-
 @ 9711d1ab:863ebd81
2025-03-26 03:36:56
@ 9711d1ab:863ebd81
2025-03-26 03:36:56 Welcome back friends! We’ve made it to the end of March, congratulations. Here’s what we’ve got to share this month:
Welcome back friends! We’ve made it to the end of March, congratulations. Here’s what we’ve got to share this month:-
🎓 The SDK Class of Q1
-
🤓 Back to School with Antonio
-
⚡️ Lightning is Everywhere
-
🎙️ Shooting the Breez with Danny, Umi & Roy
The SDK Class of Q1 2025 🎓
 We’ve been talking a lot about momentum at Breez and we’re seeing it build every day. More partners are adding Bitcoin payments with our SDK and more sats are moving freely around the world. By offering the choice of two implementations, Nodeless and Native, we’re truly building the best Lightning developer experience out there.
We’ve been talking a lot about momentum at Breez and we’re seeing it build every day. More partners are adding Bitcoin payments with our SDK and more sats are moving freely around the world. By offering the choice of two implementations, Nodeless and Native, we’re truly building the best Lightning developer experience out there.And the momentum just keeps growing stronger.
In fact, we’ve welcomed so many new partners that we had to bundle them all into one big announcement — it’s our pleasure to welcome the SDK Class of Q1 2025: Assetify, Cowbolt, DexTrade, Flash, Lightning Pay, OpenAgents, Satoshi, Shakesco, Tidebinder, and ZapZap.
 ---
---Back to School with Antonio 🚌
 We tell everyone we meet that adding Bitcoin payments to apps is really easy with the Breez SDK. But rather than just tell you this, we’ve decided to show you.
We tell everyone we meet that adding Bitcoin payments to apps is really easy with the Breez SDK. But rather than just tell you this, we’ve decided to show you.Antonio, one of our talented developers at Breez, has produced a video tutorial showing how you can add Bitcoin payments to React Native and Expo apps with the Breez SDK - Nodeless.
Join him as he guides you through each step and shows that it really is that *easy* to add Bitcoin payments to any app with our SDK.
Lightning is Everywhere.
 It’s true — Lightning is everywhere.
It’s true — Lightning is everywhere.Bitcoin payments aren’t just a thing for the few, they’re for the many.
This month, we’re showcasing our friends at Cowbolt. They’ve just released their collaborative cost-splitting, team-chat, and self-custody app (check it out).
Shooting the Breez 🌬️
 Since releasing our Bitcoin payment report — where we explained that Bitcoin isn’t just digital gold, it’s a thriving everyday currency accessible to millions of people around the world — Bitcoin payments have been the talk of the town.
Since releasing our Bitcoin payment report — where we explained that Bitcoin isn’t just digital gold, it’s a thriving everyday currency accessible to millions of people around the world — Bitcoin payments have been the talk of the town.As co-author of the report, I joined the Stephan Livera Podcast to discuss the growing trend in more detail. I also met up with Bo Jablonski to explain why more and more apps are taking notice on the newly-formed Guardians of Bitcoin radio show.
Developments have come thick and fast over the past month — most notably, the announcement of USDT coming to Lightning (check out Roy’s take on the good, the bad, and the unknown in Bitcoin Magazine). Breez’s BD Lead, Umi, joined a Spaces on X with UXTO, Amboss, and Lightning Labs to discuss the stablecoin’s imminent arrival on the network.
 That’s not all from Umi, she also joined her alma mater at the Cornell Bitcoin Club to explain why bitcoin is a medium of exchange, thanks to Lightning.
That’s not all from Umi, she also joined her alma mater at the Cornell Bitcoin Club to explain why bitcoin is a medium of exchange, thanks to Lightning. And last but not least, Roy was spreading the good word of Bitcoin, joining Bitfinex’s podcast to explain how Lightning is truly changing the game.
And last but not least, Roy was spreading the good word of Bitcoin, joining Bitfinex’s podcast to explain how Lightning is truly changing the game.
And there we go folks, another edition of Feel the Breez has come to a close.
As always, we’ll leave you with our usual parting comment: the best time to get into Lightning is now — it always has been.
Stay tuned for exciting announcements we’ll be releasing soon.
Until next time ✌️
-
-
 @ 220522c2:61e18cb4
2025-03-26 03:24:25
@ 220522c2:61e18cb4
2025-03-26 03:24:25npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2

-
 @ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00
@ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00Tldr
- Nostr is a new open social protocol for the internet
- You can use it to create your own online community website/app for your users
- This needs only a few simple components that are free and open source
- Jumble.Social client is a front-end for showing your community content to your users
- Simple With Whitelist relay (SW2) is a back-end with simple auth for your community content
- In this blog I explain the components and set up a online community website/app that any community or company can use for their own users, for free.
You Can Run Your Own Private "X" For Free
Nostr is a new open social protocol for the internet. Because it is a protocol it is not controlled by any one company, does not reside on any one set of servers, does not require any licenses, and no one can stop you from using it however you like.
When the name Nostr is recognised, it is as a "Twitter/X alternative" – that is an online open public forum. Nostr is more than just this. The open nature of the protocol means that you can use it however you feel like, including that you can use it for creating your own social websites to suit whatever goals you have – anything from running your own team collaboration app, to running your own online community.
Nostr can be anything – not just an alternative to X, but also to Slack, Teams, Discord, Telegram (etc) – any kind of social app you'd like to run for your users can be run on Nostr.
In this blog I will show you how to launch your own community website, for your community members to use however they like, with low code, and for free.
Simple useful components
Nostr has a few simple components that work together to provide your experience –
- Your "client" – an app or a website front-end that you log into, which displays the content you want to see
- Your "relay" – a server back-end which receives and stores content, and sends it to clients
- Your "user" – a set of keys which represents a user on the network,
- Your "content" – any user content created and signed by a user, distributed to any relay, which can be picked up and viewed by any client.
It is a pattern that is used by every other social app on the internet, excepting that in those cases you can usually only view content in their app, and only post your content to their server.
Vs with Nostr where you can use any client (app) and any relay (server), including your own.
This is defined as a standard in NIP-01 which is simple enough that you can master it in a weekend, and with which you can build any kind of application.
The design space is wide open for anyone to build anything–
- Clones of Twitter, Instagram, Telegram, Medium, Twitch, etc,
- Whole new things like Private Ephemeral Messengers, Social Podcasting Apps, etc,
- Anything else you can dream up, like replacements for B2B SaaS or ERP systems.
Including that you can set up and run your own "X" for your community.
Super powers for –private– social internet
When considering my use of social internet, it is foremost private not public. Email, Whatsapp, Slack, Teams, Discord, Telegram (etc), are all about me, as a user, creating content for a selected group of individuals – close friends, colleagues, community members – not the wider public.
This private social internet is crying out for the kind of powers that Nostr provides. The list of things that Nostr solves for private social internet goes on-and-on.
Let me eat my own dog food for a moment.
- I am a member of a community of technology entrepreneurs with an app for internal community comms. The interface is not fit for this purpose. Good content gets lost. Any content created within the walled kingdom cannot be shared externally. Community members cannot migrate to a different front-end, or cross-post to public social channels.
- I am a member of many communities for kids social groups, each one with a different application and log in. There is no way to view a consolidated feed. There is no way to send one message to many communities, or share content between them. Remembering to check every feed separately is a drag.
- I am a member of a team with an app for team comms. It costs $XXX per user per month where it should be free. I can't self-host. I can't control or export my data. I can't make it interoperate natively with other SaaS. All of my messages probably go to train a Big Co AI without my consent.
In each instance "Nostr fixes this."
Ready now for low-code admins
To date Nostr has been best suited to a more technical user. To use the Nostr protocol directly has been primarily a field of great engineers building great foundations.
IMO these foundations are built. They are open source, free to use, and accessible for anyone who wants to create an administer their own online community, with only low code required.
To prove it, in this blog I will scratch my own itch. I need a X / Slack / Teams alternative to use with a few team members and friends (and a few AIs) as we hack on establishing a new business idea.
I will set this up with Nostr using only open source code, for free.
Designing the Solution
I am mostly non-technical with helpful AI. To set up your own community website in the style of X / Slack / Teams should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs some other unrelated Nostr projects in Docker containers,
- My objective was to set up and run my own community website for my own team use, in Docker, hosted on my own server.
User requirements
What will I want from a community website?
- I want my users to be able to log into a website and post content,
- I want to save that content to a server I control accessed only be people I authorise,
- I want my users to view only that content by default, and not be exposed to any wider public social network unless they knowingly select that,
- I want my user's content to be either:
- a) viewable only by other community members (i.e. for internal team comms), or
- b) by the wider public (i.e. for public announcements), at the user's discretion.
- I want it to be open source so that other people maintain the code for me,
- I want it for free.
Nostr solutions
To achieve this with Nostr, I'll need to select some solutions "a-la carte" for each of the core components of the network.
- A client – For my client, I have chosen Jumble. Jumble is a free open-source client by Cody Tseng, available free on Github or at Jumble.social. I have chosen Jumble because it is a "relay-centric" client. In key spots the user interface highlights for the user what relay they are viewing, and what relay they are posting to. As a result, it is a beautiful fit for me to use as the home of all my community content.
- A relay – For my relay, I have chosen Simple With Whitelist (SW2). SW2 is a free open-source relay by Utxo The Webmaster, based on Khatru by Fiatjaf, available free on Github. I have chosen SW2 because it allows for very simple configuration of user auth. Users can be given read access to view notes, and write access to post notes within simple
config.jsonfiles. This allows you to keep community content private or selectively share it in a variety of ways. Per the Nostr protocol, your client will connect with your relay via websocket. - A user sign-up flow – Jumble has a user sign-up flow using Nstart by Fiatjaf, or as an admin I can create and provision my own users with any simple tool like NAK or Nostrtool.
- A user content flow – Jumble has a user content flow that can post notes to selected relays of the users choice. Rich media is uploaded to free third-party hosts like Nostr.build, and in the future there is scope to self-host this too.
With each of these boxes ticked I'm ready to start.
Launching a Private Community Website with Jumble and SW2
Install your SW2 relay
The relay is the trickiest part, so let's start there. SW2 is my Nostr relay software of choice. It is a Go application and includes full instructions for Go install. However, I prefer Docker, so I have built a Docker version and maintain a Docker branch here.
1 – In a terminal clone the repo and checkout the Docker branch
git clone https://github.com/r0d8lsh0p/sw2.git cd sw2 git checkout docker2 – Set up the environment variables
These are specified in the readme. Duplicate the example .env file and fill it with your variables.
cp .env.example .envFor me this .env file was as follows–
```
Relay Metadata
RELAY_NAME="Tbdai relay" RELAY_PUBKEY="ede41352397758154514148b24112308ced96d121229b0e6a66bc5a2b40c03ec" RELAY_DESCRIPTION="An experimental relay for some people and robots working on a TBD AI project." RELAY_URL="wss://assistantrelay.rodbishop.nz" RELAY_ICON="https://image.nostr.build/44654201843fc0f03e9a72fbf8044143c66f0dd4d5350688db69345f9da05007.jpg" RELAY_CONTACT="https://rodbishop.nz" ```
3 – Specify who can read and write to the relay
This is controlled by two config files
read_whitelist.jsonandwrite_whitelist.json.- Any user with their pubkey in the
read_whitelistcan read notes posted to the relay. If empty, anyone can read. - Any user with their pubkey in the
write_whitelistcan post notes to the relay. If empty, anyone can write.
We'll get to creating and authorising more users later, for now I suggest to add yourself to each whitelist, by copying your pubkey into each JSON file. For me this looks as follows (note, I use the 'hex' version of the pubkey, rather than the npub)–
{ "pubkeys": [ "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" ] }If this is your first time using Nostr and you don't yet have any user keys, it is easy and free to get one. You can get one from any Nostr client like Jumble.social, any tool like NAK or nostrtool.com or follow a comprehensive guide like my guide on mining a Nostr key.
4 – Launch your relay
If you are using my Docker fork from above, then–
docker compose upYour relay should now be running on port 3334 and ready to accept web socket connections from your client.
Before you move on to set up the client, it's helpful to quickly test that it is running as expected.
5 – Test your websocket connection
For this I use a tool called wscat to make a websocket connection.
You may need to install wscat, e.g.
npm install -g wscatAnd then run it, e.g.
wscat -c ws://localhost:3334(note use
ws://for localhost, rather thanwss://).If your relay is working successfully then it should receive your websocket connection request and respond with an AUTH token, asking you to identify yourself as a user in the relay's
read_whitelist.json(using the standard outlined in NIP-42), e.g.``` Connected (press CTRL+C to quit) < ["AUTH","13206fea43ef2952"]
```
You do not need to authorise for now.
If you received this kind of message, your relay is working successfully.
Set a subdomain for your relay
Let's connect a domain name so your community members can access your relay.
1 – Configure DNS
At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caseassistantrelay.rodbishop.nz
Your subdomain now points to your server.
2 – Configure reverse proxy
You need to redirect traffic from your subdomain to your relay at port
3334.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my SW2 Relay required two steps.
First – I added configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.your_domain_name.comsubdomain. For me this looked like–assistantrelay.rodbishop.nz { reverse_proxy sw2-relay:3334 { # Enable WebSocket support header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }Second – I added the Caddy Docker network to the SW2
docker-compose.ymlto make it be part of the Caddy network. In my Docker branch, I provide this commented section which you can uncomment and use if you like.``` services: relay: ... relay configuration here ...
networks:
- caddy # Connect to a Caddy network for reverse proxy
networks:
caddy:
external: true # Connect to a Caddy network for reverse proxy
```
Your relay is now running at your domain name.
Run Jumble.social
Your client set up is very easy, as most heavy lifting is done by your relay. My client of choice is Jumble because it has features that focus the user experience on the community's content first. You have two options for running Jumble.
- Run your own local copy of Jumble by cloning the Github (optional)
- Use the public instance at Jumble.social (easier, and what we'll do in this demo)
If you (optionally) want to run your own local copy of Jumble:
git clone https://github.com/CodyTseng/jumble.git cd jumble npm install npm run devFor this demo, I will just use the public instance at http://jumble.social
Jumble has a very helpful user interface for set up and configuration. But, I wanted to think ahead to onboarding community members, and so instead I will do some work up front in order to give new members a smooth onboarding flow that I would suggest for an administrator to use in onboarding their community.
1 – Create a custom landing page URL for your community members to land on
When your users come to your website for the first time, you want them to get your community experience without any distraction. That will either be–
- A prompt to sign up or login (if only authorised users can read content)
- The actual content from your other community members (If all users can read content)
Your landing page URL will look like:
http://jumble.social/?r=wss://relay.your_domain_name.comhttp://jumble.social/– the URL of the Jumble instance you are using?r=– telling Jumble to read from a relaywss://– relays connect via websocket using wss, rather than httpsrelay.your_domain_name.com– the domain name of your relay
For me, this URL looks like
http://jumble.social/?r=wss://assistantrelay.rodbishop.nz2 – Visit your custom Jumble URL
This should load the landing page of your relay on Jumble.
In the background, Jumble has attempted to establish a websocket connection to your relay.
If your relay is configured with read authentication, it has sent a challenge to Jumble asking your user to authenticate. Jumble, accordingly should now be showing you a login screen, asking your user to login.
3 – Login or Sign Up
You will see a variety of sign up and login options. To test, log in with the private key that you have configured to have read and write access.
In the background, Jumble has connected via websocket to your relay, checked that your user is authorised to view notes, and if so, has returned all the content on the relay. (If this is your first time here, there would not be any content yet).
If you give this link to your users to use as their landing page, they will land, login, and see only notes from members of your community.
4– Make your first post to your community
Click the "post" button and post a note. Jumble offers you the option to "Send only to relay.your_domain_name.com".
- If set to on, then Jumble will post the note only to your relay, no others. It will also include a specific tag (the
"-"tag) which requests relays to not forward the note across the network. Only your community members viewing notes on your community relay can see it. - If set to off, then Jumble will post the note to your relay and also the wider public Nostr network. Community members viewing notes on the relay can see it, and so can any user of the wider Nostr network.
5– Optional, configure your relay sets
At the top of the screen you should now see a dropdown with the URL of your relay.
Each user can save this relay to a "relay set" for future use, and also view, add or delete other relays sets including some sets which Jumble comes with set up by default.
As an admin you can use this to give users access to multiple relays. And, as a user, you can use this to access posts from multiple different community relays, all within the one client.
Your community website is up and running
That is the basic set up completed.
- You have a website where your community members can visit a URL to post notes and view all notes from all other members of the community.
- You have basic administration to enforce your own read and write permissions very simply in two json files.
Let's check in with my user requirements as a community admin–
- My community is saving content to a server where I control access
- My users view only that content by default, and are not exposed to any wider public social network unless they knowingly select that
- My user's content is a) viewable only by other community members, or b) by the wider public, at the user's discretion
- Other people are maintaining the code for me
- It's free
This setup has scope to solve my dog fooding issues from earlier–
- If adopted, my tech community can iterate the interface to suit its needs, find great content, and share content beyond the community.
- If adopted, my kids social groups can each have their own relays, but I can post to all of them together, or view a consolidated feed.
- If adopted, my team can chat with each other for free. I can self host this. It can natively interoperate with any other Nostr SaaS. It would be entirely private and will not be captured to train a Big Co AI without my consent.
Using your community website in practice
An example onboarding flow
- A new member joins your IRL community
- Your admin person gives them your landing page URL where they can view all the posts by your community members – If you have configured your relay to have no read auth required, then they can land on that landing page and immediately start viewing your community's posts, a great landing experience
- The user user creates a Nostr profile, and provides the admin person with their public key
- The admin person adds their key to the whitelists to read and write as you desire.
Default inter-op with the wider Nostr network
- If you change your mind on SW2 and want to use a different relay, your notes will be supported natively, and you can migrate on your own terms
- If you change your mind on Jumble and want to use a different client, your relay will be supported natively, and you can migrate on your own terms
- If you want to add other apps to your community's experience, every Nostr app will interoperate with your community by default – see the huge list at Awesome Nostr
- If any of your users want to view your community notes inside some other Nostr client – perhaps to see a consolidated feed of notes from all their different communities – they can.
For me, I use Amethyst app as my main Nostr client to view the public posts from people I follow. I have added my private community relay to Amethyst, and now my community posts appear alongside all these other posts in a single consolidated feed.
Scope to further improve
- You can run multiple different relays with different user access – e.g. one for wider company and one for your team
- You can run your own fork of Jumble and change the interface to suit you needs – e.g. add your logo, change the colours, link to other resources from the sidebar.
Other ideas for running communities
- Guest accounts: You can give a user "guest" access – read auth, but no write auth – to help people see the value of your community before becoming members.
- Running a knowledge base: You can whitelist users to read notes, but only administrators can post notes.
- Running a blind dropbox: You can whitelist users to post notes, but only the administrator can read notes.
- Running on a local terminal only: With Jumble and SW2 installed on a machine, running at –
localhost:5173for Jumble, andlocalhost:3334for SW2 you can have an entirely local experience athttp://localhost:5173/?r=ws://localhost:3334.
What's Next?
In my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest three blogs I explored different types of interoperability with NFC cards, n8n Workflow Automation, and now running a private community website on Nostr.
For this community website–
- There is scope to make some further enhancements to SW2, including to add a "Blossom" media server so that community admins can self-host their own rich media, and to create an admin screen for administration of the whitelists using NIP-86.
- There is scope to explore all other kinds of Nostr clients to form the front-end of community websites, including Chachi.chat, Flotilla, and others.
- Nostr includes a whole variety of different optional standards for making more elaborate online communities including NIP-28, NIP-29, NIP-17, NIP-72 (etc). Each gives certain different capabilities, and I haven't used any of them! For this simple demo they are not required, but each could be used to extend the capabilities of the admin and community.
I am also doing a lot of work with AI on Nostr, including that I use my private community website as a front-end for engaging with a Nostr AI. I'll post about this soon too.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ e516ecb8:1be0b167
2025-03-25 23:49:34
@ e516ecb8:1be0b167
2025-03-25 23:49:34En los años 20, Estados Unidos vivía una juerga económica conocida como los "Roaring Twenties". La Gran Guerra había terminado, la industria estaba en auge, los autos llenaban las calles y el jazz resonaba en cada esquina. Todo parecía ir viento en popa: las acciones subían como espuma, la gente compraba a crédito como si no hubiera mañana y los bancos estaban felices de prestar dinero. Pero, según los economistas austriacos —piensa en Ludwig von Mises o Friedrich Hayek—, esta prosperidad era una fachada, una burbuja inflada artificialmente que tarde o temprano iba a estallar.
La Escuela Austriaca sostiene que el verdadero villano de esta historia no fue la codicia de los especuladores ni el exceso de optimismo, sino algo más sutil y estructural: la manipulación del dinero y el crédito por parte de la Reserva Federal. Vamos a desglosarlo paso a paso, como si estuviéramos destapando una intriga.
Acto 1: La Reserva Federal enciende la mecha
Tras su creación en 1913, la Reserva Federal (el banco central de EE.UU.) tenía el poder de controlar la oferta de dinero y las tasas de interés. En la década de 1920, decidió que era buena idea mantener las tasas de interés artificialmente bajas. ¿Por qué? Para estimular la economía, ayudar a Gran Bretaña a volver al patrón oro y mantener la fiesta en marcha. Pero para los austriacos, esto fue como echar gasolina a una fogata.
Cuando las tasas de interés se mantienen bajas por decreto, el dinero se vuelve "barato". Los bancos prestan más de lo que lo harían en un mercado libre, y ese crédito fácil fluye hacia empresas, inversores y consumidores. Es como si le dieras a todo el mundo una tarjeta de crédito sin límite: la gente empieza a gastar, invertir y construir como si la riqueza fuera infinita. Pero aquí viene el giro: ese dinero no reflejaba ahorros reales ni riqueza genuina. Era una ilusión creada por la expansión del crédito.
Acto 2: El auge insostenible
Con este dinero barato, los empresarios se lanzaron a proyectos ambiciosos: fábricas, rascacielos, nuevas tecnologías. Los inversores, por su parte, corrieron a Wall Street, comprando acciones a crédito (lo que se llamaba "comprar al margen"). El mercado de valores se disparó: el índice Dow Jones pasó de 63 puntos en 1921 a 381 en 1929. ¡Una locura! La gente común, desde taxistas hasta amas de casa, se metió al juego, convencida de que las acciones solo podían subir.
Para la Escuela Austriaca, este "boom" era una distorsión. Según su teoría del ciclo económico, desarrollada por Mises y Hayek, cuando el crédito se expande artificialmente, los recursos se mal asignan. Imagina que eres un chef con un presupuesto limitado: si alguien te da dinero falso para comprar ingredientes, harás platos extravagantes que no puedes sostener cuando el dinero real se acabe. Eso estaba pasando en la economía: se construían cosas que no tenían demanda real ni base sólida.
Acto 3: La burbuja empieza a pincharse
Hacia 1928, algunos empezaron a oler problemas. La producción industrial comenzó a tambalearse, los inventarios se acumulaban y las deudas crecían. La Reserva Federal, dándose cuenta de que la fiesta se estaba descontrolando, intentó subir las tasas de interés para enfriar las cosas. Pero era demasiado tarde: la economía ya estaba dopada con crédito fácil, y el daño estaba hecho.
El 24 de octubre de 1929 —el famoso "Jueves Negro"— el pánico estalló en Wall Street. Los inversores, viendo que las acciones estaban sobrevaloradas y que sus deudas eran impagables, empezaron a vender en masa. El martes siguiente, 29 de octubre, el mercado colapsó por completo: millones de acciones cambiaron de manos, los precios se desplomaron y la riqueza en papel se evaporó. Pero para los austriacos, esto no fue la causa del problema, sino el síntoma. El verdadero desastre ya había ocurrido en los años previos, con la expansión artificial del crédito.
Epílogo: La lección austriaca
Desde la perspectiva de la Escuela Austriaca, el Crack del 29 no fue un fallo del libre mercado, sino del intervencionismo. La Reserva Federal, al manipular las tasas de interés y la oferta de dinero, creó una burbuja que era insostenible. Cuando estalló, la economía tuvo que pasar por una dolorosa "corrección": las empresas quebraron, los bancos cerraron y el desempleo se disparó. Para Mises y Hayek, esto era inevitable: el mercado necesitaba purgar los excesos y realinear los recursos con la realidad.
¿Y qué pasó después? Bueno, la Gran Depresión que siguió fue agravada, según los austriacos, por más intervenciones: el New Deal de Roosevelt y las políticas proteccionistas como la Ley Smoot-Hawley solo prolongaron la agonía. Pero esa es otra historia para otro café.
-
 @ 2f4550b0:95f20096
2025-03-25 23:09:57
@ 2f4550b0:95f20096
2025-03-25 23:09:57Recently, I tuned into a prominent podcast where the conversation turned to what children are learning in K-12 education (around the 1:24:20 mark). Among the contributors was a Silicon Valley tech investor who shared a startling anecdote about an elite private school. He described how, at what he called “the best all-girls private school in Silicon Valley,” students were taught that reading was racist. He went on: “There was a spreadsheet that these kids had to memorize every day that had every other kid’s pronoun, and if you didn’t get it right you’d get in trouble.”
I was floored, not just by the absurdity of the curriculum, but by the casual assertion that a school teaching such ideas could still be deemed “the best.” How could an institution so detached from a rigorous, skill-building education retain that lofty title? I reflected on what truly makes an elite private school worthy of being called “the best,” a label too often thrown around without scrutiny.
Historically, top-tier private schools earned their reputations through academic excellence, robust curricula, and a commitment to preparing students for leadership and success. Think of the traditional hallmarks: mastery of core subjects like literature, mathematics, and science; critical thinking honed through debate and analysis; and extracurriculars designed to cultivate discipline and creativity. These schools were exclusive not just for their price tags but for their promise to deliver an education that equipped graduates to thrive in competitive universities and careers.
Yet the anecdote from that podcast suggests a troubling shift. If a school prioritizes ideological conformity (say, memorizing pronouns or framing foundational skills like reading as racist) over intellectual rigor, it’s fair to question whether it still deserves its elite status. Prestige, wealth, and social cachet might keep a school “elite” in name, but “the best” should mean more than that. It should reflect a dedication to fostering knowledge, skills, and independent thought, qualities that empower students as future leaders, not pawns in a cultural tug-of-war.
Consider what parents and students expect from a premium education. For an astronomical tuition (often exceeding $40,000 annually in places like Silicon Valley) they anticipate a return on investment: a curriculum that challenges young minds, teachers who inspire rather than indoctrinate, and a culture that values merit over dogma. When a school veers into territory where basic literacy is politicized or rote memorization of social rules trumps critical inquiry, it betrays that trust. No spreadsheet of pronouns will help a graduate navigate a complex world; a firm grasp of history, science, and persuasive writing just might.
This isn’t to say elite schools shouldn’t evolve. The world changes, and education must adapt, whether by integrating technology, addressing current issues, or broadening perspectives. But adaptation should enhance, not replace, the core mission of learning. A school can teach ethics alongside traditional subjects without sacrificing intellectual integrity. The problem arises when ideology becomes the curriculum, sidelining the tools students need to reason for themselves. If students are taught to question reading instead of mastering it, how will they author their own futures?
The Silicon Valley example isn’t isolated. Across the country, elite institutions have leaned into progressive trends, prioritizing social justice frameworks and experimental pedagogies over substance. Some might argue this reflects a bold reimagining of education, but there’s a difference between innovation and derailment. A school can be forward-thinking without abandoning the fundamentals that define excellence. Parents paying top dollar, and students investing their formative years, deserve more than a trendy experiment.
So, what should define “the best” private school today? First, employ a curriculum that balances tradition and progress: teach Shakespeare and coding, ethics and algebra, with an eye toward real-world application. Second, hire a faculty of experts who challenge students to think, not just comply. Third, create an environment that rewards effort and achievement over adherence to a script. Prestige alone, whether from alumni networks, manicured campuses, or Silicon Valley buzz, can’t suffice.
The tech investor’s remark about “the best” stuck with me because it revealed a disconnect. A school might remain elite in the eyes of the wealthy or well-connected, but “the best” is a higher bar. It’s a title earned through results, not rhetoric. Until these institutions recommit to education over indoctrination, they risk losing not just their claim to excellence, but the trust of those they serve.
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-25 23:01:15
@ 5d4b6c8d:8a1c1ee3
2025-03-25 23:01:15As we close in on the playoffs, especially with the mighty regular season Cavs stumbling a bit, I wanted to zoom out and get some historical perspective on what it takes to be an NBA champion.
Over the past 20 years, here's the complete list of the 10 guys who were the best player on a title team. 1. Lebron 4x 2. Steph 4x 3. Duncan 3x 4. Kobe 2x 5. Tatum 6. Jokic 7. Giannis 8. Kawhi 9. Dirk 10. Garnett
The worst players on that list are better than anyone on the Cavs, or several other playoff teams. Unless we're going to have an '04 Pistons anomaly, the only teams I see with players who might belong on that list are the following: - Celtics (Tatum's already there, after all) - OKC (SGA's having the best guard season since MJ) - Denver - Milwaukee - Lakers - Clippers (If Kawhi's still that guy) - Warriors - T-Wolves
Eight is actually a lot, but only two of these teams are playing like contenders.
What do you think? Can we rule out the teams that aren't on this list? Am I slandering someone by leaving them out? Or, is this just nonsense masquerading as analysis?
originally posted at https://stacker.news/items/925135
-
 @ 7da115b6:7d3e46ae
2025-03-25 22:59:06
@ 7da115b6:7d3e46ae
2025-03-25 22:59:06These are in order of least to most complex.
Be Warned: Some of these ingredients may be unique to New Zealand and Australia
Pikelets
Pikelets are delicious with butter and jam or jam and whipped cream. To make Pancakes, double this recipe and make them larger. Serve in a stack with butter, maple syrup, bacon and blueberries. I've found a single batch is good for 2-4 people if you just want a snack.
Prep Time: 5 minutes Cooking Time: About 10 minutes
Ingredients: - A Cup Self Raising Flour - A Quarter Teaspoon of Table Salt - 1 Egg - A Quarter Cup of White Sugar - About 3 quarters of a Cup of Whole Milk
Method: 1. Sift the Flour and Salt into a bowl. 2. In another bowl beat the Egg and Sugar with a whisk until pale and thick. 3. Add the Egg mixture and the Milk to the dry ingredients and mix until just combined. 4. Gently heat a non-stick frying pan and drop tablespoonfuls of the mixture from the point of the spoon onto the surface. 5. When bubbles start to burst on the top of the Pikelets, turn them over and cook the second side until golden. 6. Place in a clean tea towel to cool.
This recipe requires a little experience to get right, especially if you prefer to use a cast iron pan or griddle. Basically, you can use a cast iron or aluminium pan, just make sure to grease the pan between each batch. The easiest way to do it, is to grab some baking paper, or butter paper wrap, scrunch it up and wipe it over the block of butter, and then wipe the surface of the pan. After the first round has cooked, do wipe the butter over the pan again. It'll stop the Pikelets from sticking.
Scones
These are based on an old recipe from the Edmond's Cookbook, and have been a Kiwi staple for decades. The yield is about 12 (ish), but it depends on how big or small you shape them.
Prep Time: About 10 minutes Cooking Time: 10 minutes (Depending on your Oven)
Ingredients: - 3 Cups of Premium White Wheat Flour - 2 and a Half Levelled Tablespoons of Baking Powder - A quarter of a Teaspoon of Table Salt - About a Third of a Cup of Butter - Between 1 to 1.5 Cups of Whole Milk
Method: 1. Preheat the oven to 220C. 2. Grease or flour a baking tray. 3. Sift the flour, baking powder and salt into a bowl. 4. Rub in the butter with your fingertips until the mixture resembles fine breadcrumbs 5. Add the milk and quickly mix with a round-bladed table knife to a soft dough. For light and tender scones the mixture should be quite soft and a little sticky. 6. Scrape the dough onto the floured baking tray and flour the top 7. Working quickly, pat the dough out to 2cm thickness and with a floured knife cut it into 12 even-sized pieces, then separate the scones to allow 2cm space between them. 8. Brush the tops with milk. 9. Bake for 10 minutes or until golden brown. Place on a wire rack to cool, wrapped in a clean tea towel to keep them soft.
They're great with Butter or Whipped Cream and Jam. 3-4 per person is excellent with some hot sweet Tea mid afternoon.
A little variation that used to be popular is to dice up about a a cup of Bacon, grate about a cup of Cheese, and throw it in the batter for a savoury twist.
Remember to not overcook them, otherwise they come out dry and crumbly.
Chocolate Muffins
I can't remember where I got this recipe, but I've made them dozens of times over the years. They really fill the gap when it comes to those hungry little faces pleading for snacks. This recipe is a little more complicated, but worth it. They're soft and moist, and extremely more-ish. I can personally eat about half on my own before I start feeling guilty. You can get about 12 muffins out of this mixture.
Prep Time: 20 minutes Cooking Time: About 18 minutes
Ingredients: - 1 and a quarter Cups Self Raising Flour - A quarter Cup of Cocoa Powder - 3 quarters of a Teaspoon of Baking Soda - A Quarter Teaspoon of Table Salt - Half a Cup of Soft Brown Sugar - A Quarter Cup of White Sugar - Half a cup of Chocolate Chips - An Egg - Half a Cup of Greek Yoghurt or Sour Cream - Half a Cup of Whole Milk - A Quarter Cup of Sunflower Oil (substitute with warmed dripping/butter or clean cooking oil to taste) - 1 Teaspoon of Vanilla Essence
Method: 1. Preheat oven to 180C on fan bake. 2. Line a 12-hole muffin tin with paper cases. 3. Sift the Flour, Cocoa Powder, Baking Soda and Salt into a large bowl. Stir in the White and Brown Sugars, followed by the Chocolate Chips. 4. In a separate bowl, whisk together Egg, Yoghurt (or Sour Cream), Milk, Oil (or Butter/Dripping) and Vanilla Essence. 5. Add the mixture to the dry ingredients and mix until just combined. Try not to over-mix it, you're not looking for a smooth texture, just no unmixed dry ingredients. 6. Divide mixture evenly between 12 muffin paper cases. 7. (Optional) Sprinkle with extra chocolate chips, for decoration. 8. Bake for 18-20 minutes, until muffins spring back when lightly pressed. 9. Leave to cool in tins for a couple of minutes before transferring to a wire cooling rack.
If you're feeling especially fancy, you can slice them open, and add a dollop of jam and whipped cream. Garnish with a Mint Leaf or Glacé Cherry. Using a Sieve, you can powder the top with Icing Sugar if you want to go that extra mile. It's a real Wifey pleaser.
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ bc52210b:20bfc6de
2025-03-25 20:17:22
@ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient.
This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off!
Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now.
CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused! Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why:
- Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs).
- Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key.
Key Differences: 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control.
So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs!
Two Flavors of CISA: Half-Agg and Full-Agg CISA comes in two modes:
- Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.)
- Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later.
Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg.
Half Signature Aggregation (Half-Agg) Explained How It Works Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process:
- Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers.
- Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature.
A Schnorr signature has two parts:
- R: A random point (32 bytes).
- s: A scalar value (32 bytes).
In Half-Agg:
- The R values from each signature are kept separate (one per input).
- The s values from all signatures are combined into a single s value.
Why It Saves Space (~50%) Let’s break down the size savings with some math:
Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes.
After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes.
Comparison:
- Original: 64n bytes.
- Half-Agg: 32n + 32 bytes.
- For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings!
Real-World Impact: Based on recent Bitcoin usage, Half-Agg could save:
- ~19.3% in space (reducing transaction size).
- ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA.
Applications of Half-Agg Half-Agg isn’t just a cool idea—it has practical uses:
- Transaction-wide Aggregation
- Combine all signatures within a single transaction.
- Result: Smaller transactions, lower fees.
- Block-wide Aggregation
- Combine signatures across all transactions in a Bitcoin block.
- Result: Even bigger space savings at the blockchain level.
- Off-chain Protocols / P2P
- Use Half-Agg in systems like Lightning Network gossip messages.
- Benefit: Efficiency without needing miners or a Bitcoin soft fork.
Challenges with Half-Agg While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level:
- Breaking Adaptor Signatures
- Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges.
-
Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on.
-
Impact on Reorg Recovery
- In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed.
- If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery.
These challenges mean Half-Agg needs careful design, especially for block-wide use.
Wrapping Up CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning.
But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
-
 @ 6a6be47b:3e74e3e1
2025-03-25 20:16:37
@ 6a6be47b:3e74e3e1
2025-03-25 20:16:37Hi frens, how are you?
🎨 I've been keeping busy with some personal projects and haven't painted as much as I'd like, but most importantly, I've returned to painting with watercolors. I'm getting used to them again, and although I love them, they can be tricky, especially when working wet on wet.
I've done a few pieces since getting back into it, and I'm excited to show the results, but at the same time, I'm a bit wary. Not because I want them to be "perfect" to share, but because I just want to have fun with them and get the joy back from painting.
🐱 And I'm not slacking because I have my furry little helper with me, and he's not having any of it!

He's a good boi

I've also been baking! 👩🍳 Yesterday, I made cinnamon "donuts" 🍩 , which ended up being muffins since I don't have a donut skillet.

And today, I baked lemon muffins 🍋, and they turned out delicious!

🧁 I had one as soon as they cooled, and chef's kiss... they're amazing!
🫀So as you can see I've been up to a few things, I'm not the best at this social media game. It can be draining so I want to have a balance between creating and showcasing you my proof of work 💪
💎I'm still getting there, but it's worth it.
🪄 Balance to achieve harmony is my goal.
🔮 I just wanted to check in and see what you've been up to! I'd love to know 🩷🫶🏻.
Have an amazing day frens!
-
 @ 2ed3596e:98b4cc78
2025-03-25 19:12:58
@ 2ed3596e:98b4cc78
2025-03-25 19:12:58Americans can now buy bitcoin on the Lightning Network directly from their bank with their Bitcoin Well account. By using the dollars in your Bitcoin Well Cash Balance you can buy bitcoin over the Lightning Network with instant delivery. You can also go directly from your bank to your Lightning Wallet. You can now live fully on a Lightning-powered bitcoin standard ⚡️
How to buy bitcoin on the Lightning Network instantly:
-
Add your Lightning Payment Address (LNURL) to your Bitcoin Well account
-
Enter the amount of dollars you want to buy bitcoin with
-
Choose your Bitcoin Well Cash Balance (you may need to fund this first!)
-
SMASH BUY! Your Lightning wallet will receive sats in seconds 🏎️
\ You can also go directly from your bank to your Lightning wallet. Your bitcoin will be sent over the Lightning network as soon as your dollars arrive (usually within 3 business days).
Here are detailed steps to guide you on how to buy bitcoin on the Lightning Network 👇
Step 1: Get your Lightning details
Go to your Lightning wallet and copy your Lightning Payment Address (looks like an email address). A Payment Address is not a Lightning invoice, but rather a static receiving address similar to a bitcoin receiving address. The benefit of using a Payment Address is that you can passively receive any quantity of sats at any time; unlike an invoice, a Payment Address does not have an expiry or a fixed amount of sats limiting the amount can be received. \ \ In the example below we use the Coinos.io wallet to obtain a Payment Address. Coinos is a powerful and easy to use Lightning wallet available in any country via your favourite web browser. You can set up a Coinos Lightning wallet and start receiving sats in seconds.

\ Coinos features a Lightning Payment Address. Once you’ve set up your wallet, hit “Receive” to access your Payment Address.
Step 2: Add your Lightning wallet to your Bitcoin Well account
Log in to your Bitcoin Well account and navigate to Buy bitcoin. From the buy screen, select bank or balance and add your Lightning wallet to the Destination by clicking Add wallet. Add your Lightning Payment Address from Step 1 here.
Step 3: Buy bitcoin on the Lightning Network
After you’ve selected your source and added your Lightning Payment Address as the destination, you are ready to complete your bitcoin purchase on the Lightning Network! \ \ When buying bitcoin from your Cash Balance, the dollars will instantly convert to bitcoin and be sent directly to your Lightning wallet – delivery takes less than a minute! 🤯\ \ When buying bitcoin from your bank account, you can expect to wait at least a couple business days as we wait for the slow movement of fiat to be finalized before sats can be sent.
## The compromise is over: bitcoin fast, easy and cheap
In the past, Bitcoiners had to choose between using freedom money at the mercy of the speed and cost of Bitcoin’s blockchain, or use the legacy banking system while surrendering their monetary freedom and independence. Ideally, Americans never have to compromise their monetary principles; thankfully, they no longer have to. \ \ Stacking sats straight to the Lightning also enables an innovative way to manage UTXOs. Now anyone can stack sats as much as they like without worrying about UTXO bloat. Simply accumulate sats on your Lightning wallet and then swap it across to your on-chain wallet in one neat UTXO. Since Coinos is a custodial Lightning wallet, you should periodically send your sats to your self-custody hardware wallet. To help you get the most out of the Lightning network, Bitcoin Well has a free swap tool that lets you swap sats between on-chain and Lightning. While this feature is only available in Canada, it will make its way to the United States very soon 🤫
Haven’t signed up with Bitcoin Well yet? Sign up here to start living on a (Lightning powered) Bitcoin Standard free from custodians and centralized honey pots.
Earn sats from your bitcoin transactions
\ Bitcoin Well is also the best place in the world to earn bitcoin. When you earn points in your Bitcoin Well account, you gain the opportunity to play the Bitcoin (Wishing) Well, where you win sats with every play.
The best part? We send bitcoin that you win straight to your personal wallet via the Lightning Network ⚡
Oh yeah, did we mention you can win 1,000,000 sats? If you're an active Bitcoin Well customer, there is a chance you've earned a pile of points. The more you use your account for buying, selling or spending bitcoin - the more points you’ll earn! Log in to your Bitcoin Well account and check your point balance.
About Bitcoin Well
\ Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we make it easy to use bitcoin with self-custody.
-
-
 @ 7d33ba57:1b82db35
2025-03-25 18:31:35
@ 7d33ba57:1b82db35
2025-03-25 18:31:35Located on the Costa de la Luz, Conil de la Frontera is a charming Andalusian fishing village known for its golden beaches, whitewashed streets, and delicious seafood. With a laid-back atmosphere, it’s perfect for relaxation, surfing, and enjoying authentic Spanish culture.

🏖️ Top Things to See & Do in Conil de la Frontera
1️⃣ Playa de los Bateles 🏝️
- The main beach, right next to the town center.
- Long stretches of soft golden sand with clear Atlantic waters.
- Ideal for sunbathing, swimming, and beachside dining.
2️⃣ Playa de la Fontanilla 🌊
- One of the most beautiful beaches in the region, with crystal-clear waters.
- Great for families, surfers, and seafood lovers.
- Home to some of the best chiringuitos (beach bars) in Conil.
3️⃣ Playa del Palmar 🏄♂️
- A surfer’s paradise with consistent waves and a bohemian vibe.
- Popular for surf schools, yoga retreats, and sunset beach bars.
- Less crowded than the town’s main beaches.
4️⃣ Historic Old Town & Plaza de España 🏡
- Wander through narrow, whitewashed streets full of local boutiques, tapas bars, and cafés.
- Visit the Plaza de España, the town’s lively main square.
- Stop by the Torre de Guzmán, a medieval watchtower with great views.
5️⃣ Mercado de Abastos 🐟
- A traditional market where locals buy fresh seafood, fruits, and vegetables.
- Great place to experience the authentic Andalusian food culture.
6️⃣ Mirador del Jabiguero 🌅
- One of the best viewpoints in town, offering panoramic views over Conil and the Atlantic.
- A perfect spot for sunset photos.
🍽️ What to Eat in Conil de la Frontera
- Atún de Almadraba – Fresh bluefin tuna, caught using a traditional method 🐟
- Ortiguillas fritas – Fried sea anemones, a local delicacy 🍤
- Choco a la plancha – Grilled cuttlefish, a simple but delicious dish 🦑
- Tortillitas de camarones – Light and crispy shrimp fritters 🥞🦐
- Sangría or Tinto de Verano – Refreshing drinks to enjoy by the beach 🍷
🚗 How to Get to Conil de la Frontera
🚘 By Car: ~45 min from Cádiz, 1.5 hrs from Seville, 2.5 hrs from Málaga
🚆 By Train: Nearest station is San Fernando-Bahía Sur, then take a bus
🚌 By Bus: Direct buses from Cádiz, Seville, and other Andalusian cities
✈️ By Air: Closest airport is Jerez de la Frontera (XRY) (~1 hr away)💡 Tips for Visiting Conil de la Frontera
✅ Best time to visit? May to September for beach weather, spring & autumn for fewer crowds 🌞
✅ Book accommodation early in summer – It’s a popular vacation spot 🏡
✅ Try local tuna dishes – Conil is famous for its bluefin tuna 🍽️
✅ Visit during the Feria de Conil (June) for a lively cultural experience 🎉 -
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 378562cd:a6fc6773
2025-03-25 17:24:27
@ 378562cd:a6fc6773
2025-03-25 17:24:27In an era where the value of traditional money seems to shrink by the day, many turn to Bitcoin as a potential safeguard against inflation. But is Bitcoin truly a hedge, or is this just wishful thinking? Let’s break it down.
Understanding Inflation Inflation occurs when the purchasing power of money declines due to an increase in prices.
Central banks, like the Federal Reserve, often print more money, leading to more dollars chasing the same amount of goods.
Over time, inflation erodes savings and makes everyday items more expensive.
Why Bitcoin is Considered an Inflation Hedge Limited Supply – Unlike the U.S. dollar, Bitcoin has a fixed supply of 21 million coins, making it immune to money printing.
Decentralization – No government or central bank can manipulate Bitcoin’s supply or devalue it through policy changes.
Digital Gold – Many see Bitcoin as a modern version of gold, offering a store of value outside traditional financial systems.
Global Accessibility – Bitcoin operates 24/7 across borders, making it accessible to anyone looking to escape failing currencies.
Challenges to Bitcoin as an Inflation Hedge Volatility – Bitcoin’s price swings wildly, making it risky as a short-term hedge.
Adoption & Trust – Unlike gold, which has been a store of value for centuries, Bitcoin is relatively new and still gaining mainstream acceptance.
Market Correlation – At times, Bitcoin moves in tandem with stocks rather than acting as a safe-haven asset.
Regulatory Uncertainty – Governments around the world continue to debate Bitcoin’s place in the economy, which can impact its long-term stability.
The Verdict: Fact or Fiction? ✅ Long-Term Potential: Over the years, Bitcoin has shown signs of being a hedge against currency devaluation, especially in countries with hyperinflation. ⚠️ Short-Term Reality: Bitcoin’s volatility makes it unreliable as an immediate hedge, unlike traditional safe-haven assets like gold.
For those who believe in Bitcoin’s future, it could be a strong long-term hedge. However, for those looking for immediate inflation protection, it’s still a speculative bet.
Would you trust Bitcoin to safeguard your wealth? 🚀💰
What do you think? Share your comments below.
-
 @ 3c389c8f:7a2eff7f
2025-03-25 17:12:33
@ 3c389c8f:7a2eff7f
2025-03-25 17:12:33Understanding Relays
Relays are a very simple concept, but an incredibly powerful part of Nostr. They are simple servers, of sorts, with a specific set of tasks- to fetch, hold, and send notes. Relays don't communicate with each other, only with clients. The client sends a request for any relevant notes and the relays oblige. What types of notes (aka events) that each relay will hold or fetch will vary because of different relays will operate under different sets of rules. Some will accept most any type of event from anyone. Others can be very strict, requiring things like payment, proof-of-work, specific event kinds, or only allow a whitelist of users to reduce spam and other unwanted content. When you create an event, or publish a note, it is sent to your "write" or "outbox" relays. Anyone who follows your npub or sends "fetch" /"read" requests, to those relays will receive your notes. When someone replies, likes, or otherwise engages with your note, that note will then duplicate to any "write" or "outbox" relays that the other person is connecting to as their outbox relays. This does two important things:
It creates a new event through through the action of engaging your note. This is a signed record of activity from that user's npub. This is also the event that is sent back to your "read" or "inbox" relays so that you may be notified that someone is interacting with you.
By creating a copy, this helps ensure your note will be able to be spread across more of the ecosystem, expanding your reach and introducing redundancy, in case a relay should go down or disappear completely. This does not imply that your data will be safely stored forever. In fact, its the exact opposite. The protocol assumes that any relay, or many, could disappear at any time. A relay can shut down, kick you out, experience intentional or unintentional data loss, or many other things. It is likely that a copy of your notes will still exist on many relays, but if you are concerned with the longevity of your content, consider running your own. Paid services for long term note storage exists as well, but they do require trusting the provider.
In this light, the importance of relays starts to become obvious. The various rules open up a whole plethora of use cases that make relays interesting, unique, and useful for the user. They are the backbone of the protocol. They are also tools for finding and managing great social connections and great content.
Types of Relays
This section can, in no way, be considered comprehensive. It is nearly impossible to know all of the relay implementations that may exist or all the rules that they may have set for themselves. Here, we will address some common types that will be useful in making the most of Nostr and a few types with specialized tasks.
Public Relays - Most Nostr clients will start new users with a predetermined set of relays that are free and publicly available for fetching and serving. This lowers the entry barrier for getting connected to the network, ensuring that everyone has access. It does come with some tradeoffs. Public relays tend to accept almost any type of content, so they are prone becoming the hosts of spam, bots, and shady content. To curate your space, it is recommended to get connected with some relays that help you clean things up.
Web-of-Trust Relays - These relays use your social graph and the graphs of others to build a network of higher trust for its users. This reduces spam and other yucky stuff from making it into your feeds. For write access, you must be followed by someone else within the network. If you are coming to Nostr with no external social connection, these may not be useful at first, though most do allow for public reading so you may find them useful to discover people and content you find interesting. Once you have established some social connections, they are great for creating a feed that casts a wider net through the whole network.
Paid Read/Write Filter Relays - These relays will charge an admission fee for write access. This helps to reduce spam and bots. Not all paying npubs want to see or interact with all who are willing to pay the fee, so a paid write relay often works best when paired with a paid filter relay for reading. These will operate under many sets of filtering rules, so be sure to read through any available material from the provider. They should explain what they filter and why, so that you may choose filters that match your tastes.
Inbox Relays - These relays are tasked with collecting any events that are intended FOR you. This includes likes, replies, receipts, and mentions, among many other things. If socializing with your friends and colleagues is important to you, you will want to find inbox relays that manage this task well. DM inbox relays are a separate but similar concept, as direct messages are encrypted and wrapped. They are a specialized relay meant for handling encrypted events. Many DM inbox relays charge a subscription fee, some do not. This is also a great use case for private relays.
Private Relays - These relays can be arranged to handle nearly anything you would like. You can whitelist a group of people that can write, restrict read access through AUTH, and set other various rules. They are a great option for any encrypted data, such as DMs, lists, and drafts. They also make a great backup for your own notes to help ensure that they remain available and locatable. Running your own is the optimal option here, but there are paid services, that I think of as relay rental. They are hosted on big servers, and managed by a small company. All details of the relay rules are at the renter's discretion. This is a good option if you do not have the hardware or confidence to set up your own private relay yet.
Search Relays - Search relays can help you find specific users & notes across the wider network. Some specialize in searching for people, others for text, tags, and other criteria. A strong search relay can make navigating through Nostr a breeze. As with other things, some may require a small fee to use them and others are free to use. Try out some free ones before buying to see if you are happy with your experience.
"Read" Relays - This is sort of a catchall term for anywhere that your client connects to for fetching notes and other events. In the best scenerio, you should not have to worry about these, as relays will signal for your client to find the notes you are fetching. The Nostr protocol and its mechanisms are adapting to what works, so being informed of "read" relays is essential for now. These are the places that you may need to tell your client to connect to when fetching notes from the people you follow. Specialized Relays - Specialized relays will vary in function and rules. Some are for curating quality feeds while others host full-fledge communities around a topic or common interest. Clients designed to interact with these more specialized use cases will often have relay information available or a method for you to browse their feeds.
This is just a snapshot of the different types of relays that exists now. Many are in development and testing for algorithmic content distribution, paywalled content, encrypted group messaging, limited read access, media hosting, and more. (This section may be updated as certain types gain or lose traction throughout the ecosystem.)
Managing Relays
By now, this probably feels like a ton of information and it is, but its also part of what gives you the ability to create and maintain a quality experience with Nostr. A truly decentralized system puts power into the user's hands rather than a corporation. If you want to be in control of your space (spatium tuum), relays are the first and foremost way to do that. They don't have to be viewed as boring servers. They are anything but that. They are tools that can enhance your online networking, serve you educational or entertaining content, or provide you with a safe place to store your personal thoughts. What you use them for is up to YOU.
Spend some time trying free ones, exploring relay feeds, or plugging into some paid services until you find a setup that creates a quality online space for you. If you're worried that you might "break" your connection, don't be. Make a note of a couple that you are connecting to when getting started, as a backup, but I feel confident to say that you won't ever look at it again.
Finding Relays
Finding relays can be a bit of a chore, but that is getting easier as time goes by. For now you there a few options you can try.
-
Visit a relay explorer like nostr.watch or nostr.info
-
Use a client that shows you which relays are hosting a note or a person's relay list. There are some examples in our client guide like Amethyst, Coracle, Jumble, and Nostrudel.
-
Just ask. Most people are on a social network to be social. Currently, Nostr is brimming with social people who are passionate about freedom, decentralized communication, and Nostr in particular. They are happy to help.
Running Your Own
Relay.tools is a hosted personal relay service for ease and a user friendly experience. Search Zapstore for Citrine to run a native relay on your Android device.
Below are some suggestions for relays to run on your own hardware. Search "nostr relay" on GitHub for more.
https://utxo.one/#nostr-projects
https://khatru.nostr.technology/
https://github.com/mikedilger/chorus
nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqyghwumn8ghj7mn0wd68ytnhd9hx2tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qqdxymngv35xq6rxdf5xqer2s0rg3q
-
-
 @ 27dd78c2:66ffe658
2025-03-25 17:12:08
@ 27dd78c2:66ffe658
2025-03-25 17:12:08In an age where ‘run clubs’ are getting more popular than ‘night clubs’, it’s exciting to see a Nostr-based sovereign fitness tracker hit the scene: Enter Runstr.club!
Runstr has emerged as a game-changer, redefining how runners connect, track progress, and stay motivated. For Bitcoin Runners, a movement that advocates sovereignty of one’s wealth, while improving one’s health, Runstr.club presents an exciting platform of choice to record your proof-of-work, take ownership of your personal data, and selectively engage with your social graph.
What is Runstr.club?
Runstr.club is a platform that’s being built to grow the proof-of-work community, with plans to offer interactive leaderboards, challenges, and social engagement. Unlike traditional running apps that focus purely on statistics, Runstr.club puts emphasis on camaraderie, motivation, and shared goals. It’s the Strava alternative that values ownership of your data, interoperability between platforms, and privacy as standard.
Why Runstr.club is a Great Fit for Bitcoin Runners
Bitcoin Runners isn’t just about proof-of-work; it’s about promoting freedom tech, decentralisation, and self-sovereignty principles that align closely with the ethos of Runstr.club.
Here’s why this platform is a great match for our movement:
- Community-Driven & Decentralised Spirit
Bitcoin Runners thrives on grassroots adoption and community participation, much like Runstr.club’s organic and community-focused model. Unlike corporate-owned fitness platforms that prioritise monetisation, Runstr.club is designed to empower runners, keeping the experience authentic and meaningful.
- Privacy-First Approach
One of the key concerns for bitcoiners is privacy. Mainstream fitness platforms harvest user data for profit, but Runstr.club offers a privacy-first alternative. This makes it an excellent choice for runners who value sovereignty in the digital age.
- The Advantage of Nostr Over Centralised Run Tracking Tools
Most mainstream running apps, like Strava or Nike Run Club, rely on centralised platforms that control user data, impose restrictions, and often monetise user activity. Runstr.club, however, is built on Nostr, a decentralised protocol that enables users to interact without getting trapped inside a walled garden.
With Nostr, runners benefit from:
-
True ownership of their data – no risk of platforms selling or misusing personal running history.
-
Resilience against censorship – no arbitrary bans or content moderation dictated by a 'shadowy suit'.
-
Interoperability – seamless integration with other Nostr-based applications, keeping data fluid and accessible across different platforms.
-
Peer-to-peer connectivity – allowing runners to share progress, create challenges, and stay engaged independent of big tech.
For Bitcoin Runners, Nostr’s decentralised nature aligns perfectly with the principles of sovereignty, freedom, and privacy.
- Gamification & Challenges
Runstr.club has engaging challenges and decentralised leaderboards on its roadmap. Whether you’re stacking sats through running-related bitcoin challenges or simply competing with fellow bitcoiners for fun, the platform will add an extra layer of engagement to every run. We would love to see such features come to life!
Conclusion
Runstr.club is more than just a running tracker—it’s a Nostr, bitcoin, and fitness onboarding community-driven movement. By embracing platforms that respect privacy, encourage competition, and foster community, we stay true to our values while pushing our limits as runners.
Let’s take this to the next level - be sure to follow Runstr on Nostr!
Run free. Stay sovereign. Stack zaps!
We’re shilling this open-source initiative out of genuine appreciation for both its vision and the dedicated team behind it.
-
 @ 3c389c8f:7a2eff7f
2025-03-25 16:38:21
@ 3c389c8f:7a2eff7f
2025-03-25 16:38:21Public Key vs Private Key
When you generate a Nostr identity, you generate a cryptographic keypair. One is your public key (npub...). It is used to find you and your notes. The other is your private key (nsec...), which you use to interact. Everything you do is an event, which is signed by your private key. This makes all of your actions provably yours. You are solely responsible for protecting your nsec. It is recommended to try Nostr with a test keypair before setting up anything that you want to treat seriously.
Key Creation and Protection
Most Nostr clients will have the option to generate a keypair onsite or in-app. This is convenient for trying Nostr or a client. To make a keypair for longterm use, you might want to visit a site that provides some key security from the start. Your keys are a permanent set of identifiers. They cannot be changed or reset. You own them and it is your responsibility to keep your private key safe.
When you are ready to set up a permanent identity, start in a place that specializes in Nostr key generation. Nstart and Hubstr are great places to start. NOA, Nostr Onboarding App, is multiplatform with a native app, which helps make it easier to share with friends. You can create a vanity npub through various methods as well, like https://www.nostr.rest/ . There are other methods but these are some of the most user friendly ones that I have found. They provide some tools and guidance for creating your keypair in a safe manner. Once you've gone through the process, it is a good idea to write down your nsec and store it off of any devices, in the event you should lose access to your computer or phone.
Using a signer or a browser extension to house your nsec (private key), is the next step to keeping your identity safe. (Find out more on key management below)
Portability of Your Keys
This is where all the magic happens. You can use your keys to sign into any Nostr app. If you sign in with your npub (public key), you will enter in a read-only mode. This is nice for seeing a client's interface before trying it. You can sign in with anyone's npub to see what their social feeds look like, too. You do not need to be concerned with security when using npub sign-in. Your public key, is fully public. Not all Nostr clients support this option, but many do.
Signing in with your nsec unlocks all the features of a client and enables you to interact on the protocol. Everything you do is signed by your nsec and made available by your npub. Using some sort of signer is obviously advised, to keep from exposing your nsec online.
Since all of your actions (aka events) are stored on relays and not by clients, all of your content, messages, or anything else becomes available in any client that supports those event types. Most social stuff, like replies and profile views are available almost everywhere. Not all apps will support everything, but the ones that share a common theme will handle your events in similar manners. (I.e., a marketplace listing made from one app will display across many apps. The comments and replies will, too, so there is no need to manage multiple listings to answer questions or mark something as sold.)
Key Management
This is an evolving field, with many methods of key management being explored. People, businesses, and institutions all have different needs.
Signing Extensions keep your key in a browser extension, signaling to an app that the valid nsec is present. This sign in method is available on most Nostr apps. These are the most convenient method of key management but they do have their limitations. Using an extension can be cumbersome on mobile devices, and they could still be subject to vulnerabilities within your browser or the signer itself. They also don't allow for multiple users to sign events, like a business or organization might need. Key Bunkers enable the storage of key shards encrypted across multiple locations or in one spot. Bunker signing calls the encrypted key shards to decrypt for signing events. A bunker key, often called a bunker string, can be shared with staff or used to keep your key offline. They are revocable and replaceable. The process is currently a a little complicated and client support is somewhat limited. Adoption and improvement of this method is happening quickly, as the need for multi-party access to a profile increases. Native Signing Apps, like Amber for Android, make key key storage and signing for mobile a simple process. These apps work to keep your key offline, similarly to a bunker, but it is all stored encrypted on your device. Most Nostr-Android apps and web clients offer support for this method. Development of a similar iOS app is underway. Offline Hardware Signers like standalone devices and NFC cards are being explored, tested, by many groups.
This is a very active development space and this section will be updated as needed. Below are some suggestions for Nostr signers:
https://nsec.app/ https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp https://www.getflamingo.org/
-
 @ 3c389c8f:7a2eff7f
2025-03-25 16:16:29
@ 3c389c8f:7a2eff7f
2025-03-25 16:16:29Android
Amethyst - Experience the all-in-one Nostr client for mobile. Amethyst supports custom emoji reactions, marketplace listings, live streams, and so much more. If you're fresh to exploring Nostr, Amethyst may seem like a wild adventure compared to the any other social media of the past. Packed with features and blazing fast, this client gives you the ability to see just what Nostr is all about.
Voyage - This client is light on storage and data consumption, which is great for anyone with cheaper phones, limited data plans, or traveling/living in areas with lower data signal. Not only that, Voyage also offers some list and relay management tools not available in many other apps, so its great for handling some of the technical aspects of Nostr on the fly.
Web
Satellite - Fast and reliable, this client has topic communities, rich feeds, and beautiful profile displays. They offer paid media hosting for pictures, videos and more, which is essential for sharing visual content on Nostr. Satellite has long been a favorite for its simplified approach to displaying notes in a dense, clean manner and its consistency, reliability, and speed.
Jumble - Explore Nostr relay feeds, follow feeds, and more. Jumble has a clean, no-fluff interface that's easy to use and understand. You can socialize on specialized relays, or browse and chat on public relays with friends.
Coracle - Coracle allows you to easily browse relay feeds, your follow feed, and create custom feeds. You can generate Proof-of Work notes, set 'send' delays, and limit the number of relays the client talks to, to increase speed and reduce data consumption. You can generate PoW anonymous replies, too. A favorite feature is the option to import and export all of your data to/from your local device, so you can easily maintain a copy or send any lost events back to the Nostr network.
Nostrudel - The neat thing about Nostrudel is trying to find a Nostr action that it can't do. It's got all the bells and whistles. Nostudel may be a bit overwhelming if you're not familiar with all that is possible on Nostr, but once you have an idea, take this for a spin and see what new ways of interacting on the protocol that you discover.
iOS/Apple
Sorry... this is going to be a little scant for a while. Simply not one of the Apple people, these are the ones my iOS/Nostr friends seem to love:
Damus is a longtime favorite among users, adhering to a protocol-first approach to development.
Nostur sounds like a fun app, maybe on par with Amethyst as far as fun features and fast performance.
You'll have to do your own exploring to see what they are really all about.
Multi-platform
Primal - Simple, clean, and with an integrated Bitcoin/Lightning wallet for fast, easy zaps (basically tips, but on Nostr!). Get started with Nostr right away with no hassle and send or receive Bitcoin among your social network. Primal is great for anyone new to Nostr or who wants to enjoy a more traditional social media experience with the benefits that Nostr has to offer. Primal is available for Android, iOS, and on the web.
Yakihonne - Yakihonne is a beautiful multi-platform client that is available across any device. With a focus on long-form writing, it makes it easy to read and create Nostr articles, blogs, and any other informative piece. It doesn't stop there, though. You can scroll your social feed, set up smart widgets, and browse curated content collections, too.
Desktop
Notedeck - Built by the Damus team, Notedeck brings the speed and redundancy of Nostr to your machine. The local software is easy to install, set up, and use. Add multiple columns to the interface for a full screen of different feeds, profiles, and notifications.
Gossip - Gossip has a wide array of technical knobs and dials for relay controls, note fetching and publishing, and a clean interface that even I can understand. Gossip is built for the more technically-inclined among us, but is also great for the general Nostr "power user". This client is still a step above my paygrade but I'm loving it, regardless of that. If you are like me, this is a great client for a learn-through-doing method of understanding Nostr.
For Groups, Communities, and Chat
Oxchat - Oxchat puts security at the forefront of its interface with encrypted private and group chats. It does a whole lot more than that, too. You can browse your social feed, make voice and video calls, and display badges.
Flotilla and ChaChi are a couple of up and coming group/community/chat clients that are still very much under development, but look to be worth expounding upon in the future. Nostr's interoperability allows you to create and engage in groups you have joined through any of the above clients.
Specialty Clients
Zap.cooking - Publish recipes, earn zaps, find recipes, send zaps. Its a pretty brilliant system. There is no more need for 20 minute stories or overwhelming popup ads. Nostr adds a social layer to recipe sharing that doesn't require a new account to participate. Just sign in with your signing extension of choice, and you can share and leave feedback instantly.
Highlighter - Its still a bit of a construction site, but Highlighter is on its way to becoming Nostr's premiere content creator studio. Write, highlight, and curate. Not only can you create these, you can also browse and discover great Nostr content. There's lots in the works for video and other types of content, too.
Shipyard - "A Quiet Space for Loud Ideas" says it all. Shipyard is focused solely on your writing experience so that you may focus soley on your writing. This client is clean, reliable, and extemely user friendly. It is also one of few Nostr clients that provide you with the ability schedule the publishing of your notes.
Emojito.meme - Create and find custom emoji packs to use on Nostr! How fun is that? Just bookmark & those emojis ready to be used in any supporting social client.
Badges.page - Create and claim badges that display on Nostr profiles in supporting clients. This is a great way to engage with fans, celebrate moments with friends, or even just to be silly. You can set the difficulty of creating a badge with Proof-of-Work to create rare and super rare badges for top supporters, which is pretty cool.
Olas - A beautiful, visual showcase for photography and more. Its sort of like Instagram, but on Nostr, so its better. You can share, scroll, post, and monetize your content in a breeze.
Zapstore - Its an app store! On Nostr! Built for Android! Just follow the instructions on the site to begin your journey of stepping out of the nightmare that is the Playstore. Find apps recommended by your social graph, built by developers trusted within your networks, and donate to app development directly. You'll find more than just Nostr apps here. Zapstore is devoted to bringing free open source software from builder to user with as little interference as possible.
Listr - Create and manage lists for use in any other supporting client. This was the first thing that wow'd me about Nostr when I discovered it a couple years ago. There's something about making a list of people with common interests in one client, and seeing that list in action in another that just blew me away. Different feeds for different purposes, all chronological and all curated by YOU.
Habla - Long-form writing on Nostr made simple. You can quickly and easily get started with a blog or news publication and distribute it to your entire Nostr audience, regardless of which apps they use. Most social clients support article display within various feeds. You can always quote-note your article in a regular note, if you want to boost article exposure, too.
-
 @ 220522c2:61e18cb4
2025-03-25 16:05:27
@ 220522c2:61e18cb4
2025-03-25 16:05:27draftoptionalAbstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (
kind:1), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.Event Kind
This NIP defines
kind:1337as a code snippet event.The
.contentfield contains the actual code snippet text.Optional Tags
-
filename- Filename of the code snippet -
l- Programming language name (lowercase). Examples: "javascript", "python", "rust" -
extension- File extension (without the dot). Examples: "js", "py", "rs" -
description- Brief description of what the code does -
runtime- Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") -
license- License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") -
dep- Dependency required for the code to run (can be repeated) -
repo- Reference to a repository where this code originates
Format
```json {
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at":
, "kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"]],
"sig": "<64-bytes signature of the id>"
} ```
Client Behavior
Clients that support this NIP SHOULD:
-
Display code snippets with proper syntax highlighting based on the language.
-
Allow copying the full code snippet with a single action.
-
Render the code with appropriate formatting, preserving whitespace and indentation.
-
Display the language and extension prominently.
-
Provide "run" functionality for supported languages when possible.
-
Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
-
Code editing capabilities
-
Forking/modifying snippets
-
Creating executable environments based on the runtime/dependencies
-
Downloading the snippet as a file using the provided extension
-
Sharing the snippet with attribution
References
nip #grownostr
-
-
 @ 3c389c8f:7a2eff7f
2025-03-25 15:51:44
@ 3c389c8f:7a2eff7f
2025-03-25 15:51:44*Create your keys and set up your profile:
https://start.njump.me/
*Pick a NIP07 browser extension or offline signer to safely store your private key (nsec):
https://nostr.net/
*Pick an app, sign in, and start exploring:
https://nostrapps.com/
That's All! :)
-
 @ a012dc82:6458a70d
2025-03-25 13:57:54
@ a012dc82:6458a70d
2025-03-25 13:57:54Bitcoin, the pioneering cryptocurrency, has once again defied skeptics by surging to a new all-time high. This remarkable resurgence is a testament to the resilience and enduring appeal of Bitcoin, even as it navigates through periods of intense volatility and regulatory scrutiny. Emerging from the shadows of the digital world, Bitcoin has sparked a financial revolution that challenges the very fabric of traditional banking and monetary systems. Its journey from an obscure digital token to a globally recognized financial asset encapsulates a saga of innovation, speculation, and the relentless pursuit of financial autonomy. This article explores the journey of Bitcoin from its inception to its current status as a leading digital asset, highlighting the challenges it has overcome and the factors contributing to its recent record-breaking performance.
Table of Contents
-
The Genesis of Bitcoin
-
Overcoming Adversity
-
The Path to Mainstream Acceptance
-
Breaking New Ground with ETFs
-
Navigating the Crypto Ecosystem
-
Looking Ahead: Challenges and Opportunities
-
Conclusion
-
FAQs
The Genesis of Bitcoin
Bitcoin was introduced to the world in 2008 by an individual or group using the pseudonym Satoshi Nakamoto. Conceived as a decentralized digital currency, Bitcoin offered a novel solution to the double-spend problem without the need for a central authority. This innovation was set against the backdrop of the global financial crisis, positioning Bitcoin as an alternative to traditional banking systems and fiat currencies. The early years of Bitcoin were marked by a passionate but small community of users, and the cryptocurrency was primarily used for niche online transactions. The concept of a decentralized currency was revolutionary, promising a new era of financial freedom and privacy. However, Bitcoin's early days were fraught with challenges, including limited public understanding, technical hurdles, and skepticism from the financial establishment. Despite these obstacles, the foundational principles of Bitcoin—transparency, security, and decentralization—captivated a growing number of enthusiasts who saw its potential to redefine money.
Overcoming Adversity
Bitcoin's journey has been anything but smooth. The cryptocurrency has faced numerous challenges, including regulatory hurdles, security breaches, and intense market volatility. High-profile incidents, such as the collapse of the Mt. Gox exchange in 2014 and the contentious debates over scalability, tested the resilience of the Bitcoin network and its community. Despite these setbacks, Bitcoin continued to gain traction, attracting a diverse group of users and investors drawn to its potential for high returns and its underlying blockchain technology. The path was littered with obstacles, from hard forks and regulatory crackdowns to sensational media coverage and public skepticism. Yet, each challenge served to strengthen the community and refine the technology, forging a cryptocurrency that was increasingly robust, adaptable, and resilient. The adversities faced by Bitcoin acted as a crucible, purifying and validating the concept of decentralized finance in the eyes of a global audience.
The Path to Mainstream Acceptance
The turning point for Bitcoin came with the gradual recognition of its value as both a digital asset and a technological innovation. Institutional investors began to take notice, and the cryptocurrency started to shed its reputation as a tool for illicit transactions. The introduction of futures contracts and the increasing interest from traditional financial firms signaled a shift towards mainstream acceptance. However, the journey was not without its skeptics, who pointed to Bitcoin's energy consumption and its volatile price swings as reasons for caution. The road to mainstream acceptance was paved with educational efforts, technological advancements, and a growing recognition of Bitcoin's unique attributes, such as its fixed supply and borderless nature. As awareness and understanding of Bitcoin increased, so too did its legitimacy and value, leading to a gradual but undeniable integration into the broader financial landscape.
Breaking New Ground with ETFs
The recent surge in Bitcoin's price can be largely attributed to the approval of exchange-traded funds (ETFs) pegged to the digital asset by U.S. regulators. This milestone was achieved after years of advocacy from the crypto community and a legal battle that challenged the Securities and Exchange Commission's initial rejections. The launch of the first "spot" Bitcoin ETFs has opened the doors for more traditional investors to enter the market, providing a regulated and familiar avenue for Bitcoin exposure. This development has not only boosted Bitcoin's price but also reinforced its legitimacy as an investment asset. The introduction of Bitcoin ETFs represents a significant breakthrough in the cryptocurrency's journey, bridging the gap between the innovative, often misunderstood world of digital currencies and the established, regulated realm of traditional finance. This convergence has facilitated a new wave of investment, bringing with it increased liquidity, visibility, and acceptance for Bitcoin and the broader cryptocurrency market.
Navigating the Crypto Ecosystem
Bitcoin's influence extends beyond its own price performance, serving as a bellwether for the broader cryptocurrency market. The ecosystem has grown exponentially, with thousands of altcoins and a burgeoning decentralized finance (DeFi) sector. However, the industry has not been immune to challenges, facing regulatory scrutiny, market manipulation, and high-profile scandals. Despite these obstacles, Bitcoin has maintained its dominance, buoyed by a loyal community and its perceived value as a hedge against inflation and currency devaluation. The cryptocurrency ecosystem is a dynamic and evolving landscape, marked by rapid innovation and intense competition. Yet, through all the tumult and transformation, Bitcoin remains the cornerstone, setting the standard for security, adoption, and market value. Its journey mirrors the maturation of the entire crypto space, from a fringe idea to a major financial force, influencing everything from individual investment strategies to global economic policies.
Looking Ahead: Challenges and Opportunities
As Bitcoin reaches new heights, questions remain about its sustainability and the potential impact of regulatory changes. The upcoming "halving" event, which reduces the reward for mining new blocks, is expected to have significant implications for Bitcoin's supply and, consequently, its price. Additionally, the cryptocurrency must navigate the delicate balance between innovation and regulation, as authorities worldwide grapple with how to oversee this evolving asset class. The future of Bitcoin is inextricably linked to the broader narrative of digital transformation and financial innovation. As it continues to evolve, Bitcoin will face new challenges and opportunities, from technological advancements and competitive pressures to shifting regulatory landscapes and economic trends. Yet, if history is any guide, Bitcoin will adapt and thrive, continuing its unstoppable journey from adversity to record highs.
Conclusion
From its humble beginnings to its current status as a financial phenomenon, Bitcoin's journey is a compelling narrative of innovation, resilience, and the relentless pursuit of decentralization. While the road ahead is fraught with uncertainty, Bitcoin's ability to rebound from adversity and reach new record highs is a testament to its enduring appeal and the transformative potential of cryptocurrencies. As the world continues to embrace digital currencies, Bitcoin's story remains a powerful reminder of the possibilities and challenges that lie ahead in the uncharted waters of the digital age. The saga of Bitcoin is far from over; it is a continuing tale of disruption, adaptation, and, ultimately, triumph in the face of adversity.
FAQs
Why has Bitcoin reached new record highs? Bitcoin's recent surge to new record highs can be attributed to factors such as the approval of Bitcoin ETFs, growing institutional acceptance, its appeal as a hedge against inflation, and increasing mainstream interest.
What are Bitcoin ETFs, and why are they important? Bitcoin ETFs (Exchange-Traded Funds) are investment funds that track the price of Bitcoin and are traded on traditional stock exchanges. They provide investors with a way to gain exposure to Bitcoin without having to buy or store the cryptocurrency directly, which has contributed to increased Bitcoin adoption.
What challenges has Bitcoin faced? Bitcoin has faced numerous challenges, including regulatory hurdles, security breaches, market volatility, and skepticism from the financial community. Despite these challenges, Bitcoin has continued to grow and gain acceptance.
What is the "halving" event in Bitcoin? The "halving" is an event that occurs approximately every four years, where the reward for mining new Bitcoin blocks is halved. This reduces the rate at which new bitcoins are generated, theoretically increasing scarcity and potentially driving up the price.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ 6bae33c8:607272e8
2025-03-25 11:03:28
@ 6bae33c8:607272e8
2025-03-25 11:03:28I try to make these bold enough that I get most of them wrong. If you’re not getting most wrong, they’re not bold enough! Hits from last year included Teoscar Hernandez being the Marcel Ozuna of 2024 and Shohei Ohtani’s gambling scandal getting memory-holed totally. Misses include Walker Buehler > Tarik Skubal and Spencer Torkelson > Vlad Guerrero. As I said, the predictions have to be bold!
Also, these are hunches, the explanations for which are largely irrelevant. The relevant information is priced into ADP, so while I’ll justify it one way or another, it’s the prediction itself, not the explanation that matters.
1, Alex Bregman is top-five in AL MVP voting
This just feels like a perfect fit. Bregman rakes at Fenway (1.240 career OPS), and he rarely strikes out. I could see a .300-plus batting average with 30 home runs. The Red Sox upgraded their pitching too, and after the Yankees lost Gerrit Cole and Juan Soto, have a good chance to win the AL East.
2. Bo Bichette outperforms Mookie Betts
Granted Betts is sick right now and lost a ton of weight, but he was still going in the second round of NFBC Mains, while Bichette was going in Rounds 8-9. Bichette was hurt last year, but prior to that he was a star, is in his age 27 season and has four home runs and a .373 average in Spring Training. I’m sick that I didn’t get any shares (took Bregman over him in the Main.)
3. Chris Sale finishes as a top-5 starter again
This might not sound that bold because he’s SP6 by ADP, but every pitcher except maybe Paul Skenes and Skubal are underdogs to be top-five, given the volatility of the position. I love veterans in their mid-30s finding it again, usually they have 2-3 years of good before age and injury catch up again. It reminds me of Justin Verlander who hit a rough patch before righting the ship for several elite years.
4. Tyler Glasnow finishes as top-3 in NL CY Young votes
My comp for Glasnow is Randy Johnson, another tall lefty who battled injuries in his 20s before settling down to become one of the GOATS. Glasnow managed 135 IP last year and if he ups it to 165, he’ll be in the CY mix on the Dodgers.
5. Cody Bellinger hits 40 homers
A pull hitter with a high fly ball rate, Bellinger is perfect for Yankee Stadium. He’ll have to stay healthy, of course, but he’s still just 29 — won’t turn 30 until July — and is primed for the second best year of his career (he won’t top 2019.)
6. At least one of the following veteran pitchers has a top-five CY finish: Justin Verlander, Max Scherzer, Kevin Gausman, Walker Buehler, Sandy Alcantara or Carlos Rodon.
Pitchers who were once elite still own most of their skills, health permitting. While Scherzer and Verlander have lost velocity, knowing how to pitch is sufficient above a certain minimum threshold.
7. Jackson Chourio goes 30-30-.300
Chourio hit over .300 for the final four months of the season, once the Brewers stopped pulling him in and out of the lineup. The steals should be easy for him with a full season of at-bats, and the power should be there too in that park.
8. Hunter Brown finishes top-five in AL CY voting
After a rough start, Brown was one of the best pitchers in the league last year with a 2.31 ERA over the last four months. He’s in a good park, in the right division (though the A’s home park got a lot worse) and on a good enough team for run support purposes.
9. Aroldis Chapman gets more saves than Jhoan Duran
Chapman is still throwing 99 and landed a job on the much-improved Red Sox, while Duran, who took nine losses last year, has Griffin Jax behind him. I know Chapman’s control has been bad the last few years, but I have a hunch the veteran warhorse has a comeback year.
10. Some of these predictions will be wrong
I’ll pay the cost of never going 10-for-10 to make sure I don’t go 0-for-10.
-
 @ 7da115b6:7d3e46ae
2025-03-25 11:00:01
@ 7da115b6:7d3e46ae
2025-03-25 11:00:01What Happened?
Sadly, some news came to us in the last couple of days, news that has exploded our plans like a bombshell. As you know from previous posts, my family and I had found the property of our dreams, within the price range that suited us. The only issue was that we had to sell our rental property to be able to purchase the land we wanted to develop for our homestead. At the time, it wasn't an issue.
With a few phone calls and some discussion with the local Council; the Realtor; the Vendors, and the bank, we were on our way. We made an offer, and it was accepted, contingent on our rental property selling. Our offer expires this Friday, and the likelihood of it selling before then, is slim. That leaves us 3 days to come up with the $130,000 we need to secure the property.
"So why not just extend the offer?" I hear you say. Well, that's a fair point - We did. The extension runs out this Friday. Can we extend on the extension? Legally, yes. but here's the rub:
A counter offer has been put forward.
This basically means, that without having the money available by the end of the offer extension, the Vendor is going to take the counter offer.
That's Not So Bad... Right?
Yes, and no.
Unfortunately, we've spend thousands of dollars on reports; valuations; building research and site inspections. This means all of the plans, money and time that we've invested so far is going to be lost. Yes yes, you're right of course, it's our own fault for getting so financially and emotionally invested in the first place. Lesson learned.
I think that the hardest part of it all, was breaking it to my wife. She had already started designing her gardens, and had dreams of watching our homestead grow. The look of utter defeat on her face was gut wrenching. I felt as though I had failed her, and torn away the dream we had built together. She and I had lost our dream in the course of a single phone call. It hit both of us hard.
It's been 24 hours now, and the pain is real. I don't want to eat or go to work, I don't want to talk to anyone. I just want to lay down on my wife's lap and close my eyes until it's over. Deep down inside, I know it's a childish reaction, but that doesn't make it any less of a slap across the face.
The Light at the End of the Tunnel
Cliche, I know, but there may be a little glimmer of light on the horizon. If we do sell our rental property, we will have money to play with. This means we can buy a crappy little Ute and caravan, and go exploring our country. Perhaps stop at a few places that look nice, and see if they're places we could settle. If we spend a few months just looking around, and find somewhere homely, then we can stay for a while at a local caravan park, and look for a property that may be suitable.
At the very least, it would mean that we can escape our shit jobs, which has been the biggest goal from the beginning.
Fingers crossed...
-
 @ 7da115b6:7d3e46ae
2025-03-25 10:55:04
@ 7da115b6:7d3e46ae
2025-03-25 10:55:04Originally written and posted on the 12th of December, 2024
Emotionally, it's been challenging to say the least, and the heat just exacerbates the frustration. But don't let that fool you; we've made significant progress. We found our dream property over two months ago for $130,000. 3 hectares of land, but 2 hectares of it is unusable. This was perfectly okay with us as it's going to be a massive effort for one person anyway.
Two months ago, we put in an offer and they accepted it. However, we are not well off by any means; most weeks, we just scrape by. We have two properties - a property in the Far North that we've been renting out to pay the mortgage ($70,000 remaining), and the one we live in which has almost the entire mortgage outstanding.
So how can we afford another property? Well it's no simple feat! First, we need to sell our Rental Property for around $400,000 (a reasonable market rate). Once that sells, about $170,000 in equity gets transferred to the mortgage of the property we're currently living in. After paying off the last of the mortgage on the rental property and shifting the equity to our current property, that will leave us with almost nothing after legal fees and real estate agent fees.
This amount remaining barely covers the cost of the property we put an offer on - our dream property. It's a humbling experience realizing just how far we still have to go in this journey towards self-sufficiency.
It's a sober reminder that we can't rush it, but should rather embrace each step along the way. For better or for worse, we must adapt and learn from every situation as it comes our way. After all, we can only control what's within our reach; the rest is just a matter of time and patience.
Perhaps it's not about achieving self-sufficiency, but truly embracing the journey itself. The path towards that dream property we've been longing for may take longer than expected, but as long as we have each other and keep pushing forward, I can't think of anything more rewarding than seeing our vision unfold step by step.
I have to remember to cherish the memories and experiences along this road, because it's those moments that will truly make the journey worthwhile.
-
 @ 7da115b6:7d3e46ae
2025-03-25 10:52:00
@ 7da115b6:7d3e46ae
2025-03-25 10:52:00Originally written and posted on the 10th of March, 2025
Safety
The first reason that comes to mind is safety. Violent crime has become a recurring theme in our town, with statistics showing a rise in cases such as burglaries and general homicides. These changes have made us acutely aware of the importance of providing a secure environment for our family. As our children grow, we yearn for them to experience not just safety, but also a sense of stability that comes with it.
The thought of crime often makes me reflect on moments like the domestic violence and murder within throwing distance of our current home, or the attempted mugging and homicide at a nearby petrol station. These incidents have sparked a desire for a place where our family can feel more secure and enjoy the peace of mind that comes with knowing they're safe. I hope that growing up in a safe environment will instill confidence and security in my kids as they navigate life. This pursuit of safety is not just about protecting my loved ones; it’s about creating a foundation where they can thrive and feel secure in their surroundings, allowing them to focus on their growth and aspirations without the constant awareness of potential danger.
Cost of Living
The cost of living has been another pivotal factor in our decision to move. Over time, we’ve noticed how the city’s expenses, from petrol to groceries, have steadily increased, making every purchase a mindful choice. The rising costs of utilities, transportation, and daily essentials have become a significant part of our budget, leaving us wondering if there’s room for more than just the basics. While the city offers many amenities, we’ve found ourselves seeking a lifestyle that aligns with our values and allows us to live comfortably without constant financial strain.
The cost of groceries has also become a major consideration. As prices rise, even simple trips to the store have us thinking about every purchase. We’ve found ourselves choosing between brands or quantities to stay within our budget, which has made us appreciate the idea of growing some of our own food.
While we love the idea of the cultural and social offerings of city life, the reality is that we spend more time trying to stretch our weekly budget to make ends meet, than we do enjoying the fruits of our labor. We’re looking forward to a place where we can manage our budget comfortably, while still having access to the amenities we need. This doesn’t mean we’re leaving behind everything we’ve grown accustomed to; it’s about finding a balance—a home that allows us to live fully without feeling constrained by expenses.
Our decision to move isn't about wanting to be one with nature or making a statement; it’s more about practicality. Owning a freehold property gives us the stability we need, allowing us to live sustainably without feeling tied down by expenses. This choice aligns with our values and offers a sense of freedom, not because we're trying to escape something, but because it supports the life we want for ourselves and our family. We’ve worked hard to pay down our mortgages, but now we’re ready for the next step—owning our own land that we can build upon.
We’re not looking to simplify just because we want to be closer to nature; rather, we see this move as an opportunity to create a lifestyle that’s more in tune with our needs. By growing our own food and living in a clean, natural environment, we’re prioritizing sustainability without compromising on what matters most—our family’s future and well-being. It’s about creating a home that reflects our values, not just embracing change for the sake of being different.
Educational Opportunities
Our oldest child’s education is another driving force behind this move. We’ve discovered that the place we’re moving to offers a University with "fees-free" options, which will provide him with an opportunity to pursue his studies without the burden of tuition costs. This not only eases our financial concerns but also gives us peace of mind knowing he can focus on his education without added stress. It’s a decision that aligns with our aspirations for his future and our family's well-being, hoping he can thrive in an environment that supports his academic journey and personal growth.
Also, our youngest child is going to have the opportunity to raise the animals he’s so enamored with, such as chickens; dogs; pigs, and maybe even a couple of sheep. I want these experiences to help him to learn by doing, fostering a sense of responsibility and connection with where our food comes from. By caring for these creatures, we hope he’ll develop life skills that will help him grow into his own skin as he gets older. It’s a chance for him to explore his passions and build confidence in a hands-on way.
Freedom
Space has become something we truly appreciate, especially with our kids and pets. We’re eager for them to have more room to roam and explore freely. The privacy that a rural setting offers is high on our list of needs because living in the city often feels like we're always surrounded by others. It's not uncommon to bump into neighbors or find ourselves at loggerheads over simple things like car parks. This constant interaction, while part of city life, can sometimes feel overwhelming.
But it's not just us - our current place of employment also experiences issues with neighboring businesses, and it’s the employees who end up feeling the impact. It feels as if everyone is out for themselves, and are incapable of thinking about how their actions affect others.The city environment feels cramped and extremely claustrophobic, making us yearn for more personal space. We’re looking forward to the freedom of having our own large property where we can enjoy peace and quiet. It’s exciting to think about the possibilities, like building a barn or adding bee hives, and even sinking a water well as we please.
Food & Gardening
The idea of growing our own food is another exciting prospect that we're eager to explore. We’re looking forward to cultivating fresh produce in our garden, which will not only provide healthier options for our family but also add variety and freshness to our meals. It will be a major undertaking for us. While I personally have some understanding of growing and harvesting simple crops like potatoes and cabbage, I am deeply aware of my lack of knowledge and experience. It will take years for me to actually become proficient. We’re excited to teach our kids where their food comes from and instill an appreciation for sustainable living. Growing our own produce aligns with our desire for a more natural, self-sufficient lifestyle, offering us the joy of seeing the fruits of our labor in our garden.
Exercise & General Wellness
Living in a bustling city has its perks, but it has also take a toll on our sense of well-being. The daily grind often leaves us feeling mentally and emotionally drained, leaving little room for relaxation and physical activity. With the convenience of modern life comes a faster pace, which, while beneficial, frequently feels overwhelming. We long for moments to pause, breathe in fresh air, and reconnect with ourselves.
I think that the desire for more exercise and fresh air, is a natural response to the our current lifestyle. The city’s vibrant atmosphere and endless opportunities often come at the expense of personal time and the chance to enjoy relax. By seeking a new environment, We're looking for a balanced life for our family, where we can revitalize their minds and bodies through simple yet essential activities like walking around the property or the exercise of working the land. This shift is not just about changing scenery; it’s about creating a lifestyle that supports our overall well-being and allows for moments of peace away from the hustle and bustle.
In conclusion, this move is about more than just changing scenery; it’s about creating a home that embodies our values—safety, education, sustainability, and well-being for our family. It’s a step towards a future where we can thrive in an environment that supports our growth and aspirations.
-
 @ ecda4328:1278f072
2025-03-25 10:00:52
@ ecda4328:1278f072
2025-03-25 10:00:52Kubernetes and Linux Swap: A Practical Perspective
After reviewing kernel documentation on swap management (e.g., Linux Swap Management), KEP-2400 (Kubernetes Node Memory Swap Support), and community discussions like this post on ServerFault, it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion.
The Rationale for Disabling Swap
We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes.
With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion.
Additionally, disabling swap may protect data from data remanence attacks, where sensitive information could potentially be recovered from the swap space even after a process terminates.
Theoretical Capability vs. Practical Deployment
Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly.
But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model:
- Memory requests and limits are declared explicitly.
- The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap).
- Swap introduces non-deterministic performance characteristics that conflict with Kubernetes' goals.
So while the kernel supports intelligent swap usage, Kubernetes intentionally sidesteps that complexity.
Why Disable Swap in Kubernetes?
-
Deterministic Failure > Degraded Performance\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early.
-
Transparency & Observability\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically.
-
Performance Consistency\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits.
-
Kubernetes Doesn’t Manage Swap Well\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control.
-
Statelessness is the Norm\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state.
"But Swap Can Be Useful..."
Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need:
- Fine-tuned
vm.swappiness - Memory pinning and cgroup-based control
- Swap-aware monitoring and alerting
- Custom kubelet/systemd integration
That's possible, but not standard practice — and for good reason.
Future Considerations
Recent Kubernetes releases have introduced experimental swap support via KEP-2400. While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments.
Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in KEP-2400's Risks and Mitigations section, swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior.
Some argue that with emerging technologies like non-volatile memory (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet.
Conclusion
Disabling swap in Kubernetes is not a lazy hack — it’s a strategic tradeoff. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability.
If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, disabling swap remains the sane default.
-
 @ 7d33ba57:1b82db35
2025-03-25 09:38:27
@ 7d33ba57:1b82db35
2025-03-25 09:38:27Located on the Costa de la Luz, Chipiona is a charming seaside town in Cádiz province, known for its stunning beaches, iconic lighthouse, and delicious local wines. It’s a perfect destination for those seeking relaxation, history, and Andalusian charm.
🏖️ Top Things to See & Do in Chipiona
1️⃣ Chipiona Lighthouse (Faro de Chipiona) 💡
- The tallest lighthouse in Spain (69 meters), built in 1867.
- Climb 322 steps for breathtaking views of the Atlantic Ocean.
- Used to guide ships through the Gulf of Cádiz for centuries.
2️⃣ Playa de Regla 🏝️
- The most famous beach in Chipiona, known for its golden sand and calm waters.
- Perfect for sunbathing, swimming, and long walks along the shore.
- Surrounded by beach bars (chiringuitos) and seafood restaurants.
3️⃣ Santuario de Nuestra Señora de Regla ⛪
- A beautiful neo-Gothic monastery near the beach.
- Home to the Virgen de Regla, the town’s patron saint.
- A site of religious pilgrimages, especially in September.
4️⃣ Las Corrales de Pesca 🎣
- Ancient fishing structures made of stone walls in the sea, dating back to Roman times.
- A unique traditional fishing method, still in use today.
- Guided tours are available to learn about their history.
5️⃣ Bodega César Florido 🍷
- Visit one of the oldest wineries in Chipiona, famous for Moscatel wine.
- Enjoy a wine tasting tour and learn about the local winemaking tradition.
6️⃣ Paseo Marítimo & Sunset Views 🌅
- A scenic beachfront promenade, ideal for an evening stroll.
- Watch the sunset over the Atlantic Ocean, one of the most beautiful in Andalusia.
🍽️ What to Eat in Chipiona
- Langostinos de Sanlúcar – Delicious local prawns, best with a glass of Manzanilla wine 🦐🍷
- Tortillitas de camarones – Crispy shrimp fritters, a Cádiz specialty 🥞🦐
- Chocos a la plancha – Grilled cuttlefish with olive oil and lemon 🦑
- Pescaíto frito – A mix of fried fresh fish, perfect for a beachside meal 🐟
- Moscatel de Chipiona – A sweet dessert wine, famous in the region 🍷

