-

@ da0b9bc3:4e30a4a9
2025-02-24 06:35:50
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/895451
-

@ 57d1a264:69f1fee1
2025-02-24 04:10:33
As your involvement in open source design increases, you’ll face challenges that go beyond basic UI work. From creating scalable design systems to mentoring new contributors, these advanced areas require strategic thinking, collaboration, and leadership.
This chapter dives into these complexities, helping you handle real-world situations while continuing to grow as a designer.
- Championing Design Initiatives
- Creating and Maintaining Design Systems
- Handling Complex Design Challenges
- Conducting In-Depth User Research
- Balancing Open Source Work with Other Commitments
- Navigating Project Dynamics
-0 Mentoring New Designers
Read more:
https://opendesign.guide/10-advanced-topics
```
#design #nostrdesign #bitcoindesign #ln #grownostr #asknostr #zap #btc #bitcoin #nostr #cashu
```
originally posted at https://stacker.news/items/895377
-

@ c11cf5f8:4928464d
2025-02-23 20:42:52
Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about?
If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on.
originally posted at https://stacker.news/items/895134
-

@ 3ffac3a6:2d656657
2025-02-23 19:40:19
## Renoters: Proposal for Anonymous Event Relaying in Nostr
*This document is a proposal and not an official NIP.*
This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message.
### **Motivation**
While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity.
In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools.
### **Proposed Solution**
Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps:
1. **Event Creation:** The user creates the Nostr event they wish to publish.
2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen.
3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order:
- A *new* random Nostr private key (`sk_wrapper`) is generated.
- The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key).
- A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing.
4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path.
5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter.
6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network.
### **Example**
Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3.
1. Alice creates her event.
2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`.
3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`.
4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`.
5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`.
6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`.
7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`.
8. Alice publishes this final wrapper event.
R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event.
### **Renoter Incentives (using Cashu)**
To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism.
- **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it.
- **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it.
- **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service.
- **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed.
- **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means.
### **Security Threats and Mitigations**
- **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce:
- Random delays in event relaying.
- Dummy packets to complicate statistical analysis by malicious observers.
- **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again.
- **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network.
- **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat.
### **Operational Considerations**
- **Renoter Reliability:** The reliability of the Renoter network is crucial.
- **Latency:** Relaying through multiple Renoters will introduce latency.
- **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure.
This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability.
### **References**
- **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563)
- **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf)
- **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr)
- **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/)
- **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/)
- **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf)
#Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development
-

@ 2e8970de:63345c7a
2025-02-23 18:38:06
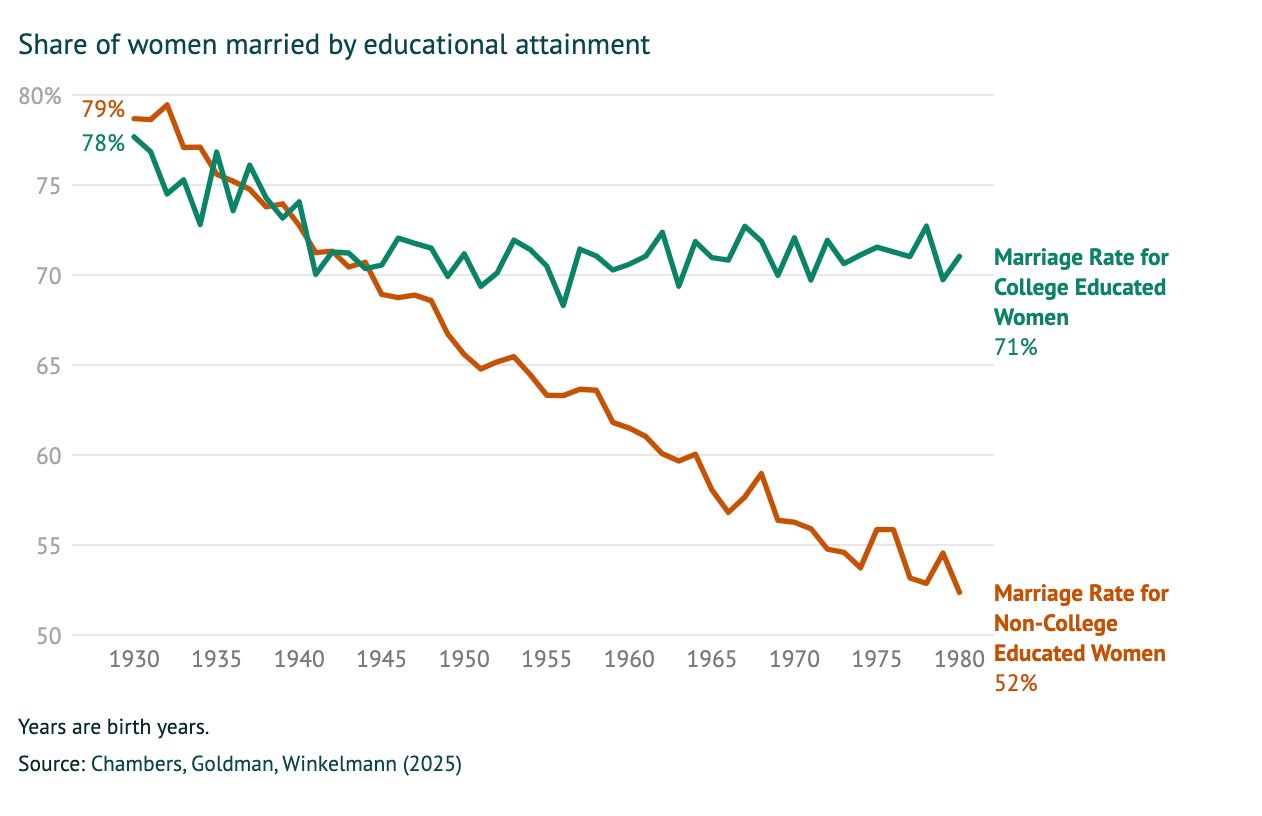
> 1 in 5 women with a BA are willing to marry a man without one
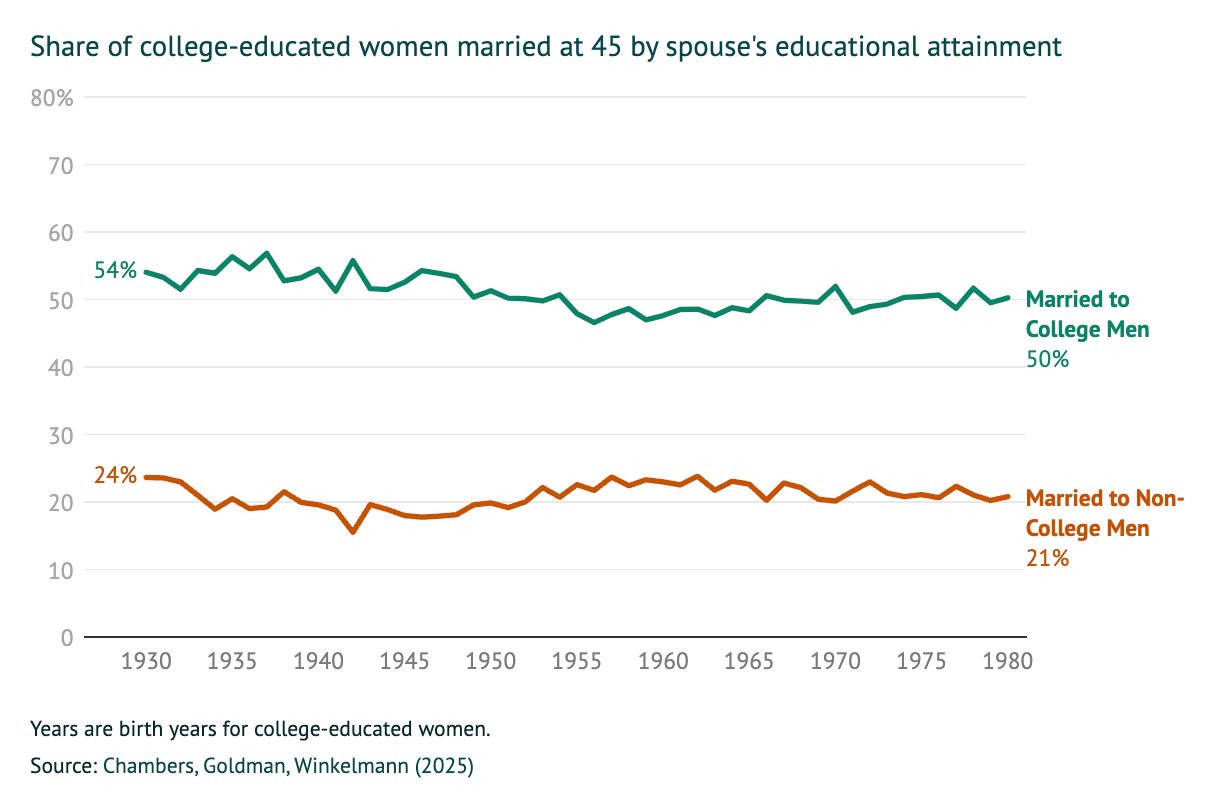
> But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically
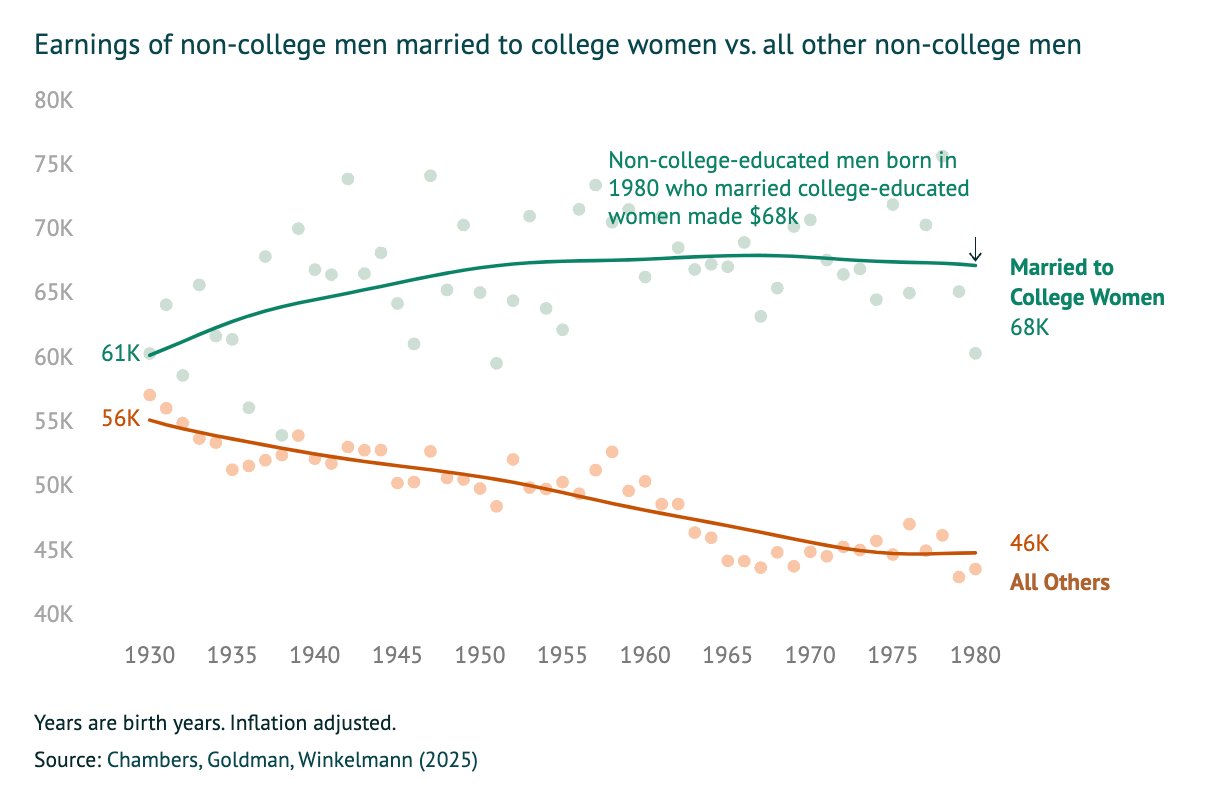
> Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married

https://aibm.org/research/will-college-educated-women-find-someone-to-marry/
originally posted at https://stacker.news/items/895044
-

