-

@ c11cf5f8:4928464d
2025-02-23 20:42:52
Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about?
If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on.
originally posted at https://stacker.news/items/895134
-

@ 3ffac3a6:2d656657
2025-02-23 19:40:19
## Renoters: Proposal for Anonymous Event Relaying in Nostr
*This document is a proposal and not an official NIP.*
This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message.
### **Motivation**
While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity.
In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools.
### **Proposed Solution**
Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps:
1. **Event Creation:** The user creates the Nostr event they wish to publish.
2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen.
3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order:
- A *new* random Nostr private key (`sk_wrapper`) is generated.
- The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key).
- A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing.
4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path.
5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter.
6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network.
### **Example**
Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3.
1. Alice creates her event.
2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`.
3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`.
4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`.
5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`.
6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`.
7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`.
8. Alice publishes this final wrapper event.
R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event.
### **Renoter Incentives (using Cashu)**
To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism.
- **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it.
- **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it.
- **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service.
- **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed.
- **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means.
### **Security Threats and Mitigations**
- **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce:
- Random delays in event relaying.
- Dummy packets to complicate statistical analysis by malicious observers.
- **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again.
- **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network.
- **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat.
### **Operational Considerations**
- **Renoter Reliability:** The reliability of the Renoter network is crucial.
- **Latency:** Relaying through multiple Renoters will introduce latency.
- **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure.
This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability.
### **References**
- **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563)
- **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf)
- **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr)
- **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/)
- **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/)
- **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf)
#Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development
-