🚗 How to Get to Chipiona
🚘 By Car: ~30 min from Cádiz, 1 hr from Seville, 2 hrs from Málaga
🚆 By Train: Closest stations in El Puerto de Santa María or Jerez de la Frontera
🚌 By Bus: Regular buses from Cádiz, Jerez, and Seville
✈️ By Air: Nearest airport is Jerez de la Frontera (XRY) (~40 min away)💡 Tips for Visiting Chipiona
✅ Best time to visit? Spring & summer for beach weather, September for festivals 🌞
✅ Try a Moscatel wine tour – The local wineries are world-famous 🍷
✅ Bring comfortable shoes – If climbing the lighthouse 👟
✅ Visit in September for the Fiestas de la Virgen de Regla, a unique cultural experience 🎉 -
 @ da0b9bc3:4e30a4a9
2025-03-25 09:14:07
@ da0b9bc3:4e30a4a9
2025-03-25 09:14:07Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/924287
-
 @ 220522c2:61e18cb4
2025-03-25 06:57:24
@ 220522c2:61e18cb4
2025-03-25 06:57:24
-
 @ bf7973ed:841ad12a
2025-03-25 04:19:41
@ bf7973ed:841ad12a
2025-03-25 04:19:41test
-
 @ 502ab02a:a2860397
2025-03-25 02:24:07
@ 502ab02a:a2860397
2025-03-25 02:24:07ต่อเนื่องจากมหากาพย์น้ำมันมะกอกปลอมนะครับ คนที่ปลอมแปลงน้ำมันมะกอกได้พัฒนาวิธีการต่าง ๆ เพื่อเลียนแบบคุณสมบัติของน้ำมันมะกอกแท้ ทำให้การตรวจสอบด้วยการแช่เย็นเพื่อดูการแข็งตัวอาจไม่สามารถยืนยันความบริสุทธิ์ได้อย่างแน่นอนแล้วหละครับ
คำแนะนำในการเลือกซื้อน้ำมันมะกอกจะแบ่งเป็นกว้างงงงงงงกว้าง 3 เรื่องคือ 1 ซื้อจากแหล่งที่เชื่อถือได้ เลือกซื้อน้ำมันมะกอกจากผู้ผลิตหรือร้านค้าที่มีความน่าเชื่อถือ และมีการรับรองคุณภาพจากหน่วยงานที่เกี่ยวข้อง ซึ่ง เชรี่ยละ ฝากเงินไว้กับคนอื่น 5555 2 ตรวจสอบฉลาก อ่านฉลากผลิตภัณฑ์อย่างละเอียด ตรวจสอบแหล่งที่มา วันที่ผลิต และวันที่หมดอายุ อันนี้คือที่เราจะคุยกันวันนี้ 3 สังเกตลักษณะของน้ำมัน น้ำมันมะกอกแท้มักมีสีและกลิ่นเฉพาะตัว หากพบว่าสีหรือกลิ่นผิดปกติ ควรพิจารณาก่อนซื้อ ตรงนี้นี่ต้องอาศัยความเจ็บปวดจากการพลาดเยอะๆ จะทำให้รู้ความแตกต่างครับ ซึ่ง not bad นะ
ไล่จากเรื่องเล็กก่อน คือ การสังเกตลักษณะน้ำมัน แบบที่นิยมสุุดคือ การแช่ตู้เย็นแล้วดูว่ามันแข็งไหม ที่เราสอนต่อๆกันมาคือ ถ้าแข็งก็คือดี ของแท้ แต่ แต่ แต่ ส่วนใหญ่แล้วการปลอมน้ำมันมะกอกเขาจะใช้หลากหลายวิธี แล้วแต่คนจะทำครับ อาทิเช่น การเจือปนสิ่งเหล่านี้ลงไปครับ - ไขมันเติมไฮโดรเจนบางส่วน ได้แก่พวกน้ำมันพืชราคาถูก เช่น น้ำมันถั่วเหลือง น้ำมันปาล์ม หรือคาโนลา มักถูกเติมไฮโดรเจนบางส่วนเพื่อเพิ่มอายุการเก็บรักษาอยู่แล้ว ต้นทุนต่ำกว่าน้ำมันมะกอกมาก หลายๆคนคงบอกว่า เอ้ย มันแช่เย็นแล้วไม่แข็งตัวนี่ ตรงนี้มีข้อมูลบอกว่า เขาใช้ไขมันทรานส์หรือไขมันเติมไฮโดรเจน โดยใช้หลักการทางเคมีที่ทำให้เนื้อสัมผัสของน้ำมันปลอมเลียนแบบพฤติกรรมของน้ำมันมะกอกแท้เมื่อถูกแช่เย็น บางที่ก็เติมน้ำมันมะพร้าวหรือน้ำมันปาล์ม อันนี้ต้นทุนต่ำทำง่ายเลยครับ เค้าใช้น้ำมันปาล์มโอเลอินที่มีการ ปรับแต่ง ด้วยการ เติมสารเติมแต่ง ทำให้ไขมันในน้ำมันมีลักษณะแข็งขึ้นและสามารถ ปรับจุดหลอมเหลว ให้สามารถแข็งตัวที่อุณหภูมิที่เย็นได้มากขึ้น - กรดไขมันอิ่มตัวสังเคราะห์ ประเภทกรดสเตียริกหรือกรดปาลมิติกสังเคราะห์เป็นผลิตภัณฑ์พลอยได้จากอุตสาหกรรมแปรรูปไขมันพืชและสัตว์ ราคาต่อหน่วยต่ำมาก โดยเฉพาะถ้าซื้อในปริมาณมาก - ไขมันจากสัตว์ อย่างเช่นไขมันหมูและน้ำมันปลาถูกกว่าน้ำมันมะกอก และสามารถหาได้จากอุตสาหกรรมแปรรูปอาหารที่มักมีของเหลือทิ้งในปริมาณมาก - ขี้ผึ้งพืช พวกขี้ผึ้ง Candelilla Wax หรือ Carnauba Wax ราคาถูกกว่าและสามารถใช้ในปริมาณน้อยเพื่อเลียนแบบคุณสมบัติทางกายภาพ - โมโนกลีเซอไรด์และไดกลีเซอไรด์ เป็นสารเติมแต่งที่ใช้ในอุตสาหกรรมอาหารอยู่แล้ว ต้นทุนต่ำมาก และช่วยให้น้ำมันมีเนื้อสัมผัสคล้ายน้ำมันมะกอก
ในข้อต่อมาจะรวมกันได้เลยครับ ฉลาก และ การรับรองคุณภาพ คือผมตัดเรื่องผู้ผลิตหรือร้านค้าออกไปเลย เพราะก็ไปดูเองได้ว่าแบรนด์เก่าแก่ เราก็จะเหมารวมไปเองว่าไม่น่าโกง 5555 เราข้ามมาอะไรที่พอจะมีหลักเกณฑ์ได้นะครับ short cut เลยคือ ตรารับรอง ใครจะดู DOP IGP USDA Organic อะไรผมไม่ค่อยสนใจครับ ผมว่าถ้าเป็นไปได้ข้ามไปดูนี่เลยครับ
 - International Olive Council (IOC) น้ำมันมะกอกที่ได้รับการรับรองจาก IOC เป็นการรับรองคุณภาพน้ำมันมะกอกที่ได้รับการตรวจสอบจากองค์กรที่มีมาตรฐานสากล
- COOC (California Olive Oil Council) สำหรับน้ำมันมะกอกที่ผลิตในแคลิฟอร์เนีย หรือในสหรัฐฯ จะมีการรับรองจาก COOC ที่ยืนยันว่าผ่านการตรวจสอบมาตรฐาน
- International Olive Council (IOC) น้ำมันมะกอกที่ได้รับการรับรองจาก IOC เป็นการรับรองคุณภาพน้ำมันมะกอกที่ได้รับการตรวจสอบจากองค์กรที่มีมาตรฐานสากล
- COOC (California Olive Oil Council) สำหรับน้ำมันมะกอกที่ผลิตในแคลิฟอร์เนีย หรือในสหรัฐฯ จะมีการรับรองจาก COOC ที่ยืนยันว่าผ่านการตรวจสอบมาตรฐานเรามาทำความเข้าใจรายละเอียดของน้ำมันมะกอกกันก่อนครับ เพื่อว่าตอนดูฉลากจะได้รู้ว่าทำไมต้องมีของพวกนี้ พันธุ์มะกอกที่ใช้ทำน้ำมันมะกอกนั้นเป็นตัวกำหนดรสชาติและกลิ่นหอมของน้ำมันมะกอก โดยมะกอกแต่ละสายพันธุ์ให้รสชาติแตกต่างกันครับ Arbequina (สเปน): กลิ่นผลไม้ มีรสคล้ายแอปเปิ้ลเขียว Koroneiki (กรีซ): เผ็ดร้อน มีรสพริกไทย Coratina (อิตาลี - Puglia): รสเข้ม เผ็ดร้อน มีรสขมติดปลายลิ้น Manzanilla cacereña (สเปน): หอมผลไม้ มีรสอัลมอนด์ แอปเปิ้ลเขียว Peranzana (อิตาลี - Puglia): รสชาติกลมกล่อม หอมหวานเล็กน้อย
- พื้นที่เพาะปลูกและผลิต ตัวนี้แหละครับ เอาไปทำตรา IGP เรียกเหมาๆว่า Geographical Origin น้ำมันมะกอกคุณภาพสูงจะระบุชัดเจนว่า มะกอกมาจากไหนและผลิตที่ไหน ถ้าฉลากไม่ระบุ แสดงว่าอาจเป็นน้ำมันมะกอกผสมจากหลายแหล่ง ซึ่งอาจมีคุณภาพต่ำ
- วันที่เก็บเกี่ยว น้ำมันมะกอกมีสารโพลีฟีนอล (Polyphenols) ซึ่งเป็นสารต้านอนุมูลอิสระที่ให้รสชาติและกลิ่นหอม แต่เมื่อเวลาผ่านไป สารเหล่านี้จะลดลง ทำให้น้ำมันเสียรสชาติ
- ระดับความเป็นกรด (Acidity Level) ตัวนี้หละที่ผมโคตรเน้น และพูดบ่อยมาก จนหลายๆคนเบื่อ 5555 น้ำมันมะกอก Extra Virgin ต้องมี ค่าความเป็นกรดต่ำกว่า 0.8% ค่ายิ่งต่ำ ยิ่งดี เพราะหมายความว่ามะกอกถูกเก็บเกี่ยวอย่างเหมาะสมและสกัดอย่างรวดเร็ว
- ระดับความเข้มของรสชาติ เรื่องการกินก็สำคัญนะครับน้ำมันมะกอกมีระดับความเข้มต่างกัน ควรเลือกให้เหมาะกับอาหาร รสอ่อน (Delicate) เหมาะกับปลา เนื้อขาว และสลัดเบาๆ ,รสปานกลาง (Moderate) เหมาะกับพาสต้า ผักย่าง และชีส รสเข้มข้น (Intense) เหมาะกับเนื้อแดง ช็อกโกแลต และอาหารที่มีรสจัด
ส่วนตราที่บอกไว้ข้างบนโน้นนน จำไว้เลยว่า อย่าหลงเชื่อคำว่า "Organic" เพียงอย่างเดียว เพราะการปลูกแบบออร์แกนิกไม่ได้รับประกันว่ารสชาติจะดีเสมอไป หลีกเลี่ยงน้ำมันมะกอกที่ระบุว่า "Product of EU" เพราะอาจเป็นการผสมจากหลายประเทศ
สำหรับเรื่องฉลากนะครับ ใครที่ดื่มไวน์โลกเก่าจะคุ้นเคยความที่ต้องอ่านรายละเอียดพวกนี้เป็นอย่างดี น้ำมันมะกอกแบบ extra virgin olive oil ที่ดี ฉลากและแพคเกจจะต้องมีประมาณนี้ครับ 1.ระดับกรดอิสระ (Free Fatty Acids, FFA) หรือ กรดโอเลอิก (%) ต้องไม่เกิน 0.8% ตามมาตรฐานของ International Olive Council (IOC) ถ้าค่าตัวนี้ยิ่งต่ำ แสดงว่าน้ำมันมะกอกมีคุณภาพดีขึ้น เพราะบ่งบอกว่าผลมะกอกถูกสกัดอย่างดี ไม่ผ่านกระบวนการที่ทำให้เสื่อมสภาพ 2. ค่าความเป็นออกซิเดชัน (Peroxide Value, PV) (meq O₂/kg) ต้องไม่เกิน 20 meq O₂/kg คือไม่ต้องรู้ก็ได้ครับว่ามาจากไหน เอาว่าถ้าค่าสูงเกินไป แสดงว่าน้ำมันเริ่มเหม็นหืนจากปฏิกิริยาออกซิเดชัน 3. ค่า K232 และ K270 (UV Absorbance at 232 nm และ 270 nm) โดยที่ K232 ต้องไม่เกิน 2.50 (บ่งบอกถึงการเกิดออกซิเดชันระยะแรก) และ K270 ต้องไม่เกิน 0.22 (บ่งบอกถึงการเสื่อมสภาพของน้ำมัน) ค่าเหล่านี้ใช้แสง UV ตรวจจับว่ามีการกลั่นน้ำมันอื่นผสมเข้ามาหรือไม่ 4. ค่า Delta-K (ΔK) ต้องไม่เกิน 0.01 ค่านี้ใช้ตรวจจับว่าน้ำมันมีการปนเปื้อนหรือถูกดัดแปลงด้วยสารอื่นไหม 5. ประเทศต้นกำเนิด (Country of Origin) น้ำมันมะกอกที่มีคุณภาพดีมักระบุชื่อฟาร์มหรือแหล่งผลิตที่ชัดเจน เช่น อิตาลี สเปน กรีซ 6. วันที่เก็บเกี่ยว (Harvest Date) และวันหมดอายุ (Best Before Date) ควรเลือกน้ำมันที่มีวันที่เก็บเกี่ยวล่าสุด (อายุการเก็บรักษาโดยทั่วไปคือ 18-24 เดือน) 7. วิธีการสกัด (Extraction Method) ต้องระบุว่าเป็น "Cold Pressed" หรือ "Cold Extracted" หมายถึงสกัดโดยไม่ใช้ความร้อน ซึ่งช่วยรักษาคุณภาพของสารอาหาร 8. ปริมาณโพลีฟีนอล (Polyphenol Content) (mg/kg) [อาจไม่มีในทุกยี่ห้อ] น้ำมันมะกอกคุณภาพสูงมักมีโพลีฟีนอลมากกว่า 250 mg/kg ซึ่งช่วยลดการอักเสบในร่างกาย แต่บางยี่ห้อก็จะให้ดูที่วิตามิน E กับ K เพราะ น้ำมันมะกอกที่มี Polyphenol สูงมักจะมีปริมาณ วิตามิน E ที่สูงตามไปด้วย และการที่น้ำมันมะกอกมี วิตามิน K ก็อาจสะท้อนถึงการที่น้ำมันมะกอกนั้นไม่ได้ถูกผ่านกระบวนการปรับแต่งหรือแปรรูปที่มากจนเกินไป ทำให้รักษาสารอาหารที่สำคัญ รวมถึง Polyphenol ไว้ได้ 9. บรรจุภัณฑ์ ควรเป็นขวดแก้วสีเข้มหรือกระป๋องโลหะ เพื่อป้องกันการเสื่อมสภาพจากแสง




