pairing it with tax cut promises and deregulation pitches, aiming to offset the squeeze with private-sector juice. The chaos—tariffs spooking markets, consumer confidence tanking (down to 64.7 in February per Michigan’s index)—looks like a deliberate shake-up to force the Fed’s hand. Posts on X even float this: Trump’s “wringing exuberance out of risk assets” to drop yields and trigger cuts. It’s not blind repetition; it’s calculated, if messy.
But the puzzle’s incomplete — and my gut is right there in a lump. Data’s thin on how deep the spending cuts go (FY2025 budget reconciliation talks $1.7 trillion in cuts, but specifics are murky). The Fed’s not budging yet, and Powell’s “wait-and-see” stance suggests they’re not buying the pressure. Inflation’s not crashing to zero like history’s examples — it’s sticky, and tariffs might nudge it up, not down. Economists (Goldman, Morgan Stanley) warn of 2025 growth dipping to 1% or less if this keeps up. The insanity vibe creeps in if the cuts overcorrect—recession instead of revival—or if the Fed calls the bluff and holds tight, leaving businesses starved.
Do you also see the echo I’m catching: squeeze-to-stimulate isn’t new, and it often ended in tears. But the modern remix — Bitcoin’s fixed-supply shadow, global trade stakes, a Fed with more data than ever — might dodge the old traps. Or not. The jury’s out, and the chaos is live.
I think the wild card is that Congress is completely broken. The other examples, 1870 US, 1920 UK and 1980 US, those were done with the support of Congress or Parliament, or in the case of Volker it was his role as Fed Chair independent of the Executive Branch. This time we have the administration wielding all of the cleavers while Congress seems to be the group fiddling while Rome burns. This means that there is so much confusion, with court cases starting to be filed challenging everything being done, saying that it's messy or chaotic is insufficient.
Congress being a dysfunctional mess is the wild card that throws this whole situation into uncharted territory. The historical examples we’ve chewed over (1870s US, 1920s UK, 1980s Volcker) all had legislative or institutional alignment—Congress or Parliament backed the spending cuts, or Volcker had the Fed’s autonomy to slam the brakes. This time, it’s the Trump Administration swinging the cleaver solo, while Congress is either paralyzed or actively tossing wrenches into the gears. “Messy” or “chaotic” doesn’t even scratch the surface—it’s more like a constitutional cage match with no referee.
Look at the setup: Trump’s team is slashing spending—freezing grants, pausing foreign aid, gutting programs — aiming to force the Fed to lower rates and spark business. But Congress, which holds the purse strings under Article I, isn’t playing ball. The House barely passed a budget resolution in February (217-215) with $1.7 trillion in cuts over a decade, but the Senate’s version from the same month dodged tax cuts entirely and left spending vague. Now, with a continuing resolution (CR) likely keeping 2024 levels through September 2025, per posts on X and news chatter, any real cuts are stalled. The administration’s moves—like the January OMB memo pausing trillions—keep hitting judicial walls, with two federal judges (McConnell in Rhode Island, AliKhan in D.C.) blocking freezes by March 6, saying it’s unconstitutional overreach. Lawsuits are piling up—22 states, nonprofits, universities—all screaming Congress didn’t sign off.
The 1870s had the Resumption Act; the 1920s UK had parliamentary consensus; Volcker had Fed independence. Today? Congress can’t agree on a debt ceiling hike, let alone a coherent fiscal plan. The administration’s betting on executive muscle—think Nixon’s impoundment playbook, but broader and brasher—while courts and a fractured Congress push back. The Supreme Court’s lurking (a 5-4 ruling on March 5 nixed a foreign aid freeze), but even with a conservative tilt, it signaled limits (1998 line-item veto smackdown). Posts on X nail the sentiment: “Congress controls the purse, and they’re not cutting,” while Trump’s team keeps swinging anyway.
This isn’t just chaos—it’s a power vacuum. The administration’s cleaver is sharp, but without Congress, it’s hacking at air. Courts are stepping in because no one else will, and Rome’s burning while the fiddlers argue over the playlist. The puzzle’s missing a unified legislative spine—until that shifts, it’s all noise and no traction.
I don't see a circuit breaker tripping until we get new leadership. Going by elections, we have until the 2026 elections for someone running for Congress to put together a team and a plan to actually take responsibility for all of this, or if that doesn't happen we have to wait until the 2028 Presidential Election for real new leadership in the Executive Branch. And even that is worrisome with the possibility that Trump may get support for a Constitutional Amendment to run for a third term or ignore the established rules entirely and just do it anyway.
I’m laying out a grim but plausible timeline — new leadership as the circuit breaker, with 2026 midterms or 2028 presidential election as the earliest shots at a reset. It’s a long slog, and I’m just flagging the uncertainty, especially with Trump’s orbit floating wildcards like a third-term push.
Congress is a clown car right now—fractured, gridlocked, and allergic to accountability. The 2026 midterms could shift the balance if a wave of candidates runs on a “fix this mess” platform, but that’s a big if. Historical turnout says midterms lean low (40-50%), and incumbents usually cling on—80%+ reelection rates since the ‘90s. Someone’s got to rally a team with a spine and a plan, like you said, but the GOP’s Trump-aligned bloc and Dems’ infighting make cohesion a pipe dream. Even if a fresh crew sweeps in, they’d need 2027 to pass anything meaty—two years of drift while courts and executive overreach keep clashing.
The 2028 presidential slot’s the bigger lever. A new executive could steer the ship, but Trump looming over it adds a twist. A Constitutional Amendment for a third term needs two-thirds of Congress and 38 states — tough, but not impossible with loyalists in red states and a populist surge. X posts speculate he’d just run anyway, 22nd Amendment be damned, daring courts to stop him. Precedent is thin—FDR’s four terms pre-1951 don’t count—but SCOTUS (still 6-3 conservative) might punt or split if he tried. Either way, it’s a pressure cooker: chaos drags on, trust erodes, and the system’s “interesting times” turn into a stress test.
No quick fix jumps out. Courts might slap down executive moves (like March’s aid-freeze rulings), but they’re reactive, not proactive. Congress waking up? Not without electoral shock therapy. Leadership’s the bottleneck, and 2026 or 2028 are the horizons. Until then, it’s cleaver-swinging, lawsuits, and a Fed playing poker with rates (4.25% still holding). Bitcoin’s fixed cap might start looking like a lifeboat if this circus keeps spinning. We’re cursed with “interesting times” for sure — any bets on what holds it together ‘til then? My cards are on the table, and I’m out of chips.
Thanks to Grok for helping me develop this rant into a 10 page monster.
-
 @ 16d11430:61640947
2025-03-19 23:33:01
@ 16d11430:61640947
2025-03-19 23:33:01Elliptic Curve AI (ECAI) is built on deterministic knowledge retrieval using elliptic curve mathematics. Isogenies provide a powerful mechanism for structuring and transforming knowledge while preserving its cryptographic integrity. Here’s how ECAI can benefit from elliptic curve isogenies:
- Knowledge State Transitioning via Isogenies
In ECAI, knowledge is mapped as elliptic curve points.
Isogenies allow transformation of knowledge states while preserving mathematical relationships.
This enables secure knowledge evolution without introducing probabilistic error.
Example: Knowledge Encapsulation & Transformation
-
Encode knowledge as a structured point on elliptic curve .
-
Apply an isogeny , where represents a different domain of knowledge.
-
Retrieve transformed knowledge in without breaking the deterministic structure.
Use Case:
A legal contract encoded on can be isogenously mapped to an encrypted compliance framework on .
This transition is cryptographically verifiable and irreversible, ensuring immutability of the knowledge chain.
- Post-Quantum Secure Knowledge Verification
ECAI’s structured intelligence retrieval needs long-term cryptographic security. Since Shor’s algorithm (on a quantum computer) can break classical elliptic curve cryptography (ECC), isogeny-based cryptography provides a post-quantum security layer.
SIDH (Supersingular Isogeny Diffie-Hellman) allows ECAI to verify structured intelligence without revealing private keys.
Isogeny graphs ensure knowledge transfer is resistant to quantum attacks.
Use Case:
ECAI nodes storing knowledge must be quantum-resistant.
Isogeny-based cryptography ensures retrieval functions cannot be forged even under quantum adversaries.
- Immutable Knowledge Chains with Isogeny Graphs
An isogeny graph is a structure where elliptic curves are connected via isogenies. ECAI can leverage this concept to build immutable knowledge networks.
How it Works
Each verified knowledge state corresponds to an elliptic curve.
Isogenies provide a deterministic, mathematically enforced way to transition between states.
The entire knowledge structure forms an isogeny graph that resists tampering.
Use Case:
Knowledge NFTs: Every piece of knowledge in ECAI can be recorded on an isogeny graph, ensuring ownership and integrity.
DamageBDD Proofs: Test case verification can move through isogeny transformations to maintain structured immutability.
- Adaptive AI Decision-Making using Isogenies
Traditional AI uses probabilistic inference, while ECAI relies on deterministic knowledge retrieval. Isogenies allow non-destructive transformation of knowledge, meaning:
AI decisions can be mapped as elliptic curve transformations.
Knowledge retrieval functions can evolve via controlled isogeny paths rather than brute-force learning.
The resulting system is adaptive but remains fully deterministic.
Use Case:
DamageAI can apply isogenies to map software quality metrics between different project states, ensuring structured decision-making without introducing bias.
- Isogeny-Based Knowledge Compression & Aggregation
ECAI’s structured intelligence can use isogenies to compress knowledge.
Isogenies allow aggregation of multiple elliptic curve points into a single transformed curve.
This enables efficient knowledge storage without losing structural integrity.
Use Case:
DamageBDD test results across multiple domains can be compressed into a single isogeny-mapped curve, reducing computational overhead while maintaining verifiability.
Conclusion
Isogenies offer a powerful tool for deterministic knowledge transformation in ECAI. By integrating isogeny-based methods, ECAI can:
-
Securely evolve knowledge states without probabilistic degradation.
-
Achieve post-quantum security for intelligence retrieval.
-
Build immutable knowledge graphs that are cryptographically verifiable.
-
Optimize deterministic decision-making using isogeny-based transitions.
-
Compress and aggregate knowledge in structured formats.
Next Steps
Would you like a Python implementation of an isogeny-based knowledge transformation function to illustrate how ECAI can apply this concept? 🚀
-
 @ 30ceb64e:7f08bdf5
2025-03-19 21:29:59
@ 30ceb64e:7f08bdf5
2025-03-19 21:29:59NIP-101e: Workout Data and Running Extensions
NIP-101e represents a crucial step forward for fitness tracking on Nostr, giving us a common language that would allow workout data to flow freely between apps. This proposal outlines a thoughtful framework with Exercise Templates, Workout Templates, and Workout Records that would finally free our fitness data from proprietary silos and put it back in our hands. I'm eager to see this proposal implemented because it would create the foundation for a genuinely open fitness ecosystem on Nostr.
