-

@ a79bb203:dde63268
2024-11-16 21:38:18
I was quite happy with the result (about 3 hours of work)
https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMYNb.jpg
Bumblebees symbolize hard work, diligence, and productivity.
originally posted at https://stacker.news/items/770779
-

@ 5d4b6c8d:8a1c1ee3
2024-11-16 17:07:19
We almost all survived!
Sorry, @BlokchainB. You took what should have been a very safe Denver team and then neither their very good head coach nor the best player in the world showed up.
**Ode to the fallen**:
> In peace, may you leave this shore. In love, may you find the next. Safe passage on your travels, until our final journey to the ground. May we meet again.
Let's all pour one out for Blok.
----------
# Winners' Recap
The Pistons were really trying to get @supercyclone eliminated, but the Raptors were just too pathetic to hold onto the win.
Despite putting up almost 50 points in the first quarter, Cleveland let the lowly Bulls back into the game. Ultimately, I doubt @realBitcoinDog was ever particularly concerned that the now 14-0 Cavs would put Chicago away.
After seeming to have the game in hand, the Knicks somehow allowed cross-town rival Brooklyn back in the game. Thankfully for @gnilma's wallet, they made two big plays to close out the game.
The Magic, sans young star Paolo, clobbered the supposedly contending 76ers. @Carresan really never had to sweat this one.
In a game of which I watched not one second, the Hawks defeated the woeful Wizards and secured survival for the rest of us.
# Other Notable Games
The Jimmy-less Heat put a real whooping on the Pacers, who are looking miserable this season.
OKC continues winning, despite having no centers in their rotation. I think 6'3" Lu Dort might be playing center.
I caught a little bit of the Lakers, Warriors, and T-Wolves, all of whom looked good in their wins.
# Prize
Closing in on 50k!
originally posted at https://stacker.news/items/770488
-

@ 5d4b6c8d:8a1c1ee3
2024-11-16 00:24:01
I've got Heat-Pacers on and I'm excited about some of the later games.
Is anyone else tuning into the second night of the Emirates Cup?
originally posted at https://stacker.news/items/769843
-

@ f33c8a96:5ec6f741
2024-11-15 21:45:12
# Voltage Tipper ⚡
A Simple Lightning tipping app template built with NextJS and Voltage.
[Voltage Tipper Video Walkthrough](https://www.youtube.com/watch?v=y2eFBtRLRUk)
To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work!
[](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper)
**Run on Replit**
[https://replit.com/@voltage-cloud/voltage-tipper](https://replit.com/@voltage-cloud/voltage-tipper)
## Table of Contents
1. [Deployment](#deployment)
2. [Environment Variables](#environment-variables)
3. [API](#api)
4. [Contributing](#contributing)
5. [License](#license)
## Deployment
To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work!
[](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper)
## Environment Variables
- `NEXT_PUBLIC_HOST`: The host URL for your LND lightning node (not including port).
- `NEXT_PUBLIC_INVOICE_MACAROON`: The invoice macaroon.
- `NEXT_PUBLIC_READ_MACAROON`: The read-only macaroon.
#### Host
The host is your Node's 'API endpoint' you can copy it from your Voltage Dashboard, be sure to include 'https://'. Example: `https://plebdev.m.voltageapp.io`
#### Macaroons
The Invoice and Read macaroons are authentication tokens that allows you to interact with your LND node's REST API with permissions for reading data, and creating invoices. You can also grab a "Admin" macaroon for permissions to spend but that is not required here since we are only receiving through this webapp, so your funds are safu.
**You can find your Macaroons in your Voltage Dashboard by visiting Manage Access -> Macaroon Bakery**
## API
- `/api/lnurl`
Returns lnurlPay response object defined in [LUD-06](https://github.com/lnurl/luds/blob/luds/06.md)
- `/api/getlnurl`
Returns bech32 encoded lnurlPay
- `/.well-known/lnurlp/{NodeAlias}`
This is your lightning address endpoint, returns lnurlPay response defined in [LUD-16](https://github.com/lnurl/luds/blob/luds/16.md)
- `/api/callback?amount=21000`
This is your callback endpoint that will return an invoice when `amount` query parameter is passed with millisat value
## Contributing
Contributions are welcome! Please open an issue or submit a pull request.
## License
This project is licensed under the MIT License. See the LICENSE file for details.
-

@ 5d4b6c8d:8a1c1ee3
2024-11-15 21:03:43
This is a requested topic for a future podcast episode. I do have a giant spreadsheet with a bunch of stats and stuff in it to help figure this out, but I'm doing this off the top of my head.
# My Top 10
1. Jordan: 6 titles, 6 Finals MVPs, 5 MVPs, 1 DPOY, and tops by my eye test
2. Lebron: 4 titles, 4 Finals MVPs, 4 MVPs, 20 All-NBAs, holds virtually all the career playoff stats
3. Kareem: 6 titles, 2 Finals MVPs, 6 MVPs, 15 All-NBAs, also the greatest HS and college player ever
4. Wilt: 2 titles, 1 Finals MVP, 4 MVPs, 10 All-NBAs, holds virtually all single game and single season records
5. Magic: 5 titles, 3 Finals MVPs, 3 MVPs, 10 All-NBAs, greatest passer of all time and played every position
6. Bird: 3 titles, 2 Finals MVPs, 3 MVPs, 10 All-NBAs, most well-rounded player ever
7. Russell: 11 titles, 5 MVPs, 11 All-NBAs, greatest winner in the history of professional sports
8. Duncan: 5 titles, 3 Finals MVPs, 2 MVPs, 15 All-NBAs, most underrated player in NBA history
9. Kobe: 5 titles, 2 Finals MVPs, 1 MVP, 15 All-NBAs, 12 All-Defense teams, more All-Star MVPs than anyone
10. Steph: 4 titles, 1 Finals MVP, 2 MVPs, 10 All-NBA, greatest shooter ever
Honorable mentions: Shaq and Jokic
Shaq and Steph are a toss-up to me. I came down on the side of positional balance. You could think of this as an All-time 1st and 2nd team, rather than purely a top 10.
I expect Jokic to make it, but he's right in the middle of his prime and hasn't yet matched the career achievements of these guys.
Let the arguments begin!
originally posted at https://stacker.news/items/769603
-

@ f33c8a96:5ec6f741
2024-11-15 18:44:32
# Setting Up a React App from Scratch: A Minimal Guide
## Prerequisites
- Node.js and npm installed on your machine
- A text editor of your choice
## Step 1: Create a New Project Directory
```bash
mkdir my-react-app
cd my-react-app
```
## Step 2: Initialize the Project
```bash
npm init -y
```
This creates a package.json file with default values.
## Step 3: Install Dependencies
```bash
npm install react react-dom
npm install --save-dev parcel @babel/preset-react
```
## Step 4: Create Project Structure
Create the following files and directories:
```
my-react-app/
├── src/
│ ├── index.html
│ └── index.js
└── package.json
```
## Step 5: Set Up HTML
In src/index.html, add the following content:
```html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>My React App</title>
</head>
<body>
<div id="root"></div>
<script src="./index.js"></script>
</body>
</html>
```
## Step 6: Create React Entry Point
In src/index.js, add the following content:
```javascript
import React from 'react';
import ReactDOM from 'react-dom/client';
const App = () => {
return <h1>Hello, React!</h1>;
};
const root = ReactDOM.createRoot(document.getElementById('root'));
root.render(<App />);
```
## Step 7: Configure Babel
Create a .babelrc file in the project root:
```json
{
"presets": ["@babel/preset-react"]
}
```
## Step 8: Update package.json Scripts
Add the following scripts to your package.json:
```json
"scripts": {
"start": "parcel src/index.html",
"build": "parcel build src/index.html"
}
```
## Step 9: Run the Development Server
```bash
npm start
```
Your app should now be running at http://localhost:1234.
## Step 10: Build for Production
When you're ready to deploy:
```bash
npm run build
```
This will create a dist folder with your optimized production build.
---
Congratulations! You've set up a React app from scratch using Parcel. This setup provides a lightweight and modern development environment with minimal overhead.
-

@ f33c8a96:5ec6f741
2024-11-15 18:39:13
# node-backend-walkthrough

A step-by-step walkthrough on how to setup and deploy a nodejs backend built with Express / Knex / SQLite (dev db) / Postgres (production db)
## Step 1: Setting up your project / dependencies
### 1.1 Create a new Node.js project
To set up a new Node.js project, follow these steps:
- Create a new directory for your project by running the following command in the terminal:
`mkdir my-project`
- Navigate into the new directory by running:
`cd my-project`
- Initialize a new Node.js project by running:
`npm init -y`
### 1.2 Install necessary dependencies
To install the necessary dependencies for your project, run the following command in the terminal:
`npm install express knex sqlite3 dotenv pg nodemon helmet morgan`
This will install the following packages:
- express: A popular web framework for Node.js that simplifies the process of building web applications.
- knex: A SQL query builder for Node.js that provides a convenient way to interact with databases.
- sqlite3: A Node.js module that provides an SQLite database driver for use with Knex.
- dotenv: A zero-dependency module that loads environment variables from a .env file into process.env.
- pg: A PostgreSQL database driver for use with Knex, which enables you to connect and interact with PostgreSQL databases from your Node.js application.
- nodemon: A utility that monitors changes to your source code and automatically restarts your server, saving you from manually stopping and starting your server every time you make changes.
- helmet: A middleware that helps secure your Express app by setting various HTTP headers.
- morgan: A middleware that logs HTTP requests and responses.
You can install additional packages as needed for your project. Once the dependencies are installed, you can begin setting up your Node.js app with Express and Knex.
## Step 2: Setting up your Express server
### 2.1 Create an app.js file
To create the basic Express server, follow these steps:
Create a new file called app.js in the root directory of your project by running the following command in the terminal:
`touch app.js`
Open the app.js file in your preferred code editor.
### 2.2 Import necessary modules and middleware
To use Express, Knex, Dotenv, pg, helmet, and morgan in your app.js file, you need to import them at the top of the file:
```
const express = require('express');
const knex = require('knex');
const dotenv = require('dotenv');
const pg = require('pg');
const helmet = require('helmet');
const morgan = require('morgan');
require('dotenv').config();
```
### 2.3 Set up the server
To set up the server, you need to define the necessary routes and middleware, and configure any necessary settings. Here's an example:
```
const app = express();
const port = process.env.PORT || 5500;
// Middleware
app.use(express.json());
app.use(express.urlencoded({ extended: false }));
app.use(helmet());
app.use(morgan('common'));
// Routes
app.get('/', (req, res) => {
res.send('Hello, world!');
});
// Listen
app.listen(port, () => {
console.log(`Server running on port ${port}`);
});
module.exports = app;
```
In this example, we're creating a new instance of the Express application (app) and setting the port to listen on. We're also setting up some basic middleware to parse incoming requests (using the express.json() and express.urlencoded() middleware), as well as the helmet() and morgan() middleware for security and logging purposes. We're also defining a simple route that sends a "Hello, world!" message as the response. Finally, we're starting the server by calling the listen() method on the app instance.
You can now run `node app.js` in your termnial and start up the server!
You should now see your .listen() message in the terminal `Server running on port 5500` if there are no errors.
Now you can go into Insomnia or Postman and make a get request to `http://localhost:5500` and you should see your welcome message!
## Step 3: Setting up database config with settings for a local SQLite db and a production Postgres db
### 3.1 Create a knexfile.js file
To use Knex to manage your database, you need to create a knexfile.js file in the root directory of your project. This file will contain the configuration settings for your database, including the connection settings for your local SQLite database and your production Postgres database.
Here's an example knexfile.js:
```
module.exports = {
development: {
client: "sqlite3",
connection: {
filename: "./db/dev.sqlite3",
},
useNullAsDefault: true,
migrations: {
directory: "./db/migrations",
},
seeds: {
directory: "./db/seeds",
},
},
production: {
client: "pg",
connection: process.env.DATABASE_URL,
migrations: {
directory: "./db/migrations",
},
seeds: {
directory: "./db/seeds",
},
},
};
```
In this example, we're defining two environments: development and production. For the development environment, we're using SQLite as the database client and specifying a connection to a local file (./dev.sqlite3). We're also specifying the directories for our migrations and seeds.
For the production environment, we're using Postgres as the database client and specifying a connection to a URL stored in the process.env.DATABASE_URL environment variable. We're using the same directories for our migrations and seeds.
### 3.2 Create a database directory and config
To use the settings from your knexfile.js file in your Express server, you need to create a new directory called `db` (the directory our knexfile is referencing) and inside of db add a file called `dbConfig.js` to create a database instance.
Here's an example:
```
const knex = require('knex');
const config = require('../knexfile');
const env = process.env.NODE_ENV || 'development';
const db = knex(config[env]);
module.exports = db;
```
In this example, we're importing the knex library and the knexfile.js configuration settings. We're then setting the environment to use based on the NODE_ENV environment variable, defaulting to 'development' if the variable is not set. Finally, we're creating a new instance of the database using the configuration settings for the current environment and exporting it for use in our Express server.
You can customize this example to fit your specific needs by updating the configuration settings in your knexfile.js file, or using a different method to set the environment (such as using process.env.DB_ENV).
## Step 4: Setting up a user model and migration
### 4.1 Create a new migration
To set up a user model and database table, you will need to create a new migration file. Migrations are scripts that describe how to modify the database schema.
To create a new migration file, run the following command in your terminal:
`npx knex migrate:make create_users_table`
This will generate a new migration file inside the directory specified in the knexfile.js for migrations (e.g. /db/migrations in the example).
### 4.2 Define the user table schema
Open the newly created migration file and add the schema for the user table. Here is an example:
```
exports.up = function (knex) {
return knex.schema.createTable("users", function (table) {
// Creates an auto-incrementing PK column called id
table.increments("id").primary();
// Creates a text column called username which is both required and unique
table.string("username").notNullable().unique();
// Creates a text column called password which is required
table.string("password").notNullable();
// Creates a timestamp column called created_at which is both required and defaults to the current time
table.timestamps(true, true);
});
};
exports.down = function (knex) {
// Drops the entire table if it exists (opposite of createTable)
// This is useful for rolling back migrations if something goes wrong
return knex.schema.dropTableIfExists("users");
};
```
In this example, we are creating a users table with id, name, email, and password columns. The id column is a primary key, which will automatically generate a unique ID for each row added to the table. The email column is set to be unique, which means that it will be enforced as a unique constraint in the database. The timestamps method is used to automatically create created_at and updated_at columns for the table.
The down method describes how to undo the changes made by the up method.
### 4.3 Seed the database
To seed the database with initial data, you need to create seed files that contain the data you want to insert into your tables. Seed files should be named with a descriptive name and should be placed in the directory specified in your knexfile.js.
To create a new seed file, run the following command in your terminal:
`npx knex seed:make 01_users`
This will create a new seed file named 01_users.js in the seeds directory of your project. You can then edit this file to add the data you want to insert.
In your seed files, you can use Knex to insert data into your tables. Here's an example:
```
exports.seed = function(knex) {
// Deletes ALL existing entries
return knex('users').del()
.then(function () {
// Inserts seed entries
return knex('users').insert([
{ username: 'user1', password: 'password1' },
{ username: 'user2', password: 'password2' },
{ username: 'user3', password: 'password3' }
]);
});
};
```
In this example, we're deleting all existing entries in the users table and then inserting new entries. You can modify this code to match the data you want to insert into your table.
### 4.4 Run the migration
To apply the migration and create the users table in your database, run the following command in your terminal:
`npx knex migrate:latest`
This will execute all pending migrations and update your database schema.
### 4.5 Run the seeds
Now that the user table is created in our local database we can test it by running our seeds and attempting to save our dummy user objects into our database
To run your seed files run the following command in your terminal:
`npx knex seed:run`
Great now we have a local database, we have a schema for our users table, and a seed file with dummy data to save to our db and test our user schema!
## Step 5: Creating and testing a User model
### 5.1 Create a User model
Now that the users table has been created in the database, you can create a User model to interact with it.
These will be the methods that our endpoints call to make changes or get data from our database.
Create a new `models` directory in our `db/` directory and add a file called `User.js` in the models directory and add the following code:
```
// require the database configuration module
const db = require("../dbConfig");
module.exports = {
// a function to find a user by id
findById: (id) => {
// query the 'users' table for the user with the given id
return db("users").where({ id }).first();
},
// a function to create a new user
create: (user) => {
// insert the user object into the 'users' table and return the inserted user object
return db("users").insert(user).returning("*");
},
// a function to update an existing user with the given id
update: (id, user) => {
// update the user object in the 'users' table where the id matches and return the updated user object
return db("users").where({ id }).update(user).returning("*");
},
// a function to delete an existing user with the given id
delete: (id) => {
// delete the user from the 'users' table where the id matches
return db("users").where({ id }).del();
},
};
```
This model has four methods:
- findById: finds a user by their ID
- create: creates a new user in the database
- update: updates an existing user in the database
- delete: deletes a user from the database
Each method returns a Knex query object.
## 5.2 Add routes to interact with the User model
To test the User model, you need to add some routes to your Express app that interact with the User model.
- Create a `routers` directory at the root of your repository.
- Create a new file called `userRouter.js` in the routers directory with the following code:
```
const User = require("../db/models/User");
const router = require("express").Router();
// This route is for creating a new user.
router.post("/", async (req, res) => {
// Extracts the name, email, and password from the request body.
const { username, password } = req.body;
// Calls the User.create function and passes in the extracted values to create a new user.
const user = await User.create({ username, password });
// Sends the created user as a JSON response.
res.json(user);
});
// This route is for getting a user by ID.
router.get("/:id", async (req, res) => {
// Extracts the ID parameter from the request.
const { id } = req.params;
// Calls the User.findById function and passes in the ID to retrieve the user with that ID.
const user = await User.findById(id);
// Sends the retrieved user as a JSON response.
res.json(user);
});
// This route is for updating a user by ID.
router.put("/:id", async (req, res) => {
// Extracts the ID parameter from the request.
const { id } = req.params;
// Extracts the updated username, and password from the request body.
const { username, password } = req.body;
// Calls the User.update function and passes in the ID and updated values to update the user with that ID.
const user = await User.update(id, { username, password });
// Sends the updated user as a JSON response.
res.json(user);
});
// This route is for deleting a user by ID.
router.delete("/:id", async (req, res) => {
// Extracts the ID parameter from the request.
const { id } = req.params;
// Calls the User.delete function and passes in the ID to delete the user with that ID.
const user = await User.delete(id);
// Sends the deleted user as a JSON response.
res.json(user);
});
module.exports = router;
```
Now back in app.js, import the userRouter module and add a new /users route
Your updated app.js should look like this:
```
const express = require("express");
const knex = require("knex");
const dotenv = require("dotenv");
const pg = require("pg");
const helmet = require("helmet");
const morgan = require("morgan");
const userRouter = require("./routers/userRouter");
require("dotenv").config();
const app = express();
const port = process.env.PORT || 5500;
// Middleware
app.use(express.json());
app.use(express.urlencoded({ extended: false }));
app.use(helmet());
app.use(morgan("common"));
// Routes
app.get("/", (req, res) => {
res.send("Hello, world!");
});
// Points to the userRouter and adds the /users prefix to all routes in the userRouter.
app.use("/users", userRouter);
// Listen
app.listen(port, () => {
console.log(`Server running on port ${port}`);
});
module.exports = app;
```
You can now test these routes using a tool like Insomnia or Postman.
## Step 6: Deploying to Heroku
### 6.1 Create a new Heroku app
To deploy your Node.js app to Heroku, you need to create a new Heroku app. Follow these steps to create a new Heroku app:
- Log in to your Heroku account and navigate to the Heroku Dashboard.
- Click the "New" button in the top right corner and select "Create new app" from the dropdown menu.
- Enter a unique name for your app and select a region.
- Click the "Create app" button.
### 6.2 Connect your Heroku app to your GitHub repository
To connect your Heroku app to your GitHub repository, follow these steps:
- In the "Deploy" tab of your Heroku app dashboard, select "GitHub" as the deployment method.
- Connect your Heroku account to your GitHub account by clicking the "Connect to GitHub" button and following the prompts.
- Select the GitHub repository that contains your Node.js app.
- Choose the branch you want to deploy.
- Click the "Enable Automatic Deploys" button.
### 6.3 Set up environment variables on Heroku
To set up environment variables on Heroku, follow these steps:
- In the "Settings" tab of your Heroku app dashboard, click the "Reveal Config Vars" button.
- Enter the name and value for each environment variable you want to set.
- Click the "Add" button for each environment variable.
In this example, you would need to set the following environment variables:
DATABASE_URL: The connection URL for your production Postgres database. You can find this in the Heroku Postgres add-on settings.
NODE_ENV: The environment setting for your app. Set this to "production".
### 6.4 Deploy your app to Heroku
To deploy your app to Heroku, follow these steps:
- In the "Deploy" tab of your Heroku app dashboard, click the "Deploy Branch" button to deploy your app to Heroku.
- Wait for the deployment process to complete.
- Once the deployment is complete, click the "View" button to open your app in a new browser window.
That's it! Your Node.js app should now be deployed and running on Heroku. If you run into any issues, you can view the logs in the "More" tab of your Heroku app dashboard to help diagnose the problem.
-

@ f33c8a96:5ec6f741
2024-11-15 18:36:56
# pleb-node-template
A simple fullstack Lightning App template for learning / development with LND
## Features:
- Vite frontend with simple darkmode styling / form management / data display.
- LND-GRPC library reducing code and making LND methods easier to work with.
- Express server with basic middleware setup / routes for lightning methods.
- Prebuilt LND methods for creating/paying invoices, openeing/closing channels, and adding/removing peers.
## Local Setup (in regtest using Polar):
1. Make sure that you have [Docker Desktop](https://www.docker.com/products/docker-desktop/) and [Polar](https://lightningpolar.com) installed
2. Open Docker Desktop and wait for it to start
<img width="912" alt="image" src="https://user-images.githubusercontent.com/53542748/234646702-30806d33-85e6-42d2-9409-71c42d00ef4d.png">
3. Open Polar and create a new Lightning network
<img width="832" alt="image" src="https://user-images.githubusercontent.com/53542748/234647029-0c79aabf-6448-49f9-821c-dc54a407b637.png">
4. Create your network however you like, though for starting out it's best to have at least 2 LND nodes to talk to each other.
<img width="1426" alt="image" src="https://user-images.githubusercontent.com/53542748/234647812-84a1472d-2464-4874-b8c7-d6151686ca6b.png">
5. Start your network
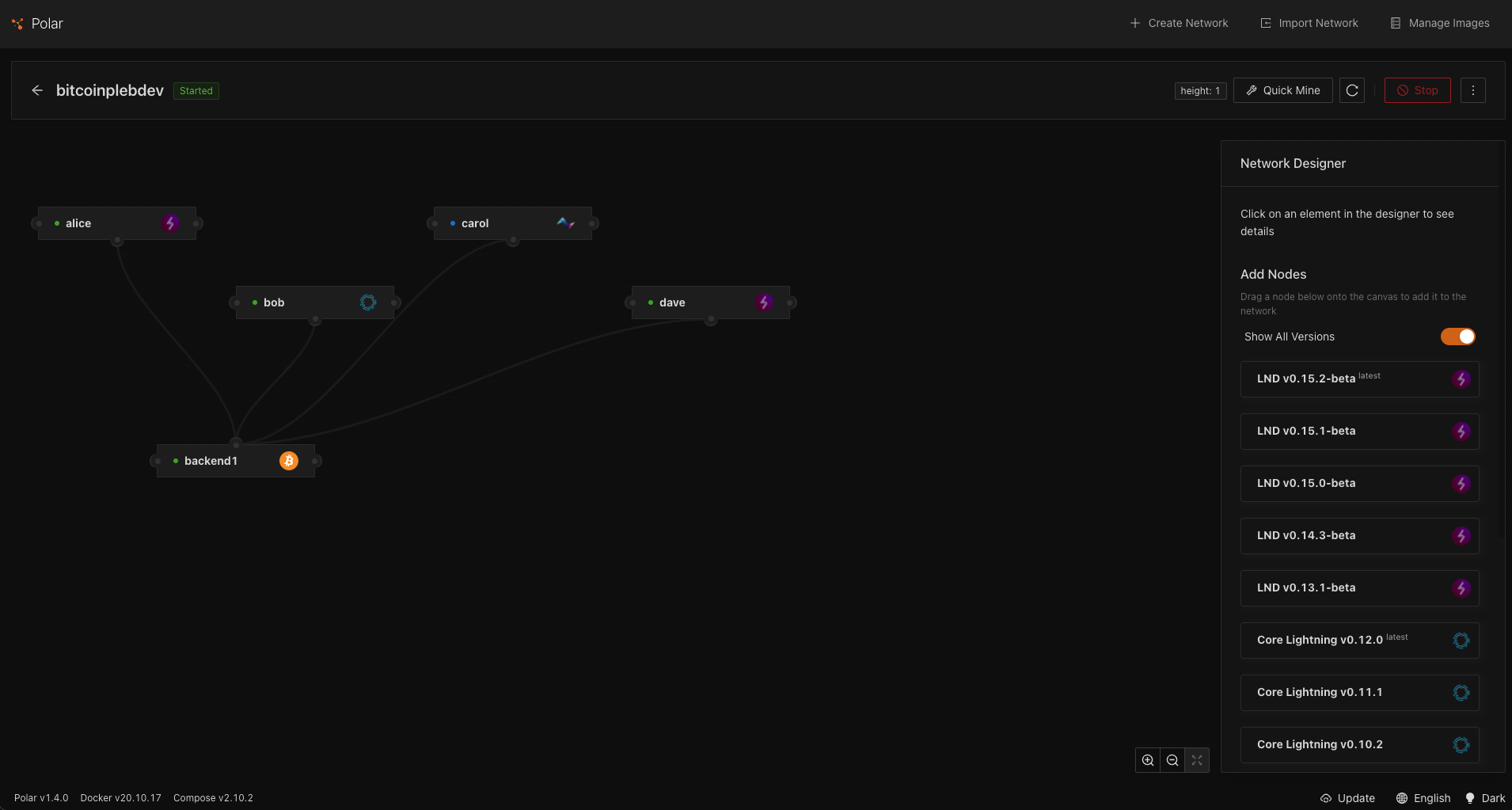
6. Click on the Alice node, visit the connect tab on the right, and copy the 'GRPC Host' value
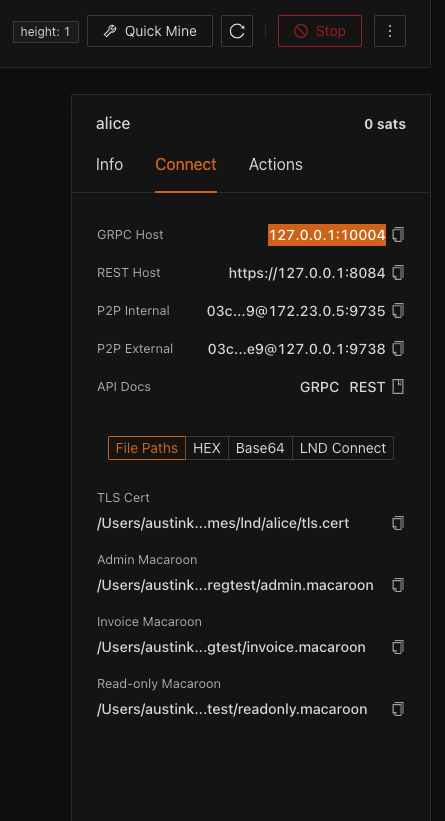
7. Add this as the value to LND_HOST in the .env.sample file
<img width="481" alt="image" src="https://user-images.githubusercontent.com/53542748/235537038-3ba636a8-0931-4db9-91cf-9ad4001781e7.png">
8. Go back to the Connect tab and copy the 'TLS Cert' and 'Admin Macaroon' File Paths and add them as the LND_CERT and LND_MACAROON in .env.sample
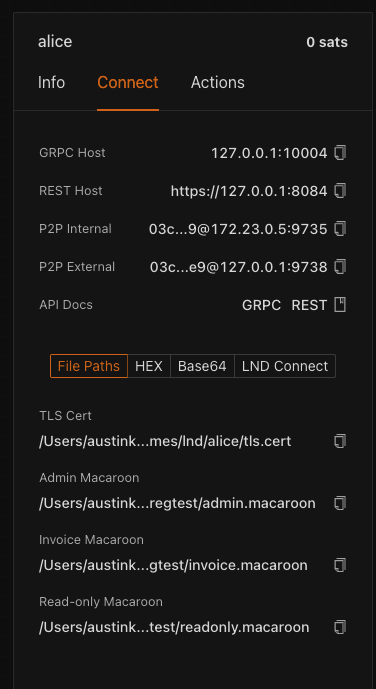
9. Rename the .env.sample to .env
<img width="258" alt="image" src="https://user-images.githubusercontent.com/53542748/235537647-875db3c9-c604-464c-9b61-386d08846a9f.png">
10. Open up the terminal and run `npm i` to install all of the packages and then run `npm run start' to start the server.
<img width="521" alt="image" src="https://user-images.githubusercontent.com/53542748/235538036-0d361a53-c36e-44e0-847c-b439a73172b5.png">
11. Open up a new terminal and run `cd frontend` to navigate to the frontend directory, run `npm i` to install all of the packages, now finally run `npm run dev` to start the frontend.
<img width="657" alt="image" src="https://user-images.githubusercontent.com/53542748/235538322-99afd03b-bc71-4a82-a4ac-fa4753acb57d.png">
12. Visit the Vite local host and you should see pleb-node running. Click 'Connect to your node' and you will see your pubkey and alias immediately populate. Click this button anytime you want to refresh.
<img width="1289" alt="image" src="https://user-images.githubusercontent.com/53542748/235538753-bf63e4e7-de63-4a98-84a0-44fa7e921898.png">
Now in combination with Polar you can open/close channels, create/pay invoices, and add/remove peers.
There is so much more you can do with LND then what is in pleb-node but this should be a great way for you to get started.
Check out lnd.js to see all of the lnd methods being called in pleb-node
-

@ f33c8a96:5ec6f741
2024-11-15 18:33:35
# Rustin Buster Cheatsheet
## Table of Contents
1. [Variable Declaration](#variable-declaration)
2. [Basic Data Types](#basic-data-types)
3. [Structs](#structs)
4. [Implementations (impls)](#implementations-impls)
5. [Enums](#enums)
6. [Pattern Matching](#pattern-matching)
7. [Vectors](#vectors)
8. [Ownership and Borrowing](#ownership-and-borrowing)
9. [Traits](#traits)
10. [Error Handling](#error-handling)
11. [Closures](#closures)
12. [Iterators](#iterators)
13. [Generics](#generics)
14. [Lifetimes](#lifetimes)
15. [Smart Pointers](#smart-pointers)
16. [Concurrency](#concurrency)
17. [Modules](#modules)
## Variable Declaration
In Rust, variables are immutable by default, promoting safer and more predictable code.
```rust
let x = 5; // Immutable variable
let mut y = 10; // Mutable variable
const MAX_POINTS: u32 = 100_000; // Constant
```
- `let` declares an immutable variable.
- `let mut` declares a mutable variable that can be changed later.
- `const` declares a constant, which must have a type annotation and be assigned a constant expression.
## Basic Data Types
Rust has several basic data types to represent numbers, characters, and strings.
```rust
let a: u32 = 42; // Unsigned 32-bit integer
let b: i64 = -100; // Signed 64-bit integer
let c: f32 = 3.14; // 32-bit floating-point number
let d: bool = true; // Boolean
let e: char = 'x'; // Character
let f: &str = "Hello, World!"; // String slice
let g: String = String::from("Hello, World!"); // Owned String
```
- `u32`: Unsigned 32-bit integer (0 to 4,294,967,295)
- `i64`: Signed 64-bit integer (-9,223,372,036,854,775,808 to 9,223,372,036,854,775,807)
- `f32`: 32-bit floating-point number
- `bool`: Boolean (true or false)
- `char`: Unicode scalar value
- `&str`: String slice (borrowed string)
- `String`: Owned string (can be modified)
## Structs
Structs are custom data types that group related data together.
```rust
struct Person {
name: String,
age: u32,
}
// Creating an instance of a struct
let person = Person {
name: String::from("Alice"),
age: 30,
};
// Accessing struct fields
println!("Name: {}", person.name); // Name: Alice
println!("Age: {}", person.age); // Age: 30
// Mutable struct instance
let mut mutable_person = Person {
name: String::from("Bob"),
age: 25,
};
mutable_person.age = 26; // Updating age field
// Tuple Struct
struct Point(i32, i32);
let point = Point(10, 20);
// Unit Struct (marker)
struct Unit;
let unit = Unit;
```
- Regular structs have named fields.
- Tuple structs have unnamed fields, accessed by index.
- Unit structs have no fields and are often used as markers.
## Implementations (impls)
Implementations allow you to define methods and associated functions for structs.
```rust
impl Person {
// Associated function (constructor)
fn new(name: &str, age: u32) -> Person {
Person {
name: String::from(name),
age,
}
}
// Method
fn say_hello(&self) {
println!("Hello, my name is {}", self.name);
}
// Mutable method
fn have_birthday(&mut self) {
self.age += 1;
}
}
// Using the `new` constructor and methods
let mut alice = Person::new("Alice", 30);
alice.say_hello(); // Hello, my name is Alice
alice.have_birthday();
println!("Alice's new age: {}", alice.age); // Alice's new age: 31
```
- Associated functions (like `new`) are called on the struct itself.
- Methods take `&self` or `&mut self` as the first parameter and are called on instances.
## Enums
Enums allow you to define a type that can be one of several variants.
```rust
enum Direction {
North,
South,
East,
West,
}
let direction = Direction::East;
enum OptionalInt {
Value(i32),
Nothing,
}
let x = OptionalInt::Value(42);
let y = OptionalInt::Nothing;
```
- Enums can have variants with no data, like `Direction`.
- Enums can also have variants with associated data, like `OptionalInt`.
## Pattern Matching
Pattern matching is a powerful feature in Rust for destructuring and matching against patterns.
```rust
match direction {
Direction::North => println!("Going North"),
Direction::South => println!("Going South"),
Direction::East => println!("Going East"),
Direction::West => println!("Going West"),
}
match x {
OptionalInt::Value(n) => println!("Value: {}", n),
OptionalInt::Nothing => println!("Nothing"),
}
```
- `match` expressions must be exhaustive, covering all possible cases.
- Pattern matching can destructure enums, tuples, and structs.
## Vectors
Vectors are dynamic arrays that can grow or shrink in size.
```rust
let mut vec = Vec::new();
vec.push(1);
vec.push(2);
vec.push(3);
let first = vec[0]; // 1
// Slices
let slice = &vec[1..3]; // Creates a slice of the vector from index 1 to 2
println!("Slice: {:?}", slice); // Slice: [2, 3]
// Iterating over vectors
for x in &vec {
println!("{}", x);
}
```
- Vectors can store elements of the same type.
- Slices are references to a contiguous sequence of elements in a collection.
- Vectors can be iterated over using a `for` loop.
## Ownership and Borrowing
Rust's ownership system is a key feature that ensures memory safety without a garbage collector.
```rust
let s1 = String::from("hello");
let s2 = s1; // s1 is invalid after this line
let s3 = s2.clone(); // Create a clone
let s4 = String::from("world");
let s5 = &s4; // Borrowing reference
println!("{}, {}", s5, s4); // world, world
```
- When a value is assigned to another variable, ownership is transferred (moved).
- To create a deep copy, use the `clone()` method.
- References allow you to refer to a value without taking ownership.
## Traits
Traits define shared behavior across types.
```rust
trait Summary {
fn summarize(&self) -> String;
}
struct Article {
headline: String,
content: String,
}
impl Summary for Article {
fn summarize(&self) -> String {
format!("{} - {}", self.headline, self.content.split_whitespace().take(5).collect::<Vec<&str>>().join(" "))
}
}
let article = Article {
headline: String::from("Rust Cheatsheet"),
content: String::from("This is a cheatsheet for the Rust programming language."),
};
println!("{}", article.summarize());
```
- Traits are similar to interfaces in other languages.
- Types can implement multiple traits.
- Trait methods can have default implementations.
## Error Handling
Rust uses the `Result` and `Option` types for error handling.
```rust
// Using Result
fn divide(x: f64, y: f64) -> Result<f64, String> {
if y == 0.0 {
Err(String::from("Division by zero"))
} else {
Ok(x / y)
}
}
match divide(10.0, 2.0) {
Ok(result) => println!("Result: {}", result),
Err(e) => println!("Error: {}", e),
}
// Using Option
fn find_user(id: u32) -> Option<String> {
if id == 1 {
Some(String::from("Alice"))
} else {
None
}
}
match find_user(1) {
Some(name) => println!("User found: {}", name),
None => println!("User not found"),
}
```
- `Result<T, E>` represents either success (`Ok(T)`) or failure (`Err(E)`).
- `Option<T>` represents either some value (`Some(T)`) or no value (`None`).
## Closures
Closures are anonymous functions that can capture their environment.
```rust
let add_one = |x: i32| x + 1;
println!("5 + 1 = {}", add_one(5));
```
- Closures can be used as arguments to higher-order functions.
- They can capture variables from their surrounding scope.
## Iterators
Iterators allow you to process sequences of elements.
```rust
let numbers = vec![1, 2, 3, 4, 5];
let doubled: Vec<i32> = numbers.iter().map(|&x| x * 2).collect();
println!("Doubled numbers: {:?}", doubled);
```
- Iterators are lazy and don't compute values until consumed.
- Many methods like `map`, `filter`, and `fold` are available on iterators.
## Generics
Generics allow you to write flexible, reusable code that works with multiple types.
```rust
fn largest<T: PartialOrd>(list: &[T]) -> &T {
let mut largest = &list[0];
for item in list.iter() {
if item > largest {
largest = item;
}
}
largest
}
let numbers = vec![34, 50, 25, 100, 65];
println!("The largest number is {}", largest(&numbers));
```
- `<T: PartialOrd>` specifies that the type `T` must implement the `PartialOrd` trait.
- Generics can be used with functions, structs, and enums.
## Lifetimes
Lifetimes ensure that references are valid for as long as they're used.
```rust
fn longest<'a>(x: &'a str, y: &'a str) -> &'a str {
if x.len() > y.len() {
x
} else {
y
}
}
let result;
{
let string1 = String::from("short");
let string2 = String::from("longer");
result = longest(string1.as_str(), string2.as_str());
}
println!("The longest string is {}", result);
```
- Lifetimes are denoted with an apostrophe, like `'a`.
- They ensure that references don't outlive the data they refer to.
## Smart Pointers
Smart pointers are data structures that act like pointers but have additional metadata and capabilities.
```rust
use std::rc::Rc;
let s = Rc::new(String::from("Hello, Rust!"));
let s1 = Rc::clone(&s);
let s2 = Rc::clone(&s);
println!("{} has {} strong references", s, Rc::strong_count(&s));
```
- `Rc<T>` (Reference Counted) allows multiple ownership of the same data.
- It keeps track of the number of references to a value.
## Concurrency
Rust provides tools for safe and efficient concurrent programming.
```rust
use std::thread;
use std::time::Duration;
let handle = thread::spawn(|| {
for i in 1..10 {
println!("hi number {} from the spawned thread!", i);
thread::sleep(Duration::from_millis(1));
}
});
handle.join().unwrap();
```
- `thread::spawn` creates a new thread.
- `handle.join()` waits for the spawned thread to finish.
## Modules
Modules help organize and encapsulate code.
```rust
mod math {
pub fn add(a: i32, b: i32) -> i32 {
a + b
}
}
use math::add;
println!("5 + 3 = {}", add(5, 3));
```
- `mod` defines a module.
- `pub` makes items public and accessible outside the module.
- `use` brings items into scope.
This cheatsheet covers many of the fundamental concepts in Rust. Each section provides code examples and explanations to help you understand and use these features effectively in your Rust programs.
-

@ f33c8a96:5ec6f741
2024-11-15 18:31:02
# JavaScript Cheatsheet for Beginners
## Table of Contents
1. [Variable Declaration](#variable-declaration)
2. [Basic Data Types](#basic-data-types)
3. [Operators](#operators)
4. [Objects](#objects)
5. [Functions](#functions)
6. [Arrays](#arrays)
7. [Conditional Statements](#conditional-statements)
8. [Loops](#loops)
9. [Error Handling](#error-handling)
10. [ES6+ Features](#es6-features)
11. [DOM Manipulation](#dom-manipulation)
12. [Event Handling](#event-handling)
13. [Asynchronous JavaScript](#asynchronous-javascript)
14. [Modules](#modules)
## Variable Declaration
In JavaScript, variables can be declared using `var`, `let`, or `const`.
```javascript
var x = 5; // Function-scoped variable (avoid using in modern JavaScript)
let y = 10; // Block-scoped variable
const MAX_POINTS = 100; // Constant (cannot be reassigned)
```
- `var` is function-scoped and hoisted (avoid using in modern JavaScript).
- `let` is block-scoped and can be reassigned.
- `const` is block-scoped and cannot be reassigned (but object properties can be modified).
## Basic Data Types
JavaScript has several basic data types.
```javascript
let num = 42; // Number
let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats)
let str = "Hello, World!"; // String
let bool = true; // Boolean
let nullValue = null; // Null
let undefinedValue; // Undefined
let symbol = Symbol("unique"); // Symbol (ES6+)
let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+)
```
- `Number`: Represents both integers and floating-point numbers.
- `String`: Represents textual data.
- `Boolean`: Represents `true` or `false`.
- `Null`: Represents a deliberate non-value.
- `Undefined`: Represents a variable that has been declared but not assigned a value.
- `Symbol`: Represents a unique identifier.
- `BigInt`: Represents integers larger than 2^53 - 1.
## Operators
JavaScript includes various types of operators for different operations.
```javascript
// Arithmetic Operators
let sum = 5 + 3; // Addition: 8
let diff = 10 - 4; // Subtraction: 6
let product = 3 * 4; // Multiplication: 12
let quotient = 15 / 3;// Division: 5
let remainder = 17 % 5;// Modulus: 2
let power = 2 ** 3; // Exponentiation: 8
let increment = 5;
increment++; // Increment: 6
let decrement = 5;
decrement--; // Decrement: 4
// Assignment Operators
let x = 10; // Basic assignment
x += 5; // Addition assignment (x = x + 5)
x -= 3; // Subtraction assignment
x *= 2; // Multiplication assignment
x /= 4; // Division assignment
x %= 3; // Modulus assignment
x **= 2; // Exponentiation assignment
// Comparison Operators
console.log(5 == "5"); // Equal to (with type coercion): true
console.log(5 === "5"); // Strictly equal to: false
console.log(7 != "7"); // Not equal to: false
console.log(7 !== "7"); // Strictly not equal to: true
console.log(10 > 5); // Greater than: true
console.log(10 >= 10); // Greater than or equal to: true
console.log(5 < 10); // Less than: true
console.log(5 <= 5); // Less than or equal to: true
// Logical Operators
let a = true, b = false;
console.log(a && b); // Logical AND: false
console.log(a || b); // Logical OR: true
console.log(!a); // Logical NOT: false
// Nullish Coalescing Operator (ES2020)
let nullValue = null;
let defaultValue = nullValue ?? "default"; // "default"
// Optional Chaining Operator (ES2020)
let user = {
address: {
street: "123 Main St"
}
};
console.log(user?.address?.street); // "123 Main St"
console.log(user?.contact?.email); // undefined
// Bitwise Operators
console.log(5 & 3); // Bitwise AND: 1
console.log(5 | 3); // Bitwise OR: 7
console.log(5 ^ 3); // Bitwise XOR: 6
console.log(~5); // Bitwise NOT: -6
console.log(5 << 1); // Left shift: 10
console.log(5 >> 1); // Right shift: 2
console.log(5 >>> 1); // Unsigned right shift: 2
// String Operators
let str1 = "Hello";
let str2 = "World";
console.log(str1 + " " + str2); // Concatenation: "Hello World"
let greeting = "Hello";
greeting += " World"; // Concatenation assignment
// Type Operators
console.log(typeof "Hello"); // "string"
console.log(typeof 123); // "number"
console.log(typeof true); // "boolean"
console.log(obj instanceof Object); // Check if object is instance of a class
```
Key points about operators:
- Arithmetic operators perform mathematical operations
- Assignment operators combine operation with assignment
- Comparison operators return boolean values
- Logical operators work with boolean values and provide short-circuit evaluation
- Nullish coalescing (??) provides a way to specify a default value
- Optional chaining (?.) safely accesses nested object properties
- Bitwise operators perform operations on binary representations
- String operators handle string concatenation
- Type operators help determine variable types
## Objects
Objects are collections of key-value pairs.
```javascript
let person = {
name: "Alice",
age: 30,
sayHello: function() {
console.log("Hello, my name is " + this.name);
}
};
// Accessing object properties
console.log(person.name); // Alice
console.log(person["age"]); // 30
// Calling object methods
person.sayHello(); // Hello, my name is Alice
// Adding a new property
person.job = "Developer";
// Object destructuring (ES6+)
let { name, age } = person;
console.log(name, age); // Alice 30
```
- Objects can contain properties and methods.
- Properties can be accessed using dot notation or bracket notation.
- New properties can be added dynamically.
- Object destructuring allows you to extract multiple properties at once.
## Functions
Functions are reusable blocks of code.
```javascript
// Function declaration
function greet(name) {
return "Hello, " + name + "!";
}
// Function expression
const multiply = function(a, b) {
return a * b;
};
// Arrow function (ES6+)
const add = (a, b) => a + b;
// Default parameters (ES6+)
function power(base, exponent = 2) {
return Math.pow(base, exponent);
}
console.log(greet("Alice")); // Hello, Alice!
console.log(multiply(3, 4)); // 12
console.log(add(5, 3)); // 8
console.log(power(3)); // 9
console.log(power(2, 3)); // 8
```
- Functions can be declared using the `function` keyword or as arrow functions.
- Arrow functions provide a more concise syntax and lexically bind `this`.
- Default parameters allow you to specify default values for function arguments.
## Arrays
Arrays are ordered lists of values.
```javascript
let fruits = ["apple", "banana", "orange"];
// Accessing array elements
console.log(fruits[0]); // apple
// Array methods
fruits.push("grape"); // Add to the end
fruits.unshift("mango"); // Add to the beginning
let lastFruit = fruits.pop(); // Remove from the end
let firstFruit = fruits.shift(); // Remove from the beginning
// Iterating over arrays
fruits.forEach(fruit => console.log(fruit));
// Array transformation
let upperFruits = fruits.map(fruit => fruit.toUpperCase());
// Filtering arrays
let longFruits = fruits.filter(fruit => fruit.length > 5);
// Reducing arrays
let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0);
// Spread operator (ES6+)
let moreFruits = ["kiwi", "pear"];
let allFruits = [...fruits, ...moreFruits];
```
- Arrays can contain elements of any type.
- Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array.
- Higher-order functions like `map`, `filter`, and `reduce` create new arrays.
- The spread operator `...` can be used to combine arrays.
## Conditional Statements
Conditional statements allow you to execute code based on certain conditions.
```javascript
let age = 18;
// if...else statement
if (age >= 18) {
console.log("You are an adult");
} else {
console.log("You are a minor");
}
// Ternary operator
let status = age >= 18 ? "adult" : "minor";
// switch statement
switch (age) {
case 13:
console.log("You're a teenager");
break;
case 18:
console.log("You're now an adult");
break;
default:
console.log("You're neither 13 nor 18");
}
```
- `if...else` statements allow you to execute different code blocks based on conditions.
- The ternary operator provides a concise way to write simple if-else statements.
- `switch` statements are useful when you have multiple conditions to check against a single value.
## Loops
Loops allow you to repeat code multiple times.
```javascript
// for loop
for (let i = 0; i < 5; i++) {
console.log(i);
}
// while loop
let count = 0;
while (count < 5) {
console.log(count);
count++;
}
// do...while loop
let x = 0;
do {
console.log(x);
x++;
} while (x < 5);
// for...of loop (ES6+)
let numbers = [1, 2, 3, 4, 5];
for (let num of numbers) {
console.log(num);
}
// for...in loop (for object properties)
let person = { name: "Alice", age: 30 };
for (let key in person) {
console.log(key + ": " + person[key]);
}
```
- `for` loops are commonly used when you know how many times you want to iterate.
- `while` loops continue as long as a condition is true.
- `do...while` loops always execute at least once before checking the condition.
- `for...of` loops are used to iterate over iterable objects like arrays.
- `for...in` loops are used to iterate over object properties.
## Error Handling
Error handling allows you to gracefully handle and recover from errors.
```javascript
try {
// Code that might throw an error
throw new Error("Something went wrong");
} catch (error) {
console.error("Caught an error:", error.message);
} finally {
console.log("This always runs");
}
// Custom error
class CustomError extends Error {
constructor(message) {
super(message);
this.name = "CustomError";
}
}
try {
throw new CustomError("A custom error occurred");
} catch (error) {
if (error instanceof CustomError) {
console.log("Caught a custom error:", error.message);
} else {
console.log("Caught a different error:", error.message);
}
}
```
- The `try` block contains code that might throw an error.
- The `catch` block handles any errors thrown in the `try` block.
- The `finally` block always executes, regardless of whether an error was thrown.
- You can create custom error types by extending the `Error` class.
## ES6+ Features
ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript.
```javascript
// Template literals
let name = "Alice";
console.log(`Hello, ${name}!`);
// Destructuring
let [a, b] = [1, 2];
let { x, y } = { x: 3, y: 4 };
// Default parameters
function greet(name = "Guest") {
console.log(`Hello, ${name}!`);
}
// Rest parameters
function sum(...numbers) {
return numbers.reduce((total, num) => total + num, 0);
}
// Spread operator
let arr1 = [1, 2, 3];
let arr2 = [...arr1, 4, 5];
// Arrow functions
const square = x => x * x;
// Classes
class Animal {
constructor(name) {
this.name = name;
}
speak() {
console.log(`${this.name} makes a sound.`);
}
}
// Promises
const fetchData = () => {
return new Promise((resolve, reject) => {
// Asynchronous operation
setTimeout(() => resolve("Data fetched"), 1000);
});
};
// Async/Await
async function getData() {
try {
const data = await fetchData();
console.log(data);
} catch (error) {
console.error(error);
}
}
```
- Template literals allow for easy string interpolation.
- Destructuring makes it easy to extract values from arrays or properties from objects.
- Default parameters provide fallback values for function arguments.
- Rest parameters allow functions to accept an indefinite number of arguments as an array.
- The spread operator can be used to expand arrays or objects.
- Arrow functions provide a concise syntax for writing function expressions.
- Classes provide a cleaner syntax for creating objects and implementing inheritance.
- Promises and async/await simplify asynchronous programming.
## DOM Manipulation
DOM manipulation allows you to interact with HTML elements on a web page.
```javascript
// Selecting elements
const element = document.getElementById("myElement");
const elements = document.getElementsByClassName("myClass");
const queryElement = document.querySelector(".myClass");
const queryElements = document.querySelectorAll(".myClass");
// Modifying elements
element.textContent = "New text content";
element.innerHTML = "<strong>New HTML content</strong>";
element.style.color = "red";
element.classList.add("newClass");
element.classList.remove("oldClass");
// Creating and appending elements
const newElement = document.createElement("div");
newElement.textContent = "New element";
document.body.appendChild(newElement);
// Removing elements
element.parentNode.removeChild(element);
// or
element.remove(); // Modern browsers
```
- The DOM (Document Object Model) represents the structure of an HTML document.
- You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`.
- Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`.
- New elements can be created with `createElement` and added to the DOM with `appendChild`.
- Elements can be removed using `removeChild` or the `remove` method.
## Event Handling
Event handling allows you to respond to user interactions and other events.
```javascript
const button = document.querySelector("#myButton");
// Adding event listeners
button.addEventListener("click", function(event) {
console.log("Button clicked!");
console.log("Event object:", event);
});
// Removing event listeners
function handleClick(event) {
console.log("Button clicked!");
}
button.addEventListener("click", handleClick);
button.removeEventListener("click", handleClick);
// Event delegation
document.body.addEventListener("click", function(event) {
if (event.target.matches("#myButton")) {
console.log("Button clicked using event delegation!");
}
});
// Preventing default behavior
const link = document.querySelector("a");
link.addEventListener("click", function(event) {
event.preventDefault();
console.log("Link click prevented");
});
```
- Event listeners can be added to elements using the `addEventListener` method.
- The event object contains information about the event that occurred.
- Event listeners can be removed using `removeEventListener`.
- Event delegation allows you to handle events for multiple elements with a single listener.
- `preventDefault` can be used to stop the default action of an event.
## Asynchronous JavaScript
Asynchronous JavaScript allows you to perform operations without blocking the main thread.
```javascript
// Callbacks
function fetchData(callback) {
setTimeout(() => {
callback("Data fetched");
}, 1000);
}
fetchData(data => console.log(data));
// Promises
function fetchDataPromise() {
return new Promise((resolve, reject) => {
setTimeout(() => {
resolve("Data fetched");
}, 1000);
});
}
fetchDataPromise()
.then(data => console.log(data))
.catch(error => console.error(error));
// Async/Await
async function fetchDataAsync() {
try {
const data = await fetchDataPromise();
console.log(data);
} catch (error) {
console.error(error);
}
}
fetchDataAsync();
// Fetch API
fetch('https://api.example.com/data')
.then(response => response.json())
.then(data => console.log(data))
.catch(error => console.error('Error:', error));
```
- Callbacks are functions passed as arguments to be executed later.
- Promises represent the eventual completion or failure of an asynchronous operation.
- Async/await provides a more synchronous-looking way to write asynchronous code.
- The Fetch API is a modern interface for making HTTP requests.
## Modules
Modules allow you to organize your code into reusable pieces.
```javascript
// math.js
export function add(a, b) {
return a + b;
}
export function multiply(a, b) {
return a * b;
}
// main.js
import { add, multiply } from './math.js';
console.log(add(5, 3)); // 8
console.log(multiply(4, 2)); // 8
// Default export
// utils.js
export default function sayHello(name) {
console.log(`Hello, ${name}!`);
}
// main.js
import sayHello from './utils.js';
sayHello("Alice"); // Hello, Alice!
```
- The `export` keyword is used to expose functions, objects, or primitives from a module.
- The `import` keyword is used to bring functionality from other modules into the current module.
- Default exports can be imported without curly braces and can be given any name when importing.
This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs.
-

@ f33c8a96:5ec6f741
2024-11-15 18:23:58
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/7dsR7um-DxA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ f33c8a96:5ec6f741
2024-11-15 18:21:00
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/QY6euaT_G_E?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ f33c8a96:5ec6f741
2024-11-15 18:06:42
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/tGVxP4RgyI4?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 468f729d:5ab4fd5e
2024-11-15 17:52:45
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 5d4b6c8d:8a1c1ee3
2024-11-15 15:07:59
Heading into episode 6, here's a rough outline of what we're planning on talking about.
~Stacker_Sports contest updates: UEFA, Cricket, NFL, NBA
Bitcoiner Athletes: two sports celebrities were in the bitcoin news recently
Hockey: a hot start for a surprising team
NFL
- our head-to-head fantasy matchup (if @grayruby still wants to talk about it after his team's reprehensible outing),
- which contenders are on the outside looking in,
- Why are the Bears so bad at picking OC's?
Tyson vs Paul
NBA
- By popular demand, KAT Corner makes a return
- Thoughts and expectations for the Emirates CUp
- Can the best player win MVP on a garbage team?
- Our early hits and misses of the season
Degenerate Corner: bets we're excited about, platforms we're excited about, ongoing bets we have with each other.
originally posted at https://stacker.news/items/769019
-

@ 07907690:d4e015f6
2024-11-15 10:10:05
PGP (Pretty Good Privacy) adalah protokol enkripsi yang digunakan untuk memastikan kerahasiaan, integritas, dan otentikasi data dalam komunikasi digital. Diciptakan oleh Phil Zimmermann pada tahun 1991, PGP menggunakan kombinasi teknik kriptografi asimetris (kunci publik dan kunci privat) serta simetris untuk melindungi informasi. Berikut adalah berbagai kegunaan PGP:
## Mengamankan Email (Enkripsi dan Dekripsi)
- Kegunaan: Melindungi isi email agar hanya penerima yang memiliki kunci privat yang benar yang dapat membacanya.
- Cara Kerja:
- Pengirim mengenkripsi email menggunakan kunci publik penerima.
- Hanya penerima yang memiliki kunci privat yang dapat mendekripsi dan membaca email tersebut.
- Contoh: Jurnalis yang berkomunikasi dengan informan atau organisasi yang mengirim data sensitif dapat menggunakan PGP untuk melindungi komunikasi mereka dari penyusup.
## Tanda Tangan Digital (Digital Signature)
- Kegunaan: Memastikan keaslian dan integritas pesan atau dokumen, memastikan bahwa pesan tidak diubah dan benar-benar berasal dari pengirim yang sah.
- Cara Kerja:
- Pengirim membuat tanda tangan digital menggunakan kunci privatnya.
- Penerima dapat memverifikasi tanda tangan tersebut menggunakan kunci publik pengirim.
- Contoh: Digunakan untuk memverifikasi keaslian dokumen hukum, email penting, atau perangkat lunak yang diunduh.
## Melindungi File dan Dokumen
- Kegunaan: Mengenkripsi file sensitif agar hanya orang yang memiliki kunci dekripsi yang benar yang dapat membukanya.
- Cara Kerja: File dienkripsi menggunakan kunci publik penerima, dan penerima menggunakan kunci privatnya untuk mendekripsinya.
- Contoh: Perusahaan dapat menggunakan PGP untuk mengenkripsi laporan keuangan, data pelanggan, atau informasi penting lainnya sebelum membagikannya.
## Mengamankan Backup Data
- Kegunaan: Mengenkripsi cadangan data penting untuk melindunginya dari akses yang tidak sah.
- Cara Kerja: File backup dienkripsi dengan PGP sebelum disimpan, sehingga meskipun backup dicuri, data tetap aman.
- Contoh: Organisasi menyimpan cadangan data klien di server eksternal yang dienkripsi dengan PGP untuk mencegah kebocoran data.
## Perlindungan Identitas dan Anonimitas
- Kegunaan: Melindungi identitas pengirim dan penerima dalam komunikasi online.
- Cara Kerja: Penggunaan enkripsi end-to-end menjamin bahwa hanya pihak yang berwenang yang dapat membaca pesan.
- Contoh: Aktivis atau peneliti yang bekerja di negara dengan pengawasan ketat dapat menggunakan PGP untuk melindungi komunikasi mereka.
## Memverifikasi Integritas Perangkat Lunak
- Kegunaan: Memastikan bahwa perangkat lunak atau paket yang diunduh berasal dari sumber yang terpercaya dan tidak dimodifikasi oleh pihak ketiga.
- Cara Kerja: Pengembang menandatangani perangkat lunak menggunakan kunci privat mereka, dan pengguna dapat memverifikasi tanda tangan menggunakan kunci publik yang disediakan.
- Contoh: Distribusi Linux atau aplikasi open-source sering kali menyertakan tanda tangan PGP untuk memverifikasi keasliannya.
## Komunikasi di Forum atau Jaringan Terdistribusi
- Kegunaan: Memastikan privasi komunikasi di platform terdesentralisasi atau anonim.
- Cara Kerja: Pesan dienkripsi sebelum dikirim dan hanya dapat didekripsi oleh penerima yang sah.
- Contoh: Pengguna di forum yang membahas topik sensitif dapat menggunakan PGP untuk melindungi identitas mereka.
---
## Mengapa PGP Penting?
- Keamanan yang Kuat: Kombinasi kriptografi asimetris dan simetris membuat PGP sangat sulit ditembus oleh peretas.
-Privasi: Menjaga komunikasi Anda tetap aman dan pribadi dari penyadapan atau pengawasan.
- Integritas: Memastikan bahwa pesan atau data yang dikirim tidak diubah selama transmisi.
- Otentikasi: Membuktikan identitas pengirim melalui tanda tangan digital.
---
## Kelebihan PGP
- Sangat Aman: Jika digunakan dengan benar, PGP menawarkan tingkat keamanan yang sangat tinggi.
- Terbuka: Banyak digunakan di kalangan profesional dan komunitas open-source.
- Fleksibel: Dapat digunakan untuk berbagai keperluan, mulai dari komunikasi email hingga penyimpanan data.
## Kekurangan PGP
- Kompleks untuk Pemula: Relatif sulit digunakan oleh pengguna awam.
- Pengelolaan Kunci yang Rumit: Memerlukan pengelolaan kunci publik/privat yang benar.
- Tidak Ada Pemulihan Data: Jika kunci privat hilang, data yang dienkripsi tidak dapat dipulihkan.
---
PGP adalah alat yang sangat berguna untuk memastikan keamanan dan privasi dalam komunikasi dan data. Dengan meningkatnya risiko kejahatan siber, penggunaan PGP menjadi semakin penting, terutama di sektor yang menangani data sensitif.
-

@ bcea2b98:7ccef3c9
2024-11-14 23:38:37
@chess a3
originally posted at https://stacker.news/items/768303
-

@ dbb19ae0:c3f22d5a
2024-11-14 20:39:37
Hello,
As I've registered with Alby a few months ago I told a friend (who complained about the current toxicity of twitter/X) about this new social media Nostr and told him he could get rewarded for posting.
The deal was that I would help him to create his nostr account and get a wallet, https://guides.getalby.com/user-guide/alby-account-and-browser-extension
downloading the extension, creating the nostr account was a breeze, and then ....
As I wanted to send him a few sats to get started
that is when the whole thing went down.
Alby is now forcing its users to get a hub (and a channel), this was not my experience when I started back in March 2024 and I was surprised of this new direction Alby is taking.
Opening a channel costs ~25K sat -- and that was not expected, for a brand new user
Now my friend thinks that this whole new social media and bitcoin stuff is all a big scam.
What can I do?
Is there a way to open a wallet (compatible with Nostr) elsewhere?
originally posted at https://stacker.news/items/768090
-

@ bcea2b98:7ccef3c9
2024-11-14 18:03:14
We all have that one movie or show we turn to when we need a little comfort. Whether it’s for the laughs, the nostalgia, or the familiar characters, these are the ones that never get old.
What’s a movie or series you can watch again and again? What makes it so comforting, and why do you keep coming back to it?
I enjoy The Office with Michael Scott and Dwight Schrute. We watched a lot of that in the past and then again during the pandemic during isolation.
originally posted at https://stacker.news/items/767870
-

@ e968e50b:db2a803a
2024-11-14 17:03:38
<sub>TLDR: No, but if you own bitcoin and can afford to, you should get one anyway.</sub>
# Secure the network.
First off, I'm not mining to heat my house, and I'm not mining to earn bitcoin. I'm not mining out of the goodness of my heart either. I'm mining because I store my family's savings in bitcoin, and mining centralization looks like a real threat to me. I've written about it [here](https://stacker.news/items/629837) and [here](https://stacker.news/items/735779) if you're interested in reading more about why this is so important for average bitcoiners. That being said, I'd like to earn (or at least not lose) bitcoin in the process, and I'd also love to heat my home with it.