@ da0b9bc3:4e30a4a9
2025-02-23 07:08:22
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/894609
-

@ e3ba5e1a:5e433365
2025-02-23 06:35:51
My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\.
Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group.
Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people.
As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them.
For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement.
There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope).
And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions.
A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join.
Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves.
When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view.
Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will.
My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed.
-

@ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46
Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick.
Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions.
Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them.
Here's the current state of the competition with your max possible score next to your nym:
| Contestant | MVP | Champ | All NBA | | | | |
|--------------|------|---------|----------|-|-|-|-|
| @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson |
| @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson|
| @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA |
| @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA|
| @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA|
| @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson|
| @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson|
| @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA|
| @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA|
| @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA|
| @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson |
| @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA|
| @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA|
| @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA|
**Prize**
At least 6k (I'll keep adding zaps to the pot).
If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details.
originally posted at https://stacker.news/items/894412
-

@ 6260f29f:2ee2fcd4
2025-02-22 22:46:27
# A title before again
```js
import React, { useEffect, useState } from 'react';
import dynamic from 'next/dynamic';
import { Dialog } from 'primereact/dialog';
import { track } from '@vercel/analytics';
import { LightningAddress } from '@getalby/lightning-tools';
import { useToast } from '@/hooks/useToast';
import { useSession } from 'next-auth/react';
import { ProgressSpinner } from 'primereact/progressspinner';
import axios from 'axios';
import GenericButton from '@/components/buttons/GenericButton';
import useWindowWidth from '@/hooks/useWindowWidth';
import { useRouter } from 'next/router';
const Payment = dynamic(
() => import('@getalby/bitcoin-connect-react').then((mod) => mod.Payment),
{ ssr: false }
);
const ResourcePaymentButton = ({ lnAddress, amount, onSuccess, onError, resourceId }) => {
const [invoice, setInvoice] = useState(null);
const [isLoading, setIsLoading] = useState(false);
const { showToast } = useToast();
const { data: session, status } = useSession();
const [dialogVisible, setDialogVisible] = useState(false);
const router = useRouter();
const windowWidth = useWindowWidth();
const isMobile = windowWidth < 768;
useEffect(() => {
let intervalId;
if (invoice) {
intervalId = setInterval(async () => {
const paid = await invoice.verifyPayment();
if (paid && invoice.preimage) {
clearInterval(intervalId);
// handle success
handlePaymentSuccess({ paid, preimage: invoice.preimage });
}
}, 2000);
} else {
console.error('no invoice');
}
return () => {
if (intervalId) {
clearInterval(intervalId);
}
};
}, [invoice]);
const fetchInvoice = async () => {
setIsLoading(true);
try {
const ln = new LightningAddress(lnAddress);
await ln.fetch();
const invoice = await ln.requestInvoice({ satoshi: amount });
setInvoice(invoice);
setDialogVisible(true);
} catch (error) {
console.error('Error fetching invoice:', error);
showToast('error', 'Invoice Error', 'Failed to fetch the invoice.');
if (onError) onError(error);
}
setIsLoading(false);
};
const handlePaymentSuccess = async (response) => {
try {
const purchaseData = {
userId: session.user.id,
resourceId: resourceId,
amountPaid: parseInt(amount, 10)
};
const result = await axios.post('/api/purchase/resource', purchaseData);
if (result.status === 200) {
track('Resource Payment', { resourceId: resourceId, userId: session?.user?.id });
if (onSuccess) onSuccess(response);
} else {
throw new Error('Failed to update user purchases');
}
} catch (error) {
console.error('Error updating user purchases:', error);
showToast('error', 'Purchase Update Failed', 'Payment was successful, but failed to update user purchases.');
if (onError) onError(error);
}
setDialogVisible(false);
};
return (
<>
<GenericButton
label={`${amount} sats`}
icon="pi pi-wallet"
onClick={() => {
if (status === 'unauthenticated') {
console.log('unauthenticated');
router.push('/auth/signin');
} else {
fetchInvoice();
}
}}
disabled={isLoading}
severity='primary'
rounded
className={`text-[#f8f8ff] text-sm ${isLoading ? 'hidden' : ''}`}
/>
{isLoading && (
<div className='w-full h-full flex items-center justify-center'>
<ProgressSpinner
style={{ width: '30px', height: '30px' }}
strokeWidth="8"
animationDuration=".5s"
/>
</div>
)}
<Dialog
visible={dialogVisible}
onHide={() => setDialogVisible(false)}
header="Make Payment"
style={{ width: isMobile ? '90vw' : '50vw' }}
>
{invoice ? (
<Payment
invoice={invoice.paymentRequest}
onPaid={handlePaymentSuccess}
paymentMethods='all'
title={`Pay ${amount} sats`}
/>
) : (
<p>Loading payment details...</p>
)}
</Dialog>
</>
);
};
export default ResourcePaymentButton;
```
-

@ b8851a06:9b120ba1
2025-02-22 19:43:13
The digital guillotine has fallen. The Bybit hack wasn’t just a theft—it was a surgical strike exposing the fatal flaw of “crypto” that isn’t Bitcoin. This wasn’t a bug. It was a feature of a system designed to fail.
Here’s how North Korea’s Lazarus Group stole $1.5B in ETH, why “decentralized finance” is a joke, and how Bitcoin remains the only exit from this circus.
## I. The Heist: How Centralized “Crypto” Betrayed Its Users
### A. The Multisig Mousetrap (Or: Why You’re Still Using a Bank)
Bybit’s Ethereum cold wallet used multisig, requiring multiple approvals for transactions. Sounds secure, right? Wrong.
• The Con: Hackers didn’t pick the lock; they tricked the keyholders using a UI masking attack. The wallet interface showed “SEND TO BYBIT”, but the smart contract was whispering “SEND TO PYONGYANG.”
• Bitcoin Parallel: Bitcoin’s multisig is enforced on hardware, not a website UI. No browser spoofing, no phishing emails—just raw cryptography.
Ethereum’s multisig is a vault with a touchscreen PIN pad. Bitcoin’s is a mechanical safe with a key only you hold. Guess which one got robbed?
### B. Smart Contracts: Dumb as a Bag of Hammers
The thieves didn’t “hack” Ethereum—they exploited its smart contract complexity.
• Bybit’s security depended on a Safe.global contract. Lazarus simply tricked Bybit into approving a malicious upgrade.
• Imagine a vending machine that’s programmed to take your money but never give you a soda. That’s Ethereum’s “trustless” tech.
Why Bitcoin Wins: Bitcoin doesn’t do “smart contracts” in the Ethereum sense. Its scripting language is deliberately limited—less code, fewer attack vectors.
Ethereum is a Lego tower; Bitcoin is a granite slab. One topples, one doesn’t.
## II. The Laundering: Crypto’s Dirty Little Secret
### A. Mixers, Bridges, and the Art of Spycraft
Once the ETH was stolen, Lazarus laundered it at lightspeed:
1. Mixers (eXch) – Obfuscating transaction trails.
2. Bridges (Chainflip) – Swapping ETH for Bitcoin because that’s the only exit that matters.
Bitcoin Reality Check: Bitcoin’s privacy tools (like CoinJoin) are self-custodial—no third-party mixers. You keep control, not some “decentralized” website waiting to be hacked.
Ethereum’s “bridges” are burning rope ladders. Bitcoin’s privacy? An underground tunnel only you control.
### B. The $1.5B Lie: “Decentralized” Exchanges Are a Myth
Bybit’s “cold wallet” was on Safe.global—a so-called “decentralized” custodian. Translation? A website with extra steps.
• When Safe.global got breached, the private keys were stolen instantly.
• “Decentralized” means nothing if your funds depend on one website, one server, one weak link.
Bitcoin’s Answer: Self-custody. Hardware wallets. Cold storage. No trusted third parties.
Using Safe.global is like hiding your life savings in a gym locker labeled “STEAL ME.”
## III. The Culprits: State-Sponsored Hackers & Crypto’s Original Sin
### A. Lazarus Group: Crypto’s Robin Hood (For Dictators)
North Korea’s hackers didn’t break cryptography—they broke people.
• Phishing emails disguised as job offers.
• Bribes & social engineering targeting insiders.
• DeFi governance manipulation (because Proof-of-Stake is just shareholder voting in disguise).
Bitcoin’s Shield: No CEO to bribe. No “upgrade buttons” to exploit. No governance tokens to manipulate. Code is law—and Bitcoin’s law is written in stone.
Ethereum’s security model is “trust us.” Bitcoin’s is “verify.”
### B. The $3B Elephant: Altcoins Fund Dictators
Since 2017, Lazarus has stolen $3B+ in crypto, funding North Korea’s missile program.
Why? Because Ethereum, Solana, and XRP are built on Proof-of-Stake (PoS)—which centralizes power in the hands of a few rich validators.
• Bitcoin’s Proof-of-Work: Miners secure the network through energy-backed cryptography.
• Altcoins’ Proof-of-Stake: Security is dictated by who owns the most tokens.
Proof-of-Stake secures oligarchs. Proof-of-Work secures money. That’s why Lazarus can drain altcoin treasuries but hasn’t touched Bitcoin’s network.
## IV. Bybit’s Survival: A Centralized Circus
### A. The Bailout: Banks 2.0
Bybit took bridge loans from “undisclosed partners” (read: Wall Street vultures).
• Just like a traditional bank, Bybit printed liquidity out of thin air to stay solvent.
• If that sounds familiar, it’s because crypto exchanges are just banks in hoodies.
Bitcoin Contrast: No loans. No bailouts. No “trust.” Just 21 million coins, mathematically secured.
Bybit’s solvency is a confidence trick. Bitcoin’s solvency is math.
### B. The Great Withdrawal Panic
Within hours, 350,000+ users scrambled to withdraw funds.
A digital bank run—except this isn’t a bank. It’s an exchange that pretended to be decentralized.
Bitcoin fixes this: your wallet isn’t an IOU. It’s actual money.
Bybit = a TikTok influencer promising riches. Bitcoin = the gold in your basement.
## V. The Fallout: Regulators vs Reality
### A. ETH’s 8% Crash vs Bitcoin’s Unshakable Base
Ethereum tanked because it’s a tech stock, not money. Bitcoin? Dropped 2% and stabilized.
No CEO, no headquarters, no attack surface.
### B. The Regulatory Trap
Now the bureaucrats come in demanding:
1. Wallet audits (they don’t understand public ledgers).
2. Mixer bans (criminalizing privacy).
3. KYC everything (turning crypto into a surveillance state).
Bitcoin’s Rebellion: You can’t audit what’s already transparent. You can’t ban what’s unstoppable.
## VI. Conclusion: Burn the Altcoins, Stack the Sats
The Bybit hack isn’t a crypto problem. It’s an altcoin problem.
Ethereum’s smart contracts, DeFi bridges, and “decentralized” wallets are Swiss cheese for hackers. Bitcoin? A titanium vault.
The Only Lessons That Matter:
✅ Multisig isn’t enough unless it’s Bitcoin’s hardware-enforced version.
✅ Complexity kills—every altcoin “innovation” is a security risk waiting to happen.
Lazarus Group won this round because “crypto” ignored Bitcoin’s design. The solution isn’t better regulations—it’s better money.
Burn the tokens. Unplug the servers. Bitcoin is the exit.
Take your money off exchanges. Be sovereign.
-

@ b4403b24:83542d4e
2025-02-22 17:59:03
Chainflip says it has limited some frontend services but can’t fully block transactions as a decentralized protocol.
Over $1.1M in ETH has already been converted.