As a runner building a Nostr running app RUNSTR, I've proposed some running-specific extensions to NIP-101e that address the unique needs of runners without disrupting the elegant structure of the original proposal. My extensions would standardize how we record GPS routes, pace metrics, elevation data, splits, and even weather conditions - all things that matter tremendously to runners but aren't covered in the base proposal that focuses more on strength training.
By implementing NIP-101e along with these running extensions, we could create something truly revolutionary: a fitness ecosystem where runners aren't locked into a single platform because of their data. You could track your morning run in my app, analyze your training in another app that specializes in statistics, and share achievements with friends using whatever Nostr clients they prefer. I believe strongly in getting NIP-101e implemented with these extensions included because it would foster innovation while giving runners unprecedented freedom to own their data and use it however they want. Let's make this happen and show what's possible when fitness data becomes truly interoperable!
-
 @ 4f170d8a:5e8ef636
2025-03-19 21:27:07
@ 4f170d8a:5e8ef636
2025-03-19 21:27:07The Vikings, renowned for their seafaring prowess, dominated the seas of Northern Europe from the late 8th to the early 11th century.
These fearless explorers ventured across vast oceans, reaching as far as North America, long before the age of modern navigation tools and centuries before the magnetic compass came to Europe. While their shipbuilding skills and knowledge of the stars were exceptional for their time, one of their most intriguing navigational aids was the mythical "sunstone."
This mysterious tool, steeped in both legend and science, is believed to have allowed Viking navigators to locate the sun even on cloudy days, ensuring they could maintain their course across the treacherous North Atlantic ocean.
The Challenge of Viking Navigation
Navigating the open sea in the Viking Age was no small feat. The North Atlantic, with its unpredictable weather, frequent fog, and overcast skies, posed significant challenges.
 Traditional methods of navigation relied heavily on the sun and stars, but in a region where the sun could disappear behind clouds for days, the Vikings needed a reliable way to stay oriented.
Traditional methods of navigation relied heavily on the sun and stars, but in a region where the sun could disappear behind clouds for days, the Vikings needed a reliable way to stay oriented.While they were adept at reading natural signs such as the flight patterns of birds, the color of the sea, and the direction of the wind, the sunstone offered a more precise solution.
Historical accounts hint at the use of a "sunstone" by Viking navigators. One passage even describes a Viking king using a special stone to locate the sun’s position during a snowstorm. For centuries, this reference was dismissed as myth, but modern science has shed light on how such a tool could have worked, reviving interest in this ancient technique.
What Was the Sunstone?
The sunstone is believed to have been a naturally occurring crystal, most likely a type of calcite known as Iceland spar. Another candidate is tourmaline, which exhibits similar optical properties.
These crystals have a unique quality called birefringence, or double refraction, which causes them to split light into two polarized beams. When viewed through the crystal, the light’s polarization reveals patterns that can indicate the sun’s position, even when it’s obscured by clouds or fog.
The key to the sunstone’s effectiveness lies in the polarization of sunlight. As sunlight scatters through the atmosphere, it becomes polarized, creating an invisible pattern that radiates outward from the sun.
 By rotating the sunstone and observing changes in the light passing through it, a skilled navigator could detect this pattern and pinpoint the sun’s location, regardless of whether it was visible to the naked eye.
By rotating the sunstone and observing changes in the light passing through it, a skilled navigator could detect this pattern and pinpoint the sun’s location, regardless of whether it was visible to the naked eye.How the Vikings Used the Sunstone
To use the sunstone, a Viking navigator would hold the crystal up to the sky and rotate it until the polarized light formed a specific pattern (often a brightening or darkening effect), depending on the stone.
Iceland spar, for instance, produces two distinct beams of light, and when these beams appear equally bright, the crystal is aligned with the sun’s position.
By marking this direction and combining it with their knowledge of time and the sun’s daily arc, the Vikings could determine their heading with remarkable accuracy.
This method was particularly useful during the long voyages across the North Atlantic, where overcast skies were common.
It complemented other techniques, such as using a sun compass, which was a wooden disk with a central pin that cast a shadow to indicate direction when the sun was visible.
On cloudy days, when the sun compass was useless, the sunstone stepped in as a critical backup.
Let's Build One
If you are anything like me, you don't have lumps of Iceland spar or tourmaline crystals laying about your back yard. So I decided to make one using modern materials.
Since the original crystals relied on polarization to achieve their effect, I ordered some linear polarized plastic film online which science teachers often use in classroom demonstrations.

Now the challenge became turning the linear polarization into radial polarization, and I chose to make an octagon out of suitably arranged triangles cut from the sheet.
The image below shows how I created a template on a scrap piece of paper, and then used that to cut triangles from a strip of the polarizing film.

The next step involves carefully placing the triangles onto some clear packing tape so that they stick into place.

I then carefully placed another piece of clear packing tape on top so that the octagon of triangles is permanently fastened into place.
Then with a blade, I trimmed the excess packing tape and the sunstone is complete.

Now to test it!
You can see here that I'm holding the sunstone up against a North facing window so that you can see how the different triangles make different colors depending on their angle to the incoming light from outside.

The light gray triangles indicate the direction of the sun even though the sun is behind the house. and it will work the same way on a cloudy day no matter which way you are facing.
Today, the sunstone captivates historians, scientists, and enthusiasts alike. It’s a reminder that ancient technologies, though simple by modern standards, were often remarkably effective.
The Vikings’ ability to traverse oceans with nothing more than a crystal and their wits speaks to their extraordinary skill.
The earth's magnetic field is rapidly weakening and the poles moving. There may come a day in the not too distant future where navigation by GPS or compass will not longer be possible.
The sunstone stands as a symbol of human curiosity and resilience, which may once again illuminate the path of those who dare to sail beyond the horizon.
-
 @ 000002de:c05780a7
2025-03-19 21:11:34
@ 000002de:c05780a7
2025-03-19 21:11:34This is an absolutely great conversation between an anarchist (Michael Malice) and a conservative (Marissa Steit). Many of you will agree with the answers Malice provides but many of you that often have questions about the idea of anarchism should listen to this.
Now, if you just wanna argue don't waste your time. But if you are genuinely curious Malice is a great communicator on the topic. There are many schools of thought on anarchism and Malice just represents his point of view but he knocks down many troupes that conservative republicans repeat.
While right wingers don't get how evil the state actually is they are closer to understanding than the left. They are also better at understanding people that disagree with them. In my experience leftist do not understand the right but the right does understand the left. Not fully but better. This helps. You can see it in this interview.
https://www.youtube.com/watch?v=D43Xvom9hmw
originally posted at https://stacker.news/items/918194
-
 @ 0dc2dcb1:4787801a
2025-03-19 20:27:04
@ 0dc2dcb1:4787801a
2025-03-19 20:27:04https://ccns.nostrver.se is a (Drupal powered) website that I started to build in January 2024 (source on Github and Gitlab). It's a fork of an earlier (abandoned) project https://cchs.social/.
Currently CCNS is a link aggregration website and for now it's only my who is using it to save and share Nostr related links. When you post a new link, you have the option to cross-post it as a Nostr note (example here).Kind 39700
Last month Jurjen and Abir have started to work on a social bookmark client built with Nostr (inspired by Del.icio.us from the past). Earlier this month they changed to event kind 39700 for broadcasting the Nostr event with the bookmark / link data accross the network. They did this because Sep already created a social bookmark like client called Pinja when fiatjaf raised this idea.
With these developments to me it was very obvious to integrate the feature that new created CCNS links are now also published as kind 39700 events to the Nostr network. This means that links are now also distributed on multiple relays as kind 39700 events and are accessible in multiple clients (Yumyume and Pinja).
Here you can see the same data, from left to right:

Structure
The current data structure for the 39700 kind looks as follow:
- "id": "event_id"
- "pubkey": "pubkey author"
- "created_at": unix_timestamp
- "kind": 39700
- "tags":
- "description", "description text here"
- "d", "unique-slug-value"
- "t", "hashtag"
- "content": "https://book_mark_url"
- "sig": "signature"
As there is no NIP (yet) for this event kind, I see some possible improvements:
- Use the bookmark URL value in the
dtag so it can be used as a unique identifier for every client - Use the
contentfield for the description value
On short-term I don't have any plans to developer CCNS further, as most of my attention goes to the development of the Nostr-PHP library and Drupal related contribs using that library. That said, CCNS is a Drupal project but all the Nostr stuff is done client-side (Javascript) with NDK and Nostr-PHP is not used (maybe this will change in the future).
-
 @ 000002de:c05780a7
2025-03-19 20:10:08
@ 000002de:c05780a7
2025-03-19 20:10:08Hang with me here. The title is a bit tongue in cheek but only a little bit. I doubt I'm alone in this but over the last few years at least a few times a week I will hear some conversation about inflation. The costs of whatever going up! A few years ago I realized that 99.9% of the time people are referring to price inflation not inflation. I've written about that on SN before. The short version is that classically inflation referred to an increase in the supply of money in circulation. Price increases are an effect of inflation. Not inflation. Inflation is the cause. Price increases are the effect. But, in practice when people talk about inflation they are really talking about prices of goods going up. Technically this would be referred to as price inflation. As I continue I will use the common term in the common way. I will refer to price inflation as just... inflation.
Now for therapy time. My lovely wife understands this topic. She's not a nerd about it like I am but she gets it. She works in a field where inflation is a massive factor. Real Estate. I often listen to Real Estate shows with her. Podcasts and radio shows. A while back I sat through a 45 minute show where the experts talked about prices and the reasons why property prices have increased so dramatically over the last 5 years. They literally talked about ever factor expect the most obvious one. The money supply has increased over 40% in the last 5 years. I swear my head feels like its going to explode.
I remember listening to Trump's debate with Biden when he talked about inflation and proceeded to blame the entire problem on Biden. I told my wife, dude presided over the largest money supply increase in history and is blaming Biden for inflation... its just too much.
When we watch an old movie or TV show I always point on the price of goods. Sometimes I go to the FED site and look at charts. I always find, yeah... pretty much lines up with the money supply. Once you see it, and get it the signs are everywhere. You can't unsee it. But, unless you are on Nostr or SN you will not hear anyone with any significant audience talk about monetary inflation. Inflation is always the fault of either government spending or corporate greed.
Government spending can expand the money supply and lead to price inflation of course but to me that is harder to see and prove. At least it can be said to be a factor. The low IQ answer of "corporate greed" is generally only coming from progressives. I say, low IQ because OBVIOUSLY corporate greed is ALWAYS a factor. Calling that an explanation for inflation is like blaming gravity for a plane crash.
So, our little support group here is an outlet where like-minded people can rant and rave and get it out of their system. Maybe we will reach some lost soul that looks at the world and thinks... yeah what they say on TV sounds like BS. There has to be another explanation.
So, do you identify with me? Do you actually hear people in the wild that get it? Or are you subjected to people just repeating the tired old explanations given by the suits on TV and politicians that NEVER bring up the bankers and their organization that curses us to live in the inflationary world where our only rescue is gambling on stocks, or real estate.