# Nano 3
In one of the aforementioned posts, I made a stink about how little hash one contributes with a lottery miner and @OT called me out on ignoring hardware centralization concerns with Bitmain. Well, Canaan isn't exactly a small company, and they're not open source, but they aren't Bitmain, and I found a miner that's about eight times as powerful as the virtual signaling[^1] solo miners at about the same cost.
My big find was the Nano 3. It's actually marketed as a space heater with three heating settings. At it's warmest, this guy mines at 4TH/s and uses about 140 watts. So it's about as efficient as a midrange s19, hashes about the a third as much as an s9, and costs as much as a Bitaxe. As a tool for decentralization, I'd say that's a great combo.
Ironically, most of the folks I see talking about it online are shitcoiners that use it to solo mine Bitcoin Cash. I wonder if this phenomenon is culturally turning bitcoiners off to a better decentralizing tool.


# Recycled Heat
So, now that I have them, I can tell you from personal experience how they're doing as heaters. Well, they are pushing heat out. However, it's a very small fraction of what my s9s do. They look better in house[^2], and they're significantly quieter (but not silent), but there's no way these guys are going to let me go furnace free this winter like a similar amount[^3] of Bitmain products would do.
#Conclusion
So I don't see the Nano 3 as the silver bullet for home miners. I do, however, think it's a great option and am not at all bummed with my purchase. At my current electricity price, I'll pay them off (even denominated in bitcoin) at some point. But I'm also going back to the drawing board about trying to replace my furnace with miners.
[^1]: totally unfair characterization... I get it. Just trying to make a point with some hyperbole
[^2]: The lighting is also pretty cool. You can make it pulse or strobe, and the full color spectrum is available. They're keep my kids' rooms a LITTLE bit warmer this winter and double as a cool night lite that teaches them about bitcoin. The ones in living areas do the same for guests. I consider these non-trivial features.
[^3]: Similar price too! Most s9s online are about the same price as the Nano 3s.
originally posted at https://stacker.news/items/767748
-

@ 5d4b6c8d:8a1c1ee3
2024-11-14 15:30:36
So, I had been maintaining a position of not muting anyone on Stacker News. In part, that's because I don't want SN to become an echo chamber like so much of the rest of social media. I also don't want to risk missing out on something valuable that someone has to say, just because I don't like them.
As I hope is clear to everyone here, and my record is fairly abundant, I'll engage on just about any topic with just about anyone. I've had many civil disagreements with folks (as well as some uncivil ones): sometimes I change my mind, sometimes I don't, but I do always listen to what the other person said and try to understand where they're coming from. I don't argue to win (shifting the goal posts when the other person makes a good point or simply ignoring it), but rather to learn.
High-level civil disagreements are one of the things that sets Stacker News apart from the rest of the internet.
What finally got someone muted was not their opinion (which I do disagree with), but their conduct. We had gone through the same tedious argument several times and the person never engaged with my points, but just kept repeating their assertions. When they attempted to start the same argument again recently, I told them I wasn't interested in rehashing it with them and they could go reread our past exchanges to see what I think. Rather than respect my wishes, the person belligerently insisted on pressing their argument. When I set my terms for continuing the conversation (read our past exchanges and bring up something new), they resorted to name calling. Mute.
As much as I enjoy talking about stuff and having disagreements, I don't owe anyone my time or attention. If someone tells me that they're sick of talking to me about something, I will drop it (or I will at least acknowledge that I should have). I expect the same courtesy from others. Have some respect for the person you're interacting with, if you want them to interact with you.
Have whatever opinion you want, but argue it in good faith and be respectful.
originally posted at https://stacker.news/items/767536
-

@ 7b8a7a4b:910f3874
2024-11-14 10:05:23
123 test test
originally posted at https://stacker.news/items/459399
-

@ 4ba8e86d:89d32de4
2024-11-14 09:17:14
Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade.
Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
## O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
## O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular;
• Computador com adb;
• Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular;
• Termux;
• Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular;
• Lista de bloatwares para seu dispositivo;
## Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
## Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid:
https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
## Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
```
Samsung Galaxy Note 10 Plus bloatware list
```
Provavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
### De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
## Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
## Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
## Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
## Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
```
./adb start-server
```
O resultado deve ser:
*daemon not running; starting now at tcp:5037
*daemon started successfully
E caso não apareça nada, execute:
```
./adb kill-server
```
E inicie novamente.
Com o adb conectado ao celular, execute:
```
./adb shell
```
Para poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized.
This adb server’s $ADB_VENDOR_KEYS is not set
Try ‘adb kill-server’ if that seems wrong.
Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
## No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
```
pkg install android-tools
```
Quando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
```
adb pair localhost:porta CódigoDeEmparelhamento
```
De acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
```
adb connect localhost:porta
```
Obs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
```
adb shell
```
Remoção na prática
Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
```
pm uninstall –user 0 com.google.android.apps.maps
```
E pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
```
cmd package install-existing nome.do.pacote
```
## Pós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências:
Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264
http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-

@ b4403b24:83542d4e
2024-11-14 00:55:14
Donald Trump officially announced his nomination of Tucker Carlson for a White House Press Secretary. 🫶
originally posted at https://stacker.news/items/766758
-

@ bcea2b98:7ccef3c9
2024-11-14 00:42:08
Sometimes we come across values that resonate deeply only after going through certain experiences. These values may not have been obvious to us earlier, but now they play a meaningful role in how we approach life.
Is there a value you’ve discovered later in life that’s become important to you?
originally posted at https://stacker.news/items/766754
-

@ b4403b24:83542d4e
2024-11-13 21:00:29
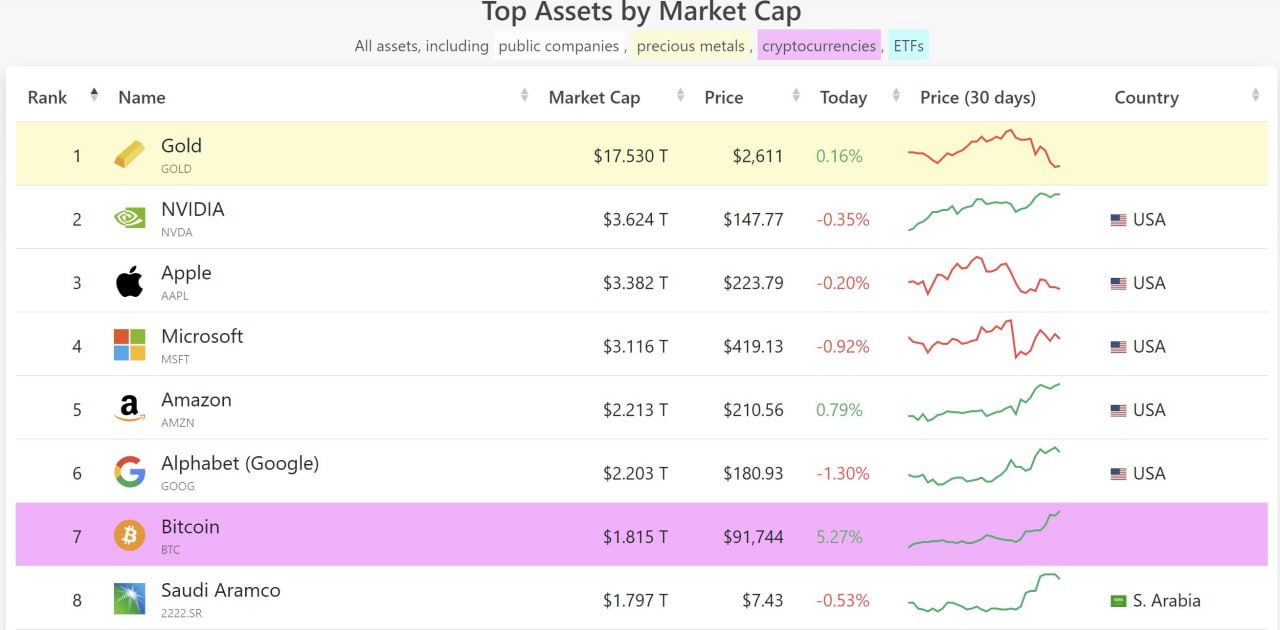
originally posted at https://stacker.news/items/766497
-

@ 000002de:c05780a7
2024-11-13 19:46:44
Here's the official list.
[A-Z index of U.S. government departments and agencies | USAGov](https://www.usa.gov/agency-index).
My answer: Department of Education
Why?
* Its completely unnecessary. Every state has its own.
* It is a mechanism for centralizing thought.
* It wields great influence over schools and states with its massive budget
* If you want to change the future of the nation in a positive direction stop allowing progressives manipulate the minds of the youth.
* Decentralizing to at least the state level puts more power back into the states vs. a single agency that is largely unaccountable.
What do you think?
originally posted at https://stacker.news/items/766383
-

@ 6f170f27:711e26dd
2024-11-13 19:17:52
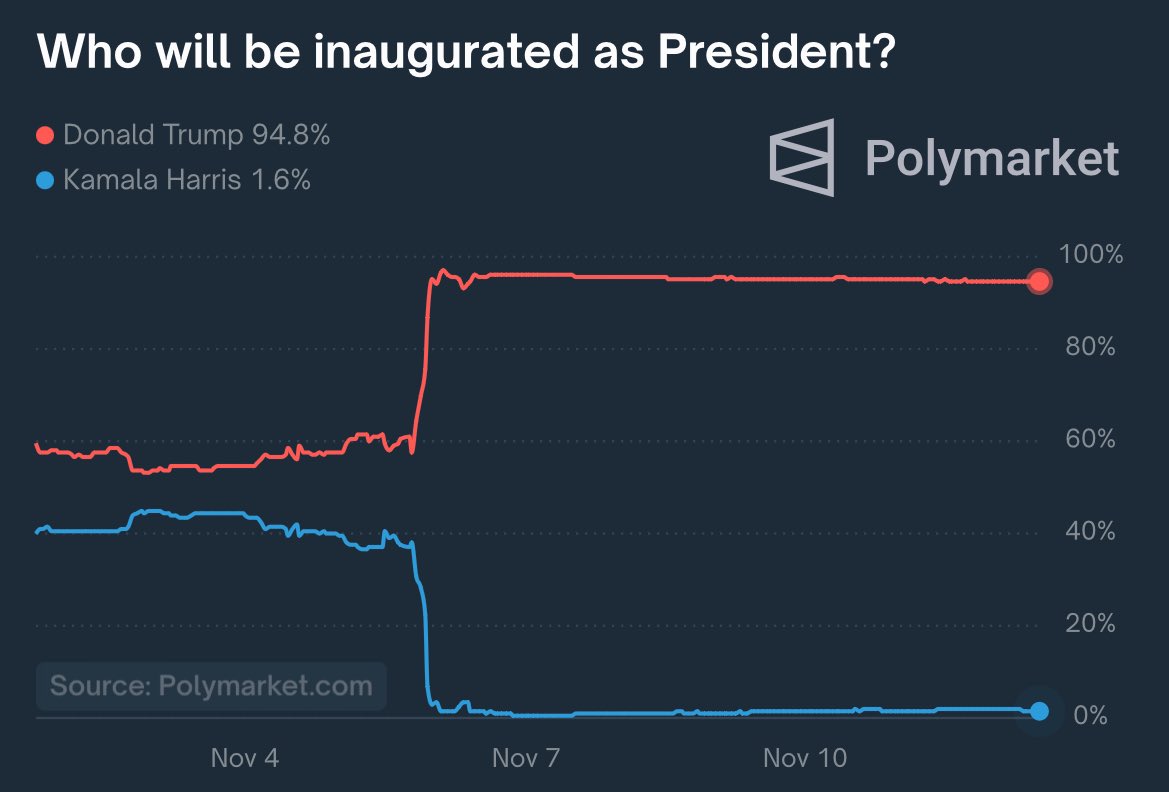
originally posted at https://stacker.news/items/766349
-

@ 5d4b6c8d:8a1c1ee3
2024-11-13 18:46:27
We've got two of our three re-buys on the books, with the third expected to come in once @BlokchainB recovers from his recent slate of sports defeats. We've all been there, Blok.
I like these second round options much more than round 1. Once again, I'll put off my pick for a day or two, but I'm looking at the Pacers, Hawks, Lakers, Rockets, and Nuggets. I might want to save a couple of them for later, so the Hawks could be the most attractive option.
# Friday's Games
- Heat @ Pacers
- 76ers @ Magic
- Pistons @ Raptors
- Wizards @ Hawks
- Bulls @ Cavs
- Nets @ Knicks
- Lakers @ Spurs
- Clippers @ Rockets
- Nuggets @ Pelicans
- Suns @ Thunder
- Grizzlies @ Warriors
- T-Wolves @ Kings
Picks due by tip-off of the game you're choosing on Friday.
# Prize Pool
40 kilosats! (with 5k more on the way)
originally posted at https://stacker.news/items/766272
-

@ 5d4b6c8d:8a1c1ee3
2024-11-13 15:05:59
That was a great night of basketball!
The Steph-Klay reunion easily met expectations and was another reminder of just how great Steph Curry is. It also cemented the Warriors as legit contenders this season.
We also had three big upsets, with Boston, Miami, and Minnesota all losing to likely lottery teams. Boston and Miami cost @siggy47, @BlokchainB, and @supercyclone their first strike (Let me know in the comments if you want to buy-back in).
The Miami loss had to be the craziest, as no one expects Spoelstra to pull a Webber and try to call a timeout he doesn't have.
Boston's loss was quite embarrassing in it's own right, though, since all they needed to do is complete a wide open in-bounds pass. This team still seems to have some issue performing under pressure.
What were your impressions of last night's games and the Emirates Cup so far?
# Prize
Still about 30k, but will be 45k if last night's losers buy back in (C'mon guys, it was just an off night. You've got this!).
I'll get the round 2 picks post up later today.
originally posted at https://stacker.news/items/765972
-

@ bcea2b98:7ccef3c9
2024-11-13 02:44:17
@chess a3
originally posted at https://stacker.news/items/765445
-

@ bcea2b98:7ccef3c9
2024-11-13 02:18:58
Sometimes our strongest values are the ones that people wouldn’t expect. These unique principles often reveal something special about who we are and what we believe in. Do you hold a value that might surprise others?
originally posted at https://stacker.news/items/765433
-

@ 6f170f27:711e26dd
2024-11-12 21:12:17

Less Chinese PhD student enroll in US universities. Less Chinese PhD students in the US get jobs in the US.
The start of this trend aligns suspicously good with the start us the US-Chinese trade war.
Source:
> Building a Wall Around Science: The Effect of U.S.-China Tensions on International Scientific Research
https://www.nber.org/papers/w32622
originally posted at https://stacker.news/items/765173
-

@ 5d4b6c8d:8a1c1ee3
2024-11-12 19:48:49
As we head into the first night of the Emirates Cup Tournament ([Survivor Pool here](https://stacker.news/items/760645)), I wanted to share the data I've gathered through my NBA contests.
# Emirates Cup first round of Group play
- 50% of stackers chose Orlando
- 25% of stackers chose Miami
- 12.5% of stackers chose Boston
- 12.5% of stackers chose New York
# [NBA Prediction Contest](https://stacker.news/items/739939/r/Undisciplined)
## Champ
- Celtics (4/14)
- Pacers (3/14)
- Thunder (2/14)
- Nuggets (1/14)
- T-Wolves (1/14)
- Mavericks (1/14)
- Lakers (1/14)
- Knicks (1/14)
## MVP
- Luka (8/14)
- SGA (3/14)
- Giannis (2/14)
- Jokic (1/14)
## All NBA First Team
- Luka (13/14)
- Jokic (12/14)
- Giannis (12/14)
- SGA (11/14)
- Edwards (8/14)
- Brunson (6/14)
- Wemby (3/14)
- Tatum (2/14)
- Mitchell (1/14)
- Embiid (1/14)
- Davis (1/14)
originally posted at https://stacker.news/items/765075
-

@ 30ceb64e:7f08bdf5
2024-11-12 15:41:27
Hey Freaks,
Listen to these.
## Joy Again - How you Feel
https://music.youtube.com/watch?v=g94AbYYL678&si=JVzaqFjtG0s-SKqQ
## Vacations - Young
https://music.youtube.com/watch?v=oAur1xQx-sc&si=HB7PrvtOA2phz3Jk
## The Rare Occasions - Notion
https://music.youtube.com/watch?v=3vEiqil5d3Q&si=LdRtoEFrO4kldPzw
## Current Joys - Blondie
https://music.youtube.com/watch?v=XVuBw7TYvHg&si=_mm3U5Rj29xEAXiD
## Mac Demarco - On The Level
https://music.youtube.com/watch?v=WOV3c0t-Mwk&si=HZC2Ei-rnIE6-K4I
## Snail Mail - Habit
https://music.youtube.com/watch?v=MHYxZKEV0bY&si=_XBaUw4O4DZKp6iq
## Modest Mouse - Trailer Trash
https://music.youtube.com/watch?v=5kwLVhnTYlI&si=qEhasX5NckmoW_ke
## Third Eye Blind - Darkness
https://music.youtube.com/watch?v=WlLyAMU7MtQ&si=edt-dNgbgg-m0HJ_
## Weezer - Pink Triangle
https://music.youtube.com/watch?v=v2vWDWxYJBc&si=UlMuJjofu_l__dak
## The Mars Volta - The Widow
https://music.youtube.com/watch?v=0lAXFjAmcnM&si=YOOo4lCo1iMzzRQi
And let me know what you think.
originally posted at https://stacker.news/items/764730
-

@ 5d4b6c8d:8a1c1ee3
2024-11-12 14:44:24

There are some new soccer matches up at [freebitcoin](https://freebitco.in/?r=51325722).
Using my proprietary [Risk Balanced Odds Arbitrage](https://stacker.news/items/342765/r/Undisciplined) approach, you too can lock in some easy wins.
# Bets
All you have to do is apportion your sats in accord with the following 1000 sat splits (scale up or down in proportion to how much you like winning):
| Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 |
|--------------|-------------|--------------|-------|-------|-------|
| Verona| Inter Milan| Draw | 120| 700 | 180 |
| Napoli| Roma| Draw | 540| 200| 260|
| AC Milan| Juventus| Draw | 450| 270| 280|
| AC Milan| Empoli| Draw | 700| 100| 200|
| Union Berlin| Leverkusen| Draw | 220| 540| 240|
| RB Leipzig| Wolfsburg| Draw | 650| 140| 210|
| Leverkusen| Heidenheim| Draw | 800| 70| 130|
| Hoffenheim| RB Leipzig| Draw | 250| 520| 230|
| Dortmund| SC Freiburg| Draw | 590| 190| 220|
| Dortmund| FC Bayern| Draw | 230| 540| 230|
# Updates
The payouts from [these matches](https://stacker.news/items/743312/r/Undisciplined) have all been made. Our hypothetical 14k returned just over 15k.
originally posted at https://stacker.news/items/764646
-

@ 74718b83:b8204bd8
2024-11-12 13:48:52
Hey guys, do you think a big bullrun might cause a spike in activity here? or do you think that the learning curve and journey when a noob takes longer with people only learning about things like nostr and SN later in the curve?
originally posted at https://stacker.news/items/764581
-

@ 5d4b6c8d:8a1c1ee3
2024-11-12 01:09:13
I almost forgot about Mock Draft Monday. The Raiders had their bye week, which means I'm not wallowing in the memory of a fresh humiliation.
Week 10 broke their way a little bit and the Raiders are now picking 5th. Unfortunately, the teams ahead of them also need QB's. In this draft, three of the first four picks were QB's. That didn't leave any who were worth spending a top five pick on.
Results
- 5th Pick: CB Travis Hunter
- 36th Pick: QB Garrett Nussmeier
- 67th Pick: LB Danny Stutsman
- 74th Pick: S Kevin Winston Jr.
- 106th Pick: RB Ollie Gordon II
- 142nd Pick: WR Tory Horton
- 179th Pick: DE Anto Saka
- 212th Pick: IOL Seth McLaughlin
- 215th Pick: OT Jalen Travis
- 220th Pick: QB Miller Moss
This draft was a disaster. Unless some of these guys wildly over perform, this is something of a worst case scenario. The board just refused to bread my way.
originally posted at https://stacker.news/items/764061
-

@ b4403b24:83542d4e
2024-11-11 22:26:38

originally posted at https://stacker.news/items/763926
-

@ 000002de:c05780a7
2024-11-11 21:02:50
The US Government (administrative state) is not only evil, its also stupid.
On March 14 of 2023 the gov sold 9,861 bitcoin that it had stolen from the Silk Road. At the time this was valued at 215 million dollars. At today's market price those coins are valued at $860,051,175, an increase of 300%.
For every seller there is a buyer. Here's to those bitcoiners that bought those coins.
[source](https://jlopp.github.io/us-marshals-bitcoin-auctions/)
Now, I know 645 million is nothing for the US Federal government.... but still. Its pretty comical. Guys, I don't think you want the government buying bitcoin.... Not if we want the state to go away... May not be a popular opinion but that's fine. Its mine.
originally posted at https://stacker.news/items/763834
-

@ b4403b24:83542d4e
2024-11-11 20:42:43
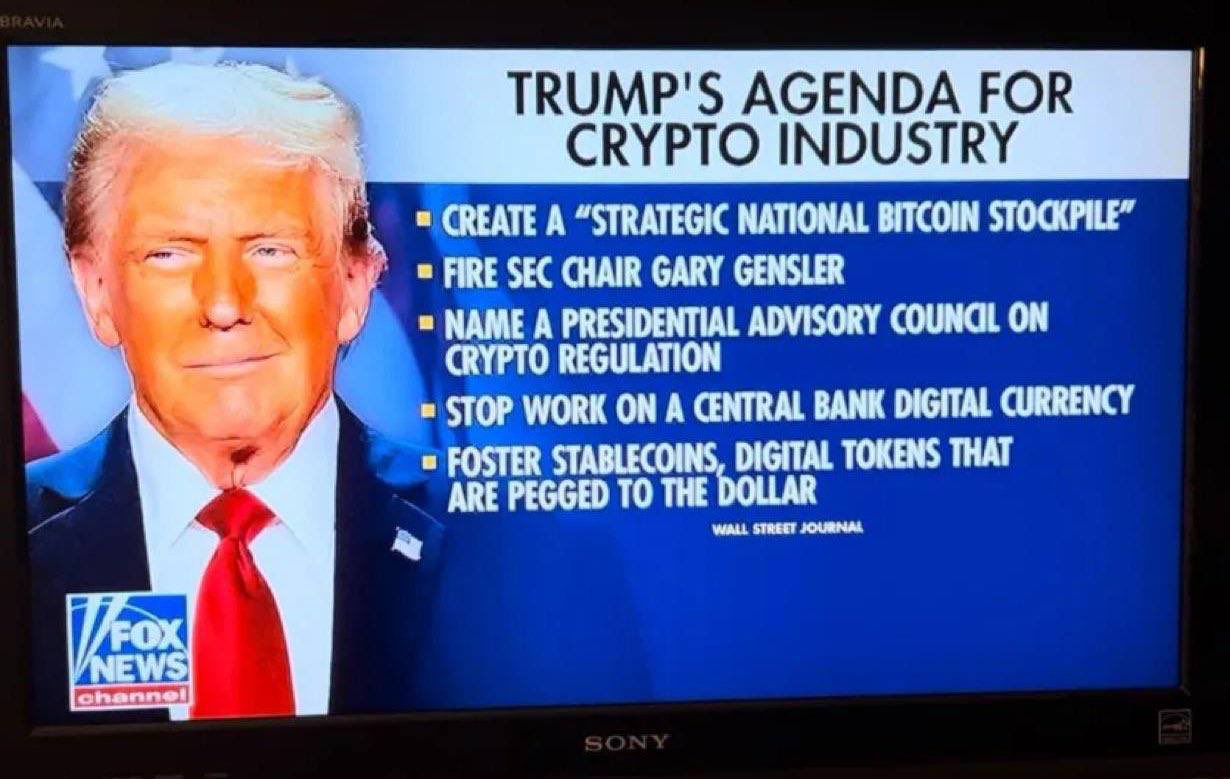
originally posted at https://stacker.news/items/763814
-

@ 5d4b6c8d:8a1c1ee3
2024-11-11 17:06:58
Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined.
For a hypothetical 1k wager on each match, distribute your sats as follows:
| Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 |
|--------------|-------------|--------------|-------|-------|-------|
| FC Bayern| Augsburg| Draw | 860| 50 | 90 |
| West Ham| Arsenal| Draw | 150| 650| 200|
| Southampton| Liverpool| Draw | 100| 730| 170|
| Newcastle| West Ham| Draw | 610| 170| 220|
| Man City| Tottenham| Draw | 630| 160| 210|
| Leicester| Chelsea| Draw | 180| 600| 220|
| Ipswich| Man United| Draw | 210| 590| 240|
| Crystal Palace| Newcastle| Draw | 310| 420| 270 |
| Arsenal| Nottingham Forest| Draw | 720| 100 | 180|
| Leganes| Real Madrid| Draw | 120| 690| 190 |
| Celta Viga| Barcelona| Draw | 210| 570| 220|
| Atletico Madrid| Alaves| Draw | 710| 100| 190|
| Athletic Club| Real Sociedad| Draw | 410| 280| 310|
As of writing this, I'm up almost 85 kilosats with RBOA, thanks to Real Sociedad beating Barcelona last week as a wildly underpriced underdog.
originally posted at https://stacker.news/items/763403
-

@ 000002de:c05780a7
2024-11-11 17:06:01
I'm curious. I don't push my political views on people. If they ask I talk pretty freely about my views but most progressives I call friends or colleagues don't ask. But they sure do whine about Trump. I've heard two people in my circle talk about actively searching for places to move. One said they had passports if they need to leave quickly.
I know...
Curious if others that actually have "progressive" friends are hearing stuff like this. Now, I will be very surprised if they actually go through with it. I think these people have been mentally abused by the corporate press, the establishment, and the Democrat party into believing lies about Donald Trump. I'm not a fan of Mr. Trump but the dogma about him has reached absurd levels.
I honestly feel sorry for these folks. I try to talk them down. They have none of it. Its sad. Their brains are switched off. What has been done to them is truly evil.
So, am I alone in this experience. I realize some of you probably don't have friends so you can just abstain from responding ;)
originally posted at https://stacker.news/items/763402
-

@ dca6e1cc:ea7d1750
2024-11-11 15:16:49
Hi all,
Here's a review of our activity over the last two weeks or so...
### Ww/P Geyser fund & Postcards
[Wandering w/ Purpose started its own geyser fund](https://geyser.fund/project/wanderingwpurpose) to offer more perks to our followers. [Check out our latest reward](https://geyser.fund/project/wanderingwpurpose/rewards/view/5299). It's a post card from wherever we are in the world to wherever you are in the world :)
### Bitcoin Nakawa
[Bitcoin Nakawa is currently featured on the front page of the geyser fund website.](https://geyser.fund/) We're very thankful for the steady stream of sats coming from the exposure.
Here's a contribution and thoughtful comment from one of Geyser Fund's co-Founders.

[We also recently announced a children's book being written about the Nakawa story.](https://wanderingwpurpose.substack.com/p/update-2-nakawa-childrens-book-and) Each purchase will gift a free copy to a student at the Nakawa school. [Pre-order is available now :)](https://geyser.fund/project/bitcoinnakawa/rewards/view/5192)
Here is an infographic of all current Bitcoin projects in Africa. Hopefully Bitcoin Nakawa will soon be included!

### Mozambique protests update
We are currently in Mozambique. If you haven't heard, the country is going through a significant transition. Mass protests are taking place to rebuke against the stagnation of 50 years of corrupt political monopolisation.
We are safe from the violence, thankfully. It's just a matter of patience to wait for our opportunity to leave the country. Hopefully this happens before our visa expires...then it's a mission to get to the border however possible.
Public transport in Mozambique is painfully slow, and even more so due to the protests. 10-12 hours to travel 500km is commonplace.
### Our Substack activity
Recent(ish) posts:
[Mass protests in Mozambique](https://wanderingwpurpose.substack.com/p/mass-protests-in-mozambique)
[Our most popular post thus far](https://substack.com/@wanderingwpurpose/note/c-75263839)
Recent notes:
[Our recent Substack Notes](https://wanderingwpurpose.substack.com/notes)
### Stacker News
[Our recent posts on Stacker News](https://stacker.news/gpvansat/posts)
## Closing thoughts
I'm currently preparing an Investment Memoranda intended for Hedge Funds, Family Offices, Institutional Investors, etc. looking to invest into Bitcoin mining machinery and associated hosting services.
During my research, I found a report titled, ["Leveraging Bitcoin mining to improve access to electricity in rural Africa" by Tikula Research Network](https://www.tikula.net/_files/ugd/e1de83_6945ec0a6d074146a3503cdd14d475dc.pdf) to be especially interesting.
Thanks everyone! Stay safe out there.
Ww/P
originally posted at https://stacker.news/items/763238
-

@ dca6e1cc:ea7d1750
2024-11-11 13:10:17
What are the odds that we can crowd-source a Bitcoin Mining operation that supports the energy development of a rural African village?
For anyone who knows, there are plenty of environmental, social, and economic benefits that Bitcoin mining can bring to the development of rural mini-grids.
More info:
https://www.gama.africa/gama-programs.html
https://x.com/GridlessCompute/status/1752679599601782846
Africa is home to massive amounts of untapped energy that can be ethically sourced. Access to energy is fundamental to human flourishing, meaning the upside for Africans' lifestyles is considerable given that many have zero electricity access aside from the odd solar panel. What can we do to accelerate this process?
originally posted at https://stacker.news/items/763008
-

@ 36bedab2:524acad4
2024-11-10 21:37:52
### 1. **Power ON**
- Quando você liga o computador, ele inicia o processo de boot.
- Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes).
### 2. **BIOS (Basic Input/Output System)**
- O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado.
- Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU.
- O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot.
### 3. **Master Boot Record (MBR) ou EFI Partition**
- O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional.
- Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função.
- O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional.
### 4. **Boot Loader (e.g., GRUB)**
- O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot.
- Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema.
- GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux.
### 5. **Kernel**
- O **kernel** é o núcleo do sistema operacional Linux.
- Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware.
- O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software.
### 6. **Initial RAM disk - initramfs**
- O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel.
- Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco.
- O initramfs é desmontado após o sistema principal estar carregado.
### 7. **/sbin/init (parent process)**
- Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos.
- O init é responsável por iniciar e gerenciar todos os outros processos do sistema.
- Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos.
### 8. **Command Shell using getty**
- **Getty** é o processo que configura e gerencia terminais para o login do usuário.
- Ele exibe a tela de login em sistemas baseados em linha de comando.
- Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico.
### 9. **Graphical User Interface (X Window ou Wayland)**
- Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno).
- Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc.
- X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela.
---
### Como esses processos se intercalam?
1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas.
2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**.
3. **MBR/EFI** localiza e executa o **boot loader** (GRUB).
4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux.
5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**.
6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal.
7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema.
8. **Init** executa o **getty** para configurar o terminal de login.
9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
-

@ bcea2b98:7ccef3c9
2024-11-10 19:34:24
@chess a3
originally posted at https://stacker.news/items/762161
-

@ c11cf5f8:4928464d
2024-11-10 07:58:46
Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, [here](https://stacker.news/items/751696/r/AG) are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/761231
-

@ a10260a2:caa23e3e
2024-11-10 04:35:34
nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard.
In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW.
I took some screenshots to give you an idea of how things work.
The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).

Clicking login allows signing in with a browser extension.
The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.
Existing blog posts (i.e. long form notes) are synced.

Same for product listings. There’s a nice interface to create new ones and preview them before publishing.
That’s all for now. As you can see, super slick stuff!
Bullish on Cypher.
So much so I had to support the project and buy a subdomain. 😎
https://bullish.cypher.space
originally posted at https://stacker.news/items/760592
-

@ b6424601:a11e4ff4
2024-11-09 19:45:51
**Personal Asset Architecture - Breaking Free from the Fiat-Driven Housing Market**
***Subheading – How Individuals Can Opt Out of the Fiat-Driven System and Create Homes with long term value***
As a self-inflicted residential architect, I am passionate about creating new, renovated homes that matter to interesting people. However, I've realized that the traditional housing market is built on a foundation of fiat currency, leading to several problems, including the potential devaluation of homes and, increasingly, the creation of empty stores of value.
**The Fiat Death Spiral**
Construction financing drives the most decisions in the housing market, which leads to a system where production homes are built to sell and create an initial profit rather than to provide a high-quality construction or a well-conceived living space.
**The Choice: Custom vs. Fiat**
When building or buying a home, you have two main options: a custom home built or renovated to your specifications or a production home pre-designed and pre-built by a builder.
**Fiat-Driven Homes: The Short-Term Solution**
Fiat-driven homes are built to sell quickly, often using materials that fit the deals proforma. Because of lower-quality materials and construction methods, Fiat homes depreciate more like cars than buildings.
**Custom Homes: The Long-Term Solution**
On the other hand, custom homes are typically built with higher quality and better design because the owner and designer are more invested in creating one-of-a-kind designs.
**A New Approach: Personal Asset Architecture**
As an architectural design firm owner focusing on homes, I've always known that the percentage of all homes architects design is low. I've used the low percentage as a filter for working with longer-term thinking clients, typically paying with cash. Clients who pay with cash have the flexibility to pay for what they want, allowing them to think about the total cost over the life of the house rather than just jumping through the hoops of a loan-to-value appraisal.
Bitcoin standard architectural practice and Bitcoin standard homes are the escape valves to continue the work we want for the individuals we want to work for. Our thesis is that Bitcoin can improve the housing market, both for our practice and for the clients we work with. Our thesis is that Bitcoin changed the housing market for our practice and the people we work with to build a personal architecture that is as hard an asset as Bitcoin.
**Asset Architecture Benefits**
Homes designed in a BTC standard have four big benefits for the individual to create personal asset architecture that holds value over time.
1\. Allows owners to think in a longer time horizon – Decisions made when designing homes need to consider a longer time horizon to include the operating cost of the house in addition to the cost of construction. Production homes are built to sell and create profit based on profit produced, netting profit by the sales price vs cost. Custom homes have more flexibility in spending more on quality and life cycle improvements.
2\. Allows for a density of design thought - Can you design a better-conceived home that considers how to use space more effectively to provide a denser space so the house can require less square footage? Can the smaller square footage be planned to work as a lifetime home from a starter home, through offspring to empty nesting and multigenerational housing?
3\. Providing a return on investment beyond money – A home should produce a better quality of life. Can homes produce income, food, energy, resilience, conservation of resources, and interior air quality and become your favorite place to be? Can the utility of needing a place to live be your family citadel?
4\. Working with the system to minimize the power of the system to increase taxes on the asset - Can we design homes to reduce property taxes with a creative design to minimize bedrooms and the taxable house value? Can we put more investment and design in outdoor space that helps owners maximize the use of properties for uses that are not taxed, like quality outdoor space or properties that produce food and energy?
The future of housing is uncertain, but one thing is evident from the trenches: the traditional fiat-driven system is not sustainable. Personal Asset Architecture offers a new approach to housing design that prioritizes long-term value, efficiency, and quality. By embracing this approach, we can create precious homes that produce a return on investment beyond money. The future of housing is in our hands, and it's time to create a new way of thinking about home design.
**What is possible?**
As individual owners and architects, we can build Stores of value buildings. By incorporating the goal of creating Personal Asset Architecture, we can create homes that produce a return on investment that goes beyond money and minimize the values of a banking system and the ability to increase taxes on the asset.
Stay humble, stack stakes, and when you are ready, choose to build stuff that holds actual value.**
**HODL on**
-

@ 5d4b6c8d:8a1c1ee3
2024-11-09 19:04:04
The Emirates Cup begins on Tuesday, so it's time to start thinking about our first picks.
For a refresher on the tournament, see the [first post](https://stacker.news/items/751054/r/Undisciplined). Note, though, that there are actually going to be seven group play days with each team playing four total group play games.
# Games
Here is the first slate of games (plus the home spread):
- Hawks @ Celtics (-12.5)
- Heat @ Pistons (+3)
- Hornets @ Magic (-8)
- Knicks @ 76ers (-1)
- Raptors @ Bucks (-8)
- Suns @ Jazz (+4.5)
- Mavs @ Warriors (+2.5)
Just pick one of the teams above to win their game on Tuesday.
Remember, you can only take each team once and the options will dwindle once we get to the Knock Out round. There are at most 10 choices to make during the tournament, but you don't know which ones will be available towards the end.
I'm going to wait a couple of days, to get more clarity on the injury situations for the Heat, Magic, 76ers, and Bucks. At first glance, I'm leaning towards taking either the Heat, but with Jimmy hurt and the Pistons looking a little frisky, I don't love it.
# Prize
27133 sats! plus whatever else comes in from here on out
# Participants
@Undisciplined, @gnilma, @BlokchainB, @realBitcoinDog, @Carresan, @supercyclone, @grayruby
There's still time to join. The initial buy-in is only 3k sats.
originally posted at https://stacker.news/items/760645
-

@ eac63075:b4988b48
2024-11-09 17:57:27
*Based on a recent paper that included collaboration from renowned experts such as [Lynn Alden](nostr:nprofile1qyt8wumn8ghj7un9d3shjtntv9khqtnnd96x2tcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtcqyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057nwgm4w), [Steve Lee](https://x.com/moneyball), and [Ren Crypto Fish](https://twitter.com/0xren_cf), we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.*
[PT-BR version](https://www.eddieoz.com/consenso-no-bitcoin-como-a-rede-evolui-sem-comprometer-a-seguranca/)
**Podcast**
https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
**Presentation**
https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
### 1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
**Evolution of Consensus in Bitcoin**
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
---
### 2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
**Validation of Blocks and Transactions**
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
**Chain Selection**
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
**Soft Forks vs. Hard Forks**
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
- **Soft Forks**: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
- **Hard Forks**: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
---
### 3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
**1. Economic Nodes**
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
**2. Investors**
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
**3. Media Influencers**
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
**4. Miners**
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
**5. Protocol Developers**
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
**6. Users and Application Developers**
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
---
### 4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
**Flag Day**
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
- **Advantages**: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
- **Disadvantages**: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
**BIP34 and BIP9**
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
- **Advantages**: Allows the network to activate updates gradually, giving more time for participants to adapt.
- **Disadvantages**: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
**User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)**
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
- **Advantages**: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
- **Disadvantages**: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
**BIP8 (LOT=True)**
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
- **Advantages**: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
- **Disadvantages**: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
---
### 5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
**Network Fragility with Alternative Implementations**
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
**Chain Splits and Impact on Stakeholders**
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
- **Institutional Investors and ETFs**: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
- **Miners**: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
- **Economic Nodes**: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
**Regulatory Impacts and Institutional Investors**
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
**Security Considerations in Soft Forks and Hard Forks**
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
**Bounty Claim Risks and Attack Scenarios**
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
---
### 6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
**1. Careful Evaluation of Proposal Maturity**
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
**2. Extensive Testing in Secure and Compatible Networks**
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
**3. Importance of Stakeholder Engagement**
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
**4. Key Questions for Evaluating Consensus Proposals**
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
**5. Coordination and Timing in Implementations**
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
**6. Continuous Monitoring and Re-evaluation**
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
---
### 7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
---
### 8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-

@ 35f3a26c:92ddf231
2024-11-09 17:10:57
## "Files" by Google new feature
"Files" by Google added a "feature"... "Smart Search", you can toggle it to OFF and it is highly recommended to do so.
- 
Toggle the Smart Search to OFF, otherwise, google will search and index every picture, video and document in your device, no exceptions, anything you have ever photographed and you forgot, any document you have downloaded or article, etc...
## How this could affect you?
Google is actively combating child abuse and therefore it has built in its "AI" a very aggressive algorithm searching of material that "IT THINKS" is related, therefore the following content could be flagged:
- [ ] Pictures of you and your children in the beach
- [ ] Pictures or videos which are innocent in nature but the "AI" "thinks" are not
- [ ] Articles you may have save for research to write your next essay that have links to flagged information or sites
***The results:***
- [ ] Your google account will be canceled
- [ ] You will be flagged as a criminal across the digital world
You think this is non sense? Think again:
https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html
## How to switch it off:
1. Open files by Google
2. Tap on Menu -> Settings
3. Turn OFF Smart Search
## But you can do more for your privacy and the security of your family
1. Stop using google apps, if possible get rid off of Google OS and use Graphene OS
2. Go to Settings -> Apps
3. Search for Files by Google
4. Unistall the app, if you can't disable it
5. Keep doing that with most Google apps that are not a must if you have not switched already to GrapheneOS
***Remember, Google keeps advocating for privacy, but as many others have pointed out repeatedly, they are the first ones lobbying for the removal of your privacy by regulation and draconian laws, their hypocrisy knows no limits***
## Recommendation:
I would assume you have installed F-Droid in your android, or Obtainium if you are more advanced, if so, consider "Simple File Manager Pro" by Tibor Kaputa, this dev has a suite of apps that are basic needs and the best feature in my opinion is that not one of his apps connect to the internet, contacts, gallery, files, phone, etc.
- 
> Note
> As most people, we all love the convenience of technology, it makes our lives easier, however, our safety and our family safety should go first, between technology being miss-used and abused by corporations and cyber-criminals data mining and checking for easy targets to attack for profit, we need to keep our guard up. Learning is key, resist the use of new tech if you do not understand the privacy trade offs, no matter how appealing and convenient it looks like. .
***Please leave your comments with your favorite FOSS Files app!***
-

@ bcea2b98:7ccef3c9
2024-11-09 17:01:32
Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-

@ 5d4b6c8d:8a1c1ee3
2024-11-09 15:00:44
The wife and I were drinking our coffee, while a fair bit of commotion was coming from our daughter in the bathroom.
She came out and very shyly said "'Scuse me."
We've been working with her on manners and not interrupting, so this was very encouraging.
She continued very sweetly, "There's a pwoblem in the potty."
That was decidedly less encouraging.
originally posted at https://stacker.news/items/760318
-

@ 72592ec9:ffa64d2c
2024-11-09 11:00:37
Really good read so far, thought I'd share this part from https://bitcoindevphilosophy.com/
> It seems that we can’t have a decentralized system based on trust, and that’s why trustlessness is important in Bitcoin.
>
> To use Bitcoin in a trustless manner, you have to run a fully-validating Bitcoin node. Only then will you be able to verify that the blocks you receive from others are following the consensus rules; for example, that the coin issuance schedule is kept and that no double-spends occur on the blockchain. If you don’t run a full node, you outsource verification of Bitcoin blocks to someone else and trust them to tell you the truth, which means you’re not using Bitcoin trustlessly.
>
> Diagram
> David Harding has authored an article on the bitcoin.org website explaining how running a full node - or using Bitcoin trustlessly - actually helps you.
>
> The bitcoin currency only works when people accept bitcoins in exchange for other valuable things. That means it’s the people accepting bitcoins who give it value and who get to decide how Bitcoin should work.
>
> When you accept bitcoins, you have the power to enforce Bitcoin’s rules, such as preventing confiscation of any person’s bitcoins without access to that person’s private keys.
>
> Unfortunately, many users outsource their enforcement power. This leaves Bitcoin’s decentralization in a weakened state where a handful of miners can collude with a handful of banks and free services to change Bitcoin’s rules for all those non-verifying users who outsourced their power.
>
> Unlike other wallets, Bitcoin Core does enforce the rules—so if the miners and banks change the rules for their non-verifying users, those users will be unable to pay full validation Bitcoin Core users like you.
>
> — David Harding
> Full Validation on bitcoin.org (2015)
> He says that running a full node will help you verify every aspect of the blockchain without trusting anyone else, so as to ensure that the coins you receive from others are genuine. This is great, but there’s one important thing that a full node can’t help you with: it can’t prevent double- spending through chain rewrites:
>
> Note that although all programs—including Bitcoin Core—are vulnerable to chain rewrites, Bitcoin provides a defense mechanism: the more confirmations your transactions have, the safer you are. There is no known decentralized defense better than that.
>
> — David Harding
> Full Validation on bitcoin.org (2015)
> No matter how advanced your software is, you still have to trust that the blocks containing your coins won’t be rewritten. However, as pointed out by Harding, you can await a number of confirmations, after which you consider the probability of a chain rewrite small enough to be acceptable.
>
> The incentives for using Bitcoin in a trustless way align with the system’s need for full node decentralization. The more people who use their own full nodes, the more full node decentralization, and thus the stronger Bitcoin stands against malicious changes to the protocol. But unfortunately, as explained in the full node decentralization section, users often opt for trusted services as consequence of the inevitable trade-off between trustlessness and convenience.
originally posted at https://stacker.news/items/760051
-

@ 5d4b6c8d:8a1c1ee3
2024-11-09 04:02:26
As always, we're going to lead off with the on-going contests at ~Stacker_Sports.
@BlokchainB requested some NHL coverage, so @grayruby is going to try to explain hockey to me.
We'll check in on the NFL post trade deadline and see if the landscape shifted appreciably. Also, we had a requested topic on why the top picks of the past two drafts are paling in comparison to the guys taken immediately after them. Tune is as we flounder for answers.
We had some disagreements on our hastily slapped together [NBA power rankings](https://stacker.news/items/757639/r/Undisciplined), so we'll have to hash those out. Thankfully, @BlokchainB has already confirmed that mine were better.
Then I wanted to talk about [Predyx](https://beta.predyx.com/market) in a little more detail, because they're on Stacker News and their project is very cool. I'm sure we'll cover our other gambling (mis)adventures.
What say you about any of those topics? Are there other topics you want our thoughts on?
The Stacker Sports Pod is for stackers by stackers.
originally posted at https://stacker.news/items/759836
-

@ bcea2b98:7ccef3c9
2024-11-09 01:30:29
@chess h3
originally posted at https://stacker.news/items/759635
-

@ b4403b24:83542d4e
2024-11-08 22:34:45

Imagine what will be in the upcoming years if this trend continues.
Bullish 🚀🌕
originally posted at https://stacker.news/items/759487
-

@ 5d4b6c8d:8a1c1ee3
2024-11-08 13:59:13
@Coffee proposed a topic for [The Stacker Sports Podcast](https://fountain.fm/show/syQHHkLs59GQ1eFAe64t) on our nostr thread and I wanted to share it here.
Why have the top picks in the past two drafts (Bryce Young and Caleb Williams) been so significantly outplayed by the players taken immediately after them (CJ Stroud and Jayden Daniels)?
It's early in the careers of each of these players, but Stroud and Daniels are already looking like MVP caliber franchise QB's. Why did teams miss this?
The most obvious hypothesis (that the Bears and Panthers flubbed their picks) doesn't make much sense, because Young and Williams were the consensus top picks in their drafts.
A bigger question is why it's so difficult to spot an MVP caliber QB from their college play.
originally posted at https://stacker.news/items/758917
-

@ c11cf5f8:4928464d
2024-11-08 13:31:22
The Magnificent 7:

Here we are again with our monthly [Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times) summary, trying to give you a hit of what you missed this month in the ~AGORA territory.
- - -
### Top-Performing Ads
This month, the most zapranked ones are:
* `01` [[OFFER] IPv4+IPv6 KVM VPS, from 1.75EUR/month (Stockholm/SE SWEDEN)](https://stacker.news/items/750336/r/AG) by @skhron
* `02` [[SWAP] SN Cowboy credits](https://stacker.news/items/723069/r/AG) by @DarthCoin
* `03` [[SELL] “NO⚡️TR T-Shirt” for 21K sats](https://stacker.news/items/730098/r/AG) by @thebullishbitcoiner
* `04` [[sell] iptv subscription 10k+ live tv channels and 20k+ vod (tv/movies)](https://stacker.news/items/730963/r/AG) by @profullstack
This month we ran short, so here other 3 from previous month
* `05` [[SELL] StackerNews Archived Territories - Your chance to own a piece of history!](https://stacker.news/items/698471/r/AG) by @Design_r
* `06` [[SELL] Stickers for Stackers! SN Nostr Badges vinyl stickers - from 3,456 sats](https://stacker.news/items/711431/r/AG) by @AGORA
* `07` [[SELL] 3 WishMesh Meshtastic radios and 2 extended antennas 325,000 SATS](https://stacker.news/items/710750/r/AG) by @fe3c522a6f
- - -
###### In case you missed
Here some interesting post opening conversation and free speech:
@supratic share some interesting tools for merchants and businesses:
- https://stacker.news/items/745053/r/AG TinyPine: A simple LN and CASHU ecash POS system for merchants
- https://stacker.news/items/750705/r/AG
PLEBEIAN – Simple, Anonymous & Free Market for Everyone
And here some more insights on how to do business in the private:
- https://stacker.news/items/732291/r/AG Classifieds vs. Listings: Navigating Nostr Protocol's Approach to Advertising by @AGORA
- https://stacker.news/items/742973/r/AG The Watchman Privacy Podcast – Escape the Servile Society with Vonu by @mo
- https://stacker.news/items/746325/r/AG How to Operate a Business in the Private with Trust by @mo
- https://stacker.news/items/741906/r/AG Paying out debt and bills using the Bills of Exchange act by @supratic
- https://stacker.news/items/751074/r/AG The Separation of Business and State by @mo
- https://stacker.news/items/718979/r/AG Mystery Paper: Ancient Merchant Paper, For Merchants Only & Corporate Countries by @AGORA
- https://stacker.news/items/720288/r/AG Parallel Society • Free Man's Perspective by @DarthCoin
###### 🏷️ Spending Sunday is back!
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats!
Read more https://stacker.news/items/721244/r/AG
- - -
###### Just a reminder for you all
This territory aims to connect stackers and curious buyers for IRL P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it!
To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting.
- - -
### Create your Ads now!

Looking to start something new? Hit one of the links below to free your mind:
* [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation,
* [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or,
* if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)!
* [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners
* [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats
* [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item
* [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else
* [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift!
* [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to
- - -
Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we can help you publish a personalized post.
Coinomi Bitcoin Testnet
skull quantum digital allow faculty enforce spatial emotion fun candy plunge stick stairs salad dish pass fix between shock scene ivory cargo unhappy fault
originally posted at https://stacker.news/items/758878
-

@ b4403b24:83542d4e
2024-11-08 13:03:32
I recently came across a funny Star Wars themed meme which I couldn't resist to post here with a message
@DarthCoin vs no/shit coiners

**P.S.:** Sorry in advance if some of you find it as disturbing or vulgar
originally posted at https://stacker.news/items/758857
-

@ b4403b24:83542d4e
2024-11-08 11:46:54
To my great surprise, when I checked my SN notification feed today, I found out 👇

To be honest, I don't know what I did to earn it, what it means or gives me or whether I can loose it (similar to the cowboy's hat maybe @k00b can give more insights) but I am pretty satisfied adding it under my belt. 🎉
I'll keep my activity high hoping I'll find the other cowboy collectible I miss - the pistol

originally posted at https://stacker.news/items/758749
-

@ fd208ee8:0fd927c1
2024-11-08 10:27:40
## You have no idea
I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.

It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse.
I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._
But you were always apart. You were always two different people. You just didn't notice, until now.

I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship.
## I was raised by relaxed revolutionaries
Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics.
It's like magic, but it's the result of a mindset, not a worldview.
Or, as I like to quip:
> The best way to stay married, is to not get divorced.

My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live.
My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.

The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on.
And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer.
You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.