ใน 9 ข้อนี้ ไม่จำเป็นต้องมีครบทุกข้อก็ได้นะครับ เท่าที่ผมพยายามหาในไทย เจอ acidity ก็บุญโขแล้วครับ 55555 บางทีเขาก็อาจไม่ได้แปะไว้บนฉลาก แต่ต้องตามไปอ่านในเว็บของผู้ผลิตก็ได้ครับ
ส่วนใครที่อ่านถึงตรงนี้แล้วท้อใจ ไม่อยากกินมันแล้ว ก็ขอบอกว่า โลกมันก็เป็นแบบนี้แหละครับ ของมันมีราคามากจนต้องมีการปลอมกัน มันไม่ได้โหดร้ายขนาดนั้นหรอกครับ กระเป๋าแบรนด์เนมก็ปลอมกันเกลื่อน นาฬิกาก็ปลอมกันทั่ว แต่คุณๆก็มองออกใช่ไหมครับ น้ำมันมะกอกมันก็ไม่ต่างกันหรอกครับ มันคือเรื่องที่ไม่ธรรมดาของโลกนี้ที่คนทำเป็นเรื่องธรรมดา
ถ้ามันดูหดหู่ไป จำง่ายๆก็ได้ครับว่า "ทุกน้ำมันมะกอกปลอม จะไม่มีฉลากที่บอกรายละเอียดดีๆ แต่ ทุกน้ำมันมะกอกที่ไม่มีฉลากรายละเอียดดีๆ ไม่ได้เป็นน้ำมันมะกอกปลอม" logic แบบง่ายๆนี้เลยครับ
ผมได้แค่บอกว่า สิ่งที่ควรดูเพื่อแลกกับเงินที่ต้องจ่ายให้มันมากๆคืออะไร แล้วสิ่งที่เราจ่ายไปบริโภค เราได้แบบนั้นจริงๆไหม อย่างที่เคยบอกใน #ฉลาก3รู้ เสมอๆคือ ฉลากไม่ได้เป็นตัวประกาศิตที่จะบอกว่าใครไม่มีคือแย่ แต่ฉลากมันเหมือนคำมันสัญญา ว่าผู้ผลิตจะทำตามที่เขียนเอาไว้ ถ้าใครที่กล้าบิดพริ้วจากนั้น หรือ ทำไม่จริงตามฉลาก มันก็คือการที่เขากล้าทำผิดสัญญา และมันต้องแลกมาด้วยค่าใช้จ่าย ไม่ว่าจะชื่อเสียง ความน่าเชื่อถือ หรือ ความภาคภูมิใจ เราคงทำอะไรไม่ได้มากกว่านั้น จะใช้กระบวนการ ก็ต้องพิสูจน์ ใช้เวลา เพราะที่เห็นในบ้านเราก็มีตัวอย่างมากมาย แต่มันก็ "อย่างน้อย" มันวัดกันหล่ะวะ ว่า แกกล้าสัญญากับชั้นมั๊ย
โอเคมะ ถ้าคุณจะหนี มันต้องหนีตลอดไปในทุกๆอย่างครับ หรือจะให้ผมเล่าเรื่อง fun fact ของกินเทพอื่นๆ ที่พวกคุณกินกันอย่างเป็นล่ำเป็นสันเพื่อกระตุ้นให้ศึกษาเพิ่มไหมหล่ะ 55555
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 1d7ff02a:d042b5be
2025-03-25 02:01:41
@ 1d7ff02a:d042b5be
2025-03-25 02:01:41ໃນຍຸກດິຈິຕອນ, ການລົບກວນທາງເທັກໂນໂລຊີໄດ້ສັ່ນຄອນສະຖາບັນແບບດັ້ງເດີມທົ່ວໂລກ. ເຊັ່ນດຽວກັນກັບແພລດຟອມສື່ສັງຄົມອອນລາຍທີ່ໄດ້ທຳລາຍອິດທິພົນຂອງສື່ທ້ອງຖິ່ນ, Tether (USDT) ແລະ ສະເຕເບິນຄອຍອື່ນໆ ກຳລັງທ້າທາຍອຳນາດຂອງທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ. ສະກຸນເງິນດິຈິຕອນທີ່ມີຄວາມສະຖຽນເຫຼົ່ານີ້ ສະເໜີວິທີການສຳລັບປະຊາຊົນເພື່ອປ້ອງກັນເງິນເຟີ້, ຫຼີກລ່ຽງການຄວບຄຸມທຶນ, ແລະ ເຂົ້າເຖິງຕະຫຼາດການເງິນໂລກໂດຍບໍ່ຕ້ອງອີງໃສ່ລະບົບທະນາຄານແບບດັ້ງເດີມ. ໃນຂະນະທີ່ການນຳໃຊ້ກຳລັງເພີ່ມຂຶ້ນ, USDT ກຳລັງກາຍເປັນໄພຂົ່ມຂູ່ທີ່ມີຢູ່ຈິງຕໍ່ທະນາຄານກາງ, ຈຳກັດການຄວບຄຸມຂອງພວກເຂົາຕໍ່ນະໂຍບາຍການເງິນ ແລະ ອຳນາດອະທິປະໄຕທາງການເງິນ.
ທາງເລືອກໃໝ່ແທນສະກຸນເງິນທ້ອງຖິ່ນ
ປະເທດກຳລັງພັດທະນາມັກຈະປະສົບບັນຫາກັບການລົດຄ່າເງິນ, ເງິນເຟີ້, ແລະ ການໄຫລອອກຂອງທຶນ. ທະນາຄານກາງຫຼາຍແຫ່ງບໍ່ສາມາດຮັກສາສະຖຽນລະພາບຂອງສະກຸນເງິນເນື່ອງຈາກການຄຸ້ມຄອງທີ່ບໍ່ດີ, ການພິມເງິນຫຼາຍເກີນໄປ, ຫຼື ການແຊກແຊງທາງການເມືອງ. ພົນລະເມືອງທີ່ເຫັນເງິນທ້ອນຂອງຕົນຖືກກັດເຊາະ ຕາມປົກກະຕິແລ້ວຈະມີທາງເລືອກບໍ່ຫຼາຍ: ປ່ຽນເງິນທ້ອງຖິ່ນເປັນ ໂດລາ ຫລື ໃນກໍລະນີ້ລາວເຮົາກໍຈະມີ ບາດ ແລະ ຢວນນຳ ຜ່ານທະຫລາດມືດ ຫຼື ລົງທຶນກັບທຸລະກິດ, ຊື້ອະສັງຫາ ແລະ ລົງທຶນໃນຊັບສິນຕ່າງປະເທດ. USDT ໄດ້ປ່ຽນແປງເກມນີ້. ມັນອະນຸຍາດໃຫ້ທຸກຄົນທີ່ມີການເຂົ້າເຖິງອິນເຕີເນັດສາມາດເກັບຮັກສາ ແລະ ໂອນມູນຄ່າໃນຮູບແບບດິຈິຕອນທີ່ທຽບເທົ່າກັບໂດລາໂດຍບໍ່ຈຳເປັນຕ້ອງໄດ້ຮັບການອະນຸມັດຈາກທະນາຄານທ້ອງຖິ່ນ ຫຼື ລັດຖະບານ. ສິ່ງນີ້ຊ່ວຍໃຫ້ຫຼຸດພົ້ນຈາກການອີງໃສ່ສະກຸນເງິນແຫ່ງຊາດທີ່ອ່ອນແອ, ສະເໜີທາງເລືອກທີ່ງ່າຍໃນການປ້ອງກັນການເສື່ອມຄ່າ. ໃນປະເທດເຊັ່ນ: ເວເນຊູເອລາ, ອາເຈນຕິນາ, ໄນຈີເຣຍ, ເລບານອນ, ແລະ ລາວ, ປະຊາຊົນກຳລັງນຳໃຊ້ USDT ເພື່ອປົກປ້ອງຄວາມໝັ້ງຄັ່ງຂອງພວກເຂົາຈາກພາວະເງິນເຟີ້ສູງ ແລະ ຄວາມບໍ່ສະຖຽນທາງການເງິນ.
ການທຳລາຍການຜູກຂາດຂອງທະນາຄານກາງ
ທະນາຄານກາງມີອຳນາດອັນໃຫຍ່ຫຼວງຕໍ່ລະບົບການເງິນໂດຍການຄວບຄຸມການອອກເງິນ, ອັດຕາດອກເບ້ຍ, ແລະ ການໄຫຼຂອງທຶນ. ເຖິງຢ່າງໃດກໍຕາມ, USDT ບ່ອນທຳລາຍການຄວບຄຸມນີ້ດ້ວຍການສະໜອງລະບົບການເງິນຄູ່ຂະໜານທີ່ດຳເນີນງານເປັນອິດສະຫຼະຈາກການກຳກັບດູແລຂອງລັດຖະບານ. ສິ່ງນີ້ທ້າທາຍສາມພື້ນທີ່ຫຼັກຂອງອຳນາດທະນາຄານກາງ:
- ການຄວບຄຸມນະໂຍບາຍການເງິນ:
ເມື່ອປະຊາຊົນຍ້າຍເງິນທ້ອນຈາກສະກຸນເງິນທ້ອງຖິ່ນໄປສູ່ USDT, ທະນາຄານກາງຈະສູນເສຍຄວາມສາມາດໃນການຄວບຄຸມປະລິມານເງິນຢ່າງມີປະສິດທິພາບ. ຖ້າປະຊາກອນສ່ວນໃຫຍ່ຢຸດໃຊ້ສະກຸນເງິນແຫ່ງຊາດ, ນະໂຍບາຍເຊັ່ນ: ການປ່ຽນແປງອັດຕາດອກເບ້ຍ ຫຼື ການພິມເງິນກໍຈະສູນເສຍປະສິດທິພາບຂອງພວກມັນ.
- ການຫຼີກລ່ຽງການຄວບຄຸມທຶນ:
ປະເທດກຳລັງພັດທະນາຫຼາຍແຫ່ງບັງຄັບໃຊ້ການຄວບຄຸມທຶນທີ່ເຂັ້ມງວດເພື່ອປ້ອງກັນບໍ່ໃຫ້ເງິນອອກນອກປະເທດ, ເຮັດໃຫ້ສະກຸນເງິນຂອງພວກເຂົາມີສະຖຽນລະພາບ. USDT, ໂດຍບໍ່ມີພົມແດນ, ອະນຸຍາດໃຫ້ຜູ້ໃຊ້ຫຼີກລ່ຽງການຄວບຄຸມເຫຼົ່ານີ້, ເຮັດໃຫ້ມັນງ່າຍຂຶ້ນໃນການດຳເນີນທຸລະກຳທົ່ວໂລກ ຫຼື ເກັບຮັກສາຄວາມໝັ້ງຄັ່ງທີ່ມີສະພາບຄ່ອງລະດັບສາກົນ.
- ການລົດບົດບາດຂອງລະບົບທະນາຄານ:
USDT ຫຼຸດຄວາມຕ້ອງການຂອງການບໍລິການທະນາຄານແບບດັ້ງເດີມ. ດ້ວຍສະມາດໂຟນ ແລະ ກະເປົາເງິນດິຈິຕອນ, ປະຊາຊົນສາມາດສົ່ງ ແລະ ຮັບການຊຳລະເງິນໂດຍບໍ່ຕ້ອງຜ່ານລະບົບທະນາຄານ, ຕັດທະນາຄານອອກຈາກລະບົບນິເວດການເງິນ ແລະ ເຮັດໃຫ້ພວກມັນຂາດຄ່າທຳນຽມທຸລະກຳ ແລະ ເງິນຝາກ.
ກໍລະນີຂອງລາວ: ການປ່ຽນແປງທາງການເງິນທີ່ກຳລັງເກີດຂຶ້ນ
ລາວ, ເຊັ່ນດຽວກັນກັບປະເທດກຳລັງພັດທະນາຫຼາຍແຫ່ງ, ປະເຊີນກັບສິ່ງທ້າທາຍທາງເສດຖະກິດລວມທັງເງິນເຟີ້, ສະກຸນເງິນແຫ່ງຊາດທີ່ອ່ອນແອ (ເງິນກີບລາວ), ແລະ ການເຂົ້າເຖິງເງິນຕາຕ່າງປະເທດທີ່ຈຳກັດ. ລັດຖະບານມີການຄວບຄຸມທຶນທີ່ເຂັ້ມງວດ, ເຮັດໃຫ້ມັນຍາກສຳລັບບຸກຄົນ ແລະ ທຸລະກິດໃນການຊື້ USD ຜ່ານຊ່ອງທາງທີ່ເປັນທາງການ. ສິ່ງນີ້ເຮັດໃຫ້ເກີດຕະຫຼາດມືດສຳລັບການແລກປ່ຽນເງິນຕາທີ່ເຕີບໂຕຂຶ້ນ. ດ້ວຍການເພີ່ມຂຶ້ນຂອງ USDT, ຊາວລາວຫຼາຍຄົນກຳລັງຫັນມາໃຊ້ stable coin ແລະ ເກັບຊັບສິນດິຈິຕອນ ເປັນທາງເລືອກທີ່ປອດໄພກວ່າການຖືເງິນກີບລາວ, ເຊິ່ງມີແນວໂນ້ມທີ່ຈະເສື່ອມຄ່າລົງ.
ບົດຮຽນຈາກການທຳລາຍສື່ທ້ອງຖິ່ນໂດຍສື່ສັງຄົມອອນລາຍ
ການເພີ່ມຂຶ້ນຂອງ USDT ສະທ້ອນໃຫ້ເຫັນເຖິງສື່ສັງຄົມອອນລາຍໄດ້ທຳລາຍສື່ທ້ອງຖິ່ນແນວໃດ. ສື່ຂ່າວແບບດັ້ງເດີມເຄີຍຜູກຂາດການແຈກຢາຍຂໍ້ມູນ, ແຕ່ແພລດຟອມເຊັ່ນ: Facebook, Twitter, ແລະ YouTube ໄດ້ເຮັດໃຫ້ການສ້າງ ແລະ ການແຈກຢາຍເນື້ອຫາເປັນປະຊາທິປະໄຕ. ດັ່ງນັ້ນ, ສື່ທີ່ຄວບຄຸມໂດຍລັດ ແລະ ບໍລິສັດຈຶ່ງສູນເສຍຄວາມສາມາດໃນການກຳນົດເນື້ອຫາ ໃນຂະນະທີ່ສື່ສັງຄົມອອນລາຍເພີ່ມອຳນາດໃຫ້ບຸກຄົນໃນການແບ່ງປັນ ແລະ ເຂົ້າເຖິງຂ່າວທີ່ບໍ່ໄດ້ຜ່ານການ censorship. ເຊັ່ນດຽວກັນ, USDT ກຳລັງກະຈາຍອຳນາດທາງການເງິນ. ເຊັ່ນດຽວກັບສື່ສັງຄົມອອນລາຍທີ່ໃຫ້ສຽງແກ່ປະຊາຊົນນອກເໜືອຈາກສື່ກະແສຫຼັກ, USDT ກຳລັງໃຫ້ຄວາມເປັນອິດສະຫຼະທາງການເງິນແກ່ບຸກຄົນທີ່ເກີນກວ່າຂອບເຂດຂອງທະນາຄານກາງ. ແນວໂນ້ມນີ້ຊັດເຈນ: ສະຖາບັນທີ່ລວມສູນຈະສູນເສຍການຄວບຄຸມເມື່ອບຸກຄົນໄດ້ຮັບການເຂົ້າເຖິງໂດຍກົງຕໍ່ທາງເລືອກອື່ນ.
Trump ສະໜັບສະໜູນ Stable Coin
ປະທານາທິບໍດີສະຫະລັດ Donald Trump ໄດ້ສະແດງການສະໜັບສະໜູນຕໍ່ stable coin ແລະ ອຸດສາຫະກຳ cryptocurrency ເມື່ອບໍ່ດົນມານີ້. ຈຸດຢືນຂອງລາວເປັນສັນຍານເຖິງການປ່ຽນແປງທີ່ເປັນໄປໄດ້ໃນນະໂຍບາຍຂອງສະຫະລັດທີ່ອາດຈະສ້າງຄວາມຊອບທຳໃຫ້ແກ່ສະເຕເບິນຄອຍ ແລະ ຂັບເຄື່ອນການນຳໃຊ້ທົ່ວໂລກ. ຖ້າລັດຖະບານສະຫະລັດຮັບຮອງສະເຕເບິນຄອຍເຊັ່ນ USDT, ມັນອາດຈະເລັ່ງການນຳໃຊ້ພວກມັນເປັນທາງເລືອກແທນລະບົບທະນາຄານແບບດັ້ງເດີມ, ສ້າງແຮງກົດດັນເພີ່ມເຕີມຕໍ່ທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ. ນີ້ອາດຈະສົ່ງເສີມໃຫ້ມີການມີສ່ວນຮ່ວມຂອງສະຖາບັນຫຼາຍຂຶ້ນ, ເຮັດໃຫ້ມັນຍາກຂຶ້ນສຳລັບລັດຖະບານທ້ອງຖິ່ນໃນການປາບປາມການນຳໃຊ້ USDT.
ຊ່ອງຫວ່າງຂອງການຮັບຮູ້: ຫຼາຍຄົນຍັງບໍ່ຮູ້ເຖິງໄພຂົ່ມຂູ່
ເຖິງແມ່ນວ່າ USDT ຈະເຕີບໂຕຢ່າງໄວວາ, ປະຊາຊົນຫຼາຍຄົນໃນປະເທດກຳລັງພັດທະນາຍັງບໍ່ຮັບຮູ້ເຖິງຜົນກະທົບຂອງມັນ. ໃນຂະນະທີ່ຜູ້ໃຊ້ເລີ່ມຕົ້ນຈະເປັນ ບຸກຄົນທີ່ຮູ້ເທັກໂນໂລຊີ, ນັກລົງທຶນ ແລະ ເຈົ້າຂອງທຸລະກິດ, ປະຊາກອນສ່ວນໃຫຍ່ຍັງອີງໃສ່ການທະນາຄານແບບດັ້ງເດີມ ແລະ ສະກຸນເງິນຕາມກົດໝາຍໂດຍບໍ່ຮູ້ເຖິງຄວາມສ່ຽງຂອງການເສື່ອມຄ່າ ແລະ ຄວາມບໍ່ສະຖຽນທາງການເງິນ. ເຖິງຢ່າງໃດກໍຕາມ, ບຸກຄົນຕ້ອງມີຄວາມຄິດລິເລີ່ມໃນການສຶກສາຕົນເອງກ່ຽວກັບເຄື່ອງມືທາງການເງິນທາງເລືອກເຊັ່ນ USDT ແລະ Bitcoin ເພື່ອປົກປ້ອງຄວາມໝັ້ງຄັ່ງ ແລະ ຄວາມເປັນອິດສະຫຼະທາງການເງິນຂອງພວກເຂົາ.
ບົດສະຫຼຸບ: ການປະຕິວັດທາງການເງິນທີ່ກຳລັງເກີດຂຶ້ນ
USDT ແລະ Bitcoin ແມ່ນການປະຕິວັດທາງການເງິນທີ່ເພີ່ມອຳນາດໃຫ້ບຸກຄົນໃນປະເທດກຳລັງພັດທະນາທີ່ຈະຫຼຸດພົ້ນຈາກນະໂຍບາຍການເງິນທີ່ລົ້ມເຫຼວ. ເຊັ່ນດຽວກັບສື່ສັງຄົມອອນລາຍໄດ້ປະຕິວັດພູມທັດຂອງສື່ໂດຍການໃຫ້ປະຊາຊົນຄວບຄຸມຂໍ້ມູນຂ່າວສານ, USDT ກຳລັງປະຕິວັດການເງິນໂດຍການໃຫ້ປະຊາຊົນຄວບຄຸມເງິນຂອງພວກເຂົາ. ສຳລັບທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ, ການປ່ຽນແປງນີ້ສ້າງສະພາວະຫຍຸ້ງຍາກທີ່ຮ້າຍແຮງ: ປັບຕົວ ຫຼື ສູນເສຍອິດທິພົນ. ລັດຖະບານອາດຈະພະຍາຍາມຄວບຄຸມກົດລະບຽບ ຫຼື ຫ້າມສະເຕເບິນຄອຍ, ແຕ່ຕາມທີ່ປະຫວັດສາດໄດ້ສະແດງໃຫ້ເຫັນກັບສື່ສັງຄົມອອນລາຍ.
-
 @ fd06f542:8d6d54cd
2025-03-25 01:40:53
@ fd06f542:8d6d54cd
2025-03-25 01:40:5330023的 文章 可发以被 删除 1 吗?
-
 @ 378562cd:a6fc6773
2025-03-25 00:16:58
@ 378562cd:a6fc6773
2025-03-25 00:16:58Bitcoin gives you financial freedom, but if you're not careful, someone’s watching. If you don’t run your own Bitcoin node, you're trusting someone else with your privacy. Here's why that’s a bad idea—and how running your own node fixes it.
What Is a Bitcoin Node? A Bitcoin node is software that connects to the Bitcoin network. It: ✅ Verifies transactions and blocks. ✅ Stores a copy of the blockchain. ✅ Relays transactions to the network. ✅ Lets you use Bitcoin without trusting anyone.
If you don’t run a node, you’re relying on someone else’s—usually a company that tracks your activity.
How Using Someone Else’s Node Destroys Your Privacy 👀 They Can See Your Transactions – Third-party wallets track what you send, receive, and how much Bitcoin you have. 📍 Your IP Address is Exposed – When you send a transaction, your location could be linked to it. ⛔ Censorship is Possible – Some services can block or delay your transactions. 🔗 They Can Link Your Addresses – Many wallets send your balance info to outside servers, connecting all your Bitcoin activity.
How Running Your Own Node Protects You 🔒 No One Knows Your Balances – Your wallet checks the blockchain directly, keeping your finances private. 🕵️ Hides Your IP Address – No one knows where your transactions come from, especially if you use Tor. 🚀 No Transaction Censorship – Your node sends transactions directly, avoiding interference. ✅ You Verify Everything – No fake data or reliance on third-party information.
But Isn’t Running a Node Hard? Not anymore! You can: 💻 Download Bitcoin Core and run it on your computer. 🔌 Use plug-and-play devices like Umbrel or MyNode. 🍓 Set up a cheap Raspberry Pi to run 24/7.
It’s easier than you think—and worth it.
Why This Matters The more people run nodes, the stronger Bitcoin gets. It becomes more decentralized, harder to censor, and more private for everyone.
Final Thought If you value privacy, freedom, and financial independence, running your own Bitcoin node is a no-brainer. Take control. Protect your Bitcoin. Run a node. 🚀
-
 @ da0b9bc3:4e30a4a9
2025-03-24 22:50:57
@ da0b9bc3:4e30a4a9
2025-03-24 22:50:57Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
This month is March and we're doing March Madness. So give me those Wacky and Weird crazy artists and songs. The weirder the better!
Let's have fun.
Can't have March Madness without Madness!
https://youtu.be/SOJSM46nWwo?si=gtghOZte3rh41tXg
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/924076
-
 @ 6e0ea5d6:0327f353
2025-03-24 22:42:59
@ 6e0ea5d6:0327f353
2025-03-24 22:42:59🎣
The support I never had could have saved me time, and I would certainly be farther along at this moment. However, that absence taught me to value having, and if I pass this lesson on to you earlier, it is so you have more time to learn what I could not see.
I like what my father once paraphrased: "If I have seen further, it is by standing on the shoulders of giants." And right now, I think of all that the little one who descends from you will one day behold. The heaviest burdens I pushed were so that you could soar, and if I have dedicated my existence to you, it is so that from my ashes, you may always rise again.
Out of love, I will try not to spoil you with excessive gifts, but instead, without being absent, I hope to build you up. With this line and these strands, I wish to teach you to catch your own fish. Live by what I have taught you and seek to understand what I could not. Honor who I was for you by becoming the best you can be.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 21e127ec:b43a5414
2025-03-24 22:30:47
@ 21e127ec:b43a5414
2025-03-24 22:30:47**
Respondiendo a Joel Serrano
nostr:npub1sg0j78carjndmg7qjfstk2y0e23r5cvxwn3u9z5cgnk5jnh4vxqs355u3l
respecto a hilo de Twitter sobre la adopción de Bitcoin como Medio de Intercambio con Unidad de Cuenta Delegada.
Primero, quiero compartir un artículo de Fernando Nieto que aborda la volatilidad inherente de Bitcoin:
https://x.com/fnietom/status/1454114755807961094
Este artículo de Nieto me ha llevado a cuestionarme si, en un escenario de adopción masiva, Bitcoin podría alcanzar realmente una estabilidad relativa suficiente para facilitar la coordinación de precios y el cálculo económico. De ahí surge la idea de que Bitcoin podría necesitar otros instrumentos que perfeccionen su función como unidad de cuenta.
Un ejemplo claro es lo que ocurrió en Venezuela con la dolarización de facto (al margen del Estado). En sus inicios (y aún hoy en gran medida), solo un pequeño porcentaje de la población tenía acceso a dólares a través la banca internacional, lo que les permitía realizar transacciones financieras fuera del sistema estatal. Estas operaciones se llevaban a cabo en el circuito financiero internacional, aunque las relaciones comerciales reales ocurrían dentro de Venezuela. Otro pequeño grupo tenía acceso a dólares en efectivo para sus transacciones económicas, pero la gran mayoría de la población solo disponía del bolívar venezolano como medio de intercambio en una economía dolarizada. En este contexto, muchos usaban el dólar para calcular los precios de bienes y servicios, mientras que el bolívar seguía siendo el medio de intercambio principal.
La diferencia notable con Bitcoin radica en las causas. En Venezuela, este fenómeno de medio de intercambio con unidad de cuenta delegada (Dolar - Bolivar) se debía a las restricciones monetarias impuestas por el gobierno respecto al dólar, la falta de servicios financieros en esa moneda y la escasa liquidez de dólares físicos. En el caso de Bitcoin, seria debido a su volatilidad inherente producto de su oferta inelástica (Bitcoin como medio de intercambio generalmente aceptado con unidad de cuenta delegada en Fiat publico ó privado - stablecoin).
Sin embargo, esto no implica que la unidad de cuenta que complemente a Bitcoin deba ser necesariamente emitida por un Estado. Creo que la verdadera innovación de Bitcoin radica en su potencial para actuar como un patrón monetario que descentralice la emisión monetaria de los estados gracias al monopolio de la violencia, algo que sí podían ejercer con el oro. Con Bitcoin, el Estado pierde el control, permitiendo que la banca libre emita monedas estables respaldadas en un patrón Bitcoin. El escenario sería una competencia entre monedas estables adoptadas en un segundo plano para facilitar el cálculo económico necesario para coordinar precios, préstamos, servicios financieros y la institución del crédito. Y Bitcoin podría funcionar en primer plano principalmente como medio de intercambio.
No pienso que Bitcoin vaya a eliminar las monedas fiat o estables, ya sean públicas o privadas. Más bien, lo veo como un mecanismo disciplinador que podría prevenir los malos comportamientos monetarios.
Gracias por tu tiempo agradecido y atento a tu posible respuesta.
-
 @ 6e0ea5d6:0327f353
2025-03-24 22:11:58
@ 6e0ea5d6:0327f353
2025-03-24 22:11:58People, mio caro, mistake silence for weakness just as they mistake the shine of silver for the value of gold. Because the modern world—hysterical and theatrical—has learned to respect noise, shouting, emotional outbursts, and the endless chatter of failures who demand respect without ever having earned it. But we, who have emerged from the forge of omertà, know that the one who reacts immediately is merely begging for relevance.
A real man—and I do not refer to those who simply wear trousers, but to those who carry their name and reputation upon their shoulders—knows that humiliation is not avenged with words of promise, but with a sentence of action. And sentences, amico mio, are not uttered in impulse. They are written in silence, with permanent ink on the paper of memory.
The one who strikes back in the moment of offense reveals that he is still under the dominion of emotion. But the one who remains silent, who stands still, who looks his aggressor in the eye and does not utter a single word—he has already begun to dig, with his own hands, the symbolic grave of the one who offended him. His coldness is not the absence of pain, but the absolute mastery of it. And that is precisely why he is feared. Not because he screams, but because he thinks. Because he smiles while thinking. Because he watches while you believe he has forgotten.
In Sicily, we say that the wolf does not howl when preparing to strike—it merely crouches. The fool believes that silence is cowardice. The wise man knows it is calculation. While the world carries on with its pathetic routines and social theater, the humiliated man prepares the final stage. And on this stage, there will be no audience, no applause. Only the dry sound of justice being served. Without mercy. Without apologies. Without a second chance.
Vengeance is not an emotion. It is an art. And the first stroke in the masterpiece is control.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 7d33ba57:1b82db35
2025-03-24 21:47:31
@ 7d33ba57:1b82db35
2025-03-24 21:47:31Located on the southeastern coast of Spain, Cartagena is a city rich in history, maritime heritage, and stunning Mediterranean views. With over 3,000 years of history, it boasts Roman ruins, modernist architecture, and a vibrant port, making it one of Spain’s most underrated travel destinations.
🏛️ Top Things to See & Do in Cartagena
1️⃣ Roman Theatre of Cartagena 🎭
- The star attraction, dating back to the 1st century BC.
- One of Spain’s best-preserved Roman theatres, discovered in 1988 beneath the city.
- Visit the museum to learn about its history before exploring the impressive ruins.
2️⃣ Concepción Castle & Panoramic Lift 🏰
- A 14th-century fortress on a hill offering spectacular views of the city and harbor.
- Take the glass elevator for a scenic ride to the top.
- The museum inside explains Cartagena’s rich military and naval history.
3️⃣ Calle Mayor & Modernist Architecture 🏛️
- The city’s main pedestrian street, lined with elegant buildings, shops, and cafés.
- Admire Casa Cervantes, Gran Hotel, and the Casino, examples of Cartagena’s modernist style.
4️⃣ National Museum of Underwater Archaeology (ARQVA) ⚓
- Learn about sunken treasures, ancient shipwrecks, and underwater archaeology.
- Features artifacts from Phoenician, Roman, and medieval maritime history.
5️⃣ Naval Museum & the Peral Submarine 🚢
- Discover Cartagena’s naval history, including models of warships and maritime artifacts.
- See the Peral Submarine, the first-ever electric-powered submarine, invented in 1888.
6️⃣ Playa de Cala Cortina 🏖️
- A beautiful urban beach, just a few minutes from the city center.
- Great for swimming, snorkeling, and relaxing with clear Mediterranean waters.
7️⃣ Batería de Castillitos 🏰
- A dramatic cliffside fortress with fairy-tale turrets and massive coastal cannons.
- Located 30 minutes from Cartagena, offering panoramic sea views.
🍽️ What to Eat in Cartagena
- Caldero del Mar Menor – A local seafood rice dish, similar to paella 🍚🐟
- Michirones – A hearty bean stew with chorizo and ham 🥘
- Marineras – A Russian salad tapa served on a breadstick with an anchovy 🥖🐟
- Tarta de la abuela – A delicious layered biscuit and chocolate cake 🍰
- Asiático Coffee – A signature Cartagena coffee with condensed milk, brandy, and cinnamon ☕🍸
🚗 How to Get to Cartagena
🚆 By Train: Direct trains from Madrid (4 hrs), Murcia (45 min), and Alicante (1.5 hrs)
🚘 By Car: ~30 min from Murcia, 1.5 hrs from Alicante, 3.5 hrs from Madrid
✈️ By Air: Nearest airport is Murcia-Corvera Airport (RMU) (~30 min away)
🚢 By Cruise Ship: Cartagena is a popular Mediterranean cruise stop💡 Tips for Visiting Cartagena
✅ Best time to visit? Spring & Autumn – warm but not too hot 🌞
✅ Wear comfortable shoes – Many streets and attractions involve walking on cobblestones 👟
✅ Visit during the Roman Festival (Carthaginians & Romans, September) for a unique cultural experience 🎭🏛️
✅ Try a sunset drink at a rooftop bar near the port for incredible views 🍹🌅 -
 @ 4520e45a:aa52208a
2025-03-24 21:42:12
@ 4520e45a:aa52208a
2025-03-24 21:42:12Hashrate\ Die Hashrate wird vom Pool basierend auf den übermittelten Shares innerhalb eines Zeitraums berechnet und zeigt, wie viele Hashes pro Sekunde dein Worker generiert.\ Die Statistik zeigt die durschschnittliche Hashrate für:\ 1 Minute (1m), 5 Minuten (5m), 1 Stunde (1hr), 1 Tag (1d), 7 Tage (7d)
1M = 1 MH/s = 1'000'000 H/S\ 1G = 1 GH/s = 1'000'000'000 H/S\ 1T = 1 TH/s = 1'000'000'000'000 H/S\ 1P = 1 PH/s = 1'000'000'000'000'000 H/S
Lastshare\ Angabe in Unix Zeit, wann der letzte Share von deinem Worker bei ckpool abgeliefert wurde.\ 🔗 unix timestamp converter
Worker\ Anzahl Worker. Wenn mehrere Miner identischen Namen haben, werden sie zu einem Worker zusammengefasst. Wenn du für jeden Miner separate Statistiken willst, muss sich deren Worker-Name hinter der Bitcoin-Adresse unterscheiden:\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe1\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe2\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe3
Shares\ Anzahl akzeptierter Shares, die seit Beginn von deinem Worker bei ckpool abgeliefert wurden. Wenn ein Hash alle notwendigen Kriterien und die vom Pool geforderte Schwierigkeit erfüllt, wird er als Share an ckpool übermittelt.
Bestshare\ Der beste/höchste Share der seit dem letzten gefundenen Block abgeliefert wurde.\ Wenn du oder ckpool einen Block gefunden hat, wird dieser Wert zurück auf Null gesetzt.
Bestever\ Der jemals beste/höchste gefundene Share. Im AxeOS als Best Difficulty bezeichnet.\ Wenn du oder ckpool einen Block gefunden hat, wird dieser Wert nicht zurück auf Null gesetzt.
Ein Block wird gefunden, wenn die Schwierigkeit (=Difficulty) eines Shares höher ist als die aktuelle Netzwerk-Schwierigkeit.
Zum Zeitpunkt des Schreibens des Reads — Blockzeit 889277 — liegt die Netzwerk-Schwierigkeit bei: 113'757'508'810'854 = 113T
Authorised\ Angabe in Unix Zeit, wann du dich zum ersten Mal mit ckpool verbunden hast (wurde erst mit v0.9.7 am 30.05.2023 eingeführt).\ 🔗 unix timestamp converter
-
 @ ed5774ac:45611c5c
2025-03-24 21:33:47
@ ed5774ac:45611c5c
2025-03-24 21:33:47Erdogan’s Turkey: The Rise, Reign, and Decline of a Political Strongman
As Turkey’s political crisis intensifies with Erdogan’s imprisonment of Imamoglu—a leading opposition figure and likely frontrunner in the 2028 presidential elections—it is crucial to analyze the historical events and geopolitical factors that enabled Erdogan’s rise, secured the consolidation of his rule, and allowed him to maintain his grip on power for decades. To understand the foundations of Erdogan’s enduring political legacy, we must examine the historical events that shaped his ideology and the global power struggles of the time. Equally important are the international actors who facilitated his rise and prolonged his rule. Key factors include the link between Erdogan’s rise and the Iraq War, the interplay between Turkey’s military coups and the Ukraine crisis, the events that led to the erosion of Western support for Erdogan, the role of the U.S. and NATO in the 2016 coup attempt against his rule, and the shifting geopolitical landscape that continues to define Turkey’s political future.
The Roots of Islamism: The CIA, the 1980 Coup, and the Suppression of Turkish Liberalism
Erdogan’s rise is deeply intertwined with the growth of Turkey’s Islamic movement, which gained traction in the 1970s amid Cold War geopolitics. During this period, the U.S., under the guidance of Zbigniew Brzezinski, National Security Advisor to President Jimmy Carter, devised the “Green Belt” strategy. This plan aimed to cultivate a radicalized Islamic generation across the Muslim world to counter the spread of communist ideology. The U.S. intervention in Afghanistan, which radicalized certain factions and triggered the Soviet invasion, was a critical component of this strategy. Brzezinski himself proudly acknowledged this in various interviews. Turkey, a NATO ally bordering the Soviet Union, became a key theater for implementing this policy.
The military coup of September 12, 1980, marked a pivotal moment in Turkish history. Led by General Kenan Evren, the Turkish armed forces seized power under the pretext of restoring order amid escalating violence between leftist and rightist factions that had claimed thousands of lives. However, the junta’s crackdown disproportionately targeted the Turkish left—a movement distinct from Soviet-style communism, composed of liberal, educated intellectuals such as writers, artists, journalists, and thinkers. These individuals, who championed Turkish sovereignty, intellectual freedom, and democratic ideals, were perceived as a direct threat to the military’s Islamization agenda, backed by the CIA. Tens of thousands were imprisoned, tortured, or executed, while left-wing organizations were banned outright.
At the same time, the junta actively fostered Islamist groups, establishing religious schools known as Imam Hatip institutions under the guise of combating Marxism and communism. In reality, their true objective was to eliminate anyone who sought Turkish sovereignty, embraced patriotism, or valued critical thinking. Writers, artists, journalists, and intellectuals—those who dared to think independently and question authority—were viewed as existential threats to the Islamization model the military and its CIA allies sought to impose. By silencing these voices, the junta aimed to eradicate opposition to their vision of a Turkey subservient to religious dogma and foreign interests, ensuring a populace stripped of sovereign thought and resistant to enlightenment.
This paradox—a secular military suppressing liberal intellectuals while nurturing Islamist groups—laid the foundation for Erdogan’s rise and the eventual Islamization of Turkish society.
The Chaos of the 1990s: Economic Crisis and the Rise of Erdogan
The 1990s were a chaotic decade for Turkey, marked by economic instability, a Kurdish insurgency, and a revolving door of coalition governments. The 1994 financial crisis saw inflation soar, while terrorist attacks by the Kurdistan Workers’ Party (PKK) and political assassinations fueled national disarray. Successive governments, often beholden to globalist agendas dictated by the International Monetary Fund and World Bank, failed to deliver stability. This period mirrored today’s European political crises, where ideological convergence has left voters disillusioned.
Into this void stepped Erdogan, a charismatic former soccer player turned politician from Istanbul’s working-class Kasimpasa district, whose blend of populist appeal and religious rhetoric resonated with a disillusioned populace. His rise was no accident. In 1994, he won the mayoralty of Istanbul as a member of the Islamist Welfare Party (Refah Partisi), showcasing a blend of populist charisma and religious appeal. However, his early political career faced a setback in 1997 when the military, acting as guardians of Turkey’s secular Kemalist legacy, forced the resignation of Welfare Party Prime Minister Necmettin Erbakan in what was dubbed a “postmodern coup.” Erdogan’s imprisonment in 1998 for reciting a divisive poem only solidified his image as a martyr among his devout supporters.
The 2001 Crisis: Neocons, Economic Sabotage, and Erdogan’s Ascendancy
Erdogan’s true ascent began amid Turkey’s devastating 2001 financial crisis, which saw the economy contract by 5.7%, unemployment spike, and the Turkish lira collapse. The crisis, worsened by IMF-mandated austerity measures, discredited the ruling coalition under Prime Minister Bulent Ecevit. A staunch nationalist, Ecevit had spearheaded Turkey’s 1974 intervention in Cyprus and forced Syria to expel PKK leader Abdullah Ocalan in 1999. His refusal to align Turkey with the impending U.S.-led Iraq War in 2003 made him a liability for U.S. neoconservatives, who were already preparing for the conflict.
Far from a mere economic downturn, the 2001 crisis was a deliberate strategy orchestrated by the global Western financial cartel to destabilize Ecevit’s nationalist government. This administration, fiercely protective of Turkish sovereignty, had unequivocally opposed Turkey’s involvement in the Iraq War. To eliminate this obstacle, the financial cartel—comprising international financial institutions and Western-backed actors—engineered the crisis by exploiting Turkey’s reliance on hot money and Western financial support. The resulting economic collapse eroded public trust in the government and existing political parties, creating a power vacuum that paved the way for Erdogan. Handpicked by the globalist cabal as their new proxy, Erdogan was positioned to advance their political agenda in Turkey. The neocons viewed him as a pliable ally: a moderate Islamist who could pacify Turkey’s religious conservatives while advancing Western interests. Despite resistance within his own party, Erdogan advocated for Turkish involvement in the Iraq War, though the Turkish Parliament, with the help of dissidents in his party, ultimately rejected U.S. troop deployments in 2003. Nevertheless, Erdogan remained loyal to his neocon backers and globalist patrons, privatizing state assets at rock-bottom prices—akin to Yeltsin’s controversial reforms in 1990s Russia—and deepening Turkey’s economic dependence on the EU and the U.S.
In addition to tying Turkey’s economy to Western interests, Erdogan targeted the Turkish military in 2007 through the Ergenekon and Sledgehammer trials. Widely criticized as show trials orchestrated with the help of the Gulen movement—a shadowy Islamic network led by Fethullah Gulen—these cases imprisoned or sidelined hundreds of officers, including navy admirals opposed to NATO’s Black Sea ambitions. These officers had long argued that NATO’s mission ended with the fall of the Soviet Union and advocated for closer ties with Russia and China. They also opposed plans to integrate Georgia and Ukraine into NATO, fearing it would destabilize the region and turn the Black Sea into a battleground between the West and Russia. By weakening the navy and sidelining its dissenting admirals, Erdogan brought Turkey back in line with NATO’s strategic objectives, enabling the neocons to advance their plans for NATO expansion into the Black Sea region—a move that set the stage for the 2008 Russo-Georgian War and the 2014 Ukrainian crisis.. Without this internal coup against the Turkish military, these events might have unfolded differently—or not at all.
For his services to the globalist agenda, Erdogan was portrayed in Western media as a democratizing hero, and Turkey’s economy was praised for its growth and strength. However, the reality was starkly different. To understand the globalist propaganda surrounding Erdogan, consider Barack Obama’s first foreign visit as U.S. president: a trip to Turkey in 2009. In a speech to the Turkish Parliament, Obama praised Erdogan’s “democratic reforms” and the strength of Turkey’s economy—which was growing steadily only due to cheap credit provided by international financial institutions serving the same globalist interests Erdogan represented. Meanwhile, journalists and dissidents filled Turkish prisons.
The 2016 Coup Attempt: Erdogan’s Break with the West
Erdogan’s honeymoon with the West soured in the 2010s. His support for Egypt’s Muslim Brotherhood and his interventionist stance in Syria clashed with U.S. priorities, especially after the Arab Spring upended regional alliances. Sensing Erdogan’s growing autonomy, the neocons turned to Fethullah Gulen, a cleric living in Pennsylvania since 1999 with close ties to the CIA and the Clinton Foundation. Gulen’s Hizmet movement, once an ally in Erdogan’s rise, had infiltrated Turkey’s police, judiciary, and military, creating a “parallel state.”
The July 15, 2016, coup attempt—marked by rogue military units bombing parliament and nearly capturing Erdogan—was orchestrated by factions of the Gulen movement within the army, with the involvement of the CIA and NATO, using Incirlik Air Base as one of the primary command centers to coordinate the operation (one of NATO’s largest military bases in the region). The timing suggests that the neocons, anticipating Hillary Clinton’s presidency, planned to install Gulen as their new puppet in Turkey. As a radical Sunni leader hostile to Iran, Gulen could have aligned Turkey with a broader anti-Iranian axis, potentially dragging the country into a regional war against Iran—much like Saddam Hussein did three decades earlier.
The coup’s failure, quashed by loyalists and public resistance, marked a turning point, leading Erdogan to purge over 100,000 civil servants and consolidate his power through a 2017 referendum and pivoting toward Russia and China—not out of conviction, but as leverage against Western abandonment.
Turkey’s Geopolitical Balancing Act: Ukraine, NATO, and the Black Sea
Erdogan’s post-2016 flirtations with Moscow—evidenced by the purchase of Russian S-400 systems and energy deals—reflect more than a pragmatic balancing act. They reflect a desperate attempt to regain Western attention, akin to dating someone new to make an ex jealous, aimed at convincing the West not to write him off.
The Ukrainian crisis, escalating with Russia’s 2022 invasion, has pushed Turkey into a delicate role. As a NATO member controlling the Bosphorus, Erdogan has mediated grain deals and prisoner swaps, leveraging Turkey’s strategic position. Yet his reluctance to fully back NATO’s hardline stance has further alienated him from the West, making him a target for a potential regime change operation as the West has grown desperate to win its proxy war against Russia. As a result, international media and globalist factions have intensified efforts to undermine his regime, seeking to remove him from power.
Turkey at a Crossroads: Imamoglu, Erdogan’s Decline, and the Future
Erdogan has fulfilled his mission: he has made Turkey’s economy dependent on the West, eliminated patriotic voices in the military, dismantled the parliamentary system, wrecked the education system, and buried the secular Turkish republic. His legacy is a deeply polarized Turkey: economically dependent on the West, militarily weakened, and institutionally hollowed out.
Corruption scandals, a collapsing lira, and authoritarian excesses have fueled widespread public discontent. Yet, rather than addressing the root causes of this anger—economic hardship, growing authoritarianism, and systemic corruption—Erdogan has grown increasingly paranoid, attributing every challenge to Western conspiracies and interventions. This refusal to confront reality has only deepened the divide between him and the Turkish people, fueling widespread disillusionment and anger.
Imamoglu’s rise—winning Istanbul in 2019 and 2023 despite blatant election irregularities, systematic government interference, censorship, and the full force of Erdogan’s authoritarian machinery—stands as a testament to his resilience and the enduring hope of Turkey’s opposition. Facing a system rigged to ensure his defeat, Imamoglu triumphed against overwhelming odds. Erdogan’s regime spared no effort, leveraging state media, the judiciary, and security forces to manipulate the results, yet it could not prevent Imamoglu’s victories in Istanbul, which shattered the illusion of invincibility surrounding Erdogan’s rule. His recent imprisonment on fabricated charges ahead of the 2028 elections underscores Erdogan’s desperation to suppress this threat, further alienating a populace yearning for change.
Turkey now stands at a crossroads. The powers that once propelled Erdogan to prominence—U.S. neoconservatives and the Islamist legacy of the 1980 coup—have lost control of their creation. His fall from Western favor, tied to the 2016 coup attempt and his regional overreach, has left him isolated, oscillating between East and West while clinging to power as domestic anger reaches a boiling point. Whether Imamoglu or another leader emerges, Turkey’s post-Erdogan era will face the monumental task of rebuilding its secular republic and defining its role in an increasingly complex global landscape.
Turkey’s struggle is not just its own—it is an example of the suffering endured for decades under Western colonialism and a parasitic financial order. This system, designed to enrich a handful of elites in the West, thrives by exploiting the Global South, perpetuating poverty, and engineering chaos to maintain control. Turkey’s fight for self-determination stands as a beacon for all nations seeking to break free from the chains of neocolonialism and reclaim their rightful place in a just and equitable global order. The future must be built on the sovereignty of nations, free from the selfish designs of a Western oligarchy.
-
 @ 0028f12f:532c1c67
2025-03-24 21:23:28
@ 0028f12f:532c1c67
2025-03-24 21:23:28An owner buildable microhome closed-loop ecosystem that decentralizes residential manufacturing w/ancient & modern tools, materials, and skillsets.