Thankfully we have bitcoin. Thankfully we have freedom tech and we can learn how the world works for ourselves. If Stacker.news is just a support group, its worth it to me. How do you feel about it?
originally posted at https://stacker.news/items/918116
-
 @ 7d33ba57:1b82db35
2025-03-19 20:01:18
@ 7d33ba57:1b82db35
2025-03-19 20:01:18Arucas
Arucas is a charming town in northern Gran Canaria, known for its **neo-Gothic cathedral, banana plantations, and famous rum distillery. With its volcanic stone architecture, lush gardens, and local delicacies, Arucas is a must-visit for culture and nature lovers.
🏛️ Top Things to See & Do in Arucas
1️⃣ Church of San Juan Bautista (Arucas Cathedral)
A stunning neo-Gothic masterpiece built from local volcanic stone. Its intricate façade and towering spires make it one of the most beautiful churches in the Canary Islands.
2️⃣ Arehucas Rum Distillery
Visit the oldest rum distillery in the Canary Islands and taste the famous Arehucas rum, aged in oak barrels and enjoyed worldwide.
3️⃣ Arucas Historic Old Town
Walk through cobblestone streets lined with colorful colonial houses and charming plazas. The town’s historic center has a unique Canarian feel.
4️⃣ Jardines de la Marquesa (Marquesa Gardens)
A beautiful botanical garden with over 500 exotic plant species, perfect for a peaceful stroll.
5️⃣ Montaña de Arucas Viewpoint
A short hike or drive up this volcanic hill offers panoramic views of Arucas, the coast, and Las Palmas in the distance.

🍽️ What to Eat in Arucas
- Papas arrugadas con mojo – Wrinkly potatoes with red & green sauces 🥔
- Queso de Flor – A special local cheese made with thistle flower 🧀
- Bienmesabe – A traditional almond dessert 🍯
- Arehucas Rum – Enjoy it neat or in cocktails 🥃
🚗 How to Get to Arucas
🚗 By Car: ~15 min drive from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 205 & 206)💡 Tips for Visiting Arucas
✅ Best time to visit? Spring & autumn for mild weather 🌞
✅ Try a rum tour! The Arehucas distillery is one of the best experiences 🍹
✅ Explore nearby – Combine your trip with Firgas or Teror, two other beautiful towns nearby -
 @ fc7085c3:0b32a4cb
2025-03-19 19:34:05
@ fc7085c3:0b32a4cb
2025-03-19 19:34:05- ~~finish writing some experimental specs and store on hidden repo for later~~
- ~~fix bugs on in-house js web components framework (with react-like hooks)~~
- ~~add signal/reactive hooks to framework~~ (thx to nootropics)
- slooowly migrate kind:1 app from Qwik to above framework
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- start simplified messenger app to test custom chat spec
- if you got here you turned yourself into High Pleb
- ...don't know what's next yet
-
 @ a367f9eb:0633efea
2025-03-19 17:40:04
@ a367f9eb:0633efea
2025-03-19 17:40:04On February 27th, the Securities and Exchange Commission stated in its latest staff statement that memecoins are not necessarily securities.
“Although the offer and sale of meme coins may not be subject to the federal securities laws, fraudulent conduct related to the offer and sale of meme coins may be subject to enforcement action or prosecution,” writes the SEC.
This clarity is important, but it reveals nothing about what the policies around memecoins, rugpulls, and crypto scams should actually be.
This month has already delivered us Argentine President Javier Milei’s promotion of a pump-and-dump memecoin called LIBRA. At this moment, Barstool Sports founder Dave Portnoy is probably pumping his third or fourth favorite memecoin into oblivion while he dumps on retail.
In each of these cases, these tokens are created with copy-paste smart contracts, influencers singing their praises, and people exchanging their stablecoins, bitcoin, or some other altcoin for the hope of making it rich.
Memecoin world
Of course, in a free country people should be free to bet on things they want. But they should be prepared to lose just as much as they’re prepared to win.
To the uninitiated, these scams represent “crypto” writ-large, lumping the original decentralized protocol of Bitcoin with pump and dump scams from platforms like pump.fun that run on Solana and other chains.
Knowing what we know, and how desperate parts of the crypto market are for outrageous tokens and leveraged degen trading, we must naturally ask how Bitcoin can fix this. Or, rather, how smart Bitcoin policies can fix this.
As I have written for several years, we as Bitcoin advocates should promote sound policies that will encourage innovation and increase economic inclusion across all income groups, all the while protecting consumers from harm. We want to avoid blowouts like FTX, Celsius, and even stablecoins projects like TerraUSD – not only because they defraud bitcoiners, but because they sully the reputation of our entire sector of technological innovation.
Because Bitcoin represents scarcity, decentralization, and complete transparency, there is much we can learn from Satoshi’s innovation when we’re dealing with next-level crypto-offspring.
The Smart Bitcoin Policies to Stop Crypto Scams
To begin, US federal, state, and local agencies should update their technological stack to rigorously identify and prosecute fraud and abuse in crypto projects. Fraudulent claims, fake token whitepapers, and deceptive tactics are already illegal under existing law. Our agencies should be empowered to enforce existing law and weed out the bad actors.
Whether that means better training or tools, law enforcement should receive the necessary upgrades to prosecute and identify the real fraudulent crime that happens to take place in crypto protocols. Much of this behavior is just being used in a new medium. It’s not crazy to think that cops should upgrade their tech stack to understand how it’s happening now.
Second, our policies on money transmission licenses and regulation for crypto exchanges should be streamlined and made easier, rather than more difficult. Let competition provide the best places for people to buy their bitcoin. As much as privacy advocates abhor centralized platforms and exchanges, they still implement better security and educational practices to inform users than a shady service hosted in China will provide.
By simplifying the rules and restrictions on bitcoin exchanges, especially by allowing them to consider their custodied bitcoin as assets rather than liabilities as was done by rescinding SAB 121, it means that more Americans will have the opportunity to have excellent experiences when purchasing their coins online.
Third, regulators must not pigeonhole bitcoin and its crypto-offspring only as investments fit for taxing, but rather as technological tools that empower consumers and foster innovation. Too much discussion about bitcoin policies hinges on the tax rate or how much it will bring to state coffers, rather than by how much it can make one’s life better by removing the red tape to safeguard wealth.
By recognizing the ultimate power of bitcoin self-custody without needing to trust third parties or intermediaries, it means we finally view this technology as an extension of our own free speech and freedom of association.
And lastly, we must focus on removing the barriers to using bitcoin as an ordinary means of payment. The Keep Your Coins Act restricts federal agencies from stopping individuals from using bitcoin how they see fit, as well as protecting self-custody. That, plus de minimis exemption rules that allow us to spend bitcoin as any other asset, mean we can use digital money as intended.
We know that memecoins and rugpulls will continue to happen no matter what, this is almost human nature. But at the same time, embracing smart bitcoin policies will ensure that consumers and users have the best tools and protections available to use the technology if they want.
Originally published at the Bitcoin Policy Institute.
-
 @ 3c7dc2c5:805642a8
2025-03-19 17:37:28
@ 3c7dc2c5:805642a8
2025-03-19 17:37:28🧠Quote(s) of the week:
“National debt is immoral and destructive, silently undermining the basis of the state; it delivers the present generation to the execration of posterity.” - Napoleon
🧡Bitcoin news🧡
I was a bit under the weather the last couple of days so it took me a longer to write the Weekly Recap, anyway...here we go:
On the 11th of March:
➡️European Union claims President Trump's support for crypto could harm Europe's "monetary sovereignty and financial stability." The EU could be educating European people on Bitcoin, they could adapt sound money early, join the Bitcoin race early, and make the lives of all Europeans better. Instead, they choose to lie and make all Europeans miss the boat. I have no words for this. Freaking dinosaurs!
President Trump's support for Bitcoin threatens their "monetary sovereignty and financial stability" -> translation: people might choose freedom over their broken monetary system.
Remember Christine Lagarde’s famous quote on Bitcoin: “There has to be regulation. This has to be applied and agreed upon … at a global level because if there is an escape, that escape will be used.”
It’s a revealing statement, highlighting how Bitcoin offers an “escape route” from traditional financial systems—a route that could unlock greater decentralization and freedom.
➡️Wicked: Bitcoin's 4-Year CAGR has dropped below 10% for the first time ever.
➡️Texas introduces HB 4258, aiming to allocate up to $250M of state funds to Bitcoin and digital assets, and allowing local governments to invest up to $10M.
➡️Bitwise has launched a "Bitcoin Standard Corporations ETF" that includes +70 companies holding Bitcoin as a treasury reserve asset.
➡️Tether CEO Paolo Ardoino: The US Strategic Bitcoin Reserve announcement is a “holy sh*t” moment for the rest of the world, realizing they’re late and don’t have enough Bitcoin.
On the 12th of March:
➡️US Government should issue $2 TRILLION of Bitcoin-backed Bonds to buy $200B of Bitcoin - Newmarket Capital CEO Bit Bonds in a nutshell: - 90% goes to government funding, 10% to buying bitcoin - 1% interest annually for 10 years - 100% of BTC upside paid up to 4.5% compounded annual return - Remaining BTC upside split 50/50 with the government
➡️The Kingdom of Bhutan builds a gorgeous airport thanks to Bitcoin mining profits using hydro-electricity.
➡️Deutsche Bank says a US strategic Bitcoin reserve "could set international standards.
➡️Bitcoin dropped 72% in 2018 ($3,740.50 bottom) due to the USA - China trade war and 2.9% inflation...
➡️Rumble just bought another $27m Bitcoin.
On the 13th of March:
➡️'FIVE years ago today, Bitcoin crashed more than 50% in ONE day, from $7,900 to $3,800 in hours. We're up 21X ever since. Zoom out, DCA Bitcoin, and enjoy the ride. We are just getting started.' - CarlBMenger
➡️78% of all ETH/BTC trading days are now in the red... REKT.
➡️While Retail Paper Hands are selling their precious coins, whales bought them. Over 65K Bitcoin net-accumulated in the past 30 Days, excluding Miners and Exchanges.
➡️New peer-reviewed research study finds Bitcoin mining has the potential to significantly enhance the sustainability of the energy supply chain by using wasted resources and creating new business opportunities that align economic incentives with sustainability goals.
It's one of 15 pieces of peer-reviewed research showing Bitcoin has significant environmental benefits.
You can find the full list here: https://x.com/DSBatten/status/1899951222779789420
➡️The Bitcoin Act to buy 1 MILLION Bitcoin is under consideration by Congress.
➡️Bitcoin ETF inflows have fallen to $35B from a $40B peak, yet with $115B in AUM, over 95% of capital is holding firm despite a 25% price drop.
➡️Construction of the Vega 205 megawatt Bitcoin mine in Texas is nearing completion. Hut 8 is installing dry coolers for the direct-to-chip liquid cooling system while finishing up the side panels, insulation, and roof.