We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something.
Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
-

@ eac63075:b4988b48
2024-11-07 21:27:53
Every night, you draw your curtains without thinking twice. It's instinctive—a simple act that protects your personal space. Yet in our digital lives, we've somehow accepted living in houses made entirely of glass, with countless unseen observers watching our every move.
https://www.fountain.fm/episode/wPZLCJ3fD6vzsWQ3XSE1
## Why Privacy Matters to Everyone
Privacy isn't just for those with something to hide; it's a fundamental human need. Think about the conversations you have with friends, the late-night web searches you make, the personal moments you capture in photos. Would you want all of that broadcasted to the world?
I remember my friend Lisa planning a surprise party for her husband. She searched for gift ideas and coordinated with friends through social media. To her dismay, targeted ads for the exact gift she intended to buy started popping up on their shared devices at home. The surprise was ruined. It wasn't malicious, but it was a stark reminder of how our online activities are constantly monitored.
When a major retailer's customer database was breached, my neighbor Sarah discovered her shopping history, credit card details, and even her children's names were exposed to criminals. She hadn't realized how much personal information she'd unknowingly shared through routine purchases. It was a wake-up call that privacy breaches can affect anyone, not just the tech-savvy or those in high-profile positions.
Edward Snowden once said, **"Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say."** Privacy isn't about secrecy; it's about autonomy over our personal information.
## The Rise of the Cypherpunks
Back in the '90s, a group known as the cypherpunks saw the writing on the wall. They recognized that as we moved into a digital era, our personal freedoms could be at risk. So they took action.
One of them, Eric Hughes, famously wrote, **"Privacy is necessary for an open society in the electronic age."** They developed encryption tools to protect individual privacy, laying the groundwork for technologies like Bitcoin and cryptocurrencies. These innovations were about more than digital money; they were about empowering individuals to take control of their own data.
## When Technology Knows Too Much
Fast forward to today, and artificial intelligence (AI) is everywhere—in our phones, homes, and even cars. While AI brings convenience, it also raises serious privacy concerns.
Remember when you mentioned needing new running shoes, and suddenly every ad on your browser was for footwear? It's not your imagination. AI algorithms analyze our conversations, searches, and purchases to predict what we'll want next. But where does it stop?
A few years ago, a major retailer guessed a teenager was pregnant based on her shopping habits before she had told her family. They sent her targeted coupons for baby products, leading to a very uncomfortable situation at home. This isn't just marketing—it's intrusion.
Naomi Brockwell, a privacy advocate, [warns](https://x.com/naomibrockwell/status/1833055298288058624), **"Our relationship with financial privacy has fundamentally changed. What was once seen as a constitutional right and personal freedom is now simply part of the trade-off for using digital payments. Our baseline for what’s acceptable has shifted."** It's a wake-up call that our digital footprints are larger and more revealing than we might think.
### Privacy-Preserving AI
While AI often threatens privacy, emerging technologies like **federated learning** offer hope. This approach allows AI models to learn from data without directly accessing personal information. Imagine your phone improving its predictive text without sending your messages to a central server. It's AI that respects your privacy.
## The Watchful Eye: Mass Surveillance and AI
Governments and corporations often justify mass surveillance as a means to keep us safe. But at what cost? When every email, message, or phone call can be monitored, we're sacrificing more than just data—we're giving up our freedom to think and communicate without fear.
Think about how you'd behave if someone followed you around with a camera all day. You might avoid certain places or people, censor your conversations, or feel constantly on edge. That's the chilling effect of mass surveillance.
I spoke with Alex, a journalist who covers political activism. "After attending a peaceful protest, I noticed unusual activity on my devices," he told me. "It made me second-guess my work, wondering who's watching." This isn't paranoia; it's a reality for many who challenge the status quo.
## Building Digital Fortresses: Cryptographic Innovations
So how do we reclaim our privacy? Cryptography offers some solutions.
### Zero-Knowledge Proofs: Proving Without Revealing
**Zero-knowledge proofs** allow you to prove you know something without revealing the actual information. Imagine showing a bouncer a card that confirms you're over 21 without exposing your birth date or any other details. In the digital world, this means verifying your identity or eligibility without handing over all your personal data.
### Homomorphic Encryption: Secure Processing
Then there's **homomorphic encryption**, which lets companies process your data without actually seeing it. Think of it like sending a locked suitcase with your belongings; they can weigh it or move it, but they can't open it to see what's inside.
### Quantum-Resistant Algorithms: Future-Proofing Privacy
As quantum computers become more powerful, they could potentially break current encryption methods. **Quantum-resistant algorithms** are being developed to safeguard our data against these future threats. It's like reinforcing your digital locks today to withstand the super lock-picking tools of tomorrow.
## Decentralization: Taking Back Control
Decentralization aims to put power back into the hands of individuals. Bitcoin let you be your own bank, controlling your finances without a middleman. Decentralized social media platforms like Nostr, Bluesky or Fascaster allow you to own your content without algorithms dictating what you see or who sees you.
### Decentralized Identity Systems
**Decentralized identity systems** let you prove who you are without revealing more than necessary. It's like showing only your age at a bar instead of handing over your entire driver's license. You maintain control over your personal information.
But with great power comes great responsibility. Without a bank to reset your password or customer service to recover your account, the onus is on you to protect your assets and information.
## Practical Tips to Protect Your Privacy
You don't have to be a tech guru to safeguard your privacy. Here are some steps you can take today:
- **Use Encrypted Messaging Apps**: Switch to apps like **Signal, SimpleX or Session** for secure communication. Your messages will be end-to-end encrypted, meaning only you and the recipient can read them.
- **Limit Social Media Sharing**: Be mindful of what you post. Do you really need to share your location or personal details publicly?
- **Choose Privacy-Focused Browsers and Search Engines**: Use browsers like **Brave** or **Firefox** and search engines like **DuckDuckGo** that don't track your every move.
- **Secure Your Passwords**: Use strong, unique passwords for each account, and consider a password manager like **Bitwarden**. Enable two-factor authentication whenever possible.
- **Use Encrypted Email Services**: Consider email providers like **ProtonMail** that offer end-to-end encryption for your communications.
- **Regularly Audit App Permissions**: Check which apps have access to your location, microphone, and contacts. Revoke permissions that aren't necessary.
- **Be Wary of Public Wi-Fi**: Public networks can be a hotbed for hackers. If you must use them, a VPN like **ProtonVPN** can add a layer of security.
- **Consider Privacy-Focused Alternatives**: Explore services like **Nextcloud** for cloud storage or **Jitsi Meet** for video conferencing, which prioritize user privacy.
- **Keep Software Updated**: Regular updates often include security patches. Don't ignore them.
- **Stay Informed and Skeptical**: Phishing scams are getting more sophisticated. Think before you click on suspicious links or download attachments.
## Final Thoughts
Privacy isn't a lost cause; it's a right worth fighting for. As Edward Snowden reminds us, **"Privacy is the fountainhead of all other rights."**
By taking control of our data and digital habits, we can navigate the online world with greater confidence and peace of mind. After all, wouldn't it be nice to live in a digital home where we decide when to close the curtains?
## Read more
**OPSEC and Digital Hygiene Plan:** <https://www.eddieoz.com/opsec-and-digital-hygiene-plan/>
-

@ bcea2b98:7ccef3c9
2024-11-07 18:43:30
If you could accomplish one major goal, what would it be? Why does it matter to you, and how would it change your life or the lives of others?
My ultimate goal is to be part of a mission to Mars one day. I’ve always been fascinated by space exploration.
originally posted at https://stacker.news/items/757861
-

@ 4ba8e86d:89d32de4
2024-11-07 13:56:21
Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas.
Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW.
Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW.
Sem mais delongas, vamos ao tutorial de fato.
## 1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P.
Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo.
Após entrar no site vá para a página '1 - Creating a mailbox'
https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos.
https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados.
https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg
https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
## 2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd.
Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso.
Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf
https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf
https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
```
sudo systemctl restart i2pd
```
Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.
Com os túneis cliente criados, vamos agora configurar o Thunderbird
## 3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir.
https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg
https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta.
https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir.
https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue'
https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta.
https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
## 4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-

@ 74718b83:b8204bd8
2024-11-07 11:51:14
Hi guys, i thought it would be interesting to compare some basic cost of living stats among stackers and ask, how hard is it to hit your basic number?
for me, in Bulgaria with 2 kids , to be comfortable, NOT in the capital , about 2k euros is a number that works for my family. i could reduce that number by up to 1000 euro if my kids didn't go to a private school. also worth noting is i own the house so have no rent or mortgage.
if i was renting or had a mortgage, i would simply pay that instead of doing private school, so the number would be similar.
bills are cheap, maybe 10 euro water per month and about 40 euro electricity (this will vary though )
finding a job that pays 2k euros is quite hard outside of the capital city, even if you are a software programmer.
i manage to hit this freelancing, and it's ok, i have a 10x higher lifestyle than i would in the UK and i own a property etc . the downside is a client will randomly leave etc and it puts a lot more strain on the budget, the upside is i am at least the master of my time, which i find very valuable
originally posted at https://stacker.news/items/757311
-

@ b184e3ed:27924b0d
2024-11-07 03:06:37
When I joined AA, this question started to haunt my thoughts during those frequent nighttime anxiety attacks. Among all the chaos in my life, there were a few things I was certain of. And one of those things was the certainty of never having felt God, I didn't even know that God was something you could feel. For me, when I started the 12-step program, God was a social construct, something humans had invented to control a society thirsty for basic survival instincts. And perhaps I wasn't so wrong, but like everything in life, this was only half the truth. Despite my deep cognitive analysis that my anxiety forced me to do almost every night for hours, often until the first ray of sun pierced my bedroom window, my spiritual bias didn't allow me to see the whole picture, or a complete reality. On that side, there had always been a void
Later, I realized that this emptiness was the main cause of all my problems. From there came that feeling of always being incomplete, that anxiety of always feeling like something was missing, that need to always want to fill voids that weren't mine, without realizing that it was only creating more emptiness within me
Once, in those heart-to-heart talks that we in AA call sponsorship, my soul expressed the painful doubt, 'What does it mean to feel God?' My sponsor simply replied, 'I assure you that when you feel God, you won't doubt that what you feel is God. There is no doubt in matters of God.
And so I left, with that answer that left me right where I started. And with more doubts. Why is there no doubt in matters of God?
After thinking about it for so long, I paused for a few seconds. I closed my eyes and decided, for the first time, to talk to this so-called God. I let go of all my feelings, all my disbelief, and I prepared myself to accept anything different from what I already had, because what I had wasn't working for me at all. With all sincerity and feeling a pressure in my chest, closer to my heart than usual, I asked in a low voice
God, what does it feel like to feel you? What should I do to feel you? What's the manual for feeling you? I've tried everything, I don't know what else to do, what else to plan. I accept that I need to feel you. Everyone tells me that when I feel you, everything will make sense and only then will I start to let go of this violent need to consume my drug of choice. But nobody tells me how. What am I not seeing? Please, give me something. I can't take it anymore, I'm running out of strength, I'm wasting my life stuck in the same cycle. I can't do this anymore, help me feel you. Then a pain began to flow, but a particular one that every addict knows, that soul-deep pain that comes from emptiness, that pain that turns on the faucet of tears that began to flow non-stop.
I allowed myself to feel that pain, everything turned dark and negative, suicidal thoughts returned, hate, resentment, selfishness, depression, all together, all that is lived in darkness, all that is felt in solitude, all that came from emptiness.
And only by feeling it, could I see where that deep pain came from, I could visualize the path it left behind. For the first time, I recognized my spiritual emptiness.
And it was only then that I began to see the whole picture of my life.
Doubt has no place in the things of God because God is not logic, God is not reason, much less a manual. Doubt comes from logic, therefore where there is doubt, there is also an absence of God, emptiness. And right at the moment of recognizing that, very specific images came to my mind. My sponsor hugging me for the first time when I arrived and interviewed me. With that hug came the words, 'You're not alone, you're already in a safe harbor, we'll be with you from start to finish.
One day at a massive AA event, right in the middle of a workshop dynamic, that deep and sincere hug my fellow sufferer and I shared, in the midst of deep crying with our eyes closed, someone guided our arms to each other. To end up keeping each other company in that darkness we had always gone through alone.
That trip to a Group Anniversary outside the city, where a fellow member of my group and I were simply enjoying the scenery, the wind on our faces, and laughing at the craziness of our daily lives, this on my motorcycle on the highway. That hug it took me years to find in the arms of my younger sister, right after arriving after a writing session. That hug of forgiveness to my mother and father that I had never been able to give before because I didn't want to go through the pain that came with feeling.
Those few seconds in the rain that we spent lost on our way to the new location of our Group that I experienced in the company of a fellow member.
Seeing a new person arrive with a desire to start their process.
Connecting in the same feeling and emotion that comes with the death of a best friend.
Serving a cup of coffee to that fellow member who returns after months of absence.
Arriving at the group with hope of seeing that fellow member who hasn't been coming for weeks and little is known about what happened, but they no longer come to meetings. Day after day, their chair remains empty. And then start letting go of their defenses and their craziness.
Standing in front of several strangers, with my head held high, my gaze firm, saying my name and then, 'I am a drug addict.
To say, 'I feel like shit, but I'm here for whatever I can contribute.
To feel like I'm that support for those who were my support when I was at rock bottom. And not just feel it, but also be able to be it.
And that, to mention just a few of the scenes that came to my mind, then I understood 'I had already felt God.' I wasn't lacking spirituality, I wasn't lacking God, I just needed to stay still for a moment to feel it. And to feel that he has always been there. And that he will never leave my side.
So today I can answer my own question, 'That's what it feels like to feel God' but not just any God.
But a very special one, the God of the 4th and 5th step addicts and alcoholics...
originally posted at https://stacker.news/items/756957
-

@ 5d4b6c8d:8a1c1ee3
2024-11-07 01:50:21
I'm watching the Warriors laying it on the Celtics and I'm struck by how uniquely fun to watch Steph still is.
If you were picking a team of who you're most enjoying this season, who would be in the starting five?
Here's my most entertaining starting 5 (ordered by position, not entertainingness):
1. Lamelo
2. Steph
3. Ant
4. Chet
5. Jokic
originally posted at https://stacker.news/items/756861
-

@ e968e50b:db2a803a
2024-11-06 21:10:16
https://youtu.be/vAM8rcmb4oQ?si=qpnJHtoVhLyG4Mek
originally posted at https://stacker.news/items/756531
-

@ 5d4b6c8d:8a1c1ee3
2024-11-06 17:44:00
Now that Trump is heading back the White House, once again promising to "drain the swamp", let's consider how that might actually be accomplished.
It's damn near impossible to fire federal employees and abolishing entire agencies is very difficult politically. The later hasn't been done since Jimmy Carter. Of course, I'm all for Ron Paul and Elon Musk pursuing both of those paths, but they'll definitely be ice skating uphill.
There are two proposals that I know will result in massive voluntary resignations, labor savings, and reduction in DC bureaucrats:
1. Relocate departments and agencies away from the major metropolitan areas
2. Rescind locality pay for remote eligible workers
The first option was implemented by Trump for a couple of agencies. It was big news in econ world when the USDA was relocated, because hundreds of USDA economists resigned.
I'm not sure how easy it would be to implement the second idea (perhaps @Cje95 can weigh in), but it would also have a dramatic effect. During the pandemic, the feds followed the trend of making many positions remote work eligible. However, the federal pay scale still grants locality based pay increases for those living in expensive areas. If you are allowed to do your job from anywhere, why should you get an enormous raise (at taxpayer expense) for living in the most expensive place in the country? Pay all remote eligible workers as though they live in rural Arkansas, because they are allowed to do so.
As with the relocation, most workers would probably resign rather than either move or take a huge paycut. And, if they don't, then at least the federal workforce is getting spread out and not costing nearly as much.
What are some other feasible ways to dramatically reduce the federal workforce?
originally posted at https://stacker.news/items/756327
-

@ fca435eb:e53931d9
2024-11-06 17:38:35
# Setting up a hybrid lightning node, even behid CGNAT:
## 1. Motivation
To run a lightning node in a completely sovereign way, we must host it on hardware under our control. To make our node accessible to other peers we must publish on the gossip network how to find our node, but since many of our local networks are behind a **carrier grade NAT** and the router does not have a public IP, it becomes a bit difficult. In this post I will explain how to expose our node with a **ssh tunnel with a vps**, even behind CGNAT. I won't explain how to create a tor hidden service because I think is trivial, if you are running a node, almost sure that you have one.
## 2. Prerequisities:
1- Running a lightning node
2- Having a vps with a public ip:
[lunanode](https://www.lunanode.com/?r=31080) is easy to use, and you can pay with lightning
## 3. Exposing the node
Connect to your VPS by ssh and edit /etc/ssh/sshd_config
```
sudo vim /etc/ssh/sshd_config
```
Ensure that:
```
AllowTcpForwarding yes
GatewayPorts clientspecified
```
Make sure that the port that you want to expose is accessible by the internet, in my case it will be the default port 9735, replace 9735 by your custom port if you want:
```
sudo ufw allow 9735
sudo ufw reload
```
Now let's move to our local machine, where the node is running. With the assumption that your node is exposed in localhost:9735 (that's how it is by default) let's test our implementation, remember to change the ports if you have others, paste your vps public ip address and your vps user :
```
ssh -nNTv -R 0.0.0.0:9735:localhost:9735 **YOUR_VPS_IP_ADDRESS**
```
Now you must change the config of your node to advertise the new address. If you use CLN you can edit the config file and set announce-addr=**YOUR_VPS_IP_ADDRESS**:9735 (or your port). If you are using another lightning node implementation I am sure you can find the config file, and announce the address.
Now everything must work, you can try to find your node from another node (maybe a friend's node) by the new ip:port address and the pubkey of course.
## 4. Finishing
You can close that now, and prepare to make it more robust.
First we need to install autossh
```
sudo apt-get update && sudo apt-get install autossh
```
Create system d service
```
sudo vim /etc/system/systemd/autossh-lightning.service
```
and there put the service description, remember to replace the needed fields with your own data.
```
[Unit]
Description=port forwarding through auto ssh
After=network.target
[Service]
User=USERLOCAL
ExecStart=/usr/bin/autossh -M 0 -o ServerAliveInterval=30 -o ServerAliveCountMax=3 -i /home/USERLOCAL/.ssh/id_rsa -nNTv -R 0.0.0.0:9735:localhost:9735 YOUR_VPS_IP_ADDRESS
[Install]
WantedBy=multi-user.target
```
Then run:
```
sudo systemctl start autossh-lightning
sudo systemctl status autossh-lightning
```
If status is active we are all set.
originally posted at https://stacker.news/items/756320
-

@ 0861144c:e68a1caf
2024-11-06 16:20:18
I saw many people here (and other sites) claiming that they voted Trump because he will pardon Ross Ulbritch. Politicians live from promises and is their biggest bond. Since Trump have the...experience of saying half-truth, one possibility is that he doesn't pardon Ross and still in jail.
As non-US, all I can do is [zap my support to their legal fund](https://freeross.org/). Trump doesn't release Ross, **what is the next step**?
originally posted at https://stacker.news/items/756208
-

@ b4403b24:83542d4e
2024-11-06 13:43:13

originally posted at https://stacker.news/items/755988
-

@ b4403b24:83542d4e
2024-11-06 12:05:17
Republicans are hilarious 😂

originally posted at https://stacker.news/items/755844
-

@ 74718b83:b8204bd8
2024-11-06 11:09:14
curious to hear some opinions on this as i know many hate the idea of the gov having anything to do with btc, on the flip side, having it as a reserve currency in a large country could be the thing that tips mass adoption and understanding on a global scale , which would mean more people waking up to the power of btc.
it would also end the paper arguments no coiners make and silence them forever
originally posted at https://stacker.news/items/755779
-

@ 000002de:c05780a7
2024-11-06 03:24:27
You may not realize it, but you voted today. You vote everyday. Not in an election but in a much more mundane but infinitely more important way.
You voted with your time, talent, and treasure.
* What you gave your time to.
* What you gave your talents to push forward.
* What you spent your life force (money, savings, bitcoin) towards.
Its easy to let the world around you shift your focus. Make you feel good or bad for your participation in its rituals. But ask yourself.
What am I spending my time, talent, and treasure towards? Does it align with what I tell myself is important? Is it moving me and those around me closer to the world as I'd like to see it?
We have more control over our lives than any clowns that suck up to us for votes will ever have. Don't sell yourself short. You can become better. You can enrich others lives. You have value and worth. I believe our creator loves us more than we can even imagine. But, even if you don't believe that you can make your world better.
Make your vote count.
originally posted at https://stacker.news/items/755525
-

@ 35f3a26c:92ddf231
2024-11-06 00:07:28
##### **Who is the Cult of the Dead Cow (cDc)?** #####
A known USA based hacktivist group. According to the record in Wikipedia, it was started in 1984 at the Farm Pac slaughterhouse by Grandmaster Ratte' (aka Swamp Ratte'), Franken Gibe, Sid Vicious, and three BBS SysOps
You can check their member list in their [web site](https://cultdeadcow.com/members.html)
##### **Thinks of the cDc group that I have found quite interesting** #####
- Group member ***Drunkfux*** (Jesse Dryden) is the grand nephew of ***Charlie Chaplin***
- In 1991, the group began distributing ***music*** in the form of cassette tape albums
- In November 1994, the group claimed responsibility for giving ***President Ronald Reagan*** Alzheimer's disease, claiming to have done so in 1986 with a blowgun
- In 1995, the group declared war on the Church of Scientology stating "We believe that El Ron Hubbard [sic] is actually none other than Heinrich Himmler of the SS, who fled to Argentina and is now responsible for the stealing of babies from hospitals and raising them as 'super-soldiers' for the purpose of overthrowing the U.S. Fed. Govt. in a bloody revolution. We fear plans for a 'Fourth Reich' to be established on our home soil under the vise-like grip of oppression known as Scientology!"
- On January 7, 1999, the group joined with an international coalition of hackers to denounce a call to cyber-war against the governments of China and Iraq
- In February 2000, the group was the subject of an 11 minute documentary short titled "Disinformation".
- In February 2000, a member of the group by the code-name Mudge briefed ***President Bill Clinton*** on "Internet security".
- In 2003 the tool created by the group by the name of ***Six/Four System*** became the first product of a hacker group to receive approval from the ***United States Department of Commerce*** for export of strong encryption
- Member by the name of "Psychedelic Warlord" is congressman ***Beto O'Rourke***, an American politician who served as the U.S. representative for Texas's 16th congressional district from 2013 to 2019. ***A member of the Democratic Party***, party's nominee for the U.S. Senate in 2018, candidate for the presidential nomination in 2020, and the party's nominee for the 2022 Texas gubernatorial election.
#### **Do they have a political affiliation?** ####
From the previous section we could at least assume that they sympathize with the USA Democratic party, they supported President Bill Clinton and claimed responsibility for doing serious harm to President Ronald Reagan, I could not find any information if the government opened an investigation about this allegation or not.
#### **Their latest contribution?** ###
Recently, they have developed an application framework by the name of ***Veilid***, described as "like TOR" but for apps.
This application framework, if adopted by many developers will improve privacy by default for applications developed under that framework. The web site claim that it is open source
*You can review the information and project at the web site: [VEILID](https://veilid.com/)*
***In the Web site the group describe it as follows:***
"***Veilid*** allows anyone to build a distributed, private app. ***Veilid*** gives users the privacy to opt out of data collection and online tracking. ***Veilid*** is being built with user experience, privacy, and safety as our top priorities. It is open source and available to everyone to use and build upon."
"***Veilid*** goes above and beyond existing privacy technologies and has the potential to completely change the way people use the Internet. ***Veilid*** _has no profit motive_, which puts us in a unique position to promote ideals without the compromise of capitalism."
#### Summary ####
***Veilid*** seems to be exactly what is needed at the moment to bring privacy to the masses, even though TOR is doing a very good job and with the improved throughput its usage experience has improved, having a native privacy oriented FOSS application framework is paramount.
Most people is not technically savvy and therefore, not skilled in cyber security, they are constantly victims of cyber crime in many forms and shapes. eliminating one vector of attack by making the applications to opt out of data collection and online tracking from the get go is a step in the right direction, the question is, Would developers in general use the framework? Considering the ads will not be a possible source of income if the framework is used, well... Time will say...
-

@ 35f3a26c:92ddf231
2024-11-05 22:17:49
#### What is Peer Thinking?
The cognitive and emotional processes that occur when individuals are influenced by their peers.
#### The psychology behind it:
The psychology behind peer influence encompasses various factors, including:
1. Social belonging and acceptance,
2. Identity formation,
3. The dynamics of group behavior
#### Is it being used to control us?
https://image.nostr.build/cf90335bbf59e3395dc4324d123cd3a058ca716cf6172f079eb1d78547008147.jpg
IMO, yes, at the core of it is the basic human need for belonging. Social belonging is a critical component since it is craved by most, specially but not only by the youngest, those with power across the world know this very well, therefore, thinking that they will not use it to control the population in order to profit from it or change public opinion would be irrational.
The media is used to brain wash the population creating something that most will consider "the norm", thus, the majority will try to conform to that norm in order to belong. That include manipulating the population to take an experimental drug (even if it could be very dangerous due to its unknown effects) or to accept as a norm a behavior that few years back would have been considered inappropriate.
#### Cognitive Dissonance
https://image.nostr.build/60f24a810be1dd6badb36d70c5a691d4361207590dea1a8e64e09a75a252cfbf.jpg
This is a term that we should get familiar with. It is a psychological state where conflicting beliefs or behaviors create discomfort.
***Example:***
A kid in high school that has a good loving family but all his close friends are on drugs (legal ones) and they keep telling him he is an idiot for not using as well. Now his is that state of conflict believes, on one side his best friends, all tell him is okay, on the other hand his family that loves him has explained him at length the dangers and issues that the drugs will have in his life. To resolve the dissonance he has three options, one, join the group and start taking drugs with the rest, two try to rationalize it, considering to take drugs just occasionally to belong but not to make it a habit, three lose his friends (and here it comes again the peer thinking to bite). Extrapolate to many other cases.
> As an anecdote
Recently, on a friend's reunion, one of the guest was complaining about one of his daughters, she was quite confused asking him why so many of her classmates were bisexual, she was wondering if something was wrong with her since she was not; a 13 year old girl; the father was having a hard time explaining her that the majority are saying so just to feel as part of what the school was teaching to be the norm, it was not cool to be straight, the tally was 37% of the class. Consider that, statistically, the number of people, “worldwide” identifying as bisexual are between 3% and 5% (less than 1% in less accepting countries), that number used to be less than 2% less than a decade ago. But 37% is far from the statistical norm, indicating a peer thinking behavior but not the reality of their sexual preferences. Once again, extrapolate to any ideology, religion, gender identity, political agenda that a country desires to push forward for whatever reason, adding that to the official school program and to federal mandatory training programs would do the trick.
A powerful tool, that can be used for good or bad.
#### What are the strategies to counter negative peer thinking?
https://image.nostr.build/4b70949b8af76ed53a5be5507f41f1d1c960dc3592f199eab78e2d25688975c5.jpg
Reading the literature about the subject, few strategies are recommended:
1. *Self-Awareness*: teaching ourselves and our children to recognize when we are being influenced by peers
2. *Being selective with your friends*: peers with similar values will reinforce positive behaviors
3. *Learning to be assertive*: teaching ourselves and our children to communicate assertively our boundaries will empower us and them to resist unwanted pressure to adopt negative behaviors.
4. *Less judging more talking*: this applies to our children and partners, judging less and listening more will make our beloved ones more open to discuss social pressures.
***What do you think?***
***What strategies you use as counter measures?***
-

@ 35f3a26c:92ddf231
2024-11-05 22:14:02
#### What is Bitaxe?
Bitaxe is an open source ASIC (Application-Specific Integrated Circuit) Bitcoin miner that has been making waves in the cryptocurrency community. This innovative project aims to empower miners at every level with powerful, efficient, and **low-cost** mining solutions.
It is a fully open source ASIC Bitcoin miner developed by Skot9000, an advocate for open-source innovation in the Bitcoin space.
With all software and hardware specs available on GitHub, this project aims to provide miners with a transparent and accessible platform for Bitcoin mining.
https://image.nostr.build/db35c2a028e9f740181daabe2deef4e707653fa2d82f1602086e0ac4b5ee84fd.png
#### **Pros**
1. **Open Source**:
The Bitaxe is fully open source, allowing users to access and modify its source code, hardware designs, and build gerbers for PCB ordering.
2. **Low Cost**:
Bitaxe offers low-cost solutions for miners, making it an attractive option for those looking to enter the world of Bitcoin mining without breaking the bank.
3. **Efficient**:
The Bitaxe series is designed to be power-efficient, utilizing either the Bitmain BM1387 or BM1397 ASICs for SHA256 hashing.
#### **Cons**
1. **Technical Complexity**: Being an open-source project, users are required to be technically savvy to set up and maintain the miner, which could pose challenges for those without experience.
3. **Bricking Potential**:
Like any complex technology, there is a risk of bricking (rendering the device unusable) the Bitaxe if not handled properly.
#### **Summary**
The Bitaxe represents an exciting development in the world of Bitcoin mining, offering a low cost, efficient, and open-source solution for miners. While it may present some challenges for users who are new to the technology or lack technical expertise, the potential benefits far outweigh these drawbacks. As the project continues to evolve and gain traction, we can expect to see further improvements in performance, accessibility, and innovation within the Bitcoin mining landscape.
#### Where can I get more information
Go to their Github page:
https://github.com/skot/bitaxe
originally posted at https://stacker.news/items/659572
-

@ 5d4b6c8d:8a1c1ee3
2024-11-05 14:17:57
On the [Stacker Sports Podcast](https://fountain.fm/clip/SoqXGiWqaFFGwTjtD0pJ) we talked about the Emirates Cup Survivor Pool and a revision that needs to be made.
I messed up in describing the Group Stage as only taking place on Tuesdays. Group Stage games will actually be played on Tuesdays and Fridays, just like last year.
That means there are going to be seven Group Stage picks and we'll be picking games twice a week.
Check out the [original post](https://stacker.news/items/751054/r/Undisciplined) for the full details.
We already have eight contestants and hopefully a few more will join in the next week.
**Current Prize**
About 25k sats!
cc: @grayruby, @gnilma, @BlokchainB, @siggy47, @supercyclone, @realBitcoinDog, @Carresan,
originally posted at https://stacker.news/items/754602
-

@ 5d4b6c8d:8a1c1ee3
2024-11-05 13:35:10
We finally have an event other than soccer!
[Freebitcoin](https://freebitco.in/?r=51325722) is taking wagers on the Las Vegas Grand Prix.
Here's how to optimally allocate a hypothetical 2k sats on this event (according to [RBOA](https://stacker.news/items/342765/r/Undisciplined)):
| Driver | Wager |
|--------|--------|
| Vertappen | 486 |
| Norris | 521 |
| Leclerc | 456 |
| Alonso | 6 |
| Hamilton | 63 |
| Piastri | 107 |
| Tsunoda | 4 |
| Perez | 12 |
| Sainz | 243 |
| Russell | 63 |
| Stroll | 2 |
| Ocon | 4 |
| Ganyu | 1 |
| Bottas | 2 |
| Albon | 4 |
| Hulkenberg | 7 |
| Gasly | 4 |
| Magnussen | 6 |
Enjoy your winnings
originally posted at https://stacker.news/items/754549
-

@ 0861144c:e68a1caf
2024-11-05 12:23:01
Read the other parts: [Part 1](https://stacker.news/items/735219)|[Part 2](https://stacker.news/items/736674)|[Part 3](https://stacker.news/items/738294)|[Part 4](https://stacker.news/items/739692)|[Part 5](https://stacker.news/items/743142)| [Part 6](https://stacker.news/items/744965)| [Part 7](https://stacker.news/items/746621)| [Part 8](https://stacker.news/items/748225)| [Part 9](https://stacker.news/items/749793)| [Part 10](https://stacker.news/items/753048)
---
We continue with a story of Popes who want to take control of the Church but one of them is going to make a huge big mistake.

---
126. Leo VII [936-939] Stepbrother of Alberic II, Roman Senator. He was a Benedictine monk at the time of his appointment. He focused heavily on monastic life, granting much power to Alberic, Hugh of Arles, and Odo, Abbot of Cluny, to take control of ecclesiastical life and reform monastic living. He prohibited forced baptism of Jews.
127. Stephen VIII [939-942] Elected by Alberic II, he was a poor politician who combined secular and ecclesiastical powers, threatening to excommunicate the French if they did not recognize Louis IV of Outremer as King of France.
128. Marinus II [942-946] Elected by Alberic II, not much is notable except that he appointed the Archbishop of Mainz as papal legate and Apostolic Vicar of France and Germany.
129. Agapetus II [946-955] Elected by Alberic II. He favored ecclesiastical life, empowering Otto I, King of Germany, to organize ecclesiastical territories. He established the diocese of Hamburg-Bremen to continue missionary work in Nordic territories.
130. John XII [955-964] His name was Octavian of Tusculum. Elected by Alberic II. He ascended to the Papacy at 18, without religious training. He was lazy, idle, and fond of indulgence. He carried out one of the most significant acts in history: he called upon Otto I to take control of both Germany and Italy through the *Privilegium Ottonianum*, an improved copy of the *Constitutio Lotharii* that had been reviewed with Pope Eugene II [99]. This reignited the drama started with the Theophylact family, challenging papal independence once more. This led to the appointment, transfer, and sale of bishoprics, where laypeople had direct influence over Church matters. The Pope watched as Otto grew in power and sought help from the Emperor’s enemies until Otto realized this, marched to Rome, and confronted the Pope. He was murdered by a blow to the head with a hammer by the husband of one of his lovers.
- In the brief period between his death and flight (February-May), the Emperor Otto's secretary appointed Leo VIII as the new pope, but he lacked support from both the clergy and the people. He is considered an antipope.
131. Benedict V [964] Otto I did not recognize him as Pope and, invoking the document signed with his predecessor, informed Rome that they had lost the right to elect Popes. The Emperor had him arrested. He died in exile in Hamburg 30 days after his appointment.
132. Leo VIII [964-965] There is controversy over whether to consider this man as Pope or antipope. However, he was elected by Otto I in a synod. He issued documents during this short time, but they were not recognized due to an investiture dispute.
133. John XIII [965-972] John Crescentius. Rumors (still persistent) suggest he was a son of Theodora the Younger, Marozia's sister. He was a member of the Papal Court at the time of his appointment. His appointment was unpopular in Rome, and he reprimanded those who opposed it. His main achievement was spreading the Roman liturgy to Byzantium and supporting evangelization efforts among Slavs and Hungarians. He created the archdiocese of Magdeburg.
134. Benedict VI [973-974] Elected by Otto I. When Otto died, Crescentius I, brother of the previous Pope, organized a rebellion, imprisoned the Pope, and had him killed to prevent his liberation by the new emperor, Otto II. Boniface VII (antipope) tried to take power but was not recognized by the Emperor or Count Sicco of Spoleto, his secretary.
135. Benedict VII [974-983] Benedict of Sutri. Elected by imperial power and the Roman aristocracy. He founded the diocese of Prague and supported evangelical missions worldwide. In the synod of Rome (981), he condemned simony due to the growing number of married priests inheriting positions and benefits at the Church's expense.
136. John XIV [983-984] Pietro of Canossa. Imposed by the imperial power of Otto II, he was Italy’s vice-chancellor. Upon Otto II's death, his three-year-old son Otto III succeeded him. The antipope Boniface VII returned from exile and tried to reclaim the throne. This Pope allegedly died from poisoning.
137. John XV [985-996] Of the Imperial faction and imposed by Crescentius II. He replaced the Capetian dynasty with the Carolingian dynasty. He maintained open communication with all archbishoprics and bishoprics and established diplomatic relations with Russia, which was under Byzantine control. He canonized Ulrich of Augsburg.
138. Gregory V [996-999] Bruno of Carinthia. A cousin of Otto III. He was the first German pope. As expected, not being Roman or Italian, he lacked support from the Roman populace. He led an ascetic life. In 997, a revolt led by John Crescentius rose against him, appointing John Philagathos as John XVI (antipope). The revolt failed. John was beheaded, and the antipope was mutilated and exiled.
---
And so the series of Popes dependent on imperial power with lay interference continues, but that will be for the next chapter.
originally posted at https://stacker.news/items/754476
-

@ a367f9eb:0633efea
2024-11-05 08:48:41
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
> In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
>
> The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
> In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
>
> The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)?
**As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).**
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
## **Open-source matters**
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
## **Open-source is for your friends, and enemies**
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
## **Limiting open-source threatens our own advancement**
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols.
The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
*Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).*
-

@ a10260a2:caa23e3e
2024-11-05 06:21:10
TIL Google Authenticator can potentially collect a lot of data, more than some of the other popular 2FA apps[^1].
[^1]: https://www.pcmag.com/reviews/google-authenticator
Whether it does or it doesn’t, if you’re like me, you don’t turn down an opportunity to remove some Google from your life and add in some open-source.
Here’s a quick overview of the migration process.
**Step 1: Download [2FAS](https://apps.apple.com/us/app/2fa-authenticator-2fas/id1217793794)**

**Step 2: Export accounts from Authenticator**
This can be done via “Transfer accounts” in the sidebar. If you’re transferring on the same phone, take a screenshot of the QR code.
**Step 3: Import accounts into 2FAS**
During the setup process for 2FAS, you’ll be given the option to import existing tokens from Google. This is where you’ll tap “Choose QR Code” and select the screenshot you took in step 2.
Note that when you tap continue after importing the tokens, you’ll be taken back to the same screen as above. I think it should take you to your list of accounts after. Either way, don’t think the import failed. Just tap cancel, and you’ll be taken there.
If you’re on Android, check out [Aegis](https://github.com/beemdevelopment/Aegis). 🫡
originally posted at https://stacker.news/items/753472
-

@ 5d4b6c8d:8a1c1ee3
2024-11-04 16:07:54
It's week 2 of Mock Draft Monday and the Raiders continue climbing the draft board. Now picking 6th and still needing to play NO, while having the tie-breaker with Carolina, there's a great chance of getting into the top three.
The Raiders O-Line was obliterated this week. Ted Hendricks had a career day lined up against our third string left tackle. The silver lining is that JPJ was moved to center and it's clearly the right place for him.
That all indicates that for approximately the 17th year in a row, the Raiders primary draft needs are QB, OT, and Guard. They also need to improve the WR and RB rooms. The defense is fine, but could also use upgrades at every level.
Here we go:
6th Pick: QB Cam Ward
37th Pick: IOL Jonah Savaiinaea
68th Pick: LB Danny Stutsman
74th Pick: OT Marcus Mbow
104th Pick: DT Jordan Burch
140th Pick: WR Bru McCoy
177th Pick: RB Jo'Quavious Marks
212th Pick: CB Cobee Bryant
215th Pick: QB Conner Weigman
222nd Pick: S Shilo Sanders
Two in a row with Cobee Bryant going 212th.
I opted for the 49ers strategy of taking the QB we want with our first pick, but then taking another one later on day 3. The QB room has three seats in it, so I say bring in two QB's every year until we find our franchise guy: AOC is a perfectly serviceable backup/bridge QB.
originally posted at https://stacker.news/items/753327
-

@ 5d4b6c8d:8a1c1ee3
2024-11-04 15:45:30
The first moves of the Raiders bye-week adjustments have already happened. OC Luke Getsy, as well as their offensive line and quarterback coaches.
This had to happen, after the woeful offensive performances of the team. The run game especially has been abysmal and it's clearly due to coaching because the personnel is better than last year's o-line.
Getsy showed absolutely no ability to adapt to the defenses the team faced. His opening scripted plays often worked really well, but then the offense became completely stagnant for the remainder of the game.
It's not clear who will take over the play calling duties, or fill the other vacated roles, but the Raiders bloated coaching staff has three former play callers on it. The most likely candidate is Scott Turner.
---
This needs to be the first of several changes to the coaching staff. Situational game management has been atrocious, so the person filling that role needs to be relieved as well. Reports are that assistant head coach Marvin Lewis has been completely phoning it in, so he should be gone to.
The Raiders season has been over for a few weeks already and the remainder of the season needs to be about evaluating who to keep around. That should entail pairing down the largest coaching staff in the league, so we can see what Antonio Pierce does without the training wheels. This should also entail shutting down veterans like Minshew and Kolton Miller, in favor of getting a look at all the young guys on the roster.
originally posted at https://stacker.news/items/753300
-

@ 57d1a264:69f1fee1
2024-11-04 15:17:28



———
NEW YORK (Nov. 4, 2024) — The Human Rights Foundation (HRF), along with partners dedicated to artistic freedom, expresses deep concern over the arrest and arbitrary detention of Gao Zhen, a prominent contemporary Chinese artist and a member of the well-known Gao Brothers, a collaborative artist duo. In [a letter](https://hrf.org/wp-content/uploads/2024/10/Letter-Demanding-Gao-Zhens-Release_Final.pdf) to the Consulate General of the People’s Republic of China in New York and other embassies, we call for his unconditional release.
On Aug. 26, Gao was arrested and detained after 30 police officers conducted a raid on his studio in Yanjiao, a town in the small city of Sanhe, in the northern province of Hebei. He has been held since at the Sanhe City Detention Center on charges of “slandering China’s heroes and martyrs” — a crime punishable by up to three years in prison.
A United States lawful permanent resident, Gao, 68, has made a career out of exposing the horrors of the Cultural Revolution through satirical humor that pushes the boundaries of social commentary. His works are also bold critiques of the Cultural Revolution and former Chinese Communist Party (CCP) leader Mao Zedong and his authoritarian rule of the country.
“These topics are sensitive and considered taboo in today’s CCP-controlled China, yet it is crucial to educate the world on the truth of Mao’s dictatorial legacy,” HRF Chief Advocacy Officer Roberto Gonzalez said. “Mr. Zhen’s detention is not only a violation of his basic rights but also an attack on the fundamental freedoms of all Chinese people, who have the right to learn the truth about dictator Mao Zedong.”
HRF demands Gao Zhen’s immediate and unconditional release as well as the CCP’s repeal of the Heroes and Martyrs Protection Law to safeguard artistic freedom in China.
- - -
For press inquiries, please contact [media@hrf.org](mailto:media@hrf.org).
- - -
_<sub>The Human Rights Foundation (HRF) is a nonpartisan nonprofit organization that promotes and protects human rights globally, with a focus on closed societies.</sub>_
originally posted at https://stacker.news/items/753275
-

@ 0861144c:e68a1caf
2024-11-04 12:27:35
These are the previous parts: [Part 1](https://stacker.news/items/735219)|[Part 2](https://stacker.news/items/736674)|[Part 3](https://stacker.news/items/738294)|[Part 4](https://stacker.news/items/739692)|[Part 5](https://stacker.news/items/743142)| [Part 6](https://stacker.news/items/744965)| [Part 7](https://stacker.news/items/746621)| [Part 8](https://stacker.news/items/748225)| [Part 9](https://stacker.news/items/749793)
---
The papacy enters one of its darkest periods, not only marked by a series of medieval violence but also by the utter prostitution of power in scenarios so obscene that, by the time you finish reading, you may question the absolute sanctity of the pontificate.
111. **Formosus [891-896]** Consecrated as bishop by Nicholas [105]; he was a missionary whose main strength was encouraging Christians to combat paganism through letters. He supported the coronation of Arnulf of Carinthia, against the wishes of Charles the Bald (France), who had the favor of John VIII [107]; Guido of Spoleto was forced to crown his son Lambert as Emperor, while the Pope began talks with Arnulf. The Pope sought Arnulf's help to free Italy from the Spoletos.
112. **Boniface VI [896]** He suffered from gout when elected and died 15 days later.
113. **Stephen VI [896-897]** Elected with the support of the Emperor of the Holy Roman Empire and King of Italy, Lambert. This is one of the most shameful moments in the Church's history. In March 897, a posthumous trial was initiated against Formosus [111], during which Formosus' body was exhumed, dressed in papal vestments, given a defense lawyer, and put on trial. He was found guilty, his election as Pope invalidated, all his appointments and ordinations annulled, his body stripped of its vestments, and his remains thrown into the Tiber River. A few months later, following an earthquake, a mob took advantage of the chaos to assassinate the Pope, strangling him, presumably on the orders of the Spoletos in revenge for the trial known today as the *Cadaver Synod* or the *Synod of Horror*.

*This is a representation of the Cadaver Synod. Too strong for me. Jean-Paul Laurens (1870)*
114. **Romanus [897]** Seeing the chaos left by his predecessor, he began the process of rehabilitating Formosus [111] but died 90 days after assuming office. It is hypothesized that he was poisoned.
115. **Theodore II [897]** Held power for 20 days. His first order was to return Formosus' remains to St. Peter's Basilica and convened a synod that annulled all decisions from the *Synod of Horror*, declaring it void. Notably, Lambert of Spoleto's supporters wanted Count of Tusculum, Sergius, as Pope. Theodore was murdered, possibly by poisoning.
116. **John IX [898-900]** A Benedictine monk, elected with Lambert of Spoleto's support. He completed the work of his predecessor and, to avoid further violence, decreed that Papal Consecration must take place in the presence of the Emperor's representative. This reversed the *Constitutio Lotharii*. He also prohibited the tradition of looting bishops' palaces or papal palaces upon their death, declared Arnulf's consecration invalid, and granted all prerogatives to Lambert, his protector. The anti-Formosus faction wanted Sergius [119] as Pope but failed. The Theophylact family began tightening its grip on the papacy.
117. **Benedict IV [900-903]** Elected when the throne of the Holy Roman Empire was vacant. Lambert died in 899. Berengar I, King of Italy and grandson of Louis the Pious, claimed the imperial title, but the Pope granted it to Louis III the Blind, hoping he would defend against Hungarian invasions from the north and Saracens from the south. Louis was defeated by Berengar, blinded, and exiled. Lacking support, Benedict sought (a major error) support from the Theophylact family, including Theodora and her daughter Marozia, who would dominate the papacy henceforth.
118. **Leo V [903]** Elected Pope, little is known about his papacy. He was imprisoned and murdered 30 days after his election, likely by Pope Sergius III (his successor). Christopher the Priest declared himself Pope (antipope) but was also murdered, allegedly by Sergius III.
119. **Sergius III [904-911]** Linked to the Theophylact family and a supporter of the *Synod of Horror*, where he actively participated. He began the *pornocracy*[^1] period. He attempted to desecrate Formosus' tomb, without success. He married Alberic to Marozia, rumored to be the Pope's mistress. The Cluny Abbey was founded in 910 by William of Aquitaine and linked to the papal estate, initiating the Cluniac reform.
120. **Anastasius III [911-913]** Elected with the support of Theodora and Marozia. The second period of the *pornocracy*. A puppet of the Theophylact family. The conversion of the Normans began during his papacy.
121. **Lando [913-914]** Elected with Theodora and Marozia's support. The third period of the *pornocracy*. Nothing significant is recorded.
122. **John X [914-928]** Fiscal agent for the Archbishop of Ravenna. The fourth period of the *pornocracy*. Favored by Theodora, widow of Theophylact, with whom he had relations. His main role was leading an army for the first time in history, supported by Alberic, to defeat the Saracens at the Battle of Garigliano [916] and permanently expel them. Berengar I was assassinated in 924, the last Emperor of the Holy Roman Empire. John appointed the five-year-old Hugh of Vermandois as Archbishop of Reims. He was murdered by Marozia's henchmen for being useless to her family's interests.
123. **Leo VI [928]** The fifth period of the *pornocracy*. No significant events are recorded. He was murdered on Marozia's orders.
124. **Stephen VII [928-931]** The sixth period of the *pornocracy*. He was murdered on Marozia's orders.
125. **John XI [931-935]** The seventh and final period of the *pornocracy*. An illegitimate son of Marozia, reportedly fathered by Alberic, Duke of Spoleto. Became Pope at age 20. Marozia erred by marrying Hugh, King of Italy, prompting a rebellion by her eldest son from her first marriage, Alberic II. He imprisoned his mother with the Pope's and his half-brother's support. John granted Cluny Abbey the power to include monastic houses following their rules. Abbot Hugh rose to prominence and is considered one of the greats in history.
[^1]: *Pornocracy* is an Italian term meaning the government by courtesans or prostitutes. It first appeared in the writings of Cardinal Baronius, referring to a period in which two women wielded real power: Theodora, wife of the Roman senator Theophylact, and her daughter Marozia. This term has been used throughout history regardless of gender or sexual orientation.
originally posted at https://stacker.news/items/753048
-

@ 5d4b6c8d:8a1c1ee3
2024-11-04 02:05:22
I just saw that Adam Silver is considering alternative formats for the NBA All-Star Game, in an effort to have something fans might actually enjoy watching. There are no details about what's under consideration, but this seems like a fun topic to speculate on.
Personally, I'd like to see the game replaced with a 3x3 tournament. The same 24 players could be assigned to 8 teams and play a three round tournament of short games.
I would also love a one on one tournament, but I know most of the best players would chicken out.
What say you?
originally posted at https://stacker.news/items/752728
-

@ fd208ee8:0fd927c1
2024-11-03 21:51:39
## All memed out
It finally happened. I think it was October 25th, at circa 18:45 in the evening. I was doomscrolling my Nostr feed, and kept seeing the same Bitcoin memes repeated over and over, by different people. They weren't even reposts, they were copy-pasted versions of the same image. A very funny image. Well, it was very funny last year... and the year before that... and probably the year before that, when it appeared on a different network.
Because it's all just reposts, copy-pastes and rehashes of the Best of Bitcoin Twitter, just like the tiresome influencers, with their groupies and their Episode 498 of *Let's all eat a large chunk of lightly-burnt dead animal and count our stacks before jetting off to talk about how to save the poors by getting them to buy individual satoshis with money they don't have*.

## I'm the poors your looking for
It's all so tiresome. It has little bearing on the real world I see around me, where most people are thinking all day about 99 problems and Bitcoin ain't one.

Which is, of course, what the Bitcoin influencers would have you believe, is the reason that they're poor. What in the world could be more important, than thinking about Bitcoin? Why do these people not get with the program? Don't they know, that we are trying to save them?

Why are they worrying about OtherProblems? Don't they know that all OtherProblems can be fixed with Bitcoin? Really, if you just go back far enough, in any current, situational problem, you will discover that there was some slight, negative shift to the history record that involved soft money. It's the financial version of the Butterfly Effect.

That's why #BitcoinFixesThis. Bitcoin fixes everything, if you just think about it, for long enough.
The same way that we all actually come out of Africa, supposedly, if you go back enough generations. So, coming out of Africa, now, as a Real Life Person in The Present is supposed to have no significance. What does someone from Cameroon know about Africa, that someone from Alaska doesn't? Both people come out of Africa, if you just think about it, for long enough.

And maybe that really is true. Maybe Bitcoin will eventually end all vice and crimes, save the planet, and we will all just hold hands and sing kumbaya all day, while waiting for the Singularity to upload us to Satoshi.
## Bitcoin envelope budgeting
Or maybe it's not. Maybe it's just a really hard, digital money that incentivizes savings, functions as a reliable measure, and makes micropayments possible on a global scale. Those really are things that will help the poors, including myself. I can see it, already, when trying to organize pre-paid meetups or figure out what to do with our household's meager savings, when the stock market is looking particularly bubblicious.

But this is what I would consider Boring Bitcoin. Bitcoin home economics. Penny-pinching Bitcoin. Bitcoin for homemakers. How to use the Bitcoin envelope budgeting system to beat inflation by a margin of 13%.
The actual use of Bitcoin as money, rather than as a mere investment gamble or hype machine. That's the part of Bitcoin that nobody seems to really talk about because it's incredibly practical, dull, and useful, and it can only be tested by -- Oh, the horror! -- actually spending Bitcoin.
But... perhaps I will begin talking about it. Perhaps those of us, Bitcoiners, who are having fun staying poor, while stacking sats, should speak up a bit more. Perhaps the boring stuff is actually the interesting stuff. Perhaps there is more to say about Bitcoin, than can fit into a meme.
-

@ c11cf5f8:4928464d
2024-11-03 09:21:30
Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, [here](https://stacker.news/items/741746/r/AG) are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/751696
-

@ 57d1a264:69f1fee1
2024-11-02 18:12:56
If'd have to make a list of functionalities that you miss from the current Ui, what it would be?
Signup with nostr https://gitworkshop.dev
Below the current screens, compared with Github:
# Landing
|||
|---|---|
|  |  |
# Explore Repos
|||
|---|---|
|  |  |
# Profile
|||
|---|---|
|  |  |
# Repo
|||
|---|---|
|  |  |
# Issues
|||
|---|---|
|  |  |
#NostrDesign #BitcoinDesign #Bitcoin #Nostr #Design
originally posted at https://stacker.news/items/751209
-

@ 5d4b6c8d:8a1c1ee3
2024-11-02 15:47:53
We're back with a new name (that @grayruby hates it)!
Last year's [NBA In-Season Tournament Survivor Pool](https://stacker.news/items/340815/r/Undisciplined) was a lot of fun and @POTUS walked away with 27k sats when the Pacers won the tournament.
# Emirates Cup Details
The tournament has four Group Play rounds, followed by three Knockout rounds.
The Group Play rounds are played every Tuesday from Nov. 12th to Dec. 3rd. Every team in the NBA is randomly assigned to one of the groups. This is three games fewer than last year.
The Knockout rounds are a single elimination tournament between the eight best teams from the Group Play rounds. The first round will be played on Dec. 10th and 11th. The second round will be played on Dec. 14th. The final round will be played on Dec. 17th.
# Survivor Pool Details
- The survivor pool will have a 3k buy-in and a 5k second buy-in, for those who need it.
- The second buy-in can only be used prior to the Knockout Rounds.
- That means the pool is starting with at least 5k in prize money (8k if I miss a pick).
- Any sats zapped to survivor pool contest posts on SN or to my comments on those posts will be added to the buy-ins to make up the final prize (no sybil fee deductions)
- You can only pick each team once, so be careful not to use up the eventual contenders too early.
- If you forget to make a pick, I'll assign you whichever team has the worst odds for that round that you are still allowed to pick.
- In the event of a tie, the winner will be determined by whoever correctly predicts the Cup MVP first. If no one correctly predicts the cup MVP, then the winner will be decided by whoever most closely predicts the pointspread of the championship game.
- Posts for each round will go up the day after the previous round and selections can be made up until tip-off of the team you're selecting.
Leave a comment if you're interested in joining and I'll reply with a comment for you to zap your initial buy-in to.
cc last year's participants: @grayruby, @POTUS, @gnilma, @elnosh, @Wumbo, @BTC_Bellzer, @siggy47, @Chep, @BlokchainB
originally posted at https://stacker.news/items/751054
-

@ acc925af:db9fb0bb
2024-11-02 15:47:14
https://open.spotify.com/track/02ppMPbg1OtEdHgoPqoqju?si=d6518df327eb46ee
originally posted at https://stacker.news/items/751017
-

@ acc925af:db9fb0bb
2024-11-02 15:46:18
https://open.spotify.com/track/6ttYF5VadzTssGV2i1Q08T?si=1fc0f37b2bf04be2
Need a soothing song to relax?, look no further
originally posted at https://stacker.news/items/750993
-

@ 5d4b6c8d:8a1c1ee3
2024-11-02 14:24:23
Mornin' Stackers,
Here are our proposed topics for today's episode:
Contests
- Wrapping up the MLB Pool
- Update on NFL Pool
- Introducing the Cricket Pools
- Previewing NBA Emirates Cup Pool and College Football Playoff Contest
Posts
- Guess my favorite pitcher
- Stacker grudge match
- The future of Juan Soto
Sports
- World Series recap
- NFL Trade Deadline
- NBA early season thoughts
Gamblin'
- Betting on sports futures using lightning
Share your takes, be they hot, medium, or mild, and we'll try to fit them in. Stacker Sports Pod is for stackers by stackers.
originally posted at https://stacker.news/items/750965
-

@ 188302bb:9052db11
2024-11-02 11:59:46
I'm considering building an application specifically designed for use by insurance companies and banks. Before diving into development, I'd like to validate the idea to ensure it addresses real needs in the industry. What steps should I take to effectively validate the concept, assess market demand, and gather feedback from potential users? Should I conduct interviews, use surveys, or create a prototype to present to stakeholders? Additionally, what are the key metrics or indicators that would confirm this app idea has strong potential before I start coding?
originally posted at https://stacker.news/items/750765
-