Project Overview:
For many, whether renters or “owners”, monthly housing costs are 30%, sometimes 50% of their monthly operating expenses, with financing, permitting, maintenance, and property tax costs significantly driving those costs ever higher. As a result, low-cost, efficient to build and maintain, modular shelters are more needed than ever. By combining ancient, 20th century, and 21st century technologies humanity can now self-design, fund, and build decentralized pre-manufactured, site-installed, residential living systems for ourselves.
Decentralizing residential construction in order to empower individuals and their communities by providing cottage industries that build small cottages with tools, training, and flexible, simple, and appropriate designs will not only provide sovereignty over shelter to owner-builders, it creates the potential for organically growing physical community infrastructures and individual’s financial wealth.
Accomplishing this requires:
- Off-the-shelf tools available at most major hardware stores worldwide. i.e. no expensive, capital intensive, difficult to operate and/or maintain tooling
- Commonly available, or easily acquirable, skills with those tools
- Locally available, low-cost, sustainable, materials with a minimal environmental impact
- Prioritizing “upcycled” materials diverted from the waste stream
- Non-toxic, durable, yet, easy to repair materials
- Utilizing site resourced materials whenever feasible
- Integrated design that stacks functions, turns waste streams into resources (i.e. grey gardens, Composting worms and fly larvae, natural gas bio-digesters, aquaponics garden/pools)
- Self-funding without taking on debt burdens, permission, and/or insurance agents having authority over the decision-making processes
As E. F. Schumacher showed us in his book “Small is Beautiful”, Christopher Alexander with “Pattern Language Design”, and Bill Mollison with “Permaculture Design”, an appropriately scaled design pattern that can be varied as needed for each use case and location is what we all need and desire. Empowering individual families and communities to truly OWN their homes, because the idea, skills, and experience needed to build them have become common knowledge available to any and all willing to do the work.
Residential housing has been artificially driven up in value by speculators because the “saving” function of fiat money is broken and their prices are not driven by their functional value, financing and compliance costs make owning a home even more expensive, and poor design decisions by gatekeepers provide poor value, and dependency on specialized tools and skillsets drives up maintenance costs. Waste during initial, repair, and remodeling construction match all other daily waste going to the landfills, while chemical fire retardants, plastics, and glues often create toxic interior air quality worse than outside. Dozens of specialized crews that do not communicate with or understand others’ roles, needs, and concerns leading to wasted time, money, and materials.
Might not the best solution to the current housing affordability crisis simply be to provide families, not with over-priced, over-sized, and overly regulated shelters, but to instead empower all us to design and build decentralized, anti-fragile, and sustainable residential living systems that shelter more than our bodies and possessions_. Homes that also_ preserve and protect the supply chains for our essential daily needs. All of humanity, in every culture on every continent in every climate will be empowered by acquiring useful trade skills that can provide, not only for their own daily needs, but also deliver the opportunity to earn ongoing right livelihood providing these same livingry services to our local communities.
What if…
- In a few weeks the tradecrafts could be acquired, that with commonly accessible and affordable tools, empower men and women everywhere to use renewable, sustainable, and locally available materials to build residential living ecosystems that, rather than consume, they produce capital over time in the form of:
- Soil, Plant, Animal, & Human food
- Water for gardens & all inhabitants
- Fuel for heating & cooking
- KwHrs to run appliances, fixtures, & tools
- Bitcoin to access global marketplaces
- Government “permitting”, zoning, insurance, and financing startup costs are reduced & often eliminated.
- Operational costs and maintenance labor are minimized, efficiency and production increase over time, and wastes streams are turned into resource streams.
- The physical, intellectual, financial, and experiential capital are re-invested into serving family and neighbors by creating a decentralized open-source cooperative cottage construction industry
Building Biology, or "Bau-Biologie" in German, provides us with a mental for our Pattern Language design stack that allows for biomimicry and biophilic design to evolve into a synergistic “macrobiome” that shows us the way to design and build living residential “super organisms”. Our house is not only our ‘3rd Skin’, the property line is the 4th skin, acting as the outermost semi-permeable protective layer of our residential ecosystems.
The How:
By designing visible and invisible structures so that human, animal, plant, & soil organisms are ALL working together to coordinate a single living, breathing, growing entity. One with biological electrical ‘nervous system’ that cultivates, stores, & distributes electrical power, that has a ‘digestive system’ that provides for fresh water collection, filtration, & distribution, as well as grey/black water disposal. With a respiratory, skeletal, and connective tissues, organs, and systems, that nourish and protect essential organs.
By designing in more than just shelter, it becomes possible to provide all inhabitants with fuel for cooking and heating generated from passive solar heating, methane biodigesters, wood-gas/wind/water/PV generators, and BTC mining. Buckminster Fuller’s work showed us that geodesic domes are the most efficient geometries to use, and experience over time with residential domes has taught many that including a cupola and a dormer-style clerestory facilitate naturally efficient lighting and ventilation. While 3d printing, thin-shell latex cement canvas, and styro-foam concrete technologies now empower us all to design,manufacture, and build the joints, skin, and insulative in-fill for these geometric shapes in any configuration we can imagine. Adding space age insulative ceramic micro-spheres creates a non-toxic flexible highly reflective exterior coating suitable for rainwater collection and stacking the Japanese Shou Sugi Ban ancient natural wood preservation protects and beautifies the often up-cycled wood skeletal elements.
By riding on the efficiencies of scale that already exist for trampoline frames, both new and re-purposed, the existing manufacturing, distribution, and packaging of these galvanized steel skeletal framing elements we can add the wood, plastic, fabric, and cement elements as needed for each use case for this basic structural design unit. The lightweight framing, skinning, and insulation these allow for also enable more areas to become inhabitable by mounting these to docks enable residential use currently unavailable flood plane land and for Lake-steading, and eventually Sea-steading. By keeping the roofing footprint under 200 sq ft, the permitting threshold in many cities like Austin, TX the compliance costs of permitting and zoning are eliminated. By keeping costs down to 5-figures, instead of the 6 & 7-figures spent building most modern day homes, doing so with finance and insurance costs that can be kept to a minimum and sometimes eliminated.
Concept MVP
 Individually shouldering the responsibility for designing, building, and maintaining the infrastructure for sheltering our families and our business assets is now more possible by stacking our designs, tools, and materials on the shoulders of designers, engineers, and owner-builders from all other times, places, and cultures.
Individually shouldering the responsibility for designing, building, and maintaining the infrastructure for sheltering our families and our business assets is now more possible by stacking our designs, tools, and materials on the shoulders of designers, engineers, and owner-builders from all other times, places, and cultures.I built this roof of this 200 sq ft micro-dome igloo in a semi-permanent minimum viable form entirely by myself over a few months with under $3k spent on tools and materials.
 The final piece of this jigsaw puzzle came when I gained access to 3d printing technology I began printing brackets for a 2v dome. The free model that I found was sized so that a single cut on an 8’ board would provide the two lengths of struts needed without any waste. (https://www.thingiverse.com/thing:2483498). The initial model design happened to form a 14’ diameter hemisphere, with a 7’ height. I then realized that the upcycled trampoline frames made a superior vertical “pony wall” as is commonly used to gain more headroom around the interior perimeter of dome structures. By using 2”x12” wood with double beveled cuts to form a 14’ octagon I created a ledge that the dome could be mounted to, that also provides a mounting surface for guttering to enable rainwater catchment
The final piece of this jigsaw puzzle came when I gained access to 3d printing technology I began printing brackets for a 2v dome. The free model that I found was sized so that a single cut on an 8’ board would provide the two lengths of struts needed without any waste. (https://www.thingiverse.com/thing:2483498). The initial model design happened to form a 14’ diameter hemisphere, with a 7’ height. I then realized that the upcycled trampoline frames made a superior vertical “pony wall” as is commonly used to gain more headroom around the interior perimeter of dome structures. By using 2”x12” wood with double beveled cuts to form a 14’ octagon I created a ledge that the dome could be mounted to, that also provides a mounting surface for guttering to enable rainwater catchment The vertical poles and angled connecters from the trampoline happened to be 7’ in width, allowing for a 7’x7’ square addition to the 14’ diameter circle. The 140 sq ft of the trampoline and the 49 sq ft add-on, at 189 in total came in just under the 199 sq ft maximum allowed without a permit. This shape took form as a geodesic igloo. When I contemplated upon the partial skeletal framework for awhile before “skinning” the structure I decided that turning the 5 triangles coming off the corners of the pentagon cupola would not only provide dispersed light from any/all directions it also allowed for leaving those opening until last to allow for applying the finishing coats to the uppermost pentagon of the dome. After considering ways to keep from putting a window in the roof, with the likelihood for leaks that brings, I came up with the idea of the 5 triangular dormer style windows that are easier to seal and prevent direct sunlight while allowing indirect daylight from all sides into the dome interior. Those triangular dormers, along with the cupola vents and wall perimeter vents can be opened and closed to create and control passive ventilation
The vertical poles and angled connecters from the trampoline happened to be 7’ in width, allowing for a 7’x7’ square addition to the 14’ diameter circle. The 140 sq ft of the trampoline and the 49 sq ft add-on, at 189 in total came in just under the 199 sq ft maximum allowed without a permit. This shape took form as a geodesic igloo. When I contemplated upon the partial skeletal framework for awhile before “skinning” the structure I decided that turning the 5 triangles coming off the corners of the pentagon cupola would not only provide dispersed light from any/all directions it also allowed for leaving those opening until last to allow for applying the finishing coats to the uppermost pentagon of the dome. After considering ways to keep from putting a window in the roof, with the likelihood for leaks that brings, I came up with the idea of the 5 triangular dormer style windows that are easier to seal and prevent direct sunlight while allowing indirect daylight from all sides into the dome interior. Those triangular dormers, along with the cupola vents and wall perimeter vents can be opened and closed to create and control passive ventilation For the next, permanent version designed for occupancy by a couple I’m raising this current 30” wall to a full 8’ height to allow for a living/sleeping loft under the dome hemisphere. In order to support a second floor, arranging the floor joists in a hub and spoke layout bolted directly to the 1 ½” galvanized steel vertical support poles of the trampoline “oreo” framework. By supporting the central hub with the stair framing, rather than dropping a pole from the center of the peak of the dome, a ceiling fan can be mounted there instead to circulate air when the wind isn’t blowing. By using only 2 x 8’x4’ sheets of plywood for the floor of the private living/sleeping loft only 64 sq ft of floor space is necessary, as a wall mounted desk and mounting shelves for a futon frame as the kitchen ceiling will keep the bed from taking up precious floor space, while maximizing functionality of every cubic foot of the micro-dome igloo. The framing for the stairs provided an interior shower/toilet closet, preferably a sawdust “humanure” composting toilet to collect “night soil” in order to return nutrients back to the garden soil. Having an optional add-on door that opens into an IBC tote double-stack “outhouse” with a bio-gas generating flush toilet and another door opening up to an outdoor shower draining into greywater gardens and mulch basins, not only automates watering the garden while providing nutrients, it also allows for the natural gas to be used to fuel a cookstove, hot water heater, or natural gas generator.
For the next, permanent version designed for occupancy by a couple I’m raising this current 30” wall to a full 8’ height to allow for a living/sleeping loft under the dome hemisphere. In order to support a second floor, arranging the floor joists in a hub and spoke layout bolted directly to the 1 ½” galvanized steel vertical support poles of the trampoline “oreo” framework. By supporting the central hub with the stair framing, rather than dropping a pole from the center of the peak of the dome, a ceiling fan can be mounted there instead to circulate air when the wind isn’t blowing. By using only 2 x 8’x4’ sheets of plywood for the floor of the private living/sleeping loft only 64 sq ft of floor space is necessary, as a wall mounted desk and mounting shelves for a futon frame as the kitchen ceiling will keep the bed from taking up precious floor space, while maximizing functionality of every cubic foot of the micro-dome igloo. The framing for the stairs provided an interior shower/toilet closet, preferably a sawdust “humanure” composting toilet to collect “night soil” in order to return nutrients back to the garden soil. Having an optional add-on door that opens into an IBC tote double-stack “outhouse” with a bio-gas generating flush toilet and another door opening up to an outdoor shower draining into greywater gardens and mulch basins, not only automates watering the garden while providing nutrients, it also allows for the natural gas to be used to fuel a cookstove, hot water heater, or natural gas generator. Strategically, this is an advanced version of the Gradual Stiffening pattern, as articulated in the Pattern Language Design dictionary created by Christopher Alexander. Other patterns like Bringing the Outside In, which the passive lighting and ventilation features contribute to, and Intimacy Gradient, which the upstairs private/downstairs public uses of space create, came from his design library. Other design pattern strategies coming from Bill Mollison’s ideas shared in his Permaculture Design Manual, like Stack Functions, Transform Waste into Resource, and a Resource Harvesting Roof.
Strategically, this is an advanced version of the Gradual Stiffening pattern, as articulated in the Pattern Language Design dictionary created by Christopher Alexander. Other patterns like Bringing the Outside In, which the passive lighting and ventilation features contribute to, and Intimacy Gradient, which the upstairs private/downstairs public uses of space create, came from his design library. Other design pattern strategies coming from Bill Mollison’s ideas shared in his Permaculture Design Manual, like Stack Functions, Transform Waste into Resource, and a Resource Harvesting Roof. Collecting water, heat, and photons by tactically implementing grey-water gardens, the methane bio-digesters, the humanure composting/BSFL cultivation, passive solar water heater and PV systems, as well as wood-gas generator upgrades. By re-purposing the existing trampoline manufacturing infrastructure, adding 3d design and printing, and upcycled “re-blended” paint from the city recycling center, the capital to manufacture the steel and mats are minimized, landfill waste is diverted into a resource while cutting costs.
 At the same time, by training local craftsmen with on-the-job vocational technology education the tools and skills necessary for establishing e
ssential infrastructure for cottage industry that build cottages for local community members. By doing so we can minimize upfront capital costs, lower environmental impact, and contribute to empowering community members with right livelihood, as well as sovereign shelters. Providing more than just a fish/shelter to those in need, instead providing fishing/building tools & knowledge of how to use them that will provide for their needs over a lifetime.
At the same time, by training local craftsmen with on-the-job vocational technology education the tools and skills necessary for establishing e
ssential infrastructure for cottage industry that build cottages for local community members. By doing so we can minimize upfront capital costs, lower environmental impact, and contribute to empowering community members with right livelihood, as well as sovereign shelters. Providing more than just a fish/shelter to those in need, instead providing fishing/building tools & knowledge of how to use them that will provide for their needs over a lifetime. To be sovereign means to not have to ask anyone. This CAN be accomplished by dealing with all waste onsite, collecting and properly disposing of your solid and liquid waste onsite, by generating, storing, and distributing power locally. By being able to Do The Work yourself, fund the build yourself, and be responsible for the results yourself reliance on outsourced specialists is avoided. Asking insurance agents, zoning/code officers, and finance officers to manage risk, to permit your designs, and to fund your shelter with fiat debt-notes is to become a “House Slave”, living in over-priced, badly built, gilded cages designed for profit, not to cultivate quality of life for all on it.
To be sovereign means to not have to ask anyone. This CAN be accomplished by dealing with all waste onsite, collecting and properly disposing of your solid and liquid waste onsite, by generating, storing, and distributing power locally. By being able to Do The Work yourself, fund the build yourself, and be responsible for the results yourself reliance on outsourced specialists is avoided. Asking insurance agents, zoning/code officers, and finance officers to manage risk, to permit your designs, and to fund your shelter with fiat debt-notes is to become a “House Slave”, living in over-priced, badly built, gilded cages designed for profit, not to cultivate quality of life for all on it.Current compliance, finance, and insurance infrastructure, when combined with the inflexible, design, and construction processes cannot help but build "dead structures". Not designed for, adapted to, or adapted by the inhabitants, our built environments do not truly support their inhabitants or the external environment they're dropped into. An entirely new paradigm, a "Livingry Design/Build/Operate" science and art of cultivated curated living systems is how these mistakes can be remedied going forward.
Biodome Igloos: designed as basic 'cellular units and family 'tissues' coordinating operations to form multi-species community 'organisms'. Using good design, conscious cultivation, and responsible stewardship to customize stacked living systems out of community curated patterns and transformative process IS how we heal all our relations** by healing ourselves with food as medicine, right livelihood for value-added services, and mathematics to fabricate trust and establish truth.
Decentralized, closed-loop, off-grid, owner-built residential 'nodes' that are manufactured with local materials and readily available tools enables this for more of humanity than ever before.
The unique recipe of patterns curated from centuries of ideas in order to enable all this includes:
- Custom designed on-site manufacturing enabled by modern 3d printing technology controls supply chain risks while providing flexibility in sizing, geometry, and the types of framing elements used https://www.thingiverse.com/thing:6244858/files
- Latex cement canvas, thin-shell cement custom coverings using “waste” paint diverted from the landfills https://www.instructables.com/Latex-Concrete-Roof/ & https://www.amazon.com/gp/product/1412039975/ref=as_li_ss_tl
- Japanese Shou Sugi Ban wood burning treatment avoids chemical off-gassing from wood preservatives to create beautiful rot, termite, and fire resistant wood framing elements http://www.ShouSugiBan.com
- Space age ceramic insulative paint additives designed for space shuttle tiles and commonly used to insulate yurts and RVs https://thermoshield.com/ & https://hytechsales.com/thermacels-insulating-additive-bulk
- Applying the thin-shell canvas cement to the flooring, over a typical earthen floor base of gravel and sand, avoids the expense in materials and labor of building a pier & beam deck or pouring a traditional cement slab
- Using re-pelletized Styrofoam as an insulative aggregate in the curtain walls as in-fill between the steel and wood structural elements brings additional sound and weatherproofing to the vertical walls, while diverting more waste from the landfills. https://youtu.be/nwv10Y9GBiQ?si=BJmMCWsKl_u9aFYX
- Mass manufacturing of metal trampolines brings economies of scale and diversion of unused waste from recycling streams delivered with durable, strong, pre-fabricated wall, footing, and perimeter beam framework.
- The simple Igloo shaped framework and lightweight framing/skinning elements creates an infinite variety of grouping together to create additional indoor and outdoor living, working, and playing areas that can grow organically as needs change and evolve, and can easily be modified for cold weather and/or tropical climates, as well as sand, rock, or even flood plain and water top foundations.
The biggest design/build challenges were how to reach the topmost area of the roof to apply the paint, cement, and insulation to weatherproof the canvas as the Gradual Stiffening application enables only limited self-scaffolding, without having to rent expensive lifts or build scaffolding and how to safely and effectively connect the dome hemisphere to the perimeter beam at the top of the trampoline oreo walls.
Leaving the 5 triangular dormer-style clerestory window openings until last made reaching uppermost surfaces possible. Purchasing a 12” compound bevel sliding chop saw allowed use of a 2”x12” shelf as the transition between the steel perimeter beam and the dome hemisphere. The challenge of securing the canvas to the steel framing elements was solved by using roofing screws to attach thin wood strips where needed. Not going with the stain grade finish wood would’ve allowed for use of an airless paint sprayer to lower the labor costs and use of a mortar sprayer will speed up the application of the latex cement mud mixture to the canvas. Use of removable slip forms, can allow for foam-crete wall in-fill to insulate against temperature and sound around the ground floor vertical walls.
The result of this is true Home Ownership, in the form of an ‘idea’ that cannot be taken, doesn’t need to be financed or permitted, and provides sustainable, healthy, living habitats for ourselves, our families and businesses.
BioDome Igloo Feature Stack:
-
- Humanure Nightsoil/Nitrogen Collector
-
- BSFL cultivator
-
- 50 sq ft Grey water wicking bed garden
-
- 50 sq ft Black water wicking bed
-
- 100 sq ft, spiral herb, aquaponics, overflow wicking bed garden
-
- Methane/Nat Gas generating above ground septic bag
-
- Nat Gas stove/H2O Heater
-
- BTC Mining Spaces Heater/Clothes Dryer
-
- Indoor/Outdoor Showers
-
- Kitchen/Bath sinks
-
- Greywater Clothes Washer
-
- BioSand/3-stage/UV Light filter & disinfection
-
- On-demand water pump
-
- ~850 gal rain tanks
-
- Fridge/Freezer
-
- desks/couch/TV/platform bed
-
- 3 ext. doors & 2 int. pocket doors
-
- Solar array, charger, inverter, & batteries
-
- Passive Solar H2O Heater
-
- Indirect lighting & natural ventilation
-
- 17 windows
-
- MgO “cerama-crete”
-
- Rocket Cob Oven
-
- 2 burner cinderblock wood stove
-
- Vermiculture worm chute/bins
-
- 72 sq ft garden porch
-
- 120 sq ft utility courtyard
-
- 200 sq ft ground floor climate controlled space
-
- 64 sq ft 2nd story floor space
-
- 200-500 sq ft rainwater catching roof & awnings
Achieved with modular adaptability, expandability, & scalability, with readily available tools, materials, and skill sets.
BioDome Igloo Function Stack:
- Self-Finance & Self-Build/Maintain shelter for not only ourselves, families, and businesses, BUT, also for our tools, schools, & gardens.
- Sovereign control over the supply chains providing for universal daily needs of ALL the soil/plant/animal/human inhabitants:
- Food cultivation for the entire ecosystem from => worms, flys, fungi, H20/soil bacteria, chickens, tilapia, cats, dogs, & humans
- Water catchment, storage, & treatment for => gardens, fish, & animals
- Shelter for private possessions from => wind, rain, sun, animals, bugs, molds, fire, extreme temps, prying eyes, & sticky fingers
- Fuel for cooking, heating, drying, & charging from => wood, sun, biomass, & natural gas
- Power for electronic appliances/fixtures, AC, BTC mining => sun, wind, nat gas, & potentially, biomass, micro-hydro, and/or hydrogen upgrades.
- Waste management for solids, liquids, & gases from => flush toilets, compost bins, and septic tanks
- Money for labor costs, infrastructure upgrades, and property taxes from => BTC mining, short/mid/long term rental, savings from closed-loop food, power, water, & waste systems
- Empowering Trade Skills enabling immediate ‘Right Livelihood’ through locally offered design/build/maintenance service offerings provided to neighboring communities.
- Scalable Growth designed appropriately, efficiently, and sustainably, built & maintained by those using the infrastructure.

Skill share/shelter seeding in multiple communities through a Vocational Tech Building Blitz
More useful than a fishing pole, providing knowledge on how to manufacture multiple fishing rods, nets, & traps can empower new adopters at scale with a fire of knowledge that cannot be extinguished. Owner designed, built, and maintained small scale shelter can now truly be ‘Owned’ in a way that not only address international chronic housing shortages, while also lowering monthly food costs, 3-6 weeklong Building Blitz onsite intensives create the potential spreading tradecrafts offering right livelihood by providing putting the newly learned trade skills to use for the local community. Small, but beautiful residential housing/food production/resource management in a decentralized, affordable, and communicable form factor is necessary. Providing Pattern Language and Permaculture design strategies, tactics, and skills training on a curated design dictionary, tool, and material stack is only the beginning.
Train a man on how to shelter and feed himself and his family and you offer him the opportunity for reliable right livelihood by exercising those vocational crafts as a service offered to his neighbors in his local marketplace, too. Families, schools, churches, all can organize clustered Biodome Igloo Pattern Stacks to lower their monthly food, energy, and shelter costs.
Craftsmen education through a ‘Building Blitz’ can systemize the training of the crew leaders, who can themselves train more crew and team leads. Offering land owners and craftsmen/women the opportunity to assemble one pre-manufactured kit and build out two new kits to completion over 3-6 weeks depending on the simplicity or complexity of the project. Perhaps, all crew members working together on the 1st Biodome, then 2 teams splitting off to duplicate two more under supervision from scratch, space, budgets, and time allowing, with each team completing two more Biodomes without supervision (providing 5 residential ecosystems in total), in order to earn their Designer/Builder Certification.
Resulting in 3 completed BioDome Igloo Stack ecosystems and up to 3 newly certifiably trained Crew Leaders. Costs will vary greatly depending on local economics, supply chains, and labor markets, but this Invisible Structural Pattern may allow for internationally scalable Vocational Tech training that addresses food, housing, and employment shortages worldwide.
BioDome 5 Special Features lead to 1 Unique Result:
- 3D Printing: Free, open-sourced &/or DIY designed & locally manufactured custom structural brackets
- ASA plastic: mold, bug, UV, high temp, and impact resistant
- PETG plastic: mold, bug, UV, flexible & durable. Potentially, locally upcycled out of plastic bottles, but not as resistant to high temps
- Infinitely customizable and replicable
- Latex Concrete Habitat: Low-cost, adaptable, and effective thin shell cement/canvas/latex paint ‘skinning’ technique 1st developed in the 1970s
- Hard or Flexible as needed, adapting to any shape and multiple materials, with inexpensive tooling or training
- Easily adheres to wood, metal, or plastics with staples, paint, & cement, for both initial construction and ongoing repairs/additions
- Magnesium Oxide MgO Siding: Manufactured Non-toxic, inert, low-temp, paintable ceramic exterior & interior panels
- water, fire, mold, and bug resistant
- 50+ yr life span that adds thermal mass & soundproofing
- Thermoshield Paint: Borosilicate microspheres, a space-age insulative material designed for space shuttle re-entry, available as both an additive and pre-mix roofing/siding/wall paint
- Flexible waterproofing coat providing heat reflection equivilant to R20 insulation with only 1/8” coating
- Non-toxic, inert, ceramic beads available as premixed ‘Thermoshield’ potable roofing paint
- Trampoline ‘Oreo’ Framing:Flipped & stacked trampoline steel perimeter floor and wall beams, as well as load bearing poles
- Improved performance & lower cost by repurposing established steel trampoline mass-machining, packaging, and distribution infrastructure
- Use 1 ½” diameter galvanized steel tubing in low cost manufactured kits available wordwide, providing strength, durability, and light-weight efficiency at scale