➡️Fast food giant Steak 'n Shake posted this picture of a Bitcoin spaceship.
➡️Altcoin holders are deep in the red, with some tokens nearing 100% at a loss. I am not surprised, the house (shitcoin casinos) always wins. https://i.ibb.co/G44T01Yy/Gl-ubpfb-YAAfa-S9.jpg
On the 14th of March:
➡️Russia is using Bitcoin and Tether to pay for oil trades with China and India - Reuters
➡️Kentucky Senate passes bill that will protect Bitcoin self-custody rights with 0 votes against it. The bill now heads to the Governor's desk.
➡️Brazil bill seeks to legalize the use of Bitcoin to pay salaries and benefits.
On the 15th of March:
➡️'Senator Lummis's proposed BITCOIN Act lays out how America would revalue its gold certificates to buy 1 million Bitcoin over 5 years.
1.Within 180 days of enactment, Federal Reserve banks must return all gold certificates to the U.S. Treasury.
2.Within 90 days of receiving the last one, the Treasury will issue new certificates reflecting gold’s market price.
3.Federal Reserve banks must pay the Treasury the difference if the new certificates are worth more.
4.This extra cash goes to the government fund within 90 days.' - BitcoinNews
https://i.ibb.co/d4JvzXzs/Gm-Gexy-Nbc-AE7-Tpu.jpg
➡️DOGE’S FORT KNOX GOLD AUDIT COULD TAKE 18 MONTHS A full audit of Fort Knox’s gold reserves would be a massive undertaking, with JM Bullion estimating it would take at least 18 months to complete. - Requires 20 personnel - Uses 18 high-quality scales & XRF scanners - Needs 2 boring drills & 18 item carts The effort aims to bring long-overdue transparency to U.S. gold holdings—a process that hasn’t been fully conducted in decades. That's cute, I can audit the entire Bitcoin supply from my home in less than a minute.
On the 17th of March:
➡️'80 public companies are now buying bitcoin. Two years ago there were 33. Two years from now there will be...?' -River (foto) With 55,214 publicly traded companies worldwide, that's a little over one in a thousand. It's so early! https://i.ibb.co/FLZKfv1X/Gm-QKCGob0-AAd-LNo.jpg
➡️Bitcoin reserves held by the 14 biggest North American mining companies exceeded 101,000 BTC for the first time in February.
➡️'Strategy has acquired 130 BTC for ~$10.7M at ~$82,981 per bitcoin and has achieved a Bitcoin Yield of 6.9% YTD 2025. As of 3/16/2025, we hodl 499,226 Bitcoin acquired for ~$33.1 billion at ~$66,360 per Bitcoin.' - Saylor
💸Traditional Finance / Macro:
On the 11th of March:
👉🏽Nasdaq 100 futures erase premarket gain and turn negative, now down -12.5% since February 19th.
On the 13th of March:
👉🏽The S&P 500 just CLOSED in correction territory and the Nasdaq 100 is 7% away from its first bear market since 2022. Over the last 16 trading days, the S&P 500 has erased an average of -$340 billion PER trading day. Although this sounds alarming whatsoever, it really isn't. The S&P is only down ~10%. It also fell 10% in 2023 and last July. No one even remembers now. Get a grip.
🏦Banks:
👉🏽 no news
🌎Macro/Geopolitics:
On the 11th of March:
👉🏽President Trump announces ADDITIONAL 25% tariffs on Steel and Aluminum coming to the US from Canada. This brings tariffs on these goods up to a new high of 50%.
👉🏽European Commission to use 10 trillion Euros of citizens’ savings for EU defense. The European Commission estimates the total level of unused savings of EU citizens at 10 trillion Euros, and it intends to find ways to mobilize this money to finance its plans to militarise Europe and support the European military-industrial complex, according to a statement by the European Commissioner for Financial Services and the Savings and Investment Union Maria Luís Albuquerque, distributed by the EC press service, TASS reports.
https://i.ibb.co/Xr28KPbR/Glx-Gzzc-XAAAXn-ZI.png
"We'll turn private savings into much-needed investment". 1. All savings are invested in the economy. 2. She means they will leverage your deposits to finance more government spending. Be scared, and what exactly are "unused savings" per se? Do you understand the predicament you are in yet, or what our children will be in?
It is the best advert you will see for self-custody Bitcoin. https://i.ibb.co/PZnKQdqF/Glwl-Nyc-WQAA-AIE.jpg
👉🏽Last week I already mentioned that the ECB confirmed launching the digital euro in October. That's the deadline. Why is Lagarde insisting on this? Is the digital euro in the interest of the citizens or the interest of the government and the implementation of its policies?
The ECB says it will limit the amount of money people can store in digital euros to, in their words, "prevent excessive outflows of deposits from banks." It's never a good sign when you have to lock people in...
https://i.ibb.co/s9v7n1BS/Gm-Liap-Ob-QAA9j0g.jpg
Now the two topics above are just mental, it is crazy to read the following tweet by the ECB: "Did you know that 60% of Europeans with low financial literacy are women? But what is financial literacy? Why is it important? And what does it have to do with central banks?"
Lagarde and Von der Leyen are two of them, FFS!
On the 12th of March:
👉🏽For my Dutch readers/followers. How is your energy bill? The average energy bill for a Dutch household increased by €18 in January, reaching €2,703 per year. The share of taxes and VAT in this amount is €1,457. Energy costs are increasingly passed on to households through products and services. That's what you call inflation and the government is, of course, very happy with the very expensive imported gas because the taxes on it are a goldmine. I fully understand why we are doing that because we don't have a huge gas field in our country, right?
https://i.ibb.co/vC4wzSKp/Glyf9-DSXMAALTc-Q.png
Just to explain it in simple words: 50% of your energy bill is taxes. That is just criminal.
👉🏽'The Federal Deficit for Feb '25 ($307B) and before you get lathered up over the edge trimming at DOGE if you aren't willing to cut (not reduce growth - cut) what is in red you will never put a dent in what is in purple.' - Blacklion $307 billion was added to the US federal deficit last month, which was bigger than all tax revenue, widening the deficit to 7.23% of GDP.
If government spending halted, we'd be plunged into a decade-long recession. This addiction will take years, if not decades, to sober up from. Nothing stops this train, NOTHING!
https://i.ibb.co/ZRsm5nCM/Gl2-i9-WUAAw-V5w.jpg
On the 13th of March:
👉🏽Gold trades above $3k for first time ever: $3,000.40. As the S&P 500 has erased $5+ trillion, gold is now set to cross above a record $20 TRILLION in market cap. Gold has more than QUADRUPLED the S&P 500's return over the last 12 months. Gold is telling us something. Nothing says Sovereign Debt Crisis like gold pressing toward new ATH. In the past Bitcoin always followed with a lag and harder.
On the 14th of March:
👉🏽German debt deal compromise foresees €100 bln for climate and transformation fund - Source familiar with talks
ZeroHedge: 'GERMAN DEBT DEAL TO EXEMPT DEFENCE SPENDING FROM DEBT BRAKE ABOVE 1% OF GDP BUT INCLUDES EXPANDED DEFINITION OF DEFENCE SPENDING, SOURCE SAYS.
In other words, "defense against Russia" is just a pretext to flood the economy with a new debt-funded fiscal stimulus, just like Covid.'
As I mentioned above, financial literacy at the ECB and EU Commission.
Von der Leyen: 'We are presenting a new EUR 4.7 billion Global Gateway investment package for South Africa. For projects that support a just energy transition. For connectivity – both physical and digital. And for vaccines, produced in Africa, for Africa.'
Africa is not a member of the EU. So they should stop wasting (spending) our money, 4.7 billion of European taxpayers.
The people, Von der Leyen, who want to "mobilize" the €10T in private citizens' savings, and who are overseeing €13.8T in combined government debt, seem to be as excited as ever about subsidizing questionable regimes all around the world. You don't believe me...I have another example.
Now for the next example, I don't want to make it political but for fuck sake.
'The EU and its partners just pledged €5.8 billion for Syria and its neighbors. This will support Syria at a crucial time of transition and address the dire needs on the ground. This is a chance for the people of Syria to seize the moment and shape their own destiny.' - EU High Representative for Foreign Affairs and Security Policy / Vice-President of the European Commission, Kaja Kallas
No matter your view on the Syria situation sending money to Syria now while supporting the current regime who kill Christians and Alawites. I am an atheist so couldn't care less if we are talking about Christians, Alawites, Muslims, or another religion, people in Syria are getting slaughtered at the moment.
Are these our European values?
€5.8 billion in taxpayer money disappears into Syria again, while Europeans struggle with skyrocketing costs, unaffordable groceries, and failed migration policies. The EU never learns: billions are sent to corrupt regimes while our own people are left behind. Giving Syria a ‘chance’ to determine its own future? That money will end up in the pockets of dictators and militants, just like always. Europe must stop this wasteful spending and focus on its own citizens first.
So 4.7 billion to South Africa and 5.8 billion to Syria, that's 10.5 billion wasted tax payer's money already. Again, hello financial literacy!
Just remember Ursula von der Leyen has previously disregarded defense procurement rules in Germany—the McKinsey affair.
She also committed plagiarism.
In Brussels, lawsuits are ongoing against her regarding the infamous €35 billion SMS-Pfizer deal.
Next example: Christine Lagarde says ‘impossible’ for ECB to always guarantee 2% inflation.
Potential price pressure from the trade war and debt-fuelled borrowing add to the uncertainty, warns the central bank president. Don’t forget, that Macron appointed her. It is all so obvious…
Lex Hoogduin: "This is how a politician makes a turn towards an inflation rate that is, on average, too high and a policy that is too loose, I fear. She has listened carefully to Macron and is executing this in an extremely sophisticated manner—just as she is pushing through the CBDC."
Long-term global inflation chart. WTF happened in 1971? https://i.ibb.co/YYj1kDR/Gm-EHbfk-WAAAm-Sx-P.jpg
Another example:
ECB's Villeroy (a man, full disclosure): The EU has the resources to retaliate against Trump's threatened tariffs on wine and liquor. Now ask yourself, why is a central banker commenting on a trade war? Is that within their mandate? I have the answer: NO!
And it is not only the EU Commission or the ECB. France wants to boost defense spending, but with higher taxes and more debt ruled out as options, Macron’s government is desperately looking for solutions.
Meanwhile, France: - High public debt (112% of GDP) - Large budget deficit (6.2% of GDP) - Ambitious plans for additional spending - Rising interest rates
What could possibly go wrong?
Anyway, I can give example after example but the only thing you need to know we are in a debt rat race without brakes.
If things go wrong, all EU member states will pay the price. And the collateral?
You!
Got Bitcoin?
On the 16th of March:
👉🏽'US interest payments are set to rise even higher: US interest expense on national debt hit a record $1.2 trillion over the last 12 months. To put this into perspective, defense spending was $900 billion during the same period. If rates remain FLAT, interest payments are set to hit $1.5 trillion by the end of the year, doubling in just 4 years.