@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
> ### 第三方API合集:
---
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 |
| --- | --- | --- | --- |
| AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) |
| OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) |
| CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) |
| OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) |
` 持续更新。。。`
---
### 推广:
访问不了openai,去`低调云`购买VPN。
官网:https://didiaocloud.xyz
邀请码:`w9AjVJit`
价格低至1元。
 @ a79bb203:dde63268
2024-11-16 21:38:18I was quite happy with the result (about 3 hours of work) https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMYNb.jpg Bumblebees symbolize hard work, diligence, and productivity. originally posted at https://stacker.news/items/770779
@ a79bb203:dde63268
2024-11-16 21:38:18I was quite happy with the result (about 3 hours of work) https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMYNb.jpg Bumblebees symbolize hard work, diligence, and productivity. originally posted at https://stacker.news/items/770779 @ 5d4b6c8d:8a1c1ee3
2024-11-16 17:07:19We almost all survived! Sorry, @BlokchainB. You took what should have been a very safe Denver team and then neither their very good head coach nor the best player in the world showed up. **Ode to the fallen**: > In peace, may you leave this shore. In love, may you find the next. Safe passage on your travels, until our final journey to the ground. May we meet again. Let's all pour one out for Blok. ---------- # Winners' Recap The Pistons were really trying to get @supercyclone eliminated, but the Raptors were just too pathetic to hold onto the win. Despite putting up almost 50 points in the first quarter, Cleveland let the lowly Bulls back into the game. Ultimately, I doubt @realBitcoinDog was ever particularly concerned that the now 14-0 Cavs would put Chicago away. After seeming to have the game in hand, the Knicks somehow allowed cross-town rival Brooklyn back in the game. Thankfully for @gnilma's wallet, they made two big plays to close out the game. The Magic, sans young star Paolo, clobbered the supposedly contending 76ers. @Carresan really never had to sweat this one. In a game of which I watched not one second, the Hawks defeated the woeful Wizards and secured survival for the rest of us. # Other Notable Games The Jimmy-less Heat put a real whooping on the Pacers, who are looking miserable this season. OKC continues winning, despite having no centers in their rotation. I think 6'3" Lu Dort might be playing center. I caught a little bit of the Lakers, Warriors, and T-Wolves, all of whom looked good in their wins. # Prize Closing in on 50k! originally posted at https://stacker.news/items/770488
@ 5d4b6c8d:8a1c1ee3
2024-11-16 17:07:19We almost all survived! Sorry, @BlokchainB. You took what should have been a very safe Denver team and then neither their very good head coach nor the best player in the world showed up. **Ode to the fallen**: > In peace, may you leave this shore. In love, may you find the next. Safe passage on your travels, until our final journey to the ground. May we meet again. Let's all pour one out for Blok. ---------- # Winners' Recap The Pistons were really trying to get @supercyclone eliminated, but the Raptors were just too pathetic to hold onto the win. Despite putting up almost 50 points in the first quarter, Cleveland let the lowly Bulls back into the game. Ultimately, I doubt @realBitcoinDog was ever particularly concerned that the now 14-0 Cavs would put Chicago away. After seeming to have the game in hand, the Knicks somehow allowed cross-town rival Brooklyn back in the game. Thankfully for @gnilma's wallet, they made two big plays to close out the game. The Magic, sans young star Paolo, clobbered the supposedly contending 76ers. @Carresan really never had to sweat this one. In a game of which I watched not one second, the Hawks defeated the woeful Wizards and secured survival for the rest of us. # Other Notable Games The Jimmy-less Heat put a real whooping on the Pacers, who are looking miserable this season. OKC continues winning, despite having no centers in their rotation. I think 6'3" Lu Dort might be playing center. I caught a little bit of the Lakers, Warriors, and T-Wolves, all of whom looked good in their wins. # Prize Closing in on 50k! originally posted at https://stacker.news/items/770488 @ 5d4b6c8d:8a1c1ee3
2024-11-16 00:24:01I've got Heat-Pacers on and I'm excited about some of the later games. Is anyone else tuning into the second night of the Emirates Cup? originally posted at https://stacker.news/items/769843
@ 5d4b6c8d:8a1c1ee3
2024-11-16 00:24:01I've got Heat-Pacers on and I'm excited about some of the later games. Is anyone else tuning into the second night of the Emirates Cup? originally posted at https://stacker.news/items/769843 @ f33c8a96:5ec6f741
2024-11-15 21:45:12# Voltage Tipper ⚡ A Simple Lightning tipping app template built with NextJS and Voltage. [Voltage Tipper Video Walkthrough](https://www.youtube.com/watch?v=y2eFBtRLRUk) To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work! [](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper) **Run on Replit** [https://replit.com/@voltage-cloud/voltage-tipper](https://replit.com/@voltage-cloud/voltage-tipper) ## Table of Contents 1. [Deployment](#deployment) 2. [Environment Variables](#environment-variables) 3. [API](#api) 4. [Contributing](#contributing) 5. [License](#license) ## Deployment To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work! [](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper) ## Environment Variables - `NEXT_PUBLIC_HOST`: The host URL for your LND lightning node (not including port). - `NEXT_PUBLIC_INVOICE_MACAROON`: The invoice macaroon. - `NEXT_PUBLIC_READ_MACAROON`: The read-only macaroon. #### Host The host is your Node's 'API endpoint' you can copy it from your Voltage Dashboard, be sure to include 'https://'. Example: `https://plebdev.m.voltageapp.io` #### Macaroons The Invoice and Read macaroons are authentication tokens that allows you to interact with your LND node's REST API with permissions for reading data, and creating invoices. You can also grab a "Admin" macaroon for permissions to spend but that is not required here since we are only receiving through this webapp, so your funds are safu. **You can find your Macaroons in your Voltage Dashboard by visiting Manage Access -> Macaroon Bakery** ## API - `/api/lnurl` Returns lnurlPay response object defined in [LUD-06](https://github.com/lnurl/luds/blob/luds/06.md) - `/api/getlnurl` Returns bech32 encoded lnurlPay - `/.well-known/lnurlp/{NodeAlias}` This is your lightning address endpoint, returns lnurlPay response defined in [LUD-16](https://github.com/lnurl/luds/blob/luds/16.md) - `/api/callback?amount=21000` This is your callback endpoint that will return an invoice when `amount` query parameter is passed with millisat value ## Contributing Contributions are welcome! Please open an issue or submit a pull request. ## License This project is licensed under the MIT License. See the LICENSE file for details.
@ f33c8a96:5ec6f741
2024-11-15 21:45:12# Voltage Tipper ⚡ A Simple Lightning tipping app template built with NextJS and Voltage. [Voltage Tipper Video Walkthrough](https://www.youtube.com/watch?v=y2eFBtRLRUk) To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work! [](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper) **Run on Replit** [https://replit.com/@voltage-cloud/voltage-tipper](https://replit.com/@voltage-cloud/voltage-tipper) ## Table of Contents 1. [Deployment](#deployment) 2. [Environment Variables](#environment-variables) 3. [API](#api) 4. [Contributing](#contributing) 5. [License](#license) ## Deployment To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work! [](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper) ## Environment Variables - `NEXT_PUBLIC_HOST`: The host URL for your LND lightning node (not including port). - `NEXT_PUBLIC_INVOICE_MACAROON`: The invoice macaroon. - `NEXT_PUBLIC_READ_MACAROON`: The read-only macaroon. #### Host The host is your Node's 'API endpoint' you can copy it from your Voltage Dashboard, be sure to include 'https://'. Example: `https://plebdev.m.voltageapp.io` #### Macaroons The Invoice and Read macaroons are authentication tokens that allows you to interact with your LND node's REST API with permissions for reading data, and creating invoices. You can also grab a "Admin" macaroon for permissions to spend but that is not required here since we are only receiving through this webapp, so your funds are safu. **You can find your Macaroons in your Voltage Dashboard by visiting Manage Access -> Macaroon Bakery** ## API - `/api/lnurl` Returns lnurlPay response object defined in [LUD-06](https://github.com/lnurl/luds/blob/luds/06.md) - `/api/getlnurl` Returns bech32 encoded lnurlPay - `/.well-known/lnurlp/{NodeAlias}` This is your lightning address endpoint, returns lnurlPay response defined in [LUD-16](https://github.com/lnurl/luds/blob/luds/16.md) - `/api/callback?amount=21000` This is your callback endpoint that will return an invoice when `amount` query parameter is passed with millisat value ## Contributing Contributions are welcome! Please open an issue or submit a pull request. ## License This project is licensed under the MIT License. See the LICENSE file for details. @ 5d4b6c8d:8a1c1ee3
2024-11-15 21:03:43This is a requested topic for a future podcast episode. I do have a giant spreadsheet with a bunch of stats and stuff in it to help figure this out, but I'm doing this off the top of my head. # My Top 10 1. Jordan: 6 titles, 6 Finals MVPs, 5 MVPs, 1 DPOY, and tops by my eye test 2. Lebron: 4 titles, 4 Finals MVPs, 4 MVPs, 20 All-NBAs, holds virtually all the career playoff stats 3. Kareem: 6 titles, 2 Finals MVPs, 6 MVPs, 15 All-NBAs, also the greatest HS and college player ever 4. Wilt: 2 titles, 1 Finals MVP, 4 MVPs, 10 All-NBAs, holds virtually all single game and single season records 5. Magic: 5 titles, 3 Finals MVPs, 3 MVPs, 10 All-NBAs, greatest passer of all time and played every position 6. Bird: 3 titles, 2 Finals MVPs, 3 MVPs, 10 All-NBAs, most well-rounded player ever 7. Russell: 11 titles, 5 MVPs, 11 All-NBAs, greatest winner in the history of professional sports 8. Duncan: 5 titles, 3 Finals MVPs, 2 MVPs, 15 All-NBAs, most underrated player in NBA history 9. Kobe: 5 titles, 2 Finals MVPs, 1 MVP, 15 All-NBAs, 12 All-Defense teams, more All-Star MVPs than anyone 10. Steph: 4 titles, 1 Finals MVP, 2 MVPs, 10 All-NBA, greatest shooter ever Honorable mentions: Shaq and Jokic Shaq and Steph are a toss-up to me. I came down on the side of positional balance. You could think of this as an All-time 1st and 2nd team, rather than purely a top 10. I expect Jokic to make it, but he's right in the middle of his prime and hasn't yet matched the career achievements of these guys. Let the arguments begin! originally posted at https://stacker.news/items/769603
@ 5d4b6c8d:8a1c1ee3
2024-11-15 21:03:43This is a requested topic for a future podcast episode. I do have a giant spreadsheet with a bunch of stats and stuff in it to help figure this out, but I'm doing this off the top of my head. # My Top 10 1. Jordan: 6 titles, 6 Finals MVPs, 5 MVPs, 1 DPOY, and tops by my eye test 2. Lebron: 4 titles, 4 Finals MVPs, 4 MVPs, 20 All-NBAs, holds virtually all the career playoff stats 3. Kareem: 6 titles, 2 Finals MVPs, 6 MVPs, 15 All-NBAs, also the greatest HS and college player ever 4. Wilt: 2 titles, 1 Finals MVP, 4 MVPs, 10 All-NBAs, holds virtually all single game and single season records 5. Magic: 5 titles, 3 Finals MVPs, 3 MVPs, 10 All-NBAs, greatest passer of all time and played every position 6. Bird: 3 titles, 2 Finals MVPs, 3 MVPs, 10 All-NBAs, most well-rounded player ever 7. Russell: 11 titles, 5 MVPs, 11 All-NBAs, greatest winner in the history of professional sports 8. Duncan: 5 titles, 3 Finals MVPs, 2 MVPs, 15 All-NBAs, most underrated player in NBA history 9. Kobe: 5 titles, 2 Finals MVPs, 1 MVP, 15 All-NBAs, 12 All-Defense teams, more All-Star MVPs than anyone 10. Steph: 4 titles, 1 Finals MVP, 2 MVPs, 10 All-NBA, greatest shooter ever Honorable mentions: Shaq and Jokic Shaq and Steph are a toss-up to me. I came down on the side of positional balance. You could think of this as an All-time 1st and 2nd team, rather than purely a top 10. I expect Jokic to make it, but he's right in the middle of his prime and hasn't yet matched the career achievements of these guys. Let the arguments begin! originally posted at https://stacker.news/items/769603 @ f33c8a96:5ec6f741
2024-11-15 18:44:32# Setting Up a React App from Scratch: A Minimal Guide ## Prerequisites - Node.js and npm installed on your machine - A text editor of your choice ## Step 1: Create a New Project Directory ```bash mkdir my-react-app cd my-react-app ``` ## Step 2: Initialize the Project ```bash npm init -y ``` This creates a package.json file with default values. ## Step 3: Install Dependencies ```bash npm install react react-dom npm install --save-dev parcel @babel/preset-react ``` ## Step 4: Create Project Structure Create the following files and directories: ``` my-react-app/ ├── src/ │ ├── index.html │ └── index.js └── package.json ``` ## Step 5: Set Up HTML In src/index.html, add the following content: ```html <!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>My React App</title> </head> <body> <div id="root"></div> <script src="./index.js"></script> </body> </html> ``` ## Step 6: Create React Entry Point In src/index.js, add the following content: ```javascript import React from 'react'; import ReactDOM from 'react-dom/client'; const App = () => { return <h1>Hello, React!</h1>; }; const root = ReactDOM.createRoot(document.getElementById('root')); root.render(<App />); ``` ## Step 7: Configure Babel Create a .babelrc file in the project root: ```json { "presets": ["@babel/preset-react"] } ``` ## Step 8: Update package.json Scripts Add the following scripts to your package.json: ```json "scripts": { "start": "parcel src/index.html", "build": "parcel build src/index.html" } ``` ## Step 9: Run the Development Server ```bash npm start ``` Your app should now be running at http://localhost:1234. ## Step 10: Build for Production When you're ready to deploy: ```bash npm run build ``` This will create a dist folder with your optimized production build. --- Congratulations! You've set up a React app from scratch using Parcel. This setup provides a lightweight and modern development environment with minimal overhead.
@ f33c8a96:5ec6f741
2024-11-15 18:44:32# Setting Up a React App from Scratch: A Minimal Guide ## Prerequisites - Node.js and npm installed on your machine - A text editor of your choice ## Step 1: Create a New Project Directory ```bash mkdir my-react-app cd my-react-app ``` ## Step 2: Initialize the Project ```bash npm init -y ``` This creates a package.json file with default values. ## Step 3: Install Dependencies ```bash npm install react react-dom npm install --save-dev parcel @babel/preset-react ``` ## Step 4: Create Project Structure Create the following files and directories: ``` my-react-app/ ├── src/ │ ├── index.html │ └── index.js └── package.json ``` ## Step 5: Set Up HTML In src/index.html, add the following content: ```html <!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>My React App</title> </head> <body> <div id="root"></div> <script src="./index.js"></script> </body> </html> ``` ## Step 6: Create React Entry Point In src/index.js, add the following content: ```javascript import React from 'react'; import ReactDOM from 'react-dom/client'; const App = () => { return <h1>Hello, React!</h1>; }; const root = ReactDOM.createRoot(document.getElementById('root')); root.render(<App />); ``` ## Step 7: Configure Babel Create a .babelrc file in the project root: ```json { "presets": ["@babel/preset-react"] } ``` ## Step 8: Update package.json Scripts Add the following scripts to your package.json: ```json "scripts": { "start": "parcel src/index.html", "build": "parcel build src/index.html" } ``` ## Step 9: Run the Development Server ```bash npm start ``` Your app should now be running at http://localhost:1234. ## Step 10: Build for Production When you're ready to deploy: ```bash npm run build ``` This will create a dist folder with your optimized production build. --- Congratulations! You've set up a React app from scratch using Parcel. This setup provides a lightweight and modern development environment with minimal overhead. @ f33c8a96:5ec6f741
2024-11-15 18:39:13# node-backend-walkthrough  A step-by-step walkthrough on how to setup and deploy a nodejs backend built with Express / Knex / SQLite (dev db) / Postgres (production db) ## Step 1: Setting up your project / dependencies ### 1.1 Create a new Node.js project To set up a new Node.js project, follow these steps: - Create a new directory for your project by running the following command in the terminal: `mkdir my-project` - Navigate into the new directory by running: `cd my-project` - Initialize a new Node.js project by running: `npm init -y` ### 1.2 Install necessary dependencies To install the necessary dependencies for your project, run the following command in the terminal: `npm install express knex sqlite3 dotenv pg nodemon helmet morgan` This will install the following packages: - express: A popular web framework for Node.js that simplifies the process of building web applications. - knex: A SQL query builder for Node.js that provides a convenient way to interact with databases. - sqlite3: A Node.js module that provides an SQLite database driver for use with Knex. - dotenv: A zero-dependency module that loads environment variables from a .env file into process.env. - pg: A PostgreSQL database driver for use with Knex, which enables you to connect and interact with PostgreSQL databases from your Node.js application. - nodemon: A utility that monitors changes to your source code and automatically restarts your server, saving you from manually stopping and starting your server every time you make changes. - helmet: A middleware that helps secure your Express app by setting various HTTP headers. - morgan: A middleware that logs HTTP requests and responses. You can install additional packages as needed for your project. Once the dependencies are installed, you can begin setting up your Node.js app with Express and Knex. ## Step 2: Setting up your Express server ### 2.1 Create an app.js file To create the basic Express server, follow these steps: Create a new file called app.js in the root directory of your project by running the following command in the terminal: `touch app.js` Open the app.js file in your preferred code editor. ### 2.2 Import necessary modules and middleware To use Express, Knex, Dotenv, pg, helmet, and morgan in your app.js file, you need to import them at the top of the file: ``` const express = require('express'); const knex = require('knex'); const dotenv = require('dotenv'); const pg = require('pg'); const helmet = require('helmet'); const morgan = require('morgan'); require('dotenv').config(); ``` ### 2.3 Set up the server To set up the server, you need to define the necessary routes and middleware, and configure any necessary settings. Here's an example: ``` const app = express(); const port = process.env.PORT || 5500; // Middleware app.use(express.json()); app.use(express.urlencoded({ extended: false })); app.use(helmet()); app.use(morgan('common')); // Routes app.get('/', (req, res) => { res.send('Hello, world!'); }); // Listen app.listen(port, () => { console.log(`Server running on port ${port}`); }); module.exports = app; ``` In this example, we're creating a new instance of the Express application (app) and setting the port to listen on. We're also setting up some basic middleware to parse incoming requests (using the express.json() and express.urlencoded() middleware), as well as the helmet() and morgan() middleware for security and logging purposes. We're also defining a simple route that sends a "Hello, world!" message as the response. Finally, we're starting the server by calling the listen() method on the app instance. You can now run `node app.js` in your termnial and start up the server! You should now see your .listen() message in the terminal `Server running on port 5500` if there are no errors. Now you can go into Insomnia or Postman and make a get request to `http://localhost:5500` and you should see your welcome message! ## Step 3: Setting up database config with settings for a local SQLite db and a production Postgres db ### 3.1 Create a knexfile.js file To use Knex to manage your database, you need to create a knexfile.js file in the root directory of your project. This file will contain the configuration settings for your database, including the connection settings for your local SQLite database and your production Postgres database. Here's an example knexfile.js: ``` module.exports = { development: { client: "sqlite3", connection: { filename: "./db/dev.sqlite3", }, useNullAsDefault: true, migrations: { directory: "./db/migrations", }, seeds: { directory: "./db/seeds", }, }, production: { client: "pg", connection: process.env.DATABASE_URL, migrations: { directory: "./db/migrations", }, seeds: { directory: "./db/seeds", }, }, }; ``` In this example, we're defining two environments: development and production. For the development environment, we're using SQLite as the database client and specifying a connection to a local file (./dev.sqlite3). We're also specifying the directories for our migrations and seeds. For the production environment, we're using Postgres as the database client and specifying a connection to a URL stored in the process.env.DATABASE_URL environment variable. We're using the same directories for our migrations and seeds. ### 3.2 Create a database directory and config To use the settings from your knexfile.js file in your Express server, you need to create a new directory called `db` (the directory our knexfile is referencing) and inside of db add a file called `dbConfig.js` to create a database instance. Here's an example: ``` const knex = require('knex'); const config = require('../knexfile'); const env = process.env.NODE_ENV || 'development'; const db = knex(config[env]); module.exports = db; ``` In this example, we're importing the knex library and the knexfile.js configuration settings. We're then setting the environment to use based on the NODE_ENV environment variable, defaulting to 'development' if the variable is not set. Finally, we're creating a new instance of the database using the configuration settings for the current environment and exporting it for use in our Express server. You can customize this example to fit your specific needs by updating the configuration settings in your knexfile.js file, or using a different method to set the environment (such as using process.env.DB_ENV). ## Step 4: Setting up a user model and migration ### 4.1 Create a new migration To set up a user model and database table, you will need to create a new migration file. Migrations are scripts that describe how to modify the database schema. To create a new migration file, run the following command in your terminal: `npx knex migrate:make create_users_table` This will generate a new migration file inside the directory specified in the knexfile.js for migrations (e.g. /db/migrations in the example). ### 4.2 Define the user table schema Open the newly created migration file and add the schema for the user table. Here is an example: ``` exports.up = function (knex) { return knex.schema.createTable("users", function (table) { // Creates an auto-incrementing PK column called id table.increments("id").primary(); // Creates a text column called username which is both required and unique table.string("username").notNullable().unique(); // Creates a text column called password which is required table.string("password").notNullable(); // Creates a timestamp column called created_at which is both required and defaults to the current time table.timestamps(true, true); }); }; exports.down = function (knex) { // Drops the entire table if it exists (opposite of createTable) // This is useful for rolling back migrations if something goes wrong return knex.schema.dropTableIfExists("users"); }; ``` In this example, we are creating a users table with id, name, email, and password columns. The id column is a primary key, which will automatically generate a unique ID for each row added to the table. The email column is set to be unique, which means that it will be enforced as a unique constraint in the database. The timestamps method is used to automatically create created_at and updated_at columns for the table. The down method describes how to undo the changes made by the up method. ### 4.3 Seed the database To seed the database with initial data, you need to create seed files that contain the data you want to insert into your tables. Seed files should be named with a descriptive name and should be placed in the directory specified in your knexfile.js. To create a new seed file, run the following command in your terminal: `npx knex seed:make 01_users` This will create a new seed file named 01_users.js in the seeds directory of your project. You can then edit this file to add the data you want to insert. In your seed files, you can use Knex to insert data into your tables. Here's an example: ``` exports.seed = function(knex) { // Deletes ALL existing entries return knex('users').del() .then(function () { // Inserts seed entries return knex('users').insert([ { username: 'user1', password: 'password1' }, { username: 'user2', password: 'password2' }, { username: 'user3', password: 'password3' } ]); }); }; ``` In this example, we're deleting all existing entries in the users table and then inserting new entries. You can modify this code to match the data you want to insert into your table. ### 4.4 Run the migration To apply the migration and create the users table in your database, run the following command in your terminal: `npx knex migrate:latest` This will execute all pending migrations and update your database schema. ### 4.5 Run the seeds Now that the user table is created in our local database we can test it by running our seeds and attempting to save our dummy user objects into our database To run your seed files run the following command in your terminal: `npx knex seed:run` Great now we have a local database, we have a schema for our users table, and a seed file with dummy data to save to our db and test our user schema! ## Step 5: Creating and testing a User model ### 5.1 Create a User model Now that the users table has been created in the database, you can create a User model to interact with it. These will be the methods that our endpoints call to make changes or get data from our database. Create a new `models` directory in our `db/` directory and add a file called `User.js` in the models directory and add the following code: ``` // require the database configuration module const db = require("../dbConfig"); module.exports = { // a function to find a user by id findById: (id) => { // query the 'users' table for the user with the given id return db("users").where({ id }).first(); }, // a function to create a new user create: (user) => { // insert the user object into the 'users' table and return the inserted user object return db("users").insert(user).returning("*"); }, // a function to update an existing user with the given id update: (id, user) => { // update the user object in the 'users' table where the id matches and return the updated user object return db("users").where({ id }).update(user).returning("*"); }, // a function to delete an existing user with the given id delete: (id) => { // delete the user from the 'users' table where the id matches return db("users").where({ id }).del(); }, }; ``` This model has four methods: - findById: finds a user by their ID - create: creates a new user in the database - update: updates an existing user in the database - delete: deletes a user from the database Each method returns a Knex query object. ## 5.2 Add routes to interact with the User model To test the User model, you need to add some routes to your Express app that interact with the User model. - Create a `routers` directory at the root of your repository. - Create a new file called `userRouter.js` in the routers directory with the following code: ``` const User = require("../db/models/User"); const router = require("express").Router(); // This route is for creating a new user. router.post("/", async (req, res) => { // Extracts the name, email, and password from the request body. const { username, password } = req.body; // Calls the User.create function and passes in the extracted values to create a new user. const user = await User.create({ username, password }); // Sends the created user as a JSON response. res.json(user); }); // This route is for getting a user by ID. router.get("/:id", async (req, res) => { // Extracts the ID parameter from the request. const { id } = req.params; // Calls the User.findById function and passes in the ID to retrieve the user with that ID. const user = await User.findById(id); // Sends the retrieved user as a JSON response. res.json(user); }); // This route is for updating a user by ID. router.put("/:id", async (req, res) => { // Extracts the ID parameter from the request. const { id } = req.params; // Extracts the updated username, and password from the request body. const { username, password } = req.body; // Calls the User.update function and passes in the ID and updated values to update the user with that ID. const user = await User.update(id, { username, password }); // Sends the updated user as a JSON response. res.json(user); }); // This route is for deleting a user by ID. router.delete("/:id", async (req, res) => { // Extracts the ID parameter from the request. const { id } = req.params; // Calls the User.delete function and passes in the ID to delete the user with that ID. const user = await User.delete(id); // Sends the deleted user as a JSON response. res.json(user); }); module.exports = router; ``` Now back in app.js, import the userRouter module and add a new /users route Your updated app.js should look like this: ``` const express = require("express"); const knex = require("knex"); const dotenv = require("dotenv"); const pg = require("pg"); const helmet = require("helmet"); const morgan = require("morgan"); const userRouter = require("./routers/userRouter"); require("dotenv").config(); const app = express(); const port = process.env.PORT || 5500; // Middleware app.use(express.json()); app.use(express.urlencoded({ extended: false })); app.use(helmet()); app.use(morgan("common")); // Routes app.get("/", (req, res) => { res.send("Hello, world!"); }); // Points to the userRouter and adds the /users prefix to all routes in the userRouter. app.use("/users", userRouter); // Listen app.listen(port, () => { console.log(`Server running on port ${port}`); }); module.exports = app; ``` You can now test these routes using a tool like Insomnia or Postman. ## Step 6: Deploying to Heroku ### 6.1 Create a new Heroku app To deploy your Node.js app to Heroku, you need to create a new Heroku app. Follow these steps to create a new Heroku app: - Log in to your Heroku account and navigate to the Heroku Dashboard. - Click the "New" button in the top right corner and select "Create new app" from the dropdown menu. - Enter a unique name for your app and select a region. - Click the "Create app" button. ### 6.2 Connect your Heroku app to your GitHub repository To connect your Heroku app to your GitHub repository, follow these steps: - In the "Deploy" tab of your Heroku app dashboard, select "GitHub" as the deployment method. - Connect your Heroku account to your GitHub account by clicking the "Connect to GitHub" button and following the prompts. - Select the GitHub repository that contains your Node.js app. - Choose the branch you want to deploy. - Click the "Enable Automatic Deploys" button. ### 6.3 Set up environment variables on Heroku To set up environment variables on Heroku, follow these steps: - In the "Settings" tab of your Heroku app dashboard, click the "Reveal Config Vars" button. - Enter the name and value for each environment variable you want to set. - Click the "Add" button for each environment variable. In this example, you would need to set the following environment variables: DATABASE_URL: The connection URL for your production Postgres database. You can find this in the Heroku Postgres add-on settings. NODE_ENV: The environment setting for your app. Set this to "production". ### 6.4 Deploy your app to Heroku To deploy your app to Heroku, follow these steps: - In the "Deploy" tab of your Heroku app dashboard, click the "Deploy Branch" button to deploy your app to Heroku. - Wait for the deployment process to complete. - Once the deployment is complete, click the "View" button to open your app in a new browser window. That's it! Your Node.js app should now be deployed and running on Heroku. If you run into any issues, you can view the logs in the "More" tab of your Heroku app dashboard to help diagnose the problem.
@ f33c8a96:5ec6f741
2024-11-15 18:39:13# node-backend-walkthrough  A step-by-step walkthrough on how to setup and deploy a nodejs backend built with Express / Knex / SQLite (dev db) / Postgres (production db) ## Step 1: Setting up your project / dependencies ### 1.1 Create a new Node.js project To set up a new Node.js project, follow these steps: - Create a new directory for your project by running the following command in the terminal: `mkdir my-project` - Navigate into the new directory by running: `cd my-project` - Initialize a new Node.js project by running: `npm init -y` ### 1.2 Install necessary dependencies To install the necessary dependencies for your project, run the following command in the terminal: `npm install express knex sqlite3 dotenv pg nodemon helmet morgan` This will install the following packages: - express: A popular web framework for Node.js that simplifies the process of building web applications. - knex: A SQL query builder for Node.js that provides a convenient way to interact with databases. - sqlite3: A Node.js module that provides an SQLite database driver for use with Knex. - dotenv: A zero-dependency module that loads environment variables from a .env file into process.env. - pg: A PostgreSQL database driver for use with Knex, which enables you to connect and interact with PostgreSQL databases from your Node.js application. - nodemon: A utility that monitors changes to your source code and automatically restarts your server, saving you from manually stopping and starting your server every time you make changes. - helmet: A middleware that helps secure your Express app by setting various HTTP headers. - morgan: A middleware that logs HTTP requests and responses. You can install additional packages as needed for your project. Once the dependencies are installed, you can begin setting up your Node.js app with Express and Knex. ## Step 2: Setting up your Express server ### 2.1 Create an app.js file To create the basic Express server, follow these steps: Create a new file called app.js in the root directory of your project by running the following command in the terminal: `touch app.js` Open the app.js file in your preferred code editor. ### 2.2 Import necessary modules and middleware To use Express, Knex, Dotenv, pg, helmet, and morgan in your app.js file, you need to import them at the top of the file: ``` const express = require('express'); const knex = require('knex'); const dotenv = require('dotenv'); const pg = require('pg'); const helmet = require('helmet'); const morgan = require('morgan'); require('dotenv').config(); ``` ### 2.3 Set up the server To set up the server, you need to define the necessary routes and middleware, and configure any necessary settings. Here's an example: ``` const app = express(); const port = process.env.PORT || 5500; // Middleware app.use(express.json()); app.use(express.urlencoded({ extended: false })); app.use(helmet()); app.use(morgan('common')); // Routes app.get('/', (req, res) => { res.send('Hello, world!'); }); // Listen app.listen(port, () => { console.log(`Server running on port ${port}`); }); module.exports = app; ``` In this example, we're creating a new instance of the Express application (app) and setting the port to listen on. We're also setting up some basic middleware to parse incoming requests (using the express.json() and express.urlencoded() middleware), as well as the helmet() and morgan() middleware for security and logging purposes. We're also defining a simple route that sends a "Hello, world!" message as the response. Finally, we're starting the server by calling the listen() method on the app instance. You can now run `node app.js` in your termnial and start up the server! You should now see your .listen() message in the terminal `Server running on port 5500` if there are no errors. Now you can go into Insomnia or Postman and make a get request to `http://localhost:5500` and you should see your welcome message! ## Step 3: Setting up database config with settings for a local SQLite db and a production Postgres db ### 3.1 Create a knexfile.js file To use Knex to manage your database, you need to create a knexfile.js file in the root directory of your project. This file will contain the configuration settings for your database, including the connection settings for your local SQLite database and your production Postgres database. Here's an example knexfile.js: ``` module.exports = { development: { client: "sqlite3", connection: { filename: "./db/dev.sqlite3", }, useNullAsDefault: true, migrations: { directory: "./db/migrations", }, seeds: { directory: "./db/seeds", }, }, production: { client: "pg", connection: process.env.DATABASE_URL, migrations: { directory: "./db/migrations", }, seeds: { directory: "./db/seeds", }, }, }; ``` In this example, we're defining two environments: development and production. For the development environment, we're using SQLite as the database client and specifying a connection to a local file (./dev.sqlite3). We're also specifying the directories for our migrations and seeds. For the production environment, we're using Postgres as the database client and specifying a connection to a URL stored in the process.env.DATABASE_URL environment variable. We're using the same directories for our migrations and seeds. ### 3.2 Create a database directory and config To use the settings from your knexfile.js file in your Express server, you need to create a new directory called `db` (the directory our knexfile is referencing) and inside of db add a file called `dbConfig.js` to create a database instance. Here's an example: ``` const knex = require('knex'); const config = require('../knexfile'); const env = process.env.NODE_ENV || 'development'; const db = knex(config[env]); module.exports = db; ``` In this example, we're importing the knex library and the knexfile.js configuration settings. We're then setting the environment to use based on the NODE_ENV environment variable, defaulting to 'development' if the variable is not set. Finally, we're creating a new instance of the database using the configuration settings for the current environment and exporting it for use in our Express server. You can customize this example to fit your specific needs by updating the configuration settings in your knexfile.js file, or using a different method to set the environment (such as using process.env.DB_ENV). ## Step 4: Setting up a user model and migration ### 4.1 Create a new migration To set up a user model and database table, you will need to create a new migration file. Migrations are scripts that describe how to modify the database schema. To create a new migration file, run the following command in your terminal: `npx knex migrate:make create_users_table` This will generate a new migration file inside the directory specified in the knexfile.js for migrations (e.g. /db/migrations in the example). ### 4.2 Define the user table schema Open the newly created migration file and add the schema for the user table. Here is an example: ``` exports.up = function (knex) { return knex.schema.createTable("users", function (table) { // Creates an auto-incrementing PK column called id table.increments("id").primary(); // Creates a text column called username which is both required and unique table.string("username").notNullable().unique(); // Creates a text column called password which is required table.string("password").notNullable(); // Creates a timestamp column called created_at which is both required and defaults to the current time table.timestamps(true, true); }); }; exports.down = function (knex) { // Drops the entire table if it exists (opposite of createTable) // This is useful for rolling back migrations if something goes wrong return knex.schema.dropTableIfExists("users"); }; ``` In this example, we are creating a users table with id, name, email, and password columns. The id column is a primary key, which will automatically generate a unique ID for each row added to the table. The email column is set to be unique, which means that it will be enforced as a unique constraint in the database. The timestamps method is used to automatically create created_at and updated_at columns for the table. The down method describes how to undo the changes made by the up method. ### 4.3 Seed the database To seed the database with initial data, you need to create seed files that contain the data you want to insert into your tables. Seed files should be named with a descriptive name and should be placed in the directory specified in your knexfile.js. To create a new seed file, run the following command in your terminal: `npx knex seed:make 01_users` This will create a new seed file named 01_users.js in the seeds directory of your project. You can then edit this file to add the data you want to insert. In your seed files, you can use Knex to insert data into your tables. Here's an example: ``` exports.seed = function(knex) { // Deletes ALL existing entries return knex('users').del() .then(function () { // Inserts seed entries return knex('users').insert([ { username: 'user1', password: 'password1' }, { username: 'user2', password: 'password2' }, { username: 'user3', password: 'password3' } ]); }); }; ``` In this example, we're deleting all existing entries in the users table and then inserting new entries. You can modify this code to match the data you want to insert into your table. ### 4.4 Run the migration To apply the migration and create the users table in your database, run the following command in your terminal: `npx knex migrate:latest` This will execute all pending migrations and update your database schema. ### 4.5 Run the seeds Now that the user table is created in our local database we can test it by running our seeds and attempting to save our dummy user objects into our database To run your seed files run the following command in your terminal: `npx knex seed:run` Great now we have a local database, we have a schema for our users table, and a seed file with dummy data to save to our db and test our user schema! ## Step 5: Creating and testing a User model ### 5.1 Create a User model Now that the users table has been created in the database, you can create a User model to interact with it. These will be the methods that our endpoints call to make changes or get data from our database. Create a new `models` directory in our `db/` directory and add a file called `User.js` in the models directory and add the following code: ``` // require the database configuration module const db = require("../dbConfig"); module.exports = { // a function to find a user by id findById: (id) => { // query the 'users' table for the user with the given id return db("users").where({ id }).first(); }, // a function to create a new user create: (user) => { // insert the user object into the 'users' table and return the inserted user object return db("users").insert(user).returning("*"); }, // a function to update an existing user with the given id update: (id, user) => { // update the user object in the 'users' table where the id matches and return the updated user object return db("users").where({ id }).update(user).returning("*"); }, // a function to delete an existing user with the given id delete: (id) => { // delete the user from the 'users' table where the id matches return db("users").where({ id }).del(); }, }; ``` This model has four methods: - findById: finds a user by their ID - create: creates a new user in the database - update: updates an existing user in the database - delete: deletes a user from the database Each method returns a Knex query object. ## 5.2 Add routes to interact with the User model To test the User model, you need to add some routes to your Express app that interact with the User model. - Create a `routers` directory at the root of your repository. - Create a new file called `userRouter.js` in the routers directory with the following code: ``` const User = require("../db/models/User"); const router = require("express").Router(); // This route is for creating a new user. router.post("/", async (req, res) => { // Extracts the name, email, and password from the request body. const { username, password } = req.body; // Calls the User.create function and passes in the extracted values to create a new user. const user = await User.create({ username, password }); // Sends the created user as a JSON response. res.json(user); }); // This route is for getting a user by ID. router.get("/:id", async (req, res) => { // Extracts the ID parameter from the request. const { id } = req.params; // Calls the User.findById function and passes in the ID to retrieve the user with that ID. const user = await User.findById(id); // Sends the retrieved user as a JSON response. res.json(user); }); // This route is for updating a user by ID. router.put("/:id", async (req, res) => { // Extracts the ID parameter from the request. const { id } = req.params; // Extracts the updated username, and password from the request body. const { username, password } = req.body; // Calls the User.update function and passes in the ID and updated values to update the user with that ID. const user = await User.update(id, { username, password }); // Sends the updated user as a JSON response. res.json(user); }); // This route is for deleting a user by ID. router.delete("/:id", async (req, res) => { // Extracts the ID parameter from the request. const { id } = req.params; // Calls the User.delete function and passes in the ID to delete the user with that ID. const user = await User.delete(id); // Sends the deleted user as a JSON response. res.json(user); }); module.exports = router; ``` Now back in app.js, import the userRouter module and add a new /users route Your updated app.js should look like this: ``` const express = require("express"); const knex = require("knex"); const dotenv = require("dotenv"); const pg = require("pg"); const helmet = require("helmet"); const morgan = require("morgan"); const userRouter = require("./routers/userRouter"); require("dotenv").config(); const app = express(); const port = process.env.PORT || 5500; // Middleware app.use(express.json()); app.use(express.urlencoded({ extended: false })); app.use(helmet()); app.use(morgan("common")); // Routes app.get("/", (req, res) => { res.send("Hello, world!"); }); // Points to the userRouter and adds the /users prefix to all routes in the userRouter. app.use("/users", userRouter); // Listen app.listen(port, () => { console.log(`Server running on port ${port}`); }); module.exports = app; ``` You can now test these routes using a tool like Insomnia or Postman. ## Step 6: Deploying to Heroku ### 6.1 Create a new Heroku app To deploy your Node.js app to Heroku, you need to create a new Heroku app. Follow these steps to create a new Heroku app: - Log in to your Heroku account and navigate to the Heroku Dashboard. - Click the "New" button in the top right corner and select "Create new app" from the dropdown menu. - Enter a unique name for your app and select a region. - Click the "Create app" button. ### 6.2 Connect your Heroku app to your GitHub repository To connect your Heroku app to your GitHub repository, follow these steps: - In the "Deploy" tab of your Heroku app dashboard, select "GitHub" as the deployment method. - Connect your Heroku account to your GitHub account by clicking the "Connect to GitHub" button and following the prompts. - Select the GitHub repository that contains your Node.js app. - Choose the branch you want to deploy. - Click the "Enable Automatic Deploys" button. ### 6.3 Set up environment variables on Heroku To set up environment variables on Heroku, follow these steps: - In the "Settings" tab of your Heroku app dashboard, click the "Reveal Config Vars" button. - Enter the name and value for each environment variable you want to set. - Click the "Add" button for each environment variable. In this example, you would need to set the following environment variables: DATABASE_URL: The connection URL for your production Postgres database. You can find this in the Heroku Postgres add-on settings. NODE_ENV: The environment setting for your app. Set this to "production". ### 6.4 Deploy your app to Heroku To deploy your app to Heroku, follow these steps: - In the "Deploy" tab of your Heroku app dashboard, click the "Deploy Branch" button to deploy your app to Heroku. - Wait for the deployment process to complete. - Once the deployment is complete, click the "View" button to open your app in a new browser window. That's it! Your Node.js app should now be deployed and running on Heroku. If you run into any issues, you can view the logs in the "More" tab of your Heroku app dashboard to help diagnose the problem. @ f33c8a96:5ec6f741
2024-11-15 18:36:56# pleb-node-template A simple fullstack Lightning App template for learning / development with LND ## Features: - Vite frontend with simple darkmode styling / form management / data display. - LND-GRPC library reducing code and making LND methods easier to work with. - Express server with basic middleware setup / routes for lightning methods. - Prebuilt LND methods for creating/paying invoices, openeing/closing channels, and adding/removing peers. ## Local Setup (in regtest using Polar): 1. Make sure that you have [Docker Desktop](https://www.docker.com/products/docker-desktop/) and [Polar](https://lightningpolar.com) installed 2. Open Docker Desktop and wait for it to start <img width="912" alt="image" src="https://user-images.githubusercontent.com/53542748/234646702-30806d33-85e6-42d2-9409-71c42d00ef4d.png"> 3. Open Polar and create a new Lightning network <img width="832" alt="image" src="https://user-images.githubusercontent.com/53542748/234647029-0c79aabf-6448-49f9-821c-dc54a407b637.png"> 4. Create your network however you like, though for starting out it's best to have at least 2 LND nodes to talk to each other. <img width="1426" alt="image" src="https://user-images.githubusercontent.com/53542748/234647812-84a1472d-2464-4874-b8c7-d6151686ca6b.png"> 5. Start your network  6. Click on the Alice node, visit the connect tab on the right, and copy the 'GRPC Host' value  7. Add this as the value to LND_HOST in the .env.sample file <img width="481" alt="image" src="https://user-images.githubusercontent.com/53542748/235537038-3ba636a8-0931-4db9-91cf-9ad4001781e7.png"> 8. Go back to the Connect tab and copy the 'TLS Cert' and 'Admin Macaroon' File Paths and add them as the LND_CERT and LND_MACAROON in .env.sample  9. Rename the .env.sample to .env <img width="258" alt="image" src="https://user-images.githubusercontent.com/53542748/235537647-875db3c9-c604-464c-9b61-386d08846a9f.png"> 10. Open up the terminal and run `npm i` to install all of the packages and then run `npm run start' to start the server. <img width="521" alt="image" src="https://user-images.githubusercontent.com/53542748/235538036-0d361a53-c36e-44e0-847c-b439a73172b5.png"> 11. Open up a new terminal and run `cd frontend` to navigate to the frontend directory, run `npm i` to install all of the packages, now finally run `npm run dev` to start the frontend. <img width="657" alt="image" src="https://user-images.githubusercontent.com/53542748/235538322-99afd03b-bc71-4a82-a4ac-fa4753acb57d.png"> 12. Visit the Vite local host and you should see pleb-node running. Click 'Connect to your node' and you will see your pubkey and alias immediately populate. Click this button anytime you want to refresh. <img width="1289" alt="image" src="https://user-images.githubusercontent.com/53542748/235538753-bf63e4e7-de63-4a98-84a0-44fa7e921898.png"> Now in combination with Polar you can open/close channels, create/pay invoices, and add/remove peers. There is so much more you can do with LND then what is in pleb-node but this should be a great way for you to get started. Check out lnd.js to see all of the lnd methods being called in pleb-node
@ f33c8a96:5ec6f741
2024-11-15 18:36:56# pleb-node-template A simple fullstack Lightning App template for learning / development with LND ## Features: - Vite frontend with simple darkmode styling / form management / data display. - LND-GRPC library reducing code and making LND methods easier to work with. - Express server with basic middleware setup / routes for lightning methods. - Prebuilt LND methods for creating/paying invoices, openeing/closing channels, and adding/removing peers. ## Local Setup (in regtest using Polar): 1. Make sure that you have [Docker Desktop](https://www.docker.com/products/docker-desktop/) and [Polar](https://lightningpolar.com) installed 2. Open Docker Desktop and wait for it to start <img width="912" alt="image" src="https://user-images.githubusercontent.com/53542748/234646702-30806d33-85e6-42d2-9409-71c42d00ef4d.png"> 3. Open Polar and create a new Lightning network <img width="832" alt="image" src="https://user-images.githubusercontent.com/53542748/234647029-0c79aabf-6448-49f9-821c-dc54a407b637.png"> 4. Create your network however you like, though for starting out it's best to have at least 2 LND nodes to talk to each other. <img width="1426" alt="image" src="https://user-images.githubusercontent.com/53542748/234647812-84a1472d-2464-4874-b8c7-d6151686ca6b.png"> 5. Start your network  6. Click on the Alice node, visit the connect tab on the right, and copy the 'GRPC Host' value  7. Add this as the value to LND_HOST in the .env.sample file <img width="481" alt="image" src="https://user-images.githubusercontent.com/53542748/235537038-3ba636a8-0931-4db9-91cf-9ad4001781e7.png"> 8. Go back to the Connect tab and copy the 'TLS Cert' and 'Admin Macaroon' File Paths and add them as the LND_CERT and LND_MACAROON in .env.sample  9. Rename the .env.sample to .env <img width="258" alt="image" src="https://user-images.githubusercontent.com/53542748/235537647-875db3c9-c604-464c-9b61-386d08846a9f.png"> 10. Open up the terminal and run `npm i` to install all of the packages and then run `npm run start' to start the server. <img width="521" alt="image" src="https://user-images.githubusercontent.com/53542748/235538036-0d361a53-c36e-44e0-847c-b439a73172b5.png"> 11. Open up a new terminal and run `cd frontend` to navigate to the frontend directory, run `npm i` to install all of the packages, now finally run `npm run dev` to start the frontend. <img width="657" alt="image" src="https://user-images.githubusercontent.com/53542748/235538322-99afd03b-bc71-4a82-a4ac-fa4753acb57d.png"> 12. Visit the Vite local host and you should see pleb-node running. Click 'Connect to your node' and you will see your pubkey and alias immediately populate. Click this button anytime you want to refresh. <img width="1289" alt="image" src="https://user-images.githubusercontent.com/53542748/235538753-bf63e4e7-de63-4a98-84a0-44fa7e921898.png"> Now in combination with Polar you can open/close channels, create/pay invoices, and add/remove peers. There is so much more you can do with LND then what is in pleb-node but this should be a great way for you to get started. Check out lnd.js to see all of the lnd methods being called in pleb-node @ f33c8a96:5ec6f741
2024-11-15 18:33:35# Rustin Buster Cheatsheet ## Table of Contents 1. [Variable Declaration](#variable-declaration) 2. [Basic Data Types](#basic-data-types) 3. [Structs](#structs) 4. [Implementations (impls)](#implementations-impls) 5. [Enums](#enums) 6. [Pattern Matching](#pattern-matching) 7. [Vectors](#vectors) 8. [Ownership and Borrowing](#ownership-and-borrowing) 9. [Traits](#traits) 10. [Error Handling](#error-handling) 11. [Closures](#closures) 12. [Iterators](#iterators) 13. [Generics](#generics) 14. [Lifetimes](#lifetimes) 15. [Smart Pointers](#smart-pointers) 16. [Concurrency](#concurrency) 17. [Modules](#modules) ## Variable Declaration In Rust, variables are immutable by default, promoting safer and more predictable code. ```rust let x = 5; // Immutable variable let mut y = 10; // Mutable variable const MAX_POINTS: u32 = 100_000; // Constant ``` - `let` declares an immutable variable. - `let mut` declares a mutable variable that can be changed later. - `const` declares a constant, which must have a type annotation and be assigned a constant expression. ## Basic Data Types Rust has several basic data types to represent numbers, characters, and strings. ```rust let a: u32 = 42; // Unsigned 32-bit integer let b: i64 = -100; // Signed 64-bit integer let c: f32 = 3.14; // 32-bit floating-point number let d: bool = true; // Boolean let e: char = 'x'; // Character let f: &str = "Hello, World!"; // String slice let g: String = String::from("Hello, World!"); // Owned String ``` - `u32`: Unsigned 32-bit integer (0 to 4,294,967,295) - `i64`: Signed 64-bit integer (-9,223,372,036,854,775,808 to 9,223,372,036,854,775,807) - `f32`: 32-bit floating-point number - `bool`: Boolean (true or false) - `char`: Unicode scalar value - `&str`: String slice (borrowed string) - `String`: Owned string (can be modified) ## Structs Structs are custom data types that group related data together. ```rust struct Person { name: String, age: u32, } // Creating an instance of a struct let person = Person { name: String::from("Alice"), age: 30, }; // Accessing struct fields println!("Name: {}", person.name); // Name: Alice println!("Age: {}", person.age); // Age: 30 // Mutable struct instance let mut mutable_person = Person { name: String::from("Bob"), age: 25, }; mutable_person.age = 26; // Updating age field // Tuple Struct struct Point(i32, i32); let point = Point(10, 20); // Unit Struct (marker) struct Unit; let unit = Unit; ``` - Regular structs have named fields. - Tuple structs have unnamed fields, accessed by index. - Unit structs have no fields and are often used as markers. ## Implementations (impls) Implementations allow you to define methods and associated functions for structs. ```rust impl Person { // Associated function (constructor) fn new(name: &str, age: u32) -> Person { Person { name: String::from(name), age, } } // Method fn say_hello(&self) { println!("Hello, my name is {}", self.name); } // Mutable method fn have_birthday(&mut self) { self.age += 1; } } // Using the `new` constructor and methods let mut alice = Person::new("Alice", 30); alice.say_hello(); // Hello, my name is Alice alice.have_birthday(); println!("Alice's new age: {}", alice.age); // Alice's new age: 31 ``` - Associated functions (like `new`) are called on the struct itself. - Methods take `&self` or `&mut self` as the first parameter and are called on instances. ## Enums Enums allow you to define a type that can be one of several variants. ```rust enum Direction { North, South, East, West, } let direction = Direction::East; enum OptionalInt { Value(i32), Nothing, } let x = OptionalInt::Value(42); let y = OptionalInt::Nothing; ``` - Enums can have variants with no data, like `Direction`. - Enums can also have variants with associated data, like `OptionalInt`. ## Pattern Matching Pattern matching is a powerful feature in Rust for destructuring and matching against patterns. ```rust match direction { Direction::North => println!("Going North"), Direction::South => println!("Going South"), Direction::East => println!("Going East"), Direction::West => println!("Going West"), } match x { OptionalInt::Value(n) => println!("Value: {}", n), OptionalInt::Nothing => println!("Nothing"), } ``` - `match` expressions must be exhaustive, covering all possible cases. - Pattern matching can destructure enums, tuples, and structs. ## Vectors Vectors are dynamic arrays that can grow or shrink in size. ```rust let mut vec = Vec::new(); vec.push(1); vec.push(2); vec.push(3); let first = vec[0]; // 1 // Slices let slice = &vec[1..3]; // Creates a slice of the vector from index 1 to 2 println!("Slice: {:?}", slice); // Slice: [2, 3] // Iterating over vectors for x in &vec { println!("{}", x); } ``` - Vectors can store elements of the same type. - Slices are references to a contiguous sequence of elements in a collection. - Vectors can be iterated over using a `for` loop. ## Ownership and Borrowing Rust's ownership system is a key feature that ensures memory safety without a garbage collector. ```rust let s1 = String::from("hello"); let s2 = s1; // s1 is invalid after this line let s3 = s2.clone(); // Create a clone let s4 = String::from("world"); let s5 = &s4; // Borrowing reference println!("{}, {}", s5, s4); // world, world ``` - When a value is assigned to another variable, ownership is transferred (moved). - To create a deep copy, use the `clone()` method. - References allow you to refer to a value without taking ownership. ## Traits Traits define shared behavior across types. ```rust trait Summary { fn summarize(&self) -> String; } struct Article { headline: String, content: String, } impl Summary for Article { fn summarize(&self) -> String { format!("{} - {}", self.headline, self.content.split_whitespace().take(5).collect::<Vec<&str>>().join(" ")) } } let article = Article { headline: String::from("Rust Cheatsheet"), content: String::from("This is a cheatsheet for the Rust programming language."), }; println!("{}", article.summarize()); ``` - Traits are similar to interfaces in other languages. - Types can implement multiple traits. - Trait methods can have default implementations. ## Error Handling Rust uses the `Result` and `Option` types for error handling. ```rust // Using Result fn divide(x: f64, y: f64) -> Result<f64, String> { if y == 0.0 { Err(String::from("Division by zero")) } else { Ok(x / y) } } match divide(10.0, 2.0) { Ok(result) => println!("Result: {}", result), Err(e) => println!("Error: {}", e), } // Using Option fn find_user(id: u32) -> Option<String> { if id == 1 { Some(String::from("Alice")) } else { None } } match find_user(1) { Some(name) => println!("User found: {}", name), None => println!("User not found"), } ``` - `Result<T, E>` represents either success (`Ok(T)`) or failure (`Err(E)`). - `Option<T>` represents either some value (`Some(T)`) or no value (`None`). ## Closures Closures are anonymous functions that can capture their environment. ```rust let add_one = |x: i32| x + 1; println!("5 + 1 = {}", add_one(5)); ``` - Closures can be used as arguments to higher-order functions. - They can capture variables from their surrounding scope. ## Iterators Iterators allow you to process sequences of elements. ```rust let numbers = vec![1, 2, 3, 4, 5]; let doubled: Vec<i32> = numbers.iter().map(|&x| x * 2).collect(); println!("Doubled numbers: {:?}", doubled); ``` - Iterators are lazy and don't compute values until consumed. - Many methods like `map`, `filter`, and `fold` are available on iterators. ## Generics Generics allow you to write flexible, reusable code that works with multiple types. ```rust fn largest<T: PartialOrd>(list: &[T]) -> &T { let mut largest = &list[0]; for item in list.iter() { if item > largest { largest = item; } } largest } let numbers = vec![34, 50, 25, 100, 65]; println!("The largest number is {}", largest(&numbers)); ``` - `<T: PartialOrd>` specifies that the type `T` must implement the `PartialOrd` trait. - Generics can be used with functions, structs, and enums. ## Lifetimes Lifetimes ensure that references are valid for as long as they're used. ```rust fn longest<'a>(x: &'a str, y: &'a str) -> &'a str { if x.len() > y.len() { x } else { y } } let result; { let string1 = String::from("short"); let string2 = String::from("longer"); result = longest(string1.as_str(), string2.as_str()); } println!("The longest string is {}", result); ``` - Lifetimes are denoted with an apostrophe, like `'a`. - They ensure that references don't outlive the data they refer to. ## Smart Pointers Smart pointers are data structures that act like pointers but have additional metadata and capabilities. ```rust use std::rc::Rc; let s = Rc::new(String::from("Hello, Rust!")); let s1 = Rc::clone(&s); let s2 = Rc::clone(&s); println!("{} has {} strong references", s, Rc::strong_count(&s)); ``` - `Rc<T>` (Reference Counted) allows multiple ownership of the same data. - It keeps track of the number of references to a value. ## Concurrency Rust provides tools for safe and efficient concurrent programming. ```rust use std::thread; use std::time::Duration; let handle = thread::spawn(|| { for i in 1..10 { println!("hi number {} from the spawned thread!", i); thread::sleep(Duration::from_millis(1)); } }); handle.join().unwrap(); ``` - `thread::spawn` creates a new thread. - `handle.join()` waits for the spawned thread to finish. ## Modules Modules help organize and encapsulate code. ```rust mod math { pub fn add(a: i32, b: i32) -> i32 { a + b } } use math::add; println!("5 + 3 = {}", add(5, 3)); ``` - `mod` defines a module. - `pub` makes items public and accessible outside the module. - `use` brings items into scope. This cheatsheet covers many of the fundamental concepts in Rust. Each section provides code examples and explanations to help you understand and use these features effectively in your Rust programs.
@ f33c8a96:5ec6f741
2024-11-15 18:33:35# Rustin Buster Cheatsheet ## Table of Contents 1. [Variable Declaration](#variable-declaration) 2. [Basic Data Types](#basic-data-types) 3. [Structs](#structs) 4. [Implementations (impls)](#implementations-impls) 5. [Enums](#enums) 6. [Pattern Matching](#pattern-matching) 7. [Vectors](#vectors) 8. [Ownership and Borrowing](#ownership-and-borrowing) 9. [Traits](#traits) 10. [Error Handling](#error-handling) 11. [Closures](#closures) 12. [Iterators](#iterators) 13. [Generics](#generics) 14. [Lifetimes](#lifetimes) 15. [Smart Pointers](#smart-pointers) 16. [Concurrency](#concurrency) 17. [Modules](#modules) ## Variable Declaration In Rust, variables are immutable by default, promoting safer and more predictable code. ```rust let x = 5; // Immutable variable let mut y = 10; // Mutable variable const MAX_POINTS: u32 = 100_000; // Constant ``` - `let` declares an immutable variable. - `let mut` declares a mutable variable that can be changed later. - `const` declares a constant, which must have a type annotation and be assigned a constant expression. ## Basic Data Types Rust has several basic data types to represent numbers, characters, and strings. ```rust let a: u32 = 42; // Unsigned 32-bit integer let b: i64 = -100; // Signed 64-bit integer let c: f32 = 3.14; // 32-bit floating-point number let d: bool = true; // Boolean let e: char = 'x'; // Character let f: &str = "Hello, World!"; // String slice let g: String = String::from("Hello, World!"); // Owned String ``` - `u32`: Unsigned 32-bit integer (0 to 4,294,967,295) - `i64`: Signed 64-bit integer (-9,223,372,036,854,775,808 to 9,223,372,036,854,775,807) - `f32`: 32-bit floating-point number - `bool`: Boolean (true or false) - `char`: Unicode scalar value - `&str`: String slice (borrowed string) - `String`: Owned string (can be modified) ## Structs Structs are custom data types that group related data together. ```rust struct Person { name: String, age: u32, } // Creating an instance of a struct let person = Person { name: String::from("Alice"), age: 30, }; // Accessing struct fields println!("Name: {}", person.name); // Name: Alice println!("Age: {}", person.age); // Age: 30 // Mutable struct instance let mut mutable_person = Person { name: String::from("Bob"), age: 25, }; mutable_person.age = 26; // Updating age field // Tuple Struct struct Point(i32, i32); let point = Point(10, 20); // Unit Struct (marker) struct Unit; let unit = Unit; ``` - Regular structs have named fields. - Tuple structs have unnamed fields, accessed by index. - Unit structs have no fields and are often used as markers. ## Implementations (impls) Implementations allow you to define methods and associated functions for structs. ```rust impl Person { // Associated function (constructor) fn new(name: &str, age: u32) -> Person { Person { name: String::from(name), age, } } // Method fn say_hello(&self) { println!("Hello, my name is {}", self.name); } // Mutable method fn have_birthday(&mut self) { self.age += 1; } } // Using the `new` constructor and methods let mut alice = Person::new("Alice", 30); alice.say_hello(); // Hello, my name is Alice alice.have_birthday(); println!("Alice's new age: {}", alice.age); // Alice's new age: 31 ``` - Associated functions (like `new`) are called on the struct itself. - Methods take `&self` or `&mut self` as the first parameter and are called on instances. ## Enums Enums allow you to define a type that can be one of several variants. ```rust enum Direction { North, South, East, West, } let direction = Direction::East; enum OptionalInt { Value(i32), Nothing, } let x = OptionalInt::Value(42); let y = OptionalInt::Nothing; ``` - Enums can have variants with no data, like `Direction`. - Enums can also have variants with associated data, like `OptionalInt`. ## Pattern Matching Pattern matching is a powerful feature in Rust for destructuring and matching against patterns. ```rust match direction { Direction::North => println!("Going North"), Direction::South => println!("Going South"), Direction::East => println!("Going East"), Direction::West => println!("Going West"), } match x { OptionalInt::Value(n) => println!("Value: {}", n), OptionalInt::Nothing => println!("Nothing"), } ``` - `match` expressions must be exhaustive, covering all possible cases. - Pattern matching can destructure enums, tuples, and structs. ## Vectors Vectors are dynamic arrays that can grow or shrink in size. ```rust let mut vec = Vec::new(); vec.push(1); vec.push(2); vec.push(3); let first = vec[0]; // 1 // Slices let slice = &vec[1..3]; // Creates a slice of the vector from index 1 to 2 println!("Slice: {:?}", slice); // Slice: [2, 3] // Iterating over vectors for x in &vec { println!("{}", x); } ``` - Vectors can store elements of the same type. - Slices are references to a contiguous sequence of elements in a collection. - Vectors can be iterated over using a `for` loop. ## Ownership and Borrowing Rust's ownership system is a key feature that ensures memory safety without a garbage collector. ```rust let s1 = String::from("hello"); let s2 = s1; // s1 is invalid after this line let s3 = s2.clone(); // Create a clone let s4 = String::from("world"); let s5 = &s4; // Borrowing reference println!("{}, {}", s5, s4); // world, world ``` - When a value is assigned to another variable, ownership is transferred (moved). - To create a deep copy, use the `clone()` method. - References allow you to refer to a value without taking ownership. ## Traits Traits define shared behavior across types. ```rust trait Summary { fn summarize(&self) -> String; } struct Article { headline: String, content: String, } impl Summary for Article { fn summarize(&self) -> String { format!("{} - {}", self.headline, self.content.split_whitespace().take(5).collect::<Vec<&str>>().join(" ")) } } let article = Article { headline: String::from("Rust Cheatsheet"), content: String::from("This is a cheatsheet for the Rust programming language."), }; println!("{}", article.summarize()); ``` - Traits are similar to interfaces in other languages. - Types can implement multiple traits. - Trait methods can have default implementations. ## Error Handling Rust uses the `Result` and `Option` types for error handling. ```rust // Using Result fn divide(x: f64, y: f64) -> Result<f64, String> { if y == 0.0 { Err(String::from("Division by zero")) } else { Ok(x / y) } } match divide(10.0, 2.0) { Ok(result) => println!("Result: {}", result), Err(e) => println!("Error: {}", e), } // Using Option fn find_user(id: u32) -> Option<String> { if id == 1 { Some(String::from("Alice")) } else { None } } match find_user(1) { Some(name) => println!("User found: {}", name), None => println!("User not found"), } ``` - `Result<T, E>` represents either success (`Ok(T)`) or failure (`Err(E)`). - `Option<T>` represents either some value (`Some(T)`) or no value (`None`). ## Closures Closures are anonymous functions that can capture their environment. ```rust let add_one = |x: i32| x + 1; println!("5 + 1 = {}", add_one(5)); ``` - Closures can be used as arguments to higher-order functions. - They can capture variables from their surrounding scope. ## Iterators Iterators allow you to process sequences of elements. ```rust let numbers = vec![1, 2, 3, 4, 5]; let doubled: Vec<i32> = numbers.iter().map(|&x| x * 2).collect(); println!("Doubled numbers: {:?}", doubled); ``` - Iterators are lazy and don't compute values until consumed. - Many methods like `map`, `filter`, and `fold` are available on iterators. ## Generics Generics allow you to write flexible, reusable code that works with multiple types. ```rust fn largest<T: PartialOrd>(list: &[T]) -> &T { let mut largest = &list[0]; for item in list.iter() { if item > largest { largest = item; } } largest } let numbers = vec![34, 50, 25, 100, 65]; println!("The largest number is {}", largest(&numbers)); ``` - `<T: PartialOrd>` specifies that the type `T` must implement the `PartialOrd` trait. - Generics can be used with functions, structs, and enums. ## Lifetimes Lifetimes ensure that references are valid for as long as they're used. ```rust fn longest<'a>(x: &'a str, y: &'a str) -> &'a str { if x.len() > y.len() { x } else { y } } let result; { let string1 = String::from("short"); let string2 = String::from("longer"); result = longest(string1.as_str(), string2.as_str()); } println!("The longest string is {}", result); ``` - Lifetimes are denoted with an apostrophe, like `'a`. - They ensure that references don't outlive the data they refer to. ## Smart Pointers Smart pointers are data structures that act like pointers but have additional metadata and capabilities. ```rust use std::rc::Rc; let s = Rc::new(String::from("Hello, Rust!")); let s1 = Rc::clone(&s); let s2 = Rc::clone(&s); println!("{} has {} strong references", s, Rc::strong_count(&s)); ``` - `Rc<T>` (Reference Counted) allows multiple ownership of the same data. - It keeps track of the number of references to a value. ## Concurrency Rust provides tools for safe and efficient concurrent programming. ```rust use std::thread; use std::time::Duration; let handle = thread::spawn(|| { for i in 1..10 { println!("hi number {} from the spawned thread!", i); thread::sleep(Duration::from_millis(1)); } }); handle.join().unwrap(); ``` - `thread::spawn` creates a new thread. - `handle.join()` waits for the spawned thread to finish. ## Modules Modules help organize and encapsulate code. ```rust mod math { pub fn add(a: i32, b: i32) -> i32 { a + b } } use math::add; println!("5 + 3 = {}", add(5, 3)); ``` - `mod` defines a module. - `pub` makes items public and accessible outside the module. - `use` brings items into scope. This cheatsheet covers many of the fundamental concepts in Rust. Each section provides code examples and explanations to help you understand and use these features effectively in your Rust programs. @ f33c8a96:5ec6f741