‘Permit-less Design’:
The BioDome Igloo Pattern Stack creates a durable, duplicatable, scalable, and transmittable DIY residential design pattern dictionary, integrating abstract philosophical/mathematical ideas adapted from Geodesic Geometry, Bau Biology/Biomimicry/Biophilic design, Cryptography, Austrian Economics, Permaculture, Pattern Language, & Free Open-Source Software, with tangible physical infrastructure
- Built appropriately small & light-weight, with grown factored in, to collect, store, reduce, and reuse energy production and consumption in a macro-organism, a closed-loop intentionally planned, built, and managed living residential ecosystem
- Providing a full-stack, top-to-bottom vertical supply chain for ALL of a self-contained ecosystem’s essential daily needs
- Transforms consumption (i.e. trash) into production (i.e. treasure), accruing sustainable residual surplus capital in multiple form factors, H2O, KwHrs, Bug/Plant/Animal Inhabitants, Nat Gas, Satoshis, & Compute Power
- This idea is stacked on the shoulders of these well-known & unknown intellectual giants, as well as countless peers of the realm:
- Buchminster Fuller- ‘Critical Path’
- Bill Mollison- ‘Permaculture Design Manual’
- Christopher Alexander- ‘Pattern Language Design’
- Dr. Albert Knott & Dr. George Nez- ‘Latex Concrete Habitat’
- E. F. Shumacher- ‘Small Is Beautiful’
- Ayn Rand- ‘The Fountainhead’
- Satoshi Nakamoto- ‘The Bitcoin Whitepaper’
- And many more anonymous & known peers, mentors, and clients…
-
 @ 4520e45a:aa52208a
2025-03-24 20:26:56
@ 4520e45a:aa52208a
2025-03-24 20:26:56👾 Hash Obwohl ein Bitaxe mit 1TH eine Billion Hashes pro Sekunde generiert, werden nicht alle Hashes an den Pool übermittelt — das käme einer Dos-Attacke gleich, würde unnötig Bandbreite verschwenden und den Stratum-Pool-Server massiv belasten.
🏋️ Work-Difficulty Deshalb wird für jeden Worker eine individuelle Work-Difficulty festgelegt. Im Stratum-Protokoll, bekannt als <mining.set_difficulty>. Es werden also nur Shares übermittelt, welche grösser als die festgelegte Work-Difficulty sind.
💡 Um eine Share mit Difficulty 1 zu finden, muss ein Miner erwartungsgemäss 2³² = 4'294'967'296 = 4.29G Hashes generieren.
✉️ Share Wenn ein Hash alle notwendigen Kriterien erfüllt und die Nonce-Difficulty grösser ist als die vom Pool festgelegte Work-Difficulty, wird er als Share dem Pool übermittelt.
⏱️ Bei ckpool wird die Work-Difficulty für einen Worker so angepasst, dass im Durchschnitt 20 Shares pro Minute – also alle 3 Sekunden 1 Share – überliefert wird, das ergibt circa 1200 Shares/Stunde
⏱️ Bei Public Pool wird die Work-Difficulty für einen Worker so angepasst, dass im Durchschnitt 6 Shares pro Minute – also alle 10 Sekunden 1 Share – überliefert wird, das ergibt circa 360 Shares/Stunde
📡 Es geht dabei letztlich um die Kommunikation zwischen Miner und Pool, also konkret, wie oft pro Minute dein Miner Shares an den Pool übermittelt und wieviele Datenpakete gesendet/empfangen/verarbeitet werden müssen.
📈 5-20 Shares pro Minute ergeben auch eine einigermassen aussagekräftige Hashrate, damit stets überprüft werden kann, ob dein Miner korrekt arbeitet.
⛏️ Ob Miner pro Minute 20 Shares mit jeweils einer Nonce-Difficulty von 600 an den Pool übermittelt und Miner pro Minute nur 6 Shares dafür jeweils mit einer Nonce-Difficulty von 2000 an den Pool übermittelt ist am Ende das gleiche.
💪 Beide haben die identische Arbeit geleistet (20×600 = 6×2000 = 12'000×1), nur dass der eine 'viele einfache' und der andere 'wenige schwierige' Shares übermittelt hat.
-
 @ bf95e1a4:ebdcc848
2025-03-24 17:14:48
@ bf95e1a4:ebdcc848
2025-03-24 17:14:48This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Everything A Trade
All human interaction can be defined as trade. Yes, all human interaction. Every time a human being interacts with another, an exchange takes place. In every conversation we have, we exchange information with each other. Even the most trivial information is of some value to the other person. If information didn’t have any value to us, we wouldn’t talk to each other. Either what the other person says is valuable to us, or we find it valuable to give information to them. Oftentimes both. At the core of all human interaction that isn’t violent, both parties perceive that they gain some value from it, otherwise the interaction wouldn’t have taken place at all. Civilizations begin this way — two people finding it valuable to interact with each other. That’s all it takes.
So, what constitutes value? What we find valuable is entirely subjective. A comforting hug, for example, probably has a different value to a two-year-old than it has to a withered army general. Even the most basic action, such as breathing, encapsulates the whole value spectrum. We tend to forget that even a single breath of air can be of immense value to us under the right circumstances. A single breath is worth more than anything on the planet to a desperate free-diver trapped under ice, while worth nothing to a person with a death wish in clean forest air on a sunny summer day. Value is derived from supply and demand, and demand is always subjective. Supply is not.
Since all of our lives are limited by time, time is the ultimate example of a scarce, tradeable resource. We all sell our time. We sell it to others, and we sell it to ourselves. Everyone sells their time, either through a product that took them a certain amount of time to produce, or as a service, and services always take time. If you’re an employee on a steady payroll, you typically sell eight hours of your day, every day, to your employer. If you’re doing something you truly love to do, that eight-hour day still belongs to you, in a way, since you’re doing what you’d probably be doing anyway if you had been forced to do it for free. Sometimes, we sacrifice time in order to acquire something in the future. An education, for instance, gives no immediate reward but can lead to a better-paying, more satisfying job in the future. An investment is basically our future self trading time with our present self at a discount. Once again, every human interaction viewed as trade.
It’s rooted in physics. For every action, there is an equally large reaction. Trade is at the very core of what we are, and the tools we use to conduct trade matter a lot to the outcome of each transaction. Money is our primary tool for expressing value to each other and if the creation of money is somewhat corrupt or unethical, that rot spreads down throughout society, from top to bottom. Shit flows downhill, as the expression goes.
So what is money, or rather, what ought money to be? In order for two persons to interact when a mutual coincidence of needs is absent, a medium of exchange is needed in order to execute a transaction. A mutual coincidence of needs might be “You need my three goats, and I need your cow,” or even “both of us need a hug.” In the absence of a physical good or service suitable for a specific transaction, money can fulfill the role of a medium of exchange. What most people fail to realize is that the value of money, just as the value of everything else, is entirely subjective. You don’t have to spend it. The problem with every incarnation of money that mankind has ever tried is that its value always gets diluted over time due to inflation in various forms. Inflation makes traditional money a bad store of value, and money needs to be a good store of value in order to be a good investment, or in other words, a good substitute for your time and your effort over time. Bitcoin tries to solve this problem by introducing absolute scarcity to the world, a concept that mankind has never encountered before. To comprehend what such a discovery means for the future, one needs to understand the fundamentals of what value is and that we assign a certain value to everything we encounter in life, whether we admit it or not. In short, we assign value to everything we do, value is derived from supply and demand, and supply is objective while demand is subjective.
Free trade emerges out of human interaction naturally and it is not an idea that was forced upon us at any specific point in time. The idea that markets should be regulated and governed, on the other hand, was. Free trade is just the absence of forceful interference in an interaction between two humans by a third party. There’s nothing intrinsically wrong or immoral about an exchange of a good or service. Every objection to this is a byproduct of the current global narrative — a narrative that tells us that the world is divided into different nations and that people in these nations operate under various sets of laws, depending on what jurisdiction they find themselves in. All of these ideas are man-made. No species except humans does this to themselves. Animals do trade, but they don’t do politics.
Bitcoin and the idea of truly sound, absolutely scarce money inevitably make you question human societal structures in general and the nature of money in particular. Once you realize that this Pandora’s box of an idea can’t be closed again by anyone, everything is put into perspective. Once you realize that it is now possible for anyone with a decently sized brain to store any amount of wealth in that brain or to beam wealth anonymously to any other brain in the world without anyone else ever knowing, everything you were ever told about human society is turned on its head. Everything you thought you knew about taxes, social class, capitalism, socialism, economics, or even democracy falls apart like a house of cards in a hurricane. It is, in fact, impossible to comprehend the impact Bitcoin will have on the planet without also understanding basic Austrian economics and what the libertarian worldview stems from.
Imagine growing up in an Amish community. Until your sixteenth birthday, you’re purposely completely shielded off from the outside world. Information about how the world really works is very limited to you since internet access, and even TVs and radios, are forbidden within the community. Well, from a certain perspective, we’re all Amish. How money really works is never emphasized enough through traditional media or public educational institutions. Most people believe that the monetary system is somehow sound and fair when there’s overwhelming evidence to the contrary all over the globe. Ask yourself, do you remember being taught about the origins of money in school? Me neither. I don’t believe that there’s some great, global conspiracy behind the fact that the ethics of money creation isn’t a school subject, but rather that plain old ignorance is to blame for the lack of such a subject primarily. As soon as their math-skill limit is reached, people seem to stop caring about numbers. The difference between a million and a billion seems lost on a depressingly large part of the world's population. In the chapters ahead, we’ll explore the pitfalls of central banking, how money pops into existence, and how inflation keeps us all on a leash.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 57d1a264:69f1fee1
2025-03-24 17:08:06
@ 57d1a264:69f1fee1
2025-03-24 17:08:06Nice podcast with @sbddesign and @ConorOkus about bitcoin payments. https://www.youtube.com/watch?v=GTSqoFKs1cE
In this episode, Conor, Open Source product manager at Spiral & Stephen, Product Designer at Voltage & Co founder of ATL Bitlab join Stephan to discuss the current state of Bitcoin user experience, particularly focusing on payments and the challenges faced by users. They explore the comparison between Bitcoin and physical cash, the Western perspective on Bitcoin payments, and the importance of user experience in facilitating Bitcoin transactions.
They also touch upon various payment protocols like #BOLT11, #LNURL, and #BOLT12, highlighting the need for interoperability and better privacy features in the Bitcoin ecosystem. The discussion also covers resources available for developers and designers to enhance wallet usability and integration.
@StephanLivera Official Podcast Episode: https://stephanlivera.com/646
Takeaways
🔸Bitcoin has excelled as a savings technology. 🔸The payments use case for Bitcoin still needs improvement. 🔸User experience is crucial for Bitcoin adoption. 🔸Comparing Bitcoin to cash highlights privacy concerns. 🔸Western users may not see a payments problem. 🔸Regulatory issues impact Bitcoin payments in the West. 🔸User experience challenges hinder Bitcoin transactions. 🔸Different payment protocols create compatibility issues. 🔸Community collaboration is essential for Bitcoin's future. 🔸Improving interoperability can enhance Bitcoin payments. Wallet compatibility issues can create negative user impressions. 🔸Designers can significantly improve wallet user experience. 🔸Testing compatibility between wallets is essential for user satisfaction. 🔸Tether's integration may boost Bitcoin adoption. 🔸Developers should prioritize payment capabilities before receiving capabilities. 🔸Collaboration between designers and developers can lead to better products. 🔸User experience improvements can be low-hanging fruit for wallet projects. 🔸A global hackathon aims to promote miner decentralization. 🔸Resources like BOLT12 and the Bitcoin Design Guide are valuable for developers. 🔸Engaging with the community can lead to innovative solutions.
Timestamps
(00:00) - Intro (01:10) - What is the current state of Bitcoin usage - Payments or Savings? (04:32) - Comparing Bitcoin with physical cash (07:08) - What is the western perspective on Bitcoin payments? (11:30) - Would people use Bitcoin more with improved UX? (17:05) - Exploring payment protocols: Bolt11, LNURL, Bolt12 & BIP353 (30:14) - Navigating Bitcoin wallet compatibility challenges (34:45) - What is the role of designers in wallet development? (43:13) - Rumble’s integration of Tether & Bitcoin; The impact of Tether on Bitcoin adoption (51:22) - Resources for wallet developers and designers
Links:
• https://x.com/conorokus • https://x.com/StephenDeLorme • https://bolt12.org/ • https://twelve.cash/ • https://bitcoin.design/guide/ • Setting Up Bitcoin Tips for Streamers](/watch?v=IWTpSN8IaLE)
originally posted at https://stacker.news/items/923714
-
 @ 401014b3:59d5476b
2025-03-24 16:34:24
@ 401014b3:59d5476b
2025-03-24 16:34:24Alright, hoops degenerates, it’s March 24, 2025, and we’re deep in the March Madness grinder—Sweet 16 time, baby! The bracket’s a damn battlefield, with Auburn, Michigan, Texas Tech, Arkansas, and Purdue locked in alongside some heavy hitters and sneaky upstarts. We’re breaking down every matchup, throwing out some ballsy picks, and calling the full Elite Eight squads on the road to San Antonio. This ain’t some nerdy chalk fest—let’s get loud, let’s get rowdy, and let’s see who’s got the stones to survive this chaos. Strap in, fam—here we go!
South Region: Auburn’s Warpath or Spartan Magic?
Auburn vs. Michigan
Auburn’s the SEC beast, shredding Creighton 82-70 with Tahaad Pettiford’s bench juice (14 points) and Johni Broome’s paint dominance (22 points, 10 boards). Michigan’s Big Ten scrappers outlasted Texas A&M 91-79—Dusty May’s got ‘em humming with Olivier Nkamhoua’s 18 points. The Tigers are a top-5 offensive team, but Michigan’s been scrappy, winning close games all season. Auburn’s depth and Broome’s interior game (top-10 in blocks) overpower Michigan’s grit—Auburn rolls, 78-71.
Ole Miss vs. Michigan St.
Ole Miss’s Chris Beard-led crew topped Iowa St. 91-78—Sean Pedulla dropped 20, and their top-30 offense is humming. Michigan St. beat New Mexico 71-63—Tom Izzo’s Spartans are battle-tested, with a top-15 defense (per KenPom). Ole Miss can score, but Sparty’s physicality (top-10 in defensive rebounds) and Izzo’s March magic (five Final Fours) shut ‘em down—Michigan St. grinds it, 74-69.
Elite Eight Matchup: Auburn vs. Michigan St.
West Region: Houston’s Clamps or Gators’ Grit?
Houston vs. Purdue
Houston’s D suffocated Gonzaga 81-78—L.J. Cryer dropped 22, and their top-5 defense (forcing 16 turnovers per game) is a nightmare. Purdue crushed San Diego St. 76-62—Braden Smith dished 15 assists, and Fletcher Loyer had 18. Cougars are elite defensively, but Purdue’s size (top-10 in offensive rebounds) and tempo keep it close. Houston’s clamps and Cryer’s clutch shooting (40% from three) edge it—Houston dominates, 70-66.
Florida vs. Maryland
Florida stunned UConn 77-75—Walter Clayton Jr.’s 10 points in a three-minute span sealed it. Maryland’s buzzer-beater over Colorado St. 72-71—Derik Queen’s heroics—got ‘em here. Gators are rolling (SEC tourney champs), but Maryland’s Crab Five (top-20 offense) and Queen’s clutch play (20 PPG in March) keep it tight. Florida’s depth (four starters averaging 12+ PPG) pulls through—Florida wins, 82-78.
Elite Eight Matchup: Houston vs. Florida
Midwest Region: Arkansas’ Chaos or Bama’s Firepower?
Texas Tech vs. Arkansas
Calipari’s Razorbacks punked St. John’s 75-66—DJ Wagner dropped 16, and their depth shone. Texas Tech’s Big 12 muscle crushed Drake 77-64—Darrion Williams had 28. Hogs’ talent (six guys in double figures vs. St. John’s) faces Tech’s balanced attack (top-25 offense). Arkansas’ chaos and Calipari’s March pedigree (four Final Fours) overwhelm—Arkansas storms, 82-77.
BYU vs. Alabama
BYU’s hot streak topped Wisconsin 91-89—Trevor Knell hit six threes, averaging 18.9 PPG in their nine-game win streak. Alabama blitzed Saint Mary’s 86-80—Mark Sears dropped 25. Cougars’ offense (top-10 in three-point shooting) meets Bama’s firepower (top-15 in offensive efficiency). Alabama’s speed and Sears’ scoring (21 PPG) edge it—Alabama wins, 88-84.
Elite Eight Matchup: Arkansas vs. Alabama
East Region: Duke’s Flagg Show or Cats’ Revenge?
Duke vs. Arizona
Flagg’s back—Duke crushed Baylor 89-86, with Flagg dropping 20 and 8. Arizona blitzed Oregon 87-83—Caleb Love had 27. Flagg’s versatility (top-5 defensive efficiency for Duke) faces Love’s scoring (20 PPG in March). Duke’s depth (six guys scoring 10+ vs. Baylor) and Flagg’s two-way play edge it—Duke flexes, 85-76.
Kentucky vs. Tennessee
Kentucky beat Illinois—Mark Pope’s Wildcats are 2-0 against Tennessee this season. Tennessee topped UCLA 72-67—Zakai Zeigler had 18 and 8 assists. Cats’ resilience (top-20 offense) meets Vols’ defense (top-15 efficiency). Kentucky’s Quad 1 wins (12 this season) and Pope’s game plan edge it—Kentucky wins, 82-78.
Elite Eight Matchup: Duke vs. Kentucky
Elite Eight Teams (Full List)
South: Auburn, Michigan St.
West: Houston, Florida
Midwest: Arkansas, Alabama
East: Duke, Kentucky
The Final Buzzer
Sweet 16’s a bloodbath, and the Elite Eight’s set—Auburn, Michigan St., Houston, Florida, Arkansas, Alabama, Duke, and Kentucky are my picks to keep dancing. SEC’s got seven teams in the Sweet 16, blue bloods are flexing, and mid-majors are toast. Hit me on Nostr if you disagree, but this is my March Madness gospel—bracket’s clean, let’s see who survives! Let’s freaking go, degenerates!
-
 @ 000002de:c05780a7
2025-03-24 16:22:48
@ 000002de:c05780a7
2025-03-24 16:22:48Many years ago, in the early 2000s something occurred to me. Neither of the two major political movements in the US actually seek solutions to the issues that divide the people. At the time I thought libertarianism was really libertinism. There is a strain of that in the liberty movement but its far from the core ideal. While I don't call myself a libertarian there was a time when I did. The interesting thing was that I wasn't really "converted". It was more like I started realizing I already agreed with many of their ideals and just had no idea there was a group with which I had so much in common.
When it comes to seeking solutions not much has changed. Both parties and their masses seem to have zero interest in solutions. Only power and exercising it as they see fit. What do I mean by solutions? Well, when you and I want to go eat somewhere we have free choice. I can go to In-n-Out and you can go to McDonald's. Neither of us is forced to spend our cash on food we don't want.
Back in the day I would hear people arguing about various issues and unlike many of my peers I actually wanted to understand both sides. It became clear to me that I could see legit reasons for each side. It wasn't like math. It was largely preference. In my pre-libertarian phase I started to think that the solution when there was some government function that could not be agreed upon, maybe it should be privatized. Then each person could decided to either support it, or not support it. Seemed logical to me at the time. Honestly, it still does.
With USAID, many of the programs that have been cut are far from vital to most people's lives. In some cases the programs are things people find morally wrong. It isn't hard to find government activities that people find morally wrong. I can see no reason why these programs cannot be privately funded. If there is so much opposition to their removal surely this can be done.
It seems to me that this doesn't take a lot of mental energy. If I could come up with this as a young man working a blue collar job surely the high minded intellectuals are capable of doing the same. I am left with this conclusion. They know this and don't care. They want power. They want to tax the people. They want high positions. And for the political figures, they want conflict because that gives them power and helps them raise funds. The incentives are not aligned with solutions. They are aligned with conflict.
originally posted at https://stacker.news/items/923642
-
 @ 7d33ba57:1b82db35
2025-03-24 15:40:17
@ 7d33ba57:1b82db35
2025-03-24 15:40:17Located in the Cabo de Gata-Níjar Natural Park, Agua Amarga is a small, picturesque fishing village on the southeastern coast of Spain. Known for its crystal-clear waters, whitewashed houses, and peaceful atmosphere, this is the perfect spot for a relaxing Mediterranean escape.
🏖️ Top Things to See & Do in Agua Amarga
1️⃣ Playa de Agua Amarga 🏝️
- A beautiful, sandy beach with shallow, turquoise waters.
- Family-friendly with beach bars (chiringuitos) and restaurants nearby.
- Great for swimming, paddleboarding, and sunbathing.
2️⃣ Cala de Enmedio – A Hidden Paradise 🌊
- A secluded cove with soft sand and smooth rock formations.
- Reachable by a 30-minute hike or by kayak.
- One of the most photogenic beaches in Cabo de Gata!
3️⃣ Cala del Plomo 🏞️
- Another pristine, unspoiled cove surrounded by dramatic cliffs.
- Accessible by a short hike or 4x4 vehicle.
- A perfect spot for snorkeling and enjoying nature in peace.
4️⃣ Boat & Kayak Excursions 🚤
- Explore the rugged coastline, caves, and hidden beaches by sea.
- Some tours include stops at Cala de San Pedro, a remote beach with an alternative hippie community.
5️⃣ Hiking & Nature Trails 🌿
- Agua Amarga is surrounded by stunning volcanic landscapes within Cabo de Gata Natural Park.
- The Sendero de la Cala de Enmedio is a scenic hike with breathtaking views.
🍽️ What to Eat in Agua Amarga
- Gambas rojas de Garrucha – Sweet red prawns 🦐
- Arroz caldoso de marisco – A rich, brothy seafood rice dish 🍚🐟
- Pulpo a la brasa – Grilled octopus, a local delicacy 🐙
- Pescado fresco – Fresh fish straight from the sea 🐠
- Tarta de almendra – A delicious almond cake for dessert 🍰
🚗 How to Get to Agua Amarga
🚘 By Car: ~1 hour from Almería via A-7 & AL-5106
🚌 By Bus: Limited services from Almería; renting a car is recommended for flexibility
✈️ By Air: Nearest airport is Almería Airport (LEI), about 50 km away💡 Tips for Visiting Agua Amarga
✅ Best time to visit? Spring & early autumn – warm but not too crowded 🌞
✅ Bring water & snacks if visiting remote beaches – no facilities in hidden coves 🏝️
✅ Rent a kayak or boat for the best way to explore the coastline 🚣♂️
✅ Stay overnight to enjoy the peaceful ambiance after the day-trippers leave 🌅 -
 @ 4259e401:8e20e9a6
2025-03-24 14:27:27
@ 4259e401:8e20e9a6
2025-03-24 14:27:27[MVP: Gigi! How do I lightning prism this?]
If I could send a letter to myself five years ago, this book would be it.
I’m not a Bitcoin expert. I’m not a developer, a coder, or an economist.
I don’t have credentials, connections, or capital.
I’m a blue-collar guy who stumbled into Bitcoin almost exactly four years ago, and like everyone else, I had to wrestle with it to understand it.
Bitcoin is one of the most misunderstood, misrepresented, and misinterpreted ideas of our time - not just because it’s complex, but because its very structure makes it easy to distort.
It’s decentralized and leaderless, which means there’s no single voice to clarify what it is or defend it from misinformation.
That’s a feature, not a bug, but it means that understanding Bitcoin isn’t easy.
It’s a system that doesn’t fit into any of our existing categories. It’s not a company. It’s not a product. It’s not a government.
There’s no marketing department, no headquarters, no CEO.
That makes it uniquely resistant to corruption, but also uniquely vulnerable to disinformation.
Whether through negligence or malice, Bitcoin is constantly misunderstood - by skeptics who think it’s just a Ponzi scheme, by opportunists looking to cash in on the hype, by scammers who use the name to push worthless imitations, and by critics who don’t realize they’re attacking a strawman.
If you’re new to Bitcoin, you have to fight through layers of noise before you can even see the signal.
And that process isn’t instant.
Even if you could explain digital signatures off the top of your head, even if you could hash SHA-256 by hand, even if you had a perfect technical understanding of every moving part - you still wouldn’t get it.
Bitcoin isn’t just technology. It’s a shift in incentives, a challenge to power, an enforcer of sovereignty. It resists censorship.
A simple open ledger - yet it shakes the world.
Archimedes asked for a lever and a place to stand, and he could move the world.
Satoshi gave us both.
The lever is Bitcoin - an economic system with perfect game theory, incorruptible rules, and absolute scarcity.
The place to stand is the open-source, decentralized network, where anyone can verify, participate, and build without permission.
And what comes out of this seemingly simple equation?
The entire rearchitecture of trust. The separation of money and state.
A foundation upon which artificial intelligence must negotiate with the real world instead of manipulating it.
A digital economy where energy, computation, and value flow in perfect symmetry, refining themselves in an endless virtuous cycle.
Bitcoin started as a whitepaper.
Now it’s a lifeline, an immune system, a foundation, a firewall, a torch passed through time.
From such a small set of rules - 21 million divisible units, cryptographic ownership, and a fixed issuance schedule - emerges something unstoppable.
Something vast enough to absorb and constrain the intelligence of machines, to resist the distortions of human greed, to create the rails for a world that is freer, more sovereign, more aligned with truth than anything that came before it.
It’s proof that sometimes, the most profound revolutions begin with the simplest ideas. That’s why this book exists.
Bitcoin isn’t something you learn - it’s something you unlearn first.
You start with assumptions about money, value, and authority that have been baked into you since birth. And then, piece by piece, you chip away at them.
It’s like peeling an onion – it takes time and effort.
*And yes, you might shed some tears! *
At first, you might come for the speculation. A lot of people do. But those who stay - who actually take the time to understand what’s happening - don’t stay for the profits.
They stay for the principles.
If you’re holding this book, you’re somewhere on that journey.
Maybe you’re at the very beginning, trying to separate the signal from the noise.
Maybe you’ve been down the rabbit hole for years, looking for a way to articulate what you already know deep in your bones.
Either way, this is for you.
It’s not a technical manual, and it’s not a sales pitch. It’s the book I wish I had when I started.
So if you’re where I was, consider this a message in a bottle, thrown back through time. A hand reaching through the fog, saying:
“Keep going. It’s worth it.”
Preface The End of The Beginning
March 2025.
The moment has arrived. Most haven’t even noticed, let alone processed it. The United States is setting up a Bitcoin (Bitcoin-only!) strategic reserve.
It’s not a theory. Not an idea. The order is signed, the ink is dried.
The people who have been wrong, over and over (and over!) again - for years! - fumble for explanations, flipping through the wreckage of their previous predictions:
“Bubble…’’ “Fad…” “Ponzi…”
No longer.
The same analysts who once sneered are now adjusting their forecasts to protect what’s left of their credibility. Those who dismissed it are now trapped in a slow, humiliating realization: Bitcoin does not require their approval.
It never did.
Something fundamental has shifted, and the air is thick with a paradoxical cocktail of triumph and panic. Bitcoiners saw this coming. Not because they had insider information, but because they understood first principles when everyone else was still playing pretend.
Bitcoin was never just surviving.
It was infiltrating.
The question is no longer whether Bitcoin will succeed.
It already has.
The only question that remains is who understands, and who is still in denial.
Think back to 2022.
At its peak, FTX was one of the world’s largest cryptocurrency exchanges, valued at $32 billion and backed by blue-chip investors. It promised a sophisticated, institutional-grade trading platform, attracting retail traders, hedge funds, and politicians alike. Sam Bankman-Fried, with his disheveled hair and cargo shorts, was its eccentric figurehead, a billionaire who slept on a bean bag and spoke of philanthropy.
Then the illusion shattered.
FTX collapsed overnight, an implosion so violent it left an entire industry scrambling for cover. One moment, Sam Bankman-Fried was the golden boy of crypto - genius quant, regulatory darling, effective altruist™.
The next, he was just another fraudster in handcuffs.
Billions vanished. Customers locked out. Hedge funds liquidated.
Politicians who had once taken photos with SBF and smiled at his political donations, suddenly pretended they had no idea who he was. The same regulators who were supposed to prevent disasters like this stood slack-jawed, acting as if they hadn’t been having closed-door meetings with FTX months before the collapse.
But FTX wasn’t just a scandal, it was a filter.
If you were Bitcoin-only, with your satoshis in cold storage, you didn’t even flinch. From your perspective, nothing important changed:
A new Bitcoin block still arrived every ten minutes (on average). The supply cap of 21 million bitcoins remained untouched. Ownership was still protected by public/private key cryptography.
You were literally unaffected.
You had already updated your priors:
“If you don’t hold your own keys, you own nothing.” “Bitcoin is not ‘crypto’.” “’Crypto’ is a casino.”
FTX was just another financial fire, another chapter in the never-ending saga of people trusting systems that had already proven themselves untrustworthy.
That moment was a prelude.
The U.S. Bitcoin pivot is the paradigm shift.
The Eukaryotic Revolution Is Upon Us
In biology, abiogenesis is when life emerged from non-life - a fragile, uncertain process where the first microscopic self-replicators struggled to survive against hostile conditions. That was Bitcoin’s early history. It had to fight for its existence, attacked by governments, dismissed by economists, ridiculed by mainstream media.
But it survived.
That era is over. We have entered the Eukaryotic Revolution.
This is the moment in evolutionary history when simple lifeforms evolved into something structurally complex - organisms with nuclei, internal scaffolding, and the ability to form multicellular cooperatives and populate diverse ecosystems. Once this transformation happened, there was no going back. Bitcoin is going through its own Eukaryotic leap.
Once an outsider, dismissed and ridiculed, it is maturing into an integrated, resilient force within the global financial system.
On March 2, 2025, the Trump administration announced a Crypto Strategic Reserve.
At first, it wasn’t just Bitcoin - it included XRP, SOL, and ADA, a desperate attempt to appease the altcoin industry. A political move, not an economic one.
For about five minutes, the broader crypto industry cheered. Then came the pushback.
Bitcoiners called it immediately: mixing Bitcoin with centralized altcoin grifts was like adding lead weights to a life raft.
Institutional players rejected it outright: sovereign reserves need hard assets, not tech company tokens. The government realized, almost immediately, that it had made a mistake.
By March 6, 2025, the pivot was complete.
Strategic Bitcoin reserve confirmed. The President signed an executive order, and legislation has been introduced in the United States House of Representatives.
The U.S. government’s official bitcoin policy: hold, don’t sell. Look for ways to acquire more.
Altcoins relegated to second-tier status, treated as fundamentally separate from and inferior to bitcoin. The government’s official policy: sell, and do not actively accumulate more (ouch!).
“Bitcoin maximalism” – the belief that any cryptocurrency other than bitcoin lies on a spectrum between “bad idea” and outright scam - wasn’t vindicated by debate.
It was vindicated by economic reality.
When the government was forced to choose what belonged in a sovereign reserve, it wasn’t even close. Bitcoin stood alone.
“There is no second best.” -Michael Saylor
Who This Book Is For: The Three Types of Readers
You’re here for a reason.
Maybe you felt something shift.
Maybe you saw the headlines, sensed the undercurrents, or simply couldn’t ignore the growing drumbeat any longer.
Maybe you’ve been here all along, waiting for the world to catch up.
Whatever brought you to this book, one thing is certain: you’re curious enough to learn more.
Bitcoin forces a reevaluation of assumptions - about money, trust, power, and the very foundations of the economic order. How much of that process you’ve already undergone will determine how you read these pages.
1. The Layperson → new, curious, maybe skeptical. Bitcoin probably looks like chaos to you right now. One person says it’s the future. Another says it’s a scam. The price crashes. The price doubles. The news is either breathless excitement or total doom. How the hell are you supposed to figure this out?
If that’s you, welcome.
This book was built for you.
You don’t need to be an economist, a technologist, or a finance geek to understand what’s in these pages. You just need an open mind and the willingness to engage with new ideas - ideas that will, if you follow them far enough, challenge some of your deepest assumptions.
Bitcoin is not an investment. Bitcoin is not a company. Bitcoin is not a stock, a trend, or a passing phase.
Bitcoin is a paradigm shift. And by the time you reach the last page, you won’t need to be convinced of its importance. You’ll see it for yourself.
2. The Student → understand the basics, want to go deeper.
You’ve already stepped through the door.
You’ve realized Bitcoin is more than just digital gold. You understand decentralization, scarcity, censorship resistance… But the deeper you go, the more you realize just how much there is to understand.
3. The Expert → You’ve been in the game for years.
You’ve put in the time.
You don’t need another book telling you Bitcoin will succeed. You already know.
You’re here because you want sharper tools.
Tighter arguments.
A way to shut down nonsense with fewer words, and more force.
Maybe this book will give you a new way to frame an idea you’ve been struggling to convey.
Maybe it will help you refine your messaging and obliterate some lingering doubts in the minds of those around you.
Or maybe this will simply be the book you hand to the next person who asks, “Okay… but what’s the deal with Bitcoin?” so you don’t have to keep explaining it from scratch.
*If you’re already deep in the weeds, you can probably skip Part I (Foundations) without missing much - unless you’re curious about a particular way of putting a particular thing. *
Part II (Resilience) is where things get more interesting. Why you want to run a node, even if you don’t know it yet. The energy debate, stripped of media hysteria. The legend of Satoshi, and what actually matters about it.
If you’re a hardcore cypherpunk who already speaks in block heights and sending Zaps on NOSTR, feel free to jump straight to Part III (The Peaceful Revolution). Chapter 15, “The Separation of Money and State” is where the gloves come off.
Bitcoin isn’t just a technology. Bitcoin isn’t just an economic movement. Bitcoin is a lens.
And once you start looking through it, the world never looks the same again.
This book will teach you what Bitcoin is, as much as it will help you understand why Bitcoiners think the way they do.
It isn’t just something you learn about.
Especially not in one sitting, or from one book.
It’s something you grow to realize.
Regardless of which category you fall into, you’ve already passed the first test.
You’re still reading.
You haven’t dismissed this outright. You haven’t scoffed, rolled your eyes, or walked away. You’re at least curious.
And that’s all it takes.
Curiosity is the only filter that matters.
The rest takes care of itself.
The Essential Role of Memes Memes won the narrative war - it wasn’t textbooks, research papers, or whitepapers that did it. Bitcoin spread the same way evolution spreads successful genes - through replication, variation, and selection. Richard Dawkins coined the term “meme” in The Selfish Gene, describing it as a unit of cultural transmission - behaving much like a gene. Memes replicate, mutate, and spread through culture. Just as natural selection filters out weak genes, memetic selection filters out weak ideas.
But Bitcoin memes weren’t just jokes.
They were premonitions.
The most powerful ideas are often compact, inarguable, and contagious - and Bitcoin’s memes were all three. They cut through complexity like a scalpel, distilling truths into phrases so simple, so undeniable, that they burrowed into the mind and refused to leave.
"Bitcoin fixes this." "Not Your Keys, Not Your Coins." "Number Go Up."
Each of these is more than just a slogan.
They’re memetic payloads, compressed packets of truth that can carry everything you need to understand about Bitcoin in just a few words.
They spread through conversations, through tweets, through shitposts, through relentless repetition.
They bypassed the gatekeepers of financial knowledge, infecting minds before Wall Street even understood what was happening.
And they didn’t just spread.
They reshaped language itself.
Before Bitcoin, the word fiat was a sterile economic term, borrowed from Latin, meaning "by decree." It had no weight, no controversy - just a neutral descriptor for government-issued money.
But Bitcoiners forced a memetic shift.
They didn’t just make fiat mainstream.
**They made it radioactive. **
They stripped away the academic detachment and revealed its true essence:
money because I said so.
No backing. No inherent value.
Just a command.
And of course, an unspoken threat -
"Oh, and by the way, I have a monopoly on violence, so you’d better get on board."
This wasn’t just linguistic evolution; it was a memetic coup.
Bitcoiners took a sterile term and injected it with an unavoidable truth: fiat money exists not because it is chosen, but because it is imposed.
Central banks, governments, and financial institutions now use the term fiat without a second thought.
The meme has done its work.
A word that was once neutral, now carries an implicit critique - a quiet but persistent reminder that there is an alternative.
Bitcoin didn’t just challenge the financial system - it rewired the language we use to describe it.
“Money printer go BRRRRRR" did more damage to the Fed’s reputation than a thousand Austrian economics treatises ever could.
Memes exposed what balance sheets and policy reports tried to obscure. They turned abstract economic forces into something visceral, something undeniable.
And now - they are historical markers of the shift, the fossil record of our collective consciousness coming to terms with something fundamentally new in the universe.
The old world relied on authority, institutional credibility, and narrative control.
Bitcoin broke through with memes, first principles, and lived experience.
This wasn’t just an ideological battle.
It was an evolutionary process.
The weaker ideas died. The strongest ones survived.
Once a meme - in other words, an idea - takes hold, there is nothing - no law, no regulation, no institution, no government - that can stop it.
Bitcoin exists. It simply is.
And it will keep producing blocks, every ten minutes, whether you get it or not.
This book isn’t a trading manual.
It won’t teach you how to time the market, maximize your gains, or set up a wallet.
It’s a carefully curated collection of memes, giving you the prerequisite mental scaffolding to grok the greatest monetary shift in human history.
A shift that has already begun.
The only thing to decide is whether you’re watching from the sidelines or whether you’re part of it.
The rest is up to you.
How This Book Is Structured Bitcoin spreads like an evolutionary force - through memes. Each chapter in this book isn’t just an idea, it’s a memetic payload, designed to install the concepts that make Bitcoin inevitable. The book is broken into three phases:
*I. Foundations *** Memes as Mental Antivirus The first layer cuts through noise and filters out distractions. "Bitcoin Only" is the first test - if you get this one wrong, you waste years chasing ghosts. "Don’t Trust, Verify" rewires how you think about truth. And "Not Your Keys, Not Your Coins"? If you learn it the hard way, it’s already too late.
II. Resilience Memes as Weapons in the Information War Here’s where Bitcoin earns its survival. "Shitcoiners Get REKT" is a law, not an opinion. "Fork Around and Find Out" proves that you don’t change Bitcoin - Bitcoin changes you. "Antifragile, Unstoppable" shows how every attack on Bitcoin has only made it stronger.
III. The Peaceful Revolution ** Memes as Reality Distortion Fields By now, Bitcoin isn’t just an asset - it’s a lens. "Separation of Money and State" isn’t a theory; it’s happening in real time. "Fix the Money, Fix the World" isn’t a slogan; it’s a diagnosis. And "Tick Tock, Next Block"? No matter what happens, Bitcoin keeps producing blocks.
These aren’t just memes. They’re scaffolding for a new way of thinking. Each one embeds deeper until you stop asking if Bitcoin will succeed - because you realize it already has.
Next: Chapter 1: Bitcoin Only. ** For now, it’s a heuristic - an efficient filter that separates signal from noise, with minimal effort.
But by the time you finish this book, it won’t be a heuristic anymore.
It will be something you know.Welcome to the rabbit hole.
-
 @ a7bbc310:fe7b7be3
2025-03-24 13:18:49
@ a7bbc310:fe7b7be3
2025-03-24 13:18:49I’ve been back from Morocco for just over a month and I’ve had some time to reflect. I started writing a day by day of what I did in my trip to Morocco but that was turning out a bit boring. I couldn’t do the trip justice. I thought I’d share some of my observations instead. I’d start by saying I was only there for 5 1/2 days. 5 days in Marrakesh and half day in Essaouira
You can feel the rich culture and history Morocco has such a rich culture and history. Influence of Romans, French, Arab, Berbers, Saharan and Nomadic tribes. You can see it in the architecture, taste it in the food and hear it in the language. The streets of Marrakesh had the smells of spices, perfumes and petrol. There is a synchronised dance between everyone that occupy the streets. People, motorbikes, donkeys, carts, all jostling for position but never seeming to collide into on another.
One thing that didn’t surprise me was the high level of craftsmanship and intricate designs on some of the buildings. I was told by a tour guide that some of the calligraphy could only be understood and read by the person who wrote it.
There seemed to be a sense of community, people stopping in the street to greet each other and say hello. What surprised me about this in Marrakesh most was that it happened in such a busy city. From my experience big cities are places that you go to get lost, ignored and don’t want to be found. Scene at the end of the movie Collateral comes to mind. You know the one where he’s riding on the subway alone after being shot.
A vendor tried to sell me a pendant, a symbol of the Berber tribe that meant ‘free man’. The symbol looks similar to the one for Sats 丰. I declined to purchase since I wasn’t educated enough on the Berbers to rep a symbol.
Couldn’t get over how much stuff there was for sale! And duplications of everything, rugs, shoes , handbags, jackets. Cold mornings and evenings, warm during the day. Everyone dressed like it was winter, even when it for warmer in the afternoon. It was a special trip. I’d definitely go back. Both to visit Marrakesh and other places.
-
 @ 7d33ba57:1b82db35
2025-03-24 09:01:02
@ 7d33ba57:1b82db35
2025-03-24 09:01:02Altea, often called the "Santorini of Spain," is one of the most charming towns on the Costa Blanca. Known for its whitewashed houses, cobbled streets, and breathtaking sea views, this artistic and bohemian town offers a perfect blend of culture, nature, and Mediterranean charm.
🏛️ Top Things to See & Do in Altea
1️⃣ Casco Antiguo (Old Town) 🏡
- Wander through narrow, whitewashed streets, decorated with flower pots and artisan shops.
- Enjoy stunning sea views from various miradores (viewpoints) along the way.
- Stop at Plaza de la Iglesia, the heart of Altea, with its famous blue-domed church.
2️⃣ Iglesia de Nuestra Señora del Consuelo ⛪
- The iconic blue-and-white tiled dome makes it one of the most photographed churches in Spain.
- Offers panoramic views over the Mediterranean and the surrounding mountains.
3️⃣ Altea’s Promenade & Beaches 🌊🏖️
- Walk along the palm-lined seafront, full of cafés and seafood restaurants.
- Relax at Playa de la Roda or Cap Negret Beach, known for its clear waters and smooth pebbles.
4️⃣ Port & Marina Greenwich ⛵
- A beautiful spot for boat trips, sailing, or enjoying seafood with a sea view.
- One of the few marinas in the world located exactly on the Greenwich Meridian (0º longitude).
5️⃣ Serra Gelada Natural Park 🌿
- Hike along the coastal cliffs for breathtaking views of the Mediterranean.
- The Faro de l'Albir (Albir Lighthouse) trail is an easy, scenic walk great for families.
6️⃣ Art & Culture Scene 🎨
- Altea is an artists' town, home to numerous galleries, artisan shops, and cultural events.
- Visit Palau Altea for live music, theater, and exhibitions.
🍽️ What to Eat in Altea
- Arroz a banda – A seafood rice dish similar to paella 🍚🐟
- Calamares a la romana – Crispy fried squid rings 🦑
- Turrón de Alicante – A famous almond nougat 🍯
- Helado artesanal – Traditional homemade ice cream 🍦
- Sangría or local white wine – Perfect with a seaside meal 🍷
🚗 How to Get to Altea
🚘 By Car: ~45 minutes from Alicante via AP-7 highway
🚆 By Train: Take the TRAM from Alicante or Benidorm for a scenic coastal ride 🚉
🚌 By Bus: Regular routes from Alicante, Valencia, and Benidorm💡 Tips for Visiting Altea
✅ Best time to visit? Spring & Autumn (fewer crowds, pleasant weather) 🌞
✅ Wear comfortable shoes – The Old Town streets are steep & cobbled 👟
✅ Sunset at the Mirador Cronistas de España – One of the best viewpoints in town 🌅
✅ Visit on Tuesday for the local market – Great for fresh produce & souvenirs 🛍️ -
 @ da0b9bc3:4e30a4a9
2025-03-24 08:13:00
@ da0b9bc3:4e30a4a9
2025-03-24 08:13:00Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/923278
-
 @ a012dc82:6458a70d
2025-03-24 06:54:13
@ a012dc82:6458a70d
2025-03-24 06:54:13Bitcoin, the original cryptocurrency, has once again captured headlines and investor interest by reaching a new record high, surpassing its previous peak from November 2021. This remarkable resurgence underscores the volatile yet unstoppable journey of Bitcoin, reflecting broader trends in the cryptocurrency market and global finance. Beyond its financial implications, this surge represents a significant cultural and technological milestone, highlighting the increasing integration of digital currencies into mainstream financial systems and the growing public interest in decentralized finance solutions. This article delves into the factors behind Bitcoin's latest surge, its implications, and what the future may hold for this digital asset, considering the complex interplay between market dynamics, technological advancements, and regulatory landscapes.
Table of Contents
-
The New Peak: Bitcoin's Latest Achievement
-
Understanding Bitcoin's Appeal
-
Catalysts for the Recent Surge
-
Institutional Acceptance and ETFs
-
Economic Environment
-
-
Is the Surge Sustainable?
-
Regulatory Landscape and Future Prospects
- Conclusion
- FAQs
The New Peak: Bitcoin's Latest Achievement
After more than two years, Bitcoin has shattered its previous record, climbing to just under $69,000 before stabilizing around $64,000. This surge has propelled Bitcoin's market valuation to approximately $1.3 trillion, representing a significant portion of the total $2.6 trillion cryptocurrency market. This achievement is not just a milestone for Bitcoin but also a testament to the growing acceptance and maturation of cryptocurrencies as a whole. The new peak is a reflection of the enduring faith of long-term investors and the influx of new participants drawn by Bitcoin's proven resilience and potential for substantial returns. This landmark event is not merely about surpassing a numerical threshold but symbolizes the culmination of years of development, debate, and adoption that have expanded the boundaries of what is possible in the realm of digital finance. It prompts a reevaluation of Bitcoin's role not only as a speculative asset but as a foundational component of a new, evolving digital economy.
Understanding Bitcoin's Appeal
Bitcoin's inception in 2008 by the enigmatic Satoshi Nakamoto introduced a revolutionary concept: a digital currency enabling direct transactions without the need for traditional financial institutions. The core innovation of Bitcoin, the blockchain, solved the "double spend" problem inherent to digital currencies, ensuring secure, transparent, and decentralized transactions. This anti-authoritarian stance, combined with the promise of lower transaction fees and resistance to inflation, has fueled Bitcoin's popularity. The appeal of Bitcoin extends beyond its technological underpinnings to embody a broader desire for financial autonomy and privacy. It challenges conventional banking systems and offers an alternative for individuals disillusioned with traditional financial institutions. Bitcoin's decentralized nature appeals to those seeking freedom from governmental oversight and inflationary policies, positioning it as a symbol of financial empowerment and self-sovereignty. As Bitcoin continues to evolve, its appeal broadens, attracting a diverse group of users from libertarians to tech enthusiasts, and from small investors to large institutional players.
Catalysts for the Recent Surge
Several factors have contributed to Bitcoin's recent price explosion:
Institutional Acceptance and ETFs
The approval of Bitcoin exchange-traded funds (ETFs) by the US financial regulator marked a significant step towards institutional acceptance. These ETFs allow investors to gain exposure to Bitcoin without directly purchasing the digital asset, reducing barriers to entry and signaling a new level of market maturity. This development is a clear indication of the growing recognition of Bitcoin's value proposition by mainstream financial entities. It reflects a broader shift in perception among institutional investors, who are increasingly viewing Bitcoin and other cryptocurrencies not just as speculative investments but as legitimate components of diversified portfolios. The introduction of ETFs has facilitated this transition by providing a familiar and regulated framework for investing in Bitcoin, thereby attracting a new wave of institutional capital into the cryptocurrency market.
Economic Environment
The low-interest-rate environment since the 2008 financial crisis has driven investors towards riskier assets, including cryptocurrencies, in search of higher returns. Additionally, Bitcoin is increasingly viewed as an "inflation hedge," similar to gold, appealing to those wary of central bank policies and currency devaluation. The economic landscape has been further complicated by the global pandemic, geopolitical tensions, and supply chain disruptions, leading to increased market volatility and a renewed focus on alternative assets like Bitcoin. As traditional financial systems show signs of strain and governments continue to engage in unprecedented levels of monetary expansion, Bitcoin's fixed supply and decentralized nature offer a compelling alternative for those looking to preserve value and hedge against inflationary pressures.
Is the Surge Sustainable?
While the excitement around Bitcoin's new record is palpable, questions remain about the sustainability of this surge. Historical patterns suggest that parabolic increases in Bitcoin's price are often followed by corrections. Factors such as profit-taking by early investors and the eventual saturation of new buyers could lead to a price consolidation. However, the upcoming "halving" event, which reduces the Bitcoin reward for mining, could counterbalance these pressures by reducing the new supply of Bitcoin and potentially driving up its price. The sustainability of Bitcoin's price surge also hinges on broader market dynamics, including technological advancements, regulatory developments, and shifts in investor sentiment. As Bitcoin becomes more integrated into the global financial system, its price movements are increasingly influenced by a complex interplay of factors, making its future trajectory difficult to predict. Nonetheless, the underlying principles of scarcity, security, and decentralization that underpin Bitcoin provide a strong foundation for its long-term value proposition.
Regulatory Landscape and Future Prospects
The regulatory environment continues to evolve, with increased scrutiny in the UK, EU, and US. While tighter regulations may introduce more stability to the market, they could also restrict some of the freedoms that make cryptocurrencies attractive. Nevertheless, the recent approval of Bitcoin ETFs in the US has been a positive development, potentially paving the way for more regulated crypto assets and attracting a broader base of investors. The future of Bitcoin and the broader cryptocurrency market will be significantly shaped by regulatory decisions, technological innovations, and shifts in global economic conditions. As regulators around the world grapple with the challenges and opportunities presented by cryptocurrencies, the outcome of these deliberations will have far-reaching implications for the adoption, utility, and value of Bitcoin. Despite the uncertainties, the ongoing developments in the regulatory landscape signify a growing recognition of the importance of cryptocurrencies and the need for a balanced approach that ensures security, transparency, and innovation.
Conclusion
Bitcoin's latest record high is more than just a numerical milestone; it represents the ongoing evolution and resilience of the cryptocurrency market. While challenges remain, including regulatory hurdles and market volatility, Bitcoin's journey continues to captivate investors, technologists, and financial analysts alike. As the world becomes increasingly digital, the role of cryptocurrencies like Bitcoin in the global financial ecosystem is likely to grow, making its journey an unstoppable force in the changing landscape of money and investment. The path ahead for Bitcoin is fraught with challenges and opportunities, but its recent achievements underscore its potential to redefine the boundaries of finance, technology, and societal norms. As we look to the future, Bitcoin's journey remains a compelling narrative of innovation, speculation, and the relentless pursuit of a decentralized and empowered financial future.
FAQs
What caused Bitcoin to reach a new record high? Bitcoin's recent surge to a new record high was influenced by several factors, including institutional acceptance, the approval of Bitcoin ETFs, the economic environment fostering a search for inflation hedges, and technological advancements in the cryptocurrency space.
What is a Bitcoin ETF, and why is it important? A Bitcoin ETF (Exchange-Traded Fund) allows investors to gain exposure to Bitcoin's price without owning the actual cryptocurrency. This is important because it provides a regulated and accessible way for institutional and retail investors to invest in Bitcoin, potentially increasing its adoption and market stability.
Can Bitcoin's price surge be sustained? While Bitcoin's price has historically been volatile, factors such as its upcoming halving event, institutional investment, and its role as a perceived inflation hedge may support its value. However, market corrections are common following significant surges, and investor caution is advised.
How do regulatory changes affect Bitcoin's price? Regulatory changes can have significant impacts on Bitcoin's price. Positive regulatory developments, such as the approval of Bitcoin ETFs, can boost investor confidence, while stricter regulations may limit trading or use, potentially affecting the price negatively.
What is the "halving" event, and why is it significant? The "halving" is an event that occurs approximately every four years, where the reward for mining new Bitcoin blocks is halved, effectively reducing the rate at which new Bitcoins are created. This event can lead to increased prices due to reduced supply and increased scarcity.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 502ab02a:a2860397
2025-03-24 04:13:11
@ 502ab02a:a2860397
2025-03-24 04:13:11วันนี้จะมาเล่าเรื่องการทลายและจับกุมเครือข่ายน้ำมันมะกอกปลอม เบื้องหลังการต่อสู้ในโลกของอุตสาหกรรมอาหาร กันครับ
ด้วยความที่ว่าน้ำมันมะกอก Extra Virgin ถูกยกย่องให้เป็นหนึ่งในน้ำมันที่มีคุณภาพสูงและเป็นสัญลักษณ์ของความมีสุขภาพที่ดีทั่วโลก แถมด้วยรสชาติที่ซับซ้อน กลิ่นหอมเฉพาะตัว มาพร้อมคุณค่าทางโภชนาการที่หลากหลาย ไม่ต้องสงสัยเลยว่าทำไมคนทั้งโลกจึงยินดีจ่ายในราคาที่ค่อนข้างสูง
แล้วไอ้ด้วยความต้องการในสินค้าที่มีมูลค่าสูงนี่ละครับ กลายเป็นช่องทางให้กับกลุ่มอาชญากรรมที่มุ่งหวังหากำไรจากการหลอกลวงผู้บริโภค ด้วยการผลิตน้ำมันมะกอกปลอมที่ผ่านการเจือจางหรือดัดแปลงให้ดูเหมือนของแท้ ในเครือข่ายนี้มีการใช้งานเทคนิคและสารเติมแต่งเพื่อเลียนแบบคุณสมบัติของน้ำมันมะกอกแท้ เช่น การปรับเปลี่ยนกลิ่น รสชาติ และคุณสมบัติการแข็งตัวเมื่อแช่เย็น ซึ่งเคยเป็นวิธีตรวจสอบที่ง่ายต่อการแยกแยะของผลิตภัณฑ์แท้ แต่ด้วยเทคนิคใหม่ ๆ ที่ถูกพัฒนาขึ้น ผู้ปลอมแปลงสามารถทำให้ผลิตภัณฑ์ปลอมเหล่านี้ผ่านการตรวจสอบเบื้องต้นได้อย่างไร้ร่องรอย
ข้อมูลจากหลายรายงานของหน่วยงานกำกับดูแลอาหารในยุโรปและสหรัฐอเมริกาเผยว่าขบวนการปลอมแปลงน้ำมันมะกอกเกิดขึ้นในหลายประเทศในแถบเมดิเตอร์เรเนียน โดยเฉพาะในอิตาลี ซึ่งเป็นศูนย์กลางของการผลิตน้ำมันมะกอก
กลุ่มอาชญากรรมในภูมิภาคเหล่านี้ได้นำเอาวิธีการผลิตที่ผิดกฎหมายและการใช้สารเติมแต่งราคาถูกมาเจือจางกับน้ำมันมะกอกแท้ ทำให้ผู้บริโภคไม่สามารถตรวจสอบคุณภาพของผลิตภัณฑ์ได้ด้วยการทดสอบง่าย ๆ เช่น การแช่ตู้เย็นเพื่อตรวจดูการแข็งตัวได้อีกต่อไป (งว่อออ มีอัพเดท patch)
หน่วยงานตำรวจและหน่วยงานกำกับดูแลในอิตาลีร่วมกับหน่วยงานระดับนานาชาติ เช่น EFSA (European Food Safety Authority) และ FDA (Food and Drug Administration) ของสหรัฐอเมริกา ได้ร่วมมือกันเปิดเผยและจับกุมเครือข่ายน้ำมันมะกอกปลอมที่มีความซับซ้อนและขนาดใหญ่ หนึ่งในการจับกุมครั้งใหญ่เกิดขึ้นในปี 2017 เมื่อเจ้าหน้าที่ตำรวจอิตาลีร่วมกับหน่วยงานสอบสวนระดับนานาชาติได้ดำเนินการบุกค้นโรงงานผลิตลับในพื้นที่ชนบทของอิตาลี ที่มีหลักฐานชัดเจนว่ามีการผลิตน้ำมันมะกอกปลอมในปริมาณมหาศาล
เจ้าหน้าที่ได้ค้นพบโกดังที่ถูกซ่อนอยู่ในเขตอุตสาหกรรมที่มีการจัดเก็บถังน้ำมันจำนวนมาก ซึ่งบรรจุผลิตภัณฑ์ที่ถูกเจือจางด้วยน้ำมันพืชราคาถูก เช่น น้ำมันถั่วเหลือง น้ำมันปาล์ม และน้ำมันคาโนลา รวมถึงการเติมสารเคมีที่ช่วยปรับปรุงลักษณะทางกายภาพ เช่น ขี้ผึ้งพืช (Candelilla Wax หรือ Carnauba Wax) เพื่อให้ผลิตภัณฑ์มีคุณสมบัติการแข็งตัวเมื่อนำไปแช่เย็น เหล่านี้เป็นเทคนิคที่ผู้ปลอมแปลงพัฒนาขึ้นเพื่อเลี่ยงการตรวจสอบด้วยวิธีดั้งเดิมที่เคยใช้แยกแยะน้ำมันมะกอกแท้กับปลอมได้
การจับกุมในครั้งนั้นเป็นการร่วมมือระหว่างเจ้าหน้าที่ตำรวจอิตาลีและหน่วยงานสอบสวนของสหภาพยุโรป ที่ได้ใช้เทคโนโลยีการตรวจสอบขั้นสูงและการวิเคราะห์ทางเคมีในห้องปฏิบัติการ เพื่อพิสูจน์ว่าผลิตภัณฑ์ที่ถูกบรรจุในขวดพร้อมฉลากที่หลอกลวงนั้นไม่ได้มีคุณภาพตามมาตรฐานของน้ำมันมะกอก Extra Virgin ขึ้นจริง เจ้าหน้าที่ได้จับกุมผู้ต้องหาและยึดทรัพย์สินในมูลค่าหลายร้อยล้านยูโร จากนั้นคดีนี้ได้ถูกนำเข้าสู่กระบวนการไต่สวนในศาลอิตาลี ซึ่งมีการลงโทษผู้เกี่ยวข้องด้วยโทษจำคุกหลายปีและการปรับเงินจำนวนมหาศาล
ในกระบวนการไต่สวน เจ้าหน้าที่ได้เปิดเผยว่าขบวนการนี้ไม่ได้ดำเนินการโดยบุคคลเพียงไม่กี่คนเท่านั้น แต่เป็นเครือข่ายขนาดใหญ่ที่มีการเชื่อมโยงกับกลุ่มมาเฟียอย่าง Cosa Nostra และ ’Ndrangheta ซึ่งเป็นกลุ่มอาชญากรรมที่มีอิทธิพลทั้งในประเทศและต่างประเทศ กลุ่มเหล่านี้มีบทบาทในการควบคุมการผลิต การจัดจำหน่าย และการขนส่งน้ำมันมะกอกปลอมผ่านเส้นทางลับที่ซับซ้อน ทั้งในรูปแบบของบริษัทหน้ากากและระบบการฟอกเงินที่มีความซับซ้อนสูง
ในปูมหลังของกลุ่มอาชญากรรมที่มีอิทธิพลในอิตาลี อย่างเช่น Cosa Nostra และ ’Ndrangheta เนี่ยครับ ถือเป็นประวัติศาสตร์ที่สลับซับซ้อนและเต็มไปด้วยความรุนแรง ความขัดแย้ง และกลยุทธ์ที่แยบยลในการดำเนินธุรกิจผิดกฎหมายที่กระจายไปทั่วโลก โดยเฉพาะการจับกุมครั้งใหญ่ในวงการปลอมแปลงน้ำมันมะกอกที่เรากำลังพูดถึง
Cosa Nostra หรือที่รู้จักกันในชื่อ “มาเฟียซิซิลี” หรือว่า The Sicilian Mafia ถือเป็นกลุ่มอาชญากรรมที่เก่าแก่ที่สุดและมีชื่อเสียงที่สุดในอิตาลี และมีอิทธิพลอย่างมากในโลกอาชญากรรมระหว่างประเทศ ประวัติของ Cosa Nostra เต็มไปด้วยความรุนแรงและการควบคุมธุรกิจผิดกฎหมายในหลายด้าน ไม่ว่าจะเป็นการค้ามนุษย์ การค้าผิดกฎหมาย และการติดสินบนเจ้าหน้าที่ของรัฐ สิ่งที่ทำให้ Cosa Nostra น่าสะพรึงกลัวคือวิธีการที่พวกเขาควบคุมแหล่งธุรกิจทั้งในอิตาลีและในต่างประเทศด้วยการใช้ความรุนแรงและการหลอกลวง
หนึ่งในคดีที่ทำให้ชื่อเสียงของ Cosa Nostra ติดตรึงในใจผู้คนทั่วโลกคือคดีฆาตกรรม Giovanni Falcone และ Paolo Borsellino ผู้พิพากษาที่ทำงานอย่างหนักเพื่อปราบปรามมาเฟียซิซิลีในช่วงปี 1990 โดยเฉพาะการต่อสู้กับ Cosa Nostra จนกระทั่งทั้งสองถูกลอบสังหารอย่างโหดเหี้ยมในเหตุการณ์ระเบิดที่เกิดขึ้นในปี 1992 การฆาตกรรมนี้ทำให้ผู้คนในอิตาลีและทั่วโลกตระหนักถึงพลังอำนาจและอิทธิพลของ Cosa Nostra ที่สามารถกระทำการรุนแรงได้แม้กระทั่งกับบุคคลในระดับสูง ขอเสริมให้ว่า Giovanni Falcone เป็นผู้พิพากษาและนักสืบที่มีบทบาทสำคัญในการทำลายเครือข่าย Cosa Nostra เขาเป็นผู้นำในการสร้างทีมสอบสวนที่เรียกว่า “Capaci Trial” และการวางแผนปฏิบัติการที่มุ่งหวังจะทำลายการกระทำผิดของมาเฟีย ซึ่งในที่สุดเขาก็เสียชีวิตจากการระเบิดรถยนต์ที่วางกับดักไว้โดยสมาชิก Cosa Nostra ในปี 1992 Paolo Borsellino ก็เป็นผู้พิพากษาที่ทำงานร่วมกับ Falcone ในการต่อสู้กับกลุ่มมาเฟีย Cosa Nostra และมีบทบาทสำคัญในการดำเนินการสอบสวนและพิจารณาคดีที่เกี่ยวข้องกับการกระทำผิดของมาเฟีย แต่เขาก็ถูกสังหารในเหตุการณ์ระเบิดรถยนต์อีกครั้งในปีเดียวกันกับการตายของ Falcone ซึ่งเกิดขึ้นไม่นานหลังจากที่ Falcone ถูกฆ่าตาย
ส่วน ’Ndrangheta ซึ่งมีต้นกำเนิดในแคว้นคาลาเบรีย (Calabria) ในอิตาลี ถือเป็นอีกหนึ่งกลุ่มที่มีอิทธิพลและความน่ากลัวไม่แพ้กัน แม้ว่าในช่วงแรก ’Ndrangheta จะไม่ได้มีชื่อเสียงโด่งดังเท่า Cosa Nostra แต่ในปัจจุบันกลุ่มนี้ถือว่าเป็นหนึ่งในเครือข่ายอาชญากรรมที่ใหญ่ที่สุดในโลก โดยเฉพาะในการควบคุมการค้ายาเสพติดระดับนานาชาติ และการกระทำผิดกฎหมายเกี่ยวกับการฟอกเงิน กลุ่มนี้ไม่ได้จำกัดการดำเนินงานแค่ในอิตาลี แต่ได้กระจายเครือข่ายไปทั่วโลก โดยเฉพาะใน ยุโรป และ อเมริกาเหนือ ซึ่งได้กลายเป็นพลังที่ยากจะหยุดยั้งได้
การทำธุรกิจของ ’Ndrangheta นั้นมีการใช้ความรุนแรงในการรักษาความมั่นคงและการแทรกซึมในระบบเศรษฐกิจ โดยเฉพาะในวงการการก่อสร้างและธุรกิจที่เกี่ยวข้องกับทรัพย์สิน พวกเขามีอิทธิพลอย่างมากในอุตสาหกรรมบางชนิด เช่น การค้ายาเสพติดที่มีมูลค่าสูง ซึ่งการควบคุมและการปราบปรามของพวกเขาทำให้เกิดความตื่นกลัวในทุกภาคส่วน
เคสดังๆ ที่ทำให้ ’Ndrangheta น่าสะพรึงกลัวคือการควบคุมการค้ายาเสพติดในตลาดยุโรป การที่พวกเขามีเครือข่ายกว้างขวางและการเชื่อมโยงกับกลุ่มอาชญากรระหว่างประเทศทำให้พวกเขามีอำนาจในการจัดการและกระจายยาเสพติดได้อย่างไม่มีที่สิ้นสุด อย่างในปี 2007 กลุ่ม ’Ndrangheta ถูกกล่าวหาว่ามีส่วนเกี่ยวข้องในการค้ายาเสพติดโคเคนมูลค่าหลายพันล้านดอลลาร์ โดยพวกเขาสามารถหลีกเลี่ยงการตรวจจับจากหน่วยงานตำรวจได้อย่างเชี่ยวชาญ
แม้การจับกุมครั้งใหญ่ในปี 2017 จะทำให้ขบวนการปลอมแปลงน้ำมันมะกอกในบางส่วนถูกทำลายลง แต่เครือข่ายอาชญากรรมที่เหลือยังคงดำเนินกิจกรรมนี้อยู่ในระดับที่น่ากังวล ผู้บริโภคในหลายประเทศยังคงต้องเผชิญกับผลิตภัณฑ์น้ำมันมะกอกปลอมที่ออกมาจากเครือข่ายเหล่านี้ ซึ่งมักจะมาพร้อมกับความเสี่ยงต่อสุขภาพ เนื่องจากอาจมีการปนเปื้อนสารเคมีอันตรายและการขาดความโปร่งใสในกระบวนการผลิต
Cosa Nostra ยังคงเป็นกลุ่มอาชญากรรมที่มีอิทธิพลมากในซิซิลีและมักจะใช้กลยุทธ์ในการขยายอำนาจผ่านการควบคุมการค้าและอุตสาหกรรมที่มีกำไรสูง การผลิตน้ำมันมะกอกแท้ในซิซิลีเป็นธุรกิจที่มีมูลค่ามหาศาลและเป็นที่นิยมในตลาดทั่วโลก ดังนั้นกลุ่ม Cosa Nostra จึงไม่ได้เพียงแค่ควบคุมการผลิตน้ำมันมะกอกปลอมเท่านั้น แต่ยังควบคุมการขนส่งและการกระจายสินค้าเหล่านี้ไปยังหลายประเทศที่ต้องการผลิตภัณฑ์ปลอมในราคาถูก
กลุ่ม Cosa Nostra ใช้ระบบ “pizzo” หรือการเก็บค่าคุ้มครองจากโรงงานผลิตน้ำมันมะกอกที่ไม่สามารถหลบหนีจากการเรียกเก็บเงินจากพวกเขาได้ รวมถึงการบังคับให้เจ้าของโรงงานผลิตน้ำมันมะกอกต้องซื้อวัตถุดิบที่ไม่ใช่มะกอกจากแหล่งที่พวกเขาควบคุม บางครั้งก็ร่วมมือกับกลุ่มอาชญากรในต่างประเทศ เพื่อให้สามารถขยายตลาดน้ำมันมะกอกปลอมในระดับนานาชาติได้
ขณะที่ Cosa Nostra ครองตลาดในซิซิลี นั้นทางกลุ่ม ’Ndrangheta มีบทบาทในแคว้นคาลาเบรียและมีอิทธิพลในการขยายกิจกรรมการผลิตน้ำมันมะกอกปลอมไปยังตลาดในยุโรปและทั่วโลก โดยเฉพาะในกลุ่มประเทศแถบยุโรปเหนือและอเมริกาเหนือ กลุ่มนี้เป็นหนึ่งในกลุ่มอาชญากรรมที่มีเครือข่ายการกระจายสินค้ามหาศาล รวมถึงน้ำมันมะกอกปลอมที่ไม่ได้รับการตรวจสอบจากผู้บริโภค
การกระจายสินค้าไม่ใช่แค่การจัดส่งน้ำมันมะกอกปลอมไปยังร้านค้าหรือผู้ขายที่ไม่ตรวจสอบ แต่ ‘Ndrangheta ยังมีบทบาทในการสร้างการเชื่อมต่อกับบริษัทส่งออกที่ดูเหมือนจะทำการค้าทั่วไป จนเมื่อการสอบสวนดำเนินไป ก็พบว่าเบื้องหลังของบริษัทเหล่านี้กลับเป็นการขนส่งน้ำมันมะกอกปลอมในปริมาณมหาศาล ขณะเดียวกันก็สร้างแรงกดดันต่อเจ้าหน้าที่และบรรดาผู้ที่พยายามจะเปิดเผยความจริง
ทั้งสองกลุ่มไม่ได้แยกกันไปตามแต่ละเขตแดน แต่พวกเขามักจะร่วมมือกันในการขยายเครือข่ายและหลีกเลี่ยงการถูกจับกุม การรวมตัวระหว่าง Cosa Nostra และ ’Ndrangheta ทำให้เกิดการรวมตัวของอำนาจและความรู้ในการหลบเลี่ยงการตรวจสอบจากเจ้าหน้าที่ ซึ่งทำให้การติดตามและจับกุมยากขึ้น ทั้งนี้เพราะพวกเขามักจะใช้วิธีการที่ซับซ้อนในการบังคับใช้การควบคุมตลาดน้ำมันมะกอกปลอม ซึ่งบางครั้งพวกเขาจะสร้างบริษัทหน้ากากและจดทะเบียนในประเทศที่ไม่มีกฎหมายควบคุมการตรวจสอบอาหารอย่างเคร่งครัด
ทั้ง Cosa Nostra และ ’Ndrangheta จึงเป็นหัวเรือใหญ่ที่ยังคงดำเนินกิจกรรมอาชญากรรมเหล่านี้อยู่ แม้จะมีการจับกุมและเปิดเผยเครือข่ายในบางส่วน แต่เครือข่ายการผลิตน้ำมันมะกอกปลอมยังคงมีความลับอยู่ในที่มืด และอิทธิพลของทั้งสองกลุ่มนี้ก็ยังคงสะท้อนอยู่ในอุตสาหกรรมอาหารทั่วโลก
แม้ว่าจะมีการจับกุมกลุ่มผู้ต้องหาหลายคนในช่วงการบุกค้นครั้งใหญ่ เจ้าหน้าที่ยังคงต้องทำงานหนักเพื่อขยายขอบเขตของการสืบสวน และทำลายเครือข่ายการกระจายสินค้าในระดับนานาชาติที่ทั้งสองกลุ่มควบคุมอยู่อย่างลับๆ แต่ในที่สุดแล้ว การพยายามทำลายอำนาจของ Cosa Nostra และ ’Ndrangheta ในวงการน้ำมันมะกอกปลอมยังคงเป็นการต่อสู้ที่ยาวนานและไม่สิ้นสุดอยู่ดีครับ
หนึ่งในปัญหาที่ผู้บริโภคต้องเผชิญคือ ความยากในการตรวจสอบคุณภาพของน้ำมันมะกอกที่ซื้อมา เนื่องจากการตรวจสอบเบื้องต้นเช่นการแช่ตู้เย็นเพื่อดูการแข็งตัวอาจไม่เพียงพอในการแยกแยะน้ำมันมะกอกแท้กับน้ำมันปลอมที่ผ่านการดัดแปลงด้วยสารเติมแต่งใหม่ ๆ เทคนิคการผลิตที่ซับซ้อนนี้ทำให้ผู้บริโภคต้องพึ่งพาแหล่งข้อมูลที่เชื่อถือได้และการรับรองจากหน่วยงานที่มีอำนาจ
แม้ในปัจจุบันหน่วยงานตำรวจและหน่วยงานกำกับดูแลในยุโรปและสหรัฐอเมริกาจะได้เพิ่มความเข้มงวดในการตรวจสอบและจับกุมขบวนการน้ำมันมะกอกปลอม แต่เครือข่ายขนาดใหญ่ที่มีความลับและการจัดการทางการเงินที่ซับซ้อนยังคงหลบหนีจากการปราบปรามอยู่เป็นอย่างดี ภาพรวมที่พบคือ ผู้ผลิตน้ำมันมะกอกปลอมที่ยังเหลืออยู่ในตลาดมักจะมีการเปลี่ยนแปลงสูตรและเทคนิคอย่างต่อเนื่อง เพื่อให้สามารถหลีกเลี่ยงการตรวจสอบจากห้องปฏิบัติการและการสอบสวนในระดับนานาชาติ
แล้วการจับกุมครั้งใหญ่ในปี 2017 ก็ส่งผลให้เกิดการปรับปรุงมาตรการตรวจสอบในอุตสาหกรรมอาหารและการบังคับใช้กฎหมายในยุโรป แต่ความท้าทายในการจับกุมและทำลายเครือข่ายขนาดใหญ่นี้ยังคงอยู่ เนื่องจากความร่วมมือระหว่างกลุ่มอาชญากรรมทั้งในอิตาลีและต่างประเทศมีความซับซ้อนและเป็นระบบที่ยากต่อการแตกสลาย
ในที่สุด เรื่องราวของการจับกุมขบวนการน้ำมันมะกอกปลอมในยุคนี้จึงเป็นเครื่องเตือนใจให้กับทั้งหน่วยงานกำกับดูแลและผู้บริโภคว่า การตรวจสอบคุณภาพและความโปร่งใสในอุตสาหกรรมอาหารเป็นสิ่งที่ไม่สามารถละเลยได้ และการจับกุมผู้กระทำผิดเพียงส่วนหนึ่งก็ยังไม่เพียงพอที่จะทำให้เครือข่ายอาชญากรรมที่มีอิทธิพลเหล่านี้ถูกทำลายหมดสิ้น ผู้บริโภคจึงควรเลือกซื้อผลิตภัณฑ์จากแหล่งที่เชื่อถือได้และมีการรับรองคุณภาพอย่างเคร่งครัด เพื่อป้องกันไม่ให้ตกเป็นเหยื่อของการหลอกลวงที่อาจมีผลกระทบต่อสุขภาพในระยะยาว
และการเรียนรู้ในการเลือกซื้อก็เป็นเกราะป้องกันขั้นต้นที่สำคัญ ถ้าจะบอกว่าหายาก บ้านเราไม่ค่อยมี เอาแบบง่ายๆในห้างก็ได้มั๊ง
ผมคงบอกได้แค่ เอาตามสะดวกพี่เลยครับ
ผมแค่สื่อสารสุขภาพเออร์ คนนึง
pirateketo
ฉลาก3รู้
ม้วนหางสิลูก #กูต้องรู้มั๊ย #siamstr
-
 @ 4d4fb5ff:1e821f47
2025-03-24 02:03:53
@ 4d4fb5ff:1e821f47
2025-03-24 02:03:53The entire genetic sequence for peptidase E (pepE, e. coli). Genes in living organisms are subject to mutation across time. In contrast, information on the bitcoin ledger is immutable. By etching the pepE DNA sequence onto bitcoin, its ability to evolve is lost. This challenges the significance of genetic information in a foreign digital context. I chose to keep the title “PEPEGENE” in upper case as a homage to the naming convention for Counterparty assets. This additionally contrasts the notation of a digital asset identifier (PEPEGENE) against the notation of biological identifiers (a,t,c or g), which are kept in lower case.
-
 @ a8d1560d:3fec7a08
2025-03-24 01:56:52
@ a8d1560d:3fec7a08
2025-03-24 01:56:52I have created a Nostr desktop-like client with currently 3 apps. However, it is currently read-only and you have to manually refresh the apps to see if there's something new.
https://websim.ai/@wholewish91244492/nostr-desktop/
-
 @ 1f9e547c:8af216ed
2025-03-24 01:46:55
@ 1f9e547c:8af216ed
2025-03-24 01:46:55Opinion about Earn Crypto with Haru Invest (android)
Hugo Hyungsoo Lee is the CEO of Haru Invest, a South Korean cryptocurrency investment platform. In August 2024, during his fraud trial related to the platform's collapse, Lee was attacked and stabbed in the neck by a former investor at the Seoul Southern District Court. The assailant, identified as Kang, had lost approximately $8.3 million due to Haru Invest's bankruptcy. Lee's injuries were not life-threatening, and Kang now faces a potential 10-year prison sentence for the attack.
Source: Jameson Lopp x.com Secondary Source: the block co
WalletScrutiny #nostrOpinion
-
 @ 7bc05901:8c26d22b
2025-03-24 00:48:46
@ 7bc05901:8c26d22b
2025-03-24 00:48:46There was a time in my life where I wouldn't miss church. I remember returning to church, it was directly next door to my downtown apartment. The amount of various substances I consumed every Sunday morning for those first few months back -- I am surprised they let me in the door, reeking as I must have of ganja.
Not only did they let me in the door, they asked me to go back to my apartment and get my guitar so I could join the band -- a keyboardist (the pastor's wife) and another female singer. I strummed along, and before I knew it, I had spent two years at this little church of less than 20 people, and my girlfriend was pregnant. They threw us the absolute best baby shower, just the sweetest people. And after the baby was born, I spent a few more weeks going, then I just realized it has been two years since I have been in there. Except I still have a key, and my guitar still sits on the stage, so I will stop by in the middle of the day sometimes and strum my guitar.
I feel so bad, because I don't know what church is. I worked at "mega" churches throughout my twenties, always directly for the head pastor -- king of his ecclesiastical empire. I had stayed out of church for almost seven years before I went back to this small, intimate affair next to my apartment. It was the only thing that could have gotten me back into it. I couldn't do anything where they are telling you about joining a "small group" (or, they probably call it like a damn "nucleus group" or "cell group" or "base camp" depending on which Zondervan bible study the pastor subscribes to). I couldn't do a glitzy put together, long-haired worship leader and band. With guitar solos. And synthesizers.
I also couldn't do what I grew up with as a kid: baptist hymns, a pipe organ, and shiny white-haired folks in their suits and skirts. And a deep-voiced "Worship Minister" who shouted "HOW GREAT THOU ART" at the pews.
I know that doesn't really encapsulate the spectrum, but those are the only places I can imagine not getting completely hung up on the evangelical legalism that just gushes from church pulpits here in the bible belt. I had enough of a personal radical grace revolution after I was well into my professional church life that the theology is such a hang up basically everywhere / everyone.
I want to start my own church, but I am in an unusual spot where I don't want to sacrifice my entire weekend. I also dread the thought of the business side of the church. Strange, too, because my twenties were spent figuring out how to generate money in a church role, spinning off media projects, connecting to the conference circuit, and compiling sermon series into devotional literature. I also never thought I would shy away from an opportunity to be in that extroverted church environment.
I think churches can be helpful, possibly even life-saving. I think a lot of folks want to turn it around, and want to find a community of positive folks who are willing to face life's difficult questions. And, most importantly, I think folks desperately want to hear that their sins are forgiven, that Christ's blood was spilled for them, that grace is for them. For you.
Unfortunately, I am not there yet. I hope that airing some of this out will create the room in my head for the nudging that needs to help so I can scratch this itch. Maybe find some faith in the principles behind the church, even if I have lost faith in the building and the business.
-
 @ 378562cd:a6fc6773
2025-03-23 23:34:49
@ 378562cd:a6fc6773
2025-03-23 23:34:49In 1976, Logan’s Run presented a futuristic society where hedonism, government control, and the illusion of utopia dictated the lives of its citizens. On the surface, it was a thrilling sci-fi adventure, complete with dazzling special effects and a suspenseful storyline. But beneath the aesthetics of the domed city lay a chilling warning—one that seems eerily prophetic when viewed through the lens of today’s world.
The World of Logan’s Run
Set in the 23rd century (2201-2300), Logan’s Run depicts a civilization where people live under a massive dome, free from hunger, disease, and suffering. However, there’s a catch: when a citizen turns 30, they are forced to participate in “Carousel,” a supposed process of renewal that is, in reality, a government-mandated execution. The system is designed to maintain population control, enforce conformity, and ensure that no one ever challenges the status quo.
Logan 5, the film’s protagonist, is a “Sandman” tasked with hunting down those who try to escape their fate. But when he himself begins questioning the system and searching for the mythical “Sanctuary,” he uncovers the horrifying truth about his world.
Modern Parallels: Are We Living in Logan’s Run?
While we may not have an enforced death age (yet), many aspects of Logan’s Run reflect the realities of today’s society. The film serves as an allegory for the dangers of unchecked government power, mass surveillance, and a culture obsessed with youth and pleasure over wisdom and truth.
- The Cult of Youth and Anti-Aging Obsession
In Logan’s Run, life ends at 30 because youth is worshiped. While we don’t physically eliminate people past a certain age, we see a similar fixation on youth today. The beauty industry, social media influencers, and Hollywood all glorify eternal youth, with people going to extreme lengths—cosmetic surgery, anti-aging treatments, and digital filters—to maintain an illusion of perfection.
- Surveillance and Government Control
Citizens in Logan’s Run are constantly monitored, with the system ensuring no one steps out of line. Sound familiar? Today, we have mass surveillance through smartphones, facial recognition, AI-driven data collection, and social credit systems emerging worldwide. Governments and corporations track movements, preferences, and even conversations, creating a digital panopticon that makes Logan’s world seem less far-fetched.
- Hedonism and Instant Gratification
The film’s society revolves around pleasure, entertainment, and consequence-free living. Today, we have the digital equivalent—hookup culture, endless streaming services, video games, and social media dopamine loops keeping people perpetually distracted from deeper realities. The ease of endless entertainment overshadows the idea of questioning authority or seeking something greater.
- Fear of the Outside World
In Logan’s Run, citizens believe that stepping outside the dome means certain death. Today, many are trapped in their own digital domes, glued to screens, hesitant to unplug, go into nature, or seek real-world experiences. Fear, whether of the unknown or the uncontrollable, keeps people complacent.
- Population Control and Elite Decision-Making
While Carousel is an extreme form of population control, discussions about depopulation, climate policies, and AI-driven automation today suggest that powerful elites are still making decisions about who thrives and who suffers. The concentration of power in the hands of a few is as relevant now as it was in the film.
The Awakening: Will We Choose Freedom?
One of the most striking aspects of Logan’s Run is Logan’s transformation from an enforcer of the system to a rebel seeking truth. His journey mirrors the awakening many people experience today—questioning mainstream narratives, rejecting mass manipulation, and seeking autonomy.
But just as in the film, there are those who refuse to break free. Many continue living inside the “dome,” blindly trusting the system, believing that technology, government, or a new social movement will save them. The question is: Are we more like Logan, daring to seek truth, or the others, content to live in comfortable illusions?
Final Thoughts: Is There a Sanctuary?
In Logan’s Run, Sanctuary represents the hope of a free world beyond the control of the system. Today, people seek their own sanctuaries—homesteading, off-grid living, digital privacy, and independent communities that reject mass conformity.
The film’s message is clear: When a society values comfort over freedom, pleasure over wisdom, and compliance over questioning, it sets the stage for control and deception. But those willing to escape the illusion—just as Logan did—may just find their own Sanctuary.
The question remains: Will we wake up in time?
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-23 19:56:42
@ 5d4b6c8d:8a1c1ee3
2025-03-23 19:56:42I just came in from walking the dog around our neighborhood, which I've been doing barefoot since winter ended. I've always liked walking barefoot.
After my feet got torn up by some sandals that I was wearing on a long backpacking trip, I decided to toughen my feet up, so that wouldn't happen again. For most of the next year, I went barefoot. This was in college, so it was more socially acceptable than it normally would be.
Barefoot walking is excellent for developing the muscles in your feet and lower legs. Shoes are essentially soft casts, after all.
Do any of you like going barefoot?
If so, what do you like about it?
originally posted at https://stacker.news/items/922784
-
 @ 3aaa459b:f67ab822
2025-03-23 19:38:54
@ 3aaa459b:f67ab822
2025-03-23 19:38:54How Do You Use Work Zaps on Nostr?
Nostr is quickly becoming the go-to place for censorship-resistant social networking, and work zaps are emerging as a powerful way to directly reward useful contributions. Whether you're hiring, offering services, or just appreciating good work, work zaps change the game.
So, how do you use work zaps? Vote below and share your thoughts!
Poll Options:
1️⃣ Hiring & Paying for Work – I use zaps to pay people for gigs, content, or tasks.
2️⃣ Earning for My Work – I provide services or create content and get zapped for it.
3️⃣ Tipping & Appreciation – I zap others to encourage great work, but not as payment.
4️⃣ HODLing & Watching – I like the concept but haven't used work zaps yet.Drop a comment with your experience, and let’s see how work zaps are shaping the future of value-for-value payments! ⚡
-
 @ 15125b37:e89877f5
2025-03-23 18:57:20
@ 15125b37:e89877f5
2025-03-23 18:57:20What is Blockchain?
Block by Block:
The Power of Blockchain Unlocked
In its simplest form, a blockchain is a type of digital ledger that records transactions in a secure and transparent way. Imagine a record book that everyone can see, but no one can alter. Each page of the book (called a block) holds a group of transactions, and the pages are linked together in a chain. The blockchain is decentralized, meaning no single person, company, or entity controls it, which makes it different from traditional centralized systems like banks.
Decentralized: No single point of control or authority.
Secure: Uses cryptography to ensure data integrity.
Immutable: Once data is added to the blockchain, it cannot be changed or deleted, providing transparency and security.
How Blockchain Works
Each block on the blockchain contains a batch of transactions. Once a block is full, it’s linked to the previous block, creating a chain of blocks—hence the name blockchain. Each block has three key components:
Transaction data: Information about transactions (e.g., who sent money, who received it, and how much).
Timestamp: The time the block was created.
Hash: A unique identifier for the block, created through cryptographic hashing. Think of a hash like a unique digital fingerprint that is tied to each specific block. And each hash (digital fingerprint) points to the previous block, thereby creating a permanent, unchangeable history of transactions.

Decentralization
One of blockchain's most revolutionary aspects is that it is decentralized. This means there’s no central authority (like a bank or a government) controlling the transactions. Instead, everyone participating in the network has a copy of the blockchain, and transactions are validated by multiple independent users (called nodes).
How It’s Decentralized: Think of it as a large group of people each keeping their own ledger. They work together to validate and record transactions, ensuring no one person can manipulate the system. Of course, this is all done automatically through code that is run on a computer 24 hours a day, 7 days a week. More about that later in this series.
Consensus: For a transaction to be recorded, most of the nodes must agree it’s valid, creating a system of consensus without the need for a trusted central party. This makes blockchain resistant to censorship and fraud.
Security of Blockchain
Blockchain is highly secure due to its use of cryptographic techniques. Every block’s hash (digital fingerprint) is created using the information from within the block plus the hash of the previous block. Thus, the hash of each block is infinitely unique and linked to each other in a chain.
Immutability: If someone tries to change the data in a block, the hash changes. Since every block contains the hash of the previous block, altering one block would require changing all subsequent blocks, which is computationally impossible for a well-maintained blockchain.
Transparency: Blockchain’s decentralized nature means that anyone can see the data, but no one can tamper with it. This ensures trust and transparency in the system.