Even if the Fed cuts rates by 100 basis points, interest costs will still hit ~$1.3 trillion in 2025.
This all assumes the economy will avoid a recession or any material economic slowdown.
This is a crisis.' -TKL
🎁If you have made it this far I would like to give you a little gift:
'A long but thoughtful analysis and opinion on the current volatility and pricing of Bitcoin. We’re in the midst of a technological, monetary, fiscal & currency shift. This is more than an investment idea. The unbanked around the world might soon find freedom as a result.'
https://x.com/JoeConsorti/status/1900285521084965204
After that, kick back, relax, and enjoy: Bitcoin Mastermind Q1 2025 with Joe Carlasare, Jeff Ross, & American HODL.
'A deep dive into the dollar’s weakness, Bitcoin bonds, regulatory updates, and market liquidity trends. Plus, an analysis of major economic shifts, technical buy signals, and the outlook for global assets.'
https://www.youtube.com/watch?v=XzgXe-42PI0
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 7776c32d:45558888
2025-03-19 13:16:46
@ 7776c32d:45558888
2025-03-19 13:16:46March 18, 55 years after UNIX epoch
My name is Mahmoud Khalil and I am a political prisoner. I am writing to you from a detention facility in Louisiana where I wake to cold mornings and spend long days bearing witness to the quiet injustices underway against a great many people precluded from the protections of the law.
Who has the right to have rights? It is certainly not the humans crowded into the cells here. It isn't the Senegalese man I met who has been deprived of his liberty for a year, his legal situation in limbo and his family an ocean away. It isn't the 21-year-old detainee I met, who stepped foot in this country at age nine, only to be deported without so much as a hearing.
Justice escapes the contours of this nation's immigration facilities.
On March 8, I was taken by DHS agents who refused to provide a warrant, and accosted my wife and me as we returned from dinner. By now, the footage of that night has been made public. Before I knew what was happening, agents handcuffed and forced me into an unmarked car. At that moment, my only concern was for Noor's safety. I had no idea if she would be taken too, since the agents had threatened to arrest her for not leaving my side. DHS would not tell me anything for hours - I did not know the cause of my arrest or if I was facing immediate deportation. At 26 Federal Plaza, I slept on the cold floor. In the early morning hours, agents transported me to another facility in Elizabeth, New Jersey. There, I slept on the ground and was refused a blanket despite my request.
My arrest was a direct consequence of exercising my right to free speech as I advocated for a free Palestine and an end to the genocide in Gaza, which resumed in full force Monday night. With January's ceasefire now broken, parents in Gaza are once again cradling too-small shrouds, and families are forced to weigh starvation and displacement against bombs. It is our moral imperative to persist in the struggle for their complete freedom.
I was born in a Palestinian refugee camp in Syria to a family which has been displaced from their land since the 1948 Nakba. I spent my youth in proximity to yet distant from my homeland. But being Palestinian is an experience that transcends borders. I see in my circumstances similarities to Israel's use of administrative detention imprisonment without trial or charge to strip Palestinians of their rights. I think of our friend Omar Khatib, who was incarcerated without charge or trial by Israel as he returned home from travel. I think of Gaza hospital director and pediatrician Dr. Hussam Abu Safiya, who was taken captive by the Israeli military on December 27 and remains in an Israeli torture camp today. For Palestinians, imprisonment without due process is commonplace.
I have always believed that my duty is not only to liberate myself from the oppressor, but also to liberate my oppressors from their hatred and fear. My unjust detention is indicative of the anti-Palestinian racism that both the Biden and Trump administrations have demonstrated over the past 16 months as the U.S. has continued to supply Israel with weapons to kill Palestinians and prevented international intervention. For decades, anti-Palestinian racism has driven efforts to expand U.S. laws and practices that are used to violently repress Palestinians, Arab Americans, and other communities. That is precisely why I am being targeted.
While I await legal decisions that hold the futures of my wife and child in the balance, those who enabled my targeting remain comfortably at Columbia University. Presidents Shafik, Armstrong, and Dean Yarhi-Milo laid the groundwork for the U.S. government to target me by arbitrarily disciplining pro-Palestinian students and allowing viral doxing campaigns - based on racism and disinformation - to go unchecked.
Columbia targeted me for my activism, creating a new authoritarian disciplinary office to bypass due process and silence students criticizing Israel. Columbia surrendered to federal pressure by disclosing student records to Congress and yielding to the Trump administration's latest threats. My arrest, the expulsion or suspension of at least 22 Columbia students some stripped of their B.A. degrees just weeks before graduation and the expulsion of SWC President Grant Miner on the eve of contract negotiations, are clear examples.
If anything, my detention is a testament to the strength of the student movement in shifting public opinion toward Palestinian liberation. Students have long been at the forefront of change leading the charge against the Vietnam War, standing on the frontlines of the civil rights movement, and driving the struggle against apartheid in South Africa. Today, too, even if the public has yet to fully grasp it, it is students who steer us toward truth and justice.
The Trump administration is targeting me as part of a broader strategy to suppress dissent. Visa-holders, green-card carriers, and citizens alike will all be targeted for their political beliefs. In the weeks ahead, students, advocates, and elected officials must unite to defend the right to protest for Palestine. At stake are not just our voices, but the fundamental civil liberties of all.
Knowing fully that this moment transcends my individual circumstances, I hope nonetheless to be free to witness the birth of my first-born child.
-
 @ 266815e0:6cd408a5
2025-03-19 11:10:21
@ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using applesauce
In this guide we are going to build a nostr app that lets users follow and unfollow fiatjaf
1. Setup new project
Start by setting up a new vite app using
pnpm create vite, then set the name and selectSolidandTypescript```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run:
cd followjaf pnpm install pnpm run dev ```
2. Adding nostr dependencies
There are a few useful nostr dependencies we are going to need.
nostr-toolsfor the types and small methods, andrx-nostrfor making relay connectionssh pnpm install nostr-tools rx-nostr3. Setup rx-nostr
Next we need to setup rxNostr so we can make connections to relays. create a new
src/nostr.tsfile with```ts import { createRxNostr, noopVerifier } from "rx-nostr";
export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ```
4. Setup the event store
Now that we have a way to connect to relays, we need a place to store events. We will use the
EventStoreclass fromapplesauce-corefor this. create a newsrc/stores.tsfile withThe event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI
```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools";
export const eventStore = new EventStore();
// verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ```
5. Create the query store
The event store is where we store all the events, but we need a way for the UI to query them. We can use the
QueryStoreclass fromapplesauce-corefor this.Create a query store in
src/stores.ts```ts import { QueryStore } from "applesauce-core";
// ...
// the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ```
6. Setup the profile loader
Next we need a way to fetch user profiles. We are going to use the
ReplaceableLoaderclass fromapplesauce-loadersfor this.applesauce-loadersis a package that contains a few loader classes that can be used to fetch different types of data from relays.First install the package
sh pnpm install applesauce-loadersThen create a
src/loaders.tsfile with```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores";
export const replaceableLoader = new ReplaceableLoader(rxNostr);
// Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ```
7. Fetch fiatjaf's profile
Now that we have a way to store events, and a loader to help with fetching them, we should update the
src/App.tsxcomponent to fetch the profile.We can do this by calling the
nextmethod on the loader and passing apubkey,kindandrelaysto it```tsx function App() { // ...
onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); });
// ... } ```
8. Display the profile
Now that we have a way to fetch the profile, we need to display it in the UI.
We can do this by using the
ProfileQuerywhich gives us a stream of updates to a pubkey's profile.Create the profile using
queryStore.createQueryand pass in theProfileQueryand the pubkey.tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" );But this just gives us an observable, we need to subscribe to it to get the profile.
Luckily SolidJS profiles a simple
frommethod to subscribe to any observable.To make things reactive SolidJS uses accessors, so to get the profile we need to call
fiatjaf()```tsx function App() { // ...
// Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") );
return ( <> {/ replace the vite and solid logos with the profile picture /}
{fiatjaf()?.name}
{/* ... */}); } ```
9. Letting the user signin
Now we should let the user signin to the app. We can do this by creating a
AccountManagerclass fromapplesauce-accountsFirst we need to install the packages
sh pnpm install applesauce-accounts applesauce-signersThen create a new
src/accounts.tsfile with```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts";
// create an account manager instance export const accounts = new AccountManager();
// Adds the common account types to the manager registerCommonAccountTypes(accounts); ```
Next lets presume the user has a NIP-07 browser extension installed and add a signin button.
```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return;
// create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account);};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div>); } ```
Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start.
We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the docs
10. Showing the signed-in state
We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out
```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$);
// ...
const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return;
// signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive();};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div>); } ```
11. Fetching the user's profile
Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in.
```tsx function App() { // ...
// fetch the user's profile when they sign in createEffect(async () => { const active = account();
if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); }});
// ... } ```
Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together.
```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs";
function App() { // ...
// subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) );
// ...
return ( <> {/ ... /}
<div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div>); } ```
12. Showing if the user is following fiatjaf
Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf.
```tsx function App() { // ...
// subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) );
const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); });
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div>); } ```
13. Adding the follow button
Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with Actions which are pre-built methods to modify nostr events for a user.
First we need to install the
applesauce-actionsandapplesauce-factorypackagesh pnpm install applesauce-actions applesauce-factoryThen create a
src/actions.tsfile with```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts";
// The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, });
// The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ```
Then create a
toggleFollowmethod that will add or remove fiatjaf from the users contacts.We are using the
execmethod to run the action, and theforEachmethod from RxJS allows us to await for all the events to be published```tsx function App() { // ...
const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); };
if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); }};
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div>); } ```
14. Adding outbox support
The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays.
To do this we can subscribe to the signed in users mailboxes using the query store in
src/nostr.ts```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores";
// ...
// subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ```
And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
-
 @ da0b9bc3:4e30a4a9
2025-03-19 08:49:13
@ da0b9bc3:4e30a4a9
2025-03-19 08:49:13Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/917523
-
 @ a012dc82:6458a70d
2025-03-19 06:28:40
@ a012dc82:6458a70d
2025-03-19 06:28:40In recent years, the global economy has faced unprecedented challenges, with inflation rates soaring to levels not seen in decades. This economic turmoil has led investors and consumers alike to seek alternative stores of value and investment strategies. Among the various options, Bitcoin has emerged as a particularly appealing choice. This article explores the reasons behind Bitcoin's growing appeal in an inflation-stricken economy, delving into its characteristics, historical performance, and the broader implications for the financial landscape.
Table of Contents
-
Understanding Inflation and Its Impacts
-
Bitcoin: A New Safe Haven?
-
Decentralization and Limited Supply
-
Portability and Liquidity
-
Bitcoin's Performance in Inflationary Times
-
Challenges and Considerations
-
The Future of Bitcoin in an Inflationary Economy
-
Conclusion
-
FAQs
Understanding Inflation and Its Impacts
Inflation is the rate at which the general level of prices for goods and services is rising, eroding purchasing power. It can be caused by various factors, including increased production costs, higher energy prices, and expansive government policies. Inflation affects everyone in the economy, from consumers and businesses to investors and retirees, as it diminishes the value of money. When inflation rates rise, the purchasing power of currency falls, leading to higher costs for everyday goods and services. This can result in decreased consumer spending, reduced savings, and overall economic slowdown.