2024-11-15 18:31:02# JavaScript Cheatsheet for Beginners ## Table of Contents 1. [Variable Declaration](#variable-declaration) 2. [Basic Data Types](#basic-data-types) 3. [Operators](#operators) 4. [Objects](#objects) 5. [Functions](#functions) 6. [Arrays](#arrays) 7. [Conditional Statements](#conditional-statements) 8. [Loops](#loops) 9. [Error Handling](#error-handling) 10. [ES6+ Features](#es6-features) 11. [DOM Manipulation](#dom-manipulation) 12. [Event Handling](#event-handling) 13. [Asynchronous JavaScript](#asynchronous-javascript) 14. [Modules](#modules) ## Variable Declaration In JavaScript, variables can be declared using `var`, `let`, or `const`. ```javascript var x = 5; // Function-scoped variable (avoid using in modern JavaScript) let y = 10; // Block-scoped variable const MAX_POINTS = 100; // Constant (cannot be reassigned) ``` - `var` is function-scoped and hoisted (avoid using in modern JavaScript). - `let` is block-scoped and can be reassigned. - `const` is block-scoped and cannot be reassigned (but object properties can be modified). ## Basic Data Types JavaScript has several basic data types. ```javascript let num = 42; // Number let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats) let str = "Hello, World!"; // String let bool = true; // Boolean let nullValue = null; // Null let undefinedValue; // Undefined let symbol = Symbol("unique"); // Symbol (ES6+) let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+) ``` - `Number`: Represents both integers and floating-point numbers. - `String`: Represents textual data. - `Boolean`: Represents `true` or `false`. - `Null`: Represents a deliberate non-value. - `Undefined`: Represents a variable that has been declared but not assigned a value. - `Symbol`: Represents a unique identifier. - `BigInt`: Represents integers larger than 2^53 - 1. ## Operators JavaScript includes various types of operators for different operations. ```javascript // Arithmetic Operators let sum = 5 + 3; // Addition: 8 let diff = 10 - 4; // Subtraction: 6 let product = 3 * 4; // Multiplication: 12 let quotient = 15 / 3;// Division: 5 let remainder = 17 % 5;// Modulus: 2 let power = 2 ** 3; // Exponentiation: 8 let increment = 5; increment++; // Increment: 6 let decrement = 5; decrement--; // Decrement: 4 // Assignment Operators let x = 10; // Basic assignment x += 5; // Addition assignment (x = x + 5) x -= 3; // Subtraction assignment x *= 2; // Multiplication assignment x /= 4; // Division assignment x %= 3; // Modulus assignment x **= 2; // Exponentiation assignment // Comparison Operators console.log(5 == "5"); // Equal to (with type coercion): true console.log(5 === "5"); // Strictly equal to: false console.log(7 != "7"); // Not equal to: false console.log(7 !== "7"); // Strictly not equal to: true console.log(10 > 5); // Greater than: true console.log(10 >= 10); // Greater than or equal to: true console.log(5 < 10); // Less than: true console.log(5 <= 5); // Less than or equal to: true // Logical Operators let a = true, b = false; console.log(a && b); // Logical AND: false console.log(a || b); // Logical OR: true console.log(!a); // Logical NOT: false // Nullish Coalescing Operator (ES2020) let nullValue = null; let defaultValue = nullValue ?? "default"; // "default" // Optional Chaining Operator (ES2020) let user = { address: { street: "123 Main St" } }; console.log(user?.address?.street); // "123 Main St" console.log(user?.contact?.email); // undefined // Bitwise Operators console.log(5 & 3); // Bitwise AND: 1 console.log(5 | 3); // Bitwise OR: 7 console.log(5 ^ 3); // Bitwise XOR: 6 console.log(~5); // Bitwise NOT: -6 console.log(5 << 1); // Left shift: 10 console.log(5 >> 1); // Right shift: 2 console.log(5 >>> 1); // Unsigned right shift: 2 // String Operators let str1 = "Hello"; let str2 = "World"; console.log(str1 + " " + str2); // Concatenation: "Hello World" let greeting = "Hello"; greeting += " World"; // Concatenation assignment // Type Operators console.log(typeof "Hello"); // "string" console.log(typeof 123); // "number" console.log(typeof true); // "boolean" console.log(obj instanceof Object); // Check if object is instance of a class ``` Key points about operators: - Arithmetic operators perform mathematical operations - Assignment operators combine operation with assignment - Comparison operators return boolean values - Logical operators work with boolean values and provide short-circuit evaluation - Nullish coalescing (??) provides a way to specify a default value - Optional chaining (?.) safely accesses nested object properties - Bitwise operators perform operations on binary representations - String operators handle string concatenation - Type operators help determine variable types ## Objects Objects are collections of key-value pairs. ```javascript let person = { name: "Alice", age: 30, sayHello: function() { console.log("Hello, my name is " + this.name); } }; // Accessing object properties console.log(person.name); // Alice console.log(person["age"]); // 30 // Calling object methods person.sayHello(); // Hello, my name is Alice // Adding a new property person.job = "Developer"; // Object destructuring (ES6+) let { name, age } = person; console.log(name, age); // Alice 30 ``` - Objects can contain properties and methods. - Properties can be accessed using dot notation or bracket notation. - New properties can be added dynamically. - Object destructuring allows you to extract multiple properties at once. ## Functions Functions are reusable blocks of code. ```javascript // Function declaration function greet(name) { return "Hello, " + name + "!"; } // Function expression const multiply = function(a, b) { return a * b; }; // Arrow function (ES6+) const add = (a, b) => a + b; // Default parameters (ES6+) function power(base, exponent = 2) { return Math.pow(base, exponent); } console.log(greet("Alice")); // Hello, Alice! console.log(multiply(3, 4)); // 12 console.log(add(5, 3)); // 8 console.log(power(3)); // 9 console.log(power(2, 3)); // 8 ``` - Functions can be declared using the `function` keyword or as arrow functions. - Arrow functions provide a more concise syntax and lexically bind `this`. - Default parameters allow you to specify default values for function arguments. ## Arrays Arrays are ordered lists of values. ```javascript let fruits = ["apple", "banana", "orange"]; // Accessing array elements console.log(fruits[0]); // apple // Array methods fruits.push("grape"); // Add to the end fruits.unshift("mango"); // Add to the beginning let lastFruit = fruits.pop(); // Remove from the end let firstFruit = fruits.shift(); // Remove from the beginning // Iterating over arrays fruits.forEach(fruit => console.log(fruit)); // Array transformation let upperFruits = fruits.map(fruit => fruit.toUpperCase()); // Filtering arrays let longFruits = fruits.filter(fruit => fruit.length > 5); // Reducing arrays let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0); // Spread operator (ES6+) let moreFruits = ["kiwi", "pear"]; let allFruits = [...fruits, ...moreFruits]; ``` - Arrays can contain elements of any type. - Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array. - Higher-order functions like `map`, `filter`, and `reduce` create new arrays. - The spread operator `...` can be used to combine arrays. ## Conditional Statements Conditional statements allow you to execute code based on certain conditions. ```javascript let age = 18; // if...else statement if (age >= 18) { console.log("You are an adult"); } else { console.log("You are a minor"); } // Ternary operator let status = age >= 18 ? "adult" : "minor"; // switch statement switch (age) { case 13: console.log("You're a teenager"); break; case 18: console.log("You're now an adult"); break; default: console.log("You're neither 13 nor 18"); } ``` - `if...else` statements allow you to execute different code blocks based on conditions. - The ternary operator provides a concise way to write simple if-else statements. - `switch` statements are useful when you have multiple conditions to check against a single value. ## Loops Loops allow you to repeat code multiple times. ```javascript // for loop for (let i = 0; i < 5; i++) { console.log(i); } // while loop let count = 0; while (count < 5) { console.log(count); count++; } // do...while loop let x = 0; do { console.log(x); x++; } while (x < 5); // for...of loop (ES6+) let numbers = [1, 2, 3, 4, 5]; for (let num of numbers) { console.log(num); } // for...in loop (for object properties) let person = { name: "Alice", age: 30 }; for (let key in person) { console.log(key + ": " + person[key]); } ``` - `for` loops are commonly used when you know how many times you want to iterate. - `while` loops continue as long as a condition is true. - `do...while` loops always execute at least once before checking the condition. - `for...of` loops are used to iterate over iterable objects like arrays. - `for...in` loops are used to iterate over object properties. ## Error Handling Error handling allows you to gracefully handle and recover from errors. ```javascript try { // Code that might throw an error throw new Error("Something went wrong"); } catch (error) { console.error("Caught an error:", error.message); } finally { console.log("This always runs"); } // Custom error class CustomError extends Error { constructor(message) { super(message); this.name = "CustomError"; } } try { throw new CustomError("A custom error occurred"); } catch (error) { if (error instanceof CustomError) { console.log("Caught a custom error:", error.message); } else { console.log("Caught a different error:", error.message); } } ``` - The `try` block contains code that might throw an error. - The `catch` block handles any errors thrown in the `try` block. - The `finally` block always executes, regardless of whether an error was thrown. - You can create custom error types by extending the `Error` class. ## ES6+ Features ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript. ```javascript // Template literals let name = "Alice"; console.log(`Hello, ${name}!`); // Destructuring let [a, b] = [1, 2]; let { x, y } = { x: 3, y: 4 }; // Default parameters function greet(name = "Guest") { console.log(`Hello, ${name}!`); } // Rest parameters function sum(...numbers) { return numbers.reduce((total, num) => total + num, 0); } // Spread operator let arr1 = [1, 2, 3]; let arr2 = [...arr1, 4, 5]; // Arrow functions const square = x => x * x; // Classes class Animal { constructor(name) { this.name = name; } speak() { console.log(`${this.name} makes a sound.`); } } // Promises const fetchData = () => { return new Promise((resolve, reject) => { // Asynchronous operation setTimeout(() => resolve("Data fetched"), 1000); }); }; // Async/Await async function getData() { try { const data = await fetchData(); console.log(data); } catch (error) { console.error(error); } } ``` - Template literals allow for easy string interpolation. - Destructuring makes it easy to extract values from arrays or properties from objects. - Default parameters provide fallback values for function arguments. - Rest parameters allow functions to accept an indefinite number of arguments as an array. - The spread operator can be used to expand arrays or objects. - Arrow functions provide a concise syntax for writing function expressions. - Classes provide a cleaner syntax for creating objects and implementing inheritance. - Promises and async/await simplify asynchronous programming. ## DOM Manipulation DOM manipulation allows you to interact with HTML elements on a web page. ```javascript // Selecting elements const element = document.getElementById("myElement"); const elements = document.getElementsByClassName("myClass"); const queryElement = document.querySelector(".myClass"); const queryElements = document.querySelectorAll(".myClass"); // Modifying elements element.textContent = "New text content"; element.innerHTML = "<strong>New HTML content</strong>"; element.style.color = "red"; element.classList.add("newClass"); element.classList.remove("oldClass"); // Creating and appending elements const newElement = document.createElement("div"); newElement.textContent = "New element"; document.body.appendChild(newElement); // Removing elements element.parentNode.removeChild(element); // or element.remove(); // Modern browsers ``` - The DOM (Document Object Model) represents the structure of an HTML document. - You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`. - Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`. - New elements can be created with `createElement` and added to the DOM with `appendChild`. - Elements can be removed using `removeChild` or the `remove` method. ## Event Handling Event handling allows you to respond to user interactions and other events. ```javascript const button = document.querySelector("#myButton"); // Adding event listeners button.addEventListener("click", function(event) { console.log("Button clicked!"); console.log("Event object:", event); }); // Removing event listeners function handleClick(event) { console.log("Button clicked!"); } button.addEventListener("click", handleClick); button.removeEventListener("click", handleClick); // Event delegation document.body.addEventListener("click", function(event) { if (event.target.matches("#myButton")) { console.log("Button clicked using event delegation!"); } }); // Preventing default behavior const link = document.querySelector("a"); link.addEventListener("click", function(event) { event.preventDefault(); console.log("Link click prevented"); }); ``` - Event listeners can be added to elements using the `addEventListener` method. - The event object contains information about the event that occurred. - Event listeners can be removed using `removeEventListener`. - Event delegation allows you to handle events for multiple elements with a single listener. - `preventDefault` can be used to stop the default action of an event. ## Asynchronous JavaScript Asynchronous JavaScript allows you to perform operations without blocking the main thread. ```javascript // Callbacks function fetchData(callback) { setTimeout(() => { callback("Data fetched"); }, 1000); } fetchData(data => console.log(data)); // Promises function fetchDataPromise() { return new Promise((resolve, reject) => { setTimeout(() => { resolve("Data fetched"); }, 1000); }); } fetchDataPromise() .then(data => console.log(data)) .catch(error => console.error(error)); // Async/Await async function fetchDataAsync() { try { const data = await fetchDataPromise(); console.log(data); } catch (error) { console.error(error); } } fetchDataAsync(); // Fetch API fetch('https://api.example.com/data') .then(response => response.json()) .then(data => console.log(data)) .catch(error => console.error('Error:', error)); ``` - Callbacks are functions passed as arguments to be executed later. - Promises represent the eventual completion or failure of an asynchronous operation. - Async/await provides a more synchronous-looking way to write asynchronous code. - The Fetch API is a modern interface for making HTTP requests. ## Modules Modules allow you to organize your code into reusable pieces. ```javascript // math.js export function add(a, b) { return a + b; } export function multiply(a, b) { return a * b; } // main.js import { add, multiply } from './math.js'; console.log(add(5, 3)); // 8 console.log(multiply(4, 2)); // 8 // Default export // utils.js export default function sayHello(name) { console.log(`Hello, ${name}!`); } // main.js import sayHello from './utils.js'; sayHello("Alice"); // Hello, Alice! ``` - The `export` keyword is used to expose functions, objects, or primitives from a module. - The `import` keyword is used to bring functionality from other modules into the current module. - Default exports can be imported without curly braces and can be given any name when importing. This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs.
@ f33c8a96:5ec6f741
2024-11-15 18:31:02# JavaScript Cheatsheet for Beginners ## Table of Contents 1. [Variable Declaration](#variable-declaration) 2. [Basic Data Types](#basic-data-types) 3. [Operators](#operators) 4. [Objects](#objects) 5. [Functions](#functions) 6. [Arrays](#arrays) 7. [Conditional Statements](#conditional-statements) 8. [Loops](#loops) 9. [Error Handling](#error-handling) 10. [ES6+ Features](#es6-features) 11. [DOM Manipulation](#dom-manipulation) 12. [Event Handling](#event-handling) 13. [Asynchronous JavaScript](#asynchronous-javascript) 14. [Modules](#modules) ## Variable Declaration In JavaScript, variables can be declared using `var`, `let`, or `const`. ```javascript var x = 5; // Function-scoped variable (avoid using in modern JavaScript) let y = 10; // Block-scoped variable const MAX_POINTS = 100; // Constant (cannot be reassigned) ``` - `var` is function-scoped and hoisted (avoid using in modern JavaScript). - `let` is block-scoped and can be reassigned. - `const` is block-scoped and cannot be reassigned (but object properties can be modified). ## Basic Data Types JavaScript has several basic data types. ```javascript let num = 42; // Number let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats) let str = "Hello, World!"; // String let bool = true; // Boolean let nullValue = null; // Null let undefinedValue; // Undefined let symbol = Symbol("unique"); // Symbol (ES6+) let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+) ``` - `Number`: Represents both integers and floating-point numbers. - `String`: Represents textual data. - `Boolean`: Represents `true` or `false`. - `Null`: Represents a deliberate non-value. - `Undefined`: Represents a variable that has been declared but not assigned a value. - `Symbol`: Represents a unique identifier. - `BigInt`: Represents integers larger than 2^53 - 1. ## Operators JavaScript includes various types of operators for different operations. ```javascript // Arithmetic Operators let sum = 5 + 3; // Addition: 8 let diff = 10 - 4; // Subtraction: 6 let product = 3 * 4; // Multiplication: 12 let quotient = 15 / 3;// Division: 5 let remainder = 17 % 5;// Modulus: 2 let power = 2 ** 3; // Exponentiation: 8 let increment = 5; increment++; // Increment: 6 let decrement = 5; decrement--; // Decrement: 4 // Assignment Operators let x = 10; // Basic assignment x += 5; // Addition assignment (x = x + 5) x -= 3; // Subtraction assignment x *= 2; // Multiplication assignment x /= 4; // Division assignment x %= 3; // Modulus assignment x **= 2; // Exponentiation assignment // Comparison Operators console.log(5 == "5"); // Equal to (with type coercion): true console.log(5 === "5"); // Strictly equal to: false console.log(7 != "7"); // Not equal to: false console.log(7 !== "7"); // Strictly not equal to: true console.log(10 > 5); // Greater than: true console.log(10 >= 10); // Greater than or equal to: true console.log(5 < 10); // Less than: true console.log(5 <= 5); // Less than or equal to: true // Logical Operators let a = true, b = false; console.log(a && b); // Logical AND: false console.log(a || b); // Logical OR: true console.log(!a); // Logical NOT: false // Nullish Coalescing Operator (ES2020) let nullValue = null; let defaultValue = nullValue ?? "default"; // "default" // Optional Chaining Operator (ES2020) let user = { address: { street: "123 Main St" } }; console.log(user?.address?.street); // "123 Main St" console.log(user?.contact?.email); // undefined // Bitwise Operators console.log(5 & 3); // Bitwise AND: 1 console.log(5 | 3); // Bitwise OR: 7 console.log(5 ^ 3); // Bitwise XOR: 6 console.log(~5); // Bitwise NOT: -6 console.log(5 << 1); // Left shift: 10 console.log(5 >> 1); // Right shift: 2 console.log(5 >>> 1); // Unsigned right shift: 2 // String Operators let str1 = "Hello"; let str2 = "World"; console.log(str1 + " " + str2); // Concatenation: "Hello World" let greeting = "Hello"; greeting += " World"; // Concatenation assignment // Type Operators console.log(typeof "Hello"); // "string" console.log(typeof 123); // "number" console.log(typeof true); // "boolean" console.log(obj instanceof Object); // Check if object is instance of a class ``` Key points about operators: - Arithmetic operators perform mathematical operations - Assignment operators combine operation with assignment - Comparison operators return boolean values - Logical operators work with boolean values and provide short-circuit evaluation - Nullish coalescing (??) provides a way to specify a default value - Optional chaining (?.) safely accesses nested object properties - Bitwise operators perform operations on binary representations - String operators handle string concatenation - Type operators help determine variable types ## Objects Objects are collections of key-value pairs. ```javascript let person = { name: "Alice", age: 30, sayHello: function() { console.log("Hello, my name is " + this.name); } }; // Accessing object properties console.log(person.name); // Alice console.log(person["age"]); // 30 // Calling object methods person.sayHello(); // Hello, my name is Alice // Adding a new property person.job = "Developer"; // Object destructuring (ES6+) let { name, age } = person; console.log(name, age); // Alice 30 ``` - Objects can contain properties and methods. - Properties can be accessed using dot notation or bracket notation. - New properties can be added dynamically. - Object destructuring allows you to extract multiple properties at once. ## Functions Functions are reusable blocks of code. ```javascript // Function declaration function greet(name) { return "Hello, " + name + "!"; } // Function expression const multiply = function(a, b) { return a * b; }; // Arrow function (ES6+) const add = (a, b) => a + b; // Default parameters (ES6+) function power(base, exponent = 2) { return Math.pow(base, exponent); } console.log(greet("Alice")); // Hello, Alice! console.log(multiply(3, 4)); // 12 console.log(add(5, 3)); // 8 console.log(power(3)); // 9 console.log(power(2, 3)); // 8 ``` - Functions can be declared using the `function` keyword or as arrow functions. - Arrow functions provide a more concise syntax and lexically bind `this`. - Default parameters allow you to specify default values for function arguments. ## Arrays Arrays are ordered lists of values. ```javascript let fruits = ["apple", "banana", "orange"]; // Accessing array elements console.log(fruits[0]); // apple // Array methods fruits.push("grape"); // Add to the end fruits.unshift("mango"); // Add to the beginning let lastFruit = fruits.pop(); // Remove from the end let firstFruit = fruits.shift(); // Remove from the beginning // Iterating over arrays fruits.forEach(fruit => console.log(fruit)); // Array transformation let upperFruits = fruits.map(fruit => fruit.toUpperCase()); // Filtering arrays let longFruits = fruits.filter(fruit => fruit.length > 5); // Reducing arrays let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0); // Spread operator (ES6+) let moreFruits = ["kiwi", "pear"]; let allFruits = [...fruits, ...moreFruits]; ``` - Arrays can contain elements of any type. - Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array. - Higher-order functions like `map`, `filter`, and `reduce` create new arrays. - The spread operator `...` can be used to combine arrays. ## Conditional Statements Conditional statements allow you to execute code based on certain conditions. ```javascript let age = 18; // if...else statement if (age >= 18) { console.log("You are an adult"); } else { console.log("You are a minor"); } // Ternary operator let status = age >= 18 ? "adult" : "minor"; // switch statement switch (age) { case 13: console.log("You're a teenager"); break; case 18: console.log("You're now an adult"); break; default: console.log("You're neither 13 nor 18"); } ``` - `if...else` statements allow you to execute different code blocks based on conditions. - The ternary operator provides a concise way to write simple if-else statements. - `switch` statements are useful when you have multiple conditions to check against a single value. ## Loops Loops allow you to repeat code multiple times. ```javascript // for loop for (let i = 0; i < 5; i++) { console.log(i); } // while loop let count = 0; while (count < 5) { console.log(count); count++; } // do...while loop let x = 0; do { console.log(x); x++; } while (x < 5); // for...of loop (ES6+) let numbers = [1, 2, 3, 4, 5]; for (let num of numbers) { console.log(num); } // for...in loop (for object properties) let person = { name: "Alice", age: 30 }; for (let key in person) { console.log(key + ": " + person[key]); } ``` - `for` loops are commonly used when you know how many times you want to iterate. - `while` loops continue as long as a condition is true. - `do...while` loops always execute at least once before checking the condition. - `for...of` loops are used to iterate over iterable objects like arrays. - `for...in` loops are used to iterate over object properties. ## Error Handling Error handling allows you to gracefully handle and recover from errors. ```javascript try { // Code that might throw an error throw new Error("Something went wrong"); } catch (error) { console.error("Caught an error:", error.message); } finally { console.log("This always runs"); } // Custom error class CustomError extends Error { constructor(message) { super(message); this.name = "CustomError"; } } try { throw new CustomError("A custom error occurred"); } catch (error) { if (error instanceof CustomError) { console.log("Caught a custom error:", error.message); } else { console.log("Caught a different error:", error.message); } } ``` - The `try` block contains code that might throw an error. - The `catch` block handles any errors thrown in the `try` block. - The `finally` block always executes, regardless of whether an error was thrown. - You can create custom error types by extending the `Error` class. ## ES6+ Features ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript. ```javascript // Template literals let name = "Alice"; console.log(`Hello, ${name}!`); // Destructuring let [a, b] = [1, 2]; let { x, y } = { x: 3, y: 4 }; // Default parameters function greet(name = "Guest") { console.log(`Hello, ${name}!`); } // Rest parameters function sum(...numbers) { return numbers.reduce((total, num) => total + num, 0); } // Spread operator let arr1 = [1, 2, 3]; let arr2 = [...arr1, 4, 5]; // Arrow functions const square = x => x * x; // Classes class Animal { constructor(name) { this.name = name; } speak() { console.log(`${this.name} makes a sound.`); } } // Promises const fetchData = () => { return new Promise((resolve, reject) => { // Asynchronous operation setTimeout(() => resolve("Data fetched"), 1000); }); }; // Async/Await async function getData() { try { const data = await fetchData(); console.log(data); } catch (error) { console.error(error); } } ``` - Template literals allow for easy string interpolation. - Destructuring makes it easy to extract values from arrays or properties from objects. - Default parameters provide fallback values for function arguments. - Rest parameters allow functions to accept an indefinite number of arguments as an array. - The spread operator can be used to expand arrays or objects. - Arrow functions provide a concise syntax for writing function expressions. - Classes provide a cleaner syntax for creating objects and implementing inheritance. - Promises and async/await simplify asynchronous programming. ## DOM Manipulation DOM manipulation allows you to interact with HTML elements on a web page. ```javascript // Selecting elements const element = document.getElementById("myElement"); const elements = document.getElementsByClassName("myClass"); const queryElement = document.querySelector(".myClass"); const queryElements = document.querySelectorAll(".myClass"); // Modifying elements element.textContent = "New text content"; element.innerHTML = "<strong>New HTML content</strong>"; element.style.color = "red"; element.classList.add("newClass"); element.classList.remove("oldClass"); // Creating and appending elements const newElement = document.createElement("div"); newElement.textContent = "New element"; document.body.appendChild(newElement); // Removing elements element.parentNode.removeChild(element); // or element.remove(); // Modern browsers ``` - The DOM (Document Object Model) represents the structure of an HTML document. - You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`. - Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`. - New elements can be created with `createElement` and added to the DOM with `appendChild`. - Elements can be removed using `removeChild` or the `remove` method. ## Event Handling Event handling allows you to respond to user interactions and other events. ```javascript const button = document.querySelector("#myButton"); // Adding event listeners button.addEventListener("click", function(event) { console.log("Button clicked!"); console.log("Event object:", event); }); // Removing event listeners function handleClick(event) { console.log("Button clicked!"); } button.addEventListener("click", handleClick); button.removeEventListener("click", handleClick); // Event delegation document.body.addEventListener("click", function(event) { if (event.target.matches("#myButton")) { console.log("Button clicked using event delegation!"); } }); // Preventing default behavior const link = document.querySelector("a"); link.addEventListener("click", function(event) { event.preventDefault(); console.log("Link click prevented"); }); ``` - Event listeners can be added to elements using the `addEventListener` method. - The event object contains information about the event that occurred. - Event listeners can be removed using `removeEventListener`. - Event delegation allows you to handle events for multiple elements with a single listener. - `preventDefault` can be used to stop the default action of an event. ## Asynchronous JavaScript Asynchronous JavaScript allows you to perform operations without blocking the main thread. ```javascript // Callbacks function fetchData(callback) { setTimeout(() => { callback("Data fetched"); }, 1000); } fetchData(data => console.log(data)); // Promises function fetchDataPromise() { return new Promise((resolve, reject) => { setTimeout(() => { resolve("Data fetched"); }, 1000); }); } fetchDataPromise() .then(data => console.log(data)) .catch(error => console.error(error)); // Async/Await async function fetchDataAsync() { try { const data = await fetchDataPromise(); console.log(data); } catch (error) { console.error(error); } } fetchDataAsync(); // Fetch API fetch('https://api.example.com/data') .then(response => response.json()) .then(data => console.log(data)) .catch(error => console.error('Error:', error)); ``` - Callbacks are functions passed as arguments to be executed later. - Promises represent the eventual completion or failure of an asynchronous operation. - Async/await provides a more synchronous-looking way to write asynchronous code. - The Fetch API is a modern interface for making HTTP requests. ## Modules Modules allow you to organize your code into reusable pieces. ```javascript // math.js export function add(a, b) { return a + b; } export function multiply(a, b) { return a * b; } // main.js import { add, multiply } from './math.js'; console.log(add(5, 3)); // 8 console.log(multiply(4, 2)); // 8 // Default export // utils.js export default function sayHello(name) { console.log(`Hello, ${name}!`); } // main.js import sayHello from './utils.js'; sayHello("Alice"); // Hello, Alice! ``` - The `export` keyword is used to expose functions, objects, or primitives from a module. - The `import` keyword is used to bring functionality from other modules into the current module. - Default exports can be imported without curly braces and can be given any name when importing. This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs. @ f33c8a96:5ec6f741
2024-11-15 18:23:58<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/7dsR7um-DxA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2024-11-15 18:23:58<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/7dsR7um-DxA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ f33c8a96:5ec6f741
2024-11-15 18:21:00<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/QY6euaT_G_E?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2024-11-15 18:21:00<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/QY6euaT_G_E?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ f33c8a96:5ec6f741
2024-11-15 18:06:42<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/tGVxP4RgyI4?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2024-11-15 18:06:42<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/tGVxP4RgyI4?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 468f729d:5ab4fd5e
2024-11-15 17:52:45<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 468f729d:5ab4fd5e
2024-11-15 17:52:45<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 5d4b6c8d:8a1c1ee3
2024-11-15 15:07:59Heading into episode 6, here's a rough outline of what we're planning on talking about. ~Stacker_Sports contest updates: UEFA, Cricket, NFL, NBA Bitcoiner Athletes: two sports celebrities were in the bitcoin news recently Hockey: a hot start for a surprising team NFL - our head-to-head fantasy matchup (if @grayruby still wants to talk about it after his team's reprehensible outing), - which contenders are on the outside looking in, - Why are the Bears so bad at picking OC's? Tyson vs Paul NBA - By popular demand, KAT Corner makes a return - Thoughts and expectations for the Emirates CUp - Can the best player win MVP on a garbage team? - Our early hits and misses of the season Degenerate Corner: bets we're excited about, platforms we're excited about, ongoing bets we have with each other. originally posted at https://stacker.news/items/769019
@ 5d4b6c8d:8a1c1ee3
2024-11-15 15:07:59Heading into episode 6, here's a rough outline of what we're planning on talking about. ~Stacker_Sports contest updates: UEFA, Cricket, NFL, NBA Bitcoiner Athletes: two sports celebrities were in the bitcoin news recently Hockey: a hot start for a surprising team NFL - our head-to-head fantasy matchup (if @grayruby still wants to talk about it after his team's reprehensible outing), - which contenders are on the outside looking in, - Why are the Bears so bad at picking OC's? Tyson vs Paul NBA - By popular demand, KAT Corner makes a return - Thoughts and expectations for the Emirates CUp - Can the best player win MVP on a garbage team? - Our early hits and misses of the season Degenerate Corner: bets we're excited about, platforms we're excited about, ongoing bets we have with each other. originally posted at https://stacker.news/items/769019 @ 07907690:d4e015f6
2024-11-15 10:10:05PGP (Pretty Good Privacy) adalah protokol enkripsi yang digunakan untuk memastikan kerahasiaan, integritas, dan otentikasi data dalam komunikasi digital. Diciptakan oleh Phil Zimmermann pada tahun 1991, PGP menggunakan kombinasi teknik kriptografi asimetris (kunci publik dan kunci privat) serta simetris untuk melindungi informasi. Berikut adalah berbagai kegunaan PGP: ## Mengamankan Email (Enkripsi dan Dekripsi) - Kegunaan: Melindungi isi email agar hanya penerima yang memiliki kunci privat yang benar yang dapat membacanya. - Cara Kerja: - Pengirim mengenkripsi email menggunakan kunci publik penerima. - Hanya penerima yang memiliki kunci privat yang dapat mendekripsi dan membaca email tersebut. - Contoh: Jurnalis yang berkomunikasi dengan informan atau organisasi yang mengirim data sensitif dapat menggunakan PGP untuk melindungi komunikasi mereka dari penyusup. ## Tanda Tangan Digital (Digital Signature) - Kegunaan: Memastikan keaslian dan integritas pesan atau dokumen, memastikan bahwa pesan tidak diubah dan benar-benar berasal dari pengirim yang sah. - Cara Kerja: - Pengirim membuat tanda tangan digital menggunakan kunci privatnya. - Penerima dapat memverifikasi tanda tangan tersebut menggunakan kunci publik pengirim. - Contoh: Digunakan untuk memverifikasi keaslian dokumen hukum, email penting, atau perangkat lunak yang diunduh. ## Melindungi File dan Dokumen - Kegunaan: Mengenkripsi file sensitif agar hanya orang yang memiliki kunci dekripsi yang benar yang dapat membukanya. - Cara Kerja: File dienkripsi menggunakan kunci publik penerima, dan penerima menggunakan kunci privatnya untuk mendekripsinya. - Contoh: Perusahaan dapat menggunakan PGP untuk mengenkripsi laporan keuangan, data pelanggan, atau informasi penting lainnya sebelum membagikannya. ## Mengamankan Backup Data - Kegunaan: Mengenkripsi cadangan data penting untuk melindunginya dari akses yang tidak sah. - Cara Kerja: File backup dienkripsi dengan PGP sebelum disimpan, sehingga meskipun backup dicuri, data tetap aman. - Contoh: Organisasi menyimpan cadangan data klien di server eksternal yang dienkripsi dengan PGP untuk mencegah kebocoran data. ## Perlindungan Identitas dan Anonimitas - Kegunaan: Melindungi identitas pengirim dan penerima dalam komunikasi online. - Cara Kerja: Penggunaan enkripsi end-to-end menjamin bahwa hanya pihak yang berwenang yang dapat membaca pesan. - Contoh: Aktivis atau peneliti yang bekerja di negara dengan pengawasan ketat dapat menggunakan PGP untuk melindungi komunikasi mereka. ## Memverifikasi Integritas Perangkat Lunak - Kegunaan: Memastikan bahwa perangkat lunak atau paket yang diunduh berasal dari sumber yang terpercaya dan tidak dimodifikasi oleh pihak ketiga. - Cara Kerja: Pengembang menandatangani perangkat lunak menggunakan kunci privat mereka, dan pengguna dapat memverifikasi tanda tangan menggunakan kunci publik yang disediakan. - Contoh: Distribusi Linux atau aplikasi open-source sering kali menyertakan tanda tangan PGP untuk memverifikasi keasliannya. ## Komunikasi di Forum atau Jaringan Terdistribusi - Kegunaan: Memastikan privasi komunikasi di platform terdesentralisasi atau anonim. - Cara Kerja: Pesan dienkripsi sebelum dikirim dan hanya dapat didekripsi oleh penerima yang sah. - Contoh: Pengguna di forum yang membahas topik sensitif dapat menggunakan PGP untuk melindungi identitas mereka. --- ## Mengapa PGP Penting? - Keamanan yang Kuat: Kombinasi kriptografi asimetris dan simetris membuat PGP sangat sulit ditembus oleh peretas. -Privasi: Menjaga komunikasi Anda tetap aman dan pribadi dari penyadapan atau pengawasan. - Integritas: Memastikan bahwa pesan atau data yang dikirim tidak diubah selama transmisi. - Otentikasi: Membuktikan identitas pengirim melalui tanda tangan digital. --- ## Kelebihan PGP - Sangat Aman: Jika digunakan dengan benar, PGP menawarkan tingkat keamanan yang sangat tinggi. - Terbuka: Banyak digunakan di kalangan profesional dan komunitas open-source. - Fleksibel: Dapat digunakan untuk berbagai keperluan, mulai dari komunikasi email hingga penyimpanan data. ## Kekurangan PGP - Kompleks untuk Pemula: Relatif sulit digunakan oleh pengguna awam. - Pengelolaan Kunci yang Rumit: Memerlukan pengelolaan kunci publik/privat yang benar. - Tidak Ada Pemulihan Data: Jika kunci privat hilang, data yang dienkripsi tidak dapat dipulihkan. --- PGP adalah alat yang sangat berguna untuk memastikan keamanan dan privasi dalam komunikasi dan data. Dengan meningkatnya risiko kejahatan siber, penggunaan PGP menjadi semakin penting, terutama di sektor yang menangani data sensitif.
@ 07907690:d4e015f6
2024-11-15 10:10:05PGP (Pretty Good Privacy) adalah protokol enkripsi yang digunakan untuk memastikan kerahasiaan, integritas, dan otentikasi data dalam komunikasi digital. Diciptakan oleh Phil Zimmermann pada tahun 1991, PGP menggunakan kombinasi teknik kriptografi asimetris (kunci publik dan kunci privat) serta simetris untuk melindungi informasi. Berikut adalah berbagai kegunaan PGP: ## Mengamankan Email (Enkripsi dan Dekripsi) - Kegunaan: Melindungi isi email agar hanya penerima yang memiliki kunci privat yang benar yang dapat membacanya. - Cara Kerja: - Pengirim mengenkripsi email menggunakan kunci publik penerima. - Hanya penerima yang memiliki kunci privat yang dapat mendekripsi dan membaca email tersebut. - Contoh: Jurnalis yang berkomunikasi dengan informan atau organisasi yang mengirim data sensitif dapat menggunakan PGP untuk melindungi komunikasi mereka dari penyusup. ## Tanda Tangan Digital (Digital Signature) - Kegunaan: Memastikan keaslian dan integritas pesan atau dokumen, memastikan bahwa pesan tidak diubah dan benar-benar berasal dari pengirim yang sah. - Cara Kerja: - Pengirim membuat tanda tangan digital menggunakan kunci privatnya. - Penerima dapat memverifikasi tanda tangan tersebut menggunakan kunci publik pengirim. - Contoh: Digunakan untuk memverifikasi keaslian dokumen hukum, email penting, atau perangkat lunak yang diunduh. ## Melindungi File dan Dokumen - Kegunaan: Mengenkripsi file sensitif agar hanya orang yang memiliki kunci dekripsi yang benar yang dapat membukanya. - Cara Kerja: File dienkripsi menggunakan kunci publik penerima, dan penerima menggunakan kunci privatnya untuk mendekripsinya. - Contoh: Perusahaan dapat menggunakan PGP untuk mengenkripsi laporan keuangan, data pelanggan, atau informasi penting lainnya sebelum membagikannya. ## Mengamankan Backup Data - Kegunaan: Mengenkripsi cadangan data penting untuk melindunginya dari akses yang tidak sah. - Cara Kerja: File backup dienkripsi dengan PGP sebelum disimpan, sehingga meskipun backup dicuri, data tetap aman. - Contoh: Organisasi menyimpan cadangan data klien di server eksternal yang dienkripsi dengan PGP untuk mencegah kebocoran data. ## Perlindungan Identitas dan Anonimitas - Kegunaan: Melindungi identitas pengirim dan penerima dalam komunikasi online. - Cara Kerja: Penggunaan enkripsi end-to-end menjamin bahwa hanya pihak yang berwenang yang dapat membaca pesan. - Contoh: Aktivis atau peneliti yang bekerja di negara dengan pengawasan ketat dapat menggunakan PGP untuk melindungi komunikasi mereka. ## Memverifikasi Integritas Perangkat Lunak - Kegunaan: Memastikan bahwa perangkat lunak atau paket yang diunduh berasal dari sumber yang terpercaya dan tidak dimodifikasi oleh pihak ketiga. - Cara Kerja: Pengembang menandatangani perangkat lunak menggunakan kunci privat mereka, dan pengguna dapat memverifikasi tanda tangan menggunakan kunci publik yang disediakan. - Contoh: Distribusi Linux atau aplikasi open-source sering kali menyertakan tanda tangan PGP untuk memverifikasi keasliannya. ## Komunikasi di Forum atau Jaringan Terdistribusi - Kegunaan: Memastikan privasi komunikasi di platform terdesentralisasi atau anonim. - Cara Kerja: Pesan dienkripsi sebelum dikirim dan hanya dapat didekripsi oleh penerima yang sah. - Contoh: Pengguna di forum yang membahas topik sensitif dapat menggunakan PGP untuk melindungi identitas mereka. --- ## Mengapa PGP Penting? - Keamanan yang Kuat: Kombinasi kriptografi asimetris dan simetris membuat PGP sangat sulit ditembus oleh peretas. -Privasi: Menjaga komunikasi Anda tetap aman dan pribadi dari penyadapan atau pengawasan. - Integritas: Memastikan bahwa pesan atau data yang dikirim tidak diubah selama transmisi. - Otentikasi: Membuktikan identitas pengirim melalui tanda tangan digital. --- ## Kelebihan PGP - Sangat Aman: Jika digunakan dengan benar, PGP menawarkan tingkat keamanan yang sangat tinggi. - Terbuka: Banyak digunakan di kalangan profesional dan komunitas open-source. - Fleksibel: Dapat digunakan untuk berbagai keperluan, mulai dari komunikasi email hingga penyimpanan data. ## Kekurangan PGP - Kompleks untuk Pemula: Relatif sulit digunakan oleh pengguna awam. - Pengelolaan Kunci yang Rumit: Memerlukan pengelolaan kunci publik/privat yang benar. - Tidak Ada Pemulihan Data: Jika kunci privat hilang, data yang dienkripsi tidak dapat dipulihkan. --- PGP adalah alat yang sangat berguna untuk memastikan keamanan dan privasi dalam komunikasi dan data. Dengan meningkatnya risiko kejahatan siber, penggunaan PGP menjadi semakin penting, terutama di sektor yang menangani data sensitif. @ bcea2b98:7ccef3c9
2024-11-14 23:38:37@chess a3 originally posted at https://stacker.news/items/768303
@ bcea2b98:7ccef3c9
2024-11-14 23:38:37@chess a3 originally posted at https://stacker.news/items/768303 @ dbb19ae0:c3f22d5a
2024-11-14 20:39:37Hello, As I've registered with Alby a few months ago I told a friend (who complained about the current toxicity of twitter/X) about this new social media Nostr and told him he could get rewarded for posting. The deal was that I would help him to create his nostr account and get a wallet, https://guides.getalby.com/user-guide/alby-account-and-browser-extension downloading the extension, creating the nostr account was a breeze, and then .... As I wanted to send him a few sats to get started that is when the whole thing went down. Alby is now forcing its users to get a hub (and a channel), this was not my experience when I started back in March 2024 and I was surprised of this new direction Alby is taking. Opening a channel costs ~25K sat -- and that was not expected, for a brand new user Now my friend thinks that this whole new social media and bitcoin stuff is all a big scam. What can I do? Is there a way to open a wallet (compatible with Nostr) elsewhere? originally posted at https://stacker.news/items/768090
@ dbb19ae0:c3f22d5a
2024-11-14 20:39:37Hello, As I've registered with Alby a few months ago I told a friend (who complained about the current toxicity of twitter/X) about this new social media Nostr and told him he could get rewarded for posting. The deal was that I would help him to create his nostr account and get a wallet, https://guides.getalby.com/user-guide/alby-account-and-browser-extension downloading the extension, creating the nostr account was a breeze, and then .... As I wanted to send him a few sats to get started that is when the whole thing went down. Alby is now forcing its users to get a hub (and a channel), this was not my experience when I started back in March 2024 and I was surprised of this new direction Alby is taking. Opening a channel costs ~25K sat -- and that was not expected, for a brand new user Now my friend thinks that this whole new social media and bitcoin stuff is all a big scam. What can I do? Is there a way to open a wallet (compatible with Nostr) elsewhere? originally posted at https://stacker.news/items/768090 @ bcea2b98:7ccef3c9
2024-11-14 18:03:14We all have that one movie or show we turn to when we need a little comfort. Whether it’s for the laughs, the nostalgia, or the familiar characters, these are the ones that never get old. What’s a movie or series you can watch again and again? What makes it so comforting, and why do you keep coming back to it? I enjoy The Office with Michael Scott and Dwight Schrute. We watched a lot of that in the past and then again during the pandemic during isolation. originally posted at https://stacker.news/items/767870
@ bcea2b98:7ccef3c9
2024-11-14 18:03:14We all have that one movie or show we turn to when we need a little comfort. Whether it’s for the laughs, the nostalgia, or the familiar characters, these are the ones that never get old. What’s a movie or series you can watch again and again? What makes it so comforting, and why do you keep coming back to it? I enjoy The Office with Michael Scott and Dwight Schrute. We watched a lot of that in the past and then again during the pandemic during isolation. originally posted at https://stacker.news/items/767870 @ e968e50b:db2a803a
2024-11-14 17:03:38<sub>TLDR: No, but if you own bitcoin and can afford to, you should get one anyway.</sub> # Secure the network. First off, I'm not mining to heat my house, and I'm not mining to earn bitcoin. I'm not mining out of the goodness of my heart either. I'm mining because I store my family's savings in bitcoin, and mining centralization looks like a real threat to me. I've written about it [here](https://stacker.news/items/629837) and [here](https://stacker.news/items/735779) if you're interested in reading more about why this is so important for average bitcoiners. That being said, I'd like to earn (or at least not lose) bitcoin in the process, and I'd also love to heat my home with it.   # Nano 3 In one of the aforementioned posts, I made a stink about how little hash one contributes with a lottery miner and @OT called me out on ignoring hardware centralization concerns with Bitmain. Well, Canaan isn't exactly a small company, and they're not open source, but they aren't Bitmain, and I found a miner that's about eight times as powerful as the virtual signaling[^1] solo miners at about the same cost. My big find was the Nano 3. It's actually marketed as a space heater with three heating settings. At it's warmest, this guy mines at 4TH/s and uses about 140 watts. So it's about as efficient as a midrange s19, hashes about the a third as much as an s9, and costs as much as a Bitaxe. As a tool for decentralization, I'd say that's a great combo. Ironically, most of the folks I see talking about it online are shitcoiners that use it to solo mine Bitcoin Cash. I wonder if this phenomenon is culturally turning bitcoiners off to a better decentralizing tool.   # Recycled Heat So, now that I have them, I can tell you from personal experience how they're doing as heaters. Well, they are pushing heat out. However, it's a very small fraction of what my s9s do. They look better in house[^2], and they're significantly quieter (but not silent), but there's no way these guys are going to let me go furnace free this winter like a similar amount[^3] of Bitmain products would do. #Conclusion So I don't see the Nano 3 as the silver bullet for home miners. I do, however, think it's a great option and am not at all bummed with my purchase. At my current electricity price, I'll pay them off (even denominated in bitcoin) at some point. But I'm also going back to the drawing board about trying to replace my furnace with miners. [^1]: totally unfair characterization... I get it. Just trying to make a point with some hyperbole [^2]: The lighting is also pretty cool. You can make it pulse or strobe, and the full color spectrum is available. They're keep my kids' rooms a LITTLE bit warmer this winter and double as a cool night lite that teaches them about bitcoin. The ones in living areas do the same for guests. I consider these non-trivial features. [^3]: Similar price too! Most s9s online are about the same price as the Nano 3s. originally posted at https://stacker.news/items/767748
@ e968e50b:db2a803a
2024-11-14 17:03:38<sub>TLDR: No, but if you own bitcoin and can afford to, you should get one anyway.</sub> # Secure the network. First off, I'm not mining to heat my house, and I'm not mining to earn bitcoin. I'm not mining out of the goodness of my heart either. I'm mining because I store my family's savings in bitcoin, and mining centralization looks like a real threat to me. I've written about it [here](https://stacker.news/items/629837) and [here](https://stacker.news/items/735779) if you're interested in reading more about why this is so important for average bitcoiners. That being said, I'd like to earn (or at least not lose) bitcoin in the process, and I'd also love to heat my home with it.   # Nano 3 In one of the aforementioned posts, I made a stink about how little hash one contributes with a lottery miner and @OT called me out on ignoring hardware centralization concerns with Bitmain. Well, Canaan isn't exactly a small company, and they're not open source, but they aren't Bitmain, and I found a miner that's about eight times as powerful as the virtual signaling[^1] solo miners at about the same cost. My big find was the Nano 3. It's actually marketed as a space heater with three heating settings. At it's warmest, this guy mines at 4TH/s and uses about 140 watts. So it's about as efficient as a midrange s19, hashes about the a third as much as an s9, and costs as much as a Bitaxe. As a tool for decentralization, I'd say that's a great combo. Ironically, most of the folks I see talking about it online are shitcoiners that use it to solo mine Bitcoin Cash. I wonder if this phenomenon is culturally turning bitcoiners off to a better decentralizing tool.   # Recycled Heat So, now that I have them, I can tell you from personal experience how they're doing as heaters. Well, they are pushing heat out. However, it's a very small fraction of what my s9s do. They look better in house[^2], and they're significantly quieter (but not silent), but there's no way these guys are going to let me go furnace free this winter like a similar amount[^3] of Bitmain products would do. #Conclusion So I don't see the Nano 3 as the silver bullet for home miners. I do, however, think it's a great option and am not at all bummed with my purchase. At my current electricity price, I'll pay them off (even denominated in bitcoin) at some point. But I'm also going back to the drawing board about trying to replace my furnace with miners. [^1]: totally unfair characterization... I get it. Just trying to make a point with some hyperbole [^2]: The lighting is also pretty cool. You can make it pulse or strobe, and the full color spectrum is available. They're keep my kids' rooms a LITTLE bit warmer this winter and double as a cool night lite that teaches them about bitcoin. The ones in living areas do the same for guests. I consider these non-trivial features. [^3]: Similar price too! Most s9s online are about the same price as the Nano 3s. originally posted at https://stacker.news/items/767748 @ 5d4b6c8d:8a1c1ee3
2024-11-14 15:30:36So, I had been maintaining a position of not muting anyone on Stacker News. In part, that's because I don't want SN to become an echo chamber like so much of the rest of social media. I also don't want to risk missing out on something valuable that someone has to say, just because I don't like them. As I hope is clear to everyone here, and my record is fairly abundant, I'll engage on just about any topic with just about anyone. I've had many civil disagreements with folks (as well as some uncivil ones): sometimes I change my mind, sometimes I don't, but I do always listen to what the other person said and try to understand where they're coming from. I don't argue to win (shifting the goal posts when the other person makes a good point or simply ignoring it), but rather to learn. High-level civil disagreements are one of the things that sets Stacker News apart from the rest of the internet. What finally got someone muted was not their opinion (which I do disagree with), but their conduct. We had gone through the same tedious argument several times and the person never engaged with my points, but just kept repeating their assertions. When they attempted to start the same argument again recently, I told them I wasn't interested in rehashing it with them and they could go reread our past exchanges to see what I think. Rather than respect my wishes, the person belligerently insisted on pressing their argument. When I set my terms for continuing the conversation (read our past exchanges and bring up something new), they resorted to name calling. Mute. As much as I enjoy talking about stuff and having disagreements, I don't owe anyone my time or attention. If someone tells me that they're sick of talking to me about something, I will drop it (or I will at least acknowledge that I should have). I expect the same courtesy from others. Have some respect for the person you're interacting with, if you want them to interact with you. Have whatever opinion you want, but argue it in good faith and be respectful. originally posted at https://stacker.news/items/767536
@ 5d4b6c8d:8a1c1ee3
2024-11-14 15:30:36So, I had been maintaining a position of not muting anyone on Stacker News. In part, that's because I don't want SN to become an echo chamber like so much of the rest of social media. I also don't want to risk missing out on something valuable that someone has to say, just because I don't like them. As I hope is clear to everyone here, and my record is fairly abundant, I'll engage on just about any topic with just about anyone. I've had many civil disagreements with folks (as well as some uncivil ones): sometimes I change my mind, sometimes I don't, but I do always listen to what the other person said and try to understand where they're coming from. I don't argue to win (shifting the goal posts when the other person makes a good point or simply ignoring it), but rather to learn. High-level civil disagreements are one of the things that sets Stacker News apart from the rest of the internet. What finally got someone muted was not their opinion (which I do disagree with), but their conduct. We had gone through the same tedious argument several times and the person never engaged with my points, but just kept repeating their assertions. When they attempted to start the same argument again recently, I told them I wasn't interested in rehashing it with them and they could go reread our past exchanges to see what I think. Rather than respect my wishes, the person belligerently insisted on pressing their argument. When I set my terms for continuing the conversation (read our past exchanges and bring up something new), they resorted to name calling. Mute. As much as I enjoy talking about stuff and having disagreements, I don't owe anyone my time or attention. If someone tells me that they're sick of talking to me about something, I will drop it (or I will at least acknowledge that I should have). I expect the same courtesy from others. Have some respect for the person you're interacting with, if you want them to interact with you. Have whatever opinion you want, but argue it in good faith and be respectful. originally posted at https://stacker.news/items/767536 @ 7b8a7a4b:910f3874
2024-11-14 10:05:23123 test test originally posted at https://stacker.news/items/459399
@ 7b8a7a4b:910f3874
2024-11-14 10:05:23123 test test originally posted at https://stacker.news/items/459399 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo: Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1 Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2 Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb. ## O que são bloatwares? Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades. ## O que é o adb? O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode. Requisitos: Para computadores: • Depuração USB ativa no celular; • Computador com adb; • Cabo USB; Para celulares: • Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior; Para ambos: • Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo; ## Ativação de depuração: Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux. ## Instalação e configuração do NetGuard O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria. F-Droid: https://f-droid.org/packages/eu.faircode.netguard/ Github: https://github.com/M66B/NetGuard/releases Após instalado, configure da seguinte maneira: Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’); Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet); Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo. ## Lista de bloatwares Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região. Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por: ``` Samsung Galaxy Note 10 Plus bloatware list ``` Provavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica. Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível. ### De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente. ## Download do adb em computadores Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux. Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb. ## Download do adb em celulares com Termux. Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto. F-Droid: https://f-droid.org/en/packages/com.termux/ Github: https://github.com/termux/termux-app/releases ## Processo de debloat Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis. Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid. Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover. Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard. MTP tentando comunicação com servidores externos: ## Executando o adb shell No computador Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular. Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando: ``` ./adb start-server ``` O resultado deve ser: *daemon not running; starting now at tcp:5037 *daemon started successfully E caso não apareça nada, execute: ``` ./adb kill-server ``` E inicie novamente. Com o adb conectado ao celular, execute: ``` ./adb shell ``` Para poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia. Logo o resultado deve ser: begonia:/ $ Caso ocorra algum erro do tipo: adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device. Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo. ## No celular Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando: ``` pkg install android-tools ``` Quando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux. Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir: Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute: ``` adb pair localhost:porta CódigoDeEmparelhamento ``` De acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”. Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute: ``` adb connect localhost:porta ``` Obs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio. Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell: ``` adb shell ``` Remoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote. Dentro do NetGuard, verificando as informações do Google Maps: Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar: ``` pm uninstall –user 0 com.google.android.apps.maps ``` E pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote. Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro. Exemplo de lista: Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando: ``` cmd package install-existing nome.do.pacote ``` ## Pós-debloat Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade? Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store. Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23 Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo: Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1 Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2 Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb. ## O que são bloatwares? Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades. ## O que é o adb? O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode. Requisitos: Para computadores: • Depuração USB ativa no celular; • Computador com adb; • Cabo USB; Para celulares: • Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior; Para ambos: • Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo; ## Ativação de depuração: Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux. ## Instalação e configuração do NetGuard O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria. F-Droid: https://f-droid.org/packages/eu.faircode.netguard/ Github: https://github.com/M66B/NetGuard/releases Após instalado, configure da seguinte maneira: Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’); Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet); Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo. ## Lista de bloatwares Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região. Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por: ``` Samsung Galaxy Note 10 Plus bloatware list ``` Provavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica. Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível. ### De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente. ## Download do adb em computadores Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux. Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb. ## Download do adb em celulares com Termux. Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto. F-Droid: https://f-droid.org/en/packages/com.termux/ Github: https://github.com/termux/termux-app/releases ## Processo de debloat Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis. Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid. Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover. Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard. MTP tentando comunicação com servidores externos: ## Executando o adb shell No computador Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular. Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando: ``` ./adb start-server ``` O resultado deve ser: *daemon not running; starting now at tcp:5037 *daemon started successfully E caso não apareça nada, execute: ``` ./adb kill-server ``` E inicie novamente. Com o adb conectado ao celular, execute: ``` ./adb shell ``` Para poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia. Logo o resultado deve ser: begonia:/ $ Caso ocorra algum erro do tipo: adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device. Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo. ## No celular Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando: ``` pkg install android-tools ``` Quando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux. Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir: Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute: ``` adb pair localhost:porta CódigoDeEmparelhamento ``` De acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”. Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute: ``` adb connect localhost:porta ``` Obs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio. Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell: ``` adb shell ``` Remoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote. Dentro do NetGuard, verificando as informações do Google Maps: Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar: ``` pm uninstall –user 0 com.google.android.apps.maps ``` E pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote. Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro. Exemplo de lista: Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando: ``` cmd package install-existing nome.do.pacote ``` ## Pós-debloat Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade? Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store. Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23 Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms @ b4403b24:83542d4e
2024-11-14 00:55:14Donald Trump officially announced his nomination of Tucker Carlson for a White House Press Secretary. 🫶  originally posted at https://stacker.news/items/766758
@ b4403b24:83542d4e
2024-11-14 00:55:14Donald Trump officially announced his nomination of Tucker Carlson for a White House Press Secretary. 🫶  originally posted at https://stacker.news/items/766758 @ bcea2b98:7ccef3c9
2024-11-14 00:42:08Sometimes we come across values that resonate deeply only after going through certain experiences. These values may not have been obvious to us earlier, but now they play a meaningful role in how we approach life. Is there a value you’ve discovered later in life that’s become important to you? originally posted at https://stacker.news/items/766754
@ bcea2b98:7ccef3c9
2024-11-14 00:42:08Sometimes we come across values that resonate deeply only after going through certain experiences. These values may not have been obvious to us earlier, but now they play a meaningful role in how we approach life. Is there a value you’ve discovered later in life that’s become important to you? originally posted at https://stacker.news/items/766754 @ b4403b24:83542d4e
2024-11-13 21:00:29 originally posted at https://stacker.news/items/766497
@ b4403b24:83542d4e
2024-11-13 21:00:29 originally posted at https://stacker.news/items/766497 @ 000002de:c05780a7
2024-11-13 19:46:44Here's the official list. [A-Z index of U.S. government departments and agencies | USAGov](https://www.usa.gov/agency-index). My answer: Department of Education Why? * Its completely unnecessary. Every state has its own. * It is a mechanism for centralizing thought. * It wields great influence over schools and states with its massive budget * If you want to change the future of the nation in a positive direction stop allowing progressives manipulate the minds of the youth. * Decentralizing to at least the state level puts more power back into the states vs. a single agency that is largely unaccountable. What do you think? originally posted at https://stacker.news/items/766383
@ 000002de:c05780a7
2024-11-13 19:46:44Here's the official list. [A-Z index of U.S. government departments and agencies | USAGov](https://www.usa.gov/agency-index). My answer: Department of Education Why? * Its completely unnecessary. Every state has its own. * It is a mechanism for centralizing thought. * It wields great influence over schools and states with its massive budget * If you want to change the future of the nation in a positive direction stop allowing progressives manipulate the minds of the youth. * Decentralizing to at least the state level puts more power back into the states vs. a single agency that is largely unaccountable. What do you think? originally posted at https://stacker.news/items/766383 @ 6f170f27:711e26dd
2024-11-13 19:17:52 originally posted at https://stacker.news/items/766349
@ 6f170f27:711e26dd
2024-11-13 19:17:52 originally posted at https://stacker.news/items/766349 @ 5d4b6c8d:8a1c1ee3
2024-11-13 18:46:27We've got two of our three re-buys on the books, with the third expected to come in once @BlokchainB recovers from his recent slate of sports defeats. We've all been there, Blok. I like these second round options much more than round 1. Once again, I'll put off my pick for a day or two, but I'm looking at the Pacers, Hawks, Lakers, Rockets, and Nuggets. I might want to save a couple of them for later, so the Hawks could be the most attractive option. # Friday's Games - Heat @ Pacers - 76ers @ Magic - Pistons @ Raptors - Wizards @ Hawks - Bulls @ Cavs - Nets @ Knicks - Lakers @ Spurs - Clippers @ Rockets - Nuggets @ Pelicans - Suns @ Thunder - Grizzlies @ Warriors - T-Wolves @ Kings Picks due by tip-off of the game you're choosing on Friday. # Prize Pool 40 kilosats! (with 5k more on the way) originally posted at https://stacker.news/items/766272
@ 5d4b6c8d:8a1c1ee3
2024-11-13 18:46:27We've got two of our three re-buys on the books, with the third expected to come in once @BlokchainB recovers from his recent slate of sports defeats. We've all been there, Blok. I like these second round options much more than round 1. Once again, I'll put off my pick for a day or two, but I'm looking at the Pacers, Hawks, Lakers, Rockets, and Nuggets. I might want to save a couple of them for later, so the Hawks could be the most attractive option. # Friday's Games - Heat @ Pacers - 76ers @ Magic - Pistons @ Raptors - Wizards @ Hawks - Bulls @ Cavs - Nets @ Knicks - Lakers @ Spurs - Clippers @ Rockets - Nuggets @ Pelicans - Suns @ Thunder - Grizzlies @ Warriors - T-Wolves @ Kings Picks due by tip-off of the game you're choosing on Friday. # Prize Pool 40 kilosats! (with 5k more on the way) originally posted at https://stacker.news/items/766272 @ 5d4b6c8d:8a1c1ee3