**Well done to them - not for the heist but for the decision to convert weak money to sound money** 😜
originally posted at https://stacker.news/items/894141
-

@ 2e8970de:63345c7a
2025-02-22 14:41:31
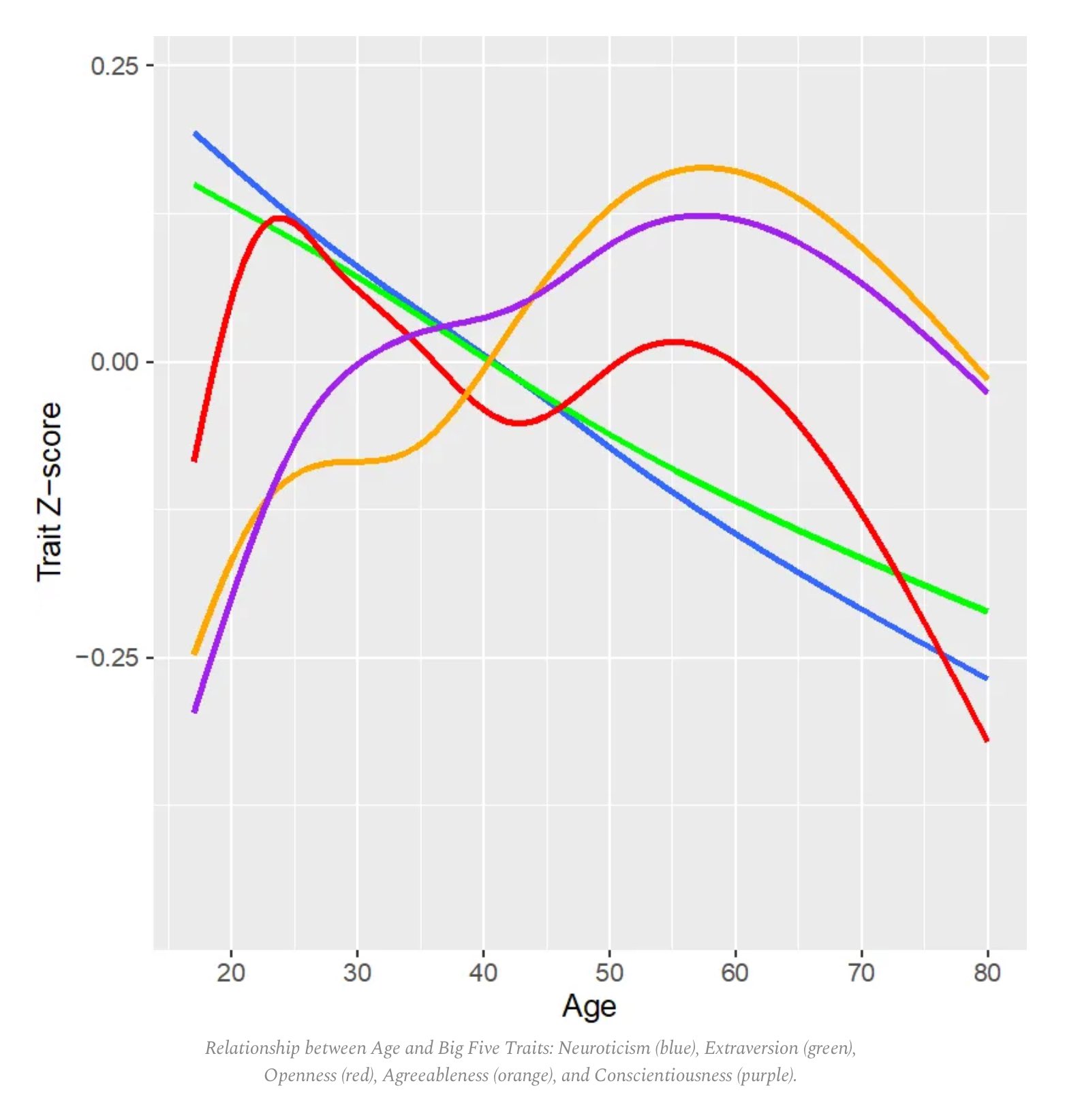
-Blue: Neuroticism
-Green: Extraversion
-Red: Openness to experience
-Orange: Agreeableness
-Purple: Conscientiousness
[sourcs(https://www.stevestewartwilliams.com/p/are-there-age-and-sex-differences)]
originally posted at https://stacker.news/items/893992
-

@ ac6f9572:8a6853dd
2025-02-22 13:01:56
# The old world crumbles. The sovereign rises.

Join #Bitshala at #BitPlebs Summit in Goa — a gathering of builders, creators, educators, and hodlers forging #India’s #Bitcoin future.
Open forums. Un-conference style talks. By @bitshala & @plebstogether
RSVP now: https://lu.ma/cd55r5d4
X: https://x.com/bitshala_org/status/1893252853709365684?s=09
originally posted at https://stacker.news/items/893899
-

@ da0b9bc3:4e30a4a9
2025-02-22 10:55:44
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/893831
-

@ 2e8970de:63345c7a
2025-02-22 09:03:55
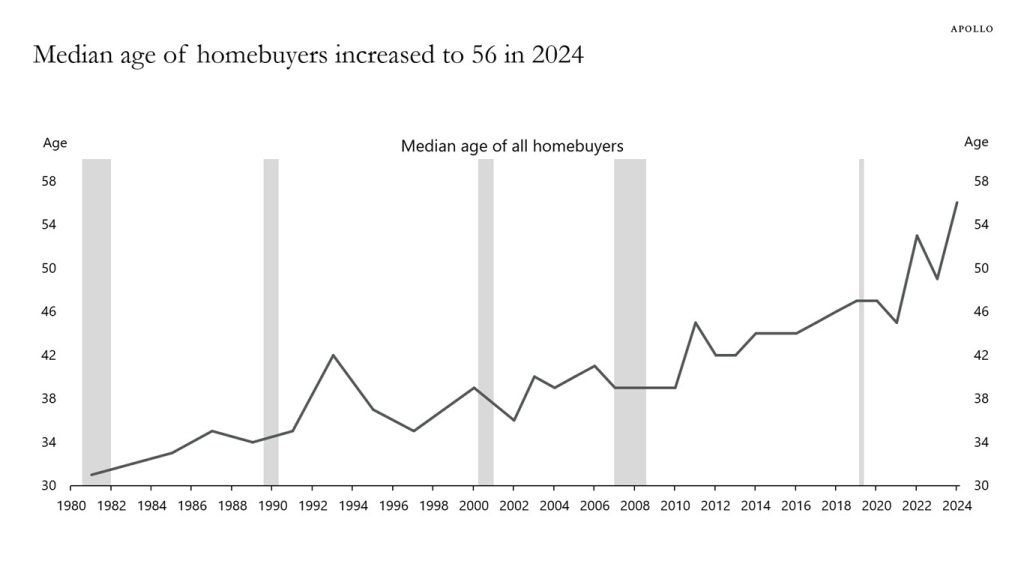
> Rising home prices and high mortgage rates have pushed the median age of homebuyers to a record-high 56 years old in 2024, up from 45 in 2021. In 1981, the median age of homebuyers was 31 years old,
[source](https://www.apolloacademy.com/median-age-of-homebuyers-56/)
originally posted at https://stacker.news/items/893804
-

@ 4857600b:30b502f4
2025-02-21 21:15:04
In a revealing development that exposes the hypocrisy of government surveillance, multiple federal agencies including the CIA and FBI have filed lawsuits to keep Samourai Wallet's client list sealed during and after trial proceedings. This move strongly suggests that government agencies themselves were utilizing Samourai's privacy-focused services while simultaneously condemning similar privacy tools when used by ordinary citizens.
The situation bears striking parallels to other cases where government agencies have hidden behind "national security" claims, such as the Jeffrey Epstein case, highlighting a troubling double standard: while average citizens are expected to surrender their financial privacy through extensive reporting requirements and regulations, government agencies claim exemption from these same transparency standards they enforce on others.
This case exemplifies the fundamental conflict between individual liberty and state power, where government agencies appear to be using the very privacy tools they prosecute others for using. The irony is particularly stark given that money laundering for intelligence agencies is considered legal in our system, while private citizens seeking financial privacy face severe legal consequences - a clear demonstration of how the state creates different rules for itself versus the people it claims to serve.
Citations:
[1] https://www.bugle.news/cia-fbi-dnc-rnc-all-sue-to-redact-samourais-client-list-from-trial/
-

@ 6e0ea5d6:0327f353
2025-02-21 18:15:52
"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.
— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend!
If this message helped you in any way,
consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-

@ 266815e0:6cd408a5
2025-02-21 17:54:15
I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use
A lot of the core concepts and classes are in place and stable enough where they wont change too much next release
If you want to skip straight to the documentation you can find at [hzrd149.github.io/applesauce](https://hzrd149.github.io/applesauce/) or the typescript docs at [hzrd149.github.io/applesauce/typedoc](https://hzrd149.github.io/applesauce/typedoc)
## Whats new
### Accounts
The `applesauce-accounts` package is an extension of the `applesauce-signers` package and provides classes for building a multi-account system for clients
Its primary features are
- Serialize and deserialize accounts so they can be saved in local storage or IndexededDB
- Account manager for multiple accounts and switching between them
- Account metadata for things like labels, app settings, etc
- Support for NIP-46 Nostr connect accounts
see [documentation](https://hzrd149.github.io/applesauce/accounts/manager.html) for more examples
### Nostr connect signer
The `NostrConnectSigner` class from the `applesauce-signers` package is now in a stable state and has a few new features
- Ability to create `nostrconnect://` URIs and waiting for the remote signer to connect
- SDK agnostic way of subscribing and publishing to relays
For a simple example, here is how to create a signer from a `bunker://` URI
```js
const signer = await NostrConnectSigner.fromBunkerURI(
"bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70",
{
permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]),
async onSubOpen(filters, relays, onEvent) {
// manually open REQ
},
async onSubClose() {
// close previouse REQ
},
async onPublishEvent(event, relays) {
// Pubilsh an event to relays
},
},
);
```
see [documentation](https://hzrd149.github.io/applesauce/signers/nostr-connect.html) for more examples and other signers
### Event Factory
The `EventFactory` class is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates ([blueprints](https://hzrd149.github.io/applesauce/typedoc/modules/applesauce_factory.Blueprints.html)) and is really simple to use
For example:
```js
import { EventFactory } from "applesauce-factory";
import { NoteBlueprint } from "applesauce-factory/blueprints";
const factory = new EventFactory({
// optionally pass a NIP-07 signer in to use for encryption / decryption
signer: window.nostr
});
// Create a kind 1 note with a hashtag
let draft = await factory.create(NoteBlueprint, "hello world #grownostr");
// Sign the note so it can be published
let signed = await window.nostr.signEvent(draft);
```
Its included in the `applesauce-factory` package and can be used with any other nostr SDKs or vanilla javascript
It also can be used to modify existing replaceable events
```js
let draft = await factory.modifyTags(
// kind 10002 event
mailboxes,
// add outbox relays
addOutboxRelay("wss://relay.io/"),
addOutboxRelay("wss://nostr.wine/"),
// remove inbox relay
removeInboxRelay("wss://personal.old-relay.com/")
);
```
see [documentation](https://hzrd149.github.io/applesauce/overview/factory.html) for more examples
### Loaders
The `applesauce-loaders` package exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identities
They use [rx-nostr](https://penpenpng.github.io/rx-nostr/) under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs
I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events
*They are stable enough to start using but they are not fully tested and they might change slightly in the future*
The following is a short list of the loaders and what they can be used for
- `ReplaceableLoader` loads any replaceable events (0, 3, 1xxxx, 3xxxx)
- `SingleEventLoader` loads single events based on ids
- `TimelineLoader` loads a timeline of events from multiple relays based on filters
- `TagValueLoader` loads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc
- `DnsIdentityLoader` loads NIP-05 identities and supports caching
- `UserSetsLoader` loads all lists events for users
see [documentation](https://hzrd149.github.io/applesauce/overview/loaders.html) for more examples
### Real tests
For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later
I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do
At the moment there are about 230 tests covering 45 files. not much but its a start
## Apps built using applesauce
If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months
- [noStrudel](https://github.com/hzrd149/nostrudel) The main app everything is being built for and tested in
- [nsite-manager](https://github.com/hzrd149/nsite-manager) Still a work-in-progress but supports multiple accounts thanks to the `applesauce-accounts` package
- [blossomservers.com](https://github.com/hzrd149/blossomservers) A simple (and incomplete) nostr client for listing and reviewing public blossom servers
- [libretranslate-dvm](https://github.com/hzrd149/libretranslate-dvm) A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu
- [cherry-tree](https://github.com/hzrd149/cherry-tree) A chunked blob uploader / downloader. only uses applesauce for boilerplate
- [nsite-homepage](https://github.com/hzrd149/nsite-homepage) A simple landing page for [nsite.lol](https://nsite.lol)
Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster
-

@ 0c503f08:4aed05c7
2025-02-21 17:30:53
originally posted at https://stacker.news/items/893208
-