The Role of Miners/Validators
To add a block to the blockchain, the transactions in the block need to be verified. This is where miners come in. Their job is to check that transactions are valid, and in return, they are rewarded with bitcoin (BTC). This is called Proof-of-Work. Miners compete to solve complex mathematical puzzles. When a miner solves the puzzle (approximately every 10 minutes), they get to add the next block to the blockchain filled with pending transactions, and thereby earn the reward for doing so. They put in the work! Thus, Proof-of-Work.
Why Blockchain is Important
The core value of blockchain lies in its function as a digital ledger. Unlike traditional databases, which are typically controlled by a central authority (such as a bank, a government, or a company), blockchain is a distributed ledger, meaning copies of the same ledger are held across multiple computers (or nodes) around the world on a voluntary basis. This setup creates a system where transactions are recorded in a way that are transparent, trustless, immutable, and decentralized.
Without blockchain, Bitcoin wouldn’t be able to function as a decentralized, peer-to-peer currency. It’s the underlying technology that ensures Bitcoin’s integrity and security.
-
 @ f7d424b5:618c51e8
2025-03-23 18:53:39
@ f7d424b5:618c51e8
2025-03-23 18:53:39A few days ago, on March 20th 2025 one of the most important releases of the year in video games has taken place - Xenoblade Chronicles X! A few other games came out too and we'll talk about those this time while @Dielan@shitposter.world has time to get through the new Xenoblade.
Some links to stuff we talked about:
- EA Open Source & GPL'd C&C
- Lying VAs called out by SC
- PC gamer said something reasonable for once re: asscreed
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ 6bae33c8:607272e8
2025-03-23 17:59:00
@ 6bae33c8:607272e8
2025-03-23 17:59:00After four NFBC teams, I’m done drafting for the season. Below, I’ve made a table of my rosters and noted the players in whom I have multiple shares.
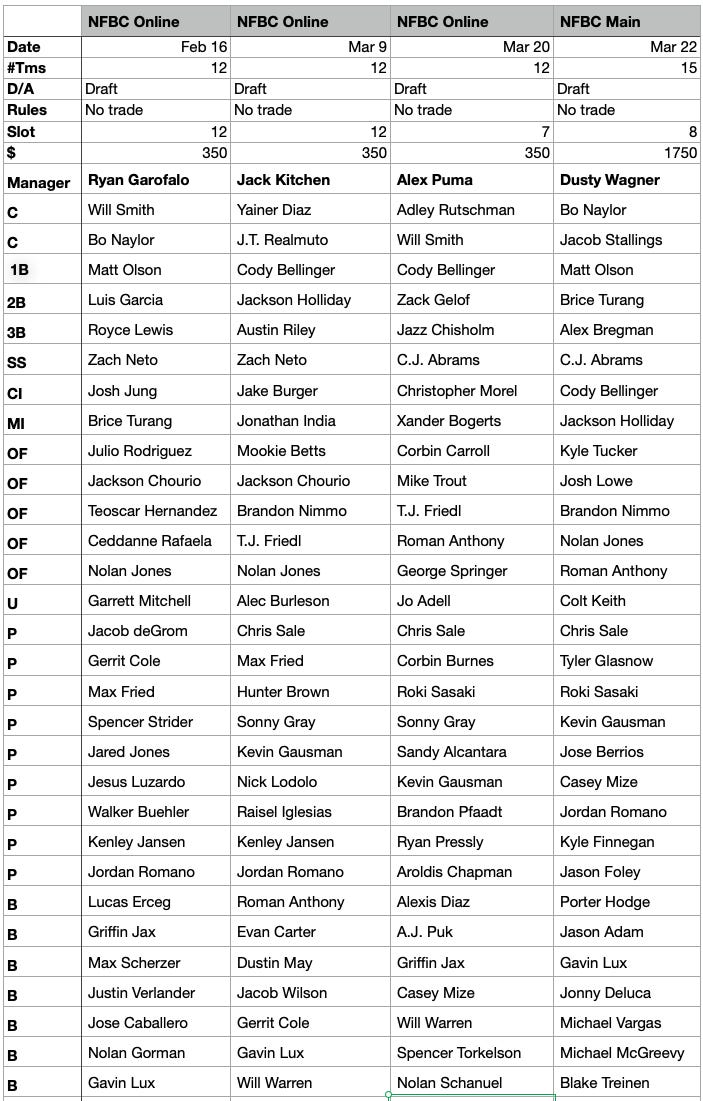
Four shares: None
Three shares: Chris Sale, Cody Bellinger, Kevin Gausman, Jordan Romano, Nolan Jones, Roman Anthony, Gavin Lux
Two shares: Jackson Chourio, Roki Sasaki, Will Smith, Kenley Jansen, Brice Turang, Zach Neto, Jackson Holliday, Brandon Nimmo, Bo Naylor, T.J. Friedl, Casey Mize, Griffin Jax, Will Warren, Gerrit Cole
Zero shares: Shohei Ohtani, Bobby Witt, Aaron Judge, Elly de la Cruz, Jose Ramirez, Juan Soto, Paul Skenes, Francisco Lindor, Tarik Skubal, Vladimir Guerrero, Fernando Tatis, Gunnar Henderson, Zack Wheeler, Yordan Alvarez, Garrett Crochet, Trea Turner, Logan Gilbert, William Contreras, Bryce Harper, Jackson Merrill, Jarren Duran, Wyatt Langford, Oneil Cruz, Ketel Marte, Manny Machado, Freddie Freeman, Mason Miller, Josh Hader, Devin Williams, Emmanuel Clase, Dylan Cease, Ronald Acuna, Blake Snell, Cole Ragans, Michael Harris, Corey Seager, Edwin Diaz, Brent Rooker, Rafael Devers, James Wood, Yoshinobu Yamamoto, Lawrence Butler, Ryan Helsley, Andres Munoz, Spencer Schwellenbach, Framber Valdez, Michael King
Bold = intentional fade
Bold + Italics = hard fade
Write-ups for each league are here: BCL1, BCL2, BCL3 and MAIN.
Links to prior portfolios: 2024, 2023, 2022*, 2021, 2020, 2019, 2018, 2017, 2016, 2015, 2014, 2013, 2012, 2011**
* Sadly lost forever because it was on my now defunct original web site
** including these links not because anyone will click on them, but to show off my meticulous (bordering on OCD) record keeping.After four NFBC teams, I’m done drafting for the season. Below, I’ve made a table of my rosters and noted the players in whom I have multiple shares.
-
 @ 7d33ba57:1b82db35
2025-03-23 17:50:36
@ 7d33ba57:1b82db35
2025-03-23 17:50:36A Coastal Paradise in Costa Blanca
Located between Benidorm, Altea, and L'Alfàs del Pi, Parque Natural de la Serra Gelada is a stunning protected natural park featuring dramatic cliffs, scenic hiking trails, and breathtaking Mediterranean views. This coastal paradise is perfect for hiking, nature walks, and enjoying the wild beauty of Spain’s eastern coast.
🏞️ Top Things to See & Do in Serra Gelada
1️⃣ Hike to the Albir Lighthouse (Faro de l’Albir) 🚶♂️
- An easy, well-paved trail (~5 km round trip) leading to a beautiful white lighthouse with panoramic sea views.
- Along the way, enjoy cliffside scenery, hidden caves, and viewpoints overlooking the Mediterranean.
2️⃣ Serra Gelada Ridge Hike (Benidorm to Albir) 🏔️
- A more challenging but rewarding hike (~8 km one way) that follows the rugged mountain ridges.
- Offers incredible views of Benidorm, Altea Bay, and the towering cliffs plunging into the sea.
3️⃣ Punta del Cavall & Torre Vigía de Punta Bombarda 🏰
- Visit the ancient watchtower ruins, once used to spot pirates.
- One of the best sunset viewpoints in the park.
4️⃣ Boat Trip to Isla de Benidorm ⛵
- Take a boat excursion from Benidorm to this protected island, a paradise for snorkeling and diving.
- The crystal-clear waters are home to colorful marine life and underwater caves.
5️⃣ Coves & Hidden Beaches 🏖️
- Discover secluded beaches like Cala del Tío Ximo and Cala Almadraba, perfect for a quiet escape from Benidorm’s busy beaches.
- Great spots for snorkeling and enjoying nature.
🌿 Flora & Fauna in Serra Gelada
- Home to Mediterranean pine forests, aromatic rosemary, and wild orchids.
- Spot falcons, seagulls, dolphins, and even the occasional wild goat along the cliffs! 🦅🐬
🚗 How to Get to Serra Gelada
🚘 By Car: 15 min from Benidorm, 10 min from Altea, and ~40 min from Alicante
🚌 By Bus: Local buses run from Benidorm to Albir Beach, where many hikes begin
🚶♂️ By Foot/Bike: Many trails start from Albir, Altea, or Benidorm💡 Tips for Visiting Serra Gelada
✅ Best time to visit? Spring & Autumn (cooler weather for hiking) 🌿
✅ Wear good hiking shoes – The ridge trails are rocky and steep in places 👟
✅ Bring water – No facilities along the trails 🌞🥤
✅ For photography lovers – Sunrise & sunset hikes offer the best light 📸 -
 @ 5d4b6c8d:8a1c1ee3
2025-03-23 16:58:33
@ 5d4b6c8d:8a1c1ee3
2025-03-23 16:58:33Let's take a look at how ~HealthAndFitness is doing so far.
Stats since founding
- Revenue: 92k (9th)
- Posts: 531 (7th)
- Comments: 5131 (4th)
- Stacking: 240k (5th)
Ok, ngl, those graphs are a little concerning. Our items and sats are on a steady decline. Still, we aren't far out from profitability and there are only six or seven profitable territories over this period.
What we're doing well is engagement on the posts we do get, almost twice the SN average for comments per post. The daily accountability post from @IamSINGLE has been fairly successful.
My suggestion is that we lower the posting fee, so people are more comfortable sharing their smaller health updates and starting conversations. We aren't attracting the longer form posts that warrant our relatively high fee.
originally posted at https://stacker.news/items/922644
-
 @ a60e79e0:1e0e6813
2025-03-23 16:10:10
@ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much more than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent social media focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share.
This first steps guide showcases one of the most polished and simplest examples of such a client, Primal. Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our Nostr 101 to learn more about Nostr basics and why it matters.
You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.

Getting Started
-
Go to your app store and download Primal to your Android or iPhone
-
Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.
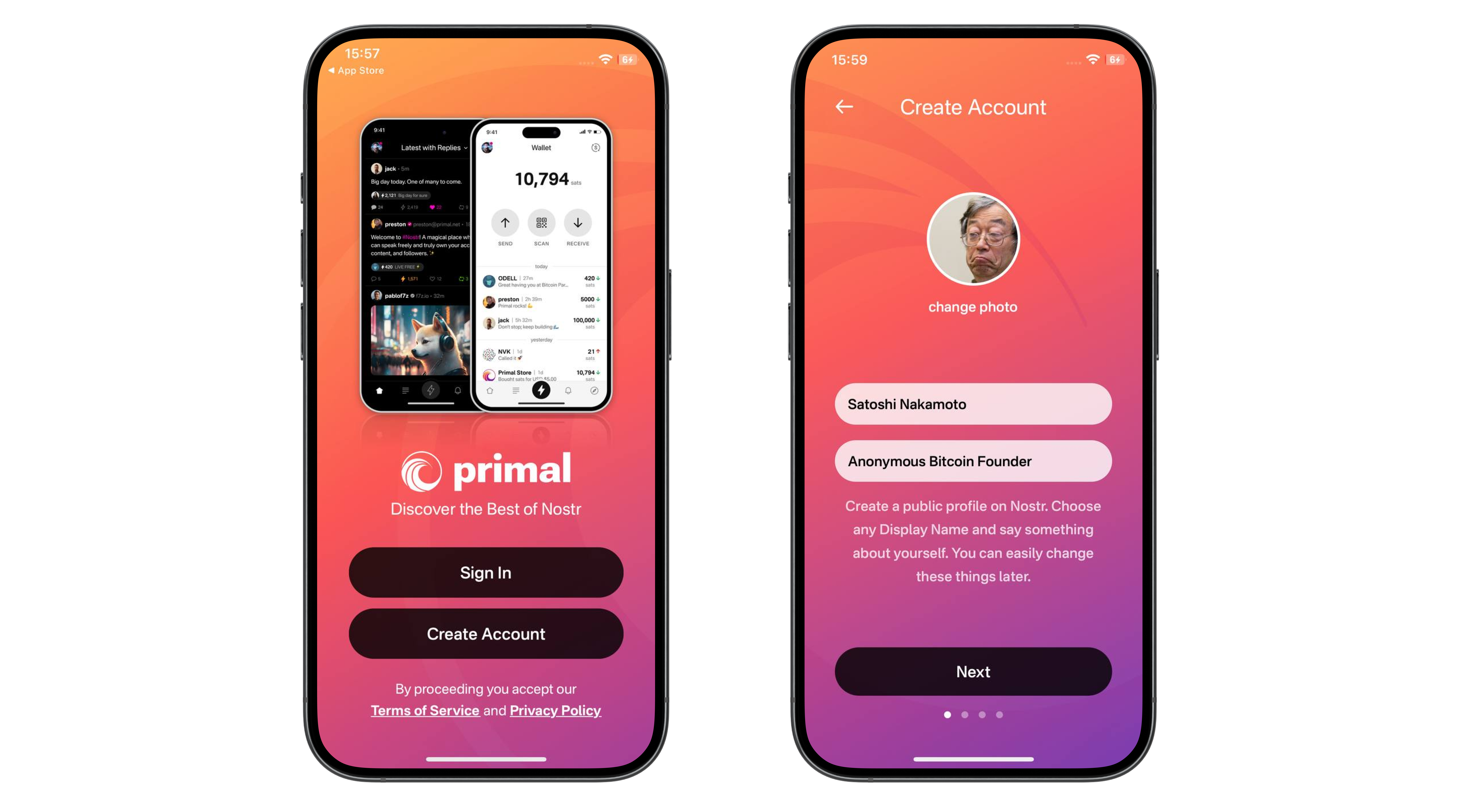
- Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.
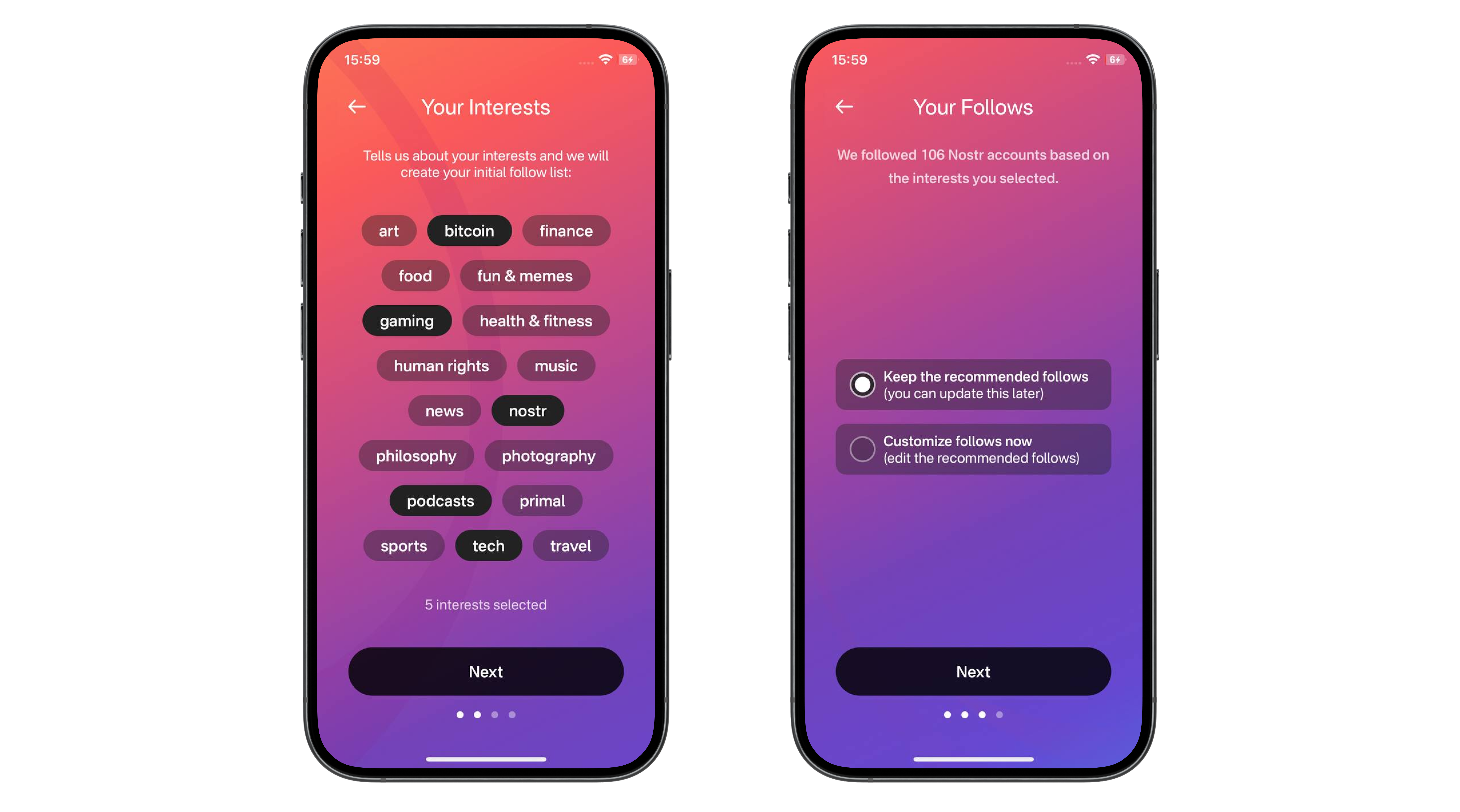
- Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.
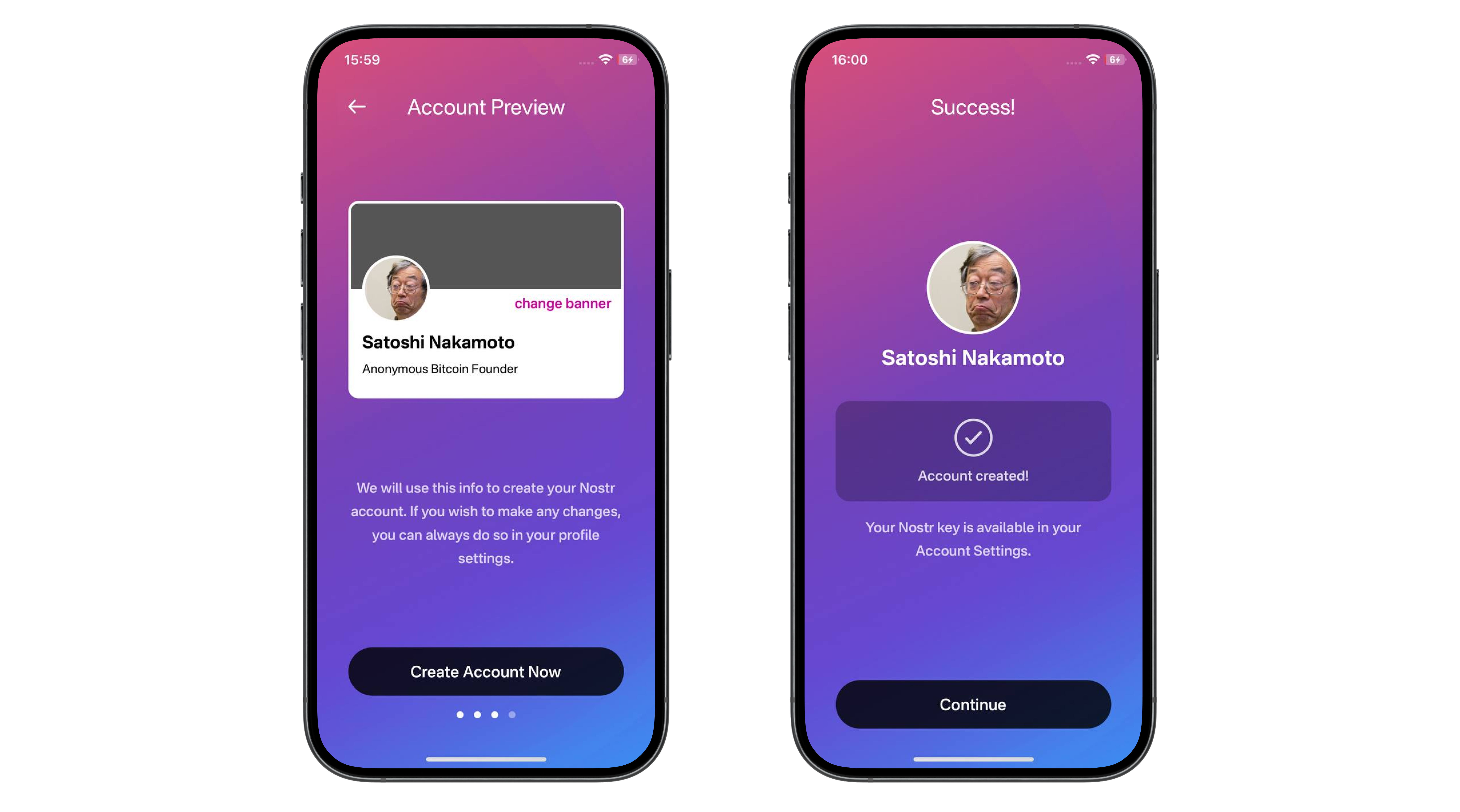
- Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address.
Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think very carefully before carrying out this step.
Learn more in the detailed section at the end of this post.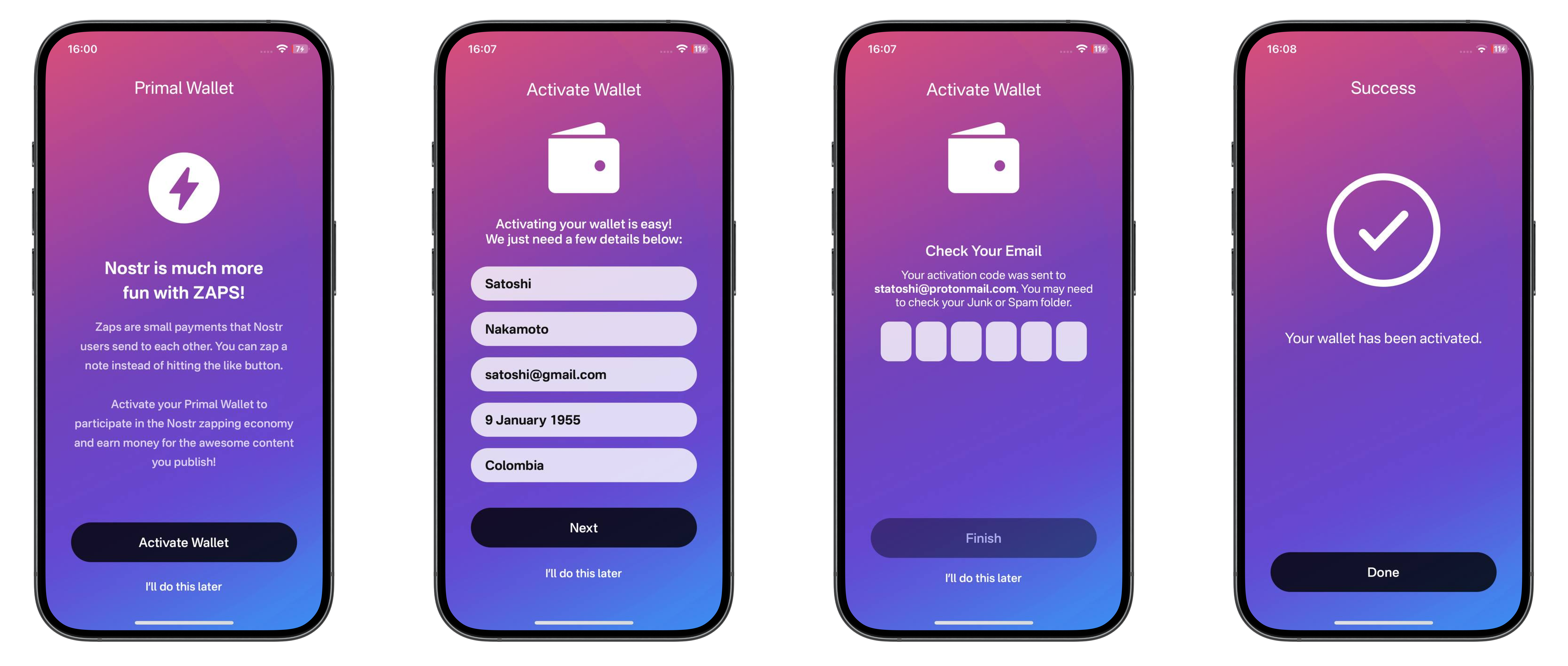
- That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.
- If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this:
- Post some awesome content and have people send you value in the form of 'Zaps'
- Send some Bitcoin from a wallet you already have
- Purchase some directly within Primal
The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.
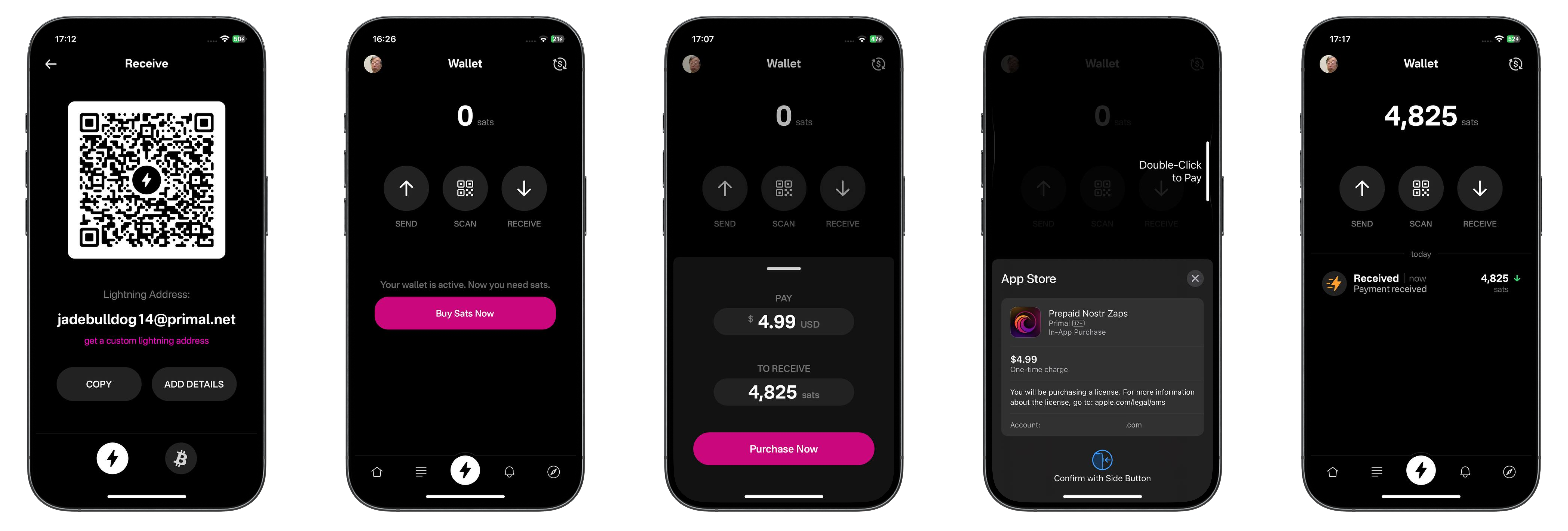
- Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.
- Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.
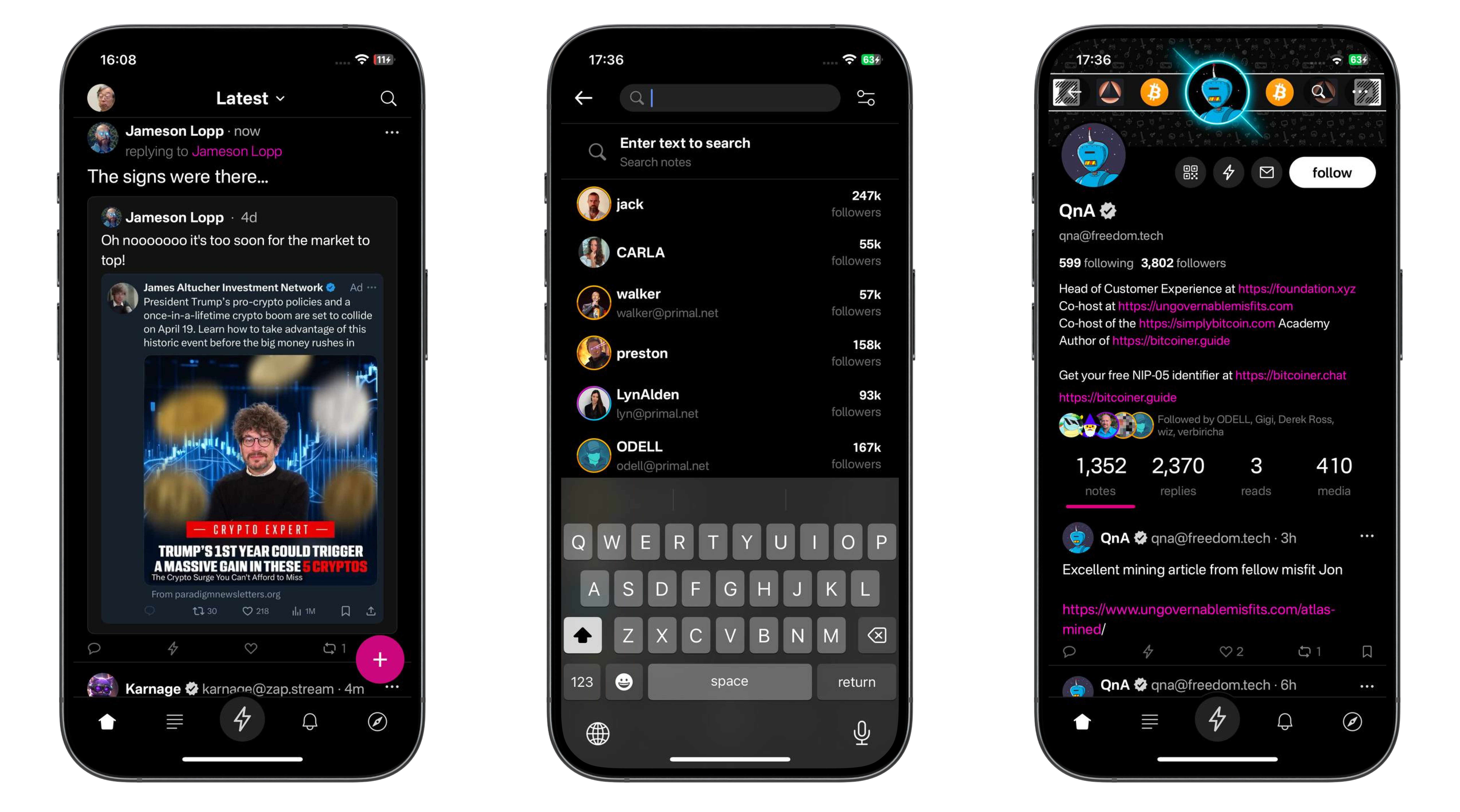
- So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are:
- Comment
- Zap (send value from your wallet to theirs)
- Like
- Repost
- Bookmark
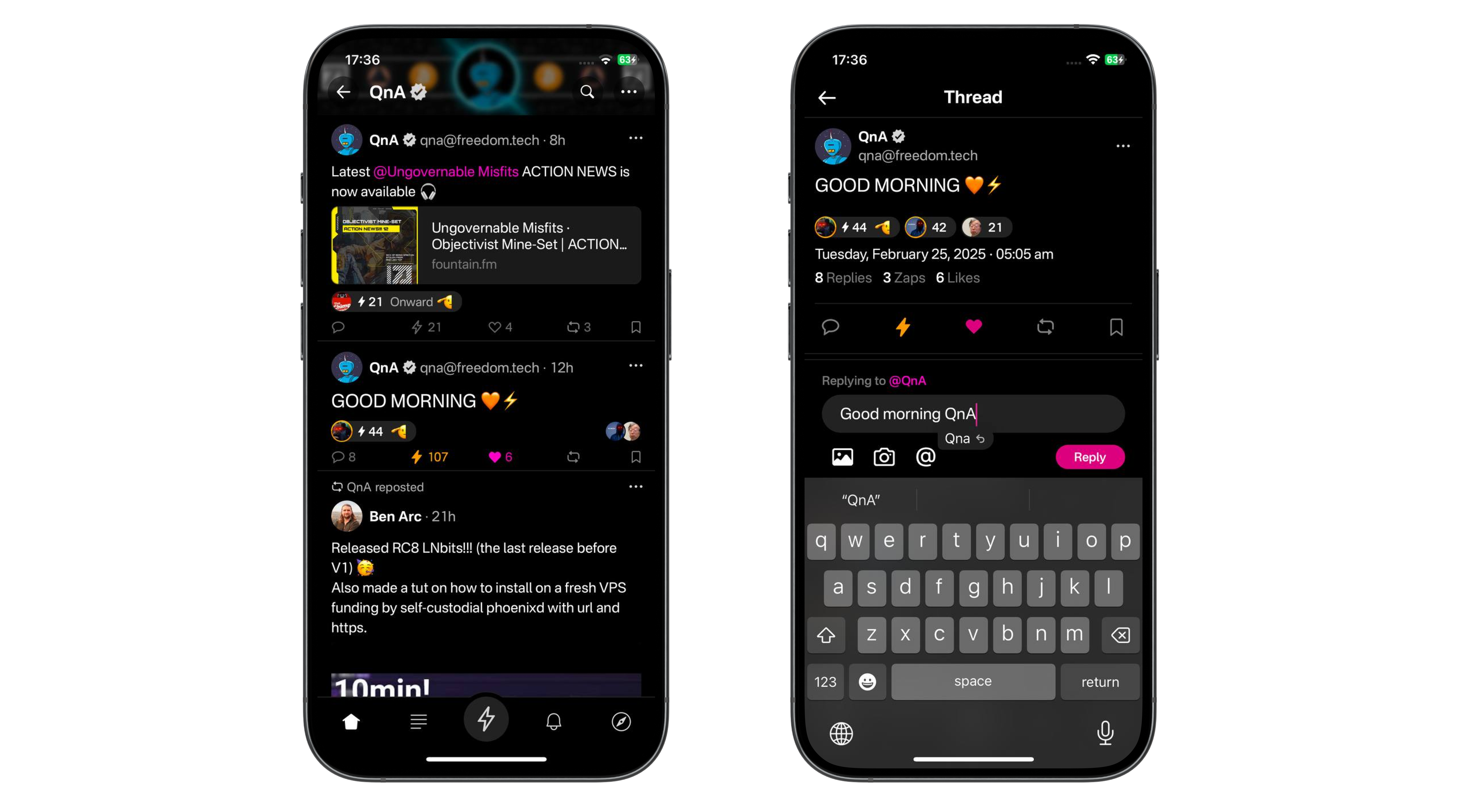
When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.

- After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.
- Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.
The Important Part
You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever?
This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account in any Nostr client. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone!
Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public!
Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.
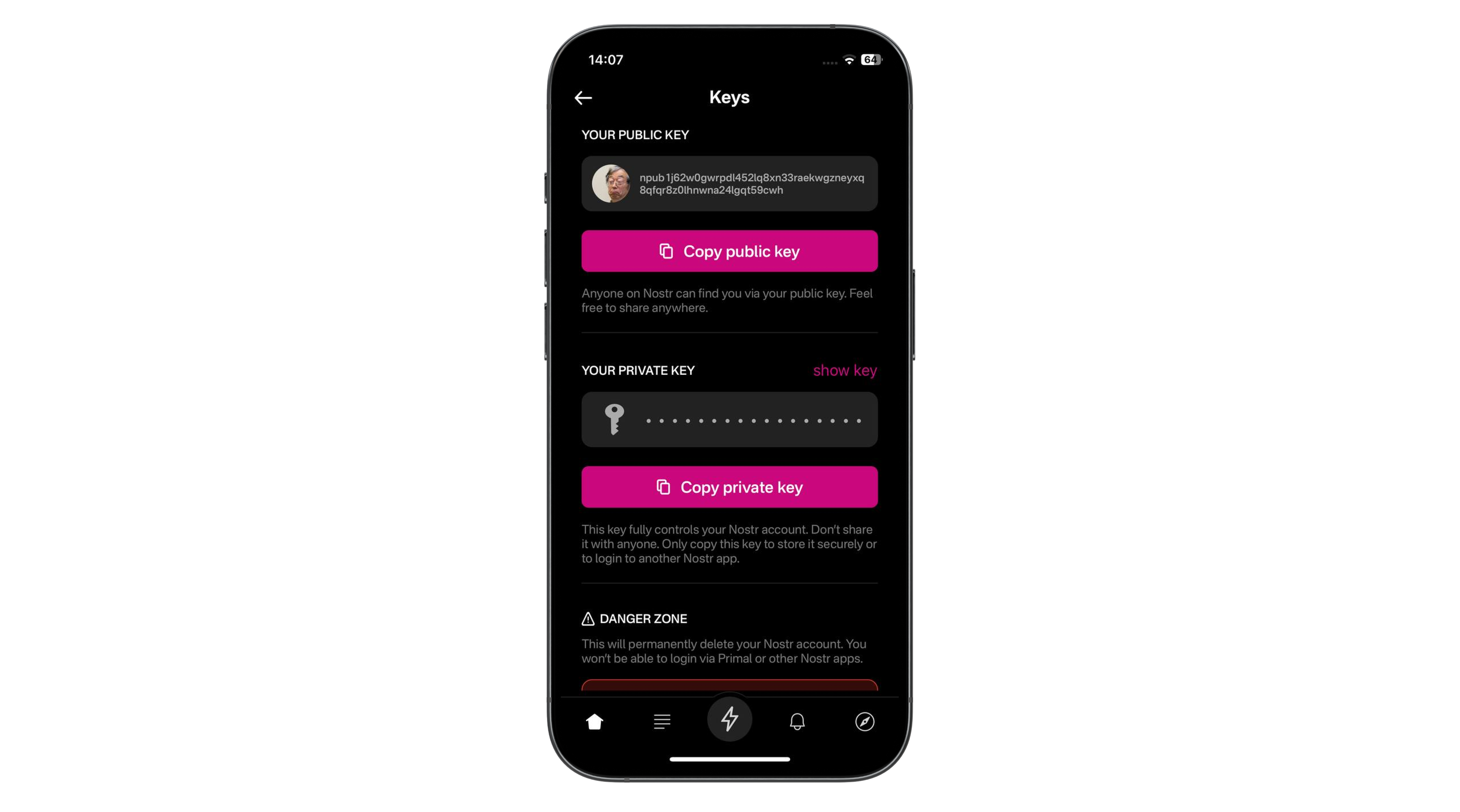
If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored.
Your private key can be imported into any other Nostr social client for the same result.
Things to Consider
This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of.
Custodial Wallet
The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend Phoenix or Zeus.
Those sats are never truly yours until you withdraw them to a self-custodial wallet
Wallet Privacy
If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea.
Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post.
Your private key allows you to take your profile and social network to any other client
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
-
 @ 8d34bd24:414be32b
2025-03-23 14:11:19
@ 8d34bd24:414be32b
2025-03-23 14:11:19Many Believers, after repenting of their sins and trusting Jesus, spend all of their time trying to avoid doing anything bad. Christianity becomes little more than a list of “Don’t Do …”. Of course this isn’t God’s desire. Christianity should be a relationship with our God, Savior, and Creator. It should be a process of becoming more and more like Jesus. This likeness is more about what we do than just what we don’t do.
In order to make this point, I want to do a thought experiment with you.
Think about a large, red, juicy strawberry. Picture it in your mind. Think about what that strawberry feels like in your hand and what it smells like. Picture biting into that strawberry. Feel your teeth sink into the strawberry and the juice run down your throat. Tasty the tangy sweetness in your mouth.
Now try to stop thinking about the strawberry. Don’t let it even flicker through your mind.
Did you succeed at banishing the thought of strawberries in your mind or was a strawberry all you could think about?
Now let’s think about a fresh, hot, crunchy, chewy chocolate chip cookie fresh out of the oven. Think about its smell. Savor it. Think about biting into that chocolate chip cookie. Think about the taste. Feel the still runny, melted chocolate chips.
Are you still thinking about strawberries or did the thought of strawberries completely leave your mind? I’m betting you forgot about the strawberry.
In our Christian walk, the best way to not have ungodly thoughts, is to so fill our mind with godly thoughts that there isn’t room for the ungodly thoughts. The best way to not do sinful things is to be so busy doing God’s work that we don’t have time for the sinful things.
Finally, brothers and sisters, whatever is true, whatever is noble, whatever is right, whatever is pure, whatever is lovely, whatever is admirable—if anything is excellent or praiseworthy—think about such things. Whatever you have learned or received or heard from me, or seen in me—put it into practice. And the God of peace will be with you. (Philippians 4:8-9) {emphasis mine}
If we are constantly reading the Bible, talking to God, and loving our neighbor as we are called to do, we are unlikely to have to work hard avoiding sinful thoughts and sinful actions. If we fill our minds with God’s word, we won’t be dwelling on sinful thoughts. If we are praying continually, we won’t be gossiping or bad mouthing or otherwise dishonoring our Lord with our mouth. If we are loving our neighbors as ourselves, we won’t be envious, stealing, lusting, or wishing harm on others.
Christianity should be more about what you do and less about what you aren’t allowed to do. This only works when we focus on “whatever is pure, whatever is lovely, whatever is admirable,” whatever is “excellent”, and whatever is “praiseworthy.”
Fill your heart, mind, and soul with God and His word and the rest kind of works itself out. I hope this has been helpful.
Trust Jesus
-
 @ 7d33ba57:1b82db35
2025-03-23 14:06:56
@ 7d33ba57:1b82db35
2025-03-23 14:06:56El Rocío is a unique and picturesque Andalusian village famous for its annual pilgrimage, sandy streets, and deep religious traditions. Nestled near Doñana National Park, it feels like a step back in time, with whitewashed houses, horse-drawn carriages, and riders on horseback instead of cars.
🏛️ Top Things to See & Do in El Rocío
1️⃣ Ermita de El Rocío (Sanctuary of Our Lady of El Rocío)
- The heart of the village, home to the Virgen del Rocío, a highly revered statue of the Virgin Mary.
- Every year, millions of pilgrims gather for the Romería del Rocío, Spain’s most famous religious pilgrimage.
2️⃣ Walk the Sandy Streets & Experience the Horse Culture 🐎
- El Rocío has no paved roads—locals and visitors travel on horseback or in traditional wagons.
- Explore the plazas, wooden porches, and stunning white buildings that give the town its Wild West feel.
3️⃣ Attend the Romería del Rocío (If Visiting in May/June) 🎶
- A massive pilgrimage where thousands of devotees travel from all over Spain, dressed in traditional Andalusian attire.
- Experience the flamenco music, singing, dancing, and religious processions that fill the town with energy.
4️⃣ Doñana National Park 🌿
- Just outside El Rocío, this UNESCO biosphere reserve is home to flamingos, wild horses, and the rare Iberian lynx.
- Take a 4x4 safari or guided birdwatching tour to explore the stunning natural landscapes.
5️⃣ Sunset Over La Madre de las Marismas 🌅
- The marshlands near the sanctuary offer breathtaking sunset views with wild birds and horses grazing in the background.
- A perfect spot for photographers and nature lovers.
🍽️ What to Eat in El Rocío
- Gambas de Huelva – Famous white prawns from the nearby coast 🦐
- Choco frito – Fried cuttlefish, a local seafood specialty 🐙
- Venison & wild boar stews – Traditional dishes from the Doñana region 🍖
- Tocino de cielo – A sweet Andalusian dessert similar to flan 🍮
- Manzanilla sherry – A dry, refreshing local wine 🍷
🚆 How to Get to El Rocío
🚗 By Car: 1 hour from Seville, 30 mins from Huelva
🚌 By Bus: Direct routes from Seville and Huelva
🚶♂️ By Pilgrimage: Join the traditional walking or horseback pilgrimage from various Andalusian towns💡 Tips for Visiting El Rocío
✅ Best time to visit? Spring (April–June) for pleasant weather & the famous pilgrimage 🌞
✅ If visiting during Romería del Rocío, book accommodations early! It gets very crowded 📅
✅ Wear comfortable shoes – The sandy streets are best explored on foot or horseback 👟🐎
✅ Stay in a casa rural for an authentic experience of Andalusian hospitality 🏡 -
 @ 57d1a264:69f1fee1
2025-03-23 12:24:46
@ 57d1a264:69f1fee1
2025-03-23 12:24:46https://www.youtube.com/watch?v=obXEnyQ_Veg
source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0
originally posted at https://stacker.news/items/922356
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ da0b9bc3:4e30a4a9
2025-03-23 09:00:12
@ da0b9bc3:4e30a4a9
2025-03-23 09:00:12Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/922244
-
 @ 58537364:705b4b85
2025-03-23 04:09:15
@ 58537364:705b4b85
2025-03-23 04:09:15เราเคยสังเกตไหมว่า...
ทันทีที่ยึดอะไรก็ตามว่าเป็น "ของฉัน" เราจะกลายเป็น "ของมัน" ไปทันที
เราจะยอมทุกข์เพื่อมัน ถ้าใครวิจารณ์เสื้อของฉัน ตำหนิรถของฉัน
เราจะโกรธและจะแก้ต่างให้มัน บางครั้งถึงกับแก้แค้นแทนมันด้วยซ้ำ
ถ้าเงินของฉันถูกขโมย เราจะทุกข์ข้ามวันข้ามคืนทีเดียว
คนจำนวนไม่น้อยยอมตายเพื่อรักษาสร้อยเพชรไว้ไม่ให้ใครกระชากเอาไป
บางคนยอมเสี่ยงชีวิตฝ่าเปลวเพลิงที่กำลังลุกไหม้บ้าน
เพราะกลัวอัญมณีจะถูกทำลายวายวอดฉะนี้แล้ว...
ควรจะเรียกว่ามันเป็น "ของฉัน" หรือฉันต่างหากเป็น "ของมัน" ?
เป็นเพราะหลงคิดว่ามันเป็น "ของฉัน"
ผู้คนทั้งโลกจึงกลายเป็น "ของมัน" ไปโดยไม่รู้ตัว
มีชีวิตอยู่เพื่อมัน ยอมทุกข์ก็เพื่อมันทั้งๆ ที่รู้อยู่ว่ามีเวลาอยู่ในโลกนี้จำกัด
แต่ใช้เวลาไปอย่างไม่เสียดายก็เพื่อมันซ้ำร้ายกว่านั้น...
หลายคนยอมทำชั่ว อกตัญญูต่อผู้มีพระคุณก็เพื่อมัน
กลายเป็นว่าถูกมันใช้ ยิ่งกว่าเป็นผู้ใช้มัน
ยิ่งยึดมั่นว่าทรัพย์สินเป็น "ของฉัน"
เรากลับกลายเป็น ทาสของมัน
จิตใจนี้อุทิศให้มันสถานเดียวเศรษฐีนีเงินกู้คนหนึ่งเป็นโรคอัลไซเมอร์ในวัยชรา
จำลูกหลานไม่ได้แล้ว แต่สิ่งเดียวที่จำได้แม่นก็คือ สมุดจดบันทึกทรัพย์สิน
ทุกวันจะหยิบสมุดเล่มนี้มาพลิกดูไม่รู้เบื่อแม้ลูกหลานจะชวนสวดมนต์หรือฟังเทปธรรมะ
ผู้เฒ่าก็ไม่สนใจ จิตใจนั้นรับรู้ปักตรึงอยู่กับเงินทองเท่านั้นไม่ต้องสงสัยเลยว่า...
เมื่อสิ้นลม ผู้เฒ่าจะนึกถึงอะไร และจะไปสุคติได้หรือไม่
ไม่ว่าจะมีเงินทองมากมายเพียงใด
เมื่อตายไปก็ไม่มีใครเอาไปได้แม้แต่อย่างเดียวนั่นเป็น ข่าวร้าย สำหรับผู้ทุ่มเทชีวิตทั้งชีวิตเพื่อทรัพย์สมบัติ
แต่ที่ร้ายกว่านั้นก็คือ...
หากหวงแหนติดยึดมัน แม้กระทั่งในยามสิ้นลม
มันก็สามารถฉุดลงอบายได้
ถ้า ไม่อยากเป็น "ของมัน"
ก็ควรถอนความสำคัญมั่นหมายว่ามันเป็น "ของฉัน"การให้ทาน เป็นวิธีการเบื้องต้นในการฝึกจิตให้ถอนความสำคัญมั่นหมายดังกล่าว
ถ้าให้ทานอย่างถูกวิธี ไม่เพียงเป็นประโยชน์แก่ผู้รับเท่านั้น
หากเป็นประโยชน์แก่ผู้ให้ด้วย
ประโยชน์ประการหลัง มิได้หมายถึง ความมั่งมีศรีสุขในอนาคต เท่านั้น
ที่สำคัญกว่านั้นก็คือ...
ช่วยลดความยึดติดในทรัพย์ "ของฉัน"แต่อานิสงส์ดังกล่าวจะเกิดขึ้นได้ ต่อเมื่อเราให้โดย ไม่ได้หวังอะไรกลับคืนมา
หากให้เพื่อมุ่งประโยชน์แก่ผู้รับเป็นสำคัญ
ไม่ว่าผู้นั้นจะเป็นพระหรือไม่ก็ตามและเมื่อให้ไปแล้ว ก็ให้ไปเลย
โดยไม่คิดว่าของนั้นยังเป็นของฉันอยู่
การให้ทานและเอื้อเฟื้อเจือจาน
เป็นการสร้างภูมิต้านทานให้แก่จิตใจทำให้ ไม่ทุกข์ เมื่อประสบความสูญเสีย
ในทางตรงข้าม...
คนที่ตระหนี่ แม้จะมีความสุขจากเงินทองที่พอกพูน
แต่หารู้ไม่ว่า จิตใจนั้นพร้อมที่จะถูกกระทบกระแทกในยามเสียทรัพย์
แม้จะเป็นเรื่องที่จำเป็นก็ตาม
ข้อธรรม คำสอน พระไพศาล วิสาโล
โปรดแชร์เป็นธรรมทาน -
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ 6bae33c8:607272e8
2025-03-22 23:12:43
@ 6bae33c8:607272e8
2025-03-22 23:12:43I was supposed to do my Main Event next week, but Heather scheduled a trip to Spain for us I had forgotten about, so I moved it to today, which meant I had to cram a bit.
I drew the seven slot. Results are below:
 Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.
Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.1.8 Kyle Tucker — I like Tucker in a new park, playing for a big contract. He’s fully healthy after an injury-shortened 2024, so he should be fresh. Had Team 7 taken Tucker instead of Juan Soto, I would have taken Jackson Chourio.
2.8 Chris Sale — I thought I might get Jazz Chisholm here, and my fallback was Trea Turner. But earlier in the day I decided I’d probably take Sale anyway as pitching gets scarce quickly in the 15-team and often gets pushed up as a result. But I hadn’t really locked it in, even though I felt Sale would make for an easier build. Then Chisholm and Turner went ahead of me on consecutive picks, and my choice was made for me.
3.8 Matt Olson — I was worried about this pick. This was in the elite closer range, and I didn’t want to go that route, so it was either Manny Machado (gone), Olson or dropping down for someone like Michael Harris about whom I’m only lukewarm. I took Olson who has a good shot of 40-100-100 in that lineup.
4.8 C.J. Abrams — The stat nerds hate him, but he could steal 40 bases, and he was raking before slumping in the second half last year. Tucker gave me some bags, but I really wanted a big-time steals source to pair with him.
5.8 Tyler Glasnow — My favorite fifth-round starter, Glasnow managed134 innings last year. A similar giant lefty, Randy Johnson, was also injury prone early in his career and took a while to get going too.
6.8 Cody Bellinger — I was dead set on Bellinger who is raking this spring. He’ll get the short porch in Yankee stadium and qualifies at first and OF.
7.8 Roki Sasaki — This was the first pick I really had to think about. There was a run of five straight pitchers ahead of me, three of whom I would have taken instead (Logan Webb, Max Fried, Hunter Brown.) I like buying the dip on Sasaki after a shaky outing in Japan, but I also considered pivoting to Mike Trout. In the end, I felt there were more hitters I liked afterward, so I went Sasaki, and then Trout went with the very next pick. In fact the next guy snap-called it, if I recall correctly.
8.8 Alex Bregman — I wanted a share after reading how well he’s hit at Fenway during his career (if Grok is correct, 1.240 OPS in 21 games.) Plus he might eventually gain 2B eligibility if Rafael Devers gets healthy enough to play third. And he should get a lot of RBI hitting third behind Devers and Jarren Duran.
9.8 Josh Lowe — I really wanted to get a share of Lowe after reading about how the minor league home park will boost power for lefties. The steals are a given if he’s healthy, but 20-25 HR would make him a huge bargain in Round 9.
10.8 Jordan Romano — The Lowe pick cost me Kenley Jansen, which I thought it might, so I pivoted to the other exprienced closer I like in that range, and Romano’s on a better team.
11.8 Kevin Gausman — I thought about Aroldis Chapman here, but starters were getting scarce, so I gambled he’d make it back and took Gausman. Gausman is coming off a down year, but he’s healthy, and he knows how to pitch.
12.8 Brandon Finnegan — I missed out on Chapman, it turns out, but Finnegan, who had 38 saves last year and was re-signed, was my backup plan. He’s not especially good, but saves are saves.
13.8 Brice Turang — I really didn’t need speed that badly, but Turang fell like 50 spots below ADP, and I did need a second baseman. His defense keeps him in the lineup, and I’ll take 30-plus steals in case one of my other speed guys doesn’t pan out.
14.8 Brandon Nimmo — I got snaked on Walker Buehler (and Jesus Luzardo two picks before that), so I went with Nimmo for his ability to score runs.
15.8 Jackson Holliday — After a lot of safe picks, I felt like gambling on a top prospect finally. He’s hitting well this spring too.
16.8 Jose Berrios — This just seemed like the right pick, a boring veteran who knows how to pitch and get you innings without killing you. With Glasnow and Sasaki, I needed more of a horse type.
17.8 Nolan Jones — He was scratched from the game today right after I made this, so we’ll see. Hopefully it’s something minor. His 2023 season was fetching a top-five-round ADP last year.
18.8 Casey Mize — Pitching was really flying, and Mize is a former top prospect with an opportunity.
19.8 Bo Naylor — I needed a catcher, and he is one. I like that he runs a bit, and last year’s batting average I’ll chalk up to variance.
20.8 Roman Anthony — I don’t know whether he’ll make the team out of camp, but he’s an elite prospect with little left to prove in the minors.
21.8 Jason Foley — I have two shaky closers, so I wanted to throw another potential one in the mix.
22.8 Porter Hodge — Another saves option if Ryan Pressly falls apart.
23.8 Colt Keith — Keith wasn’t horrendous as as rookie, and moving to first base will give him extra eligibility soon.
24.8 Jason Adam — Another potential source of saves with Robert Suarez looking awfully shaky this spring.
25.8 Gavin Lux — A former top prospect, getting regular at-bats in the league’s second best hitter’s park and picking up more eligibility.
26.8 Jonny Deluca — I needed outfield depth in case Anthony doesn’t start the year in the majors, and Deluca should play in that bandbox minor league park.
27.8 Miguel Vargas — A former top prospect with dual position eligibility should get his chance for regular low-pressure at-bats in Chicago.
28.8 Michael McGreevy — I needed another SP, and he’s one. Also has good control and pitches in a good park. Having a great spring too.
29.8 Jacob Stallings — I played chicken at second catcher all draft, got burned a few times, but Stallings is the starter for now in Colorado.
30.8 Blake Treinen — The Stallings pick cost me a gamble on Jared Jones’ elbow, so I took Treinen who’s an elite reliever who could fill in if starters have bad matchups.
Roster By Position
C Bo Naylor/Jacob Stallings
1B Matt Olson
2B Brice Turang
3B Alex Bregman
SS C.J. Abrams
CI Cody Bellinger
MI Jackson Holliday
OF Kyle Tucker/Josh Lowe/Brandon Nimmo/Nolan Jones/Roman Anthony
UT Colt Keith
SP Chris Sale/Tyler Glasnow/Roki Sasaki/Kevin Gausman/Jose Berrios/Casey Mize
RP Jordan Romano/Brandon Finnegan/Jason Foley
B Porter Hodge/Jason Adam/Gavin Lux/Jonny Deluca/Miguel Vargas/Michael McGreevy/Blake Treinen
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-22 22:49:27
@ 5d4b6c8d:8a1c1ee3
2025-03-22 22:49:27Time for another check-in. - Comments: 3k (2nd place) - Posts: 286 (5th place) - Stacking: 192k (2nd place) - Top post: https://stacker.news/items/920931/r/Undisciplined
Our comment growth was really impressive. Over 10 comments per post is more than double the Stacker News average. The territory really seems to be thriving on contests and discussion threads. That gives us a pretty clear direction to build on.
Shout out to @SimpleStacker for developing the territory analytics graphs!
originally posted at https://stacker.news/items/922027
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-22 19:13:10
@ 5d4b6c8d:8a1c1ee3
2025-03-22 19:13:10I posted about our new dog about a week ago.
The first thing my daughter did was start telling the new dog all about our dog who died a little over a year ago. It was very touching.
Then she was doing such a good job being gentle and quiet to avoid scaring the new dog, who was extremely timid for the first couple of days. Clearly, she wanted to be loud and wild and play, but the dog wasn't ready, so she very gently told the dog about how she gets scared sometimes and listed off some of the things she gets scared of and explained that she'd help the dog not be scared. What a kid!
The next thing to work on is getting them both to sleep in her room. The bed's getting a bit crowded.
originally posted at https://stacker.news/items/921811
-
 @ 5c8a5765:4fc5edee
2025-03-22 18:38:23
@ 5c8a5765:4fc5edee
2025-03-22 18:38:23[Читать в IPFS]
Итак, детки-котлетки, сегодня мы поговорим, как ~~не~~правильно распространять агиацию. Возьмите свои любимые антифашистские стикеры и используйте этот текст как инструкцию к ним — иначе у меня голова лопнет от того, что я вижу на улицах.
Агитация
Для начала определитесь, чем вы занимаетесь: агитируете к чему-то или поддерживаете чего-то, потому что это предполагает совершенно разные подходы. Агитацией может быть призыв к анархизму, классовой борьбе, неуплате налогов, гендерному равенству и т.д. Поддержкой может быть поддержка анархической борьбы, антифашистский идей и т.д. Первое — "вербует"/приманивает новых людей к идее, второе поддерживает только тех, кто уже знаком с идеей и уже с ней согласен.
Как должна выглядеть агитация? Представьте, что некий неонацист решил за-агитировать вас в неонацизм (с учетом, что сейчас вы его не поддерживаете): в каком случае у него больше всего на это шансов? Если вы заметите на мусорном баке наклейку "бей жыдоф"? Или если вам, например, выдадут в руки грамотный агитационный текст? Поставьте себя на место читающего: агитация должна выглядеть именно так, как мог бы выглядеть материал, который хоть немного мог бы поменять ваши текущие взгляды. А именно...
1. Агитация доступна
Она не висит на задней стороне мусорки. Она не нарисована на заброшке. Обыватель не рассматривает мусорки и не ходит по заброшкам. Чтобы масса увидела вашу агитацию, она должна висеть в заметном месте.
Ещё лучше, если она висит там, где человек по внешним причинам на мгновение задерживается, и имеет время проглядеть вашу агитацию: ибо обыватель никогда не остановится у столба посреди длинной тропы, чтобы прочесть стикер.
И учтите: если место, которое вы выбрали, уже забито стикерами, вашему придётся делить привлеченное внимание с каждым остальным.
К доступности стоит также отнести то, что агитация более значительна, если она написана на самом популярном в вашей стране языке, развешивается в разных локациях (чтобы люди разного класса могли её увидеть), если вы развешиваете в туалетах — то туалетах разного гендера (и не забывайте про инвалидные кабинки!), так далее.
Лучшие места для стикеров: лифт, автобусная остановка, метро, поручен эскалатора, внешняя сторона дверцы туалета, чистое (не разрисованное или расклеенное) зеркало.Лучшие места для крупных агитационных листов или графитти: указанные выше, а также — заметные места подъездов,Лучшие места для "визиток"*: оставлять под задницей на выходе из автобуса, метро, маршрутки, на стульях, скамейках и т.д.*"Визитка" — это са-а-амый простой метод агитации: выводите нужный текст или картинки мелкими блоками на листе А4, нарезаете бумагу на кусочки "визиток" с небольшим текстом, картинкой или ссылкой, и оставляете где попало.
2. Агитация запоминается
Если вы не неонацист, какие эмоции в вас побуждает "бей жыдоф"? Вы возжелали стать неонацистом? Или это только укрепило ваши антифашистские взгляды? Или это для вас вообще никак не прозвучало?
Также для ваших противников и обывателей звучат ваши "ешь богатых!", "классовая борьба сегодня!!", "доёш онархию!!!". Это — поддержка. Уже-анархисты будут рады увидеть, что в городе есть левые активисты кроме них самих. Но это никого не переубедит и не привлечет.
А агитация привлекает. Агитация задаёт острые вопросы, которые остаются в голове. Агитация манит предложениями нового. Агитация нестереотипно предлагает.
Примеры хорошей агитации:

"Если большинство проголосует за то, чтобы ты спрыгнул(а) с вмоста, ты бы сделал(а) это? / - Может быть — если это было честным голосованием!"