For investors, inflation is a significant concern because it can erode the real returns on their investments. Traditional investments like bonds and savings accounts may not keep pace with inflation, leading to a loss in purchasing power over time. This has prompted a search for alternative investments that can provide a hedge against inflation and preserve, if not increase, the value of their capital.
Bitcoin: A New Safe Haven?
Traditionally, assets like gold, real estate, and Treasury Inflation-Protected Securities (TIPS) have been considered safe havens during times of inflation. However, the digital age has introduced a new player: Bitcoin. Bitcoin is a decentralized digital currency that operates without the oversight of a central authority. Its supply is capped at 21 million coins, a feature that many believe gives it anti-inflationary properties. This inherent scarcity is akin to natural resources like gold, which have historically been used as hedges against inflation.
The decentralization of Bitcoin means that it is not subject to the whims of central banking policies or government interference, which are often seen as contributing factors to inflation. This aspect of Bitcoin is particularly appealing to those who have lost faith in traditional financial systems and are looking for alternatives that offer more autonomy and security.
Decentralization and Limited Supply
One of the key features that make Bitcoin appealing as a hedge against inflation is its decentralized nature. Unlike fiat currencies, which central banks can print in unlimited quantities, Bitcoin's supply is finite. This scarcity mimics the properties of gold and is seen as a buffer against inflation. The decentralized nature of Bitcoin also means that it is not subject to the same regulatory pressures and monetary policies that can lead to currency devaluation.
Furthermore, the process of "mining" Bitcoin, which involves validating transactions and adding them to the blockchain, is designed to become progressively more difficult over time. This not only ensures the security of the network but also introduces a deflationary element to Bitcoin, as the rate at which new coins are created slows down over time.
Portability and Liquidity
Bitcoin's digital nature makes it highly portable and divisible, allowing for easy transfer and exchange worldwide. This liquidity and global accessibility make it an attractive option for investors looking to diversify their portfolios beyond traditional assets. Unlike physical assets like gold or real estate, Bitcoin can be transferred across borders without the need for intermediaries, making it a truly global asset.
The ease of transferring and dividing Bitcoin means that it can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. This versatility, combined with its growing acceptance as a form of payment, enhances its utility and appeal as an investment.
Bitcoin's Performance in Inflationary Times
Historically, Bitcoin has shown significant growth during periods of high inflation. While it is known for its price volatility, many investors have turned to Bitcoin as a speculative hedge against depreciating fiat currencies. The digital currency's performance during inflationary periods has bolstered its reputation as a potential safe haven. However, it's important to note that Bitcoin's market is still relatively young and can be influenced by a wide range of factors beyond inflation, such as market sentiment, technological developments, and regulatory changes.
Despite its volatility, Bitcoin has provided substantial returns for some investors, particularly those who entered the market early. Its performance, especially during times of financial instability, has led to increased interest and investment from both individual and institutional investors. As more people look to Bitcoin as a potential hedge against inflation, its role in investment portfolios is likely to evolve.
Challenges and Considerations
Despite its growing appeal, Bitcoin is not without its challenges. The cryptocurrency's price volatility can lead to significant losses, and regulatory uncertainties remain a concern. Additionally, the environmental impact of Bitcoin mining has sparked debate. The energy-intensive process required to mine new coins and validate transactions has raised concerns about its sustainability and environmental footprint.
Investors considering Bitcoin as a hedge against inflation should weigh these factors and consider their risk tolerance and investment horizon. While Bitcoin offers potential benefits as an inflation hedge, it also comes with risks that are different from traditional investments. Understanding these risks, and how they align with individual investment strategies, is crucial for anyone considering adding Bitcoin to their portfolio.
The Future of Bitcoin in an Inflationary Economy
As the global economy continues to navigate through turbulent waters, the appeal of Bitcoin is likely to grow. Its properties as a decentralized, finite, and easily transferable asset make it a unique option for those looking to protect their wealth from inflation. However, the future of Bitcoin remains uncertain, and its role in the broader financial landscape is still being defined. As with any investment, due diligence and a balanced approach are crucial.
The increasing institutional interest in Bitcoin and the development of financial products around it, such as ETFs and futures, suggest that Bitcoin is becoming more mainstream. However, its acceptance and integration into the global financial system will depend on a variety of factors, including regulatory developments, technological advancements, and market dynamics.
Conclusion
The growing appeal of Bitcoin in an inflation-stricken economy highlights the changing dynamics of investment in the digital age. While it offers a novel approach to wealth preservation, it also comes with its own set of risks and challenges. As the world continues to grapple with inflation, the role of Bitcoin and other cryptocurrencies will undoubtedly be a topic of keen interest and debate among investors and policymakers alike. Whether Bitcoin will become a permanent fixture in investment portfolios as a hedge against inflation remains to be seen, but its impact on the financial landscape is undeniable.
FAQs
What is inflation, and how does it affect the economy? Inflation is the rate at which the general level of prices for goods and services is rising, leading to a decrease in purchasing power. It affects the economy by reducing the value of money, increasing costs for consumers and businesses, and potentially leading to economic slowdown.
Why is Bitcoin considered a hedge against inflation? Bitcoin is considered a hedge against inflation due to its decentralized nature, limited supply capped at 21 million coins, and its independence from government monetary policies, which are often seen as contributing factors to inflation.
What are the risks associated with investing in Bitcoin? The risks include high price volatility, regulatory uncertainties, and concerns over the environmental impact of Bitcoin mining. Investors should consider their risk tolerance and investment horizon before investing in Bitcoin.
How does Bitcoin's limited supply contribute to its value? Bitcoin's limited supply mimics the scarcity of resources like gold, which has traditionally been used as a hedge against inflation. This scarcity can help to maintain its value over time, especially in contrast to fiat currencies, which can be printed in unlimited quantities.
Can Bitcoin be used for everyday transactions? Yes, Bitcoin can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. Its digital nature allows for easy transfer and division, making it a versatile form of currency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnewsco
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e97aaffa:2ebd765d
2025-03-19 05:55:17
@ e97aaffa:2ebd765d
2025-03-19 05:55:17Como é difícil encontrar informações sobre o eurodigital, a CBDC da União Europeia, vou colocando aqui, os documentos mais interessantes que fui encontrando:
FAQ: https://www.ecb.europa.eu/euro/digital_euro/faqs/html/ecb.faq_digital_euro.pt.html
Directório BCE: https://www.ecb.europa.eu/press/pubbydate/html/index.en.html?topic=Digital%20euro
https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/html/index.en.html
Documentos mais técnicos:
2025
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
2024
Relatório de progresso https://www.ecb.europa.eu/euro/digital_euro/progress/html/ecb.deprp202412.en.html
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
The impact of central bank digital currency on central bank profitability, risk-taking and capital https://www.ecb.europa.eu/pub/pdf/scpops/ecb.op360~35915b25bd.en.pdf
2023
Progress on the investigation phase of a digital euro - fourth report https://www.ecb.europa.eu/paym/digital_euro/investigation/governance/shared/files/ecb.degov230713-fourth-progress-report-digital-euro-investigation-phase.en.pdf
Digital euro - Prototype summary and lessons learned https://www.ecb.europa.eu/pub/pdf/other/ecb.prototype_summary20230526%7E71d0b26d55.en.pdf
Functional and non-functional requirements linked to the market research for a potential digital euro implementation https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf//ecb.dedocs230113_Annex_1_Digital_euro_market_research.en.pdf
A stocktake on the digital euro https://www.ecb.europa.eu/euro/digital_euro/progress/shared/pdf/ecb.dedocs231018.en.pdf
-
 @ ee9aaefe:1e6952f4
2025-03-19 05:01:44
@ ee9aaefe:1e6952f4
2025-03-19 05:01:44Introduction to Model Context Protocol (MCP)
Model Context Protocol (MCP) serves as a specialized gateway allowing AI systems to access real-time information and interact with external data sources while maintaining security boundaries. This capability transforms AI from closed systems limited to training data into dynamic assistants capable of retrieving current information and performing actions. As AI systems integrate into critical infrastructure across industries, the security and reliability of these protocols have become crucial considerations.
Security Vulnerabilities in Web-Based MCP Services
Traditional MCP implementations operate as web services, creating a fundamental security weakness. When an MCP runs as a conventional web service, the entire security model depends on trusting the service provider. Providers can modify underlying code, alter behavior, or update services without users' knowledge or consent. This creates an inherent vulnerability where the system's integrity rests solely on the trustworthiness of the MCP provider.
This vulnerability is particularly concerning in high-stakes domains. In financial applications, a compromised MCP could lead to unauthorized transactions or exposure of confidential information. In healthcare, it might result in compromised patient data. The fundamental problem is that users have no cryptographic guarantees about the MCP's behavior – they must simply trust the provider's claims about security and data handling.
Additionally, these services create single points of failure vulnerable to sophisticated attacks. Service providers face internal threats from rogue employees, external pressure from bad actors, or regulatory compulsion that could compromise user security or privacy. With traditional MCPs, users have limited visibility into such changes and few technical safeguards.
ICP Canisters: Enabling the Verifiable MCP Paradigm
The Internet Computer Protocol (ICP) offers a revolutionary solution through its canister architecture, enabling what we term "Verifiable MCP" – a new paradigm in AI security. Unlike traditional web services, ICP canisters operate within a decentralized network with consensus-based execution and verification, creating powerful security properties:
- Cryptographically verifiable immutability guarantees prevent silent code modifications
- Deterministic execution environments allow independent verification by network participants
- Ability to both read and write web data while operating under consensus verification
- Control of off-chain Trusted Execution Environment (TEE) servers through on-chain attestation
These capabilities create the foundation for trustworthy AI context protocols that don't require blind faith in service providers.
Technical Architecture of Verifiable MCP Integration
The Verifiable MCP architecture places MCP service logic within ICP canisters that operate under consensus verification. This creates several distinct layers working together to ensure security:
-
Interface Layer: AI models connect through standardized APIs compatible with existing integration patterns.
-
Verification Layer: The ICP canister validates authentication, checks permissions, and verifies policy adherence within a consensus-verified environment.
-
Orchestration Layer: The canister coordinates necessary resources for data retrieval or computation.
-
Attestation Layer: For sensitive operations, the canister deploys and attests TEE instances, providing cryptographic proof that correct code runs in a secure environment.
-
Response Verification Layer: Before returning results, cryptographic verification ensures data integrity and provenance.
This architecture creates a transparent, verifiable pipeline where component behavior is guaranteed through consensus mechanisms and cryptographic verification—eliminating the need to trust service provider claims.
Example: Secure Financial Data Access Through Verifiable MCP
Consider a financial advisory AI needing access to banking data and portfolios to provide recommendations. In a Verifiable MCP implementation:
-
The AI submits a data request through the Verifiable MCP interface.