2024-11-13 15:05:59That was a great night of basketball! The Steph-Klay reunion easily met expectations and was another reminder of just how great Steph Curry is. It also cemented the Warriors as legit contenders this season. We also had three big upsets, with Boston, Miami, and Minnesota all losing to likely lottery teams. Boston and Miami cost @siggy47, @BlokchainB, and @supercyclone their first strike (Let me know in the comments if you want to buy-back in). The Miami loss had to be the craziest, as no one expects Spoelstra to pull a Webber and try to call a timeout he doesn't have. Boston's loss was quite embarrassing in it's own right, though, since all they needed to do is complete a wide open in-bounds pass. This team still seems to have some issue performing under pressure. What were your impressions of last night's games and the Emirates Cup so far? # Prize Still about 30k, but will be 45k if last night's losers buy back in (C'mon guys, it was just an off night. You've got this!). I'll get the round 2 picks post up later today. originally posted at https://stacker.news/items/765972
@ 5d4b6c8d:8a1c1ee3
2024-11-13 15:05:59That was a great night of basketball! The Steph-Klay reunion easily met expectations and was another reminder of just how great Steph Curry is. It also cemented the Warriors as legit contenders this season. We also had three big upsets, with Boston, Miami, and Minnesota all losing to likely lottery teams. Boston and Miami cost @siggy47, @BlokchainB, and @supercyclone their first strike (Let me know in the comments if you want to buy-back in). The Miami loss had to be the craziest, as no one expects Spoelstra to pull a Webber and try to call a timeout he doesn't have. Boston's loss was quite embarrassing in it's own right, though, since all they needed to do is complete a wide open in-bounds pass. This team still seems to have some issue performing under pressure. What were your impressions of last night's games and the Emirates Cup so far? # Prize Still about 30k, but will be 45k if last night's losers buy back in (C'mon guys, it was just an off night. You've got this!). I'll get the round 2 picks post up later today. originally posted at https://stacker.news/items/765972 @ bcea2b98:7ccef3c9
2024-11-13 02:44:17@chess a3 originally posted at https://stacker.news/items/765445
@ bcea2b98:7ccef3c9
2024-11-13 02:44:17@chess a3 originally posted at https://stacker.news/items/765445 @ bcea2b98:7ccef3c9
2024-11-13 02:18:58Sometimes our strongest values are the ones that people wouldn’t expect. These unique principles often reveal something special about who we are and what we believe in. Do you hold a value that might surprise others? originally posted at https://stacker.news/items/765433
@ bcea2b98:7ccef3c9
2024-11-13 02:18:58Sometimes our strongest values are the ones that people wouldn’t expect. These unique principles often reveal something special about who we are and what we believe in. Do you hold a value that might surprise others? originally posted at https://stacker.news/items/765433 @ 6f170f27:711e26dd
2024-11-12 21:12:17 Less Chinese PhD student enroll in US universities. Less Chinese PhD students in the US get jobs in the US. The start of this trend aligns suspicously good with the start us the US-Chinese trade war. Source: > Building a Wall Around Science: The Effect of U.S.-China Tensions on International Scientific Research https://www.nber.org/papers/w32622 originally posted at https://stacker.news/items/765173
@ 6f170f27:711e26dd
2024-11-12 21:12:17 Less Chinese PhD student enroll in US universities. Less Chinese PhD students in the US get jobs in the US. The start of this trend aligns suspicously good with the start us the US-Chinese trade war. Source: > Building a Wall Around Science: The Effect of U.S.-China Tensions on International Scientific Research https://www.nber.org/papers/w32622 originally posted at https://stacker.news/items/765173 @ 5d4b6c8d:8a1c1ee3
2024-11-12 19:48:49As we head into the first night of the Emirates Cup Tournament ([Survivor Pool here](https://stacker.news/items/760645)), I wanted to share the data I've gathered through my NBA contests. # Emirates Cup first round of Group play - 50% of stackers chose Orlando - 25% of stackers chose Miami - 12.5% of stackers chose Boston - 12.5% of stackers chose New York # [NBA Prediction Contest](https://stacker.news/items/739939/r/Undisciplined) ## Champ - Celtics (4/14) - Pacers (3/14) - Thunder (2/14) - Nuggets (1/14) - T-Wolves (1/14) - Mavericks (1/14) - Lakers (1/14) - Knicks (1/14) ## MVP - Luka (8/14) - SGA (3/14) - Giannis (2/14) - Jokic (1/14) ## All NBA First Team - Luka (13/14) - Jokic (12/14) - Giannis (12/14) - SGA (11/14) - Edwards (8/14) - Brunson (6/14) - Wemby (3/14) - Tatum (2/14) - Mitchell (1/14) - Embiid (1/14) - Davis (1/14) originally posted at https://stacker.news/items/765075
@ 5d4b6c8d:8a1c1ee3
2024-11-12 19:48:49As we head into the first night of the Emirates Cup Tournament ([Survivor Pool here](https://stacker.news/items/760645)), I wanted to share the data I've gathered through my NBA contests. # Emirates Cup first round of Group play - 50% of stackers chose Orlando - 25% of stackers chose Miami - 12.5% of stackers chose Boston - 12.5% of stackers chose New York # [NBA Prediction Contest](https://stacker.news/items/739939/r/Undisciplined) ## Champ - Celtics (4/14) - Pacers (3/14) - Thunder (2/14) - Nuggets (1/14) - T-Wolves (1/14) - Mavericks (1/14) - Lakers (1/14) - Knicks (1/14) ## MVP - Luka (8/14) - SGA (3/14) - Giannis (2/14) - Jokic (1/14) ## All NBA First Team - Luka (13/14) - Jokic (12/14) - Giannis (12/14) - SGA (11/14) - Edwards (8/14) - Brunson (6/14) - Wemby (3/14) - Tatum (2/14) - Mitchell (1/14) - Embiid (1/14) - Davis (1/14) originally posted at https://stacker.news/items/765075 @ 30ceb64e:7f08bdf5
2024-11-12 15:41:27Hey Freaks, Listen to these. ## Joy Again - How you Feel https://music.youtube.com/watch?v=g94AbYYL678&si=JVzaqFjtG0s-SKqQ ## Vacations - Young https://music.youtube.com/watch?v=oAur1xQx-sc&si=HB7PrvtOA2phz3Jk ## The Rare Occasions - Notion https://music.youtube.com/watch?v=3vEiqil5d3Q&si=LdRtoEFrO4kldPzw ## Current Joys - Blondie https://music.youtube.com/watch?v=XVuBw7TYvHg&si=_mm3U5Rj29xEAXiD ## Mac Demarco - On The Level https://music.youtube.com/watch?v=WOV3c0t-Mwk&si=HZC2Ei-rnIE6-K4I ## Snail Mail - Habit https://music.youtube.com/watch?v=MHYxZKEV0bY&si=_XBaUw4O4DZKp6iq ## Modest Mouse - Trailer Trash https://music.youtube.com/watch?v=5kwLVhnTYlI&si=qEhasX5NckmoW_ke ## Third Eye Blind - Darkness https://music.youtube.com/watch?v=WlLyAMU7MtQ&si=edt-dNgbgg-m0HJ_ ## Weezer - Pink Triangle https://music.youtube.com/watch?v=v2vWDWxYJBc&si=UlMuJjofu_l__dak ## The Mars Volta - The Widow https://music.youtube.com/watch?v=0lAXFjAmcnM&si=YOOo4lCo1iMzzRQi And let me know what you think. originally posted at https://stacker.news/items/764730
@ 30ceb64e:7f08bdf5
2024-11-12 15:41:27Hey Freaks, Listen to these. ## Joy Again - How you Feel https://music.youtube.com/watch?v=g94AbYYL678&si=JVzaqFjtG0s-SKqQ ## Vacations - Young https://music.youtube.com/watch?v=oAur1xQx-sc&si=HB7PrvtOA2phz3Jk ## The Rare Occasions - Notion https://music.youtube.com/watch?v=3vEiqil5d3Q&si=LdRtoEFrO4kldPzw ## Current Joys - Blondie https://music.youtube.com/watch?v=XVuBw7TYvHg&si=_mm3U5Rj29xEAXiD ## Mac Demarco - On The Level https://music.youtube.com/watch?v=WOV3c0t-Mwk&si=HZC2Ei-rnIE6-K4I ## Snail Mail - Habit https://music.youtube.com/watch?v=MHYxZKEV0bY&si=_XBaUw4O4DZKp6iq ## Modest Mouse - Trailer Trash https://music.youtube.com/watch?v=5kwLVhnTYlI&si=qEhasX5NckmoW_ke ## Third Eye Blind - Darkness https://music.youtube.com/watch?v=WlLyAMU7MtQ&si=edt-dNgbgg-m0HJ_ ## Weezer - Pink Triangle https://music.youtube.com/watch?v=v2vWDWxYJBc&si=UlMuJjofu_l__dak ## The Mars Volta - The Widow https://music.youtube.com/watch?v=0lAXFjAmcnM&si=YOOo4lCo1iMzzRQi And let me know what you think. originally posted at https://stacker.news/items/764730 @ 5d4b6c8d:8a1c1ee3
2024-11-12 14:44:24 There are some new soccer matches up at [freebitcoin](https://freebitco.in/?r=51325722). Using my proprietary [Risk Balanced Odds Arbitrage](https://stacker.news/items/342765/r/Undisciplined) approach, you too can lock in some easy wins. # Bets All you have to do is apportion your sats in accord with the following 1000 sat splits (scale up or down in proportion to how much you like winning): | Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | Verona| Inter Milan| Draw | 120| 700 | 180 | | Napoli| Roma| Draw | 540| 200| 260| | AC Milan| Juventus| Draw | 450| 270| 280| | AC Milan| Empoli| Draw | 700| 100| 200| | Union Berlin| Leverkusen| Draw | 220| 540| 240| | RB Leipzig| Wolfsburg| Draw | 650| 140| 210| | Leverkusen| Heidenheim| Draw | 800| 70| 130| | Hoffenheim| RB Leipzig| Draw | 250| 520| 230| | Dortmund| SC Freiburg| Draw | 590| 190| 220| | Dortmund| FC Bayern| Draw | 230| 540| 230| # Updates The payouts from [these matches](https://stacker.news/items/743312/r/Undisciplined) have all been made. Our hypothetical 14k returned just over 15k. originally posted at https://stacker.news/items/764646
@ 5d4b6c8d:8a1c1ee3
2024-11-12 14:44:24 There are some new soccer matches up at [freebitcoin](https://freebitco.in/?r=51325722). Using my proprietary [Risk Balanced Odds Arbitrage](https://stacker.news/items/342765/r/Undisciplined) approach, you too can lock in some easy wins. # Bets All you have to do is apportion your sats in accord with the following 1000 sat splits (scale up or down in proportion to how much you like winning): | Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | Verona| Inter Milan| Draw | 120| 700 | 180 | | Napoli| Roma| Draw | 540| 200| 260| | AC Milan| Juventus| Draw | 450| 270| 280| | AC Milan| Empoli| Draw | 700| 100| 200| | Union Berlin| Leverkusen| Draw | 220| 540| 240| | RB Leipzig| Wolfsburg| Draw | 650| 140| 210| | Leverkusen| Heidenheim| Draw | 800| 70| 130| | Hoffenheim| RB Leipzig| Draw | 250| 520| 230| | Dortmund| SC Freiburg| Draw | 590| 190| 220| | Dortmund| FC Bayern| Draw | 230| 540| 230| # Updates The payouts from [these matches](https://stacker.news/items/743312/r/Undisciplined) have all been made. Our hypothetical 14k returned just over 15k. originally posted at https://stacker.news/items/764646 @ 74718b83:b8204bd8
2024-11-12 13:48:52Hey guys, do you think a big bullrun might cause a spike in activity here? or do you think that the learning curve and journey when a noob takes longer with people only learning about things like nostr and SN later in the curve? originally posted at https://stacker.news/items/764581
@ 74718b83:b8204bd8
2024-11-12 13:48:52Hey guys, do you think a big bullrun might cause a spike in activity here? or do you think that the learning curve and journey when a noob takes longer with people only learning about things like nostr and SN later in the curve? originally posted at https://stacker.news/items/764581 @ 5d4b6c8d:8a1c1ee3
2024-11-12 01:09:13I almost forgot about Mock Draft Monday. The Raiders had their bye week, which means I'm not wallowing in the memory of a fresh humiliation. Week 10 broke their way a little bit and the Raiders are now picking 5th. Unfortunately, the teams ahead of them also need QB's. In this draft, three of the first four picks were QB's. That didn't leave any who were worth spending a top five pick on. Results - 5th Pick: CB Travis Hunter - 36th Pick: QB Garrett Nussmeier - 67th Pick: LB Danny Stutsman - 74th Pick: S Kevin Winston Jr. - 106th Pick: RB Ollie Gordon II - 142nd Pick: WR Tory Horton - 179th Pick: DE Anto Saka - 212th Pick: IOL Seth McLaughlin - 215th Pick: OT Jalen Travis - 220th Pick: QB Miller Moss This draft was a disaster. Unless some of these guys wildly over perform, this is something of a worst case scenario. The board just refused to bread my way. originally posted at https://stacker.news/items/764061
@ 5d4b6c8d:8a1c1ee3
2024-11-12 01:09:13I almost forgot about Mock Draft Monday. The Raiders had their bye week, which means I'm not wallowing in the memory of a fresh humiliation. Week 10 broke their way a little bit and the Raiders are now picking 5th. Unfortunately, the teams ahead of them also need QB's. In this draft, three of the first four picks were QB's. That didn't leave any who were worth spending a top five pick on. Results - 5th Pick: CB Travis Hunter - 36th Pick: QB Garrett Nussmeier - 67th Pick: LB Danny Stutsman - 74th Pick: S Kevin Winston Jr. - 106th Pick: RB Ollie Gordon II - 142nd Pick: WR Tory Horton - 179th Pick: DE Anto Saka - 212th Pick: IOL Seth McLaughlin - 215th Pick: OT Jalen Travis - 220th Pick: QB Miller Moss This draft was a disaster. Unless some of these guys wildly over perform, this is something of a worst case scenario. The board just refused to bread my way. originally posted at https://stacker.news/items/764061 @ b4403b24:83542d4e
2024-11-11 22:26:38 originally posted at https://stacker.news/items/763926
@ b4403b24:83542d4e
2024-11-11 22:26:38 originally posted at https://stacker.news/items/763926 @ 000002de:c05780a7
2024-11-11 21:02:50The US Government (administrative state) is not only evil, its also stupid. On March 14 of 2023 the gov sold 9,861 bitcoin that it had stolen from the Silk Road. At the time this was valued at 215 million dollars. At today's market price those coins are valued at $860,051,175, an increase of 300%. For every seller there is a buyer. Here's to those bitcoiners that bought those coins. [source](https://jlopp.github.io/us-marshals-bitcoin-auctions/) Now, I know 645 million is nothing for the US Federal government.... but still. Its pretty comical. Guys, I don't think you want the government buying bitcoin.... Not if we want the state to go away... May not be a popular opinion but that's fine. Its mine. originally posted at https://stacker.news/items/763834
@ 000002de:c05780a7
2024-11-11 21:02:50The US Government (administrative state) is not only evil, its also stupid. On March 14 of 2023 the gov sold 9,861 bitcoin that it had stolen from the Silk Road. At the time this was valued at 215 million dollars. At today's market price those coins are valued at $860,051,175, an increase of 300%. For every seller there is a buyer. Here's to those bitcoiners that bought those coins. [source](https://jlopp.github.io/us-marshals-bitcoin-auctions/) Now, I know 645 million is nothing for the US Federal government.... but still. Its pretty comical. Guys, I don't think you want the government buying bitcoin.... Not if we want the state to go away... May not be a popular opinion but that's fine. Its mine. originally posted at https://stacker.news/items/763834 @ b4403b24:83542d4e
2024-11-11 20:42:43 originally posted at https://stacker.news/items/763814
@ b4403b24:83542d4e
2024-11-11 20:42:43 originally posted at https://stacker.news/items/763814 @ 5d4b6c8d:8a1c1ee3
2024-11-11 17:06:58Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined. For a hypothetical 1k wager on each match, distribute your sats as follows: | Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | FC Bayern| Augsburg| Draw | 860| 50 | 90 | | West Ham| Arsenal| Draw | 150| 650| 200| | Southampton| Liverpool| Draw | 100| 730| 170| | Newcastle| West Ham| Draw | 610| 170| 220| | Man City| Tottenham| Draw | 630| 160| 210| | Leicester| Chelsea| Draw | 180| 600| 220| | Ipswich| Man United| Draw | 210| 590| 240| | Crystal Palace| Newcastle| Draw | 310| 420| 270 | | Arsenal| Nottingham Forest| Draw | 720| 100 | 180| | Leganes| Real Madrid| Draw | 120| 690| 190 | | Celta Viga| Barcelona| Draw | 210| 570| 220| | Atletico Madrid| Alaves| Draw | 710| 100| 190| | Athletic Club| Real Sociedad| Draw | 410| 280| 310| As of writing this, I'm up almost 85 kilosats with RBOA, thanks to Real Sociedad beating Barcelona last week as a wildly underpriced underdog. originally posted at https://stacker.news/items/763403
@ 5d4b6c8d:8a1c1ee3
2024-11-11 17:06:58Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined. For a hypothetical 1k wager on each match, distribute your sats as follows: | Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | FC Bayern| Augsburg| Draw | 860| 50 | 90 | | West Ham| Arsenal| Draw | 150| 650| 200| | Southampton| Liverpool| Draw | 100| 730| 170| | Newcastle| West Ham| Draw | 610| 170| 220| | Man City| Tottenham| Draw | 630| 160| 210| | Leicester| Chelsea| Draw | 180| 600| 220| | Ipswich| Man United| Draw | 210| 590| 240| | Crystal Palace| Newcastle| Draw | 310| 420| 270 | | Arsenal| Nottingham Forest| Draw | 720| 100 | 180| | Leganes| Real Madrid| Draw | 120| 690| 190 | | Celta Viga| Barcelona| Draw | 210| 570| 220| | Atletico Madrid| Alaves| Draw | 710| 100| 190| | Athletic Club| Real Sociedad| Draw | 410| 280| 310| As of writing this, I'm up almost 85 kilosats with RBOA, thanks to Real Sociedad beating Barcelona last week as a wildly underpriced underdog. originally posted at https://stacker.news/items/763403 @ 000002de:c05780a7
2024-11-11 17:06:01I'm curious. I don't push my political views on people. If they ask I talk pretty freely about my views but most progressives I call friends or colleagues don't ask. But they sure do whine about Trump. I've heard two people in my circle talk about actively searching for places to move. One said they had passports if they need to leave quickly. I know... Curious if others that actually have "progressive" friends are hearing stuff like this. Now, I will be very surprised if they actually go through with it. I think these people have been mentally abused by the corporate press, the establishment, and the Democrat party into believing lies about Donald Trump. I'm not a fan of Mr. Trump but the dogma about him has reached absurd levels. I honestly feel sorry for these folks. I try to talk them down. They have none of it. Its sad. Their brains are switched off. What has been done to them is truly evil. So, am I alone in this experience. I realize some of you probably don't have friends so you can just abstain from responding ;) originally posted at https://stacker.news/items/763402
@ 000002de:c05780a7
2024-11-11 17:06:01I'm curious. I don't push my political views on people. If they ask I talk pretty freely about my views but most progressives I call friends or colleagues don't ask. But they sure do whine about Trump. I've heard two people in my circle talk about actively searching for places to move. One said they had passports if they need to leave quickly. I know... Curious if others that actually have "progressive" friends are hearing stuff like this. Now, I will be very surprised if they actually go through with it. I think these people have been mentally abused by the corporate press, the establishment, and the Democrat party into believing lies about Donald Trump. I'm not a fan of Mr. Trump but the dogma about him has reached absurd levels. I honestly feel sorry for these folks. I try to talk them down. They have none of it. Its sad. Their brains are switched off. What has been done to them is truly evil. So, am I alone in this experience. I realize some of you probably don't have friends so you can just abstain from responding ;) originally posted at https://stacker.news/items/763402 @ dca6e1cc:ea7d1750
2024-11-11 15:16:49Hi all, Here's a review of our activity over the last two weeks or so... ### Ww/P Geyser fund & Postcards [Wandering w/ Purpose started its own geyser fund](https://geyser.fund/project/wanderingwpurpose) to offer more perks to our followers. [Check out our latest reward](https://geyser.fund/project/wanderingwpurpose/rewards/view/5299). It's a post card from wherever we are in the world to wherever you are in the world :) ### Bitcoin Nakawa [Bitcoin Nakawa is currently featured on the front page of the geyser fund website.](https://geyser.fund/) We're very thankful for the steady stream of sats coming from the exposure. Here's a contribution and thoughtful comment from one of Geyser Fund's co-Founders.  [We also recently announced a children's book being written about the Nakawa story.](https://wanderingwpurpose.substack.com/p/update-2-nakawa-childrens-book-and) Each purchase will gift a free copy to a student at the Nakawa school. [Pre-order is available now :)](https://geyser.fund/project/bitcoinnakawa/rewards/view/5192) Here is an infographic of all current Bitcoin projects in Africa. Hopefully Bitcoin Nakawa will soon be included!  ### Mozambique protests update We are currently in Mozambique. If you haven't heard, the country is going through a significant transition. Mass protests are taking place to rebuke against the stagnation of 50 years of corrupt political monopolisation. We are safe from the violence, thankfully. It's just a matter of patience to wait for our opportunity to leave the country. Hopefully this happens before our visa expires...then it's a mission to get to the border however possible. Public transport in Mozambique is painfully slow, and even more so due to the protests. 10-12 hours to travel 500km is commonplace. ### Our Substack activity Recent(ish) posts: [Mass protests in Mozambique](https://wanderingwpurpose.substack.com/p/mass-protests-in-mozambique) [Our most popular post thus far](https://substack.com/@wanderingwpurpose/note/c-75263839) Recent notes: [Our recent Substack Notes](https://wanderingwpurpose.substack.com/notes) ### Stacker News [Our recent posts on Stacker News](https://stacker.news/gpvansat/posts) ## Closing thoughts I'm currently preparing an Investment Memoranda intended for Hedge Funds, Family Offices, Institutional Investors, etc. looking to invest into Bitcoin mining machinery and associated hosting services. During my research, I found a report titled, ["Leveraging Bitcoin mining to improve access to electricity in rural Africa" by Tikula Research Network](https://www.tikula.net/_files/ugd/e1de83_6945ec0a6d074146a3503cdd14d475dc.pdf) to be especially interesting. Thanks everyone! Stay safe out there. Ww/P originally posted at https://stacker.news/items/763238
@ dca6e1cc:ea7d1750
2024-11-11 15:16:49Hi all, Here's a review of our activity over the last two weeks or so... ### Ww/P Geyser fund & Postcards [Wandering w/ Purpose started its own geyser fund](https://geyser.fund/project/wanderingwpurpose) to offer more perks to our followers. [Check out our latest reward](https://geyser.fund/project/wanderingwpurpose/rewards/view/5299). It's a post card from wherever we are in the world to wherever you are in the world :) ### Bitcoin Nakawa [Bitcoin Nakawa is currently featured on the front page of the geyser fund website.](https://geyser.fund/) We're very thankful for the steady stream of sats coming from the exposure. Here's a contribution and thoughtful comment from one of Geyser Fund's co-Founders.  [We also recently announced a children's book being written about the Nakawa story.](https://wanderingwpurpose.substack.com/p/update-2-nakawa-childrens-book-and) Each purchase will gift a free copy to a student at the Nakawa school. [Pre-order is available now :)](https://geyser.fund/project/bitcoinnakawa/rewards/view/5192) Here is an infographic of all current Bitcoin projects in Africa. Hopefully Bitcoin Nakawa will soon be included!  ### Mozambique protests update We are currently in Mozambique. If you haven't heard, the country is going through a significant transition. Mass protests are taking place to rebuke against the stagnation of 50 years of corrupt political monopolisation. We are safe from the violence, thankfully. It's just a matter of patience to wait for our opportunity to leave the country. Hopefully this happens before our visa expires...then it's a mission to get to the border however possible. Public transport in Mozambique is painfully slow, and even more so due to the protests. 10-12 hours to travel 500km is commonplace. ### Our Substack activity Recent(ish) posts: [Mass protests in Mozambique](https://wanderingwpurpose.substack.com/p/mass-protests-in-mozambique) [Our most popular post thus far](https://substack.com/@wanderingwpurpose/note/c-75263839) Recent notes: [Our recent Substack Notes](https://wanderingwpurpose.substack.com/notes) ### Stacker News [Our recent posts on Stacker News](https://stacker.news/gpvansat/posts) ## Closing thoughts I'm currently preparing an Investment Memoranda intended for Hedge Funds, Family Offices, Institutional Investors, etc. looking to invest into Bitcoin mining machinery and associated hosting services. During my research, I found a report titled, ["Leveraging Bitcoin mining to improve access to electricity in rural Africa" by Tikula Research Network](https://www.tikula.net/_files/ugd/e1de83_6945ec0a6d074146a3503cdd14d475dc.pdf) to be especially interesting. Thanks everyone! Stay safe out there. Ww/P originally posted at https://stacker.news/items/763238 @ dca6e1cc:ea7d1750
2024-11-11 13:10:17What are the odds that we can crowd-source a Bitcoin Mining operation that supports the energy development of a rural African village? For anyone who knows, there are plenty of environmental, social, and economic benefits that Bitcoin mining can bring to the development of rural mini-grids. More info: https://www.gama.africa/gama-programs.html https://x.com/GridlessCompute/status/1752679599601782846 Africa is home to massive amounts of untapped energy that can be ethically sourced. Access to energy is fundamental to human flourishing, meaning the upside for Africans' lifestyles is considerable given that many have zero electricity access aside from the odd solar panel. What can we do to accelerate this process? originally posted at https://stacker.news/items/763008
@ dca6e1cc:ea7d1750
2024-11-11 13:10:17What are the odds that we can crowd-source a Bitcoin Mining operation that supports the energy development of a rural African village? For anyone who knows, there are plenty of environmental, social, and economic benefits that Bitcoin mining can bring to the development of rural mini-grids. More info: https://www.gama.africa/gama-programs.html https://x.com/GridlessCompute/status/1752679599601782846 Africa is home to massive amounts of untapped energy that can be ethically sourced. Access to energy is fundamental to human flourishing, meaning the upside for Africans' lifestyles is considerable given that many have zero electricity access aside from the odd solar panel. What can we do to accelerate this process? originally posted at https://stacker.news/items/763008 @ 36bedab2:524acad4
2024-11-10 21:37:52### 1. **Power ON** - Quando você liga o computador, ele inicia o processo de boot. - Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes). ### 2. **BIOS (Basic Input/Output System)** - O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado. - Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU. - O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot. ### 3. **Master Boot Record (MBR) ou EFI Partition** - O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional. - Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função. - O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional. ### 4. **Boot Loader (e.g., GRUB)** - O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot. - Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema. - GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux. ### 5. **Kernel** - O **kernel** é o núcleo do sistema operacional Linux. - Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware. - O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software. ### 6. **Initial RAM disk - initramfs** - O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel. - Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco. - O initramfs é desmontado após o sistema principal estar carregado. ### 7. **/sbin/init (parent process)** - Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos. - O init é responsável por iniciar e gerenciar todos os outros processos do sistema. - Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos. ### 8. **Command Shell using getty** - **Getty** é o processo que configura e gerencia terminais para o login do usuário. - Ele exibe a tela de login em sistemas baseados em linha de comando. - Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico. ### 9. **Graphical User Interface (X Window ou Wayland)** - Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno). - Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc. - X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela. --- ### Como esses processos se intercalam? 1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas. 2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**. 3. **MBR/EFI** localiza e executa o **boot loader** (GRUB). 4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux. 5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**. 6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal. 7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema. 8. **Init** executa o **getty** para configurar o terminal de login. 9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
@ 36bedab2:524acad4
2024-11-10 21:37:52### 1. **Power ON** - Quando você liga o computador, ele inicia o processo de boot. - Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes). ### 2. **BIOS (Basic Input/Output System)** - O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado. - Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU. - O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot. ### 3. **Master Boot Record (MBR) ou EFI Partition** - O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional. - Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função. - O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional. ### 4. **Boot Loader (e.g., GRUB)** - O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot. - Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema. - GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux. ### 5. **Kernel** - O **kernel** é o núcleo do sistema operacional Linux. - Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware. - O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software. ### 6. **Initial RAM disk - initramfs** - O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel. - Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco. - O initramfs é desmontado após o sistema principal estar carregado. ### 7. **/sbin/init (parent process)** - Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos. - O init é responsável por iniciar e gerenciar todos os outros processos do sistema. - Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos. ### 8. **Command Shell using getty** - **Getty** é o processo que configura e gerencia terminais para o login do usuário. - Ele exibe a tela de login em sistemas baseados em linha de comando. - Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico. ### 9. **Graphical User Interface (X Window ou Wayland)** - Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno). - Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc. - X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela. --- ### Como esses processos se intercalam? 1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas. 2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**. 3. **MBR/EFI** localiza e executa o **boot loader** (GRUB). 4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux. 5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**. 6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal. 7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema. 8. **Init** executa o **getty** para configurar o terminal de login. 9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica. @ bcea2b98:7ccef3c9
2024-11-10 19:34:24@chess a3 originally posted at https://stacker.news/items/762161
@ bcea2b98:7ccef3c9
2024-11-10 19:34:24@chess a3 originally posted at https://stacker.news/items/762161 @ c11cf5f8:4928464d
2024-11-10 07:58:46Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/751696/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/761231
@ c11cf5f8:4928464d
2024-11-10 07:58:46Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/751696/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/761231 @ a10260a2:caa23e3e
2024-11-10 04:35:34nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard. In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW. I took some screenshots to give you an idea of how things work. The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).  Clicking login allows signing in with a browser extension.  The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.  Existing blog posts (i.e. long form notes) are synced.  Same for product listings. There’s a nice interface to create new ones and preview them before publishing.   That’s all for now. As you can see, super slick stuff! Bullish on Cypher. So much so I had to support the project and buy a subdomain. 😎 https://bullish.cypher.space originally posted at https://stacker.news/items/760592
@ a10260a2:caa23e3e
2024-11-10 04:35:34nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard. In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW. I took some screenshots to give you an idea of how things work. The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).  Clicking login allows signing in with a browser extension.  The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.  Existing blog posts (i.e. long form notes) are synced.  Same for product listings. There’s a nice interface to create new ones and preview them before publishing.   That’s all for now. As you can see, super slick stuff! Bullish on Cypher. So much so I had to support the project and buy a subdomain. 😎 https://bullish.cypher.space originally posted at https://stacker.news/items/760592 @ b6424601:a11e4ff4
2024-11-09 19:45:51**Personal Asset Architecture - Breaking Free from the Fiat-Driven Housing Market** ***Subheading – How Individuals Can Opt Out of the Fiat-Driven System and Create Homes with long term value*** As a self-inflicted residential architect, I am passionate about creating new, renovated homes that matter to interesting people. However, I've realized that the traditional housing market is built on a foundation of fiat currency, leading to several problems, including the potential devaluation of homes and, increasingly, the creation of empty stores of value. **The Fiat Death Spiral** Construction financing drives the most decisions in the housing market, which leads to a system where production homes are built to sell and create an initial profit rather than to provide a high-quality construction or a well-conceived living space. **The Choice: Custom vs. Fiat** When building or buying a home, you have two main options: a custom home built or renovated to your specifications or a production home pre-designed and pre-built by a builder. **Fiat-Driven Homes: The Short-Term Solution** Fiat-driven homes are built to sell quickly, often using materials that fit the deals proforma. Because of lower-quality materials and construction methods, Fiat homes depreciate more like cars than buildings. **Custom Homes: The Long-Term Solution** On the other hand, custom homes are typically built with higher quality and better design because the owner and designer are more invested in creating one-of-a-kind designs. **A New Approach: Personal Asset Architecture** As an architectural design firm owner focusing on homes, I've always known that the percentage of all homes architects design is low. I've used the low percentage as a filter for working with longer-term thinking clients, typically paying with cash. Clients who pay with cash have the flexibility to pay for what they want, allowing them to think about the total cost over the life of the house rather than just jumping through the hoops of a loan-to-value appraisal. Bitcoin standard architectural practice and Bitcoin standard homes are the escape valves to continue the work we want for the individuals we want to work for. Our thesis is that Bitcoin can improve the housing market, both for our practice and for the clients we work with. Our thesis is that Bitcoin changed the housing market for our practice and the people we work with to build a personal architecture that is as hard an asset as Bitcoin. **Asset Architecture Benefits** Homes designed in a BTC standard have four big benefits for the individual to create personal asset architecture that holds value over time. 1\. Allows owners to think in a longer time horizon – Decisions made when designing homes need to consider a longer time horizon to include the operating cost of the house in addition to the cost of construction. Production homes are built to sell and create profit based on profit produced, netting profit by the sales price vs cost. Custom homes have more flexibility in spending more on quality and life cycle improvements. 2\. Allows for a density of design thought - Can you design a better-conceived home that considers how to use space more effectively to provide a denser space so the house can require less square footage? Can the smaller square footage be planned to work as a lifetime home from a starter home, through offspring to empty nesting and multigenerational housing? 3\. Providing a return on investment beyond money – A home should produce a better quality of life. Can homes produce income, food, energy, resilience, conservation of resources, and interior air quality and become your favorite place to be? Can the utility of needing a place to live be your family citadel? 4\. Working with the system to minimize the power of the system to increase taxes on the asset - Can we design homes to reduce property taxes with a creative design to minimize bedrooms and the taxable house value? Can we put more investment and design in outdoor space that helps owners maximize the use of properties for uses that are not taxed, like quality outdoor space or properties that produce food and energy? The future of housing is uncertain, but one thing is evident from the trenches: the traditional fiat-driven system is not sustainable. Personal Asset Architecture offers a new approach to housing design that prioritizes long-term value, efficiency, and quality. By embracing this approach, we can create precious homes that produce a return on investment beyond money. The future of housing is in our hands, and it's time to create a new way of thinking about home design. **What is possible?** As individual owners and architects, we can build Stores of value buildings. By incorporating the goal of creating Personal Asset Architecture, we can create homes that produce a return on investment that goes beyond money and minimize the values of a banking system and the ability to increase taxes on the asset. Stay humble, stack stakes, and when you are ready, choose to build stuff that holds actual value.** **HODL on**
@ b6424601:a11e4ff4
2024-11-09 19:45:51**Personal Asset Architecture - Breaking Free from the Fiat-Driven Housing Market** ***Subheading – How Individuals Can Opt Out of the Fiat-Driven System and Create Homes with long term value*** As a self-inflicted residential architect, I am passionate about creating new, renovated homes that matter to interesting people. However, I've realized that the traditional housing market is built on a foundation of fiat currency, leading to several problems, including the potential devaluation of homes and, increasingly, the creation of empty stores of value. **The Fiat Death Spiral** Construction financing drives the most decisions in the housing market, which leads to a system where production homes are built to sell and create an initial profit rather than to provide a high-quality construction or a well-conceived living space. **The Choice: Custom vs. Fiat** When building or buying a home, you have two main options: a custom home built or renovated to your specifications or a production home pre-designed and pre-built by a builder. **Fiat-Driven Homes: The Short-Term Solution** Fiat-driven homes are built to sell quickly, often using materials that fit the deals proforma. Because of lower-quality materials and construction methods, Fiat homes depreciate more like cars than buildings. **Custom Homes: The Long-Term Solution** On the other hand, custom homes are typically built with higher quality and better design because the owner and designer are more invested in creating one-of-a-kind designs. **A New Approach: Personal Asset Architecture** As an architectural design firm owner focusing on homes, I've always known that the percentage of all homes architects design is low. I've used the low percentage as a filter for working with longer-term thinking clients, typically paying with cash. Clients who pay with cash have the flexibility to pay for what they want, allowing them to think about the total cost over the life of the house rather than just jumping through the hoops of a loan-to-value appraisal. Bitcoin standard architectural practice and Bitcoin standard homes are the escape valves to continue the work we want for the individuals we want to work for. Our thesis is that Bitcoin can improve the housing market, both for our practice and for the clients we work with. Our thesis is that Bitcoin changed the housing market for our practice and the people we work with to build a personal architecture that is as hard an asset as Bitcoin. **Asset Architecture Benefits** Homes designed in a BTC standard have four big benefits for the individual to create personal asset architecture that holds value over time. 1\. Allows owners to think in a longer time horizon – Decisions made when designing homes need to consider a longer time horizon to include the operating cost of the house in addition to the cost of construction. Production homes are built to sell and create profit based on profit produced, netting profit by the sales price vs cost. Custom homes have more flexibility in spending more on quality and life cycle improvements. 2\. Allows for a density of design thought - Can you design a better-conceived home that considers how to use space more effectively to provide a denser space so the house can require less square footage? Can the smaller square footage be planned to work as a lifetime home from a starter home, through offspring to empty nesting and multigenerational housing? 3\. Providing a return on investment beyond money – A home should produce a better quality of life. Can homes produce income, food, energy, resilience, conservation of resources, and interior air quality and become your favorite place to be? Can the utility of needing a place to live be your family citadel? 4\. Working with the system to minimize the power of the system to increase taxes on the asset - Can we design homes to reduce property taxes with a creative design to minimize bedrooms and the taxable house value? Can we put more investment and design in outdoor space that helps owners maximize the use of properties for uses that are not taxed, like quality outdoor space or properties that produce food and energy? The future of housing is uncertain, but one thing is evident from the trenches: the traditional fiat-driven system is not sustainable. Personal Asset Architecture offers a new approach to housing design that prioritizes long-term value, efficiency, and quality. By embracing this approach, we can create precious homes that produce a return on investment beyond money. The future of housing is in our hands, and it's time to create a new way of thinking about home design. **What is possible?** As individual owners and architects, we can build Stores of value buildings. By incorporating the goal of creating Personal Asset Architecture, we can create homes that produce a return on investment that goes beyond money and minimize the values of a banking system and the ability to increase taxes on the asset. Stay humble, stack stakes, and when you are ready, choose to build stuff that holds actual value.** **HODL on** @ 5d4b6c8d:8a1c1ee3
2024-11-09 19:04:04The Emirates Cup begins on Tuesday, so it's time to start thinking about our first picks. For a refresher on the tournament, see the [first post](https://stacker.news/items/751054/r/Undisciplined). Note, though, that there are actually going to be seven group play days with each team playing four total group play games. # Games Here is the first slate of games (plus the home spread): - Hawks @ Celtics (-12.5) - Heat @ Pistons (+3) - Hornets @ Magic (-8) - Knicks @ 76ers (-1) - Raptors @ Bucks (-8) - Suns @ Jazz (+4.5) - Mavs @ Warriors (+2.5) Just pick one of the teams above to win their game on Tuesday. Remember, you can only take each team once and the options will dwindle once we get to the Knock Out round. There are at most 10 choices to make during the tournament, but you don't know which ones will be available towards the end. I'm going to wait a couple of days, to get more clarity on the injury situations for the Heat, Magic, 76ers, and Bucks. At first glance, I'm leaning towards taking either the Heat, but with Jimmy hurt and the Pistons looking a little frisky, I don't love it. # Prize 27133 sats! plus whatever else comes in from here on out # Participants @Undisciplined, @gnilma, @BlokchainB, @realBitcoinDog, @Carresan, @supercyclone, @grayruby There's still time to join. The initial buy-in is only 3k sats. originally posted at https://stacker.news/items/760645
@ 5d4b6c8d:8a1c1ee3
2024-11-09 19:04:04The Emirates Cup begins on Tuesday, so it's time to start thinking about our first picks. For a refresher on the tournament, see the [first post](https://stacker.news/items/751054/r/Undisciplined). Note, though, that there are actually going to be seven group play days with each team playing four total group play games. # Games Here is the first slate of games (plus the home spread): - Hawks @ Celtics (-12.5) - Heat @ Pistons (+3) - Hornets @ Magic (-8) - Knicks @ 76ers (-1) - Raptors @ Bucks (-8) - Suns @ Jazz (+4.5) - Mavs @ Warriors (+2.5) Just pick one of the teams above to win their game on Tuesday. Remember, you can only take each team once and the options will dwindle once we get to the Knock Out round. There are at most 10 choices to make during the tournament, but you don't know which ones will be available towards the end. I'm going to wait a couple of days, to get more clarity on the injury situations for the Heat, Magic, 76ers, and Bucks. At first glance, I'm leaning towards taking either the Heat, but with Jimmy hurt and the Pistons looking a little frisky, I don't love it. # Prize 27133 sats! plus whatever else comes in from here on out # Participants @Undisciplined, @gnilma, @BlokchainB, @realBitcoinDog, @Carresan, @supercyclone, @grayruby There's still time to join. The initial buy-in is only 3k sats. originally posted at https://stacker.news/items/760645 @ eac63075:b4988b48
2024-11-09 17:57:27*Based on a recent paper that included collaboration from renowned experts such as [Lynn Alden](nostr:nprofile1qyt8wumn8ghj7un9d3shjtntv9khqtnnd96x2tcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtcqyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057nwgm4w), [Steve Lee](https://x.com/moneyball), and [Ren Crypto Fish](https://twitter.com/0xren_cf), we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.* [PT-BR version](https://www.eddieoz.com/consenso-no-bitcoin-como-a-rede-evolui-sem-comprometer-a-seguranca/) **Podcast** https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC **Presentation** https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn ### 1. Introduction to Consensus in Bitcoin Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability. The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network. **Evolution of Consensus in Bitcoin** Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators. Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization. --- ### 2. Technical Components of Consensus Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus. **Validation of Blocks and Transactions** The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts. Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules. **Chain Selection** Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one. This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus. **Soft Forks vs. Hard Forks** In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users: - **Soft Forks**: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division. - **Hard Forks**: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation. These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time. --- ### 3. Stakeholders in Bitcoin's Consensus Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus. **1. Economic Nodes** Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork. Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements. **2. Investors** Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development. Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change. **3. Media Influencers** Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process. On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus. **4. Miners** Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary. Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable. **5. Protocol Developers** Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders. Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles. **6. Users and Application Developers** This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem. If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications. These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin. --- ### 4. Mechanisms for Activating Updates in Bitcoin For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates. **Flag Day** The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block. - **Advantages**: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date. - **Disadvantages**: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update. An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues. **BIP34 and BIP9** BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change. - **Advantages**: Allows the network to activate updates gradually, giving more time for participants to adapt. - **Disadvantages**: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented. BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms. **User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)** To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network. URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes. - **Advantages**: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners. - **Disadvantages**: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders. An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption. **BIP8 (LOT=True)** BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated. - **Advantages**: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo. - **Disadvantages**: Can lead to network splits if miners or other important stakeholders do not support the update. Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary. These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion. --- ### 5. Risks and Considerations in Consensus Updates Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders. **Network Fragility with Alternative Implementations** One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors. Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset. **Chain Splits and Impact on Stakeholders** Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors. Each group of stakeholders reacts differently to a chain split: - **Institutional Investors and ETFs**: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints. - **Miners**: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks. - **Economic Nodes**: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network. Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value. **Regulatory Impacts and Institutional Investors** With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus. Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors. **Security Considerations in Soft Forks and Hard Forks** While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules. In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network. **Bounty Claim Risks and Attack Scenarios** Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards. These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability. The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders. --- ### 6. Recommendations for the Consensus Process in Bitcoin To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation. **1. Careful Evaluation of Proposal Maturity** Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts. **2. Extensive Testing in Secure and Compatible Networks** Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin. The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network. **3. Importance of Stakeholder Engagement** The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability. **4. Key Questions for Evaluating Consensus Proposals** To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change: - Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability? - Does it maintain backward compatibility or introduce the risk of network split? - Are the implementation requirements clear and feasible for each group involved? - Are there clear and aligned incentives for all stakeholder groups to accept the change? **5. Coordination and Timing in Implementations** Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation. Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure. **6. Continuous Monitoring and Re-evaluation** After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network. These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network. --- ### 7. Conclusion Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant. Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network. Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability. By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience. --- ### 8. Links Whitepaper: https://github.com/bitcoin-cap/bcap Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
@ eac63075:b4988b48
2024-11-09 17:57:27*Based on a recent paper that included collaboration from renowned experts such as [Lynn Alden](nostr:nprofile1qyt8wumn8ghj7un9d3shjtntv9khqtnnd96x2tcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtcqyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057nwgm4w), [Steve Lee](https://x.com/moneyball), and [Ren Crypto Fish](https://twitter.com/0xren_cf), we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.* [PT-BR version](https://www.eddieoz.com/consenso-no-bitcoin-como-a-rede-evolui-sem-comprometer-a-seguranca/) **Podcast** https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC **Presentation** https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn ### 1. Introduction to Consensus in Bitcoin Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability. The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network. **Evolution of Consensus in Bitcoin** Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators. Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization. --- ### 2. Technical Components of Consensus Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus. **Validation of Blocks and Transactions** The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts. Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules. **Chain Selection** Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one. This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus. **Soft Forks vs. Hard Forks** In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users: - **Soft Forks**: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division. - **Hard Forks**: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation. These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time. --- ### 3. Stakeholders in Bitcoin's Consensus Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus. **1. Economic Nodes** Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork. Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements. **2. Investors** Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development. Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change. **3. Media Influencers** Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process. On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus. **4. Miners** Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary. Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable. **5. Protocol Developers** Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders. Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles. **6. Users and Application Developers** This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem. If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications. These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin. --- ### 4. Mechanisms for Activating Updates in Bitcoin For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates. **Flag Day** The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block. - **Advantages**: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date. - **Disadvantages**: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update. An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues. **BIP34 and BIP9** BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change. - **Advantages**: Allows the network to activate updates gradually, giving more time for participants to adapt. - **Disadvantages**: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented. BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms. **User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)** To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network. URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes. - **Advantages**: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners. - **Disadvantages**: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders. An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption. **BIP8 (LOT=True)** BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated. - **Advantages**: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo. - **Disadvantages**: Can lead to network splits if miners or other important stakeholders do not support the update. Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary. These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion. --- ### 5. Risks and Considerations in Consensus Updates Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders. **Network Fragility with Alternative Implementations** One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors. Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset. **Chain Splits and Impact on Stakeholders** Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors. Each group of stakeholders reacts differently to a chain split: - **Institutional Investors and ETFs**: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints. - **Miners**: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks. - **Economic Nodes**: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network. Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value. **Regulatory Impacts and Institutional Investors** With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus. Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors. **Security Considerations in Soft Forks and Hard Forks** While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules. In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network. **Bounty Claim Risks and Attack Scenarios** Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards. These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability. The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders. --- ### 6. Recommendations for the Consensus Process in Bitcoin To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation. **1. Careful Evaluation of Proposal Maturity** Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts. **2. Extensive Testing in Secure and Compatible Networks** Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin. The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network. **3. Importance of Stakeholder Engagement** The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability. **4. Key Questions for Evaluating Consensus Proposals** To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change: - Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability? - Does it maintain backward compatibility or introduce the risk of network split? - Are the implementation requirements clear and feasible for each group involved? - Are there clear and aligned incentives for all stakeholder groups to accept the change? **5. Coordination and Timing in Implementations** Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation. Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure. **6. Continuous Monitoring and Re-evaluation** After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network. These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network. --- ### 7. Conclusion Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant. Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network. Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability. By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience. --- ### 8. Links Whitepaper: https://github.com/bitcoin-cap/bcap Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb @ 35f3a26c:92ddf231
2024-11-09 17:10:57## "Files" by Google new feature "Files" by Google added a "feature"... "Smart Search", you can toggle it to OFF and it is highly recommended to do so. -  Toggle the Smart Search to OFF, otherwise, google will search and index every picture, video and document in your device, no exceptions, anything you have ever photographed and you forgot, any document you have downloaded or article, etc... ## How this could affect you? Google is actively combating child abuse and therefore it has built in its "AI" a very aggressive algorithm searching of material that "IT THINKS" is related, therefore the following content could be flagged: - [ ] Pictures of you and your children in the beach - [ ] Pictures or videos which are innocent in nature but the "AI" "thinks" are not - [ ] Articles you may have save for research to write your next essay that have links to flagged information or sites ***The results:*** - [ ] Your google account will be canceled - [ ] You will be flagged as a criminal across the digital world You think this is non sense? Think again: https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html ## How to switch it off: 1. Open files by Google 2. Tap on Menu -> Settings 3. Turn OFF Smart Search ## But you can do more for your privacy and the security of your family 1. Stop using google apps, if possible get rid off of Google OS and use Graphene OS 2. Go to Settings -> Apps 3. Search for Files by Google 4. Unistall the app, if you can't disable it 5. Keep doing that with most Google apps that are not a must if you have not switched already to GrapheneOS ***Remember, Google keeps advocating for privacy, but as many others have pointed out repeatedly, they are the first ones lobbying for the removal of your privacy by regulation and draconian laws, their hypocrisy knows no limits*** ## Recommendation: I would assume you have installed F-Droid in your android, or Obtainium if you are more advanced, if so, consider "Simple File Manager Pro" by Tibor Kaputa, this dev has a suite of apps that are basic needs and the best feature in my opinion is that not one of his apps connect to the internet, contacts, gallery, files, phone, etc. -  > Note > As most people, we all love the convenience of technology, it makes our lives easier, however, our safety and our family safety should go first, between technology being miss-used and abused by corporations and cyber-criminals data mining and checking for easy targets to attack for profit, we need to keep our guard up. Learning is key, resist the use of new tech if you do not understand the privacy trade offs, no matter how appealing and convenient it looks like. . ***Please leave your comments with your favorite FOSS Files app!***
@ 35f3a26c:92ddf231
2024-11-09 17:10:57## "Files" by Google new feature "Files" by Google added a "feature"... "Smart Search", you can toggle it to OFF and it is highly recommended to do so. -  Toggle the Smart Search to OFF, otherwise, google will search and index every picture, video and document in your device, no exceptions, anything you have ever photographed and you forgot, any document you have downloaded or article, etc... ## How this could affect you? Google is actively combating child abuse and therefore it has built in its "AI" a very aggressive algorithm searching of material that "IT THINKS" is related, therefore the following content could be flagged: - [ ] Pictures of you and your children in the beach - [ ] Pictures or videos which are innocent in nature but the "AI" "thinks" are not - [ ] Articles you may have save for research to write your next essay that have links to flagged information or sites ***The results:*** - [ ] Your google account will be canceled - [ ] You will be flagged as a criminal across the digital world You think this is non sense? Think again: https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html ## How to switch it off: 1. Open files by Google 2. Tap on Menu -> Settings 3. Turn OFF Smart Search ## But you can do more for your privacy and the security of your family 1. Stop using google apps, if possible get rid off of Google OS and use Graphene OS 2. Go to Settings -> Apps 3. Search for Files by Google 4. Unistall the app, if you can't disable it 5. Keep doing that with most Google apps that are not a must if you have not switched already to GrapheneOS ***Remember, Google keeps advocating for privacy, but as many others have pointed out repeatedly, they are the first ones lobbying for the removal of your privacy by regulation and draconian laws, their hypocrisy knows no limits*** ## Recommendation: I would assume you have installed F-Droid in your android, or Obtainium if you are more advanced, if so, consider "Simple File Manager Pro" by Tibor Kaputa, this dev has a suite of apps that are basic needs and the best feature in my opinion is that not one of his apps connect to the internet, contacts, gallery, files, phone, etc. -  > Note > As most people, we all love the convenience of technology, it makes our lives easier, however, our safety and our family safety should go first, between technology being miss-used and abused by corporations and cyber-criminals data mining and checking for easy targets to attack for profit, we need to keep our guard up. Learning is key, resist the use of new tech if you do not understand the privacy trade offs, no matter how appealing and convenient it looks like. . ***Please leave your comments with your favorite FOSS Files app!*** @ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492 @ 5d4b6c8d:8a1c1ee3
2024-11-09 15:00:44The wife and I were drinking our coffee, while a fair bit of commotion was coming from our daughter in the bathroom. She came out and very shyly said "'Scuse me." We've been working with her on manners and not interrupting, so this was very encouraging. She continued very sweetly, "There's a pwoblem in the potty." That was decidedly less encouraging. originally posted at https://stacker.news/items/760318
@ 5d4b6c8d:8a1c1ee3
2024-11-09 15:00:44The wife and I were drinking our coffee, while a fair bit of commotion was coming from our daughter in the bathroom. She came out and very shyly said "'Scuse me." We've been working with her on manners and not interrupting, so this was very encouraging. She continued very sweetly, "There's a pwoblem in the potty." That was decidedly less encouraging. originally posted at https://stacker.news/items/760318 @ 72592ec9:ffa64d2c
2024-11-09 11:00:37Really good read so far, thought I'd share this part from https://bitcoindevphilosophy.com/ > It seems that we can’t have a decentralized system based on trust, and that’s why trustlessness is important in Bitcoin. > > To use Bitcoin in a trustless manner, you have to run a fully-validating Bitcoin node. Only then will you be able to verify that the blocks you receive from others are following the consensus rules; for example, that the coin issuance schedule is kept and that no double-spends occur on the blockchain. If you don’t run a full node, you outsource verification of Bitcoin blocks to someone else and trust them to tell you the truth, which means you’re not using Bitcoin trustlessly. > > Diagram > David Harding has authored an article on the bitcoin.org website explaining how running a full node - or using Bitcoin trustlessly - actually helps you. > > The bitcoin currency only works when people accept bitcoins in exchange for other valuable things. That means it’s the people accepting bitcoins who give it value and who get to decide how Bitcoin should work. > > When you accept bitcoins, you have the power to enforce Bitcoin’s rules, such as preventing confiscation of any person’s bitcoins without access to that person’s private keys. > > Unfortunately, many users outsource their enforcement power. This leaves Bitcoin’s decentralization in a weakened state where a handful of miners can collude with a handful of banks and free services to change Bitcoin’s rules for all those non-verifying users who outsourced their power. > > Unlike other wallets, Bitcoin Core does enforce the rules—so if the miners and banks change the rules for their non-verifying users, those users will be unable to pay full validation Bitcoin Core users like you. > > — David Harding > Full Validation on bitcoin.org (2015) > He says that running a full node will help you verify every aspect of the blockchain without trusting anyone else, so as to ensure that the coins you receive from others are genuine. This is great, but there’s one important thing that a full node can’t help you with: it can’t prevent double- spending through chain rewrites: > > Note that although all programs—including Bitcoin Core—are vulnerable to chain rewrites, Bitcoin provides a defense mechanism: the more confirmations your transactions have, the safer you are. There is no known decentralized defense better than that. > > — David Harding > Full Validation on bitcoin.org (2015) > No matter how advanced your software is, you still have to trust that the blocks containing your coins won’t be rewritten. However, as pointed out by Harding, you can await a number of confirmations, after which you consider the probability of a chain rewrite small enough to be acceptable. > > The incentives for using Bitcoin in a trustless way align with the system’s need for full node decentralization. The more people who use their own full nodes, the more full node decentralization, and thus the stronger Bitcoin stands against malicious changes to the protocol. But unfortunately, as explained in the full node decentralization section, users often opt for trusted services as consequence of the inevitable trade-off between trustlessness and convenience. originally posted at https://stacker.news/items/760051
@ 72592ec9:ffa64d2c
2024-11-09 11:00:37Really good read so far, thought I'd share this part from https://bitcoindevphilosophy.com/ > It seems that we can’t have a decentralized system based on trust, and that’s why trustlessness is important in Bitcoin. > > To use Bitcoin in a trustless manner, you have to run a fully-validating Bitcoin node. Only then will you be able to verify that the blocks you receive from others are following the consensus rules; for example, that the coin issuance schedule is kept and that no double-spends occur on the blockchain. If you don’t run a full node, you outsource verification of Bitcoin blocks to someone else and trust them to tell you the truth, which means you’re not using Bitcoin trustlessly. > > Diagram > David Harding has authored an article on the bitcoin.org website explaining how running a full node - or using Bitcoin trustlessly - actually helps you. > > The bitcoin currency only works when people accept bitcoins in exchange for other valuable things. That means it’s the people accepting bitcoins who give it value and who get to decide how Bitcoin should work. > > When you accept bitcoins, you have the power to enforce Bitcoin’s rules, such as preventing confiscation of any person’s bitcoins without access to that person’s private keys. > > Unfortunately, many users outsource their enforcement power. This leaves Bitcoin’s decentralization in a weakened state where a handful of miners can collude with a handful of banks and free services to change Bitcoin’s rules for all those non-verifying users who outsourced their power. > > Unlike other wallets, Bitcoin Core does enforce the rules—so if the miners and banks change the rules for their non-verifying users, those users will be unable to pay full validation Bitcoin Core users like you. > > — David Harding > Full Validation on bitcoin.org (2015) > He says that running a full node will help you verify every aspect of the blockchain without trusting anyone else, so as to ensure that the coins you receive from others are genuine. This is great, but there’s one important thing that a full node can’t help you with: it can’t prevent double- spending through chain rewrites: > > Note that although all programs—including Bitcoin Core—are vulnerable to chain rewrites, Bitcoin provides a defense mechanism: the more confirmations your transactions have, the safer you are. There is no known decentralized defense better than that. > > — David Harding > Full Validation on bitcoin.org (2015) > No matter how advanced your software is, you still have to trust that the blocks containing your coins won’t be rewritten. However, as pointed out by Harding, you can await a number of confirmations, after which you consider the probability of a chain rewrite small enough to be acceptable. > > The incentives for using Bitcoin in a trustless way align with the system’s need for full node decentralization. The more people who use their own full nodes, the more full node decentralization, and thus the stronger Bitcoin stands against malicious changes to the protocol. But unfortunately, as explained in the full node decentralization section, users often opt for trusted services as consequence of the inevitable trade-off between trustlessness and convenience. originally posted at https://stacker.news/items/760051 @ 5d4b6c8d:8a1c1ee3