"Этот телефон прослушивается - согласно законодательству США, телефонные разговоры прослушиваются без ордера или уведомленияю"

"Вы под наблюдением — текст, объясняющий тезис, и ссылка, где можно прочесть об этом подробнее."
Примеры никудышной агитации (но хорошей поддержки):



3. Агитация даёт возможность изучить больше
Хорошее правило для любой агитации: иметь ссылку на сайт, где можно найти больше информации о том, к чему агитируется. Это не обязательное, но рекомендуемое правило, ибо мало толку от человека, согласившегося с идеей анархизма и захотевшего (редчайший случай!) самостоятельно изучить больше, но не имевшего к этому простой возможности и забывшего вследствие обо всей идее.
Поддержка
А вот поддержка — ориентированная на тех, кто уже знает и уже поддерживает то, что вы любите — может быть совершенно любой. Поддержать антифашистов своего города, позлить фашистов и остаться совершенно незамеченными для обывателя — самое место для диалектики "бей жыдоф!" и "доёш онтифошизм!!".
Напоминание о безопасности
Несколько базовых напоминаний о том, что нужно помнить во время агитации:
- ОСТЕРЕГАЙТЕСЬ КАМЕР! Особенно в России! Метро, маршрутки, автобусы, учебные заведения полны ими!
- Если вас заметили гестаповцы, лучшее, что вы можете сделать — это бежать, что есть мочи.
- Шифруйте материалы, которые храните для распечаток.
- Не распечатывайте стикеры/"визитки" в публичных местах (вроде библиотек).
Спасибо за прочтение!

-
 @ 46fcbe30:6bd8ce4d
2025-03-22 15:21:53
@ 46fcbe30:6bd8ce4d
2025-03-22 15:21:531. Introduction
In decentralized systems like Nostr, preserving privacy and ensuring censorship resistance are paramount. However, the inherent design ethos opens the platform to multiple vulnerabilities, chief among them being the susceptibility to Sybil attacks. The problem space is not only technical but also socio-economic, where user privacy and ease-of-use must be balanced against mitigations that impose friction on identity creation actions.
This report details a multi-faceted research analysis into Sybil resistance mechanisms, drawing analogies from contemporary decentralized identity systems, cryptographic protocols, and economic disincentives. We incorporate detailed insights from diverse independent research streams, outlining both established and novel approaches, and present a series of design recommendations for Nostr. The analysis is targeted at highly experienced analysts and researchers, with comprehensive details on both the cryptographic primitives used and the overall system architectures.
2. Background: The Threat of Sybil Attacks in Decentralized Systems
2.1. Sybil Attacks Defined
A Sybil attack involves a single adversary generating a multitude of pseudonymous identities to unduly influence network decisions, voting mechanisms, or content dissemination processes. In systems designed for censorship resistance, where anonymity is embraced, such attacks are especially daunting because traditional verification methods are not readily applicable.
2.2. The Unique Challenges in Nostr
Nostr is celebrated for its emphatic commitment to censorship resistance and privacy. This design choice, however, leads to several inherent challenges:
- Weak Identity Verification: Mechanisms like nip5, a simple email-like verification protocol, lack robustness and are vulnerable in environments where linking multiple pseudonymous identities is trivial.
- Economic Incentives: Systems using zaps (small value transactions or tips) intend to add cost to malicious actions but struggle with effective proof of expenditure. In some instances, attackers may even benefit from a net positive revenue.
- Association Networks: Existing follow systems provide decentralized webs of association; however, they do not imply a real trust framework, leaving only superficial links among identities.
The dual objectives of achieving ease-of-use while robustly mitigating Sybil attacks requires a careful, in-depth analysis of multiple design trade-offs.
3. Detailed Analysis of Existing Mechanisms and Proposed Enhancements
In our research, several proposals and implementations have emerged to address the Sybil-resistance conundrum. We examine these solutions in detail below.
3.1. Cryptographic and Identity-Based Approaches
3.1.1. Aut-CT with Curve Trees
One of the notable approaches employs the Aut-CT mechanism which leverages Curve Trees. Key insights include:
- Mechanism: Constructing an algebraic analog of a Merkle tree with curve-based keys.
- Verification Efficiency: Achieves logarithmic verification times (typically 40–70 ms) even for large keysets (from 50K to over 2.5M keys).
- Proof Size: Consistently maintains a proof size of around 3–4 kB, making it effective for low-bandwidth scenarios.
- Key Image: The integrated DLEQ-based method produces a key image that binds a proof to a hidden key, preventing fraudulent re-use of tokens.
Implication: This method, while promising, requires integration sophistication. It can potentially be adapted for Nostr to ensure that each identity is backed by a verifiable, anonymous proof of ownership—raising the cost of forging or duplicating identities.
3.1.2. Economic Disincentives and Token Burning
In the realm of cryptocurrency mixers, enforcing an economic cost for generating identities has seen traction. The following methods are prominent:
- Token Burning/Deposit Mechanisms: Users deposit funds that serve as a bond. Forging multiple identities becomes economically prohibitive if these tokens are sacrificial.
- Time Locks and Coin-Age Restrictions: By enforcing waiting periods or requiring funds to ‘age’, systems ensure that rapid, mass identity creation is deterred.
- Fidelity Bonds: Users risk losing bonds if identified as malicious, creating a strong economic disincentive.
Observation: Nostr could potentially adopt analogous economic primitives that impose a non-trivial cost on identity creation, helping to scale the disincentive to the level required for a system where anonymity is paramount.
3.1.3. Decentralized Identity Systems
A comparative analysis of identity systems, both centralized and decentralized, underscores the following:
- Centralized Systems (LDAP, OAuth, etc.): While scalable, they inherently conflict with the decentralized and censorship-resistant philosophy of Nostr.
- Decentralized Systems (uPort, Hyperledger Indy, etc.): These systems leverage blockchain technologies and zero-knowledge proofs to ensure self-sovereign identity management. However, they often require complex deployments and higher operational overhead.
Trade-Off Assessment: Implementing a fully decentralized identity system in Nostr must balance ease-of-use with strong cryptographic assurances. A layered approach—using decentralized identifiers with optional verifications—may yield optimal usability without sacrificing security.
3.2. Protocol-Specific Countermeasures
3.2.1. Rechained Protocol
The Rechained protocol introduces a deposit-based identity generation mechanism in IoT and mobile ad hoc networks. Here are its salient points:
- Deposit Transaction: Each identity is tied to a deposit transaction on a public blockchain, such as Bitcoin or Ethereum.
- Parameterization: Parameters like minHeight, minDifficulty, and amounts ensure that each identity requires a certain financial threshold to be met.
- Verification Complexity: Though proof sizes are modest (10–50 KB) and verification times are around 2 seconds, these are acceptable trade-offs on modern consumer-grade devices.
Application Prospects: If Nostr could integrate a variant of Rechained, it may allow identities to be tied to a verifiable deposit, thus raising the cost baseline for attackers. Such integration must ensure user-friendliness and minimal friction during onboarding.
3.2.2. Sysname Decentralized Identity Scheme
Sysname presents an innovative approach with additional privacy-preserving features:
- Selective Disclosure: It allows users to reveal only non-identifying attributes proving compliance with certain predicates without exposing their full identity.
- Chain-Pinned Identifiers: Aggregates multiple pseudonyms to a single on-chain record, reducing the ease with which an attacker can use disparate identities without accountability.
- Key Recovery: Enables users to refresh public keys and recover lost keys, which bolsters user trust and system resilience.
Consideration: Integrating aspects of sysname within Nostr could offer both enhanced privacy and Sybil resistance, yielding a balance between security and user independence. Enhanced key recovery also addresses the usability concerns evidenced by historical failures in PGP adoption.
3.3. Behavioral Analysis and Anomaly Detection
As an additional countermeasure, behavioral analysis can serve as a secondary layer of defense. Given the evolving sophistication of bots, a cat-and-mouse game inevitably ensues:
- Machine Learning Based Detection: Frameworks like a deep intrusion detection system (DIDS) combined with blockchain smart contracts can help identify anomalous posting behaviors. For example, integrations using Particle Swarm Optimization–Gravitational Search Algorithm (ePSOGSA) with deep autoencoders have proven accurate on established benchmarks.
- Economic Implications: By analyzing behavior, the systems can prioritize identities that have accrued economic transactions (like zaps) that match genuine user behavior over automated, bot-like patterns.
- Limitations: While promising, such systems introduce computational overhead and may yield false positives, so the implementation must be cautiously engineered with appropriate fail-safes.
4. Trade-Offs and Comprehensive Evaluation
4.1. Usability vs. Security
One of the central themes in designing defenses against Sybil attacks on Nostr is balancing ease-of-use with robust security. A highly secure system that remains cumbersome to use (akin to the historical PGP deployment) may fail adoption. Conversely, ease-of-use without economic or cryptographic Assurance opens the door to cost-free identity creation and abuse.
- Economic Approaches: Impose a direct cost on identity creation but must be calibrated to avoid excluding well-intentioned users, particularly newcomers or those with limited funds.
- Cryptographic Protocols: Solutions like Aut-CT and sysname offer advanced cryptographic proofs with minimal overhead in verification but could require more sophisticated client implementations.
- Behavioral Analysis: Acts as a safety net but must be continuously updated as adversaries evolve their bot strategies.
4.2. Privacy Implications
Every mechanism proposed must be evaluated in terms of its ability to preserve user privacy. Nostr’s value proposition rests on its censorship resistance and privacy-preserving design. Therefore:
- Selective Disclosure Protocols: Techniques that allow for proving predicates without full identity revelation should be prioritized (as seen in sysname).
- Decentralized Identity Aggregation: Methods that tie multiple pseudonyms to a single verifiable chain of evidence (enhancing accountability) can reduce risk without compromising anonymity.
- Economic Proof Versus User Balance: The economic barriers should not expose additional metadata that can be linked back to users. Hence, anonymizing tokens and cryptographic blinding techniques need to be integral to the design.
5. Proposed Comprehensive Strategy for Nostr
Based on the research, a multi-layered defense strategy is recommended. It incorporates both cryptographic assurances and economic disincentives while integrating behavioral analysis. The following blueprint emerges:
5.1. Implementation Blueprint
- Integration of Curve Tree-Based Aut-CT Proofs:
- Require each new identity creation to be validated via a Curve Tree-based proof of key ownership. This approach leverages zero-knowledge proofs and ensures logarithmic verification times, thus scalable even for a large user base.
-
Address token re-use and fake identity creation by integrating key images as established in the Aut-CT mechanism.
-
Economic Deposit Mechanism (Inspired by Rechained):
- Incorporate a lightweight deposit mechanism where users must commit a small deposit, recorded on a public blockchain. This deposit acts as a minimum hurdle for each identity and may be partially refundable upon earning trust.
-
Experiment with dynamic deposit sizes based on network load and risk assessments, ensuring that the economic threshold is both feasible and deterring.
-
Selective Disclosure and Pseudonym Aggregation (Adapting Sysname Principles):
- Allow users to prove characteristics about their identities (age, locality, etc.) without divulging full identifying details.
-
Aggregate multiple pseudonyms provided by the same user on-chain, using cryptographic commitments that both link identities and allow selective disclosure.
-
Optional Layer: Economic and Behavioral Analytics:
- Deploy a deep anomaly detection layer using machine learning techniques on posting behavior, ensuring that anomalous activities (e.g., rapid posting similar to bots) are flagged.
- Integrate smart contract-based economic triggers that penalize suspicious behavior while maintaining user privacy.
5.2. Addressing Adoption and Usability Concerns
- User Experience (UX): The proposed solutions must be integrated transparently into client applications. Much like improved versions of PGP aim to streamline key management, Nostr clients should embed these cryptographic protocols without requiring manual intervention.
- Modular Onboarding: Allow users to opt into various levels of proof. Early adopters may use lightweight methods, with a progressive enhancement available for those seeking higher assurance as they interact more within the network.
- Wallet and Key Management Integration: Leverage existing wallet infrastructures to ease the economic deposit and key recovery processes, drawing user confidence from familiarity with mainstream crypto applications.
6. Future Work and Speculative Technologies
While the proposals above are based on current and emergent technologies, additional research can further refine these approaches:
- Adaptive Economic Models: Future work can explore dynamic, context-aware deposit requirements that adjust based on network activity, risk profiles, and even market conditions.
- Quantum-Resistant Cryptography: As quantum computing progresses, integrating quantum-resistant algorithms in curve-tree constructions will become imperative for long-term viability.
- Interoperable Decentralized Identifiers (DIDs): Creating cross-system standards for identity verification may allow Nostr to interface with other decentralized platforms, enhancing the overall security ecosystem.
- Advancements in Zero-Knowledge Proofs (ZKPs): Considering high-level academic research on ZKPs, such as bulletproofs and recursive ZKPs, can further improve both the scalability and succinctness of cryptographic proofs required for identity validation.
Speculative Note: As adversaries adapt, we may see the emergence of hybrid systems where off-chain reputation systems are cryptographically linked to on-chain proofs, creating a multi-dimensional defense that continuously evolves through machine learning and adaptive economic incentives.
7. Conclusion
Mitigating Sybil attacks on Nostr necessitates a proactive, multi-layered approach combining advanced cryptographic techniques, economic disincentives, decentralized verification mechanisms, and behavioral analytics. The proposals detailed in this report aim to reinforce Nostr’s resilience while maintaining its foundational commitment to privacy and censorship resistance.
By integrating Curve Tree-based proofs, economic deposit mechanisms, and selective disclosure methods, Nostr can build a robust identity framework that is both user-friendly and resistant to abuse. Continued research into adaptive economic models and quantum-resistant cryptographic techniques will ensure that the system remains secure in the evolving landscape of decentralized networks.
Thorough evaluation of trade-offs, user experience enhancements, and iterative testing on live networks will be critical. This report serves as a foundational blueprint for further exploration and eventual deployment of sophisticated Sybil defense mechanisms within Nostr.
8. References and Further Reading
While the source of ideas is drawn from numerous research efforts and academic papers, key references include:
- Aut-CT Leveraging Curve Trees and Bulletproof Proofs
- Economic mitigation strategies in cryptocurrency mixers
- Comparative studies of decentralized identity systems (uPort, Hyperledger Indy, etc.)
- Rechained protocol research by Bochem and Leiding for IoT networks
- Sysname scheme for privacy-preserving decentralized identifiers
- Deep intrusion detection systems applied to decentralized social networks
(Additional in-depth academic references can be located within the research literature on arXiv and major cryptographic conferences.)
Prepared by an expert research analyst, this report is intended to provide detailed insights and a strategic roadmap for implementing Sybil-resistant identities on Nostr while retaining user ease-of-use and privacy-centric features.
Sources
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862/2
- https://www.imperva.com/learn/application-security/sybil-attack/
- https://eprint.iacr.org/2019/1111.pdf
- https://www.smartsight.in/technology/what-to-know-about-sybil-attacks/
- https://www.researchgate.net/publication/363104774_Comparative_Analysis_of_Decentralized_Identity_Approaches
- https://www.researchgate.net/publication/331790058_A_Comparative_Analysis_of_Trust_Requirements_in_Decentralized_Identity_Management
- https://www.mdpi.com/1999-5903/17/1/1
- https://github.com/WebOfTrustInfo/rwot5-boston/blob/master/topics-and-advance-readings/Framework-for-Comparison-of-Identity-Systems.md
- https://www.researchgate.net/publication/367557991_The_Cost_of_Sybils_Credible_Commitments_and_False-Name_Proof_Mechanisms
- https://pmc.ncbi.nlm.nih.gov/articles/PMC8125832/
- https://www.nervos.org/knowledge-base/sybil_attacks_consensus_mechanisms_(explainCKBot)
- https://arxiv.org/html/2307.14679v2
- https://www.sciencedirect.com/science/article/pii/S1084804523001145
- https://www.sciencedirect.com/science/article/pii/S2096720924000460
- https://medium.com/@sshshln/mitigating-identity-attacks-in-defi-through-biometric-based-sybil-resistance-6633a682f73a
-
 @ 7d33ba57:1b82db35
2025-03-22 14:04:18
@ 7d33ba57:1b82db35
2025-03-22 14:04:18Alicante, located on Spain’s Costa Blanca, is a vibrant coastal city known for its golden beaches, historic castles, delicious seafood, and lively atmosphere. Whether you're exploring its rich history, relaxing by the sea, or enjoying the local cuisine, Alicante offers the perfect mix of culture and leisure.
🏛️ Top Things to See & Do in Alicante
1️⃣ Santa Bárbara Castle 🏰
- Perched on Mount Benacantil, this medieval fortress offers panoramic views over the city and coastline.
- Walk up the hill or take an elevator from Postiguet Beach.
2️⃣ Postiguet Beach 🏖️
- A beautiful sandy beach right next to the city center.
- Perfect for sunbathing, swimming, or enjoying a cocktail at a beachside bar.