-
The ICP canister verifies authorization using immutable access control logic.
-
For sensitive data, the canister deploys a TEE instance with privacy-preserving code.
-
The canister cryptographically verifies the TEE is running the correct code.
-
Financial services provide encrypted data directly to the verified TEE.
-
The TEE returns only authorized results with cryptographic proof of correct execution.
-
The canister delivers verified insights to the AI.
This ensures even the service provider cannot access raw financial data while maintaining complete auditability. Users verify exactly what code processes their information and what insights are extracted, enabling AI applications in regulated domains otherwise too risky with traditional approaches.
Implications for AI Trustworthiness and Data Sovereignty
The Verifiable MCP paradigm transforms the trust model for AI systems by shifting from "trust the provider" to cryptographic verification. This addresses a critical barrier to AI adoption in sensitive domains where guarantees about data handling are essential.
For AI trustworthiness, this enables transparent auditing of data access patterns, prevents silent modifications to processing logic, and provides cryptographic proof of data provenance. Users can verify exactly what information AI systems access and how it's processed.
From a data sovereignty perspective, users gain control through cryptographic guarantees rather than policy promises. Organizations implement permissions that cannot be circumvented, while regulators can verify immutable code handling sensitive information. For cross-border scenarios, Verifiable MCP enables compliance with data localization requirements while maintaining global AI service capabilities through cryptographically enforced data boundaries.
Conclusion
The Verifiable MCP paradigm represents a breakthrough in securing AI systems' external interactions. By leveraging ICP canisters' immutability and verification capabilities, it addresses fundamental vulnerabilities in traditional MCP implementations.
As AI adoption grows in regulated domains, this architecture provides a foundation for trustworthy model-world interactions without requiring blind faith in service providers. The approach enables new categories of AI applications in sensitive sectors while maintaining robust security guarantees.
This innovation promises to democratize secure context protocols, paving the way for responsible AI deployment even in the most security-critical environments.
-
 @ 8671a6e5:f88194d1
2025-03-18 23:46:54
@ 8671a6e5:f88194d1
2025-03-18 23:46:54glue for the mind
\ You’ve seen them, these garish orange Bitcoin stickers slapped on lampposts, laptops, windows and the occasional rust-bucket Honda. They’re sometimes in some areas a sort of graffiti plague on the landscape, certainly when a meetup or bitcoin conference was held in the area (especially then the city or town can fork out some extra budget to clean things up and scrape the stickers from statues of famous folk heroes or the door to the headquarters of a local bank branche).\ \ At first glance, it might seem like enthusiasm Bitcoiners desperate to scream their obsession from the rooftops. Both for the fun of it, and to get rid of the pack of stickers they’ve got at a local meetup.\ \ But let’s cut to the chase: covering half a town in stickers isn’t clever. It’s lazy, counterproductive, and has nothing to do with what Bitcoin actually stands for.\ Worse, it reeks of the brain-dead low grade (cheap) marketing tactics you’d expect from shitcoiners or the follow up of some half-baked flyer campaign by a local communist clique.\ Proof? Bitcoin stickers are literally covering up — or being covered up themselves, usually by - communist stickers in a pointless competition for use of real-world ad space.\ \ Maybe, bitcoiners should just create a sticker where Karl Marx ànd the bitcoin logo appear in the same sticker, so both groups can enjoy it’s uselessness, and call it quits to get this stupidity over with once and for all.\ A sticker with a shiny B might look cool at first. But what does it actually do?
 Communist and Bitcoin logo sticker
Communist and Bitcoin logo stickerSpamming stickers doesn’t make “frens”
There’s a psychology behind these stickers of course: people slap them up to feel part of a rebel tribe, flipping off central banks or feeling part of the crew.\ This crude, omnipresent approach to marketing echoes the late 1960s— an era of peak fiat, not Bitcoin’s time.\ Mimicking those tactics today, as if Bitcoin were some hip underground record store trying to spread its brand name, is utterly irrelevant.\ Sure, people love signaling affiliations with an easy and cheap identity flex — like a bumper sticker yelling: “Look at me I’m special!”\ \ But plaster a town with Bitcoin logos, and it stops being edgy and it was never funny; it becomes an eyesore and puts bitcoiners in the same category as the social justice warriors and political youth movements or brands of local energy drinks doing some weird campaign.\ \ Advertising psychology shows overexposure breeds resentment, not interest. Flood a street with stickers, and you’re not lighting a spark. You’re making people uninterested, gag, associating Bitcoin with spam or worse: get totally blended into the background along all the other noise from the street marketeers.\ \ The "mere exposure effect" (Zajonc, 1968)1 claims familiarity breeds liking, even from annoyance. Since the 1960s however, a lot has changed, as we’ll see… and above all, yet, after years of Bitcoin stickers in many areas, they’ve just turned into meaningless wallpaper. It has usually no strong message, no slogan, no conversation starter other than “buy bitcoin”, it’s disassociated from reality for many people, as the reaction show us. It’s also happening in a vacuum, where “normies” and no-coiners pass by and don’t even recognize such stickers for anything else than background colors.
It’s Lazy Man’s Work
Let’s talk effort — or the lack of it - for these kind of campaigns and stickers. Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. It’s easy, cheap and also quick to distribute.\ \ These stickers aren’t masterful designs from an artistic genius (safe some clever exceptions). They’re usually ripped off from somewhere else, tweaked for five minutes, and bulk-ordered online. It’s the “IKEA effect” gone wrong: a tiny bit of customization, and suddenly people think they’re visionaries. But it’s a low-effort form of activism at best. Compare that to coding a Bitcoin tool or patiently explaining its value to a normie or organizing a meetup or conference, starting a company.\ Not that low-level or guerrilla marketing can’t work, I just don’t see it happen with stickers. Why not go out there and try to convince a whole series of fruit and vegetable market owners to accept bitcoin instead of using very expensive bank Point-of-sale systems?\ Why not direct mailing? Why not… do more than just putting a sticker on a signpost and walk away like a sneaky student promoting his 4 person political group?\ \ Stickers are the “Save the whales (pun intended)” magnet on your fridge: lazy-ass advocacy that screams intellectual deficiency. They’re a shortcut to feeling involved, not a strategy for real impact.
 imaginary Save-the-Whales bitcoin sticker
imaginary Save-the-Whales bitcoin stickerStrategy territory signaling
Here’s the kicker: Bitcoin’s strength lies in its tech and value properties — decentralized, borderless value transfer that eliminates middlemen and has provable digital scarcity.\ Stickers? They’re just physical garbage. Sure, they might feel like a way to make an abstract idea tangible, tapping into “embodied cognition.” But they explain nothing about Bitcoin’s purpose or how it revolutionizes finance.\ They’re a dopamine hit for the people sticking them anywhere — a pathetic “I did something” moment — while everyone else walks by without a glance.\ Bitcoin is about innovation, not old-school social groups with low-budget marketing tactics.
\ The psychology of Bitcoin stickers
Why bother? Stickers are simple and loud—easy for the brain to process, a cheap thrill of rebellion. The person who spends an afternoon covering a city in them thinks they’re spreading the gospel. In reality, they’re just littering. Real advocacy takes effort, discussion, and substance — not a pack of adhesive stickers ordered with the click of a button.\ It’s the same reason nobody turns communist from a hammer-and-sickle sticker on a pole. It’s dead air.\ \ The proof of their uselessness? In 2 years, not one person I know has bought, researched, or even asked about Bitcoin because of a sticker in the neighborhood bar. A bar near me has had one on the wall for years — zero requests to pay with Bitcoin.
A sticker sitting on a bar wall for five years without impact isn’t “subtle marketing”—it’s a neon sign of failure. And the people cleaning those stickers off street signs, or the local communist student activists constantly covering them with their own, are locked in an endless, mindless sticker war.\ \ Other areas are even having a tsunami of bitcoin stickers, and hardly any places where they actually accept bitcoin for goods.\ More so, places where they do accept bitcoin readily, usually only need one sticker: the one at the door of a business saying “bitcoin accepted here”. And that’s about it.
What the little amount of research says
Studies shows stickers work for movements claiming public space and resisting dominant narratives — when done on a massive scale, targeting a specific audience have a visual and emotional effect when combined with other forms of resistance in social movements.\ "Stickin' it to the Man: The Geographies of Protest Stickers" 2\ \ For Bitcoin, a global monetary network meant for everyone, that localized, niche-based campaign makes little sense.\ Unlike sports teams or clothing brands, Bitcoiners can’t pinpoint a target area. A random sticker on a busy street claims nothing—no momentum, atmosphere, or intrigue. Political campaigns and underground youth movements concentrate stickers in student neighborhoods, universities, or subcultures where the message resonates. But Bitcoin isn’t a corporation, company, or fashion brand—it’s a Wall Street-embraced asset by now, with activists not really situated in the sticker-guerrilla kind of persons.
When was the last time you saw a "Buy Gold!" sticker? A "Get Your Microsoft Stock Options Now!" sticker? Or a "Crude Oil—Yeah, Baby!" sticker? Never. Serious assets don’t need guerrilla marketing.
The overload on stickers is also becoming an issue (especially in some areas with higher concentration of bitcoiners).
Bitcoin stickers fall flat
Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. Protest stickers massively appear after protest rallies or campaigns with multi-level plans to reach audiences.\ As significant, overlooked tools of resistance and debate, their effect remains under-studied, with no data on “recruitment.”\ \ If Bitcoin stickers (which don’t provoke debate ever, other than people being angry about having to clean them up) in a bar are any clue—after one full year, not a single person asked why it was there or if Bitcoin was accepted—they’re just decor, lost among the clutter.
Bitcoiners still think slapping a shiny "B" logo on a street sign without explanation or slogan will spark momentum. But that requires a massive, organized campaign with thousands of people and a clear audience while you claim certain well aimed areas of public space — that something that’s not happening in bitcoin. There’s no plan, no campaign, just someone sticking a bitcoin logo at the supermarkt trolley or the backside of a street sign.\ And even if we did reach a higher number of stickers, it would annoy the f out of people.
"Study: Ad Overload Could Pose Steeper Risk to Brands Than Messages Near Inappropriate Content" (GWI & WARC, 2021) 3\ \ There’s also the effect of high ad exposure. When a whole street is covered in bitcoin stickers, it’s having the opposite effect. Or still… no one cares.
"Coping with High Advertising Exposure: A Source-Monitoring Perspective" (Bell et al., 2022)4
No synergy, no consensus
The synergy between offline sticker placement and online sharing? Absent. Bitcoiners online might be called “cyber hornets”, but this swarm is notoriously bad at sharing content. Post a Bitcoin sticker photo, and at best 1-2% will share it — no momentum, no discussion, no engagement.\ \ Non-Bitcoiners have zero reason to care. When was the last time you, as a Bitcoiner, shared a soccer team’s sticker? A political campaign sticker? Never. That’s normal, as you’re not in their bubble, so for us, it’s irrelevant. We won’t share the soccer team’s sticker (unless it’s Real Bedford FC probably).\ \ It's just a layer of plastic with adhesive glued to a surfase where someone will sooner or later either have to clean it up, or where the bitcoin sticker will be covered over by another person wasting his or her time by claiming that “sticker real-estate space” for their cause or brand-awareness.