2024-11-09 04:02:26As always, we're going to lead off with the on-going contests at ~Stacker_Sports. @BlokchainB requested some NHL coverage, so @grayruby is going to try to explain hockey to me. We'll check in on the NFL post trade deadline and see if the landscape shifted appreciably. Also, we had a requested topic on why the top picks of the past two drafts are paling in comparison to the guys taken immediately after them. Tune is as we flounder for answers. We had some disagreements on our hastily slapped together [NBA power rankings](https://stacker.news/items/757639/r/Undisciplined), so we'll have to hash those out. Thankfully, @BlokchainB has already confirmed that mine were better. Then I wanted to talk about [Predyx](https://beta.predyx.com/market) in a little more detail, because they're on Stacker News and their project is very cool. I'm sure we'll cover our other gambling (mis)adventures. What say you about any of those topics? Are there other topics you want our thoughts on? The Stacker Sports Pod is for stackers by stackers. originally posted at https://stacker.news/items/759836
@ 5d4b6c8d:8a1c1ee3
2024-11-09 04:02:26As always, we're going to lead off with the on-going contests at ~Stacker_Sports. @BlokchainB requested some NHL coverage, so @grayruby is going to try to explain hockey to me. We'll check in on the NFL post trade deadline and see if the landscape shifted appreciably. Also, we had a requested topic on why the top picks of the past two drafts are paling in comparison to the guys taken immediately after them. Tune is as we flounder for answers. We had some disagreements on our hastily slapped together [NBA power rankings](https://stacker.news/items/757639/r/Undisciplined), so we'll have to hash those out. Thankfully, @BlokchainB has already confirmed that mine were better. Then I wanted to talk about [Predyx](https://beta.predyx.com/market) in a little more detail, because they're on Stacker News and their project is very cool. I'm sure we'll cover our other gambling (mis)adventures. What say you about any of those topics? Are there other topics you want our thoughts on? The Stacker Sports Pod is for stackers by stackers. originally posted at https://stacker.news/items/759836 @ bcea2b98:7ccef3c9
2024-11-09 01:30:29@chess h3 originally posted at https://stacker.news/items/759635
@ bcea2b98:7ccef3c9
2024-11-09 01:30:29@chess h3 originally posted at https://stacker.news/items/759635 @ b4403b24:83542d4e
2024-11-08 22:34:45 Imagine what will be in the upcoming years if this trend continues. Bullish 🚀🌕 originally posted at https://stacker.news/items/759487
@ b4403b24:83542d4e
2024-11-08 22:34:45 Imagine what will be in the upcoming years if this trend continues. Bullish 🚀🌕 originally posted at https://stacker.news/items/759487 @ 5d4b6c8d:8a1c1ee3
2024-11-08 13:59:13@Coffee proposed a topic for [The Stacker Sports Podcast](https://fountain.fm/show/syQHHkLs59GQ1eFAe64t) on our nostr thread and I wanted to share it here. Why have the top picks in the past two drafts (Bryce Young and Caleb Williams) been so significantly outplayed by the players taken immediately after them (CJ Stroud and Jayden Daniels)? It's early in the careers of each of these players, but Stroud and Daniels are already looking like MVP caliber franchise QB's. Why did teams miss this? The most obvious hypothesis (that the Bears and Panthers flubbed their picks) doesn't make much sense, because Young and Williams were the consensus top picks in their drafts. A bigger question is why it's so difficult to spot an MVP caliber QB from their college play. originally posted at https://stacker.news/items/758917
@ 5d4b6c8d:8a1c1ee3
2024-11-08 13:59:13@Coffee proposed a topic for [The Stacker Sports Podcast](https://fountain.fm/show/syQHHkLs59GQ1eFAe64t) on our nostr thread and I wanted to share it here. Why have the top picks in the past two drafts (Bryce Young and Caleb Williams) been so significantly outplayed by the players taken immediately after them (CJ Stroud and Jayden Daniels)? It's early in the careers of each of these players, but Stroud and Daniels are already looking like MVP caliber franchise QB's. Why did teams miss this? The most obvious hypothesis (that the Bears and Panthers flubbed their picks) doesn't make much sense, because Young and Williams were the consensus top picks in their drafts. A bigger question is why it's so difficult to spot an MVP caliber QB from their college play. originally posted at https://stacker.news/items/758917 @ c11cf5f8:4928464d
2024-11-08 13:31:22The Magnificent 7:  Here we are again with our monthly [Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times) summary, trying to give you a hit of what you missed this month in the ~AGORA territory. - - - ### Top-Performing Ads This month, the most zapranked ones are: * `01` [[OFFER] IPv4+IPv6 KVM VPS, from 1.75EUR/month (Stockholm/SE SWEDEN)](https://stacker.news/items/750336/r/AG) by @skhron * `02` [[SWAP] SN Cowboy credits](https://stacker.news/items/723069/r/AG) by @DarthCoin * `03` [[SELL] “NO⚡️TR T-Shirt” for 21K sats](https://stacker.news/items/730098/r/AG) by @thebullishbitcoiner * `04` [[sell] iptv subscription 10k+ live tv channels and 20k+ vod (tv/movies)](https://stacker.news/items/730963/r/AG) by @profullstack This month we ran short, so here other 3 from previous month * `05` [[SELL] StackerNews Archived Territories - Your chance to own a piece of history!](https://stacker.news/items/698471/r/AG) by @Design_r * `06` [[SELL] Stickers for Stackers! SN Nostr Badges vinyl stickers - from 3,456 sats](https://stacker.news/items/711431/r/AG) by @AGORA * `07` [[SELL] 3 WishMesh Meshtastic radios and 2 extended antennas 325,000 SATS](https://stacker.news/items/710750/r/AG) by @fe3c522a6f - - - ###### In case you missed Here some interesting post opening conversation and free speech: @supratic share some interesting tools for merchants and businesses: - https://stacker.news/items/745053/r/AG TinyPine: A simple LN and CASHU ecash POS system for merchants - https://stacker.news/items/750705/r/AG PLEBEIAN – Simple, Anonymous & Free Market for Everyone And here some more insights on how to do business in the private: - https://stacker.news/items/732291/r/AG Classifieds vs. Listings: Navigating Nostr Protocol's Approach to Advertising by @AGORA - https://stacker.news/items/742973/r/AG The Watchman Privacy Podcast – Escape the Servile Society with Vonu by @mo - https://stacker.news/items/746325/r/AG How to Operate a Business in the Private with Trust by @mo - https://stacker.news/items/741906/r/AG Paying out debt and bills using the Bills of Exchange act by @supratic - https://stacker.news/items/751074/r/AG The Separation of Business and State by @mo - https://stacker.news/items/718979/r/AG Mystery Paper: Ancient Merchant Paper, For Merchants Only & Corporate Countries by @AGORA - https://stacker.news/items/720288/r/AG Parallel Society • Free Man's Perspective by @DarthCoin ###### 🏷️ Spending Sunday is back! Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! Read more https://stacker.news/items/721244/r/AG - - - ###### Just a reminder for you all This territory aims to connect stackers and curious buyers for IRL P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it! To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting. - - - ### Create your Ads now!  Looking to start something new? Hit one of the links below to free your mind: * [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation, * [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or, * if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)! * [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners * [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats * [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item * [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else * [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift! * [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to - - - Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we can help you publish a personalized post. Coinomi Bitcoin Testnet skull quantum digital allow faculty enforce spatial emotion fun candy plunge stick stairs salad dish pass fix between shock scene ivory cargo unhappy fault originally posted at https://stacker.news/items/758878
@ c11cf5f8:4928464d
2024-11-08 13:31:22The Magnificent 7:  Here we are again with our monthly [Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times) summary, trying to give you a hit of what you missed this month in the ~AGORA territory. - - - ### Top-Performing Ads This month, the most zapranked ones are: * `01` [[OFFER] IPv4+IPv6 KVM VPS, from 1.75EUR/month (Stockholm/SE SWEDEN)](https://stacker.news/items/750336/r/AG) by @skhron * `02` [[SWAP] SN Cowboy credits](https://stacker.news/items/723069/r/AG) by @DarthCoin * `03` [[SELL] “NO⚡️TR T-Shirt” for 21K sats](https://stacker.news/items/730098/r/AG) by @thebullishbitcoiner * `04` [[sell] iptv subscription 10k+ live tv channels and 20k+ vod (tv/movies)](https://stacker.news/items/730963/r/AG) by @profullstack This month we ran short, so here other 3 from previous month * `05` [[SELL] StackerNews Archived Territories - Your chance to own a piece of history!](https://stacker.news/items/698471/r/AG) by @Design_r * `06` [[SELL] Stickers for Stackers! SN Nostr Badges vinyl stickers - from 3,456 sats](https://stacker.news/items/711431/r/AG) by @AGORA * `07` [[SELL] 3 WishMesh Meshtastic radios and 2 extended antennas 325,000 SATS](https://stacker.news/items/710750/r/AG) by @fe3c522a6f - - - ###### In case you missed Here some interesting post opening conversation and free speech: @supratic share some interesting tools for merchants and businesses: - https://stacker.news/items/745053/r/AG TinyPine: A simple LN and CASHU ecash POS system for merchants - https://stacker.news/items/750705/r/AG PLEBEIAN – Simple, Anonymous & Free Market for Everyone And here some more insights on how to do business in the private: - https://stacker.news/items/732291/r/AG Classifieds vs. Listings: Navigating Nostr Protocol's Approach to Advertising by @AGORA - https://stacker.news/items/742973/r/AG The Watchman Privacy Podcast – Escape the Servile Society with Vonu by @mo - https://stacker.news/items/746325/r/AG How to Operate a Business in the Private with Trust by @mo - https://stacker.news/items/741906/r/AG Paying out debt and bills using the Bills of Exchange act by @supratic - https://stacker.news/items/751074/r/AG The Separation of Business and State by @mo - https://stacker.news/items/718979/r/AG Mystery Paper: Ancient Merchant Paper, For Merchants Only & Corporate Countries by @AGORA - https://stacker.news/items/720288/r/AG Parallel Society • Free Man's Perspective by @DarthCoin ###### 🏷️ Spending Sunday is back! Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! Read more https://stacker.news/items/721244/r/AG - - - ###### Just a reminder for you all This territory aims to connect stackers and curious buyers for IRL P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it! To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting. - - - ### Create your Ads now!  Looking to start something new? Hit one of the links below to free your mind: * [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation, * [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or, * if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)! * [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners * [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats * [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item * [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else * [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift! * [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to - - - Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we can help you publish a personalized post. Coinomi Bitcoin Testnet skull quantum digital allow faculty enforce spatial emotion fun candy plunge stick stairs salad dish pass fix between shock scene ivory cargo unhappy fault originally posted at https://stacker.news/items/758878 @ b4403b24:83542d4e
2024-11-08 13:03:32I recently came across a funny Star Wars themed meme which I couldn't resist to post here with a message @DarthCoin vs no/shit coiners  **P.S.:** Sorry in advance if some of you find it as disturbing or vulgar originally posted at https://stacker.news/items/758857
@ b4403b24:83542d4e
2024-11-08 13:03:32I recently came across a funny Star Wars themed meme which I couldn't resist to post here with a message @DarthCoin vs no/shit coiners  **P.S.:** Sorry in advance if some of you find it as disturbing or vulgar originally posted at https://stacker.news/items/758857 @ b4403b24:83542d4e
2024-11-08 11:46:54To my great surprise, when I checked my SN notification feed today, I found out 👇  To be honest, I don't know what I did to earn it, what it means or gives me or whether I can loose it (similar to the cowboy's hat maybe @k00b can give more insights) but I am pretty satisfied adding it under my belt. 🎉 I'll keep my activity high hoping I'll find the other cowboy collectible I miss - the pistol  originally posted at https://stacker.news/items/758749
@ b4403b24:83542d4e
2024-11-08 11:46:54To my great surprise, when I checked my SN notification feed today, I found out 👇  To be honest, I don't know what I did to earn it, what it means or gives me or whether I can loose it (similar to the cowboy's hat maybe @k00b can give more insights) but I am pretty satisfied adding it under my belt. 🎉 I'll keep my activity high hoping I'll find the other cowboy collectible I miss - the pistol  originally posted at https://stacker.news/items/758749 @ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
@ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart. @ eac63075:b4988b48
2024-11-07 21:27:53Every night, you draw your curtains without thinking twice. It's instinctive—a simple act that protects your personal space. Yet in our digital lives, we've somehow accepted living in houses made entirely of glass, with countless unseen observers watching our every move. https://www.fountain.fm/episode/wPZLCJ3fD6vzsWQ3XSE1 ## Why Privacy Matters to Everyone Privacy isn't just for those with something to hide; it's a fundamental human need. Think about the conversations you have with friends, the late-night web searches you make, the personal moments you capture in photos. Would you want all of that broadcasted to the world? I remember my friend Lisa planning a surprise party for her husband. She searched for gift ideas and coordinated with friends through social media. To her dismay, targeted ads for the exact gift she intended to buy started popping up on their shared devices at home. The surprise was ruined. It wasn't malicious, but it was a stark reminder of how our online activities are constantly monitored. When a major retailer's customer database was breached, my neighbor Sarah discovered her shopping history, credit card details, and even her children's names were exposed to criminals. She hadn't realized how much personal information she'd unknowingly shared through routine purchases. It was a wake-up call that privacy breaches can affect anyone, not just the tech-savvy or those in high-profile positions. Edward Snowden once said, **"Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say."** Privacy isn't about secrecy; it's about autonomy over our personal information. ## The Rise of the Cypherpunks Back in the '90s, a group known as the cypherpunks saw the writing on the wall. They recognized that as we moved into a digital era, our personal freedoms could be at risk. So they took action. One of them, Eric Hughes, famously wrote, **"Privacy is necessary for an open society in the electronic age."** They developed encryption tools to protect individual privacy, laying the groundwork for technologies like Bitcoin and cryptocurrencies. These innovations were about more than digital money; they were about empowering individuals to take control of their own data. ## When Technology Knows Too Much Fast forward to today, and artificial intelligence (AI) is everywhere—in our phones, homes, and even cars. While AI brings convenience, it also raises serious privacy concerns. Remember when you mentioned needing new running shoes, and suddenly every ad on your browser was for footwear? It's not your imagination. AI algorithms analyze our conversations, searches, and purchases to predict what we'll want next. But where does it stop? A few years ago, a major retailer guessed a teenager was pregnant based on her shopping habits before she had told her family. They sent her targeted coupons for baby products, leading to a very uncomfortable situation at home. This isn't just marketing—it's intrusion. Naomi Brockwell, a privacy advocate, [warns](https://x.com/naomibrockwell/status/1833055298288058624), **"Our relationship with financial privacy has fundamentally changed. What was once seen as a constitutional right and personal freedom is now simply part of the trade-off for using digital payments. Our baseline for what’s acceptable has shifted."** It's a wake-up call that our digital footprints are larger and more revealing than we might think. ### Privacy-Preserving AI While AI often threatens privacy, emerging technologies like **federated learning** offer hope. This approach allows AI models to learn from data without directly accessing personal information. Imagine your phone improving its predictive text without sending your messages to a central server. It's AI that respects your privacy. ## The Watchful Eye: Mass Surveillance and AI Governments and corporations often justify mass surveillance as a means to keep us safe. But at what cost? When every email, message, or phone call can be monitored, we're sacrificing more than just data—we're giving up our freedom to think and communicate without fear. Think about how you'd behave if someone followed you around with a camera all day. You might avoid certain places or people, censor your conversations, or feel constantly on edge. That's the chilling effect of mass surveillance. I spoke with Alex, a journalist who covers political activism. "After attending a peaceful protest, I noticed unusual activity on my devices," he told me. "It made me second-guess my work, wondering who's watching." This isn't paranoia; it's a reality for many who challenge the status quo. ## Building Digital Fortresses: Cryptographic Innovations So how do we reclaim our privacy? Cryptography offers some solutions. ### Zero-Knowledge Proofs: Proving Without Revealing **Zero-knowledge proofs** allow you to prove you know something without revealing the actual information. Imagine showing a bouncer a card that confirms you're over 21 without exposing your birth date or any other details. In the digital world, this means verifying your identity or eligibility without handing over all your personal data. ### Homomorphic Encryption: Secure Processing Then there's **homomorphic encryption**, which lets companies process your data without actually seeing it. Think of it like sending a locked suitcase with your belongings; they can weigh it or move it, but they can't open it to see what's inside. ### Quantum-Resistant Algorithms: Future-Proofing Privacy As quantum computers become more powerful, they could potentially break current encryption methods. **Quantum-resistant algorithms** are being developed to safeguard our data against these future threats. It's like reinforcing your digital locks today to withstand the super lock-picking tools of tomorrow. ## Decentralization: Taking Back Control Decentralization aims to put power back into the hands of individuals. Bitcoin let you be your own bank, controlling your finances without a middleman. Decentralized social media platforms like Nostr, Bluesky or Fascaster allow you to own your content without algorithms dictating what you see or who sees you. ### Decentralized Identity Systems **Decentralized identity systems** let you prove who you are without revealing more than necessary. It's like showing only your age at a bar instead of handing over your entire driver's license. You maintain control over your personal information. But with great power comes great responsibility. Without a bank to reset your password or customer service to recover your account, the onus is on you to protect your assets and information. ## Practical Tips to Protect Your Privacy You don't have to be a tech guru to safeguard your privacy. Here are some steps you can take today: - **Use Encrypted Messaging Apps**: Switch to apps like **Signal, SimpleX or Session** for secure communication. Your messages will be end-to-end encrypted, meaning only you and the recipient can read them. - **Limit Social Media Sharing**: Be mindful of what you post. Do you really need to share your location or personal details publicly? - **Choose Privacy-Focused Browsers and Search Engines**: Use browsers like **Brave** or **Firefox** and search engines like **DuckDuckGo** that don't track your every move. - **Secure Your Passwords**: Use strong, unique passwords for each account, and consider a password manager like **Bitwarden**. Enable two-factor authentication whenever possible. - **Use Encrypted Email Services**: Consider email providers like **ProtonMail** that offer end-to-end encryption for your communications. - **Regularly Audit App Permissions**: Check which apps have access to your location, microphone, and contacts. Revoke permissions that aren't necessary. - **Be Wary of Public Wi-Fi**: Public networks can be a hotbed for hackers. If you must use them, a VPN like **ProtonVPN** can add a layer of security. - **Consider Privacy-Focused Alternatives**: Explore services like **Nextcloud** for cloud storage or **Jitsi Meet** for video conferencing, which prioritize user privacy. - **Keep Software Updated**: Regular updates often include security patches. Don't ignore them. - **Stay Informed and Skeptical**: Phishing scams are getting more sophisticated. Think before you click on suspicious links or download attachments. ## Final Thoughts Privacy isn't a lost cause; it's a right worth fighting for. As Edward Snowden reminds us, **"Privacy is the fountainhead of all other rights."** By taking control of our data and digital habits, we can navigate the online world with greater confidence and peace of mind. After all, wouldn't it be nice to live in a digital home where we decide when to close the curtains? ## Read more **OPSEC and Digital Hygiene Plan:** <https://www.eddieoz.com/opsec-and-digital-hygiene-plan/>
@ eac63075:b4988b48
2024-11-07 21:27:53Every night, you draw your curtains without thinking twice. It's instinctive—a simple act that protects your personal space. Yet in our digital lives, we've somehow accepted living in houses made entirely of glass, with countless unseen observers watching our every move. https://www.fountain.fm/episode/wPZLCJ3fD6vzsWQ3XSE1 ## Why Privacy Matters to Everyone Privacy isn't just for those with something to hide; it's a fundamental human need. Think about the conversations you have with friends, the late-night web searches you make, the personal moments you capture in photos. Would you want all of that broadcasted to the world? I remember my friend Lisa planning a surprise party for her husband. She searched for gift ideas and coordinated with friends through social media. To her dismay, targeted ads for the exact gift she intended to buy started popping up on their shared devices at home. The surprise was ruined. It wasn't malicious, but it was a stark reminder of how our online activities are constantly monitored. When a major retailer's customer database was breached, my neighbor Sarah discovered her shopping history, credit card details, and even her children's names were exposed to criminals. She hadn't realized how much personal information she'd unknowingly shared through routine purchases. It was a wake-up call that privacy breaches can affect anyone, not just the tech-savvy or those in high-profile positions. Edward Snowden once said, **"Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say."** Privacy isn't about secrecy; it's about autonomy over our personal information. ## The Rise of the Cypherpunks Back in the '90s, a group known as the cypherpunks saw the writing on the wall. They recognized that as we moved into a digital era, our personal freedoms could be at risk. So they took action. One of them, Eric Hughes, famously wrote, **"Privacy is necessary for an open society in the electronic age."** They developed encryption tools to protect individual privacy, laying the groundwork for technologies like Bitcoin and cryptocurrencies. These innovations were about more than digital money; they were about empowering individuals to take control of their own data. ## When Technology Knows Too Much Fast forward to today, and artificial intelligence (AI) is everywhere—in our phones, homes, and even cars. While AI brings convenience, it also raises serious privacy concerns. Remember when you mentioned needing new running shoes, and suddenly every ad on your browser was for footwear? It's not your imagination. AI algorithms analyze our conversations, searches, and purchases to predict what we'll want next. But where does it stop? A few years ago, a major retailer guessed a teenager was pregnant based on her shopping habits before she had told her family. They sent her targeted coupons for baby products, leading to a very uncomfortable situation at home. This isn't just marketing—it's intrusion. Naomi Brockwell, a privacy advocate, [warns](https://x.com/naomibrockwell/status/1833055298288058624), **"Our relationship with financial privacy has fundamentally changed. What was once seen as a constitutional right and personal freedom is now simply part of the trade-off for using digital payments. Our baseline for what’s acceptable has shifted."** It's a wake-up call that our digital footprints are larger and more revealing than we might think. ### Privacy-Preserving AI While AI often threatens privacy, emerging technologies like **federated learning** offer hope. This approach allows AI models to learn from data without directly accessing personal information. Imagine your phone improving its predictive text without sending your messages to a central server. It's AI that respects your privacy. ## The Watchful Eye: Mass Surveillance and AI Governments and corporations often justify mass surveillance as a means to keep us safe. But at what cost? When every email, message, or phone call can be monitored, we're sacrificing more than just data—we're giving up our freedom to think and communicate without fear. Think about how you'd behave if someone followed you around with a camera all day. You might avoid certain places or people, censor your conversations, or feel constantly on edge. That's the chilling effect of mass surveillance. I spoke with Alex, a journalist who covers political activism. "After attending a peaceful protest, I noticed unusual activity on my devices," he told me. "It made me second-guess my work, wondering who's watching." This isn't paranoia; it's a reality for many who challenge the status quo. ## Building Digital Fortresses: Cryptographic Innovations So how do we reclaim our privacy? Cryptography offers some solutions. ### Zero-Knowledge Proofs: Proving Without Revealing **Zero-knowledge proofs** allow you to prove you know something without revealing the actual information. Imagine showing a bouncer a card that confirms you're over 21 without exposing your birth date or any other details. In the digital world, this means verifying your identity or eligibility without handing over all your personal data. ### Homomorphic Encryption: Secure Processing Then there's **homomorphic encryption**, which lets companies process your data without actually seeing it. Think of it like sending a locked suitcase with your belongings; they can weigh it or move it, but they can't open it to see what's inside. ### Quantum-Resistant Algorithms: Future-Proofing Privacy As quantum computers become more powerful, they could potentially break current encryption methods. **Quantum-resistant algorithms** are being developed to safeguard our data against these future threats. It's like reinforcing your digital locks today to withstand the super lock-picking tools of tomorrow. ## Decentralization: Taking Back Control Decentralization aims to put power back into the hands of individuals. Bitcoin let you be your own bank, controlling your finances without a middleman. Decentralized social media platforms like Nostr, Bluesky or Fascaster allow you to own your content without algorithms dictating what you see or who sees you. ### Decentralized Identity Systems **Decentralized identity systems** let you prove who you are without revealing more than necessary. It's like showing only your age at a bar instead of handing over your entire driver's license. You maintain control over your personal information. But with great power comes great responsibility. Without a bank to reset your password or customer service to recover your account, the onus is on you to protect your assets and information. ## Practical Tips to Protect Your Privacy You don't have to be a tech guru to safeguard your privacy. Here are some steps you can take today: - **Use Encrypted Messaging Apps**: Switch to apps like **Signal, SimpleX or Session** for secure communication. Your messages will be end-to-end encrypted, meaning only you and the recipient can read them. - **Limit Social Media Sharing**: Be mindful of what you post. Do you really need to share your location or personal details publicly? - **Choose Privacy-Focused Browsers and Search Engines**: Use browsers like **Brave** or **Firefox** and search engines like **DuckDuckGo** that don't track your every move. - **Secure Your Passwords**: Use strong, unique passwords for each account, and consider a password manager like **Bitwarden**. Enable two-factor authentication whenever possible. - **Use Encrypted Email Services**: Consider email providers like **ProtonMail** that offer end-to-end encryption for your communications. - **Regularly Audit App Permissions**: Check which apps have access to your location, microphone, and contacts. Revoke permissions that aren't necessary. - **Be Wary of Public Wi-Fi**: Public networks can be a hotbed for hackers. If you must use them, a VPN like **ProtonVPN** can add a layer of security. - **Consider Privacy-Focused Alternatives**: Explore services like **Nextcloud** for cloud storage or **Jitsi Meet** for video conferencing, which prioritize user privacy. - **Keep Software Updated**: Regular updates often include security patches. Don't ignore them. - **Stay Informed and Skeptical**: Phishing scams are getting more sophisticated. Think before you click on suspicious links or download attachments. ## Final Thoughts Privacy isn't a lost cause; it's a right worth fighting for. As Edward Snowden reminds us, **"Privacy is the fountainhead of all other rights."** By taking control of our data and digital habits, we can navigate the online world with greater confidence and peace of mind. After all, wouldn't it be nice to live in a digital home where we decide when to close the curtains? ## Read more **OPSEC and Digital Hygiene Plan:** <https://www.eddieoz.com/opsec-and-digital-hygiene-plan/> @ bcea2b98:7ccef3c9
2024-11-07 18:43:30If you could accomplish one major goal, what would it be? Why does it matter to you, and how would it change your life or the lives of others? My ultimate goal is to be part of a mission to Mars one day. I’ve always been fascinated by space exploration. originally posted at https://stacker.news/items/757861
@ bcea2b98:7ccef3c9
2024-11-07 18:43:30If you could accomplish one major goal, what would it be? Why does it matter to you, and how would it change your life or the lives of others? My ultimate goal is to be part of a mission to Mars one day. I’ve always been fascinated by space exploration. originally posted at https://stacker.news/items/757861 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima. @ 74718b83:b8204bd8
2024-11-07 11:51:14Hi guys, i thought it would be interesting to compare some basic cost of living stats among stackers and ask, how hard is it to hit your basic number? for me, in Bulgaria with 2 kids , to be comfortable, NOT in the capital , about 2k euros is a number that works for my family. i could reduce that number by up to 1000 euro if my kids didn't go to a private school. also worth noting is i own the house so have no rent or mortgage. if i was renting or had a mortgage, i would simply pay that instead of doing private school, so the number would be similar. bills are cheap, maybe 10 euro water per month and about 40 euro electricity (this will vary though ) finding a job that pays 2k euros is quite hard outside of the capital city, even if you are a software programmer. i manage to hit this freelancing, and it's ok, i have a 10x higher lifestyle than i would in the UK and i own a property etc . the downside is a client will randomly leave etc and it puts a lot more strain on the budget, the upside is i am at least the master of my time, which i find very valuable originally posted at https://stacker.news/items/757311
@ 74718b83:b8204bd8
2024-11-07 11:51:14Hi guys, i thought it would be interesting to compare some basic cost of living stats among stackers and ask, how hard is it to hit your basic number? for me, in Bulgaria with 2 kids , to be comfortable, NOT in the capital , about 2k euros is a number that works for my family. i could reduce that number by up to 1000 euro if my kids didn't go to a private school. also worth noting is i own the house so have no rent or mortgage. if i was renting or had a mortgage, i would simply pay that instead of doing private school, so the number would be similar. bills are cheap, maybe 10 euro water per month and about 40 euro electricity (this will vary though ) finding a job that pays 2k euros is quite hard outside of the capital city, even if you are a software programmer. i manage to hit this freelancing, and it's ok, i have a 10x higher lifestyle than i would in the UK and i own a property etc . the downside is a client will randomly leave etc and it puts a lot more strain on the budget, the upside is i am at least the master of my time, which i find very valuable originally posted at https://stacker.news/items/757311 @ b184e3ed:27924b0d
2024-11-07 03:06:37When I joined AA, this question started to haunt my thoughts during those frequent nighttime anxiety attacks. Among all the chaos in my life, there were a few things I was certain of. And one of those things was the certainty of never having felt God, I didn't even know that God was something you could feel. For me, when I started the 12-step program, God was a social construct, something humans had invented to control a society thirsty for basic survival instincts. And perhaps I wasn't so wrong, but like everything in life, this was only half the truth. Despite my deep cognitive analysis that my anxiety forced me to do almost every night for hours, often until the first ray of sun pierced my bedroom window, my spiritual bias didn't allow me to see the whole picture, or a complete reality. On that side, there had always been a void Later, I realized that this emptiness was the main cause of all my problems. From there came that feeling of always being incomplete, that anxiety of always feeling like something was missing, that need to always want to fill voids that weren't mine, without realizing that it was only creating more emptiness within me Once, in those heart-to-heart talks that we in AA call sponsorship, my soul expressed the painful doubt, 'What does it mean to feel God?' My sponsor simply replied, 'I assure you that when you feel God, you won't doubt that what you feel is God. There is no doubt in matters of God. And so I left, with that answer that left me right where I started. And with more doubts. Why is there no doubt in matters of God? After thinking about it for so long, I paused for a few seconds. I closed my eyes and decided, for the first time, to talk to this so-called God. I let go of all my feelings, all my disbelief, and I prepared myself to accept anything different from what I already had, because what I had wasn't working for me at all. With all sincerity and feeling a pressure in my chest, closer to my heart than usual, I asked in a low voice God, what does it feel like to feel you? What should I do to feel you? What's the manual for feeling you? I've tried everything, I don't know what else to do, what else to plan. I accept that I need to feel you. Everyone tells me that when I feel you, everything will make sense and only then will I start to let go of this violent need to consume my drug of choice. But nobody tells me how. What am I not seeing? Please, give me something. I can't take it anymore, I'm running out of strength, I'm wasting my life stuck in the same cycle. I can't do this anymore, help me feel you. Then a pain began to flow, but a particular one that every addict knows, that soul-deep pain that comes from emptiness, that pain that turns on the faucet of tears that began to flow non-stop. I allowed myself to feel that pain, everything turned dark and negative, suicidal thoughts returned, hate, resentment, selfishness, depression, all together, all that is lived in darkness, all that is felt in solitude, all that came from emptiness. And only by feeling it, could I see where that deep pain came from, I could visualize the path it left behind. For the first time, I recognized my spiritual emptiness. And it was only then that I began to see the whole picture of my life. Doubt has no place in the things of God because God is not logic, God is not reason, much less a manual. Doubt comes from logic, therefore where there is doubt, there is also an absence of God, emptiness. And right at the moment of recognizing that, very specific images came to my mind. My sponsor hugging me for the first time when I arrived and interviewed me. With that hug came the words, 'You're not alone, you're already in a safe harbor, we'll be with you from start to finish. One day at a massive AA event, right in the middle of a workshop dynamic, that deep and sincere hug my fellow sufferer and I shared, in the midst of deep crying with our eyes closed, someone guided our arms to each other. To end up keeping each other company in that darkness we had always gone through alone. That trip to a Group Anniversary outside the city, where a fellow member of my group and I were simply enjoying the scenery, the wind on our faces, and laughing at the craziness of our daily lives, this on my motorcycle on the highway. That hug it took me years to find in the arms of my younger sister, right after arriving after a writing session. That hug of forgiveness to my mother and father that I had never been able to give before because I didn't want to go through the pain that came with feeling. Those few seconds in the rain that we spent lost on our way to the new location of our Group that I experienced in the company of a fellow member. Seeing a new person arrive with a desire to start their process. Connecting in the same feeling and emotion that comes with the death of a best friend. Serving a cup of coffee to that fellow member who returns after months of absence. Arriving at the group with hope of seeing that fellow member who hasn't been coming for weeks and little is known about what happened, but they no longer come to meetings. Day after day, their chair remains empty. And then start letting go of their defenses and their craziness. Standing in front of several strangers, with my head held high, my gaze firm, saying my name and then, 'I am a drug addict. To say, 'I feel like shit, but I'm here for whatever I can contribute. To feel like I'm that support for those who were my support when I was at rock bottom. And not just feel it, but also be able to be it. And that, to mention just a few of the scenes that came to my mind, then I understood 'I had already felt God.' I wasn't lacking spirituality, I wasn't lacking God, I just needed to stay still for a moment to feel it. And to feel that he has always been there. And that he will never leave my side. So today I can answer my own question, 'That's what it feels like to feel God' but not just any God. But a very special one, the God of the 4th and 5th step addicts and alcoholics... originally posted at https://stacker.news/items/756957
@ b184e3ed:27924b0d
2024-11-07 03:06:37When I joined AA, this question started to haunt my thoughts during those frequent nighttime anxiety attacks. Among all the chaos in my life, there were a few things I was certain of. And one of those things was the certainty of never having felt God, I didn't even know that God was something you could feel. For me, when I started the 12-step program, God was a social construct, something humans had invented to control a society thirsty for basic survival instincts. And perhaps I wasn't so wrong, but like everything in life, this was only half the truth. Despite my deep cognitive analysis that my anxiety forced me to do almost every night for hours, often until the first ray of sun pierced my bedroom window, my spiritual bias didn't allow me to see the whole picture, or a complete reality. On that side, there had always been a void Later, I realized that this emptiness was the main cause of all my problems. From there came that feeling of always being incomplete, that anxiety of always feeling like something was missing, that need to always want to fill voids that weren't mine, without realizing that it was only creating more emptiness within me Once, in those heart-to-heart talks that we in AA call sponsorship, my soul expressed the painful doubt, 'What does it mean to feel God?' My sponsor simply replied, 'I assure you that when you feel God, you won't doubt that what you feel is God. There is no doubt in matters of God. And so I left, with that answer that left me right where I started. And with more doubts. Why is there no doubt in matters of God? After thinking about it for so long, I paused for a few seconds. I closed my eyes and decided, for the first time, to talk to this so-called God. I let go of all my feelings, all my disbelief, and I prepared myself to accept anything different from what I already had, because what I had wasn't working for me at all. With all sincerity and feeling a pressure in my chest, closer to my heart than usual, I asked in a low voice God, what does it feel like to feel you? What should I do to feel you? What's the manual for feeling you? I've tried everything, I don't know what else to do, what else to plan. I accept that I need to feel you. Everyone tells me that when I feel you, everything will make sense and only then will I start to let go of this violent need to consume my drug of choice. But nobody tells me how. What am I not seeing? Please, give me something. I can't take it anymore, I'm running out of strength, I'm wasting my life stuck in the same cycle. I can't do this anymore, help me feel you. Then a pain began to flow, but a particular one that every addict knows, that soul-deep pain that comes from emptiness, that pain that turns on the faucet of tears that began to flow non-stop. I allowed myself to feel that pain, everything turned dark and negative, suicidal thoughts returned, hate, resentment, selfishness, depression, all together, all that is lived in darkness, all that is felt in solitude, all that came from emptiness. And only by feeling it, could I see where that deep pain came from, I could visualize the path it left behind. For the first time, I recognized my spiritual emptiness. And it was only then that I began to see the whole picture of my life. Doubt has no place in the things of God because God is not logic, God is not reason, much less a manual. Doubt comes from logic, therefore where there is doubt, there is also an absence of God, emptiness. And right at the moment of recognizing that, very specific images came to my mind. My sponsor hugging me for the first time when I arrived and interviewed me. With that hug came the words, 'You're not alone, you're already in a safe harbor, we'll be with you from start to finish. One day at a massive AA event, right in the middle of a workshop dynamic, that deep and sincere hug my fellow sufferer and I shared, in the midst of deep crying with our eyes closed, someone guided our arms to each other. To end up keeping each other company in that darkness we had always gone through alone. That trip to a Group Anniversary outside the city, where a fellow member of my group and I were simply enjoying the scenery, the wind on our faces, and laughing at the craziness of our daily lives, this on my motorcycle on the highway. That hug it took me years to find in the arms of my younger sister, right after arriving after a writing session. That hug of forgiveness to my mother and father that I had never been able to give before because I didn't want to go through the pain that came with feeling. Those few seconds in the rain that we spent lost on our way to the new location of our Group that I experienced in the company of a fellow member. Seeing a new person arrive with a desire to start their process. Connecting in the same feeling and emotion that comes with the death of a best friend. Serving a cup of coffee to that fellow member who returns after months of absence. Arriving at the group with hope of seeing that fellow member who hasn't been coming for weeks and little is known about what happened, but they no longer come to meetings. Day after day, their chair remains empty. And then start letting go of their defenses and their craziness. Standing in front of several strangers, with my head held high, my gaze firm, saying my name and then, 'I am a drug addict. To say, 'I feel like shit, but I'm here for whatever I can contribute. To feel like I'm that support for those who were my support when I was at rock bottom. And not just feel it, but also be able to be it. And that, to mention just a few of the scenes that came to my mind, then I understood 'I had already felt God.' I wasn't lacking spirituality, I wasn't lacking God, I just needed to stay still for a moment to feel it. And to feel that he has always been there. And that he will never leave my side. So today I can answer my own question, 'That's what it feels like to feel God' but not just any God. But a very special one, the God of the 4th and 5th step addicts and alcoholics... originally posted at https://stacker.news/items/756957 @ 5d4b6c8d:8a1c1ee3
2024-11-07 01:50:21I'm watching the Warriors laying it on the Celtics and I'm struck by how uniquely fun to watch Steph still is. If you were picking a team of who you're most enjoying this season, who would be in the starting five? Here's my most entertaining starting 5 (ordered by position, not entertainingness): 1. Lamelo 2. Steph 3. Ant 4. Chet 5. Jokic originally posted at https://stacker.news/items/756861
@ 5d4b6c8d:8a1c1ee3
2024-11-07 01:50:21I'm watching the Warriors laying it on the Celtics and I'm struck by how uniquely fun to watch Steph still is. If you were picking a team of who you're most enjoying this season, who would be in the starting five? Here's my most entertaining starting 5 (ordered by position, not entertainingness): 1. Lamelo 2. Steph 3. Ant 4. Chet 5. Jokic originally posted at https://stacker.news/items/756861 @ e968e50b:db2a803a
2024-11-06 21:10:16https://youtu.be/vAM8rcmb4oQ?si=qpnJHtoVhLyG4Mek originally posted at https://stacker.news/items/756531
@ e968e50b:db2a803a
2024-11-06 21:10:16https://youtu.be/vAM8rcmb4oQ?si=qpnJHtoVhLyG4Mek originally posted at https://stacker.news/items/756531 @ 5d4b6c8d:8a1c1ee3
2024-11-06 17:44:00Now that Trump is heading back the White House, once again promising to "drain the swamp", let's consider how that might actually be accomplished. It's damn near impossible to fire federal employees and abolishing entire agencies is very difficult politically. The later hasn't been done since Jimmy Carter. Of course, I'm all for Ron Paul and Elon Musk pursuing both of those paths, but they'll definitely be ice skating uphill. There are two proposals that I know will result in massive voluntary resignations, labor savings, and reduction in DC bureaucrats: 1. Relocate departments and agencies away from the major metropolitan areas 2. Rescind locality pay for remote eligible workers The first option was implemented by Trump for a couple of agencies. It was big news in econ world when the USDA was relocated, because hundreds of USDA economists resigned. I'm not sure how easy it would be to implement the second idea (perhaps @Cje95 can weigh in), but it would also have a dramatic effect. During the pandemic, the feds followed the trend of making many positions remote work eligible. However, the federal pay scale still grants locality based pay increases for those living in expensive areas. If you are allowed to do your job from anywhere, why should you get an enormous raise (at taxpayer expense) for living in the most expensive place in the country? Pay all remote eligible workers as though they live in rural Arkansas, because they are allowed to do so. As with the relocation, most workers would probably resign rather than either move or take a huge paycut. And, if they don't, then at least the federal workforce is getting spread out and not costing nearly as much. What are some other feasible ways to dramatically reduce the federal workforce? originally posted at https://stacker.news/items/756327
@ 5d4b6c8d:8a1c1ee3
2024-11-06 17:44:00Now that Trump is heading back the White House, once again promising to "drain the swamp", let's consider how that might actually be accomplished. It's damn near impossible to fire federal employees and abolishing entire agencies is very difficult politically. The later hasn't been done since Jimmy Carter. Of course, I'm all for Ron Paul and Elon Musk pursuing both of those paths, but they'll definitely be ice skating uphill. There are two proposals that I know will result in massive voluntary resignations, labor savings, and reduction in DC bureaucrats: 1. Relocate departments and agencies away from the major metropolitan areas 2. Rescind locality pay for remote eligible workers The first option was implemented by Trump for a couple of agencies. It was big news in econ world when the USDA was relocated, because hundreds of USDA economists resigned. I'm not sure how easy it would be to implement the second idea (perhaps @Cje95 can weigh in), but it would also have a dramatic effect. During the pandemic, the feds followed the trend of making many positions remote work eligible. However, the federal pay scale still grants locality based pay increases for those living in expensive areas. If you are allowed to do your job from anywhere, why should you get an enormous raise (at taxpayer expense) for living in the most expensive place in the country? Pay all remote eligible workers as though they live in rural Arkansas, because they are allowed to do so. As with the relocation, most workers would probably resign rather than either move or take a huge paycut. And, if they don't, then at least the federal workforce is getting spread out and not costing nearly as much. What are some other feasible ways to dramatically reduce the federal workforce? originally posted at https://stacker.news/items/756327 @ fca435eb:e53931d9
2024-11-06 17:38:35# Setting up a hybrid lightning node, even behid CGNAT: ## 1. Motivation To run a lightning node in a completely sovereign way, we must host it on hardware under our control. To make our node accessible to other peers we must publish on the gossip network how to find our node, but since many of our local networks are behind a **carrier grade NAT** and the router does not have a public IP, it becomes a bit difficult. In this post I will explain how to expose our node with a **ssh tunnel with a vps**, even behind CGNAT. I won't explain how to create a tor hidden service because I think is trivial, if you are running a node, almost sure that you have one. ## 2. Prerequisities: 1- Running a lightning node 2- Having a vps with a public ip: [lunanode](https://www.lunanode.com/?r=31080) is easy to use, and you can pay with lightning ## 3. Exposing the node Connect to your VPS by ssh and edit /etc/ssh/sshd_config ``` sudo vim /etc/ssh/sshd_config ``` Ensure that: ``` AllowTcpForwarding yes GatewayPorts clientspecified ``` Make sure that the port that you want to expose is accessible by the internet, in my case it will be the default port 9735, replace 9735 by your custom port if you want: ``` sudo ufw allow 9735 sudo ufw reload ``` Now let's move to our local machine, where the node is running. With the assumption that your node is exposed in localhost:9735 (that's how it is by default) let's test our implementation, remember to change the ports if you have others, paste your vps public ip address and your vps user : ``` ssh -nNTv -R 0.0.0.0:9735:localhost:9735 **YOUR_VPS_IP_ADDRESS** ``` Now you must change the config of your node to advertise the new address. If you use CLN you can edit the config file and set announce-addr=**YOUR_VPS_IP_ADDRESS**:9735 (or your port). If you are using another lightning node implementation I am sure you can find the config file, and announce the address. Now everything must work, you can try to find your node from another node (maybe a friend's node) by the new ip:port address and the pubkey of course. ## 4. Finishing You can close that now, and prepare to make it more robust. First we need to install autossh ``` sudo apt-get update && sudo apt-get install autossh ``` Create system d service ``` sudo vim /etc/system/systemd/autossh-lightning.service ``` and there put the service description, remember to replace the needed fields with your own data. ``` [Unit] Description=port forwarding through auto ssh After=network.target [Service] User=USERLOCAL ExecStart=/usr/bin/autossh -M 0 -o ServerAliveInterval=30 -o ServerAliveCountMax=3 -i /home/USERLOCAL/.ssh/id_rsa -nNTv -R 0.0.0.0:9735:localhost:9735 YOUR_VPS_IP_ADDRESS [Install] WantedBy=multi-user.target ``` Then run: ``` sudo systemctl start autossh-lightning sudo systemctl status autossh-lightning ``` If status is active we are all set. originally posted at https://stacker.news/items/756320
@ fca435eb:e53931d9
2024-11-06 17:38:35# Setting up a hybrid lightning node, even behid CGNAT: ## 1. Motivation To run a lightning node in a completely sovereign way, we must host it on hardware under our control. To make our node accessible to other peers we must publish on the gossip network how to find our node, but since many of our local networks are behind a **carrier grade NAT** and the router does not have a public IP, it becomes a bit difficult. In this post I will explain how to expose our node with a **ssh tunnel with a vps**, even behind CGNAT. I won't explain how to create a tor hidden service because I think is trivial, if you are running a node, almost sure that you have one. ## 2. Prerequisities: 1- Running a lightning node 2- Having a vps with a public ip: [lunanode](https://www.lunanode.com/?r=31080) is easy to use, and you can pay with lightning ## 3. Exposing the node Connect to your VPS by ssh and edit /etc/ssh/sshd_config ``` sudo vim /etc/ssh/sshd_config ``` Ensure that: ``` AllowTcpForwarding yes GatewayPorts clientspecified ``` Make sure that the port that you want to expose is accessible by the internet, in my case it will be the default port 9735, replace 9735 by your custom port if you want: ``` sudo ufw allow 9735 sudo ufw reload ``` Now let's move to our local machine, where the node is running. With the assumption that your node is exposed in localhost:9735 (that's how it is by default) let's test our implementation, remember to change the ports if you have others, paste your vps public ip address and your vps user : ``` ssh -nNTv -R 0.0.0.0:9735:localhost:9735 **YOUR_VPS_IP_ADDRESS** ``` Now you must change the config of your node to advertise the new address. If you use CLN you can edit the config file and set announce-addr=**YOUR_VPS_IP_ADDRESS**:9735 (or your port). If you are using another lightning node implementation I am sure you can find the config file, and announce the address. Now everything must work, you can try to find your node from another node (maybe a friend's node) by the new ip:port address and the pubkey of course. ## 4. Finishing You can close that now, and prepare to make it more robust. First we need to install autossh ``` sudo apt-get update && sudo apt-get install autossh ``` Create system d service ``` sudo vim /etc/system/systemd/autossh-lightning.service ``` and there put the service description, remember to replace the needed fields with your own data. ``` [Unit] Description=port forwarding through auto ssh After=network.target [Service] User=USERLOCAL ExecStart=/usr/bin/autossh -M 0 -o ServerAliveInterval=30 -o ServerAliveCountMax=3 -i /home/USERLOCAL/.ssh/id_rsa -nNTv -R 0.0.0.0:9735:localhost:9735 YOUR_VPS_IP_ADDRESS [Install] WantedBy=multi-user.target ``` Then run: ``` sudo systemctl start autossh-lightning sudo systemctl status autossh-lightning ``` If status is active we are all set. originally posted at https://stacker.news/items/756320 @ 0861144c:e68a1caf
2024-11-06 16:20:18I saw many people here (and other sites) claiming that they voted Trump because he will pardon Ross Ulbritch. Politicians live from promises and is their biggest bond. Since Trump have the...experience of saying half-truth, one possibility is that he doesn't pardon Ross and still in jail. As non-US, all I can do is [zap my support to their legal fund](https://freeross.org/). Trump doesn't release Ross, **what is the next step**? originally posted at https://stacker.news/items/756208
@ 0861144c:e68a1caf
2024-11-06 16:20:18I saw many people here (and other sites) claiming that they voted Trump because he will pardon Ross Ulbritch. Politicians live from promises and is their biggest bond. Since Trump have the...experience of saying half-truth, one possibility is that he doesn't pardon Ross and still in jail. As non-US, all I can do is [zap my support to their legal fund](https://freeross.org/). Trump doesn't release Ross, **what is the next step**? originally posted at https://stacker.news/items/756208 @ b4403b24:83542d4e
2024-11-06 13:43:13 originally posted at https://stacker.news/items/755988
@ b4403b24:83542d4e
2024-11-06 13:43:13 originally posted at https://stacker.news/items/755988 @ b4403b24:83542d4e
2024-11-06 12:05:17Republicans are hilarious 😂  originally posted at https://stacker.news/items/755844
@ b4403b24:83542d4e
2024-11-06 12:05:17Republicans are hilarious 😂  originally posted at https://stacker.news/items/755844 @ 74718b83:b8204bd8
2024-11-06 11:09:14curious to hear some opinions on this as i know many hate the idea of the gov having anything to do with btc, on the flip side, having it as a reserve currency in a large country could be the thing that tips mass adoption and understanding on a global scale , which would mean more people waking up to the power of btc. it would also end the paper arguments no coiners make and silence them forever originally posted at https://stacker.news/items/755779
@ 74718b83:b8204bd8
2024-11-06 11:09:14curious to hear some opinions on this as i know many hate the idea of the gov having anything to do with btc, on the flip side, having it as a reserve currency in a large country could be the thing that tips mass adoption and understanding on a global scale , which would mean more people waking up to the power of btc. it would also end the paper arguments no coiners make and silence them forever originally posted at https://stacker.news/items/755779 @ 000002de:c05780a7
2024-11-06 03:24:27You may not realize it, but you voted today. You vote everyday. Not in an election but in a much more mundane but infinitely more important way. You voted with your time, talent, and treasure. * What you gave your time to. * What you gave your talents to push forward. * What you spent your life force (money, savings, bitcoin) towards. Its easy to let the world around you shift your focus. Make you feel good or bad for your participation in its rituals. But ask yourself. What am I spending my time, talent, and treasure towards? Does it align with what I tell myself is important? Is it moving me and those around me closer to the world as I'd like to see it? We have more control over our lives than any clowns that suck up to us for votes will ever have. Don't sell yourself short. You can become better. You can enrich others lives. You have value and worth. I believe our creator loves us more than we can even imagine. But, even if you don't believe that you can make your world better. Make your vote count. originally posted at https://stacker.news/items/755525
@ 000002de:c05780a7
2024-11-06 03:24:27You may not realize it, but you voted today. You vote everyday. Not in an election but in a much more mundane but infinitely more important way. You voted with your time, talent, and treasure. * What you gave your time to. * What you gave your talents to push forward. * What you spent your life force (money, savings, bitcoin) towards. Its easy to let the world around you shift your focus. Make you feel good or bad for your participation in its rituals. But ask yourself. What am I spending my time, talent, and treasure towards? Does it align with what I tell myself is important? Is it moving me and those around me closer to the world as I'd like to see it? We have more control over our lives than any clowns that suck up to us for votes will ever have. Don't sell yourself short. You can become better. You can enrich others lives. You have value and worth. I believe our creator loves us more than we can even imagine. But, even if you don't believe that you can make your world better. Make your vote count. originally posted at https://stacker.news/items/755525 @ 35f3a26c:92ddf231
2024-11-06 00:07:28##### **Who is the Cult of the Dead Cow (cDc)?** ##### A known USA based hacktivist group. According to the record in Wikipedia, it was started in 1984 at the Farm Pac slaughterhouse by Grandmaster Ratte' (aka Swamp Ratte'), Franken Gibe, Sid Vicious, and three BBS SysOps You can check their member list in their [web site](https://cultdeadcow.com/members.html) ##### **Thinks of the cDc group that I have found quite interesting** ##### - Group member ***Drunkfux*** (Jesse Dryden) is the grand nephew of ***Charlie Chaplin*** - In 1991, the group began distributing ***music*** in the form of cassette tape albums - In November 1994, the group claimed responsibility for giving ***President Ronald Reagan*** Alzheimer's disease, claiming to have done so in 1986 with a blowgun - In 1995, the group declared war on the Church of Scientology stating "We believe that El Ron Hubbard [sic] is actually none other than Heinrich Himmler of the SS, who fled to Argentina and is now responsible for the stealing of babies from hospitals and raising them as 'super-soldiers' for the purpose of overthrowing the U.S. Fed. Govt. in a bloody revolution. We fear plans for a 'Fourth Reich' to be established on our home soil under the vise-like grip of oppression known as Scientology!" - On January 7, 1999, the group joined with an international coalition of hackers to denounce a call to cyber-war against the governments of China and Iraq - In February 2000, the group was the subject of an 11 minute documentary short titled "Disinformation". - In February 2000, a member of the group by the code-name Mudge briefed ***President Bill Clinton*** on "Internet security". - In 2003 the tool created by the group by the name of ***Six/Four System*** became the first product of a hacker group to receive approval from the ***United States Department of Commerce*** for export of strong encryption - Member by the name of "Psychedelic Warlord" is congressman ***Beto O'Rourke***, an American politician who served as the U.S. representative for Texas's 16th congressional district from 2013 to 2019. ***A member of the Democratic Party***, party's nominee for the U.S. Senate in 2018, candidate for the presidential nomination in 2020, and the party's nominee for the 2022 Texas gubernatorial election. #### **Do they have a political affiliation?** #### From the previous section we could at least assume that they sympathize with the USA Democratic party, they supported President Bill Clinton and claimed responsibility for doing serious harm to President Ronald Reagan, I could not find any information if the government opened an investigation about this allegation or not. #### **Their latest contribution?** ### Recently, they have developed an application framework by the name of ***Veilid***, described as "like TOR" but for apps. This application framework, if adopted by many developers will improve privacy by default for applications developed under that framework. The web site claim that it is open source *You can review the information and project at the web site: [VEILID](https://veilid.com/)* ***In the Web site the group describe it as follows:*** "***Veilid*** allows anyone to build a distributed, private app. ***Veilid*** gives users the privacy to opt out of data collection and online tracking. ***Veilid*** is being built with user experience, privacy, and safety as our top priorities. It is open source and available to everyone to use and build upon." "***Veilid*** goes above and beyond existing privacy technologies and has the potential to completely change the way people use the Internet. ***Veilid*** _has no profit motive_, which puts us in a unique position to promote ideals without the compromise of capitalism." #### Summary #### ***Veilid*** seems to be exactly what is needed at the moment to bring privacy to the masses, even though TOR is doing a very good job and with the improved throughput its usage experience has improved, having a native privacy oriented FOSS application framework is paramount. Most people is not technically savvy and therefore, not skilled in cyber security, they are constantly victims of cyber crime in many forms and shapes. eliminating one vector of attack by making the applications to opt out of data collection and online tracking from the get go is a step in the right direction, the question is, Would developers in general use the framework? Considering the ads will not be a possible source of income if the framework is used, well... Time will say...
@ 35f3a26c:92ddf231
2024-11-06 00:07:28##### **Who is the Cult of the Dead Cow (cDc)?** ##### A known USA based hacktivist group. According to the record in Wikipedia, it was started in 1984 at the Farm Pac slaughterhouse by Grandmaster Ratte' (aka Swamp Ratte'), Franken Gibe, Sid Vicious, and three BBS SysOps You can check their member list in their [web site](https://cultdeadcow.com/members.html) ##### **Thinks of the cDc group that I have found quite interesting** ##### - Group member ***Drunkfux*** (Jesse Dryden) is the grand nephew of ***Charlie Chaplin*** - In 1991, the group began distributing ***music*** in the form of cassette tape albums - In November 1994, the group claimed responsibility for giving ***President Ronald Reagan*** Alzheimer's disease, claiming to have done so in 1986 with a blowgun - In 1995, the group declared war on the Church of Scientology stating "We believe that El Ron Hubbard [sic] is actually none other than Heinrich Himmler of the SS, who fled to Argentina and is now responsible for the stealing of babies from hospitals and raising them as 'super-soldiers' for the purpose of overthrowing the U.S. Fed. Govt. in a bloody revolution. We fear plans for a 'Fourth Reich' to be established on our home soil under the vise-like grip of oppression known as Scientology!" - On January 7, 1999, the group joined with an international coalition of hackers to denounce a call to cyber-war against the governments of China and Iraq - In February 2000, the group was the subject of an 11 minute documentary short titled "Disinformation". - In February 2000, a member of the group by the code-name Mudge briefed ***President Bill Clinton*** on "Internet security". - In 2003 the tool created by the group by the name of ***Six/Four System*** became the first product of a hacker group to receive approval from the ***United States Department of Commerce*** for export of strong encryption - Member by the name of "Psychedelic Warlord" is congressman ***Beto O'Rourke***, an American politician who served as the U.S. representative for Texas's 16th congressional district from 2013 to 2019. ***A member of the Democratic Party***, party's nominee for the U.S. Senate in 2018, candidate for the presidential nomination in 2020, and the party's nominee for the 2022 Texas gubernatorial election. #### **Do they have a political affiliation?** #### From the previous section we could at least assume that they sympathize with the USA Democratic party, they supported President Bill Clinton and claimed responsibility for doing serious harm to President Ronald Reagan, I could not find any information if the government opened an investigation about this allegation or not. #### **Their latest contribution?** ### Recently, they have developed an application framework by the name of ***Veilid***, described as "like TOR" but for apps. This application framework, if adopted by many developers will improve privacy by default for applications developed under that framework. The web site claim that it is open source *You can review the information and project at the web site: [VEILID](https://veilid.com/)* ***In the Web site the group describe it as follows:*** "***Veilid*** allows anyone to build a distributed, private app. ***Veilid*** gives users the privacy to opt out of data collection and online tracking. ***Veilid*** is being built with user experience, privacy, and safety as our top priorities. It is open source and available to everyone to use and build upon." "***Veilid*** goes above and beyond existing privacy technologies and has the potential to completely change the way people use the Internet. ***Veilid*** _has no profit motive_, which puts us in a unique position to promote ideals without the compromise of capitalism." #### Summary #### ***Veilid*** seems to be exactly what is needed at the moment to bring privacy to the masses, even though TOR is doing a very good job and with the improved throughput its usage experience has improved, having a native privacy oriented FOSS application framework is paramount. Most people is not technically savvy and therefore, not skilled in cyber security, they are constantly victims of cyber crime in many forms and shapes. eliminating one vector of attack by making the applications to opt out of data collection and online tracking from the get go is a step in the right direction, the question is, Would developers in general use the framework? Considering the ads will not be a possible source of income if the framework is used, well... Time will say... @ 35f3a26c:92ddf231