@ d34e832d:383f78d0
2025-02-21 16:00:08
[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
Data Storage via Blobs in a Decentralized Manner
Blobs (Binary Large Objects) offer a flexible method of storing large chunks of data, and in the context of decentralized systems, they allow for secure, distributed storage solutions. In a decentralized world, where privacy and autonomy are key, managing data in a distributed manner ensures data isn't controlled or censored by a single entity. Here are three key systems enabling decentralized blob storage:
1. **Blossom Server**
[Blossom Server](https://github.com/hzrd149/blossom-server?tab=readme-ov-file) provides a decentralized platform for storing and sharing large blobs of data. Blossom Server allows users to host their own data and retrieve it from a decentralized network, ensuring that data is not stored in centralized servers. This platform is open-source, offering flexibility and security through peer-to-peer data storage.
2. **Perkeep**
[Perkeep](https://perkeep.org/) (formerly known as Camlistore) is a decentralized data storage system that allows for storing blobs of data in a distributed manner. It focuses on the long-term storage of large data sets, such as personal collections of photos, videos, and documents. By using Perkeep, users can ensure that their data remains private and is not controlled by any central authority. The system uses a unique identifier to access data, promoting both privacy and integrity.
3. **IPFS (InterPlanetary File System)**
[IPFS](https://ipfs.io/) is another popular decentralized file storage system that uses the concept of blobs to store and share data. IPFS allows users to store and access data in a decentralized manner by using a peer-to-peer network. Each piece of data is given a unique hash, ensuring that it is verifiable and tamper-proof. By leveraging IPFS, users can store everything from simple files to large applications, all without relying on centralized servers.
By using these decentralized data storage solutions, individuals and organizations can safeguard their information, increase privacy, and contribute to a more resilient and distributed internet infrastructure.
**Higher-Level Goals for Blob Storage**
Blob storage via Blossom ,Perkeep and IPFS has goals to become a decentralized, self-sufficient protocol for data storage, management, and sharing. While some of these features are already being implemented, they represent a broader vision for the future of decentralized personal data management.
1. **Filesystem Backups**
Allows for easy, incremental backups. Using the **`pk-put`** tool, users can back up files and directories quickly and efficiently. Incremental backups, which save only the changes made since the last backup, are essentially free, making Perkeep an efficient choice for backup solutions. This initial use case has already been implemented, providing seamless and secure backups for personal data.
2. **Efficient Remote Filesystem**
The goal is to create a highly efficient, aggressively caching remote filesystem using Perkeep. A **read-only** version of this filesystem is already trivial to implement, while **read-write** functionality remains an area of active development. Every modification in the filesystem would be snapshotted implicitly, providing version control as a default. This would enable users to interact with their data in a remote environment while ensuring that every change is tracked and recoverable.
3. **Decentralized Sharing System**
Perkeep is working towards enabling users to share data in a decentralized manner. The system will allow individuals to share anything with anyone or everyone, with privacy being the default setting. This decentralized sharing is already starting to work, and users can now share data with others while retaining control over who sees their information.
4. **Blog / Photo Hosting / Document Management CMS**
Perkeep aims to replace traditional blog platforms, photo hosting services, and document management software. By running a **personal blog**, **photo gallery**, and **document management system (CMS)** on Perkeep, users will have full control over their content. Permissions will be configurable, allowing for personal or public sharing. The author intends to use Perkeep for his own blog, gallery, and document management needs, further demonstrating its versatility.
5. **Decentralized Social Networking**
While still a lofty goal, decentralized social networking is a persistent aim for Perkeep. By implementing features like **comments** and **tagging**, users could attach metadata to images and content. Through claims, users could sign data and verify identities, promoting trust in social interactions. This would allow for decentralized social networking where users control their own data and interactions.
6. **Import/Export Adapters for Hosted Web Services**
Perkeep intends to bridge the gap between decentralized storage and traditional hosted web services. This feature would allow users to **mirror data** between hosted services and their private Perkeep storage. Whether content is created in Perkeep or hosted services, the goal is to ensure that data is always backed up privately, ensuring users' data is theirs forever.
### Combined Goals for Blossom and IPFS
Both Blossom and IPFS share common goals of decentralizing data storage, enhancing privacy, and providing users with greater control over their data. Together, these technologies enable:
- **Self-Sovereign Data Management**: Empowering users to store and manage their data without relying on centralized platforms.
- **Resilient and Redundant Storage**: Offering decentralized and redundant data storage that ensures availability and security.
- **Private and Permissioned Sharing**: Enabling secure, private data sharing where the user controls who has access to their content.
By focusing on these goals, both Blossom and IPFS are contributing to a future where individuals control their own data, collaborate more efficiently in decentralized networks and P4P protocols, and ensure the privacy and security of their digital assets.
These technologies in conjunction with nostr lead one to discover user agency and autonomy, where you can actually own and interface with your own data allowing for value creation and content creation strategies.
Donations via
- lightninglayerhash@getalby.com
-