And so, the red sticker calling all students and workers to vote for a Leninist party (with 10 members) is stickered over by a bright orange Bitcoin logo, and that one, in turn, will be over-stickered by a local fitness company's new logo, and so forth. It’s all a pointless rush for giggles and dopamine. And it’s time to recognize it for what it really is: retardation.
Bitcoin deserves better than this 70s guerrilla marketing ploy, from a time when activism was more than sitting behind a computer ordering stickers and (mostly not) clicking a link. Leave the sticker wars to students searching for an ideological dopamine rush and soccer fans claiming a neighborhood as "their territory."\ \ As Bitcoiners, we can do something more useful. For example: ask yourself how many businesses in your area accept Bitcoin, or what coworker you can save from investing in blatant scams, or… invent something nice, start a meetup, podcast, or learn to code, convince, build.
Bitcoin deserves better.
by AVB / tips go here
@avbpodcast - allesvoorbitcoin.be - 12 Bitcoin Food for Thought
https://typeset.io/papers/attitudinal-effects-of-mere-exposure-12e5gwrysc
https://www.research.ed.ac.uk/en/publications/stickin-it-to-the-man-the-geographies-of-protest-stickers
https://www.warc.com/content/article/warc-datapoints-gwi/too-many-ads-is-the-most-damaging-factor-for-brands/en-gb/136530
https://pmc.ncbi.nlm.nih.gov/articles/PMC9444107/
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ bbb5dda0:f09e2747
2025-03-18 20:11:54
@ bbb5dda0:f09e2747
2025-03-18 20:11:54Time isn't constant, or at least my perception of it isn't. The past two weeks have been like 2 months for me! In a good way... I'm playing catch-up with my updates so this one will only focus on week 10 because so much happened!
I'm lucky enough to be joining #SovEng for the second time, where a bunch of Nostr geeks get together and all work on our part to fix the internet, join in deliberation, hike, demo, and repeat...
GitHub actions in GitWorkshop
I hit off the first week by working with nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr to see what the Git Actions workflow looks like in a decentralized world. Because now anyone can be an operator, the flow will be different than on legacy git collaboration tools. We hashed out an early version of a user interface. You can check it out at vnext.gitworkshop.dev. Go to profile icon > settings > experimental mode (on).
The issues we face
We're having some debates wether or not the workflow runners fit within the DVM spec. The main difference between this and all DVM implementations that i'm aware of. Is that most DVM are quite cookie-cutter input, processing, then answer within a few seconds.
Costs not known up front
The workflow runners are long-running jobs, they can run for hours potentially, AND it's impossible to know how long a job is going to take beforehand, meaning there can be no set price per invocation. So we send a pre-payment for the maximum runtime (
price/sec*timeoutSec) and expect the runner to return the change when the job is done, so we need to account for that.Handling cancellations
Also when a job is cancelled, which in the DVM spec is done by a delete request, which forms a problem because we want to keep a history of our runs, even if they're cancelled.
DVM partial results
We currently use partial results to 'stream' back logs from the job. However the log output of jobs can be massive and we might not want to keep them around for long, Ephemeral would might be better suited for that and the final log output could be saved on blossom to be included in the final status.
Queueing runs
The DVM spec does not specify any queuing messaging/statuses. Workflows can rely heavily on the type of machine they run on. Architecture, OS, memory or vCPU's. That means you might want to schedule jobs even though all potential runners are currently busy. Therefore a queueing system makes a lot of sense. We might be able to squeeze such a system into our implementation of the DVM spec. But it's just one of the things that makes us wonder if we're not drifting too far from the spec to still call it a DVM.
Some screenshots of our implementation: https://vnext.gitworkshop.dev/arjen@swissdash.site/dvm-cicd-runner
|
 | |
| ----------------------------------------------------------------------------------------------------- | --- |
|
| |
| ----------------------------------------------------------------------------------------------------- | --- |
|  | |
| | |
| |
| | |
Infernal Insights
 Aaah... Logging and metrics, our favourite hard-to-manage infrastructure thing we don't really want to do but kind of need to make a good product.
Aaah... Logging and metrics, our favourite hard-to-manage infrastructure thing we don't really want to do but kind of need to make a good product.Coming from the DevOps world, these systems usually can be incredibly valuable, but can be a pain to set up and/or maintain.
I ended up on a fun proof-of-concept together with nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr and nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr we made this dead simple nostr message:
json { "kind": 1314, "expires": "tags": [ ["expiration", nostrNow() + oneMonth], ["n" "tollgate-site"] // Application Namespace ["p, "1096f6b...a74c7ecc"] // pubkey of person behind current deployment ], "content": "The button on the top-right disappears when i hover on it." }It basically tags the developer of the application/site and a namespace (aka: the name of the software). @hzrd created this simple button to add to a website header that creates the ability to send these events.The
ntag is there to give the name of the software, that way different people (npubs) can gather feedback on seperate deployments, and the developer of said software could also utilize this data for its own purposes by filtering on thentag. Whereas a developer is probably only interested in their own deploymentThe events are ONLY meant as raw data, like human written feedback, maybe crash logs. It can be anything and they're not meant to be kept around for long, it should be ingested by a pipeline, which can then run one or more rounds of filtering, tagging, categorizing. Each resulting in a new refined event, ingestable by the next.
However for this experiment we stuck with ingesting it, and do just one step of refinement and send it off to a logging-aggregation system, in this case Grafana Loki. We basically sent the logs straight over there, but we also added a fun extra feature, sentiment analysis!
We sent the contents of the logs over to ppq.ai and let it give us a sentiment score from 1 to 10. So we can get a sense of how positive/negative the feedback is. This same principle can be applied in so many ways. Think of categorizing by LLM. You can group feedback based on if it's about the UI for example. It'd be easy to group them and create a Nostr git issue out of those.
Find my software for the dat ingestion here.
-
 @ bd32f268:22b33966
2025-03-18 18:59:23
@ bd32f268:22b33966
2025-03-18 18:59:23O que torna um homem um modelo a ser seguido ? Que qualidades pode apresentar um homem que demonstram as suas aspirações ?
Nos dias que correm a nobreza de carácter não parece ser o factor chave nas figuras que são mais celebradas pelo mundo inteiro. A nossa sociedade dá mais atenção ao indigente moral célebre pelas sacadas narcísicas do que ao guerreiro, ao santo, ao patriarca que dedicaram a sua vida a um propósito e aspirações manifestamente superiores.
É frequente vermos ser objeto de atenção o homem vaidoso, efeminado, narcísico e corrupto até. O facto de serem estas as referências que temos na cultura moderna diz muito da sociedade em que vivemos. É importante notar que nós somos como espelhos que refletem aquilo que reverenciamos, isto é, vamo-nos tornando mais parecidos com o objeto da nossa admiração. É nosso instinto tentar imitar aquilo que admiramos, portanto isto é um grave problema quando admiramos as coisas erradas.
Pode parecer contraintuitivo mas por vezes as coisas mais admiráveis na vida são na verdade as mais simples. Prestemos atenção ao que nos diz o auto G.K Chesterton a este propósito.

Há algo de magnificamente sóbrio no pai de família que não procura atenção e se dedica exclusivamente ao seu dever. Esta figura é, por hora, demonizada tantas e tantas vezes, sendo frequentemente apresentado como sendo o mandatário de uma cultura misógina e machista.
Estou convencido que enquanto a figura de pai de família não for devidamente reabilitada, dificilmente teremos um ressurgimento de famílias propriamente ordenadas. É importante notar aqui um ponto, este pai de família deve ser alguém capaz de colocar os interesses da família primeiro que os seus interesses individuais. Deve ser alguém que não viva no relativismo moral, mas sim um homem de fé, algo que está em vias de extinção no ocidente e em particular em Portugal. Este homem deve ser o porto de abrigo para a sua família, alguém disposto a travar o bom combate, e será sempre portanto um defensor acérrimo da verdade. Não será naturalmente alguém obcecado com a sua própria imagem, mas sim um homem desejavelmente forte quer em termos físicos, tendo zelo na forma como se exercita, quer em termos mentais, sendo uma pessoa capaz mas com autocontrolo. Deve também ser um homem com uma vida intelectual, isto é, alguém que nutre interesse pelo legado que lhe foi confiado e procura aprender sobre o mesmo. Muitos homens antes de si fizeram sacrifícios para que o homem da atualidade usufrua dos mais variados benefícios.
A atualidade oferece-nos por vezes a promoção de algumas destas facetas, algo que seria desejável e bom, contudo com algumas distorções. Há homens fortes, capazes de feitos atléticos ímpares, que se cultivam nesse domínio mas pelas razões erradas. Por vezes o imperativo moral que os guia é a vaidade, sendo que esse trabalho físico que fazem conspira para consolidar o seu narcisismo.
Outros há com uma determinação inabalável, algo louvável quando usada para os fins próprios. Esta determinação não deve ser usada para a procura de grandes riquezas como um fim em si mesmas, nem como um isco usado para o oportunismo sexual com as mulheres.
Poderíamos também dar como exemplo, homens com uma prodigiosa inteligência mas que, não a tendo devidamente orientada, a usam para manipular e corromper o discurso público não olhando a meios para atingir os fins.
Um factor chave que dificulta a formação de mais homens com este tipo de espinha dorsal é uma certa apropriação da linguagem que tem existido no discurso público que procura rotular quem ousa desafiar este status quo. Termos como “negacionista”, “radical”, “fascista”, “fundamentalista”, “ultranacionalista” entre outros, são constantemente atirados remetendo o homem para uma falsa conclusão:
“ Tu não podes defender nada, nem ter certeza de nada”.
Outra ferramenta importante nesta desconstrução é o apelo ao vício. Sendo através da pornografia, da comida ultra-processada ou de uma vida de conforto , há claramente um incentivo ao hedonismo e à autoindulgência. Procura-se alimentar cada vez mais esta busca do prazer com o fim último, e por conseguinte a coragem, o sacrifício e o trabalho, como pedras angulares da construção do carácter do homem ficam para segundo plano.
O cavalheirismo ficou-se apenas pelas aparências. Por vezes, há um verniz de algumas das propriedades que descrevi em várias situações, contudo não passa de uma máscara. É fácil segurar uma porta para uma senhora e dizer “com licença”, “por favor”, para se mostrar alguém educado quando o custo para o fazer é mínimo. Difícil é estar disposto a fazer sacríficos em que nos doamos inteiramente pelos outros, no entanto é isso que é pedido ao homem. Doando-se encontrará o seu verdadeiro propósito.






