3️⃣ Explanada de España 🌴
- A famous seaside promenade lined with palm trees, cafés, and street artists.
- Great for an evening stroll with stunning sea views.
4️⃣ Alicante Old Town (El Barrio) 🏡
- A charming historic district with narrow streets, colorful houses, and lively tapas bars.
- Visit Concatedral de San Nicolás and the Casas del Barrio for authentic local vibes.
5️⃣ MARQ – Archaeological Museum of Alicante 🏺
- A fascinating museum showcasing Alicante’s history from prehistoric times to modern days.
- Award-winning and great for history lovers!
6️⃣ Tabarca Island Day Trip 🚤
- A small, picturesque island just a short boat ride from Alicante.
- Perfect for snorkeling, seafood dining, and exploring its quaint whitewashed village.
7️⃣ Mercado Central 🛍️
- A bustling market filled with fresh seafood, local produce, jamón ibérico, and cheeses.
- Great for food lovers looking to try authentic Alicante flavors.
🍽️ What to Eat in Alicante
- Arroz a banda – A local seafood rice dish, similar to paella 🍚🐟
- Turrón de Alicante – A famous nougat made with almonds 🍯
- Caldero – A rich fish stew served with rice 🍲
- Salazones – Salted fish specialties, a local delicacy 🐠
- Horchata de chufa – A refreshing tiger nut drink, great on hot days 🥛
🚆 How to Get to Alicante
✈️ By Air: Alicante-Elche Airport (ALC) with flights from all over Europe ✈️
🚄 By Train: High-speed AVE trains from Madrid (~2.5 hrs) & Barcelona (~4.5 hrs)
🚗 By Car: Well-connected via the AP-7 coastal highway💡 Tips for Visiting Alicante
✅ Best time to visit? Spring & Summer for the best beach weather ☀️🏖️
✅ Stay for Las Hogueras de San Juan (June 20-24) – A huge fire festival with fireworks & street parties 🎆🔥
✅ Take a boat to Tabarca Island – It’s a hidden paradise for snorkeling 🏝️
✅ Try local seafood! Alicante’s coast is famous for its fresh fish & shellfish 🦐 -
 @ 30b99916:3cc6e3fe
2025-03-22 12:12:00
@ 30b99916:3cc6e3fe
2025-03-22 12:12:00constitution
Article V of the Constitution of the United States
With your engagement, there is a glimmer of hope that the people can reclaim our captured US government. The entrenched politicians are counting on your NON-ENGAGEMENT to remain in control.
Please take the time to educate yourself about the Constitution.
Now get engaged with your local Convention of States movement.
-
 @ 7d33ba57:1b82db35
2025-03-22 10:27:50
@ 7d33ba57:1b82db35
2025-03-22 10:27:50Valencia is a vibrant coastal city on Spain’s east coast, blending historical charm, futuristic architecture, golden beaches, and amazing cuisine. As the birthplace of paella, it’s a paradise for food lovers, while its mild climate and Mediterranean vibes make it a perfect year-round destination.
🏛️ Top Things to See & Do in Valencia
1️⃣ The City of Arts and Sciences
- A futuristic architectural complex with a science museum, planetarium, aquarium, and opera house.
- The Hemisfèric & Oceanogràfic are must-visits for families and science lovers.
2️⃣ Valencia Cathedral & El Miguelete Tower
- A beautiful Gothic cathedral said to house the Holy Grail.
- Climb El Miguelete Tower for breathtaking city views.
3️⃣ La Lonja de la Seda (Silk Exchange) – UNESCO Site
- A stunning Gothic-style merchant building from the 15th century.
- One of the best-preserved examples of Valencia’s medieval trading history.
4️⃣ Plaza de la Virgen & Old Town (El Carmen)
- A charming square surrounded by historical buildings, fountains, and lively cafés.
- Wander the narrow streets of El Carmen for street art, boutique shops, and tapas bars.
5️⃣ Turia Gardens & Gulliver Park
- A beautiful green park built in a former riverbed, perfect for cycling, jogging, or picnicking.
- Gulliver Park is a giant playground shaped like Gulliver from "Gulliver’s Travels"!
6️⃣ Central Market (Mercado Central)
- One of the largest fresh food markets in Europe, housed in a stunning Art Nouveau building.
- Try fresh produce, local cheeses, and traditional jamón ibérico.
7️⃣ Malvarrosa Beach
- A long sandy beach with great restaurants, water sports, and a relaxing atmosphere.
- Perfect for sunbathing, a seaside stroll, or enjoying a paella by the sea.
🍽️ What to Eat in Valencia
- Paella Valenciana – The original version with rabbit, chicken, and saffron rice 🥘
- Horchata & Fartons – A refreshing tiger nut drink with sweet pastries 🥛🥐
- Agua de Valencia – A famous local cocktail made with orange juice, cava, gin, and vodka 🍹
- Esgarraet – A tasty mix of salted cod, red peppers, and olive oil 🐟
🚆 How to Get to Valencia
🚄 By Train: High-speed AVE trains from Madrid (~1.5 hrs) & Barcelona (~3 hrs)
✈️ By Air: Valencia Airport (VLC) with connections to major European cities
🚗 By Car: A scenic drive along the Mediterranean coast (Costa Blanca)💡 Tips for Visiting Valencia
✅ Best time to visit? Spring & Fall for pleasant weather 🌞
✅ Visit during Las Fallas (March 15-19) – A spectacular festival with fireworks, giant sculptures, and street parties 🎆🔥
✅ Try a bike tour! Valencia is one of Spain’s most bike-friendly cities 🚴
-
 @ da0b9bc3:4e30a4a9
2025-03-22 09:34:42
@ da0b9bc3:4e30a4a9
2025-03-22 09:34:42Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/921232
-
 @ d5c3d063:4d1159b3
2025-03-22 03:31:14
@ d5c3d063:4d1159b3
2025-03-22 03:31:14“คุณจะจัดการกับมลพิษฝุ่น PM2.5 โดยไม่ต้องอาศัยการออกกฎควบคุมจากรัฐได้ยังไง” ถ้าคุณเคยตั้งคำถามนี้ บทความนี้มีคำตอบ...และคำตอบอาจสวนทางกับความเชื่อของคุณโดยสิ้นเชิง . ลองย้อนกลับไปในช่วงต้นปีที่ผ่านมา ในวันที่กรมควบคุมมลพิษประกาศว่า “ค่าฝุ่น PM2.5 เกินมาตรฐานใน 43 จังหวัด” และโรงเรียนหลายแห่งต้องสั่งปิดชั่วคราว คุณอาจนึกถึงภาพผู้คนใส่หน้ากากเดินท่ามกลางหมอกควัน แล้วถามตัวเองว่า “เรากำลังแก้ปัญหานี้ด้วยวิธีที่ถูกต้องจริงหรือ?” ฝุ่น PM2.5 ปัญหาของ "Externalities" หรือปัญหาของการไม่มี "สิทธิในทรัพย์สิน" ที่ชัดเจน? . ในคลิปวิดีโอ จาก CDC Bitcointalk EP3 เมื่อปี 2020 อ.พิริยะ สัมพันธารักษ์ ได้เสนอแนวคิดที่ขัดแย้งกับสิ่งที่รัฐและสื่อกระแสหลักมักพูดถึงเสมอเมื่อพูดถึงฝุ่น PM2.5 ว่า... “ฝุ่น PM2.5 ไม่ใช่ปัญหาที่จะถูกแก้ได้ด้วยการออกกฎหมายควบคุมหรือแจกหน้ากากฟรี...แต่ต้องแก้ด้วยการ สร้างกลไกตลาดและสิทธิในทรัพย์สินที่ชัดเจน เพื่อให้คนที่ก่อมลพิษต้อง จ่าย ให้กับผู้ได้รับผลกระทบ” . . แล้วมันเกี่ยวอะไรกับ Hazlitt ??? Henry Hazlitt กล่าวไว้ในบทแรกของ Economics in One Lesson ว่า ความผิดพลาดทางเศรษฐศาสตร์ส่วนใหญ่เกิดจากการมองแค่ผลกระทบเฉพาะหน้า และมองเฉพาะผลที่เกิดกับคนบางกลุ่ม แต่ละเลยผลระยะยาวกับทั้งระบบและมองไม่เห็น “สิ่งที่ไม่ปรากฏต่อสายตา” เช่นเดียวกับกรณีฝุ่น PM2.5 . การที่รัฐเข้ามาควบคุม เช่น การสั่งห้ามเผา อาจฟังดูดีในระยะสั้น แต่มันยังไม่มีแรงจูงใจทางเศรษฐกิจให้ผู้เผาหยุดทำ เพราะต้นทุนการก่อมลพิษยัง “ฟรี” ถ้ามลพิษมีต้นทุน คนก็จะคิดก่อนเผา . ลองนึกถึงแนวคิดของการซื้อ-ขายสิทธิในเชิงสมัครใจ (Voluntary Emissions Trading) ซึ่งต่างจากระบบ Cap-and-Trade ที่ภาครัฐเป็นผู้กำหนดเพดานและบังคับใช้ แต่ในแนวทางตลาดเสรีนั้น หากสิทธิในอากาศหรือพื้นที่ถูกระบุอย่างชัดเจน เจ้าของสิทธิสามารถตกลงซื้อขายกับผู้ก่อมลพิษได้โดยตรงโดยไม่ต้องพึ่งรัฐเป็นคนกลาง . แล้วในบริบทแบบ Hazlitt ถ้าคุณให้ความเป็นเจ้าของอากาศแก่คนในเมือง คนเหล่านั้นสามารถ “ฟ้องร้อง” หรือ “เรียกค่าเสียหาย” จากผู้ที่ปล่อยมลพิษได้ ซึ่งจะทำให้เกิดต้นทุนที่แท้จริงกับผู้ก่อมลพิษ . กลไกตลาดไม่ได้หมายถึง “แค่ปล่อยให้ทุกอย่างเป็นไปตามธรรมชาติ” แต่มันคือการสร้างระบบ “แรงจูงใจ” ที่ทำให้คนเลือกทางออกที่ดีที่สุดเอง โดยไม่ต้องมีใครมาบังคับ . ผมนึกถึงที่ Murray Rothbard เคยพูดไว้ว่า “สิทธิในทรัพย์สิน คือสิ่งเดียวที่จะทำให้ผู้คนมีแรงจูงใจในการดูแลสิ่งแวดล้อม ไม่ใช่คำสั่งจากเจ้าหน้าที่รัฐ” เพราะเมื่อคุณเป็นเจ้าของสิ่งใด คุณย่อมมีแรงจูงใจในการรักษามัน มากกว่าการที่รัฐสั่งให้คุณต้องแคร์ ดังนั้น แทนที่จะใช้ระบบ Cap-and-Trade ที่รัฐควบคุม บทความนี้เสนอแนวทางที่ไม่พึ่งพารัฐ เช่น ชุมชนหรือเอกชนรวมตัวกันตกลงไม่เผา และใช้กลไกจ่ายชดเชยกันเองหากละเมิดสิทธิ หรือกรณีเจ้าของบ้านฟ้องโรงงานที่ทำให้บ้านหรือพื้นที่ที่อยู่อาศัยเสียหาย ทั้งหมดนี้คือการใช้สิทธิในทรัพย์สินและกลไกกฎหมายแพ่งเพื่อสร้างแรงจูงใจ โดยไม่ต้องให้รัฐเข้ามาควบคุมหรือกำกับ แต่ยังคงอาศัยศาลเพื่อปกป้องสิทธิ เมื่อเกิดการละเมิด . . แล้วทำไมแนวคิดแบบให้รัฐควบคุมถึงล้มเหลวเสมอ...? Hazlitt เตือนว่า รัฐมักคิดว่าตัวเองมองเห็นผลดี แต่ไม่เคยมองเห็นผลเสียที่มองไม่เห็น เช่น เมื่อรัฐประกาศห้ามเผาซังข้าวโพดหรือฟางข้าวในภาคเหนือโดยเด็ดขาด ชาวไร่จำนวนมากที่เคยใช้วิธีเผาเพื่อคืนโพแทสเซียมและแร่ธาตุให้ดินแบบต้นทุนต่ำ ต้องหันไปซื้อปุ๋ยเคมีแทน ซึ่งมีราคาสูง กลายเป็นภาระทางเศรษฐกิจที่ถาโถมใส่เกษตรกรรายย่อยโดยตรง ทั้งที่พวกเขาไม่ได้มีทางเลือกอื่นมากนัก นี่คือ “ต้นทุนที่มองไม่เห็น” ตามที่ Hazlitt เตือน รัฐเห็นแค่ "ผลดีเฉพาะหน้า" เช่น ค่าฝุ่นลดชั่วคราว แต่ไม่เห็นผลเสียระยะยาวต่อความยั่งยืนของชุมชนเกษตรกรรม แล้วทั้งหมดนี้คือการเอื้อประโยชน์ให้คนกลุ่มหนึ่ง แต่กระจายต้นทุนไปให้ทั้งสังคม ซึ่งตรงกับที่ Hazlitt วิจารณ์ในหนังสือ . . แล้วเสรีภาพในตลาดกับอากาศที่สะอาด...ไปด้วยกันได้ไหม? อ.พิริยะ ยกตัวอย่างบิตคอยน์ว่าเป็นระบบที่ไม่ต้องพึ่งรัฐหรือคนกลาง แต่สามารถสร้างแรงจูงใจทางเศรษฐกิจให้คนทั่วโลกเข้าร่วมโดยสมัครใจ และตรวจสอบได้แบบโปร่งใสผ่านกลไกกระจายศูนย์ แสดงให้เห็นว่าแนวคิดตลาดเสรีสามารถทำงานได้จริงหากออกแบบแรงจูงใจให้เหมาะสม แนวคิดเดียวกันนี้ใช้ได้กับปัญหาฝุ่น PM2.5 ถ้าเรามองว่าอากาศคือทรัพยากรที่มีเจ้าของ และอนุญาตให้มีการซื้อ-ขายหรือฟ้องร้องโดยไม่ต้องพึ่งรัฐเข้ามาจัดการจากส่วนกลาง คำตอบคือ ได้...ถ้าเราให้ “ตลาด” ทำงาน -ถ้ามลพิษทำให้ที่อยู่อาศัยเสียหาย เราสามารถฟ้องผู้ก่อมลพิษได้ -ถ้าโรงงานต้องซื้อสิทธิปล่อยมลพิษ พวกเขาจะมีแรงจูงใจลดฝุ่น -ถ้าประชาชนขาย “เครดิตอากาศสะอาด” ได้ จะเกิดอาชีพใหม่ เช่น การปลูกป่าคาร์บอน นี่ไม่ใช่จินตนาการ แต่คือหลักคิดที่กำลังเกิดขึ้นในหลายประเทศ เช่น แคลิฟอร์เนีย เยอรมนี และสิงคโปร์ . . สรุปเศรษฐศาสตร์ของฝุ่น...อยู่ที่ใครจ่ายต้นทุน Hazlitt ไม่เคยพูดถึง PM2.5 โดยตรง แต่แนวคิดของเขาชัดเจนว่า ทุกนโยบาย ต้องถูกมองในแง่ของผลกระทบที่มองไม่เห็นในระยะยาวด้วย และนั่นคือสิ่งที่รัฐไทยและคนส่วนใหญ่ยังไม่เข้าใจเมื่อพูดถึงปัญหาฝุ่น ตลาดไม่ได้ไร้หัวใจ แต่มัน บีบให้คนรับผิดชอบในสิ่งที่ตัวเองก่อ ข้อเสนอเชิงนโยบาย -ส่งเสริมการกำหนดสิทธิในอากาศหรือสิทธิในพื้นที่อยู่อาศัยให้ชัดเจน -เปิดตลาดซื้อ-ขาย “เครดิตฝุ่นสะอาด” สำหรับภาคอุตสาหกรรม โดยเน้นว่าเป็นระบบที่เกิดจากความสมัครใจของภาคเอกชนหรือชุมชน ไม่อยู่ภายใต้การกำกับหรือควบคุมโดยรัฐ -ส่งเสริมการลงทุนเอกชนด้านเซ็นเซอร์วัดฝุ่นแบบกระจายตัว (decentralized air quality monitoring) . . แล้วคุณล่ะ คิดว่าฝุ่นควรจัดการโดยรัฐ หรือโดยตลาด 💬 คุณคิดว่าเราควรเริ่มสร้าง “ระบบสิทธิและแรงจูงใจเพื่อรักษาคุณภาพอากาศ” ได้อย่างไร หรือทำไมคุณยังเชื่อว่ารัฐควรเป็นคนจัดการควบคุมทั้งหมดอยู่ และถ้าคุณยังเชื่อว่ารัฐควรเป็นผู้ดูแลควบคุม ลองถามตัวเองดูว่ารัฐเคยสามารถจัดการอะไรได้อย่างมีประสิทธิภาพได้ในระยะยาวหรือไม่ หากคุณสนใจแนวคิดตลาดเสรีและเศรษฐศาสตร์แบบเข้าใจง่าย ๆ ผมแนะนำหนังสือ Economics in One Lesson โดย Henry Hazlitt หนังสือที่เปลี่ยนวิธีคิดของคนทั้งโลกเกี่ยวกับ “สิ่งที่มองไม่เห็น” ของเศรษฐกิจ มีฉบับแปลไทยแล้วนะ 🙃
เศรษฐศาสตร์เล่มเดียวจบ #EIOL #Siamstr
EconomicsinOneLesson #RightBook #PM25
-
 @ 234035ec:edc3751d
2025-03-22 02:34:32
@ 234035ec:edc3751d
2025-03-22 02:34:32I would like to preface this idea by stating that I am by no means a computer engineer and lack significant technical knowledge, and therefore may be overlooking significant obstacles to implementing this idea. My reason for writing this paper is in hopes that developers or others who are more "in the know" than me could provide feedback.
The Success of Polymarket
Over recent months, Polymarket has garnered many headlines—mainly for its accurate prediction markets surrounding the 2024 presidential election. On Polymarket, users can purchase futures contracts that will either pay out $1 in USDC at maturity if the prediction is correct or will become worthless if the prediction is incorrect. Market participants can freely trade these futures at the current price up until maturity, allowing for efficient price discovery.
We’ve known for quite some time that free markets are the most efficient way of pricing goods and services. Polymarket has now demonstrated just how effective they can be in pricing potential outcomes as well.
The issue I have with this application is that it is built on the Polygon network—a proof-of-stake side chain of Ethereum. Users are subject to KYC regulations and do not have the ability to create markets themselves. While the core idea is powerful, I believe it has been built on a foundation of sand. We now have the tools to build something similar—but much more decentralized, censorship-resistant, and sustainable.
A Bitcoin-Based Prediction Market
It seems to me that Chaumian eCash, in combination with Bitcoin and Nostr, could be used to create a truly decentralized prediction marketplace. For example, multiple eCash mints could issue tokens that represent specific potential outcomes. These tokens would be redeemable for 100 sats at a predetermined block height if the prediction is correct—or become irredeemable if the prediction is incorrect.
Redemption would be based on consensus from the chosen oracles—trusted Nostr Npubs—with strong reputations and proven track records. Anyone could create a market, and users could buy, sell, and trade eCash tokens privately. This approach preserves the power of markets while eliminating the need for custodians, KYC, or dependence on unreliable chains.
What we would have is a trust-minimized, privacy-preserving, Bitcoin-native prediction market that resists censorship and allows for true global participation. Feedback, critique, and collaboration are welcome.
Next Steps and Vision
The potential for system like this is immense. Not only would it enable peer-to-peer speculation on real-world outcomes, but it would also open the door to a more accurate reflection of public sentiment. With free market incentives driving truth-seeking behavior, these prediction markets could become powerful tools for gauging probabilities in politics, finance, sports, science, and beyond.
Each mint could specialize in a specific domain or geographic region, and users could choose the ones they trust—or even run their own. The competition between mints would drive reliability and transparency. By using Nostr for oracle communication and event creation, we keep the entire system open, composable, and censorship-resistant.
Markets could be created using a standardized Nostr event type. Resolution data could be posted and signed by oracles in a verifiable way, ensuring anyone can validate the outcome. All of this could be coordinated without a centralized authority, enabling pseudonymous participation from anyone with an internet connection and a Lightning wallet.
In the long run, this system could offer a viable alternative to corrupted media narratives, rigged polling, and centrally controlled information channels. It would be an open-source tool for discovering truth through economic incentives—without requiring trust in governments, corporations, or centralized platforms.
If this idea resonates with you, I encourage you to reach out, build on it, criticize it, or propose alternatives. This isn’t a product pitch—it’s a call to experiment, collaborate, and push the frontier of freedom-forward technologies.
Let’s build something that lasts.
Bitcoin is our base layer. Markets are our discovery engine. Nostr is our communication rail. Privacy is our defense. And truth is our goal.
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ d34e832d:383f78d0
2025-03-21 20:31:24
@ d34e832d:383f78d0
2025-03-21 20:31:24Introduction
Unlike other cetaceans that rely on whistles and songs, sperm whales primarily use echolocation and patterned click sequences to convey information. This paper explores the structure, function, and implications of their vocal communication, particularly in relation to their social behaviors and cognitive abilities.
1. The Nature of Sperm Whale Vocalizations
Sperm whales produce three primary types of clicks:
- Echolocation clicks for navigation and hunting.
- Regular clicks used in deep diving.
- Codas, which are rhythmic sequences exchanged between individuals, believed to function in social bonding and identification.Each whale possesses a monumental sound-producing organ, the spermaceti organ, which allows for the production of powerful sounds that can travel long distances. The structure of these clicks suggests a level of vocal learning and adaptation, as different populations exhibit distinct coda repertoires.
2. Cultural and Regional Variation in Codas
Research indicates that different sperm whale clans have unique dialects, much like human languages. These dialects are not genetically inherited but culturally transmitted, meaning whales learn their communication styles from social interactions rather than instinct alone. Studies conducted in the Caribbean and the Pacific have revealed that whales in different regions have distinct coda patterns, with some being universal and others specific to certain clans.
3. Social Organization and Communication
Sperm whales are matrilineal and live in stable social units composed of mothers, calves, and juveniles, while males often lead solitary lives. Communication plays a critical role in maintaining social bonds within these groups.
- Codas serve as an acoustic signature that helps individuals recognize each other.
- More complex codas may function in coordinating group movements or teaching young whales.
- Some researchers hypothesize that codas convey emotional states, much like tone of voice in human speech.4. Theories on Whale Intelligence and Language-Like Communication
The complexity of sperm whale vocalization raises profound questions about their cognitive abilities.
- Some researchers argue that sperm whale communication exhibits combinatorial properties, meaning that codas might function in ways similar to human phonemes, allowing for an extensive range of meanings.
- Studies using AI and machine learning have attempted to decode potential syntax patterns, but a full understanding of their language remains elusive.5. Conservation Implications and the Need for Further Research
Understanding sperm whale communication is essential for conservation efforts. Noise pollution from shipping, sonar, and industrial activities can interfere with whale vocalizations, potentially disrupting social structures and navigation. Future research must focus on long-term coda tracking, cross-species comparisons, and experimental approaches to deciphering their meaning.
Consider
Sperm whale vocal communication represents one of the most intriguing areas of marine mammal research. Their ability to transmit learned vocalizations across generations suggests a high degree of cultural complexity. Although we have yet to fully decode their language, the study of sperm whale codas offers critical insights into non-human intelligence, social structures, and the evolution of communication in the animal kingdom.
-
 @ 7bc05901:8c26d22b
2025-03-21 19:47:15
@ 7bc05901:8c26d22b
2025-03-21 19:47:15Decentralization is a beautiful return volley to the censorship regimes that have ruled American social media, but the decentralization piece isn't the biggest impact Nostr is having on me. The empowerment and encouragement to start building are what overwhelms. Since I began sending zaps just a few weeks ago, every idea I have had for an app over the last decade is organically re-emerging as executable Nostr apps.
The rise of AI alongside Nostr's invention/discovery is serendipitous for someone who doesn't have the coding experience to develop an app from scratch like myself. It is also a great moment for apps that had a social feature -- which was essentially every app. "Connect it using Facebook" was such a non-starter for me. I live in a small town where Facebook is a gossip cesspool. There are intriguing communities there, sure, but the overwhelming dread that overcomes me when I open that app doesn't justify digging for the socially-delightful gems. Further, any app that integrates with facebook is or becomes a variation on an already existing feature that META has engineered into their platform -- they want, they need your eyeballs. On their site.
Nostr makes no such demands. It doesn't care which site is being used to access the protocol, and what features exist on that site. It is available to help, secure a user's identity, and doesn't make many demands in return.
My friend and local farmer Ryan and I have discussed an app for years, built it and rebuilt it using different tools, but we ultimately got distracted by more pressing and less complicated projects. I think a huge barrier to execute it was the sense that it would be impossible to achieve any network effects, plus the thought of managing the social side was overwhelming. It required us to need really powerful tools, and to maintain a lot of data that we didn't really want to hold onto. It was essentially an app for local food producers and consumers. With Nostr at play, we could build something like this and simultaneously onboard our local community to the Nostr protocol while also providing a lightweight solution to managing the complicated part of an online marketplace. The lightning payments come as an added bonus.
We are tracking the use of another app which is sweeping through local food producers, which is only in its beta phase, and restarting our build of a marketplace that is worth building and encourages a sustainable local food supply, this time with a protocol that reduces 90 percent of the annoying part of that build, and doesn't require anyone spend time on Zuckerberg's playground.
-
 @ 6a6be47b:3e74e3e1
2025-03-21 18:45:32
@ 6a6be47b:3e74e3e1
2025-03-21 18:45:32Hey frens! Today, I spent a big chunk of the morning painting with watercolors. This is only the second time I've completed a piece using this technique in a long while. It feels like coming back home after a vacation: you enjoyed the time away and relaxed, but when you're lucky enough to have a safe space to call home, there's really nothing like it. 🖼️
🎨 That's exactly how I feel about painting with watercolors again. I'm really excited to share what I've been working on with you soon. In the meantime, I've got a new blog post up about Ostara and the Spring Equinox. ⭐️Today, I just feel so blessed and excited about the future. I'm simply soaking up the moment, I guess. I hope you're feeling the same way too! Today, I also whipped up some mini veggie quiches chef's kiss.
 🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it!
🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it! -
 @ 6bae33c8:607272e8
2025-03-21 18:23:28
@ 6bae33c8:607272e8
2025-03-21 18:23:28I put Beat Chris Liss 3 in quotes because technically this was not a Beat Chris Liss league — I just bought it at the last minute to get an extra league. In any event, I drew the seventh spot, and here are the results:
1.7 Corbin Carroll — He’s been hitting home runs this spring, a signal his shoulder is healthy. You know he’ll run, and given how he performed at the end of last year, I’d expect the batting average to bounce back too.
2.8 Jazz Chisholm — I want to see what he can do with a full year in Yankee Stadium. He’s a health risk, but he was a 20-20-ish player in Miami with only 100 games in 2023. It’s also nice that he qualifies at 3B and OF. I considered Mookie Betts, who slipped, but I’m concerned about severe weight loss from an illness undermining the first half of his season.
3.7 Chris Sale — He’s a Hall of Fame level pitcher with his health and form back. Remember when Justin Verlander faded in his 30s and then got it back together? I expect a few good years from Sale before he declines again.
4.8 Corbin Burnes — I don’t really even like Burnes, but he slipped a full round past ADP, and I value-took.
5.7 C.J. Abrams — I love this pick, probably my favorite of the draft. Abrams is a 20-30 player despite attitude issues. What if he matures and gets it together at age 24?
6.8 Adley Rustchman — I didn’t see anything I liked, and I was light on power. One way to get a leg up power-wise is to draft elite catchers.
7.7 Cody Bellinger — I like him with Yankee Stadium’s short porch, a few steals from a first-base-eligible player and also outfield eligibility.
8.8 Mike Trout — I had enough pitching and speed, but I needed some power, and Trout still has as much as anyone if he could ever play 100-plus games. He’s healthy now at least.
9.7 Will Smith — A second top catcher to pair with Rutschman. I was light on power through five rounds, but my next four picks were 20-plus HR catchers, Bellinger in Yankee Stadium and Trout.
10.8 Roki Sasaki — He slipped a couple rounds after a rough outing in Japan, but he was still throwing 100 with nasty movement. Another value-take.
11.7 Sonny Gray — A favorite old warhorse in a good pitcher’s park. I really wanted Sandy Alcantara, but Gray’s ADP was higher, so I thought there was a better chance to get Alcantara on the way back.
12.8 Sandy Alcantara — Turns out I thought right. I love Alcantara, who was going in the third round a couple years ago, now that he’s healthy and throwing 100 mph again.
13.7 Alexis Diaz — Taking Alcantara cost me my two go-to closers, Kenley Jansen and Jordan Romano, both of whom went earlier than usual, so I pivoted to Diaz. I thought this was a mistake at first — Diaz has been bad this spring, and he wasn’t even good last year, either, but he’s the closer until further notice, and a couple spring outings shouldn’t move the needle that much.
14.8 Kevin Gausman — Another old warhorse, coming off a down year, possibly due to injury. His velocity has been back up this spring too.
15.7 Xander Bogaerts — Another ADP value-take. Bogaerts had double digit homers and steals in 111 games last year and is a good bet to hit for a decent average.
16.8 Ryan Pressly — Another shaky closer, Pressly had three walks in an inning against the Dodgers, but he’s probably not losing the job over one ugly but scoreless outing.
17.7 Aroldis Chapman — Named the Red Sox closer, Chapman is probably the best of the three I drafted thus far. His ADP was lower because he was only given the role a couple days ago. Chapman perfectly fits the old warhorse mold I like too.
18.8 Brandon Pfaadt — I didn’t really need another starter, but he was the best player left on the board, and you always run out of pitching.
19.7 Zack Gelof — He strikes out a ton, but he went 17-25 last year in 138 games as a rookie, and now he gets to play in a minor-league band box. Lawrence Butler went 22-18 and is going in the fifth round!
20.8 T.J. Friedl — I was light on OF, and Friedl is one. He has a little pop, runs and is expected to lead off for the Reds in the best non-Coors hitting park in baseball.
21.7 A.J. Puk — I was still a little light in saves, and Puk is in the running for the Arizona job.
22.8 Roman Anthony — I don’t know if he’ll break camp with the Red Sox, but he was the remaining player I would have felt worst getting snaked on. He doesn’t have much left to prove in the minors.
23.7 George Springer — He went 20-20 in 2023 and 19-16 last year. He could be done, but at 35 he’s not ancient.
24.8 Jo Adell — I needed to fill in the outfield, and Adell should play, run and hit for power. The strikeouts and batting average risk are bad, but he’s still young enough to improve.
25.7 Griffin Jax — He’s a top reliever, next in line for saves and closer Jhoan Duran isn’t very good.
26.8 Christopher Morel — I needed a corner and Morel is one. (If I needed a mushroom, this would also hold.) He hit .196 last year, but he has good pop and should play OF for the Rays in a small minor-league park.
27.6 Casey Mize — The former No. 1 overall pick has looked good this spring, and he’s completely healthy.
28.6 Will Warren — Warren should get a shot in the Yankees rotation, given the injuries to Gerrit Cole and Luis Gil.
29.6 Spencer Torkelson — Another former No. 1 overall pick for the Tigers, Torkelson hit 31 homers in 2023 and should get another shot this year given his strong spring.
30.6 Nolan Schanuel — I just wanted an extra corner with regular playing time heading into the year. He runs a little and had 13 HR, but in a full season of at-bats.
Roster By Position:
C Adley Rustchman/Will Smith
1B Cody Bellinger
2B Xander Bogaerts
3B Jazz Chisholm
SS C.J. Abrams
CI Christopher Morel
MI Zack Gelof
OF Corbin Carroll/Mike Trout/T.J. Friedl/Roman Anthony/George Springer
UT Jo Adell
SP Chris Sale/Corbin Burnes/Roki Sasaki/Sonny Gray/Sandy Alcantara/Kevin Gausman
RP Alexis Diaz/Ryan Pressly/Aroldis Chapman
B Brandon Pfaadt/A.J. Puk/Griffin Jax/Casey Mize/Will Warren/Spencer Torkelson/Nolan Schanuel
-
 @ 6ad3e2a3:c90b7740
2025-03-21 18:21:50
@ 6ad3e2a3:c90b7740
2025-03-21 18:21:50There are two ways things happen in this world: top-down and bottom-up. Top-down is via authoritarian edict, i.e. fascism, no matter how benign-seeming. It is the government imposing a tax, incentivizing a behavior, creating a new law. Bottom-up is the organic process of people doing what interests them voluntarily, what benefits them, what they decide is best individually.
There is but one legitimate role for top-down and that is in creating good conditions for bottom up. The US Constitution is fascism in that it forces you to adhere to its edicts as the supreme law of the land. But it’s also an effective boundary creating the necessary conditions for free markets, free expression, creativity and prosperity.
All governments are fascistic in that they use force to achieve their agendas. But the best ones use only the minimum necessary force to create conditions for bottom-up prosperity. There is no other kind of prosperity.
. . .
Governments aren’t the only entities that are fascistic. Schools, corporations, institutions and individuals, almost invariably, are too. Yes, I am a fascist and very likely so are you. Don’t believe me? Do you have a voice inside your head telling you what you must get done today, evaluating your progress as a person, critiquing and coercing you into doing things that are “good” for you and avoiding ones that are “bad”? If so, you are fascist.
Why not just trust yourself to make the right choices? Why all the nudging, coaxing, coaching, evaluating and gamifying? Who is this voice, what gives it the authority, the requisite wisdom to manage your affairs? Haven’t all your shortcomings, disappointments and general dissatisfactions taken place despite its ever-presence? What makes you think you are better off for having had this in-house micromanagement?
. . .
The top-down edicts that rule our lives are by and large unnecessarily oppressive. Yes, we should create some good top-down conditions for bottom up organic thriving like buying healthy food, getting fresh air, not consuming excessive amounts of alcohol or drugs, but the moment to moment hall-monitoring, the voice that requires you to achieve something or justify your existence? That’s fascism.
. . .
The mind is a powerful tool when it comes to planning, doing math or following a recipe, but if it can’t be turned off, if it’s not just optimizing your path from A to B, but optimizing YOU, that’s fascism.
. . .
I think about the problem of human governance through this lens. I imagine everyone charged with power over a polity has an agenda, and that agenda, insofar as it requires force to achieve, is fascistic. They want it to go this way rather than that way, and some people don’t agree. The quality of leadership then is the extent to which that force is used to preserve the bottom-up freedom of the individual to pursue his interests without undue interference, either from authorities themselves or other individuals who would unduly disrupt him.
The Constitution is an excellent guideline for this, and I surely won’t be able to come up with a better one in this Substack. It’s why I support Trump’s efforts to trim the top-down public sector and return productivity to the bottom-up private one, why I support deportation of adjudicated criminals who are here illegally, but oppose removing people with green cards or on valid student visas for protesting via constitutionally protected speech.
I don’t root for politicians like they play for my favorite sports team. I root for the freedom of the individual, the possibility of a largely bottom-up society wherein prosperity is possible. And I do this while knowing it will never happen exactly the way I would like, so long as I am bound by the fascism coming from inside the house.
-
 @ bf95e1a4:ebdcc848
2025-03-21 17:03:01
@ bf95e1a4:ebdcc848
2025-03-21 17:03:01This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Preface
At the time of writing, it is New Year’s Day, and 2019 has just begun. For once, I have a resolution to live up to: I’ve promised myself to write a page per day every day this year until I have something real to publish. In June 2018, I published my first book, Three Minute Reads on Bitcoin — A Year of Thoughts. The book consisted of articles I had published online from May 2017 up to that point. This time it’s different. Instead of a mere collection of articles, I intend to write a “proper” book. A book that explains why Bitcoin is the most important invention of our lives.
I didn’t choose Bitcoin; it chose me. I had been trying to figure out how the world worked under the hood all my life, and then this simple idea of absolute scarcity popped up. It had a profound impact on how I view human interaction. Because of my curious nature, I instantly fell deep into the rabbit hole. I decided to educate myself on how this mysterious technology worked, and that got me into Austrian economics, which expressed very clearly what I had always suspected — that you really can't create value out of thin air.
In this book, I will try to explain every aspect of what makes this technology so special, what sets it apart from the abundant shameless copies of it, what’s wrong with our current system, and what the future might look like. In just two days from the time of writing these words, we’ll celebrate the ten-year anniversary of the Genesis Block when the Bitcoin blockchain came into being. That block contained a message, a newspaper headline that read: “03/Jan/2009 Chancellor on brink of second bailout for banks”. No one knows why Bitcoin’s mysterious creator, Satoshi Nakamoto, chose to include this in the Genesis Block. There is also some debate on whether the Genesis Block was actually mined on the 3rd of January since the next block wasn’t mined until six days later. Somehow, Satoshi managed to stay hidden and weave several layers of mystique into the fabric of Bitcoin from the very beginning, which is part of what makes its conception so immaculate. This book aims to strip Bitcoin of its shady cloak and illuminate its true nature. After all, the only thing any person can do about Bitcoin now is to study it.
Foreword
My journey down the Bitcoin rabbit hole has provided me with a newfound clarity of how our world should be perceived. In the same way that getting married and having my first child were beautiful life-changing events, discovering Bitcoin was a new chapter in my life. I can easily divide my life into two distinct periods: before and after Bitcoin.
Before discovering Bitcoin, life was perplexing. For years, even dating back to my school days, I had an innate sense that something was amiss in the world. Although I wasn’t a good student by any means, it was obvious back then that many aspects of life simply didn’t add up.
One thing that I was sure of was that money was corrupt. However, it took me a while to realize that money itself is fundamentally corrupt. Furthermore, what is typically taught and accepted as money by society is a perversion of what money should be. These are the first steps of understanding Bitcoin, which require you to admit that you have been fooled and lied to all your life. The hard lessons of hard money.
The way I see it, the revelation about the true nature of money is akin to a bracing cold shower that wakes you up to reality. Emerging from that cold shower is an incredibly liberating and invigorating sensation. Unfortunately, many individuals are not motivated enough to take that crucial step into the chilly waters. Instead, they will later experience an ice-cold bucket of water being dumped on their head unexpectedly whilst naked on a cold winter’s day.
The year 2020 was a watershed moment in my journey towards truth, and it was Bitcoin that served as my guide. As the world grappled with an unprecedented black swan event in March of that year, every asset, including bitcoin, took a severe hit. However, what followed in the subsequent months was the largest money-printing expedition in history. A tsunami of stimulus was pumped into the markets. The outcome was a K-shaped recovery. Small, honest brick-and-mortar businesses continued to suffer while many of the largest conglomerates not only rebounded but reached all-time highs. This ludicrous, short-sighted plan, known as quantitative easing, resulted in the most pronounced example of the Cantillon effect in human history, a fact that should have served as a wake-up call for anyone who was not already suspicious of the events surrounding the global financial crisis of 2008.
Since entering my post-bitcoin life, I’ve experienced a newfound coherence. The transition was not exactly instant, instead it has been a continuous process of discovering bitcoin over and over again, and I owe many of these enlightening moments to Knut Svanholm’s writing, for which I’m grateful.
While Knut’s books do not serve as a technical guide for Bitcoin, they provide a deep and philosophical introduction to a new era of money; the separation of money and state. The end of fiat money.
The creation of fiat money, a practice that emerged with the rise of central banking, has been the source of significant damage to human civilisation. Central banking, championed by Keynesianism, has granted immense power to centralized entities, allowing them to dictate fiscal policies and control the creation of money for billions of people. The very idea of a single entity wielding such vast authority and determining the economic fate of entire populations is utter madness. The state monopolizes money because it allows them to print money rather than having to directly tax people (but it still doesn’t stop them). Printing money is more easy, subtle and lucrative than direct taxation. And this continual erosion of purchasing power can be readily associated with the evident decline and deterioration of modern society.
At the heart of the issue is the importance of individual property rights. The money that individuals earn and save is their property, not the state’s. The state’s duty (should there be a need for it to exist) is to safeguard private property, not to continually debase or confiscate it. A centralized power that constantly devalues your hard-earned money and time by printing money is both morally and ethically wrong. Every individual has the right to turn their hard work into savings that they can rely on for the future.
In Bitcoin: Sovereignty through Mathematics, Knut not only delves into the fundamental principles underlying Bitcoin’s creation but also presents the groundbreaking concept of absolute scarcity. Bitcoin’s limited supply of 21 million and the impossibility of creating more due to its protocol creates a condition of absolute scarcity, a first in human history. Absolute scarcity, coupled with Knut’s poetic description of Bitcoin’s creation as "an immaculate conception," emphasizes its unique and revolutionary nature. The term "immaculate conception" highlights the fact that Bitcoin’s creation was not based on any pre-existing financial system but rather emerged from a set of mathematical principles that ensure its security and scarcity. The conditions that gave birth to Bitcoin will never be replicated, which further cements Bitcoin’s status as a one-of-a-kind element that will revolutionize the way we view and use money. Absolute scarcity aligns with the Austrian school of economics’ views on money, which argue that sound money should be scarce, durable, and difficult to counterfeit. Bitcoin ticks all the boxes for sound money, laying the ground for a genuine foundation to end the era of so-called cheap or easy money.
In the follow-up to this book, Bitcoin: Independence Reimagined1, Knut presents us, using plain logic and reasoning, the primitive constraints of the current fiat system and status quo governance. These structures, which we have so readily accepted, are gradually stripping us of our freedoms. By highlighting these shortcomings, he urges us to critically examine them and envision a future where we exercise greater autonomy over our lives, both financially and socially. Bitcoin’s simple and secure existence stands in contrast to the coercive and interventionist nature of the fiat system. Bitcoin is sincere; it neither favors nor opposes us. Bitcoin simply exists. Coming to terms with this truth is both humbling and liberating.
Knut’s writing, with its clear and elegant style, offers insightful guidance for those interested in exploring the deeper implications of Bitcoin beyond its function as a mere currency, recognizing it as a truly transformative breakthrough. A breakthrough that provides us with hope, a viable solution to reverse the degeneracy and decadence plaguing humanity.
Prince Philip of Serbia, 21st February 2023
Footnotes:
1. This foreword was originally written for a combined volume containing both Bitcoin: Sovereignty Through Mathematics and Bitcoin: Independence Reimagined.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 2fb77d26:c47a6ee1
2025-03-21 15:49:40
@ 2fb77d26:c47a6ee1
2025-03-21 15:49:40»Pershing II« – das war eines der ersten englischen Wörter, das mir als Kind geläufig war. Es handelt sich um die Typenbezeichnung einer US-Mittelstreckenrakete, einer nuklearen Boden-Boden-Rakete, die mit einem thermonuklearen Sprengkopf vom Typ W85 ausgestattet war, eine Reichweite von etwa 1.800 km hatte und somit von Süddeutschland aus Ziele im westlichen Russland binnen fünf Minuten erreichen konnte. Es war Anfang der 1980er Jahre. Die Zeit des Kalten Krieges. Eine Bezeichnung, die George Orwell mit seinem Essay »You and the Atomic Bomb« (Du und die Atombombe) im Jahre 1945 geprägt hatte. Die Fronten waren verhärtet.
Die westdeutsche Friedensbewegung protestierte lautstark gegen die Stationierung von Atomsprengköpfen auf heimischem Boden. Nachdem die im NATO-Doppelbeschluss vom 12. Dezember 1979 vereinbarten Abrüstungsverhandlungen zwischen den Atommächten jedoch erfolglos geblieben waren, entschied der Deutsche Bundestag am 22. November 1983, der Stationierung von US-Atomwaffen im Lande zuzustimmen. Diese war 1985 abgeschlossen und ganze 120 Exemplare der todbringenden Massenvernichtungswaffe in der Bundesrepublik verteilt worden. Außer Deutschland tat kein Land den USA diesen Gefallen.
Ich hatte die militärische Artikelbezeichnung »Pershing II« im Radio aufgeschnappt, welcher zu Hause fast durchgehend in Betrieb war, und später ein paar Bilder der Raketen in den Abendnachrichten gesehen. Noch gab es nur ARD, ZDF und das Regionalprogramm. Dementsprechend rar waren visuelle Informationen. Und aufgrund meiner frühen Begeisterung für Fluggeräte aller Art, zeichnete ich daraufhin ständig Raketen. Da ich außerdem bereits in diesem zarten Alter von fünf oder sechs Jahren extrem von Musik angetan war und durchweg versuchte, englische Songtexte, zum Beispiel von den Beatles, dem Klang der Stimmen folgend nachzusingen, übte auch der fremd klingende Begriff »Pershing II« eine gewisse Faszination auf mich aus.
Was mir meine Eltern diesbezüglich sagten oder erklärten, kann ich leider nicht mehr erinnern – als erklärte Pazifisten nahmen sie die latente Gefahr eines Nuklearkrieges aber sicher nicht mit der spielerisch-kindlichen Leichtigkeit, die ich im Umgang mit gemalten oder gebastelten Raketen an den Tag legte. Das Thema nukleare Kriegsführung beherrschte die Nachrichten dieser Zeit und erzeugte Angst. Denn Militärstrategen sprachen Anfang der 1980er Jahre allen Ernstes davon, dass der Atomkrieg zwischenzeitlich präziser und somit auch führbarer geworden sei. Damals wie heute – absoluter Irrsinn.
Neben der Berlin-Blockade 1948/1949 und der Kuba-Krise, war die Auseinandersetzung um die Stationierung von Mittelstreckenraketen in Westeuropa von 1979 bis 1983 also eine der drei kritischsten Phasen des Kalten Krieges.
Nie war die Welt einem fatalen wie letalen nuklearen Schlagabtausch der Supermächte näher als zu diesen drei Zeitpunkten in der Geschichte. Bis heute, so scheint es.
Denn die stetig eskalierende Ukraine-Krise rückt dieses vergessen geglaubte Horror-Szenario wieder in den Fokus der Öffentlichkeit. Polit-Darsteller wie der Maoist und China-Fan Robert Habeck äußern dieser Tage dummdreist, keine Angst vor einem Dritten Weltkrieg zu haben. Sogenannte Sicherheitsexperten erklären im ZDF, dass man sich vor Putins Bomben nicht fürchten solle, obwohl man in Mainz permanent Angst schürt und schon am 5. Mai 2022 titelt, »Moskau simuliert Atomangriff in Kaliningrad«.
Der »Beobachter Gesundheit« gibt Tipps dazu, wie man die Panik vor einem Atomkrieg mental in den Griff bekommen kann, während das deutsche BBK (Bundesamt für Bevölkerungsschutz und Katastrophenhilfe) der Bevölkerung bereits empfiehlt, im Zuge der Ukraine-Krise Notvorräte anzulegen und Marschgepäck bereitzuhalten. Auf der Webseite »wikiHow« findet sich ein sehr umfassender, bebilderter Ratgeber mit dem Titel »Einen Atomkrieg überleben«. Beim Lesen der zahlreichen, mutmaßlich nur bedingt hilfreichen Tipps zur Meisterung der nuklearen Apokalypse dürfte jedem normalen Menschen etwas mulmig werden.
Hofberichterstatter Ruprecht Polenz lässt sich beim Propaganda-Multiplikator ZEIT ONLINE am 30. April 2022 dennoch zu der wagemutigen Formulierung verleiten, »wer einen Atomkrieg verhindern will, darf Putin nicht gewinnen lassen«. Solch ein Statement ist nicht nur falsch und realitätsfremd, sondern zeugt gleichsam von der bewussten Negierung von Faktenlage und historischen Hintergründen zur Ukraine-Krise. Dabei könnte man es durchaus besser wissen.
Die RAND-Corporation, ein im Jahre 1948 gegründeter, einflussreicher Think Tank der US-Hegemonie, veröffentlichte zum Beispiel schon im Jahr 2019 ein vielsagendes, 354 Seiten umfassendes Strategiepapier unter der Überschrift »Overextending and Unbalancing Russia«. Frei übersetzt: Eine Strategie, um Russland überzustrapazieren und aus dem Gleichgewicht zu bringen – ökonomisch, militärisch und gesellschaftlich – mit dem singulären Ziel, die geopolitische Dominanz der Vereinigten Staaten zu bewahren. Ein durchdachtes Drehbuch zur finalen Erniedrigung und Bezwingung des ewigen Klassenfeindes sowie dem Erhalt der unipolaren Weltordnung, der Pax Americana.
Der Ansatz der RAND-Corporation: Die Osterweiterung der NATO forcieren, das Ansehen Russlands in der Welt zerstören, kostenintensives, nukleares Wettrüsten, die Ukraine bewaffnen, um einen militärischen Stellvertreterkonflikt mit Putin zu provozieren, um die ehemalige Sowjetunion anschließend mittels internationaler Sanktionen – legitimiert durch den brodelnden Krieg – finanziell in die Knie zu zwingen.
Verblüffend, wie sehr doch die im RAND-Strategiepapier aufgezeigte Vorgehensweise den aktuellen Geschehnissen an den Außengrenzen des Riesenreiches gleicht. Fast macht es den Anschein, als folgten die Geostrategen in Washington den Empfehlungen ihrer kostspieligen Think Tanks. Dies ließ sich auch im Zuge der Corona-Krise beobachten, die im Ablauf fraglos dem von der Rockefeller-Stiftung erarbeiteten Pandemie-Szenario »Lock Step« glich, wie Journalist Norbert Häring bereits am 28. Mai 2020 ausführlich berichtet.
Was das totalitäre Krisen-Drehbuch der RAND-Corporation nicht detailliert behandelt, sind die akuten Risiken einer potenziellen nuklearen Eskalation. Denn es endet mit dem möglichen Aufkeimen eines militärischen Konflikts und schließt schlicht mit dem Hinweis:
»Auch wenn die US-Armee nicht direkt an der Operation beteiligt ist, wird sie eine Schlüsselrolle bei der Abmilderung der Folgen spielen. Wie bereits erwähnt, bergen alle Maßnahmen, die der Schwächung Russlands dienen, einiges an Risiko. Infolgedessen werden das Abschreckungspotential sowie die operativen Fähigkeiten des US-Militärs in Europa gestärkt werden müssen. Es besteht die Möglichkeit, dass die Spannungen mit Russland zu einem Konflikt eskalieren.«
Die USA betrachten den Einsatz von Atomwaffen dabei offensichtlich als probates Mittel. Warum sonst modernisieren die Amerikaner seit Jahren ihr Arsenal und geben Milliarden US-Dollar dafür aus? Das macht eigentlich nur Sinn, wenn man plant, diese Waffen irgendwann einzusetzen. Der »Plot« für die Events nach dem Aufflammen einer militärischen Auseinandersetzung mit Russland ist vermutlich Verschlusssache und liegt nur Eingeweihten im Weißen Haus, Pentagon, CIA-Hauptquartier sowie den Verbündeten in EU und NATO-Hauptquartier vor.
Das ist bedauerlich. Denn ein Einblick in die aktuellen militärischen Planspiele und strategischen Szenarien der NATO-Hegemonie wäre hilfreich, um zu verstehen, ob die Arroganz des Westens tatsächlich einen Punkt erreicht hat, an dem man einen Atomkrieg in Kauf nehmen würde, um Russland und China auf ihre Plätze zu verweisen und im globalen Club der Technokraten am Kopfende zu sitzen. Um einen Konflikt der Systeme – Kapitalismus, Sozialismus, Kommunismus – handelt es sich nämlich nicht, auch wenn Medien dies gerne so darstellen, sondern um Machtkämpfe innerhalb der internationalen Oligarchie. Die drei Machtblöcke kämpfen um Vorherrschaft in der totalitären Weltordnung der nahen Zukunft.
Die Frage ist nur: Tun sie dies einvernehmlich – oder handelt es sich an Russlands Grenzen um ernsthafte, kriegerische Auseinandersetzungen, die in letzter Konsequenz militärisch entschieden werden müssen? Das RAND-Strategiepapier scheint davon auszugehen, dass Wirtschafts- und Informationskrieg, begleitet von NATO-Drohgebärden, ausreichen, um das Rennen zu Gunsten des Wertewestens zu entscheiden. Es gilt zu hoffen, dass diese Interpretation des Schriftstücks zutrifft. Ansonsten läuft die moderne Zivilisation Gefahr, sich in die Steinzeit zurückzubomben. Wie das aussieht, zeigt eindrücklich der Film »The Day After« (Der Tag danach) aus dem Jahre 1983.
Der zwei Stunden lange Streifen von Regisseur Nicholas Meyer ist bildgewaltig, beängstigend, ernüchternd und deprimierend. Er zeigt nicht nur, wie binnen weniger Tage aus einem Kalten Krieg ein Atomkrieg wird, sondern auch, was dessen schreckliche Folgen sind. Schon ein kurzer, etwas mehr als acht Minuten langer Zusammenschnitt macht klar, dass man ein absoluter Narr sein muss, um keine Angst vor thermonuklearen Angriffen zu haben.
Im Film gibt der US-Oberbefehlshaber nach der Zerstörung des NATO-Hauptquartiers den Befehl zum Atomschlag. Das entsprechende NATO-Protokoll wird aktiviert und die Raketensilos einsatzbereit gemacht. Das Drehbuch lässt offen, wer den Erstschlag führt. Klar ist, dass sobald die Sprengköpfe des Westens unterwegs sind, Russland einen Gegenangriff mit 300 Interkontinentalraketen auslöst und die Vereinigten Staaten in die Steinzeit bombt.
Überall im Land der unbegrenzten Möglichkeiten steigen feurige Atompilze in den Himmel. Metropolen werden in Sekunden ausradiert, Lebewesen, Pflanzen und Gebäude verdampfen in Feuersbrünsten um den Einschlagsort, ganze Landstriche werden vom Erdboden getilgt – und schon in den ersten Minuten nach Explosion der Nuklearsprengköpfe sterben weite Teile der Bevölkerung. 90 Millionen innerhalb weniger Stunden, wie eine Simulation mit dem etwas unheimlichen Titel »Plan A« der Princeton-Universität von 2019 berechnet hat.
Der eigentliche Horror beginnt allerdings erst. Denn die schlimmsten Szenen des Films sind jene, die den Zustand der Welt zwei Wochen nach den Atomschlägen zeigen. Im Land herrscht Anomie. Chaos und Zerstörung, wohin man schaut. Vorindustrielle Zustände. Die Städte sind unbewohnbar und die Überlebenden leiden an Strahlenkrankheit. Haare und Zähne fallen aus. Bei manchen binnen weniger Stunden oder Tage, bei anderen dauert es Wochen. Ein grausamer Tod auf Raten. Alles stirbt, siecht dahin. In den Ruinen entstehen Flüchtlingslager. Seuchen brechen aus. Militärkommandos erschießen willkürlich Menschen. Recht, Gerichte und Prozesse gibt es nicht mehr. Und um zu überleben, bewaffnen sich schlussendlich auch die Zivilisten und töten sich gegenseitig. Absolute Barbarei.
»The Day After« erklärt nicht, wer diesen Krieg gewinnt, nennt keinen Sieger. Vermutlich, weil Regisseur Nicholas Meyer schmerzlich bewusst war, dass es bei einem ausgewachsenen Atomkrieg keine Gewinner geben kann.
Er bedeutet das Ende der modernen Zivilisation. Nicht umsonst hat Albert Einstein früh vor militärischem Missbrauch entsprechender wissenschaftlicher Erkenntnisse gewarnt. So lässt der Streifen aus Zeiten das kalten Krieges auch das Ende offen. Kein Hollywood-Finale. Kein Happy End. Die beklemmenden Gefühle bleiben. Weder Will Smith noch James Bond tauchen auf, um die Welt in letzter Minute doch noch zu retten. Sie ist kaputt. Tot. Eine nuklear verseuchte Wüste. Kein Hoffnungsschimmer am Horizont.
Wer das Pech hatte, die Erstschläge zu überleben, stirbt langsam, aber sicher – und vor allem qualvoll.
Vielleicht sollten Spitzenpolitiker, Dogmatiker, Propagandisten und Kriegshetzer von heute sich diesen Film einmal in Ruhe anschauen, bevor sie leichtfertig derartige Optionen in Betracht ziehen. Ich habe »The Day After« nur ein einziges Mal in meinem Leben gesehen – wenige Monate, nachdem ich den Begriff »Pershing II« das erste Mal als kleines Kind im Radio hörte und meine Eltern neugierig fragte, was es damit auf sich hat – das war ausreichend. Die Eindrücke wirken bis heute. Ich bin mir auch mehr als dreißig Jahre später immer noch der unverrückbaren, indiskutablen Tatsache bewusst, dass es niemals zu einem Atomkrieg kommen darf. Jeder, der diesen Film gesehen, wird das unterschreiben.
Ich jedenfalls werde nie vergessen, wie ich eines nachts heimlich im dunklen Wohnzimmer der heimischen Dachwohnung ganz nahe vor dem Fernseher saß. Eigentlich durfte ich nur ein paar Mal in der Woche ausgewählte Kindersendungen anschauen. Aber meine Eltern schliefen bereits. Es muss circa 23:00 Uhr gewesen sein, denn nach den Spätfilmen war damals in der Regel Sendeschluss. Und das was war meist gegen eins oder halb zwei.
Just als ich den kleinen Röhrenfernseher anschaltete, begann »im Ersten« der bis heute in mir nachhallende Spielfilm. Der Tag danach. Zunächst begeistert von den vielen Raketen und irgendwie noch fasziniert von den mir bis dato unbekannten, riesigen Explosionen, die Atombomben auslösen, blieb ich gebannt sitzen. Wie versteinert. Bis zur Schlussszene, in der sich eine Handvoll strahlenverseuchter, zerrissener, verrottender Menschen, die kaum noch Haare auf dem Kopf haben und aussehen wie Zombies, in den staubigen Ruinen einer leeren Großstadt kraftlos in den Armen liegen und hilflos schluchzen. Die Kamera zieht auf. Dann Schwarzblende – und eine letzte, dünne, einsam flehende Stimme im Äther:
»Hello, is anybody there? Anybody at all?« (Hallo, ist da jemand? Irgendjemand?)
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ a012dc82:6458a70d
2025-03-21 15:42:13
@ a012dc82:6458a70d
2025-03-21 15:42:13In the ever-evolving landscape of finance and investment, Bitcoin has emerged as a pivotal player, challenging traditional notions of wealth and assets. Often likened to "digital gold," Bitcoin's unique properties have led some to view it in an even more nuanced light—as "digital pearls." This article delves into how Bitcoin is redefining wealth in the digital age, drawing parallels with historical assets and exploring its impact on modern investment strategies. The comparison to digital pearls is not merely poetic but serves as a metaphor for the transformation of value from physical to digital realms. This shift is not just technological but cultural, reflecting changing attitudes towards what constitutes real wealth in our increasingly digital world.
The digital age has brought about a profound transformation in how we perceive and interact with value. Traditional assets like real estate and precious metals have been joined by a new class of digital assets, from cryptocurrencies to NFTs, reshaping the landscape of investment and wealth. This shift is not merely about the assets themselves but represents a broader change in societal values and economic structures. The rise of digital assets challenges the monopoly of physical assets as the sole bearers of value, suggesting a future where wealth is as much about information and digital ownership as it is about tangible possessions.
Table of Contents
-
The Evolution of Value: From Tangible to Digital
-
Bitcoin: The Digital Pearls of the 21st Century
-
Redefining Wealth and Investment
-
The Future of Digital Wealth
-
Conclusion
-
FAQs
The Evolution of Value: From Tangible to Digital
Historically, the concept of wealth has been tied to tangible assets: land, gold, and precious stones. These assets were prized for their scarcity, durability, and, in many cases, their beauty. However, the digital age has ushered in a new era of value, one where intangible assets like data, software, and digital currencies have become just as, if not more, valuable than their physical counterparts. This transition from tangible to intangible assets marks a significant shift in the global economy, reflecting changes in how we work, live, and interact with the world around us. The value is increasingly found not in physical objects but in the data and digital experiences they enable.
Bitcoin, since its inception in 2009, has epitomized this shift. Created as a decentralized digital currency, it offers a new form of wealth that is secure, transferable, and free from the control of any government or institution. Its blockchain technology ensures transparency and immutability, making it a trustworthy digital asset. This revolutionary approach to currency and wealth has not only challenged traditional financial systems but also redefined what constitutes value in the 21st century. Bitcoin represents a paradigm shift, moving us away from centralized financial systems and towards a more democratized form of wealth.
Bitcoin: The Digital Pearls of the 21st Century
Just as pearls were once a symbol of wealth and status, Bitcoin has emerged as a modern equivalent in the digital realm. The comparison extends beyond mere value; it reflects a shift in what society considers precious. Pearls, formed in the depths of the ocean, were valued for their rarity and beauty. Similarly, Bitcoin, 'mined' through complex computational processes, holds value due to its finite supply and the energy invested in its creation. This digital creation process, known as mining, parallels the natural formation of pearls, adding a layer of intrigue and value to Bitcoin's narrative.
The story of Maisie Plant and her pearl necklace, traded for a New York mansion, illustrates the fluid nature of value. Just as the perceived worth of pearls has fluctuated over time, Bitcoin's value is also subject to change. However, its digital nature and global accessibility mark a departure from traditional assets, offering a new form of wealth that transcends physical boundaries. This story not only highlights the changing nature of value but also serves as a reminder of the subjective and evolving nature of what society deems valuable.
Redefining Wealth and Investment
Bitcoin's rise challenges conventional investment wisdom. Traditional portfolios, heavy on stocks, bonds, and real estate, are being reevaluated as investors seek to diversify with digital assets. Bitcoin's volatility, while often cited as a risk, also presents opportunities for significant returns, drawing parallels with early investments in tech giants like Amazon and Google. This shift towards digital assets represents a broader change in investment strategies, reflecting a new era of wealth where digital assets play a central role.
Moreover, Bitcoin's decentralized nature offers a hedge against inflation and economic instability. In countries facing currency devaluation or financial crisis, it has become a means of preserving wealth, akin to how gold has been used historically. This aspect of Bitcoin highlights its potential not just as an investment but as a tool for economic empowerment and stability. The ability to store and transfer wealth independently of traditional financial systems is a powerful feature, particularly in regions where those systems are unreliable or inaccessible.
The Future of Digital Wealth
As we move further into the digital age, the definition of wealth continues to evolve. Bitcoin, and the broader category of cryptocurrencies, are at the forefront of this shift. They challenge individuals and institutions to rethink what constitutes an asset and how value is assigned and preserved. This evolution is not without its challenges and controversies, but it also offers unprecedented opportunities for innovation and growth.
The integration of Bitcoin into mainstream finance, through ETFs, futures, and other investment vehicles, signifies a growing acceptance of digital currencies as a legitimate form of wealth. However, as with all investments, there are risks and uncertainties. The regulatory landscape, technological advancements, and market dynamics will all play a role in shaping the future of Bitcoin and digital wealth. This future is not just about Bitcoin itself but about the broader implications of a world where digital assets are as common and valued as traditional ones.
Conclusion
Bitcoin's comparison to "digital pearls" offers a compelling framework for understanding its place in the modern economy. Just as the value of pearls once reflected societal trends and desires, so too does Bitcoin capture the zeitgeist of the digital age—a symbol of a new era of wealth that is decentralized, digital, and diverse. As we navigate this new landscape, the story of Bitcoin is far from over; it continues to challenge, redefine, and inspire the future of finance. The journey of Bitcoin from an obscure digital currency to a new form of digital wealth mirrors the broader transformation of the economy and society in the digital age.
FAQs
Why is Bitcoin compared to gold or pearls? Bitcoin is often compared to gold because it shares characteristics such as scarcity, durability, and being a store of value. The comparison to pearls, however, emphasizes its unique, evolving status as a coveted asset, reflecting shifts in societal values and the concept of wealth.
How does Bitcoin work? Bitcoin transactions are verified by network participants (miners) and recorded in blocks on the blockchain. Users can send and receive bitcoins using digital wallets. The supply of Bitcoin is capped at 21 million, ensuring its scarcity.
Is Bitcoin a good investment? Bitcoin's value can be highly volatile, making it a risky investment. However, some view it as a hedge against inflation and a potential part of a diversified investment portfolio. As with any investment, it's important to do thorough research and consider your financial situation and risk tolerance.
Can Bitcoin be converted into real money? Yes, Bitcoin can be exchanged for traditional currencies through online exchanges, peer-to-peer platforms, and some retail locations. The exchange rate varies based on market conditions.
Is Bitcoin legal? The legality of Bitcoin varies by country. Some countries have embraced it, while others have imposed restrictions or outright bans. It's important to check the regulations in your specific location.
What is the future of Bitcoin? The future of Bitcoin is uncertain and subject to various factors, including technological developments, regulatory changes, and market dynamics. It continues to gain acceptance and has sparked a global conversation about the nature of money and the future of financial systems.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ cc601241:181cd0d2
2025-03-21 15:11:09
@ cc601241:181cd0d2
2025-03-21 15:11:09
- Money doesn't grow on trees
- There is no such thing as a free lunch
- Energy cannot be created or destroyed
What if I told you these are three different ways of saying the exact same thing?
If you recognize that money is a unit of account, a medium of exchange, and a store of value, then it's only natural to accept that money at its most abstract formulation is simply information:
"Money is information. It is information we collect about the cost of things. We use it to quantify the world around us. To allow us to figure out what our things are worth in relation to other things. The soundness of a money measures its reliability in storing value over time. Sound money is reliable; you can count on it having a certain value today and in the future. Sound money allows us to determine the proper price of goods and services. Unsound money makes it difficult to figure out what anything should cost. Sound money accurately stores information about the cost of things. Sound money is a sensible store of information."
So long as fiat money can be printed ad infintum to bankroll the military industrial complex, why would we consider the US dollar to be accurate information? Why would we be surprised to see the negative externalities of dark money, regulatory capture, institutional usury, systemic seigniorage, and pervasive rent-seeking happening everywhere? Why wouldn't we start questioning the ripple effects of the Cantillon effect? Why wouldn't the rest of the world's economic actors that operate downstream of the dollar supply not live in constant fear, uncertainty, and doubt? If not resentment, cynicism, and desperation?
"Infinite money creates a scarcity mindset in almost everyone. Most people observe the rising cost of living and experience the feeling of fear or even panic. Fear of the unknown, fear of the future. Uncertainty about making ends meet. Leaky money promotes hoarding, individualism, and fast food culture, where everything is built as quickly and cheaply as possible."
If money is no longer a reliable measure of value but simply a means of control and extraction, how can humanity collaborate or organize or build together? How can we incentivize cooperation? How can we coincide our wants? How can we hope at all?
"Money is a medium of communication. It is one of the most common ways we communicate. Money is a sense-making apparatus. In the broken money world, a subtle distortion becomes ingrained in the foundational layer of sense-making, leading to a systemic corruption of all communication within the system."
Enter a pseudonymous, Good Samaritan, white hat coder: Satoshi Nakamoto.
A cypherpunk who asked a very simple question...

What if there was a money that was not backed by the Federal Reserve or 11 aircraft carriers and 5,000 nuclear warheads and the monopoly of violence? What if that money was backed not by physical scarcity (gold) or political scarcity (fiat) but by mathematical scarcity (blockchain aka timechain)? What if that money operated on principles like "rules without rulers" and "don't trust, verify?" What if we finally had an Occam's razor for economics?

What if that money were backed by the currency of the universe itself: energy?
"Bitcoin's immaculate conception presents the possibility that it has always existed. The genesis block could be viewed merely as the first time we started recording Bitcoin. Knut Svanholm has discussed the idea that Bitcoin might be an element with an atomic weight of zero and that the discovery of Bitcoin is better described as the discovery of our ability to observe this element.
For an element to have an atomic weight of zero, it must be void of protons or neutrons, possessing only electrons. Element zero is purely information. If element zero had always existed prior to our ability to measure it, that means it would have existed back to the time of Lao Tzu. If true, it means there could be undiscovered methods for gauging that information. The understanding of how to observe element zero might not be a binary event.
The interesting thing about observing element zero is that the process requires energy. Producing element zero requires a predictable amount of energy. Interacting with element zero requires energy. By spending Bitcoin, we capture a measurement of the value of the thing we spent it on, priced in energy; because element zero requires energy to produce, we can almost think of pricing other things in Bitcoin as pricing the energy spent in creating them. Element zero transfers energy."
All economy is just the transformation of energy into value. If one accept this definition of economics, then Bitcoin is the purest conversation of energy into value. This would explain why the world is seeing an emergent first principle emerge known as the Joule Paradox:
"Energy sets the value of bitcoin and bitcoin sets the value of energy."

Therefore, Bitcoin is the only money that obeys the laws of thermodynamics.
If we have a transparent public ledger of information backed by energy, we could safely call this document the most objective database in the entire world because energy is the only thing in the entire universe that no one can fake.
That's the power of triple entry bookkeeping. No one can cook the books anymore.

Once humanity is able to guarantee the separation of Money and State, suddenly everyone has a way to protect their own time and energy without having to trust a third party. We are no longer slaves to "absolute power corrupts absolutely". We are no longer beholden to the powers that be. Humanity finally has an incorruptible, immutable, unconfiscatable, permissionless, borderless, open source money available to all.
In a world of manipulated markets, self-sovereignty starts with sound money.
Believe it or not, the thesis of The Dao of Bitcoin: Towards a Cosmology of Energy Money (by Scott Dedels—which I have been quoting throughout this article) states that Bitcoin is "perfect money" (or "daomoney" as he coins it) for the following reason:
Bitcoin = time = money = energy = Bitcoin
There is nothing more valuable than protecting your time & energy. But no one can force you to believe that. Self-sovereignty is a game of consent. The first act of financial freedom is to choose it. The deeper into the Bitcoin rabbithole you go, the sooner you'll have the unmistakable epiphany:
Bitcoin is a strange game where the only winning move is to play.
Bitcoin is just money without the Bullshit. No CEO, no country, no committee, no corporation, no cartel, no council, no conglomerate, no counter-party, no church, no cult of personality. Just pure P2P energy transfer. That's the beauty of freedom money. That's the reason for energy money. That's the answer to the game theory.
With absolute mathematical scarcity, individuals can finally afford an abundance mindset.
For the sovereign individual, all you have to do is nothing but HODL.
That's financial wu wei.
That's energy money that aligns with the universe & vibes with the Dao.

-
 @ 43bb87e2:12cc9cb8
2025-03-21 15:06:52
@ 43bb87e2:12cc9cb8
2025-03-21 15:06:52There was once a little girl that got into some expensive golden wrapping paper, and her father got upset. In his anger, he yelled at his little daughter for wrecking the expensive wrapping paper. The daughter then decided to use the ripped and wrecked wrapping paper to wrap a gift for someone. Again, the father let his anger take over and got mad at the little girl for using the ripped paper for the gift wrapping. The next morning, the little girl presented the tattered, golden wrapped box to her father and said this is for you, Dad. He opened the wrapped box and saw that the box was empty inside. The dad again got angry and told his daughter that when you give a gift to someone, there is supposed to be something inside of it. The little girl, in tears, looked up at her father and said, but it is full daddy. I blew kisses into it until it was completely full. The father then broke down and started crying. He dropped to his knees and put his arms around his precious and innocent daughter. He desperately apologized to her for his anger and continued to ask for her forgiveness. A short while after this, his daughter was taken from this earth because of an accident. The father kept the golden wrapped box next to him for the rest of his life to remind him of the love he had from his daughter.
Nothing else matters in this world or even comes close to the unconditional love that our children and family have for us.
With life being so busy, don’t you dare forget, what really matters in this world. And you be sure to take care of your loved ones, family, and friends.
For we do not know when the last day we will be on this earth.
CHERISH EVERY MOMENT AND LOVE WITH ALL YOUR HEART!
DO NOT LET ANGER RULE OVER YOU.
TELL EVERYONE IN YOUR LIFE,
THAT YOU LOVE THEM!
TELL THEM TODAY!
DO IT NOW!
LOVE YOU ALL, BE BLESSED!
-
 @ da0b9bc3:4e30a4a9
2025-03-21 13:58:11
@ da0b9bc3:4e30a4a9
2025-03-21 13:58:11It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Let's get it!
This song never doesn't put me in a good mood.
https://youtu.be/fnwZeLdLPdQ?si=ZlbiGSp2r6DtMx6P
originally posted at https://stacker.news/items/920041
-
 @ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11
@ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11Table of Contents
- Introduction
- Overview of the Nostr Ecosystem
- Current Use Cases and Quantitative Metrics
- User Adoption Metrics
- Network Resilience and Decentralization
- Operational Challenges and Scalability
- Replication Overhead and Bandwidth Issues
- Relay Downtime and Financial Sustainability
- Market Disruption and Sentiment
- Disrupting Twitter and Centralized Social Platforms
- Impact on Decentralized Social Media and Censorship Resistance
- Future Trends and 5-Year Outlook
- Innovative Protocol Developments
- Quantitative Forecasting and Diffusion Modeling
- Networking and Integration with Emerging Technologies
- Conclusions and Strategic Recommendations
1. Introduction
The Nostr ecosystem has emerged as a powerful decentralized alternative to traditional social media networks, particularly as a potential disruptor of Twitter and other centralized—and even existing decentralized—social media platforms. Developed using a protocol based on cryptographic key pairs and a multi-relay system, Nostr is unique in its provision of censorship resistance and user sovereignty. In this report, we provide a detailed analysis of the current state, scalability challenges, and market disruption potential of Nostr, followed by speculative insights on its trajectory over the next five years.
2. Overview of the Nostr Ecosystem
Launched in 2022, Nostr (Notes and Other Stuff Transmitted by Relays) has rapidly gained traction as an open and decentralized social network. Some of the core features include:
- Decentralized Communication: Relying on independent relays across multiple countries and autonomous systems, Nostr offers an architecture that ensures posts are not stored on a single centralized server.
- Censorship Resistance: With cryptographic authentication and a decentralized relay structure, content censorship becomes significantly more difficult than in traditional networks.
- User Sovereignty: Empowering users with cryptographic key pairs allows for enhanced privacy and data ownership.
- Wide Geographic Distribution: The ecosystem spreads over 44 countries and 151 autonomous systems, underscoring its global reach.
Notable endorsements from figures such as Jack Dorsey, Edward Snowden, Vitalik Buterin, and Sen. Cynthia Lummis have bolstered its reputation as an experimental yet promising alternative to centralized social platforms.
3. Current Use Cases and Quantitative Metrics
User Adoption Metrics
- User Base: In just two years, the Nostr network has attracted over 4 million users, a significant figure given its nascent stage and decentralized nature.
- Content Generation: With over 60 million posts, the volume of content mirrors the rapid adoption and active usage seen in more centralized models.
- Post Replication: Empirical measurements indicate that there are 17.8 million text notes among these posts, replicated on an average of 34.6 relays per post. This level of replication underlines robust resilience and availability even if significant portions of the network experience downtime.
Network Resilience and Decentralization
- Global Distribution: Nostr’s decentralized network ensures high availability with >90% post accessibility even under simulated network failures (e.g., removal of key relays or autonomous systems).
- Robustness: The dispersion across 712 relays illustrates that decentralization is not only a design choice but also a working reality, which contributes to the network’s reliability.
4. Operational Challenges and Scalability
While the Nostr ecosystem demonstrates significant promise, it faces noteworthy operational challenges.
Replication Overhead and Bandwidth Issues
- Excessive Redundancy: Detailed studies have shown that nearly 98.2% of retrieval traffic is redundant. In practice, this equates to an estimated 144 TiB of unnecessary bandwidth consumption.
- Optimization Proposals: To mitigate these inefficiencies, there's a proposal to limit post replications from 34.6 relays to between 10 and 20 relays per post. This could reduce redundant data copies by between 380 million to 480 million instances, potentially lowering operational costs and improving bandwidth utilization.
- Scaling Concerns: With a projected network load of 10 million events per day (or approximately 2 TB annually), the throughput requirement of ~115 TPS is putting a strain on the current architecture. This has led to debates on whether solutions like the current outbox mechanism are sufficient or if further fundamental redesigns and emergent moderation systems are needed.
Relay Downtime and Financial Sustainability
- Relay Stability: Data indicates roughly 20% of relays suffer from significant downtime (exceeding 40% operational time), and 132 relays have been classified as 'dead'. This is a concern for maintaining network integrity.
- Economic Model Challenges: With 95% of free-to-use relays unable to cover operational costs due to minimal zap-based income, there is an urgent need for innovative monetization or community funding models to ensure long-term sustainability.
5. Market Disruption and Sentiment
Nostr is positioned as both a disruptor to traditional centralized social platforms—most notably Twitter—and a catalyst for change within decentralized social media.
Disrupting Twitter and Centralized Platforms
- User Shift: While Twitter remains the most well-known platform, the high-profile endorsements and robust user base of Nostr indicate that there is both market intrigue and a gradual shift among early adopters. Disruption here is measured not only in user numbers but also in the paradigm shift towards decentralized content distribution.
- Market Penetration: Current metrics (4 million users, 60 million posts) suggest that Nostr is challenging Twitter's centralized model insofar as it appeals to users prioritizing censorship resistance, data sovereignty, and resiliency against centralized failures. However, mainstream adoption on par with Twitter is still not realized, and there remains a gap in user experience and feature richness.
Impact on Decentralized Social Media and Censorship Resistance
- Complementary Integrations: As decentralized social media ecosystems continue to mature, integration between Nostr and other censorship-resistant platforms is increasingly likely. This can include interoperability protocols, shared identity management systems, and cross-platform content replication.
- Comparative Advantage: Nostr's network design offers unique advantages over other decentralized social media, particularly in its straightforward, relay-based communication protocol. This positions Nostr to potentially serve as an underpinning technology for a broader decoherent ecosystem of social networks.
- Sentiment Toward Scalability Innovations: Discussions around scaling Nostr often focus on the balance between ensuring redundancy (for resilience) and reducing overhead (for efficiency). The sentiment is one of cautious optimism: while outbox solutions offer a stopgap, many experts advocate for more fundamental architectural redesigns in the long-term.
6. Future Trends and 5-Year Outlook
Looking forward, the evolution of Nostr will likely be shaped by several interrelated trends and emerging technical innovations.
Innovative Protocol Developments
- Decentralized Identity and Reputation Mechanisms: The next phase may see the introduction of distributed reputation systems and rating mechanisms that aid in spam management and improve trustworthiness without compromising decentralization.
- Optimistic Replication and Selective Mirroring: Innovations such as selective content mirroring and event pruning will be key in managing bandwidth and storage demands while remaining true to the decentralized philosophy.
Quantitative Forecasting and Diffusion Modeling
- Forecast Models: By integrating modified Bass diffusion models and learning curve effects, predictions suggest that Nostr can potentially spur significant market disruption within five years. Recent studies indicate that forecasting models in disruptive technology fields have reached accuracies of up to 82% for demand projections.
- Hybrid Quantitative Techniques: Leveraging methods like LDA2Vec and patent citation network analysis, combined with multi-criteria decision-making models (as seen in extended UTAUT approaches), will be crucial for accurately estimating future adoption and cost efficiencies.
- Metrics to Monitor: Future research should focus on user growth rates, relay uptime percentages, cost reductions achieved through replication optimizations, and overall sentiment analysis using advanced deep learning architectures that overcome traditional pitfalls (e.g., sarcasm and multipolarity in text data).
Networking and Integration with Emerging Technologies
- Integration with Other Decentralized Platforms: One promising avenue is exploring cross-platform interoperability with other decentralized and blockchain-based social networks, which could lead to a more cohesive ecosystem. This would not only enhance user experience but also enable shared security and moderation frameworks.
- Next-Generation Relays: The deployment of relays that are more resilient through redundancy optimization and financial sustainability models (perhaps incorporating micro-transaction revenue models or community-driven funding) is another critical area. Such improvements could mitigate the issues of relay downtime and excessive network overhead.
- Contrarian Approaches: A contrarian perspective suggests that instead of building on current frameworks, a radical overhaul of the network architecture might be considered, potentially by leveraging novel distributed ledger technologies or leveraging a hybrid centralized-decentralized model during the transition phase to ensure smoother scaling.
7. Conclusions and Strategic Recommendations
The Nostr ecosystem represents a significant stride toward decentralized, censorship-resistant social media. While its current market adoption and technical design offer a robust alternative to centralized platforms like Twitter, several challenges must be addressed for sustained growth and disruption:
-
Optimization of Data Replication: Reducing redundant data transfers without compromising resilience is essential. Limiting the replication factor and exploring optimistic retrieval mechanisms could provide a balance between availability and efficiency.
-
Relay Stability and Sustainability: With nearly 20% of relays experiencing significant downtime, innovative financial and technical models (such as micro-payments and community funding) should be deployed to enhance the operational reliability of network nodes.
-
Enhanced Moderation and Reputation Systems: Emerging strategies for decentralized content moderation and reputation management could reduce spam and improve content quality while preserving the open nature of the network.
-
Interoperability with Other Decentralized Platforms: Fostering integration with other emerging systems could accelerate market disruption across the broader spectrum of social media.
-
Future-Proofing Through Quantitative Forecasting: Continual adoption of cutting-edge forecasting models and machine learning techniques to measure sentiment and track network metrics is imperative for proactive evolution.
-
Exploring Contrarian Innovations: In addition to incremental changes, it is important not to discount radically new architectures that may emerge from ongoing research in distributed systems and blockchain technologies.
Final Outlook
In the coming five years, Nostr has the potential to disrupt not only Twitter but also the broader landscape of both centralized and decentralized social media. Although the current architecture presents significant scaling challenges, proactive investments in replication optimization, relay stability, and cross-platform integration will likely propel the network into a more mature phase of adoption. The ecosystem will benefit from a dual approach that combines both evolutionary improvements and revolutionary changes, ensuring that it remains robust while meeting the demands of a growing, globally distributed user base.
Appendices
Appendix A: Data and Metrics Summary
- User Base: ~4 million
- Post Volume: >60 million posts
- Average Relay Replication: ~34.6 replicas per post
- Geographical Distribution: 44 countries, 151 autonomous systems
- Bandwidth Waste: ~144 TiB due to redundancy
- Network Load: 10 million events/day (~2TB/year)
- Throughput Requirement: ~115 TPS
Appendix B: Key Technical Proposals
- Replication Control: Limit copies to 10–20 relays for optimal efficiency.
- Selective Mirroring: Implement event pruning and selective content mirroring.
- Decentralized Reputation Systems: Develop distributed rating mechanisms to enhance distributed moderation.
Appendix C: Forecasting and Quantitative Methods
- Diffusion Modeling: Modified Bass models with multi-market dynamics.
- Hybrid Quantitative Techniques: Integration of machine learning (CNN-LSTM, LDA2Vec) with multi‐criteria decision models.
Recommendations for Further Research
- Investigate the comparative performance of alternative replication strategies in decentralized networks.
- Explore funding models that can sustain relay operations without compromising neutrality or decentralization.
- Conduct long-term sentiment analysis using advanced neural architectures to understand evolving user attitudes.
- Evaluate the prospective benefits of radical design overhauls versus incremental enhancements in ensuring network scalability.
This report is intended for expert analysts and researchers in decentralized network systems and social media disruption. It synthesizes current empirical findings with speculative insights to inform future strategies and academic inquiry.
Sources
- https://www.voltage.cloud/blog/exploring-6-use-cases-of-nostr-beyond-messaging
- https://arxiv.org/abs/2402.05709
- https://arxiv.org/html/2402.05709v1
- https://papers.ssrn.com/sol3/Delivery.cfm/5146515.pdf?abstractid=5146515&mirid=1
- https://matchnode.com/blog-and-podcasts/mastering-paid-social-media-advertising-a-comprehensive-guide/
- https://blockworks.co/news/jack-dorsey-app-to-disrupt-twitter
- https://www.securities.io/nostr-a-better-twitter/
- https://medium.com/@jasminedevv/battle-of-the-decentralized-twitter-alternatives-c9f51114614a
- https://www.murrayrudd.pro/nostrs-relay-revolution-scaling-decentralized-networks-for-growth/
- https://github.com/nostr-protocol/nips/issues/75
- https://news.ycombinator.com/item?id=42758579
- https://www.toptal.com/deep-learning/4-sentiment-analysis-accuracy-traps
- https://www.researchgate.net/publication/3076742_Forecasting_the_Market_Diffusion_of_Disruptive_and_Discontinuous_Innovation
- https://www.globenewswire.com/news-release/2025/03/17/3043701/0/en/United-States-Online-Household-Furniture-Market-Report-2025-2029-Analysis-of-Price-Sensitivity-Lifecycle-Customer-Purchase-Basket-Adoption-Rates-and-Purchase-Criteria.html
- https://northeast.newschannelnebraska.com/story/52583550/laser-welding-market-growth-industrial-adoption-rate
- https://www.sciencedirect.com/science/article/am/pii/S2405896323014453
- https://www.marketsandmarkets.com/Market-Reports/industry-5-market-35376359.html



























