@ d34e832d:383f78d0
2025-02-21 15:32:49
Decentralized Publishing: ChainScribe: How to Approach Studying NIPs (Nostr Improvement Proposals)
[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
How to Approach Studying NIPs (Nostr Improvement Proposals)
NIPs (Nostr Improvement Proposals) provide a framework for suggesting and discussing improvements to the Nostr protocol, a decentralized network for open communication. Studying NIPs is crucial for understanding the evolution of Nostr and its underlying principles. To effectively approach this, it's essential to follow a systematic, structured process.
1. **Familiarize with the Nostr Protocol**: Before diving into the specifics of each NIP, gain a solid understanding of the core Nostr protocol. This includes its goals, architecture, and key components like pubkeys, events, and relays.
2. **Explore the NIP Catalog**: Visit [nostr-nips.com](https://nostr-nips.com/) to browse through the available NIPs. Focus on the most recent proposals and those that align with your interests or areas of expertise.
3. **Review the Proposal Structure**: Each NIP follows a standard structure, typically including a description of the problem, proposed solution, and rationale. Learn to read and evaluate these elements critically, paying attention to how each proposal aligns with Nostr’s decentralized ethos.
4. **Follow Active Discussions**: Many NIPs are actively discussed within the community. Follow relevant channels, such as GitHub issues or dedicated discussion forums, to understand community feedback and potential revisions.
5. **Understand Dependencies**: Some NIPs are designed to work in tandem with others or require other technological advancements. Recognize these relationships to better understand the broader implications of any proposal.
6. **Hands-On Testing**: If possible, test NIPs in a development environment to see how they function in practice. Experimenting with proposals will help deepen your understanding and expose potential challenges or flaws.
7. **Contribute to Proposals**: If you have insights or suggestions, contribute to the discussion or propose your own improvements. NIPs thrive on community participation, and your input can help shape the future of Nostr.
Donations via
- lightninglayerhash@getalby.com
 @ da0b9bc3:4e30a4a9
2025-02-24 06:35:50Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/895451
@ da0b9bc3:4e30a4a9
2025-02-24 06:35:50Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/895451 @ 57d1a264:69f1fee1
2025-02-24 04:10:33As your involvement in open source design increases, you’ll face challenges that go beyond basic UI work. From creating scalable design systems to mentoring new contributors, these advanced areas require strategic thinking, collaboration, and leadership. This chapter dives into these complexities, helping you handle real-world situations while continuing to grow as a designer. - Championing Design Initiatives - Creating and Maintaining Design Systems - Handling Complex Design Challenges - Conducting In-Depth User Research - Balancing Open Source Work with Other Commitments - Navigating Project Dynamics -0 Mentoring New Designers Read more: https://opendesign.guide/10-advanced-topics ``` #design #nostrdesign #bitcoindesign #ln #grownostr #asknostr #zap #btc #bitcoin #nostr #cashu ``` originally posted at https://stacker.news/items/895377
@ 57d1a264:69f1fee1
2025-02-24 04:10:33As your involvement in open source design increases, you’ll face challenges that go beyond basic UI work. From creating scalable design systems to mentoring new contributors, these advanced areas require strategic thinking, collaboration, and leadership. This chapter dives into these complexities, helping you handle real-world situations while continuing to grow as a designer. - Championing Design Initiatives - Creating and Maintaining Design Systems - Handling Complex Design Challenges - Conducting In-Depth User Research - Balancing Open Source Work with Other Commitments - Navigating Project Dynamics -0 Mentoring New Designers Read more: https://opendesign.guide/10-advanced-topics ``` #design #nostrdesign #bitcoindesign #ln #grownostr #asknostr #zap #btc #bitcoin #nostr #cashu ``` originally posted at https://stacker.news/items/895377 @ c11cf5f8:4928464d
2025-02-23 20:42:52Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about? If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on. originally posted at https://stacker.news/items/895134
@ c11cf5f8:4928464d
2025-02-23 20:42:52Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about? If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on. originally posted at https://stacker.news/items/895134 @ 3ffac3a6:2d656657
2025-02-23 19:40:19## Renoters: Proposal for Anonymous Event Relaying in Nostr *This document is a proposal and not an official NIP.* This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message. ### **Motivation** While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity. In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools. ### **Proposed Solution** Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps: 1. **Event Creation:** The user creates the Nostr event they wish to publish. 2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen. 3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order: - A *new* random Nostr private key (`sk_wrapper`) is generated. - The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key). - A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing. 4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path. 5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter. 6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network. ### **Example** Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3. 1. Alice creates her event. 2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`. 3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`. 4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`. 5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`. 6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`. 7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`. 8. Alice publishes this final wrapper event. R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event. ### **Renoter Incentives (using Cashu)** To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism. - **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it. - **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it. - **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service. - **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed. - **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means. ### **Security Threats and Mitigations** - **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce: - Random delays in event relaying. - Dummy packets to complicate statistical analysis by malicious observers. - **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again. - **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network. - **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat. ### **Operational Considerations** - **Renoter Reliability:** The reliability of the Renoter network is crucial. - **Latency:** Relaying through multiple Renoters will introduce latency. - **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure. This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability. ### **References** - **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563) - **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf) - **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr) - **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/) - **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/) - **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf) #Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development
@ 3ffac3a6:2d656657
2025-02-23 19:40:19## Renoters: Proposal for Anonymous Event Relaying in Nostr *This document is a proposal and not an official NIP.* This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message. ### **Motivation** While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity. In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools. ### **Proposed Solution** Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps: 1. **Event Creation:** The user creates the Nostr event they wish to publish. 2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen. 3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order: - A *new* random Nostr private key (`sk_wrapper`) is generated. - The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key). - A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing. 4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path. 5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter. 6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network. ### **Example** Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3. 1. Alice creates her event. 2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`. 3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`. 4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`. 5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`. 6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`. 7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`. 8. Alice publishes this final wrapper event. R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event. ### **Renoter Incentives (using Cashu)** To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism. - **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it. - **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it. - **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service. - **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed. - **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means. ### **Security Threats and Mitigations** - **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce: - Random delays in event relaying. - Dummy packets to complicate statistical analysis by malicious observers. - **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again. - **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network. - **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat. ### **Operational Considerations** - **Renoter Reliability:** The reliability of the Renoter network is crucial. - **Latency:** Relaying through multiple Renoters will introduce latency. - **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure. This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability. ### **References** - **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563) - **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf) - **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr) - **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/) - **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/) - **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf) #Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development @ 2e8970de:63345c7a
2025-02-23 18:38:06 > 1 in 5 women with a BA are willing to marry a man without one  > But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically  > Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married  https://aibm.org/research/will-college-educated-women-find-someone-to-marry/ originally posted at https://stacker.news/items/895044
@ 2e8970de:63345c7a
2025-02-23 18:38:06 > 1 in 5 women with a BA are willing to marry a man without one  > But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically  > Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married  https://aibm.org/research/will-college-educated-women-find-someone-to-marry/ originally posted at https://stacker.news/items/895044 @ da0b9bc3:4e30a4a9
2025-02-23 07:08:22Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/894609
@ da0b9bc3:4e30a4a9
2025-02-23 07:08:22Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/894609 @ e3ba5e1a:5e433365
2025-02-23 06:35:51My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\. Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group. Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people. As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them. For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement. There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope). And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions. A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join. Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves. When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view. Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will. My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed.
@ e3ba5e1a:5e433365
2025-02-23 06:35:51My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\. Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group. Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people. As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them. For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement. There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope). And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions. A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join. Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves. When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view. Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will. My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed. @ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick. Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions. Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them. Here's the current state of the competition with your max possible score next to your nym: | Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson | | @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA| **Prize** At least 6k (I'll keep adding zaps to the pot). If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details. originally posted at https://stacker.news/items/894412
@ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick. Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions. Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them. Here's the current state of the competition with your max possible score next to your nym: | Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson | | @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA| **Prize** At least 6k (I'll keep adding zaps to the pot). If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details. originally posted at https://stacker.news/items/894412 @ 6260f29f:2ee2fcd4
2025-02-22 22:46:27# A title before again ```js import React, { useEffect, useState } from 'react'; import dynamic from 'next/dynamic'; import { Dialog } from 'primereact/dialog'; import { track } from '@vercel/analytics'; import { LightningAddress } from '@getalby/lightning-tools'; import { useToast } from '@/hooks/useToast'; import { useSession } from 'next-auth/react'; import { ProgressSpinner } from 'primereact/progressspinner'; import axios from 'axios'; import GenericButton from '@/components/buttons/GenericButton'; import useWindowWidth from '@/hooks/useWindowWidth'; import { useRouter } from 'next/router'; const Payment = dynamic( () => import('@getalby/bitcoin-connect-react').then((mod) => mod.Payment), { ssr: false } ); const ResourcePaymentButton = ({ lnAddress, amount, onSuccess, onError, resourceId }) => { const [invoice, setInvoice] = useState(null); const [isLoading, setIsLoading] = useState(false); const { showToast } = useToast(); const { data: session, status } = useSession(); const [dialogVisible, setDialogVisible] = useState(false); const router = useRouter(); const windowWidth = useWindowWidth(); const isMobile = windowWidth < 768; useEffect(() => { let intervalId; if (invoice) { intervalId = setInterval(async () => { const paid = await invoice.verifyPayment(); if (paid && invoice.preimage) { clearInterval(intervalId); // handle success handlePaymentSuccess({ paid, preimage: invoice.preimage }); } }, 2000); } else { console.error('no invoice'); } return () => { if (intervalId) { clearInterval(intervalId); } }; }, [invoice]); const fetchInvoice = async () => { setIsLoading(true); try { const ln = new LightningAddress(lnAddress); await ln.fetch(); const invoice = await ln.requestInvoice({ satoshi: amount }); setInvoice(invoice); setDialogVisible(true); } catch (error) { console.error('Error fetching invoice:', error); showToast('error', 'Invoice Error', 'Failed to fetch the invoice.'); if (onError) onError(error); } setIsLoading(false); }; const handlePaymentSuccess = async (response) => { try { const purchaseData = { userId: session.user.id, resourceId: resourceId, amountPaid: parseInt(amount, 10) }; const result = await axios.post('/api/purchase/resource', purchaseData); if (result.status === 200) { track('Resource Payment', { resourceId: resourceId, userId: session?.user?.id }); if (onSuccess) onSuccess(response); } else { throw new Error('Failed to update user purchases'); } } catch (error) { console.error('Error updating user purchases:', error); showToast('error', 'Purchase Update Failed', 'Payment was successful, but failed to update user purchases.'); if (onError) onError(error); } setDialogVisible(false); }; return ( <> <GenericButton label={`${amount} sats`} icon="pi pi-wallet" onClick={() => { if (status === 'unauthenticated') { console.log('unauthenticated'); router.push('/auth/signin'); } else { fetchInvoice(); } }} disabled={isLoading} severity='primary' rounded className={`text-[#f8f8ff] text-sm ${isLoading ? 'hidden' : ''}`} /> {isLoading && ( <div className='w-full h-full flex items-center justify-center'> <ProgressSpinner style={{ width: '30px', height: '30px' }} strokeWidth="8" animationDuration=".5s" /> </div> )} <Dialog visible={dialogVisible} onHide={() => setDialogVisible(false)} header="Make Payment" style={{ width: isMobile ? '90vw' : '50vw' }} > {invoice ? ( <Payment invoice={invoice.paymentRequest} onPaid={handlePaymentSuccess} paymentMethods='all' title={`Pay ${amount} sats`} /> ) : ( <p>Loading payment details...</p> )} </Dialog> </> ); }; export default ResourcePaymentButton; ```