2024-11-05 22:17:49#### What is Peer Thinking? The cognitive and emotional processes that occur when individuals are influenced by their peers. #### The psychology behind it: The psychology behind peer influence encompasses various factors, including: 1. Social belonging and acceptance, 2. Identity formation, 3. The dynamics of group behavior #### Is it being used to control us? https://image.nostr.build/cf90335bbf59e3395dc4324d123cd3a058ca716cf6172f079eb1d78547008147.jpg IMO, yes, at the core of it is the basic human need for belonging. Social belonging is a critical component since it is craved by most, specially but not only by the youngest, those with power across the world know this very well, therefore, thinking that they will not use it to control the population in order to profit from it or change public opinion would be irrational. The media is used to brain wash the population creating something that most will consider "the norm", thus, the majority will try to conform to that norm in order to belong. That include manipulating the population to take an experimental drug (even if it could be very dangerous due to its unknown effects) or to accept as a norm a behavior that few years back would have been considered inappropriate. #### Cognitive Dissonance https://image.nostr.build/60f24a810be1dd6badb36d70c5a691d4361207590dea1a8e64e09a75a252cfbf.jpg This is a term that we should get familiar with. It is a psychological state where conflicting beliefs or behaviors create discomfort. ***Example:*** A kid in high school that has a good loving family but all his close friends are on drugs (legal ones) and they keep telling him he is an idiot for not using as well. Now his is that state of conflict believes, on one side his best friends, all tell him is okay, on the other hand his family that loves him has explained him at length the dangers and issues that the drugs will have in his life. To resolve the dissonance he has three options, one, join the group and start taking drugs with the rest, two try to rationalize it, considering to take drugs just occasionally to belong but not to make it a habit, three lose his friends (and here it comes again the peer thinking to bite). Extrapolate to many other cases. > As an anecdote Recently, on a friend's reunion, one of the guest was complaining about one of his daughters, she was quite confused asking him why so many of her classmates were bisexual, she was wondering if something was wrong with her since she was not; a 13 year old girl; the father was having a hard time explaining her that the majority are saying so just to feel as part of what the school was teaching to be the norm, it was not cool to be straight, the tally was 37% of the class. Consider that, statistically, the number of people, “worldwide” identifying as bisexual are between 3% and 5% (less than 1% in less accepting countries), that number used to be less than 2% less than a decade ago. But 37% is far from the statistical norm, indicating a peer thinking behavior but not the reality of their sexual preferences. Once again, extrapolate to any ideology, religion, gender identity, political agenda that a country desires to push forward for whatever reason, adding that to the official school program and to federal mandatory training programs would do the trick. A powerful tool, that can be used for good or bad. #### What are the strategies to counter negative peer thinking? https://image.nostr.build/4b70949b8af76ed53a5be5507f41f1d1c960dc3592f199eab78e2d25688975c5.jpg Reading the literature about the subject, few strategies are recommended: 1. *Self-Awareness*: teaching ourselves and our children to recognize when we are being influenced by peers 2. *Being selective with your friends*: peers with similar values will reinforce positive behaviors 3. *Learning to be assertive*: teaching ourselves and our children to communicate assertively our boundaries will empower us and them to resist unwanted pressure to adopt negative behaviors. 4. *Less judging more talking*: this applies to our children and partners, judging less and listening more will make our beloved ones more open to discuss social pressures. ***What do you think?*** ***What strategies you use as counter measures?***
@ 35f3a26c:92ddf231
2024-11-05 22:17:49#### What is Peer Thinking? The cognitive and emotional processes that occur when individuals are influenced by their peers. #### The psychology behind it: The psychology behind peer influence encompasses various factors, including: 1. Social belonging and acceptance, 2. Identity formation, 3. The dynamics of group behavior #### Is it being used to control us? https://image.nostr.build/cf90335bbf59e3395dc4324d123cd3a058ca716cf6172f079eb1d78547008147.jpg IMO, yes, at the core of it is the basic human need for belonging. Social belonging is a critical component since it is craved by most, specially but not only by the youngest, those with power across the world know this very well, therefore, thinking that they will not use it to control the population in order to profit from it or change public opinion would be irrational. The media is used to brain wash the population creating something that most will consider "the norm", thus, the majority will try to conform to that norm in order to belong. That include manipulating the population to take an experimental drug (even if it could be very dangerous due to its unknown effects) or to accept as a norm a behavior that few years back would have been considered inappropriate. #### Cognitive Dissonance https://image.nostr.build/60f24a810be1dd6badb36d70c5a691d4361207590dea1a8e64e09a75a252cfbf.jpg This is a term that we should get familiar with. It is a psychological state where conflicting beliefs or behaviors create discomfort. ***Example:*** A kid in high school that has a good loving family but all his close friends are on drugs (legal ones) and they keep telling him he is an idiot for not using as well. Now his is that state of conflict believes, on one side his best friends, all tell him is okay, on the other hand his family that loves him has explained him at length the dangers and issues that the drugs will have in his life. To resolve the dissonance he has three options, one, join the group and start taking drugs with the rest, two try to rationalize it, considering to take drugs just occasionally to belong but not to make it a habit, three lose his friends (and here it comes again the peer thinking to bite). Extrapolate to many other cases. > As an anecdote Recently, on a friend's reunion, one of the guest was complaining about one of his daughters, she was quite confused asking him why so many of her classmates were bisexual, she was wondering if something was wrong with her since she was not; a 13 year old girl; the father was having a hard time explaining her that the majority are saying so just to feel as part of what the school was teaching to be the norm, it was not cool to be straight, the tally was 37% of the class. Consider that, statistically, the number of people, “worldwide” identifying as bisexual are between 3% and 5% (less than 1% in less accepting countries), that number used to be less than 2% less than a decade ago. But 37% is far from the statistical norm, indicating a peer thinking behavior but not the reality of their sexual preferences. Once again, extrapolate to any ideology, religion, gender identity, political agenda that a country desires to push forward for whatever reason, adding that to the official school program and to federal mandatory training programs would do the trick. A powerful tool, that can be used for good or bad. #### What are the strategies to counter negative peer thinking? https://image.nostr.build/4b70949b8af76ed53a5be5507f41f1d1c960dc3592f199eab78e2d25688975c5.jpg Reading the literature about the subject, few strategies are recommended: 1. *Self-Awareness*: teaching ourselves and our children to recognize when we are being influenced by peers 2. *Being selective with your friends*: peers with similar values will reinforce positive behaviors 3. *Learning to be assertive*: teaching ourselves and our children to communicate assertively our boundaries will empower us and them to resist unwanted pressure to adopt negative behaviors. 4. *Less judging more talking*: this applies to our children and partners, judging less and listening more will make our beloved ones more open to discuss social pressures. ***What do you think?*** ***What strategies you use as counter measures?*** @ 35f3a26c:92ddf231
2024-11-05 22:14:02#### What is Bitaxe? Bitaxe is an open source ASIC (Application-Specific Integrated Circuit) Bitcoin miner that has been making waves in the cryptocurrency community. This innovative project aims to empower miners at every level with powerful, efficient, and **low-cost** mining solutions. It is a fully open source ASIC Bitcoin miner developed by Skot9000, an advocate for open-source innovation in the Bitcoin space. With all software and hardware specs available on GitHub, this project aims to provide miners with a transparent and accessible platform for Bitcoin mining. https://image.nostr.build/db35c2a028e9f740181daabe2deef4e707653fa2d82f1602086e0ac4b5ee84fd.png #### **Pros** 1. **Open Source**: The Bitaxe is fully open source, allowing users to access and modify its source code, hardware designs, and build gerbers for PCB ordering. 2. **Low Cost**: Bitaxe offers low-cost solutions for miners, making it an attractive option for those looking to enter the world of Bitcoin mining without breaking the bank. 3. **Efficient**: The Bitaxe series is designed to be power-efficient, utilizing either the Bitmain BM1387 or BM1397 ASICs for SHA256 hashing. #### **Cons** 1. **Technical Complexity**: Being an open-source project, users are required to be technically savvy to set up and maintain the miner, which could pose challenges for those without experience. 3. **Bricking Potential**: Like any complex technology, there is a risk of bricking (rendering the device unusable) the Bitaxe if not handled properly. #### **Summary** The Bitaxe represents an exciting development in the world of Bitcoin mining, offering a low cost, efficient, and open-source solution for miners. While it may present some challenges for users who are new to the technology or lack technical expertise, the potential benefits far outweigh these drawbacks. As the project continues to evolve and gain traction, we can expect to see further improvements in performance, accessibility, and innovation within the Bitcoin mining landscape. #### Where can I get more information Go to their Github page: https://github.com/skot/bitaxe originally posted at https://stacker.news/items/659572
@ 35f3a26c:92ddf231
2024-11-05 22:14:02#### What is Bitaxe? Bitaxe is an open source ASIC (Application-Specific Integrated Circuit) Bitcoin miner that has been making waves in the cryptocurrency community. This innovative project aims to empower miners at every level with powerful, efficient, and **low-cost** mining solutions. It is a fully open source ASIC Bitcoin miner developed by Skot9000, an advocate for open-source innovation in the Bitcoin space. With all software and hardware specs available on GitHub, this project aims to provide miners with a transparent and accessible platform for Bitcoin mining. https://image.nostr.build/db35c2a028e9f740181daabe2deef4e707653fa2d82f1602086e0ac4b5ee84fd.png #### **Pros** 1. **Open Source**: The Bitaxe is fully open source, allowing users to access and modify its source code, hardware designs, and build gerbers for PCB ordering. 2. **Low Cost**: Bitaxe offers low-cost solutions for miners, making it an attractive option for those looking to enter the world of Bitcoin mining without breaking the bank. 3. **Efficient**: The Bitaxe series is designed to be power-efficient, utilizing either the Bitmain BM1387 or BM1397 ASICs for SHA256 hashing. #### **Cons** 1. **Technical Complexity**: Being an open-source project, users are required to be technically savvy to set up and maintain the miner, which could pose challenges for those without experience. 3. **Bricking Potential**: Like any complex technology, there is a risk of bricking (rendering the device unusable) the Bitaxe if not handled properly. #### **Summary** The Bitaxe represents an exciting development in the world of Bitcoin mining, offering a low cost, efficient, and open-source solution for miners. While it may present some challenges for users who are new to the technology or lack technical expertise, the potential benefits far outweigh these drawbacks. As the project continues to evolve and gain traction, we can expect to see further improvements in performance, accessibility, and innovation within the Bitcoin mining landscape. #### Where can I get more information Go to their Github page: https://github.com/skot/bitaxe originally posted at https://stacker.news/items/659572 @ 5d4b6c8d:8a1c1ee3
2024-11-05 14:17:57On the [Stacker Sports Podcast](https://fountain.fm/clip/SoqXGiWqaFFGwTjtD0pJ) we talked about the Emirates Cup Survivor Pool and a revision that needs to be made. I messed up in describing the Group Stage as only taking place on Tuesdays. Group Stage games will actually be played on Tuesdays and Fridays, just like last year. That means there are going to be seven Group Stage picks and we'll be picking games twice a week. Check out the [original post](https://stacker.news/items/751054/r/Undisciplined) for the full details. We already have eight contestants and hopefully a few more will join in the next week. **Current Prize** About 25k sats! cc: @grayruby, @gnilma, @BlokchainB, @siggy47, @supercyclone, @realBitcoinDog, @Carresan, originally posted at https://stacker.news/items/754602
@ 5d4b6c8d:8a1c1ee3
2024-11-05 14:17:57On the [Stacker Sports Podcast](https://fountain.fm/clip/SoqXGiWqaFFGwTjtD0pJ) we talked about the Emirates Cup Survivor Pool and a revision that needs to be made. I messed up in describing the Group Stage as only taking place on Tuesdays. Group Stage games will actually be played on Tuesdays and Fridays, just like last year. That means there are going to be seven Group Stage picks and we'll be picking games twice a week. Check out the [original post](https://stacker.news/items/751054/r/Undisciplined) for the full details. We already have eight contestants and hopefully a few more will join in the next week. **Current Prize** About 25k sats! cc: @grayruby, @gnilma, @BlokchainB, @siggy47, @supercyclone, @realBitcoinDog, @Carresan, originally posted at https://stacker.news/items/754602 @ 5d4b6c8d:8a1c1ee3
2024-11-05 13:35:10We finally have an event other than soccer! [Freebitcoin](https://freebitco.in/?r=51325722) is taking wagers on the Las Vegas Grand Prix. Here's how to optimally allocate a hypothetical 2k sats on this event (according to [RBOA](https://stacker.news/items/342765/r/Undisciplined)): | Driver | Wager | |--------|--------| | Vertappen | 486 | | Norris | 521 | | Leclerc | 456 | | Alonso | 6 | | Hamilton | 63 | | Piastri | 107 | | Tsunoda | 4 | | Perez | 12 | | Sainz | 243 | | Russell | 63 | | Stroll | 2 | | Ocon | 4 | | Ganyu | 1 | | Bottas | 2 | | Albon | 4 | | Hulkenberg | 7 | | Gasly | 4 | | Magnussen | 6 | Enjoy your winnings originally posted at https://stacker.news/items/754549
@ 5d4b6c8d:8a1c1ee3
2024-11-05 13:35:10We finally have an event other than soccer! [Freebitcoin](https://freebitco.in/?r=51325722) is taking wagers on the Las Vegas Grand Prix. Here's how to optimally allocate a hypothetical 2k sats on this event (according to [RBOA](https://stacker.news/items/342765/r/Undisciplined)): | Driver | Wager | |--------|--------| | Vertappen | 486 | | Norris | 521 | | Leclerc | 456 | | Alonso | 6 | | Hamilton | 63 | | Piastri | 107 | | Tsunoda | 4 | | Perez | 12 | | Sainz | 243 | | Russell | 63 | | Stroll | 2 | | Ocon | 4 | | Ganyu | 1 | | Bottas | 2 | | Albon | 4 | | Hulkenberg | 7 | | Gasly | 4 | | Magnussen | 6 | Enjoy your winnings originally posted at https://stacker.news/items/754549 @ 0861144c:e68a1caf
2024-11-05 12:23:01Read the other parts: [Part 1](https://stacker.news/items/735219)|[Part 2](https://stacker.news/items/736674)|[Part 3](https://stacker.news/items/738294)|[Part 4](https://stacker.news/items/739692)|[Part 5](https://stacker.news/items/743142)| [Part 6](https://stacker.news/items/744965)| [Part 7](https://stacker.news/items/746621)| [Part 8](https://stacker.news/items/748225)| [Part 9](https://stacker.news/items/749793)| [Part 10](https://stacker.news/items/753048) --- We continue with a story of Popes who want to take control of the Church but one of them is going to make a huge big mistake.  --- 126. Leo VII [936-939] Stepbrother of Alberic II, Roman Senator. He was a Benedictine monk at the time of his appointment. He focused heavily on monastic life, granting much power to Alberic, Hugh of Arles, and Odo, Abbot of Cluny, to take control of ecclesiastical life and reform monastic living. He prohibited forced baptism of Jews. 127. Stephen VIII [939-942] Elected by Alberic II, he was a poor politician who combined secular and ecclesiastical powers, threatening to excommunicate the French if they did not recognize Louis IV of Outremer as King of France. 128. Marinus II [942-946] Elected by Alberic II, not much is notable except that he appointed the Archbishop of Mainz as papal legate and Apostolic Vicar of France and Germany. 129. Agapetus II [946-955] Elected by Alberic II. He favored ecclesiastical life, empowering Otto I, King of Germany, to organize ecclesiastical territories. He established the diocese of Hamburg-Bremen to continue missionary work in Nordic territories. 130. John XII [955-964] His name was Octavian of Tusculum. Elected by Alberic II. He ascended to the Papacy at 18, without religious training. He was lazy, idle, and fond of indulgence. He carried out one of the most significant acts in history: he called upon Otto I to take control of both Germany and Italy through the *Privilegium Ottonianum*, an improved copy of the *Constitutio Lotharii* that had been reviewed with Pope Eugene II [99]. This reignited the drama started with the Theophylact family, challenging papal independence once more. This led to the appointment, transfer, and sale of bishoprics, where laypeople had direct influence over Church matters. The Pope watched as Otto grew in power and sought help from the Emperor’s enemies until Otto realized this, marched to Rome, and confronted the Pope. He was murdered by a blow to the head with a hammer by the husband of one of his lovers. - In the brief period between his death and flight (February-May), the Emperor Otto's secretary appointed Leo VIII as the new pope, but he lacked support from both the clergy and the people. He is considered an antipope. 131. Benedict V [964] Otto I did not recognize him as Pope and, invoking the document signed with his predecessor, informed Rome that they had lost the right to elect Popes. The Emperor had him arrested. He died in exile in Hamburg 30 days after his appointment. 132. Leo VIII [964-965] There is controversy over whether to consider this man as Pope or antipope. However, he was elected by Otto I in a synod. He issued documents during this short time, but they were not recognized due to an investiture dispute. 133. John XIII [965-972] John Crescentius. Rumors (still persistent) suggest he was a son of Theodora the Younger, Marozia's sister. He was a member of the Papal Court at the time of his appointment. His appointment was unpopular in Rome, and he reprimanded those who opposed it. His main achievement was spreading the Roman liturgy to Byzantium and supporting evangelization efforts among Slavs and Hungarians. He created the archdiocese of Magdeburg. 134. Benedict VI [973-974] Elected by Otto I. When Otto died, Crescentius I, brother of the previous Pope, organized a rebellion, imprisoned the Pope, and had him killed to prevent his liberation by the new emperor, Otto II. Boniface VII (antipope) tried to take power but was not recognized by the Emperor or Count Sicco of Spoleto, his secretary. 135. Benedict VII [974-983] Benedict of Sutri. Elected by imperial power and the Roman aristocracy. He founded the diocese of Prague and supported evangelical missions worldwide. In the synod of Rome (981), he condemned simony due to the growing number of married priests inheriting positions and benefits at the Church's expense. 136. John XIV [983-984] Pietro of Canossa. Imposed by the imperial power of Otto II, he was Italy’s vice-chancellor. Upon Otto II's death, his three-year-old son Otto III succeeded him. The antipope Boniface VII returned from exile and tried to reclaim the throne. This Pope allegedly died from poisoning. 137. John XV [985-996] Of the Imperial faction and imposed by Crescentius II. He replaced the Capetian dynasty with the Carolingian dynasty. He maintained open communication with all archbishoprics and bishoprics and established diplomatic relations with Russia, which was under Byzantine control. He canonized Ulrich of Augsburg. 138. Gregory V [996-999] Bruno of Carinthia. A cousin of Otto III. He was the first German pope. As expected, not being Roman or Italian, he lacked support from the Roman populace. He led an ascetic life. In 997, a revolt led by John Crescentius rose against him, appointing John Philagathos as John XVI (antipope). The revolt failed. John was beheaded, and the antipope was mutilated and exiled. --- And so the series of Popes dependent on imperial power with lay interference continues, but that will be for the next chapter. originally posted at https://stacker.news/items/754476
@ 0861144c:e68a1caf
2024-11-05 12:23:01Read the other parts: [Part 1](https://stacker.news/items/735219)|[Part 2](https://stacker.news/items/736674)|[Part 3](https://stacker.news/items/738294)|[Part 4](https://stacker.news/items/739692)|[Part 5](https://stacker.news/items/743142)| [Part 6](https://stacker.news/items/744965)| [Part 7](https://stacker.news/items/746621)| [Part 8](https://stacker.news/items/748225)| [Part 9](https://stacker.news/items/749793)| [Part 10](https://stacker.news/items/753048) --- We continue with a story of Popes who want to take control of the Church but one of them is going to make a huge big mistake.  --- 126. Leo VII [936-939] Stepbrother of Alberic II, Roman Senator. He was a Benedictine monk at the time of his appointment. He focused heavily on monastic life, granting much power to Alberic, Hugh of Arles, and Odo, Abbot of Cluny, to take control of ecclesiastical life and reform monastic living. He prohibited forced baptism of Jews. 127. Stephen VIII [939-942] Elected by Alberic II, he was a poor politician who combined secular and ecclesiastical powers, threatening to excommunicate the French if they did not recognize Louis IV of Outremer as King of France. 128. Marinus II [942-946] Elected by Alberic II, not much is notable except that he appointed the Archbishop of Mainz as papal legate and Apostolic Vicar of France and Germany. 129. Agapetus II [946-955] Elected by Alberic II. He favored ecclesiastical life, empowering Otto I, King of Germany, to organize ecclesiastical territories. He established the diocese of Hamburg-Bremen to continue missionary work in Nordic territories. 130. John XII [955-964] His name was Octavian of Tusculum. Elected by Alberic II. He ascended to the Papacy at 18, without religious training. He was lazy, idle, and fond of indulgence. He carried out one of the most significant acts in history: he called upon Otto I to take control of both Germany and Italy through the *Privilegium Ottonianum*, an improved copy of the *Constitutio Lotharii* that had been reviewed with Pope Eugene II [99]. This reignited the drama started with the Theophylact family, challenging papal independence once more. This led to the appointment, transfer, and sale of bishoprics, where laypeople had direct influence over Church matters. The Pope watched as Otto grew in power and sought help from the Emperor’s enemies until Otto realized this, marched to Rome, and confronted the Pope. He was murdered by a blow to the head with a hammer by the husband of one of his lovers. - In the brief period between his death and flight (February-May), the Emperor Otto's secretary appointed Leo VIII as the new pope, but he lacked support from both the clergy and the people. He is considered an antipope. 131. Benedict V [964] Otto I did not recognize him as Pope and, invoking the document signed with his predecessor, informed Rome that they had lost the right to elect Popes. The Emperor had him arrested. He died in exile in Hamburg 30 days after his appointment. 132. Leo VIII [964-965] There is controversy over whether to consider this man as Pope or antipope. However, he was elected by Otto I in a synod. He issued documents during this short time, but they were not recognized due to an investiture dispute. 133. John XIII [965-972] John Crescentius. Rumors (still persistent) suggest he was a son of Theodora the Younger, Marozia's sister. He was a member of the Papal Court at the time of his appointment. His appointment was unpopular in Rome, and he reprimanded those who opposed it. His main achievement was spreading the Roman liturgy to Byzantium and supporting evangelization efforts among Slavs and Hungarians. He created the archdiocese of Magdeburg. 134. Benedict VI [973-974] Elected by Otto I. When Otto died, Crescentius I, brother of the previous Pope, organized a rebellion, imprisoned the Pope, and had him killed to prevent his liberation by the new emperor, Otto II. Boniface VII (antipope) tried to take power but was not recognized by the Emperor or Count Sicco of Spoleto, his secretary. 135. Benedict VII [974-983] Benedict of Sutri. Elected by imperial power and the Roman aristocracy. He founded the diocese of Prague and supported evangelical missions worldwide. In the synod of Rome (981), he condemned simony due to the growing number of married priests inheriting positions and benefits at the Church's expense. 136. John XIV [983-984] Pietro of Canossa. Imposed by the imperial power of Otto II, he was Italy’s vice-chancellor. Upon Otto II's death, his three-year-old son Otto III succeeded him. The antipope Boniface VII returned from exile and tried to reclaim the throne. This Pope allegedly died from poisoning. 137. John XV [985-996] Of the Imperial faction and imposed by Crescentius II. He replaced the Capetian dynasty with the Carolingian dynasty. He maintained open communication with all archbishoprics and bishoprics and established diplomatic relations with Russia, which was under Byzantine control. He canonized Ulrich of Augsburg. 138. Gregory V [996-999] Bruno of Carinthia. A cousin of Otto III. He was the first German pope. As expected, not being Roman or Italian, he lacked support from the Roman populace. He led an ascetic life. In 997, a revolt led by John Crescentius rose against him, appointing John Philagathos as John XVI (antipope). The revolt failed. John was beheaded, and the antipope was mutilated and exiled. --- And so the series of Popes dependent on imperial power with lay interference continues, but that will be for the next chapter. originally posted at https://stacker.news/items/754476 @ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history? As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times. At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols. The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)? **As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).** At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. ## **Open-source matters** When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. ## **Open-source is for your friends, and enemies** In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. ## **Limiting open-source threatens our own advancement** If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols. The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. *Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).*
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history? As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times. At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols. The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)? **As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).** At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. ## **Open-source matters** When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. ## **Open-source is for your friends, and enemies** In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. ## **Limiting open-source threatens our own advancement** If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols. The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. *Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).* @ a10260a2:caa23e3e
2024-11-05 06:21:10TIL Google Authenticator can potentially collect a lot of data, more than some of the other popular 2FA apps[^1]. [^1]: https://www.pcmag.com/reviews/google-authenticator  Whether it does or it doesn’t, if you’re like me, you don’t turn down an opportunity to remove some Google from your life and add in some open-source. Here’s a quick overview of the migration process. **Step 1: Download [2FAS](https://apps.apple.com/us/app/2fa-authenticator-2fas/id1217793794)**  **Step 2: Export accounts from Authenticator** This can be done via “Transfer accounts” in the sidebar. If you’re transferring on the same phone, take a screenshot of the QR code.   **Step 3: Import accounts into 2FAS** During the setup process for 2FAS, you’ll be given the option to import existing tokens from Google. This is where you’ll tap “Choose QR Code” and select the screenshot you took in step 2.  Note that when you tap continue after importing the tokens, you’ll be taken back to the same screen as above. I think it should take you to your list of accounts after. Either way, don’t think the import failed. Just tap cancel, and you’ll be taken there.  If you’re on Android, check out [Aegis](https://github.com/beemdevelopment/Aegis). 🫡 originally posted at https://stacker.news/items/753472
@ a10260a2:caa23e3e
2024-11-05 06:21:10TIL Google Authenticator can potentially collect a lot of data, more than some of the other popular 2FA apps[^1]. [^1]: https://www.pcmag.com/reviews/google-authenticator  Whether it does or it doesn’t, if you’re like me, you don’t turn down an opportunity to remove some Google from your life and add in some open-source. Here’s a quick overview of the migration process. **Step 1: Download [2FAS](https://apps.apple.com/us/app/2fa-authenticator-2fas/id1217793794)**  **Step 2: Export accounts from Authenticator** This can be done via “Transfer accounts” in the sidebar. If you’re transferring on the same phone, take a screenshot of the QR code.   **Step 3: Import accounts into 2FAS** During the setup process for 2FAS, you’ll be given the option to import existing tokens from Google. This is where you’ll tap “Choose QR Code” and select the screenshot you took in step 2.  Note that when you tap continue after importing the tokens, you’ll be taken back to the same screen as above. I think it should take you to your list of accounts after. Either way, don’t think the import failed. Just tap cancel, and you’ll be taken there.  If you’re on Android, check out [Aegis](https://github.com/beemdevelopment/Aegis). 🫡 originally posted at https://stacker.news/items/753472 @ 5d4b6c8d:8a1c1ee3
2024-11-04 16:07:54It's week 2 of Mock Draft Monday and the Raiders continue climbing the draft board. Now picking 6th and still needing to play NO, while having the tie-breaker with Carolina, there's a great chance of getting into the top three. The Raiders O-Line was obliterated this week. Ted Hendricks had a career day lined up against our third string left tackle. The silver lining is that JPJ was moved to center and it's clearly the right place for him. That all indicates that for approximately the 17th year in a row, the Raiders primary draft needs are QB, OT, and Guard. They also need to improve the WR and RB rooms. The defense is fine, but could also use upgrades at every level. Here we go: 6th Pick: QB Cam Ward 37th Pick: IOL Jonah Savaiinaea 68th Pick: LB Danny Stutsman 74th Pick: OT Marcus Mbow 104th Pick: DT Jordan Burch 140th Pick: WR Bru McCoy 177th Pick: RB Jo'Quavious Marks 212th Pick: CB Cobee Bryant 215th Pick: QB Conner Weigman 222nd Pick: S Shilo Sanders Two in a row with Cobee Bryant going 212th. I opted for the 49ers strategy of taking the QB we want with our first pick, but then taking another one later on day 3. The QB room has three seats in it, so I say bring in two QB's every year until we find our franchise guy: AOC is a perfectly serviceable backup/bridge QB. originally posted at https://stacker.news/items/753327
@ 5d4b6c8d:8a1c1ee3
2024-11-04 16:07:54It's week 2 of Mock Draft Monday and the Raiders continue climbing the draft board. Now picking 6th and still needing to play NO, while having the tie-breaker with Carolina, there's a great chance of getting into the top three. The Raiders O-Line was obliterated this week. Ted Hendricks had a career day lined up against our third string left tackle. The silver lining is that JPJ was moved to center and it's clearly the right place for him. That all indicates that for approximately the 17th year in a row, the Raiders primary draft needs are QB, OT, and Guard. They also need to improve the WR and RB rooms. The defense is fine, but could also use upgrades at every level. Here we go: 6th Pick: QB Cam Ward 37th Pick: IOL Jonah Savaiinaea 68th Pick: LB Danny Stutsman 74th Pick: OT Marcus Mbow 104th Pick: DT Jordan Burch 140th Pick: WR Bru McCoy 177th Pick: RB Jo'Quavious Marks 212th Pick: CB Cobee Bryant 215th Pick: QB Conner Weigman 222nd Pick: S Shilo Sanders Two in a row with Cobee Bryant going 212th. I opted for the 49ers strategy of taking the QB we want with our first pick, but then taking another one later on day 3. The QB room has three seats in it, so I say bring in two QB's every year until we find our franchise guy: AOC is a perfectly serviceable backup/bridge QB. originally posted at https://stacker.news/items/753327 @ 5d4b6c8d:8a1c1ee3
2024-11-04 15:45:30The first moves of the Raiders bye-week adjustments have already happened. OC Luke Getsy, as well as their offensive line and quarterback coaches. This had to happen, after the woeful offensive performances of the team. The run game especially has been abysmal and it's clearly due to coaching because the personnel is better than last year's o-line. Getsy showed absolutely no ability to adapt to the defenses the team faced. His opening scripted plays often worked really well, but then the offense became completely stagnant for the remainder of the game. It's not clear who will take over the play calling duties, or fill the other vacated roles, but the Raiders bloated coaching staff has three former play callers on it. The most likely candidate is Scott Turner. --- This needs to be the first of several changes to the coaching staff. Situational game management has been atrocious, so the person filling that role needs to be relieved as well. Reports are that assistant head coach Marvin Lewis has been completely phoning it in, so he should be gone to. The Raiders season has been over for a few weeks already and the remainder of the season needs to be about evaluating who to keep around. That should entail pairing down the largest coaching staff in the league, so we can see what Antonio Pierce does without the training wheels. This should also entail shutting down veterans like Minshew and Kolton Miller, in favor of getting a look at all the young guys on the roster. originally posted at https://stacker.news/items/753300
@ 5d4b6c8d:8a1c1ee3
2024-11-04 15:45:30The first moves of the Raiders bye-week adjustments have already happened. OC Luke Getsy, as well as their offensive line and quarterback coaches. This had to happen, after the woeful offensive performances of the team. The run game especially has been abysmal and it's clearly due to coaching because the personnel is better than last year's o-line. Getsy showed absolutely no ability to adapt to the defenses the team faced. His opening scripted plays often worked really well, but then the offense became completely stagnant for the remainder of the game. It's not clear who will take over the play calling duties, or fill the other vacated roles, but the Raiders bloated coaching staff has three former play callers on it. The most likely candidate is Scott Turner. --- This needs to be the first of several changes to the coaching staff. Situational game management has been atrocious, so the person filling that role needs to be relieved as well. Reports are that assistant head coach Marvin Lewis has been completely phoning it in, so he should be gone to. The Raiders season has been over for a few weeks already and the remainder of the season needs to be about evaluating who to keep around. That should entail pairing down the largest coaching staff in the league, so we can see what Antonio Pierce does without the training wheels. This should also entail shutting down veterans like Minshew and Kolton Miller, in favor of getting a look at all the young guys on the roster. originally posted at https://stacker.news/items/753300 @ 57d1a264:69f1fee1
2024-11-04 15:17:28   ——— NEW YORK (Nov. 4, 2024) — The Human Rights Foundation (HRF), along with partners dedicated to artistic freedom, expresses deep concern over the arrest and arbitrary detention of Gao Zhen, a prominent contemporary Chinese artist and a member of the well-known Gao Brothers, a collaborative artist duo. In [a letter](https://hrf.org/wp-content/uploads/2024/10/Letter-Demanding-Gao-Zhens-Release_Final.pdf) to the Consulate General of the People’s Republic of China in New York and other embassies, we call for his unconditional release. On Aug. 26, Gao was arrested and detained after 30 police officers conducted a raid on his studio in Yanjiao, a town in the small city of Sanhe, in the northern province of Hebei. He has been held since at the Sanhe City Detention Center on charges of “slandering China’s heroes and martyrs” — a crime punishable by up to three years in prison. A United States lawful permanent resident, Gao, 68, has made a career out of exposing the horrors of the Cultural Revolution through satirical humor that pushes the boundaries of social commentary. His works are also bold critiques of the Cultural Revolution and former Chinese Communist Party (CCP) leader Mao Zedong and his authoritarian rule of the country. “These topics are sensitive and considered taboo in today’s CCP-controlled China, yet it is crucial to educate the world on the truth of Mao’s dictatorial legacy,” HRF Chief Advocacy Officer Roberto Gonzalez said. “Mr. Zhen’s detention is not only a violation of his basic rights but also an attack on the fundamental freedoms of all Chinese people, who have the right to learn the truth about dictator Mao Zedong.” HRF demands Gao Zhen’s immediate and unconditional release as well as the CCP’s repeal of the Heroes and Martyrs Protection Law to safeguard artistic freedom in China. - - - For press inquiries, please contact [media@hrf.org](mailto:media@hrf.org). - - - _<sub>The Human Rights Foundation (HRF) is a nonpartisan nonprofit organization that promotes and protects human rights globally, with a focus on closed societies.</sub>_ originally posted at https://stacker.news/items/753275
@ 57d1a264:69f1fee1
2024-11-04 15:17:28   ——— NEW YORK (Nov. 4, 2024) — The Human Rights Foundation (HRF), along with partners dedicated to artistic freedom, expresses deep concern over the arrest and arbitrary detention of Gao Zhen, a prominent contemporary Chinese artist and a member of the well-known Gao Brothers, a collaborative artist duo. In [a letter](https://hrf.org/wp-content/uploads/2024/10/Letter-Demanding-Gao-Zhens-Release_Final.pdf) to the Consulate General of the People’s Republic of China in New York and other embassies, we call for his unconditional release. On Aug. 26, Gao was arrested and detained after 30 police officers conducted a raid on his studio in Yanjiao, a town in the small city of Sanhe, in the northern province of Hebei. He has been held since at the Sanhe City Detention Center on charges of “slandering China’s heroes and martyrs” — a crime punishable by up to three years in prison. A United States lawful permanent resident, Gao, 68, has made a career out of exposing the horrors of the Cultural Revolution through satirical humor that pushes the boundaries of social commentary. His works are also bold critiques of the Cultural Revolution and former Chinese Communist Party (CCP) leader Mao Zedong and his authoritarian rule of the country. “These topics are sensitive and considered taboo in today’s CCP-controlled China, yet it is crucial to educate the world on the truth of Mao’s dictatorial legacy,” HRF Chief Advocacy Officer Roberto Gonzalez said. “Mr. Zhen’s detention is not only a violation of his basic rights but also an attack on the fundamental freedoms of all Chinese people, who have the right to learn the truth about dictator Mao Zedong.” HRF demands Gao Zhen’s immediate and unconditional release as well as the CCP’s repeal of the Heroes and Martyrs Protection Law to safeguard artistic freedom in China. - - - For press inquiries, please contact [media@hrf.org](mailto:media@hrf.org). - - - _<sub>The Human Rights Foundation (HRF) is a nonpartisan nonprofit organization that promotes and protects human rights globally, with a focus on closed societies.</sub>_ originally posted at https://stacker.news/items/753275 @ 0861144c:e68a1caf
2024-11-04 12:27:35These are the previous parts: [Part 1](https://stacker.news/items/735219)|[Part 2](https://stacker.news/items/736674)|[Part 3](https://stacker.news/items/738294)|[Part 4](https://stacker.news/items/739692)|[Part 5](https://stacker.news/items/743142)| [Part 6](https://stacker.news/items/744965)| [Part 7](https://stacker.news/items/746621)| [Part 8](https://stacker.news/items/748225)| [Part 9](https://stacker.news/items/749793) --- The papacy enters one of its darkest periods, not only marked by a series of medieval violence but also by the utter prostitution of power in scenarios so obscene that, by the time you finish reading, you may question the absolute sanctity of the pontificate. 111. **Formosus [891-896]** Consecrated as bishop by Nicholas [105]; he was a missionary whose main strength was encouraging Christians to combat paganism through letters. He supported the coronation of Arnulf of Carinthia, against the wishes of Charles the Bald (France), who had the favor of John VIII [107]; Guido of Spoleto was forced to crown his son Lambert as Emperor, while the Pope began talks with Arnulf. The Pope sought Arnulf's help to free Italy from the Spoletos. 112. **Boniface VI [896]** He suffered from gout when elected and died 15 days later. 113. **Stephen VI [896-897]** Elected with the support of the Emperor of the Holy Roman Empire and King of Italy, Lambert. This is one of the most shameful moments in the Church's history. In March 897, a posthumous trial was initiated against Formosus [111], during which Formosus' body was exhumed, dressed in papal vestments, given a defense lawyer, and put on trial. He was found guilty, his election as Pope invalidated, all his appointments and ordinations annulled, his body stripped of its vestments, and his remains thrown into the Tiber River. A few months later, following an earthquake, a mob took advantage of the chaos to assassinate the Pope, strangling him, presumably on the orders of the Spoletos in revenge for the trial known today as the *Cadaver Synod* or the *Synod of Horror*.  *This is a representation of the Cadaver Synod. Too strong for me. Jean-Paul Laurens (1870)* 114. **Romanus [897]** Seeing the chaos left by his predecessor, he began the process of rehabilitating Formosus [111] but died 90 days after assuming office. It is hypothesized that he was poisoned. 115. **Theodore II [897]** Held power for 20 days. His first order was to return Formosus' remains to St. Peter's Basilica and convened a synod that annulled all decisions from the *Synod of Horror*, declaring it void. Notably, Lambert of Spoleto's supporters wanted Count of Tusculum, Sergius, as Pope. Theodore was murdered, possibly by poisoning. 116. **John IX [898-900]** A Benedictine monk, elected with Lambert of Spoleto's support. He completed the work of his predecessor and, to avoid further violence, decreed that Papal Consecration must take place in the presence of the Emperor's representative. This reversed the *Constitutio Lotharii*. He also prohibited the tradition of looting bishops' palaces or papal palaces upon their death, declared Arnulf's consecration invalid, and granted all prerogatives to Lambert, his protector. The anti-Formosus faction wanted Sergius [119] as Pope but failed. The Theophylact family began tightening its grip on the papacy. 117. **Benedict IV [900-903]** Elected when the throne of the Holy Roman Empire was vacant. Lambert died in 899. Berengar I, King of Italy and grandson of Louis the Pious, claimed the imperial title, but the Pope granted it to Louis III the Blind, hoping he would defend against Hungarian invasions from the north and Saracens from the south. Louis was defeated by Berengar, blinded, and exiled. Lacking support, Benedict sought (a major error) support from the Theophylact family, including Theodora and her daughter Marozia, who would dominate the papacy henceforth. 118. **Leo V [903]** Elected Pope, little is known about his papacy. He was imprisoned and murdered 30 days after his election, likely by Pope Sergius III (his successor). Christopher the Priest declared himself Pope (antipope) but was also murdered, allegedly by Sergius III. 119. **Sergius III [904-911]** Linked to the Theophylact family and a supporter of the *Synod of Horror*, where he actively participated. He began the *pornocracy*[^1] period. He attempted to desecrate Formosus' tomb, without success. He married Alberic to Marozia, rumored to be the Pope's mistress. The Cluny Abbey was founded in 910 by William of Aquitaine and linked to the papal estate, initiating the Cluniac reform. 120. **Anastasius III [911-913]** Elected with the support of Theodora and Marozia. The second period of the *pornocracy*. A puppet of the Theophylact family. The conversion of the Normans began during his papacy. 121. **Lando [913-914]** Elected with Theodora and Marozia's support. The third period of the *pornocracy*. Nothing significant is recorded. 122. **John X [914-928]** Fiscal agent for the Archbishop of Ravenna. The fourth period of the *pornocracy*. Favored by Theodora, widow of Theophylact, with whom he had relations. His main role was leading an army for the first time in history, supported by Alberic, to defeat the Saracens at the Battle of Garigliano [916] and permanently expel them. Berengar I was assassinated in 924, the last Emperor of the Holy Roman Empire. John appointed the five-year-old Hugh of Vermandois as Archbishop of Reims. He was murdered by Marozia's henchmen for being useless to her family's interests. 123. **Leo VI [928]** The fifth period of the *pornocracy*. No significant events are recorded. He was murdered on Marozia's orders. 124. **Stephen VII [928-931]** The sixth period of the *pornocracy*. He was murdered on Marozia's orders. 125. **John XI [931-935]** The seventh and final period of the *pornocracy*. An illegitimate son of Marozia, reportedly fathered by Alberic, Duke of Spoleto. Became Pope at age 20. Marozia erred by marrying Hugh, King of Italy, prompting a rebellion by her eldest son from her first marriage, Alberic II. He imprisoned his mother with the Pope's and his half-brother's support. John granted Cluny Abbey the power to include monastic houses following their rules. Abbot Hugh rose to prominence and is considered one of the greats in history. [^1]: *Pornocracy* is an Italian term meaning the government by courtesans or prostitutes. It first appeared in the writings of Cardinal Baronius, referring to a period in which two women wielded real power: Theodora, wife of the Roman senator Theophylact, and her daughter Marozia. This term has been used throughout history regardless of gender or sexual orientation. originally posted at https://stacker.news/items/753048
@ 0861144c:e68a1caf
2024-11-04 12:27:35These are the previous parts: [Part 1](https://stacker.news/items/735219)|[Part 2](https://stacker.news/items/736674)|[Part 3](https://stacker.news/items/738294)|[Part 4](https://stacker.news/items/739692)|[Part 5](https://stacker.news/items/743142)| [Part 6](https://stacker.news/items/744965)| [Part 7](https://stacker.news/items/746621)| [Part 8](https://stacker.news/items/748225)| [Part 9](https://stacker.news/items/749793) --- The papacy enters one of its darkest periods, not only marked by a series of medieval violence but also by the utter prostitution of power in scenarios so obscene that, by the time you finish reading, you may question the absolute sanctity of the pontificate. 111. **Formosus [891-896]** Consecrated as bishop by Nicholas [105]; he was a missionary whose main strength was encouraging Christians to combat paganism through letters. He supported the coronation of Arnulf of Carinthia, against the wishes of Charles the Bald (France), who had the favor of John VIII [107]; Guido of Spoleto was forced to crown his son Lambert as Emperor, while the Pope began talks with Arnulf. The Pope sought Arnulf's help to free Italy from the Spoletos. 112. **Boniface VI [896]** He suffered from gout when elected and died 15 days later. 113. **Stephen VI [896-897]** Elected with the support of the Emperor of the Holy Roman Empire and King of Italy, Lambert. This is one of the most shameful moments in the Church's history. In March 897, a posthumous trial was initiated against Formosus [111], during which Formosus' body was exhumed, dressed in papal vestments, given a defense lawyer, and put on trial. He was found guilty, his election as Pope invalidated, all his appointments and ordinations annulled, his body stripped of its vestments, and his remains thrown into the Tiber River. A few months later, following an earthquake, a mob took advantage of the chaos to assassinate the Pope, strangling him, presumably on the orders of the Spoletos in revenge for the trial known today as the *Cadaver Synod* or the *Synod of Horror*.  *This is a representation of the Cadaver Synod. Too strong for me. Jean-Paul Laurens (1870)* 114. **Romanus [897]** Seeing the chaos left by his predecessor, he began the process of rehabilitating Formosus [111] but died 90 days after assuming office. It is hypothesized that he was poisoned. 115. **Theodore II [897]** Held power for 20 days. His first order was to return Formosus' remains to St. Peter's Basilica and convened a synod that annulled all decisions from the *Synod of Horror*, declaring it void. Notably, Lambert of Spoleto's supporters wanted Count of Tusculum, Sergius, as Pope. Theodore was murdered, possibly by poisoning. 116. **John IX [898-900]** A Benedictine monk, elected with Lambert of Spoleto's support. He completed the work of his predecessor and, to avoid further violence, decreed that Papal Consecration must take place in the presence of the Emperor's representative. This reversed the *Constitutio Lotharii*. He also prohibited the tradition of looting bishops' palaces or papal palaces upon their death, declared Arnulf's consecration invalid, and granted all prerogatives to Lambert, his protector. The anti-Formosus faction wanted Sergius [119] as Pope but failed. The Theophylact family began tightening its grip on the papacy. 117. **Benedict IV [900-903]** Elected when the throne of the Holy Roman Empire was vacant. Lambert died in 899. Berengar I, King of Italy and grandson of Louis the Pious, claimed the imperial title, but the Pope granted it to Louis III the Blind, hoping he would defend against Hungarian invasions from the north and Saracens from the south. Louis was defeated by Berengar, blinded, and exiled. Lacking support, Benedict sought (a major error) support from the Theophylact family, including Theodora and her daughter Marozia, who would dominate the papacy henceforth. 118. **Leo V [903]** Elected Pope, little is known about his papacy. He was imprisoned and murdered 30 days after his election, likely by Pope Sergius III (his successor). Christopher the Priest declared himself Pope (antipope) but was also murdered, allegedly by Sergius III. 119. **Sergius III [904-911]** Linked to the Theophylact family and a supporter of the *Synod of Horror*, where he actively participated. He began the *pornocracy*[^1] period. He attempted to desecrate Formosus' tomb, without success. He married Alberic to Marozia, rumored to be the Pope's mistress. The Cluny Abbey was founded in 910 by William of Aquitaine and linked to the papal estate, initiating the Cluniac reform. 120. **Anastasius III [911-913]** Elected with the support of Theodora and Marozia. The second period of the *pornocracy*. A puppet of the Theophylact family. The conversion of the Normans began during his papacy. 121. **Lando [913-914]** Elected with Theodora and Marozia's support. The third period of the *pornocracy*. Nothing significant is recorded. 122. **John X [914-928]** Fiscal agent for the Archbishop of Ravenna. The fourth period of the *pornocracy*. Favored by Theodora, widow of Theophylact, with whom he had relations. His main role was leading an army for the first time in history, supported by Alberic, to defeat the Saracens at the Battle of Garigliano [916] and permanently expel them. Berengar I was assassinated in 924, the last Emperor of the Holy Roman Empire. John appointed the five-year-old Hugh of Vermandois as Archbishop of Reims. He was murdered by Marozia's henchmen for being useless to her family's interests. 123. **Leo VI [928]** The fifth period of the *pornocracy*. No significant events are recorded. He was murdered on Marozia's orders. 124. **Stephen VII [928-931]** The sixth period of the *pornocracy*. He was murdered on Marozia's orders. 125. **John XI [931-935]** The seventh and final period of the *pornocracy*. An illegitimate son of Marozia, reportedly fathered by Alberic, Duke of Spoleto. Became Pope at age 20. Marozia erred by marrying Hugh, King of Italy, prompting a rebellion by her eldest son from her first marriage, Alberic II. He imprisoned his mother with the Pope's and his half-brother's support. John granted Cluny Abbey the power to include monastic houses following their rules. Abbot Hugh rose to prominence and is considered one of the greats in history. [^1]: *Pornocracy* is an Italian term meaning the government by courtesans or prostitutes. It first appeared in the writings of Cardinal Baronius, referring to a period in which two women wielded real power: Theodora, wife of the Roman senator Theophylact, and her daughter Marozia. This term has been used throughout history regardless of gender or sexual orientation. originally posted at https://stacker.news/items/753048 @ 5d4b6c8d:8a1c1ee3
2024-11-04 02:05:22I just saw that Adam Silver is considering alternative formats for the NBA All-Star Game, in an effort to have something fans might actually enjoy watching. There are no details about what's under consideration, but this seems like a fun topic to speculate on. Personally, I'd like to see the game replaced with a 3x3 tournament. The same 24 players could be assigned to 8 teams and play a three round tournament of short games. I would also love a one on one tournament, but I know most of the best players would chicken out. What say you? originally posted at https://stacker.news/items/752728
@ 5d4b6c8d:8a1c1ee3
2024-11-04 02:05:22I just saw that Adam Silver is considering alternative formats for the NBA All-Star Game, in an effort to have something fans might actually enjoy watching. There are no details about what's under consideration, but this seems like a fun topic to speculate on. Personally, I'd like to see the game replaced with a 3x3 tournament. The same 24 players could be assigned to 8 teams and play a three round tournament of short games. I would also love a one on one tournament, but I know most of the best players would chicken out. What say you? originally posted at https://stacker.news/items/752728 @ fd208ee8:0fd927c1
2024-11-03 21:51:39## All memed out It finally happened. I think it was October 25th, at circa 18:45 in the evening. I was doomscrolling my Nostr feed, and kept seeing the same Bitcoin memes repeated over and over, by different people. They weren't even reposts, they were copy-pasted versions of the same image. A very funny image. Well, it was very funny last year... and the year before that... and probably the year before that, when it appeared on a different network. Because it's all just reposts, copy-pastes and rehashes of the Best of Bitcoin Twitter, just like the tiresome influencers, with their groupies and their Episode 498 of *Let's all eat a large chunk of lightly-burnt dead animal and count our stacks before jetting off to talk about how to save the poors by getting them to buy individual satoshis with money they don't have*.  ## I'm the poors your looking for It's all so tiresome. It has little bearing on the real world I see around me, where most people are thinking all day about 99 problems and Bitcoin ain't one.  Which is, of course, what the Bitcoin influencers would have you believe, is the reason that they're poor. What in the world could be more important, than thinking about Bitcoin? Why do these people not get with the program? Don't they know, that we are trying to save them?  Why are they worrying about OtherProblems? Don't they know that all OtherProblems can be fixed with Bitcoin? Really, if you just go back far enough, in any current, situational problem, you will discover that there was some slight, negative shift to the history record that involved soft money. It's the financial version of the Butterfly Effect.  That's why #BitcoinFixesThis. Bitcoin fixes everything, if you just think about it, for long enough. The same way that we all actually come out of Africa, supposedly, if you go back enough generations. So, coming out of Africa, now, as a Real Life Person in The Present is supposed to have no significance. What does someone from Cameroon know about Africa, that someone from Alaska doesn't? Both people come out of Africa, if you just think about it, for long enough.  And maybe that really is true. Maybe Bitcoin will eventually end all vice and crimes, save the planet, and we will all just hold hands and sing kumbaya all day, while waiting for the Singularity to upload us to Satoshi. ## Bitcoin envelope budgeting Or maybe it's not. Maybe it's just a really hard, digital money that incentivizes savings, functions as a reliable measure, and makes micropayments possible on a global scale. Those really are things that will help the poors, including myself. I can see it, already, when trying to organize pre-paid meetups or figure out what to do with our household's meager savings, when the stock market is looking particularly bubblicious.  But this is what I would consider Boring Bitcoin. Bitcoin home economics. Penny-pinching Bitcoin. Bitcoin for homemakers. How to use the Bitcoin envelope budgeting system to beat inflation by a margin of 13%. The actual use of Bitcoin as money, rather than as a mere investment gamble or hype machine. That's the part of Bitcoin that nobody seems to really talk about because it's incredibly practical, dull, and useful, and it can only be tested by -- Oh, the horror! -- actually spending Bitcoin. But... perhaps I will begin talking about it. Perhaps those of us, Bitcoiners, who are having fun staying poor, while stacking sats, should speak up a bit more. Perhaps the boring stuff is actually the interesting stuff. Perhaps there is more to say about Bitcoin, than can fit into a meme.
@ fd208ee8:0fd927c1
2024-11-03 21:51:39## All memed out It finally happened. I think it was October 25th, at circa 18:45 in the evening. I was doomscrolling my Nostr feed, and kept seeing the same Bitcoin memes repeated over and over, by different people. They weren't even reposts, they were copy-pasted versions of the same image. A very funny image. Well, it was very funny last year... and the year before that... and probably the year before that, when it appeared on a different network. Because it's all just reposts, copy-pastes and rehashes of the Best of Bitcoin Twitter, just like the tiresome influencers, with their groupies and their Episode 498 of *Let's all eat a large chunk of lightly-burnt dead animal and count our stacks before jetting off to talk about how to save the poors by getting them to buy individual satoshis with money they don't have*.  ## I'm the poors your looking for It's all so tiresome. It has little bearing on the real world I see around me, where most people are thinking all day about 99 problems and Bitcoin ain't one.  Which is, of course, what the Bitcoin influencers would have you believe, is the reason that they're poor. What in the world could be more important, than thinking about Bitcoin? Why do these people not get with the program? Don't they know, that we are trying to save them?  Why are they worrying about OtherProblems? Don't they know that all OtherProblems can be fixed with Bitcoin? Really, if you just go back far enough, in any current, situational problem, you will discover that there was some slight, negative shift to the history record that involved soft money. It's the financial version of the Butterfly Effect.  That's why #BitcoinFixesThis. Bitcoin fixes everything, if you just think about it, for long enough. The same way that we all actually come out of Africa, supposedly, if you go back enough generations. So, coming out of Africa, now, as a Real Life Person in The Present is supposed to have no significance. What does someone from Cameroon know about Africa, that someone from Alaska doesn't? Both people come out of Africa, if you just think about it, for long enough.  And maybe that really is true. Maybe Bitcoin will eventually end all vice and crimes, save the planet, and we will all just hold hands and sing kumbaya all day, while waiting for the Singularity to upload us to Satoshi. ## Bitcoin envelope budgeting Or maybe it's not. Maybe it's just a really hard, digital money that incentivizes savings, functions as a reliable measure, and makes micropayments possible on a global scale. Those really are things that will help the poors, including myself. I can see it, already, when trying to organize pre-paid meetups or figure out what to do with our household's meager savings, when the stock market is looking particularly bubblicious.  But this is what I would consider Boring Bitcoin. Bitcoin home economics. Penny-pinching Bitcoin. Bitcoin for homemakers. How to use the Bitcoin envelope budgeting system to beat inflation by a margin of 13%. The actual use of Bitcoin as money, rather than as a mere investment gamble or hype machine. That's the part of Bitcoin that nobody seems to really talk about because it's incredibly practical, dull, and useful, and it can only be tested by -- Oh, the horror! -- actually spending Bitcoin. But... perhaps I will begin talking about it. Perhaps those of us, Bitcoiners, who are having fun staying poor, while stacking sats, should speak up a bit more. Perhaps the boring stuff is actually the interesting stuff. Perhaps there is more to say about Bitcoin, than can fit into a meme. @ c11cf5f8:4928464d
2024-11-03 09:21:30Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/741746/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/751696
@ c11cf5f8:4928464d
2024-11-03 09:21:30Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/741746/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/751696 @ 57d1a264:69f1fee1
2024-11-02 18:12:56If'd have to make a list of functionalities that you miss from the current Ui, what it would be? Signup with nostr https://gitworkshop.dev Below the current screens, compared with Github: # Landing ||| |---|---| |  |  | # Explore Repos ||| |---|---| |  |  | # Profile ||| |---|---| |  |  | # Repo ||| |---|---| |  |  | # Issues ||| |---|---| |  |  | #NostrDesign #BitcoinDesign #Bitcoin #Nostr #Design originally posted at https://stacker.news/items/751209
@ 57d1a264:69f1fee1
2024-11-02 18:12:56If'd have to make a list of functionalities that you miss from the current Ui, what it would be? Signup with nostr https://gitworkshop.dev Below the current screens, compared with Github: # Landing ||| |---|---| |  |  | # Explore Repos ||| |---|---| |  |  | # Profile ||| |---|---| |  |  | # Repo ||| |---|---| |  |  | # Issues ||| |---|---| |  |  | #NostrDesign #BitcoinDesign #Bitcoin #Nostr #Design originally posted at https://stacker.news/items/751209 @ 5d4b6c8d:8a1c1ee3
2024-11-02 15:47:53We're back with a new name (that @grayruby hates it)! Last year's [NBA In-Season Tournament Survivor Pool](https://stacker.news/items/340815/r/Undisciplined) was a lot of fun and @POTUS walked away with 27k sats when the Pacers won the tournament. # Emirates Cup Details The tournament has four Group Play rounds, followed by three Knockout rounds. The Group Play rounds are played every Tuesday from Nov. 12th to Dec. 3rd. Every team in the NBA is randomly assigned to one of the groups. This is three games fewer than last year. The Knockout rounds are a single elimination tournament between the eight best teams from the Group Play rounds. The first round will be played on Dec. 10th and 11th. The second round will be played on Dec. 14th. The final round will be played on Dec. 17th. # Survivor Pool Details - The survivor pool will have a 3k buy-in and a 5k second buy-in, for those who need it. - The second buy-in can only be used prior to the Knockout Rounds. - That means the pool is starting with at least 5k in prize money (8k if I miss a pick). - Any sats zapped to survivor pool contest posts on SN or to my comments on those posts will be added to the buy-ins to make up the final prize (no sybil fee deductions) - You can only pick each team once, so be careful not to use up the eventual contenders too early. - If you forget to make a pick, I'll assign you whichever team has the worst odds for that round that you are still allowed to pick. - In the event of a tie, the winner will be determined by whoever correctly predicts the Cup MVP first. If no one correctly predicts the cup MVP, then the winner will be decided by whoever most closely predicts the pointspread of the championship game. - Posts for each round will go up the day after the previous round and selections can be made up until tip-off of the team you're selecting. Leave a comment if you're interested in joining and I'll reply with a comment for you to zap your initial buy-in to. cc last year's participants: @grayruby, @POTUS, @gnilma, @elnosh, @Wumbo, @BTC_Bellzer, @siggy47, @Chep, @BlokchainB originally posted at https://stacker.news/items/751054
@ 5d4b6c8d:8a1c1ee3
2024-11-02 15:47:53We're back with a new name (that @grayruby hates it)! Last year's [NBA In-Season Tournament Survivor Pool](https://stacker.news/items/340815/r/Undisciplined) was a lot of fun and @POTUS walked away with 27k sats when the Pacers won the tournament. # Emirates Cup Details The tournament has four Group Play rounds, followed by three Knockout rounds. The Group Play rounds are played every Tuesday from Nov. 12th to Dec. 3rd. Every team in the NBA is randomly assigned to one of the groups. This is three games fewer than last year. The Knockout rounds are a single elimination tournament between the eight best teams from the Group Play rounds. The first round will be played on Dec. 10th and 11th. The second round will be played on Dec. 14th. The final round will be played on Dec. 17th. # Survivor Pool Details - The survivor pool will have a 3k buy-in and a 5k second buy-in, for those who need it. - The second buy-in can only be used prior to the Knockout Rounds. - That means the pool is starting with at least 5k in prize money (8k if I miss a pick). - Any sats zapped to survivor pool contest posts on SN or to my comments on those posts will be added to the buy-ins to make up the final prize (no sybil fee deductions) - You can only pick each team once, so be careful not to use up the eventual contenders too early. - If you forget to make a pick, I'll assign you whichever team has the worst odds for that round that you are still allowed to pick. - In the event of a tie, the winner will be determined by whoever correctly predicts the Cup MVP first. If no one correctly predicts the cup MVP, then the winner will be decided by whoever most closely predicts the pointspread of the championship game. - Posts for each round will go up the day after the previous round and selections can be made up until tip-off of the team you're selecting. Leave a comment if you're interested in joining and I'll reply with a comment for you to zap your initial buy-in to. cc last year's participants: @grayruby, @POTUS, @gnilma, @elnosh, @Wumbo, @BTC_Bellzer, @siggy47, @Chep, @BlokchainB originally posted at https://stacker.news/items/751054 @ acc925af:db9fb0bb
2024-11-02 15:47:14https://open.spotify.com/track/02ppMPbg1OtEdHgoPqoqju?si=d6518df327eb46ee originally posted at https://stacker.news/items/751017
@ acc925af:db9fb0bb
2024-11-02 15:47:14https://open.spotify.com/track/02ppMPbg1OtEdHgoPqoqju?si=d6518df327eb46ee originally posted at https://stacker.news/items/751017 @ acc925af:db9fb0bb
2024-11-02 15:46:18https://open.spotify.com/track/6ttYF5VadzTssGV2i1Q08T?si=1fc0f37b2bf04be2 Need a soothing song to relax?, look no further originally posted at https://stacker.news/items/750993
@ acc925af:db9fb0bb
2024-11-02 15:46:18https://open.spotify.com/track/6ttYF5VadzTssGV2i1Q08T?si=1fc0f37b2bf04be2 Need a soothing song to relax?, look no further originally posted at https://stacker.news/items/750993 @ 5d4b6c8d:8a1c1ee3
2024-11-02 14:24:23Mornin' Stackers, Here are our proposed topics for today's episode: Contests - Wrapping up the MLB Pool - Update on NFL Pool - Introducing the Cricket Pools - Previewing NBA Emirates Cup Pool and College Football Playoff Contest Posts - Guess my favorite pitcher - Stacker grudge match - The future of Juan Soto Sports - World Series recap - NFL Trade Deadline - NBA early season thoughts Gamblin' - Betting on sports futures using lightning Share your takes, be they hot, medium, or mild, and we'll try to fit them in. Stacker Sports Pod is for stackers by stackers. originally posted at https://stacker.news/items/750965
@ 5d4b6c8d:8a1c1ee3
2024-11-02 14:24:23Mornin' Stackers, Here are our proposed topics for today's episode: Contests - Wrapping up the MLB Pool - Update on NFL Pool - Introducing the Cricket Pools - Previewing NBA Emirates Cup Pool and College Football Playoff Contest Posts - Guess my favorite pitcher - Stacker grudge match - The future of Juan Soto Sports - World Series recap - NFL Trade Deadline - NBA early season thoughts Gamblin' - Betting on sports futures using lightning Share your takes, be they hot, medium, or mild, and we'll try to fit them in. Stacker Sports Pod is for stackers by stackers. originally posted at https://stacker.news/items/750965 @ 188302bb:9052db11
2024-11-02 11:59:46I'm considering building an application specifically designed for use by insurance companies and banks. Before diving into development, I'd like to validate the idea to ensure it addresses real needs in the industry. What steps should I take to effectively validate the concept, assess market demand, and gather feedback from potential users? Should I conduct interviews, use surveys, or create a prototype to present to stakeholders? Additionally, what are the key metrics or indicators that would confirm this app idea has strong potential before I start coding? originally posted at https://stacker.news/items/750765
@ 188302bb:9052db11
2024-11-02 11:59:46I'm considering building an application specifically designed for use by insurance companies and banks. Before diving into development, I'd like to validate the idea to ensure it addresses real needs in the industry. What steps should I take to effectively validate the concept, assess market demand, and gather feedback from potential users? Should I conduct interviews, use surveys, or create a prototype to present to stakeholders? Additionally, what are the key metrics or indicators that would confirm this app idea has strong potential before I start coding? originally posted at https://stacker.news/items/750765 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集: --- 免责申明: 在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。 | 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) | ` 持续更新。。。` --- ### 推广: 访问不了openai,去`低调云`购买VPN。 官网:https://didiaocloud.xyz 邀请码:`w9AjVJit` 价格低至1元。
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集: --- 免责申明: 在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。 | 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | [官网](https://aihubmix.com?aff=mPS7) | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | [官网](https://openai-hk.com/?i=45878) | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | [官网](https://www.closeai-asia.com/) | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | [官网](https://www.openai-sb.com/) | ` 持续更新。。。` --- ### 推广: 访问不了openai,去`低调云`购买VPN。 官网:https://didiaocloud.xyz 邀请码:`w9AjVJit` 价格低至1元。