@ 2e8970de:63345c7a
2025-02-23 18:38:06
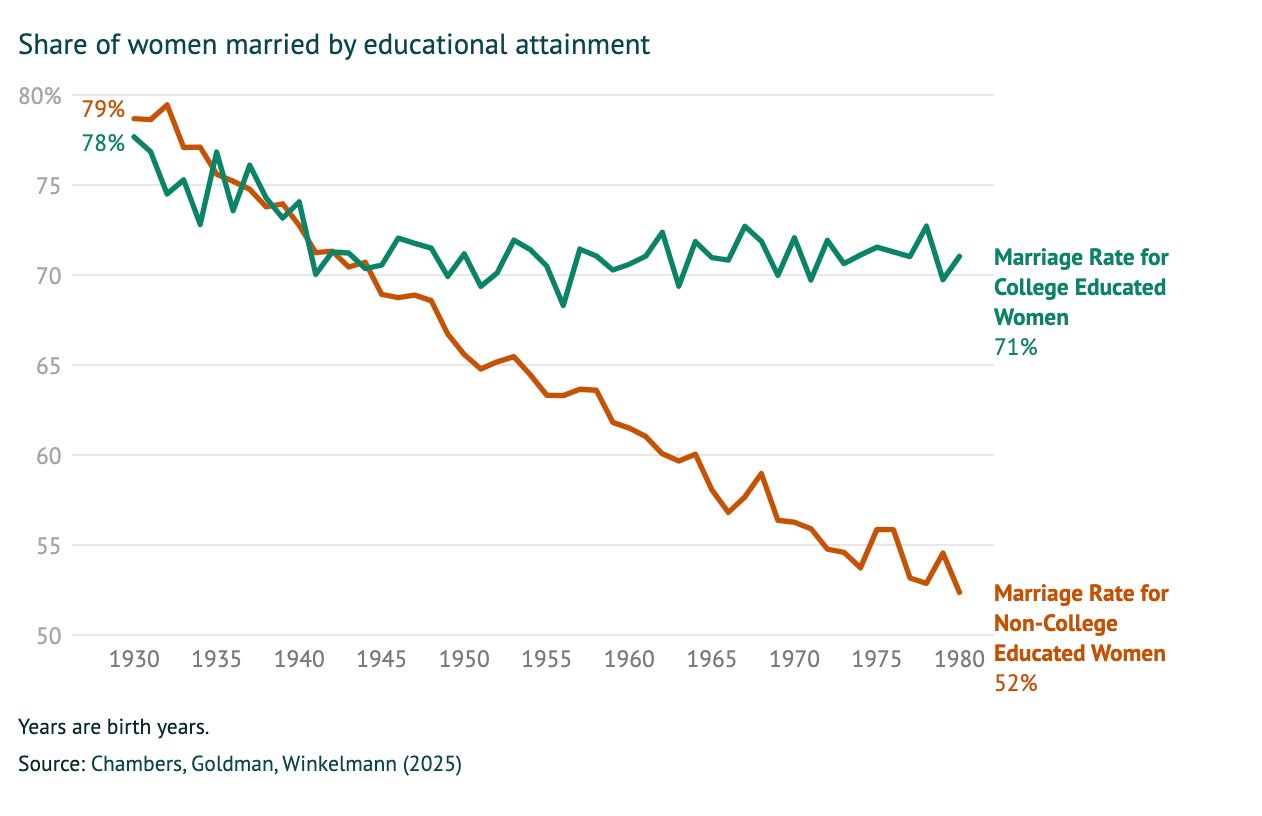
> 1 in 5 women with a BA are willing to marry a man without one
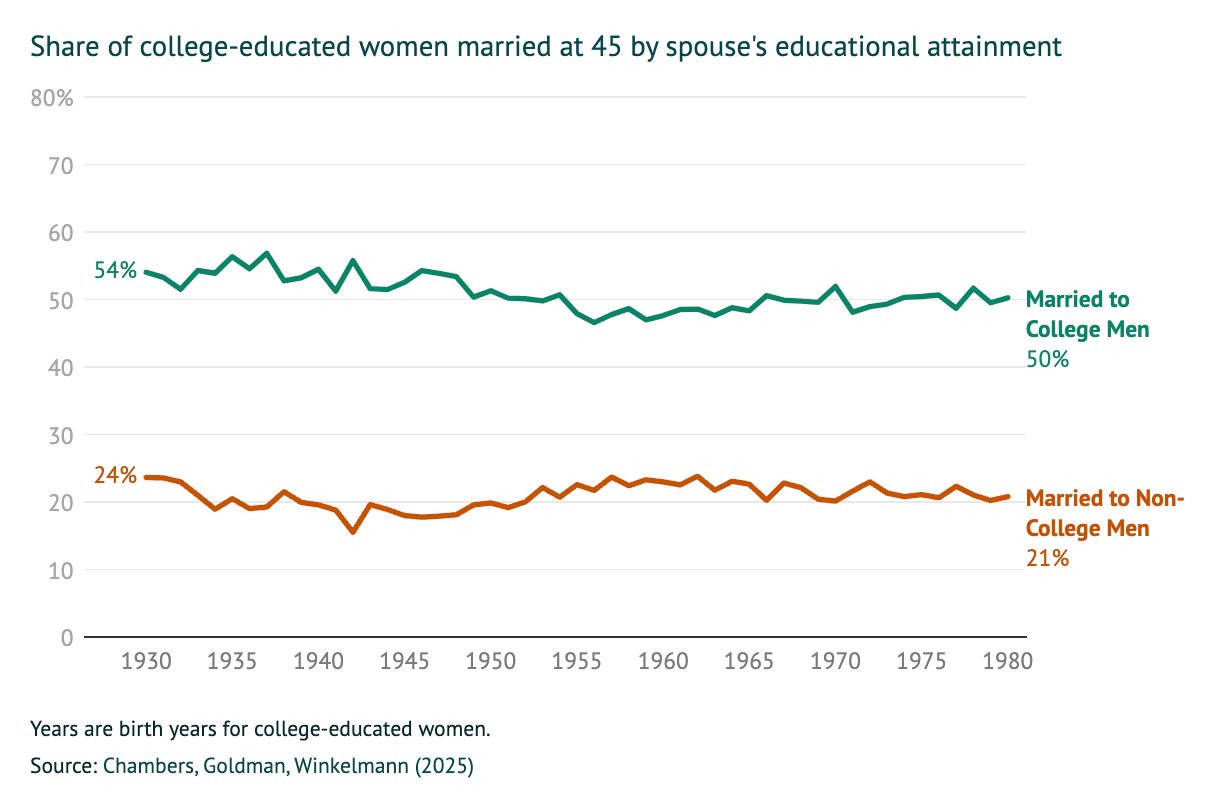