@ 6260f29f:2ee2fcd4
2025-02-22 22:46:27# A title before again ```js import React, { useEffect, useState } from 'react'; import dynamic from 'next/dynamic'; import { Dialog } from 'primereact/dialog'; import { track } from '@vercel/analytics'; import { LightningAddress } from '@getalby/lightning-tools'; import { useToast } from '@/hooks/useToast'; import { useSession } from 'next-auth/react'; import { ProgressSpinner } from 'primereact/progressspinner'; import axios from 'axios'; import GenericButton from '@/components/buttons/GenericButton'; import useWindowWidth from '@/hooks/useWindowWidth'; import { useRouter } from 'next/router'; const Payment = dynamic( () => import('@getalby/bitcoin-connect-react').then((mod) => mod.Payment), { ssr: false } ); const ResourcePaymentButton = ({ lnAddress, amount, onSuccess, onError, resourceId }) => { const [invoice, setInvoice] = useState(null); const [isLoading, setIsLoading] = useState(false); const { showToast } = useToast(); const { data: session, status } = useSession(); const [dialogVisible, setDialogVisible] = useState(false); const router = useRouter(); const windowWidth = useWindowWidth(); const isMobile = windowWidth < 768; useEffect(() => { let intervalId; if (invoice) { intervalId = setInterval(async () => { const paid = await invoice.verifyPayment(); if (paid && invoice.preimage) { clearInterval(intervalId); // handle success handlePaymentSuccess({ paid, preimage: invoice.preimage }); } }, 2000); } else { console.error('no invoice'); } return () => { if (intervalId) { clearInterval(intervalId); } }; }, [invoice]); const fetchInvoice = async () => { setIsLoading(true); try { const ln = new LightningAddress(lnAddress); await ln.fetch(); const invoice = await ln.requestInvoice({ satoshi: amount }); setInvoice(invoice); setDialogVisible(true); } catch (error) { console.error('Error fetching invoice:', error); showToast('error', 'Invoice Error', 'Failed to fetch the invoice.'); if (onError) onError(error); } setIsLoading(false); }; const handlePaymentSuccess = async (response) => { try { const purchaseData = { userId: session.user.id, resourceId: resourceId, amountPaid: parseInt(amount, 10) }; const result = await axios.post('/api/purchase/resource', purchaseData); if (result.status === 200) { track('Resource Payment', { resourceId: resourceId, userId: session?.user?.id }); if (onSuccess) onSuccess(response); } else { throw new Error('Failed to update user purchases'); } } catch (error) { console.error('Error updating user purchases:', error); showToast('error', 'Purchase Update Failed', 'Payment was successful, but failed to update user purchases.'); if (onError) onError(error); } setDialogVisible(false); }; return ( <> <GenericButton label={`${amount} sats`} icon="pi pi-wallet" onClick={() => { if (status === 'unauthenticated') { console.log('unauthenticated'); router.push('/auth/signin'); } else { fetchInvoice(); } }} disabled={isLoading} severity='primary' rounded className={`text-[#f8f8ff] text-sm ${isLoading ? 'hidden' : ''}`} /> {isLoading && ( <div className='w-full h-full flex items-center justify-center'> <ProgressSpinner style={{ width: '30px', height: '30px' }} strokeWidth="8" animationDuration=".5s" /> </div> )} <Dialog visible={dialogVisible} onHide={() => setDialogVisible(false)} header="Make Payment" style={{ width: isMobile ? '90vw' : '50vw' }} > {invoice ? ( <Payment invoice={invoice.paymentRequest} onPaid={handlePaymentSuccess} paymentMethods='all' title={`Pay ${amount} sats`} /> ) : ( <p>Loading payment details...</p> )} </Dialog> </> ); }; export default ResourcePaymentButton; ``` @ b8851a06:9b120ba1
2025-02-22 19:43:13The digital guillotine has fallen. The Bybit hack wasn’t just a theft—it was a surgical strike exposing the fatal flaw of “crypto” that isn’t Bitcoin. This wasn’t a bug. It was a feature of a system designed to fail. Here’s how North Korea’s Lazarus Group stole $1.5B in ETH, why “decentralized finance” is a joke, and how Bitcoin remains the only exit from this circus. ## I. The Heist: How Centralized “Crypto” Betrayed Its Users ### A. The Multisig Mousetrap (Or: Why You’re Still Using a Bank) Bybit’s Ethereum cold wallet used multisig, requiring multiple approvals for transactions. Sounds secure, right? Wrong. • The Con: Hackers didn’t pick the lock; they tricked the keyholders using a UI masking attack. The wallet interface showed “SEND TO BYBIT”, but the smart contract was whispering “SEND TO PYONGYANG.” • Bitcoin Parallel: Bitcoin’s multisig is enforced on hardware, not a website UI. No browser spoofing, no phishing emails—just raw cryptography. Ethereum’s multisig is a vault with a touchscreen PIN pad. Bitcoin’s is a mechanical safe with a key only you hold. Guess which one got robbed? ### B. Smart Contracts: Dumb as a Bag of Hammers The thieves didn’t “hack” Ethereum—they exploited its smart contract complexity. • Bybit’s security depended on a Safe.global contract. Lazarus simply tricked Bybit into approving a malicious upgrade. • Imagine a vending machine that’s programmed to take your money but never give you a soda. That’s Ethereum’s “trustless” tech. Why Bitcoin Wins: Bitcoin doesn’t do “smart contracts” in the Ethereum sense. Its scripting language is deliberately limited—less code, fewer attack vectors. Ethereum is a Lego tower; Bitcoin is a granite slab. One topples, one doesn’t. ## II. The Laundering: Crypto’s Dirty Little Secret ### A. Mixers, Bridges, and the Art of Spycraft Once the ETH was stolen, Lazarus laundered it at lightspeed: 1. Mixers (eXch) – Obfuscating transaction trails. 2. Bridges (Chainflip) – Swapping ETH for Bitcoin because that’s the only exit that matters. Bitcoin Reality Check: Bitcoin’s privacy tools (like CoinJoin) are self-custodial—no third-party mixers. You keep control, not some “decentralized” website waiting to be hacked. Ethereum’s “bridges” are burning rope ladders. Bitcoin’s privacy? An underground tunnel only you control. ### B. The $1.5B Lie: “Decentralized” Exchanges Are a Myth Bybit’s “cold wallet” was on Safe.global—a so-called “decentralized” custodian. Translation? A website with extra steps. • When Safe.global got breached, the private keys were stolen instantly. • “Decentralized” means nothing if your funds depend on one website, one server, one weak link. Bitcoin’s Answer: Self-custody. Hardware wallets. Cold storage. No trusted third parties. Using Safe.global is like hiding your life savings in a gym locker labeled “STEAL ME.” ## III. The Culprits: State-Sponsored Hackers & Crypto’s Original Sin ### A. Lazarus Group: Crypto’s Robin Hood (For Dictators) North Korea’s hackers didn’t break cryptography—they broke people. • Phishing emails disguised as job offers. • Bribes & social engineering targeting insiders. • DeFi governance manipulation (because Proof-of-Stake is just shareholder voting in disguise). Bitcoin’s Shield: No CEO to bribe. No “upgrade buttons” to exploit. No governance tokens to manipulate. Code is law—and Bitcoin’s law is written in stone. Ethereum’s security model is “trust us.” Bitcoin’s is “verify.” ### B. The $3B Elephant: Altcoins Fund Dictators Since 2017, Lazarus has stolen $3B+ in crypto, funding North Korea’s missile program. Why? Because Ethereum, Solana, and XRP are built on Proof-of-Stake (PoS)—which centralizes power in the hands of a few rich validators. • Bitcoin’s Proof-of-Work: Miners secure the network through energy-backed cryptography. • Altcoins’ Proof-of-Stake: Security is dictated by who owns the most tokens. Proof-of-Stake secures oligarchs. Proof-of-Work secures money. That’s why Lazarus can drain altcoin treasuries but hasn’t touched Bitcoin’s network. ## IV. Bybit’s Survival: A Centralized Circus ### A. The Bailout: Banks 2.0 Bybit took bridge loans from “undisclosed partners” (read: Wall Street vultures). • Just like a traditional bank, Bybit printed liquidity out of thin air to stay solvent. • If that sounds familiar, it’s because crypto exchanges are just banks in hoodies. Bitcoin Contrast: No loans. No bailouts. No “trust.” Just 21 million coins, mathematically secured. Bybit’s solvency is a confidence trick. Bitcoin’s solvency is math. ### B. The Great Withdrawal Panic Within hours, 350,000+ users scrambled to withdraw funds. A digital bank run—except this isn’t a bank. It’s an exchange that pretended to be decentralized. Bitcoin fixes this: your wallet isn’t an IOU. It’s actual money. Bybit = a TikTok influencer promising riches. Bitcoin = the gold in your basement. ## V. The Fallout: Regulators vs Reality ### A. ETH’s 8% Crash vs Bitcoin’s Unshakable Base Ethereum tanked because it’s a tech stock, not money. Bitcoin? Dropped 2% and stabilized. No CEO, no headquarters, no attack surface. ### B. The Regulatory Trap Now the bureaucrats come in demanding: 1. Wallet audits (they don’t understand public ledgers). 2. Mixer bans (criminalizing privacy). 3. KYC everything (turning crypto into a surveillance state). Bitcoin’s Rebellion: You can’t audit what’s already transparent. You can’t ban what’s unstoppable. ## VI. Conclusion: Burn the Altcoins, Stack the Sats The Bybit hack isn’t a crypto problem. It’s an altcoin problem. Ethereum’s smart contracts, DeFi bridges, and “decentralized” wallets are Swiss cheese for hackers. Bitcoin? A titanium vault. The Only Lessons That Matter: ✅ Multisig isn’t enough unless it’s Bitcoin’s hardware-enforced version. ✅ Complexity kills—every altcoin “innovation” is a security risk waiting to happen. Lazarus Group won this round because “crypto” ignored Bitcoin’s design. The solution isn’t better regulations—it’s better money. Burn the tokens. Unplug the servers. Bitcoin is the exit. Take your money off exchanges. Be sovereign.
@ b8851a06:9b120ba1
2025-02-22 19:43:13The digital guillotine has fallen. The Bybit hack wasn’t just a theft—it was a surgical strike exposing the fatal flaw of “crypto” that isn’t Bitcoin. This wasn’t a bug. It was a feature of a system designed to fail. Here’s how North Korea’s Lazarus Group stole $1.5B in ETH, why “decentralized finance” is a joke, and how Bitcoin remains the only exit from this circus. ## I. The Heist: How Centralized “Crypto” Betrayed Its Users ### A. The Multisig Mousetrap (Or: Why You’re Still Using a Bank) Bybit’s Ethereum cold wallet used multisig, requiring multiple approvals for transactions. Sounds secure, right? Wrong. • The Con: Hackers didn’t pick the lock; they tricked the keyholders using a UI masking attack. The wallet interface showed “SEND TO BYBIT”, but the smart contract was whispering “SEND TO PYONGYANG.” • Bitcoin Parallel: Bitcoin’s multisig is enforced on hardware, not a website UI. No browser spoofing, no phishing emails—just raw cryptography. Ethereum’s multisig is a vault with a touchscreen PIN pad. Bitcoin’s is a mechanical safe with a key only you hold. Guess which one got robbed? ### B. Smart Contracts: Dumb as a Bag of Hammers The thieves didn’t “hack” Ethereum—they exploited its smart contract complexity. • Bybit’s security depended on a Safe.global contract. Lazarus simply tricked Bybit into approving a malicious upgrade. • Imagine a vending machine that’s programmed to take your money but never give you a soda. That’s Ethereum’s “trustless” tech. Why Bitcoin Wins: Bitcoin doesn’t do “smart contracts” in the Ethereum sense. Its scripting language is deliberately limited—less code, fewer attack vectors. Ethereum is a Lego tower; Bitcoin is a granite slab. One topples, one doesn’t. ## II. The Laundering: Crypto’s Dirty Little Secret ### A. Mixers, Bridges, and the Art of Spycraft Once the ETH was stolen, Lazarus laundered it at lightspeed: 1. Mixers (eXch) – Obfuscating transaction trails. 2. Bridges (Chainflip) – Swapping ETH for Bitcoin because that’s the only exit that matters. Bitcoin Reality Check: Bitcoin’s privacy tools (like CoinJoin) are self-custodial—no third-party mixers. You keep control, not some “decentralized” website waiting to be hacked. Ethereum’s “bridges” are burning rope ladders. Bitcoin’s privacy? An underground tunnel only you control. ### B. The $1.5B Lie: “Decentralized” Exchanges Are a Myth Bybit’s “cold wallet” was on Safe.global—a so-called “decentralized” custodian. Translation? A website with extra steps. • When Safe.global got breached, the private keys were stolen instantly. • “Decentralized” means nothing if your funds depend on one website, one server, one weak link. Bitcoin’s Answer: Self-custody. Hardware wallets. Cold storage. No trusted third parties. Using Safe.global is like hiding your life savings in a gym locker labeled “STEAL ME.” ## III. The Culprits: State-Sponsored Hackers & Crypto’s Original Sin ### A. Lazarus Group: Crypto’s Robin Hood (For Dictators) North Korea’s hackers didn’t break cryptography—they broke people. • Phishing emails disguised as job offers. • Bribes & social engineering targeting insiders. • DeFi governance manipulation (because Proof-of-Stake is just shareholder voting in disguise). Bitcoin’s Shield: No CEO to bribe. No “upgrade buttons” to exploit. No governance tokens to manipulate. Code is law—and Bitcoin’s law is written in stone. Ethereum’s security model is “trust us.” Bitcoin’s is “verify.” ### B. The $3B Elephant: Altcoins Fund Dictators Since 2017, Lazarus has stolen $3B+ in crypto, funding North Korea’s missile program. Why? Because Ethereum, Solana, and XRP are built on Proof-of-Stake (PoS)—which centralizes power in the hands of a few rich validators. • Bitcoin’s Proof-of-Work: Miners secure the network through energy-backed cryptography. • Altcoins’ Proof-of-Stake: Security is dictated by who owns the most tokens. Proof-of-Stake secures oligarchs. Proof-of-Work secures money. That’s why Lazarus can drain altcoin treasuries but hasn’t touched Bitcoin’s network. ## IV. Bybit’s Survival: A Centralized Circus ### A. The Bailout: Banks 2.0 Bybit took bridge loans from “undisclosed partners” (read: Wall Street vultures). • Just like a traditional bank, Bybit printed liquidity out of thin air to stay solvent. • If that sounds familiar, it’s because crypto exchanges are just banks in hoodies. Bitcoin Contrast: No loans. No bailouts. No “trust.” Just 21 million coins, mathematically secured. Bybit’s solvency is a confidence trick. Bitcoin’s solvency is math. ### B. The Great Withdrawal Panic Within hours, 350,000+ users scrambled to withdraw funds. A digital bank run—except this isn’t a bank. It’s an exchange that pretended to be decentralized. Bitcoin fixes this: your wallet isn’t an IOU. It’s actual money. Bybit = a TikTok influencer promising riches. Bitcoin = the gold in your basement. ## V. The Fallout: Regulators vs Reality ### A. ETH’s 8% Crash vs Bitcoin’s Unshakable Base Ethereum tanked because it’s a tech stock, not money. Bitcoin? Dropped 2% and stabilized. No CEO, no headquarters, no attack surface. ### B. The Regulatory Trap Now the bureaucrats come in demanding: 1. Wallet audits (they don’t understand public ledgers). 2. Mixer bans (criminalizing privacy). 3. KYC everything (turning crypto into a surveillance state). Bitcoin’s Rebellion: You can’t audit what’s already transparent. You can’t ban what’s unstoppable. ## VI. Conclusion: Burn the Altcoins, Stack the Sats The Bybit hack isn’t a crypto problem. It’s an altcoin problem. Ethereum’s smart contracts, DeFi bridges, and “decentralized” wallets are Swiss cheese for hackers. Bitcoin? A titanium vault. The Only Lessons That Matter: ✅ Multisig isn’t enough unless it’s Bitcoin’s hardware-enforced version. ✅ Complexity kills—every altcoin “innovation” is a security risk waiting to happen. Lazarus Group won this round because “crypto” ignored Bitcoin’s design. The solution isn’t better regulations—it’s better money. Burn the tokens. Unplug the servers. Bitcoin is the exit. Take your money off exchanges. Be sovereign. @ b4403b24:83542d4e
2025-02-22 17:59:03Chainflip says it has limited some frontend services but can’t fully block transactions as a decentralized protocol. Over $1.1M in ETH has already been converted.  **Well done to them - not for the heist but for the decision to convert weak money to sound money** 😜 originally posted at https://stacker.news/items/894141
@ b4403b24:83542d4e
2025-02-22 17:59:03Chainflip says it has limited some frontend services but can’t fully block transactions as a decentralized protocol. Over $1.1M in ETH has already been converted.  **Well done to them - not for the heist but for the decision to convert weak money to sound money** 😜 originally posted at https://stacker.news/items/894141 @ 2e8970de:63345c7a
2025-02-22 14:41:31 -Blue: Neuroticism -Green: Extraversion -Red: Openness to experience -Orange: Agreeableness -Purple: Conscientiousness [sourcs(https://www.stevestewartwilliams.com/p/are-there-age-and-sex-differences)] originally posted at https://stacker.news/items/893992
@ 2e8970de:63345c7a