> But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically
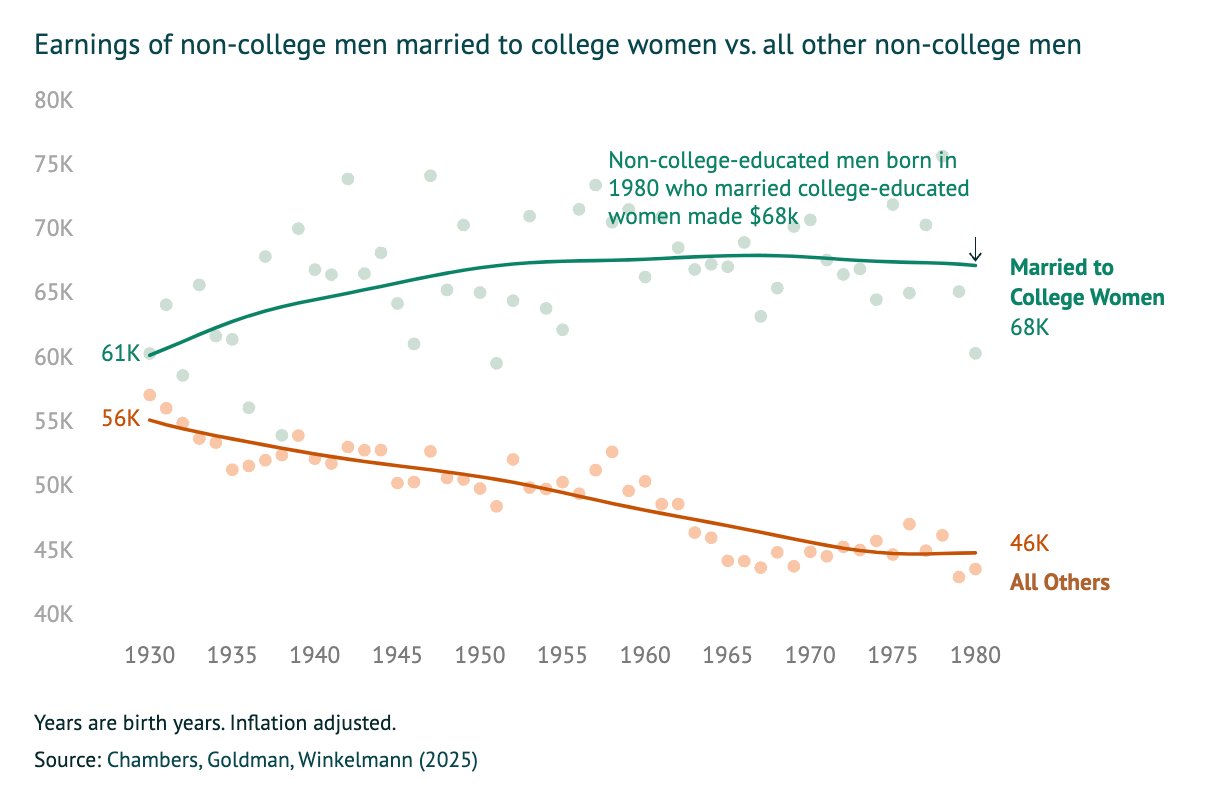
> Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married