2025-02-22 14:41:31 -Blue: Neuroticism -Green: Extraversion -Red: Openness to experience -Orange: Agreeableness -Purple: Conscientiousness [sourcs(https://www.stevestewartwilliams.com/p/are-there-age-and-sex-differences)] originally posted at https://stacker.news/items/893992 @ ac6f9572:8a6853dd
2025-02-22 13:01:56# The old world crumbles. The sovereign rises.  Join #Bitshala at #BitPlebs Summit in Goa — a gathering of builders, creators, educators, and hodlers forging #India’s #Bitcoin future. Open forums. Un-conference style talks. By @bitshala & @plebstogether RSVP now: https://lu.ma/cd55r5d4 X: https://x.com/bitshala_org/status/1893252853709365684?s=09 originally posted at https://stacker.news/items/893899
@ ac6f9572:8a6853dd
2025-02-22 13:01:56# The old world crumbles. The sovereign rises.  Join #Bitshala at #BitPlebs Summit in Goa — a gathering of builders, creators, educators, and hodlers forging #India’s #Bitcoin future. Open forums. Un-conference style talks. By @bitshala & @plebstogether RSVP now: https://lu.ma/cd55r5d4 X: https://x.com/bitshala_org/status/1893252853709365684?s=09 originally posted at https://stacker.news/items/893899 @ da0b9bc3:4e30a4a9
2025-02-22 10:55:44Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/893831
@ da0b9bc3:4e30a4a9
2025-02-22 10:55:44Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/893831 @ 2e8970de:63345c7a
2025-02-22 09:03:55 > Rising home prices and high mortgage rates have pushed the median age of homebuyers to a record-high 56 years old in 2024, up from 45 in 2021. In 1981, the median age of homebuyers was 31 years old, [source](https://www.apolloacademy.com/median-age-of-homebuyers-56/) originally posted at https://stacker.news/items/893804
@ 2e8970de:63345c7a
2025-02-22 09:03:55 > Rising home prices and high mortgage rates have pushed the median age of homebuyers to a record-high 56 years old in 2024, up from 45 in 2021. In 1981, the median age of homebuyers was 31 years old, [source](https://www.apolloacademy.com/median-age-of-homebuyers-56/) originally posted at https://stacker.news/items/893804 @ 4857600b:30b502f4
2025-02-21 21:15:04In a revealing development that exposes the hypocrisy of government surveillance, multiple federal agencies including the CIA and FBI have filed lawsuits to keep Samourai Wallet's client list sealed during and after trial proceedings. This move strongly suggests that government agencies themselves were utilizing Samourai's privacy-focused services while simultaneously condemning similar privacy tools when used by ordinary citizens. The situation bears striking parallels to other cases where government agencies have hidden behind "national security" claims, such as the Jeffrey Epstein case, highlighting a troubling double standard: while average citizens are expected to surrender their financial privacy through extensive reporting requirements and regulations, government agencies claim exemption from these same transparency standards they enforce on others. This case exemplifies the fundamental conflict between individual liberty and state power, where government agencies appear to be using the very privacy tools they prosecute others for using. The irony is particularly stark given that money laundering for intelligence agencies is considered legal in our system, while private citizens seeking financial privacy face severe legal consequences - a clear demonstration of how the state creates different rules for itself versus the people it claims to serve. Citations: [1] https://www.bugle.news/cia-fbi-dnc-rnc-all-sue-to-redact-samourais-client-list-from-trial/
@ 4857600b:30b502f4
2025-02-21 21:15:04In a revealing development that exposes the hypocrisy of government surveillance, multiple federal agencies including the CIA and FBI have filed lawsuits to keep Samourai Wallet's client list sealed during and after trial proceedings. This move strongly suggests that government agencies themselves were utilizing Samourai's privacy-focused services while simultaneously condemning similar privacy tools when used by ordinary citizens. The situation bears striking parallels to other cases where government agencies have hidden behind "national security" claims, such as the Jeffrey Epstein case, highlighting a troubling double standard: while average citizens are expected to surrender their financial privacy through extensive reporting requirements and regulations, government agencies claim exemption from these same transparency standards they enforce on others. This case exemplifies the fundamental conflict between individual liberty and state power, where government agencies appear to be using the very privacy tools they prosecute others for using. The irony is particularly stark given that money laundering for intelligence agencies is considered legal in our system, while private citizens seeking financial privacy face severe legal consequences - a clear demonstration of how the state creates different rules for itself versus the people it claims to serve. Citations: [1] https://www.bugle.news/cia-fbi-dnc-rnc-all-sue-to-redact-samourais-client-list-from-trial/ @ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard. — We want to speak with the president — the man said in a low voice. — He will be busy all day — the secretary replied curtly. — We will wait. The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that. — If you speak with them for just a few minutes, maybe they will decide to go away — she said. The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple. — We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus. — My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery. — Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard. The president looked at the woman's faded dress and her husband's old suit and exclaimed: — A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard. The lady was silent for a moment, then said to her husband: — If that’s all it costs to found a university, why don’t we have our own? The husband agreed. The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student." Text extracted from: "Mileumlivros - Stories that Teach Values." Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard. — We want to speak with the president — the man said in a low voice. — He will be busy all day — the secretary replied curtly. — We will wait. The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that. — If you speak with them for just a few minutes, maybe they will decide to go away — she said. The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple. — We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus. — My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery. — Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard. The president looked at the woman's faded dress and her husband's old suit and exclaimed: — A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard. The lady was silent for a moment, then said to her husband: — If that’s all it costs to found a university, why don’t we have our own? The husband agreed. The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student." Text extracted from: "Mileumlivros - Stories that Teach Values." Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family! @ 266815e0:6cd408a5
2025-02-21 17:54:15I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use A lot of the core concepts and classes are in place and stable enough where they wont change too much next release If you want to skip straight to the documentation you can find at [hzrd149.github.io/applesauce](https://hzrd149.github.io/applesauce/) or the typescript docs at [hzrd149.github.io/applesauce/typedoc](https://hzrd149.github.io/applesauce/typedoc) ## Whats new ### Accounts The `applesauce-accounts` package is an extension of the `applesauce-signers` package and provides classes for building a multi-account system for clients Its primary features are - Serialize and deserialize accounts so they can be saved in local storage or IndexededDB - Account manager for multiple accounts and switching between them - Account metadata for things like labels, app settings, etc - Support for NIP-46 Nostr connect accounts see [documentation](https://hzrd149.github.io/applesauce/accounts/manager.html) for more examples ### Nostr connect signer The `NostrConnectSigner` class from the `applesauce-signers` package is now in a stable state and has a few new features - Ability to create `nostrconnect://` URIs and waiting for the remote signer to connect - SDK agnostic way of subscribing and publishing to relays For a simple example, here is how to create a signer from a `bunker://` URI ```js const signer = await NostrConnectSigner.fromBunkerURI( "bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70", { permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]), async onSubOpen(filters, relays, onEvent) { // manually open REQ }, async onSubClose() { // close previouse REQ }, async onPublishEvent(event, relays) { // Pubilsh an event to relays }, }, ); ``` see [documentation](https://hzrd149.github.io/applesauce/signers/nostr-connect.html) for more examples and other signers ### Event Factory The `EventFactory` class is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates ([blueprints](https://hzrd149.github.io/applesauce/typedoc/modules/applesauce_factory.Blueprints.html)) and is really simple to use For example: ```js import { EventFactory } from "applesauce-factory"; import { NoteBlueprint } from "applesauce-factory/blueprints"; const factory = new EventFactory({ // optionally pass a NIP-07 signer in to use for encryption / decryption signer: window.nostr }); // Create a kind 1 note with a hashtag let draft = await factory.create(NoteBlueprint, "hello world #grownostr"); // Sign the note so it can be published let signed = await window.nostr.signEvent(draft); ``` Its included in the `applesauce-factory` package and can be used with any other nostr SDKs or vanilla javascript It also can be used to modify existing replaceable events ```js let draft = await factory.modifyTags( // kind 10002 event mailboxes, // add outbox relays addOutboxRelay("wss://relay.io/"), addOutboxRelay("wss://nostr.wine/"), // remove inbox relay removeInboxRelay("wss://personal.old-relay.com/") ); ``` see [documentation](https://hzrd149.github.io/applesauce/overview/factory.html) for more examples ### Loaders The `applesauce-loaders` package exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identities They use [rx-nostr](https://penpenpng.github.io/rx-nostr/) under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events *They are stable enough to start using but they are not fully tested and they might change slightly in the future* The following is a short list of the loaders and what they can be used for - `ReplaceableLoader` loads any replaceable events (0, 3, 1xxxx, 3xxxx) - `SingleEventLoader` loads single events based on ids - `TimelineLoader` loads a timeline of events from multiple relays based on filters - `TagValueLoader` loads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc - `DnsIdentityLoader` loads NIP-05 identities and supports caching - `UserSetsLoader` loads all lists events for users see [documentation](https://hzrd149.github.io/applesauce/overview/loaders.html) for more examples ### Real tests For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do At the moment there are about 230 tests covering 45 files. not much but its a start  ## Apps built using applesauce If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months - [noStrudel](https://github.com/hzrd149/nostrudel) The main app everything is being built for and tested in - [nsite-manager](https://github.com/hzrd149/nsite-manager) Still a work-in-progress but supports multiple accounts thanks to the `applesauce-accounts` package - [blossomservers.com](https://github.com/hzrd149/blossomservers) A simple (and incomplete) nostr client for listing and reviewing public blossom servers - [libretranslate-dvm](https://github.com/hzrd149/libretranslate-dvm) A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu - [cherry-tree](https://github.com/hzrd149/cherry-tree) A chunked blob uploader / downloader. only uses applesauce for boilerplate - [nsite-homepage](https://github.com/hzrd149/nsite-homepage) A simple landing page for [nsite.lol](https://nsite.lol) Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster
@ 266815e0:6cd408a5
2025-02-21 17:54:15I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use A lot of the core concepts and classes are in place and stable enough where they wont change too much next release If you want to skip straight to the documentation you can find at [hzrd149.github.io/applesauce](https://hzrd149.github.io/applesauce/) or the typescript docs at [hzrd149.github.io/applesauce/typedoc](https://hzrd149.github.io/applesauce/typedoc) ## Whats new ### Accounts The `applesauce-accounts` package is an extension of the `applesauce-signers` package and provides classes for building a multi-account system for clients Its primary features are - Serialize and deserialize accounts so they can be saved in local storage or IndexededDB - Account manager for multiple accounts and switching between them - Account metadata for things like labels, app settings, etc - Support for NIP-46 Nostr connect accounts see [documentation](https://hzrd149.github.io/applesauce/accounts/manager.html) for more examples ### Nostr connect signer The `NostrConnectSigner` class from the `applesauce-signers` package is now in a stable state and has a few new features - Ability to create `nostrconnect://` URIs and waiting for the remote signer to connect - SDK agnostic way of subscribing and publishing to relays For a simple example, here is how to create a signer from a `bunker://` URI ```js const signer = await NostrConnectSigner.fromBunkerURI( "bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70", { permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]), async onSubOpen(filters, relays, onEvent) { // manually open REQ }, async onSubClose() { // close previouse REQ }, async onPublishEvent(event, relays) { // Pubilsh an event to relays }, }, ); ``` see [documentation](https://hzrd149.github.io/applesauce/signers/nostr-connect.html) for more examples and other signers ### Event Factory The `EventFactory` class is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates ([blueprints](https://hzrd149.github.io/applesauce/typedoc/modules/applesauce_factory.Blueprints.html)) and is really simple to use For example: ```js import { EventFactory } from "applesauce-factory"; import { NoteBlueprint } from "applesauce-factory/blueprints"; const factory = new EventFactory({ // optionally pass a NIP-07 signer in to use for encryption / decryption signer: window.nostr }); // Create a kind 1 note with a hashtag let draft = await factory.create(NoteBlueprint, "hello world #grownostr"); // Sign the note so it can be published let signed = await window.nostr.signEvent(draft); ``` Its included in the `applesauce-factory` package and can be used with any other nostr SDKs or vanilla javascript It also can be used to modify existing replaceable events ```js let draft = await factory.modifyTags( // kind 10002 event mailboxes, // add outbox relays addOutboxRelay("wss://relay.io/"), addOutboxRelay("wss://nostr.wine/"), // remove inbox relay removeInboxRelay("wss://personal.old-relay.com/") ); ``` see [documentation](https://hzrd149.github.io/applesauce/overview/factory.html) for more examples ### Loaders The `applesauce-loaders` package exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identities They use [rx-nostr](https://penpenpng.github.io/rx-nostr/) under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events *They are stable enough to start using but they are not fully tested and they might change slightly in the future* The following is a short list of the loaders and what they can be used for - `ReplaceableLoader` loads any replaceable events (0, 3, 1xxxx, 3xxxx) - `SingleEventLoader` loads single events based on ids - `TimelineLoader` loads a timeline of events from multiple relays based on filters - `TagValueLoader` loads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc - `DnsIdentityLoader` loads NIP-05 identities and supports caching - `UserSetsLoader` loads all lists events for users see [documentation](https://hzrd149.github.io/applesauce/overview/loaders.html) for more examples ### Real tests For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do At the moment there are about 230 tests covering 45 files. not much but its a start  ## Apps built using applesauce If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months - [noStrudel](https://github.com/hzrd149/nostrudel) The main app everything is being built for and tested in - [nsite-manager](https://github.com/hzrd149/nsite-manager) Still a work-in-progress but supports multiple accounts thanks to the `applesauce-accounts` package - [blossomservers.com](https://github.com/hzrd149/blossomservers) A simple (and incomplete) nostr client for listing and reviewing public blossom servers - [libretranslate-dvm](https://github.com/hzrd149/libretranslate-dvm) A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu - [cherry-tree](https://github.com/hzrd149/cherry-tree) A chunked blob uploader / downloader. only uses applesauce for boilerplate - [nsite-homepage](https://github.com/hzrd149/nsite-homepage) A simple landing page for [nsite.lol](https://nsite.lol) Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster @ 0c503f08:4aed05c7
2025-02-21 17:30:53originally posted at https://stacker.news/items/893208
@ 0c503f08:4aed05c7
2025-02-21 17:30:53originally posted at https://stacker.news/items/893208 @ d34e832d:383f78d0
2025-02-21 16:00:08[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv] Data Storage via Blobs in a Decentralized Manner Blobs (Binary Large Objects) offer a flexible method of storing large chunks of data, and in the context of decentralized systems, they allow for secure, distributed storage solutions. In a decentralized world, where privacy and autonomy are key, managing data in a distributed manner ensures data isn't controlled or censored by a single entity. Here are three key systems enabling decentralized blob storage: 1. **Blossom Server** [Blossom Server](https://github.com/hzrd149/blossom-server?tab=readme-ov-file) provides a decentralized platform for storing and sharing large blobs of data. Blossom Server allows users to host their own data and retrieve it from a decentralized network, ensuring that data is not stored in centralized servers. This platform is open-source, offering flexibility and security through peer-to-peer data storage. 2. **Perkeep** [Perkeep](https://perkeep.org/) (formerly known as Camlistore) is a decentralized data storage system that allows for storing blobs of data in a distributed manner. It focuses on the long-term storage of large data sets, such as personal collections of photos, videos, and documents. By using Perkeep, users can ensure that their data remains private and is not controlled by any central authority. The system uses a unique identifier to access data, promoting both privacy and integrity. 3. **IPFS (InterPlanetary File System)** [IPFS](https://ipfs.io/) is another popular decentralized file storage system that uses the concept of blobs to store and share data. IPFS allows users to store and access data in a decentralized manner by using a peer-to-peer network. Each piece of data is given a unique hash, ensuring that it is verifiable and tamper-proof. By leveraging IPFS, users can store everything from simple files to large applications, all without relying on centralized servers. By using these decentralized data storage solutions, individuals and organizations can safeguard their information, increase privacy, and contribute to a more resilient and distributed internet infrastructure. **Higher-Level Goals for Blob Storage** Blob storage via Blossom ,Perkeep and IPFS has goals to become a decentralized, self-sufficient protocol for data storage, management, and sharing. While some of these features are already being implemented, they represent a broader vision for the future of decentralized personal data management. 1. **Filesystem Backups** Allows for easy, incremental backups. Using the **`pk-put`** tool, users can back up files and directories quickly and efficiently. Incremental backups, which save only the changes made since the last backup, are essentially free, making Perkeep an efficient choice for backup solutions. This initial use case has already been implemented, providing seamless and secure backups for personal data. 2. **Efficient Remote Filesystem** The goal is to create a highly efficient, aggressively caching remote filesystem using Perkeep. A **read-only** version of this filesystem is already trivial to implement, while **read-write** functionality remains an area of active development. Every modification in the filesystem would be snapshotted implicitly, providing version control as a default. This would enable users to interact with their data in a remote environment while ensuring that every change is tracked and recoverable. 3. **Decentralized Sharing System** Perkeep is working towards enabling users to share data in a decentralized manner. The system will allow individuals to share anything with anyone or everyone, with privacy being the default setting. This decentralized sharing is already starting to work, and users can now share data with others while retaining control over who sees their information. 4. **Blog / Photo Hosting / Document Management CMS** Perkeep aims to replace traditional blog platforms, photo hosting services, and document management software. By running a **personal blog**, **photo gallery**, and **document management system (CMS)** on Perkeep, users will have full control over their content. Permissions will be configurable, allowing for personal or public sharing. The author intends to use Perkeep for his own blog, gallery, and document management needs, further demonstrating its versatility. 5. **Decentralized Social Networking** While still a lofty goal, decentralized social networking is a persistent aim for Perkeep. By implementing features like **comments** and **tagging**, users could attach metadata to images and content. Through claims, users could sign data and verify identities, promoting trust in social interactions. This would allow for decentralized social networking where users control their own data and interactions. 6. **Import/Export Adapters for Hosted Web Services** Perkeep intends to bridge the gap between decentralized storage and traditional hosted web services. This feature would allow users to **mirror data** between hosted services and their private Perkeep storage. Whether content is created in Perkeep or hosted services, the goal is to ensure that data is always backed up privately, ensuring users' data is theirs forever. ### Combined Goals for Blossom and IPFS Both Blossom and IPFS share common goals of decentralizing data storage, enhancing privacy, and providing users with greater control over their data. Together, these technologies enable: - **Self-Sovereign Data Management**: Empowering users to store and manage their data without relying on centralized platforms. - **Resilient and Redundant Storage**: Offering decentralized and redundant data storage that ensures availability and security. - **Private and Permissioned Sharing**: Enabling secure, private data sharing where the user controls who has access to their content. By focusing on these goals, both Blossom and IPFS are contributing to a future where individuals control their own data, collaborate more efficiently in decentralized networks and P4P protocols, and ensure the privacy and security of their digital assets. These technologies in conjunction with nostr lead one to discover user agency and autonomy, where you can actually own and interface with your own data allowing for value creation and content creation strategies. Donations via - lightninglayerhash@getalby.com
@ d34e832d:383f78d0
2025-02-21 16:00:08[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv] Data Storage via Blobs in a Decentralized Manner Blobs (Binary Large Objects) offer a flexible method of storing large chunks of data, and in the context of decentralized systems, they allow for secure, distributed storage solutions. In a decentralized world, where privacy and autonomy are key, managing data in a distributed manner ensures data isn't controlled or censored by a single entity. Here are three key systems enabling decentralized blob storage: 1. **Blossom Server** [Blossom Server](https://github.com/hzrd149/blossom-server?tab=readme-ov-file) provides a decentralized platform for storing and sharing large blobs of data. Blossom Server allows users to host their own data and retrieve it from a decentralized network, ensuring that data is not stored in centralized servers. This platform is open-source, offering flexibility and security through peer-to-peer data storage. 2. **Perkeep** [Perkeep](https://perkeep.org/) (formerly known as Camlistore) is a decentralized data storage system that allows for storing blobs of data in a distributed manner. It focuses on the long-term storage of large data sets, such as personal collections of photos, videos, and documents. By using Perkeep, users can ensure that their data remains private and is not controlled by any central authority. The system uses a unique identifier to access data, promoting both privacy and integrity. 3. **IPFS (InterPlanetary File System)** [IPFS](https://ipfs.io/) is another popular decentralized file storage system that uses the concept of blobs to store and share data. IPFS allows users to store and access data in a decentralized manner by using a peer-to-peer network. Each piece of data is given a unique hash, ensuring that it is verifiable and tamper-proof. By leveraging IPFS, users can store everything from simple files to large applications, all without relying on centralized servers. By using these decentralized data storage solutions, individuals and organizations can safeguard their information, increase privacy, and contribute to a more resilient and distributed internet infrastructure. **Higher-Level Goals for Blob Storage** Blob storage via Blossom ,Perkeep and IPFS has goals to become a decentralized, self-sufficient protocol for data storage, management, and sharing. While some of these features are already being implemented, they represent a broader vision for the future of decentralized personal data management. 1. **Filesystem Backups** Allows for easy, incremental backups. Using the **`pk-put`** tool, users can back up files and directories quickly and efficiently. Incremental backups, which save only the changes made since the last backup, are essentially free, making Perkeep an efficient choice for backup solutions. This initial use case has already been implemented, providing seamless and secure backups for personal data. 2. **Efficient Remote Filesystem** The goal is to create a highly efficient, aggressively caching remote filesystem using Perkeep. A **read-only** version of this filesystem is already trivial to implement, while **read-write** functionality remains an area of active development. Every modification in the filesystem would be snapshotted implicitly, providing version control as a default. This would enable users to interact with their data in a remote environment while ensuring that every change is tracked and recoverable. 3. **Decentralized Sharing System** Perkeep is working towards enabling users to share data in a decentralized manner. The system will allow individuals to share anything with anyone or everyone, with privacy being the default setting. This decentralized sharing is already starting to work, and users can now share data with others while retaining control over who sees their information. 4. **Blog / Photo Hosting / Document Management CMS** Perkeep aims to replace traditional blog platforms, photo hosting services, and document management software. By running a **personal blog**, **photo gallery**, and **document management system (CMS)** on Perkeep, users will have full control over their content. Permissions will be configurable, allowing for personal or public sharing. The author intends to use Perkeep for his own blog, gallery, and document management needs, further demonstrating its versatility. 5. **Decentralized Social Networking** While still a lofty goal, decentralized social networking is a persistent aim for Perkeep. By implementing features like **comments** and **tagging**, users could attach metadata to images and content. Through claims, users could sign data and verify identities, promoting trust in social interactions. This would allow for decentralized social networking where users control their own data and interactions. 6. **Import/Export Adapters for Hosted Web Services** Perkeep intends to bridge the gap between decentralized storage and traditional hosted web services. This feature would allow users to **mirror data** between hosted services and their private Perkeep storage. Whether content is created in Perkeep or hosted services, the goal is to ensure that data is always backed up privately, ensuring users' data is theirs forever. ### Combined Goals for Blossom and IPFS Both Blossom and IPFS share common goals of decentralizing data storage, enhancing privacy, and providing users with greater control over their data. Together, these technologies enable: - **Self-Sovereign Data Management**: Empowering users to store and manage their data without relying on centralized platforms. - **Resilient and Redundant Storage**: Offering decentralized and redundant data storage that ensures availability and security. - **Private and Permissioned Sharing**: Enabling secure, private data sharing where the user controls who has access to their content. By focusing on these goals, both Blossom and IPFS are contributing to a future where individuals control their own data, collaborate more efficiently in decentralized networks and P4P protocols, and ensure the privacy and security of their digital assets. These technologies in conjunction with nostr lead one to discover user agency and autonomy, where you can actually own and interface with your own data allowing for value creation and content creation strategies. Donations via - lightninglayerhash@getalby.com @ d34e832d:383f78d0
2025-02-21 15:32:49Decentralized Publishing: ChainScribe: How to Approach Studying NIPs (Nostr Improvement Proposals) [npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv] How to Approach Studying NIPs (Nostr Improvement Proposals) NIPs (Nostr Improvement Proposals) provide a framework for suggesting and discussing improvements to the Nostr protocol, a decentralized network for open communication. Studying NIPs is crucial for understanding the evolution of Nostr and its underlying principles. To effectively approach this, it's essential to follow a systematic, structured process. 1. **Familiarize with the Nostr Protocol**: Before diving into the specifics of each NIP, gain a solid understanding of the core Nostr protocol. This includes its goals, architecture, and key components like pubkeys, events, and relays. 2. **Explore the NIP Catalog**: Visit [nostr-nips.com](https://nostr-nips.com/) to browse through the available NIPs. Focus on the most recent proposals and those that align with your interests or areas of expertise. 3. **Review the Proposal Structure**: Each NIP follows a standard structure, typically including a description of the problem, proposed solution, and rationale. Learn to read and evaluate these elements critically, paying attention to how each proposal aligns with Nostr’s decentralized ethos. 4. **Follow Active Discussions**: Many NIPs are actively discussed within the community. Follow relevant channels, such as GitHub issues or dedicated discussion forums, to understand community feedback and potential revisions. 5. **Understand Dependencies**: Some NIPs are designed to work in tandem with others or require other technological advancements. Recognize these relationships to better understand the broader implications of any proposal. 6. **Hands-On Testing**: If possible, test NIPs in a development environment to see how they function in practice. Experimenting with proposals will help deepen your understanding and expose potential challenges or flaws. 7. **Contribute to Proposals**: If you have insights or suggestions, contribute to the discussion or propose your own improvements. NIPs thrive on community participation, and your input can help shape the future of Nostr. Donations via - lightninglayerhash@getalby.com
@ d34e832d:383f78d0
2025-02-21 15:32:49Decentralized Publishing: ChainScribe: How to Approach Studying NIPs (Nostr Improvement Proposals) [npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv] How to Approach Studying NIPs (Nostr Improvement Proposals) NIPs (Nostr Improvement Proposals) provide a framework for suggesting and discussing improvements to the Nostr protocol, a decentralized network for open communication. Studying NIPs is crucial for understanding the evolution of Nostr and its underlying principles. To effectively approach this, it's essential to follow a systematic, structured process. 1. **Familiarize with the Nostr Protocol**: Before diving into the specifics of each NIP, gain a solid understanding of the core Nostr protocol. This includes its goals, architecture, and key components like pubkeys, events, and relays. 2. **Explore the NIP Catalog**: Visit [nostr-nips.com](https://nostr-nips.com/) to browse through the available NIPs. Focus on the most recent proposals and those that align with your interests or areas of expertise. 3. **Review the Proposal Structure**: Each NIP follows a standard structure, typically including a description of the problem, proposed solution, and rationale. Learn to read and evaluate these elements critically, paying attention to how each proposal aligns with Nostr’s decentralized ethos. 4. **Follow Active Discussions**: Many NIPs are actively discussed within the community. Follow relevant channels, such as GitHub issues or dedicated discussion forums, to understand community feedback and potential revisions. 5. **Understand Dependencies**: Some NIPs are designed to work in tandem with others or require other technological advancements. Recognize these relationships to better understand the broader implications of any proposal. 6. **Hands-On Testing**: If possible, test NIPs in a development environment to see how they function in practice. Experimenting with proposals will help deepen your understanding and expose potential challenges or flaws. 7. **Contribute to Proposals**: If you have insights or suggestions, contribute to the discussion or propose your own improvements. NIPs thrive on community participation, and your input can help shape the future of Nostr. Donations via - lightninglayerhash@getalby.com