https://aibm.org/research/will-college-educated-women-find-someone-to-marry/
originally posted at https://stacker.news/items/895044
-

@ da0b9bc3:4e30a4a9
2025-02-23 07:08:22
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/894609
-

@ e3ba5e1a:5e433365
2025-02-23 06:35:51
My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\.
Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group.
Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people.
As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them.
For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement.
There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope).
And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions.
A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join.
Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves.
When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view.
Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will.
My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed.
-

@ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46
Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick.
Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions.
Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them.
Here's the current state of the competition with your max possible score next to your nym:
| Contestant | MVP | Champ | All NBA | | | | |
|--------------|------|---------|----------|-|-|-|-|
| @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson |
| @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson|
| @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA |
| @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA|
| @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA|
| @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson|
| @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson|
| @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA|
| @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA|
| @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA|
| @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson |
| @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA|
| @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA|
| @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA|
**Prize**
At least 6k (I'll keep adding zaps to the pot).
If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details.
originally posted at https://stacker.news/items/894412
 @ c11cf5f8:4928464d
2025-02-23 20:42:52Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about? If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on. originally posted at https://stacker.news/items/895134
@ c11cf5f8:4928464d
2025-02-23 20:42:52Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about? If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on. originally posted at https://stacker.news/items/895134 @ 3ffac3a6:2d656657
2025-02-23 19:40:19## Renoters: Proposal for Anonymous Event Relaying in Nostr *This document is a proposal and not an official NIP.* This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message. ### **Motivation** While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity. In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools. ### **Proposed Solution** Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps: 1. **Event Creation:** The user creates the Nostr event they wish to publish. 2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen. 3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order: - A *new* random Nostr private key (`sk_wrapper`) is generated. - The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key). - A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing. 4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path. 5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter. 6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network. ### **Example** Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3. 1. Alice creates her event. 2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`. 3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`. 4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`. 5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`. 6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`. 7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`. 8. Alice publishes this final wrapper event. R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event. ### **Renoter Incentives (using Cashu)** To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism. - **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it. - **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it. - **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service. - **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed. - **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means. ### **Security Threats and Mitigations** - **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce: - Random delays in event relaying. - Dummy packets to complicate statistical analysis by malicious observers. - **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again. - **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network. - **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat. ### **Operational Considerations** - **Renoter Reliability:** The reliability of the Renoter network is crucial. - **Latency:** Relaying through multiple Renoters will introduce latency. - **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure. This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability. ### **References** - **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563) - **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf) - **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr) - **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/) - **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/) - **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf) #Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development
@ 3ffac3a6:2d656657
2025-02-23 19:40:19## Renoters: Proposal for Anonymous Event Relaying in Nostr *This document is a proposal and not an official NIP.* This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message. ### **Motivation** While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity. In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools. ### **Proposed Solution** Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps: 1. **Event Creation:** The user creates the Nostr event they wish to publish. 2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen. 3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order: - A *new* random Nostr private key (`sk_wrapper`) is generated. - The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key). - A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing. 4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path. 5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter. 6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network. ### **Example** Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3. 1. Alice creates her event. 2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`. 3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`. 4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`. 5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`. 6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`. 7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`. 8. Alice publishes this final wrapper event. R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event. ### **Renoter Incentives (using Cashu)** To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism. - **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it. - **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it. - **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service. - **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed. - **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means. ### **Security Threats and Mitigations** - **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce: - Random delays in event relaying. - Dummy packets to complicate statistical analysis by malicious observers. - **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again. - **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network. - **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat. ### **Operational Considerations** - **Renoter Reliability:** The reliability of the Renoter network is crucial. - **Latency:** Relaying through multiple Renoters will introduce latency. - **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure. This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability. ### **References** - **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563) - **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf) - **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr) - **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/) - **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/) - **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf) #Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development @ 2e8970de:63345c7a
2025-02-23 18:38:06 > 1 in 5 women with a BA are willing to marry a man without one  > But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically  > Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married  https://aibm.org/research/will-college-educated-women-find-someone-to-marry/ originally posted at https://stacker.news/items/895044
@ 2e8970de:63345c7a
2025-02-23 18:38:06 > 1 in 5 women with a BA are willing to marry a man without one  > But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically  > Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married  https://aibm.org/research/will-college-educated-women-find-someone-to-marry/ originally posted at https://stacker.news/items/895044 @ da0b9bc3:4e30a4a9
2025-02-23 07:08:22Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/894609
@ da0b9bc3:4e30a4a9
2025-02-23 07:08:22Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/894609 @ e3ba5e1a:5e433365
2025-02-23 06:35:51My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\. Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group. Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people. As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them. For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement. There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope). And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions. A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join. Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves. When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view. Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will. My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed.
@ e3ba5e1a:5e433365
2025-02-23 06:35:51My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\. Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group. Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people. As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them. For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement. There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope). And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions. A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join. Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves. When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view. Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will. My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed. @ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick. Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions. Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them. Here's the current state of the competition with your max possible score next to your nym: | Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson | | @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA| **Prize** At least 6k (I'll keep adding zaps to the pot). If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details. originally posted at https://stacker.news/items/894412
@ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick. Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions. Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them. Here's the current state of the competition with your max possible score next to your nym: | Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson | | @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA| **Prize** At least 6k (I'll keep adding zaps to the pot). If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details. originally posted at https://stacker.news/items/894412